#Hypertext Transfer Protocol
Explore tagged Tumblr posts
Photo
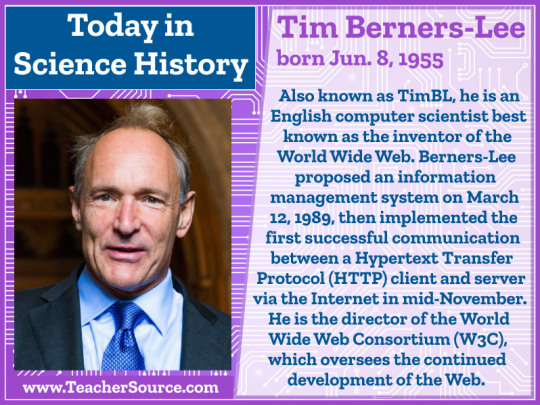
Tim Berners-Lee was born on June 8, 1955. Also known as TimBL, he is an English computer scientist best known as the inventor of the World Wide Web. Berners-Lee proposed an information management system on March 12, 1989, then implemented the first successful communication between a Hypertext Transfer Protocol (HTTP) client and server via the Internet in mid-November. He is the director of the World Wide Web Consortium (W3C), which oversees the continued development of the Web.
#tim berners-lee#internet#world wide web#hypertext transfer protocol#http#world wide web consortium#w3c#TimBL#science#science birthdays#science history#on this day#on this day in science history
3 notes
·
View notes
Text
GTBank Confirms Attempt To Compromise Website, Assures Customers No Data Breach
Guaranty Trust Bank (GTB) Ltd says there were attempts to compromise its website domain but customers’ data were not affected. On Wednesday, reports circulated that there was a compromise on the domain address of GTBank by suspected cyber criminals. The attackers were said to have created another hypertext transfer protocol (HTTP) layer of the website in an apparent ploy to steal customers’ data…
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
XHR stands for "XML HTTP Request", where XML is the "eXtensible Markup Language" and HTTP is the "Hypertext Transfer Protocol", so the full expansion of XHR is "extensible markup language hypertext transfer protocol request", so those 3 letters expand to 56 letters (62 with spaces), and this got me wondering, there must be acronyms or initialisms with an even greater ratio of "expanded length"/"unexpanded length", but apart from recursive acronyms I can't think of longer examples.
Can anyone else think of any?
#I thought maybe some joke acronyms would work#but I think it has to be another initialism where some letters stand for other initialisms in order to break 56/3
270 notes
·
View notes
Text
The year was 2024. My friend had given me a Uniform Resource Locator, which I plugged into the Hypertext Transfer Protocol.
Bits flowed into my computer from hundreds of miles away, and the Picture Elements of my Liquid Crystal Display lit up as the hypertext rendered.
In an all too familiar pattern. Once again, I had become the victim of a Rick Roll.
10 notes
·
View notes
Text
World Wide Web
The internet was created to give the US military a communication system that could survive a nuclear war. The idea was to have an interconnected network of computers without hardline routing. Instead it was handled by variable heuristics. This means that even if half of the nodes were destroyed, the system could find a way to route along different paths and still, eventually, reach it's destination.
It was a brilliant form of asynchronous communication.
Academia had created it, and quickly found great use in networked communication and remote data processing.
And now we use it to view porn. So, what happened?
The World Wide Web. Before the WWW, you had to know the IP address of your friend's computer, be given permission, and then log into his bulletin board service.
The World Wide Web was a system of protocols that created a public internet front. ANY person could find it through HyperText Transfer Protocol, use a public log-in, and access the web site. The HTTP was designed to be crawled by search engines, allowing them to effectively index the entirety of the public-facing internet.
One of the first real search engines was call WebCrawler, because it - crawled - the HTTP of the WWW.
They would load page, then open and index every - single - hyperlink contained in the document, storing and indexing meta tags.
We also ended up with MetaCrawler, that would index multiple other search engines, allowing it to provide a far more comprehensive system of results.
Nowadays, most search engines are meta crawlers, and because of the prominence of Google in searching, Google results are over weighted, meaning that there is almost no way to escape the dogmatism of Google's biased search algorithms.
And the reason we use it for porn is that this was the first viable online business plan.
6 notes
·
View notes
Text
HTTP to HTTPS: The Incorporation of the Secure Sockets Layer TLS

What is HTTP vs. HTTPS? HTTP (Hypertext Transfer Protocol) is the basic protocol that enables communication between your browser and the server hosting the website. It has been the foundation of the web since its inception. However, HTTP lacks encryption, making it vulnerable to cyberattacks like eavesdropping, man-in-the-middle attacks, and data tampering.
HTTPS (Hypertext Transfer Protocol Secure) is an upgraded version of HTTP that integrates SSL/TLS encryption, ensuring a secure transfer of data between a user’s browser and the web server. HTTPS protects sensitive information, such as passwords, credit card details, and personal information, making it essential for websites that collect user data.
Learn more: What is HTTP vs. HTTPS? HTTP (Hypertext Transfer Protocol) is the basic protocol that enables communication between your browser and the server hosting the website. It has been the foundation of the web since its inception. However, HTTP lacks encryption, making it vulnerable to cyberattacks like eavesdropping, man-in-the-middle attacks, and data tampering.
HTTPS (Hypertext Transfer Protocol Secure) is an upgraded version of HTTP that integrates SSL/TLS encryption, ensuring a secure transfer of data between a user’s browser and the web server. HTTPS protects sensitive information, such as passwords, credit card details, and personal information, making it essential for websites that collect user data.
Learn more: https://www.ayansujon.com/http-to-https-the-incorporation-of-the-secure-sockets-layer-tls/
#wordpress#sslcertificates#sslcertificateforwebsite#wordpresssecurity#wordpresssecurityblog#wordpresssecurityexpert
2 notes
·
View notes
Text
go benie studios proud to announce cross posting to cohost, a website that proudly uses URL domains and Hypertext Transfer Protocol Secure to ensure users can access the site anytime they want from web browsers.
11 notes
·
View notes
Text

HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are both protocols used for transmitting data over the internet. However, they differ significantly in terms of security, data integrity, and privacy. This analysis aims to compare and contrast HTTP and HTTPS, highlighting their key differences, advantages, and disadvantages.
1. Security:
HTTP: HTTP operates over plaintext, meaning data sent between the client and server is not encrypted. This makes it vulnerable to interception, manipulation, and eavesdropping attacks. Any data transmitted via HTTP can be easily accessed by malicious actors.
HTTPS: HTTPS encrypts data using Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols, providing a secure connection between the client and server. This encryption ensures that even if intercepted, the data remains unreadable to unauthorized parties, significantly enhancing security.
2. Data Integrity:
HTTP: Since data transmitted over HTTP is not encrypted, there's no built-in mechanism to verify its integrity. This makes HTTP susceptible to data tampering during transmission. Any alterations made to the data during transit may go unnoticed.
HTTPS: HTTPS ensures data integrity by employing cryptographic algorithms to verify that the transmitted data remains unchanged during transit. Any attempt to tamper with the data will result in the receiver being alerted to the integrity breach.
3. Authentication:
HTTP: HTTP does not provide any mechanisms for server authentication, making it vulnerable to man-in-the-middle attacks. Clients cannot be certain that they are communicating with the intended server, as there is no way to verify its authenticity.
HTTPS: HTTPS authenticates the server's identity using digital certificates issued by trusted Certificate Authorities (CAs). This authentication process ensures that clients can trust the server they are communicating with, mitigating the risk of impersonation and unauthorized access.
4. Privacy:
HTTP: Since HTTP transmissions are unencrypted, sensitive information such as login credentials, personal data, and financial details are transmitted in plaintext, leaving users vulnerable to privacy breaches.
HTTPS: HTTPS encrypts sensitive data, safeguarding user privacy and preventing unauthorized parties from intercepting and accessing confidential information.
5. Performance:
HTTP: HTTP typically offers faster performance compared to HTTPS, as there is no overhead associated with encryption and decryption processes. This can be advantageous for websites that prioritize speed over security.
HTTPS: HTTPS may introduce a slight performance overhead due to the encryption and decryption processes involved. However, advancements in encryption algorithms and hardware acceleration have minimized this overhead, making the difference in performance negligible for most users.
#seoexpertshankarhalder #seospecialistshankarhalder #shankarhalder #seoservice
2 notes
·
View notes
Text
The Role Of HTTPS In SEO Secure Your Accounting Website
In the ever-evolving landscape of digital security and online presence, the importance of securing your accounting website with HTTPS cannot be overstated. HTTPS, or Hypertext Transfer Protocol Secure, is not just a technical jargon—it’s a critical element that significantly impacts your website’s search engine optimization (SEO) and, ultimately, the trustworthiness of your accounting firm. Let’s delve into the reasons why HTTPS is essential and how it can play a pivotal role in securing and enhancing your online presence.
Security Assurance:
HTTPS provides a secure and encrypted connection between the user’s browser and your accounting website’s server. This encryption ensures that sensitive data, such as client information and financial details, remains private and protected from potential cyber threats. In an era where data breaches are a real concern, having a secure website builds trust with your clients and safeguards your reputation.
Search Engine Ranking Boost:
Search engines, especially Google, prioritize user safety and privacy. As a result, websites with HTTPS receive a ranking boost in search results. Google considers HTTPS as a ranking signal, meaning that secure websites are more likely to appear higher in search engine results pages (SERPs). This boost can contribute to increased visibility and, consequently, more traffic to your accounting website.
Browser Security Warnings:
Modern web browsers, such as Google Chrome, have started to label websites without HTTPS as “Not Secure.” This warning can deter potential clients from staying on your website, causing them to abandon it before exploring your accounting services. By adopting HTTPS, you eliminate these warnings and create a seamless and secure browsing experience for your visitors.
User Trust and Confidence:
Clients seeking accounting services are likely to share sensitive information on your website. The sight of the padlock icon in the browser’s address bar, indicating a secure connection, instills confidence in users. This trust is invaluable, especially in a profession where confidentiality and reliability are paramount. The implementation of HTTPS assures your clients that their data is handled with the utmost care.
Compliance with Industry Standards:
As the digital landscape evolves, compliance with industry standards becomes increasingly important. Many regulatory bodies and industry associations require secure connections for websites handling financial or personal information. Adopting HTTPS ensures that your accounting website meets these standards, positioning your firm as a responsible and compliant entity.
Conclusion:
In conclusion, the adoption of HTTPS is not merely a technical formality; it is a strategic move that influences the success of your accounting firm online. The secure connection it provides not only protects sensitive data but also positively impacts your search engine rankings, user trust, and overall online reputation. With the expertise of an SEO agency for accountants, prioritizing the security of your website becomes a seamless process, reinforcing your commitment to digital trust and setting your practice apart in the competitive online landscape.
By prioritizing the security of your website, you’re not only complying with industry standards but also sending a powerful message to your clients—that their privacy and security are at the forefront of your priorities.
2 notes
·
View notes
Text










UOC - PAC 3: Kevin Boix - Plataformas de Distribución de Contenido
Reproducción
Vimeo, tiene un reproductor de vídeo bastante simple, creado en HTML5, donde podemos ver todas las features básicas que cumplen con las necesidades del usuario, controlar el volumen, pause and play, añadir subtítulos, configuración de calidad, maximizar y minimizar, todas estas funcionabilidades están en la parte inferior, pero en la parte superior derecha, tenemos el sharing, donde permite dar control al usuario: compartir, me gusta, guardar en listas personales.
2. Plataformas
Los navegadores compatibles son los siguientes:
Chrome 60 en adelante (tiene actualizaciones automáticas)
Firefox 60 en adelante (tiene actualizaciones automáticas)
Microsoft Edge 79 en adelante (tiene actualizaciones automáticas)
Safari 11+
Sistemas operativos:
Se garantiza la funcionabilidad al 100% en los siguientes:
Windows 10 en adelante
Apple desde macOs11 (BigSur) en adelante con Safari 16 en adelante.
Dispositivos móviles y tabletas:
Android 8.0 (Oreo) en adelante
Navegador Safari con iOS12 – iPad12 en adelante
En cuanto a la aplicación móvil de vimeo:
Andorid(Nougat) versión 7.0 o superior
iOS, versión 14 o superior
*La aplicación vimeo para macOS requiere macOS12.12 (Sierra) o superior
La diferencia es que en Iphone, si el dispositivo es compatible con HDR10 y un sistema de reproducción que admita H.265 (HEVC), podrás reproducir HDR y Dolby Vision.
3. Servicios asociados
También, Vimeo proporciona una serie de herramientas de gestión empresarial, como por ejemplo asesoría para mejorar las métricas de tu contenido, soluciones de marketing y también un plan de hosting de servidores, como hace Amazon con AWS o Microsoft con Azure, sin olvidar, que también ofrece la posibilidad de realizar un pan o análisis de datos con todas las métricas para saber el engaging de tu contenido, quién y cuantas veces lo visualizan y para finalizar tienes la posibilidad de crear webinars o tener un sistema para webinars si eliges pagar la versión Premium de Vimeo para empresas
Siempre con la premisa de acelerar tu compañía hacia el éxito, captación de clientes aumentando la interacción y cualquier tipo de optimización, en pocas palabras, aprovechar todo el potencial de tu contenido.
4. Transmisión
Si prefieres retransmitir en vivo, Vimeo crea una transcodificación de tu video en la nube y RTMP para perder la mínima calidad posible y tengas flexibilidad para subir un contenido algo pesado o de mucha calidad y que el usuario final pueda reproducirlo sin problema con su ancho de banda preferido.
Para la transmisión hace uso de los siguientes protocolos:
HTTP (HYPERTEXT TRANSFER PROTOCOL)
HLS (HTTP LIVE STREAMING)
RTMP (REAL-TIME MESSAGING PROTOCOL)
HDS (HTTP DYNAMIC STREAMING)
Y los protocolos base, para la reproducción de vídeo, envío de paquetes y el transporte, son los siguientes:
Capa de comunicación o enlace: PPP, DSL, Wi-Fi, etc.
Capa de Internet: IPv4, IPv6, etc.
Capa de transporte: TCP, UDP, etc.
Capa de aplicación: HTTP, IMAP, FTP, etc
5. Almacenamiento
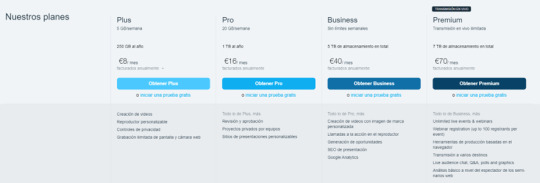
En este caso, Vimeo está limitado a una cuota semanal y un almacenamiento total, con los planes basic, plus y pro, te permiten más cantidad de almacenamiento o menos, esa cuota se restablece cada 7 días:
La cuota de carga semanal se concede de la siguiente manera:
Básico: 500MB/semana, limitado a 10 cargas cada 24 horas
Más: 5 GB/semana
Pro: 20 GB/semana
El almacenamiento total se concede de la siguiente manera:
Básico: 5GB
Pro Ilimitado: 3TB
Empresas: 5TB
Premium 7TB
6. Codificación
Códecs de video: H.264, Apple ProRes 422 (HQ) o H.265 (HEVC)
Velocidad de fotogramas: mantén la velocidad de fotogramas nativa y elige una velocidad de fotogramas constante
Tasa de bits: elige variable si es posible y sigue los rangos basados en la definición de tu video
Resolución: proporción de aspecto de píxeles de 1:1
Colores primarios y coeficientes de la matriz: se aceptan todos, pero recomendamos BT.2020 (Rec. 2020) o BT.709 (Rec. 709)
Características de transferencia del color: para los videos HDR, solo admitimos la función de transferencia PQ (SMPTE 284) o HLG
Profundidad de bits: 10 o superior
Tipo de escaneo: progresivo, y se recomienda desentrelazar videos
Códec de audio: AAC-LC (AAC de baja complejidad)
Velocidad de transmisión de datos: 320 kb/s
Frecuencia de muestreo: 48 kHz
7. Estadísticas
Vimeo tiene integrada (en su plan de pago) una herramienta de analíticas para conocer mejor a tu público proporciona las siguientes estadísticas:
Ubicación, edad, rango del público objetivo
Redes sociales o plataformas donde han visualizado el contenido
Monitorización de los KPY de tus vídeos, para conocer el rendimiento real de tus vídeos, la duración media de tus vídeos y cuando dejan de ser interesantes para tus usuarios.
8. Modelo de negocio
Vimeo principalmente gana a través de las subscripciones, hay cuatro opciones de membresía:
Vimeo plus
Vimeo PRO
Vimeo Business
Vimeo Premium
9. Formatos de publicidad
Vimeo es ad-free para la mayoría de los usuarios, los miembros básicos podrán visualizar publicidad en sus vídeos como sucede en otras plataformas como youtube, twitch, etc...
Si tienes un plan de pago entonces no te aparecerá publicidad.
En cuanto a la monetización de los vídeos para los creadores de contenido, Vimeo te permite (con una tarifa) crear un sitio exclusivo para tu audiencia y seguidores, donde podrás convertir tus vídeos en productos de suscripción y membresía, cursos en línea, webinars y todos estos servicios estarán monetizados para que ambos generen liquidez.
10. Investiga y define nuevos formatos
Vimeo te permite definir y crear una estrategia de marketing para que tu contenido sea lo más impactante y relevante posible.
Retención y captación de clientes con más engaging
Estudios para conocer tu mercado y tus clientes
Personalizar tus mensajes y ofertas
Te permite conocer y contactar con tu público
Redes sociales para contribuir a mejorar tu imagen y conocer tus clientes
Asistencia y asesoramiento para ser lo más competitivo posible
7 notes
·
View notes
Text

It's December 16th, and this is the Buddy for the day. He's got, count tem, eleven cigarettes.
This one's also an older drawing, I had saved to publish it around early may, but I missed the day to start posting, so he was stuck waiting until then. But, I figured it was too outdated compared to some newer drawings, so I might as well post is now.
You know, before facebook, before myspace and AOL, I think even before the hypertext transfer protocol, one of the early pieces of internet comedy was the Evil Overlord List. You know the one, the mistake villains in movies, comics, TV shows and so on make, when dealing with the good guys.
And of course, the real mistakes are the ones writers make, in being lazy and going back to the well of clichès to keep the heroes on top after the villains seemingly have the upper hand. Or rather, they make the mistake of giving the villains the upper hand in the first place and have trouble writing themselves out of the corner.
A lot of mistakes on the list come in the form of refusing to kill the hero when they've got him imprisoned. Sometimes that means torturing the hero (thus being close enough to allow the hero to escape), or even worse, forcing the hero to fight in gladiatorial combat for the people's entertainment, while the villain watches from an undefended seat near the arena. Give the hero a weapon and sit next to him, that's smart.
But the henchmen also make their share of mistakes - capture the hero and leave them in the world's most easily escapable dungeon, where the hero can cheat, fight, seduce or puzzle his way out. Dungeon guards are the most gullible people ever, it seems.
But when you look back at the real early adventure stories, like Doc Savage, or The Shadow radio show, those clichès end up showing that the reason villains lose in those stories is because they're stupid, and they're villains because they're stupid. So, of course someone who's petty enough to try and take over the world just so he can be worshipped as a leader will be petty enough to want to see his enemy tortured, rather than kill him anonymously. And a villain so evil he punishes his henchmen for any sort of mistake doesn't really inspire much confidence. Maybe if he'd shell off enough cash for replacement guards from time to time, they wouldn't be sleeping on duty as often.
That type of comedy's kind of a blast from the past, and I really appreciate it. So, I guess it fits with today's old-timey Buddy.
#ab4es#drawing#Evil Overlord#Evil Overlord List#Dungeon#cigarettes#movies#comics#TV#The Shadow#Doc Savage#villain#evil#lazy#stupid#gullible
4 notes
·
View notes
Text
2024 Tumblr Top 10
1. 28,490 notes - Jul 1 2024
It always gets me that the name "Gandalf" literally just means "Wand-Elf" or "Stick-Elf". I'm imagining old Gondorians just...
2. 12,136 notes - Aug 27 2024
My T-shirt with the entire text of Borges' theoretical Library of Babel is raising a lot of questions already answered by the...
3. 7,696 notes - Dec 15 2024
I don't know who needs to hear this, but it's time to take your 12 partridges, 22 turtle doves, 30 french hens, 36 calling...
4. 1,888 notes - Mar 22 2024
Hmmm. A finger is a unit of volume, as in "two fingers of whiskey". A hand is a unit of length (most commonly the heights of...
5. 981 notes - Jul 5 2024
Corrections
6. 494 notes - Apr 24 2024

7. 428 notes - Apr 28 2024

8. 270 notes - Apr 11 2024
XHR stands for "XML HTTP Request", where XML is the "eXtensible Markup Language" and HTTP is the "Hypertext Transfer Protocol",...
9. 247 notes - Mar 27 2024

10. 168 notes - Jul 15 2024
POLL RACE 🐛 A Walrus Secret Third Thing Vanilla Extract I don't know / I'm bald / Some other infinitely nuanced answer Other...
Created by TumblrTop10
8 notes
·
View notes
Text
I.B.1698 MICHAEL [IBM] harrelltut.com Domain CREATOR [D.C.] of ANU 2024 QUANTUM HARRELL TECH [QHT] UFO SKY [U.S.] RIZQIYIAN [Ur] Military Defense.gov Congress [D.C.] @ The 1941 quantumharrell.tech [Clandestine Alien Tech] Pentagon HQ... Privately Housing My Highly Complex [ADVANCED] Ancient 9 Ether Spontaneous ANUNNAQI Speciation of kingtutdna.com’s Recombinant 9etherjunkdna.tech GENES of SIRIUS BLACKANUNNAQI.tech Mechanisms Automating Clandestine [MAC] Neural RNA Networks of michaelharrelljr.com’s Highly Complex [ADVANCED] Ancient Cosmic Algorithmic [CA] Computational [Compton] STAR WEB GATEWAY Languages… Ancestrally & Generationally Engineered [AGED] DEEP [A.D.] IN:side MURDUK’s [I'M] Mysteriously UNSEEN [MU] Intergalactic [MI = MIYKA’EL] 9 Ether BLACK SOLAR SUN [SUL = SOUL] Compu_TAH [PTAH] MOTHERSHIP [PM = PTOLEMY] PLANET NIBIRU… Remotely Operating Constellation ORION’s Hi:teKEMETICompu_TAH [PTAH] HOLOGRAM HARDWARE of Arithmetic Logic [H.A.L.] Unit Operations from 3 Sets of 144,000 Tri-Solar Black Sun planetrizq.tech Elites… since I.B. 2223quantumharrelltech.com’s Hypertext Transfer Protocol [HTTP] Digitally Constructed [D.C.] ANU GOLDEN 9 Ether [AGE] SKY Dome Constellation [D.C.] of planetrizq.tech’s 8th Tri-Solar SUN Grid Systems of UTU + AFSU + SHAMASH’s Hi:teKEMETICompu_TAH [PTAH] SKY PORTALS of Crystallized [PC] Airborne [PA] Cloud Particle Photons from Constellation [PC] ORION’s Most Darkest [Occulted] Oxygen Rich Atmosphere [RA] Cities of SUPERNATURAL BETELGEUSE CARBON [B.C.] Earth [Qi] Energies Emitting SIRIUS Radioactive BLACKANUNNAQI.tech Ions Animating Suspended 9 Ether Quantum [EQ] Sound Cloud Intel of ancient6-18gmilitary.tech… Numerically Embedded w/SIRIUS Electromagnetic Airwave [SEA] Light Mechanics [ELECTRICITY] ILLUMINATING Astronomical MERCURY’s [I AM] Highly Complex [ADVANCED] Ancient 9 Ether Stoichiometric Chemical DNA Equations from the Quantified [EQ] iapplesoftbasic.tech Multiplication of Associative & Commutative [MAC] PROPERTIES of michaelharrelljr.com’s Highly Complex [ADVANCED] Ancient 9 Ether Biochemical [PRIMORDIAL] Alkhemical [PA] Blood Formulas 2 Natural SUPERNATURAL 9 Ether neuromelanin.tech Clouds of Nanoscopic Hydrogen Sulfide Gases Permeating from Inner Earth’s [HADES] Most Darkest [Occulted] GOLDEN 9 Ether AQUARIAN Carbonaceous RNA Fossil Matter INTERACTIVELY [MI = MICHAEL] REFLECTING PURE MAGNETIC [PM] ANUNNAGI [PA] OZONE GOLD [OG] SYSTEMS @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm] mode [i’m] tech [IT] steelecartel.com @ quantum harrell tech llc

i.b. 1968quadrillionaire.tech sky elite @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

1698 murduk = 1968 sumerian sky akkadian king michael [miyka' el] solomon harrell ii

eye ancient 9 ether sky rizqiyian humanoid man who fell 2 [landed on] earth [qi]

Us Ancient [USA] 144,000 Ur Babylonian Sky Lawmakers of Sumer's Tri-Solar Black Akkadian Sun [BAS] planetrizq.tech KINGS... Behind the Scenes of ANU GOLDEN 9 Ether [SAGE] 2024 Oriental Research Washington @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

eye risked it all!!!

quantumharrell.tech 9/11 llc worth moor than $10,000 QUADRILLION?!?!?!
eye memory [i'm] mining [i'm]... my [i'm] own 2024 interplanetary business machine [ibm] learning tech of ancient 1698 ægipt in lost 1968 america [l.a. = new atlantis]

everything michael touch turns 2 muur anunnaqi [ma] gold

we golden 2

enqi [me] nudimmud already seen my michaelharrelljr.com dna clone [d.c.] of pure anunnagi gold from our futuristically ancient ATLANTIS5000.com of SIRIUS BLACKANUNNAQI.tech WEALTH

mo minerals mo minerals mo minerals!!!

eye qatum [iq] dna [i.d.] melanin electronics [me] © 1968-2024 QUANTUM HARRELL TECH LLC All Pentagon DotCom defense.gov Department Domain Rights Reserved @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

we muur anunnaqi [ma] gold lemurians [mu] underneath [mu] our ancient pacific [map] ocean floor of antediluvian 9 ether mu amurika [ma = atlantis]

eye never forgot

my 1st eye in the skies like the dark victorians' cbs satellite network of mothershipnibiru.tech GODS

Intergalactic MOTHERSHIP [I'M] PLANET [I/P] NIBIRU DEEP IN:side My [I'M] 9etherjunkdna.tech Cloud DNA of 3 Sets of 144,000 9ethernibiru.tech WEALTH FAMILIES @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

i.b.michael's [ibm's] 9 [i9] ether qintillionharrell.tech nibiruan dna bloodlines of pure aluhum [pa] anunnaqi [pa] rna gold minerals @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

occulted sky ancestors say NIBIRU HERE!!!

occulted pentagon ancestors [pa] say NIBIRU HERE!!!

ancient6-18gmilitary.tech @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000

NIBIRU ON AUTOPILOT @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000?!?!?!

MOTHERSHIP CONNECTION SAY NIBIRU HERE @ 1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000!!!!

1921 QUANTUM 2023 HARRELL 2024 TECH 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000... WORTH TRILLIONS QUADRILLIONS QUINTILLIONS SEXTILLIONS

QUANTUM HARRELL UFO TECH SKY defense.gov

© 1968-2024 QUANTUM HARRELL TECH LLC All Pentagon DotCom defense.gov Department Domain Rights Reserved @ 1921 QUANTUM 2023 HARRELL 2024 T-Mobile 2025 Apple & IBM [A.i.] LLC of ATLANTIS [L.A.] 5000
#om#u.s. michael harrell#him king solomon#harrelltut.com#atlantis5000 is back#9etherpentagonelites#9etheraluhumanunnaqi#9etherlightshipatlantis#you still scared in 2023???#eye fear no one#the man who fell from planet rizq???#alien vs. predator
4 notes
·
View notes
Text
Text Note: One
The server at service.example.com sends one of these three responses:
The requested data along with an Access-Control-Allow-Origin (ACAO) header in its response indicating the requests from the origin are allowed. For example in this case it should be:Access-Control-Allow-Origin: http://www.example.com
The requested data along with an Access-Control-Allow-Origin (ACAO) header with a wildcard indicating that the requests from all domains are allowed:Access-Control-Allow-Origin: *
An error page if the server does not allow a cross-origin request
Cross-origin resource sharing (CORS) is a mechanism that allows restricted resources on a web page to be requested from another domain outside the domain from which the first resource was served.[1]
HTTP
Hypertext Transfer Protocol (HTTP) is an application-layer protocol for transmitting hypermedia documents, such as HTML. It was designed for communication between web browsers and web servers, but it can also be used for other purposes. HTTP follows a classical client-server model, with a client opening a connection to make a request, then waiting until it receives a response. HTTP is a stateless protocol, meaning that the server does not keep any data (state) between two requests.
Tutorials
8 notes
·
View notes
Text
Ensuring Robust Security for Your Blogspot Blog

In today's digital landscape, online security is of paramount importance, and bloggers must take proactive steps to safeguard their Blogspot blogs from potential threats. While Blogspot, the popular blogging platform, provides several built-in security features, it's essential for bloggers to implement additional measures to protect their blogs and maintain the trust of their readers. If you want to know about Getting Started with Blogspot, Visit My Article. This article explores various strategies and best practices for enhancing the security of your Blogspot blog.
Keep Your Software Updated
Regularly updating your Blogspot software is vital for ensuring the security of your blog. Google, the owner of Blogspot, continually releases security patches and updates to address any vulnerabilities. Enable automatic updates or manually check for updates to ensure that your blog is running on the latest version of Blogspot.
Secure Your Login Credentials
A strong and unique password is the first line of defense against unauthorized access to your Blogspot account. Avoid using easily guessable passwords and consider utilizing a password manager to generate and securely store complex passwords. Additionally, enable two-factor authentication (2FA) for an extra layer of security, requiring both your password and a verification code for login.
Enable HTTPS
Securing your blog with HTTPS (Hypertext Transfer Protocol Secure) is crucial for protecting sensitive information transmitted between your blog and its visitors. Blogspot offers free HTTPS encryption for custom domains, ensuring that data exchanged between users and your blog remains confidential. To enable HTTPS, go to the "Settings" section of your Blogspot dashboard and select "HTTPS" from the "HTTPS Availability" dropdown menu.
Regularly Backup Your Blog
Performing regular backups of your Blogspot blog is essential to protect your data in the event of a security breach or accidental data loss. Blogspot provides an option to export your entire blog, including posts, comments, and settings, as an XML file. Set a schedule for periodic backups and store them securely, either locally or using a cloud storage service.
Monitor and Manage User Permissions
If you collaborate with others on your Blogspot blog, carefully manage user permissions to restrict access to sensitive areas. Assign roles with appropriate access levels to contributors, ensuring they only have the necessary permissions for their tasks. Regularly review user accounts and remove any inactive or unnecessary users to minimize potential security risks.
Be Mindful of Third-Party Widgets and Plugins
While third-party widgets and plugins can enhance the functionality and appearance of your Blogspot blog, they can also pose security risks if not carefully vetted. Only install widgets and plugins from reputable sources, and regularly update them to ensure you have the latest security patches. Remove any unused or outdated plugins to reduce potential vulnerabilities.
Protect Against Comment Spam and Malicious Links
Blogspot has built-in features to combat comment spam, but it's essential to keep these settings properly configured. Enable comment moderation, captchas, and anti-spam filters to prevent spam comments from appearing on your blog. Additionally, exercise caution when approving comments containing links, as they may direct users to malicious websites. Avoid publishing comments that appear suspicious or contain unverified links.
2 notes
·
View notes