#DataCenterSecurity
Explore tagged Tumblr posts
Text

GCC Data Center Market size by value at USD 3.2 billion in 2024. During the forecast period between 2025 and 2031, BlueWeave expects GCC Data Center Market size to boom at a robust CAGR of 8.8% reaching a value of USD 5.3 billion by 2031. The growth of Data Center Market across GCC region (consisting of Bahrain, Kuwait, Oman, Qatar, Saudi Arabia, and United Arab Emirates (UAE)) is propelled by the burgeoning IT sector, the escalating adoption of hybrid and multi-cloud solutions, and the surging demand for automated systems and low-latency data transfers. The exponential growth of data generated by OTT platforms and social media has further intensified the need for robust data center infrastructure. The integration of Big Data, analytics, and smart technologies within the oil and gas sector, coupled with the rise of sustainable practices and innovative models, is significantly driving regional growth. The ongoing migration from on-premise infrastructure towards colocation and managed services, facilitated by government initiatives for digital transformation and the advancement of 5G technology, is poised to drive substantial growth throughout the forecast period.
Sample Request: https://www.blueweaveconsulting.com/report/gcc-data-center-market/report-sample
#BlueWeave#Consulting#Marketforecast#Marketresearch#CloudSecurity#Cybersecurity#DataCenterSecurityTrends#DataCenterSecurity
0 notes
Text
When it comes to data center relocation, security is paramount. AAA Security Guard Services provides expert protection to ensure your sensitive equipment and data remain secure during every step of the move. Our trained professionals understand the complexities of high-stakes relocations, offering peace of mind in every situation. Trust us to safeguard your valuable assets from start to finish. #DataCenterSecurity #RelocationProtection #SecureMoves
0 notes
Video
youtube
Network Rack Door Access Control System- Biometric Fingerprint Face Card...
0 notes
Text


A distributed firewall (DFW) is s replicated among multiple hosts the way the vSphere distributed switch or logical router is replicated. With the DFW, it is possible to deploy any multitier application in the same Layer 2 broadcast domain for all tiers and have the same subnet and the same default gateway. https://www.dclessons.com/distributed-logical-firewall
#DistributedFirewall#NetworkSecurity#FirewallProtection#Cybersecurity#DCLessons#LogicalFirewall#FirewallManagement#DataCenterSecurity#NetworkProtection#SecurityBestPractices#FirewallTechnology#CyberDefense#InformationSecurity#FirewallSolutions#NetworkInfrastructure
0 notes
Photo

Looking for Firewall to protect your Data centers? Look no further. Skylark partnering with Fortinet provides Next Generation Firewall to secure Data centers. Contact Skylark to know more.
#nextgenerationfirewall#firewall#skylark#skylarkinfo#fortinetpartner#cybersecurity#security#technology#skylarkinformationtechnologies#networking#vpn#networksecurity#cyberattack#datacentersecurity
0 notes
Photo

Choose The Best Email Hosting Servers For Your Business To Avail Such Services, Connect With Us Today.
#linuxvps#linuxuser#linuxdedicatedserver#datacentersecurity#topleveldomain#linuxvpsserverplan#lowcostvpshosting#alphavbox#SneakerProxies#cheapsneakerproxies#sneakerbotproxies#bestproxiesforbots#bulkemailserverhosting#bulkemailhostingproviders#unmanageddedicatedserverhosting#cloneserver
1 note
·
View note
Photo

Cloud services are sometimes deemed synonymous with web services. Cloud services is an umbrella term that may refer to a variety of resources provided over the internet from cloud computing. The usage of cloud services has become closely associated with common cloud offerings, such as SaaS, PaaS, and IaaS: http://bit.ly/Picnotes_CloudServices
#cloudservices#it#cloudcomputing#technology#cloud#datasecurity#cybersecurity#tech#cloudsolutions#cloudtechnology#digitaltransformation#security#lifelonglearner#lifelonglearners#datacenter#datacentersecurity
6 notes
·
View notes
Text
Data Center Security Best Practices: What are they?
Modern technology and cloud computing have revolutionized the way of collecting and storing data. Even if organizations are moving to the cloud infrastructure, the security of the data centers is the major concern for all. There are various practices that you can do for Data Center security. These days
web hosting service
is becoming very popular. But before going ahead, let’s learn about Data Centers and their security.What is Data Center?
The data center is the storage facility for the organization's IT infrastructure. It stores the crucial systems and data significant for the operation of the organization. The data center offers organizing, processing, storing data, data recovery, and many more.
Earlier, data centers were highly controlled physical infrastructure but the public cloud has changed the model. Modern data centers are evolving from on-premises physical servers to virtual infrastructure except where the regulatory restrictions require on-premises data centers.
Data center security includes practices, policies, measures, and technologies that are used for both physical and virtual protection. Security measures should protect the data center from external as well as internal threats.
Various risks are there such as data loss, data alteration, corruption, SQL injection, tailgating, etc. pose a constant threat to the infrastructure of the data center.
Now as you know about Data centers, you must know what you can do for Data Center Security to keep all the data safe and secure from every type of threat.
5 Best Practices for Data Center Security:-
Monitor and restrict access-
The biggest threat to any kind of security is human error. Security areas that hold servers and key assets never grant access to unauthorized personnel. Data centers need multiple access control over all layers for ensuring this security.
Biometrics is an effective way to ensure security. It uses the individual’s unique characteristics such as fingerprint, retina scan, etc. Access cards and identification badges are the best security measures that any organization can take into account. Specialized security measures should be there in each room and area. To Know More Best Practices for Data Center Security Read Full Article Here>>
1 note
·
View note
Photo

The Dedicated server plans are affordable and flexible and can blend into your existing business infrastructure and budget.
#datacentersecurity#datacenterinfrastructure#dedicateddatacenter#datacentersolutions#datacenterprovider#websitehostingcompaniesinusa#cheapunlimitedresellerhostingusa#datacenter
0 notes
Photo

Enable your business to swiftly move communication to cloud. While many say they fear failing due to the cloud telephony myths, we thought of busting a few of them and helping you in keeping your business ahead of your competitors. Read the blog to know about the myths and facts that revolve around cloud telephony solutions.
#go2market#cloudtelephony#smartoffice#voipbusiness#callmanagement#mythsvsfacts#cloudplatform#cloudtelephonyservices#investment#datasecurity#datacentersecurity#voice#communication#productivitytips#increaseproductivity
1 note
·
View note
Text

Saudi Arabia Data Center Security Market size by value at USD 142.6 million in 2024. During the forecast period between 2025 and 2031, BlueWeave expects Saudi Arabia Data Center Security Market size to boom at a robust CAGR of 16.8% reaching a value of USD 409.6 million by 2031. The growth of Data Center Security Market in Saudi Arabia is propelled by the strategic government initiatives, economic expansion, technological innovations, and a rising demand for data storage and processing. The government's supportive policies, in conjunction with the nation's commitment to digital transformation and sustainability, are fostering a conducive environment for investments and innovations. The increasing adoption of cloud computing, the emergence of the Internet of Things, and the growing sophistication of cyber threats are intensifying the demand for advanced data center solutions. Consequently, Saudi Data Center Security Market is positioned for sustained growth, attracting considerable interest from both domestic and international stakeholders, thus reinforcing the country's status as a significant contributor to the global digital landscape.
Sample Request: https://www.blueweaveconsulting.com/report/saudi-arabia-data-center-security-market/report-sample
#BlueWeave#Consulting#Marketforecast#Marketresearch#DataCenterSecurityTrends#CloudSecurity#Cybersecurity#DataCenterSecurity
0 notes
Text
Ransomware Threatens The Healthcare Industry

Coronavirus pandemic has shown the best and worst in people; which is no wonder that Ransomware attacks are on the rise.
Despite COVID-19 epidemic everywhere you look there´s another healthcare network or business that has fallen under cybercrime. Ransomware attacks have become another worldwide pandemic and damages could cost the world´s healthcare industry billions of dollars. These attacks can be difficult to prevent since cybercriminals continue to evolve their strategies; the most recent attacks have been focusing on small to medium sized companies with less sophisticated IT systems.
What is Ransomware?
This is a type of malware that target healthcare businesses looking for financial records and all sensitive data regarding patient information; than cybercriminals encrypt this information so healthcare providers’ can´t access it, and in exchanged for not displaying this information to the public, they demand a certain amount of money. This malware can enter your system in numerous ways, the most common one is phishing emails that have embedded links containing ransomware code; the most recent way is through social media, the goal is the same.
How can I prevent a Ransomware attack?
Small to Medium sized organizations may think that paying these hackers is the only way out to get their information back, but this is often the worst solutions and many never receive access to their data even after paying the ransom. So, before something like this happens to your company, there are a few security precautions that you can take:
Secure your systems. Instead of allowing all employees to access every part of the system, restrict access to certain areas of the network to administrators only.Add anti-malware and anti-virus software to your systems to prevent and even block any threats, these tools will alert any activity on possible malicious sites and emails.
Train your staff. This has been proven to be one of the most effective ways against cyberattacks; by educating your employees to identify common threats within emails or social media you can significantly reduce the risks of malware entering your system.Keep in mind that hackers are continuously evolving the way in which they attack, so continuous reminders are in order; also, consider email phishing simulators to test your staff as a complement to your training programs.
Create an emergency plan. In case of an attack, make sure you have strict protocols and procedures to execute as a quick response. In some cases, depending on the ransomware attack, a healthcare provider could seek for law enforcement´s help to get the decrypting key from the FBI´s database. Still, you must perform a deep analysis of your system to determine all specific actions that were taken on the network to identify all possible gaps within your organizations´ IT infrastructure that might have led to an attack in order to avoid future ones.
How can we help?
Ransomware attacks are a serious issue, but instead ofwaiting for an attack to occur, you need to take action now. Sometimes protocols are not enough to keep your company safe; you need a reliable hosting provider as well, like Webline-Services that can offer all the solutions you need to protect your IT system. Our services are budget friendly, and they include the most advanced features; we are your perfect business partner, and you can rest assured that in case of any possible breach, we won´t rest until all issues are solved. Our solutions are the best in the market, so if you are a small to medium sized healthcare provider, Webline-Services has the infrastructure in place to prevent any cybercrime from happening.
#cybersecurity#cyberattack#datacentersecurity#hostingprovider#hostingsolutions#hostingservices#webhost#webhostingservices#share#likes#follow#likes4likes#follow4followback
0 notes
Text
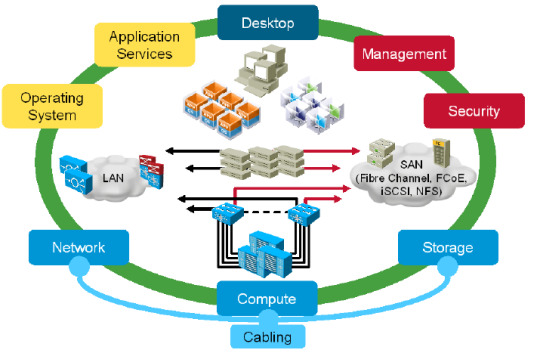
Unlock the power of Cisco #Nexus solutions. From data centers to campus networks, we've got you covered. Navigate complex architectures with confidence and drive seamless connectivity. https://www.dclessons.com/category/courses/nexus
#NetworkingPro#ScalableSolutions#cisco#nexus#datacenter#switching#routing#networking#networkengineering#devops#cloudcomputing#datacenterdesign#datacentermanagement#datacentersolutions#datacentersecurity
0 notes
Text
Is Your Data Center Prepared for Hurricane Season ? Ensure Your safety, Uptime and Data security
Hurricane season has already begun and many enterprises are looking for assurance that their data center providers can sustain uptime and prevent costly losses during a natural disaster. This is where Stream comes in, giving our customers the peace of mind to focus on growing their businesses.
0 notes