#ISO 26262 Projects
Explore tagged Tumblr posts
Text
Making ISO 26262 Compliance Smoother and More Efficient for the Automotive Industry
Complying with ISO 26262, the international standard for functional safety in the automotive industry, is a critical requirement for ensuring the safety and reliability of automotive systems. While achieving ISO 26262 compliance may seem daunting, there are strategies and best practices that can make the process easier and more efficient for automotive companies. In this blog post, we will explore key steps to simplify ISO 26262 compliance and foster a safety-oriented culture within the automotive industry.
Establishing a Comprehensive Safety Framework for ISO 26262 Compliance
To make ISO 26262 compliance more manageable, it is essential to establish a robust safety framework that aligns with the standard's requirements. This framework should encompass safety management, hazard analysis, risk assessment, safety goals, safety plans, and safety verification and validation activities. By clearly defining ISO 26262 mandated processes and responsibilities, companies can ensure a structured and systematic approach to compliance.
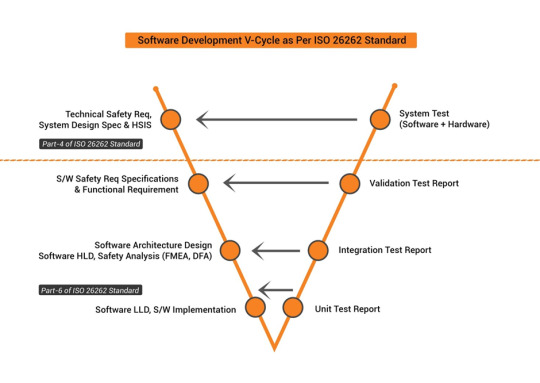
ISO 26262 Compliance Needs a Risk-Based Approach
ISO 26262 encourages a risk-based approach to functional safety. Instead of applying the same level of rigor to every aspect of a system, companies should prioritize their efforts based on the level of risk associated with each component or function. Identifying and mitigating the most critical risks first can help optimize resource allocation and streamline compliance efforts.
Promoting Cross-Functional Collaboration for ISO 26262 Projects
ISO 26262 compliance requires collaboration among various disciplines, including engineering, safety, testing, and project management. Foster a culture of cross-functional collaboration to facilitate knowledge sharing and decision-making. Encourage open communication channels and create opportunities for regular meetings and workshops to ensure all stakeholders are aligned on compliance objectives.
Leveraging ISO 26262 Compliance Experts
Engaging automotive safety experts can significantly simplify ISO 26262 compliance. These experts possess in-depth knowledge of the standard's requirements and can provide guidance on best practices, gap analysis, and compliance strategies. They can help tailor the compliance process to the organization's specific needs and provide valuable insights throughout the development lifecycle.
Implementing ISO 26262 Qualified Tools and Processes
Invest in tools and processes that support safety-oriented development and verification activities. This includes utilizing functional safety tools, safety analysis tools, requirements management tools, and traceability tools. Automating safety-related processes can enhance efficiency, accuracy, and traceability, while reducing manual effort and errors.
Conclusion
By following a structured and systematic approach, collaborating across functions, leveraging expertise, and embracing a risk-based mindset, automotive companies can simplify the ISO 26262 compliance process. Implementing safety-oriented tools, fostering a safety culture, and providing continuous training further streamline the path to compliance. Ultimately, making ISO 26262 compliance easy is about embedding safety into the DNA of automotive organizations and prioritizing the well-being of both drivers and passengers.
#ISO 26262#ISO 26262 Compliance#Automotive Industry#ISO 26262 Projects#automotive safety experts#automotive safety#ISO 26262 consulting#ISO 26262 consultant#ISO 26262 services#ISO 26262 software#ISO 26262 development
0 notes
Text
Sensors For Ev Thermal Management Market: Boosting Safety And Performance In Electric Vehicles
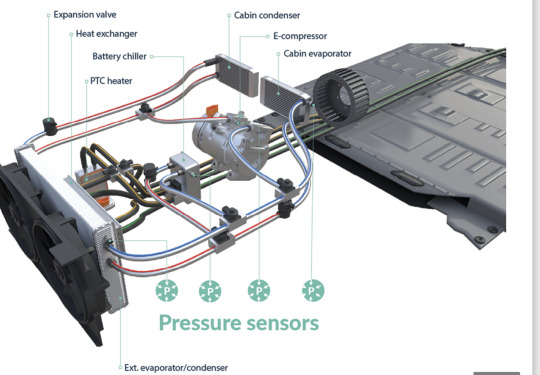
The Sensors for EV Thermal Management Market have redefined the automotive industry, marking a significant shift towards sustainability and emission-free transportation. As EV adoption grows globally, thermal management has become a critical aspect of ensuring the optimal performance of these vehicles. The thermal management system in an EV maintains the temperature of key components, such as the battery, motor, and power electronics, to prevent overheating and ensure efficiency. Sensors play a crucial role in EV thermal management systems, providing real-time data to optimize the cooling and heating processes. This blog delves into the market growth, size, legal constraints, market segmentation, and future forecast of sensors for EV thermal management.
Market Growth and Size of Sensors for EV Thermal Management Market
The sensors for EV thermal management market is rapidly expanding, driven by the rising adoption of electric vehicles worldwide. As EV technology advances, maintaining optimal temperature control is essential for ensuring safety, extending battery life, and maximizing efficiency. The increasing focus on battery efficiency, government regulations promoting EV adoption, and advancements in sensor technology are major factors propelling market growth.
In 2024, the global market for sensors used in EV thermal management was valued at approximately USD 1.8 billion and is projected to grow at a Compound Annual Growth Rate (CAGR) of 11.2% during the forecast period of 2024-2032. By 2032, the market size is expected to reach around USD 4.2 billion. The substantial growth of this market is driven by advancements in thermal management systems and an increasing number of electric vehicle launches by major automotive manufacturers. The demand for sensors that provide precise thermal control is on the rise, as manufacturers strive to improve the safety and reliability of their electric vehicles.
The growing EV sales in regions such as North America, Europe, and Asia-Pacific have further boosted the demand for sensors. The emphasis on range optimization and energy efficiency has resulted in an increased focus on advanced thermal management systems, which in turn has increased the demand for temperature, pressure, and humidity sensors.
Legal Constraints and Limitations of Sensors for EV Thermal Management Market
The growth of the sensors for EV thermal management market is not without its challenges. Various legal and regulatory constraints can affect the adoption and development of sensor technologies in EVs. Regulatory bodies in different countries have established standards for the safety and performance of electric vehicles, which include requirements for the thermal management systems and the sensors used within them.
In the European Union, there are strict standards regarding emissions and safety that impact the design and deployment of thermal management systems in EVs. Sensors must comply with industry standards such as ISO 26262 for functional safety, which applies to all electronic systems in vehicles, including thermal management. These regulations increase the cost and complexity of developing sensors, especially for small manufacturers looking to enter the market.
Moreover, privacy and data protection laws also impact the use of sensors. Many sensors collect data related to vehicle performance and driver behavior, and this data must be handled in compliance with regional data protection regulations such as GDPR in Europe. This creates additional responsibilities for manufacturers in terms of data security and compliance, which can hinder the widespread adoption of advanced sensor technologies.
Market Segmentation by Product and Application of Sensors for EV Thermal Management Market
The market for sensors used in EV thermal management can be segmented based on product type and application. Understanding these segments is essential for identifying key growth areas and opportunities in the market. By Product Type
Temperature Sensors: Temperature sensors are the most commonly used type in EV thermal management. These sensors monitor the temperature of key components, such as the battery pack, electric motor, and power electronics, to prevent overheating and ensure efficient performance. As battery technology advances, temperature sensors have become more sophisticated to provide precise temperature readings.
Pressure Sensors: Pressure sensors are used to monitor the coolant pressure in the thermal management system. Maintaining optimal pressure levels is essential for efficient heat dissipation and preventing leaks. Pressure sensors are critical in maintaining the performance and reliability of the cooling systems used in EVs.
Humidity Sensors: Humidity sensors are used to monitor the moisture levels within the vehicle's thermal management system. Excess humidity can lead to corrosion and affect the performance of electronic components, making these sensors vital for maintaining system health.
Flow Sensors: Flow sensors are used to measure the flow rate of coolant in the thermal management system. Ensuring adequate coolant flow is crucial for preventing overheating of the battery and power electronics. These sensors help maintain an efficient cooling process, enhancing the overall reliability of the EV.
By Application
Battery Thermal Management: The battery is one of the most critical components of an electric vehicle, and its performance is highly dependent on maintaining an optimal temperature range. Sensors used in battery thermal management help monitor and control the temperature to ensure battery safety, extend life, and improve efficiency. The demand for sensors in this application segment is expected to grow significantly, as battery technology continues to evolve.
Motor Thermal Management: Electric motors generate significant amounts of heat during operation, which can affect their efficiency and lifespan. Sensors are used to monitor motor temperature and ensure effective cooling to maintain performance. As motor technology advances and power densities increase, the demand for reliable thermal management solutions, including sensors, is rising.
Power Electronics Thermal Management: Power electronics, including inverters and converters, are essential for controlling the power flow in an electric vehicle. These components generate heat during operation, and sensors play a crucial role in maintaining their temperature within a safe range. This helps prevent damage to sensitive electronic components and ensures the efficient operation of the vehicle.
Cabin Thermal Management: Sensors are also used in cabin thermal management systems to ensure passenger comfort. These sensors help control the heating, ventilation, and air conditioning (HVAC) systems to maintain a comfortable cabin environment while minimizing energy consumption.
Future Forecast of Sensors for EV Thermal Management Market
The future of the sensors for EV thermal management market looks highly promising, with multiple factors contributing to its growth. The increasing adoption of electric vehicles, advancements in sensor technology, and the growing importance of energy-efficient thermal management solutions are expected to drive market growth in the coming years.
Technological Advancements: The integration of advanced technologies, such as artificial intelligence (AI) and the Internet of Things (IoT), into thermal management systems is expected to boost the demand for sensors. AI can be used to predict thermal behavior, while IoT enables real-time monitoring and data analysis, leading to more efficient and adaptive thermal management solutions.
Focus on Battery Efficiency: As electric vehicles evolve, there is an increasing emphasis on extending battery life and optimizing performance. Sensors that can provide precise and reliable data on temperature, pressure, and other parameters will be critical in achieving these goals. The development of new battery chemistries, such as solid-state batteries, will further drive the need for advanced thermal management solutions.
Increasing Government Initiatives: Governments around the world are promoting the adoption of electric vehicles through subsidies, tax benefits, and infrastructure development. This is expected to drive the demand for sensors used in thermal management systems, as manufacturers strive to meet regulatory requirements and improve the safety and efficiency of their vehicles.
Expansion in Emerging Markets: The adoption of electric vehicles is not limited to developed regions; emerging markets in Asia, Latin America, and Africa are also showing increasing interest in EVs. As these markets grow, the demand for sensors for EV thermal management is expected to rise, providing new opportunities for market players.
Cost Reduction and Scalability: Advances in sensor manufacturing techniques and economies of scale are expected to reduce the cost of sensors, making them more accessible to a broader range of manufacturers. This will facilitate the widespread adoption of sensors for thermal management in electric vehicles of all price ranges.
Conclusion
The sensors for EV thermal management market is poised for significant growth, driven by the increasing adoption of electric vehicles, advancements in thermal management systems, and supportive government policies. Sensors play a vital role in ensuring the safety, efficiency, and performance of electric vehicles by providing real-time data for temperature, pressure, and humidity control. Despite facing challenges related to regulatory compliance and data privacy, the market's future looks promising, with opportunities for innovation and expansion across different regions. As the automotive industry moves towards electrification, the importance of effective thermal management cannot be overstated. Sensors will continue to play a crucial role in optimizing thermal management systems, ensuring the safety and efficiency of electric vehicles. The future of EVs is closely tied to advancements in sensor technology, making this a critical area of focus for manufacturers, investors, and policymakers alike.
Contact Us for more information on the sensors for EV thermal management Market Research 2023–2030 Forecast :
Or Phone Call us : USA — +1 507 500 7209 | India — +91 750 648 0373 Browse More Similar Articles. Sensors for EV Battery Pack and Cell Connection System Market Size Capacitor in Electric Vehicles EV Market Structure EV Charge Connector Assemblies Market Growth EV Range Extender Market Development
#sensors for EV thermal management#ev market#ev thermal management#sensors for EV thermal management market#market research#market report#report prime
0 notes
Text
IBM Engineering Systems Design Rhapsody 10.0.1 Declaration

Rational Rhapsody 10.0.1
Design of IBM Engineering Systems Strong model-based systems engineering (MBSE) tools like Rhapsody make it easier to design, analyze, and validate complex systems and create software based on those models. The complete product development lifecycle, including specification, development, testing, and delivery, is easily integrated into Rhapsody thanks to its strong support for the unified modeling language (UML) and systems modeling language (SysML).
IBM Engineering Systems Design Rhapsody
Deliver software and systems of higher quality more quickly with digital threading across domains, production code generation, smooth simulation, and reliable modeling.
- Advertisement -
What services does Rhapsody offer?
With its suite of tools, IBM Engineering Systems Design Rhapsody (formerly known as Rational Rhapsody) provides a tried-and-true method for modeling and systems design tasks, enabling you to handle the complexity that many organizations encounter while developing new products and systems. Rhapsody is a component of the IBM Engineering portfolio, offering systems engineers a collaborative design, development, and testing environment that supports AUTOSAR import and export capabilities along with UML, SysML, and UAF. Furthermore, the solution speeds up industry standards like ISO 26262, DO-178, DO-178B/C, and UPDM and permits control of defense frameworks like DoDAF, MODAF, and UPDM.
Advantages
Provides ongoing validation
Utilize quick simulation, prototyping, and execution to get ongoing validation and address mistakes early on, when they can be fixed more affordably.
Offers automated consistency verification
Employ collaborative reuse and automatic consistency checking to boost agility and lower recurring and non-recurring expenses.
Work together with your engineering group
With the use of design tools like Mathworks Simulink or Engineering Systems Design Rhapsody, you can share, work with, and evaluate your engineering lifecycle artifacts with the larger engineering team.
- Advertisement -
Usability
Simplify the design process with a cutting-edge UX that lets you customize the tool interface to your own requirements and tastes, making model visualization simpler.
Crucial characteristics of IBM Rhapsody goods
Examine and clarify the project’s needs
System specifications, interface design papers, and system test cases are automatically generated by the software using SysML, UML, UAF, and AUTOSAR import and export capabilities.
Go from design to implementation quickly
With the use of UML, it provides an affordable comprehensive software engineering environment for graphically designing C++, C, or Java applications.
Create documentation and automate design reviews
Using a central repository accessible via the web, Rhapsody – Model Manager facilitates cross-disciplinary team collaboration, sharing, review, and management of designs and models. Customers and suppliers can use a web client to access information. The program streamlines stakeholder communication, expedites decision-making, and enhances quality by automating design evaluations. Comprehensive documentation can be produced for reporting, compliance, communication, and specifications.
Develop, model, and implement designs for early verification
In addition to having all the features of Rhapsody Architect for Systems Engineers, Rhapsody – Designer for Systems Engineers enables you to simulate, prototype, and carry out designs for early requirements, architecture, and behavior validation. This is a model-based system engineering (MBSE) environment that makes use of the widely used SysML and UML frameworks. With enhanced validation and simulation, it shortens time-to-market, increases productivity, and helps you adjust to changing client requirements.
Engage in an agile engineering environment that is embedded and real-time
Agile software engineering environment for C++, C, Java, and Ada that is embedded and real-time (includes MISRA-C and MISRA-C++) is provided by Rhapsody – Developer. Along with the features of IBM Engineering Systems Design Rhapsody (Rational Rhapsody) – Architect for Software, it offers fast prototyping and simulation for design-level debugging, automated build generation for continuous integration, and support for safety-critical software lifecycle issues.
Allow for the smooth integration of the AUTOSAR standard. The AUTOSAR Extension is a part of IBM Rhapsody Model-Driven Development (MDD). This potent combination streamlines and expedites the process of developing automotive software, freeing up developers to concentrate on building reliable and effective solutions that satisfy the stringent demands of the modern industry.
Rhapsody 10.0.1
IBM is pleased to announce the introduction of IBM Engineering Systems Design Rhapsody version 10.0.1, which includes several new features and changes aimed at optimizing usability, automation, and integration.
Improved DOORS 9 integration promotes consistency and productivity
Rhapsody 10.0.1 enhances accuracy, traceability, and smoother operations by providing closer connection with the IBM Requirements Management DOORS system.
The new ReqXChanger interaction with DOORS 9 is crucial to this release. With better requirement visualization and traceability straight within Rhapsody, ReqXChanger replaces the Rhapsody Gateway and enables a more efficient workflow between Rhapsody and DOORS.
With seamless movement across the digital thread connecting DOORS and Rhapsody, users can now access and inspect model diagrams and elements in DOORS 9. The transition to the improved functionality is easy and seamless.
Change-aware synchronization maintains requirements and model in sync between Rhapsody 10.0.1 and DOORS 9, reducing effort and complexity in tracking changes in artifacts. To fit the unique requirements and surroundings of the users, this synchronization can be automated and tailored.
Extending IBM collaboration with Siemens to improve systems design through automation and integration
IBM has one major enhancement in this release as part of our continued collaboration between the Siemens and IBM product teams. By combining several components, this improvement aims to strengthen the digital thread and promote visibility, traceability, and interoperability.
Now, you may establish connections between Siemens Teamcenter specifications and parameters and model elements: To correlate Teamcenter requirements and parameters with model elements, choose them in the Rhapsody UI. Request the enabling plug-ins by contacting Siemens.
Significant improvements to workflows, usability, and testing
Better testing and usability are more important as system design complexity and interconnection increase. To address this difficulty, Rhapsody 10.0.1 has added new features and improved Test Conductor, such as increased test case coverage that offers a thorough rundown of all test cases. By transferring message-related test scenarios across multiple architectures, a technical preview of Message Mapper further streamlines scenario mapping.
Additional parallel development prompts improve design process efficiency by warning users when they are working with out-of-date model versions, streamlining merge operations, and fostering better teamwork. The product interface has been improved, allowing for more menu controls, such as toolbar and pop-up menu items, to enable complex customisation.
Rhapsody 10.0.1’s enhancements to the Rhapsody AUTOSAR Extension aid teams in managing challenging projects and increasing output. The installation package includes updated example models that are useful for understanding and implementing AUTOSAR standards.
Try out Rhapsody 10.0.1, IBM Engineering Systems Design, right now
Rhapsody 10.0.1 keeps up its good work as a top MBSE tool by providing enhanced automation, usability, and integration to facilitate the design and implementation of complex systems. Additionally, it advances the cooperation between IBM and Siemens Digital Industries Software in their quest to develop strong system engineering tools that empower businesses to design, develop, and produce high-performing, environmentally friendly products.
Read more on govindhtech.com
#IBMEngineeringSystems#SysM#design#IBMproduct#DesignRhapsody1001Declaration#featuresofIBM#systemdesign#automation#workflows#productivity#IBMcollaboration#ImprovedDOORS9#ibm#technology#technews#news#govindhtech
0 notes
Text
Mastering Automotive Embedded Systems: A Comprehensive Course at Technoscripts
Technoscripts is proud to present an immersive and comprehensive course on Automotive Embedded Systems, designed to equip aspiring engineers and professionals with the knowledge, skills, and expertise required to excel in the dynamic automotive industry. In today's fast-evolving automotive landscape, embedded systems play a crucial role in shaping the future of transportation, with innovations ranging from advanced driver assistance systems (ADAS) to autonomous vehicles revolutionizing the way we commute and interact with vehicles.
Our Automotive Embedded Systems course at Technoscripts is meticulously crafted by industry experts and seasoned professionals, ensuring that students receive cutting-edge training aligned with the latest industry trends and technological advancements. Through a combination of theoretical learning, hands-on practical sessions, and real-world projects, participants will delve into the intricacies of automotive embedded systems architecture, software development, communication protocols, sensor integration, and testing methodologies.
With a focus on industry-relevant skills and practical application, our course covers a wide range of topics, including microcontroller programming, automotive networks (CAN, LIN, FlexRay), embedded software development (C/C++, MATLAB/Simulink), real-time operating systems (RTOS), vehicle diagnostics, cybersecurity, and compliance standards (ISO 26262). Students will have the opportunity to work on industry-standard tools and platforms, gaining valuable experience and insights that will set them apart in the competitive automotive job market.
At Technoscripts, we are committed to providing a dynamic and engaging learning environment, where students can interact with industry experts, collaborate on projects, and build a strong foundation for a successful career in automotive embedded systems engineering. Whether you are a recent graduate looking to kickstart your career or a seasoned professional seeking to upskill and stay ahead of the curve, our Automotive Embedded Systems course offers the perfect blend of theoretical knowledge and practical expertise to help you thrive in the exciting world of automotive technology. Join us at Technoscripts and embark on a journey towards becoming a sought-after automotive embedded systems engineer, driving innovation and shaping the future of mobility.

#automotiveembeddedsystemscourse#automotiveembeddedinstitute#embeddedtraining#embeddedclasses#embeddedcourse#embeddedinstitute#automotiveembeddedcourse#automotiveembeddedclasses#embeddedsystemscoursepune#automotiveembeddedtestingcourse
0 notes
Text
Automotive Embedded Systems Course: Embedded Box
Course Overview:
The Automotive Embedded Systems Course at Embedded Box is designed to provide participants with a comprehensive understanding of embedded systems in the automotive industry. This course focuses on the design, development, and implementation of software and hardware components in vehicles, covering key
concepts and practical applications.
Course Duration:
Total Duration - 3 Months
Prerequisites:
Basic knowledge of embedded systems
Proficiency in programming languages (C, C++)
Familiarity with microcontrollers and electronics
Course Outline:
Introduction to Automotive Embedded Systems
Overview of embedded systems in automobiles
Importance and applications in the automotive industry
Emerging trends and challenges in automotive embedded systems
Embedded Hardware in Vehicles
Microcontrollers and microprocessors used in automotive systems
Sensors, actuators, and interfaces in vehicles
Communication protocols (CAN, LIN, FlexRay)
Embedded Software Development for Automotive Applications
Real-time operating systems (RTOS) for automotive systems
Software architecture design for automotive systems
Programming techniques for embedded systems in vehicles
Automotive Networking Technologies
Controller Area Network (CAN) bus architecture and applications
Diagnostic protocols like OBD-II and UDS
Integration of Ethernet and other communication protocols in vehicles
Embedded System Security in Automotive Industry
Cybersecurity threats and vulnerabilities in automotive systems
Best practices for secure coding in embedded software
Implementation of intrusion detection and prevention mechanisms in vehicles
Functional Safety Standards in Automotive Systems
Overview of ISO 26262 standard for functional safety in automobiles
Safety mechanisms and requirements specific to embedded systems
Application of Failure Modes and Effects Analysis (FMEA) in automotive settings
Automotive Embedded Software Testing
Testing methodologies for automotive software development
Validation and verification techniques for embedded systems in vehicles
Tools and frameworks used for testing automotive embedded software
Case Studies and Projects
Real-world examples showcasing automotive embedded systems
Hands-on projects to apply learned concepts practically
Industry standards and best practices within the automotive embedded systems domain
Assessment:
Regular quizzes and assessments to gauge understanding
Practical assignments to implement theoretical knowledge
Final project demonstrating skills acquired during the course
Certification:
Upon successful completion of the Automotive Embedded Systems Course at Embedded Box, participants will receive a certificate of completion, validating their expertise in designing and developing embedded systems for automotive applications.

#embeddedtraining#embeddedcourses#embeddedsystems#embedded training system#embeddedd#embeddedcourse#embeddedsystem#embeddedsysytem#embeddedsystemcourse#embedded
0 notes
Text
Functional Safety (FuSa) Services in India, USA, Europe
Leading automakers are quickly evolving to Software Defined Vehicles, with modern vehicles having multiple electronic systems with millions of lines of code running on them. In an industry like Automotive, humans are increasingly dependent on electronic systems to monitor and control many aspects of the vehicle. Therefore passenger safety becomes paramount.
Functional Safety (FuSa) Services is an integral part of the product development process in any Automotive Electrical and Electronic system, to ensure the safe and reliable operation of the system. Therefore, FuSa is about adopting a systematic approach to identify, assess, and devise ways to mitigate the risk/potential hazards that may arise. In other words, should something fail, we want it to fail predictably.
For automotive applications, the “ISO 26262 - Road vehicles -Functional safety Services” standard serves as the directive based on which the Functional safety development process is to be based.
Functional Safety Process
We begin by conducting a thorough Hazard and Risk Analysis (HARA) where potential risks are identified and categorized. This is used to determine the ASIL Level ranging from A to D. Further analysis is conducted by DFMEA (Design Failure Mode Effect Analysis) and FMEDA (Failure modes, Effects and Diagnostic Analysis), and based on the assessment, the Functional Safety concept is developed, where safety requirements are defined and this is used to arrive at the System Level, Hardware and Software level requirements are defined in the implementation phase, along with rigorous testing and validation procedures used to ensure that the system meets the designed requirements. We base these processes as guided by ISO 26262 standards that is crucial in ensuring that the electronic systems operate predictably and can handle failures and events in a predetermined manner.
Our Functional Safety Services
We support major parts of ISO 26262 development such as the Concept Phase, Product Development at the System, Hardware, and Software Levels, along with Supporting processes.
Our team has a wide range of experience from more than a decade of working on individual system projects and full vehicle development projects. We can support individual aspects of the process as well as end-to-end services, traveling along with the development process.
0 notes
Text
IAR fully supports Infineon's latest TRAVEO T2G CYT6BJ body control MCU family products

According to the information received by Lansheng Technology, it has fully supported the latest CYT6BJ series in Infineon's TRAVEO™ T2G body control MCU family. IAR Embedded Workbench for Arm is a complete embedded development solution, equipped with highly optimized compiler and build tools, code analysis tools C-STAT and C-RUN, and powerful debugging functions. This enables developers working on complex automotive body electronics applications to take full advantage of the features of the TRAVEO™ T2G MCU to create innovative designs with high code quality. IAR Embedded Workbench for Arm supports AUTOSAR and provides a functional safety version to help customers accelerate product certification.
Clara Volkmar, Director Product Marketing Body and Driver Information, Infineon's Automotive Division, said: "Infineon's TRAVEO™ T2G microcontrollers provide a compact solution to meet the needs of modern automotive body electronics systems and can take advantage of IAR Professional and suitable third-party development tools such as Embedded Workbench for Arm to achieve efficient development. Thanks to such a powerful tool partner as IAR, developers can quickly realize their demanding automotive applications even with our latest CYT6BJ series chips project."
By supporting all available TRAVEO™ T2G series chips, including the latest CYT6BJ series, IAR Embedded Workbench for Arm ensures compatibility and provides developers with highly optimized build tools and advanced debugging features: such as complex code and data interrupts Points, runtime stack analysis, call stack visualization, code coverage analysis, and integrated monitoring of power consumption contribute to a seamless development experience. With the code analysis tools C-STAT and C-RUN, developers can fully control the code quality.
For companies with functional safety requirements, IAR Embedded Workbench for Arm offers a functional safety version certified by TÜV SÜD (certified according to ISO 26262 requirements). This functional safety version is also certified according to IEC 61508, IEC 62304, EN 50128, EN 50657, IEC 60730, ISO 13849, IEC 62061, IEC 61511 and ISO 25119. For companies using continuous integration (CI) workflows and automated build and test processes, IAR Build Tools is also available for Linux-based frameworks. In addition, IAR's professional technical support, training and flexible licenses enable all customers to find a solution that suits their specific needs.
Lansheng Technology Limited, which is a spot stock distributor of many well-known brands, we have price advantage of the first-hand spot channel, and have technical supports.
Our main brands: STMicroelectronics, Toshiba, Microchip, Vishay, Marvell, ON Semiconductor, AOS, DIODES, Murata, Samsung, Hyundai/Hynix, Xilinx, Micron, Infinone, Texas Instruments, ADI, Maxim Integrated, NXP, etc
To learn more about our products, services, and capabilities, please visit our website at http://www.lanshengic.com
0 notes
Text
TVS Motor Company Recruitment 2023 , Hosur plant

TVS Motor Company Recruitment 2023 | Hosur plant | White Collar Jobs in TVS Group of Company | Qualification : B.E.Mechanical & Electrical Engineer can apply Company Name : TVS Motor Company TVS Motor Company Recruitment 2023 | Hosur plant | White Collar Jobs in TVS Group of Company | Qualification : B.E.Mechanical & Electrical Engineer can apply. Development Engineer (Development Engineer_CP - Super Premium & Co-operation Projects), Sourcing & Development Engineer (Sourcing & Dev Eng_CP - Super Premium & Co-operation Projects) Office Location: Hosur Plant (Plant) Our Latest YOUTUBE Videos Link : https://www.youtube.com/channel/UCZYt-jtPk975fMuI6tLpUEg Our Telegram Channel Link: https://t.me/employmentjobs

TVS Motor Company Recruitment 2023 Related Jobs : - Sharda Motors Company Jobs - Hyundai Supplier Company Jobs - Nissan Company Jobs In Chennai Job Interview in Pegatron Company – Diploma & B. E. Engineers | Mahindra World City | Chengalpattu Designation: Engineer & Sr.Engineer Educational Qualifications: B.E. Engineer & Diploma Role: Permanent Year of Experience: Min Experience Job Location: Mahindra World City – Chengalpattu Apply link - Click Here BEL Recruitment 2023 | BEL நிறுவனத்தில் Apprenticeship Training அறிவிப்பு Designation: Apprenticeship Training Educational Qualifications: B.E, B.Tech Engineers Role: Trainee Year of Experience: Fresher Job Location: Bangalore Salary Details: 17,500 /- Per month Apply link - Click Here Latest Jobs By : Chennai JobsClick HereCoimbatore JobsClick HereBangalore JobsClick HereHyderabad JobsClick HereAndra Pradesh JobsClick HereSalem JobsClick HereMadurai JobsClick HereTrichy JobsClick HerePondicherry JobsClick HereAcross India JobsClick HereOther Cities JobsClick HereTVS Motor Company Recruitment 2023 Designation: Development Engineer Educational Qualifications: B.E.Mechanical & Electrical Role: Permanent Year of Experience: Min Experience Job Location: Hosur , Tamilnadu Salary Details: As per the Company Standard Mechanical JobsClick HereELE / ECE JobsClick HereCivil JobsClick HereIT / Software JobsClick HereBPO / Call Centre JobsClick HereH/W & Networking JobsClick HereHuman Resource Jobs Click HereAcc/Fins JobsClick HereArts & Science JobsClick HereTVS Motor Company Recruitment 2023 TVS Motor Company Recruitment 2023 Job Description : Understanding and implementation of GS / QV / LH (BMW standards - material, surface, process, marking, aesthetics etc.) requirements in EV part development Understand and review with suppliers periodically EV related standards such as i)Functional safety relevant according to ISO 26262 ii)EMI / EMC iii)Software development procedure for instance for Ensure stage wise maturity requirements are met in part development for each milestone. Status update in the project meetings and workshop to BMW Conduct & review DVP (before & after SOP) as per agreed test plan list among supplier, TVS & BMW Appearance sign off workshops between supplier, TVS & BMW for alignment on aesthetic requirements to contractual QZS requirement Evaluation of new product cost for subsystem by zero base costing / benchmarking / comparative quotations How to Apply for this Job? Details & Apply link : Click Here Titan Company Jobs | Hosur Location Designation: Mechanical Engineer Educational Qualifications: B.E.Mechanical Engineer Role: Permanent Year of Experience: Min 2 Years Job Location: Hosur , Tamilnadu Apply link - https://myemploymentjobs.com/titan-company-jobs-hosur-location-b-e-mechanical-engineer/ Foxconn Company Off Campus Drive 2023 Designation: Trainee Educational Qualifications: Mechanical , EEE , ECE & Arts and Science Role: Permanent Year of Experience: Fresher Job Location: Sriperumbudur , Chennai Apply link : https://myemploymentjobs.com/foxconn-company-off-campus-drive-2023/ TATA Auto Jobs | டாடா நிறுவன நிரந்தர வேலை வாய்ப்புகள் Designation: Engineers Educational Qualifications: B.E , B.Tech , M.E, M. Tech Role: Permanent Year of Experience: 1 – 8 Years Experience Job Location: Chennai , Bangalore & Pune Apply link : https://myemploymentjobs.com/tata-auto-jobs-permanent-job-openings-2023/ For more Job info, subscribe to our website & and check our website daily. Join Our youtube ChannelClick HereJoin Our Telegram ChannelClick HereOur linkedin PageClick HereOur Quora PageClick Here Read the full article
#TVSMotorCompanyRecruitment#TVSMotorCompanyRecruitment2023#TVSMotorCompanyRecruitment2023fresherjobs#TVSMotorCompanyRecruitment2023hosur#TVSMotorCompanyRecruitment2023hosurplant#TVSMotorCompanyRecruitmentmechanical
0 notes
Text
ISO 26262 FUNCTIONAL SAFETY TRAINING AND CERTIFICATION FOR AUTOMOTIVE
Gaining an ISO 26262 Functional basic security training and certificate offers operational security experts and their businesses that an upperhand in the business. It will help individuals develop a spot for themselves at the business enterprise. These aims are fulfilled while you gets an ISO 26262 Functional Security instruction:-

TÜV SÜD conducts instructor-led training programs to offer a practical comprehension of the idea of ISO 26262 operational safety of street vehicles at the automotive trade. The training program is tailored in accordance with the dependence on their audience. But, there are particular requirements for attending our Instructor-led ISO 26262 Functional Security Training Software conducted by TÜV SÜD at India. The requirements for your instruction module are as follows:
Make sure that you satisfy the requirements of the business enterprise through a whole comprehension of the model-based procedures to come up with safety related systems in accordance with ISO 26262 benchmark Prove your know how of operational safety with an internationally recognised ISO 26262 certificate and eventually become an essential component of the state TÜV SÜD operational security professional communityGain expertise for a operational basic security engineer, specialist or professional from the automotive industryConstruct internal competencies to successfully undertake operational security projects efficiently and economically and gain a competitive advantage WHAT ARE THE BENEFITS OF searching for THE iso 26262 training AND CERTIFICATION plan?
Any professional who's interested in realizing the operational safety related electric and electrical systems composed of hardware and software components in electrical vehicles, either working or prepared to generate a livelihood within the automotive industry sector has to attend the application. The path can be obtained upto really possess a crystal very clear understanding and working experience of the way that safety- related systems needs to be managed and commanded to mitigate threats and avoid errors. They can sometimes incorporate product programmers, R&D professionals, control engineers, engineers, safety engineers, system integrators, EPCs, managers of technology departments, sales agents to safety services and products systems and services, sales engineers, professionals and managers, promotion pros or anyone who would like to acquire their operational basic security knowledge certified in the relevant area of ISO 26262 Functional Security at the automotive trade.
Breakdown of ISO 26262 Training Program MODULES:
Course modules inch to 4 present one to the procedures essential for the function in the security lifecycle (recommended for beginners). You're going to be made knowledgeable about the respective topics together with the assistance of practical examples. All class modules 1 - 4 embrace a situation-based method of the use of safety investigations and encouraging procedures and the subsequent deliverables. Explanations of those essential job services and products and proper treatment of their security plan are naturally an integrated portion of modules.
This content with the brand new variant was revised related to the very first variant in some specific locations. Furthermore to two new parts into the variant, the Edition two introduces many developments, concretizations and brand fresh instances, that were originated from the adventures from the technical application of their norm from early decades. The 1day class offers a synopsis of the important shifts in Edition two and also exemplifies its own proper implementation with the assistance of examples.
ISO 26262 Functional Security Certification and Training Application, trains professionals to own absolute comprehension and upgraded technical understanding about their safety related systems which the normal makes up about. It is aimed in building a simple understanding about safety related works connected to electronic and electrical systems to minimise failure and risks from the automotive industry. Thus, fundamentally it covers the total life cycle of this automotive item. Implementing ISO 26262 at the original phase, really helps ensure no such risks routine at a subsequent period of manufacturing, even as it will become costly to repair the issue.
Together with gaining functional knowledge in security associated purposes, the iso 26262 certification and Training Program Offers additional advantages that are as follows-
Improve your efficacy with courses, joining theory with practical expertise in the field of operational basic security Minimise risks by maintaining your employees current concerning regulations and standards in mathematics and technology, thereby permitting them to spot issues before your surgeries are influenced Prevent product recalls and lack in standing by employing an optimized tailored procedure Prevent product failures, and save some time and monetary deficits Profit competitive advantage by employing your understanding of this diverse functions all through the security life cycle, as a way to come up with the best services for you and your clients WHO SHOULD ATTEND THE ISO 26262 TRAINING & CERTIFICATION PROGRAM?
Based on years of technical expertise within the industry of Profession basic safety training, we offer you the essential expertise in learning and understanding about ISO 26262 second Edition. Safety is just one of the vital issues in evolution now legal for several road vehicles such as buses, trucks, motor cycles and the rest of the automobiles. The sector-specific wants of electric or electronics (E/E) systems concerning road vehicles is clarified within this standard. Our training modules are all derived from the technical use with the standard in your ordinary business to prevent increasing hazard from systematic and arbitrary hardware failures. Our purpose is to offer professionals practical wisdom and experience with your assessments courses, to take informed decisions and mitigate risks.
The electric and electrical systems composed of both hardware and software components in vehicles have been regulated by this standard. Compliance to ISO 26262 operational security standards in automotive is now vital for its OEMs, automotive designers and providers for both automotive and protection improvement. ISO 26262 operational security hires automotive OEMs and providers to check out and record the operational security process to make sure their apparatus and procedures run safely and precisely with no malfunction. It places a summary for quantifying risks and ascertaining hazard categories called ASILs (Automotive Safety Integrity Levels) and targets at reducing potential threats in automotive systems. It defines the security life cycle from the concept phase before decommissioning of this automotive merchandise or system. It monitors and measures risks to make sure an acceptable degree of safety is achieved from the automotive item. With evolving automation and application of automotive systems, ISO 26262 makes up about establishing the principle for risk management by establishing the standards for hardware and applications development in addition to analyzing, looking to get the greatest levels of safety. Thus, in the modern period it's essential to coach professionals from the automotive industry to possess complete understanding of ISO 26262 operational safety automotive standards to effectively handle their systems together without minimum quantities of danger.
General Breakdown of the newest attributes of ISO 26262 Edition Two Display of this newest Part 1 2 for bicycles Display of this new Part 1-1 for semiconductor growth Changed demands Partly 2 9 New alternative options Cases of execution
TÜV SÜD has got the skill to give ISO 26262 Functional Security Certification and Training Software for all street vehicles such as buses, trucks, motor cycles and the rest of the automobiles depending on latest variant in India.
1 note
·
View note
Link
TESSY - Automated testing of embedded software
The powerful and certified Unit and Integration Testing Tool for C / C ++ Embedded Software with support for a wide range of microcontrollers, compiler environments and target platforms. TESSY is qualified for safety-related software development according to IEC 61508 and ISO 26262.
TESSY automates the whole unit test cycle including regression testing for your embedded software in C/C++ on different target systems. As an easy-to-install and easy to operate testing tool TESSY guides you through the unit test workflow from the project setup through the test design and execution to the result analysis and reporting. TESSY takes additionally care of the complete test organization as well as the test management, including requirements, coverage measurement, and traceability.
1 note
·
View note
Text
Why is this car cybersecurity standard needed?
As the automotive world evolves towards connected cars and smart mobility, an additional element of security vulnerability is emerging, the threat of cyberattacks. Because automotive cybersecurity is a new and growing field, traditional automotive security and safety standards do not fully cover the topic of cybersecurity. Therefore, in response to these cyber security threats and increased concern for driver safety and security, OEMs, Tier 1 vendors and others often adopt methods individual approach (if any). Unfortunately, an individual approach is not enough; With the growth, prevalence, and sophistication of cyberattacks, it becomes necessary to establish specific guidelines and standards for automotive cybersecurity. In 2016, SAE International, the trade association and standards development organization for technical professionals, and ISO, the International Organization for Standardization, an international standards body made up of representatives from international organizations. different standards organizations, came together to solve the problem of establishing this industry. Automotive network security standards.
Both organizations have worked individually on automotive safety and security standards in the past; ISO 26262 previously established functional safety standards, and SAE J3061 laid the foundation for cybersecurity standards. When the two organizations realized they had a common goal, they met with OEMs, ECU vendors, cybersecurity vendors, and government organizations, and with more than 100 experts from over 82 companies. Based in more than 16 countries, a joint working group has been formed to create a comprehensive and effective global standard for automotive cybersecurity. Utilize four main working groups focused on risk management; product development; production, operation, maintenance and decommissioning; and process overview, the ISO/SAE 21434 project was born.
The need for this standard is clear:
First, there is a need for common cybersecurity-related terms for use in the automotive industry. In the past, many different terms were used making it difficult to understand cyber risk and how to mitigate it. Second, criteria for effective cybersecurity within a vehicle are also needed; Prior to ISO/SAE 21434, there was never a definition of what “sufficient cybersecurity” meant. Third, although there are advanced and accepted automotive safety standards in which the concept of ASIL (Automotive Safety Integrity Level) is understood and applied, there is no standard definition of a safety standard. additional cybersecurity, because proprietary cybersecurity assurance levels vary from company to company. And finally, there must be a standardized standard that regulators can identify and use to enforce vehicle compliance by ensuring that connected vehicle drivers are protected from damage. cyber threats and attacks.
What is within the scope of the standard?
ISO/SAE 21434, in draft form as of May 2020, is the standard for vehicle manufacturers and suppliers to ensure cybersecurity risks are effectively and efficiently managed. This standard has been developed specifically to ensure the safety and security of end users/drivers on the road, and as such, the identification of the risk level and the corresponding cybersecurity measures are determined. determined according to the ultimate impact on the driver.
This standard provides a standardized cybersecurity framework that establishes cybersecurity as an integral element of engineering throughout the lifecycle of a vehicle, from concept to dismantling, ensuring ensure that cybersecurity is considered in post-production processes (software updates, service and maintenance, feedback issues, etc.), and call for effective methods of feedback, training, and communication results related to automotive cybersecurity.
More specifically, the scope of the standard includes:
Specific requirements for cybersecurity risk management
Cybersecurity Process Framework
A common language to help manufacturers and organizations communicate with their cybersecurity risks
The benefits of standards are obvious. ISO/SAE 21434 brings potential for common supply chain terminology, industry consensus, clear minimum criteria for vehicle cybersecurity engineering, cybersecurity integrated into vehicle design right out of the box. From the ground up, a well-defined threat landscape, key standards for regulators, and a new level of trust are built between stakeholders.
By design, ISO/SAE 21434 does not prescribe specific cybersecurity technologies or solutions, remediation methods, or cybersecurity requirements for telecommunications or office systems. connectivity, EV chargers or autonomous vehicles.
Instead, this standard places great emphasis on risk identification methods and established procedures to deal with cyber risks. As such, it stipulates that if a compromised facility, charger or autonomous vehicle poses a direct risk to road users, it must be monitored, controlled and mitigated. Upstream Security enables stakeholders in the automotive ecosystem to identify risks and respond as required by the standard.
Reference:
Privacy settings on social media accounts
Loads of private statistics are being exchanged for the sake of personalization each second. And that offers upward push to a worrisome concern!
How are we able to alter on-line privateness? Well, revealing an excessive amount of records on-line leaves the door open to fraudulent activities.
Thanks to more potent protection enforcement, you may determine what is going public and what remains private. With in-intensity probing of the privateness settings of your social media accounts, you may experience a secure on-line experience.
As a marketer, we're the usage of social media to sell our business. However, we nonetheless want to take heed to our privateness. It is all too clean for hackers to get a keep of touchy records.
In this post, let`s discover a way to extrade social media privateness settings without affecting your boom and reach.
But first, research what the complete factor of this whole exercising is!
Why do you need to verify your privacy settings?
Photos and content uploaded to social media platforms are not always secure. They can be downloaded in the event of impersonation, inappropriate circulation, or other unethical activities. Therefore, it is essential to learn and understand how to use the security features offered by social networking sites.
Remember that every social media platform has its settings and some are more complicated than others. We'll look at the privacy settings of the most frequently used channels like Facebook, Twitter, LinkedIn, Pinterest, and Instagram.
Facebook privacy settings
Facebook allows you to set privacy from the Privacy tab, profile and photo settings. Let's take a look at each.
1. Facebook Privacy Tab
You can access the privacy settings by clicking the down arrow in the farright corner of the feed page. Click “Settings & Privacy”, then “Settings”.
Click "Security" in the left panel to open the "Settings and Security Tools" tab. You have multiple categories to tweak your visibility. You can also manage your privacy when posting to your timeline with the audience selector. This control remembers your changes, so future posts will be shared with the same audience unless you change them. It also has a feature that many people are not aware of. It's the ability to limit the audience of old posts on your timeline. For example, let's say you post publicly all the time on Facebook and want to improve your security. Click the Limit Previous Posts button. As a result, the content on your timeline that you have shared with friends of friends or the public becomes friends. However, there may be people who have shown interest in the position. People who have liked, commented on, or tagged them can still see the post. Additionally, you have the ability to modify the audience of your messages individually. Just go to the post you want to edit and select a different audience.
You can tweak a few other things, such as choosing who can send you friend requests. In addition, you can define who can search for you. This includes your personal information such as the email address and phone number used to find you. In addition, you can decide where to store message requests from friends of friends and others.
2. Facebook profile settings
Next, you need to update the privacy settings on your Facebook profile. Go to your profile and click "About". Here you can access your basic information. Various sections like work, education, contacts, family and relationships, life events, etc. will appear. In each section, you will find several items with separate privacy settings. Click the edit icon to the right of each section and choose who can see the information: public, friends or customs to make the necessary changes.
Here you can customize each section of your profile to set privacy to your comfort level. For example, if you want the public to know about your work and education, or hide your contact details and background information, you can set it as needed.
3. Facebook Photo Settings
Finally, adjust the privacy settings for the photo section. You can set your photo settings in two ways. The first is per album and the second is per image. If you're uploading photos directly to an album, click the object in the bottom right of the album to set privacy. For images you have uploaded individually, click on the desired image and select the edit icon to moderate specific settings.
Twitter privacy settings
Twitter's privacy settings are simple. Either you have a separate account or you don't have one. By default, the "Protect my posts" setting is disabled. Correspondingly, this setting allows anyone to see your tweets, be it your followers or anyone searching on Google.
Therefore, to change the privacy settings of your Twitter account, click the More button and then the "Security & Privacy" option on the left panel. Select "Your Account" and go directly to "Account Information".
Enter your password. Then click "Protected Tweets". Check the "Protect your Tweets" box to limit the visibility of your tweets to your followers. Uncheck the same box if you want to approve people to follow instead of allowing people to read your tweets.
Additionally, Twitter offers the option to add a location to your tweets. When you tweet with the location, Twitter will store the location. You can change the "on/off position" before each tweet. Additionally, you can decide whether users can find your Twitter profile using your email address or phone number. After making changes, be sure to click the Save Changes button at the bottom.
LinkedIn privacy settings
LinkedIn's privacy settings are slightly different from those of Facebook and Twitter. To change your privacy, click the "Me" button and select Settings and Privacy. There are many privacy settings here, but most deal with how your information is shared on LinkedIn.
If you want to decide what information people can see on LinkedIn, click "Edit your public profile". Uncheck all to keep all your connections private.
You can change the secret table to public, but you cannot change the public table to secret.
Instagram privacy settings
Like Twitter and Pinterest, Instagram's privacy settings are much simpler. By default, anyone can see your profile and posts and can also tag you in photos. However, you can make your posts private so that only your approved followers can see them.
Instagram's desktop site has limited functionality, and you can't change your image privacy there. Therefore, you will need to use the mobile app to change the privacy settings. Click on your profile icon and select "Settings". Edit the required sections from your Edit Profile tab.
You can also change your privacy account settings. If you make it private, only your users can see your photos. Even if you switch to a private profile, your existing followers will remain the same. Alternatively, if you want to block a specific follower, find that user's profile and tap the three-dot icon to block or restrict them.
Noteworthy:
Even if you have a private post and you like a public post or comment on a photo or video that a public user has uploaded, it is still visible to everyone. Alternatively, you can remove yourself from a tagged photo. This is useful if you find yourself tagged in a photo that you don't want to be tagged for work reasons. Inference
Social media privacy is a hot topic for individuals as well as marketers. Recent data breaches and information leaks have made it important to comply with privacy and security rules. With everyone taking off their socks to double their reach, calculated steps must be taken to protect their content and profiles from malicious users. Controlling privacy settings should not be in the middle of your end goals. Refer to the steps we mentioned above to stay protected without compromising participation.
Reference:
What is malware?
Malware, or malicious software, is any program or file that intentionally harms a computer, network, or server.
Types of malware include computer viruses, worms, Trojan horses, ransomware, and spyware. These malicious programs steal, encrypt and delete sensitive data; modify or disrupt basic computer functions and monitor end-user computer activity.
What does malware do? Malware can infect networks and devices and are designed to harm devices, networks, and/or their users in some way.
Depending on the type of malware and its purpose, this damage can manifest differently to the user or the device. In some cases, the impact of malware is relatively mild and benign, while in others it can be catastrophic.
Regardless of the method, all types of malware are designed to exploit devices at the expense of the user and for the benefit of the hacker i.e. the person who designed and/or implemented the software toxic.
How do malware infections happen? Malware authors use a variety of physical and virtual means to deliver malware that infects devices and networks. For example, malware can be delivered to the system by means of a USB drive, through popular collaboration tools, and by downloading via the drive, which automatically uploads the malware to the system without fail. without the user's consent or knowledge.
Phishing attacks are another common pattern of malware distribution, where emails disguised as legitimate messages contain malicious links or attachments that deliver malware executables. to unsuspecting users. Sophisticated malware attacks often involve the use of command and control servers that allow hackers to communicate with infected systems, steal sensitive data, and even remotely control devices compromised or compromised server.
New lines of malware include new evasion and obfuscation techniques designed not only to trick users, but also security administrators and anti-malware products. Some of these evasion techniques are based on simple tactics, such as using web proxies to hide malicious traffic or source IP addresses. More sophisticated threats include polymorphic malware that can repeatedly modify its underlying code to avoid detection by signature-based detection engines; anti-sandbox techniques that allow malware to detect when it is scanned and delay execution until it exits the sandbox; and unfiltered malware reside only in system RAM to avoid detection.
What are the different types of malware?
Different types of malware have distinct characteristics and characteristics. Types of malware include:
Viruses are the most common type of malware that can run and spread by infecting other programs or files.
The worm can reproduce itself without a host program and often spreads without any interaction from the malware's author.
A Trojan horse is designed to appear as legitimate software to gain access to the system. Once activated after installation, Trojans can perform their malicious functions.
Spyware collects information and data of devices and users, and observes user activities without their knowledge.
Ransomware infects users' systems and encrypts their data. The cybercriminal then demands ransom from the victim in exchange for decrypting the system data.
Rootkits gain administrator-level access to the victim's system. Once installed, the program gives hackers root or privileged access to the system.
A backdoor virus or Remote Access Trojan (RAT) secretly creates a backdoor in an infected computer system that allows hackers to gain remote access without warning users or system security programs.
The adware tracks the user's browser and download history for the purpose of displaying pop-up ads or banners to entice the user to make a purchase. For example, advertisers may use cookies to track the websites users visit for better ad targeting.
Keyloggers, also known as system monitors, keep track of almost everything a user does on their computer. This includes email, open web pages, programs, and keystrokes.
How to detect malware
Users can detect malware if they observe unusual activity such as sudden loss of disk space, unusually slow speeds, repeated crashes or crashes, or an increase in activity. unwanted internet and contextual advertising.
Anti-virus and anti-malware software may be installed on the device to detect and remove malware. These tools can provide real-time protection or detect and remove malware by running periodic system scans.
For example, Windows Defender is Microsoft's anti-malware software included with the Windows 10 "OS" operating system in the Windows Defender Security Center. Windows Defender protects from threats such as spyware, adware, and viruses. Users can set "fast" and "full" automatic scans, as well as set low, medium, high, and severe priority alerts.
How to remove malware
As mentioned, a lot of security software is designed to detect and stop malware, as well as remove it from an infected system.
Malwarebytes is an example of an anti-malware engine that handles malware detection and removal. It can remove malware from Windows, macOS, Android and iOS platforms. Malwarebytes can scan a user's registry files, running programs, hard drives, and individual files. If detected, the malware can then be quarantined and removed. However, unlike some other tools, users cannot schedule automatic scans.
How to prevent malware infection
Users can prevent malware in a number of ways. In the case of personal computer protection, users can install anti-malware software.
Users can prevent malware by adopting safety practices on their computers or other personal devices. This includes not opening attachments from unknown email addresses that may contain malware disguised as legitimate attachments - such emails may even be believed to come from companies. legitimate but has an unofficial email domain. Users should regularly update their anti-malware software as hackers are constantly adapting and developing new techniques to breach security software. Security software vendors are responding by releasing updates that fix these vulnerabilities. If users accidentally update their software, they could miss a patch that leaves them vulnerable to a preventable exploit.
In a corporate environment, the network is larger than the home network, and the financial stakes are higher. Organizations should take proactive steps to enforce malware protection. Precautions towards the outdoors include the following:
Double approval for business-to-business (B2B) transactions; and
Perform second-channel verification for business-to-consumer (B2C) transactions.
Internal business precautions include:
Offline malware deployment and threat detection to detect malware before it spreads;
Implement whitelist privacy policies whenever possible; and
Implemented advanced security at the web browser level.
Does Malware Affect Macs?
Malware can affect Macs as well as Windows. Windows devices have historically been considered a bigger target of malware attacks than Macs, in part because users can download apps for macOS through the App Store. Malwarebytes reported in 2020 that Mac malware surpassed PC malware for the first time. This is partly due to the popularity of Apple devices, which attracts more attention from hackers.
Malware History
The term malware was first used by computer scientist and security researcher Yisrael Radai in 1990. However, malware has existed for a long time before that.
One of the earliest known examples of malware was the Creeper virus in 1971, experimentally created by engineer Robert Thomas of BBN Technologies. Creeper is designed to infect mainframes on ARPANET. Although the program did not modify functionality, steal or delete data, it moved from one mainframe to another without permission while displaying a teletype message that read: "I a creep: tell me if you can." Creeper was later modified by computer scientist Ray Tomlinson, who added self-replication to viruses and created the first known computer worm. The concept of malware originated in the technology industry, and examples of viruses and worms began appearing on Apple and IBM PCs in the early 1980s before becoming popular with the advent of the World Wide. Web and the commercial Internet in the 1990s. Since then, malware - and the security strategies to prevent it - have only become more complex.
Malware-like programs
There are other types of programs that share characteristics with malware, but are distinctly different. An example is a PUP or possibly unwanted program. These are applications that trick users into installing them on their systems - such as browser toolbars - but do not perform any malicious functions once installed. However, there are cases where a PUP may contain spyware-like functionality or other hidden malicious functionality, in which case the PUP will be classified as malware.
DDoS on IOT
IoT is about connecting smart devices to the internet to create something that people already use in their daily lives. This article explains how IoT makes DDoS attacks more dangerous than ever, and how to prepare your business against these potentially devastating attacks today?
What is DDoS attack?
Distributed Denial of Service (DDoS) attack is a type of network attack in which multiple devices attack a single server. This is usually done by overloading the server connection and preventing it from receiving more data. The devices that launch this type of attack can be computers, servers, or even personal devices like smartphones, but they all have one thing in common: they need to be connected to the internet to participate. attack. DDoS attacks are so common that the biggest company in the industry, Cloudflare, has had to upgrade its services and add some new features and add an extra layer of protection to keep up with the growing demand. .
Why are these attacks more dangerous?
These attacks become more dangerous because the perpetrators can now use the Internet of Things (IoT) to make them more serious. They can do this by exploiting known vulnerabilities in home devices like Wi-Fi routers, security cameras, and smart TVs. Attackers can use these sensitive devices to deliver traffic to certain websites, disabling their servers. These attacks also pose a more serious threat to those whose devices are used in the botnet. Many victims of this botnet don't even know their devices are being used in this way, leaving them vulnerable to identity theft or even physical harm.
You can take steps to guard against this type of attack. Since most IoT devices have little or no security, updating their firmware is essential. This will reduce your chances of being part of a botnet. You should also ensure that your devices are always updated with the latest security patches for their operating systems. There are also apps you can run on your computer and smartphone to prevent them from being used in botnets. Finally, avoid clicking on links that appear in unsolicited emails. The types of attacks against IoT devices are on the rise. Some experts estimate that by 2022, 20 billion IoT devices will be in use. If you're not careful, you could end up with a botnet and your device will be used against you.
How does an IoT device make DDoS attacks worse? If you are new to DDoS attacks, it is a form of cyber attack in which the perpetrator clings to a single connection point and uses it to send multiple messages or requests for information. An IoT device, such as a baby monitor or thermostat, may have an Internet connection that is not secured by a firewall. The hacker would then hack into that device and use it to trigger a DDoS attack on your company's website or another target. If your business's website is down, it can have a serious impact on your business. The best defense against IoT DDoS attacks is to take steps to secure all of your devices.
What types of IoT devices are most at risk?
Cameras are one of the most common IoT devices targeted by malicious actors. Hackers will scan for any publicly accessible IP address with the camera and then use it to launch their DDoS attack. This is what happened to one of the largest DDoS attacks ever observed, with an estimated size of 1.7 terabits per second.
How to protect my IoT devices? The best way to protect your IoT devices is to configure a firewall to restrict inbound and outbound traffic. It is important that you use a password and preferably the device to change its default login information. To avoid these problems, you can block all incoming and outgoing traffic connecting to your device. Alternatively, you can use a virtual private network (VPN) to secure your internet traffic and revoke your device's access to all external networks.
Inference
In conclusion, IoT has proven to be an integral part of many DDoS attacks. It has been shown that they can be used to spy and launch a distributed attack. In the future, attacks of this type will only become more dangerous as the number of IoT devices grows exponentially.
Reference:
Introduction to XSS Attack
A cross-Site Scripting attack is a malicious code injection, which will be executed in the victim’s browser. The malicious script can be saved on the webserver and executed every time when the user calls the appropriate functionality. It can also be performed with the other methods – without any saved script in the webserver.
The main purpose of this attack is to steal the other user’s identity data – cookies, session tokens, and other information. In most cases, this attack is being used to steal the other person‘s cookies. As we know, cookies help us to log in automatically. Therefore with stolen cookies, we can log in with the other identities. And this is one of the reasons, why this attack is considered one of the riskiest attacks.
An XSS attack is being performed on the client-side. It can be performed with different client-side programming languages. However, most often this attack is performed with Javascript and HTML.
How is XSS performed?
A cross-site scripting attack means sending and injecting malicious code or scripts. Malicious code is typically written using client-side programming languages such as Javascript, HTML, VBScript, and Flash. However, Javascript and HTML are primarily used to carry out this attack.
This attack can be carried out in various ways. Depending on the type of XSS attack, the malicious script will be displayed in the victim's browser or stored in the database and executed each time the user calls the appropriate function.
The main reason behind this attack is improper validation of user input, which can leak malicious input into the output. Malicious users can enter scripts that are injected into the website's code. Then the browser will not be able to determine if the executed code is malicious.
As such, the malicious script is executed in the victim's browser or the user is presented with a fake form. XSS attacks come in several forms.
The main forms of cross-site scripting are:
Malicious scripts running on the client side can lead to cross-site scripting.
A fake page or form presented to the user (where the victim enters credentials or clicks a malicious link).
Websites that display ads.
Malicious emails sent to victims. This attack occurs when a malicious user finds a vulnerable part of a website and submits it as well-formed malicious input. A malicious script is injected into the code and sent as output to the end user.
Types of cross-site scripting attacks
The main purpose of the XSS attack is to steal someone else's girlfriend's identity. As already mentioned, it could be a cookie, session token, etc. XSS can also be used to display fake pages and forms to victims. However, this attack can be carried out in various ways.
This attack falls into three main categories as shown below.
#1) Reflected XSS – This attack occurs when malicious scripts are not stored on his web server, but are reflected in the website results. #2) Stored XSS – This attack occurs when malicious scripts are persistently stored on a web server.
#3) DOM – This happens when the DOM environment has changed but the code remains the same.
Let's take a closer look at them.
XSS test tool
Cross-site scripting attacks are one of the most common and dangerous attacks, so there are many tools to test them automatically. You can find various scanners that look for potential XSS attack vulnerabilities, such as Nesus and Nikto. Both are considered very reliable.
From my career as a software tester, I would like to mention SOAP UI tools. SOAP UI can be considered a very powerful tool for checking for possible XSS attacks. A ready-made template is included to check this attack. This greatly simplifies the testing process.
However, in order to test this vulnerability with the SOAP UI tool, tests at the API level must already be automated with this tool. Another solution for testing against XSS is browser plugins. However, plugins are considered a rather weak tool for defending against this kind of attack. Even with automated testing, the testers should have a good knowledge of this type of attack and be able to analyze the results accordingly.
Good knowledge also helps when choosing a testing tool. It's also important to know that manual testing is also a good practice when using automated tools to scan for vulnerabilities, and that testers can review and analyze the results.
How to prevent XSS
Although this type of attack is considered one of the most dangerous and risky attacks, you should still have a preventive plan in place. Due to the frequency of this attack, there are many ways to prevent it.
The main prevention methods commonly used are:
data verification
filter
escape
The first step in preventing this attack is input validation. User input can lead to output, so anything the user types must be validated for accuracy. Data validation is a cornerstone of ensuring system security. Recall that the idea of validation is to disallow malformed input.
So while this helps mitigate risk, it may not be enough to prevent potential XSS vulnerabilities.
Another good prevention method is user input filtering. The idea of filtering is to look for dangerous keywords from user input and remove them or replace them with empty strings.
These keywords are:
[delete][delete] tag
javascript commands
HTML markup
Input filtering is fairly easy to implement. You can also do it in different ways.
As:
It's from the developer who wrote the server-side code.
Appropriate programming language libraries are used.
In this case, some developers write their own code to check for appropriate keywords and remove them. However, an easier way is to choose the right programming language library and filter the user's input. Note that these libraries are used and tested by many developers, so using them is a more reliable method.
Another possible prevention method is sign escaping. In this case the corresponding character is modified by a special code. For example, the < escape character looks like this: <. It is important to know that you can find a suitable library for escaping the character. In the meantime, don't forget proper testing as well. You should invest in good software testers and knowledge of reliable software testing tools. In this way, good software quality is more reliably guaranteed.
technology prevention
As already mentioned, filtering and escaping are the main prevention methods. However, different programming languages can do it differently. Some programming languages have good filtering libraries, some don't.
Note that the Java and PHP programming languages have appropriate libraries, so filtering can be done very easily.
Java technology is so ubiquitous that there are many solutions. If you're using Spring technology and want to escape HTML throughout your application, you'll need to write the appropriate code in your project's web.xml file.
defaultHtmlEscape
true
This code toggles HTML escaping for the entire application.
If you want to change the HTML escaping of the form on the corresponding page, write the code like this:
defaultHtmlEscape="true">
There are many ready-made XSS filters in the form of .jar files. Remember that you have to add the .jar file to your project or you can't use that library. One such XSS filter is the servlet filter, xssflt.jar. This .jar file can be easily downloaded from the Internet and added to your project.
This filter examines every request sent to your application and removes it from potential injection.
If you add an external.jar file to your project, you must also include it in your web.xml file.
XSSFilter
com.cj.xss.XSSFilter
Another possible solution is the ESAPI library. The ESAPI library is compatible with many programming languages. You can find ESAPI libraries for Java and PHP programming languages. This is an open source free library that helps you control the security of your application.
Conclusion
We strongly recommend that you evaluate the risk posed by a potential XSS attack during testing. XSS attacks can affect web applications that appear safe.
This is considered one of the most dangerous and dangerous attacks. So don't forget this kind of test. It is important to fully understand this attack when testing against XSS. This is the basis for correctly analyzing test results and choosing the right test tool.
Are you a tester investigating cross-site scripting XSS attacks? Do you have any interesting facts about XSS attacks that might help our readers? Share your experiences with us in the comments below!!
Reference
Hacking is widespread on the Internet. Even big companies like Evernote have been hacked, so it's not hard to imagine that you, as an individual, could be hacked too. While this experience is actually quite common, it doesn't always make it less painful. Immediately after a tragic event, you are confused and don't know what to do.
No matter what you've been through, whether it's phishing, hacking, or malware, there are some simple steps you can take right away to help restore your sanity to life. try to find the motive behind the hack
I know you are in a stressful situation. The last thing you can do right now is take the time to understand why you were hacked. A prime example, of course, is when a bank account is hacked. In this case, it is clear that the hackers were most likely after your money.
There may be other cases as well. B. Your email has been hacked. In this case you have many options. Hackers can spam emails from your address or call your contacts to demand money. On the other hand, they may use your email address to reset passwords for other accounts. They may even use your email to try to find their way into your business.In any case, take a moment to figure out what the reason is. You can stop hackers and take appropriate measures to prevent such things from happening in the future. Plus, it can show you how to recover quickly.
password reset
Regardless of which services are affected, you should change your password immediately. In fact, you should not only change your password on the affected service, but also on all other services that use the same or similar password. In fact, reusing passwords is definitely not recommended. Therefore, passwords should be changed regularly. Again, the first response when you realize your account has been hacked is to change your password immediately, both on the affected service and anywhere you've used similar passwords. “Password reuse is actually very common and puts many accounts at risk,” says Pauline Johnson, a security researcher at a local essay service company. In fact, people tend to use similar passwords to aid in memory, not realizing that they are taking huge risks in doing so.
A good way around this is to use a password manager. Using your password to access Password Manager generates strong and different passwords for other services. This way all your passwords are stored in one place. Make sure your password manager password is not similar to other passwords.
Update and scan your machine
Your computer could have been an attacker's primary entry point for him. In most cases, it is the victim who installs the malware on their computer and the first thing the victim has to do when they detect its presence is to remove it. Start updating to the latest version of the operating system. Then download a good antivirus software and scan your computer for any malware that may be present in your account. It's a simple process, but it's important to prevent your machine from being hijacked. Use robust antivirus software. A well-known, trusted, and affordable brand name is more likely to do the job well. However, no antivirus software is perfect. Its success rate ranges from 50% to 75%. However, this hit rate is better than nothing.
get your account back
Luckily, most online social platforms have easy ways to get your account back from someone who has taken over your account. There are methods for Twitter, Microsoft, Google, Facebook, and Apple. They will usually ask you a series of questions about your account that will help verify your identity. helps. You can recover your account even if you don't use the above platforms. Search Google for specific recovery methods for this platform.
Make sure there are no backdoors
The best hackers don't just break into computers and online accounts. It also comes out a backdoor, so even if you kick it out, it will come right back. Therefore, even after the account is restored, we must ensure that there are no backdoors that an attacker can use to regain access. For e-mail, for example, you should check your filters and rules to make sure you are not unknowingly forwarding your e-mail to another account. You should also check your security questions to see if the answers have changed. Check financial activity
If the hacked account is a financial account, all activity on that account should be thoroughly investigated. Address settings, payment methods, linked accounts, and more. return.
Confirm your account
This is more of a mindset than an action you should take. Hackers sometimes hack accounts just to give them access to something else. They can hack your email and reset your password elsewhere. If they hacked your cloud account, it could be to access certain files or folders. So, you should always scrutinize and check all files, folders and accounts associated with hacked accounts. Reset all passwords and move all important information and take steps to protect it. Assume everything is at stake and act accordingly.
credit guarantee
One of his favorite crimes for cyber attackers is identity theft. So take your time and check the security of your loan. Contact all major credit bureaus and let them know you were hacked. You can then block the credit. It may be free or paid, depending on where you live and whether you have already filed a police report. report hacked
Hacking isn't just for you. Hackers may be using your account to trick your friends into sending money. This can be done by impersonating you and claiming that you are in an emergency and need money. You may also want your friend to know because the breach involves accessing data pertaining to your friend.
The above reasons are important reasons to report if you've been hacked, but not the most important reasons. The biggest reason to tell people you've been hacked is to raise awareness. Ultimately prevention is better than cure. Letting your friends and the public know what you went through and how you got hacked gives them a chance to use the correct prevention methods. Keep your software up to date, use good passwords, and always back up your data for security reasons.
Conclusion
Being hacked is certainly confusing and frustrating. However, we recommend that you keep your cool and take necessary steps to mitigate the damage and keep hackers out of your private space. By following the steps above, you can take a step towards restoring sanity to your life.
Reference:
What is a botnet?
A botnet is a collection of devices connected over the internet, each running a single bot or set of bots. Distributed denial of service attacks (DDoS) are the most common use of botnets. However, cryptomining and click fraud are other activities performed by botnets to give hackers access to your device. Once a botnet is established, an attacker can use command and control (C&C) software to control the botnet. One of the main advantages of botnets is that they can use the computing power of hundreds or thousands of computers. Attacks come from so many different devices that the attacker's C&C is hidden and difficult to block or track.
1. Botnet Attacks Increased 23% Quarterly
Spamhaus' Q4 2021 Botnet Threat Update reported a 23% increase in botnet C&C (command and control) attacks from 2,656 in Q3 2021 to 3,271 in Q4 2021. I'm here.
2. Russia has the largest share of botnet C&C
The report further shows that his C&C for botnets increased by 64% between Q2 and Q3 of 2021 in Russia. From Q3 to Q4, these attacks increased by 124%, an even more dramatic increase.
3. The most common type of malware used was a credential stealer
Malware-Dropper is a malware bot that performs various malicious activities such as downloading and executing additional malware, participating in DDoS attacks, stealing credentials, etc. Malware bots tracked in Q3 2021 was the top of In the fourth quarter of 2021, the threat of credential theft grew and even surpassed it.
4. DDoS attacks set new records in the first half of 2021
The NetScout H1 2021 Threat Intelligence Report reveals that 5.4 million DDoS attacks were launched in the first half of 2021, an 11% year-over-year increase. DDoS attacks are typically launched using botnets to overwhelm targeted servers.
5. DDoS Extortion Attacks Targeting ISPs
NetScout also reported a spike in cybercriminals targeting his ISPs via the Lazarus DDoS ransomware campaign, which focused on authoritative domain servers in 2021. These DNS servers match IP addresses with domain names and provide details about the location of recursive DNS name server websites.
6. Adaptive DDoS attacks will rise in 2021
In 2021, attackers have developed adaptive DDoS attack strategies to evade traditional defensive techniques. Attackers tailor each attack to bypass multiple layers of DDoS mitigation for both cloud and on-premises attacks.
7. The financial sector is an industry targeted by botnets
Interpol's 2020 ASEAN Cyberthreat Assessment measured the impact of botnets on various organizations by industry. According to the report, the main targets in 2019 were the financial sector and its customers. Attackers wanted to remotely control victims' computers to collect personal information, such as banking information, or to install and distribute other types of malware.
8. Gafgyt and Mirai IoT Botnets Account for Half of All DDoS Attacks
His 2021 first half report for NetScout also revealed that attackers are using botnet clusters tracked around the world to enable more than 2.8 million DDoS attacks. The Gafgyt and Mirai botnets accounted for over half of these attacks. According to the report, “The ransomware gang added triple extortion DDoS tactics to its repertoire. At the same time, a Fancy Lazarus DDoS extortion campaign was launched, with multiple campaigns specifically focused on his ISP and its authoritative DNS servers. It threatened industry organizations.”
9. Latin America region networks hosted the most active botnet C&C
Spamhaus reports that his 60% of active botnet C&C entries in Q4 2021 were hosted in his Latm region. The chart below shows the networks that hosted the most C&C botnets in Q4 2021. Spamhaus explains that the hosts in the table either have abuse issues or do not take appropriate action when they receive reports of abuse.
How does botnet takeover work?
The first step for an attacker to create a botnet is to obtain or create malware that can be controlled remotely over the Internet.
Attackers install malware on targeted computers over the Internet. This can be by hosting files on compromised websites for victims to download, by sending files as email attachments, or by spoofing via messaging apps that infect devices when users click on links. You can do it by sending the URL of Hackers can also search the internet for vulnerable IoT devices and perform brute force login attempts to infect devices remotely.
Once a computer is infected, it makes the hacker`s job easier to spread the infection to other devices that interact over the internet. For example, the hacker could set up the malware so that the infected system sends spam emails to other systems to spread the infection, thus giving them control of a larger botnet cluster.
The malware used is often a trojan-style variant disguised as a legitimate file hiding behind an executable. Opening the executable is enough to spread the infection to another device, but sometimes IoT infections (see example below) like Mirai don`t require any user input to infect and spread between devices.
Examples of botnet attacks
Malware used to create a botnet comes in many forms, but the following examples are some of the commonly used methods to trick users into opening an infected file:
You visit a compromised website (without knowing) to find a valuable piece of software designed to speed up your computer. When you download the executable, it contains the filename you expect, so go ahead and open it. This infects the device and allows hackers to create botnets.
Someone emails you his message and the sender appears genuine and the image attachment or billing agreement calls for urgent action. You open the attachment, but it's not a PDF or JPG, it's an exe containing malware ready to infect your device.
Malvertising is a new method used by attackers to infect devices. Injects malware into pop-up and banner ads. If you visit a compromised website, you don't even need to click an ad to get infected. A file containing the infection needed to create a botnet may be automatically downloaded to your device.
Reference:
0 notes
Text
BERYK Consulting GmbH
BERYK Consulting GmbH offers extensive knowledge and experience in the development of future E/E systems in the automotive industry. Our services and projects focus on meeting ISO 26262 and ASPICE requirements, with our main focus being on helping develop future E/E systems according to ISO26262 and ASPICE. We have experience working with many different products and processes, with our independent 3rd party status giving you an on-site resource for your team. Alongside this, we offer a full package of services regarding quality management during the development process. Our services and projects focus on meeting the requirements of ISO26262 and ASPICE. By being an independent 3rd party we can help you implement the standard ISO26262 in different products and processes.
To know more visit: https://beryk.de/
0 notes
Text
ISTQB CTFL Automotive Software Tester CTFL-AuT Exam Questions
ISTQB Certified Tester Foundation Level - Automotive Software Tester CTFL-AuT exam is one of the most popular IT certifications. PassQuestion provides the latest ISTQB CTFL Automotive Software Tester CTFL-AuT Exam Questions for your best preparation. These CTFL-AuT Exam Questions are prepared by the top experts in the market who have best knowledge and skills to let the candidates achieve success in iSQI CTFL-AuT Exam. Practice in the ISTQB CTFL Automotive Software Tester CTFL-AuT Exam Questions gives chance to the candidates to improve their weaknesses and then attempt the CTFL-AuT exam with complete confidence and preparation.
CTFL-AuT Exam Overview - ISTQB Certified Tester Foundation Level - Automotive Software Tester
The ISTQB Certified Tester Automotive Software Tester (CTFL-AuT) certification focuses on the specific requirements for "testing E/E systems" in the automotive environment on the basis of established standards (Automotive SPICE, ISO 26262, AUTOSAR®, etc.). It also covers testing in virtual environments (including XiL), and automotive-specific static and dynamic test techniques.
The ISTQB CTFL Automotive Software Tester certification validates the skills of the professionals who are working within automotive projects. This certification is also beneficial for the ones who are planning to start the implementation of special automotive testing techniques in the near future. The certification trains you in Automotive activities, roles, techniques, and methodologies specific to the role of an Automotive Software Tester.
The Automotive Software Tester certification is aimed at anyone involved in software testing in the automotive area including testers, test analysts, test engineers, test consultants, test managers, release testers, and software developers. It may also be useful to people in the role of project manager, quality manager, software development manager, system analyst (business analysts), IT manager or management consultants, who wish to acquire basic knowledge and basic understanding of the topic software testing in the automotive area.
To gain this certification, candidates must hold the Certified Tester Foundation Level certificate.
Exam Structure
Number of Questions: 40 Multiple Choice Total Points: 40 Passing Score: 65% Exam Length (mins): 60 (+25% Non-Native Language) Cost: $260USD Language: English
Exam OutlineModule 1 – Introduction
1.1 Requirements from divergent project objectives and increasing product complexity 1.2 Project aspects influenced by standards 1.3 The six generic phases in the system lifecycle 1.4 The contribution/participation of the tester in the release process
Module 2 – Standards for the testing of E/E systems
2.1 Automotive SPICE (ASPICE) 2.2 ISO 26262 2.3 AUTOSAR 2.4 Comparison
Module 3 – Testing in a virtual environment
3.1 Test environment in general 3.2 Testing in XiL test environments
Module 4 – Automotive-specific static and dynamic test techniques
4.1 Static test techniques 4.2 Dynamic test techniques
View Online ISTQB CTFL Automotive Software Tester CTFL-AuT Free Questions
ISO 26262 recognizes several context factors which influence the selection of testing techniques. Which statement is correct? Please choose the BEST POSSIBLE answer. A.An testing techniques are always applied to one test basis. The specific techniques, e.g. equivalence partition analysis, however, can always be applied. B.ISO 26262 recommends specific testing techniques depending on the ASH level. Furthermore, the current state of technology must be considered C.The risk assessment provides insights regarding the risks, whose causes will then be tested Intensively (independent of the testing technique). D.For the selection and the applicability of the test techniques, the test basis is important, but not fie test level. Answer : B
Which statement characterizes back-to-back testing? A.Back-to-back testing is a variation of pair programming in which the testers should sit back to back to be able to work as independently as possible from each other. B.Back-to-back testing compares test objects with mainly overlapping requirements to recognize the results of requirement change. C.Back-to-back testing compares lest objects which are based on the same requirements. D.Back-to-back testing compares different execution environments of the same test object Answer : C
Which statement regarding requirements-based testing is true? A.Requirements-based testing can be combined with other lest practices or testing techniques. B.Requirements-based testing can solve issues like complete requirements C.Only extensive and delated requirements can be covered completely by the tester. D.Requirements-based testing is a testing technique Answer : D
Which statement regarding the coding standard MlSRA-C:2012 Is true? A.MISRA-C defines rules and guidelines. Rules are verifiable by static analysis tools and are always required. B.MISRA-C defines rules and guidelines that are supposed to help avoid anomalies In object-oriented developed software (e.g. in C++) C.MISRA-C defines rules that include among others that the source code should not include nested comments. D.A typical rule in MISRA-C is that the developer has documented the implemented behavior wen. Answer : B
Which statement regarding coding standards Is most true? A.Coding standards should increase the maintainability of the source code. B.Coding standards should educate the programmer C.Coding standards should increase the efficiency of the programmer D.Coding standards should increase the efficiency of the source code. Answer : C
0 notes
Photo

The goal of ISO SAE 21434 is to build on the ISO 26262 functional safety standard and provide a framework similar to it for the entire life cycle of road vehicles. The major components of this new standard are
Security management
Project-dependent cyber security management
Continuous cyber security activities
Associated risk assessment methods
Cyber security within the concept product development and post-development stages of road vehicles.
0 notes
Text
Title: Navigating Automotive Intelligence: Embedded Systems Course
Course Overview:
The Automotive Embedded Systems Course at Technoscripts is a specialized program designed to provide participants with a deep understanding of embedded systems within the automotive industry. This course focuses on the intricate design, development, and implementation of software and hardware components in vehicles, covering essential concepts and practical applications.
Course Duration:
Total Hours: 3 Months
Prerequisites:
Basic knowledge of embedded systems
Proficiency in programming languages (C, C++)
Familiarity with microcontrollers and electronics
Course Outline:
Introduction to Automotive Embedded Systems
Overview of embedded systems in automotive applications
Significance and impact of embedded systems in the automotive sector
Current trends and challenges in automotive embedded systems
Embedded Hardware in Vehicles
Microcontrollers and microprocessors used in automotive systems
Sensors, actuators, and interfaces in vehicles
Communication protocols such as CAN, LIN, and FlexRay
Embedded Software Development for Automotive Applications
Real-time operating systems (RTOS) for automotive environments
Software architecture design for automotive systems
Programming techniques for embedded systems in vehicles
Automotive Networking Technologies
Controller Area Network (CAN) bus architecture and applications
Diagnostic protocols like OBD-II and UDS
Integration of Ethernet and other communication protocols in vehicles
Embedded System Security in Automotive Industry
Cybersecurity threats and vulnerabilities in automotive systems
Best practices for secure coding in embedded software
Implementation of intrusion detection and prevention mechanisms in vehicles
Functional Safety Standards in Automotive Systems
Overview of ISO 26262 standard for functional safety in automobiles
Safety mechanisms and requirements specific to embedded systems
Application of Failure Modes and Effects Analysis (FMEA) in automotive settings
Automotive Embedded Software Testing
Testing methodologies for automotive software development
Validation and verification techniques for embedded systems in vehicles
Tools and frameworks used for testing automotive embedded software
Case Studies and Projects
Real-world examples showcasing automotive embedded systems
Hands-on projects to apply learned concepts practically
Industry standards and best practices within the automotive embedded systems domain
Assessment:
Regular quizzes and assessments to gauge understanding
Practical assignments to implement theoretical knowledge
Final project demonstrating skills acquired during the course
Certification:
Upon successful completion of the Automotive Embedded Systems Course at Technoscripts, participants will receive a certificate of completion, validating their expertise in designing and developing embedded systems for automotive applications.
This detailed course outline offers a structured approach to delivering an informative and engaging course on automotive embedded systems at Technoscripts. It covers essential topics, hands-on projects, and assessments to ensure participants acquire practical skills and knowledge relevant to this specialized field. Feel free to customize the content further based on specific learning objectives and audience requirements.

#automotiveembeddedsystemscourse#automotiveembeddedtestingcourse#embeddedtraining#embeddedcourse#embeddedclasses#embeddedsystemscoursepune#embeddedinstitute#automotiveembeddedcourse#automotiveembeddedclasses#automotiveembeddedinstitute
0 notes
Text
Automotive Embedded Systems and Embedded Training Online
Course Overview:
The Automotive Embedded Systems and Embedded Training Online course offered by Embedded Box provides comprehensive training in the design, development, and implementation of embedded systems tailored specifically for the automotive industry. This course equips students with the knowledge and practical skills required to excel in the rapidly evolving field of automotive electronics and embedded systems.
Course Duration: 6 months
Course Content:
1. Introduction to Automotive Embedded Systems
Overview of automotive embedded systems
Importance of embedded systems in automotive applications
Trends and advancements in automotive electronics
2. Embedded C Programming for Automotive Applications
Introduction to the C programming language
Data types, operators, and expressions
Control structures and functions in C
Memory management and optimization techniques
Debugging and testing techniques for embedded systems
3. Microcontrollers and Microprocessors in Automotive Systems
Introduction to microcontrollers and microprocessors
Architecture and features of popular automotive-grade microcontrollers
Embedded development tools and IDEs
Interfacing peripherals and sensors with microcontrollers
Real-time operating systems (RTOS) for automotive applications
4. Automotive Communication Protocols
CAN (Controller Area Network) protocol fundamentals
LIN (Local Interconnect Network) protocol overview
FlexRay and Ethernet in-vehicle networking
Introduction to automotive diagnostic protocols (OBD-II, UDS)
5. Embedded Software Development Tools
Introduction to Integrated Development Environments (IDEs)
Debugging tools and techniques (emulators, simulators)
Version control systems (Git, SVN) for collaborative development
Code optimization and profiling tools
6. Automotive Embedded Software Design
Software architecture and design principles for automotive systems
Model-Based Design (MBD) using tools like Simulink
Design considerations for safety-critical automotive applications
Implementing automotive standards such as ISO 26262
7. Embedded Linux for Automotive Systems
Introduction to Linux kernel architecture
Customizing and configuring the Linux kernel for embedded systems
Device drivers development and integration
Embedded Linux filesystems and bootloaders
Yocto Project for building custom Linux distributions
8. Hands-on Projects and Case Studies
Design and implementation of automotive embedded systems projects
Integration of sensors, actuators, and communication modules
Real-world automotive system simulations and testing
Case studies on automotive embedded systems applications and challenges
9. Career Development and Industry Insights
Guidance on building a career in automotive embedded systems
Industry trends, job opportunities, and emerging technologies
Interview preparation and resume building workshops
Guest lectures from industry experts and professionals
10. Capstone Project
Final project where students apply their skills to design and develop a complete automotive embedded system
Project presentation and demonstration to showcase proficiency in automotive embedded systems development
Prerequisites:
Basic understanding of programming concepts
Familiarity with electronics and digital circuits
Access to a computer with internet connectivity
Certification:
Upon successful completion of the Automotive Embedded Systems and Embedded Training Online course, students will receive a certificate from Embedded Box, validating their proficiency in automotive embedded systems development.

#embeddedtraining#embeddedcourses#embeddedsystems#embedded training system#embeddedd#embeddedcourse#embeddedsystem#embeddedsysytem#embeddedsystemcourse#embedded
0 notes