#System File Checker
Explore tagged Tumblr posts
Text
ClanGen Resources Masterpost
Something not so cool is that you can really only find the majority of our resources via our Discord server, and that's frustrating and exclusionary. We get it! To help bridge that gap, Fable and Chibi have put together a list of our most useful resources.
This will be kept updated and maintained for all our friends on Tumblr, we hope folks find this helpful! All of these resources are made by the amazing members of our community. Thank you all for loving our game!
Download Guides
Image Heavy ☆ No Images ☆ Screenreader Friendly Our official guides for how to download the games. Look here if you need a helping hand!
Amaa's/Selkirks' Text Guide
Stable Release ☆ Development Version These guides are meant for save-file editing, giving you a quick resource to refer to when you want to change things about your cats! Amaa no longer works on this sheet, but Selkirks has taken over!
Kenz's Visual Sprite Guide
Stable Release ☆ Development Version Ever wondered what a sienna masked tabby looked like? Wanted to know just how many white patches there truly are? Look no further than here!
Cere's Tortie Guide
☆ Link ☆ Coding in a tortoiseshell or calico can be frustrating. This concise, easy-to-follow guide goes over how to do it, complete with examples!
Cere's Conditions List & Scribble's Conditions Guide
Cere's List ☆ Scribble's Guide These two guides go hand-in-hand (or... paw-in-paw?) to walk you through editing in conditions for your cats!
Acorn's Inheritance Guide
☆ Link ☆ Have you ever wondered just how ClanGen determines what a litter of kittens might look like? How in-depth IS our genetics system, anyways?! The wonderful Acorn will walk you through it here!
blackkat's Wildcard Tortie Checker
☆ Link ☆ This spreadsheet helps determine whether or not a tortoiseshell cat is a wildcard or not! Not sure what a wildcard is? See here!
Citrus' Clan Organizer
☆ Link ☆ A beautiful spreadsheet that helps track and organize your ClanGen Clans, for those who enjoy things like that!
Various Tumblr Resources
What can I expect, joining the Discord? I want to have the day-time backgrounds, but on dark mode! How are the allegiances formatted, if i want to write my own?
1K notes
·
View notes
Text
🌆 Chapter 5 : The Neighborhood Download 🏘️
It's a big post, please read carefully ...

🥂 It's FINALLY here, the long-awaited neighborhood download post ! You'll finally be able to explore this new map yourself, add your Sims, and play fantastic brand new...old stories. However, depending on the neighborhood you want to download, you'll need to make sure you've already downloaded and installed the necessary custom content from the lots you need ! To speed things up, the "chapter" posts offer direct access to the entire download folder for the area in question (e.g. "Chapter 1" proposes the lots from Neighborhood 1 etc.)
🌃 All the neighborhood have been cleaned with Hood Checker and completely empty of all their sims (in folder, and in the neighborhood file with SimPE). The Neighborhoods with lots have 🇫🇷 FRENCH and 🇬��� ENGLISH texts for every lot titles and descriptions from the original SIMS 1 descriptions.

🌇 NEEDED NEIGHBORHOOD DECO
Redbud Tree CUSTOM version by @suratan-zir Age of Empire 3 Trees conversion by @haut-gothique Dead Trees by @mustluvcatz-reloaded Placeable Cliffs by @greatcheesecakepersona Nessie the Plesiosaur by Psychosims The Neighborhood Fog by @jodeliejodelie The Waterfall by Numenor The Osara Wood Bridge by @simborg The Wood pier fragment by @criquette-was-here on MTS Busy Road Vehicle Set by @criquette-was-here (Police car ; Garland Bubalina Tractor ; Semi-trailers ; flatbed loaded) The Bus stop and Post by @criquette-was-here Rural Road Charm’s Asphalt Tarmac Pieces by @criquette-was-here Those Telegraph Poles by @criquette-was-here The Fence & Hedge set by @criquette-was-here Smuggled Deco's Giant FS13 Harvester by @criquette-was-here Railway Tunnel Portal from Feverfew by @criquette-was-here Railway Tunnels by @criquette-was-here on MTS Street Lights Set by @criquette-was-here 4t2 Street Lights by @beautifulnerdkitty Building by @ethanmcgregor (can't find name ; begin by “fixed”) The Blue Water Tower by @funphumph Smallest Maxis Watertank by Psychosims 4t2 Stone Wall A by @lordcrumps 4t2 Dirty Long Road by @leoz94 (ts4dirtyroad1 ; ts4dirtyroadlong ; ts4dirtyroadpovorot1 ; ts4dirtyroadpovorot2) 3t2 Old Mill by @hafiseazale MagicTown default replacement for Maxis Bimp by @shastakiss 🌉 You will NEED BRIDGES for the neighborhood, but the choice of the bridges depend on which roads you are using. 🔹IF you are using MAXIS roads, you need these bridges (and you will have to place them yourself on the completely remade neighborhood) 🔸IF you are using @criquette-was-here's Rural Charms Roads like me, you will need her Unified Brigdes

🏞️ OPTIONAL NEIGHBORHOOD DECO
Skyboxes by @dramallamadingdang (I use Mixed Clouds) Skylines by @greatcheesecakepersonna (I use Green Hills)


🌲 DEFAULT REPLACEMENT PINES
You can chose to keep the Maxis ones or use one of those :
Neighborhood Pine Forest Defaults by @teaaddictyt , @lowedeus and @shastakiss My Darker Recolor of the previous set : SFS - Mediafire (it's the version used on my pictures, obviously) Tree Clump recolors by @jodeliejodelie



☑️ CHECK LIST
💾 Did you make a backup of your Sims2 folder ? 🌁 What neighborhood do you want and how to install it ? ⚒️ Did you check the master meshes post ? installed everything ? 🏘️ Did you installed all the needed lots and their CC ? 🌲 Did you install the neighborhood decorations from this post ? 🙏 Did you send a prayer to the Gamer's Gardian Angel ? 🦑 Did you exorcised the Pink Soup out of your PC ? ✅ Then you're ready to GO !
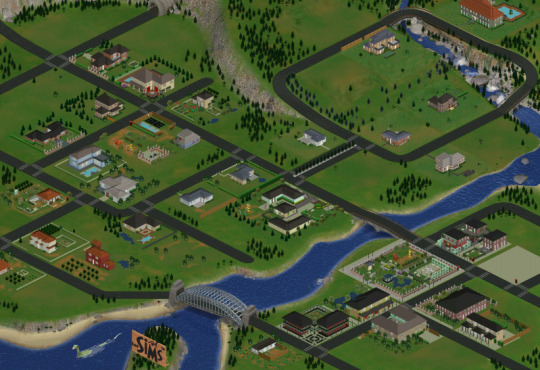


🎁 DOWNLOAD OPTIONS
The Empty one is... empty of lots, It's just my remade version off Kalisa's map. I had to change it to create MagicTown, changed the roads with SimPE and decorated the hood. The second option, is an edited neighborhood with only the MagicTown addition, all the OldTown and Downtown lots are Kalisa's CC free ones. It allows you to have less CC to install because you will need only the MagicTown related ones. That's why I had a flag system on my master meshes post . And finally, the entirely remade neighborhood has all my made and remade lot and need ALL the CC from the lots and the master-meshes post.
🟥 MAIN Empty Hood : SFS - Mediafire 🟧 MAIN MagicTown + Kalisa's OldTown : SFS - Mediafire 🟨 MAIN Entirely Remade : SFS - Mediafire 🟩 SUB Empty Hood : SFS - Mediafire 🟦 SUB MagicTown + Kalisa's OldTown : SFS - Mediafire 🟪 SUB Entirely Remade : SFS - Mediafire
To install the MAIN HOODS, you have to put the neighborhood folder in your TS2 document folder : .../My Documents/(Your Sims 2 folder)/Neighborhoods/ To Install the SUB HOODS, you have to put the neighborhood folder in your TS2 "Open for Business" installation folder : (Your TS2 Installation repertory).../EP3/TSData/Res/Neighborhood Templates/



🏘️ ★ 🛠️ ★ 🏡 ★🧍★ 👫 The TS1 Sims Neighborhood is on its way...
#sims 2#sims 2 download#sims 2 lots#sims 2 build#ts1t2 lot download#sims 2 custom content#sims 2 custom hood#ts2 lots#ts2 build#ts2#ts2 simblr#sims 2 neighborhood#ts1t2 neighborhood download#1t2#ts1t2 neighborhood project
105 notes
·
View notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
thinking of moving all of my writing to obsidian. so far I used notion for very broad planning (usually core concepts, which projects I'd be working on next, and overview of what my wip v finished list looked like), obsidian for detailed drafts and outlines of each project, and then microsoft word for actually writing
pros of putting it all into the same place:
won't need to rely on microsoft
won't need to rely on internet at all (obsidian is stored completely locally; notion and word are too but have a not unsignificant amount of cloud/synching features)
obsidian supports HTML, so no more testing HTML on AO3 specifically, and no more ugly < i > in the middle of my texts
it would force me to go through literally every single thing I have ever written and organize it properly, from scratch
probably has better organization capabilities than just windows file explorer, lol
cons of putting it all into the same place:
it will all be stored locally, on my hard drive. I'll need to remember to back it up regularly in, you guessed it, microsoft's cloud in case something happens to said hard drive
no spell checker. Im not a native speaker, and word's spell checker has taught me a lot. I don't know if it's enough to write completely on my own. might be able to find a spell checker that works with obsidian, though at low level research I came up with nothing
I have a lot of projects, and it might get too convoluted. could probably rectify this by putting enough effort into a tagging and organizational system
I don't actually know what it would be like to write full length chapters in obsidian on top of planning in obsidian. but I guess this one I would just learn with time
5 notes
·
View notes
Note
hi pinka 🤍 May I know your pc type & specifications? I’m dealing with pink soup on a windows 11 laptop so I’m curious! I’m thinking I may downgrade to an older system to run the game better. I have so much cc I can’t give it up 🙈
Hi there ♡
HP Pavillion x360 Convertible Windows 11 11th Gen Intel(R) Core(TM) i5-1155G7 @ 2.50GHz 2.50 GHz Graphic Card: Intel Iris Xe Graphics RAM: 16,0 GB
Downloads folder: 23gb
Pink flashing seems to be a tricky issue, but it has only happened to me twice and both times it was due to several high poly hairs. I don't know if it's because of that but I associate it with hair texture as I play with high poly objects and I have no issues. Try playing with low/medium or only with some high poly hairs... and see if that might be the problem with your game.
You probably already know most of them, but here are a few tips to keep your game as stable as possible:
Install graphic rules and 4gb patch
Run Delphy's Organizer to delete duplicate files
Compress your cc
Run Hood Checker
Disable neighbourhood decoration
Load the game in an empty hood and on an empty lot
I hope you get it fixed soon!
15 notes
·
View notes
Text
dbh-adjacent writing-program nonsense under the cut, a.k.a. let's talk a bit about WriteMonkey 3
I've used WriteMonkey 2 and 3 on and off for. hm. I guess it's gotta be eight or nine years now? but those instances of use have always been erratic and short lived, and I've usually returned to either Scrivener or, more frequently for many reasons, MS Word. (I also did just a ton of first-draft writing in discord back when I had an account and c/ped my writing from there into Word. near-peerless syncing between devices, appalling security practices. what can ya do 🙃)
anyway, due to ~circumstances~ I've switched to writing on a computer that isn't my writing program–filled work laptop, and so I've been experimenting with WM3 again because it's super lightweight due to plaintext markdown instead of rich text and I have a license key for it, which = fun plugins. it's also way less complicated and labor intensive to set up per project and use than, say, Scrivener. I love Scrivener! but scriv can be overwhelming and distracting when all I want to do is write, especially if I want a unique, quick-to-set-up theme (and I always do, because Aesthetic Is Everything), which is one of the reasons WM3 is so handy

in addition to the gorgeous stripped-down UI that showcases whatever background I choose (mine can be found here!), WM3 has some really neat little plugins? I don't actually use the word-frequency checker myself, but WM3's shows you where each word appears in the document via the little indicator bars to the right of the word, which. rad! (you can tell at a glance which chapters are written in whose POV based off name usage alone and I think that's neat.) also, when you click on a given word in the frequency list, it'll highlight that word throughout the document and also display all uses of it vertically over the scroll bar path. lots of nice little visual indicators of what's going on. I just really like the design, it's simple but extremely useful and intuitive
admittedly, Scrivener cannot be beat when it comes to how easily you're able to make notes in it due to its multitude of note-taking locations, plus it has internal splitscreen capabilities that make referencing a second document a breeze, so there's definitely a mental transition involved when it comes to WM3 and its single-document-at-a-time system, on top of switching to markdown-style comments/reminders. that said! being able to not only see those comments below the headings in the left-hand sidebar but also jump to them when they're clicked? stellar 10/10 would use again
finally, the repository. I <3 the repository. being able to quickly toss whatever text I'm not quite ready to delete or info I know I'll want to reference at some point in the future into the repository is great. it's a seamless process, only a couple seconds' worth of effort required, allowing my focus to stay on what I'm writing instead of distracting myself by tabbing my way through various open files to find my notes. plus the repository is searchable(!!!!!), and using it also keeps the actual text editor clean visually, especially since the right-hand sidebar can be hidden too:

hm! possibly that is a sneak preview of chapter one! who can say!
so yeah! if you're looking for a stripped-down, highly customizable, portable writing program, I absolutely recommend it. there are downsides, of course, the biggest one being no official WM3 mobile options available at present, but since the program is both portable and plaintext, you can toss it into a syncing service and access it via your handheld devices that way. it's also not open source, and you need to pay to access the truly useful plugin features. with all that said, if you don't mind fiddling around with some CSS to make everything look juuuuuuuuust right, you can get yourself a really snazzy setup with relatively little effort. but maybe that's just me—aesthetic is king and all that
9 notes
·
View notes
Text
Pixilation edit of stopmotion.
So, what happened is that we didn’t just use stop motion, but also incorporated different close-ups and some video footage of a book falling.
At first, I planned to transport everything as frames, thinking I could just copy and paste motions—that way, I’d have full control over each frame. It was definitely more time-consuming, and my professor mentioned that I could have done it in Premiere Pro just by extending the length of a selected clip.
But the thing is... I have no idea how to use Premiere Pro.
I assumed it would be similar to other editing software I’ve used, like Kinemaster, Clip Studio, Cute Cut, CapCut, Clipmaker—but sadly, it was a bit more complicated and advanced than that. I also couldn’t figure out the shortcuts (they’ll come back into the story later).
So, after discussing with my professor, I exported all my frames as a video file—which took some time (and a lot of Googling).
Next came the editing phase—clipping everything together and adding visual language for the characters (Jules and Ighor).
I wanted to go for a comic-style look, with dotted shadow effects, checkers, and contrasting colors as an isolation technique in animation to make certain elements stand out.
Insiperd by my favourite artist: https://youtu.be/NF1FboliEKg?si=BZ4Q2lVSUxN9Lm4h
(chip)
youtube
(nighligthfish)
You can see how much contrast they both use—it really resonates with me, and I believe it intensifies the emotion and captivates human attention.

After a few hours of trying to figure out how to make this star stand out... I realized it’s actually really hard to find any tutorials for it.
And just when I was happily editing—my system crashed. :D
I seem to have a lucky streak of Adobe programs crashing. The worst part? My progress wasn't autosaved, and I couldn’t retrieve my files. So, I had to redo everything—the light contrast, adding tint, and additional effects for the footage. That completely drained me.
Later on, I started recording some sounds that I wanted to incorporate into the video—not just music, but also ambient sounds and effects to add more depth.


I used Audacity since I’m most familiar with it, and honestly, I couldn’t handle another crash wiping out all my work T-T.
I recorded all the sounds as one big track, then handpicked and sliced the audio, exporting each separate track as a new file. Of course, I had to tweak the audio settings to make it more engaging and pleasing to the ear.
(my last save before the crash)
1 note
·
View note
Text
Missing EAxis Object...
So. I run a *very* heavy CC system, to the extent that I will start loading TS2 and then walk away, make dinner and come back half an hour later as the main menu finally loads. This obviously means I have a *massive* aversion to anything that requires me to load the game multiple times to diagnose an issue. So, my question for the all-knowing overlords of Tumblr is this: Is there a better way to identify a problem object that is overwriting an EA object in game than the binary-sort system where you unload 50%s of CC, load, then 25%s etc until you identify the problem file? I've tried loading my conflicts checker, but that's not pulling up anything in that area (it's the base game crib used in the Broke trailer which has vanished completely from my catalogue) If I have to binary sort, I will, but I'm open to better suggestions! ... Also, SimPE won't load for me, no idea why, so if your solution requires that, it may need a deeper layer of problem fixing...
2 notes
·
View notes
Text
hi i have a new texture pack








Mods visible in screenshots are Mod Menu ( - the mods option) and Appleskin ( - the checkered pattern behind the hunger bar). Texture pack used for clear water is here
Link to download here
If you have any feedback on it pls tell me (even if its just based off the screenshots here)
Im also not planning on a bedrock port bc im lazy and its a different file system for these
#leaf's posts#leaf's packs#minecraft#mineblr#minecraft resource pack#minecraft texture pack#minecraft resourcepack#minecraft texturepack#minecraft java
8 notes
·
View notes
Note
You can also try running the system file checker and dism tool! in command prompt do "sfc /scannow" and then when its done do "DISM /Online /Cleanup-Image /RestoreHealth"

i'm so sure there is your honor
#✨#Anonymous#not art#(( basil 🧲 any ))#fuckin windows ~~98~~ 10 get bill gates in here#anyway brb gotta get an update ig
3 notes
·
View notes
Text
Version 554
youtube
windows
zip
exe
macOS
app
linux
tar.zst
I had an excellent week. Some important bugs are fixed, and we have some basic support for CBZ and Ugoira files.
full changelog
bugs
I screwed up two important calls last week, in fixed-period checker timers and job statuses. If you had watchers not start, subscriptions with incorrect check times, and/or popup messages that threw display errors or wouldn't auto-dismiss, I am sorry! I didn't plan the changes here properly, and several things slipped through my tests.
All the affected systems have been given proper rework this week and have some unit tests to make sure this doesn't happen again. Please let me know if you still have any problems.
animations
I fixed up more of the 'while checking for transparency, this file produced x error!' issues. Checking GIFs for transparency should be a bit faster and more fault tolerant too, now.
Also, the native GIF renderer has much improved transparency support. The multilayered 'noclip' artifacts should be gone, and damaged GIFs will recover better. GIFs also now get thumbnails that are x% in with proper transparency.
Also, APNGs now get transparency: when rendering in the native renderer; in their thumbnails (which are also now x% in); and for 'has transparency' checks.
CBZ and Ugoira
I am adding basic recognition and thumbnails for these filetypes today. Behind the scenes, both formats are essentially just zips with a list of images, so all your zips will be scanned, and if they look like a CBZ or Ugoira, their filetype will change and they will get a thumbnail. Ugoira thumbnails will be x% in, like for other video.
Also, a user is working on true Ugoira rendering now, so I hope we will be able to finally roll this out in the medium term.
Unfortunately, neither format has a particularly definitive/unique specification, so while I have tried to be careful, my tests here are imperfect. We can expect a few incorrect determinations one way or the other. If you get an outrageous false positive or false negative here (e.g. something you know is a Ugoira that stays as a ZIP, or a ZIP of misc files that detects as a CBZ), please send in the details, and I'll see if I can tweak my tests.
next week
I put in extra time this week to figure out CBZ, so I'll let things breathe and just catch up on simple, small work. I have a bunch of interesting quality of life UI items in my immediate todo, so I'll probably focus on that!
2 notes
·
View notes
Text
Search Engine Optmization
Search Engine Optimization (SEO)
HOW SEARCH ENGINE WORKS?
CRAWLING- Crawler/Bots/Spider search the data and scan the data from the server / Internet / web.
INDEXING- Indexing is to store data in search engine data base centre.
RANKING- Ranking is to show the result and give them ranking.
Techniques of SEO
White Hat SEO- It refers to any practice that improve your search ranking without breaking search engine guidelines.
Black Hat SEO- It refers to increase a site ranking by breaking search engine terms and services.
Black Hat SEO Types
Cloaking- It is the method of presenting users content that is different from search engine crawlers.
Content Hiding- This is done by same text colour as the background to improve ranking.
Sneaky URL Redirection- Door way pages are proper site that redirect to different page without their knowledge.
Keyword Stuffing- Practice of filling content with repetitive keyword in an attempt to rank on search engine.
Duplicate Content- It means to copy content from other website.
WHAT IS WEBSITE?
Domain- Domain is a simply name of the company.
Hosting- Hosting is a space or storage on server where we can store website.
Dealers of Domain and Hosting
GoDaddy
Hosting Raja
Hostinger
Blue Host
Name Cheap
WHAT IS SSL?
SSL Stands for Secure Socket Layer It is a technology for keeping an internet connection secure and sensitive data that is being sent between two system preventing criminals from reading and modifying any information transferred including personal details.
WHAT IS URL AND SUB DOMAIN?
URL- Uniform Resource Locater
Sub Domain- www,web,apps,m
KEYWORDS- Any query search in search box is known as keyword.
TYPES OF KEYWORD
Generic Keyword- It is used for brand name or general keyword it helps to balance your generic keywords to capture wide range of customer. Only one word is used.
Short Tail Keyword- These keywords are phase of two or three words.
Long Tail Keyword- Specific Keyword phase consisting more than three words.
Seasonal Keyword- These Keyword generate most of their search traffic during a specific time of the year.
GOOGLE SANDBOX EFFECT
It is a observation period done by the google to check whether your site is having any technical issues, fraud, scam and user interaction towards website.
SERP
Search Engine Result Page appears after some search something in the search box.
HTML
Hyper Text Markup Language
META TAG OPTIMIZATION
Title Tag- Digital Marketing
Meta tag- content=………….150 to 170 characters
FTP TOOLS
Core FTP
Filezilla
INDEXING AND CRAWLING STATUS
Indexing Status- Status which shows exactly when the site is stored in data base centre.
Crawling Status- Status which gives information about recent crawling of our website. eg. site:abc.com.
KEYWORD PROXMITY
It refers to distance between keywords.
Keyword Mapping
It is the process of assigning or mapping keywords to a specific pages of a website based on keyword.
IMAGE OPTIMIZATION
ALT Tag- It is used for naming images also known as alt attribute
<img src=”digital.png”alt=”name/keyword>
Image compressing-The process of reducing image size to lower the load time.
Eg. Pingdom- To check load time.
Optimzilla- To compress image.
Robot.txt
It is a file in which instructions are given to the crawler how to crawl or index the web page it is mainly used for pages like privacy policy and terms and conditions.
Robots meta Tag
They are piece of core that provide crawlers instruction for how to crawl or index the content. We put this tag in head section of each page it is also called as no index tag.
<meta name=”robots”content=”nofollow,noindex……………../>
SITE MAPS
It is list of pages of website accessible to crawler or a user.
XML site map- Extensible Markup Language is specially written for search engine bots.
HTML site map- It delivers to user to find a page on your website.
XML sitemap generator
CONTENT OPTIMIZATION
Content should be quality content (grammarly)
Content should be 100% unique (plagiarism checker)
Content should be atleast 600-700 words in web page.
Include all important keyword.
BOLD AND ITALIC
<b>Digital Marketing</b> <strong>……………</strong>
<i>Digital Marketing</i> <em>………………</em>
HEAD TAGGING
<h1>………..</h1> <h5>…………</h5>
<h2>………..</h2> <h6>………..</h6>
<h3>…………</h3>
<h4>…………</h4>
DOMAIN AUTHORITY(DA)
It is a search engine ranking score developed by moz that predict how website rank on SERP.
PAGE AUTHORITY(PA)
It is a score developed by moz that predict how well page will rank om SERP.
TOOL- PADA checker
ERROR 404
Page not found
URL is missing
URL is corrupt
URL wrong (miss spilt)
ERROR 301 AND 302
301 is for permanent redirection
302 is for temporary redirection
CANONICAL LINKS
Canonical Links are the links with same domain but different URL it is a html element that helps web master to prevent duplicate issues in seo by specifying canonical version of web page.
<link ref=”canonical”href=https://abc.com/>
URL STRUCTURE AND RENAMING
No capital letters 5. Use important keyword
Don’t use space 6. Use small letters
No special character
Don’t include numbers
ANCHOR TEXT
It is a click able text in the hyperlink it is exact match if include keyword that is being linked to the text.
<a href=”https://abc.com”>Digital Marketing</a>
PRE AND POST WEBSITE ANALYSIS
PRE- Domain suggestions and call to action button
POST- To check if everything is working properly
SOME SEO TOOLS
SEO AUDIT AND WEBSITE ANALYSIS
SEOptimer
SEO site checkup
Woorank
COMPITITOR ANALYSIS AND WEBSITE ANALYSIS
K-meta
Spyfu
Semrush
CHECK BACKLINKS
Backlinks watch
Majestic Tool
Backlinks checkup
CHECK WEBSITE LOAD TIME
GT-Matrix
Google page insights
Pingdom
PLUGIN OR EXTENSION
SEO quacke- site audit and web audit
SERP Trends- To check ranking on SERP
SOME GOOGLE TOOLS
Google search console
Google Analytics
Google keyword Planner
2 notes
·
View notes
Text
General Device Maintenance for Windows
It is common for people to think they need a new laptop or desktop after a few years of use, and it is running slow. However, I’m going to show you a few tricks that I have perfected over the years to help a machine run in tip top shape. These are especially great to do after you have been uninstalling and reinstalling video games on them or just general use from office activity. These are, in my professional experience, the General Maintenance your company should be running on their Windows machines once a year, but probably is not…
-Work Machine-
Please note that for any commands I’m referencing to with quotes, you will not enter the quotes, it’s just the industry standard when specifying a string of data. We’ve all been there, on a work machine and it’s locked down on the permissions. Great news, you can run “gpupdate /force” (Group Policy Update) from Command Prompt. It’s pretty fast and either works or gives you an error that you can screenshot and send to your Service Desk, saving a ton of time. Fundamentally what it does is checks with your company’s server to make sure your computer follows the parameters of the domain. It’s typically the first thing your IT person will run and can be done with any account.
-Personal Machine-
If you haven’t already done it, you should uninstall any Bloatware. This is software that came on your computer when you got it, you don’t necessarily need or use it and it doesn’t seem to contribute to how your computer runs the way you are going to use it. Navigate to the “uninstall a program” area of your Control Panel and you will see the list, then just right click > uninstall (sometimes with stuff like Office there is a “Repair” option). If you see “Wave Browser” while in the control panel you will want to get rid of that at once and run a malware scan; actually, if you see any program you don’t recognize, Google it and/or the publisher to check that it’s legitimate or see what it does. (Note: modern browsers have Java built in, you no longer need it installed on your machine.) You may also have to do it from what we used to call the “Start” area and have no idea why they changed it, er the windows icon and “All Apps”.
-Light Clean-
Clearing your temp folders might seem like it’s not that important, but the closer your SSD drive gets to 50% the slower it performs. This is the random cache your computer stores during regular use of moving files, installing programs, error logs…etc. You’d be surprised at just how junked up they can get, I’ve seen them take up to 8GB worth of data.
From any account: Go to start > Run and type in “%temp%”. (The actual path is “C:\Users\\AppData\Local\Temp”)
With administrative rights, follow the same steps but instead type “temp”.(“C:\Windows\Temp”)
-Update Drivers-
If it’s not one thing, it’s the drivers. Easiest way you can check is to look for a caution mark on one of the listed items in the Device Manger; you might have to drop down the tree. These are the kernel code that binds your operating system and programs with the motherboard. You can set them to auto update, but sometimes the list doesn’t synchronize. Some laptops such as Lenovo have a program that you can download from their website or find in the Microsoft Store like “Lenovo Vantage” and it can be ran from a user account. If you want to look for them yourself the command is: “wmic bios get serialnumber”. The top two to look for and download if they have a newer version are the BIOS and Firmware/Chipset Management Engine.
-More in Depth Commands-
(You will need administrative rights)
Similar to Linux there are terminal commands that are native to the Windows environment that you can run to improve your system. To run these, go to start > Command Prompt > right click > run as administrator:
#1 System File Checker = "sfc /scannow"
This one will take roughly 10 minutes but it’s safe to use the machine while it runs; however, I wouldn’t install anything while it goes. It basically goes through your filesystem and makes sure everything lines up the way it should be, the right system files point to the correct location and there’s no junk files that shouldn’t be there linking to something else. This is just layman’s term, and feel free to look into it more but I assure you it’s perfectly fine to run even if you don’t know what you’re doing.
#2 DISM = "dism /online /cleanup-image /restorehealth"
It can take 15 to 45 minutes, depending on how bad your machine is, but again it’s safe to use while it runs. This connects with the Microsoft servers responsible for updates and ensures that your operating systems image matches the lines of code it should have. You can actually do a lot with dism commands.
#3 Check Disk = "chkdsk /f /r /x" (stands for: find, repair, dismount)
Please note that you will not be able to use the machine until it’s finished running and it can take up to an hour. It should automatically restart your machine after entering it so make sure to save and close everything beforehand. It sometimes gets stuck at “100%, please do not turn off or restart your machine”, but it’s safe to hard reset (press the power button or pull cord). This checks your hard drive for any irregularities and makes sure nothing is corrupt or damaged. There are several ways to run this, however this is the one I find most useful as it runs it at a very low level right after bios when it is loading the kernel (code that makes hardware talk to software).
#4 Cipher = "cipher /w:c:\"
This one will take a while, like up to 2 hours, and I wouldn’t plan on using it, so it goes faster. For when you drastically want to really clean your hard drive to sell or donate This command wipes the dark void of the strange quarks files turn into after the recycling bin. Basically, preventing anyone from restoring anything you deleted and maximizing the free space available in some parts per million way. — And that’s pretty much it! There are a few snazzy programs that I will leave below to help keep your computer stay in shape and safe. Other than that, Congratulations!!! You could be an entry level IT person now.
Noteworthy programs: ATF Cleaner, JRT Remover, Glary Utilities, CCleaner and Malwarebytes
#it support#computer repair#windows administrator#service desk#help desk#toolkit#information technology
3 notes
·
View notes
Text
[Image descriptions: A series of many screencaps from the Alt National Park Service Facebook page, only relative timestamps showing but from early February, 2025. Transcripts follow:
---
Please share: We've received word that Elon Musk's staffers are using space characters to identify information leakers. Before sharing any information, please use a checker to detect and remove these. Avoid directly leaking images; instead, request that the information be rewritten and the image recreated rather than shared directly from the source. This is essentially an email watermark—adding a space here, making a typo there, and similar subtle changes to track leaks. Stay vigilant.
---
Please be careful posting comments in public forums and use only the established secure communication channels (if you post publicly, it is suggested to hide your identity). Files have been distributed to all coalition members. There are different versions, so do not share them with other members. Some content may not be immediately relevant. Do not delete any files, and only open them on personal devices. The instructions are specific—please follow them. Our legal team is available to address any concerns. More information will be made public. Stay posted.
---
Scientists at the Centers for Disease Control and Prevention were ordered to withdraw any pending publications, at any scientific journal, that mention terms such as "transgender," "immigrant," "L.G.B.T." or "pregnant people."
---
We are fully aware that, in time, we will face retribution for the information we are sharing with the American public. However, we remain committed to standing as a line of defense. When resistance members block efforts by Elon Musk's staff, they are placed on administrative leave, their personal belongings searched, and their offices and computers locked. Our coalition now includes over 50,000 federal employees from across the government.
We want to remind Americans why Elon Musk's actions are illegal. The so-called Department of Government Efficiency (DOGE) was not established by Congress but was instead granted authority through an executive order by Trump, making its operations illegal. It is not an official department of the federal government. This system could provide Musk with a mechanism to unilaterally restrict the disbursement of funds approved by Congress—a move that has historically faced significant legal challenges.
DOGE teams have begun demanding access to data and systems at other federal agencies. However, none of these agencies control the flow of money in the way the Treasury Department does. Access to the federal payment system has always been tightly restricted due to its inclusion of sensitive personal information about millions of Americans who rely on Social Security checks, tax refunds, and other government payments.
In fiscal year 2023, the Treasury Department disbursed over $5 trillion through this system in a process typically overseen by civil servants. The stakes are incredibly high, and it is vital for Americans to understand the gravity of these actions. Please continue to spread the word and raise awareness.
---
Attn: Treasury Secretary Scott Bessent granted representatives of the so-called Department of Government Efficiency full access to the federal payment system! This is illegal.
---
Trump issued a memorandum invalidating government labor contracts finalized in the 30 days before his presidential inauguration. This action is not legal and will not hold up in court. It disregards the Federal Service Labor-Management Relations Statute (FSLMRS), which safeguards federal employees' rights to organize, collectively bargain, and enter into enforceable labor agreements.
---
1,100 EPA employees have been notified of imminent termination.
---
Thank you, Senator! Senate Finance Committee Ranking Member Ron Wyden demanded answers from Treasury Secretary Scott Bessent after reports surfaced that personnel affiliated with Elon Musk have sought access to a highly sensitive Treasury Department payment system. This system, managed by non-political staff, disburses trillions of dollars annually, including Social Security and Medicare benefits, tax credits for individuals and businesses, and grants and payments to government contractors—some of which compete directly with Musk-owned companies.
---
Elon Musk staff has been caught plugging in hard drives inside the Office of Personnel Management (OPM), the Treasury Department, and the General Services Administration (GSA). His staff encountered resistance when demanding that Treasury officials grant access to systems managing the flow of more than $6 trillion annually to programs like Social Security and Medicare. Tensions escalated when Musk's aides were discovered at OPM accessing systems, including a vast database known as the Enterprise Human Resources Integration (EHRI), which contains sensitive information such as dates of birth, Social Security numbers, performance appraisals, home addresses, pay grades, and length of service for government employees. In response to employees speaking out, Musk's aides locked civil servants out of computer systems and offices, with reports of personal items being searched.]
A series of posts from the Alt National Parks Page regarding Elon Musks take over.









12K notes
·
View notes
Link
0 notes
Link
0 notes