Don't wanna be here? Send us removal request.
Text
The Definitive Roadmap to Embark on an Ethical Hacker's Journey
Embarking on the path to becoming an ethical hacker requires a strategic roadmap that encompasses essential skills, knowledge, and ethical principles. This comprehensive guide presents a roadmap that will guide you through the stages of your journey, equipping you with the necessary tools and expertise to become a proficient ethical hacker.
I echo your excitement about exploring the realm of Ethical Hacking. My experience in this field has expanded substantially, affirming its acknowledgment and broad implementation across diverse industries.

To enhance your Ethical Hacking endeavors, I suggest exploring a well-regarded Ethical Hacking Course in Chennai Drawing on their extensive expertise and resources can provide valuable knowledge and skills, ultimately propelling your expertise in ethical hacking.
Establish a Strong Foundation in Computer Science:
To lay a solid groundwork, focus on gaining a comprehensive understanding of computer science fundamentals. Acquire knowledge in areas such as computer networks, operating systems, and programming languages. Familiarize yourself with TCP/IP, network protocols, and various operating systems like Windows, Linux, and macOS. Master programming languages such as Python, C, or Ruby, which are widely used in the field of cybersecurity.
Grasp the Fundamentals of Cybersecurity:
Develop a strong grasp of cybersecurity fundamentals by studying concepts like confidentiality, integrity, and availability. Explore common cyber threats, including malware, phishing, and social engineering. Dive into encryption techniques, firewalls, intrusion detection systems (IDS), and other security mechanisms that safeguard digital systems.
Attain Relevant Certifications:
Enhance your professional credibility and validate your ethical hacking skills by pursuing relevant certifications. Consider certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP), or GIAC Penetration Tester (GPEN). These certifications demonstrate your expertise and commitment to ethical hacking.
Embrace Legal and Ethical Considerations:
Develop a strong understanding of the legal and ethical aspects surrounding ethical hacking. Familiarize yourself with cybersecurity laws and regulations specific to your country or region. Embrace ethical guidelines, including responsible disclosure and respect for privacy rights. Cultivate a strong ethical foundation to guide your actions as an ethical hacker.
Master Ethical Hacking Techniques and Tools:
Immerse yourself in the world of ethical hacking by acquiring knowledge of various hacking techniques and tools. Study methodologies such as reconnaissance, scanning, enumeration, and exploitation. Dive into penetration testing frameworks like the Open Web Application Security Project (OWASP) Testing Guide. Gain hands-on experience with ethical hacking tools such as Nmap, Metasploit, Wireshark, Burp Suite, and John the Ripper.
Engage in Controlled Practice Environments:
Set up a controlled practice environment using virtualization software like VirtualBox or VMware. Utilize these environments to practice ethical hacking techniques and refine your skills. Engage in Capture The Flag (CTF) competitions and challenges to apply your knowledge in realistic scenarios. Join online communities and forums dedicated to ethical hacking to collaborate, share knowledge, and learn from experienced professionals.

To master the intricacies of ethical hacking and unlock its full potential, individuals can benefit from enrolling in the Best Ethical Hacking Online Training.
Embrace Continuous Learning and Stay Updated:
Stay ahead of the rapidly evolving cybersecurity landscape by embracing continuous learning. Stay updated with the latest trends, vulnerabilities, and countermeasures. Follow reputable cybersecurity blogs, podcasts, and news sources to remain informed. Attend conferences, webinars, and training programs to expand your knowledge and network with like-minded professionals.
Gain Practical Experience:
Seek practical experience through internships, entry-level positions, or freelance projects. Apply your ethical hacking skills in real-world scenarios under professional guidance. Collaborate with cybersecurity experts or participate in red teaming exercises to further enhance your practical abilities.
Following this comprehensive roadmap will guide you through the stages of your ethical hacking journey. By establishing a strong foundation, acquiring relevant certifications, embracing ethical considerations, mastering hacking techniques and tools, engaging in controlled practice environments, staying updated, and gaining practical experience, you will be well-equipped to make a meaningful impact in the field of ethical hacking.
Embrace the responsibility of safeguarding digital systems, promoting cybersecurity, and contributing to a safer digital world.
0 notes
Text
Unraveling the Responsibilities of a Computer Hacking Forensic Investigator
In our interconnected world, where technology permeates every aspect of our lives, the significance of cybersecurity cannot be overstated. With the constant evolution of hacking techniques, the role of a Computer Hacking Forensic Investigator (CHFI) has become indispensable in safeguarding digital assets and combating cybercrime.
To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai. Leveraging their wealth of expertise and resources can offer valuable insights and skills, ultimately contributing to advancing your proficiency in ethical hacking.

In this blog post, we will explore the various responsibilities and duties that CHFIs undertake to protect against cyber threats.
Defining the Computer Hacking Forensic Investigator: A Computer Hacking Forensic Investigator is a trained professional specializing in identifying, extracting, preserving, and analyzing digital evidence related to cybercrime. They play a critical role in investigating cyberattacks, preventing future incidents, and aiding in the prosecution of cybercriminals.
Investigative Skills and Techniques: CHFIs employ a diverse set of skills and techniques to conduct effective investigations. These encompass: a. Acquisition of Digital Evidence: CHFIs possess expertise in acquiring digital evidence from diverse sources like computers, servers, mobile devices, and network logs. They employ forensic tools and techniques to preserve evidence, ensuring its integrity and admissibility in legal proceedings. b. Forensic Analysis: CHFIs utilize advanced forensic analysis techniques to examine acquired data and extract vital information. By employing specialized software and tools, they uncover deleted files, identify malicious code, trace network activities, and reconstruct digital events. c. Incident Response: In the event of a cyber incident, CHFIs play a crucial role in incident response. They meticulously analyze the nature of the attack, identify compromised systems, and implement measures to contain the breach. Collaborating with other cybersecurity professionals, they restore systems and implement preventive measures against future incidents.
Cybercrime Investigation: CHFIs are at the forefront of investigating cybercrimes. Their responsibilities encompass: a. Digital Forensic Analysis: CHFIs conduct in-depth analysis of digital evidence to determine the cause, extent, and impact of cybercrimes. This involves examining malware, identifying intrusion points, and tracing the actions of attackers. b. Intrusion Detection and Prevention: CHFIs closely collaborate with intrusion detection systems (IDS) and intrusion prevention systems (IPS) to identify and mitigate cyber threats. They analyze logs and network traffic to detect unauthorized activities, taking proactive measures to prevent further intrusions. c. Legal Support: CHFIs work hand-in-hand with law enforcement agencies and legal professionals, providing expert testimony and support during legal proceedings. They ensure that the evidence collected adheres to legal standards and can be effectively presented in court.
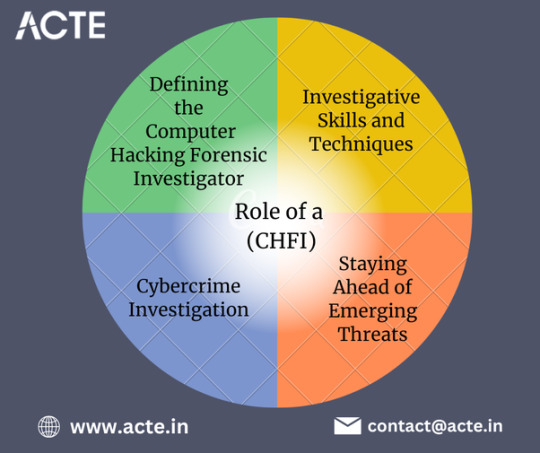
Staying Ahead of Emerging Threats: As technology constantly evolves, hackers continuously develop new techniques to exploit vulnerabilities. CHFIs must stay updated with the latest cybersecurity trends, emerging threats, and evolving forensic tools. Continuous learning and professional development are essential for CHFIs to effectively combat cybercrime.
Considering the Best Ethical Hacking Online Training becomes pivotal
In an era marked by escalating cyber threats, the role of a Computer Hacking Forensic Investigator is indispensable in protecting digital assets and holding cybercriminals accountable. Their proficiency in digital evidence acquisition, forensic analysis, incident response, and cybercrime investigation makes them a crucial component of the cybersecurity landscape.
As technology advances, the demand for skilled CHFIs will only increase, emphasizing the significance of their role in securing our digital world.
0 notes
Text
Navigating a Ransomware Attack: Essential Steps for Recovery
In our increasingly digital world, ransomware attacks pose a significant threat to both individuals and organizations. These malicious attacks encrypt files or lock computer systems, demanding a ransom for their release. If you find yourself victimized by a ransomware attack, it is crucial to respond swiftly and strategically to limit the damage and recover your valuable data.

If you have fallen victim to a ransomware attack, it is crucial to respond promptly and strategically to minimize damage and recover your data. To enhance your Ethical Hacking endeavors, I suggest exploring a well-regarded Ethical Hacking Course in Chennai
In this blog post, we will explore the intricacies of a ransomware attack and provide a comprehensive roadmap to guide you through the recovery process effectively.
Unraveling Ransomware: Ransomware stands as a form of malware that typically infiltrates systems through malicious email attachments, compromised software downloads, or infected websites. Once inside, this malicious software encrypts your files, rendering them inaccessible. Subsequently, the attackers demand a ransom payment, often in cryptocurrency, in exchange for restoring access to the encrypted files.
Isolating Infected Systems: Upon discovering a ransomware attack, it is of utmost importance to promptly isolate the infected systems from the network. Disconnect all affected devices from the internet and any connected drives to prevent the malware from spreading further. This swift action contains the damage and safeguards unaffected systems from potential compromise.
Reporting the Incident: Notify the relevant authorities and report the ransomware attack. By doing so, you document the incident and enable law enforcement agencies to pursue the attackers. Reach out to your local law enforcement agency or a dedicated cybercrime reporting organization, providing them with all pertinent details of the attack.
Identifying the Ransomware Variant: Identify the specific type of ransomware that has infiltrated your system. This knowledge is instrumental in finding decryption tools or relevant resources that may aid in recovering your files. Certain cybersecurity companies and organizations develop decryption tools for particular ransomware variants, making identification an essential step.
Assessing Data Backups: Thoroughly evaluate the availability and integrity of your data backups. Regularly backing up your files using offline or cloud-based solutions allows you to restore your data without succumbing to the ransom demand. Ensure that your backups remain disconnected from the infected systems to prevent the malware from spreading to the restored files.
Seeking Professional Assistance: Consider engaging the services of a reputable cybersecurity firm or professional incident response team. These experts specialize in handling ransomware attacks and can provide tailored guidance for your situation. They can assist in analyzing the attack, identifying vulnerabilities, and guiding you through the recovery process effectively.
Removing Ransomware from Systems: Before restoring your files or utilizing any backups, it is crucial to thoroughly eliminate the ransomware from your systems. Employ up-to-date antivirus or anti-malware software to scan and cleanse all affected devices. Ensure that your operating system, applications, and security software are all updated to their latest versions to prevent reinfection.

Look for classes that educate a basic understanding of ethical hacking. Considering the Best Ethical Hacking Online Training becomes critical.
8.Restoring Files: Once you have verified the integrity of your backups and removed the ransomware, proceed with restoring your files. Depending on your backup solution, follow the specific instructions provided by the backup software or service provider. Prioritize critical files and gradually restore data to minimize potential risks.
9.Strengthening Security Measures: Take advantage of this opportunity to bolster your cybersecurity measures. Regularly update all software and operating systems, including security patches. Implement robust antivirus and anti-malware solutions, and educate yourself and your employees about best practices for email and web browsing security. Regularly back up your data and store backups offline or in securely encrypted cloud storage.
Recovering from a ransomware attack can be a complex and time-consuming endeavor. By adhering to the steps outlined in this guide, you can mitigate the impact of an attack and enhance your chances of successfully restoring your files. Remember to remain vigilant and proactive in your cybersecurity practices to prevent future incidents from occurring.
0 notes
Text
Exploring Web Application Security: Free Tools for Uncovering SQL Injection Vulnerabilities
In today's digital landscape, ensuring the security of web applications is paramount. Among the many vulnerabilities that developers and security professionals need to address, SQL injection stands out as a critical concern. By exploiting this vulnerability, attackers can gain unauthorized access to databases and compromise sensitive data.
However, it's crucial to approach SQL injection testing responsibly and with proper authorization. In this blog post, we will delve into several free tools that can be utilized to test and gain insights into SQL injection vulnerabilities.

Enhancing your profession at the Ethical Hacking Course in Chennai requires adhering to a systematic approach and enrolling in an appropriate course that will significantly expand your learning experience while keeping with your preferences.
Here Are Few Popular And Free Sql Injection Testing Tools:
SQLMap: Automating the Detection and Exploitation of SQL Injection Flaws SQLMap, an exceptional open-source penetration testing tool, streamlines the process of identifying and exploiting SQL injection vulnerabilities. With support for various database systems, this tool offers an extensive array of options for thorough testing and vulnerability exploitation. SQLMap is a valuable asset for developers and security professionals seeking to evaluate the security robustness of their web applications.
OWASP ZAP: Safeguarding Web Applications from SQL Injection Attacks OWASP ZAP (Zed Attack Proxy) is a widely acclaimed web application security scanner encompassing a dedicated module for SQL injection testing. It serves as an indispensable resource for developers and security professionals in identifying vulnerabilities within web applications. OWASP ZAP's user-friendly interface and comprehensive feature set make it an essential tool for conducting extensive security assessments.
SQLiPy: Interactive Testing for In-Depth SQL Injection Vulnerability Analysis SQLiPy, a Python-based SQL injection testing tool, provides an interactive command-line interface for assessing SQL injection vulnerabilities. By enabling users to execute various injection techniques, SQLiPy offers detailed feedback on potential vulnerabilities. This tool serves as an educational resource for developers and security practitioners seeking a deeper understanding of SQL injection and its potential ramifications.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
BSQL Hacker: Unveiling SQL Injection Vulnerabilities with Ease BSQL Hacker is a user-friendly SQL injection tool empowering users to identify and exploit SQL injection vulnerabilities effectively. With support for multiple attack types, BSQL Hacker simplifies the process of testing for vulnerabilities. Developers and security professionals can leverage this tool to identify, address, and remediate SQL injection vulnerabilities within their applications.
The prevalence of SQL injection vulnerabilities poses a significant risk to the security of web applications. To mitigate this risk, developers and security professionals must possess a comprehensive understanding of these vulnerabilities and employ appropriate measures to address them.
The free tools discussed in this blog post, including SQLMap, OWASP ZAP, SQLiPy, and BSQL Hacker, play a crucial role in testing and comprehending SQL injection vulnerabilities.
Nevertheless, it is vital to approach security testing responsibly and obtain proper authorization before conducting assessments. By utilizing these tools responsibly, we can fortify the security of our web applications and safeguard sensitive data from potential breaches.
0 notes
Text
Unleashing Your Potential: A Roadmap to Embark on a Growth Hacking Journey
In today's dynamic digital landscape, the role of growth hackers has gained immense significance as businesses strive for scalable and sustainable growth. A growth hacker is a versatile professional who combines marketing expertise with data analysis and strategic thinking to drive rapid expansion.

In today's fast-paced digital landscape, businesses are constantly seeking innovative ways to fuel their growth. This has given rise to a new breed of professionals known as growth hackers. A growth hacker is a creative marketer, data analyst, and strategist all rolled into one, with a primary focus on driving scalable and sustainable growth.
To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai
If you're intrigued by the possibilities of a career in growth hacking, this blog post will serve as your comprehensive roadmap to get started on this exciting journey.
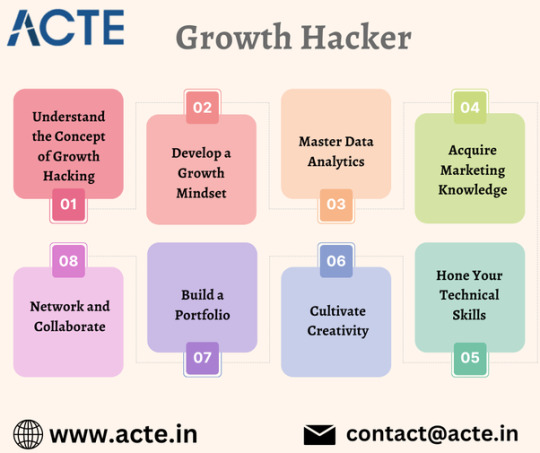
Grasp the Fundamentals of Growth Hacking: Before diving into the world of growth hacking, it's essential to comprehend its core concepts. Unlike traditional marketing, growth hacking is about experimentation, data-driven decision-making, and unconventional strategies to achieve remarkable growth. Immerse yourself in growth hacking case studies, success stories, and insights from industry experts to gain a solid foundation.
Cultivate a Growth Mindset: To succeed as a growth hacker, adopting a growth mindset is paramount. Nurture curiosity, adaptability, and a hunger for experimentation. Embrace continuous learning, stay ahead of industry trends, and develop a mindset that thrives on challenges and innovative problem-solving.
Master the Art of Data Analytics: Data forms the backbone of growth hacking. To excel in this field, it's crucial to become proficient in data analytics. Familiarize yourself with powerful tools like Google Analytics, Mixpanel, or Kissmetrics to extract actionable insights into user behavior, conversion rates, and key performance indicators (KPIs). The ability to derive meaningful conclusions from data and leverage them to drive growth strategies is a key skill for any growth hacker.
Acquire a Strong Marketing Foundation: While growth hacking has its unique characteristics, a solid understanding of marketing principles is invaluable. Gain knowledge in various marketing channels, such as content marketing, social media marketing, search engine optimization (SEO), email marketing, and conversion rate optimization (CRO). This knowledge will empower you to identify growth opportunities and create effective strategies.
Sharpen Your Technical Skills: Collaboration with developers and engineers is often integral to implementing growth strategies. While you don't need to become a coding expert, having a basic grasp of programming languages like HTML, CSS, and JavaScript will enable effective communication with technical teams and facilitate the independent execution of growth experiments.
To master the intricacies of ethical hacking and unlock its full potential, individuals can benefit from enrolling in the Best Ethical Hacking Online Training
Foster Creativity: Creativity is the lifeblood of growth hacking. Cultivate your ability to think outside the box and generate innovative ideas. Stay abreast of the latest marketing campaigns, growth hacks, and emerging technologies. Seek inspiration from diverse industries and embrace calculated risks in your pursuit of growth.
Showcase Your Expertise with a Portfolio: To demonstrate your growth hacking skills to potential employers or clients, build a portfolio that showcases your projects and experiments. Highlight case studies that outline the challenges you faced, the strategies you employed, and the measurable outcomes achieved. A compelling portfolio substantiates your practical knowledge and ability to deliver tangible results.
Network and Collaborate: Networking plays a pivotal role in any field, including growth hacking. Connect with fellow growth hackers, attend industry events, and actively engage in online communities. Participate in discussions, share your insights, and seek collaborative opportunities. Building a robust network can open doors to valuable connections, continuous learning, and exciting growth hacking endeavors.
Embarking on a growth hacking journey requires a unique blend of skills, mindset, and knowledge. By mastering the core principles of growth hacking, honing your data analytics skills, acquiring marketing expertise, nurturing creativity, and building a strong network, you position yourself for success in this ever-evolving field.
Embrace a growth mindset, persevere in experimentation, and leverage your skills to drive exponential growth for businesses. Remember, your path to becoming a growth hacker is an exciting adventure filled with learning opportunities, so stay determined, adaptable, and persistent along the way.
0 notes
Text
The Path to Expertise in Ethical Hacking and Penetration Testing: A Comprehensive Guide
In today's digital landscape, the demand for skilled professionals in ethical hacking and penetration testing is soaring, as organizations seek to fortify their cybersecurity defenses. If you're eager to embark on a journey toward becoming an expert in this field, will serve as your comprehensive guide. We will outline the essential steps you need to take to acquire the knowledge and skills necessary for mastering ethical hacking and penetration testing.
Let’s learn into some of the best ones, with a particular highlight on the unique ethical hacking course available at Chennai.

Establish a Strong Foundation:
Begin by building a solid foundation in computer networks, operating systems, and programming languages. Develop a deep understanding of TCP/IP, HTTP, DNS, and various operating system architectures. Gain proficiency in programming languages such as Python, C, or Ruby, as they are widely used in the cybersecurity domain.
Deepen Your Networking and Security Knowledge:
Expand your knowledge of networking protocols, security protocols, and encryption techniques. Delve into the intricacies of firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs). Familiarize yourself with common network vulnerabilities and effective mitigation strategies.
Master Operating Systems:
Acquire in-depth knowledge of popular operating systems like Windows, Linux, and macOS. Explore their security features, file systems, user management, and administrative controls. This understanding will enable you to identify vulnerabilities and develop effective countermeasures.
Explore Web Technologies:
Given the prevalence of web-based attacks, it is crucial to grasp the fundamentals of web technologies. Study HTML, CSS, JavaScript, and server-side scripting languages such as PHP or ASP.NET. Gain insight into common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Familiarize Yourself with Ethical Hacking Tools:
Develop proficiency in a wide range of ethical hacking tools. Tools like Nmap, Wireshark, Metasploit, Burp Suite, and John the Ripper are commonly employed for scanning, packet analysis, exploit development, and password cracking. Practice utilizing these tools in controlled environments.

Raise your career with ethical hacking course online and embark on a journey of success in the digital domain.
Pursue Relevant Certifications:
Certifications can validate your expertise and enhance your professional reputation. Consider pursuing certifications like Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or Certified Penetration Testing Engineer (CPTE). These certifications demonstrate your proficiency in ethical hacking and penetration testing.
Engage in Hands-On Practice:
Theory alone is insufficient in this field. Actively engage in hands-on practice to sharpen your skills. Set up a lab environment using virtualization software like VirtualBox or VMware. Undertake ethical hacking exercises in a controlled and legal manner, either within your lab environment or through platforms like Hack The Box or TryHackMe.
Stay Abreast of Industry Developments:
Cybersecurity is a constantly evolving field, necessitating continuous learning. Stay updated with the latest trends and vulnerabilities by following reputable cybersecurity blogs, subscribing to security newsletters, participating in online communities, and engaging in Capture The Flag (CTF) competitions. Embrace a mindset of lifelong learning to maintain your expertise.
Becoming an expert in ethical hacking and penetration testing requires dedication, continuous learning, and hands-on practice. By establishing a strong foundation, deepening your knowledge in networking, operating systems, and web technologies, exploring ethical hacking tools, pursuing certifications, engaging in practical exercises, and staying abreast of industry developments, you can chart a successful path toward mastery.
Always prioritize ethical practices and use your skills to protect and safeguard computer systems in an increasingly interconnected world.
0 notes
Text
Safeguarding Ethical Hacking Engagements: The Vital Role of Incident Response
Ethical hacking is a proactive approach to bolstering security measures, but it is crucial to recognize the significance of incident response within this process. Incident response teams play a critical role in effectively managing and mitigating security incidents that may occur during or as a result of ethical hacking engagements.
We will explore the essential role of incident response in safeguarding ethical hacking activities and ensuring a controlled and responsible testing environment.

Embracing hacking capabilities becomes even more accessible and impactful with Ethical Hacking Training in Chennai.
Key Points Regarding The Role Of Incident Response In Ethical Hacking:
Detecting and Monitoring for Early Intervention: Incident response teams maintain constant vigilance, monitoring systems and networks during ethical hacking engagements to promptly detect any signs of unauthorized activities, anomalies, or potential breaches. Their proactive detection ensures early intervention, minimizing the impact of security incidents.
Identifying and Prioritizing Incidents: Upon detecting a security incident, incident response professionals swiftly assess the situation, identify the nature and severity of the incident, and prioritize them based on their potential impact. This allows for efficient allocation of resources and timely response to mitigate risks.
Containment and Mitigation to Prevent Escalation: Incident response experts take immediate action to contain and mitigate the impact of security incidents during ethical hacking. By isolating affected systems or networks and implementing temporary countermeasures, they prevent further damage and unauthorized access.
Thorough Investigation and Analysis: Incident response teams conduct meticulous investigations to understand the root causes of security incidents, analyzing the techniques employed by potential attackers. This comprehensive analysis helps identify vulnerabilities exploited and provides valuable insights for effective remediation.
Collaborating with Ethical Hackers: Incident response professionals work closely with the ethical hacking team, fostering collaboration and open communication throughout the incident response process. They share information about the incident, provide technical expertise, and jointly develop strategies to address vulnerabilities and mitigate risks.

Remediation and Recovery Strategies: With their expertise in incident response, professionals assist in implementing remediation measures to address identified vulnerabilities and weaknesses. Their focus is on restoring systems to their normal functioning state, strengthening security controls, and ensuring a secure environment.
To master the intricacies of ethical hacking and unlock its full potential, individuals can benefit from enrolling in the Best Ethical Hacking Online Training.
Documentation and Continuous Improvement: Incident response teams document every aspect of security incidents, including response actions taken, impact assessment, and lessons learned. This documentation serves as a valuable resource for continuous improvement of incident response processes, security controls, and future ethical hacking engagements.
Incident response plays a vital role in safeguarding ethical hacking engagements by effectively managing security incidents. Incident response teams ensure early detection, swift response, containment, and thorough analysis of incidents, collaborating closely with ethical hackers to mitigate risks.
Their expertise in remediation, documentation, and continuous improvement strengthens security defenses and ensures responsible and controlled testing environments for ethical hacking activities.
0 notes
Text
A Comprehensive Roadmap to Pursuing a Career as an Information Security Analyst in 2024
In an era where information security is paramount, the demand for skilled professionals in the field is rapidly increasing. If you aspire to become an information security analyst in 2024, this comprehensive roadmap will guide you through the necessary steps to achieve your goal.
Learning Ethical Hacking is a significant decision with long-term consequences for your career and professional development.

With Ethical Hacking training in Chennai, professionals can gain the skills and knowledge needed to harness the capabilities of hacking for diverse applications and industries.
Steps To Become An Information Security Analyst In 2024:
Step 1: Attain a Relevant Degree To kickstart your journey as an information security analyst, it is advisable to pursue a bachelor's degree in a field such as cybersecurity, information technology, computer science, or a related discipline. Look for reputable educational institutions that offer specialized programs covering topics like network security, security management, computer forensics, and ethical hacking.
Step 2: Gain Practical Experience Earning a degree is only part of the equation. To stand out in the field, it is crucial to gain practical experience. Seek internships, part-time positions, or volunteer opportunities in information security-related roles. This hands-on experience will allow you to apply your theoretical knowledge in real-world scenarios and develop practical skills. Additionally, consider participating in cybersecurity competitions and joining relevant clubs and organizations to further enhance your skills and expand your professional network.
Step 3: Acquire Industry-Recognized Certifications Certifications are highly regarded in the information security field as they validate your expertise and commitment. Several certifications are widely recognized and sought after by employers, including CompTIA Security+, Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Certified Information Security Manager (CISM). Research the certifications that align with your career goals and invest time and effort in obtaining them. These certifications will not only bolster your knowledge but also make you a more desirable candidate to potential employers.
Step 4: Develop Technical Competencies Information security analysts must possess a strong technical skill set to effectively safeguard organizations' data and systems. Focus on developing skills in areas such as network security, vulnerability assessment and penetration testing, familiarity with security tools, and incident response procedures. Stay updated with the latest technological advancements and emerging threats by attending industry conferences, webinars, and joining online communities dedicated to information security.

Step 5: Stay Abreast of Industry Regulations and Best Practices Information security analysts must stay well-informed about industry regulations and best practices. Familiarize yourself with frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the General Data Protection Regulation (GDPR). Stay updated on best practices for securing various technologies and systems, and remain vigilant about emerging threats and attack vectors.
To learn the particulars of hacking and unleash its full potential, individuals can benefit from enrolling in the Best Ethical Hacking Online Training.
Step 6: Cultivate a Professional Network Networking is a crucial aspect of any career, including information security. Join professional organizations, attend local meetups, and actively engage in online forums to connect with industry professionals. Networking provides opportunities for valuable insights, mentorship, and potential job prospects.
Step 7: Pursue Entry-Level Positions Once you have acquired the necessary education, certifications, and practical experience, start applying for entry-level positions as an information security analyst. Look for organizations that prioritize cybersecurity and maintain dedicated security teams. Customize your resume and cover letter to highlight relevant skills and experiences that make you a strong candidate.
Step 8: Lifelong Learning and Professional Development Information security is a constantly evolving field, and continuous learning is essential. Stay updated with the latest cybersecurity news, participate in training programs and workshops, and pursue advanced certifications as you progress in your career.
Becoming an information security analyst requires a combination of education, practical experience, certifications, and a commitment to lifelong learning. By following this comprehensive roadmap, you will be well-equipped to pursue a successful career in information security in 2024. Stay proactive, adaptable, and passionate about staying ahead of emerging threats and technologies to excel in this dynamic field.
0 notes
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.

Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.
Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.

For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
1 note
·
View note
Text
The Significance of Thorough Risk Assessment in Ethical Hacking
In the realm of cybersecurity, ethical hacking plays a pivotal role in fortifying the security of systems and networks by identifying vulnerabilities. A crucial aspect of ethical hacking is conducting a comprehensive risk assessment.
This assessment aids in the identification of weaknesses, determining the impact of security breaches, ensuring compliance with industry standards, implementing proactive security measures, and optimizing resource allocation. We delves into the significance of comprehensive risk assessment in ethical hacking.

Enhancing your profession at the Ethical Hacking Course in Chennai requires following a systematic approach and enrolling in an appropriate course that will significantly broaden your learning experience while aligning with your preferences.
A Thorough Risk Assessment Is Important In Ethical Hacking For Various Reasons:
Uncovering Vulnerabilities: Thorough risk assessment empowers ethical hackers to uncover vulnerabilities within systems and networks. By meticulously evaluating security controls, configurations, and system architecture, ethical hackers can pinpoint weaknesses that could be exploited by malicious actors. This knowledge enables organizations to prioritize their security efforts and take appropriate measures to rectify identified vulnerabilities.
Assessing Potential Impact: Understanding the potential impact of a successful attack is crucial to devising an effective security strategy. A comprehensive risk assessment enables ethical hackers to assess the likelihood and severity of various risks. By evaluating the potential consequences of a security breach, organizations can make well-informed decisions about risk tolerance and allocate resources to mitigate high-impact risks.
Ensuring Regulatory Compliance: Various industries have specific compliance requirements to safeguard sensitive data. Ethical hackers play a vital role in assisting organizations in meeting these requirements. Through comprehensive risk assessment, ethical hackers can identify any compliance gaps and ensure that systems and processes adhere to the necessary standards. This not only helps organizations avoid penalties and reputational damage but also fosters trust among customers.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
Embracing Proactive Security: In today's rapidly evolving threat landscape, a proactive approach is paramount. Ethical hacking and risk assessments empower organizations to identify vulnerabilities and potential risks before they can be exploited. By conducting comprehensive risk assessments, ethical hackers help organizations bolster their security posture and minimize the likelihood of successful attacks. This proactive approach provides a significant advantage in staying ahead of potential threats.
Optimizing Resource Allocation: Effective resource allocation is crucial, particularly for organizations with limited budgets and resources. Comprehensive risk assessment enables ethical hackers and organizations to prioritize their security investments. By comprehending the potential impact of different risks, organizations can allocate resources to address the most critical vulnerabilities first. This ensures that resources are utilized efficiently, focusing on areas that pose the greatest risk to the organization.
Conducting a thorough risk assessment holds immense significance in the field of ethical hacking. It serves as the foundation for identifying vulnerabilities, assessing potential impact, ensuring regulatory compliance, implementing proactive security measures, and optimizing resource allocation.
Ethical hackers play a vital role in helping organizations strengthen their security posture and mitigate risks associated with potential security breaches. By embracing comprehensive risk assessment practices, organizations enhance their ability to safeguard valuable assets and confidential information from ever-evolving cybersecurity threats.
0 notes
Text
A Comprehensive Approach to Excelling in the CEH v11 Exam
The CEH (Certified Ethical Hacker) certification holds immense importance in the cybersecurity field as it validates the skills and knowledge required for identifying vulnerabilities and evaluating the security of computer systems. The latest iteration, CEH v11, covers a broad spectrum of topics, including ethical hacking techniques, network security, and penetration testing methodologies. If you are planning to undertake the CEH v11 exam and want to maximize your chances of success, this comprehensive guide will equip you with essential tips and resources to effectively prepare for the exam.
Choosing the Best Ethical hacking course in Chennai and certificates online in 2024 can be overwhelming, with so many options available.

Gain a Thorough Understanding of the Exam Objectives:
To embark on your preparation journey, it is crucial to familiarize yourself with the exam objectives. Visit the EC-Council website or refer to the official CEH v11 exam blueprint to gain a clear understanding of the topics that will be assessed. Doing so will enable you to structure your study plan and allocate appropriate time to each domain.
Delve into the Official Study Guide:
The CEH v11 Official Study Guide is an invaluable resource that delves into all the exam objectives in detail. It offers comprehensive explanations, practical examples, and hands-on exercises to reinforce your understanding of the concepts. Take the time to thoroughly read and study the guide, taking notes and highlighting key points for later review.
Utilize Supplementary Learning Materials:
To augment your grasp of the CEH v11 exam topics, make use of supplementary learning resources. Numerous books, video courses, and online tutorials are available that explore ethical hacking techniques, tools, and methodologies. Consider reputable platforms like Cybrary, Udemy, or Pluralsight, which offer comprehensive CEH v11 exam preparation materials.
Engage in Practical Hands-On Practice:
Ethical hacking is a practical skill, and hands-on practice plays a pivotal role in succeeding in the CEH v11 exam. Set up a virtual lab environment using tools such as VirtualBox or VMware and engage in controlled and ethical hacking techniques. Utilize tools like Metasploit, Wireshark, Nmap, and Burp Suite to gain practical experience and reinforce your understanding of their functionalities.
Tackle Practice Questions and Mock Exams:
To assess your knowledge and identify areas that require improvement, tackle practice questions and take mock exams specifically designed for the CEH v11 exam. These resources will familiarize you with the exam format, time constraints, and question types. Analyze your performance, review explanations for incorrect answers, and focus on strengthening your weaker areas.

Ultimately, the Best ethical hacking courses online and certificates for you will depend on your individual needs and goals.
Participate in Online Communities and Discussion Forums:
Active involvement in the cybersecurity community can provide invaluable insights and support during your CEH v11 exam preparation. Join online forums, discussion groups, and social media communities dedicated to ethical hacking and penetration testing. Engage in discussions, seek clarification on doubts, and share your knowledge and experiences. This collaborative environment will help you gain new perspectives and learn from the experiences of others.
Leverage Official Training Programs:
Consider enrolling in official CEH v11 training programs provided by EC-Council or their accredited training providers. These programs offer structured learning paths, hands-on labs, and expert guidance, ensuring comprehensive preparation for the exam. Additionally, they often include exam vouchers or discounted retake options, which can be advantageous if you require additional attempts.
Stay Abreast of the Latest Industry Trends:
The cybersecurity landscape evolves rapidly, necessitating the need to stay updated with the latest industry trends, threats, and countermeasures. Subscribe to cybersecurity blogs, industry newsletters, and participate in webinars or conferences to remain informed about emerging technologies and vulnerabilities. This knowledge will not only benefit your CEH v11 exam preparation but also contribute to your overall cybersecurity expertise.
Preparing for the CEH v11 exam demands a structured approach, dedication, and practical experience. By gaining a thorough understanding of the exam objectives, exploring the official study guide, utilizing supplementary learning materials, engaging in hands-on practice, tackling practice questions and mock exams, participating in online communities, considering official training programs, and staying updated with industry trends, you can significantly enhance your chances of success in the exam.
Remember to approach ethical hacking responsibly and ethically, as the knowledge and skills gained through this certification will empower you to contribute to a safer digital realm. Best of luck on your CEH v11 exam journey!
0 notes
Text
Unveiling the Arsenal of Kali Linux: Essential Tools for Ethical Hacking and Penetration Testing
Kali Linux, the renowned Linux distribution, is widely embraced by cybersecurity professionals, ethical hackers, and penetration testers. One of its greatest strengths lies in its comprehensive array of tools tailored for information security.

Elevate your Ethical Hacking career with a leading ethical hacking course in Chennai
In this blog post, we will delve into the world of Kali Linux tools, shedding light on its indispensable and powerful resources that empower ethical hackers and penetration testers in their quest for securing digital systems.
Nmap: Unleashing Network Exploration and Security Auditing Capabilities Nmap (Network Mapper), an instrumental tool within Kali Linux, facilitates network scanning, mapping, and auditing. By uncovering open ports, identifying hosts, and gathering vital information on network services and devices, Nmap serves as an invaluable asset for security professionals.
Metasploit Framework: Harnessing the Power of Exploitation and Penetration Testing The Metasploit Framework, a stalwart tool within Kali Linux, empowers users to exploit system vulnerabilities and execute penetration tests. With its extensive toolkit, encompassing exploit modules, payload generators, and post-exploitation utilities, Metasploit offers a comprehensive solution for effective penetration testing.
Wireshark: Decrypting Network Traffic for Enhanced Analysis Wireshark, a widely-utilized network protocol analyzer, enables meticulous inspection of network traffic. Armed with an array of features, Wireshark facilitates packet analysis, deep dives into network protocols, and identification of potential security vulnerabilities.
Burp Suite: Elevating Web Application Security Testing Burp Suite, an integrated platform within Kali Linux, serves as the ultimate companion for comprehensive web application security testing. Equipped with an array of scanning, intercepting, and manipulating tools, Burp Suite unveils security flaws such as SQL injection, cross-site scripting (XSS), and session hijacking.
John the Ripper: Mastering the Art of Password Cracking John the Ripper, a widely-admired password-cracking tool within Kali Linux, employs various techniques such as brute force, dictionary attacks, and rainbow tables to crack passwords. This valuable asset aids in assessing the strength of password security.

Considering the Best Ethical Hacking Online Training becomes pivotal.
6. Aircrack-ng: Unveiling Wi-Fi Network Vulnerabilities Aircrack-ng, a specialized network auditing tool, focuses on assessing Wi-Fi network security. By capturing packets, launching attacks against wireless networks (WEP and WPA/WPA2), and analyzing wireless protocols, Aircrack-ng exposes potential vulnerabilities within wireless infrastructures.
7. Hydra: Unleashing Potent Online Password-Cracking Capabilities Hydra, a formidable online password-cracking tool, supports numerous protocols such as FTP, SSH, Telnet, and SMTP. Employing techniques like brute-force and dictionary attacks, Hydra aims to crack passwords and gain unauthorized access to targeted systems.
SQLMap: Taming Web Application Vulnerabilities SQLMap, a specialized tool within Kali Linux, facilitates the detection and exploitation of SQL injection vulnerabilities in web applications. By automating the identification of vulnerable parameters, extraction of data from databases, and even achieving command execution, SQLMap bolsters web application security.
Kali Linux's expansive toolkit provides ethical hackers and penetration testers with a wealth of resources. The aforementioned tools merely scratch the surface of what Kali Linux has to offer. Armed with these powerful and specialized tools, professionals can strengthen their skills and make significant contributions to the ever-evolving field of cybersecurity.
By embracing Kali Linux and mastering its toolkit, individuals can effectively secure systems, identify vulnerabilities, and safeguard digital infrastructures.
0 notes
Text
Unleashing the Premier Resource for Excelling in Ethical Hacking
Absolutely! I share your enthusiasm for delving into the world of Ethical Hacking. My expertise in this domain has grown significantly, solidifying its recognition and widespread application across various industries.
Aspiring ethical hackers seeking to excel in the field of cybersecurity require access to exceptional learning resources. To become proficient in ethical hacking, it is essential to find comprehensive and reliable materials.

To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai. Their wealth of expertise and resources can offer valuable insights and skills, contributing to advancing your proficiency in ethical hacking.
In this blog post, we will unveil the premier resource that offers unparalleled knowledge and guidance for mastering ethical hacking.
Unleashing Excellence: Cybrary - Empowering Ethical Hackers
Cybrary emerges as the unrivaled resource that empowers individuals on their ethical hacking journey. This online platform provides an extensive range of resources, making it the ideal environment for beginners and experienced individuals alike. Let's explore why Cybrary stands out as the premier resource:
Extensive Array of Courses: Cybrary boasts an extensive catalog of courses that cover every facet of ethical hacking, from foundational concepts to advanced techniques. These courses are meticulously crafted by industry experts and cover topics such as penetration testing, network security, web application security, and more.
Immersive Hands-on Labs: Setting itself apart, Cybrary offers immersive virtual labs that allow learners to practice their skills in a controlled and secure environment. These labs simulate real-world scenarios, enabling users to apply the knowledge gained from the courses and gain invaluable practical experience.
Engaged and Supportive Community: Cybrary fosters an engaged community of learners and professionals who actively participate in discussions, share insights, and provide support. This collaborative environment facilitates networking opportunities, mentorship, and the exchange of ideas.
Look for classes that educate a basic understanding of ethical hacking. Considering the Best Ethical Hacking Online Training becomes critical.
4. Prestigious Certification Pathways: Cybrary provides prestigious certification pathways that validate and showcase the expertise of ethical hackers. These certifications enhance professional credibility and can be instrumental in career advancement and industry recognition.

5.Flexibility and Accessibility: Cybrary offers flexibility and accessibility, allowing learners to study at their own pace and convenience. The platform can be accessed from any location, be it on a computer or mobile device, ensuring that learning fits seamlessly into individuals' busy schedules.
When it comes to excelling in ethical hacking, Cybrary is the premier resource that equips learners with comprehensive knowledge and practical skills.
With its diverse course catalog, immersive hands-on labs, engaged community, prestigious certifications, and flexible accessibility, Cybrary provides the perfect foundation for a successful journey in ethical hacking. Embrace this resource, unleash your potential, and make a significant impact in the realm of cybersecurity.
0 notes
Text
Exploring the Top Ethical Hacking Tools for Cybersecurity Professionals
In the realm of cybersecurity, ethical hacking serves as a crucial practice for identifying vulnerabilities and strengthening the security of computer systems and networks. Cybersecurity professionals rely on a range of specialized applications and tools to carry out these authorized hacking activities.
Embracing hacking capabilities becomes even more accessible and impactful with Ethical Hacking Training in Chennai.

This article delves into some of the most widely recognized ethical hacking tools that play a significant role in the arsenal of cybersecurity experts.
Metasploit: Metasploit stands out as a renowned penetration testing framework, offering an extensive suite of tools and exploits. It empowers professionals to discover and exploit vulnerabilities within systems and networks. With Metasploit, cybersecurity experts can conduct comprehensive network discovery, vulnerability scanning, and penetration testing. This versatile tool is highly favored within the ethical hacking community.
Nmap: Nmap, also known as Network Mapper, is a powerful network scanning tool utilized by ethical hackers to identify hosts and services within a network. By employing Nmap, cybersecurity professionals can pinpoint open ports, detect operating systems, and extract valuable information about network devices. It serves as an indispensable tool for reconnaissance and initial network assessment.
Wireshark: Wireshark, a widely popular network protocol analyzer, enables cybersecurity professionals to capture and analyze network traffic in real-time. This tool proves invaluable for troubleshooting network issues, delving into network protocols, and unearthing potential security vulnerabilities. Ethical hackers rely on Wireshark's capabilities to enhance their understanding of network communications.
Burp Suite: Burp Suite is a comprehensive platform designed for security testing of web applications. It comprises an array of tools that facilitate scanning, intercepting, and modifying HTTP/HTTPS traffic. Cybersecurity professionals heavily rely on Burp Suite for web application penetration testing, vulnerability assessment, and identifying potential security weaknesses within web-based systems.
John the Ripper: John the Ripper is a widely recognized password cracking tool that aids in the identification of weak passwords. By supporting various password attack techniques such as dictionary attacks and brute-force attacks, cybersecurity professionals leverage John the Ripper to assess password strength and bolster overall security by identifying vulnerable accounts.
Aircrack-ng: Aircrack-ng serves as a comprehensive suite of tools dedicated to assessing the security of Wi-Fi networks. It encompasses features for packet capturing, WEP and WPA/WPA2-PSK key cracking, and executing various Wi-Fi-related attacks. Ethical hackers depend on Aircrack-ng to uncover and exploit weaknesses in wireless networks.
SQLMap: SQLMap is a widely utilized automated tool specifically designed to detect and exploit SQL injection vulnerabilities in web applications. This tool streamlines the process of identifying SQL injection flaws, which can be exploited to gain unauthorized access to databases. Ethical hackers rely on SQLMap to assess web application security and protect against SQL injection attacks.

To master the intricacies of ethical hacking and unlock its full potential, individuals can benefit from enrolling in the Best Ethical Hacking Online Training.
8. Hydra: Hydra serves as a potent online password cracking tool supporting multiple protocols, including HTTP, FTP, SSH, Telnet, and more. It allows cybersecurity professionals to launch brute-force and dictionary attacks against login pages and services, helping them identify weak or default credentials. Hydra plays a crucial role in assessing password strength and enhancing overall security.
Ethical hacking tools are indispensable for cybersecurity professionals seeking to fortify the security of computer systems and networks. The tools mentioned in this article, including Metasploit, Nmap, Wireshark, Burp Suite, John the Ripper, Aircrack-ng, SQLMap, and Hydra, represent some of the most popular and widely utilized ethical hacking tools.
It is essential to utilize these tools responsibly, with proper authorization and in compliance with legal and ethical guidelines. Ethical hacking serves as a crucial component in safeguarding organizations against malicious threats and bolstering their overall security posture.
0 notes
Text
Master the Art of Ethical Hacking: Top Online Courses for Cybersecurity Enthusiasts
In today's ever-evolving digital landscape, mastering the art of ethical hacking has become essential for safeguarding digital assets and combating cyber threats.

To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai. Their wealth of expertise and resources can offer valuable insights and skills, contributing to advancing your proficiency in ethical hacking.
This blog post explores some of the leading online courses available that can equip cybersecurity enthusiasts with the knowledge and skills needed to excel in the field of ethical hacking.
"Ethical Hacking: Fundamentals Unveiled" on Udemy: This Udemy course serves as a comprehensive introduction to the fundamentals of ethical hacking. It covers critical topics such as reconnaissance, scanning, enumeration, and exploitation. With hands-on exercises and practical examples, it lays a solid groundwork for beginners venturing into the world of ethical hacking.
"The Complete Ethical Hacking Course: From Beginner to Advanced!" on Udemy: Designed with beginners in mind, this extensive course covers a broad spectrum of subjects, including information gathering, vulnerability assessment, network hacking, and web application testing. Boasting over 24 hours of video content and hands-on labs, it offers a holistic learning experience for aspiring ethical hackers.
"Ethical Hacking and Penetration Testing with Kali Linux" on Udemy: Focused on leveraging Kali Linux, a renowned operating system for ethical hacking and penetration testing, this course delves into scanning networks, exploiting vulnerabilities, and advanced post-exploitation techniques. It serves as an invaluable resource for individuals seeking specialization in Kali Linux as part of their ethical hacking arsenal.
"Certified Ethical Hacker (CEH)" by EC-Council: EC-Council's Certified Ethical Hacker (CEH) certification is globally recognized and highly regarded in the ethical hacking realm. The official training program for CEH covers an extensive range of ethical hacking topics, delivering comprehensive knowledge and practical skills required to identify vulnerabilities and effectively protect against cyber threats.

Look for classes that educate a basic understanding of ethical hacking. Considering the Best Ethical Hacking Online Training becomes critical.
5. Ethical Hacking for Beginners" on Pluralsight: Tailored for beginners, this Pluralsight course provides a solid foundation in ethical hacking essentials, including network scanning, enumeration, and system hacking. Through practical demonstrations and hands-on labs, learners gain invaluable real-world experience in a guided learning environment.
6. "Learn Ethical Hacking from Scratch" on Udemy: This beginner-friendly course takes learners on a step-by-step journey, starting from the basics and building up their ethical hacking skills. It covers key areas such as foot printing, scanning, enumeration, and more. With practical exercises and real-world examples, it empowers students to develop a strong ethical hacking foundation.
By enrolling in top-notch online courses, cybersecurity enthusiasts can master the art of ethical hacking and effectively navigate the intricate world of cybersecurity. Whether you are a beginner taking your first steps or a seasoned professional aiming to enhance your skills, these courses offer valuable resources and immersive learning opportunities.
Always remember to practice ethical hacking responsibly, adhering to legal boundaries and respecting privacy. Choose the course that aligns with your proficiency level and learning preferences, and embark on your transformative journey towards becoming a proficient ethical hacker.
1 note
·
View note
Text
Safeguarding the Digital Landscape: The Significance of Ethical Hacking
In an interconnected world where cyber threats loom large, organizations must prioritize cybersecurity to protect their systems and data. Ethical hacking, also known as white-hat hacking or penetration testing, plays a pivotal role in this pursuit. This blog post highlights the importance of ethical hacking in safeguarding the digital landscape.
To enrich your Ethical Hacking journey, I recommend considering a reputable Ethical Hacking Course in Chennai. Their wealth of expertise and resources can offer valuable insights and skills, contributing to advancing your proficiency in ethical hacking.

Some Reasons Why Ethical Hacking Is Important:
Unearthing Vulnerabilities: Ethical hackers possess the expertise to identify vulnerabilities within systems, networks, and applications. By actively searching for weaknesses, they enable organizations to discover potential entry points that malicious hackers could exploit. By identifying these vulnerabilities before cybercriminals do, ethical hackers empower organizations to take preemptive measures to strengthen their defenses.
Bolstering Security Measures: Ethical hacking extends beyond vulnerability identification; it helps organizations enhance their overall security posture. Through comprehensive security assessments, ethical hackers not only pinpoint weaknesses but also provide recommendations and solutions to mitigate risks. By implementing these recommendations, organizations can fortify their systems and ensure the protection of sensitive data.
Mitigating Financial Losses: Cyberattacks can wreak havoc on an organization's financial standing. The costs associated with data breaches, legal liabilities, and reputational damage can be staggering. Ethical hacking plays a crucial role in mitigating potential financial losses by identifying security gaps and vulnerabilities that cybercriminals may exploit. By investing in ethical hacking services, organizations can potentially save significant costs in the long run.
Fostering Customer Trust: In an era where data breaches erode consumer confidence, maintaining customer trust is paramount. Ethical hacking contributes to this trust by conducting security assessments and implementing robust security measures. Such proactive measures demonstrate an organization's commitment to safeguarding customer data, bolstering its reputation, and fostering loyalty and trust among its clientele.
Ensuring Regulatory Compliance: Numerous industries are bound by stringent regulations and compliance requirements concerning data protection and cybersecurity. Ethical hacking assists organizations in meeting these obligations by identifying vulnerabilities and ensuring the implementation of appropriate security controls. Compliance with these regulations helps organizations avoid penalties, legal ramifications, and reputational damage.
Look for classes that educate a basic understanding of ethical hacking. Considering the Best Ethical Hacking Online Training becomes critical.

Staying Ahead of Cybercriminals: Cybercriminals are constantly innovating their tactics to breach systems and exploit vulnerabilities. Ethical hacking enables organizations to maintain a proactive stance. By simulating real-world attack scenarios, ethical hackers can identify emerging threats and vulnerabilities. Armed with this knowledge, organizations can develop and implement effective defense strategies, ensuring they remain one step ahead of cybercriminals.
Cultivating a Security-Focused Culture: Ethical hacking promotes a culture that prioritizes proactive security measures within organizations. By conducting regular security assessments, ethical hackers raise awareness about the significance of cybersecurity among employees. This includes imparting knowledge about best practices, implementing secure coding standards, and fostering a culture that values security at every level. A security-focused culture serves as a strong bulwark against potential breaches and minimizes risks.
By unearthing vulnerabilities, bolstering security measures, mitigating financial losses, fostering customer trust, ensuring regulatory compliance, staying ahead of cybercriminals, and cultivating a security-focused culture, ethical hacking strengthens an organization's defenses against evolving cyber threats.
Embracing ethical hacking practices is a proactive approach that fortifies systems, protects valuable data, and bolsters the resilience of organizations in the face of constant cyber risks.
0 notes
Text
Demystifying Cryptography Ciphers: Unlocking the Secrets of Secure Communication
In the realm of cybersecurity, cryptography stands tall as the guardian of secure communication and data protection. At the heart of this fascinating field lie cryptography ciphers, the mathematical algorithms that empower encryption and decryption. We embark on a captivating exploration of cryptography ciphers, unravelling their diverse types, functions, and practical implementations.
For those looking to master the art of ethical hacking, enrolling in a reputable the Ethical Hacking Course in Chennai can provide the essential skills and knowledge needed for navigating this dynamic landscape effectively.
Unveiling the Diversity of Cryptography Ciphers: Safeguarding Information: Cryptography ciphers can be classified into various types, each offering unique characteristics and catering to specific security requirements.
Let's Delve Into The Key Categories:
Symmetric Key Ciphers: Harnessing the Power of Shared Secrets: Symmetric key ciphers, also known as secret key ciphers, rely on a single shared key for both encryption and decryption. These ciphers excel in speed and efficiency, making them ideal for encrypting large volumes of data. Prominent examples include the Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple Data Encryption Standard (3DES).
Asymmetric Key Ciphers: Unleashing the Potential of Public-Private Pairs: Asymmetric key ciphers, also called public key ciphers, use mathematically related key pairs: a public key for encryption and a private key for decryption. This innovative approach simplifies key management and enables secure communication without the need for a shared secret. Well-known examples include the Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC) ciphers.
Hash Functions: Safeguarding Data Integrity: Hash functions are cryptographic algorithms that generate fixed-size outputs, known as hashes or message digests, from input data of any size. These functions play a vital role in data integrity verification and digital signatures. Noteworthy hash functions include the Secure Hash Algorithm (SHA) family, such as SHA-256, and the Message Digest Algorithm 5 (MD5).
This is where enrolling in the Top Ethical Hacking Online Training can make a significant difference.
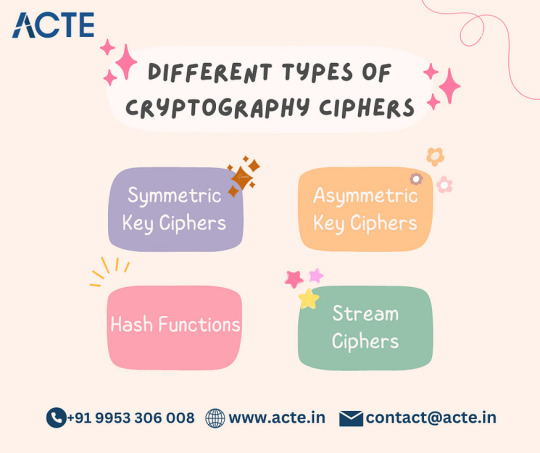
Stream Ciphers: Empowering Real-Time Encryption: Stream ciphers encrypt data in a continuous stream, typically one bit or byte at a time. They excel in real-time communication and large-scale data encryption scenarios. An example of a notable stream cipher is the Rivest Cipher 4 (RC4), which has found applications in various domains.
Practical Applications: Fortifying Confidentiality and Integrity: Cryptography ciphers find widespread use across diverse domains and applications. Some notable implementations include:
Securing Communication: Encryption ciphers ensure the confidentiality and integrity of sensitive information transmitted over networks. They are the backbone of secure email communication, virtual private networks (VPNs), and secure web browsing (HTTPS).
E-commerce and Financial Transactions: Cryptography safeguards online transactions, including e-commerce purchases and financial transactions, by encrypting sensitive data, such as credit card information, and securing communication channels.
Data Integrity and Digital Signatures: Hash functions play a vital role in ensuring data integrity, verifying message authenticity, and enabling the creation of digital signatures for non-repudiation purposes.
Cryptography ciphers serve as the guardians of secure communication, data protection, and trust in the digital landscape. With a rich variety of ciphers available, including symmetric key ciphers, asymmetric key ciphers, hash functions, and stream ciphers, individuals and organizations possess a powerful toolkit to safeguard their confidential information.
By understanding the diversity and practical applications of cryptography ciphers, we can navigate the intricate world of cybersecurity with confidence, ensuring privacy, integrity, and security in our digital interactions.
0 notes