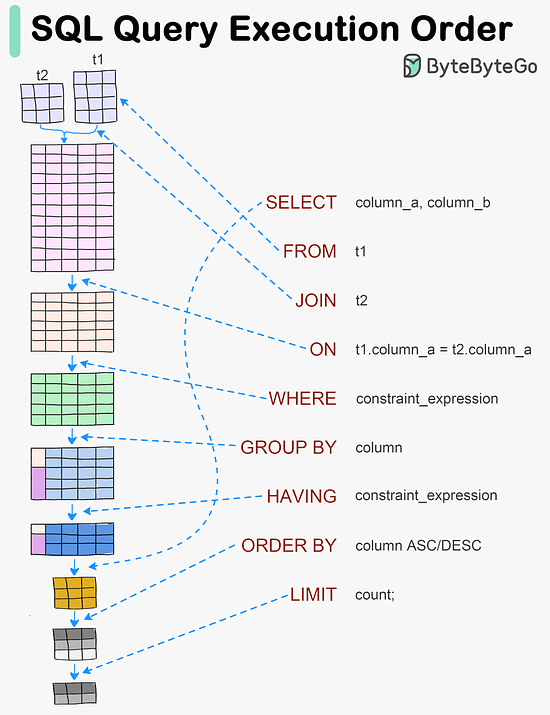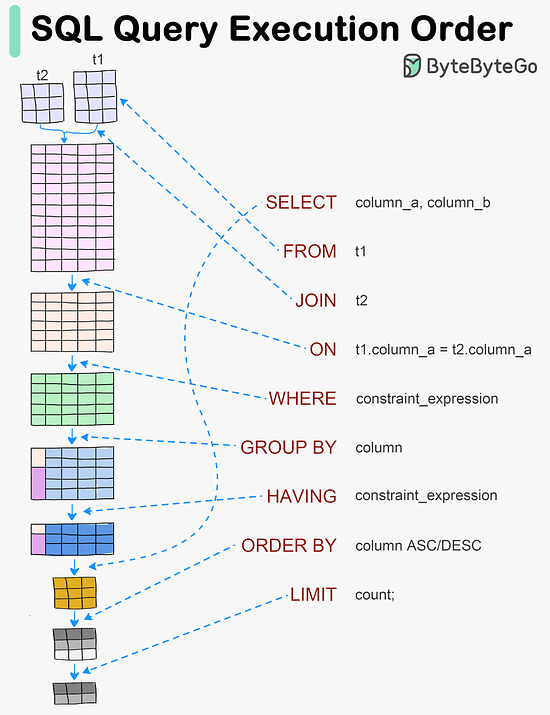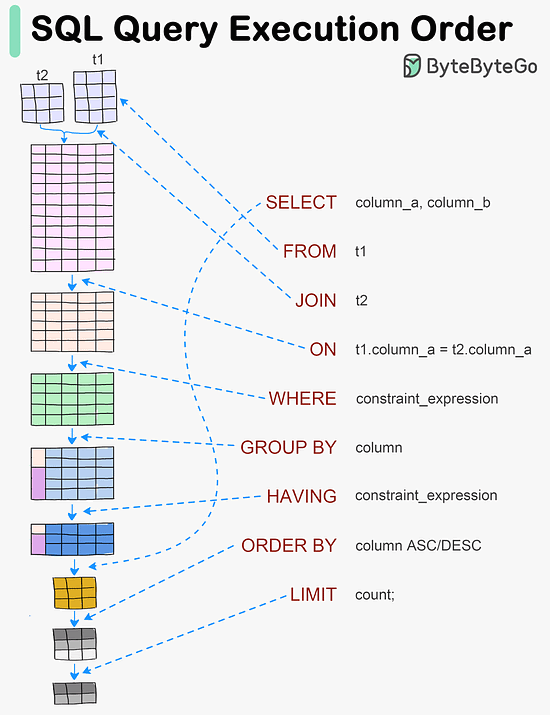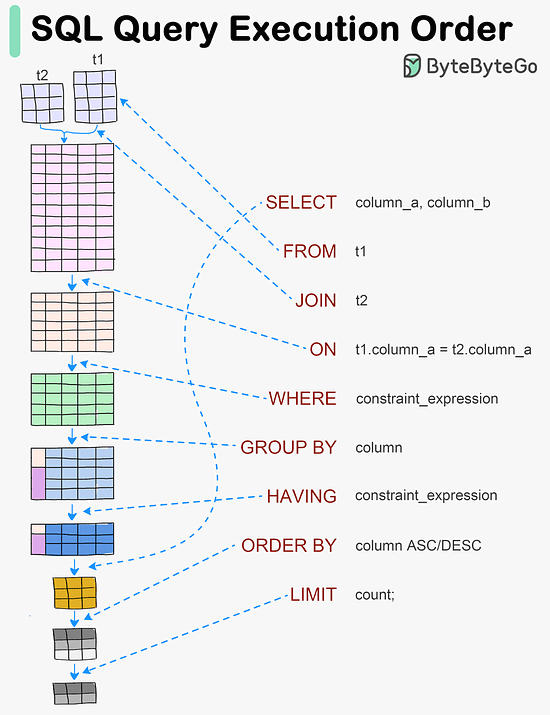
#SQL queries
Explore tagged Tumblr posts
Text
DuckDB: Unraveling the Feathers of a Revolutionary Analytical Database
In the fast-paced world of data management and analytics, one name has been gaining traction for its feather-light performance and versatile capabilities – DuckDB. This blog post takes you on a journey into the realm of DuckDB, exploring its origins, unique features, and the impact it is making on the landscape of analytical databases. The Birth of DuckDB: Born out of the need for a…

View On WordPress
1 note
·
View note
Text
Unlocking the Full Power of Apache Spark 3.4 for Databricks Runtime!
You've dabbled in the magic of Apache Spark 3.4 with my previous blog "Exploring Apache Spark 3.4 Features for Databricks Runtime", where we journeyed through 8 game-changing features
You’ve dabbled in the magic of Apache Spark 3.4 with my previous blog “Exploring Apache Spark 3.4 Features for Databricks Runtime“, where we journeyed through 8 game-changing features—from the revolutionary Spark Connect to the nifty tricks of constructing parameterized SQL queries. But guess what? We’ve only scratched the surface! In this sequel, we’re diving deeper into the treasure trove of…

View On WordPress
#Apache Spark#Azure Databricks#Azure Databricks Cluster#Data Frame#Databricks#databricks apache spark#Databricks SQL#Memory Profiler#NumPy#performance#Pivot#pyspark#PySpark UDFs#SQL#SQL queries#SQL SELECT#SQL Server
0 notes
Text
SQL queries for beginners

0 notes
Text
SQL Injection Attacks:
Understanding the Risks and Implementing Prevention Measures
Introduction:
In today's interconnected world, where data is a valuable asset, protecting the integrity and security of databases is critical. SQL injection attacks are a significant threat that database administrators and developers face. These attacks take advantage of vulnerabilities in web applications to manipulate the underlying SQL queries, potentially resulting in unauthorized access, data breaches, and compromised systems. Understanding the risks associated with SQL injection attacks and putting effective prevention measures in place are critical for protecting sensitive data. In this article, we will look into the specifics of SQL injection attacks, as well as their potential consequences and preventive measures.
What exactly is SQL Injection?
SQL injection is a technique used by attackers to insert malicious SQL code into a database query in an application, allowing them to manipulate the query's behavior. Attackers can circumvent authentication mechanisms, access unauthorized data, modify or delete records, and even take control of the entire database server by taking advantage of inadequate input validation and sanitization practices.
SQL Injection Attack Risks and Consequences:
a. Unauthorized Access: SQL injection vulnerabilities can be used by attackers to bypass login systems and gain unauthorized access to sensitive data, user accounts, or administrative privileges.
b. Data Breach: SQL injection attacks can expose sensitive data, such as personally identifiable information (PII), financial data, or intellectual property. This can have serious legal, financial, and reputational ramifications for organizations.
c. Database Manipulation: Attackers can change, delete, or manipulate data in a database, potentially resulting in data corruption, operational disruptions, or financial losses.
d. Denial of Service: SQL injection attacks can cause database servers to become overloaded, resulting in system crashes or slowdowns and making the application inaccessible to legitimate users.
Preventive measures include:
a. Input Validation and Sanitization: Enforce strict input validation by validating and sanitizing user input before it is used in SQL queries. Use parameterized queries or prepared statements to ensure code and data separation, preventing malicious code injection.
b. Least Privilege Principle: Assign database accounts the bare minimum of privileges. Reduce the potential impact of a successful SQL injection attack by restricting access and limiting the permissions granted to application accounts.
c. Web Application Firewalls (WAF): Use WAFs that specialize in detecting and preventing SQL injection. These security solutions can detect and prevent malicious SQL queries from reaching the database server.
d. Regular Patching and Updates: Maintain all software, frameworks, and libraries with the most recent security patches. This contributes to addressing known vulnerabilities that attackers could exploit.
e. Educate and Train Developers: Raise developer awareness of the risks and consequences of SQL injection attacks. Teach them secure coding techniques, with an emphasis on input validation, parameterized queries, and proper error handling techniques.
f. Security Audits and Penetration Testing: Perform regular security audits and penetration testing to identify and remediate potential SQL injection vulnerabilities. Engage ethical hackers or security professionals to assess the security posture of the application.
Conclusion:
SQL injection attacks pose a significant risk to database security and integrity, potentially resulting in unauthorized access, data breaches, and compromised systems. Understanding the risks of SQL injection and implementing strong prevention measures are critical for organizations looking to safeguard their valuable data assets. Developers and administrators can mitigate risks and stay one step ahead of malicious actors by implementing secure coding practices, deploying web application firewalls, and conducting regular security audits. Remember that prevention is the key to preventing SQL injection attacks and ensuring the security of your database systems.
Improve your SQL knowledge today! Join CACMS for our in-depth SQL complete course and discover the power of databases. Enroll right now http://cacms.in/
#sql course#sql certification#learn sql#sql database#sql queries#sql tutorial#cacms institute#enroll now#sql attacks
0 notes
Text
#tumblr#digital marketing#online learning#technology#postoftheday#education#artists on tumblr#printer#knowledge#trending#learn sql#sql training#sqlserver#sql queries#python#coding#open source#elena sqloint#sql#webdev#java#programming
1 note
·
View note
Text
1 note
·
View note
Text
fuck sql, left join deez nuts mf'ers
#after all these years I still hate sql#the more I learn the more I hate#get a real query language fuckers#sql#tech#personal
14 notes
·
View notes
Text
praying to the patron saint of fake it til you make it at a job you're only halfway qualified for (moist von lipwig)
#beck posts#discworld#moist von lipwig#(pretending to know how to read sql queries while on camera) this is happened to my good friend moist
18 notes
·
View notes
Text
I need AO3 search to allow window functions
#the search operators are helpful!#they're a good start!#but the sorting leaves something to be desired#just. let me write a sql query. that's what I really want here.#give me your database i promise i won't misuse it
15 notes
·
View notes
Text
goddamnit can my coworkers do nothing without chatgpt anymore.
7 notes
·
View notes
Text
I put the queer in SQL query
#memes#computer memes#196 rule#196 campfire#sql#SQL query#lgbtq#lgbt#lgbt memes#queer#meme#196#rule 196
28 notes
·
View notes
Text
so it turns out they weren't kidding when they said breaking a monolith into microservices is hard.
#programming#enterprise software#enterprise application development#microservices#it also doesn't help that some folks need to BANNED from writing SQL queries
3 notes
·
View notes
Text
Learn SQL Easy
If you're interested in learning SQL (Structured Query Language), the standard database access language, try learning from a place called SQL Easy. They provide a great self-learning environment where you can learn this language or troubleshoot how to code something.
I'm still learning SQL, even after using it for a few years. I came here looking for a code to pull records within a 7-day span and used this page here: https://www.sql-easy.com/learn/how-to-get-last-7-days-record-in-postgresql/
0 notes
Text
Learn SQL Easily with Takeoff Upskill and Build Your Data Skills
SQL (Structured Query Language) is one of the most important skills for anyone working with data. At Takeoff Upskill, we offer a comprehensive SQL course that makes learning this valuable skill easy and accessible. Whether you are a beginner or someone looking to enhance your database knowledge, this course is designed to meet your needs.

Our SQL course starts with the basics, such as understanding databases, tables, and data types. You will learn how to create, read, update, and delete data using SQL commands. The course also covers advanced topics like joining multiple tables, writing complex queries, and optimizing database performance. These skills are essential for roles like data analyst, software developer, and database administrator.
The training at Takeoff Upskill is practical and hands-on. We provide real-world examples and exercises that help you understand how SQL is used in businesses. By the end of the course, you will be confident in writing queries, managing data, and solving database challenges. Our experienced trainers guide you every step of the way, ensuring you gain a strong foundation.
#SQL course#SQL training#data management#Takeoff Upskill#SQL for beginners#learn SQL#database queries#SQL skills
0 notes
Text
Its fun to be taught basic programming and sql when you have ten years of experience using both and a degree in cs
0 notes