#SQLServer
Explore tagged Tumblr posts
Text
Wait what... ? this is dangerous knowledge.

33 notes
·
View notes
Text
SQL Fundamentals #1: SQL Data Definition
Last year in college , I had the opportunity to dive deep into SQL. The course was made even more exciting by an amazing instructor . Fast forward to today, and I regularly use SQL in my backend development work with PHP. Today, I felt the need to refresh my SQL knowledge a bit, and that's why I've put together three posts aimed at helping beginners grasp the fundamentals of SQL.
Understanding Relational Databases
Let's Begin with the Basics: What Is a Database?
Simply put, a database is like a digital warehouse where you store large amounts of data. When you work on projects that involve data, you need a place to keep that data organized and accessible, and that's where databases come into play.
Exploring Different Types of Databases
When it comes to databases, there are two primary types to consider: relational and non-relational.
Relational Databases: Structured Like Tables
Think of a relational database as a collection of neatly organized tables, somewhat like rows and columns in an Excel spreadsheet. Each table represents a specific type of information, and these tables are interconnected through shared attributes. It's similar to a well-organized library catalog where you can find books by author, title, or genre.
Key Points:
Tables with rows and columns.
Data is neatly structured, much like a library catalog.
You use a structured query language (SQL) to interact with it.
Ideal for handling structured data with complex relationships.
Non-Relational Databases: Flexibility in Containers
Now, imagine a non-relational database as a collection of flexible containers, more like bins or boxes. Each container holds data, but they don't have to adhere to a fixed format. It's like managing a diverse collection of items in various boxes without strict rules. This flexibility is incredibly useful when dealing with unstructured or rapidly changing data, like social media posts or sensor readings.
Key Points:
Data can be stored in diverse formats.
There's no rigid structure; adaptability is the name of the game.
Non-relational databases (often called NoSQL databases) are commonly used.
Ideal for handling unstructured or dynamic data.
Now, Let's Dive into SQL:

SQL is a :
Data Definition language ( what todays post is all about )
Data Manipulation language
Data Query language
Task: Building and Interacting with a Bookstore Database
Setting Up the Database
Our first step in creating a bookstore database is to establish it. You can achieve this with a straightforward SQL command:
CREATE DATABASE bookstoreDB;
SQL Data Definition
As the name suggests, this step is all about defining your tables. By the end of this phase, your database and the tables within it are created and ready for action.

1 - Introducing the 'Books' Table
A bookstore is all about its collection of books, so our 'bookstoreDB' needs a place to store them. We'll call this place the 'books' table. Here's how you create it:
CREATE TABLE books ( -- Don't worry, we'll fill this in soon! );
Now, each book has its own set of unique details, including titles, authors, genres, publication years, and prices. These details will become the columns in our 'books' table, ensuring that every book can be fully described.
Now that we have the plan, let's create our 'books' table with all these attributes:
CREATE TABLE books ( title VARCHAR(40), author VARCHAR(40), genre VARCHAR(40), publishedYear DATE, price INT(10) );
With this structure in place, our bookstore database is ready to house a world of books.
2 - Making Changes to the Table
Sometimes, you might need to modify a table you've created in your database. Whether it's correcting an error during table creation, renaming the table, or adding/removing columns, these changes are made using the 'ALTER TABLE' command.
For instance, if you want to rename your 'books' table:
ALTER TABLE books RENAME TO books_table;
If you want to add a new column:
ALTER TABLE books ADD COLUMN description VARCHAR(100);
Or, if you need to delete a column:
ALTER TABLE books DROP COLUMN title;
3 - Dropping the Table
Finally, if you ever want to remove a table you've created in your database, you can do so using the 'DROP TABLE' command:
DROP TABLE books;
To keep this post concise, our next post will delve into the second step, which involves data manipulation. Once our bookstore database is up and running with its tables, we'll explore how to modify and enrich it with new information and data. Stay tuned ...
Part2
#code#codeblr#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#learn to code#sql#sqlserver#sql course#data#datascience#backend
112 notes
·
View notes
Text
https://madesimplemssql.com/
2 notes
·
View notes
Text
she query on my sequel til i — no that can’t be right. there’s something here tho…
13 notes
·
View notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
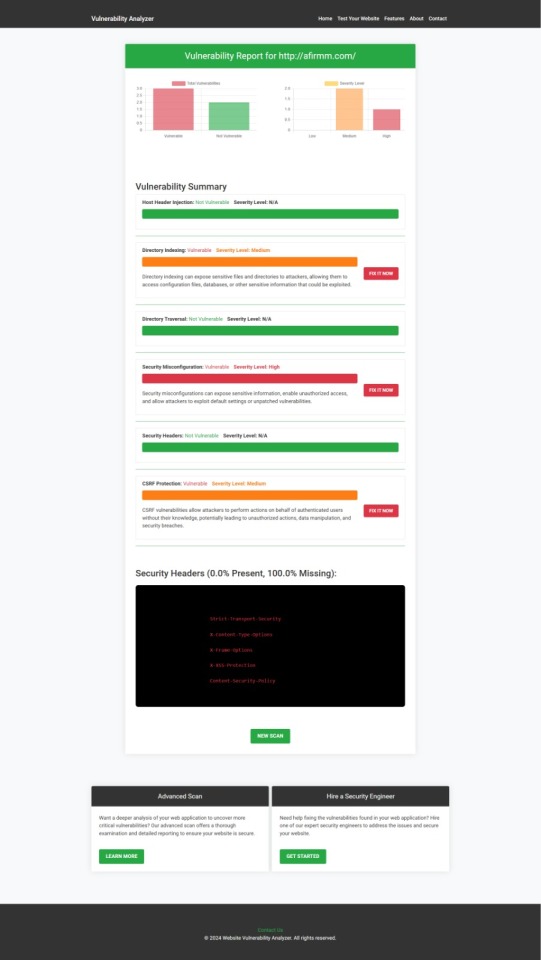
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text

Due to popular demand.
Here is complete SQL Joins cheatsheet:
3 notes
·
View notes
Text
Current status of the database code: Bit fucked lol but i stopped working on it so wc
3 notes
·
View notes
Text
With SQL Server, Oracle MySQL, MongoDB, and PostgreSQL and more, we are your dedicated partner in managing, optimizing, securing, and supporting your data infrastructure.
For more, visit: https://briskwinit.com/database-services/
4 notes
·
View notes
Text
Database design and management course and Assignment help

Contact me through : [email protected]
I will provide advice and assistance in your database and system design course. I will handle everything including;
Normalization
Database design (ERD, Use case, concept diagrams etc)
Database development (SQL and Sqlite)
Database manipulation
Documentation
#database assignment#assignment help#SQL#sqlserver#Microsoft SQL server#INSERT#UPDATE#DELETE#CREATE#college student#online tutoring#online learning#assignmentwriting#Access projects#Database and access Final exams
4 notes
·
View notes
Text

Join the Best SQL Server Online Training
Enhance your skills in SQL querying, database administration, and performance optimization through SQL Server Online Training. This in-depth course explores essential topics like data manipulation, stored procedures, triggers, indexing, and security in Microsoft SQL Server environments.
#education#certification#training#sqlserver#sqlservertraining#sqlservercourse#sqlservercertification
0 notes
Text
2 notes
·
View notes
Text
Boost Your Database Certification Prep with Real Practice Tests!
Are you preparing for top database certifications like Oracle, IBM, or Microsoft SQL Server? Don’t just read — practice like it’s the real exam! 🧠
🌐 DBExam.com offers trusted, up-to-date online practice exams for a wide range of database certifications. Whether you're aiming for Oracle OCA, IBM DB2, or MySQL certifications, you'll find:
✅ Realistic exam questions ✅ Instant result reports ✅ Unlimited practice access ✅ Proven success rate with global professionals
💡 Why Choose DBExam? Because it’s not just about passing — it’s about mastering your skills and getting career-ready in a competitive tech world.
📚 Start practicing smart. Pass with confidence. 👉 Visit www.dbexam.com now.
1 note
·
View note
Text
🚀 Boost Your SQL Game with MERGE! Looking to streamline your database operations? The SQL MERGE statement is a powerful tool that lets you INSERT, UPDATE, or DELETE data in a single, efficient command. 💡 Whether you're syncing tables, managing data warehouses, or simplifying ETL processes — MERGE can save you time and reduce complexity.
📖 In our latest blog, we break down: 🔹 What SQL MERGE is 🔹 Real-world use cases 🔹 Syntax with clear examples 🔹 Best practices & common pitfalls
Don't just code harder — code smarter. 💻 👉 https://www.tutorialgateway.org/sql-merge-statement/
0 notes
Text

📊 Learn Tally with GST – From Basics to Advance! 🔹 Join the experts at Scope Computers, Jodhpur's most trusted institute since 1993! 🔹 Master Tally ERP 9 with GST, accounting, billing, inventory, payroll, and more. 🔹 Industry-ready training with real-world projects.
📍 Address: Bhaskar Circle, Ratanada, Jodhpur 📞 Call Now: 8560000535, 8000268898 💼 Limited seats. Join Today and Boost Your Career!
#TallyWithGST#TallyCourseJodhpur#ScopeComputers#AccountingCourse#GSTTraining#TallyERP9#BestTallyInstitute#JobOrientedCourses#ComputerClassesJodhpur#AdvanceTally#TallyTraining#GSTCourseJodhpur#TallyAccounting#SAPTraining#SQLServer#ExcelCourse#LearnWithExperts#ScopeJodhpur#ComputerInstituteJodhpur
1 note
·
View note
Text

Neste artigo de hoje vamos aprender coo criar um Banco de Dados no SQL Server….
0 notes
Text
With SQL Server, Oracle MySQL, MongoDB, and PostgreSQL and more, we are your dedicated partner in managing, optimizing, securing, and supporting your data infrastructure.
For more, visit: https://briskwinit.com/database-services/
3 notes
·
View notes