#SecurityBestPractices
Explore tagged Tumblr posts
Text
How to Create an AI-Powered Chrome Extension
Chrome extensions are essential for enhancing browser functionality, and integrating AI opens new avenues for innovation. AI-powered extensions automate tasks, provide recommendations, and offer personalized interactions, benefiting both users and developers. This guide covers essential Chrome extension development, integrating AI like machine learning and NLP, and best practices for security, efficiency, and user-friendly design.
#ChromeExtensions#AIPowered#BrowserEnhancements#MachineLearning#NLP#WebDevelopment#ProductivityTools#SecurityBestPractices#UserFriendlyDesign
0 notes
Text
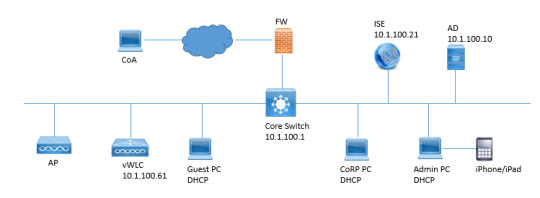
Cisco ISE and Active Directory are two of the most popular network security solutions. By integrating these two solutions, you can simplify network security management and improve security. https://www.dclessons.com/ise-ad-integration
#ISE#ActiveDirectory#Integration#NetworkSecurity#IdentityManagement#Cybersecurity#ITSecurity#Authentication#CiscoISE#DirectoryServices#TechTutorial#IdentityIntegration#NetworkInfrastructure#SecurityBestPractices#ITTraining
0 notes
Text
Safeguarding Your Digital World: Unraveling Authentication Vulnerabilities
In today's rapidly advancing digital era, ensuring the security of our online activities has never been more critical. As the reliance on digital platforms increases, so does the risk of falling victim to cyber threats. One of the most pressing concerns that internet users and businesses face is authentication vulnerabilities. In this article, we'll delve into the world of authentication vulnerabilities and explore measures to protect ourselves in the dynamic landscape of Web 2.0.
Understanding Authentication Vulnerabilities:
Authentication vulnerabilities refer to weaknesses in the mechanisms that verify and validate users' identities on digital platforms. These vulnerabilities expose sensitive information to unauthorized individuals, leading to potential data breaches, identity theft, and financial losses. As Web 2.0 continues to evolve with a focus on user-generated content and interactive experiences, it becomes crucial to address these vulnerabilities.
Common Authentication Vulnerabilities:
2.1. Weak Passwords: One of the most common authentication vulnerabilities arises from weak passwords. Users often choose passwords that are easy to remember but equally easy to guess. This makes it effortless for attackers to compromise accounts and gain unauthorized access.
2.2. Phishing Attacks: Phishing attacks trick users into revealing their login credentials through deceptive emails, messages, or websites that mimic legitimate platforms. As Web 2.0 encourages active engagement and social sharing, users become more susceptible to these cunning schemes.
2.3. Insecure Login Forms: Web 2.0 platforms are all about user interaction, and login forms are a common entry point for attackers. Inadequate security measures in login forms can lead to brute-force attacks and credential stuffing.
2.4. Insufficient Multi-Factor Authentication (MFA): MFA provides an additional layer of security by requiring users to provide multiple pieces of evidence to confirm their identities. Failing to implement MFA leaves accounts vulnerable to unauthorized access.
Mitigating Authentication Vulnerabilities:
3.1. Strong Password Policies: Web 2.0 platform administrators should enforce strong password policies, mandating the use of complex and unique passwords. Users must be educated about password best practices, such as avoiding common words and regularly updating their passwords.
3.2. User Awareness and Education: Raising awareness among users about phishing attacks and other social engineering tactics is crucial. Regular educational content on the platform can empower users to recognize and report suspicious activities.
3.3. Secure Coding Practices: Web 2.0 developers should prioritize secure coding practices while implementing login forms and user authentication. Input validation, data encryption, and protection against common attacks like SQL injection must be integral parts of the development process.
3.4. Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of protection, significantly reducing the risk of unauthorized access. Web 2.0 platforms should encourage users to enable MFA and make the process user-friendly.
Conclusion:
Authentication vulnerabilities pose a significant threat to the security and integrity of Web 2.0 platforms. As users actively engage in content creation and social interaction, safeguarding their digital identities becomes paramount. By understanding the common authentication vulnerabilities and adopting proactive security measures, both platform administrators and users can collaboratively create a safer digital environment. Embracing strong password practices, promoting user awareness, employing secure coding practices, and implementing MFA will fortify the foundations of Web 2.0, ensuring a more secure and enjoyable online experience for all.
#Authentication vulnerabilities#CyberSecurityThreats#WebSecurity#PasswordSecurity#PhishingAttacks#UserAuthentication#DataBreachRisk#MultiFactorAuthentication#Web2Security#OnlineIdentityProtection#SecureLoginPractices#UserAwareness#DigitalIdentitySecurity#WebDevelopmentSecurity#ProtectYourAccounts#OnlineSafetyTips#DataPrivacy#SecurityBestPractices#CyberThreats#IdentityTheftPrevention
1 note
·
View note
Text
Network Security: A Comprehensive Guide
#NetworkSecurity#CyberSecurity#OnlineProtection#DataPrivacy#InfoSec#CyberThreats#SecurityBestPractices#StaySafeOnline#network#security#entrepreneur#miami#business#protection#music#safety#marketing#bodyguard#photography#nyc#networking#securityguard#fashion#atlanta#hiphop#executiveprotection#motivation#police#usa#love
0 notes
Text
Safeguarding Against Credential Stuffing Attacks
https://supedium.com/cyber-security-tips/safeguarding-against-credential-stuffing-attacks/ #behavioralanalytics #credentialstuffing #multi-factorauthentication #passwordmanagement #ratelimiting #securitybestpractices Safeguarding Against Credential Stuffing Attacks https://supedium.com/cyber-security-tips/safeguarding-against-credential-stuffing-attacks/
0 notes
Text

Advanced Security Robust security measures to protect user data and ensure confidentiality, Integrity and Availability.
For more queries please visit below link 👇 www.fresatechnologies.com/products/fresa-gold
For further inquiries, please contact us : [email protected]
#Fresa | #Freightsolutions | #Freightforwarding | #Import | #FresaGold | #ERPSoftware | #G2Awards | #LeaderEMEA | #UsersLoveUs | #Leader | #EMEA | #EMEASummer2024 | #LeaderSummer2024 | #LeaderSmallBusiness | #MomentumLeader | #CategoryLeader | #BestSupport | #Crozdesk | #DataSecurity | #CyberSecurity | #DataProtection | #Confidentiality | #Integrity | #AdvancedSecurity | #PrivacyMatters | #DataConfidentiality | #SecurityBestPractices | #Encryption | #DataIntegrity | #SecureInfrastructure
0 notes
Text
Tips for Secure Code Review | CybersecurityTv

In this informative video, CybersecurityTv presents valuable tips for conducting secure code reviews, an essential practice in ensuring the safety and integrity of software applications. Secure code reviews play a crucial role in identifying and addressing potential vulnerabilities and weaknesses before they are exploited by malicious actors.
#SecureCodeReview#CybersecurityTips#CodeSecurity#SoftwareDevelopment#SecurityBestPractices#ThreatModeling#VulnerabilityAssessment#SecureCoding#ContinuousLearning#CybersecurityEducation
0 notes
Text
Threat Modeling: What is it? 🧐
In today's rapidly evolving digital landscape, security has become a paramount concern for organizations. Cyber threats and attacks are constantly on the rise, targeting sensitive data, systems, and infrastructure. To effectively combat these threats, organizations employ various security measures, one of which is threat modeling. Threat modeling is a proactive approach that helps organizations identify potential vulnerabilities and risks in their systems, allowing them to prioritize security efforts and develop effective countermeasures.
🔍 Let's delve deeper into what threat modeling entails and its benefits for organizations!
Read on 👉 https://www.valevpn.com/post/threat-modeling-what-is-it
ThreatModeling #Cybersecurity #SecurityRisk #VulnerabilityAssessment #RiskManagement #InformationSecurity #SecureDevelopment #ThreatIdentification #DataProtection #SecureSystems #SecurityBestPractices #SecureCoding #SecurityAwareness #RiskMitigation #SecurityCompliance #CyberThreats #ThreatPrevention #SecurityStrategy #SecurityMeasures #SecurityFramework #RiskAnalysis

0 notes
Photo

0 notes
Text


A distributed firewall (DFW) is s replicated among multiple hosts the way the vSphere distributed switch or logical router is replicated. With the DFW, it is possible to deploy any multitier application in the same Layer 2 broadcast domain for all tiers and have the same subnet and the same default gateway. https://www.dclessons.com/distributed-logical-firewall
#DistributedFirewall#NetworkSecurity#FirewallProtection#Cybersecurity#DCLessons#LogicalFirewall#FirewallManagement#DataCenterSecurity#NetworkProtection#SecurityBestPractices#FirewallTechnology#CyberDefense#InformationSecurity#FirewallSolutions#NetworkInfrastructure
0 notes
Text
Allowlisting: What is it? 💡
In the ever-evolving landscape of cybersecurity, it is essential to have effective measures in place to protect computer systems and networks from malicious activities. One such measure is allowlisting, also known as whitelisting.
Read on 👉 https://www.valevpn.com/post/allowlisting-what-is-it
Allowlisting #Whitelisting #Cybersecurity #SecurityMeasures #AccessControl #ProactiveSecurity #Blocklisting #MalwareProtection #ZeroDayAttacks #SecurityBestPractices #CyberDefense #DataSecurity #NetworkSecurity #TrustedEntities #ITSecurity #SystemProtection #SecureAccess #MalwarePrevention #SecurityPolicy #SecuritySolutions #EmployeeTraining

0 notes
Photo

0 notes
Photo
0 notes
Photo

0 notes
Photo

0 notes