#Embedded Systems
Explore tagged Tumblr posts
Text
2 notes
·
View notes
Text
My mentor for electronics and embedded systems is sooo good at teaching istg. I walked up to this man after his class and I asked him and he explained the basics in 15minutes and when I thanked him he said “thank YOU for your queries “ bro he almost made me tear up cuz Engineering professors/mentors have been real rough 🙌
3 notes
·
View notes
Text
Should I actually make meaningful posts? Like maybe a few series of computer science related topics?
I would have to contemplate format, but I would take suggestions for topics, try and compile learning resources, subtopics to learn and practice problems
#computer science#embedded systems#linux#linuxposting#arch linux#gcc#c language#programming#python#infosecawareness#cybersecurity#object oriented programming#arduino#raspberry pi#computer building#amd#assembly#code#software#software engineering#debugging#rtfm#documentation#learning#machine learning#artificial intelligence#cryptology#terminal#emacs#vscode
4 notes
·
View notes
Text
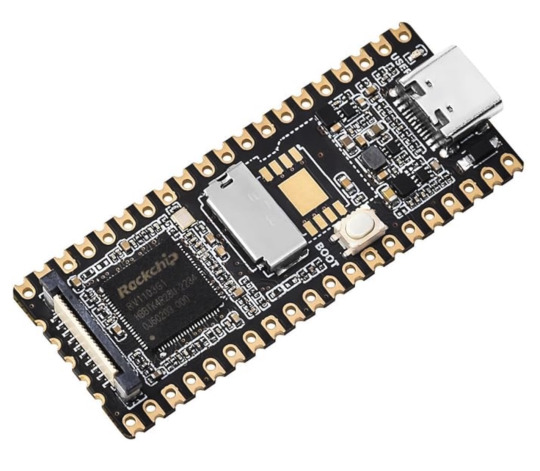
Linux Micro Development Board, Integrates ARM Cortex-A7/RISC-V MCU/NPU/ISP Processors
The LuckFox Pico represents a cost-effective Linux micro development board based on the Rockship RV1103 chip, which supplies a straightforward and efficient development platform for embedded system designers. It supports a variety of interfaces, including MIPI CSI, GPIO, UART, SPI, I2C, USB, and more. Developing applications is convenient, and debugging is quick.
3 notes
·
View notes
Text
youtube
The Indian Institute of Embedded Systems (IIES) is renowned as one of the best training institutes in Bangalore for embedded systems. With a strong focus on practical training and industry relevance, IIES offers comprehensive courses that equip students with the skills needed to excel in the field. The institute boasts experienced trainers who are industry experts, ensuring that students receive top-notch guidance. They provide state-of-the-art lab facilities and hands-on projects to enhance practical learning. Additionally, IIES has collaborations with reputed companies, offering students opportunities for internships and job placements. With a strong track record of success and a commitment to student outcomes, the Indian Institute of Embedded Systems stands out as the premier choice for aspiring embedded systems professionals in Bangalore.
Visit https://iies.in/ to know more
2 notes
·
View notes
Text
Why does digital elecronics is important for engineering?
Digital electronics is super important in engineering for a bunch of reasons—it's pretty much the backbone of modern technology. Digital electronics powers everything from smartphones and computers to cars and medical devices. Engineers across disciplines need to understand it to design, troubleshoot, or innovate with modern systems.

Digital systems work with binary signals (0s and 1s), Less sensitive to noise and signal degradation. Easier to design for precise and repeatable performance.

GET CIRCUIT DESIGNING VIDEO TUTORIAL 👈.
#crank shaft#engine mechanism#four stroke engine#mechanical arms#mechanical engineering#mechanical parts#two stroke engine#digital electronics#digital circuit#digital circuit design#iot circuits#integrated circuits#embeddedsystems#embedded circuit#embedded systems
0 notes
Text
VPX vs. OpenVPX: Key Differences and Why They Matter
As embedded systems evolve to meet modern performance and interoperability demands, the terms VPX and OpenVPX are becoming more prevalent. While often used interchangeably, they represent distinct concepts in the world of rugged embedded computing. Understanding the differences between VPX and OpenVPX is crucial when selecting the right architecture for your application, whether it's defense, aerospace, or industrial automation.
What is VPX?
VPX is a computing standard developed by VITA (VMEbus International Trade Association) that extends the legacy of VME by incorporating high-speed serial interconnects like PCI Express, RapidIO, and Ethernet. It introduces enhanced signal integrity, higher data throughput, and better thermal management. A VPX backplane supports advanced communication between modules in rugged environments, commonly found in military and aerospace systems.
What is OpenVPX?
OpenVPX builds upon the VPX standard by defining a system-level framework that specifies interoperability requirements between VPX modules. While VPX outlines the mechanical and electrical interface, OpenVPX ensures that modules from different vendors can work seamlessly together.
OpenVPX standardizes elements like:
Slot profiles
Module profiles
Payload and switch module types
OpenVPX backplane routing topologies
This added layer of definition is essential for defense integrators seeking to build plug-and-play systems with multi-vendor components.
Key Differences Between VPX and OpenVPX
1. Standard Scope
VPX: Focuses on individual module-level definitions.
OpenVPX: Defines system-level interoperability between modules.
2. Vendor Interoperability
VPX: Lacks standardization across systems, which can lead to compatibility issues.
OpenVPX: Promotes multi-vendor integration and long-term support through standardized system profiles.
3. System Integration
VPX: Ideal for custom system builds.
OpenVPX: Better suited for scalable, modular architectures that evolve over time.
4. Backplane Architecture
VPX backplane: Offers flexibility but can vary widely between implementations.
OpenVPX backplane: Uses predefined topologies and profiles, ensuring consistent performance and interoperability.
5. Form Factors
Both standards support different form factors, with 3U VPX and 3U OpenVPX being widely adopted for compact, high-performance applications.
Choosing Between VPX and OpenVPX
When to choose VPX:
Custom, single-vendor systems
Applications with tightly controlled hardware environments
When to choose OpenVPX:
Multi-vendor, interoperable systems
Programs requiring scalability, rapid integration, and long-term support
Elma Electronic: Your Source for VPX and OpenVPX Solutions
Elma Electronic offers a wide range of VPX products, including 3U VPX and 3U OpenVPX modules, rugged VPX chassis, and both VPX backplane and OpenVPX backplane configurations. Whether you're building a custom solution or looking for SOSA-aligned, interoperable systems, Elma provides expert guidance and reliable hardware.
Explore VPX and OpenVPX offerings here: Elma Electronic
Final Thoughts
While VPX and OpenVPX share the same foundational architecture, OpenVPX enhances interoperability and scalability, making it a preferred standard for modern embedded systems. Knowing the distinctions ensures that your system is not only powerful but also future-ready.
Leverage Elma Electronic's expertise and robust catalog of VPX chassis, VPX products, and standardized OpenVPX backplanes to stay ahead in mission-critical embedded computing.
#embedded software#embedded systems#backplanes#switches#electronicssolution#VPX#OpenVPX#HighPerformanceEmbeddedComputing#HPEC#VPXComputing#VPXSystems#RuggedVPX#VPXArchitecture#VPXSolutions#EmbeddedVPX#VPXInHighPerformanceComputing#WhatIsOpenVPX#BenefitsOfVPXArchitecture#VPXForDefenseComputing#HighSpeedDataVPX#OpenStandardsForHPEC#WhyUseVPXInEmbeddedSystems#NextGenEmbeddedComputing#ElmaSBC#ElmaComputing#ElmaAI#ElmaEmbedded#ElmaEdgeComputing#ElmaTech
0 notes
Text
What are power optimization techniques in embedded AI systems?
Power efficiency is a critical concern in embedded AI systems, particularly for battery-operated and resource-constrained devices. Optimizing power consumption ensures longer operational life, reduced heat dissipation, and improved overall efficiency. Several key techniques help achieve this optimization:
Dynamic Voltage and Frequency Scaling (DVFS): This technique adjusts the processor’s voltage and clock speed dynamically based on workload requirements. Lowering the frequency during idle or low-computation periods significantly reduces power consumption.
Efficient Hardware Design: Using low-power microcontrollers (MCUs), dedicated AI accelerators, and energy-efficient memory architectures minimizes power usage. AI-specific hardware, such as Edge TPUs and NPUs, improves performance while reducing energy demands.
Sleep and Low-Power Modes: Many embedded AI systems incorporate deep sleep, idle, or standby modes when not actively processing data. These modes significantly cut down power usage by shutting off unused components.
Model Quantization and Pruning: Reducing the precision of AI models (quantization) and eliminating unnecessary model parameters (pruning) lowers computational overhead, enabling energy-efficient AI inference on embedded systems.
Energy-Efficient Communication Protocols: For IoT-based embedded AI, using low-power wireless protocols like Bluetooth Low Energy (BLE), Zigbee, or LoRa helps reduce power consumption during data transmission.
Optimized Code and Algorithms: Writing power-efficient code, using optimized AI frameworks (e.g., TensorFlow Lite, TinyML), and reducing redundant computations lower energy demands in embedded AI applications.
Adaptive Sampling and Edge Processing: Instead of continuously transmitting all sensor data to the cloud, embedded AI systems perform on-device processing, reducing communication power consumption.
Mastering these power optimization techniques is crucial for engineers working on intelligent devices. Enrolling in an embedded system certification course can help professionals gain expertise in designing efficient, low-power AI-driven embedded solutions.
0 notes
Text
Board Support Package (BSP) Development - Epsum Labs

In the world of embedded systems, getting hardware and software to work together seamlessly is no small feat. That’s where the Board Support Package (BSP) comes in—a critical component that ensures your operating system (OS) communicates effectively with your hardware.
But what exactly is BSP, and why does it matter for embedded development?
Let’s break it down step by step in simple terms.
What is a Board Support Package (BSP)?
Think of BSP as a bridge between hardware and software. It contains the essential drivers, configuration files, and bootloaders that allow an OS—like Linux—to run on a specific hardware platform.
Without it, your board is just an expensive piece of silicon!
Core Components of BSP:
�� Bootloader – Wakes up the hardware and loads the OS into memory. ✅ Kernel & Device Tree (DTB) – Customizes the OS to recognize hardware features like GPIOs, buses, and memory. ✅ Device Drivers – Enables communication between the OS and peripherals (USB, Ethernet, Display, etc.). ✅ Root Filesystem (RootFS) – Houses system libraries, scripts, and utilities that run in user space. ✅ Board Configuration Files – Stores startup scripts and kernel configurations to define system behavior.
Step-by-Step BSP Development Process
Building a BSP isn’t just about writing code—it’s a structured process to ensure hardware and software integration. Here’s how it works:
🔹 Step 1: Hardware Bring-Up – Getting the board powered up and running. 🔹 Step 2: Bootloader Configuration & Debugging – Setting up the bootloader to initialize hardware correctly. 🔹 Step 3: Kernel & DTB Porting – Modifying the Linux Kernel and device tree to match the board’s hardware. 🔹 Step 4: Building the Root Filesystem (RootFS) – Creating the system environment using tools like Yocto or Buildroot. 🔹 Step 5: OS Bring-Up & Debugging – Testing and debugging system boot, drivers, and peripherals. 🔹 Step 6: Driver Development & Optimization – Customizing device drivers and improving boot times. 🔹 Step 7: BSP Finalization & Deployment – Packaging everything and deploying it onto the target board.
Each step ensures that your embedded system runs efficiently and reliably.
Read More on Board Support Package Development
0 notes
Text
Job - Alert 📢

🚗 Spannende Gelegenheit an der Universität der Bundeswehr München! 🚗
Uni_BW_M sucht eine Wissenschaftliche Mitarbeiterin bzw. einen Wissenschaftlichen Mitarbeiter (m/w/d) für das Projekt „Autonomes Ausweichen in urbanen Fahrszenarien“ am Institut für Embedded Systems im Rahmen des Forschungsprojekts MORE.
📅 Startdatum: Ab sofort
📧 Interessiert? Senden Sie Ihre Bewerbungsunterlagen bis zum 31. März 2025
Erfahren Sie mehr über diese spannende Gelegenheit und bewerben Sie sich über folgenden Link: https://www.academiceurope.com/job/?id=6948
Gestalten Sie mit uns die Zukunft der Mobilität! 🌐
#hiring#jobs#science#jobseekers#electricalengineering#informatics#mechatronics#embedded systems#robotics#research assistant
0 notes
Text
https://electronicsbuzz.in/altium-and-aws-collaborate-to-equip-indias-next-generation-of-engineers/
#Altium#nextgeneration#cloudcomputing#digitaltransformation#embedded systems#IoT#ElectronicsDesign#CloudComputing#FutureEngineers#EdTech#powerelectronics#powermanagement#powersemiconductor
0 notes
Text
Here is a cool blog post with hardware hacking tool suggestions. I would say it's fairly beginner friendly.
2 notes
·
View notes
Text

Understanding SAE J1939: A Comprehensive Guide to Monitoring, Simulation, and Development
Learn the fundamentals of SAE J1939 protocol for heavy-duty vehicle communication, including monitoring, simulation, and development tools for beginners.
0 notes
Text
The Importance of Embedded Systems in Computer Science and Communication Engineering
Technology is evolving rapidly, and embedded systems are playing a crucial role in shaping modern innovations. From everyday devices like smartphones and smartwatches to complex systems in automobiles, healthcare, and industrial automation, embedded systems are the backbone of many technological advancements.
For students pursuing computer science and communication engineering, understanding embedded systems is essential as they bridge the gap between hardware and software, creating intelligent and efficient solutions. Many CS and communication engineering courses focus on embedded systems because they are integral to modern computing and communication technologies.
What Are Embedded Systems?
Embedded systems are specialized computing systems designed to perform dedicated functions within larger systems. Unlike general-purpose computers, embedded systems are optimized for specific tasks, making them more efficient in terms of power consumption, speed, and reliability. They consist of microcontrollers or microprocessors, memory, and software that control their operations.
These systems are used in various applications, including:
Consumer Electronics – Smartphones, smart TVs, and wearable devices.
Automotive Industry – Engine control units, anti-lock braking systems, and infotainment systems.
Healthcare – Medical devices such as pacemakers, MRI scanners, and blood pressure monitors.
Industrial Automation – Robotics, factory control systems, and automated machinery.
Why Are Embedded Systems Important in Computer Science and Communication Engineering?
Embedded systems are essential in computer science and communication engineering because they power many of the devices and networks that define modern life. They are used to develop efficient, real-time computing solutions that improve performance, security, and communication between systems.
Bridging Hardware and Software
Embedded systems combine hardware and software, allowing engineers to create devices that function seamlessly. This knowledge is crucial for students in CS and communication engineering courses, as it equips them with skills to develop and optimize systems used in various industries.
Real-Time Processing
Many embedded systems are designed for real-time applications, meaning they process data instantly without delays. This is critical in sectors like healthcare, automotive, and telecommunications, where real-time responses can improve safety and efficiency.
Security and Reliability
Embedded systems are designed to be secure and reliable. They are used in applications where data protection and system stability are critical, such as banking systems, surveillance networks, and defense technologies. Engineers specializing in embedded systems ensure these systems remain robust and protected against cyber threats.
Career Opportunities in Embedded Systems
As industries increasingly rely on embedded systems, career opportunities in this field continue to grow. Graduates of computer science and communication engineering programs can explore roles such as:
Embedded Software Engineer – Developing software for embedded systems in various industries.
Firmware Engineer – Working on low-level software that controls hardware functions.
IoT Developer – Creating smart devices that connect to networks for data exchange.
Automation Engineer – Designing and maintaining industrial automation solutions.
Network Systems Engineer – Enhancing communication protocols and secure data transfer in embedded networks.
Conclusion
Embedded systems are a fundamental part of modern technology, influencing everything from consumer devices to industrial automation and healthcare innovations. For students enrolled in CS and communication engineering courses, gaining expertise in embedded systems is valuable, as it opens up diverse career paths in software development, automation, and IoT.
As technology continues to advance, the demand for skilled engineers in computer science and communication engineering will only increase, making embedded systems a key area of study and innovation.
1 note
·
View note
Text
0 notes
Text
Programming Embedded Systems (with C and GNU Development Tools)
[Programming Embedded Systems (with C and GNU Development Tools). By Michael Barr & Anthony J Massa. 2nd Edition, 1 October 2006. Publisher: O'Reilly Media. Paperback: 301 pages, Dimensions: 17.78 x 1.98 x 23.34 cm. ISBN: 978-0-596-00983-0]
In the past 15 months or so I elected to expand my personal and professional skill set to include working with small computing systems, sometimes referred to as microcontrollers. These devices have become virtually omnipresent, in everything from automobiles and bar-code scanners to toasters and doorbells. If you operate a late-model vehicle, for instance, you may have as many as 70 (!) of these devices in the car controlling everything from the fuel mixture to emissions to anti-lock brakes and collision avoidance sensing.
I was interested in moving into this arena as part of my career, as there were many openings for people with a strong understanding of the imperatives attendant on both the software and hardware of embedded systems. I knew a bit about the electronics side of things and I have done software development of one sort or another most of my 40+ years as a professional, but this arena poses unique challenges and opportunities. I knew I needed to do some specialized self-teaching, and this book seemed like a great place to start.
To start with, what exactly is an embedded system?
As the name implies, it is a system - in this case a miniature computing device - that is a component of a larger framework. This larger framework can take on myriad forms. Some of the largest such frameworks are satellite networks. The embedded system comprises hardware - a central processing unit, or CPU, along with some (minimal) on-board memory and one or more electrical interfaces (e.g. a USB or RJ45 jack) through which it can communicate with the outside world.
Unlike the computers most of us are familiar with, such as Windows or MacOS-based laptops or Linux servers, these devices often do not have an operating system (WIndows, MacOS and Linux are all operating systems) that performs many of the low-level functions needed to keep the device running and useful.
This keeps the device flexible in terms of how it can be used, but at the expense of more detailed and subtle development and maintenance requirements. Thus, the "software" on an embedded system may be a very small bit of computer code that simply turns on the interfaces electrically and then waits for something to happen.
Programming software for these systems is intriguing but fraught with issues that an ordinary computer user never sees.
For example, given that the memory and interface resources on these devices tend to be rather modest, it's necessary for the programmer to take care of any bookkeeping that is necessary to keep the basic functions from colliding. If one of the interfaces is used to provide a scanned barcode to a waiting receiver, it must pass that information through some on-board memory first.
The embedded software designer needs to be sure that this information can't be corrupted, or "clobbered", by a competing task that might be, for instance, putting the scanning laser into sleep mode to save power. Moreover, there are cases where the same locations in memory need to be shared by tasks as a part of getting work done.
But what happens if one task is trying to write data to a specific memory location while another task is trying to read from it? Is there always a specific order in which this happens? What happens if either operation is incomplete for some reason? Will the device recover and continue to operate, or will it lock up? The aforementioned are but a tiny set of examples that the developer must bear in mind.
Messrs Barr and Massa have many decades of experience between the two of them in just these kinds of environments. I was delighted to see just how easy this book is to read and how thoroughly they cover all of the issues that accompany such a software development enterprise. They are careful to create and explain examples that use commonly-available development kits (I use an STM32 ARM Cortex-M Development Board myself; there is a photo of one such system below) and free or nearly-free software tools to break down the barriers to entry in this field.

This book is really as much about operating system design as it is about microcontroller software development; if one is interested in what nearly every operating system must do, this volume talks all about it.
Above and beyond this, it is a wealth of anecdotes, sample code, and general wisdom that will really ease the novice into this exciting world of programming and small-device control.
I highly recommend it to anyone who wants to get down on the bare metal with computers. It is necessary to be at least familiar with the C programming language (almost all of the examples are coded in C) and it would be very helpful to have worked with at least one Assembly language as well. Beyond that, the only requirement for getting the most out of the book is a willingness to experiment and be delighted.


Image Credits (from above down; with thanks to copyright owners): (1) STM32 ARM Cortex-M Development Board © Copyright Owner, date unknown (2) Book Cover © O'Reilly Media 11 October 2006 (3) Michael Barr © Barr Group 2012-2025. (Anthony J Massa, no photograph found)
Kevin Gillette
Words Across Time
4 February 2025
wordsacrosstime
#Words Across Time#Kevin Gillette#wordsacrosstime#February 2025#Michael Barr#Anthony Massa#O'Reilly Media#Embedded Systems#C#Satellite Networks#Electrical Interfaces#MacOS#Linux#Flexible#Computer Code#Barcode#Scanning Laser#Memory Location#STM32#Microcontrollers#Anecdotes#Assembly Language#Sample Code#General Wisdom#Computers
0 notes