#Hidden mobile spy software
Explore tagged Tumblr posts
Text
Parental Control Made Easy with Mobile Spy App

Take control of your child's online safety with ONEMONITAR, a powerful parental control mobile spy app. With ONEMONITAR, you can monitor your child's smartphone activity in real-time, set restrictions on app usage and screen time, and receive instant alerts for any suspicious or inappropriate behavior. ONEMONITAR empowers parents to protect their children in today's digital world.
Start Monitoring Today!
#Best mobile spy app for Android#Hidden mobile spy software#Parental control mobile spy app#Undetectable mobile spy app#Mobile spy app for WhatsApp#GPS tracker mobile spy app#Mobile spy app for employee monitoring#Mobile spy app for call recording#Mobile spy app for WhatsApp without target phone#Mobile spy app for Snapchat
0 notes
Text
CHYLDMONITOR Mobile Spy for Android

Get CHYLDMONITOR, the ultimate mobile spy solution tailored for Android devices. Seamlessly monitor phone activities, including call logs, messages, and app usage, all from a centralized control panel. With CHYLDMONITOR, you can ensure the safety of your children or enhance employee productivity by keeping an eye on their digital interactions. Experience top-notch Android monitoring today.
Protect and monitor effectively. Download CHYLDMONITOR for Android!
#mobile spy app#mobile spy software#mobile spy for android#mobile spy download#mobile spy without access to phone#mobile spy app hidden#mobile spy app undetectable#mobile spy parental control#mobile spy app with GPS tracking#mobile spy app features
0 notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Spy Audio Recording
Spy Audio Recording: A Comprehensive Guide to Technology, Uses, and Ethical Considerations

1. What is Spy Audio Recording?
Spy audio recording is the process of capturing sounds or conversations using hidden equipment without the subjects’ knowledge. These gadgets are frequently small and aesthetically pleasing, resembling commonplace items like buttons, USB drives, pens, and even phone chargers.
2. Uses and Applications of Spy Audio Recording
Personal Security: For people feeling unsafe or vulnerable, audio recorders can offer an added sense of security by documenting interactions in public or private settings.
Investigative Journalism: Journalists and investigators use discreet audio recorders to gather evidence in sensitive situations, especially when conducting interviews or investigations in hostile environments.
Parental Monitoring: Some parents use audio recording tools to monitor their children’s interactions, especially in cases where they suspect bullying or other harmful influences.
Business and Corporate Security: Audio recorders are sometimes used in corporate settings to ensure transparency, protect intellectual property, and prevent unauthorized disclosures.
3. Types of Spy Audio Recording Devices
Spy audio recording devices come in various forms to meet different requirements, each with its unique features. Some common types include:
Miniature Voice Recorders: Small, discreet devices that can be placed in inconspicuous locations. Often battery-operated, they come with long-lasting power options.
Wearable Audio Recorders: These can be integrated into wearable accessories like watches, glasses, and necklaces. Wearable devices are popular for their portability and ease of access.
USB or Power Bank Recorders: These audio recorders look like regular USB drives or power banks, allowing for covert recording while blending seamlessly into most environments.
Pen Recorders: These function as regular pens while discreetly capturing audio. They are often used in meetings and interviews.
Smartphone Apps and Software: With advancements in mobile technology, apps can now enable discreet recording. Some apps have silent activation, scheduled recording, and automatic upload to the cloud for added security.
4. Key Features to Consider in Spy Audio Recorders
When selecting a spy audio recorder, certain features are essential to ensure optimal performance:
Battery Life: Choose a device with a long battery life, especially for prolonged recording sessions.
Storage Capacity: Higher storage capacity allows for more extended recording periods without interruptions.
Audio Quality: High-quality audio ensures that recorded conversations are clear and understandable, even when captured in noisy environments.
Range of Recording: Depending on the environment, the recording range varies. Select devices with sufficient range for your needs.
Motion or Voice Activation: Many spy recorders activate only when they detect sound or movement, which conserves battery life and storage.
5. Legal Considerations and Ethical Implications
Depending on the jurisdiction, utilizing spy audio recording devices may or may not be lawful. Unauthorized recording of a discussion, particularly in a private situation, is prohibited in many jurisdictions. The following are some moral and legal considerations:
Informed Consent: Recording without the other party’s consent is often against the law. Always ensure that your recordings comply with local laws.
Respect Privacy: In public and private settings, respect for privacy is paramount. Avoid recording conversations unless necessary and legally permissible.
Responsible Usage: Spy audio recording devices should not be used for invasive or harmful purposes, such as espionage, harassment, or infringement on someone’s rights.
Before using any spy audio recording device, research the laws in your area and seek legal guidance if necessary. Misuse can result in severe penalties and breach of trust.
6. Buying Guide: Choosing the Right Spy Audio Recorder
When buying a spy audio recording device, it’s essential to assess your needs carefully and match them with the device’s features. Here are some tips for choosing the right spy recorder:
Environment: Indoor settings may require different devices than outdoor spaces. Consider the environment where you’ll be using the device.
Discreet Design: Opt for designs that blend well in the intended setting. Pen recorders work well in office environments, while USB recorders are suitable for public areas.
Technical Features: Check for technical capabilities like noise cancellation, voice activation, and Wi-Fi or Bluetooth connectivity.
Brand Reputation: Choose products from reputable brands, as they typically offer better quality, warranty, and customer support.
7. Top Spy Audio Recording Devices in the Market
While it’s essential to review the latest offerings before purchasing, here are some commonly praised options for their reliability and features:
Mini Voice Activated Recorder by EVISTR: Compact and easy to use, this device offers excellent audio quality with voice activation.
Spy Pen Recorder by Aomago: A favorite for its sleek design, high-quality audio, and ease of use, especially in office settings.
TileRec Mini by Attodigital: Known for its ultra-thin design and portability, this device fits in wallets and offers impressive sound quality.
Always remember to buy from verified sellers and read customer reviews to avoid counterfeit products.
8. Tips for Using Spy Audio Recorders Responsibly
Check Local Laws: Ensure you’re following all legal requirements regarding audio recording.
Limit Recording Duration: Record only what’s necessary and avoid recording in private settings without permission.
Store Data Securely: Ensure recorded data is stored securely and is only accessible to authorized people.
Use Technology for Positive Purposes: Audio recording can be incredibly useful for ensuring safety, gathering important information, and documenting valuable data. However, it should always be used with integrity and respect for others’ privacy.
9. Final Thoughts on Spy Audio Recording
Technology for spy audio recording has created opportunities in journalism, business transparency, and personal security. It can be a useful tool for security and documentation if utilized properly and in accordance with the law. To avoid abuse and protect others’ rights and privacy, the technology must be utilized with a strong sense of ethical obligation.
0 notes
Text
Phone Spy App to Read Someone's Text Messages

Phone spy apps have become increasingly popular in recent years, allowing individuals to monitor and track the activities of others through their mobile devices. However, before delving into the benefits and limitations of these apps, it's crucial to understand their definition and purpose, as well as the considerations surrounding their use.
Definition and Purpose
Phone spy apps are software programs that can be installed on a target device to track its activities, such as text messages, calls, and social media interactions. The primary purpose of these apps is to provide remote monitoring capabilities for parents, employers, or individuals concerned about their loved ones' safety and well-being. Read more
Phone Spy Considerations
While phone spy apps can be valuable tools for monitoring and ensuring the safety of children or employees, it's essential to consider the implications of their use. Invasion of privacy and trust issues may arise when using spy apps without the target's knowledge or consent. It's crucial to weigh the benefits of monitoring against the potential harm to personal relationships and individual autonomy.
Understanding Phone Spy Apps
To effectively utilize phone spy apps, it's essential to understand the two main types: phone trackers and mobile spy software.
Phone Tracker
Phone trackers are applications that allow users to monitor a target phone's location, call logs, text messages, and browsing history. These apps offer various functionalities and features, such as real-time tracking, geofencing alerts, and remote locking capabilities. However, they also come with limitations, such as the need for physical access to the target device and compatibility issues with certain operating systems.
Mobile Spy Software
Mobile spy software goes a step further by providing users with advanced monitoring features, such as social media tracking, keystroke logging, and remote access to the target device's camera and microphone. These apps are compatible with a wide range of devices and operating systems, making them versatile tools for remote monitoring.
Remote Monitoring
One of the key advantages of phone spy apps is their ability to facilitate remote monitoring through spyware and cell phone spying functionalities.
Spyware for Phones
Spyware for phones allows users to remotely access a target device's data, including text messages, call logs, and browsing history. The data is typically encrypted to ensure security and privacy, making it difficult for unauthorized users to intercept or manipulate the information.
Cell Phone Spying
Cell phone spying involves monitoring a target device's social media activities, GPS location, and app usage. This feature is particularly useful for parents looking to track their children's whereabouts or employers monitoring their employees' productivity and compliance with company policies.
Popular Spy Apps in the Market
Several spy apps dominate the market, offering a range of surveillance and monitoring capabilities tailored to specific user needs.
Phone Surveillance
Phone surveillance apps provide hidden phone tracker options and a user-friendly interface for easy navigation and monitoring. These apps offer discreet monitoring features, ensuring that the target individual remains unaware of being monitored.
Spy App for Android
Spy apps designed for Android devices offer real-time monitoring features and compatibility with a wide range of Android smartphones and tablets. These apps provide users with comprehensive surveillance capabilities, including call recording, GPS tracking, and social media monitoring.
iPhone Spy Software
iPhone spy software is designed exclusively for iOS devices, offering unique features such as iCloud synchronization and remote access to a target device's data. These apps provide a seamless monitoring experience for iPhone users, ensuring that no activity goes unnoticed.
Covert Monitoring and Stealth Features
To maintain undetectable operation, phone spy apps offer covert monitoring and stealth features for discreet surveillance.
Covert Phone Monitoring
Covert phone monitoring allows users to track a target device's activities without alerting the user. Stealth mode operations ensure that the app remains hidden on the target device, making it virtually impossible to detect.
Stealth Spy App
Stealth spy apps feature concealed app icons and operations, making them virtually undetectable on the target device. These apps also offer remote control options for seamless monitoring and data retrieval.
Monitoring and Tracking Capabilities
Phone spy apps provide extensive monitoring and tracking capabilities, including keylogging, call and SMS tracking, and data backup options.
Phone Monitoring Tool
Phone monitoring tools offer keylogging and screenshot features for tracking text messages, browsing history, and app usage. These apps also provide call and SMS tracking functionalities for monitoring communication activities. Click here
Phone Spyware
Phone spyware enables users to back up data from a target device, as well as receive alert notifications for specific activities, such as suspicious calls or messages. These apps offer robust surveillance features for comprehensive monitoring and tracking.
Ensuring Undetectable Operation
To ensure the seamless operation of spy apps, users can take steps to prevent detection and maintain discreet surveillance.
Track Phone Activity
Regular updates and bug fixes are essential for preventing anti-virus detection and ensuring the smooth operation of spy apps. Optimizing battery usage and discrete data transmission also help maintain covert monitoring capabilities.
Conclusion
In conclusion, phone spy apps offer valuable monitoring and tracking capabilities for parents, employers, and individuals concerned about their loved ones' safety. It's essential to use these apps, considering the legal implications and privacy considerations surrounding their use.
0 notes
Text
Debugging Services in delhi | TSCM security
Debugging Services in Delhi involve a technical process aimed at operating and searching for software/tools to detect bugs and hidden spy cameras. Our team of professional technicians and engineers meticulously inspects work areas, residences, and flights for electric and radio bugs, ensuring a bug-free environment before departure. This entails a thorough search and neutralization process for electronic transmitters.For any Bug Sweeps or Technical Surveillance Countermeasures required in New Delhi, TSCM Security in India is well-equipped to assist you effectively and at competitive rates. We are dedicated to ensuring that our clients receive the best services in Delhi, offering complimentary bug sweeping consulting services. Bugs can come in various shapes and sizes, planted discreetly in furniture, walls, electronic communication devices like landline and mobile phones, computers, or any other possible location. Only experts have the expertise to properly scan doubtful areas and keep them free from bugs. As a leading Professional Private Investigation agency and bug sweeping group in New Delhi, we have assisted numerous clients in the region. We specialize in providing comprehensive investigative and intelligence services to both local and international clients. For over 15 years, we have offered TSCM Bug Sweep Services in New Delhi. Our team of experts is internationally trained for TSCM operations, and our procedural services in New Delhi are widely recognized as the best electronic countermeasures solutions available.

1 note
·
View note
Text
Ex-CIA software engineer who leaked to WikiLeaks sentenced to 40 years

A former CIA software engineer has been sentenced to 40 years in prison for leaking classified information and possessing child sexual abuse material.
Joshua Schulte, 35, was found guilty in 2022 of four counts each of espionage and computer hacking and one count of lying to FBI agents after handing over classified materials to whistleblowing organisation WikiLeaks.
.adtnl5-container { position: relative; width: 100%; max-width: 600px; /* Set your desired maximum width */ margin: auto; overflow: hidden; border-radius: 15px; /* Add border-radius for rounded corners */ } .adtnl5-image { width: 100%; height: auto; display: block; } .adtnl5-play-button { position: absolute; top: 50%; left: 50%; transform: translate(-50%, -50%); width: 120px; height: 120px; background-color: rgba(255, 0, 0, 0.6); /* Semi-transparent red */ border: none; border-radius: 50%; color: #fff; font-size: 36px; cursor: pointer; display: flex; align-items: center; justify-content: center; transition: background-color 0.3s ease; /* Smooth transition */ } .adtnl5-play-button:hover { background-color: rgba(255, 0, 0, 0.9); /* Darker red on hover */ } .adtnl5-title { position: absolute; bottom: 0; width: 100%; background-color: rgba(0, 0, 0, 0.7); color: white; text-align: center; padding: 10px; box-sizing: border-box; font-size: 18px; font-weight: bold; text-decoration: none; /* Remove underlines from the link */ } .adtnl5-title:hover { text-decoration: underline; /* Add underline on hover */ } .adtnl5-marker { position: absolute; top: 10px; right: 10px; background-color: #ffcc00; /* Yellow background for the marker */ padding: 5px; border-radius: 5px; color: black; font-size: 13px; text-decoration: none; } @media (max-width: 767px) { /* Mobile responsiveness */ .adtnl5-play-button { width: 80px; height: 80px; font-size: 24px; } .adtnl5-title { font-size: 16px; } .adtnl5-marker { font-size: 11px; padding: 3px; } }
▶

Satya Nadella & Sam Altman: Dawn of the AI Wars | The Circuit with Emily Chang
Ads by BCI
Schulte was also convicted of contempt of court and making false statements in 2020, and possession of child abuse material last year.
The bulk of the sentence announced on Thursday was imposed over the so-called Vault 7 leak, which revealed embarrassing details of the CIA’s spying overseas.
The leak, which the CIA called a “digital Pearl Harbor”, showed how US spies hacked Apple and Android smartphones and sought to turn internet-connected televisions into listening devices.
The security breach prompted US officials to plan for an “all-out war” against Wikileaks, including discussing the possible kidnapping or assassination of its founder Julian Assange, Yahoo News reported, citing anonymous officials.
Assange was indicted on espionage charges in 2019 – a move that prompted condemnation by press freedom organisations – and is currently in Britain fighting extradition to the US.
Judge Jesse M Furman said the full extent of the damage caused by Schulte would likely never be known “but I have no doubt it was massive”.
Furman said Schulte had also continued to commit crimes while in jail by trying to leak more classified materials and by creating a hidden file on his computer that contained child sexual abuse images.
US Attorney Damian Williams said in a statement that Schulte had committed some of the “most brazen, heinous crimes of espionage in American history”.
“He caused untold damage to our national security in his quest for revenge against the CIA for its response to Schulte’s security breaches while employed there,” Williams said.
Addressing the court ahead of his sentencing, Schulte complained about harsh conditions he had endured in detention, including being denied hot water and being subjected to constant noise and artificial light.
Schulte also said it was unfair for prosecutors to seek a life sentence as they had previously offered a plea deal that would have seen him sentenced to 10 years in prison.
“This is not justice the government seeks, but vengeance,” he said.
.adtnl5-container { position: relative; width: 100%; max-width: 600px; /* Set your desired maximum width */ margin: auto; overflow: hidden; border-radius: 15px; /* Add border-radius for rounded corners */ } .adtnl5-image { width: 100%; height: auto; display: block; } .adtnl5-play-button { position: absolute; top: 50%; left: 50%; transform: translate(-50%, -50%); width: 120px; height: 120px; background-color: rgba(255, 0, 0, 0.6); /* Semi-transparent red */ border: none; border-radius: 50%; color: #fff; font-size: 36px; cursor: pointer; display: flex; align-items: center; justify-content: center; transition: background-color 0.3s ease; /* Smooth transition */ } .adtnl5-play-button:hover { background-color: rgba(255, 0, 0, 0.9); /* Darker red on hover */ } .adtnl5-title { position: absolute; bottom: 0; width: 100%; background-color: rgba(0, 0, 0, 0.7); color: white; text-align: center; padding: 10px; box-sizing: border-box; font-size: 18px; font-weight: bold; text-decoration: none; /* Remove underlines from the link */ } .adtnl5-title:hover { text-decoration: underline; /* Add underline on hover */ } .adtnl5-marker { position: absolute; top: 10px; right: 10px; background-color: #ffcc00; /* Yellow background for the marker */ padding: 5px; border-radius: 5px; color: black; font-size: 13px; text-decoration: none; } @media (max-width: 767px) { /* Mobile responsiveness */ .adtnl5-play-button { width: 80px; height: 80px; font-size: 24px; } .adtnl5-title { font-size: 16px; } .adtnl5-marker { font-size: 11px; padding: 3px; } }
▶

Satya Nadella & Sam Altman: Dawn of the AI Wars | The Circuit with Emily Chang
Ads by BCI
0 notes
Text
The Positive Side of Spy Phone App
Ever since the spy apps have been introduced, they have been a controversial topic of discussion for various reasons, from safety concerns to privacy point of view there has been a lot of chatter around these spyware but how there is a positive side to those apps is often overlooked. Yes, these apps also have a positive side and can be used other than just being a source of spying on others.
Before we dive into the positive side of these mobile spy apps, it is important to understand what they are and how they work. It software installed on the device which you want to monitor. You can use these apps to spy on your child’s online activities, employees’ productivity during the office hours, and in some cases, the legal authorities also use them to catch the culprits.
What Main Advantages of Spy Apps
It is their ability to create a safe and secure environment for people in the online world. There are many threats involved when we go online such as cyberbullying, online predators, different types of scams and frauds. Using spy apps can provide the individuals and businesses the peace of mind they deserve. By spying on your child, you can keep a close eye on what type of content they are exposed to. Likewise, with the businesses, by keeping a track of your employees, you can be sure that they are using their working hours wisely. These apps can also be of great help in emergency situations.
Talking about the apps from employers’ point of view, the rise of work from home and company-owned devices, it is important that employers monitor their employees and their activities during the working hours. The mobile spy apps can help you in preventing the breaching of data and ensuring that employees are using the devices only for work-related tasks.
For legal authorities also, these spyware tools have proven to be effective as there are many features offered by these apps that can help the officials to catch the culprits. With the hidden call recorder, they can listen to the phone conversations and simultaneously with the in-built live-location tracker, they can detect the current location of the suspect.
Another benefit of spyware is for personal use and safety. In case you are away from your family then you can install the application on your phone and give its access to your family member so that they can monitor you and be sure that you are safe. Another way you can benefit from spy apps is that in case you lose your phone or in a worst case scenario, if your phone gets stolen then with the location tracking enabled on your phone, you can find it. This way, you will not lose your important data stored on your phone and also you won’t need to invest in a new phone.
Which Spy App to Choose for Android Phone ?
While there are many apps available on the internet today, there are majorly two categories; free and paid. The free apps are less secure and offer less features while the paid spy apps are more secure and offer more features. We personally recommend using apps so that you can spy on your target completely. The paid apps offer multiple features that help you monitor everything they do on their android devices.
If you are looking for a reliable and trustworthy paid spy app then ONEMONITAR is surely here to end your search. The spying tool offers more than 60 amazing features that are compatible with all android devices and work efficiently. These features include hidden call recorder, WhatsApp spy, other social media monitoring tools like Instagram spy, Snapchat spy, etc., live-location tracking, and ambient sound recorder.
Another factor to choose this app is because it is designed and developed in India and has its own secure server where the users’ data is stored and the confidentiality and security of the data is ensured by the spyware as there is no third party involved to avoid any breach of privacy. Additionally, the experts at ONEMONITAR also cannot access your control panel as the spy phone app very-well understands that the data fetched from the target device can contain sensitive information, keeping this in mind, the ONEMONITAR team does not have access to this information to maintain the confidentiality of your private data.
Conclusion
Our concluding thoughts are that while there has been a negative buzz around the spy apps, they also have a positive side that should not be overlooked. If used wisely, these spyware tools can enhance safety and security of your loved ones and also build trust in relationships with also a pinch of open communication with your loved ones to work towards betterment of the relationship. Also, not to forget the positive impact it has on businesses by accurately tracking the activities of the employees to maintain productivity during the office hours. https://www.linkedin.com/pulse/positive-side-spy-phone-app-spy-app-reviews-67jxc/
1 note
·
View note
Text
The Science of Surveillance: Techniques Used by Detective Agencies in Noida
In today’s rapidly evolving world, where technology and information flow continuously reshape our lives, the need for surveillance has never been more critical. Detective agencies in Noida have adapted to this digital age by employing an array of sophisticated surveillance techniques. These techniques enable them to collect vital information while ensuring compliance with privacy laws and ethical standards.
In this blog post, we will take a deep dive into the science of surveillance, exploring the innovative methods used by Detective agency in Noida to gather crucial evidence, protect clients’ interests, and solve complex cases.
1. GPS Tracking
One of the most common surveillance tools utilized by detective agency in Noida is GPS tracking. This technology allows investigators to monitor the movements of vehicles or individuals discreetly. Whether it’s a cheating spouse investigation or tracking the whereabouts of a missing person, GPS trackers provide real-time location data, which can be crucial for building a case.
2. Covert Cameras
Covert cameras, often referred to as hidden or spy cameras, have come a long way in terms of technology and design. Detective agency in Noida employ these miniature cameras to capture video and photographic evidence without detection. These cameras are strategically placed in various locations, ensuring that they remain inconspicuous while providing invaluable insights.
3. Drone Surveillance
As technology advances, Detective agency in Noida have also embraced the use of drones for surveillance. Drones equipped with high-resolution cameras can access hard-to-reach or remote areas, making them indispensable in cases involving large properties, events, or outdoor surveillance. Drones provide a bird’s-eye view that traditional surveillance methods cannot match.
4. Social Media Monitoring
In today’s digital age, social media platforms have become a goldmine of information. Detective agency in Noida actively monitor social media accounts to gather evidence, track the activities of subjects, and uncover potential connections or leads. Social media monitoring can be instrumental in cases related to fraud, infidelity, or missing persons.
5. Audio Surveillance
Audio surveillance involves the use of discreetly placed microphones or audio recording devices to capture conversations and sounds. Detective agency in Noida employ this technique in cases where verbal evidence is crucial. It requires careful planning and adherence to legal guidelines to ensure that the collected audio is admissible in court.
6. Computer Forensics
The digital age has brought about a surge in cybercrimes and digital evidence. Detective agency in Noida often collaborate with computer forensic experts to recover deleted data, trace online activities, and uncover digital footprints. This is particularly essential in cases involving cyberbullying, intellectual property theft, or online harassment.
7. Undercover Operations
Undercover operations remain a staple in the toolkit of Detective agency in Noida. Experienced detectives assume covert identities to infiltrate organizations or groups involved in illegal activities. These operations require a high level of skill, training, and risk management.
8. Background Checks
Background checks are fundamental in various investigations, from pre-employment screening to due diligence in business transactions. Detective agency in Noida utilize extensive databases and sources to compile comprehensive reports on individuals or entities, helping clients make informed decisions.
9. Facial Recognition Technology
Advancements in facial recognition technology have revolutionized surveillance. Detective agencies in Noida employ facial recognition software to identify individuals in crowds, track known subjects, and enhance security in public spaces.
10. Mobile Surveillance Units
Equipped with state-of-the-art technology, mobile surveillance units are essentially surveillance hubs on wheels. They allow detective agencies in Noida to conduct dynamic and adaptable surveillance operations, especially in cases where subjects are frequently on the move.
Conclusion
Detective agencies in Noida leverage a diverse range of surveillance techniques, combining traditional methods with cutting-edge technology to serve their clients effectively. While these methods are powerful tools for gathering evidence, it’s crucial to emphasize that their use must always comply with legal and ethical standards to protect the rights and privacy of all individuals involved. The science of surveillance continues to evolve, ensuring that detective agencies remain at the forefront of solving complex cases and delivering justice.
#detective agency in noida#best detective services#detective agency in faridabad#best detectives#detective agency in gurgaon#best detective agency#detective agency in delhi
0 notes
Text

ONEMONITAR - Hidden Call Recorder for Discreet Monitoring
ONEMONITAR's Hidden Call Recorder offers seamless and secure call recording for effective monitoring. Capture conversations discreetly, ensuring data privacy and compliance. Ideal for businesses and personal use, it operates in the background without interrupting device functionality.
#mobile spy app#phone spy app#whatsapp spy app#android spy app#phone spy software#hidden call recorder#hidden call recording app#hidden call recording software
0 notes
Link
Spy Shop Online deal in Latest and best Hidden Cameras, 9999332499, Spy Gadgets, Spy Camera, Wireless Camera, WiFi Camera, Online Camera, Mobile Jammer, Spy Playing Cards, Spy Mobile Software.
#hidden spy camera#spy camera#spy hidden camera#spy cam#nanny cam#watch camera#pen camera#pinhole camera#wifi camera#secret camera#wireless camera#spy mobile software#spy playing cards#spy shop online
1 note
·
View note
Text
How do Parental Spy apps track children's online activity?

Parental spy apps are a tool that give parents the privilege to track their children’s online activity. They also allow parents to control and set certain limits to these activities but that depends on the features and other factors based on which one can perform these activities.
Today, the kids are technologically very advanced. Every kid is equipped with smartphones and also has a presence on the internet. This is the reason why parents are so concerned about their safety and monitoring children’s online behavior has become crucial for them.
In this article, we will read about how these spy apps function for your child’s online activity tracking and assuring the internet safety for kids and your loved ones.
What Are Parental Spy Apps?
As mentioned above parental Spy apps are a tool with the help of which you can track your loved ones’ online activity. You can view the content they watch, the people they interact with, their real-time location. You can also block the websites that you think are not right for them and much more.
There are numerous phone monitoring apps available on the internet that you will find, some could be free while most of them would be paid apps. Usually, the free apps offer less features and security as compared to the paid apps. Also, despite offering similar services, different spy apps would have something different in them in terms of features, packages, and performance.
We will now read about the features that are commonly offered by the mobile spy apps that can help you track your child’s online behavior.
Features Of A Phone Spy App
There are many features offered by a phone spy app that are helpful in tracking your child and also allow you to take certain actions based on what the kid is doing. Let us learn more about these features.
Call Recorder: The hidden call recorder is an effective feature when you want to remotely listen to the calls of the concerned person. Not only you can listen to the calls but also get the information of the complete log that provides you the details of the other person on the call also like their name and phone number.
Location Tracker: You can remotely track your child when you want to know about their whereabouts. The GPS tracking feature shares accurate and timely information.
Social Media Monitoring: To track your child’s social media, you can use the social media tracking tool that allows you to see their activity on the social platforms like Facebook, Instagram and Snapchat.
Web Browser History: The websites your child visits is a major concern for parents and to ensure that, you can access their web browsing history with a spy app for android.
Website Blocking: You can block the websites that you think are not supposed to be viewed by your child by remotely blocking the site through certain settings.
Screen-Time Management: Most of the digital parenting tools allow you to manage the screen-time of your child so that you can ensure that they are not spending too much time in front of the screen.
How Are Digital Parenting Tools Helpful?
The digital parenting tools are the software that you need in today’s digitally advanced times. Digital parenting is the solution for digital children. The features mentioned above are not only beneficial when you have tried most of the resources available to look after your child when nothing works, but also when you intentionally want to monitor everything your child does on their phone.
We will discuss how these mentioned features can help in digital parenting. Starting from the call recording feature, this feature works well when your child is constantly on calls and won’t let you around them when they are talking on the phone. With the help of the hidden call recorder, you can remotely listen to your child along with the other person talking to them. Once the call is completed, the mobile spy app will store all the information on the dashboard.
The other feature that parents commonly look for in a phone spy app is the live location tracker. This feature allows you to view the real-time location of your child to ensure that they are exactly where they are supposed to be. Usually children lie about their whereabouts and that is when this feature comes in handy.
Today, every child is on social media and we know how impactful this platform is in both positive and negative ways. While some children find it cool to be on social media, other kids are there just because of the peer pressure. Whatever the reason is, the bottom line is that all the children are online. In the online world, all types of people are present and there are also people who wish to harm others digitally leading to a traumatizing experience also in some cases, so it is important that parents use the digital monitoring tools to ensure their children’s safety.
When new to the internet, kids would want to explore everything they see online. They may also see content that is not age-appropriate. Later on, this may become a habit to view the violating content that can turn into serious addiction. To ensure that they do not watch anything inappropriate, one can use the web browsing history tracker to see which websites the kids are visiting and if you think that it is inappropriate then you can also immediately block them, restricting your kids to not be able to watch any exploiting content.
The Spy App You Need
There are multiple apps available on the internet that provide parental monitoring but be sure to invest in an app that delivers results. Phone spy apps like Onemonitar has shown great results as it is one of the most trusted spy app providers with more than 60 features. There are basic to premium plans that you can choose from as per your requirements and the support team at service also guides you through the process from choosing the right plan for you to installation of the spyware.
The support team is also available through live-chats, emails and calls and if requested, they can also install the application on the target phone remotely for you. With so many facilities and features it is safe to say that Onemonitar can be the right choice for your digital monitoring needs.
In The End
The parental control apps are a valuable and beneficial tool when it comes to monitoring your children’s online activity as they give you proper insights of how your child is using the internet. It is also considered a more relaxed and approachable way to parenting in today’s times.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#social media#parental control#online safety#internet safety
1 note
·
View note
Text
3 Best Hidden Spy Apps for Android in 2022
Whether it is good or bad, but we are actually living in the digital era. This is one of the reasons why the uses of mobile phones have increased. As said above, we are in the digital eon; you now have a solid solution in the form of spy software. Currently, there are numerous options available in the market. If you are planning to use one, then you will get so many options. But what are the best ones?

Below, we have mentioned the best hidden spy apps for android for 2022 that you can try out to enjoy the benefits:
1. uMobix
This is the topmost and highly popular option. It is on the top due to so many good reasons. This spy mobile app option offers numerous exciting features to the users. Some of them include the user-friendly interface, 7 days FREE trial, virtually undoable, recovery of the deleted messages, real-time monitoring, etc. The provider has designed this software is the best for parental control. Since kids are spending more time on the phones to attend the classes, it becomes extremely important for you to keep a watch of their activities and this is the smarted method to do so.
2. Spy App King
If you are searching for the most affordable option of spy software, then you must count on the solutions offered by Spy App King. Being a reputed and prestigious name in the market, they will provide you with the best solution that are not only effective but created keeping your specific needs in the mind. The most exciting features of this app include the capturing of the details of call logs, SMSs, gallery, multimedia files, social media accounts, Facebook messenger & WhatsApp chats, live GPS location, web browser history, emails, installed apps, and so on. In addition to bespoke solutions, you will also get various variants for your precise operating system.
3. Coco Spy
It is yet another good option that can be used by you for the safety and monitoring purposes. Apart from the world-class inventions, Coco Spy is also known for its outstanding customer services. The best hidden spy app for android options provided by the Coco Spy come with so many amazing features that include the simple installation, no need of jailbreak or root, 24*7 customer support, professional support, and so on. You can try it out at least once.
Final Verdict
Now, you must be thinking which option is the best? Even though every option has some pros and cons, you will need to understand your needs first to pick the right spy mobile app. But if you want to get the most affordable and feature-loaded spy software and mobile application options, then you should count on Spy App King. This company not only provides customized solutions but help you with the FREE DEMO so that you can get familiar with the option chosen.
0 notes
Link

#hidden call recorder#hidden spy app#hidden call recorder for mobile#hidden call recorder for android#spy call recorder#spyware for android#spyware software
0 notes
Text

🔐 Why You (Probably) Don't Need A VPN
A rant by a software engineer sick of VPN ads from her favourite YouTubers
TL;DR:
Here are some legitimate reasons the average internet user might want to use a VPN:
To connect to their company's internal network
To bypass the Great Firewall of China (or other types of website blocks at country or organisation level)
To watch Netflix etc as if you were in another country
Here are absolutely rubbish reasons to use a VPN:
Privacy
And today, I'll tell you why.
Hang on, won't a VPN stop hackers from stealing my passwords?
I mean, it does encrypt the web traffic coming from your device.
You know what else encrypts web traffic coming from your device? Your browser.
Yes, in the year 2021, pretty much all websites on the internet are accessed over HTTPS. The "S" stands for "secure", as in "your request will be securely encrypted". If your browser is using HTTPS, nobody can capture the data you're sending over the internet. More detail in the "I like too much detail" section at the bottom of this post.
It's very easy to check if you are using HTTPS by looking at your URL bar. In most browsers, it will have a lock on it if secure:
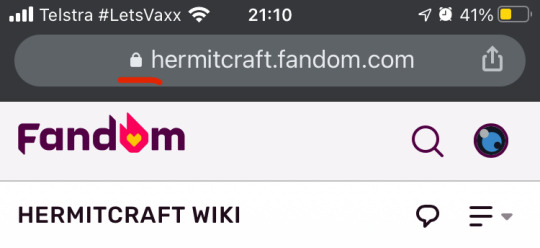
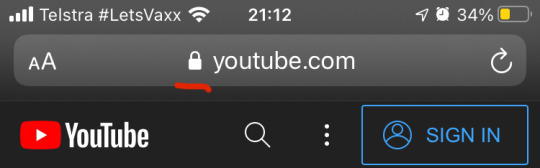




(From top left to bottom right: Chrome on iOS, Safari on iOS, Chrome on Windows, Edge on Windows, Firefox on Windows, and Safari on Mac. Screenshots reflect the UI at the time this post was written. Oh gosh this has taken over 4 hours to write.)
But isn't moar encryption better? What if somebody breaks HTTPS?
For starters, nobody's breaking your HTTPS, and there isn't any benefit from double encrypting. This is because of the maths behind encryption/decryption!
Encryption works kinda like a lock and key, except the lock is maths and the key is a special number only known to the person allowed to unlock the information.
The important thing is, without the key, all the locked data looks like complete and utter garbage. Completely unusable. Barely distinguishable from random noise. There's absolutely no way to tell what the original data was.
The other important thing is that the key is nearly unguessable. As in, with current technology, will generally take more than the lifetime of the universe to guess by chance. And when technology gets faster, we just make the numbers bigger again until they're once again secure.
For any major website you use, they will use a strong encryption algorithm (ie lock) with big numbers so your keys will be strong enough to withstand an attack. This means your data is safe as long as that lock icon is in your URL bar.
A VPN will not make the existing garble any more garbled. The extra $10/month or whatever you're paying for does not buy you any extra protection.
If you want to know more about how encryption and HTTPS in particular work, see the "I like too much detail" section at the end of this post.
Something something viruses
How's a VPN going to stop viruses? It controls the path your internet traffic takes, not the content that gets sent down that path. I guess it could block some known virus-giving hosts? But if it's known to the VPN provider, it's probably also known to the built-in antivirus on your computer who can block it for you.
(Oh yeah, 3rd party antivirus is another thing that's not worth paying for these days. Microsoft's built-in Windows Defender is as good as the third party options, and something something Macs don't get viruses easily because of how they're architected.)
Honestly though, keep your software up to date, don't click on anything suspicious, don't open files from sources you don't trust, and you'll be right most of the time.
And keep your software up to date. Then update your software. Hey, did I mention keeping your stuff updated? Update! Now! It only takes a few minutes. Please update to the latest version of your software I'm begging you. It's the number 1 way to protect yourself from viruses and other malware. Most major software attacks could have been prevented if people just updated their damn software!
But my ISP is spying on me!
Ok, it is true that there are TWO bits of data that HTTPS can't and won't hide. Those are:
The source of a request (your IP)
What website that request is going to (the website's IP)
These are the bits of information that routers use to know where to send your data, so of course they can't be hidden as the data is moving across the internet. And people can see that information very easily if they want to.
Note: this will show which website you're going to, but not which page you're looking at, and not the content of that page. So it will show that you were on Tumblr, but will not show anyone that you're still reading SuperWhoLock content in 2021.
It's this source/destination information that VPNs hide, which is why they can be used to bypass website blocks and region locks.
By using a VPN, those sniffing traffic on your side of the VPN will just show you connecting to the VPN, not the actual website you want. That means you can read AO3 at work/school without your boss/teachers knowing (unless they look over your shoulder of course).
As for those sniffing on the websites end, including the website itself, they will see the VPN as the source of the connection, not you. So if you're in the US and using a VPN node in the UK, Netflix will see you as being in the UK and show you their British library rather than the American one.
If this is what you're using a VPN for and you think the price is fair, then by all means keep doing it! This is 100% what VPNs are good for.
HOWEVER, and this is a big "however", if it's your ISP you're trying to hide your internet traffic from, then you will want to think twice before using a VPN.
Let me put it this way. Without a VPN, your ISP knows every website you connect to and when. With a VPN, do you know who has that exact same information? The VPN provider. Sure, many claim to not keep logs, but do you really trust the people asking for you to send them all your data for a fee to not just turn around and sell your data on for a profit, or worse?
In effect, you're trading one snooper for another. One snooper is heavily regulated, in many jurisdictions must obey net neutrality, and is already getting a big fee from you regardless of where you browse. The other isn't. Again, it's all a matter of who you trust more.
For me personally, I trust my ISP more than a random VPN provider, if for no other reason than my ISP is an old enough company with enough inertia and incompetence that I don't think they could organise to sell my data even if they wanted to. And with the amount of money I'm paying them per month, they've only got everything to lose if they broke consumer trust by on-selling that data. So yeah, I trust my ISP more with my privacy than the random VPN company.
But my VPN comes with a password manager!
Password managers are great. I 100% recommend you use a password manager. If there's one thing you could do right now to improve your security (other than updating your software, speaking of, have you updated yet?), it's getting and using a password manager.
Password managers also come for free.
I'm currently using LastPass free, but am planning to switch after they did a bad capitalism and only let their free accounts access either laptop or mobile but not both now. I personally am planning to move to Bitwarden on friends' recommendation since it's not only free but open source and available across devices. I also have friends who use passbolt and enjoy it, which is also free and open source, but it's also a bit DIY to set up. Great if you like tinkering though! And there are probably many other options out there if you do a bit of googling.
So, yeah, please use a password manager, but don't pay for it unless you actually have use for the extra features.
No I really need to hide my internet activity from everybody for reasons
In this case, you're probably looking for TOR. TOR is basically untraceable. It's also a terrible user experience for the most part because of this, so I'd only recommend it if you need it, such as if you're trying to escape the Great Firewall. But please don't use it for Bad Crimes. I am not to be held liable for any crime committed using information learned from this post.
Further reading viewing
If you want to know more about why you don't need a VPN, see Tom Scott's amazing video on the subject. It's honestly a great intro for beginners.
I like too much detail
Ahhh, so you're the type of person who doesn't get turned off by long explanations I see. Well, here's a little more info on the stuff I oversimplified in the main post about encryption. Uhh, words get bigger and more jargony in this section.
So first oversimplification: the assumption that all web traffic is either HTTP or HTTPS. This isn't exactly true. There are many other application layer internet standards out there, such as ssh, ftp, websockets, and all the proprietary standards certain companies use for stuff such as streaming and video conferencing. Some of these are secure, using TLS or some other security algorithm under the hood, and some of them aren't.
But most of the web requests you care about are HTTP/HTTPS calls. As for the rest, if they come from a company of a decent size that hasn't been hacked off the face of the planet already, they're probably also secure. In other words, you don't need to worry about it.
Next, we've already said that encryption works as a lock and a key, where the lock is a maths formula and the key is a number. But how do we get that key to lock and unlock the data?
Well, to answer that, we first need to talk about the two different types of encryption: symmetric and asymmetric. Symmetric encryption such as AES uses the same key to both encrypt and decrypt data, whereas asymmetric encryption such as RSA uses a different key to encode and decode.
For the sake of my writing, we're going to call the person encrypting Alice, the person decrypting Bob, and the eavesdropper trying to break our communications Eve from now on. These are standard names in crypto FYI. Also, crypto is short for cryptography not cryptocurrencies. Get your Bitcoin and Etherium outta here!
Sorry if things start getting incoherent. I'm tired. It's after 1am now.
So first, how do we get the key from symmetric crypto? This is probably the easier place to start. Well, you need a number, any number of sufficient size, that both Alice and Bob know. There are many ways you could share this number. They could decide it when they meet in person. They could send it to each other using carrier pigeons. Or they could radio it via morse code. But those aren't convenient, and somebody could intercept the number and use it to read all their messages.
So what we use instead is a super clever algorithm called Diffie-Hellman, which uses maths and, in particular, the fact it's really hard to factor large numbers (probably NP Hard to be specific, but there's no actual proof of that). The Wikipedia page for this is surprisingly easy to read, so I'll just direct you there to read all about it because I've been writing for too long. This algorithm allows Alice and Bob to agree on a secret number, despite Eve being able to read everything they send each other.
Now Alice and Bob have this secret number key, they can talk in private. Alice puts her message and the key into the encryption algorithm and out pops what looks like a load of garbage. She can then send this garbage to Bob without worrying about Eve being able to read it. Bob can then put the garbage and the key into the decryption algorithm to undo the scrambling and get the original message out telling him where the good donuts are. Voila, they're done!
But how does Alice know that she's sending her message to Bob and not Eve? Eve could pretend to be Bob so that Alice does the Diffie-Hellman dance with her instead and sends her the secret location of the good donuts instead.
This is where asymmetric crypto comes in! This is the one with private and public keys, and the one that uses prime numbers.
I'm not 100% across the maths on this one TBH, but it has something to do with group theory. Anyway, just like Diffie-Hellman, it relies on the fact that prime factorisation is hard, and so it does some magic with semi-primes, ie numbers with only 2 prime factors other than 1. Google it if you want to know more. I kinda zoned out of this bit in my security courses. Maths hard
But the effect of that maths is easier to explain: things that are encoded with one of the keys can only be decoded with the other key. This means that one of those keys can be well-known to the public and the other is known only to the person it belongs to.
If Alice wants to send a message to Bob and just Bob, no Eve allowed, she can first look up Bob's public key and encrypt a beginning message with that. Once Bob receives the message, he can decrypt it with his private key and read the contents. Eve can't read the contents though because, even though she has Bob's public key, she doesn't know his private key.
This public key information is what the lock in your browser is all about BTW. It's saying that the website is legit based on the public key they provide.
So why do we need symmetric crypto when we have asymmetric crypto? Seems a lot less hassle to exchange keys with asymmetric crypto.
Well, it's because asymmetric crypto is slooooow. So, in TLS, the security algorithm that puts the "S" in "HTTPS", asymmetric RSA is used to establish the initial connection and figure out what symmetric key to use, and then the rest of the session uses AES symmetric encryption using the agreed secret key.
And there you have it! Crypto in slightly-less-short-but-still-high-enough-level-that-I-hope-you-understand.
Just realised how long this section is. Well, I did call it "too much detail" for a reason.
Now, next question is what exactly is and isn't encrypted using HTTPS.
Well, as I said earlier, it's basically just the source IP:port and the destination IP:port. In fact, this information is actually communicated on the logical layer below the application layer HTTPS is on, known as the transport layer. Again, as I said before, you can't really encrypt this unless you don't want your data to reach the place you want at all.
Also, DNS is unencrypted. A DNS request is a request that turns a domain name, such as tumblr.com, into an IP address, by asking a special server called a Domain Name Server where to find the website you're looking for. A DNS request is made before an HTTP(S) request. Anyone who can read your internet traffic can therefore tell you wanted to go to Tumblr.
But importantly, this only shows the domain name, not the full URL. The rest of the URL, the part after the third slash (the first two slashes being part of http://), is stuff that's interpreted by the server itself and so isn't needed during transport. Therefore, it encrypted and completely unreadable, just like all the content on your page.
I was going to show a Wireshark scan of a web request using HTTP and HTTPS to show you the difference, but this has taken long enough to write as it is, so sorry!
I could probably write more, but it's 1:30am and I'm sleepy. I hope you found some of this interesting and think twice before purchasing a VPN subscription. Again, there are legit good uses for a VPN, but they're not the ones primarily being advertised in VPN ads. It's the fact that VPN ads rely so heavily on false advertising that really grinds my gears and made me want to do this rant. It's especially bad when it comes from somebody I'd think of as technologically competent (naming no names here, but if you've worked in tech and still promote VPNs as a way to keep data safe... no). Feel free to ask questions if you want and hopefully I'll get around to answering any that I feel I know enough to answer.
Nighty night Tumblr. Please update your software. And use a (free) password manager. And enable two factor authentication on all your accounts. But mostly just update your software.
577 notes
·
View notes