#Password manager with AES 256-bit encryption
Explore tagged Tumblr posts
Text
Enhance Your Digital Efficiency with RelyPass




RelyPass, the ultimate iOS password manager app designed to revolutionize your digital efficiency. RelyPass effortlessly combines user-friendly features, unbeatable pricing, and top-notch security. Upgrade your digital lifestyle today and experience the convenience of RelyPass!
Download the App today!
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Password manager with AES 256-bit encryption#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
🔒 Why Keeper Security is the Best Password Manager for Your Organization 🔑
In today’s digital age, securing sensitive data is more important than ever, and Keeper Security makes it easier than ever to safeguard your organization’s passwords. Here's why it's the best choice for businesses:
Robust Security: Keeper uses AES-256 bit encryption and zero-knowledge architecture, ensuring your data stays private and secure, even if the system is compromised.
User-Friendly: Simple interface and seamless integrations across all devices, making it easy for employees to adopt.
Advanced Features: From secure password sharing to breach monitoring and dark web scanning, Keeper provides everything you need to stay ahead of potential threats.
Team Collaboration: Effortless password management for teams, with role-based permissions and secure access for all levels of your organization.
Compliance: Meets industry standards like GDPR, HIPAA, and SOC 2, ensuring your organization is always compliant.
Protect your business with Keeper Security and give your team the tools to stay safe online! 💻🔐
0 notes
Text
🔒 Why Keeper Security is the Best Password Manager for Your Organization 🔑
In today’s digital age, securing sensitive data is more important than ever, and Keeper Security makes it easier than ever to safeguard your organization’s passwords. Here's why it's the best choice for businesses:
Robust Security: Keeper uses AES-256 bit encryption and zero-knowledge architecture, ensuring your data stays private and secure, even if the system is compromised.
User-Friendly: Simple interface and seamless integrations across all devices, making it easy for employees to adopt.
Advanced Features: From secure password sharing to breach monitoring and dark web scanning, Keeper provides everything you need to stay ahead of potential threats.
Team Collaboration: Effortless password management for teams, with role-based permissions and secure access for all levels of your organization.
Compliance: Meets industry standards like GDPR, HIPAA, and SOC 2, ensuring your organization is always compliant.
Protect your business with Keeper Security and give your team the tools to stay safe online! 💻🔐
1 note
·
View note
Text
💾🚀 Experience Speed and Durability with SanDisk 4TB Extreme Portable SSD! 🚀💾
Take your storage to the next level with the SanDisk 4TB Extreme Portable SSD – perfect for work, travel, and everything in between.
✅ Blazing Fast Performance: Up to 1050MB/s read and 1000MB/s write speeds for seamless file transfers
✅ Rugged Durability: IP65 water and dust resistance with up to 3-meter drop protection
✅ Portable Design: Compact with a handy carabiner loop to secure to your backpack or belt loop
✅ Top-Tier Security: Protect your files with 256-bit AES hardware encryption and password protection
✅ Smart File Management: Use the SanDisk Memory Zone app to easily manage files and free up space
Whether for a laptop, desktop, or tablet, this SSD is the ultimate companion for your digital needs.
👉 Check it out here: https://amzn.to/4iKUE8x
#Tech #Gadgets #Innovation #DataStorage #PortableSSD #SanDisk #TechNews #Techie #TechTrends #DigitalStorage #HighSpeed #RuggedDesign #USBTypeC #ExternalSSD #TechGear #TechLife #TechCommunity #TechLovers #TechSavvy #TechProducts #Amazon #amazonfinds #AmazonDeals #amazonmusthaves #amazonprime #giftideas #gift
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] The Western DigitaI 2TB My Passpoɾt Portable Hard Disk Drive offers a sleek and compact design, perfect for on-the-go storage. Compatible with both Windows and Mac, it provides effortless plug-and-play functionality, no matter your system. With 2TB of storage, it’s ideal for backing up documents, photos, videos, and more. The drive includes Backup software for automatic backups and Security with password protection to safeguard your data. Its durable, lightweight build makes it easy to carry, while USB 3.0 connectivity ensures fast file transfers. A reliable solution for secure, portable storage needs. Automatic backup - Easy to use Password protection + 256-bit AES hardware encryption Western DigitaI Discovery software for Western DigitaI backup, password protection and drive management Superspeed USB 3.0 port; USB 2.0 compatible 3-Year manufacturer's limited warranty [ad_2]
0 notes
Text
Need best password manager? We have compiled a list of best password managers to help you choose from multiple options. Hacking has become an acute bane in today's life. What will happen? If all our important documents are nabbed and our privacy gets lost in the hands of cyber criminals. Many daring hacking techniques and powerful exploitation tools are replete in the cyber world. With several dozens of free hacking resource available online, anyone can be stealing your information in a blink. The browsers are not safe for storing your passwords either. Many vulnerability in browser password stores are exposed in recent past. Keeping your passwords very difficult to guess is a good way to protect your online information, however it gets painful to remember it. Key Things to Keep Your Password Secure Here are some key things to keep your password secure, most of the password managers support these features. Use a difficult to guess password with more than 8 characters and containing alphabets, numbers and special characters. Use different password for different websites. Keep changing your password frequently. At least once in 90 days. Do not provide your password of one website to another website. . Keeping a secure password is not easy. So what is the resolution? It's a Password Manager Software. Password manager software not only stores large collection of passwords but retrieves all our data in an encrypted manner; with one Master Password, we can access our accounts in a secure manner, it also provides us with additional features with which we can operate all our accounts in a conveniently. A few of the best ones are described below: Lastpass Lastpass is an award winning best password manager. It generally uses AES 256 bit encryption, with other advanced combinations. Lastpass supports a wide range of browsers and syncs easily with any device. It remembers all the passwords providing a centralized, cost effective free password management and ensures advanced security features. The concept of one master password is unique and any account can be accessed through it. It has been used worldwide and highly appreciated in software management reviews. Dashlane Here is the cream of the crop! One of the best password managers ever. Dashlane keeps track of all passwords and helps in auto login to any site. It is a free password manager, imports and secures the entire passwords in a protected vault. Master password is the only way which takes incredible care of our data. The data can only be decrypted by the original user and not even Dashlane. Dashlane also ensures the most accurate and agile way to auto-fill forms on the web and saves time. . Keepass Keepass is a free open source password manager. It helps us manage everything like passwords,files,confidential accounts in a highly secured way. Many features like autotype, multiple users key, Multilanguage support,strong random password generator, easy database transfer are unique. It is browser friendly as well. Keepass is a real random password generator,so you need not worry about any security or hacking problems. Password Box Password Box is an award winning free online password safe. It saves time with one tap login to different sites. It is encrypted with AES-256, locked with a Master Password, ensures auto lock function against theft, and uses optional pincode lock for additional security. Password Box is also a digital manager with a legacy locker and can be used in any advanced operating system. Moreover, it meets a real need as it is a reliable password storage software. It can be found in any online apps store. Password Genie Security Coverage was launched in 2003. The main application of these innovative software are Secure It; For Protection , File-Hopper; For Storage and Password Genie ; for secure and management purposes. Password Genie is a master password keeper which facilitates high protection. It specializes in Android app management, website security, password management, easy backup and support systems.
It is mainly a web based password manager and this password manager app can be installed and updated from any reliable online store as well. Roboform Roboform is the world’s top password keeper. It is an industry leading encryption technology which secures all files with a principle password and has auto form filler which helps in form fill up functions. Roboform is not only browser friendly but it is easy to use, fast and can be accessed from almost any platform. Keeper Vault Keeper Vault is a secure and easy to use password vault and digital vault. It ensures the highest level of data privacy to any device. For additional security, Keeper Vault integrates a two factor authentication using an advanced encryption technology. It costs $10 per device per year- but a free trial can be opted for the period of 30 days. The website also provides 24x7 support. Handy Password As the name suggests, Handy Password Manager automatically saves login of each website account you visit. The sofwtare employs a 128-bit encryption rather than 256-bit which is still very safe for the users. It is also comprised of a new password generator tool which will attempt to discover all the partially forgotten passwords; along with that it can create 'un-hackable' complex passwords. Handy Password Manager is also available in portable USB and PC versions. Though the company provides minimum support, but facilities like auto-fill and data backup is high convenient and user friendly. Agilebits Password Agilebits Password is convenient and simple. The 1 Password offers a productive and faster password retrieving approach available for all devices. It is a 21st century digital wallet which keeps vital information in a secured safe. Its equally compatible in every browser and has an auto-fill function. Agilebits also securely shares information with others and is up to date. Agilebits is truly one of the best secure password managers around. Passpack Passpack is one of the best online password manager for individuals and teams. This team password manager helps tag, search and manage multiple auto logins. The key features are collaboration (easy access of one's account by others in a secure manner) and host proofing. The advanced technology also provides awesome customer care service which is appreciated. Furthermore, the concept of password fatigue is almost vague when using Passpack. Password Wallet Password Wallet is a free web based password manager. It retrieves all banking, website, shopping and other login information protectively behind one master password. It works well in all sorts of browsers. Password Wallet simplifies your online life by featuring the password saving and accommodation facilities as well. This online password manager provides high security as well as provides customer support.To get started, you need to download the Password Wallet toolbar and see how user friendly it is. Splashid Splashid is a password safe for all browsers. It synchronizes with any form of data provided. Splashid uses one way encryption system to secure all files and documents and also ensures high firewall protection against theft. Splashid continuously innovates and provides updates for most recent platform versions too. It is well known for its customer support and is perfectly safe for online banking or any kind of secure transactions. Intuitive Password Intuitive Password is one of the world's best online password managers and secure data storages, according to several online password manager reviews. It uses the US government approved encryption algorithms and protects its user from the accidental data breaches.The reasons to opt for this manager are as follows: quick auto login, multi-factor authentication, secure sharing of passwords,highly secure, easy tagging features, easy password organization and compatibility. Furthermore it has a free trial plan. StickyPassword StickyPassword is among one of the flexible and top notch password managers with plenty of useful attributes.
The management tools and cloud integration are well adapted as well. StickyPassword Cloud runs as a standalone application and uses the concept of one master password. It also offers good online support. It's well integrated with all platforms too. Kaspersky Password Manager Kaspersky Password Manager generates strong passwords which protects your data and money against theft. Kaspersky offers secure storage, easy access and strong passwords, it's available in free and premium versions. Kaspersky is a digital wallet also with high synchronized technology which ensures complete safety. Simple sign-in and auto-fill features are supported too. Hitachi ID Password Hitachi ID Password manages credentials across multiple systems and applications, also ensures a secure login process. Hitachi Password offers several business challenges including call volumes help, compatibility for various users according to their needs, self service password reset; it reduces the volume and duration of IT support call. Many IT companies have chosen this user productive software which is not only ensuring security, but also providing high cost-effectiveness. Trendmicro Password Manager Trendmicro Password Manager provides compatible, protective and self service solutions. It increases our security line by reducing help desk errors, eliminating the need for multiple passwords and acting as a secured digital purse. It's user oriented and a highly relevant software. Apt for all operating systems, Trendmicro Password Manager uses highly encrypted algorithms to avoid hacking related problems. Team Password Manager Team Password Manager uses AES-256 & B crypt 2FA. Additional features like self hosted responsiveness, affordable price, and 'free for two users' are highly appreciated. It has got improved security, better organization of .txt documents and workflow are all present in this all in one app. Master password, auto-fill attributes are integrated too. Soft-O Free Password Manager Free Password Manager is essentially a freeware program which encrypts your passwords, retrieves forgotten access codes and passwords, stores credit card details and logins. It integrates AES algorithm and facilitates customable database folders. Moreover, Soft-O Free Password Manager can be installed on a USB flash drive. NeedMyPassword One way encryption of NeedMyPassword is a great security option which ensures unending protection to the user. The online password manager tool not only ensures online password storage, but also retrieves forgotten passwords. However it is a little bit pricey. User friendliness, user support system and unlimited storage are few of the key features. Moreover. it's compatible with most platforms. It is a multi device era so it is not uncommon to access one’s account from a PC, tablet or smartphone run by a different operating systems. Its also an increasingly insecure online world where every week brings news of fresh types of data breach. To overcome this crisis, an antivirus program or an operating system firewall is not sufficient. You require a good password manager software. Furthermore, a password protection software saves your time with the features such as auto fill and auto login. Which password manager do you use? Do you know of any open source team password manager or a self hosted password manager? Please share with us in comments. Article Updates Article Updated August 2021. HTTP Links changed to HTTPS. Minor text changes done. Validated article for relevance in 2021.
0 notes
Text
10 Best Cloud Storage Solutions (June 2024)
New Post has been published on https://thedigitalinsider.com/10-best-cloud-storage-solutions-june-2024/
10 Best Cloud Storage Solutions (June 2024)
pCloud is a secure cloud storage platform that offers a range of features for storing, syncing, and sharing files. Founded in 2013, pCloud has grown to serve over 14 million users worldwide. The company is based in Switzerland, a country known for its strong privacy laws, and maintains servers in both the United States and Europe.
One of the standout features of pCloud is its focus on security and privacy. The platform uses 256-bit AES encryption for files at rest and TLS/SSL encryption for data in transit. pCloud also offers an optional feature called pCloud Crypto, which provides client-side, zero-knowledge encryption for an additional layer of security. With pCloud Crypto, files are encrypted on the user’s device before being uploaded to the cloud, ensuring that no one, not even pCloud employees, can access the data without the user’s encryption key.
pCloud provides a user-friendly interface for managing files and folders, with desktop apps available for Windows, Mac, and Linux, as well as mobile apps for iOS and Android. The platform offers a range of features designed to enhance productivity and collaboration, including file versioning, which allows users to access previous versions of their files, and file sharing with customizable download and upload links. pCloud also provides a unique feature called pCloud Drive, which enables users to access their cloud storage as a virtual drive on their computer, making it easy to manage files without taking up local storage space.
Secure cloud storage with 256-bit AES encryption and optional client-side encryption (pCloud Crypto)
File versioning and recovery, with up to 30 days of version history (or up to 360 days for extended file history)
pCloud Drive feature for accessing cloud storage as a virtual drive on your computer
Customizable file sharing with download and upload links, as well as password protection and expiration dates
Generous storage plans, including 10GB of free storage and paid plans ranging from 500GB to 2TB, with lifetime payment options available
Dropbox is a widely used cloud storage and file-sharing platform that has been simplifying digital file management since its launch in 2007. With over 700 million registered users, Dropbox has become a go-to solution for individuals, teams, and businesses looking to store, sync, and collaborate on files in the cloud.
One of the key strengths of Dropbox is its ease of use. The platform offers a simple, intuitive interface that makes it easy for users to upload, organize, and access their files from anywhere, on any device. Dropbox automatically syncs files across all connected devices, ensuring that users always have access to the most up-to-date versions of their files. The platform also offers a range of collaboration features, including the ability to share files and folders with others, leave comments, and work together in real time on Microsoft Office files with Dropbox Paper.
Dropbox places a strong emphasis on security, using 256-bit AES encryption for files at rest and SSL/TLS encryption for data in transit. The platform also offers two-factor authentication and remote device wipe to help users protect their accounts and data. Dropbox provides a range of storage plans to suit different needs, including a free plan with 2GB of storage and paid plans ranging from 2TB to unlimited storage for teams. The platform integrates with a wide range of third-party apps and services, including productivity tools, creative software, and security solutions, making it a versatile choice for many users.
Key features of Dropbox:
Easy file syncing and automatic updates across all connected devices
Collaboration tools, including file sharing, commenting, and real-time co-authoring with Dropbox Paper
Secure storage with 256-bit AES and SSL/TLS encryption, two-factor authentication, and remote device wipe
Integration with a wide range of third-party apps and services, including Microsoft Office and Adobe Creative Cloud
Version history and file recovery, with 30 days of version history (or 180 days for Dropbox Business users)
MEGA is a secure cloud storage platform founded in 2013 by Kim Dotcom, offering end-to-end encryption and a focus on user privacy. Based in New Zealand, MEGA provides free and paid storage plans, with features like secure file sharing, chat, and file versioning.
One of MEGA’s standout features is its zero-knowledge encryption. All files are encrypted client-side before being uploaded, meaning that MEGA does not have access to the encryption keys and cannot view the content of stored files. This ensures a high level of privacy and security for users. MEGA is also transparent about its security practices, publishing its source code and design processes for public review.
MEGA offers a generous free plan with 20GB of storage, as well as paid plans ranging from 400GB to 16TB. The platform has a user-friendly interface with cross-platform support, including desktop apps for Windows, macOS, and Linux, as well as mobile apps for iOS and Android. MEGA also provides browser extensions and a command-line interface for advanced users.
Key features of MEGA:
Zero-knowledge, end-to-end encryption ensuring user privacy and security
Generous free plan with 20GB of storage and paid plans up to 16TB
Secure file sharing with customizable permissions, link expiry dates, and password protection
Cross-platform support with desktop, mobile, and web-based access
File versioning and recovery features to protect against data loss and ransomware attacks
Microsoft OneDrive is a cloud storage and file-sharing platform that is integrated with Microsoft 365 (formerly Office 365) and Windows 10. Launched in 2007, OneDrive has become a popular choice for both personal and business users, offering seamless integration with Microsoft’s suite of productivity apps, including Word, Excel, and PowerPoint.
One of the key advantages of OneDrive is its deep integration with Microsoft products. Users can easily save, access, and share files directly from within Microsoft Office apps, making it a convenient choice for those already using Microsoft tools. OneDrive also offers automatic syncing across devices, ensuring that users always have access to the most up-to-date versions of their files. The platform provides a range of collaboration features, such as real-time co-authoring, commenting, and file sharing with customizable permissions.
OneDrive offers a variety of storage plans, including a free plan with 5GB of storage and paid plans ranging from 100GB to 6TB. For business users, OneDrive is included with Microsoft 365 subscriptions, providing 1TB of storage per user and additional features like advanced security and compliance tools. OneDrive also offers robust security features, including encryption at rest and in transit, multi-factor authentication, and ransomware detection and recovery.
Key features of Microsoft OneDrive:
Seamless integration with Microsoft 365 apps, including Word, Excel, and PowerPoint
Automatic syncing and real-time collaboration features, such as co-authoring and commenting
Secure file sharing with customizable permissions and expiration dates
Robust security features, including encryption, multi-factor authentication, and ransomware protection
Personal Vault feature for an added layer of security for sensitive files
Box is a cloud content management and file-sharing platform designed for businesses of all sizes. Founded in 2005, Box has become a leading choice for organizations looking to securely store, manage, and collaborate on their files in the cloud. The platform offers a range of features and integrations that cater to the needs of modern businesses, including workflow automation, data governance, and enterprise-grade security.
One of the standout features Box is its focus on security and compliance. The platform provides a range of security controls, including encryption, data loss prevention (DLP), and access management, to help businesses protect their sensitive data. Box also complies with various industry regulations, such as HIPAA, FINRA, and GDPR, making it a suitable choice for organizations in regulated industries. Additionally, Box offers advanced collaboration features, such as real-time co-authoring, task management, and granular permissions, enabling teams to work together seamlessly and securely.
Box integrates with over 1,500 third-party apps, including popular productivity tools like Microsoft Office 365 and Google Workspace, as well as enterprise software like Salesforce and DocuSign. This extensive integration ecosystem allows businesses to streamline their workflows and improve productivity. Box also provides a range of AI and machine learning capabilities, such as intelligent content classification and automated workflows, to help organizations manage and extract value from their content.
Key features of Box:
Enterprise-grade security and compliance, with features like encryption, DLP, and access controls
Advanced collaboration tools, including real-time co-authoring, task management, and granular permissions
Extensive integration with over 1,500 third-party apps, including Microsoft Office 365, Google Workspace, and Salesforce
AI and machine learning capabilities for intelligent content management and workflow automation
Secure file sharing and content management, with features like custom branding, expiration dates, and password protection
Icedrive is a next-generation cloud storage platform that aims to make cloud storage feel like a physical hard drive. Launched in 2019, Icedrive offers a sleek, modern interface and a unique approach to file management with its revolutionary drive-mounting software. The platform focuses on providing a secure, easy-to-use, and affordable cloud storage solution for individuals and businesses.
One of the standout features of Icedrive is its emphasis on security. The platform uses the Twofish encryption algorithm, which is considered one of the most secure encryption methods available. Icedrive also offers client-side encryption for paid subscribers, ensuring that data is encrypted on the user’s device before being transferred to the cloud. Additionally, Icedrive follows a zero-knowledge approach, meaning that only the user can view and decrypt their data.
Icedrive offers a range of apps for various platforms, including web, desktop (Windows, macOS, and Linux), and mobile (iOS and Android). The platform’s clean and intuitive interface makes it easy for users to access, manage, and update their cloud storage. Icedrive also provides a generous free plan with 10GB of storage, as well as affordable paid plans ranging from 150GB to 5TB.
Key features of Icedrive:
Twofish encryption algorithm and client-side encryption for enhanced security
Virtual drive feature that allows users to access cloud storage as a physical hard drive (currently Windows-only)
Clean, modern, and easy-to-use interface across web, desktop, and mobile apps
Generous free plan with 10GB of storage and affordable paid plans
Built-in document viewer and media player for productivity and streaming on-the-go
IDrive is a comprehensive cloud storage and backup solution designed for individuals and businesses. Founded in 1995, IDrive offers a unique combination of cloud backup, cloud storage, and file syncing capabilities, making it a versatile choice for users looking to protect and access their data from anywhere.
One of the standout features of IDrive is its support for unlimited devices. Users can back up data from multiple computers, smartphones, and tablets, as well as external hard drives and NAS devices, all under a single account. IDrive also offers a range of backup options, including scheduled backups, continuous data protection, and block-level incremental backups, ensuring that data is always up-to-date and protected against loss or damage.
In addition to its robust backup capabilities, IDrive provides cloud storage and file syncing features through its Cloud Drive. Files and folders stored in the Cloud Drive are synced in real-time across all linked devices, making it easy to access and collaborate on files from anywhere. IDrive also offers advanced security features, including 256-bit AES encryption, optional private key encryption, and two-factor authentication, ensuring that data remains secure both in transit and at rest.
Key features of IDrive:
Back up unlimited PCs, Macs, iPhones, iPads, and Android devices to a single account
Quickly back up or retrieve large amounts of data using a physical storage device, without using bandwidth
Protect against ransomware and accidental deletions with historical data views and up to 30 previous versions of files
Automatically back up modified parts of files in real-time
256-bit AES encryption, optional private key encryption, and two-factor authentication
The Importance of Cloud Storage
As data technology continues to evolve, cloud storage providers will undoubtedly adapt and innovate to meet the growing demands for security, privacy, and convenience. By understanding your specific needs and priorities, you can select the best cloud storage solution to protect your data, streamline your workflows, and collaborate seamlessly with others. Whether you prioritize encryption, ease of use, or integration with other tools, one of these providers is sure to meet your requirements and exceed your expectations.
#2024#access management#Accounts#adobe#ai#algorithm#android#approach#apps#authentication#automatic updates#automation#back up#backup#backup solution#backups#Best Of#Blog#box#Branding#browser#browser extensions#Business#client-side encryption#Cloud#cloud backup#cloud storage#code#collaborate#Collaboration
0 notes
Text
Cloud SQL Auth Proxy: Securing Your Cloud SQL Instances

Cloud SQL Auth Proxy
In this blog they will explain how to utilise the Cloud SQL Auth Proxy to create safe, encrypted data, and authorised connections to your instances. To connect to Cloud SQL from the App Engine standard environment or App Engine flexible environment, you do not need to configure SSL or use the Cloud SQL Auth Proxy.
The Cloud SQL Auth Proxy’s advantages
Without requiring authorised networks or SSL configuration, the Cloud SQL Auth Proxy is a Cloud SQL connection that offers secure access to your instances.
The following are some advantages of the Cloud SQL Auth Proxy and other Cloud SQL Connectors:
Secure connections:
TLS 1.3 with a 256-bit AES cypher is automatically used by this to encrypt traffic to and from the database. You won’t need to administer SSL certificates because they are used to validate the identities of clients and servers and are not dependent on database protocols.
Simpler authorization of connections:
IAM permissions are used by the Cloud SQL Auth Proxy to restrict who and what can connect to your Cloud SQL instances. Therefore, there is no need to supply static IP addresses because it manages authentication with Cloud SQL.
It depends on the IP connectivity that already exists; it does not offer a new way for connecting. The Cloud SQL Auth Proxy needs to be on a resource that has access to the same VPC network as the Cloud SQL instance in order to connect to it via private IP.
The operation of the Cloud SQL Auth Proxy
A local client that is operating in the local environment is required for the Cloud SQL Auth Proxy to function. Your application uses the common database protocol that your database uses to connect with the Cloud SQL Auth Proxy.
It communicates with its server-side partner process through a secure channel. One connection to the Cloud SQL instance is made for each connection made via the Cloud SQL Auth Proxy.
An application that connects to Cloud SQL Auth Proxy first determines if it can establish a connection to the target Cloud SQL instance. In the event that a connection is not established, it makes use of the Cloud SQL Admin APIs to acquire an ephemeral SSL certificate and connects to Cloud SQL using it. The expiration date of ephemeral SSL certificates is around one hour. These certificates are refreshed by Cloud SQL Auth Proxy prior to their expiration.
The only port on which the Cloud SQL Auth Proxy establishes outgoing or egress connections to your Cloud SQL instance is 3307. All egress TCP connections on port 443 must be permitted since Cloud SQL Auth Proxy uses the domain name sqladmin.googleapis.com to use APIs, which does not have a stable IP address. Make that your client computer’s outbound firewall policy permits outgoing connections to port 3307 on the IP address of your Cloud SQL instance.
Although it doesn’t offer connection pooling, it can be used in conjunction with other connection pools to boost productivity.
The connection between Cloud SQL Auth Proxy and Cloud SQL is depicted in the following diagram:
image credit to Google cloud
Use of the Cloud SQL Auth Proxy Requirements
The following conditions must be fulfilled in order for you to use the Cloud SQL Auth Proxy:
Enabling the Cloud SQL Admin API is necessary.
It is necessary to supply Google Cloud authentication credentials to this.
You need to supply a working database user account and password to this proxy.
The instance needs to be set up to use private IP or have a public IPv4 address.
It is not necessary for the public IP address to be added as an approved network address, nor does it need to be reachable from any external address.
Options for starting Cloud SQL Auth Proxy
You give the following details when you launch it:
Which Cloud SQL instances to connect to so that it can wait to receive data from your application that is sent to Cloud SQL
Where can it locate the login credentials needed to validate your application with Cloud SQL?
Which type of IP address to use, if necessary.
Whether it will listen on a TCP port or a Unix socket depends on the startup parameters you supply. It creates the socket at the specified location, which is often the /cloudsql/ directory, if it is listening on a Unix socket. The Cloud SQL Auth Proxy by default listens on localhost for TCP.
For authentication, use a service account
To authorise your connections to a Cloud SQL instance, you must authenticate as a Cloud SQL IAM identity using this Proxy.
For this purpose, the benefit of using a service account is that you may make a credential file particularly for the Cloud SQL Auth Proxy, and as long as it approach for production instances that aren’t operating on a Compute Engine instance is to use a service account
In the event that you require this to be invoked from several computers, you can replicate the credential file within a system image.
You have to make and maintain the credential file in order to use this method. The service account can only be created by users who possess the resourcemanager.projects.setIamPolicy permission, which includes project owners. You will need to get someone else to create the service account or find another way to authenticate this, if your Google Cloud user does not have this permission.
Read more on govindhtech.com
#cloudSQL#vpcnetwork#IPAddress#firewallpolicy#GoogleCloud#news#TechNews#technology#technologynews#technologytrends#govindhtech
0 notes
Text
The Importance of Two-Factor Authentication for iOS Users
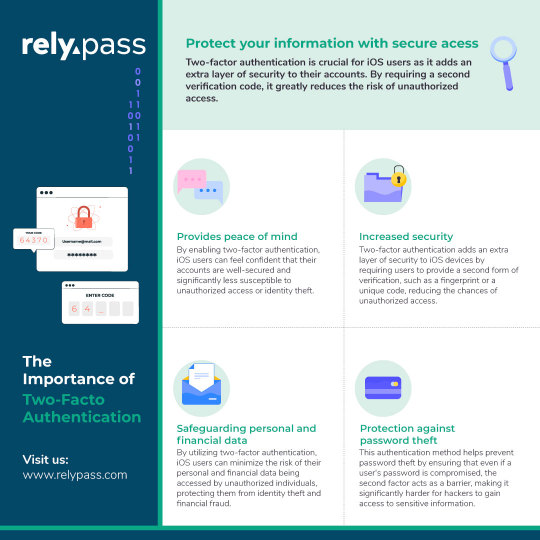
Step up your security game with two-factor authentication for iOS users! 🛡️ Add an extra layer of protection, minimize the risk of unauthorized access, safeguard your personal and financial data, and enjoy peace of mind.
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Password manager with AES 256-bit encryption#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] My Book desktop storage is ready to use out of the box so you can start transferring files, saving your memories and backing up right away. It comes with all the software you need to help protect your data, including Backup and Security software and is compatible with Time Machine Digital Storage Capacity: 12TB Form Factor: 3.5-inch | SuperSpeed USB 3.0 port |USB 2.0 compatible| Material: Plastic Formatted NTFS and compatible with Windows | Can be reformatted for Mac or other operating systems. Software for device management and automatic backup with password protection- 256-bit AES hardware encryption Warranty: 3 Year Warranty [ad_2]
0 notes
Text
will vpn protect you on public wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
will vpn protect you on public wifi
VPN encryption on public WiFi
Using a Virtual Private Network (VPN) on public WiFi networks is crucial for safeguarding sensitive information from cyber threats. Public WiFi hotspots, found in places like cafes, airports, and hotels, are convenient but inherently insecure, making users vulnerable to various forms of cyber attacks such as hacking, snooping, and data theft.
VPN encryption works by creating a secure, encrypted tunnel between the user's device and the VPN server. This encryption ensures that all data transmitted between the device and the server remains confidential and cannot be intercepted by malicious third parties. Even if a hacker manages to intercept the data, they would only see encrypted gibberish, rendering it useless without the decryption key.
Without a VPN, any data sent over a public WiFi network is essentially broadcasted in plain text, making it easy for hackers to intercept and exploit. This puts users at risk of identity theft, financial fraud, and privacy breaches. By using a VPN, however, users can protect their sensitive information, including passwords, credit card details, and personal communications, from prying eyes.
When selecting a VPN provider, it's important to choose one that offers strong encryption protocols such as AES (Advanced Encryption Standard) with 256-bit keys, which is considered virtually unbreakable even by the most sophisticated adversaries. Additionally, users should opt for VPNs that have a strict no-logs policy, ensuring that their online activities remain private and anonymous.
In conclusion, using a VPN with robust encryption on public WiFi networks is essential for maintaining online security and privacy. By encrypting data transmitted over these insecure networks, VPNs provide users with peace of mind and protection against cyber threats.
Cybersecurity risks on public WiFi
Title: Understanding the Cybersecurity Risks Associated with Public WiFi
In our interconnected world, public WiFi networks have become ubiquitous, offering convenience and accessibility. However, while they provide easy access to the internet, they also present significant cybersecurity risks. Whether you're sipping coffee at a café or waiting at an airport, connecting to public WiFi without proper precautions can expose you to various threats.
One of the primary risks of using public WiFi is the potential for data interception. Since these networks are often unsecured or have weak encryption protocols, cybercriminals can easily intercept the data transmitted between your device and the WiFi hotspot. This means that sensitive information such as login credentials, credit card numbers, and personal messages could be intercepted and exploited by malicious actors.
Moreover, public WiFi networks are frequently targeted by hackers who set up fake hotspots, known as "evil twin" networks. Unsuspecting users may inadvertently connect to these rogue networks, thinking they are legitimate, only to have their data stolen. These fake hotspots can mimic the names and appearances of genuine networks, making them difficult to detect without proper security measures in place.
Another common threat associated with public WiFi is malware distribution. Cybercriminals may inject malware into commonly accessed websites or distribute malicious files through the network itself. Once your device is infected, malware can steal sensitive information, track your online activities, or even take control of your device without your knowledge.
To mitigate the risks of using public WiFi, it's essential to take proactive measures. Use a virtual private network (VPN) to encrypt your internet traffic and protect your data from interception. Avoid accessing sensitive information, such as online banking or personal emails, while connected to public WiFi. Additionally, keep your device's software and security patches up to date to minimize vulnerabilities.
By understanding the potential cybersecurity risks associated with public WiFi and implementing necessary precautions, you can enjoy the convenience of staying connected while safeguarding your personal information and sensitive data.
VPN tunneling for public WiFi protection
Using a VPN for tunneling is crucial when connecting to public WiFi networks to ensure your online security and privacy are maintained. Public WiFi networks, such as those in cafes, airports, and hotels, are notorious for their lack of security measures, making them prime targets for cybercriminals to intercept sensitive information. By establishing a VPN tunnel, your data is encrypted, making it nearly impossible for hackers to access your online activities.
VPN tunneling works by creating a secure and encrypted connection between your device and a remote server operated by the VPN service provider. This tunnel acts as a shield, protecting your data from being intercepted by malicious third parties while browsing the internet on public WiFi networks. Additionally, VPN tunneling allows you to mask your IP address, further enhancing your anonymity and online privacy.
When selecting a VPN service for public WiFi protection, it is essential to choose a reputable provider that offers advanced encryption protocols and a strict no-logs policy. Opt for a VPN service that offers a kill switch feature, which automatically shuts down your internet connection if the VPN connection drops, preventing any data leaks.
In conclusion, VPN tunneling is a critical tool for safeguarding your sensitive information when using public WiFi networks. By encrypting your data and providing a secure connection, VPNs offer peace of mind and ensure your online activities remain private and secure, even on unsecured public WiFi networks.
Data privacy on public WiFi networks
When you're out and about, public WiFi networks can be a convenient way to stay connected on the go. However, it's important to be cautious about the security risks these networks pose, particularly when it comes to data privacy.
Public WiFi networks are generally unsecured, meaning that any data you transmit over these networks can potentially be intercepted by cybercriminals. This can include anything from your login credentials for websites and apps to sensitive personal information.
To help protect your data privacy on public WiFi networks, there are a few key steps you can take. First and foremost, avoid accessing sensitive information such as online banking or entering your credit card details while connected to public WiFi. If you absolutely must access these types of accounts while out and about, consider using a virtual private network (VPN) to encrypt your data and add an extra layer of security.
It's also a good idea to make sure your device's software is up to date, as updates often include security patches that can help protect your data. Additionally, be cautious about connecting to unfamiliar networks and consider asking staff at businesses for information about their WiFi network to ensure it's legitimate.
By taking these steps and staying vigilant about your data privacy, you can enjoy the convenience of public WiFi networks without putting your personal information at risk.
VPN protocols for secure public WiFi browsing
When it comes to browsing the internet on public WiFi networks, security should be a top priority. Using a VPN (Virtual Private Network) is essential for ensuring your online activities remain private and secure. However, not all VPN protocols are created equal, and choosing the right one can make a significant difference in your browsing experience.
There are several VPN protocols available, each with its own strengths and weaknesses. Some of the most common protocols include OpenVPN, L2TP/IPsec, IKEv2, and WireGuard. OpenVPN is widely regarded as one of the most secure and versatile protocols, offering strong encryption and excellent performance across different devices. L2TP/IPsec is another popular choice known for its stability and compatibility with a wide range of platforms.
IKEv2 is favored for its speed and reliability, making it an excellent option for mobile users who frequently switch between different networks. WireGuard is a newer protocol that boasts faster speeds and improved security features compared to traditional protocols.
When connecting to public WiFi networks, it is recommended to use protocols like OpenVPN or IKEv2 for optimal security and performance. These protocols provide robust encryption to safeguard your data from potential threats such as hackers or cybercriminals lurking on the same network.
Overall, selecting the right VPN protocol for secure public WiFi browsing is crucial in ensuring your online safety and privacy. By choosing a reliable protocol and utilizing a VPN service, you can browse the internet with peace of mind, knowing that your sensitive information is protected.
0 notes
Text
From Frustration to Freedom How Our Mobile App Simplifies Password Management

📣📱 Calling all iOS users! Tired of the password chaos? Discover the ultimate solution now on our blog. 🔐💡 Take control of your passwords with RelyPass - the simple and secure password management app! Don't miss out, check it out today!
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Password manager with AES 256-bit encryption#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
what type of vpn is pulse secure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what type of vpn is pulse secure
Pulse Secure VPN encryption protocols
Pulse Secure VPN is renowned for its robust encryption protocols, ensuring secure and private data transmission for users. The VPN employs a variety of encryption algorithms to safeguard sensitive information against unauthorized access and interception.
One of the primary encryption protocols utilized by Pulse Secure VPN is the Advanced Encryption Standard (AES). AES is a symmetric encryption algorithm that has been adopted by governments and organizations worldwide due to its exceptional security and efficiency. Pulse Secure VPN typically implements AES with 256-bit keys, which provides a high level of protection against brute-force attacks and cryptographic vulnerabilities.
In addition to AES, Pulse Secure VPN also supports other encryption protocols such as Secure Socket Layer (SSL) and Transport Layer Security (TLS). SSL and TLS are cryptographic protocols that establish a secure connection between the user's device and the VPN server, preventing eavesdropping and data tampering during transit. These protocols employ asymmetric encryption techniques, utilizing public and private keys to authenticate and encrypt data exchanges.
Furthermore, Pulse Secure VPN incorporates Perfect Forward Secrecy (PFS) into its encryption mechanisms. PFS ensures that each session key is unique and independent, preventing the compromise of past sessions even if current keys are compromised. This enhances the overall security of communications and mitigates the risk of data breaches.
Overall, Pulse Secure VPN's encryption protocols provide users with peace of mind knowing that their online activities are shielded from prying eyes and malicious actors. By leveraging cutting-edge encryption technologies like AES, SSL/TLS, and PFS, Pulse Secure VPN maintains a secure and private environment for users to browse the internet, access sensitive information, and communicate confidentially.
Pulse Secure VPN authentication methods
Pulse Secure VPN offers various authentication methods to ensure secure access to network resources for users. These authentication methods are designed to provide flexibility and robust security, catering to the diverse needs of organizations and their users.
One of the primary authentication methods offered by Pulse Secure VPN is username/password authentication. This traditional method requires users to input their unique username and password combination to authenticate themselves before gaining access to the VPN. While simple and familiar, it may not provide the highest level of security on its own.
For enhanced security, Pulse Secure VPN supports multi-factor authentication (MFA). MFA combines two or more independent authentication factors to verify the identity of a user. These factors typically include something the user knows (like a password), something the user has (like a mobile device or security token), and something the user is (like a fingerprint or other biometric data). By requiring multiple forms of authentication, MFA significantly strengthens the security of VPN access and reduces the risk of unauthorized access.
Furthermore, Pulse Secure VPN also integrates with various third-party authentication systems, such as RADIUS (Remote Authentication Dial-In User Service) and LDAP (Lightweight Directory Access Protocol). This integration enables organizations to leverage their existing authentication infrastructure seamlessly within the VPN environment, streamlining user management and ensuring consistency across systems.
In addition to these authentication methods, Pulse Secure VPN offers advanced features like single sign-on (SSO), which allows users to access multiple applications with a single set of credentials, further enhancing user convenience without compromising security.
Overall, Pulse Secure VPN provides a comprehensive range of authentication methods to meet the security and usability needs of modern organizations, enabling secure remote access to network resources from anywhere, at any time.
Pulse Secure VPN deployment options
Pulse Secure VPN offers a versatile array of deployment options to meet the diverse needs of businesses and organizations. Whether it's ensuring secure remote access for employees or facilitating seamless connectivity across multiple locations, Pulse Secure VPN provides flexible solutions tailored to specific requirements.
One of the primary deployment options offered by Pulse Secure VPN is the on-premises deployment model. With this approach, organizations can deploy the VPN solution within their own data centers or private cloud environments. This provides complete control over the infrastructure and allows for customization to align with security policies and compliance requirements. On-premises deployment is particularly suitable for organizations that prioritize data sovereignty and have stringent regulatory obligations.
Alternatively, Pulse Secure VPN offers a cloud-based deployment model, which leverages the scalability and convenience of the cloud. With this option, organizations can quickly deploy and scale their VPN infrastructure without the need for extensive hardware investments or maintenance. Cloud-based deployment is ideal for businesses looking to rapidly adapt to changing demands, as it offers flexibility, agility, and reduced operational overhead.
Furthermore, Pulse Secure VPN supports hybrid deployment scenarios, allowing organizations to seamlessly integrate on-premises and cloud-based components. This hybrid approach enables businesses to leverage the benefits of both deployment models, optimizing performance, scalability, and cost-efficiency.
In summary, Pulse Secure VPN offers a range of deployment options, including on-premises, cloud-based, and hybrid models, to accommodate the diverse needs of modern enterprises. Whether it's ensuring secure access for remote workers or facilitating seamless connectivity across distributed environments, Pulse Secure VPN delivers reliable solutions tailored to meet the evolving demands of today's digital landscape.
Pulse Secure VPN compatibility
Pulse Secure VPN is renowned for its compatibility across various devices and platforms, making it a top choice for individuals and businesses seeking reliable and secure virtual private network solutions. Whether you're using Windows, macOS, Linux, iOS, or Android, Pulse Secure VPN ensures seamless integration and consistent performance.
For Windows users, Pulse Secure VPN offers robust compatibility with all recent versions of the operating system, including Windows 10, ensuring that users can enjoy secure and encrypted connections without any compatibility issues.
Mac users also benefit from Pulse Secure VPN's compatibility, with support for macOS versions such as Catalina and Big Sur. This means that whether you're working on a MacBook, iMac, or Mac mini, you can easily install and configure Pulse Secure VPN to safeguard your online activities.
Linux enthusiasts will appreciate Pulse Secure VPN's compatibility with popular distributions like Ubuntu, Fedora, and CentOS. With Pulse Secure VPN, Linux users can enjoy the same level of security and privacy as users on other platforms.
Mobile users are not left out either, as Pulse Secure VPN offers dedicated apps for both iOS and Android devices. Whether you're using an iPhone, iPad, Android smartphone, or tablet, you can download the Pulse Secure VPN app from the respective app stores and connect to the VPN with just a few taps.
Moreover, Pulse Secure VPN is also compatible with various routers, allowing users to protect all devices connected to their home or office network. This ensures that every device, from laptops to smart TVs and gaming consoles, can benefit from the security and privacy features of Pulse Secure VPN.
In conclusion, Pulse Secure VPN's wide compatibility across different devices and platforms makes it a versatile and reliable choice for users seeking enhanced online security and privacy.
Pulse Secure VPN performance benchmarks
Title: Evaluating Pulse Secure VPN Performance: A Comprehensive Benchmark Analysis
As businesses increasingly rely on virtual private networks (VPNs) for secure remote access, evaluating the performance of different VPN solutions becomes crucial. Pulse Secure VPN stands out as a prominent player in the market, offering robust security features and ease of use. However, to make an informed decision about adopting Pulse Secure VPN, it's essential to assess its performance through comprehensive benchmarks.
One of the key metrics in VPN performance evaluation is throughput, which measures the amount of data transferred over the network within a given time frame. Benchmarks reveal that Pulse Secure VPN consistently delivers impressive throughput rates, ensuring smooth and uninterrupted data transmission for users across various applications.
Latency is another critical factor affecting user experience, especially in real-time communication and latency-sensitive applications. Pulse Secure VPN excels in minimizing latency, providing responsive and seamless connectivity even for latency-sensitive tasks such as VoIP calls and video conferencing.
Moreover, Pulse Secure VPN demonstrates remarkable stability and reliability in stress tests, maintaining consistent performance levels even under heavy network traffic loads. This reliability is essential for ensuring uninterrupted access to resources and applications, particularly in dynamic work environments.
In addition to performance metrics, security is paramount when evaluating VPN solutions. Pulse Secure VPN offers advanced encryption protocols and multi-factor authentication options, ensuring data confidentiality and integrity while mitigating the risk of unauthorized access.
Overall, benchmark analysis confirms that Pulse Secure VPN delivers exceptional performance, reliability, and security, making it a compelling choice for organizations seeking a robust remote access solution. By prioritizing performance benchmarks in the evaluation process, businesses can make informed decisions to meet their specific connectivity needs while maintaining high standards of security and performance.
0 notes
Text
can wifi see what you search with vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can wifi see what you search with vpn
VPN encryption
VPN encryption is a crucial aspect of maintaining online privacy and security in today's digital world. VPN, short for Virtual Private Network, works by creating a secure and encrypted connection between the user's device and the internet.
Encryption plays a vital role in VPN technology as it scrambles the data being transmitted, making it unreadable to any potential hackers or cybercriminals. This ensures that sensitive information such as passwords, financial data, and personal messages remain protected.
There are different encryption protocols used by VPN providers, with the most common ones being OpenVPN, L2TP/IPsec, and IKEv2/IPsec. Each protocol comes with its own level of security and speed, allowing users to choose the one that best suits their needs.
When selecting a VPN provider, it's important to consider the encryption strength offered. The industry standard is AES (Advanced Encryption Standard) with 256-bit keys, known for its high level of security. Additionally, VPN providers may offer features like Perfect Forward Secrecy (PFS) which generates a new encryption key for each session, further enhancing security.
Overall, VPN encryption is essential for safeguarding your online activities from prying eyes. By using a reputable VPN service with strong encryption protocols, you can browse the internet with peace of mind knowing that your data is secure and protected.
WiFi monitoring
WiFi monitoring is a crucial aspect of managing and optimizing your wireless network performance. By monitoring your WiFi network, you can ensure smooth connectivity, identify potential issues, and take necessary actions to improve your network efficiency.
One of the key benefits of WiFi monitoring is the ability to track network performance in real-time. This means that you can identify any disruptions or slow-downs in your network and address them promptly to minimize downtime and ensure seamless connectivity for your users.
Additionally, WiFi monitoring allows you to analyze network utilization, identify bandwidth-hungry applications or devices, and optimize your network resources. By tracking data usage patterns, you can ensure that your network resources are efficiently allocated, preventing bottlenecks and slowdowns during peak usage times.
Moreover, monitoring your WiFi network can help you identify potential security threats or unauthorized access attempts. By keeping a close eye on network traffic and activities, you can detect any suspicious behavior and take immediate action to protect your network from cyber threats.
In conclusion, WiFi monitoring is essential for ensuring the optimal performance, security, and reliability of your wireless network. By proactively monitoring your WiFi network, you can detect issues early, optimize network resources, and enhance overall user experience. Be sure to invest in robust WiFi monitoring tools to keep your network running smoothly and securely at all times.
Internet privacy
Internet privacy is a fundamental concern in this digital age, where almost everything we do online leaves a footprint. It refers to the level of privacy individuals have when it comes to storing, transmitting, and utilizing data via the internet. As technology advances, the need to safeguard our personal information has become more critical than ever.
One of the main issues surrounding internet privacy is data breaches. Hackers and cybercriminals are constantly finding ways to exploit vulnerabilities in online security systems to gain unauthorized access to sensitive information. This can lead to identity theft, financial fraud, and other forms of cybercrimes.
Moreover, online tracking and targeted advertising raise concerns about our privacy online. Companies use cookies and other tracking technologies to monitor our online behavior and gather data for targeted advertising. While this can result in a more personalized online experience, it also raises questions about the extent of data collection and its potential misuse.
Protecting your internet privacy involves taking proactive measures, such as using strong, unique passwords, enabling two-factor authentication, being cautious of the information you share online, and using virtual private networks (VPNs) for secure browsing.
Ultimately, internet privacy is a shared responsibility between individuals, service providers, and policymakers. By raising awareness about the importance of privacy online and implementing robust security measures, we can create a safer and more secure digital environment for everyone.
Data encryption
Title: Understanding the Importance of Data Encryption
In an age where digital information is the lifeblood of businesses and individuals alike, the need for robust data encryption has never been more critical. Data encryption is the process of encoding information in such a way that only authorized parties can access it. This vital security measure protects sensitive data from unauthorized access, ensuring confidentiality and integrity.
One of the primary reasons for implementing data encryption is to safeguard against potential cyber threats. With the proliferation of sophisticated hacking techniques, cybercriminals are constantly on the lookout for vulnerabilities to exploit. By encrypting data, even if unauthorized individuals manage to intercept it, they would be unable to decipher its contents without the encryption key.
Moreover, data encryption is essential for regulatory compliance. Many industries, such as finance, healthcare, and government, are subject to strict data protection regulations. Failure to comply with these regulations can result in severe consequences, including hefty fines and damage to reputation. Encrypting sensitive data helps organizations meet compliance requirements and mitigate risks associated with data breaches.
Furthermore, data encryption fosters trust among stakeholders. Whether it's customers entrusting their personal information to a company or employees sharing confidential data within an organization, encryption assures them that their data is being handled securely. This, in turn, enhances reputation and credibility, ultimately contributing to long-term success.
In conclusion, data encryption is a cornerstone of modern cybersecurity strategies. By implementing robust encryption protocols, organizations can protect sensitive information, comply with regulations, and build trust with stakeholders. In today's digital landscape, prioritizing data encryption is not just a best practice—it's a necessity.
Online anonymity
In the digital age, online anonymity has become both a shield and a sword, offering protection and empowerment to users while also presenting challenges and ethical dilemmas. At its core, online anonymity refers to the ability of individuals to conceal their identities when interacting on the internet.
One of the primary benefits of online anonymity is the freedom it affords individuals to express themselves without fear of repercussions. This can be particularly important in repressive regimes where speaking out against the government or other powerful entities can lead to severe consequences. By hiding their identities, individuals can engage in political dissent, whistleblowing, or seeking support for sensitive issues without risking their safety or livelihoods.
Moreover, online anonymity can foster a sense of community and support among marginalized or vulnerable groups. People struggling with stigmatized conditions such as mental illness or addiction may find solace in online forums where they can share their experiences anonymously and receive understanding and encouragement from others facing similar challenges.
However, online anonymity also has its drawbacks. It can enable cyberbullying, harassment, and other forms of antisocial behavior by providing perpetrators with a cloak of invisibility. Without being held accountable for their actions, some individuals may engage in harmful conduct that they would never consider in offline settings.
Furthermore, the anonymity afforded by the internet can facilitate misinformation and deceit. Fake accounts and anonymous postings can spread rumors, conspiracy theories, and false information, undermining trust in online discourse and making it difficult to distinguish fact from fiction.
In conclusion, online anonymity is a double-edged sword, offering both protection and peril to internet users. While it can empower individuals to speak freely and find support, it also presents challenges related to accountability and truthfulness. As the digital landscape continues to evolve, striking a balance between anonymity and accountability will remain a complex and ongoing endeavor.
0 notes
Text
what is the difference between vpn and vdi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is the difference between vpn and vdi
VPN encryption methods
VPN encryption methods play a crucial role in ensuring the security and privacy of online communications. By encrypting data transmitted over a virtual private network (VPN), users can prevent unauthorized access and protect their sensitive information from cyber threats.
One common encryption method used in VPNs is the Advanced Encryption Standard (AES). AES is a symmetric encryption algorithm that offers a high level of security and is widely regarded as one of the most secure encryption standards available. It uses keys of varying lengths, such as 128-bit, 192-bit, or 256-bit, to encrypt and decrypt data securely.
Another popular encryption method used in VPNs is Secure Socket Layer (SSL) and Transport Layer Security (TLS). These protocols create a secure connection between the user's device and the VPN server, ensuring that data exchanged between the two endpoints is encrypted and protected from interception.
Additionally, some VPN providers offer other encryption protocols such as Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), and Internet Protocol Security (IPsec). While these protocols may not be as secure as AES or SSL/TLS, they still provide a level of encryption that can enhance the overall security of the VPN connection.
In conclusion, VPN encryption methods are essential for safeguarding online privacy and security. By understanding the different encryption protocols available and selecting a VPN service that prioritizes strong encryption standards, users can enjoy a safe and secure browsing experience while protecting their sensitive data from prying eyes on the internet.
VDI security features
Virtual Desktop Infrastructure (VDI) offers a flexible and efficient solution for organizations looking to centralize desktop management and enhance security. However, ensuring the security of VDI environments is paramount to protect sensitive data and maintain regulatory compliance. Here are some key security features to consider when implementing VDI:
Encryption: Encrypting data both in transit and at rest is essential for safeguarding information accessed through VDI. This ensures that even if unauthorized users gain access to the data, it remains unintelligible without the decryption key.
Multi-factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as passwords, biometric data, or smart cards. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
Network Segmentation: Segmenting the network helps isolate VDI traffic from other parts of the network, limiting the potential impact of security breaches. It allows administrators to apply different security policies to VDI environments, enhancing control and minimizing the attack surface.
Patch Management: Regularly updating and patching VDI software and operating systems is crucial for addressing known vulnerabilities and mitigating security risks. Automated patch management solutions can streamline this process and ensure timely updates across the VDI infrastructure.
Endpoint Security: Securing endpoints such as desktops, laptops, and mobile devices accessing the VDI environment is essential. Endpoint security solutions, including antivirus software, firewalls, and intrusion detection/prevention systems, help detect and prevent malicious activities on client devices.
Logging and Monitoring: Comprehensive logging and monitoring mechanisms provide visibility into VDI activities, allowing administrators to detect suspicious behavior, identify security incidents, and respond promptly to threats.
By incorporating these security features into their VDI deployments, organizations can create a robust defense posture against evolving cyber threats and maintain the integrity and confidentiality of their digital assets.
VPN tunneling protocols
VPN tunneling protocols play a crucial role in ensuring secure and private communication over the internet. These protocols establish a secure connection between a user and a VPN server, encrypting the data passing through the connection. There are several VPN tunneling protocols available, each with its own set of features and capabilities.
One of the most popular VPN tunneling protocols is OpenVPN, known for its high level of security and flexibility. OpenVPN uses the OpenSSL encryption library to provide strong encryption and supports both TCP and UDP protocols. It is widely supported across various platforms, making it a versatile choice for many users.
Another commonly used VPN tunneling protocol is IPsec (Internet Protocol Security), which operates at the network layer of the OSI model. IPsec offers robust security features, including encryption, authentication, and key management. It is often used in combination with other protocols to provide a comprehensive VPN solution.
SSTP (Secure Socket Tunneling Protocol) is another VPN tunneling protocol that is integrated into Windows operating systems. SSTP uses SSL/TLS encryption to secure the connection between the user and the VPN server, making it a suitable choice for Windows users looking for a secure VPN connection.
Additionally, L2TP (Layer 2 Tunneling Protocol) and PPTP (Point-to-Point Tunneling Protocol) are older VPN protocols that are still in use today. While PPTP is known for its ease of setup and fast connection speeds, L2TP offers more robust security features by combining it with IPsec.
In conclusion, VPN tunneling protocols are essential for maintaining privacy and security when accessing the internet. Users should choose a protocol that aligns with their security needs and device compatibility to ensure a safe and private online experience.
VDI remote access solutions
Virtual Desktop Infrastructure (VDI) remote access solutions have become increasingly popular in today's digital age, especially with the rise in remote work arrangements. VDI allows users to access a virtualized desktop environment from anywhere, using any device with an internet connection. This technology offers numerous benefits, including increased flexibility, scalability, and security.
One of the key advantages of VDI remote access solutions is the ability to work from any location, whether it be from home, while traveling, or at a coffee shop. This flexibility allows employees to stay productive and connected to their work environment regardless of their physical location. Additionally, VDI enables quick and easy scalability, making it simple for organizations to add or remove users as needed without the hassle of purchasing additional hardware.
Furthermore, VDI remote access solutions offer a higher level of security compared to traditional desktop setups. Data and applications are stored in a centralized server, reducing the risk of sensitive information being compromised if a device is lost or stolen. This centralized approach also makes it easier for IT teams to monitor and manage user access, ensuring that company data remains secure at all times.
In conclusion, VDI remote access solutions provide a flexible, scalable, and secure way for employees to access their work desktops remotely. With the increasing trend of remote work, VDI technology is becoming essential for organizations looking to empower their employees to work from anywhere efficiently.
VPN vs VDI: Pros and cons
When it comes to accessing secure networks remotely, both Virtual Private Networks (VPNs) and Virtual Desktop Infrastructure (VDI) play significant roles. Let's explore the pros and cons of each to help you make an informed decision on which option suits your needs best.
VPN: Pros:
Security: VPNs encrypt data, ensuring a secure connection for users accessing the network remotely.
Ease of use: Setting up a VPN is relatively simple, making it convenient for individual users and smaller organizations.
Cost-effective: VPN services are generally more affordable, especially for small-scale use.
Cons:
Limited network access: VPNs may not provide full access to the network resources, limiting some functionalities.
Slower speed: The encryption process can sometimes result in slower internet speeds.
Vulnerability: In certain cases, VPNs can be susceptible to cyber threats and vulnerabilities.
VDI: Pros:
Enhanced security: VDI centralizes data storage, reducing the risk of data breaches and ensuring better security.
Full network access: VDI allows users to access all network resources and applications as if they were physically present in the office.
Scalability: VDI can easily scale to accommodate a growing number of users and resources.
Cons:
Complexity: Setting up and maintaining a VDI infrastructure can be complex and requires specialized knowledge.
Cost: VDI solutions can be expensive, especially for smaller organizations or individual users.
Performance issues: Connectivity problems or server failures can impact the user experience with VDI.
In conclusion, both VPNs and VDI offer unique advantages and drawbacks. It's essential to consider your specific needs and resources when deciding between the two technologies.
0 notes
Text
what does vpn mean in settings
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what does vpn mean in settings
Definition of VPN in settings
In the realm of digital security and privacy, the term VPN stands as a beacon of protection against online threats. VPN, short for Virtual Private Network, is a technology that establishes a secure connection over a public network, typically the internet, allowing users to send and receive data as if their devices were directly connected to a private network.
The primary function of a VPN is to encrypt the data transmitted between the user's device and the internet, shielding it from potential eavesdroppers and hackers. This encryption process involves encoding the data into a secure format, making it indecipherable to anyone without the proper decryption key. As a result, VPNs ensure confidentiality and integrity in data transmission, safeguarding sensitive information such as passwords, financial transactions, and personal communications.
Moreover, VPNs offer anonymity by masking the user's IP address with one from the VPN server's location. By rerouting internet traffic through remote servers located in different geographic regions, VPNs obscure the user's online identity and location, making it challenging for third parties to track their online activities.
In settings, VPN configurations allow users to customize their VPN connection according to their specific needs. This includes selecting the preferred VPN protocol, choosing the server location, enabling features like split tunneling or kill switch, and managing other security settings. By accessing the VPN settings, users can optimize their VPN experience to enhance privacy, security, and performance.
In conclusion, a VPN in settings refers to the configuration and customization options available to users for establishing a secure and private connection over the internet. By utilizing VPN technology and adjusting settings accordingly, individuals can fortify their digital defenses and enjoy a safer online experience.
VPN settings explained
VPN settings, short for Virtual Private Network, are a powerful tool to ensure your online privacy and security. VPN settings allow you to control various aspects of your VPN connection, customizing it to fit your specific needs. Understanding these settings can help you maximize the benefits of using a VPN.
One essential setting in a VPN is the protocol selection. VPN protocols determine how data is transmitted between your device and the VPN server. The most common protocols include OpenVPN, L2TP/IPsec, and IKEv2. Each protocol has its strengths and weaknesses, so choosing the right one is crucial for speed, security, and compatibility.
Another important setting is the encryption level. VPNs use encryption to scramble your data, making it unreadable to anyone trying to intercept it. Typically, VPNs offer different encryption levels, such as 128-bit or 256-bit AES encryption. While higher encryption levels provide stronger security, they may also impact connection speed. Finding the right balance between security and performance is key.
Additionally, VPN settings often include options for kill switches, split tunneling, and DNS leak protection. A kill switch shuts down your internet connection if the VPN disconnects, preventing data leaks. Split tunneling allows you to choose which traffic goes through the VPN and which doesn't. DNS leak protection ensures that your DNS queries remain private when using a VPN.
By understanding and configuring these VPN settings, you can enjoy a safer and more private online experience. Take the time to explore and optimize your VPN settings to make the most of this valuable tool in today's digital world.
Understanding VPN in device settings
When it comes to protecting your online privacy and security, using a Virtual Private Network (VPN) is essential. Understanding how to set up and utilize a VPN in your device settings can greatly enhance your online experience.
Setting up a VPN on your device allows you to create a secure connection to another network over the internet. This encrypted connection ensures that your data remains private and secure from prying eyes such as hackers, government surveillance, or even your Internet Service Provider (ISP).
To set up a VPN on your device, you typically need to go to the settings menu and locate the VPN section. From there, you can enter the necessary information provided by your VPN service provider, such as the server address, username, and password. Once you have entered the details, you can connect to the VPN with just a click.
Using a VPN in your device settings can provide several benefits, including accessing geo-restricted content, hiding your browsing activity from ISPs, securing your data on public Wi-Fi networks, and maintaining anonymity online.
In conclusion, understanding how to set up and use a VPN in your device settings is crucial for safeguarding your online privacy and security. By taking advantage of this powerful tool, you can enjoy a more secure and private internet experience.
VPN configuration in settings
Configuring a VPN in your device's settings is a vital step towards enhancing your online privacy and security. Whether you're using a computer, smartphone, or tablet, setting up a VPN can provide you with encrypted connections and mask your IP address, ensuring your online activities remain private from prying eyes.
To configure a VPN in your settings, follow these general steps:
Access Settings: Open the settings menu on your device. This can usually be found by tapping on the gear icon or by searching for "Settings" in your device's search bar.
Select Network or Connections: Look for the section related to network or connections settings. Depending on your device, this might be labeled as "Network & Internet," "Connections," or something similar.
Choose VPN: Within the network or connections settings, locate the option for VPN. It might be listed under a subcategory like "Advanced settings" or "More settings."
Add VPN Configuration: Tap on the option to add a new VPN configuration. You'll typically have the choice to add a VPN manually or through a VPN app installed on your device.
Enter VPN Details: If adding the VPN manually, you'll need to enter specific details provided by your VPN service provider. This usually includes the VPN type (such as IKEv2, L2TP/IPsec, or OpenVPN), server address, username, password, and any other required settings.
Save Configuration: After entering the VPN details, save the configuration. Your device will then attempt to establish a connection to the VPN server using the provided settings.
Connect and Verify: Once the configuration is saved, you can initiate the VPN connection from the settings menu. After connecting, you can verify that the VPN is active by checking for the VPN icon in the status bar or by visiting a website to confirm your IP address is masked.
By configuring a VPN in your device's settings, you can enjoy a safer and more private online experience, whether you're browsing the web, accessing sensitive information, or connecting to public Wi-Fi networks.
Importance of VPN settings
In the digital age, where privacy concerns and cybersecurity threats loom large, the importance of VPN (Virtual Private Network) settings cannot be overstated. VPN settings serve as a crucial shield against various online vulnerabilities, offering users a secure and encrypted connection to the internet.
One of the primary benefits of VPN settings is enhanced security. By encrypting data transmitted between the user's device and the VPN server, VPN settings prevent unauthorized access and interception by hackers, government agencies, or other malicious entities. This is particularly important when using public Wi-Fi networks, which are notorious for their lack of security and susceptibility to cyber attacks.
Moreover, VPN settings enable users to bypass geo-restrictions and censorship imposed by governments or internet service providers (ISPs). By connecting to a VPN server located in a different country, users can access content and websites that may be restricted in their region. This freedom of access is especially valuable for individuals traveling abroad or living in countries with stringent internet regulations.
Furthermore, VPN settings help safeguard users' privacy by masking their IP address and online activities from prying eyes. This is essential for protecting sensitive information such as browsing history, login credentials, and personal data from being monitored or exploited by third parties for targeted advertising or surveillance purposes.
Additionally, VPN settings can improve internet speed and performance by reducing latency and congestion, especially during peak usage hours or when accessing bandwidth-intensive applications.
In conclusion, VPN settings play a crucial role in safeguarding privacy, enhancing security, and enabling unrestricted access to the internet. By implementing VPN settings, users can enjoy peace of mind knowing that their online activities are protected from potential threats and surveillance.
0 notes