#EmailSecurity
Explore tagged Tumblr posts
Text
Top 10 Tips for Solving Email Security Problems
Email is one of the most prevalent forms of communication, but it's also a common target for cyber threats. Protecting email accounts is crucial for both individuals and organizations to safeguard sensitive data from unauthorized access, phishing attacks, and malware. Here’s a detailed guide to the best practices for securing email accounts effectively.

1. Strengthen Password Policies
Creating and enforcing strong password policies is a foundational step in email security. Passwords should be unique and complex, avoiding common phrases or easily guessable information. Encourage users to use a combination of uppercase and lowercase letters, numbers, and special characters. To further improve security, consider a password manager to store and generate strong passwords, which minimizes the risk of reuse or weak passwords.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds a second layer of protection beyond just a password. With 2FA, users are required to verify their identity through another method—such as a code sent to their phone or through an authenticator app—each time they log in. This makes it significantly harder for unauthorized users to access an email account, even if they have the password.
3. Educate Users on Phishing and Social Engineering
Phishing attacks remain one of the most common ways hackers gain access to sensitive data. Training users to recognize phishing attempts is essential. Teach them to check for signs like misspellings in URLs, unexpected attachments, or links that lead to suspicious sites. Implement policies where users can report suspected phishing emails, creating a culture of awareness and proactive defense against these attacks.
4. Implement Email Encryption
Encryption is a method of encoding email messages to prevent unauthorized access. With encryption, even if an email is intercepted, its contents remain unreadable without the decryption key. This is especially important for emails containing sensitive or personal information. Consider using end-to-end encryption tools that encrypt emails from the sender to the receiver, ensuring data protection throughout the message’s journey.
5. Use Advanced Spam Filters
Spam filters play an important role in blocking unwanted and potentially harmful emails from reaching inboxes. Today’s advanced spam filters can screen emails for specific patterns or markers associated with phishing, malware, and spam. Adjust the sensitivity of spam filters to ensure legitimate messages are not mistakenly blocked while minimizing the number of risky emails that reach users.
6. Regular Software Updates and Patch Management
Outdated software can be a security risk, as cybercriminals often exploit known vulnerabilities in email clients or systems. Implement a policy that ensures all software, including operating systems and email applications, is regularly updated to the latest version. These updates often include patches that address known security weaknesses, helping to keep email accounts secure.
7. Limit Access to Email Accounts
Only authorized individuals should have access to sensitive email accounts. Setting access controls ensures that only those who need the information can reach it. For instance, granting limited access to shared inboxes can prevent unauthorized employees or contractors from viewing sensitive communications, reducing the risk of internal threats.
8. Monitor Email Account Activity
Use email monitoring tools to track unusual or unauthorized login attempts, email forwarding rules, and other indicators of potential security threats. For example, if an account is accessed from an unfamiliar location or at odd times, the system can alert administrators or prompt users to confirm their identity. Monitoring tools also provide logs for post-incident investigations, if needed.
9. Back Up Email Data Regularly
Data backups are essential in case of a ransomware attack or accidental deletion. Regular backups ensure you have access to important information, even if the primary data is compromised. Automate backup processes and store backups securely. Test backup recovery periodically to ensure data can be restored quickly and effectively when needed.
10. Conduct Regular Security Audits
Routine audits help identify vulnerabilities within email systems and ensure compliance with security policies. During audits, assess access controls, software updates, and the effectiveness of spam filters. Security audits also provide an opportunity to review and update user education programs, helping reinforce best practices for email security.
Securing email accounts requires a combination of technical measures, user education, and ongoing vigilance. By following these ten tips, individuals and organizations can effectively minimize the risks associated with email communications and protect sensitive data from unauthorized access.
1 note
·
View note
Text
2024 Email Rules: Google & Yahoo’s New Requirements

In September this year, Google and Yahoo set new standards for email authentication for the year 2024, thus making best practices mandatory. These changes are to enhance the outlook in email defended and to minimize spam impacts on media senders, including but not limited to big companies. To stay compliant, follow these essential steps: 1.Authenticate Emails: To secure your emails you must employ the Dominick keys identified mails, sender policy fraud, and domain messages assurance and reporting. 2.Maintain Low Spam Rates: Make sure that your spam complaint rate did not go beyond 0.3%. 3.Make Unsubscribing Easy: Users should be able to opt out of the information sharing within two days. 4.Use Secure Connections: Of course, when sending emails use TLS encryption. This will help maintain an upward sender reputation and guarantee positive reaction to any email marketing.
Read more: Google yahoo new requirements for email senders
0 notes
Text
DKIM is email-authentication technique similar to SPF. DKIM allows the receiver to check that an email was indeed sent and authorized by the owner of that domain. This is done by adding a digital DKIM signature on emails. A DKIM signature is a header that is added to a message and secured with encryption.
Authenticating legitimate sending sources with DKIM gives the receiver (receiving systems) information on how trustworthy the origin of an email is, and it can significantly improve the overall deliverability of an email channel.
In practice, DKIM on its own is not enough to fully protect an email channel. The email validation system DMARC is often mandatory and required for compliance as it creates a link between SPF and DKIM by validating whether a sending source has been authenticated with either SPF or DKIM.
Furthermore, DMARC allows organizations to instruct email services like Gmail, Hotmail and others to reject all emails that are not aligned with SPF and or DKIM.
#emailsecurity#phishing#infosec#cybersecurity#linux#sysadmin#systemadministrator#systemadmin#emailserver#dns
0 notes
Text
Smart Email Solutions

Streamline communications with expert email solutions, fortified with top-tier email protection. Learn more: https://centurygroup.net/managed-it-solutions/email-solutions/
#emailprotection #cybersecurity #ransomware #antivirus #ransomwareprotection #phishing #malware #ransomwareattack #phishingscam #cyberprotection #phishingattack #dataprotection #emailsecurity #backup #becybersafe #datarecovery
1 note
·
View note
Text
#MessagingSecurity#CyberSecurity#EmailSecurity#DataProtection#CyberDefense#PhishingProtection#InformationSecurity#DigitalSecurity
0 notes
Text
Business Email Compromise: 7 Shocking Facts and How to Protect Your Company Today! 🚨

In the digital age, cyber threats are lurking around every corner, and one of the most dangerous is Business Email Compromise (BEC). This sophisticated scam has caused billions of dollars in losses for companies worldwide. Are you at risk? Discover 7 shocking facts about BEC and learn how to protect your company from this insidious threat today! 🚨
1. The Rising Threat: BEC Attacks Are Skyrocketing 📈
Business Email Compromise isn’t just a buzzword – it’s a rapidly growing menace. Cybercriminals use deceptive tactics to trick employees into transferring money or divulging sensitive information. With over $26 billion in reported losses since 2016, BEC is a threat you can’t afford to ignore.
Fact Check:
According to the FBI, BEC scams have increased by 100% over the past few years. Stay vigilant and informed!
2. CEO Fraud: The Devious Tactic Targeting Top Executives 👨💼
Imagine receiving an urgent email from your CEO requesting an immediate wire transfer. It looks legitimate, but it’s a clever ruse. CEO fraud, a type of BEC, preys on employees' trust in their executives, leading to significant financial losses.
Quick Tip:
Implement multi-factor authentication (MFA) and verify high-risk requests through multiple communication channels.
3. Vendor Email Compromise: The Sneaky Supplier Scam 📬
Cybercriminals don’t just target internal emails; they also infiltrate your suppliers’ email systems. By compromising a trusted vendor, they can redirect payments to their accounts, leaving your company out of pocket and your vendor relationship in jeopardy.
Proactive Measure:
Regularly verify payment details with suppliers using established communication methods.
4. Phishing: The Gateway to BEC 🐟
Phishing emails are a common entry point for BEC attacks. These deceptive messages lure employees into revealing login credentials or downloading malware, giving cybercriminals access to corporate email accounts.
Defense Strategy:
Conduct regular phishing awareness training for employees and use advanced email filtering solutions.
5. The Costly Consequences: Financial and Reputational Damage 💸
BEC attacks don’t just result in financial loss – they can also severely damage your company’s reputation. Clients and partners may lose trust in your ability to protect their information, leading to long-term business consequences.
Risk Mitigation:
Invest in cyber insurance to cover potential financial losses and implement robust security protocols.
6. Detection Difficulties: Why BEC Is Hard to Spot 🔍
Unlike traditional phishing scams, BEC emails often lack obvious red flags like suspicious links or attachments. This makes them harder to detect and increases the likelihood of a successful attack.
Enhanced Protection:
Utilize artificial intelligence (AI) and machine learning (ML) tools to detect unusual email patterns and anomalies.
7. Legal Ramifications: The Hidden Costs of BEC ⚖️
Beyond immediate financial losses, BEC can lead to legal troubles. Failure to protect sensitive information may result in regulatory fines and lawsuits, further exacerbating the damage to your business.
Compliance Check:
Ensure your cybersecurity measures comply with industry regulations and standards to avoid legal pitfalls.
How to Protect Your Company from BEC Today! 🛡️
1. Implement Advanced Email Security Solutions
Use email security software that provides real-time threat detection, phishing protection, and spam filtering. These tools can significantly reduce the risk of BEC attacks.
2. Strengthen Authentication Protocols
Implement multi-factor authentication (MFA) for all employees, especially those with access to sensitive financial information. This adds an extra layer of security.
3. Conduct Regular Employee Training
Educate employees about the dangers of BEC and phishing. Regular training sessions and simulated phishing exercises can keep everyone alert and aware.
4. Establish Clear Verification Processes
Create strict protocols for verifying financial transactions and sensitive requests. This should include direct verification with the requesting party through a different communication channel.
5. Monitor and Audit Email Activity
Regularly monitor email accounts for unusual activity and conduct audits to identify potential vulnerabilities. Early detection can prevent significant losses.
6. Update Software and Systems Regularly
Keep your email systems, security software, and other IT infrastructure updated with the latest security patches to protect against known vulnerabilities.
7. Collaborate with Cybersecurity Experts
Partner with cybersecurity firms to conduct regular risk assessments and implement advanced security measures tailored to your business needs.
Conclusion: Don’t Be the Next Victim! Act Now to Secure Your Business 🌟
Business Email Compromise is a serious threat that can have devastating consequences. By understanding the risks and implementing these protective measures, you can safeguard your company against BEC attacks. Don’t wait until it’s too late – start fortifying your defenses today and ensure your business stays secure and resilient in the face of cyber threats.
Call to Action:
Want to stay ahead of cyber threats? Stay tuned to protect your business and join our community of security-conscious professionals today!
#BusinessEmailCompromise#Cybersecurity#EmailSecurity#DataProtection#CyberThreats#PhishingAttacks#CyberCrime#EmailFraud#SecurityAwareness#BusinessSecurity#CyberAwareness#FraudPrevention#EmailCompromise#CyberAttack#ITSecurity#ProtectYourCompany#EmailScams#SecurityMeasures#SecurityTips#BusinessProtection
0 notes
Text
Cyber Threats Q1 2024 revealed: Cat-Phishing, Living Off the Land, Fake Invoices

Cat-phishing, using a popular Microsoft file transfer tool to become a network parasite, and bogus invoicing were among the notable techniques cybercriminals deployed in Q1 2024, per @HP Wolf Security Report. https://tinyurl.com/mpjd96xp
#cybersecurity#threats#phishing#malware#infosec#cybercrime#hacking#emailsecurity#netsec#dataprotection#ransomware#antivirus#cyberthreats#phishingattacks#scams#catphishing#asyncrat#bits#filehijacking#redirectattacks#fakeinvoices#securityawareness#threatintelligence#emailgateways#browsersecurity#mobilemalware
0 notes
Link
https://bit.ly/3SSDF86 - 🔍 Guardio Labs unveils "SubdoMailing" — a widespread subdomain hijacking campaign compromising over 8,000 domains, including MSN, VMware, and eBay. Millions of malicious emails circulate daily, exploiting trust and stolen resources. #SubdoMailing #CyberSecurity 📉 Guardio's email protection systems detect unusual patterns, leading to the discovery of thousands of hijacked subdomains. The operation involves complex DNS manipulations, facilitating the dispatch of spam and phishing emails under reputable brands. #EmailSecurity #DNSManipulation 📧 Examining a deceptive email reveals clever tactics, including image-based content to bypass spam filters. SPF, DKIM, and DMARC authentication are manipulated, allowing scam emails to reach users' inboxes. #EmailScam #CyberAttack 💻 Analysis uncovers the resurrection of abandoned domains, enabling subdomain hijacking for malicious activities. Actors manipulate SPF records, creating a web of authorized senders to evade detection. #DomainSecurity #SPFManipulation 🛡 Guardio identifies a coordinated campaign by threat actor "ResurrecAds," exploiting compromised domains for mass email dissemination. The operation spans diverse tactics, including SPF authentication injection and SMTP server hosting. #ThreatActor #CyberCrime 🔎 Tracking indicators of compromise reveals the extensive infrastructure behind "SubdoMailing," spanning hosts, SMTP servers, and IP addresses. The operation's scale and sophistication underscore the need for collaborative defense efforts. #CyberDefense #ThreatAnalysis 🔒 Guardio launches a "SubdoMailing" checker tool to empower domain owners in reclaiming control over compromised assets. The tool provides insights into abuse detection and prevention strategies. #CyberAwareness #SecurityTool 📢 Join Guardio in raising awareness about the "SubdoMailing" threat and utilizing the checker tool to fortify domain security. Together, we can mitigate the impact of malicious email campaigns and safeguard digital landscapes.
#SubdoMailing#CyberSecurity#EmailSecurity#DNSManipulation#EmailScam#CyberAttack#DomainSecurity#SPFManipulation#ThreatActor#CyberCrime#CyberDefense#ThreatAnalysis#CyberAwareness#SecurityTool#DomainProtection#ebay#dmarc#stolenresources#domain#emails#cybersecurity#operation#brands#emailsecurity
0 notes
Text
Unleash your campaign strategies and content strategy with B2BInDemand Email marketing

Unleash your campaign strategies and content strategy with B2BInDemand Email marketing
1. AI-Powered Personalization: Elevate customer experiences with AI-driven content tailored to individual preferences.
2. Interactive Emails: Engage audiences like never before with interactive elements, boosting click-through rates and conversions.
3. Privacy-First Strategies: Embrace evolving privacy regulations by prioritizing transparent, consent-driven communications.
4. Omni-Channel Integration: Seamlessly integrate email marketing with other channels for a cohesive customer journey.
5. Sustainability Initiatives: Embrace eco-friendly practices by optimizing email delivery and reducing carbon footprints.
6. Hyper-Personalization: Harness advanced segmentation techniques to deliver hyper-targeted content based on user behavior, demographics, and preferences.
7. Visual Storytelling: Utilize compelling visuals, videos, and GIFs to convey your brand story and captivate audiences, enhancing engagement and brand recall.
8. Automation and Workflow Optimization: Streamline your email marketing processes with automated workflows, from welcome sequences to post-purchase follow-ups, saving time and maximizing efficiency.
Stay ahead of the curve and revolutionize your email marketing strategy in 2024!
Get in touch with us: https://lnkd.in/d4DSZgEA
Follow Us: Instagram: https://lnkd.in/dmpTZrbX Twitter: https://lnkd.in/dGZE7pq2 Linkedin: https://lnkd.in/dyfVd2uv
contact us: 1 (302) 966 9297 www.b2bindemand.com [email protected]
#emailmarketing#trends2024#emailcampaigns#emailsecurity#emails#emailmarketingtips#emailmarketingstrategy#b2bindemand
1 note
·
View note
Text

From the get-go of establishing your digital space, even with well-documented employee training, there's a risk that someone on the team might unintentionally click or download harmful software from the 🤿backend waters. The bait? Often disguised as emails, robust email security is the ultimate fishing rod for safeguarding your environment.
It's not just about securing your emails; it's about becoming a savvy angler, identifying false positives swimming in the currents, and skilfully redirecting them to the correct inbox, ensuring smooth sailing for your business activities.
Whether it's 💰 monetary values, your reputation, 🌐email login details, or sensitive codes like OTP, you must avoid falling victim to phishing scams.
⚓ Stay sharp | Don’t Get Phished 🎣
Connect with us, and let’s discuss your current cyber plan.
#emailsecurity#phishingprotection#phishingawareness#linkedin#cyberattack#cybercrime#cyberaware#cyber
0 notes
Text

The Need of secure e-mail service . . . . for more information and tutorial https://bit.ly/47giFx3 check the above link
#cybersecurity#emailsecurity#sslstripping#mitbattck#computerscience#arpspoofing#emailhacking#sessionhacking#mitmattck#computerengineering#javatpoint
1 note
·
View note
Text
Email Security Exploration: Guide to DMARC Reports and Beyond
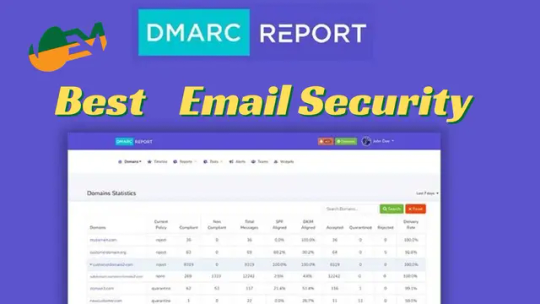
In the vast landscape of digital communication, fortifying your email security is no longer a choice but a necessity. Join us on an expedition through the intricate realm of DMARC (Domain-based Message Authentication, Reporting, and Conformance) reports – the guardian of your domain's sanctity against phishing and cyber threats. 🌐📧🛡️
Navigating the DMARC Citadel
Embark on a journey into the heart of DMARC, a formidable fortress shielding your domain from the rising tide of phishing scams and cybercrimes. Understand the pivotal role DMARC plays in ensuring your emails are not just messages but trusted emissaries from your domain. 🏰📬
DMARC: Sentinel of Email Authenticity
Delve into the significance of authenticating emails in the digital age. Explore how DMARC acts as a vigilant sentinel, protecting users from phishing attacks, fostering trust with customers, and boosting email deliverability. Uncover the power of genuine communication. 🔒📩
Deciphering the Code: Inside DMARC Reports
Unlock the mysteries concealed within DMARC reports, presented in the enigmatic XML format. From metadata to policy application, become fluent in interpreting the wealth of information these reports offer. Equip yourself with the skills to monitor and optimize your email ecosystem. 🕵️♂️📊
Strategies for Email Deliverability Mastery
Your emails deserve the spotlight, not the shadows of spam folders. Learn the art of leveraging DMARC policies to maximize email deliverability. Safeguard your sender reputation, engage with your audience, and witness the success of your email campaigns soar to new heights. 📈📧
DMARC in Marketing Alchemy
Witness the transformation of DMARC from a security protocol into a potent catalyst for marketing success. Elevate your email open rates, enhance your sender reputation, and craft marketing strategies that resonate with your audience. Unleash the alchemy of DMARC in your marketing endeavors. 🚀📈
Crafting the Invincible DMARC Policy
Forge an impregnable DMARC policy that not only shields your domain against cyber threats but also optimizes email delivery. Navigate the delicate balance between security and accessibility, gradually enforcing policies to secure your domain's reputation. ⚖️🔒
Ready to elevate your email security, authenticity, and deliverability? 🚀 Embark on this comprehensive guide, and let DMARC be your beacon in the ever-evolving digital landscape. 🔐📧🌐
🎁 To view the full review in detail: Click here!
🎊 To learn About The Power of other software, themes, or plugins: Click here!
✨ To hire any of us as a Video Editor, Audio Engineer, Shopify Expert, YouTube Manager, or Content Writer: Click here!🌐🔐🚀
#DMARC#EmailSecurity#DigitalFrontier#DMARCreports#CyberGuardian#EmailDeliverability#MarketingAlchemy
0 notes
Text

Best-in-Class Email Services
Experience Email Perfection with Magtec
#Email#emailservices#emailcontent#emailsecurity#emailmarketing#emailmarketingsolutions#emailmanagement#magtec#uaebusiness#dubai2023
1 note
·
View note
Text
Email Security Practises
Secure Email Practices: A Must for Cybersecurity!
Email is a key communication tool, but it can also be a major security risk if not handled properly. Here are some tips to ensure you practice good email cybersecurity behavior:
-Use Strong Passwords: Create complex passwords and update them regularly.
-Enable Two-Factor Authentication: Add an extra layer of security to your email account.
-Be Cautious with Attachments and Links: Verify the sender before opening attachments or clicking on links.
-Update Your Software: Ensure your email client and antivirus software are up to date.
-Avoid Public Wi-Fi: Use a secure connection or a VPN when accessing your email.
By following these practices, you can safeguard your information and maintain a secure communication channel. Stay vigilant, stay secure! #CyberSecurity #EmailSafety #StaySecure #CenturySolutionsGroup
#Secure Email Practises#emailsecurity#phishing emails#managed it services#cybersecurity#cloud technology services#cyberattack
1 note
·
View note
Text

📂 Need to open an RPMSG file in Gmail? 🔑📧
✨ Learn how to access encrypted or protected emails effortlessly. Perfect for professionals dealing with secure messages! 🙌
👉 Get the step-by-step guide here: 🔗 https://blogarium.com/how-to-open-rpmsg-file-in-gmail/
#GmailTips #EmailSecurity #RPMSG #HowToGuide #TechHacks
0 notes
Photo

Explore the safety of sending bank details by email. Understand the risks, potential security breaches, and how to adopt safer methods for protecting your sensitive financial information. read the full article: https://bit.ly/4hitK7g #BankDetails #EmailSecurity #FinancialTips #Encryption #PhishingAwareness read more: is it safe to send bank details by email
0 notes