#Securecommunication
Explore tagged Tumblr posts
Text

AI-powered, secure communication services for financial institutions!
Boost revenue, simplify operations, and deliver seamless #clientexperiences with Vitel Global.
Looking to transform your financial #communication? Get started today! www.vitelglobal.com #linkinbio #linktree 👉📧 [email protected] 👉📲 +1 855 558 4835
#SmartFinance#SecureCommunication#AIPowered#VitelGlobal#Fintech#AIinFinance#TechInnovation#FinanceSolutions#FinancialServices#ClientExperience#USA
3 notes
·
View notes
Text
Discover the benefits of using a hidden call recorder and spy call recorder to enhance security and protect your loved ones and business. Learn about the features, advantages, and legal considerations of these essential monitoring tools.
#HiddenCallRecorder#SpyCallRecorder#DigitalSafety#ChildProtection#EmployeeMonitoring#CyberSecurity#ParentalControl#BusinessSecurity#CallRecording#TechForSafety#SecureCommunication#PrivacyTools
1 note
·
View note
Text
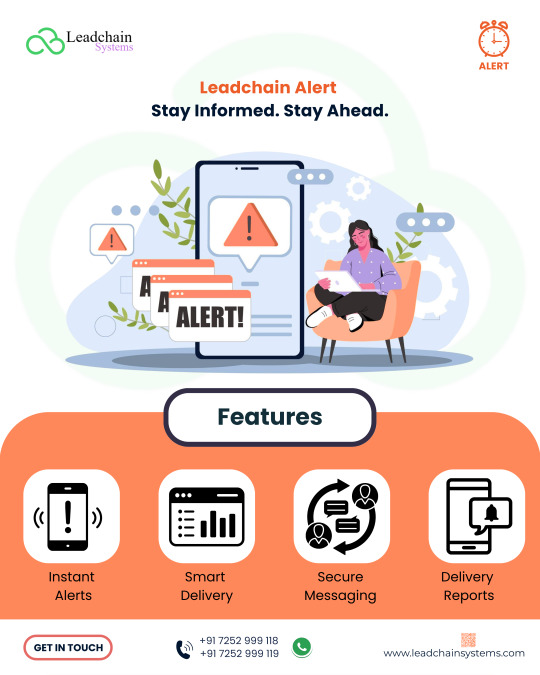
Leadchain Alert – Stay Informed. Stay Ahead.
Send important updates instantly and keep your audience in the loop with Leadchain Alert — your smart notification and alert system designed for teams, organizations, and service providers.
🔑 Key Features: 📱 Instant Alerts – Deliver urgent messages in real time 📊 Smart Delivery – Reach the right people at the right time 🔐 Secure Messaging – Communicate safely across platforms 📩 Delivery Reports – Track message status and reach
Whether it's team updates, emergency alerts, or client notifications — Leadchain Alert keeps your communication sharp, timely, and reliable.
📞 +91 7252 999 118 | +91 7252 999 119 🌐 www.leadchainsystems.com
#leadchain#alerts#instantalerts#smartnotifications#teammessaging#deliveryreports#securecommunication#realtimeupdates#alertsystem#businessnotifications#software engineering#businessautomation
0 notes
Text
Understanding the Security Behind End-to-End Encryption
In just 2024, 12 Lakhs cyber fraud crimes were registered in India, including businesses that faced devastating damages resulting from stolen data. While we have all put securing our digital assets on the back burner, now it’s high time we look into digital storage alternatives where not only is your data kept safe but also have additional layers of security such as the End-to-End encryption a part of their security. Before we jump into what are the best cloud storage platforms with high-level security, let’s first understand what E2EE is and how it can protect your business digital assets from being stolen.

What is End-to-End Encryption (E2EE)?
Online, when you text, chat, or share something, most of the platforms where you do share this information have an option where 3rd third-party website can access your data; although quite a few of these are for improved ad quality, not all of them are. This is why industry leaders such as Facebook, Instagram, WhatsApp, and others use end-to-end encryption; this is a form of sharing data on the internet where the data is encrypted in such a way that only the sender and the receiver of this information have the passkey in their systems, allowing them complete control and secure data sharing platform.
Why do Cloud Storage Platforms Need End-to-End Encryption (E2EE)?
Cloud storage platforms need End-to-End Encryption (E2EE) to ensure the highest level of security and privacy for users’ data. Here’s why:
1. Data Confidentiality
E2EE ensures that data is encrypted on the user’s device before being uploaded to the cloud and can only be decrypted by the intended recipient.
Even the cloud service provider cannot access or read the stored data.
2. Protection Against Data Breaches
Cloud storage providers are frequent targets of cyberattacks.
Without E2EE, hackers can access unencrypted data if they breach the cloud provider’s infrastructure.
3. Prevention of Insider Threats
Employees or third parties working for the cloud provider may have access to stored data if it isn’t encrypted end-to-end.
E2EE ensures that no one, not the provider, can access sensitive user data.
4. Compliance with Data Privacy Regulations
Laws like GDPR, HIPAA, and CCPA require strict data protection measures.
E2EE helps businesses meet compliance requirements by ensuring user data remains private and secure.
5. Protection from Government Surveillance
Governments can request user data from cloud providers.
With E2EE, even if the provider hands over encrypted files, they remain unreadable without the decryption key.
6. User Control Over Encryption Keys
In E2EE, only the user controls the encryption keys, not the cloud provider.
This prevents unauthorized access and strengthens data sovereignty.
7. Secure Sharing and Collaboration
E2EE allows users to share encrypted files securely, ensuring that only authorized recipients can decrypt and view the content.
8. Trust and Reliability
Users are more likely to trust cloud storage services with robust security measures.
E2EE enhances trust by guaranteeing that user data remains private and secure.
How Can you benefit from End-to-End Encryption in Cloud Storage?
One of the key aspects of securing your data on a cloud platform is being able to trust it to provide a completely secure digital space. So, platforms such as eShare.ai use end-to-end encryption to ensure not a single piece of information, regardless of chats, documents, photos, videos, presentations, client information, and many others, stays where they are without any 3rd party access. With additional features that include data monitoring, you will not only be able to share your files with others but also have additional perks such as access control, limited access duration, and so on. Making all that and more possible through their high-encrypted software solutions.
Every business owner knows the risk of what can happen when it comes to unsecured data storage. This is why switching to cloud storage platforms such as eShare.ai with E2EE is a game changer for your digital storage needs. With custom solutions that provide high-grade security for any and all data, communication within the platform, and end-to-end encryption apps, this is the perfect solution for every business regardless of their industry and size! To inquire more, visit our website today!
#EndToEndEncryption#CyberSecurity#DataEncryption#eShareAI#SecureCommunication#EncryptedData#DigitalPrivacy#CloudSecurity#FileSharingProtection
0 notes
Text
0 notes
Text
#TacticalHeadsets#MilitaryCommunication#CombatGear#TacticalGear#HeadsetTechnology#DefenseElectronics#NoiseCancellingHeadsets#SituationalAwareness#TwoWayCommunication#SecureCommunication#MilitaryTech#FieldCommunication#TacticalEquipment
0 notes
Text

Communicate with confidence. VoIP solutions offer advanced security to protect your business. Stay worry-free knowing your conversations and data are safe, so you can focus on what truly matters—your growth. VoIP solutions come with advanced, built-in security features like end-to-end encryption and multi-layered authentication, ensuring that your business communications remain secure from potential threats and breaches. These powerful security protocols safeguard sensitive information, giving you peace of mind while you communicate. With VoIP, you not only get high-quality, reliable communication but also top-notch protection for your data. Trust in secure communication that keeps your business safe, while offering seamless connectivity and collaboration. Protect your business, enhance efficiency, and ensure that every call, message, and video meeting is safe and private.
For More Information : Website:- https://www.ajoxi.com/
Contact Us : Email:- [email protected] Contact:- +1 512-855-7246
#SecureCommunication#VoIP#BusinessSecurity#TechSolutions#CloudSecurity#DataProtection#CyberSecurity#SecureConnections#BusinessProtection#ReliableTech#CloudSolutions#TechForBusiness#DigitalSecurity#SafeBusiness#CommunicationTech#PrivacyMatters#SecureTech#DataPrivacy#BusinessInnovation#CloudTech#NextGenSecurity
0 notes
Text
Quantum Teleportation is Achieved: The Future of the Internet | Researchatory.AI | Aakash Khurana
Physicists successfully achieved quantum teleportation over existing internet cables, a breakthrough that could revolutionize secure communication technologies. Imagine a world with unhackable communication. That future is closer than you think. Quantum teleportation over existing internet infrastructure is now a reality. What does this mean for the future of the web? 🤔 #FutureTech #QuantumComputing #Innovation #NextGenInternet #FiberOptics #TechBreakthrough #ScienceNews #QuantumTech #FutureTech #QuantumComputing #Innovation #NextGenInternet #ScienceExplained #Quantum #InternetNews #AmazingScience #CyberSecurity #QuantumEncryption #SecureCommunication #TechNews
This is indeed a very exciting development in the field of quantum physics and communication! Here's a breakdown of what this breakthrough entails:
* **Quantum Teleportation:**
* It's not about teleporting physical objects like in science fiction. Instead, it's the transfer of quantum information from one location to another.
* This relies on a phenomenon called quantum entanglement, where two particles are linked, and their states are correlated.
* **Breakthrough Achievement:**
* Researchers at Northwestern University have successfully demonstrated quantum teleportation over existing fiber optic cables that also carry regular internet traffic.
* This is significant because it shows that quantum communication can coexist with classical communication within the current internet infrastructure.
* **Key Challenges and Solutions:**
* A major challenge was the interference between the delicate quantum signals (single photons) and the strong classical internet signals.
* The researchers overcame this by:
* Identifying specific wavelengths of light with minimal interference.
* Using specialized filters to reduce noise.
* **Potential Implications:**
* **Secure Communication:** Quantum teleportation has the potential to revolutionize secure communication due to the fundamental properties of quantum mechanics.
* **Quantum Internet:** This advancement is a crucial step towards building a future quantum internet.
* **Simplified Infrastructure:** It suggests that we may not need to build entirely new infrastructure for quantum communication, as it can potentially be integrated with existing networks.
In essence, this research brings us closer to realizing the potential of quantum technologies for real-world applications.
For more info:
#FutureTech#QuantumComputing#Innovation#NextGenInternet#FiberOptics#TechBreakthrough#ScienceNews#QuantumTech#ScienceExplained#Quantum#InternetNews#AmazingScience#CyberSecurity#QuantumEncryption#SecureCommunication#TechNews
0 notes
Text

🚀 Boost Your Business with Reliable Email Hosting! 📧✨
Looking for secure, fast, and professional email hosting? Look no further! With EWallHost's Business Email Hosting, you get:
✅ 5GB Storage for seamless communication 📂 ✅ Affordable Pricing – Just ₹29/month! 💰 ✅ 100% Uptime & Secure Access 🔒 ✅ Easy Setup & Hassle-Free Management 🖥️
🔹 Limited-Time Offer – Don’t Miss Out! 🔹
📩 ORDER NOW & elevate your business communication! 🚀
📞 +91 96550 05757 | ✉️ [email protected]
0 notes
Text
#AutomotiveCybersecurity#MarketGrowth#CybersecuritySolutions#VehicleSecurity#ConnectedVehicles#AutonomousVehicles#AutomotiveIndustry#CyberThreats#DataProtection#NetworkSecurity#AutomotiveSoftware#EmbeddedSecurity#CloudSecurity#IoTSecurity#BlockchainInAutomotive#EncryptionTechnologies#SecureCommunication#RiskManagement#RegulatoryCompliance#AutomotiveHacking#ThreatDetection#SecurityArchitecture#AutomotiveCyberAttacks#EndpointSecurity#DigitalTransformation#SmartVehicles#CybersecurityInvestment#AutomotiveDataSecurity#FutureMobility#AutomotiveInnovation
0 notes
Text

Beyond calling VoIP is the next step in business communication! Upgrade today and enhance your communication strategy. VoIP isn’t just about making calls—it’s about transforming how businesses communicate! With features like video conferencing, call recording, AI-powered analytics, virtual numbers, and mobile compatibility, VoIP keeps your business agile, efficient, and ready for the future. Imagine seamless team collaboration, reduced communication costs, and advanced features all in one cloud-based platform! Ditch outdated phone systems and embrace all-in-one communication with VoIP today!
For more information : https://www.letsdial.com/
👉 Email:- [email protected] 👉 Contact No:- +1 917-779-0187
#VoIP#BusinessEfficiency#SmartCommunication#CloudCalling#TechInnovation#SeamlessWorkflows#FutureReady#VoIPSolutions#EnterpriseTech#ScalableCommunication#CloudTechnology#UnifiedCommunications#RemoteWork#HybridWork#CollaborationTools#VoIPTech#DigitalTransformation#BusinessGrowth#TechForBusiness#CloudComputing#GlobalConnectivity#VoIPForBusiness#VoIPPhone#CloudTelephony#ProductivityBoost#BusinessTech#SecureCommunication#NextGenTechnology#AICommunication#VoIPProviders
0 notes
Text
End-to-End Encryption by CipherChat | Secure Your Conversations Today
Secure your conversations with CipherChat's End-to-End Encryption. Ensure complete privacy with encrypted messaging from sender to recipient. Protect sensitive business data with advanced security measures. Stay compliant with data protection regulations effortlessly. Explore CipherChat's features today! Website: https://cipherchat.co/

1 note
·
View note
Text
Discover the benefits of using WhatsApp spy apps in 2024. Learn how these essential tools can help protect your loved ones, secure your business, and ensure transparency in relationships.
#WhatsAppSpy#SpyAppForWhatsApp#DigitalSafety#OnlineSecurity#ParentalControl#EmployeeMonitoring#DataProtection#TechTools#DigitalPrivacy#SecureCommunication
0 notes
Text
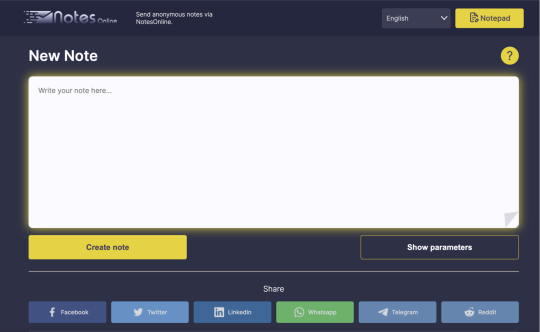
📲💥 Discover NotesOnline: The Ultimate Self-Destructing Note Service! 💥📲
Looking for a secure and anonymous way to share sensitive information? Look no further! NotesOnline is here to save the day.
✨ Why Choose NotesOnline? 🔒 Create online notes that self-destruct after being read. 🚀 Free, fast, and secure with end-to-end encryption. 🌐 Share files and notes through an encrypted SSL tunnel. 🗝 No accounts, passwords, or emails required. 🔐 Ensure your message is read only by the recipient and then erased forever. 📑 Acts as a paste bin for secure, temporary text storage. 🛡 Utilize protected text to ensure your notes are for the recipient’s eyes only.
✍ What You Can Do With Our Free Online Notepad:
Take quick notes online. Use text editor mode for advanced formatting. Create a simple and editable to-do list. Mark text online and instantly save new ideas. Keep your files safe with the password protection option. Write social media posts with a live word/character count. Write blogs and articles online.
💬 How It Works: Write your note. Get a secure link. Share the link. The note self-destructs after being read. Simple as that!
🔗 Try NotesOnline Today: https://notesonline.com/notepad
#OnlineNote#OnlineNotepad#PrivateNote#PasteBin#ProtectedText#SecureMessaging#SelfDestructingNote#EndToEndEncryption#AnonymousMessaging#SecureCommunication
0 notes
Text
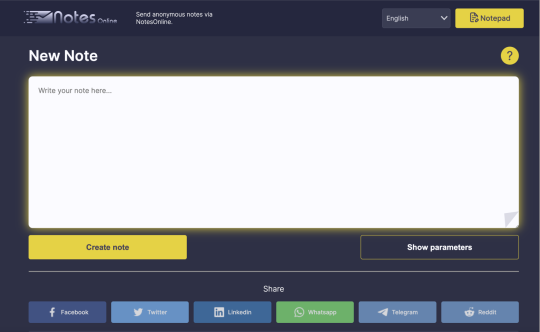
📲💥 Discover NotesOnline: The Ultimate Self-Destructing Note Service! 💥📲
Looking for a secure and anonymous way to share sensitive information? Look no further! NotesOnline is here to save the day.
✨ Why Choose NotesOnline? 🔒 Create online notes that self-destruct after being read. 🚀 Free, fast, and secure with end-to-end encryption. 🌐 Share files and notes through an encrypted SSL tunnel. 🗝 No accounts, passwords, or emails required. 🔐 Ensure your message is read only by the recipient and then erased forever. 📑 Acts as a paste bin for secure, temporary text storage. 🛡 Utilize protected text to ensure your notes are for the recipient’s eyes only.
💬 How It Works:
Write your note. Get a secure link. Share the link. The note self-destructs after being read. Simple as that!
🔗 Try NotesOnline Today: https://notesonline.com
#OnlineNote#OnlineNotepad#PrivateNote#PasteBin#ProtectedText#SecureMessaging#SelfDestructingNote#EndToEndEncryption#AnonymousMessaging#SecureCommunication
0 notes
Text

Your data, your customers, and your business are in safe hands. Trust Cloud Contact Solutions for secure communication that never compromises on reliability. When it comes to communication, security is not just a feature – it’s a priority. At [Your Brand], we understand that your business data is invaluable. That’s why our Cloud Contact Solutions are built with cutting-edge security protocols to provide you with the peace of mind you deserve. Whether it’s safeguarding sensitive customer information or ensuring compliance with industry standards, we’ve got you covered. With our cloud-based contact solutions, your communication is secure, reliable, and always available. Say goodbye to security breaches and data vulnerabilities. Stay protected, stay compliant, and keep your business thriving with solutions that prioritize your safety. Don’t compromise on security. Choose solutions that protect your data, your customers, and your reputation.
For More Information : Website:- https://www.ajoxi.com/
Contact Us : Email:- [email protected] Contact:- +1 512-855-7246
#DataSecurity#BusinessSafety#CloudContact#ReliableSolutions#SecureCommunication#DigitalTrust#CloudSecurity#CyberProtection#ComplianceAssurance#BusinessProtection#TechInnovation#SecureBusiness#CustomerPrivacy#DataProtection#SecureTech#PrivacyMatters#SafeBusiness#DigitalTransformation#CloudSolutions#BusinessGrowth#SecureYourData#FutureProof#InnovativeSecurity#EnterpriseSecurity#DataPrivacy#SecurityFirst#SmartBusiness#TechForGood#BusinessContinuity
0 notes