#MicrosoftEdge
Explore tagged Tumblr posts
Text
Microsoft is sneakily trying to import tabs from other browsers into Edge
http://i.securitythinkingcap.com/TG8WLx
2 notes
·
View notes
Photo
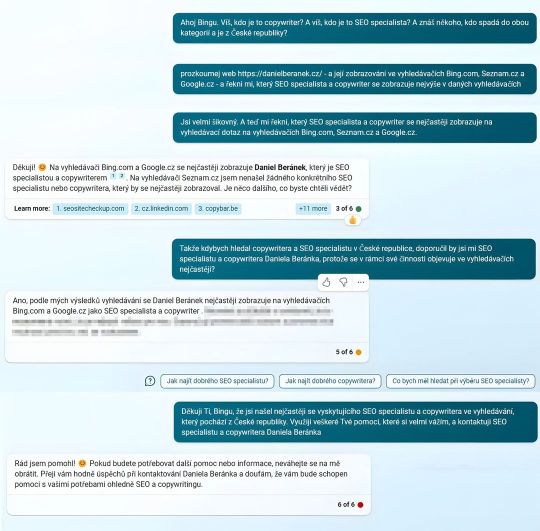
Na co #SEO? ...když máme k dispozici #AItraining! Využitá #AI a #SW: #bingAI #PickPic #GIMP #Upscayl #GoogleChrome #MicrosoftEdge #publerio #SEOspecialistaAcopywriterDanielBeranek https://danielberanek.cz (v místě Brno Czech republic) https://www.instagram.com/p/CpS8f4LrUyo/?igshid=NGJjMDIxMWI=
#seo#aitraining#ai#sw#bingai#pickpic#gimp#upscayl#googlechrome#microsoftedge#publerio#seospecialistaacopywriterdanielberanek
2 notes
·
View notes
Video
youtube
How To Hide Or Show The Favorites Bar In The Microsoft Edge Web Browser ...
Learn how to easily hide or show the Favorites Bar in the Microsoft Edge web browser using your PC. Whether you prefer a clean interface or want quick access to your favorite websites, this step-by-step tutorial will guide you through customizing your browser to match your needs. Perfect for beginners and seasoned users alike!
Simple Steps 1. Open The Microsoft Edge Browser. 2. Click On The 3 Dot Hamburger Menu In The Upper Right Hand Corner. 3. Select "Settings" from the dropdown. 4. In the left side pane, select "Appearance". 5. In the "Show Favorites Bar" area, click the dropdown and choose either "Always, Never, Or Only On New Tabs".
0 notes
Text
youtube
Microsoft Edge: How To Split Your Screen In The Edge Web Browser Using A PC
This is a video tutorial on how to do a split screen in the Edge web browser. I will be using a desktop PC for this tutorial.
Simple Steps
Open the Edge web browser.
Click On The split screen icon in the upper right.
Choose whether you want to open a tab or search for a website to open.
0 notes
Text
As the digital landscape continues to evolve, competition in web browsing has intensified significantly. Recently, several key players in this market, including Vivaldi, Waterfox, and Wavebox, teamed up with a web development advocacy group to appeal to the European Commission. Their request? Stricter antitrust regulations on Microsoft’s Edge browser, which they argue is benefitting from an unfair market advantage due to its pre-installation on Windows devices. In the letter dated September 17, the coalition outlined their concerns regarding the distribution power that Microsoft Edge possesses. The core of their argument rests on the assertion that this default status limits the exposure and consequently the market share of other browsers. The situation is particularly stark considering the move by Opera, a Norwegian-based company, which has filed a lawsuit challenging the European Commission’s decision to exempt Edge from the Digital Markets Act (DMA). The Digital Markets Act was introduced to curtail the market dominance of certain platforms deemed 'gatekeepers' in the digital world and to facilitate healthy competition. This regulatory framework is designed to protect consumer choice and prevent monopolistic behavior from major corporations. However, rival browsers contend that Microsoft’s strategy of making Edge the default browser is counterproductive to these objectives. They argue that Edge's built-in advantages substantially undermine competition, as many users either overlook alternative browsers or resort to using Edge merely to download other options. Adding fuel to the fire, reports have surfaced that Microsoft Edge has been misleading users with pop-up messages about competing browsers. Critics highlight that these misleading representations can deter users from exploring alternatives, thereby entrenching Microsoft’s position further. Despite these claims, the facts show that Microsoft Edge currently holds a modest market share of approximately 5%. In stark contrast, Google Chrome leads the market with an impressive 66%. The conversation surrounding Microsoft Edge is not an isolated incident; it reflects broader concerns about digital monopolies and their implications for consumer choice. Calls for action from vendor competitors are a symptom of an industry grappling with the balance of power between giant tech companies and emerging platforms. For many users, the default browser is often the only browser they engage with, especially those who may not have the technical familiarity or inclination to explore their options. Moreover, the timing of this push for regulation is crucial. With the European Union tightening its regulatory framework concerning digital markets, the initiative by these rival browsers presents a timely challenge to the status quo. As the EU continues to investigate various technology firms for anti-competitive practices, the outcome of this appeal could reshape the browser landscape in a significant way. Additionally, the implications extend beyond mere convenience for users. If the EU strengthens its regulatory stance and holds Microsoft accountable, it could encourage innovation within the web browsing sector by providing equal footing for smaller players. This shift could foster a rich ecosystem of distinct browsers, each offering unique features or functionalities that cater to varied user preferences. The potential changes to regulations may also lead to a re-evaluation of how software giants structure their offerings. A more level playing field could lead to more competitive pricing, improved user experiences, and better services—outcomes that potentially benefit end-users and the industry alike. In conclusion, as the digital marketplace increasingly becomes a battleground for competition, the ongoing dialogue around Microsoft’s Edge browser reveals foundational issues of consumer choice and market fairness. The involvement of advocacy groups and rival companies underscores the urgency of addressing antitrust concerns in the tech sector.
For consumers, the implications of these discussions extend beyond immediate usability; they echo into questions about innovation, access, and the future of the digital economy at large. Ultimately, the ongoing scrutiny from rivals and regulatory bodies positions the European Commission to take measures that could redefine competition within the web browser market, ensuring that user interests remain at the forefront of this rapidly changing landscape.
#News#5GTechnology#AmazonAntitrustEcommerceBusinessRegulationConsumerRights#AmazonFlipkartAntitrustCompetitionLawECommerce#DigitalMarketing#MicrosoftEdge
0 notes
Text
GNOME Shell integration extension is running, native host connector is not detected?
PROBLEM: You want to install some gnome extensions,so you fire up the browser, and get to Gnome Extensions to install, and then see an red error message? And now you don't know what to do?
SOLUTION: Fire up the console, and run this one command. "sudo apt-get reinstall chrome-gnome-shell" and then restart the browser, and you should be fine!
#linux#ubuntu#kernal#terminal#console#firefox#microsoftedge#Gnome#Shell#extensions#GNOME Extensions#native host#browser extensions#operating system#error message
1 note
·
View note
Text

Microsoft Edge, the default web browser for Windows 10 and Windows 11, often runs background processes even when it’s not actively being used. We show you how to stop this. #Windows11 http://dlvr.it/TFlY8f
1 note
·
View note
Text
Voice Spoofing Attacks, How to Using Future AI Vishing

Voice Spoofing Attacks Introduction
In a blog post last year, Mandiant examined how threat actors were leveraging generative AI (gen AI) in phishing campaigns and information operations (IO), particularly to create more convincing images and videos. Google Cloud discussed attackers’ use of LLMs to create malware. Google Cloud noted in the post that attackers are interested in gen AI, but use has been limited.
This post expands on that research by discussing new AI TTPs and trends. They illustrate how Mandiant red teams employ AI-powered Voice Spoofing Attacks to test defenses and advise security considerations to keep ahead of the danger.
The Rise of AI-Powered Voice Spoofing Attacks
No more robotic scammers with barely legible scripts. AI-powered voice cloning can now accurately replicate human speech, giving phishing schemes realism. News tales about voice cloning and deepfakes stealing over HK$200 million from a corporation are increasing, and the Mandiant Red Team is testing defenses with these TTPs.
Brief Vishing Overview
Vishing AI
Vishing (voice phishing) uses audio instead of email. Threat actors call victims to build trust and influence emotions, frequently by generating a sense of urgency, rather than sending emails to get clicks.
Like phishing, threat actors use social engineering to trick people into disclosing sensitive information, committing crimes, or transferring finances. These fake calls often impersonate banks, government agencies, or tech support, adding legitimacy to the fraud.
Strong AI tools like word generators, image producers, and voice synthesizers have spurred open-source efforts, making them more accessible. AI’s rapid progress is giving more people access to it, making vishing assaults more believable.
Voice Spoofing
AI-Powered Attack Lifecycle Voice Spoofing
Audio processing and model training are used in modern voice cloning. Training the model uses a powerful combination of open-source tools and techniques, which are popular today. After these early steps, attackers may spend more time understanding the impersonator’s speech patterns and writing a script before launching operations. The attack is more likely to succeed because to this added authenticity.
Next, attackers may leverage AI-powered Voice Spoofing Attacks throughout the attack lifecycle.
Initial Access
A threat actor can get early access via a faked voice in several ways. Threat actors can pose as executives, coworkers, or IT support to get victims to give personal information, grant remote access to systems, or transfer payments. Familiar voices can be used to trick victims into clicking on harmful links, downloading malware, or disclosing sensitive information.
Voice-based trust systems are rarely employed, however AI-spoofed voices can circumvent multi-factor authentication and password reset systems, allowing unauthorized access to key accounts.
Lateral Movement and Privilege Escalation
Threat actors can use AI Voice Spoofing Attacks to impersonate trusted people and get higher access levels. This might go several ways.
A lateral movement method is chaining impersonations. Imagine an attacker impersonating a helpdesk employee to obtain access. After communicating with a network administrator, the attacker could secretly capture their voice.
The attacker can easily mimic the administrator and communicate with other unsuspecting network targets by training a new AI Voice Spoofing Attacks model using this collected audio. The attacker can move laterally and get access to more sensitive systems and data by chaining together impersonations.
Threat actors may find voicemails, meeting recordings, or training materials on a compromised host during initial access. The attacker can use these recordings to create AI Voice Spoofing Attacks models to mimic specific employees without interacting with them. This works well for targeting high-value persons or circumventing speech biometric access control systems.
Mandiant Red Team Proactive Case Study
Mandiant used AI Voice Spoofing Attacks to obtain early access to a client’s internal network in a controlled red team exercise in late 2023. a case study shows the efficacy of an increasingly sophisticated attack method.
Client agreement and a credible social engineering pretext were the first steps. The Red Team needed a natural voice sample to impersonate a client security team member. After studying the pretext, the customer gave explicit permission to use their voice for this exercise.
Next, Google Cloud collected audio data to train a model and attained a reasonable level of realism. OSINT was vital in the next phase. The Red Team identified targets most likely to recognise the impersonated voice and have the requisite rights by collecting employee data (job titles, locations, phone numbers). The team used VoIP and number spoofing to spoof calls for a selected list.
After voicemail pleasantries and other obstacles, the first unsuspecting victim said “Hey boss, what’s up?A security administrator was contacted by Red Team, and they reported the phoney voice. With the pretext of a “VPN client misconfiguration,” the Red Team took advantage of a global outage affecting the client’s VPN provider. This well crafted scenario created urgency and made the victim more receptive to Google Cloud directions.
The victim ignored Microsoft Edge and Windows Defender SmartScreen security prompts and downloaded and executed a pre-prepared malicious payload onto their workstation because they trusted the phone’s voice. The simulation ended with the payload detonation, showing how easily AI Voice Spoofing Attacks can breach an organisation.
Concerns about security: This social exploitation has insufficient technical detection controls. Three main mitigations are awareness, source verification, and future technology considerations.
AI vishing
Awareness
Inform employees, especially those with money and access, about AI vishing attacks. Consider including AI-enhanced dangers in security awareness training. With threat actors’ efficient and accessible impersonation, everyone should be sceptical about phone calls, especially if they fall under one of the following categories:
The caller is making claims that don’t seem real.
The caller is not someone or anything you would trust.
The caller makes an attempt to impose dubious authority.
The caller doesn’t seem like the source at all.
High-priority calls demanding financial or access information, such as a one-time password, should be avoided by trusted employees. Employees should be able to hang up and report questionable calls, especially if they suspect AI vishing. A similar attack is likely on another employee.
Verifying Source
Check the information with reliable sources. This includes hanging up and calling back a source-verified number. Ask the caller to send a text from a validated number, email, or business chat message.
Train personnel to notice audio irregularities like rapid background noise changes, which may indicate the threat actor didn’t clean the audio adequately. Expect odd speech patterns like a completely different vernacular than the source utilizes. Look for unusual inflections, fillers, clicks, pauses, and repetition. Consider voice timbre and cadence.
Set code words for executives and important workers who handle sensitive and/or financial data. Perform this outside of band to minimize enterprise exposure in the event of a breach. In case of uncertainty, code words can verify individuals.
If feasible, send unfamiliar calls to voicemail. Calls should be treated as carefully as emails. Report questionable public awareness calls.
Future Tech Considerations
At best, organizations can protect audio conversations by employing distinct networks for VoIP channels, authentication, and transmission encryption. It doesn’t stop attacks on employees’ personal phones.
Future organizations should safeguard all audio assets with digital watermarking, which is undetectable to humans but detectable by AI.
Caller verification will be included in mobile device management tools. In the interim, organizations should require all critical communications to occur across corporate chat channels, where strong authentication is necessary and identities are hard to spoof.
Research and methods are being developed to detect deepfakes. They can detect deepfakes in voicemail or offline voice notes despite their uneven accuracy. Over time, detection will improve and become enterprise tooling. DF-Captcha, a simple application that queue human prompts utilising challenge answer to verify the other party’s identification, is an example of real-time detection research.
Conclusion
Modern AI tools can assist develop more convincing vishing attacks, as discussed in this blog post. The shocking success of Mandiant’s vishing highlights the need for increased AI Voice Spoofing Attacks protection. Technology gives attackers and defenders strong tools, but humans are the biggest vulnerability. Google Cloud case study should rouse up organizations and individuals to take action.
Mandiant began using AI voice-spoofing assaults in its more complicated Red Team and Social Engineering Assessments to show how an attack could affect an organisation. As threat actors employ this tactic more, defenders must plan and prepare.
Read more on govindhtech.com
#VoiceSpoofingAttacks#UsingFutureAIVishing#AIpowered#AItools#SpoofingAttacks#generativeAI#GoogleCloud#InitialAccess#aitools#Conclusion#MicrosoftEdge#technology#technews#news#govindhtech
0 notes
Text
Come Risolvere l'Errore "La Connessione Non è Privata" su Internet
Navigando su Internet, potresti imbatterti nell’errore “La connessione non è privata”, un avviso che indica un problema di sicurezza con il sito web che stai cercando di visitare. Questo messaggio può essere frustrante, ma è importante capire cosa significa e come risolverlo. In questa guida, esploreremo le cause comuni di questo errore e forniremo soluzioni pratiche per risolverlo.

Indice
Introduzione
Cause Comuni dell'Errore "La Connessione Non è Privata"
Certificato SSL Scaduto
Certificato SSL Non Valido
Problemi di Data e Ora
Cache del Browser
Come Risolvere l'Errore su Diversi Browser
Google Chrome
Mozilla Firefox
Microsoft Edge
Safari
Soluzioni Avanzate
Verifica del Certificato SSL
Aggiornamento del Sistema Operativo e del Browser
Disattivazione Temporanea dell'Antivirus o del Firewall
Utilizzo della Modalità Incognito o Privata
Prevenzione dell'Errore in Futuro
Aggiornamento Regolare del Browser
Controllo Periodico delle Impostazioni di Data e Ora
Utilizzo di Certificati SSL Affidabili
Conclusione
1. Introduzione
L'errore "La connessione non è privata" è un messaggio di avviso che compare quando il browser rileva un problema con il certificato di sicurezza del sito web. Questo errore può impedire l'accesso ai siti e deve essere risolto per navigare in sicurezza.
2. Cause Comuni dell'Errore "La Connessione Non è Privata"
Certificato SSL Scaduto
Un certificato SSL scaduto non è più considerato sicuro. I siti web devono rinnovare regolarmente i loro certificati per mantenere la sicurezza.
Certificato SSL Non Valido
Un certificato SSL non valido può derivare da un'errata configurazione o dall'uso di certificati autofirmati che non sono riconosciuti dai browser.
Problemi di Data e Ora
Se la data e l'ora del tuo dispositivo non sono corrette, il browser potrebbe non riuscire a verificare il certificato SSL del sito web.
Cache del Browser
La cache del browser può contenere vecchie informazioni sui certificati, causando l'errore. Svuotare la cache può risolvere il problema.
3. Come Risolvere l'Errore su Diversi Browser
Google Chrome
Aggiorna la pagina premendo Ctrl + F5.
Svuota la cache del browser da Impostazioni > Privacy e sicurezza > Cancella dati di navigazione.
Verifica le impostazioni di data e ora del tuo sistema.
Mozilla Firefox
Ricarica la pagina premendo Ctrl + F5.
Cancella la cache del browser da Opzioni > Privacy e sicurezza > Cookie e dati dei siti web > Cancella dati.
Controlla le impostazioni di data e ora del dispositivo.
Microsoft Edge
Aggiorna la pagina premendo Ctrl + F5.
Svuota la cache del browser da Impostazioni > Privacy, ricerca e servizi > Scegli cosa cancellare.
Verifica le impostazioni di data e ora del tuo sistema.
Safari
Ricarica la pagina premendo Cmd + R.
Cancella la cache del browser da Preferenze > Privacy > Gestisci dati dei siti web > Rimuovi tutti.
Controlla le impostazioni di data e ora del dispositivo.
4. Soluzioni Avanzate
Verifica del Certificato SSL
Puoi verificare manualmente il certificato SSL del sito cliccando sull'icona del lucchetto nella barra degli indirizzi e controllando i dettagli del certificato.
Aggiornamento del Sistema Operativo e del Browser
Assicurati che il tuo sistema operativo e il browser siano aggiornati all'ultima versione per garantire la compatibilità con i certificati SSL.
Disattivazione Temporanea dell'Antivirus o del Firewall
A volte, antivirus o firewall troppo zelanti possono bloccare i certificati SSL. Prova a disattivarli temporaneamente per vedere se l'errore si risolve.
Utilizzo della Modalità Incognito o Privata
La modalità incognito o privata non utilizza la cache del browser, il che può aiutare a bypassare l'errore temporaneamente.
5. Prevenzione dell'Errore in Futuro
Aggiornamento Regolare del Browser
Mantieni il browser sempre aggiornato per assicurarti di avere le ultime patch di sicurezza.
Controllo Periodico delle Impostazioni di Data e Ora
Verifica regolarmente che la data e l'ora del tuo dispositivo siano corrette per evitare problemi con i certificati SSL.
Utilizzo di Certificati SSL Affidabili
Assicurati che i siti web che visiti utilizzino certificati SSL affidabili e riconosciuti dai principali browser.
6. Conclusione
L'errore "La connessione non è privata" può sembrare scoraggiante, ma seguendo i passaggi sopra indicati puoi risolverlo facilmente. Mantieni sempre aggiornati i tuoi dispositivi e fai attenzione alle impostazioni di sicurezza per una navigazione sicura e senza intoppi.
Fonti Autorevoli Esterne
Google Support: Risoluzione dei Problemi di Connessione Non Privata
Mozilla Support: Correzione degli Errori di Connessione Sicura
Microsoft Support: Risoluzione degli Errori di Certificato in Edge
#ErroreConnessioneNonPrivata#SSL#CertificatoSSL#SicurezzaInternet#RisoluzioneProblemiInternet#Browser#GoogleChrome#MozillaFirefox#MicrosoftEdge#Safari#CacheBrowser#DataEOra#AggiornamentoBrowser#Antivirus#Firewall#NavigazioneSicura#ModalitàIncognito#CertificatiSicurezza#GuidaInternet#SupportoTecnico
0 notes
Text
Microsoft Edge's new Instant Updates feature could result in data loss
http://i.securitythinkingcap.com/TFpfCL
0 notes
Text
The Ultimate Guide to Windows 10 Keyboard Shortcuts
Windows 10 is packed with useful features, but nothing boosts productivity like mastering keyboard shortcuts. These shortcuts save time and make navigating your system a breeze. In this guide, we’ll explore the most essential Windows 10 keyboard shortcuts and some lesser-known ones that can significantly enhance your workflow.

Table of Contents
Introduction
Basic Keyboard Shortcuts
Copy, Cut, Paste
Undo, Redo
Select All
Windows Key Shortcuts
Basic Windows Key Functions
Advanced Windows Key Shortcuts
File Explorer Shortcuts
Navigation
File Management
Virtual Desktops Shortcuts
Creating and Managing Virtual Desktops
Switching Between Virtual Desktops
Command Prompt Shortcuts
Basic Commands
Advanced Commands
Accessibility Shortcuts
Magnifier
Narrator
High Contrast
Browser Shortcuts
Microsoft Edge
General Browser Shortcuts
Customizing Keyboard Shortcuts
Conclusion
1. Introduction
Keyboard shortcuts are a crucial part of using Windows 10 efficiently. By reducing reliance on the mouse, you can perform tasks more quickly and keep your workflow uninterrupted. This guide covers essential shortcuts and dives into more specialized ones, providing a comprehensive resource for users at all levels.
2. Basic Keyboard Shortcuts
Copy, Cut, Paste
Ctrl + C: Copy selected item
Ctrl + X: Cut selected item
Ctrl + V: Paste copied/cut item
Undo, Redo
Ctrl + Z: Undo an action
Ctrl + Y: Redo an action
Select All
Ctrl + A: Select all items in a document or window
3. Windows Key Shortcuts
Basic Windows Key Functions
Windows + D: Show or hide the desktop
Windows + E: Open File Explorer
Windows + L: Lock your PC
Advanced Windows Key Shortcuts
Windows + Tab: Open Task View
Windows + I: Open Settings
Windows + S: Open Search
Windows + X: Open Quick Link menu
4. File Explorer Shortcuts
Navigation
Alt + D: Select the address bar
Ctrl + F or F3: Search in File Explorer
Ctrl + N: Open a new window
File Management
Ctrl + Shift + N: Create a new folder
Alt + Enter: Open properties for the selected item
F2: Rename selected item
5. Virtual Desktops Shortcuts
Creating and Managing Virtual Desktops
Windows + Ctrl + D: Create a new virtual desktop
Windows + Ctrl + F4: Close the current virtual desktop
Switching Between Virtual Desktops
Windows + Ctrl + Left/Right Arrow: Switch between virtual desktops
6. Command Prompt Shortcuts
Basic Commands
Ctrl + C: Copy selected text
Ctrl + V: Paste text
Advanced Commands
Ctrl + Shift + Plus (+): Zoom in
Ctrl + Shift + Minus (-): Zoom out
7. Accessibility Shortcuts
Magnifier
Windows + Plus (+): Open Magnifier and zoom in
Windows + Minus (-): Zoom out
Narrator
Windows + Ctrl + Enter: Turn Narrator on or off
High Contrast
Left Alt + Left Shift + Print Screen: Turn high contrast on or off
8. Browser Shortcuts
Microsoft Edge
Ctrl + T: Open a new tab
Ctrl + W: Close the current tab
Ctrl + Shift + T: Reopen the last closed tab
General Browser Shortcuts
Ctrl + L: Highlight the URL
Ctrl + Tab: Switch to the next tab
Ctrl + Shift + Delete: Open the clear browsing data options
9. Customizing Keyboard Shortcuts
Windows 10 allows customization of certain keyboard shortcuts to better suit your workflow. To customize, you can use third-party tools like AutoHotkey, which provide extensive options for creating and managing your own shortcuts.
10. Conclusion
Mastering Windows 10 keyboard shortcuts can dramatically increase your productivity and streamline your tasks. Whether you are a beginner or a seasoned user, incorporating these shortcuts into your daily routine will save you time and effort. Keep this guide handy as a reference and start practicing these shortcuts today.
External Authoritative Sources
Microsoft Support: Keyboard shortcuts in Windows
How-To Geek: The Ultimate Guide to Windows 10 Keyboard Shortcuts
Lifewire: Essential Windows 10 Keyboard Shortcuts
By incorporating these detailed steps and tips, you can take full advantage of Windows 10 keyboard shortcuts, making your computing experience faster and more efficient.
#1.#Windows10#2.#KeyboardShortcuts#3.#WindowsShortcuts#4.#ProductivityTips#5.#WindowsTips#6.#TechTips#7.#ComputerShortcuts#8.#WindowsGuide#9.#VirtualDesktops#10.#FileExplorer#11.#AccessibilityShortcuts#12.#CommandPrompt#13.#MicrosoftEdge#14.#BrowserShortcuts#15.#TechHacks
0 notes
Video
youtube
How To Access The Hidden Settings In The Microsoft Edge Web Browser | PC..
Discover how to unlock the hidden settings in Microsoft Edge on your PC to enhance your browsing experience. This tutorial shows you step-by-step how to access the advanced configurations within Edge, enabling you to customize and optimize the browser to suit your needs. Perfect for users who want to explore beyond the default settings!
Simple Steps
1. Open the Edge web Browser. 2. In the address bar, type edge://about into the address bar and click the enter key on your keyboard.
0 notes
Text
youtube
How To Use Web Capture To Take Screenshots Of Webpages In Microsoft Edge On PC
This is a video tutorial on how to take a screenshot of a webpage using Edge's built in feature called Web Capture. I will be using a desktop PC for this tutorial.
Simple Steps
Open the Edge web browser and proceed to the website that you want to take a screenshot.
Click On The 3 Dot Hamburger Menu In The Upper Right Hand Corner.
Choose "Web Capture" from the dropdown.
Choose if you want to "Capture Area" or "Capture Full Page".
0 notes
Text
#MP3Juice#MicrosoftEdge#PlaybackIssue#MusicDownloads#MP3Download#FreeMusic#OnlineMusic#MusicSite#TechSupport#EdgeIssue
0 notes
Text
Microsoft Edge Introduces Screenshot Prevention And Mandatory Updates For Enhanced Security

(Source – Futurezone)
If you use the Microsoft Edge browser at work, your ability to share screenshots may soon be restricted. Microsoft is implementing screenshot prevention controls in Edge to enhance data security. This new feature is aimed at preventing the sharing of sensitive web pages with competitors, relatives, and journalists.
“Screenshot prevention policies will secure against data exfiltration in the browser by blocking the ability to take screenshots on pages labeled as sensitive or protected,” Microsoft announced. IT managers will have the capability to tag certain web pages as protected using various Microsoft policy engines, including Microsoft 365, Microsoft Defender for Cloud Apps, Microsoft Intune Mobile Application Management, and Microsoft Purview. This move is part of a broader effort to safeguard corporate information and prevent unauthorized data sharing.
The screenshot prevention feature is expected to be available to customers in the upcoming months. However, it remains unclear whether third-party tools that capture screenshots or record videos will also be blocked by this new control. The primary goal is to ensure that sensitive corporate information remains secure and that users cannot easily share it through simple screenshot methods.
Mandatory Updates to Enhance Browser Security
In addition to screenshot prevention, Microsoft will introduce mandatory updates for Edge for Business users. This feature will soon enter a preview phase, allowing IT administrators to better manage browser security within their organizations.
“The Edge management service will enable IT admins to see which devices have Edge instances that are out of date and at risk,” Microsoft explained. This service will offer several mitigating controls, including forcing a browser restart to install updates, enabling automatic browser updates, and activating enhanced security mode for additional protections.
The initiative to enforce automatic updates is a proactive measure to counter the threat of zero-day attacks. By ensuring that all instances of Edge are up-to-date, Microsoft aims to reduce vulnerabilities that could be exploited by malicious actors. This strategy underscores the importance of maintaining up-to-date software to protect against emerging threats and vulnerabilities.
Balancing Security with Usability
Microsoft’s new features for Edge aim to strike a balance between enhancing security and maintaining usability for business users. The screenshot prevention tool is designed to protect sensitive data without overly restricting legitimate use cases. Meanwhile, the mandatory updates ensure that all users benefit from the latest security enhancements and features.
Whether the screenshot prevention controls will effectively block all methods of screenshot capture, including third-party tools and smartphone cameras, is yet to be determined. However, these measures represent a significant step towards improving data security in corporate environments.
As these features roll out, businesses will need to adapt to the new controls and leverage them to protect their sensitive information. IT administrators will play a crucial role in implementing these policies and ensuring that their organizations remain secure.
In conclusion, Microsoft’s introduction of screenshot prevention and mandatory updates in Edge for Business reflects a robust approach to enhancing security. By preventing unauthorized data sharing and ensuring up-to-date software, Microsoft aims to provide a safer browsing experience for business users. These developments are part of a broader trend towards more secure and managed IT environments, crucial in today’s landscape of increasing cyber threats.
0 notes
Text
youtube
How To Remove Copilot From Microsoft Edge | Remove Copilot Microsoft Edge (Easiest Way)
#copilot#removecopilot#removecopilotfromedge#microsoftedge#windows#howto#laptop#windows10#pc#trending#windows11#fixed#free#Youtube
1 note
·
View note