#Scale-out Backup Repository
Explore tagged Tumblr posts
Text
Achieve 3-2-1 rule with SOBR on Synology or OOTBI and Wasabi
Veeam’s Scale-Out Backup Repository (SOBR) can be used to implement the 3-2-1 backup rule. The 3-2-1 backup rule recommends having three copies of your data, stored on two different types of media, with one copy kept off-site. SOBR is built upon collections of individual repositories as we will see very shortly. In this article, I will demonstrate how you can Achieve 3-2-1 rule with SOBR on…
#3-2-1 Backup Rule#3-2-1-1-0 Rule#Archive Tier#Backup Repository#Backup Target#Capacity Tier#Create a Backup Repository#Create a Bucket on Wasabi#Create an Access Key#Direct to Object Storage Backups#Implement 3-2-1 Backup with SOBR#Performance Tier#Run Tiering Jon Now#Scale-out Backup Repository#SOBR Archive Tier#SOBR Extents#SOBR Offloads#Start Veeam SOBR Offload Job Manually#Storage Bucket#Use a SOBR with Veeam Backup & Replication
0 notes
Text
Protect Your Construction Project with Secure Cloud-Based Management Software

In the growing digital age of construction, it is vital to have cloud-based management software for project managers, contractors, and their teams. These solutions remove the usual limits of local applications, offering unparalleled flexibility, scalability, and accessibility. This makes it simple for construction professionals to handle their operations more conveniently and provide projects at a speed that none others can match.
Benefits of using secure cloud-based management software
Using safe, cloud-based management software for your construction projects will unlock a great deal of advantages, including the following.
Increased Collaboration and Communication: Such software assists with immediate involvement from all involved in the project. This enables smooth information sharing, exchange of documents and communications across teams, no matter where they are.
Centralized Data Management: With cloud-based software, there will be a centralized repository of all the data regarding any project. This ensures that no kind of data silos would persist, and everyone gets updated data for better decision-making and overall coordination of projects.
Improved Accessibility and Mobility: Cloud-based solutions provide any-place, anytime access to the data and tools of the project, thus enabling construction professionals to stay connected and productive while working remotely or on-site.
Affordable and Scalable: Cloud-based software is inexpensive and scales up or down according to project requirements without using expensive hardware or IT infrastructure.
Enhanced Security and Data Protection: Good cloud service providers deliver solid security. They protect details through data encryption, controlling access to it, or periodic backups.
These measures ensure your vital project data is never compromised or misplaced.
Key features of cloud-based management software for construction projects
Comprehensive cloud-based construction project management software typically includes numerous features for managing various elements of your projects.
Following are some critical features to expect:
Project Planning and Scheduling: With detailed planning and scheduling tools, you can make thorough project blueprints, hand out duties, and distribute resources. Plus, you can monitor your project's growth on the spot to ensure it remains on track and within funds.
Document Management: Cloud-based document management systems use a central storage area. They holds all the details about projects like drawings, specifications, and contracts with controlled changes, ensuring those who are allowed, the stakeholders, can see them and share them.
Cost and Budget Management: Strong cost and budget management features allow you to track expenses, monitor budgets, and create detailed financial reports to keep tight control over project finances.
Resource Management: Effective resource management tools will provide the firm with the facility to allocate and schedule people, equipment, and materials across a number of projects. This boosts proper resource use and cuts down any wastage.
Issue and Risk Management: The integration of issue and risk management modules offers functionality for the identification and tracking of risks that may arise. It includes ways to solve worrying issues beforehand, ensuring projects have minimal interruptions.
Reporting and Analytics: Advanced reporting and analytics go a long way in delivering real-time insights into projects' performances. This requires making informed decisions and allowing for course corrections whenever called upon.
How cloud-based management software improves project collaboration and communication?
Effective collaboration and communication have always been considered crucial for a construction project, which involves multiple stakeholders performing different roles and responsibilities. In that aspect, cloud-based management software plays an important role in ensuring smooth collaboration among team members and establishing good channels of communication. Hence, everyone remains on the same platform in the project cycle.
Centralized Project Information: It consolidates all project-related data, documents, and communication threads on one cloud-based platform. This way, stakeholders can access real-time information from anywhere in the world at any time, avoiding a potential scenario of working from outdated or silo information.
Real-time Collaboration and File Sharing: Cloud-based software enables employees to collaborate in real-time on various documents, drawings, and project plans. Several team members can work on the same document at the same time and share their contributions immediately. Version control and change tracking features ensure transparency and accountability.
Integrated communication channels: Most of the cloud solutions have integrated communication tools, such as messaging, video conferencing, and discussion forums, that make it easy to communicate with project stakeholders, reduce reliance on multiple tools, and minimize miscommunication.
Automated Notifications and Updates: The cloud-based software automatically notifies all concerned parties in the event of an update, change, or any other critical event. This helps the stakeholders remain updated and take prompt action on the arising issue or opportunity.
Mobile Access and Field Collaboration: Cloud-based solutions let construction professionals access project information from mobile devices right at the job site and collaborate on the go. This is effective in updating information in real-time, reporting issues, or even making on-site decisions.
The capabilities for collaboration and communication in cloud-based management software provide for a more integrated and coordinated project team. This leads to better coordination, swift decision-making, and finally to, successful project outcomes.
Implementing and integrating cloud-based management software into your construction project
Successful implementation and integration of the cloud-based management software for construction require careful planning, stakeholder buy-in, and active execution of a change management strategy. You can only maximize these advantages and ensure a seamless transition through appropriate best practices and a structured approach where your construction teams achieve precisely what is expected.
Some key steps in this respect are as follows:
Set up a dedicated implementation team: Create a cross-functional team comprising project management, IT, finance, and operations. This team will guide the application and make specific the procedures reaches the organization's goals. They will also maintain open communication and offer proper training.
Perform thorough requirements analysis: Analyze in detail the needs, workflows, and processes of your construction project. Also, identify where the cloud-based management software can help streamline operations, improve collaboration, and enhance project visibility.
Draw up an implementation roadmap: The implementation roadmap should be detailed, showing the key milestones, timelines, and responsibilities. This roadmap should cover the phases of data migration, software configuration, user training, and testing to ensure a well-structured and controlled transition.
Engage Stakeholders and Secure Buy-in: In a change management process, it is very important to have proper stakeholder buy-in and involvement. The benefits of the cloud-based management software should be communicated to all stakeholders of project teams, executives, and external partners. Their concerns will be discussed, feedback will be listened to, and involvement will be requested with regard to the implementation process in order to develop ownership and commitment to its success.
Full training and support: Invest in comprehensive training that makes the software features and functionalities known to your construction teams, as well as best practices for using it. Provide support resources such as user guides and online tutorials, plus a designated support channel, to facilitate easy adoption and usage of the software.
Integration with current systems and tools: Identify the integrations that should be in place between the cloud-based management software and your current systems and tools, like accounting software, BIM platforms, and project scheduling applications. Seamless integration will ensure that the workflow goes smoothly, data redundancy is minimized, and the productivity level of employees is enhanced.
Conduct pilot projects and gather feedback: Wherever possible, pilot projects or proof-of-concept should be conducted in advance of a full implementation to test the capabilities of the software and to identify any potential challenges or areas of improvement. Gather feedback from the pilot users and incorporate their insights into the broader implementation plan.
Monitor and optimize: Observe the performance of the software, the rate of user adoption, and its impact on project outcomes. Collect feedback from stakeholders and analyze trends in data that may indicate areas for optimization or process improvements. Utilize the reporting and analytics capability of the software to gain real insight and make decisions based on data.
Governance and change management: Establish the policies of governance and protocols of how change management should be carried out in order to maintain consistency of control within software usage, data management, and adherence to processes across your construction projects. Regularly review the completeness of these protocols to meet evolving project requirements and industry best practices.
The steps, if followed within a structured approach, show how to adequately implement and integrate cloud-based management software into construction projects for better benefits and facilitate a smooth transition to your construction teams.
Conclusion: The future of construction project management is secure cloud-based software.
Cloud management systems are transforming the construction industry and keeping pace with its digital shift. Modern construction projects are intricate and involve remote teamwork. The need for instant data sharing and overviews of project progress is crucial.
Secure, cloud-based management software provides a comprehensive solution, equipping construction professionals with the tools and insight needed to drive operational efficiency, minimize risk, and ensure successful project delivery on time and within budget.
Using cloud technology allows construction firms to eliminate barriers, promote smooth communication, and secure access to the latest data for all involved. This encourages informed choices and proactive solutions to problems.
#cloud based construction project management software#cloud construction software#cloud-based construction management software
0 notes
Text
Amazon DynamoDB: A Complete Guide To NoSQL Databases

Amazon DynamoDB fully managed, serverless, NoSQL database has single-digit millisecond speed at any scale.
What is Amazon DynamoDB?
You can create contemporary applications at any size with DynamoDB, a serverless NoSQL database service. Amazon DynamoDB is a serverless database that scales to zero, has no cold starts, no version upgrades, no maintenance periods, no patching, and no downtime maintenance. You just pay for what you use. A wide range of security controls and compliance criteria are available with DynamoDB. DynamoDB Global Tables is a multi-region, multi-active database with a 99.999% availability SLA and enhanced resilience for globally dispersed applications. Point-in-time recovery, automated backups, and other features support DynamoDB dependability. You may create serverless event-driven applications with Amazon DynamoDB streams.
Use cases
Create software programs
Create internet-scale apps that enable caches and user-content metadata, which call for high concurrency and connections to handle millions of requests per second and millions of users.
Establish media metadata repositories
Reduce latency with multi-Region replication between AWS Regions and scale throughput and concurrency for media and entertainment workloads including interactive content and real-time video streaming.
Provide flawless shopping experiences
When implementing workflow engines, customer profiles, inventory tracking, and shopping carts, use design patterns. Amazon DynamoDB can process millions of queries per second and enables events with extraordinary scale and heavy traffic.
Large-scale gaming systems
With no operational overhead, concentrate on promoting innovation. Provide player information, session history, and leaderboards for millions of users at once when developing your gaming platform.
Amazon DynamoDB features
Serverless
You don’t have to provision any servers, patch, administer, install, maintain, or run any software when using Amazon DynamoDB. DynamoDB offers maintenance with no downtime. There are no maintenance windows or major, minor, or patch versions.
You only pay for what you use using DynamoDB’s on-demand capacity mode, which offers pay-as-you-go pricing for read and write requests. With on-demand, DynamoDB maintains performance with no management and quickly scales up or down your tables to accommodate capacity. Additionally, when there is no traffic or cold starts at your table, it scales down to zero, saving you money on throughput.
Amazon DynamoDB NoSQL
NoSQL
DynamoDB is a NoSQL database that outperforms relational databases in performance, scalability, management, and customization. DynamoDB supports several use cases with document and key-value data types.
DynamoDB does not offer a JOIN operator, in contrast to relational databases. To cut down on database round trips and the amount of processing power required to respond to queries, advise you to denormalize your data model. DynamoDB is a NoSQL database that offers enterprise-grade applications excellent read consistency and ACID transactions.
Fully managed
DynamoDB is a fully managed database service that lets you focus on creating value to your clients. It handles hardware provisioning, security, backups, monitoring, high availability, setup, configurations, and more. This guarantees that a DynamoDB table is immediately prepared for production workloads upon creation. Without the need for updates or downtime, Amazon DynamoDB continuously enhances its functionality, security, performance, availability, and dependability.
Single-digit millisecond performance at any scale
DynamoDB was specifically designed to enhance relational databases’ scalability and speed, achieving single-digit millisecond performance at any scale. DynamoDB is designed for high-performance applications and offers APIs that promote effective database utilization in order to achieve this scale and performance. It leaves out aspects like JOIN operations that are ineffective and do not function well at scale. Whether you have 100 or 100 million users, DynamoDB consistently provides single-digit millisecond performance for your application.
What is a DynamoDB Database?
Few people outside of Amazon are aware of the precise nature of this database. Although the cloud-native database architecture is private and closed-source, there is a development version called DynamoDB Local that is utilized on developer laptops and is written in Java.
You don’t provision particular machines or allot fixed disk sizes when you set up DynamoDB on Amazon Web Services. Instead, you design the database according to the capacity that has been supplied, which includes the number of transactions and kilobytes of traffic that you want to accommodate per second. A service level of read capacity units (RCUs) and write capacity units (WCUs) is specified by users.
As previously mentioned, users often don’t call the Amazon DynamoDB API directly. Rather, their application will incorporate an Amazon Web Services, which will manage the back-end interactions with the server.
Denormalization of DynamoDB data modeling is required. Rethinking their data model is a difficult but manageable step for engineers accustomed to working with both SQL and NoSQL databases.
Read more on govindhtech.com
#AmazonDynamoDB#CompleteGuide#Database#DynamoDB#DynamoDBDatabase#sql#data#AmazonWebServices#Singledigit#Fullymanaged#aws#gamingsystems#technology#technews#news#govindhtech
0 notes
Text
School Management Software Is Useful Or Not?

School Management System ERP software can transform the way schools operate by streamlining their processes and improving communications among stakeholder. Schools that implement school administration strategies save time as well as money by automating tasks that were once performed manually on documentaries on paper. Students gain fast access to vital information rapidly, allowing them to save both time and money while offering a superior learning atmosphere for their pupils. The transparency and efficiency of the organisation make these administration systems vital components in the modern educational environment.
Genius Edusoft provides an Education Management ERP System which is cloud-based software that consolidates every school's operation on a single platform. It is equipped with fast data transfer and enhanced overall productivity, better transparency, advanced decision-making capabilities, and platform compatibility. Data backups automatically and in centralized databases prevent data loss risk, while its access control system based on roles allows only users with a valid role to have access to information. Effective and robust tools for scaling like Genius Edusoft make use of these tools in schools of all sizes.
A system for School Management System Software that integrates helps to cut down costs by doing eliminating paper filing and storage requirements, making it a reliable electronic repository that allows document retrieval much easier for teachers as well as administrators. Its green design reduces paper consumption - another positive effect of integrating management systems in schools. Click here or visit our official website to know about School Management Software.
Many School Management System Software are cloud-based. It allows users to access the software at any time from anywhere connected to an internet connection. This allows both teachers and students to log in whenever required - even during holiday periods or if they're away from campus This makes this choice particularly ideal for families who live removed from school who require permanent monitoring of school progress. An effective Cloud-Based School Management System must be flexible and able to adapt, especially for larger schools that require the program so that it can be used to support existing workflows techniques instead of adapting in order to comply with an unchangeable system. So, choosing a provider which has extensive experience and comprehension of educational processes is essential to select an effective solution to manage your school.
Also, a great school management program should incorporate the ability to manage communication, which enables parents and teachers to easily communicate via texts or email. This can be particularly helpful during emergency situations or when there is a pandemic during which a face-to-face meeting may make sense; it's an effective way for parents and teachers to be aware of any issues including fee collections schedules and notices from school.
vimeo
School management software comes with an all-in-one solution that streamlines diverse tasks and activities at educational institutions. These include school information management to staff administration, academic program planning and the collection of fee as well as student security. Also, teachers are well-informed and create better academic environments by using vital details that support decision-making methods as well as communicating channels.
School ERP will allow parents and students to effortlessly reach out to administrators and teachers in real-time with updates on the latest events, assessments, tests, and other such information. This helps create a positive school environment in which each participant is able to work in partnership towards creating a better education. There's many types of School Management System Software on the market. Each comes with unique advantages and disadvantages. If you are choosing a school management software, should be a must that it is compatible with your current system and workflows. It should also be low-cost and simple to grasp as it supports multiple user roles. The software can seamlessly connect with the most popular applications from third parties to automate data entry and reduce time.
0 notes
Text
Snowflake Business

Snowflake: Disrupting the Data Warehouse
In the ever-expanding world of data, businesses are constantly grappling with managing, storing, and gleaning actionable insights from vast information reserves. Enter Snowflake, a cloud-based data platform that has revolutionized how companies approach data warehousing.
What is Snowflake?
Snowflake is a fully managed, cloud-native data warehouse solution. What sets it apart from traditional data warehouses is its unique architecture:
Separation of Storage and Compute: Snowflake decouples data storage from computational resources. This means you can independently scale your storage and compute power, optimizing costs and performance.
Scalability: Snowflake’s elastic nature allows you to scale up or down effortlessly based on your workload demands, providing significant flexibility.
Pay-as-you-go Model: With Snowflake, you only pay for the resources you use. This eliminates the need for upfront hardware investments and minimizes waste.
Key Advantages of the Snowflake Data Cloud
Near-Zero Maintenance: As a fully managed service, Snowflake takes care of infrastructure, upgrades, backups, and security, freeing up your IT resources to focus on value-adding tasks.
Support for Diverse Data: Snowflake handles structured, semi-structured (like JSON), and even unstructured data, making it a versatile platform for various use cases.
Performance at Scale: Snowflake’s multi-cluster, shared data architecture is designed to deliver lightning-fast query performance even with massive datasets and concurrent user access.
Secure Data Sharing: Snowflake enables secure, live data sharing within your organization or with external partners and customers. This fosters collaboration and can create new data-driven business opportunities.
Snowflake Use Cases
Snowflake’s adaptability makes it suitable for a wide range of industries and use cases, including:
Data Warehousing and Analytics: Snowflake is a centralized repository for all your business data, empowering you to run complex analytics and derive insights.
Customer 360: Snowflake helps you build comprehensive customer profiles by consolidating data from different sources, improving customer understanding.
Data Lakes: Snowflake complements data lakes by providing structured access to raw data, enhancing its value.
Machine Learning and AI: Snowflake streamlines data preparation and access for machine learning models.
The Future of Snowflake
Snowflake’s innovative approach to data warehousing has led to rapid adoption by enterprises of all sizes. As the company continues to expand its capabilities and partnerships, it’s well-positioned to become a cornerstone of modern data architectures. The rise of the Data Cloud, a concept heavily pioneered by Snowflake, suggests a future where data becomes seamlessly accessible across organizations, industries, and applications.
youtube
You can find more information about Snowflake in this Snowflake
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Snowflake here – Snowflake Blogs
You can check out our Best In Class Snowflake Details here – Snowflake Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
0 notes
Link
#.NET8#Angular#Angular17#ASP.NET#ASP.NET8#ASP.NETCore#Azure#C#EFCore#EntityFramework#GraphQL#MinimalAPIs#MSAzure#SignalR
0 notes
Text
Amazon Web Service & Adobe Experience Manager:- A Journey together (Part-10)
In the previous parts (1,2,3,4,5,6,7,8 & 9) we discussed how one day digital market leader meet with the a friend AWS in the Cloud and become very popular pair. It bring a lot of gifts for the digital marketing persons. Then we started a journey into digital market leader house basement and structure, mainly repository CRX and the way its MK organized. Ways how both can live and what smaller modules they used to give architectural benefits.Also visited how they are structured together to give more on AEM eCommerce and Adobe Creative cloud .In the last part we have discussed how we can use AEM as AEM cloud open source with effortless solution to take advantage of AWS, that one is first part of the story. We will continue in this part more interesting portion in this part.
As promised in the in part 8, We started journey of AEM OpenCloud , in the earlier part we have explored few interesting facts about it .In this part as well will continue see more on AEM OpenCloud, a variant of AEM cloud it provide as open source platform for running AEM on AWS.
I hope now you ready to go with this continues journey to move AEM OpenCloud with open source benefits all in one bundled solutions.
So let set go.....................

Continued....
AEM OpenCloud Full-Set Architecture
AEM OpenCloud full-set architecture is a full-featured environment, suitable for PROD and STAGE environments. It includes AEM Publish, Author-Dispatcher, and Publish-Dispatcher EC2 instances within Auto Scaling groups which (combined with an Orchestrator application) provide the capability to manage AEM capacity as the instances scale out and scale in according to the load on the Dispatcher. Orchestrator application manages AEM replication and flush agents as instances are created and terminated. This architecture also includes chaos-testing capability by using Netflix Chaos Monkey, which can be configured to randomly terminate either one of those instances within the ASG , or allow the architecture to live in production, continuously verifying that AEM OpenCloud can automatically recover from failure.
Netflix Chaos Monkey:-

Chaos Monkey is responsible for randomly terminating instances in production to ensure that engineers implement their services to be resilient to instance failures.
AEM Author Primary and Author Standby are managed separately where a failure on Author Primary instance can be mitigated by promoting an Author Standby to become the new Author Primary as soon as possible, while a new environment is being built in parallel and will take over as the new environment, replacing the one which lost its Author Primary.
Full-set architecture uses Amazon CloudFront as the CDN, sitting in front of AEM Publish-Dispatcher load balancer, providing global distribution of AEM cached content.
Full-set offers three types of content backup mechanisms: AEM package backup, live AEM repository EBS snapshots (taken when all AEM instances are up and running), and offline AEM repository EBS snapshots (taken when AEM Author and Publish are stopped). You can use any of these backups for blue-green deployment, providing the capability to replicate a complete environment, or to restore an environment from any point of time.

On the security front, this architecture provides a minimal attack surface with one public entry point to either Amazon CloudFront distribution or an AEM Publish-Dispatcher load balancer, whereas the other entry point is for AEM Author-Dispatcher load balancer.
AEM OpenCloud supports encryption using AWS KMS (Encryption Cryptography Signing - AWS Key Management Service ) keys across its AWS resources.
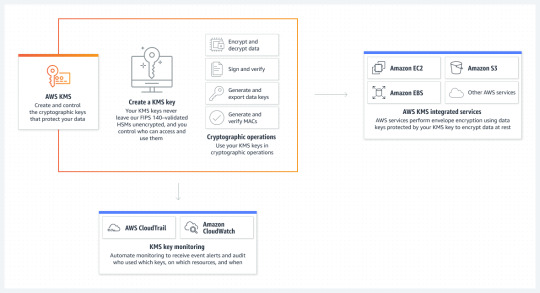
The full-set architecture also includes an Amazon CloudWatch Monitoring Dashboard (Using Amazon CloudWatch dashboards - Amazon CloudWatch) which visualizes the capacity of AEM Author-Dispatcher, Author Primary, Author Standby, Publish, and Publish-Dispatcher, along with their CPU, memory, and disk consumptions.
Amazon CloudWatch Alarms(Using Amazon CloudWatch alarms - Amazon CloudWatch) are also configured across the most important AWS resources, allowing notification mechanism via an SNS topic(Setting up Amazon SNS notifications - Amazon CloudWatch).
In this interesting journey we are continuously walking through AEM OpenCloud an open source variant of AEM and AWS. Few partner provide quick start for it in few clicks.So any this variation very quicker and effortless variation which gives deliver holistic, personalized experiences at scale, tailoring each moment of your digital marketing journey.
For more details on this interesting Journey you can browse back earlier parts from 1-9.
Keep reading.......
#aem#adobe#aws#wcm#aws lambda#cloud#programing#ec2#elb#security#AEM Open Cloud#migration#CURL#jenkins the librarians#ci/cd#xss#ddos attack#ddos protection#ddos#Distributed Denial of Service#Apache#cross site scripting#dispatcher#Security Checklist#mod_rewrite#mod_security#SAML#crx#publish#author
1 note
·
View note
Text
What are the top 10 most used Microsoft Azure services in 2023?
In 2008, Microsoft Azure services were first introduced, later commercially available in 2010. In the past few decades, the demand for Azure App services has increased and today approximately 90% of Fortune 500 companies use the services of Microsoft Azure as priorities. As a cloud service provider, Azure offers numerous services, initiating from building project repositories to managing code, tasks, deployment, and service maintenance.
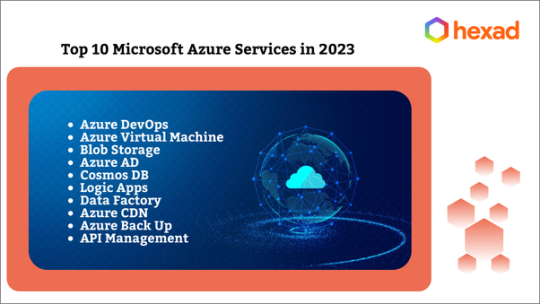
Azure offers technical support in more than 40+ geographies and more than 600 different services, making it the market leader. Coming to the top 10 most used Microsoft Azure services in 2023, I would like to list them along with a brief description of each.
1. Azure DevOps
Among all services, Azure DevOps is the ever-green of all times. It is the most reliable and intelligent tool to manage projects, test and deploy code via CI/CD. Currently, Azure DevOps is a comprehensive set of different Azure services such as Azure Repos, Azure Pipelines, Azure Boards, Azure Test Plans, Azure Artifacts, etc. At Hexad, we have DevOps which provides the best and most custom software development services as per our client’s requirements.
2. Azure Virtual Machines
A virtual machine is a computer-like environment. Microsoft Azure offers the possibility of creating virtual machines with Windows and Linux operating systems according to client’s requirements to meet their business needs. Azure allows the creation of virtual machines (VMs) such as compute-optimized VMs, memory-optimized VMs, stretchable VMs, and compute-optimized VMs. As per the knowledge and expertise of our Azure developers, each virtual machine has its own virtual hardware and specifications depending on the chosen plan.
3. Azure Blob Storage
Blob storage is a service for storing large amounts of unstructured data that does not fit a specific data model or definition. Finally, it is used to add images or documents to the browser and write log files simultaneously. It is a storage device that also offers streaming media files. Our Azure experts have found that it is used to back up and restore database backup files.
4. Azure AD
Azure Active Directory handles authentication and authorization for any system from any location and provides user credentials for users who log in. At Hexad, we have done some Azure projects where Azure AD service has allowed employees of the organization to access resources from both external and internal sources.
5. Azure CosmosDB
At Hexad, Azure developers offer a fully managed NoSQL database service. We have utilized Cosmos DB, which aims for faster response times to queries and is also used to manage large archive databases with guaranteed speed at any scale. Besides, Cosmos DB stores data in JSON documents and provides API endpoints for managing these documents via the SDK.
6. Logic Apps
In recent years, technology has enhanced and the Azure Logic Apps slowly gained popularity, but it is still a powerful integration solution for a few apps. It will help connect applications, data, and devices from anywhere, further allowing almost all types of B2B transactions to be carried out most efficiently through electronic data interchange standards.
7. Azure Data Factory
Our Azure developers have used the Azure data factory, which helps to accept data from various input resources and automates data transfer through various pipelines. Depending on the data processing, the result can be published to Azure Data Lake for business analytics applications. Thus, at Hexad, our developers have found that Data Factory is an Azure service that utilizes compute to monitor workflows and perform better data analysis rather than data storage.
8. Azure CDN
The Azure Content Delivery Network has intended its wings with a variety of service integrations such as web applications, Azure Storage, or Azure Cloud Services. In addition, it is holding a powerful position via its security mechanism, which allows a developer to spend less time in managing security solutions. One of the main advantages of using this service is the fast response time and low content load times.
9. Azure Backup
Azure Backup service has solved most companies' problems by providing privacy protection and a solution to reduce some human errors. We follow the backup SQL workloads as well as Azure VMs. Besides, providing unlimited data transfer and multiple storage options, this Azure service provides consistent backup for all applications. With its extensive use, our software developers have addressed one of the biggest issues is storage scalability and data backup management.
10. Azure API Management
This Azure service allows users to manage and publish web APIs with just a few clicks. API Management secures all APIs using filters, tokens, and keys, freeing a developer from various security vulnerabilities. It also provides API access to the microservices architecture. One of the features of this service is its consumer-based user model, which offers automatic scaling and high availability.
Azure cloud services are suitable for the whole company with reliable and cost-effective solutions thanks to the wide range of these services. At Hexad Infosoft, Azure services intended for professionals and enterprises offer all-around alternatives to the traditional means of organizational processes, with top Azure services greatly improving performance. If you require any kind of Azure consulting services or any kind of implementation or migration, please share your requirements at [email protected]. Please visit our website-https://hexad.de/en/index.html
#azure services#azuredevelopers#azuredevelopment#hexad#hexad_infosoft#softwaredevelopment#software development company
0 notes
Text
Introduction to AWS Cloud Development
Introducing AWS cloud development: an advantageous, flexible, and scalable environment that provides numerous features to organizations and individuals. Using this platform, developers can quickly build, evaluate, and deploy applications - allowing them more time to focus on other areas in their business or project! In this article, we'll review its numerous benefits and discuss the many available services and tools.

Benefits of AWS Cloud Development
AWS cloud development offers numerous benefits, including 1. With AWS, developers are provided a flexible and adjustable infrastructure that can easily grow or reduce with the changing demand. Without any fuss or hassle, resources can be modified to accommodate your applications' needs.
2. Choose AWS and be economical: With AWS, developers only pay for the required services. In turn, this makes it an economical choice regarding software development. Start saving money while receiving optimal service! 3. With AWS's reliable infrastructure, developers can confidently build and launch their applications, knowing that maximum uptime with minimal downtime is guaranteed. The dependable architecture enables them to rest assured that their services are up and running optimally day in and day out. 4. With AWS, you can confidently trust in its robust security framework, which provides multiple layers of safety for applications and data. Developers no longer need to worry about their applications or data as a secure network protects them. AWS Services
With Amazon Web Services, developers can access a plethora of services to construct, evaluate and deploy their applications. These essential features encompass: 1. Amazon Elastic Compute Cloud (EC2) offers vast, adjustable computing power in the cloud. With EC2, developers can quickly and easily deploy their apps on virtual servers - perfect for businesses with ever-evolving demands! 2. Amazon Simple Storage Service (S3) is an infinitely scalable storage solution that allows developers to securely store and access limitless quantities of data anywhere. 3. For developers who need to quickly set up, manage and scale a relational database, Amazon Relational Database Service (RDS) is the perfect solution. RDS offers seamless support for MySQL, Oracle or PostgreSQL and provides simplified maintenance operations with secure backups - ensuring top quality performance every time. 4. Amazon Elastic Beanstalk makes it simple to deploy and run applications in various languages, including Java, .NET, PHP, Python, Ruby or Node.js – with no effort needed from you! This fully managed service provides an elastic platform that dynamically scales as your requirements change. AWS Tools Uncover the power of AWS for yourself! With its comprehensive suite of tools, developers can easily create, test, and launch their applications in no time. Amongst these innovative solutions are:
1. AWS CloudFormation: With this innovative service, developers can easily create and manage their AWS resources using templates. Utilizing CloudFormation makes it effortless to automate the deployment of any applications that have been developed.
2. Cutting-edge developers utilize AWS CodePipeline to automate the release process of their applications, empowering them with a fully managed continuous delivery service that is hassle free.
3. AWS CodeCommit is the ideal solution for developers who need a safe and trustworthy cloud-based source control service. This comprehensive platform enables users to store their code repositories with confidence, knowing that they are secure and fully managed.
4. With AWS CodeBuild, developers can now leverage the power of cloud computing to build and test their code without having to manage any infrastructure. Fully managed with no setup required, CodeBuild allows developers to focus on developing innovative projects for their customers quickly and efficiently.
Conclusion:
If you are a developer in need of an agile, cost-efficient, and secure platform for your applications to thrive on - AWS cloud development is the answer. With its broad spectrum of services and tools, it becomes more accessible than ever before to create complex products while benefiting from reliability and scalability. All this can be achieved without spending too much time or money with our one-of-a kind solution!
Practical logix offers a complete range of services to cover all your Cloud needs. Conducting a Cloud Strategy and Analysis is the most effective way to comprehend available options. In this step, you will be able to understand which types of Cloud Consulting Services would be best for you. We can also guide you in streamlining current workflows within the cloud environment, building solutions specifically designed to leverage cloud technology, and maintaining them professionally to stay up-to-date while optimizing usage levels of your overall infrastructure.
0 notes
Text
How to set up command-line access to Amazon Keyspaces (for Apache Cassandra) by using the new developer toolkit Docker image
Amazon Keyspaces (for Apache Cassandra) is a scalable, highly available, and fully managed Cassandra-compatible database service. Amazon Keyspaces helps you run your Cassandra workloads more easily by using a serverless database that can scale up and down automatically in response to your actual application traffic. Because Amazon Keyspaces is serverless, there are no clusters or nodes to provision and manage. You can get started with Amazon Keyspaces with a few clicks in the console or a few changes to your existing Cassandra driver configuration. In this post, I show you how to set up command-line access to Amazon Keyspaces by using the keyspaces-toolkit Docker image. The keyspaces-toolkit Docker image contains commonly used Cassandra developer tooling. The toolkit comes with the Cassandra Query Language Shell (cqlsh) and is configured with best practices for Amazon Keyspaces. The container image is open source and also compatible with Apache Cassandra 3.x clusters. A command line interface (CLI) such as cqlsh can be useful when automating database activities. You can use cqlsh to run one-time queries and perform administrative tasks, such as modifying schemas or bulk-loading flat files. You also can use cqlsh to enable Amazon Keyspaces features, such as point-in-time recovery (PITR) backups and assign resource tags to keyspaces and tables. The following screenshot shows a cqlsh session connected to Amazon Keyspaces and the code to run a CQL create table statement. Build a Docker image To get started, download and build the Docker image so that you can run the keyspaces-toolkit in a container. A Docker image is the template for the complete and executable version of an application. It’s a way to package applications and preconfigured tools with all their dependencies. To build and run the image for this post, install the latest Docker engine and Git on the host or local environment. The following command builds the image from the source. docker build --tag amazon/keyspaces-toolkit --build-arg CLI_VERSION=latest https://github.com/aws-samples/amazon-keyspaces-toolkit.git The preceding command includes the following parameters: –tag – The name of the image in the name:tag Leaving out the tag results in latest. –build-arg CLI_VERSION – This allows you to specify the version of the base container. Docker images are composed of layers. If you’re using the AWS CLI Docker image, aligning versions significantly reduces the size and build times of the keyspaces-toolkit image. Connect to Amazon Keyspaces Now that you have a container image built and available in your local repository, you can use it to connect to Amazon Keyspaces. To use cqlsh with Amazon Keyspaces, create service-specific credentials for an existing AWS Identity and Access Management (IAM) user. The service-specific credentials enable IAM users to access Amazon Keyspaces, but not access other AWS services. The following command starts a new container running the cqlsh process. docker run --rm -ti amazon/keyspaces-toolkit cassandra.us-east-1.amazonaws.com 9142 --ssl -u "SERVICEUSERNAME" -p "SERVICEPASSWORD" The preceding command includes the following parameters: run – The Docker command to start the container from an image. It’s the equivalent to running create and start. –rm –Automatically removes the container when it exits and creates a container per session or run. -ti – Allocates a pseudo TTY (t) and keeps STDIN open (i) even if not attached (remove i when user input is not required). amazon/keyspaces-toolkit – The image name of the keyspaces-toolkit. us-east-1.amazonaws.com – The Amazon Keyspaces endpoint. 9142 – The default SSL port for Amazon Keyspaces. After connecting to Amazon Keyspaces, exit the cqlsh session and terminate the process by using the QUIT or EXIT command. Drop-in replacement Now, simplify the setup by assigning an alias (or DOSKEY for Windows) to the Docker command. The alias acts as a shortcut, enabling you to use the alias keyword instead of typing the entire command. You will use cqlsh as the alias keyword so that you can use the alias as a drop-in replacement for your existing Cassandra scripts. The alias contains the parameter –v "$(pwd)":/source, which mounts the current directory of the host. This is useful for importing and exporting data with COPY or using the cqlsh --file command to load external cqlsh scripts. alias cqlsh='docker run --rm -ti -v "$(pwd)":/source amazon/keyspaces-toolkit cassandra.us-east-1.amazonaws.com 9142 --ssl' For security reasons, don’t store the user name and password in the alias. After setting up the alias, you can create a new cqlsh session with Amazon Keyspaces by calling the alias and passing in the service-specific credentials. cqlsh -u "SERVICEUSERNAME" -p "SERVICEPASSWORD" Later in this post, I show how to use AWS Secrets Manager to avoid using plaintext credentials with cqlsh. You can use Secrets Manager to store, manage, and retrieve secrets. Create a keyspace Now that you have the container and alias set up, you can use the keyspaces-toolkit to create a keyspace by using cqlsh to run CQL statements. In Cassandra, a keyspace is the highest-order structure in the CQL schema, which represents a grouping of tables. A keyspace is commonly used to define the domain of a microservice or isolate clients in a multi-tenant strategy. Amazon Keyspaces is serverless, so you don’t have to configure clusters, hosts, or Java virtual machines to create a keyspace or table. When you create a new keyspace or table, it is associated with an AWS Account and Region. Though a traditional Cassandra cluster is limited to 200 to 500 tables, with Amazon Keyspaces the number of keyspaces and tables for an account and Region is virtually unlimited. The following command creates a new keyspace by using SingleRegionStrategy, which replicates data three times across multiple Availability Zones in a single AWS Region. Storage is billed by the raw size of a single replica, and there is no network transfer cost when replicating data across Availability Zones. Using keyspaces-toolkit, connect to Amazon Keyspaces and run the following command from within the cqlsh session. CREATE KEYSPACE amazon WITH REPLICATION = {'class': 'SingleRegionStrategy'} AND TAGS = {'domain' : 'shoppingcart' , 'app' : 'acme-commerce'}; The preceding command includes the following parameters: REPLICATION – SingleRegionStrategy replicates data three times across multiple Availability Zones. TAGS – A label that you assign to an AWS resource. For more information about using tags for access control, microservices, cost allocation, and risk management, see Tagging Best Practices. Create a table Previously, you created a keyspace without needing to define clusters or infrastructure. Now, you will add a table to your keyspace in a similar way. A Cassandra table definition looks like a traditional SQL create table statement with an additional requirement for a partition key and clustering keys. These keys determine how data in CQL rows are distributed, sorted, and uniquely accessed. Tables in Amazon Keyspaces have the following unique characteristics: Virtually no limit to table size or throughput – In Amazon Keyspaces, a table’s capacity scales up and down automatically in response to traffic. You don’t have to manage nodes or consider node density. Performance stays consistent as your tables scale up or down. Support for “wide” partitions – CQL partitions can contain a virtually unbounded number of rows without the need for additional bucketing and sharding partition keys for size. This allows you to scale partitions “wider” than the traditional Cassandra best practice of 100 MB. No compaction strategies to consider – Amazon Keyspaces doesn’t require defined compaction strategies. Because you don’t have to manage compaction strategies, you can build powerful data models without having to consider the internals of the compaction process. Performance stays consistent even as write, read, update, and delete requirements change. No repair process to manage – Amazon Keyspaces doesn’t require you to manage a background repair process for data consistency and quality. No tombstones to manage – With Amazon Keyspaces, you can delete data without the challenge of managing tombstone removal, table-level grace periods, or zombie data problems. 1 MB row quota – Amazon Keyspaces supports the Cassandra blob type, but storing large blob data greater than 1 MB results in an exception. It’s a best practice to store larger blobs across multiple rows or in Amazon Simple Storage Service (Amazon S3) object storage. Fully managed backups – PITR helps protect your Amazon Keyspaces tables from accidental write or delete operations by providing continuous backups of your table data. The following command creates a table in Amazon Keyspaces by using a cqlsh statement with customer properties specifying on-demand capacity mode, PITR enabled, and AWS resource tags. Using keyspaces-toolkit to connect to Amazon Keyspaces, run this command from within the cqlsh session. CREATE TABLE amazon.eventstore( id text, time timeuuid, event text, PRIMARY KEY(id, time)) WITH CUSTOM_PROPERTIES = { 'capacity_mode':{'throughput_mode':'PAY_PER_REQUEST'}, 'point_in_time_recovery':{'status':'enabled'} } AND TAGS = {'domain' : 'shoppingcart' , 'app' : 'acme-commerce' , 'pii': 'true'}; The preceding command includes the following parameters: capacity_mode – Amazon Keyspaces has two read/write capacity modes for processing reads and writes on your tables. The default for new tables is on-demand capacity mode (the PAY_PER_REQUEST flag). point_in_time_recovery – When you enable this parameter, you can restore an Amazon Keyspaces table to a point in time within the preceding 35 days. There is no overhead or performance impact by enabling PITR. TAGS – Allows you to organize resources, define domains, specify environments, allocate cost centers, and label security requirements. Insert rows Before inserting data, check if your table was created successfully. Amazon Keyspaces performs data definition language (DDL) operations asynchronously, such as creating and deleting tables. You also can monitor the creation status of a new resource programmatically by querying the system schema table. Also, you can use a toolkit helper for exponential backoff. Check for table creation status Cassandra provides information about the running cluster in its system tables. With Amazon Keyspaces, there are no clusters to manage, but it still provides system tables for the Amazon Keyspaces resources in an account and Region. You can use the system tables to understand the creation status of a table. The system_schema_mcs keyspace is a new system keyspace with additional content related to serverless functionality. Using keyspaces-toolkit, run the following SELECT statement from within the cqlsh session to retrieve the status of the newly created table. SELECT keyspace_name, table_name, status FROM system_schema_mcs.tables WHERE keyspace_name = 'amazon' AND table_name = 'eventstore'; The following screenshot shows an example of output for the preceding CQL SELECT statement. Insert sample data Now that you have created your table, you can use CQL statements to insert and read sample data. Amazon Keyspaces requires all write operations (insert, update, and delete) to use the LOCAL_QUORUM consistency level for durability. With reads, an application can choose between eventual consistency and strong consistency by using LOCAL_ONE or LOCAL_QUORUM consistency levels. The benefits of eventual consistency in Amazon Keyspaces are higher availability and reduced cost. See the following code. CONSISTENCY LOCAL_QUORUM; INSERT INTO amazon.eventstore(id, time, event) VALUES ('1', now(), '{eventtype:"click-cart"}'); INSERT INTO amazon.eventstore(id, time, event) VALUES ('2', now(), '{eventtype:"showcart"}'); INSERT INTO amazon.eventstore(id, time, event) VALUES ('3', now(), '{eventtype:"clickitem"}') IF NOT EXISTS; SELECT * FROM amazon.eventstore; The preceding code uses IF NOT EXISTS or lightweight transactions to perform a conditional write. With Amazon Keyspaces, there is no heavy performance penalty for using lightweight transactions. You get similar performance characteristics of standard insert, update, and delete operations. The following screenshot shows the output from running the preceding statements in a cqlsh session. The three INSERT statements added three unique rows to the table, and the SELECT statement returned all the data within the table. Export table data to your local host You now can export the data you just inserted by using the cqlsh COPY TO command. This command exports the data to the source directory, which you mounted earlier to the working directory of the Docker run when creating the alias. The following cqlsh statement exports your table data to the export.csv file located on the host machine. CONSISTENCY LOCAL_ONE; COPY amazon.eventstore(id, time, event) TO '/source/export.csv' WITH HEADER=false; The following screenshot shows the output of the preceding command from the cqlsh session. After the COPY TO command finishes, you should be able to view the export.csv from the current working directory of the host machine. For more information about tuning export and import processes when using cqlsh COPY TO, see Loading data into Amazon Keyspaces with cqlsh. Use credentials stored in Secrets Manager Previously, you used service-specific credentials to connect to Amazon Keyspaces. In the following example, I show how to use the keyspaces-toolkit helpers to store and access service-specific credentials in Secrets Manager. The helpers are a collection of scripts bundled with keyspaces-toolkit to assist with common tasks. By overriding the default entry point cqlsh, you can call the aws-sm-cqlsh.sh script, a wrapper around the cqlsh process that retrieves the Amazon Keyspaces service-specific credentials from Secrets Manager and passes them to the cqlsh process. This script allows you to avoid hard-coding the credentials in your scripts. The following diagram illustrates this architecture. Configure the container to use the host’s AWS CLI credentials The keyspaces-toolkit extends the AWS CLI Docker image, making keyspaces-toolkit extremely lightweight. Because you may already have the AWS CLI Docker image in your local repository, keyspaces-toolkit adds only an additional 10 MB layer extension to the AWS CLI. This is approximately 15 times smaller than using cqlsh from the full Apache Cassandra 3.11 distribution. The AWS CLI runs in a container and doesn’t have access to the AWS credentials stored on the container’s host. You can share credentials with the container by mounting the ~/.aws directory. Mount the host directory to the container by using the -v parameter. To validate a proper setup, the following command lists current AWS CLI named profiles. docker run --rm -ti -v ~/.aws:/root/.aws --entrypoint aws amazon/keyspaces-toolkit configure list-profiles The ~/.aws directory is a common location for the AWS CLI credentials file. If you configured the container correctly, you should see a list of profiles from the host credentials. For instructions about setting up the AWS CLI, see Step 2: Set Up the AWS CLI and AWS SDKs. Store credentials in Secrets Manager Now that you have configured the container to access the host’s AWS CLI credentials, you can use the Secrets Manager API to store the Amazon Keyspaces service-specific credentials in Secrets Manager. The secret name keyspaces-credentials in the following command is also used in subsequent steps. docker run --rm -ti -v ~/.aws:/root/.aws --entrypoint aws amazon/keyspaces-toolkit secretsmanager create-secret --name keyspaces-credentials --description "Store Amazon Keyspaces Generated Service Credentials" --secret-string "{"username":"SERVICEUSERNAME","password":"SERVICEPASSWORD","engine":"cassandra","host":"SERVICEENDPOINT","port":"9142"}" The preceding command includes the following parameters: –entrypoint – The default entry point is cqlsh, but this command uses this flag to access the AWS CLI. –name – The name used to identify the key to retrieve the secret in the future. –secret-string – Stores the service-specific credentials. Replace SERVICEUSERNAME and SERVICEPASSWORD with your credentials. Replace SERVICEENDPOINT with the service endpoint for the AWS Region. Creating and storing secrets requires CreateSecret and GetSecretValue permissions in your IAM policy. As a best practice, rotate secrets periodically when storing database credentials. Use the Secrets Manager helper script Use the Secrets Manager helper script to sign in to Amazon Keyspaces by replacing the user and password fields with the secret key from the preceding keyspaces-credentials command. docker run --rm -ti -v ~/.aws:/root/.aws --entrypoint aws-sm-cqlsh.sh amazon/keyspaces-toolkit keyspaces-credentials --ssl --execute "DESCRIBE Keyspaces" The preceding command includes the following parameters: -v – Used to mount the directory containing the host’s AWS CLI credentials file. –entrypoint – Use the helper by overriding the default entry point of cqlsh to access the Secrets Manager helper script, aws-sm-cqlsh.sh. keyspaces-credentials – The key to access the credentials stored in Secrets Manager. –execute – Runs a CQL statement. Update the alias You now can update the alias so that your scripts don’t contain plaintext passwords. You also can manage users and roles through Secrets Manager. The following code sets up a new alias by using the keyspaces-toolkit Secrets Manager helper for passing the service-specific credentials to Secrets Manager. alias cqlsh='docker run --rm -ti -v ~/.aws:/root/.aws -v "$(pwd)":/source --entrypoint aws-sm-cqlsh.sh amazon/keyspaces-toolkit keyspaces-credentials --ssl' To have the alias available in every new terminal session, add the alias definition to your .bashrc file, which is executed on every new terminal window. You can usually find this file in $HOME/.bashrc or $HOME/bash_aliases (loaded by $HOME/.bashrc). Validate the alias Now that you have updated the alias with the Secrets Manager helper, you can use cqlsh without the Docker details or credentials, as shown in the following code. cqlsh --execute "DESCRIBE TABLE amazon.eventstore;" The following screenshot shows the running of the cqlsh DESCRIBE TABLE statement by using the alias created in the previous section. In the output, you should see the table definition of the amazon.eventstore table you created in the previous step. Conclusion In this post, I showed how to get started with Amazon Keyspaces and the keyspaces-toolkit Docker image. I used Docker to build an image and run a container for a consistent and reproducible experience. I also used an alias to create a drop-in replacement for existing scripts, and used built-in helpers to integrate cqlsh with Secrets Manager to store service-specific credentials. Now you can use the keyspaces-toolkit with your Cassandra workloads. As a next step, you can store the image in Amazon Elastic Container Registry, which allows you to access the keyspaces-toolkit from CI/CD pipelines and other AWS services such as AWS Batch. Additionally, you can control the image lifecycle of the container across your organization. You can even attach policies to expiring images based on age or download count. For more information, see Pushing an image. Cheat sheet of useful commands I did not cover the following commands in this blog post, but they will be helpful when you work with cqlsh, AWS CLI, and Docker. --- Docker --- #To view the logs from the container. Helpful when debugging docker logs CONTAINERID #Exit code of the container. Helpful when debugging docker inspect createtablec --format='{{.State.ExitCode}}' --- CQL --- #Describe keyspace to view keyspace definition DESCRIBE KEYSPACE keyspace_name; #Describe table to view table definition DESCRIBE TABLE keyspace_name.table_name; #Select samples with limit to minimize output SELECT * FROM keyspace_name.table_name LIMIT 10; --- Amazon Keyspaces CQL --- #Change provisioned capacity for tables ALTER TABLE keyspace_name.table_name WITH custom_properties={'capacity_mode':{'throughput_mode': 'PROVISIONED', 'read_capacity_units': 4000, 'write_capacity_units': 3000}} ; #Describe current capacity mode for tables SELECT keyspace_name, table_name, custom_properties FROM system_schema_mcs.tables where keyspace_name = 'amazon' and table_name='eventstore'; --- Linux --- #Line count of multiple/all files in the current directory find . -type f | wc -l #Remove header from csv sed -i '1d' myData.csv About the Author Michael Raney is a Solutions Architect with Amazon Web Services. https://aws.amazon.com/blogs/database/how-to-set-up-command-line-access-to-amazon-keyspaces-for-apache-cassandra-by-using-the-new-developer-toolkit-docker-image/
1 note
·
View note
Text
Building a Mouse Squad Against COVID-19
https://sciencespies.com/nature/building-a-mouse-squad-against-covid-19/
Building a Mouse Squad Against COVID-19

Tucked away on Mount Desert Island off the coast of Maine, the Jackson Laboratory (JAX) may seem removed from the pandemic roiling the world. It’s anything but. The lab is busy breeding animals for studying the SARS-CoV-2 coronavirus and is at the forefront of efforts to minimize the disruption of research labs everywhere.
During normal times, the 91-year-old independent, nonprofit biomedical research institution serves as a leading supplier of research mice to labs around the world. It breeds, maintains and distributes more than 11,000 strains of genetically defined mice for research on a huge array of disorders: common diseases such as diabetes and cancer through to rare blood disorders such as aplastic anemia. Scientists studying aging can purchase elderly mice from JAX for their work; those researching disorders of balance can turn to mice with defects of the inner ear that cause the creatures to keep moving in circles.
But these are not normal times. The Covid-19 pandemic has skyrocketed the demand for new strains of mice to help scientists understand the progression of the disease, test existing drugs, find new therapeutic targets and develop vaccines. At the same time, with many universities scaling back employees on campus, the coronavirus crisis forced labs studying a broad range of topics to cull their research animals, many of which took years to breed and can take equally long to recoup.
JAX is responding to both concerns, having raced to collect and cryopreserve existing strains of lab mice and to start breeding new ones for CoV-2 research.
Overseeing these efforts is neuroscientist Cathleen “Cat” Lutz, director of the Mouse Repository and the Rare and Orphan Disease Center at JAX. Lutz spoke with Knowable Magazine about the lab’s current round-the-clock activity. This conversation has been edited for length and clarity.
When did you first hear about the new coronavirus?
We heard about it in early January, like everyone else. I have colleagues at the Jackson Laboratory facilities in China. One of them, a young man named Qiming Wang, contacted me on February 3. He is a researcher in our Shanghai office, but he takes the bullet train to Wuhan on the weekends to be back with his family. He was on lockdown in Wuhan. He began describing the situation in China. Police were patrolling the streets. There were a couple of people in his building who were diagnosed positive for Covid-19. It was an incredibly frightening time.
At the time, in the US we were not really thinking about the surge that was going to hit us. And here was a person who was living through it. He sent us a very heartfelt and touching email asking: What could JAX do?
We started discussing the various ways that we could genetically engineer mice to better understand Covid-19. And that led us to mice that had been developed after the 2003 SARS outbreak, which was caused by a different coronavirus called SARS-CoV. There were mouse models made by various people, including infectious disease researcher Stanley Perlman at the University of Iowa, to study the SARS-CoV infection. It became clear to us that these mice would be very useful for studying SARS-CoV-2 and Covid-19.
We got on the phone to Stanley Perlman the next day.
What’s special about Perlman’s mice?
These mice, unlike normal mice, are susceptible to SARS.
In humans, the virus’ spike protein attaches to the ACE2 receptor on epithelial cells and enters the lungs. But coronaviruses like SARS-CoV and SARS-CoV-2 don’t infect your normal laboratory mouse — or, if they do, it’s at a very low rate of infection and the virus doesn’t replicate readily. That’s because the virus’ spike protein doesn’t recognize the regular lab mouse’s ACE2 receptor. So the mice are relatively protected.
Perlman made the mice susceptible by introducing into them the gene for the human ACE2 receptor. So now, in addition to the mouse ACE2 receptor, you have the human ACE2 receptor being made in these mice, making it possible for the coronavirus to enter the lungs.




Cat Lutz (left) and colleagues at work in a lab at the Jackson Laboratory.
(Aaron Boothroyd / The Jackson Laboratory)
Perlman, in a 2007 paper about these mice, recognized that SARS wasn’t the first coronavirus, and it wasn’t going to be the last. The idea that we would be faced at some point with another potential coronavirus infection, and that these mice could possibly be useful, was like looking into a crystal ball.
How did Perlman respond to the JAX request?
It was an immediate yes. He had cryopreserved vials of sperm from these mice. One batch was kept at a backup facility. He immediately released the backup vials and sent us his entire stock — emptied his freezer and gave it to us. We had the sperm delivered to us within 48 hours from when Qiming contacted me.
What have you been doing with the sperm?
We start with C57BL/6 mice, the normal laboratory strain. We have thousands and thousands of them. We stimulate the females to superovulate and collect their eggs. And then, just like in an IVF clinic, we take the cryopreserved sperm from Perlman’s lab, thaw it very carefully, and then put the sperm in with the eggs and let them fertilize. Then we transplant the fertilized eggs into females that have been hormonally readied for pregnancy. The females accept the embryos that then gestate to term and, voila, we have Perlman’s mice. We can regenerate a thousand mice in one generation.
Have you made any changes to Perlman’s strain?
We haven’t made any changes. Our primary directive is to get these mice out to the community so that they can begin working with the antivirals and the vaccine therapies.
But these mice haven’t yet been infected with the new coronavirus. How do you know they’ll be useful?
We know that they were severely infected with SARS-CoV, and so we expect the response to be very severe with CoV-2. It’s not the same virus, but very similar. The spike protein is structurally nearly the same, so the method of entry into the lungs should be the same. If there’s any model out there that is capable of producing a response that would that would look like a severe disease, a Covid-19 infection, it’s these mice. We have every expectation that they’ll behave that way.
Have researchers been asking for these mice?
We’ve had over 250 individual requests for large numbers of mice. If you do the math, it’s quite a lot. We’ll be able to supply all of those mice within the first couple weeks of July. That’s how fast we got this up and going. It’s kind of hard to believe because, on one hand, you don’t have a single mouse to spare today, but in eight weeks, you’re going to have this embarrassment of riches.
How will researchers use these mice?
After talking with people, we learned that they don’t yet know how they are going to use them, because they don’t know how these mice are going to infect. This is Covid-19, not SARS, so it’s slightly different and they need to do some pilot experiments to understand the viral dose [the amount of the virus needed to make a mouse sick], the infectivity [how infectious the virus is in these mice], the viral replication, and so on. What’s the disease course going to be? Is it going to be multi-organ or multi-system? Is it going to be contained to the lungs? People just don’t know.
The researchers doing the infectivity experiments, which require solitary facilities and not everybody can do them, have said without hesitation: “As soon as we know how these mice respond, we’ll let you know.” They are not going to wait for their Cell publication or anything like that. They know it’s the right thing to do.




Scientist Margaret Dickie in a mouse room at JAX in 1951. Jax was founded in 1929 — today, it employs more than 2,200 people and has several United States facilities as well as one in Shanghai.
(The Jackson Laboratory)
Research labs around the country have shut down because of the pandemic and some had to euthanize their research animals. Was JAX able to help out in any way?
We were a little bit lucky in Maine because the infection rate was low. We joke that the social distancing here is more like six acres instead of six feet apart. We had time to prepare and plan for how we would reduce our research program, so that we can be ready for when we come back.
A lot of other universities around the country did not have that luxury. They had 24 hours to cull their mouse colonies. A lot of people realized that some of their mice weren’t cryopreserved. If they had to reduce their colonies, they would risk extinction of those mice. Anybody who’s invested their research and time into these mice doesn’t want that to happen.
So they called us and asked for help with cryopreservation of their mice. We have climate-controlled trucks that we use to deliver our mice. I call them limousines — they’re very comfortable. We were able to pick up their mice in these “rescue trucks” and cryopreserve their sperm and embryos here at JAX, so that when these labs do reopen, those mice can be regenerated. I think that’s very comforting to the researchers.
Did JAX have any prior experience like this, from having dealt with past crises?
Yes. But those have been natural disasters. Hurricane Sandy was one, Katrina was another. Vivariums in New York and Louisiana were flooding and people were losing their research animals. They were trying to preserve and protect anything that they could. So that was very similar.
JAX has also been involved in its own disasters. We had a fire in 1989. Before that, there was a fire in 1947 where almost the entire Mount Desert Island burned to the ground. We didn’t have cryopreservation in 1947. People ran into buildings, grabbing cages with mice, to rescue them. We are very conscientious because we’ve lived through it ourselves.
How have you been coping with the crisis?
It’s been probably the longest 12 weeks that I’ve had to deal with, waiting for these mice to be born and to breed. I’ve always known how important mice are for research, but you never know how critically important they are until you realize that they’re the only ones that are out there.
We wouldn’t have these mice if it weren’t for Stanley Perlman. And I think of my friend Qiming emailing me from his apartment in Wuhan, where he was going through this horrible situation that we’re living in now. Had it not been for him reaching out and us having these conversations and looking through the literature to see what we had, we probably wouldn’t have reached this stage as quickly as we have. Sometimes it just takes one person to really make a difference.
This article originally appeared in Knowable Magazine, an independent journalistic endeavor from Annual Reviews. Sign up for the newsletter.
#Nature
3 notes
·
View notes
Text
CRM script for your business
Customer relationship management (CRM) is a technology which is used for managing company’s relationships and interactions with potential customers. The primary purpose of this technology is to improve business relationships. A CRM system is used by companies and to stay connected to customers, streamline processes and increase profitability. A CRM system helps you to focus on company’s relationships with individuals i.e. customers, service users, colleagues, or suppliers. It provides supports and additional services throughout the relationship.
iBilling – CRM, Accounting and Billing Software
iBilling is the perfect software to manage customers data. It helps to communicate with customers clearly. It has all the essential features like simplicity, and user-friendly interface. It is affordable and scalable business software which works for your business perfectly. You can also manage payments effortlessly because it has multiple payment gateways.
DEMO DOWNLOAD
Repairer Pro – Repairs, HRM, CRM & much more
Repairer pro is complete management software which is powerful and flexible. It can be used to repair ships with timeclock, commissions, payrolls and complete inventory system. Its reporting feature is accurate and powerful. Not only You can check the status and invoices of repair but your customers can also take benefit from this feature.
DEMODOWNLOAD
Puku CRM – Realtime Open Source CRM
Puku CRM is an online software that is especially designed for any kind of business whether you are a company, freelancer or any other type of business, this CRM software is made for you. It is developed with modern design that works on multiple devices. It primarily focuses on customers and leads tracking. It helps you to increase the profit of your business.
DEMO DOWNLOAD
CRM – Ticketing, sales, products, client and business management system with material design
The purpose of CRM software is to perfectly manage the client relationship, that’s how your business can grow without any resistance. This application is made especially for such type of purpose. It is faster and secure. It is developed by using Laravel 5.4 version. You can update any time for framework or script. It has two panels; one is Admin dashboard and the other is client panel. Admin dashboard is used to manage business activities while client panel is made for customers functionalities.
DEMO DOWNLOAD
Abacus – Manufacture sale CRM with POS
It is a manufacture and sale CRM with pos. it can easily manage products, merchants and suppliers. It also can be used to see transaction histories of sellers and suppliers while managing your relationships with sellers and buyers. Moreover, its amazing features include social login and registration, manage bank accounts and transactions and manage payments. It also manages invoices and accounting tasks. It has many features which are powerful and simple to use.
DEMO DOWNLOAD
Sales management software Laravel – CRM
It is a perfect CRM software with quick installation in 5 steps. it is designed precisely according to the needs of a CRM software. It has user-friendly interface and fully functional sales system. Customer management is effortless by using this software. You can mange your products and invoices without any hustle.
DEMO DOWNLOAD
Sales CRM Marketing and Sales Management Software
It is a sales CRM that consists a tracking system for marketing campaigns, leads and conversions to sales. It can boost your sales up-to 500% ROI, following the normal standards of marketing. It has built in SMTP email integration which helps you to easily track your emails from the application and the leads easily. You can also track the status of campaign, ROI and sales quality. Sales CRM will proof very helpful to your business. Whether your business is small, freelancing, or a large-scale organization.
DEMO DOWNLOAD
doitX : Complete Sales CRM with Invoicing, Expenses, Bulk SMS and Email Marketing
it is a complete and full fledge sales CRM which includes invoicing, expenses, bulk sms and email marketing software that is an amazing feature for any company, small business owners, or many other business-related uses. It is a perfect tool which can organize all data efficiently. With its feature of excellent design, doitX helps you to look more professional to you clients as well as to the public. it improves the performance of your business in every aspect. You can do your sales operations while all the information is easily accessible. It also helps you to keep track of your products, sales, marketing records, payments, invoices and sends you timely notifications so that you can take appropriate actions. It can perform whole company’s operations in a simple and effortless way. It also has many other key features which your business deserves.
DEMO DOWNLOAD
Laravel BAP – Modular Application Platform and CRM
Laravel Bap is all in one application at low price with great benefits. If you are going to build a complex application that has multiple modules, rest API, fast and reliable, then this application is made for you. It is a modular backend application platform that is build by using Laravel 5.6, Twitter Bootstrap and SCSS. It is easy to extend and customize. It has over 20 amazing features.
DEMO DOWNLOAD
LaraOffice Ultimate CRM and Project Management System
LaraOffice is a complete CRM and Project management system which is a fully featured software. It has multi-login functionality. It helps to manage the daily sales, customer follow ups, meetings, invoices, marketing, services and orders. Customers’ requirements can be fulfilled by such an ultimate CRM and project management software solution perfectly. LaraOfficre CRM helps you to look more professional and authoritative to your customers as well as to the public.
DEMO DOWNLOAD
Banquet CRM – Events and Banquets management web application
Banquet CRM is a web application which is especially designed for restaurants, hotel and unique venues to increase sales and streamline the planning process. You can capture and convert new event leads from anywhere. It allows you to deliver branded, professional-looking proposals and orders quickly. It is also fast and durable. It has many features that are unique and perfect for you.
DEMO DOWNLOAD
Laravel CRM – Open source CRM Web application – upport CRM
Upport is a beautifully designed CRM application that is made exactly according to the feedback and real needs of users. Upport CRM helps you to increase sales with unique features. Its interface is user-friendly, responsive, real supportive and easy to use. CLI installer tool is provided for installation of Upport CRM for your convenience. It tracks sale opportunity easily using Kanban view. You don’t need to worry about data disaster because with auto backup feature of Upport you can easily set schedule to automatic backup from database and attachments.
DEMO DOWNLOAD
LCRM – Next generation CRM web application
LCRM is a modern CRM web application with a lot of features. It has three sections admin, staff and customers respectively. LCRM has many unique modules. It is a complete functional CRM and sales system. If your business needs new customers and growing sales then LCRM is perfectly made for you. It holds various advantages like recording the leads, showing the opportunities, sales team targets, actual invoices of entries. Moreover, it has amazing features like real time notifications with pusher.com, backup data to dropbox and amazon s3, repository pattern and single page application (SPA) that is appropriate with VueJS.
DEMODOWNLOAD
Microelephant – CRM & Project management system built with Laravel
Microelephant CRM is a web-based software which provides customer relationship & Project management and billing facilities. It is suitable for almost every company. It is developed by using Laravel 5.7 and Bootstrap 4.2 CSS framework. It has unique features like client portal for each customer, leads management. Tasks & timesheet, customers and contacts management, proposals, electronic signature, credit notes and invoices.
DEMO DOWNLOAD
Incoded CRM – Customer Relationship Management System
Incoded CRM – Customer relationship management system is developed according to the feedback of project managers and business owners who actually use it. After findings the key ideas which we need the most, we gathered these ideas in one place and make this CRM out of these ideas perfectly. Now it is shared with the world. It hasn’t stopped progressing yet because it is expanding everyday as more and more ideas are coming. It is an app which updates itself every day.
It has multiple unique features. As the top entity in the CRM is Work space Incoded CRM is organized in work spaces. You can use it to easily separate and organize your resources, projects, tasks etc. work spaces have their own dashboards. It contains major and contemporary information form the CRM i.e. notes, activities and tasks, tasks chart etc.
DEMO DOWNLOAD
Zoho CRM
CRM systems play an imperative role to manage your sales revenue, sales teams, and most importantly increase customer relationships. You don’t have to worry about it because Zoho CRM is the system which fulfill all your needs. It is loaded with features to help you start, equip, and grow your business for free, for up to 3 users.
It manages users, profiles and roles efficiently. You can easily import data for free with import history and manage your leads, accounts, contacts and deals by using Zoho CRM. It can also export any module data and import leads directly with the business card scanner.
Zoho CRM turn data into sales. You can sell through telephony, email, live chat, and social media. It gets you real-time notifications when customers interact with your brand and add tasks, calls, and events, and sync them with your calendar. It helps you to collaborate with your team through feeds and give you access to multiple CRM views.
It Makes planning and expanding easier. You can get 1GB file storage & 25k record storage and set up recurring activities for your team. It helps you to export activities to google calendar and google tasks.
DEMO DOWNLOAD
Powerful CRM – LiveCRM Pro
LiveCRM pro is a perfect and complete CRM solution with fully PHP7 compatibility. It has unique features and developed by using Yii 2.0 framework. It has excellent sales system that manage leads store all the leads and organization information that your sales process demands. You can look up leads and the associated contact and business information ins a few seconds. The method which is integrated in it is paypal payment gateway. It provides precise customer management and user management. It also has a unique feature of messenger and chatting system.
DEMO DOWNLOAD
1 note
·
View note
Text
AC0/RD Digest & our network ambitions
Something that’s been needed for a long time is a reliable network digest for our users and subscribers. I’ve used Wordpress.org for the longest time (almost 4 years, in fact) as the HQ for our community site, however I’ve started to use Git and static sites as the new skeleton for the AC0/RD Network. In today’s post, I’m going to talk about what happened to the old portal, why Github alone isn’t good enough for what we are doing, and also about what the actual title of the post suggests: our email subscription service.
Grab yourself a tasty beverage and snack, because this is going to be a slightly longer post than usual...

Rest in peace Portal #1 - 2016-20
Thanks to AC0RD’s first sponsor, Sean Firth, I got into the Wordpress.org community when I was only 13, and to this day I am still an everyday user of the popular CMS. I used Wordpress to create what was known as the “Portal” for AC0RD, which had the following features:
A blog
A database - for all the data collected by our bots & software
A forums & community section - where our members could talk about anything and everything, regardless of whether it was directly related to AC0RD or not, as well as the projects that we are/were working on
A media section (with groups & user profiles ^^)
Project management
Community growth
Over the years, I had about 10 members (Nicholas Antipas, Josh Richards, Sean, etc) contribute small bits of data and helpful stuff to the portal, but mostly it was a one-man-band. I was the singer, the guitarist, the drummer, and the roadie. Almost all of the forum posts I did myself, and the site was sort of like a large notebook, where only I contributed stuff to.
I told myself that this would only be temporary, and that it would be good for documentation (SDLC) purposes (to an extent, this is roughly the same situation now - except each post is being read by a few people, the repositories on Git & the new portal are getting edited by more people. It’s a start). But as the months stretched into years, I couldn’t help feeling disappointed about the lack of community growth. I’d thrown almost every bit of my spare time into this project, and it led to a lot of sleepless nights (not to mention every time I screwed up something on the site, like the dreaded white screen of death. I often joke that 99% of my PHP knowledge comes from reading those error messages).
This is why that when the first iteration (technically the second iteration, however the real original only lasted <72 hours before I broke it - in my defense I was VERY new to WP) bit the dust, after the initial shock, tears and screams I took a few deep breaths and decided that I would live with it.
The portal had become a wasteland, a barren wild wild west that only had 1 person as far as the eyes could see. Every now and again you’d see signs of a skeleton that still had some flesh, but those sights were rapidly being swallowed up by the growing chasm of self-doubt and despair that accumulated over my 3.5 years as the maintainer.
I talked about this to my mentor Nick, and we both agreed that maybe it was for the better. While I had recent backups of the old portal, maybe it was better for us to just make those backups open-source and create a fresh portal. This way, the documentation would still exist (it would just be less easy to navigate), but we’d have the advantage of a fresh start, and all in all a better springboard for leaping into the pool of software development. I set up a new installation of Wordpress with hostgator and that was that.
With the recent influx of members - Rishabh Chakrabanty, Basanta Kandel, Dylan Vekaria and so many others (thanks largely to the Facebook post we did on our page), we have a fledgling, but thriving, community on github, with projects being developed on git, discussed on slack & reddit, and shared on the website, with this being accumulated on the portal (for more information about this accumulation of data, I’d recommend checking out our post on dashboards: here: https://blog.acord.software/post/611809431430283264/html-dashboards-for-administration).
The old portal will live forever in my - and our - memories, and in our open-source database, but I look to the future, and this is the way it will be.
Why Github isn’t enough
Github is great for software development, especially collaborative open-source work. But when you want to build a community around your company (especially when a huge amount of your community won’t have, or want, github accounts), you need something else.
Wordpress is great, because with plugins like buddypress you can create social networks like Facebook on a smaller scale for your club/organisation (again, I’d recommend checking out another one of our posts about social network construction here: https://blog.acord.software/post/611414544827432960/constructing-a-social-network).
I’m a big sucker for integrations between our services (for a list of services that we use, check out this page on our Stellarios documentation: https://acord.software/stellarios/hydejack/2020-01-25-integrations/). Github is great, because you can connect your various online accounts to it with services like Zapier or Integromat. To get my dream network, we’re going to have to use services like those.
AC0/RD Members Digest
I’d hazard a guess that you’re part of a number of online communities. Wouldn’t it be great to have the latest notifications and news delivered daily, weekly or monthly for all those communities?
Buddypress (thanks to plugins available on wordpress.org) has had this kind of feature - email subscriptions - for a while. What I wanted when I started this project was a perfect amalgamation between our awesome online communities - Reddit, the Portal, Github, Facebook, etc. While we could implement some sort of system that would send an email from Facebook, an email from Reddit, etc, for the digest (so that you’d be burdened with 5 emails everytime you get a digest), I thought of something a bit different.
The ideal scenario would be to be able to link your Portal (wordpress) account with the online services/websites mentioned above ^^, and for the content that is relevant to your account (i.e. from your friends or groups) to be emailed to you, as well as site-wide notices. Unfortunately, the closest you can get to this at the moment is to share a link to your social media profiles on your Wordpress profile. Obviously, this won’t do.
Over the last 24 hours, I’ve been thinking: how do we create a network digest?
What we will be doing is we’ll create weekly posts on the new AC0/RD Portal, which will have the latest content from our online profiles. You’d then be able to sort through these, and as you’re logged into those accounts, be able to find what’s relevant to you easily. This post can then be sent to your email, and can work in with integrations like Gamipress.
Of course, we can also easily set up automatic post systems (for the forums WITHIN groups on the portal) that would then be sent into your newsfeed. Both of these solutions would work well, and we’ll be working on ways to implement them as best as we can very soon.
<3
Limo
1 note
·
View note
Text
The Magnus Archives ‘Meat’ (S04E10) Analysis
Well, with a title like that we know it’s going to be a good time, don’t we? Come on in to hear what I have to say about ‘Meat’.
Wow am I happy to hear Gertrude’s voice again. After the misery parade that has been this season, having an episode that’s light on meta-plot and heavy on a hell of a statement and a character we haven’t heard from in a while was a real breath of fresh air. And what meta plot we do have is essentially Jon topping every other effort he’s made at being the stupidest man in the room, so … yeah. There is that.
Let’s start by talking about the statement, which I really liked. The statement itself was beautiful in a gnarly way, and getting to hear Gertrude again brought a smile to my face. Sue Sims has a real talent for being vaguely, quietly menacing. Not in any way I can put my finger on, but in a way that very much speaks to the fact that this is an older woman with ready access to C-4.
So we open with Gertrude and a statement giver interacting, which is incredibly uncommon. Comparing Jon’s obvious but honest abrasiveness with Gertrude’s more professional but also far more menacing approach is interesting. Gertrude’s ‘whatever nightmares you’re having won’t be bothering you much longer’ is particularly nasty. It’s clear that, if she ever hoped to help the statement givers, she was long past trying or even caring by 2008. Even before finding out that she intended to kill the statement giver if Lucia was able to identify her, you just knew that Gertrude expected nothing good for the woman sitting across from her.
I also appreciate that we’re getting another statement about the Flesh, which is clearly one of Jonny’s favorite powers to write about. It’s so odd in such unexpected ways, and this episode follows in the grand tradition of ‘The Man Upstairs’ and ‘Takeaway’, which are still two of my favorite episodes.
Calling the Flesh the Demiurge is also really fantastic. I love that the powers don’t have real names, and that each can go by a thousand monikers for the same base fear. Whether it’s the Gnostics fearing the base fleshy reality of things, or animals fearing slaughter, there’s something inherently similar and inherently terrifying. Each name adds nuance, a different perspective on the same horror, and the linguist in me loves that.
It’s also interesting to get a link between the Boneturners and ‘Takeaway’. While people seem to be mostly twisted by the flesh into the beings that Jared Hopworth creates, the animals tend to be rendered simply into meat for consumption. I think this hearkens back to the base of the fears at play. While animals fear consumption, humans fear the changing of their flesh to something horrible and unrecognizable. There’s a divergence, but it all comes down to a fear of the physical reality of what we are, either through its changing or through its consumption. But of course, there is overlap. People still fear being eaten. Animals may fear being twisted into something different, though I’m not sure how that would work. That’s what makes the Flesh so engaging as a fear: that there is a strong sense of the inhuman about it.
As for the people present themselves, that’s also interesting. The Asian gentleman with the crisp RP accent driving the truck is almost certainly Tom Haan. His father was the man from ‘Takeaway’, and he himself appeared in the Endless Abattoir in ‘Killing Floor’. The tall woman with the arms going backward isn’t one I think we’re familiar with at this point. The beings of twisted flesh that may have been human seem to have been the things that Jared Hopworth was creating. The mouth in the hole is also very familiar to the thing Jared was feeding in ‘The Butcher’s Window’.
I think that thing must have been a prelude to the mouth in Istanbul, a preparation for the Ritual that was almost certainly taking place in this episode. Gertrude was obviously there, and stopped it. She was planning on killing her if she remembered Gertrude’s presence. Tom Haan also survived the explosion, but Gertrude wasn’t as keen to go after him.
Apparently, if robbed of their purpose, avatars and monsters have a tendency to fade out or burn out. Either way, she clearly didn’t view Tom as too much of a threat. She also mentioned other fallout, including a young man named Carlisle, who I believe to be Toby Carlisle, the man upstairs in ‘The Man Upstairs’, and likely descendant of the Carlisles whose husband was cannibalized in ‘Trail Rations’. I think we’ve found a (possibly still extant) few family lines tied with the flesh, both brought together in certain ways.
I’m not sure how Toby was tied in with the Feast (as it seemed to have been called), but given that Gertrude considered him fallout, he had to have been. Perhaps he was helping supply the flesh while Jared supplied the workers?
We also learned that Gertrude also coopted the dreams of statement givers, though she viewed it as more of a nuisance than anything else, and simply wished she might avoid Lucia’s nightmares. It makes me wonder how many other Archivist abilities she had. We know Jon’s a lot more in tune with his purpose than she was, and a lot more of the Archivist, but she still had certain abilities.
And this brings us back to Jon, whose idiocy apparently scales the heights this week. We all had speculations ranging from the practical (using Georgie or Martin or the Admiral as an emotional anchor) to the silly (just going out and buying an actual boat anchor and strapping a ton of tape recorders to it), I don’t think any of us could have predicted how spectacularly stupid Jonathan Sims could be. Because somehow, he took a statement about a woman surviving an encounter with a proper ritual through sheer stubbornness, gifted to him by the most manipulative and least straightforward of the powers, and concluded that it wanted him to lop off a body part and use himself as an anchor. Somehow.
I think there must have been some spider in the corner of his office just staring at him like that blinking guy gif. Because even the Web might not have predicted how stupidly literally Jon might take this hint. Hell, it was probably trying to give him a message that would only make sense when several other pieces fell into place, and only at a time most convenient to the Web.
But no. Jon, spectacular moron that he is, is going to take a knife to himself and hope for the best. This is the Archivist. This is the repository for all knowledge in the world. This idiot. I do sometimes wonder if the Beholding is the most inept of the powers.
And there’s the question of why the Web would even leave him this tidbit at all. It’s always had an interest in him, but direct help is new. I wonder if it’s interested in Daisy in some way? Or at least interested in something else in the coffin? Daisy might well not be alone down there, and the Web could be hoping to spring at least one other trapped being. Or it could just be helpful to someone it’s always liked (still waiting for that lighter to come into play). Or it could have been sent by Martin (I have a pet theory he’s working with both the Beholding and the Web behind Peter’s back, because I’d really like to think Martin isn’t stupid enough not to have a backup plan for when Peter tries to screw him over).
But sure, Jon. Lop off a finger or make a bowl of your own blood to tie you to this world. That’s guaranteed to work and not blow up in your face as your Archivist self forgets the fleshy self and you get more and more divided just like the Gnostics thought you might.
I had hoped that Jon might take the hint that him being able to find Martin at a moment’s notice consistently might be just the thing he was looking for. Clearly I underestimated the idiocy of our protagonist.
At this point, Jon, do buy that anchor and strap some tape recorders to it. At least then someone might get the hint that you’d done something stupid like flinging yourself into a coffin without adequate knowledge or preparation. You moron.
62 notes
·
View notes
Text
The Komodo Platform provides full-scale, end-to-end blockchain solutions for developers of different industries and levels. It offers customized, configurable blockchain solutions that are easy to deploy. The blockchain emerged as a ZCash blockchain fork, which was a Bitcoin fork. The Komodo ecosystem integrates zk-snark technology (zero knowledge) based on Zcash. It adds a relatively rare consensus algorithm known as delayed proof of work (dPoW). Komodo’s goal is to build a complete ecosystem consisting of various partnerships. How it works Komodo has a blockchain with autonomous infrastructure, achieved by means of parallel chains. These chains create a separate Komodo blockchain copy. The dPoW consensus mechanism secures new parallel chains. Developers on Komodo don’t build on the blockchain itself. Rather, they create their own autonomous blockchains. It’s neither a sidechain nor a fork. The Komodo platform doesn’t serve as a legacy platform to the new blockchain. Each development project on Komodo is an independent blockchain that is linked to the network. This way, Komodo can never limit any future development. The core of the network is BarterDEX, Komodo’s decentralized exchange. The DEX is the intersection between all the blockchains. It’s powered by atomic swaps, unlike other DEXs, which use proxy tokens. Key features Komodo’s most important features are related to security, privacy, scalability, adaptability, and interoperability. Security Komodo’s security stands out through the use of the dPoW consensus mechanism and the Zcash zk-snark protocols for anonymity. The mechanism offers Bitcoin-level security to all projects and blockchains associated with Komodo. The dPoW consensus mechanism creates a backup of blockchain data. Privacy The zero-knowledge proof technology used by the Zcash blockchain allows full anonymity of each transaction on the blockchain. Many users appreciate anonymous transactions as they don’t have to share information about the sender, recipient, and amount of the transaction. At the same time, the transaction is transparent, and miners can verify its validity. Data appears just like it would for a standard Bitcoin transaction. Another important advantage of anonymous transactions is preserving fungibility, a basic currency requirement. Adaptability As one of the best-known open-source projects, Komodo is well-recognized for its features and innovations. Komodo-based projects are equipped with the ability to create custom solutions depending on the different situations and needs. Scalability Komodo lets each project have a dedicated blockchain and infrastructure, unlike other enterprise solutions. Komodo network projects can scale at any time, and blockchains can be added to improve performance as needed. Interoperability Komodo’s so-called blockchain federation technology enables frictionless interoperability with federation blockchains. Atomic swaps can be used to link to non-federation blockchains. Extensive development activity Komodo has been very active in pushing code to its base repository. It has tens of repositories, all of which are quite dynamic. The ecosystem ranked 12th on Coincodecap in terms of overall coding activity. Pros · Scores well on scalability, adaptability, and interoperability · Extensive development activity · High security and reliable privacy Cons · The coin is still under development · Some issues with ledger synchronization Why should you sign up with Komodo? One reason is that security is top-notch. At the time of writing, Komodo was preparing for an external security review. They will be creating an architecture diagram and an SRS document, updating and refactoring dependencies, and doing an internal security code review so auditors can access the code. Recently, Komodo optimized the blockchain node call amounts and added an infrastructure enhancement microservice. They are in the process of integrating QuickNode blockchain nodes into their interfaces.
They created a microservice layer to be able to complete the integration. Komodo offers convenience to its users by providing the option to collect fiat price information in the API database. This way, traders can calculate fiat prices retroactively, if needed. Another advantage is the Komodo cryptocurrency (KMD) itself, which can be used to mediate transactions with tokens that don’t have a direct pair on BarterDEX and to enable instant zero-confirmation exchanges on Komodo DEX. The Komodo coin pays for Komodo’s security protocol service, is used for dICO crowdfunding on the platform, and powers UTXO-based smart contracts. If you have 10 KMD or more, you can earn 5% rewards as an active user. What makes it stand out? Komodo’s dPoW consensus algorithm increases network security by using Bitcoin’s hash power. Bitcoin has the highest hash power of all blockchain networks, rendering it practically impervious to hijacking. The bottom line Komodo has a vast and extensive library and a reliable, solid team and community. They publish updates in real-time and provide transparent yearly and quarterly reviews. They are an excellent choice of a blockchain solution for experienced developers. Read More
0 notes
Text
MongoDB Developer and Administrator Online Training

MongoDB was created in 2007 by 10gen software. It is a document-based database. It functions on the concept of collections and documents. A MongoDB server has multiple databases and offers very high performance along with the redundancy and easy scalability. Collection in MongoDB is usually considered as a group of documents databases that can have different types of fields. MongoDB is a set of key-value pairs having a dynamic schema i.e. common fields may carry different types of data and all documents kept in the same collection need not have the same data structure.Although being fresher in MongoDB language, if you are carrying experience and worked with RDBMS like SQL, then this small step will help you correlate with all terminologies of MongoDB.
Why MongoDB?
While building internet and business applications which are developing enormously and scale elegantly, MongoDB popularity is growing rapidly within developers of all kinds who are building applications using agile methodologies.
MongoDB is a good choice if one needs to:
Support quick duplication developments.
Hold and gear-up high levels of read and write traffic – MongoDB supports horizontal scaling through fragmentations, distributing data across several machines, and ease high throughput operations with large volumes of data.
Laminates your data repository to a massive size.
Evolve different types of deployment as the business grows.
Store, manage and search all data sets in the form of text, geospatial, or time-series dimensions.
What is MongoDB?
MongoDB is known as a cross-platform document-based database. Categorized as a NoSQL database, MongoDB avoids the accustomed table-oriented relational database structure that supports JSON-like documents with the dynamic structures, making the data integration in certain kinds of applications quicker and simpler.
MongoDB is an open-source NoSQL database set down in C++ language. It uses JSON-like documents with elective schemas.
It is an effective and cross-platform, document-oriented database set.
MongoDB functions on the concept of Collections and Document.
It combines the ability to adapt out with features such as secondary indexes, range queries, sorting, aggregations, and geospatial indexes.
MongoDB is licensed under the Server Side Public License (SSPL) and developed by MongoDB Inc.
What are some of the advantages of MongoDB?
Some advantages of MongoDB are as follows:
MongoDB support fields, range-based, string pattern matching type queries for looking for the data in the database.
MongoDB supports primary and secondary indexes on any pattern of the database.
MongoDB usually makes use of JavaScript objects in place of procedures.
MongoDB uses a dynamic database structured framework.
What are some features of MongoDB?
Indexing: It helps with generic secondary indexes and makes availability of unique, compound, geospatial, and full-text indexing capabilities.
Aggregation: It provides an aggregation database set based on the concept of data processing pipeline.
Collection and index types: It supports time-to-live (TTL) collections for data that expire after a certain period of time.
File storage: Easy-to-use protocol for storing double size files and metadata.
Sharding: Sharding is the process of fragmenting data up across machines.
Course Overview of MongoDB:
This MongoDB Developers and Administrators course will guide you in mastering the concepts of data modeling, query, sharding, and data duplications with MongoDB, along with its installation process, updating, and maintaining all MongoDB environments. You will learn how to work on MongoDB configuration, backup methods and operational strategies.
Highlights to complete your mongoDB Course :
49 hours of Online Bootcamp will be provided
3 industry-based projects with E-learning and telecom domains
6 hands-on lab exercises to be executed virtually in MTSS
60 demos pre-lectures for explaining key concepts
Skills Covered for being an Big Data Engineer while learning MongoDB:
Writing Java and NodeJs applications
Operating CRUD operations in MongoDB
Replication and sharding process
Indexing and aggregation process
MongoDB tools and backup methods , Replica sets will be covered
Benefits after completing MongoDB:
This MongoDB Developers and Administrators course is best suited for professionals who are determined to work on NoSQL databases and MongoDB, counting database administrators and architects, software developers and project managers, testers, system administrators, analytics, IT developers, and research professionals.
Some Important Key Learning Outcomes:
Expertising in writing Java and NodeJS applications using MongoDB
Master every skill of duplications and sharding data in MongoDB to enhance read/write performance and installation, configuration, and maintenance.
Get hands-on experience, creating and managing different types of index in every query execution of MongoDB.
Store unstructured data in MongoDB and developed skills for processing large amounts of data using MongoDB tools
Acquire expertise in MongoDB configurations, backup methods, monitoring, and operational strategies
Learn an in-depth understanding of how to supervise DB Notes, Replica sets, and master-slave concepts in MTSS
Demanding fields are :
Information Technology
Finance
Retail
Real Estate
Engineering
Hospitality Management
Business Consulting
Job opportunities for professionals
IT Developers
Analytics Managers
Information Architects
Analytics professionals
Experienced professionals
Graduates in Bachelor or Master’s Degree
Conclusion :
Today just knowing how to manage databases is not adequate. Mastering the current developments and the market dominance is important in the coming decade, a great time to add MongoDB. We have collated the detailed programs so that you can get the best learning resources without wasting much time on the internet. MTSS Education Big Data Engineer program has not only provided you with the skills to develop but also gives you a certification to validate these skills and your learnings. The future scope of MongoDB is progressively increasing with the changing climate and their disciplined management work skills in a new era.
#mongodb developers#mongodb certified developer#administrator training#administrator certification#mongodb certification#mongodb training#mongodb course#administrator course#it certification
0 notes