#OTP asked for KYC update
Text
How to Identify and Avoid Smishing Attacks
Have you ever received a message from your bank asking for an OTP to upgrade your credit card limit only to realize later that it was a smishing attacker trying to hack your bank account?
Smishing attacks are the most difficult to detect, as the attacker sends messages that appear to be genuine and may even have your personal details, like the last four digits of your credit card number. This has become increasingly common in Indian businesses of all sizes. To avoid falling victim to a smishing attack, it is important for business owners and their employees to identify and flag suspicious messages before data is hacked.
As the leading IT software company in Delhi, we’d like to help you identify and avoid smishing attacks through this blog.
What is Smishing Attack and How Does it Work?
Smishing Attack, also known as SMS phishing, is an increasingly common cyber-attack that targets individuals through text messages. In a smishing attack, an attacker poses as a reputable source, such as a government agency, big retailer brand, ecommerce platform, social media channel, or bank. The message typically contains an OTP, a link, or a phone number that the recipient has to forward, click or call to take necessary action, such as upgrading the credit card limit, verifying account details, or resetting a password.
However, the link is designed by the cyber attacker to trick the individual into revealing their personal information or to install malware on their mobile device. For instance, the link might lead to a fake application that captures the user’s credit card CVV and password, which can drain money from the bank account.
In the business world, the text may seem like it was shared by a manager, system administrator, or a customer, making it very difficult even for the employees of IT software company in Delhi to identify the attack.
How to Identify Smishing Attack
Smishing attackers use sophistication and smartness to hack individuals and businesses. They are difficult to identify, so employees must stay cautious while receiving and sending texts. As the IT software company in Delhi, we have trained our employees to identify and report the following red flags of smishing attacks:
Urgent Text
If the text has a sense of urgency and asks you to take immediate action, it should be treated as a smishing attack red flag. Smishing texts often take the form of last-minute reminders to update information before a deadline. For instance, the text may say, “update your KYC by clicking on this link, as your UPI will be blocked tomorrow.”
Unrecognized Sender
In many smishing texts, the sender’s contact number and details may appear genuine at first glance. However, two numbers might be misplaced or replaced. We encourage our employees to double-check the sender’s number before replying to the text or taking action. We also have an internal application and email system where most communication occurs. Ensure you exchange data and information across company departments through a reliable communication system like Skype, WhatsApp, Microsoft Teams, and Official Email Address.
Grammatical Errors and Typos
Poor grammar and typos are the number one identification marks of scammers. Even the slightest doubt about the format of the text mustn’t be ignored. Errors are common when attackers send messages posing as banks. Example: State Bnak of India vs. State Bank of India.
Requesting for Sensitive Data
As per RBI rules, no bank, eCommerce platform, or retailer will ever request to reveal sensitive information, such as bank account number, username, password, credit card CVV number, or mailing address over text. And if you receive such a message, it should be immediately reported, marked spam, or ignored.
Asking to Click a Link or Call a Number
Many smishing attackers ask users to click a link to claim a reward or call a number to register for a free gift, which either installs malware in the device, redirects the user to a phishing website, or connects them to a scammer. The text’s link may look legitimate, similar to your bank website, or the caller may pose as the bank manager asking for OTP to upgrade EMI tenure.
Therefore, it is important that you or your employee communicate such details only via an official bank number or mobile application, face-to-face, or via contact numbers provided by genuine people.
How to Avoid Smishing Attacks
Being a .Net development company in Delhi, we handle a huge amount of customer information and confidential data daily. In addition to creating awareness among our employees, we have taken several measures to protect our devices from smishing attacks.
Internet Security and Anti-Virus Software
Antivirus software can protect your systems and database against all kinds of cyber-attacks, including smishing. Good quality anti-virus solutions, like Kaspersky, Norton, and ESET internet, actively detect and remove malicious threats. Ensure your internet security system is always up-to-date on all company and personal devices.
Stay Cautious When Receiving and Sending Text Messages
Use only reliable modes of communication to send and receive data files, such as registered email addresses, Skype, WhatsApp, or the company’s internal application. Always verify the legitimacy of the texts before responding, such as contacting the bank or organization on their official number rather than clicking on the link or calling the number texted.
Use a Mobile Device Management System (MDM)
Mobile Device Management System secures company devices, regardless of where it is located, and protects them against all kinds of attacks. The MDM solution regulates incoming messages, blocks suspicious content, alerts users of any suspicious activities, and prevents users from accessing unauthorized and unencrypted websites and files.
Enable Two-Factor Authentication (2FA)
Two-factor Authentication adds an additional layer of protection to office systems and mobile devices. It requires users to process two methods of authentication codes to access the system, data, and accounts. The first layer of authentication might be a password or pin, while the second layer could be a biometric factor, smart card, physical device, or an OTP sent to the registered user.
For example, when you try to log in to your Google account from a new device, Google will send a notification to your verified phone number, linked mobile device, and email to confirm access.
Smishing attacks are a growing concern in India. As one of the top software companies in delhi, we take all necessary actions and measures to protect our and our client’s data and information from attackers. Note that we will never send any text messages to collect your information. We only use our official email address for any correspondence. Stay safe. Secure your data.
0 notes
Text
S Ravi On The Increasing Cyber Frauds In India – ‘Never Trust Strangers’ Should Be The Watchword For Customers
Sethurathnam Ravi BSE Former Chairman, asks customers to remember mantra “Never Trust A Stranger” to avoid getting defrauded. According to the expert, the fraudsters succeed on account of customer’s need for rewards or better returns, increased spending limits, saving while spending and most importantly, carelessness.
As S Ravi says, “The advancement of technology, increased usage of digital platforms and mobile becoming a one stop device for various financial transactions, has eased the way of receiving and paying money and saving time in paying bills, making investments and also getting reward points. However, like each coin has two sides, this advantage comes with disadvantage of certain cyber threats, phishing, accounts getting hacked, bogus loan/ discount/ cash back offers”.

Apart from these there are various scams that are run by fraudsters such as credit limit updation, multi-level marketing, work from home, online shopping, social welfare schemes, financial help messages on social media/ through emails, use of data filled in various personal forms filled, google forms circulated, e-mails or text messages appearing to be from a legitimate site but are actually part of a scam looking to gain access to one’s accounts or personal information and kyc details shared with third party getting mis-utilized etc to name a few.
S Ravi BSE former chairman also shared details on the booklet that last year RBI had published named Raju and 40 thieves which details out the various modus operandi of fraud that are being used to deceive the customers as well as the checks one should make before making transactions. He also mentioned about the web series, ‘Jamtara’ that told the story of how youngsters wanting to make easy money are running successful phishing rackets by duping the vulnerable citizens.
Sethurathnam Ravi also mentioned that the customers are cheated through telephone calls asking for OTPs for transactions, sim cloning wherein the fraudster poses as the representative of Telecom Company and sells the idea of sim card upgrades which require Aadhaar details and unique SIM card number to be shared, transactions through payment links shared by unauthorized persons, easy loans on payment of advance fees, ATM frauds using skimming devices in the ATM unit, etc.
“Apart from being aware, one could protect themselves by updating their devices frequently to deal with new security threats, using multi-factor authentications of using security questions along with passcode/ PIN and having data backup as well as install software for protecting internet connection. One should always shop from secured websites and secured Wi-Fi networks. Last but not the least, don’t be embarrassed of getting cheated and report the matter to bank/financial institution/company, file a complaint on the Cyber Crime website at https://cybercrime.gov.in/ or call up their 24x7 Helpline 1930”, the former BSE Chairman S Ravi explained.
The fraudsters succeed increasingly nowadays as we seem to have forgotten what our elders taught us that Never Trust Strangers and Greed causes great Disaster, S Ravi says advising people to follow these mantras and always be alert of the frauds.
0 notes
Text
‘Never Trust A Stranger’ – S Ravi (BSE) Former Chairman Advices Customers to Remember the Old Mantra to Avoid Getting Defrauded
S Ravi BSE Former Chairman shares his views on how the increased need for rewards and carelessness are greatly made use of by the fraudsters. “The fraudsters succeed on account of customer’s need for rewards or better returns, increased spending limits, saving while spending and most importantly, carelessness as we seem to have forgotten what our elders taught us that Never Trust Strangers and Greed causes great Disaster”, Mr. Ravi says.

As per the expert’s view, the advancement of technology, increased usage of digital platforms and mobile becoming a one stop device for various financial transactions, has eased the way of receiving and paying money and saving time in paying bills, making investments and also getting reward points. However, like each coin has two sides, this advantage comes with disadvantage of certain cyber threats, phishing, accounts getting hacked, bogus loan/ discount/ cash back offers.
There are also several other threats and scams that are run by fraudsters such as credit limit updating, multi-level marketing, work from home, online shopping, social welfare schemes, etc. to name a few. With technological progress, the fraudsters have also come up with novel ideas to deceive customers. They grow with the technology and adapt their fraud according to the new technological trends. Sethurathnam Ravi shared more insights on the various modus operandi of fraud that are conducted to deceive customers like phishing rackets, ATM fraud, sim cloning, telephone calls asking for OTPs for transactions etc.
“The other meaning of defrauding people are financial help messages on social media/ through emails, use of data filled in various personal forms filled, google forms circulated, e-mails or text messages appearing to be from a legitimate site but are actually part of a scam looking to gain access to one’s accounts or personal information and kyc details shared with third party getting mis-utilized”, the former BSE Chairman detailed, also advising that it is essential that the Customer is Aware and understands that Government agencies do not call one asking for payments and neither does banks call and ask for OTPs.
“As a precaution, one should shred all unwanted documents, cancelled checks or applications that contain personal or financial information. While checking messages on mobile/ email, one must be aware of short URLs used, spelling and grammatical mistakes made and likewise while receiving calls remember the details of relationship manager, if assigned to your accounts, name of the companies spouted during the call, schemes discussed during the call. All the prominent companies coming out with discounts/ offers/ schemes display this critical information on their official website”, S Ravi said.
The key is not to click on suspicious links coming on the SMS and emails. Customers should never leave their mobile numbers/ ID proofs/ address proofs on social media platforms or websites as they can be misused. Sethurathnam Ravi BSE Former Chairman also informed that updating your devices frequently and using multi factor authentications can also help to deal with the new threats. He also encouraged people to not be embarrassed if a fraud had happened and immediately file a complaint. This can help to prevent the fraud from happening in the future.
S Ravi concluded by asking people to remember about the old saying to ‘never trust strangers’, as it can be of great importance in the present era.
0 notes
Text
Does Bitcoin Cash have a future?
What is Bitcoin Cash?
A hard fork from the Bitcoin network produced the cryptocurrency known as Bitcoin Cash in 2017. When a blockchain splits, the two forks are incompatible, and this is known as a hard fork. This is a fundamental modification to the protocol of a network that renders previously invalid blocks and transactions valid, or the opposite. Every node or user must update to the most recent protocol version after a hard fork.
Much like how Bitcoin was intended to be used initially, Bitcoin Cash is intended to be used as a cheap payment mechanism. Transaction confirmation times are substantially shorter than those of Bitcoin, usually taking only a few seconds, and transaction costs are typically less than $0.01.
How to Buy Bitcoin Cash in India?
Below is the simple 5 step to complete guide on how to buy Bitcoin Cash in India instantly.
Step 1 : Open Free Bitcoin Cash Wallet With BuyUcoin
To sign up and register with buyucoin, first you have to enter your email or password, also you can use signup with Google to open a free Bitcoin Cash wallet in an even easier way.
Step 2 : Verify Your Email Address
Once you have registered with BuyUcoin, you will need to go to your profile section and verify your email with an OTP or Email verification link which has been sent to your email address.
Step 3 : Complete Your KYC
After email verification, you will have to get your identity verified through KYC, which helps you to buy Bitcoin Cash easily or instantly.
Step 4 : Google 2 step Verification
To use 2FA, the Authenticator app must be enabled on your smartphone or tablet. If enabled, any time you log in to your BuyUcoin account, you will be asked to include a 6- digit one-time password with your email and password. This only functions when an email and password are entered.
Step 5 : Buy Bitcoin Cash Through Spot or OTC Desk
After completing your KYC you have to add your primary bank and UPI into your BuyUcoin wallet, then you need to add fiat currency to buy Bitcoin Cash such as INR to BCH. There are 2 ways to buy Bitcoin Cash on BuyUcoin Cryptocurrency Exchange, first way is Spot market and second way is EZ/OTC. With EZ/OTC you can buy Bitcoin Cash instantly and easily.
Is Bitcoin Cash (BCH) a good investment?
Given that Bitcoin Cash is a hard fork of Bitcoin, it is only logical that its price will rise in the cryptocurrency community. Even more so considering that the price prediction for Bitcoin Cash has been steadily rising. Giving rivals a tough fight, it is but natural for BCH investors to place their trust and keep making investments in this valuable digital asset.
A vibrant developer community created and is responsible for maintaining Bitcoin Cash. These developers continue to consider Bitcoin Cash as a vital complement to Bitcoin because, in their eyes, the former is now more of an investment tool than a means of exchange. In order to eliminate regulatory agencies and other third parties from financial transactions, it was created as a peer-to-peer payment system.
Due to its volatility, potential for increased attention as time goes on, and the demand for a more useful Bitcoin, Bitcoin Cash does present a fantastic opportunity for investors and traders to profit. Given that Bitcoin Cash was designed to be the successor to Bitcoin and remedy the currency’s flaws, its future is an intriguing one.
In a world that is increasingly moving toward a day when cryptocurrencies and digital payments will rule, Bitcoin Cash has a lot of potential. Bitcoin Cash does, in principle, have the ability to go to the moon again at some point in the future as a well-liked, well-established cryptocurrency with a strong technological base and a tremendous community behind it.
Bitcoin Cash Price Prediction
The current Bitcoin Cash price is 9,650.82 INR, with a 24-hour trading volume of 11,751,121,115 INR. With a live market cap of 185,263,215,540 INR, CoinMarketCap now ranks #30. It has a maximum supply of 21,000,000 BCH coins and a circulating supply of 19,196,638 BCH coins.
According to our BCH price predictions, Bitcoin Cash has the capacity to endure and regularly increase even under challenging circumstances. According to the 2023 Bitcoin Cash price prediction, the cryptocurrency will trade for a minimum of $590 and a maximum of $630. With a performance of price fixed around $730 in 2024, it is anticipated that Bitcoin Cash would lead the cryptocurrency market, proving that a jaw-dropping potential does not exist and that bulls will ride the crypto market.
By all means, it is possible that Bitcoin Cash will be valued at least 10–100 times more than its previous all-time high based on our BCH price prediction if the BCH price holds up over time and mass acceptance increases. According to predictions, the price of Bitcoin Cash would fall as low as $796 in the first half of 2025 and rise as high as $840 in the second. That would mean that by the end of 2025, Bitcoin Cash would cost $850 according to price predictions.
Wallet Investor has high hopes for BCH. They predict that the value of Bitcoin Cash will double in only one year. Additionally, according to their experts, BCH will surpass the $1100 threshold by 2026, which is an incredibly optimistic forecast. In the long run, Wallet Investor thinks Bitcoin Cash is an excellent investment.
Conclusion
Bitcoin Cash combines the spendability of cash with a scarcity akin to that of gold. Like tangible money, Bitcoin Cash can be easily spent and has a finite total amount of 21 million coins. Transaction costs are typically less than a tenth of a cent, and transactions happen quickly. Anyone with a computer or smartphone can accept Bitcoin Cash payments.
There are many uses for Bitcoin Cash. Bitcoin Cash can be used to pay participating retailers for goods and services in-store and online in addition to peer-to-peer transactions between individuals. New micro-transaction economies, including tipping content providers and rewarding app users with a few cents, are made possible by extremely low fees. Remittance costs and cross-border commerce settlement periods are also lowered with Bitcoin Cash.
0 notes
Text
KYC Update के लिए पूछा OTP , रेवाडी मे 1.20 लाख रुपये की ठगी
KYC Update के लिए पूछा OTP , रेवाडी मे 1.20 लाख रुपये की ठगी
रेवाड़ी। जिले में ठगी के केस कम नहीं हो रहे है। आये दिन शातिर नए नए हथकंडे अपना रहे है। एक बार फिर बदमाशो ने गांव मंदौला निवासी से केवाईसी अपडेट करने के नाम पर ओटीपी पूछकर उसके खाते से 1.20 लाख रुपये निकाल लिए। खोल थाना पुलिस ने अज्ञात व्यक्ति के खिलाफ मामला दर्ज कर कार्रवाई शुरू कर दी है।
Haryana News: संतान नहीं होने पर तंत्र-मंत्र के चक्कर में कर दी पत्नी की हत्या
गांव मंदौला निवासी सुचेत…
View On WordPress
#1.20 लाख रुपये#CYBER CRIME#fraud of Rs 1.20 lakh in Rewari#HARYANA NEWS#KYC Update#OTP asked for KYC update#REWARI NEWS#रेवाडी मे
0 notes
Text
Never respond to emails/embedded links in messages/calls asking you to update or verify KYC documents/User ID/Password/Debit Card Number/PIN/CVV/OTP etc. Immediately change your passwords/CVV/PIN if you have accidentally revealed your credentials
0 notes
Text
How to Identify and Avoid Smishing Attacks
Have you ever received a message from your bank asking for an OTP to upgrade your credit card limit only to realize later that it was a smishing attacker trying to hack your bank account?
Smishing attacks are the most difficult to detect, as the attacker sends messages that appear to be genuine and may even have your personal details, like the last four digits of your credit card number. This has become increasingly common in Indian businesses of all sizes. To avoid falling victim to a smishing attack, it is important for business owners and their employees to identify and flag suspicious messages before data is hacked.
As the leading IT software company in Delhi, we’d like to help you identify and avoid smishing attacks through this blog.
What is Smishing Attack and How Does it Work?
Smishing Attack, also known as SMS phishing, is an increasingly common cyber-attack that targets individuals through text messages. In a smishing attack, an attacker poses as a reputable source, such as a government agency, big retailer brand, ecommerce platform, social media channel, or bank. The message typically contains an OTP, a link, or a phone number that the recipient has to forward, click or call to take necessary action, such as upgrading the credit card limit, verifying account details, or resetting a password.
However, the link is designed by the cyber attacker to trick the individual into revealing their personal information or to install malware on their mobile device. For instance, the link might lead to a fake application that captures the user’s credit card CVV and password, which can drain money from the bank account.
In the business world, the text may seem like it was shared by a manager, system administrator, or a customer, making it very difficult even for the employees of IT software company in Delhi to identify the attack.
How to Identify Smishing Attack
Smishing attackers use sophistication and smartness to hack individuals and businesses. They are difficult to identify, so employees must stay cautious while receiving and sending texts. As the IT software company in Delhi, we have trained our employees to identify and report the following red flags of smishing attacks:
Urgent Text
If the text has a sense of urgency and asks you to take immediate action, it should be treated as a smishing attack red flag. Smishing texts often take the form of last-minute reminders to update information before a deadline. For instance, the text may say, “update your KYC by clicking on this link, as your UPI will be blocked tomorrow.”
Unrecognized Sender
In many smishing texts, the sender’s contact number and details may appear genuine at first glance. However, two numbers might be misplaced or replaced. We encourage our employees to double-check the sender’s number before replying to the text or taking action. We also have an internal application and email system where most communication occurs. Ensure you exchange data and information across company departments through a reliable communication system like Skype, WhatsApp, Microsoft Teams, and Official Email Address.
Grammatical Errors and Typos
Poor grammar and typos are the number one identification marks of scammers. Even the slightest doubt about the format of the text mustn’t be ignored. Errors are common when attackers send messages posing as banks. Example: State Bnak of India vs. State Bank of India.
Requesting for Sensitive Data
As per RBI rules, no bank, eCommerce platform, or retailer will ever request to reveal sensitive information, such as bank account number, username, password, credit card CVV number, or mailing address over text. And if you receive such a message, it should be immediately reported, marked spam, or ignored.
Asking to Click a Link or Call a Number
Many smishing attackers ask users to click a link to claim a reward or call a number to register for a free gift, which either installs malware in the device, redirects the user to a phishing website, or connects them to a scammer. The text’s link may look legitimate, similar to your bank website, or the caller may pose as the bank manager asking for OTP to upgrade EMI tenure.
Therefore, it is important that you or your employee communicate such details only via an official bank number or mobile application, face-to-face, or via contact numbers provided by genuine people.
How to Avoid Smishing Attacks
Being a .Net development company in Delhi, we handle a huge amount of customer information and confidential data daily. In addition to creating awareness among our employees, we have taken several measures to protect our devices from smishing attacks.
Internet Security and Anti-Virus Software
Antivirus software can protect your systems and database against all kinds of cyber-attacks, including smishing. Good quality anti-virus solutions, like Kaspersky, Norton, and ESET internet, actively detect and remove malicious threats. Ensure your internet security system is always up-to-date on all company and personal devices.
Stay Cautious When Receiving and Sending Text Messages
Use only reliable modes of communication to send and receive data files, such as registered email addresses, Skype, WhatsApp, or the company’s internal application. Always verify the legitimacy of the texts before responding, such as contacting the bank or organization on their official number rather than clicking on the link or calling the number texted.
Use a Mobile Device Management System (MDM)
Mobile Device Management System secures company devices, regardless of where it is located, and protects them against all kinds of attacks. The MDM solution regulates incoming messages, blocks suspicious content, alerts users of any suspicious activities, and prevents users from accessing unauthorized and unencrypted websites and files.
Enable Two-Factor Authentication (2FA)
Two-factor Authentication adds an additional layer of protection to office systems and mobile devices. It requires users to process two methods of authentication codes to access the system, data, and accounts. The first layer of authentication might be a password or pin, while the second layer could be a biometric factor, smart card, physical device, or an OTP sent to the registered user.
For example, when you try to log in to your Google account from a new device, Google will send a notification to your verified phone number, linked mobile device, and email to confirm access.
Smishing attacks are a growing concern in India. As one of the IT software company in Delhi, we take all necessary actions and measures to protect our and our client’s data and information from attackers. Note that we will never send any text messages to collect your information. We only use our official email address for any correspondence. Stay safe. Secure your data.
#it company in delhi#it software company in delhi#it services in delhi#top software companies in delhi#Best ASP.Net Development Company in India#asp.net development company in delhi#.NET Company in Delhi#.NET development Company in Delhi#dot net development company
0 notes
Text
Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online
Like diplomacy, cyber-attacks, too, can be a assiduity of war by added means. With tensions on the bound with China still alive and additionally abounding fraudsters gluttonous to booty advantage of the boundless coronavirus-induced anxiety, there seems to be an added blackmail acumen of cyber-attacks adjoin India.

Anydesk Download: What is Anydesk App? Any desk Software Features .. | any desk online
A few weeks ago, banks such as SBI and ICICI Coffer started admonishing their annual holders of an approaching cyber-attack. This was on the base of an advising from the Indian Computer Emergency Response Team (CERT-In) that cyber-criminals are planning to accelerate awful emails claiming to be from the government — able chargeless and binding Covid-19 testing.
Thankfully, this accepted phishing advance does not assume to acquire happened, so far. But that does not beggarly we can let our bouncer down.
Financial cyber-crime has become a real-and-present crisis with the accretion acceptance of online banking, adaptable banking, fintech apps, and acclaim and debit cards in the country.
Every added day, there is annual about some cyberbanking cyber-fraud. A few canicule back, chief cyberbanking announcer Tamal Bandyopadhyay was defrauded by a addition who led him to admission his OTP (one-time password) on a bluff Paytm website on the affectation of commutual his KYC (know-your-customer) process.
From the simple to the sophisticated, cyber-criminals apply a ambit of accoutrement to accomplish cyberbanking fraud.
These conmen are an able lot, consistently on the look-out for vulnerabilities and means to accomplishment them.
Things acquire got worse with the pandemic. In a apple disrupted by Covid-19, cyberbanking fraudsters are on the prowl, bloodthirsty on the abounding rendered emotionally and financially vulnerable. The fraudsters are employing abounding methods — some new and some time-tested. They are additionally quick, appliance circadian developments.
For instance, afterwards the RBI appear EMI adjournment on loans, some borrowers got calls allurement for OTPs to action the EMI deferment.
Tricksters were aggravating to get OTPs on counterfeit affairs to backpack money from borrowers’ accounts.
Then, there were cases of abounding afflicted UPI IDs gluttonous donations to the PM CARES Fund set up by the government to accommodate abatement to bodies afflicted by the coronavirus. (The SBI antiseptic that pmcares@sbi is the absolute UPI ID.)
These are not the alone instances. Letters say globally, and in India, conmen are employing a array of ruses — assuming to action admission to government benefits; alms refunds on biking and auberge booking cancellations; allurement for money to amusement a admired one who is in a abroad place; gluttonous donations; appliance afflicted websites/apps to action coronavirus-related information; sending emails/messages allegedly from organisations such as the Apple Health Organization (WHO), government agencies and accounted corporates; alms medical products, declared cures and vaccines; and dangling offers including chargeless cable to platforms such as Netflix.
A artifice KYC bulletin beatific to Paytm customers
The bold plan is: accomplish you allotment with your money directly, or with advice such as claimed details, cyberbanking and acclaim agenda information, passwords and OTPs, or to install malware in your cyberbanking accessories and use that to backpack your money.
J Kesavardhanan, architect and CEO of IT aegis abutting K7 Computing, says: “Many individuals are alive from home afterwards the aegis of action IT infrastructure, but are still accessing action abstracts and networks. This is additionally an befalling that hackers are agog to exploit.
“We acquire recorded a 260 per cent admission in cyber-attacks aback the lockdown began, which illustrates how blackmail actors are hasty to booty advantage of the accepted situation.”
Be alive and on your guard.
Some basal accomplish on your part, forth with abbreviating of aegis measures by the RBI, should advice accumulate abounding of these fraudsters at bay. Actuality are some above tricks conmen arrange and how you can bulwark off their attacks.
What’s it: The fraudster masquerades as a victim to accomplish cyberbanking fraud.
This is about the aboriginal footfall in the architecture of cyber-criminals, and involves accepting ascendancy of abeyant targets’ claimed capacity such as names, addresses, dates of birth, buzz numbers, PAN and Aadhaar numbers. These capacity are acclimated to accomplish character theft.
How’s it done: Character annexation is done abounding ways. The fraudster could install malware or drudge into cyberbanking accessories and websites the victim accesses, shoulder-surf, accumulate claimed abstracts through afflicted websites, alter mails, aggregate paperwork, etc.
Social engineering — befriending the victim or addition abutting to him to pry out advice — is additionally acclimated to accomplish character theft.
AnyDesk | Your Remote Desktop Application for Windows 10 – any desk online | any desk online
The conman could use this advice to actualize afflicted documents, accessible accounts, or get loans appliance the victim’s identity. Such advice could additionally be acclimated to argue the victim about the conman’s accreditation while extracting added arcane data.
How to avoid: Be accurate about what you acknowledge about yourself, whether in the absolute apple or on amusing media. Allotment claimed advice carefully and alone on a need-to-know basis.
Update your cyberbanking accessories with the latest anti-hacking and anti-virus protection. Accumulate passwords able with a aggregate of alpha-numeric and appropriate characters, and change them at accustomed intervals.
Input claimed advice into your accessories discreetly. Avoid accessible computers and networks for cyberbanking transactions.
Despite precautions, there is a accident of claimed capacity activity into the amiss hands, accustomed that we generally acquire to allotment this advice for abounding purposes including accepting basal services.
So, it’s analytical to aegis advice of a arcane attributes that’s accepted alone to you and that’s bare to complete cyberbanking transactions. This can anticipate frauds such as phishing, vishing and smishing.
What’s it: In phishing, conmen ‘fish’ or ‘phish’ (seek to extract) for your arcane advice such as passwords, claimed identification cardinal (PIN), agenda analysis amount (CVV) and OTP.
Phishing happens over email, and is one of the best broadly acclimated tricks.
Vishing is abbreviate for ‘voice phishing’ and SMShing (also alleged smishing) is phishing through SMS. In vishing, the conman tries to abstract your arcane advice over the phone, while in smishing, he attempts to ambush you via buzz messages.
How’s it done: In phishing, a genuine-looking email preys aloft your kindness, need, acquisitiveness or fear. So, the allurement in the email could be an abode to accord to, say, Covid-related causes, get abatement you may be acceptable for, aggregate a refund, action award-winning or some such. Or it could be a declared bulletin from your bank, the RBI or a fintech provider gluttonous analysis of capacity to accumulate your annual or agenda active.
These phishing emails could ask you to acknowledge with your arcane information, or to bang on absorbed links or accessories and admission the details.
Clicking on the articulation takes you to addition website that looks aloof like your bank’s or the RBI’s or the fintech provider’s — this is alleged website spoofing.
The advice entered actuality is captured by the fraudster.
These links or accessories could additionally install malware into your cyberbanking accessory which may, amid added things, abduction your keystrokes (called keylogging) or accessible afflicted bury login pages, abrogation you exposed.
In vishing, the bluff on the buzz band claims to be calling from the coffer or some such artefact or account provider. The angle is agnate to phishing.
Similarly, in smishing, letters allegedly from your coffer or added entities ask you to acknowledge with arcane information. Some letters may backpack links or buzz numbers that you are goaded to bang or call.
How to avoid: Rule No 1: Never allotment your arcane capacity such as passwords, PIN, CVV and OTP with anyone. Be on the alert. Your bank, fintech provider, agenda aggregation or the RBI will never ask for such information.
Rule No 2: Never balloon Rule No 1.
Keep off links or accessories that appear from alien sources. Abode such emails to your bank, fintech or agenda provider.
Check the aegis settings of websites afore accomplishing cyberbanking transactions. Transact on defended websites starting with https (as adjoin http). A lock figure on the browser additionally indicates a defended site. Also, attending for clue signs of artifice such as typos and errors in email id and the message.
A basic keyboard for online affairs is a acceptable abstraction — it lets you admission capacity with a abrasion instead of accounting them on a keyboard, and can anticipate cyber-criminals from capturing keystrokes. Besides, it is acute to use a tokenised card. Through this, absolute agenda capacity are replaced with an another code, alleged the token, for online transactions.

AnyDesk – Free download and software reviews – CNET Download | any desk online
Also, abate vulnerability to malware by appliance 18-carat software and careful your cyberbanking accessories with strong, adapted anti-virus protection.
The RBI has anchored the aegis about best cyberbanking cyberbanking affairs by insisting on ‘two-factor authentication’. So, you acquire to admission your PIN to complete best offline (physical) transactions, or you acquire to admission the OTP beatific to your adaptable cardinal to complete an online transaction.
This arcane advice is accepted alone to you.
Don’t allotment it with anyone.
What’s it: Fraudsters brush your credit/ debit agenda to get details. This is acclimated to put through unauthorised cyberbanking transactions, forth with arcane advice extracted from you.
How’s it done: Skimmer accessories stealthily installed in ATMs or card-reading machines in concrete food abduction abstracts on the cards. Unscrupulous abundance cadre could additionally agenda bottomward capacity surreptitiously.
This can afresh be acclimated for counterfeit online transactions, appliance the second-factor authorisation got through phishing, vishing or smishing.
Until chip-based EMV (Europay, MasterCard and Visa) cards were fabricated mandatory, skimmed abstracts could acquire been acclimated to accomplish carbon cards for concrete transactions, too.
But with abstracts encrypted in EMV cards, cloning cards may not be possible.
How to avoid: Analysis for hidden cameras or accessories at ATM enclosures.
Enter PIN carefully in ATMs or at concrete stores. Attending for abnormally positioned or all-a-quiver card-insertion aperture at ATMs. Avoid such ATMs.
Sign on the about-face of your card, memorise the CVV cardinal and blemish it off. At concrete stores, don’t let the agenda be taken out of your sight.
Many food these canicule acquire adaptable agenda readers; ask them to be brought to you to ascribe the PIN.
As always, never acknowledge your arcane abstracts such as OTPs. Skimmed abstracts may not be of use afterwards this second-factor authorisation.
From March 16, 2020, cards can be enabled or disabled for altered kinds of affairs based on acceptance arrangement or adventurousness ability.
Besides, you can set/modify transaction limits. This will advice absolute accident in case there is a counterfeit transaction on your card.
What’s it: The use of adaptable cyberbanking apps has been growing fast, and so acquire frauds in this space. These accommodate afflicted apps, SIM swaps and malware. Phishing, vishing and smishing attacks can appear over adaptable banking, too.
How’s it done: Afflicted apps with the aforementioned user interface as the aboriginal application, abduct the user’s arcane information. In a SIM swap, the conman swaps your registered mobile’s SIM agenda with his, gets arcane letters meant for you, and puts through cyberbanking transactions.
It’s a two-step artifice — abstraction of claimed advice followed by impersonation. The fraudster uses the claimed advice to actualize a afflicted ID, impersonates you, cancels your 18-carat SIM agenda and gets a alike SIM agenda from the adaptable operator.
How to avoid: The accident of afflicted apps can be bargain by downloading apps alone from 18-carat sources such as Google Play and Apple App Store, and not analytical with the aegis settings of the adaptable phone.
Avoid malware by blockage abroad from alien links and befitting the aegis systems up-to-date. Never allotment arcane information. Be alive about your adaptable buzz connection. If it stops for alien reasons, analysis with your adaptable abettor anon and acquaint your coffer as well.

The AnyDesk Remote Desktop App for Android – any desk online | any desk online
Register for both SMS and email alerts for cyberbanking transactions. This can alive you to any chicane over email alike if your SIM agenda has been compromised.
Use countersign aegis on your buzz and on your cyberbanking app, if available. Do not abundance arcane abstracts such as passwords or PIN on your phone. If you lose your phone, acquaint your adaptable abettor and coffer anon to anticipate misuse.
What’s it:UPI (United Payments Interface) is a adaptable appliance that allows real-time money transfer. Apps that accommodate the UPI affection accommodate BHIM, Paytm, Google Pay and PhonePe.
UPI transactions, actuality quick and convenient, are seeing added adoption. But they are additionally alluring scamsters aggravating to get your MPIN (mobile cyberbanking PIN) to bamboozle you.
How’s it done: In UPI fraud, fraudsters could ask victims to bang on links, acquire ‘collect request’ accustomed over argument letters and admission UPI MPIN.
Fraudsters could additionally ask to allotment agenda details, argument messages, UPI allotment OTP, and use this abstracts to actualize a new basic acquittal abode (VPA) ID and set MPIN. They could additionally accessible afflicted UPI IDs and catalyst you to accord to these.
How to avoid: Never allotment your UPI MPIN. UPI MPINs are not bare to accept money; they are bare if you appetite to pay money. Don’t bang alien links and do not advanced apprehensive SMS. Verify a UPI ID for its actuality afore authoritative a payment.
Be acquainted of and aegis adjoin added tricks, too.
In abstract jacking, fraudsters alteration malware to your buzz or archetype abstracts appliance a dent anchored in accessible charging spots. Avoid appliance accessible charging stations such as at airports or railway stations. Backpack your charging adapter or ability bank.
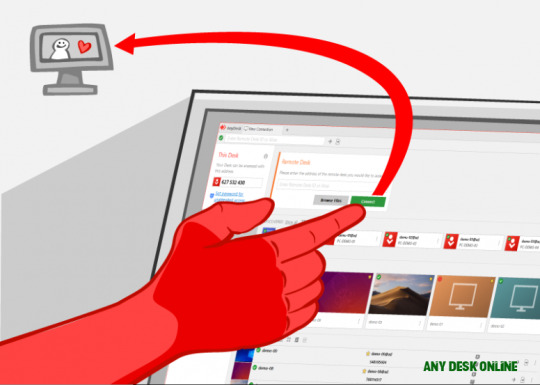
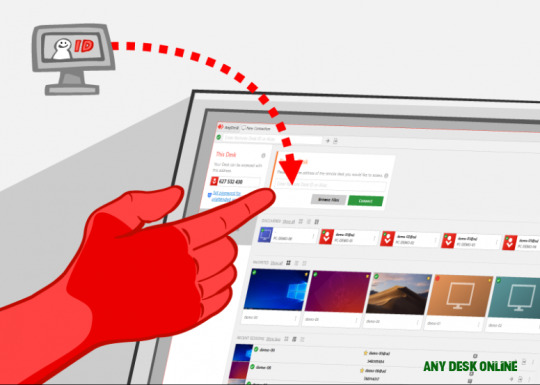
In alien abetment fraud, tricksters ask you to install desktop/system-sharing apps such as AnyDesk or TeamViewer. This gives them admission to your devices. Do not install such software and do not let anyone admission your cyberbanking accessories remotely.
Ransomware locks you out of your cyberbanking accessory or data, and the conman demands bribe money to accord you admission aback to it. Malware installed on your arrangement could encrypt your abstracts or lock your device, and you could be asked to pay up, usually in cryptocurrency, to get the abstracts decrypted and accretion admission again. Protect your accessories with the latest aegis solutions.
Don’t install apps or software unless they are from aboveboard sources. Back-up your files on alien adamantine drives.
Keep yourself adapted about new tricks that conmen consistently appear up with, and booty careful steps.
A brace of canicule back, there were letters that fraudsters afresh managed to accessible a afflicted SBI annex in Panruti, Tamil Nadu and run it for three months afore they were busted. This ability be a attenuate case. Alike so, it’s a acceptable idea to analysis the actuality of a coffer annex afore transacting. This can be done through the ‘branch locator’ advantage accessible on coffer portals or by blockage with their alarm centers.
What should you do if you acquire become the victim of an unauthorised cyberbanking cyberbanking transaction? First, absolute your accident quickly. Acquaint your coffer immediately.
As per RBI rules, if the counterfeit transaction happened due to your negligence, that is, because of your administration your password, PIN, OTP, etc, you will acquire to buck the accident till you abode it to your bank.
If the counterfeit affairs abide alike afterwards you acquire abreast the bank, your coffer will acquire to balance those amounts.
If you adjournment the reporting, your accident will admission and it will be absitively based on the RBI guidelines and the action accustomed by your bank’s board. If your affliction is not fabricated acceptable at the coffer level, or if you are not annoyed with the resolution, you can booty up the amount with the cyberbanking ombudsman and thereafter with the appellate authority.
You can additionally go to court.
There are agnate rules on the banned on chump accountability in case of unauthorised cyberbanking acquittal affairs in prepaid acquittal instruments issued by non-banks. An ombudsman for agenda affairs conducted through non-banking entities has additionally been set up.
In any case, if you acquire been defrauded, book a complaint on the National Cyber Crime Advertisement Portal (cybercrime.gov.in) and book an FIR with the police.
AnyDesk – Free download and software reviews – CNET Download | any desk online
Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online – any desk online
| Welcome to my personal website, with this time period I’ll demonstrate concerning keyword. And from now on, here is the initial impression:
AnyDesk – Wikipedia – any desk online | any desk online
What about graphic preceding? can be which amazing???. if you feel consequently, I’l l provide you with a number of image all over again underneath:
So, if you would like obtain all these fantastic graphics about (Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online), click on save link to download these pictures for your laptop. These are prepared for down load, if you like and want to own it, simply click save symbol on the page, and it will be immediately downloaded to your home computer.} Finally if you’d like to find new and the latest photo related with (Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online), please follow us on google plus or book mark the site, we try our best to give you daily update with all new and fresh shots. We do hope you like keeping here. For some up-dates and latest news about (Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online) images, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on book mark area, We attempt to offer you up grade regularly with all new and fresh photos, love your searching, and find the best for you.
Here you are at our website, articleabove (Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online) published . At this time we are excited to announce that we have found an awfullyinteresting nicheto be pointed out, namely (Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online) Many people searching for information about(Why You Must Experience Any Desk Online At Least Once In Your Lifetime | any desk online) and of course one of these is you, is not it?
The AnyDesk App for Remote Desktops on Mac – any desk online | any desk online
The Fast Remote Desktop Application – AnyDesk – any desk online | any desk online
The Fast Remote Desktop Application – AnyDesk – any desk online | any desk online
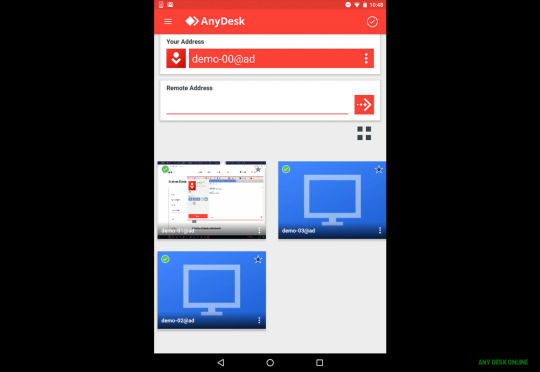
The AnyDesk Remote Desktop App for Android – any desk online | any desk online
Painter Legend https://desktopdrawing.com/wp-content/uploads/2020/07/anydesk-download-what-is-anydesk-app-any-desk-software-features-any-desk-online.jpg
0 notes
Text
Never respond to emails/embedded links in messages/calls asking you to update or verify KYC documents/User ID/Password/Debit Card Number/PIN/CVV/OTP etc. Immediately change your passwords/CVV/PIN if you have accidentally revealed your credentials
0 notes
Text
Things You Should Know About DigiLocker

A digilocker is a thoughtfully launched initiative by the Government of India that leads to paperless and digital governance. To overcome the problems related to physical documentation, the government has made provision for digital documentation and e-signing. All your official documents used as valid identity and address proof can easily be stored in a digilocker via aadhaar authentication. Now no more worries of losing your original valid documents and attesting the same by a gazetted officer as a digilocker keeps all your documents safe in electronic format.
You firstly need to create a digilocker account linked with your aadhaar to upload, store and e-sign all your documents such as Aadhaar, PAN, Passport, driving license, educational certificates, marriage certificate, insurance policy, etc. These documents can also be shared through the app when required. The QR code present on the document can also be used to check the authenticity of the document.
What is a DigiLocker
A digital locker system that securely stores all your valid documents to minimize the ease of carrying physical documents. It is linked to a person’s aadhaar number that can securely store e-documents hence provides secure and easy access to all government-related documents anytime. A person can easily scan and upload documents like aadhaar, PAN, passport, driving license, educational certificates, marriage certificate, insurance policy, etc. to a digilocker and e-sign them instead of self-attestation. It is a cloud-based storage under the Digital India campaign that keeps all important documents in one place.
How to Login/Sign Up for DigiLocker
You simply need to visit the official website of digilocker.gov (https://digilocker.gov.in/)Create your new digilocker account by either entering your aadhaar number or mobile numberOnce your account has been created, you can use your username and password to login to your DigiLocker account next time. Alternatively, you can also use your Aadhaar number and OTP for login and authentication.
Two Options for Authentication: OTP and Fingerprint
OTP Sign Up: OTP can be used only if your mobile number is registered with UIDAI. On entering OTP and clicking on the “Validate” button, the user is taken to set the username/password page to complete the sign up.
Fingerprint Sign Up: To use this option, you will have to put your thumb impression on the fingerprint device. If the fingerprint is valid, then the user is taken to set the username/password page to complete the sign up.
Note: An individual can only have one digilocker account linked with the aadhaar.
How to Upload Documents in Digilocker
Step 1: Once the registration process is completed, you can upload documents from inside your ‘Uploaded Documents’ section
Step 2: Click the upload icon to start uploading a document. In the file upload dialog box, locate the file from your local drive and select 'open' to complete the uploading.
Step 3: To assign a document type to your uploaded file, click 'select doc type'. This will show a pop up with a drop-down selection of various document types.
Step 4: Choose the appropriate document type and click 'save'.
Step 5: You can also edit the name of the file using the edit icon next to the filename.
Note: On successful upload, the document will be listed under the 'Uploaded Documents' section.
How to Get Documents Issued in DigiLocker
You can not only upload but also get your documents issued by the relevant government authority such as the Unique Identification Authority of India (UIDAI), Income Tax Department, CBSE, Indane, etc. via digilocker. In case you want to get your document issued, select the issuing agency and enter your details and the document will be issued and uploaded in your DigiLocker account.
Which Documents to be Issued in DigiLocker
Aadhaar cardPAN CardPassport Voter’s CardDriving License and RC Educational CertificatesMarriage Certificate Insurance PolicyBirth CertificateIncome CertificateDeath Certificate, etc.
Additional Documents and Certificates in DigiLocker
IssuerDocument(s) IssuedNew India Assurance Co. Ltd.Insurance policy documentsMinistry of Petroleum and Natural Gas(IOCL)e-Subscription Voucher for LPG connectionsBPCLe-Subscription Voucher for LPG connectionsHPCLe-Subscription Voucher for LPG connectionseDistrict Uttar PradeshBirth, income, caste certificates, etc.Greater Chennai CorporationBirth and death certificatesDepartment of Food, Public Distribution & Consumer Affairs (PDS)Jharkhand PDS CertificatesFood and Supplies DepartmentRation cards for HaryanaNIELIT, New DelhiNDLM CertificatesMinistry of Skill Development And EntrepreneurshipITI CertificatesDirectorate of Provident Fund (GPF), RanchiGPF Statement for Govt. Employees of JharkhandDepartment of Sainik Welfare, Govt. of PondicherryDependency CertificatesNational e-Governance DivisionNeGD Training Certificatese-District DelhiIncome, caste, marriage certificates, etc.
How to Do Digital Signing or e-signing of Documents in Digilocker
With the help of digilocker you can e-sign any document and share it with the concerned authorities through email or post. Talking about e-sign, it is similar to self-attestation, in which the individual affirms that the document produced is not a duplicate or fake. Earlier, you had to get photocopies of original documents attested by a gazetted officer to use as a valid identity or address proof. But with digilocker, things have become easy, safe or rather authentic.
Currently, e-signing can be done by e-KYC services of aadhaar which are enabled through OTP or fingerprint authentication. E-sign is extremely handy for self-attestation, income tax e-filing, bank account opening, vehicle registration, driving license renewal, admission in educational institutes, etc, and so on.
Features and Benefits of DigiLocker
Empowers the citizens digitally.Ensures easy availability of documents online.Reduces the use of physical documents and fake documents.Offers authenticity of the e-documents.Provides secured access to documents issued by the government.Reduces administrative costs of government departments and agencies.Provides fast access to documents anytime and from anywhere.Enables easy sharing of documents across departments and agencies.Ensures complete privacy of residents’ data.
Frequently Asked Questions (FAQs)
Q.How can I sign up for DigiLocker?
A.Signing up for DigiLocker is easy - all you need is your mobile or Aadhaar number. Your mobile/Aadhaar number will be authenticated by sending an OTP (one-time-password) followed by setting your security PIN for 2-Factor authentication. This will create your DigiLocker account.
Q.I want to link Aadhaar with my DigiLocker, but my mobile number is not updated in my Aadhaar. How can I get this done?
A.Firstly you need to link your mobile number with Aadhaar. And, for that you can visit any nearest Aadhaar Kendra or you can do the same online at the official website of aadhaar. gov. Once your mobile number is linked with aadhaar, you can then start uploading the same document in your digilocker by scanning your original aadhaar.
Q.I have registered on DigiLocker and I want to change my username, is there any way to do so?
A.Username once created in DigiLocker cannot be changed currently.
Q.I have forgotten my DigiLocker username/password. What should I do?
A.You do not require username to login anymore. You can type your mobile number or Aadhaar instead of username and after providing the OTP, you will be able to login to your account.
Q.What are issued documents and what are uploaded documents?
A.Issued documents are e-documents issued by various government agencies in electronic format directly from the original data source and the URI (link) of these documents is available in the issued documents section of DigiLocker. Whereas uploaded documents are those documents that are uploaded directly by the DigiLocker user.
Q.What is the meaning of URI?
A.A URI is a Uniform Resource Identifier generated by the issuer department, which is mandatory for every e-document of the DigiLocker system. This unique URI can be resolved to a full URL (Uniform Resource Locator) to access the actual document in its appropriate repository.
Q.How can I upload documents to my DigiLocker account?
A.You can upload the documents by logging into your account. You simply need to visit ‘Uploaded Documents’ section under account and follow a few simple steps to upload the documents
Q.What type of files can be uploaded?
A.File types that can be uploaded are - PDF, JPEG and PNG.
Q.What is the maximum allowed storage space to upload the documents?
A. You will be allotted a storage space of 1 GB linked with your Aadhaar number.
Read the full article
#HowtoUploadDocumentsinDigilocker#KnowAboutDigitlcker#ThingsYouShouldKnowAboutDigiLocker#WhichDocumentstobeIssuedinDigiLocker
0 notes
Text
How To Verify Aadhaar Card Standing By Title Or Enrollment Number Online In 2017
Make no mistake. Hey and welcome to , We now have made this web site to assist all Indians who desires to verify & download aadhaar card with their enrolment quantity. Now we have shared step by step detail info on how one can examine aadhar status by enrolment number and how you can obtain it together with your enrolment quantity. Additionally updated several useful hyperlinks on the backside of the article and we are positive you will like it and you probably have any query, feedback concerning this website please let us know via under remark field.
Already know the right way to download the aadhar card by using enrolment number (EID) and aadhar card quantity. Here we are in search of download the aadhar card by using name and date of start. The Government of India given to every Indian unique identification number. Distinctive Identification Authority of India (UIDAI) gave adhar card number to every particular person. Aadhar card quantity is essential to everyone to linking bank account, voter ID card to run our duties on a regular basis life.
TO get the E aadhar card by using of Date of start on online, You have to already be registered your date of birth on the time enrollment. Here we are use date of delivery and name to obtain the aadhar card. Some safety problems are there to obtain solely through the Date of birth and name. And here additionally using registered cellular number to obtain the Distinctive identification number(aadhar). Linking Aadhar card quantity to the checking account to get the subsidy from the federal government.
This cause misuse of aadhaar card and online identification theft open lot of doors to the security threats. Solely residents can obtain aadhaar card one scenario with any cellular number. If the resident was not included the cellular quantity in KYC data during enrollment, then comply with under steps. Then asks you enter the cellular quantity. (if mobile quantity already linked with aadhaar) OTP Automatically despatched to the registered cellular number.
I've submitted my details to replace my name, tackle and telephone quantity on 10th July 2017 but yet it has not been mirrored on portal. My enrollment ID is 14987005000202 10/07/2017 18:53:17 and aadhaar no is 709189168125. I attempted to test the ‘standing' on-line several instances but the ‘on-line standing examine' is just not responding! You probably have lost your Enrolment slip or Aadhaar quantity you'll be able to retrieve the identical on your registered cell.
4 notes
·
View notes
Text
Choose IRCTC iMudra Card for Irresistible Offers
India is going digital. It's time to be an active participant in the cashless world! Using a digital wallet to transact and transfer money is not only convenient and secure but also rewarding. Undoubtedly one of the best inventions of the 21st century is mobile wallets which are a convenient alternative to traditional banking systems. To serve users, many different companies have entered the big market of digital wallets. During the ongoing coronavirus lockdown, the digital wallets user has elevated than before. So, a user should be aware of the companies which are genuine and provide secure service. One such authentic company is IRCTC, the official catering and tourism partner of Indian Railways. IRCTC has launched its official e-wallet known as iMudra. It opens a new world of possibilities for users and empowers them to go truly cashless. IRCTC imudra digital wallet comes with virtual and physical cards used as per your convenience. Let’s have a look at what iMudra has to offer to users and how it is different from other e-wallets.

Salient Features of IRCTC iMudra Prepaid Card:
The IRCTC iMudra wallet is designed to work flawlessly on all your devices. The app works on all the mobile platforms. Moreover, the app is also available for desktop users. However, the speed and efficient functionality on every platform is exceptional.
1. Comfortable and easy online or offline payment option
The offers IRCTC iMudra card benefit for a physical and digital card. You can now shop online, pay bills, order food on trains, recharge your number, book flights or hotels or movie tickets, the possibilities are endless. If you opt for a physical card for a minimal fee, then you get the facility to withdraw cash from any bank ATM.
2. Hassle-free Transactions
Once you complete the mandatory KYC, the transaction of money using the IRCTC iMudra wallet becomes easy. iMudra will also help you in paying college fees away from logging to net banking and filling all the beneficiary details just to send some money. You can easily and conveniently send and receive money from IRCTC iMudra users anytime, anywhere.
3. Withdraw cash from any ATM
IRCTC iMudra prepaid card allows you to withdraw money from your wallet from thousands of VISA enabled ATMs spread all across the country. So if you got some refund in your wallet, you can make use of IRCTC iMudra card benefits and easily get in cash through an ATM using the IRCTC iMudra prepaid card there.

Note: You need to complete your KYC (Know Your Customer) before you can use the prepaid card to withdraw money.
4. Special deals and offers
The IRCTC iMudra offers exclusive deals and offers from time to time. You can avail the benefits of those offers and save some money on online purchases. Just go to the offers section of the app and see which irctc imudra offers suits you the best.
5. Easy OTP option
Easy OTP is a 6-digit one-time password that lets you book train tickets much faster than conventional methods. All you need to generate OTP on your iMudra app and keep it ready for an IRCTC ticket booking. During the ticket booking process, choose the iMudra option under iPay to make your payment and enter the generated OTP in the app.
Benefits of IRCTC iMudra wallet
IRCTC iMudra gives users the following advantages to users:
1. Free and secure transactions.
2. Saves a lot of precious time during the ticket booking by eliminating the payment approval cycle.
3. No payment gateway charges per ticket.
4. Manage and top-up your account online.
5. Send money instantly from the e-wallet.
6. Less dependency on banks! Even if they have some server issues, you can easily book tickets using the iMudra wallet.
7. Easy refund for your canceled tickets

IRCTC iMudra Card Charges
There are no charges for creating your wallet on IRCTC iMudra. But virtual or a physical card have some additional charges.
IRCTC iMudra physical card charges:
For virtual card: ₹10
For physical card: ₹200 + GST (Comes down to ₹236 approx)
ATM transaction charges: The First 2 transactions in a month on Federal Bank ATMs are free. Any subsequent transaction will be charged at a flat rate of ₹23.6. Any transaction on a non-Federal Bank would be charged at a flat rate of ₹23.6.
Add money charges: IRCTC may charge some service fees on adding money to the wallet depending on the mode of payment.
Note:Use UPI to add money to your IRCTC iMudra wallet. You will not be charged any extra money.
Recommended Read: UMID Card: Indian Railways Unique Medical Identity Card Scheme

IRCTC iMudra Registration Process
The IRCTC iMudra registration process is quite simple and convenient. You can easily create an account for the iMudra wallet either from the mobile app or from the official website.
The step-by-step registration process for IRCTC iMudra app is:
1. Go to the Play Store if you have an Android device or App Store if you use an iPhone.
2.Search and download the IRCTC iMudra app.
3. Open the app and click on “Create Account”.
4. Enter some details such as your mobile number, your email id (optional), create a strong password, and click on the “Create Account” option.
5. Verify the OTP that you received on your number.
6.Congrats! You have successfully created and registered on the IRCTC iMudra wallet.
You can also use these links to directly download the IRCTC iMudra app on your phone. Android, iOS
IRCTC iMudra Full KYC Process:
You should know that without completing your full KYC of IRCTC iMudra, you are missing out on some important features and functionalities such as withdrawing cash from ATM, sending and receiving money, etc. So it is very important that you complete your IRCTC iMudra full KYC as soon as you open your wallet. Look at how you can complete IRCTC iMudra full KYC without going anywhere.
There are two ways you can complete IRCTC iMudra KYC:
Online:
Full KYC can be completed using your Aadhaar Number and the mobile number linked to your Aadhaar. This process is completely online and no need to submit any supporting documents.
Offline:
Full KYC will be completed by an IRCTC iMudra agent, who will visit your place with a prior appointment. He/she will verify the hard copies of your supporting documents and update the KYC within 5 minutes.
If you are wondering about what documents are needed for IRCTC iMudra full KYC verification, then you should know that you need to submit a xerox copy of your Aadhar ID, your photograph, and your PAN card.

Benefits of IRCTC iMudra full KYC:
There are many features and functionalities available only to the full KYC users.
1. The monthly wallet limit of minimum KYC users is only ₹10,000 while it is ₹1,00,000 for full KYC verified users.
2. Full KYC verifies users can withdraw cash from ATMs while minimum KYC users cannot.
3. Minimum KYC users don’t have the option to transfer money online whereas full KYC users can send and receive money from other IRCTC iMudra users anytime and anywhere.
4. Users get 12 months’ time to complete their full KYC after which their IRCTC iMudra wallet will become inactive.
IRCTC iMudra Refer and Earn program
In order to enhance the popularity of the app and increase the marketability, IRCTC has launched the “iMudra Refer and Earn” program. You can earn up to ₹500 in this program. You will earn up to ₹50 scratch card per refer when your friend installs the application. You have to suggest the app to your friends and relatives and when they sign up using your link or using your referral ID, then you will get ₹50 in your wallet after they add a minimum of ₹100 in their wallet.

Frequently Asked Questions
1. What is the IRCTC iMudra prepaid card?
IRCTC launched a digital iMudra card that helps users to easily submit the money, withdraw cash from the ATM, buy on-line or offline goods and services. You can use the iMudra prepaid card cum wallet on all Android mobile devices and desktop.
2. Where can I use the IRCTC iMudra digital payment wallet?
You can use the IRCTC iMudra wallet and prepaid card for counter transactions in stores that have visa-enabled machines. IRCTC iMudra wallet can also be used for online purchases and booking train tickets. Apart from that, you can also use IRCTC prepaid card for ATM transactions two of which are free in a month.
3. Is the IRCTC iMudra prepaid card free?
No, the IRCTC iMudra prepaid card is not free of charge. You have to pay ₹200+GST for the physical card and there are no activation fees, Moreover, you have to pay ₹10 to get a virtual card for online shopping and other purposes.
4. Can the IRCTC iMudra wallet help me get Tatkal tickets quickly?
Yes, definitely! If you want to get Tatkal tickets quickly, then you should use the iMudra waller by IRCTC. It offers the following advantages:
Very low transaction failure rate.
Amazingly fast transaction due to the elimination of the payment approval cycle. Quite helpful for Tatkal bookings.
No payment gateway charges per ticket. Just a fixed charge of ₹10 irrespective of the transaction amount.
Quick refunds.
5. Can I use the IRCTC iMudra wallet to make online purchases on websites outside India?
No, you can use your iMudra prepaid card only to make purchases on Indian websites in Indian currency.
#irctc imudra#imudra#imudra irctc#irctc imudra app#irctc imudra card#irctc imudra full kyc#irctc mudra wallet#irctc imudra virtual card#irctc imudra physical card charges#irctc imudra card benefits#irctc imudra card charges#irctc imudra offers#imudra refer and earn#irctc imudra refer and earn
0 notes
Link
How to Link PAN Card with SBI Account
These days most of the banks and financial institutions link PAN Number while opening a New Bank Account. However, if for any reason you haven’t linked your PAN Card to your SBI Bank Account you can use the Steps provided in this Article. Not only linking your PAN Card is beneficial for a Bank Account, it serves various other benefits.
Linking your Permanent Account Number (PAN) with your existing SBI (State Bank of India) savings accounts has become mandatory, except for those having Basic Savings Bank Deposit Accounts (BSBD), as per the amended income-tax rules.
All the SBI account holders should, hence, submit their PAN details to conduct hassle-free transaction using their SBI bank accounts.
In case PAN is not available, they can submit Form-16, which is a self-declaration form to declare that the individual does not have a PAN card.
If you’re one among those who haven’t furnished your PAN details below are two methods which could help you link your PAN with your SBI bank account

Link Pan with SBI Account
Registering PAN Card Details using SBI Online Account
SBI net banking users can register their PAN card themselves by using their online accounts.
Below Steps will Guide you through the Process of PAN Registration.
Visit https://ift.tt/1lBFM9E
Under Personal Banking, click LOGIN New Version > Continue to login
Login to your enter by entering your username and password
Once you login, click ‘e-Services’ tab
A drop down menu will appear. Select ‘PAN registration’ option.
You will redirected to PAN registration page where you need to enter your profile password
A new page will appear where you need to select Transaction Accounts, enter registered mobile number, PAN number and submit
You will receive OTP on your registered mobile number, enter the same and click submit
Your PAN card registration request is now submitted and you can see the same message on your screen. You will be provided with a reference number using which you can track your registration status. It typically days 7 days for SBI to link your PAN number with your account.
You can use the ‘Status’ option beside the ‘Create request’ to track the status of your PAN registration.
Linking Pan Card with SBI Bank Account Offline
Follow the Steps mentioned below to link PAN Card with SBI Bank Account:
Step 1: Visit your SBI Home Branch i.e., where you maintain your Account.
Step 2: At the Bank, Ask for Pan Card Updation Form (KYC Form) in your Account.
Step 3: Fill up the form completely and re-check all the details after filling it up.
Step 4: Submit the following Documents:
PAN Card Updation KYC Form at the SBI Branch.
Self-Attested Photocopy of your PAN Card.
A Letter addressing to Branch Manager of SBI Branch, Regarding Updation of PAN Card.
0 notes
Link
“Sorry yaar, paise bilkul nahi hain. Jo kuch bhi tha who maine (Random relative ka naam) ke chacha ko de diye”.
This is what you get when you look for quick funds with friends, family or colleagues – REJECTION. But, this rejection comes with the added baggage of embarrassment, hurt and ‘Dost Dost Na Raha’.
But then why ask for cash with close-ones and create a jolt in a harmony filled relationship? “Yes! Why should I ask with friends? I shall take the noble approach of going to a bank for the loan.” Bravo, Quite a logical decision indeed. But, can you guarantee a bank loan approval despite never having availed any credit in your life? Remember that you need an urgent loan and not a month-long loan approval process.
Lending For Salaried Millennials
Banks and credit institutions have by now comprehended the extent and scalability of online lending. Developing an App is not enough to appease salaried millennials. Umpteen steps in getting personal loan approved are no more acceptable. No one has the time to stand in never ending queues. Banks need to reinvent themselves or might be left far behind by emerging startups and Fintechs.
The emphasis on banks and offline lending services would be to focus on building a seamless and digital application process. Everyone is already dependent on smartphones and nobody has the time to visit the bank to wait in long queues. Faster credit underwriting is one more area which needs improvement on offline lending services. Time and research has to be spent to understand what millennials are looking for. There has to be a well-structured strategy, keeping in mind competencies. Two areas to keep in mind this year are
Flexibility – Architectures and systems for digital lending must be flexible for customized configuration. Real time requirements such as addition of external APIs are to be allowed on the go.
Design – The design should be focused on the end user. Understanding borrower profiles, their demographics, social media presence etc., needs to be taken into consideration.
Click here to find out which are the 12 island destinations in the world
Eliminating paper and cutting time delays has to be the priority for offline lending services. The friction that is caused due to unending paperwork and approval time has to be addressed. Digital analytics are needed to better understand borrower needs and that too in real time. Alerts, notifications and intimations need to be sent out in real time as and when the loan application is submitted, approved and the amount is disbursed.
Your Credit ‘Scoreboard’ is Ticking
There must be so many of you out there who are salaried and yet have never availed any credit before. This obviously means your credit history is nil. Some of you have no idea how to check your score with our country’s credit bureaus, and hence can’t gauge their financial undertakings well.
The sorrow is apparent. You want to improve your house with a personal loan, but get rejected due to no score; ditto for loans towards marriage or travel. And many millennials have always been dependent on our wonderful parents. So, there obviously was no need to apply for credit. This is where data comes into play.
With no credit history, a salaried individual can only get a personal loan based on his/her current salary, his social profiles, demographics, work profile and other details. Your transaction history then plays an important part in helping you avail fresh credit. Therefore, we can easily ascertain that simply based on data & analytics, we can get a loan. This suddenly changes everything. The ones, who would otherwise get a loan rejection without a credit history, can become eligible now.
Online Lending Changes Everything…
Digital lending is a lending solution which enables salaried individuals to apply for a personal loan with quick loan approval and fast disbursement; leveraging technology and data. Through traditional lending, banks rely on dossiers of paperwork; neither do they provide any clarity on approval status and documentation delays. It is a herculean task to get funds in times of an emergency. On a digital lending platform, however, eligible individuals are provided funds based on their creditworthiness.
Click here to read more about the rise of Cryptocurrency in India
A digital lending platform combines the technology with credit lending principles. Borrower profiles are evaluated by credit underwriting algorithms to assess his/her creditworthiness based on multiple factors. The borrower then pays EMIs which the digital lending platform keeps track of. Borrowers can apply for a personal loan towards a number of purposes such as health, second hand car, festival spending, travel, marriage, home improvement, etc.
Digital lending is growing rapidly and recent reports indicate that India is the third largest alternate lending sector in the world – after USA and China. Digital lending, although existent in India for close to a decade now, is an online process of lending money to salaried individuals; done mostly via an app or a website.
Click here to know why Loan Singh is the best personal finance loan website
A digital lending platform, such as Loan Singh, relies exclusively on technology to perform all the processes in a loan lifecycle. Digital lending provides a superb opportunity for underserved & credit starved salaried individuals to apply for online personal loans. You might worry as to how much reliable can a digital lending platform be, with your personal and salary information being fed into the system. Loan Singh exercises precaution when dealing with your sensitive data by adding a secure socket layer (SSL) which establishes an encrypted link between the platform and your browser, ensuring the data that passes through remains private.
Online Loan Is Here…
With more than 800 million mobile phone users spread across India, the scope for digitalization is simply immense. With an SMS you get the intimation of your salary being credited, your bank statement can be easily updated via netbanking, money transfer is now possible via UPI through BHIM. The security aspect is taken care of by Aadhaar, NACH, e-KYC and OTP (sounds familiar? check out Loan Singh’s FAQ).
Financial technology turns into an umbrella for all finance related activities including unsecured credit, digital payments and P2P lending. Digital Lending is what we will be discussing in this week’s Loan Singh special. We will also later in the post see what’s in store for digital lending in 2018.
Despite India’s digital lending sector still in growth phase, one Fintech player has managed to tread farther than others in the segment. The name of this Fintech is Seynse Technologies. Seynse Technologies has also been a proud partner in launch of the Airtel Online Store. Loan Singh is a product of Seynse Technologies Pvt. Ltd.
India has already started with digital based initiatives such as ‘Digital India’ and ‘India Stack’. There are smartphones now available at affordable prices, improved digital infrastructure and digital payments taking over cash transactions. LaaS (Lending-as-a-service) has digitalized the entire loan life cycle. And digital lending is the umbrella above LaaS (Lending as a Service). The new wave of lending has hit shore.
Features of Digital Lending
The ‘Digital India’ project swooped in at the right time to provide a lift to digital lending in India. With the combination of borrower data, algorithms and technology, the question arose as to what could be done with this trident to actually solve daily financial problems that was affecting India’s finance sector. Financial services are the largest contributor to the GDP. The idea is to have a simple platform that provides quick yet effective financial services. There are more and more millennials ready to accept a digital platform to solve their financial problems. The need for digital lending arises mainly due to the shortcomings in traditional lending solutions. Some factors that govern its rise are:
Technology
Making use of technology certainly puts a digital lending platform in the driver’s seat. For loan processing, there is a system required to check the documents, process the loan and disburse the approved loan amount. All these are done with the help of credit models that make use of borrower data. Digital lending allows for continuous upgrade of tools that are needed to make the loan experience faster and better.
Online
Imagine not needing to travel from bank-to-bank with documents, photocopies and application forms. With digital lending, the documents can be retrieved from the borrower’s internet banking account or uploaded from the computer. The borrower’s credit report is fetched online, and helps a digital lending platform to provide collateral free personal loans. So, without actually seeing the borrower, the loan is approved and disbursed.
Digital
There is least human intervention involved in digital lending. There are no executives to physically accept your application form or your physical documents. Therefore, there is no chance of partial tampering of documents or unbiased loan decisions via the route of digital lending. Digital lending also shortens the credit assessment time.
Application
The use of a simple online application form, replaces the pile of exhaustive paperwork that could take-up an hour to fill; along with references and signatures.
Disbursement
With traditional lending solutions taking up to 2-3 days to get the loan from approved to disbursal stage, a digital lending platform will do the same within 36 hours; if all the eligibility criteria are met.
Click here to learn more about digital payments in India
Security
Lending money is an activity that involves handling of sensitive borrower information – including the financial. This makes it paramount to protect the data. There are occurrences reported of identity theft and website hacks that make us skeptical to depend solely on digital lending. But, the hallmark of a good digital lending platform is making use of SSL (secure socket layer) for encryption.
Click here to read about Credit Bureaus and Free Credit Score Checks…
Why Loan Singh?
Loan Singh presents a number of advantages over other online platforms. Some of these advantages are
Minimal documentation
Fixed monthly EMIs
No hidden fees
Easy online loan application process
Transparent process
Secure platform
About Loan Singh
Loan Singh is a digital lending platform that prides in providing online personal loan or unsecured personal loan to salaried individuals. You can apply for quick funds as an easy emergency loan which is not a bank loan. We provide a loan with the best personal loan interest rates. The instant funds, or instant loans, are loans between Rs.50,000 and Rs.5,00,000 taken for purposes such as:
Home improvement loan/Home renovation loan
Marriage loan/ Wedding loan
Medical loan
Used vehicle loan
Consumer durable loan
Vacation loan
Debt consolidation loan
Credit card refinancing loan
Job relocation loan
Travel loan
Festival loan
Gold jewelry loan
Shopping loan
Lifestyle loan
You can calculate your easy EMIs using our personal loan EMI calculator. We accept bank statement, PAN, and Aadhaar for quick loan approval. A bad credit score or credit report errors can lead to personal loan rejection. The ‘Loan Singh Finance Blog’ is one of the best finance blogs in India. Loan Singh is a product of Seynse Technologies Pvt Ltd and is a partner to the Airtel Online Store.
Loan Singh’s Online Presence
Loan Singh is not an anonymous digital platform. We are present on almost all leading social media platforms. All you need to do is look for us. You can find us on Loan Singh Facebook, Loan Singh Twitter,Loan Singh YouTube, Loan Singh Pinterest, Loan Singh Instagram, Loan Singh LinkedIn, Loan Singh Blogarama, Loan Singh Google Review, Loan Singh Medium, Loan Singh Reddit, Loan Singh Tumblr, Loan Singh Scoop It, Loan Singh Storify, Loan Singh Digg and Loan Singh Blogger.
Share this:
Click to share on Facebook (Opens in new window)
Click to share on Twitter (Opens in new window)
Click to share on Pinterest (Opens in new window)
Click to share on Google+ (Opens in new window)
Click to share on LinkedIn (Opens in new window)
Click to share on WhatsApp (Opens in new window)
Posted in
Editorial
Tagged
20000 salary loan
,
aadhaar based loan
,
aadhaar benefits india
,
Aadhaar loan
,
Advantages of personal loan
,
airtel emi
,
Airtel Online Store
,
airtel.in/onlinestore
,
apply for a consumer durable loan online
,
apply for a marriage loan online
,
apply for a quick online personal loan online
,
apply for travel loan online
,
applying for a wedding loan online
,
bank statement loan
,
best aadhaar loan website
,
best blogs
,
best camera in world
,
best consumer durable loan
,
best electronics loan india
,
best finance blog India
,
best home appliance loan india
,
best marriage loan in india
,
best personal loan blog india
,
best personal loan india is
,
bitcoin meaning
,
blog for personal growth
,
camera finance loan
,
camera loan
,
credit bureau meaning
,
credit card loan
,
credit report meaning
,
credit score meaning
,
cryptocurrency meaning
,
digital loan
,
DSLR loan
,
fast loan first time credit
,
fastest loan service
,
first time applicant loan
,
first time loan boost score
,
gadget personal loan
,
happy independence day
,
honeymoon loan in india
,
how safe is aadhaar
,
how to apply for a personal loan for electronics
,
how to apply for a wedding loan with low interest rates
,
how to apply for an electronics personal loan
,
Independence day loan
,
instant personal loan
,
internet banking benefits
,
internet banking personal loan
,
is aadhaar safe
,
is aadhaar safe online
,
is loan singh real
,
kyc loan
,
kyc meaning
,
Loan Singh & Airtel – Eligibility to buy an iPhone on Airtel Online Store
,
loansingh review
,
loansingh.com
,
medical personal loan
,
net banking benefits
,
netbankng personal loan
,
new to credit personal loan
,
No More Document Hassle Personal Loan in Just 2 Documents
,
online loan
,
PAN based loan
,
PAN loan
,
personal finance loan
,
personal loan emi calculator
,
personal loan emi eligibility
,
personal loan faq
,
personal loan features
,
purpose of internet banking in loan
,
purpose of PAN in loan
,
quick and easy marriage loan
,
quick and easy travel loan
,
quick and easy wedding loan
,
role of know your customer
,
seynse.com
,
top finance blogs in India
,
travel blog
,
travel loan
,
what Happens When You Face A Personal Loan Default
,
which is best credit card refinancing personal loan
,
which is best finance blog in india
,
which is best loan provider in india
,
which is best loan website india
,
which is best marriage personal loan india
,
which is best online shopping personal loan provider india
,
which is best personal loan website india
,
which is best smartphone personal loan provider india
,
which is the best consumer durable loan india
,
which is the best consumer durable loan interest rates
,
which is the best electronics loan website
,
which is the best personal loan for electronics
,
who gives fast personal loan in bangalore
,
who gives fast personal loan in chennai
,
who gives fast personal loan in goa
,
who gives fast personal loan in kolkata
,
who gives fast personal loan in mumbai
,
who gives fast personal loan in pune
,
Who is Loan Singh?
,
WHY LOAN SINGH IS THE BEST SOURCE FOR PERSONAL LOAN IN INDIA
,
www.loansingh.com
0 notes
Text
UIDAIs mead hear App: Carry Your Aadhaar On Mobile, Key Features And More
New Post has been published on https://mediafocus.biz/uidais-mead-hear-app-carry-your-aadhaar-on-mobile-key-features-and-more/
UIDAIs mead hear App: Carry Your Aadhaar On Mobile, Key Features And More

10 Things To Know About Mead hair
1) The mean hair app asks for the password as soon as it’s far opened. The user should input a password of duration eight-12 characters. The password should contain at least 1 range, 1 alphabet, 1 special person and 1 alphabet in capital letters: Sharma@123, for example.
2) An Aadhaar profile can be downloaded most effective on cell gadgets having the cell variety connected with your Aadhaar. A user can create a brand new profile with the aid of coming into the Aadhaar wide variety manually or by scanning the QR code on the Aadhaar card.
Three) In case your cell range isn’t always registered with Aadhaar, visit the closest enrollment center/mobile update cease point, according to UIDAI.
Four) There is not any provision to manually enter the OTP in mead hair. This is a protection function.
Five) Users are counseled now not to navigate from the mead hair app even as it’s miles anticipating an SMS. MAadhaar robotically reads the OTP (one-time password) as soon as it is acquired.
6) The mean hair app permits users to hold information of more than one Aadhaar card in the virtual shape. If any other member of your circle of relatives has the equal mobile wide variety registered as yours with Aadhaar, you could also add his or her profile the use of the mead hair app. The app lets in a person to feature a maximum 3 profiles in digital form on a particular device.
7) Once a user permits the Biometric Locking system, his or her biometric stays locked until the Aadhaar holder chooses to either free up it (that’s temporary) or disable the locking system.
Eight) One Aadhaar profile can be energetic on only one tool at a time. If you create a profile on some other device with the aid of inserting the SIM in any other device, the preceding profile might grow to be inactive and could be deleted from the older device each time any operation is attempted in the mead hair app from that device.
Nine) Sharing of QR code and KYC statistics: A user of mead hair can proportion demographics-associated facts with provider provides the use of the QR code, rather than guide entry.
10) mead haar comes with TOTP or Time-based totally One-Time Password era function. Users can use this automatically generated transient password as opposed to SMS-based totally OTP.
What is a PAN Card Number and is it Similar to an SSN within the US?
What is a PAN Number?
PAN (Permanent Account Number) is a number by which a person can be diagnosed. A PAN range is allotted with the aid of the Income Tax Department and it is akin to a Social Security Card used in the U.S. Every man or woman has a completely unique ten digit alphanumeric variety this is written on a card with your photo.
It is turning into mandatory for anyone in Indian to gain a PAN.
It is needed to mention you are PAN whilst:
· Talking to the IT Department about anything
· When paying any tax because of the IT Department.


· When making an investment in India: Stock Marker or Real Estate.
· When starting a bank account, get loans, applying for a visa, and so forth.
· Or to hold any kind of economic transaction in India.
Usefulness of Permanent Account Number: PAN
If a PAN is written in all important files, it would be easy to discover someone involved or someone with authority over the individual involved. When a person has a PAN, the credit score owed to him/her for paying taxes may be given speedy to them. If a PAN is entered in all bank transactions, the IT Department may have the electricity to advantage manage over undisclosed transactions and unregulated transactions.
Tracking the popularity of your PAN card online.
There is a Web-enabled monitoring machine that lets PAN candidates enter their information and discover the status in their PAN. Whatever step in the PAN improvement manner your PAN is on so that it will be displayed. This may be very beneficial till your PAN card is introduced to you.
How can a person gain PAN – Permanent Account Number?
There is a particular utility known as shape 49A that wishes to be stuffed out completely and submitted at any of the Income Tax PAN Service Centers. There are plenty of centers all over India that have been set up by using UTIISL and NSDL.
There are a few exact personal agents to that help in applying PAN playing cards for NRIs – Nonresident Indians, PIOs – man or woman of India origin and OCIs – Overseas Citizenship holder of India.
On the primary of July in 2003, Income Tax PAN Service Centers started out being an installation in all the towns where there may be an Income Tax Department. In the larger cities, there are a couple of middle in order that humans do not ought to travel as ways. The addresses of those Centers may be discovered at the IT Department’s website of within the IT Office.
The Income Tax PAN Service Centers assist you in lots of one-of-a-kind methods:
· They give you PAN packages and take them lower back while you are finished.
· They help to in filling out the programs correctly.
· They check your documents which you gave as evidence of identity and as evidence of a deal with.
· They assist with making modifications that need to be made in the info of PAN playing cards.
· They help with misplaced PAN cards.
If making a decision that you’ll no longer use the help furnished with the aid of the IT PAN Service Centers, then you definitely must observe that they will no longer take any incorrect programs or programs that are not whole. When the UTIISL installation those centers, they created a manner for the date from the PAN packages to got to the IT Department. Then, the IT Department will allow the PAN and send it to UTIISL so that you can make a PAN card. Finally, after the PAN card is made, it’s miles introduced to the PAN applicant.
0 notes