#Data Integration Industry
Explore tagged Tumblr posts
Text

Browse Full Report and TOC @ https://straitsresearch.com/report/data-integration-market/request-sample
#Data Integration Market#Data Integration Market Share#Data Integration Market Size#Data Integration Market Research#Data Integration Industry#What is Data Integration?
0 notes
Text
The Benefits of Using a B2B Contact Database for Sales and Marketing
Article by Jonathan Bomser | CEO | AccountSend.com

In today's business world, sales and marketing teams need to work smarter, not harder. One way to do this is by utilizing a B2B contact database. A B2B contact database is a collection of contact information for businesses that can be used for sales and marketing purposes. Here are some of the benefits of using a B2B contact database for sales and marketing:
Save Time and Effort on Lead Generation for B2B companies A B2B contact database can save time and effort for sales and marketing teams by providing a wealth of information on potential customers. Instead of spending hours researching companies and trying to find the right contact person, a B2B contact database can provide up-to-date contact information and key details about the business.
Identify Ideal Customers A B2B contact database can help sales and marketing teams identify ideal customers based on specific criteria. For example, a team may be looking to target businesses in a certain industry or of a certain size. With a B2B contact database, they can easily filter and sort through businesses that meet their criteria and focus their efforts on those that are most likely to convert into customers.
Improve Sales and Marketing Outreach A B2B contact database can help sales and marketing teams improve their outreach efforts by providing accurate and up-to-date contact information. This can help teams avoid sending emails or making calls to outdated or incorrect contacts, which can be a waste of time and can damage a company's reputation.
Increase Sales and Revenue By using a B2B contact database, sales and marketing teams can increase their chances of making a sale and generating revenue. With access to accurate B2B contact information and key details about a business, teams can tailor their messaging and outreach efforts to specific businesses, increasing the chances of success.
youtube
Enhance Customer Relationships A B2B contact database can also help sales and marketing teams enhance their relationships with customers. By having access to key details about a business, teams can better understand the needs and pain points of their customers and tailor their messaging and outreach efforts accordingly. This can help build trust and loyalty with customers and lead to long-term relationships.
In conclusion, a B2B contact database can provide numerous benefits for sales and marketing teams. By saving time and effort, identifying ideal customers, improving outreach efforts, increasing sales and revenue, and enhancing customer relationships, a B2B contact database can help businesses grow and succeed in today's competitive marketplace.
#B2B#Decision makers#Lead generation#Sales outreach#Email marketing#Account-based marketing#Market segmentation#CRM integration#Small business marketing#sales leads database#contact leads database#Contact data accuracy#Niche industries#b2b lead generation database#Sales pipeline#Marketing strategy#Industry trends#Sales opportunities#B2B data providers
2 notes
·
View notes
Text
Lionbridge Language AI Unleashed: Transforming Localization with Vincent Henderson
In the latest episode of the Localization Fireside Chat, I had the privilege of speaking with Vincent Henderson, Vice President of Language AI Strategy at Lionbridge, one of the leading global companies in localization and AI-driven language solutions. Our conversation focused on how Lionbridge is leveraging AI to revolutionize localization processes, transforming efficiency, quality, and…

View On WordPress
#AI Automation#AI Frameworks#AI Integration#AI Security#Artificial Intelligence#Aurora AI#Data Governance#GPT-4#Language AI#Language Solutions#Lionbridge#Localization#Localization Fireside Chat#localization industry#Localization Trends#Machine Translation#REACH framework#Translation Accuracy#Translation Technology#TRUST framework#Vincent Henderson
0 notes
Text
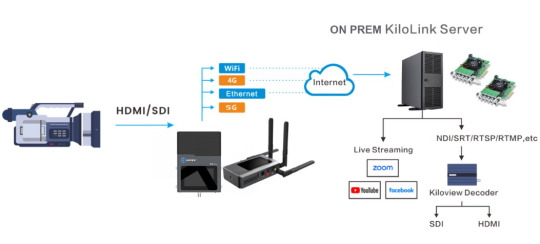
Discover Kiloview Bonding Solutions: P3 & P3 Mini for Seamless Streaming
New Post has been published on https://thedigitalinsider.com/discover-kiloview-bonding-solutions-p3-p3-mini-for-seamless-streaming/
Discover Kiloview Bonding Solutions: P3 & P3 Mini for Seamless Streaming
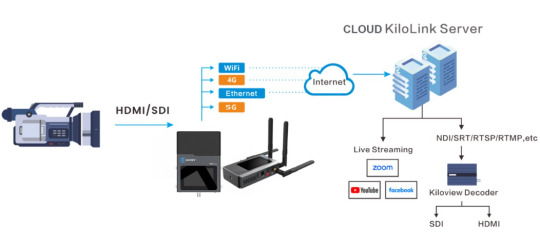
Discover the power of Kiloview’s P3 and P3 Mini cellular bonded encoders, designed for seamless live streaming with multi-network bonding and reliable video transmission. This video explores their flexible integration with top streaming platforms, key product specifications, pricing, and diverse industry use cases. With advanced NDI support, these compact, cost-effective encoders streamline video workflows without extra hardware, making them ideal for outdoor streaming and professional productions.
Watch the full video below:
youtube
Kiloview P3 Mini
The P3 mini Wireless Bonding Encoder is the perfect outdoor live streaming device built on patented KiloLink bonding transmission technology. The P3 mini features professional-grade antenna isolation design, allowing for the effective bonding and connection of multiple channels (supporting 3*4G cellular network + 1WiFi + 1*RJ45 Ethernet port), boasting exceptional anti-interference capability and stable transmission performance. It is equipped with dual input interfaces for 3G-SDI and HDMI, supporting up to 1080P60 video resolution. Additionally, the P3 mini is equipped with a 5000mAh battery with 4-hours continuous operation and supports PD fast charging, fully meeting versatile application scenarios.
3x 4G integrated modems with WiFi connectivity
USB C power delivery
Fast charging
3-inch screen with touch screen controls
Small and easy to carry
4G connectivity
1080p60 HDMI – SDI H.264/H2.65
P3 Mini Verticals
Small TV and radio for sports and racing events for on the go connectivity and social media streaming
Remote engagement style for small events and news gathering
Few camera productions with laptops and minimal setup required mainly social media streaming
Kiloview P3 Bonding Encoder
Kiloview P3 Cellular Bonding Encoder is a new generation of 5G bonding video encoder based on KiloLink, supporting multi connections bonding: 4-channel 5G cellular network, WIFI and Ethernet. P3 is equipped with dual video inputs of 3G-SDI and HDMI with resolution up to 4Kp30 through its HDMI input and up to 1080p60 through its SDI input. Upgraded H.265 encoding capability and perfectly adaption to KiloLink Server ensure the best quality of multi-protocol live streaming and video transmission.
4G and 5G modular modems with WiFi conenctivity
Redundant battery and long lasting streaming sessions
4.3-inch screen with touch controls
Modular design over time
5G coverage covers most challenging situations
4K30p HDMI
1080p60 SDI
H.264/H.265
KILOVIEW P3 Wireless Bonding Encoder Complete Bundle Solutions Including Modems
P3 Applications
Sports
Racing events
Concerts
Healthcare
Enterprise
e-Sports
Big / Mid TV and radio broadcasting
Remote engagement style for events
Events for high numbers with multi camera and REMI producitons
Which P Series Encoder is Right for your Workflow?
Small business with no 5G requirements
Easy to install in critical spots like racing cars or drone applications
1080p or HD maximum resolution needed
Low cost 4G data plans accordingly to business needed
5G essential requirements for demanding zone with low cellular network coverage
Long lasting streaming with hot swappable battery
4k up to 30p required
Eng beltpack style
Daily usage for news and sports
KiloLink Server Pro
Unlimited Streaming Channels
Patented KiloLink Transmission Technology
Direct output of NDIHX
Multi-Link Bonding
Flexible Operation via Web Interface
Centralized Firmware Management & Upgrades
Remote Control of Devices
Easy to Deploy and Operate
Workflows



#4g#4K#5G#amp#applications#battery#bundle#Business#Cars#channel#connectivity#continuous#data#Design#devices#drone#easy#enterprise#Events#fast charging#Features#firmware#Full#Hardware#hdmi#healthcare#Industry#integration#interference#it
0 notes
Text
The Importance of a Public Relations Agency in Malaysia
In today’s fast-paced and competitive business landscape, maintaining a strong brand reputation is crucial. Whether you are a startup or an established company, having a trusted partner to manage your brand’s communication can make all the difference. This is where a public relations agency in Malaysia plays a key role in shaping your brand’s image and ensuring effective communication with your target audience.
A public relations agency in Malaysia helps businesses build and maintain a positive image through strategic communication. PR agencies handle media relations, crisis management, reputation building, and social media engagement. With Malaysia being a growing hub for businesses across industries, it is essential for companies to stay ahead with well-crafted PR strategies. Purpose Communications PR Agency is one such agency that understands the unique challenges businesses face in the region.
Public relations firms work closely with brands to enhance their visibility and credibility. They create compelling narratives that resonate with audiences and foster strong relationships between brands and stakeholders. In an era where digital presence is everything, PR agencies integrate traditional media strategies with modern digital outreach to create maximum impact. Purpose Communications PR Agency specializes in delivering tailored PR solutions that help businesses thrive in the Malaysian market.

Advantages of Partnering with a Public Relations Agency in Malaysia A professional PR agency ensures that your brand is consistently featured in the media, increasing brand awareness and credibility. Companies may face unexpected crises that could harm their reputation, and a PR agency provides crisis communication strategies to mitigate damage and maintain trust. PR agencies also have strong connections with journalists, influencers, and media houses, ensuring your brand gets the right exposure at the right time. A well-structured PR campaign tells a compelling brand story that captivates and engages the audience, helping to differentiate your business from competitors. With digital media being a crucial component of brand success, PR agencies integrate social media strategies to enhance online engagement and brand loyalty.
Why Purpose Communications PR Agency Stands Out They specialize in crafting tailored PR strategies that align with business goals and drive impactful results. Purpose Communications PR Agency has a proven track record of delivering exceptional PR solutions for businesses across various industries. Their expertise in media relations, digital PR, and crisis management makes them a trusted partner for companies seeking to enhance their brand reputation.
Investing in a public relations agency in Malaysia is a strategic move that can significantly enhance your brand’s presence and credibility. PR agencies like Purpose Communications PR Agency provide tailored solutions to ensure your business remains competitive in the dynamic Malaysian market. By leveraging professional PR services, you can strengthen your brand image, foster customer trust, and achieve long-term success. If you are ready to take your brand to the next level, consider working with a top PR agency that understands your needs and can deliver measurable results.
#digital marketing agency#social media agency#marketing and public relations#integrated marketing and communications#SEO Services in india#tech pr agency in singapore#social media marketing agency#brand marketing#crisis management#integrated pr communications agency#research and data analysis services#pr agency in india#strategic positioning marketing#content curation services#bangalore pr agency#social digital marketing#pr agency for healthcare industry singapore#public relations agency in malaysia#content marketing strategy#content marketing and strategy#purpose communications pr agency
0 notes
Text
What are the next steps after obtaining an insurance broker license, and how can you generate potential leads using Mzapp CRM software?
Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful insurance brokerage. Here’s how you can proceed and leverage Mzapp CRM software to find potential leads:
Steps After Getting Your Insurance Broker License
Understand Your Market: Research your target audience (individuals, businesses, or specific sectors).
Develop a Business Plan: Set goals for client acquisition, revenue, and operational processes.
Build a Network: Partner with insurance providers and attend industry events to establish your presence.
Create an Online Presence: Build a professional website and maintain active profiles on social platforms.
Offer Value-Added Services: Educate customers on policies, claims management, and risk assessments.
Using Mzapp CRM Software to Generate Leads
Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.
Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.
Lead Scoring: Prioritize leads based on their interaction history, ensuring you focus on high-potential prospects.
Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.
Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.
Why Choose Mzapp CRM?
Mzapp CRM simplifies lead management, streamlines operations, and provides insights into customer behavior, making it easier to convert prospects into loyal clients.
Learn more about how Mzapp can transform your insurance business here.
#Question:#What are the next steps after obtaining an insurance broker license#and how can you generate potential leads using Mzapp CRM software?#Answer:#Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful i#Steps After Getting Your Insurance Broker License#Understand Your Market: Research your target audience (individuals#businesses#or specific sectors).#Develop a Business Plan: Set goals for client acquisition#revenue#and operational processes.#Build a Network: Partner with insurance providers and attend industry events to establish your presence.#Create an Online Presence: Build a professional website and maintain active profiles on social platforms.#Offer Value-Added Services: Educate customers on policies#claims management#and risk assessments.#Using Mzapp CRM Software to Generate Leads#Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.#Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.#Lead Scoring: Prioritize leads based on their interaction history#ensuring you focus on high-potential prospects.#Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.#Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.#Why Choose Mzapp CRM?#Mzapp CRM simplifies lead management#streamlines operations#and provides insights into customer behavior#making it easier to convert prospects into loyal clients.#Learn more about how Mzapp can transform your insurance business here.
1 note
·
View note
Text

Enhancing Gas Pipeline Management with GIS: Key Benefits and Applications
In the energy and utilities sector, gas pipeline management is complex, requiring precision, safety, and a clear strategy for both existing infrastructure and future expansion. Geographic Information Systems (GIS) have revolutionized pipeline management by providing a spatially accurate, data-rich view of assets. From asset management and leak detection to route planning and demand forecasting, GIS is becoming indispensable for gas companies. This blog delves into the ways GIS transforms gas pipeline management, delivering benefits across safety, efficiency, cost-saving, and planning.
#benefits of using gis for gas pipelines#ensuring gas pipeline safety with gis tools#gas network analysis#gas pipeline asset management#gas pipeline gis mapping services#gas pipeline leak detection using gis#gas pipeline management in gis#gas pipeline mapping software#gas pipeline monitoring tools#gas pipeline risk assessment#gis applications in energy sector#gis for gas pipeline monitoring#gis for infrastructure management#gis in oil and gas industry#gis pipeline maintenance software#gis pipeline monitoring system#gis pipeline route planning#gis software for gas pipeline route optimization#victoryofgoodoverevil#gis solutions for pipeline maintenance and monitoring#gis-based pipeline integrity management#pipeline data management#pipeline geographic information systems#pipeline management solutions#remote sensing for gas pipelines#spatial analysis for gas pipelines#spatial data for gas pipelines
0 notes
Text
How Celebal Technologies' Power & Utility Forecasting Framework (PUFF) is Transforming Forecasting in the Energy Sector
In today's fast-evolving energy landscape, accurate forecasting is pivotal for optimizing operations, improving decision-making, and ensuring sustainability. The Power & Utility Forecasting Framework (PUFF) by Celebal Technologies is designed to address these needs, offering a comprehensive and intelligent solution to revolutionize forecasting in the energy and sustainability sectors. By leveraging advanced industrial intelligence, PUFF provides a reliable, precise, and scalable forecasting platform tailored for utilities and energy providers.
Empowering the Energy Sector with PUFF
PUFF is a state-of-the-art solution that integrates diverse data sources and external factors, such as weather conditions and market prices, to deliver precise predictions across multiple areas of the energy sector. This holistic approach significantly enhances the accuracy of load forecasting, generation forecasting, price forecasting, and weather forecasting, enabling energy companies to make informed, data-driven decisions.
Key Features of the Power & Utility Forecasting Framework (PUFF)
Seamless Data Integration: PUFF effortlessly supports data integration from multiple sources, including historical energy data, real-time sensor data, and external inputs such as weather reports and pricing information. This data integration capability ensures a unified and accurate forecasting process.
Automated Data Cleaning: Data accuracy is paramount in forecasting. PUFF's automated data cleaning feature eliminates inconsistencies and errors, ensuring that the forecasting models work with clean, high-quality data for more reliable predictions.
Multivariate Data Exploration: PUFF allows users to explore and analyze complex datasets, identifying relationships between various factors such as energy consumption, weather patterns, and market prices. This multivariate analysis aids in refining the accuracy of forecasts.
Automatic Weather Data Acquisition: Weather plays a crucial role in energy forecasting, particularly in load forecasting and generation forecasting. PUFF automatically gathers weather data, continuously updating the forecasting models to reflect the latest conditions, ensuring timely and accurate predictions.
Advanced Time Series Forecasting Algorithms: PUFF employs cutting-edge time series forecasting algorithms that are fine-tuned to handle the complexities of energy demand, generation, and pricing fluctuations. These algorithms ensure that the forecasts are robust and adaptive to changing conditions in the energy market.
Industrial Intelligence in Energy Forecasting
The energy sector is increasingly adopting industrial intelligence to drive efficiency and innovation. PUFF is built on industrial intelligence principles, providing utilities with a predictive edge. Whether it’s predicting future energy demand through load forecasting or estimating renewable energy generation based on weather conditions, PUFF delivers actionable insights that enhance operational efficiency.
PUFF also supports the growing need for sustainability by helping energy providers optimize resource allocation and minimize waste. By accurately predicting energy supply and demand, utilities can reduce their carbon footprint, cut operational costs, and improve energy efficiency.
Unlocking Operational Excellence with Celebal Technologies
PUFF is more than just a forecasting tool. It is a platform designed to streamline operations across the energy sector, providing key advantages that enable energy providers to meet their strategic goals.
Intuitive & Self-Explanatory UI: The user interface of PUFF is designed for ease of use. It enables users to navigate through the platform effortlessly, interpret data without any technical expertise, and access critical features with minimal training.
High Degree of Customization: PUFF offers highly customizable forecasting options, allowing users to tailor the models to their specific needs. Whether it’s adding unique variables or adjusting forecasting timeframes, the platform ensures that energy providers receive accurate predictions aligned with their operational objectives.
Easily Deployable System: PUFF’s architecture supports easy deployment, making it accessible to energy utilities globally. With minimal setup time and simple integration processes, the system quickly becomes an integral part of a utility’s forecasting workflow.
Effortless Forecasting: PUFF’s simple 8-tab setup allows users to name and update forecasting experiments quickly. This ensures that energy companies can run multiple experiments simultaneously, making forecasting a seamless process.
Centralized Access: The platform centralizes access to essential features such as tracking, error analysis, and configuration, all from a single selection page. This enhances operational efficiency by enabling users to manage all aspects of forecasting from one place.
Robust Security: Built on Azure, PUFF prioritizes data security and user protection. With advanced encryption and security protocols, energy providers can trust that their data remains secure, ensuring compliance with regulatory standards.
Streamline Decision-Making with Interactive Dashboards
To further enhance the forecasting experience, PUFF offers real-time interactive dashboards that empower users to monitor and analyze a wide array of metrics. These dashboards provide a comprehensive view of various parameters such as energy consumption, generation trends, and price fluctuations, enabling power management optimization. The dashboards are easy to interpret, helping users make informed decisions to improve efficiency, reduce costs, and ensure smooth operations.
The Role of PUFF in the Sustainability Sector
Sustainability has become a primary focus for energy companies, and accurate forecasting is key to driving greener operations. By providing detailed energy forecasting, PUFF helps utilities integrate renewable energy sources more effectively, predict peak demand periods, and optimize energy generation from renewable sources such as solar and wind. The ability to forecast generation based on real-time weather data ensures that renewable energy is maximized, contributing to a sustainable future.
Why Choose Celebal Technologies?
Celebal Technologies’ PUFF offers a unique blend of innovation and operational efficiency for energy providers. The platform has proven to deliver impressive results:
70% Enhanced Operational Efficiency: By providing accurate and timely forecasts, PUFF significantly boosts the operational efficiency of energy utilities.
3X Risk Mitigation: The platform helps reduce risks related to energy shortages, overproduction, and price fluctuations by delivering precise forecasts.
60% Improvement in Planned Maintenance: With reliable forecasts, utilities can schedule maintenance more effectively, reducing unplanned downtime and ensuring continuous operation.
Conclusion
In an industry where accurate predictions are critical, Celebal Technologies' Power & Utility Forecasting Framework (PUFF) stands out as a leading solution for utilities and energy providers. By leveraging power forecasting, utility forecasting, load forecasting, generation forecasting, and price forecasting, PUFF empowers the energy and sustainability sectors to optimize operations, reduce costs, and drive sustainability goals.
With seamless data integration, advanced forecasting algorithms, and robust security measures, PUFF is the future of energy forecasting. It delivers real-time insights that transform how utilities manage resources, navigate market challenges, and contribute to a sustainable future. To know more about the solution, get in touch with the experts at [email protected] or visit Celebal Technologies.
#Power forecasting#utility forecasting#industrial intelligence#energy forecasting#energy sector#load forecasting#sustainability sector#generation forecasting#price forecasting#Data Integration#weather forecasting#Celebal technologies#PUFF#Power & Utility Forecasting Framework
0 notes
Text

#Data Integration Market#Data Integration Market Share#Data Integration Market Size#Data Integration Market Research#Data Integration Industry#What is Data Integration?
0 notes
Text
How to Build an Effective B2B Contact Database
Article by Jonathan Bomser | CEO | AccountSend.com

In the world of B2B sales and marketing, having an effective contact database is critical. But building a database that is both accurate and comprehensive can be a challenging task. Here are some tips on how to build an effective B2B contact database.
Define Your Target Audience Before building a B2B contact database, it's important to define your target audience. This includes identifying the industries, companies, job titles, and other relevant factors that you want to target. Once you have a clear understanding of your target audience, you can start building your database with precision.
Use Multiple Data Sources There are many sources of data available for building a B2B contact database. These include online directories, social media platforms, trade publications, and more. To ensure the accuracy and completeness of your database, it's important to use multiple sources of data.
Leverage Technology There are many tools and technologies available to help with building and managing B2B contact databases. These include CRM systems, data enrichment services, and automation tools. By leveraging technology, you can save time and ensure the accuracy of your database.
Verify Data Accuracy One of the biggest challenges in building a B2B contact database is ensuring the accuracy of the data. This is especially important because inaccurate data can damage your reputation and waste your sales team's time. To verify data accuracy, you can use data enrichment services, manual research, and other methods.
youtube
Keep Your Database Up-to-Date Even the most accurate B2B contact database will become outdated over time. That's why it's important to continuously update and maintain your database. This includes regularly removing outdated contacts and adding new ones.
Segment Your Database Segmenting your B2B contact database can help you tailor your messaging and outreach efforts to specific audiences. You can segment your database based on factors such as industry, job title, location, and more.
In conclusion, building an effective B2B contact database requires a strategic approach, a variety of data sources, and the use of technology. By defining your target audience, leveraging multiple data sources, verifying data accuracy, keeping your database up-to-date, and segmenting your database, you can build a database that will drive your sales and marketing efforts forward.
#B2B#Decision makers#Lead generation#Sales outreach#Email marketing#Account-based marketing#Market segmentation#CRM integration#Small business marketing#sales leads database#contact leads database#Contact data accuracy#Niche industries#b2b lead generation database#Sales pipeline#Marketing strategy#Industry trends#Sales opportunities#B2B data providers#Youtube
3 notes
·
View notes
Text
The Retail Industry and IT Data Management: Maximizing Efficiency and Customer Experience
In today’s highly competitive retail environment, managing data effectively has become one of the key drivers for success. The shift from traditional to digital retail channels has led to an exponential growth of data, making it essential for businesses to have a robust strategy for managing and analyzing their information. Data management in retail is not just about organizing data; it’s about extracting valuable insights that can improve customer experiences, drive sales, and optimize operations. This article delves into the significance of retail data management, including the role of Master Data Management (MDM) in retail, and offers real-world examples of how proper data management can transform retail businesses.

Why is Data Management Important in Retail?
Effective data management in retail is about integrating, organizing, and analyzing data from multiple sources—such as customer interactions, sales transactions, supply chain operations, and inventory data. With retail businesses dealing with diverse touchpoints like physical stores, e-commerce platforms, and social media channels, the amount of data generated is vast and complex. Managing this data properly ensures businesses can extract actionable insights, forecast trends, optimize inventory, and personalize customer experiences.
In retail, the consequences of poor data management are costly. Disjointed or outdated information can result in stockouts, overstock situations, missed sales opportunities, and an inconsistent customer experience.
The Role of MDM in the Retail Industry
Master Data Management (MDM) plays a critical role in maintaining the accuracy and consistency of key data elements, such as product, customer, supplier, and inventory data, across the entire retail organization. MDM ensures that every system within the business—whether it's the inventory management platform, the e-commerce store, or the CRM system—accesses and uses the same, up-to-date information.
Real-World Example: Improving Inventory Accuracy with MDM
A large global retailer implemented MDM solutions to streamline its inventory management. The company was facing discrepancies between in-store stock, online availability, and actual warehouse inventory, leading to frequent stockouts and poor customer satisfaction. With a centralized MDM system, the retailer synchronized its product and inventory data across all channels, ensuring real-time accuracy.
This resulted in a 25% reduction in stockouts and a significant improvement in order fulfillment speed. Customers could rely on accurate product availability, whether they were shopping online or in-store, leading to better overall customer satisfaction and higher sales.
How Data Management Drives Customer Personalization
One of the key advantages of effective retail data management is its ability to provide deep insights into customer behavior. Retailers can use data from purchase history, online browsing patterns, and social media interactions to create personalized marketing campaigns that resonate with individual customers.
For example, a leading fashion retailer used data management systems to analyze customer purchase patterns. By integrating data from their e-commerce platform, mobile app, and loyalty program, they identified customers who frequently bought products during specific seasons. They then launched targeted marketing campaigns offering personalized discounts during these seasons. This hyper-personalization effort led to a 15% increase in conversion rates and a significant boost in customer loyalty.
Optimizing Supply Chain with Data Management in Retail
Efficient retail data management also extends to optimizing the supply chain. Retailers rely on accurate data to predict demand, track shipments, manage supplier relationships, and ensure that products are available when and where they are needed.
Real-World Example: Retail Giant Enhances Supply Chain Efficiency
A well-known retail giant implemented an advanced data management in retail solution to better manage its complex supply chain. By centralizing all supplier data and integrating it with real-time inventory tracking, the retailer gained full visibility into its supply chain operations.
This data management solution allowed the retailer to:
Reduce lead times by 20%.
Streamline communication with suppliers.
Optimize stock levels across different regions based on demand forecasts.
By leveraging real-time data from its supply chain, the retailer ensured better inventory alignment, fewer delays, and ultimately a more efficient operation.
Enhancing Omni-Channel Retailing with Data Integration
Today’s consumers expect seamless experiences whether they shop online, in-store, or on mobile apps. Retailers are increasingly adopting an omni-channel strategy, which requires smooth integration of data from various channels. MDM plays a critical role in this by synchronizing product, customer, and order data across all touchpoints, ensuring a consistent customer experience.
Real-World Example: A Seamless Omni-Channel Experience
A leading department store chain successfully implemented MDM in the retail industry to support its omni-channel strategy. Customers could browse products online, check their availability at nearby stores, and either reserve items for in-store pickup or opt for home delivery.
Thanks to the retailer’s MDM solution, customer orders were processed more efficiently, reducing order fulfillment times and eliminating the frustration of out-of-stock notifications after orders were placed. The result was a 20% increase in omni-channel sales and improved customer satisfaction.
Data-Driven Insights for Better Decision Making
When retailers implement proper data management systems, they are better equipped to make informed decisions. These systems provide detailed, real-time reports on sales trends, inventory levels, customer preferences, and more. By analyzing these insights, retailers can make strategic decisions that impact their bottom line.
Case Study: Retailer Uses Data to Predict Trends
A large supermarket chain used retail data management solutions to analyze historical sales data and predict seasonal trends. By identifying which products saw spikes in demand during certain times of the year, they were able to stock appropriately, negotiate better deals with suppliers, and time their marketing campaigns effectively.
This led to a 12% increase in seasonal sales, reduced excess inventory, and minimized the risk of overstocking.
Key Takeaways: The Future of Retail Data Management
As retail continues to evolve, the importance of efficient data management in retail cannot be overstated. Whether it’s improving customer experiences through personalization, optimizing supply chains, or enhancing omni-channel strategies, data management remains at the core of modern retail success.
Here are some key best practices for implementing effective data management:
Invest in MDM: A robust MDM system ensures data consistency across all platforms and departments, leading to more accurate insights and better decision-making.
Embrace Real-Time Data: Leverage real-time data synchronization for up-to-date inventory, product, and customer information, reducing errors and improving operational efficiency.
Prioritize Customer Data: Use customer data to offer personalized experiences, boost loyalty, and drive revenue.
The retail industry is poised to benefit significantly from advances in MDM solutions and data management technologies. Retailers that invest in modern data management practices will not only improve their operational efficiency but also create stronger connections with their customers, driving long-term growth and success.
Conclusion
The future of retail lies in effective data management. From improving inventory accuracy to delivering personalized customer experiences, retail data management powered by MDM solutions offers a pathway to operational excellence and increased profitability. Retailers who embrace data as a strategic asset will be well-positioned to thrive in an increasingly data-driven world.
#data management in retail#retail data management#Data Management#Customer Experience#MDM in the Retail Industry#Data Integration
0 notes
Text
Understanding Data Integrity In GXP Softwares - Pharma Connections
Explore the importance of data integrity in GxP software within the pharmaceutical industry in our latest blog by Pharma Connections. Understand how maintaining accurate and reliable data is crucial for compliance and quality assurance in pharmaceutical practices.
0 notes
Text
SCADA Integrators
The Essential Guide to SCADA Integrators: Enhancing Efficiency and Control
In today’s fast-paced industrial landscape, the role of SCADA (Supervisory Control and Data Acquisition) systems is more crucial than ever. These systems allow businesses to monitor, control, and optimize their operations in real time. However, the effectiveness of a SCADA system often hinges on the expertise of SCADA integrators. In this blog, we’ll delve into what SCADA integrators do, why they are important, and how they can help businesses unlock the full potential of their SCADA systems.
What Are SCADA Integrators?
SCADA integrators are specialists who design, implement, and manage SCADA systems tailored to a company’s specific needs. They play a critical role in ensuring that all components of a SCADA system work harmoniously together. This includes integrating hardware, software, and network elements to create a cohesive system that provides real-time monitoring and control.
Why SCADA Integrators Are Vital
Customization and Optimization: SCADA integrators bring a wealth of expertise in tailoring systems to fit unique operational requirements. They ensure that the SCADA system is not just a generic solution but a customized tool that enhances the specific processes of a business. This includes configuring dashboards, setting up alarms, and optimizing data collection methods.
Seamless Integration: Integrators are adept at bridging various components of a SCADA system. This means connecting sensors, PLCs (Programmable Logic Controllers), and other field devices with the central SCADA software. Their work ensures that data flows seamlessly from the field to the control room, facilitating accurate and timely decision-making.
Enhanced Security: Security is a major concern for SCADA systems, as they are often linked to critical infrastructure. SCADA integrators implement robust security measures to protect against cyber threats and ensure that sensitive data remains secure. This involves setting up firewalls, encryption protocols, and regular security audits.
Scalability: As businesses grow, their SCADA systems need to evolve. SCADA integrators help in scaling the system by adding new components, expanding data storage, and integrating with other enterprise systems. This scalability ensures that the SCADA system continues to meet the changing needs of the business.
Troubleshooting and Support: Even the most well-designed SCADA systems can encounter issues. SCADA integrators provide ongoing support and troubleshooting services to resolve any problems quickly. Their expertise minimizes downtime and ensures that operations continue smoothly.
Choosing the Right SCADA Integrator
When selecting a SCADA integrator, consider the following factors:
Experience and Expertise: Look for integrators with a proven track record and experience in your industry. Their familiarity with specific applications and standards can significantly impact the success of your SCADA system.
Customization Capabilities: Ensure that the integrator can tailor the system to your specific needs rather than offering a one-size-fits-all solution. Customization can lead to better efficiency and effectiveness.
Support Services: Assess the level of ongoing support and maintenance offered. A reliable SCADA integrator should provide comprehensive support to address any issues that arise post-implementation.
Security Measures: Verify that the integrator has a strong focus on security, implementing best practices to safeguard your system against potential threats.
Conclusion
SCADA integrators are indispensable partners in harnessing the full power of SCADA systems. Their expertise in customization, integration, security, scalability, and support ensures that businesses can achieve optimal performance and reliability from their SCADA solutions. By choosing the right SCADA integrator, companies can not only enhance their operational efficiency but also stay ahead in an increasingly competitive market.
If you’re considering upgrading or implementing a SCADA system, investing in a skilled SCADA integrator can make all the difference. With their help, you can unlock new levels of control, insight, and efficiency in your operations.
#SCADA Integrators#SCADA Systems#Industrial Automation#Control Systems#Data Acquisition#SCADA Integration#Industrial Control#System Optimization#SCADA Security#Automation Solutions#Industrial Efficiency#Custom SCADA Solutions#SCADA Support#PLC Integration#Real-Time Monitoring
0 notes
Text
XLRI Hosts ReEnvision 3.0: Digital Transformation Conclave
Experts discuss data-driven consumer strategies at XLRI’s Digital Transformation event The conclave explored India’s data-driven digital transformation across various consumer sectors, featuring insights from industry leaders. JAMSHEDPUR – XLRI’s PGDM (GM) Batch 2024-25 organized ReEnvision 3.0, a Digital Transformation Conclave centered on data-driven consumer world strategies. The event…
#AI in consumer engagement#शिक्षा#business technology integration#consumer analytics#data-driven strategies#Digital Transformation Conclave#e-commerce trends#education#industry experts panel#Marketing Innovation#ReEnvision 3.0#XLRI Jamshedpur
0 notes
Text
Data Integration Market Size Is Expected To Grow USD 35.34 Billion By 2032

The Global Data Integration Market size is expected to grow from USD 11.68 billion in 2023 to USD 35.34 billion by 2032, at a CAGR of 13.09% during the forecast period (2024-2032).
Data integration software combines data from several sources to provide users with a unified picture of the information. The need for diverse applications that can access, link, utilize and integrate several heterogeneous information repositories and sources has increased dramatically in recent years (including knowledge bases, databases, file systems, information retrievals systems, digital libraries, and electronic mail systems). In the search for an ultimate information integration system for data integration and integrity software, a variety of strategies have been proposed and accepted.
The global Data Integration market provides qualitative and quantitative information on growth rate, market segmentation, market size, future trends and regional prospects. The research study represents a modern perspective aimed at securing the future potential of the Data Integration market. This report analyzes and evaluates the latest prospects for the new retail space, as well as the general and future market performance of Covid-19. In addition, this report provides a detailed overview of competition between some industries and others.
Get Free Exclusive PDF Sample Copy of This Research @ https://introspectivemarketresearch.com/request/16130
Leading Key Players Covered in Data Integration market:
IBM(US), Microsoft (US),SAP(Germany),Oracle (US),SAS Institute (US),Talend (US),Informatica (US),Precisely (US),Software AG(Germany),Salesforce (US),Qlik (US),Tibco (US) and other major players.
These companies are devising key strategies such as acquisitions, merges, collaborations, partnerships, new product launches, regional expansions, and targeting untapped markets to gain competitive advantage over other players working in the market.
Introspective Market Research offers a comprehensive overview of the market through the analysis of key parameters such as revenue, price, competition, and promotions, as well as the study, synthesis, and summarization of data from different sources. It analyzes the leading industry drivers and shows numerous market components. The information offered is thorough, dependable, and the result of a comprehensive primary and secondary study. Introspective Market Research reports offer a comprehensive global market as well as an in-depth strategic sourcing methodology and analysis based on qualitative and quantitative research to anticipate market growth.
Segmentation of Data Integration market:
By Component
Tools (Solutions)
Services
By Deployment Model
On-Premises
On-Demand
By Enterprise Size
Large Enterprises
SMEs
By Industry
BFSI
Healthcare
IT & Telecom
Others
If You Have Any Query of Data Integration Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/16130
Geographic Segment Covered in the Report
(U.S., Canada, Mexico)
(Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
(Germany, U.K., France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
(China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
(Turkey, Saudi Arabia, Bahrain, Kuwait, Qatar, UAE, Israel, South Africa)
(Brazil, Argentina, Rest of SA)
What can be explored with the Data Integration Market Study?
Gain Market Understanding
Identify Growth Opportunities
Analyze and Measure the Global Data Integration Market by Identifying Investment across various Industry Verticals
Understand the Trends that will drive Future Changes in Data Integration
Understand the Competitive Scenarios
Track Right Markets
Identify the Right Verticals
Reasons to Purchase this Market Report:
Market forecast analysis through recent trends and SWOT analysis
Data Integration Market Dynamics Scenarios with Market Growth Opportunities over the Next Year
Market segmentation analysis, including qualitative and quantitative studies that include economic and non-economic impacts
Data Integration Market Regional and country-level analysis that integrates demand and supply forces that impact the growth of the market.
Competitive environment related to the Data Integration market share for key players, along with new projects and strategies that players have adopted over the past five years
Buy Now This Report:
https://introspectivemarketresearch.com/checkout/?user=1&_sid=16130
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assist our clients grow and have a successful impact on the market. Our team at IMR is ready to assist our clients flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, specialized in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyze extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Canada Office
Introspective Market Research Private Limited, 138 Downes Street Unit 6203- M5E 0E4, Toronto, Canada.
APAC Office
Introspective Market Research Private Limited, Office No. 401-403, Saudamini Commercial Complex, Chandani Chowk, Kothrud, Pune India 411038
Ph no: +1-773-382-1049
Email: [email protected]
LinkedIn| Twitter| Facebook
#Data Integration Market#Data Integration Market Size#Data Integration Market Share#Data Integration Market Growth#Data Integration Market Trend#Data Integration Market segment#Data Integration Market Opportunity#Data Integration Market Analysis 2024#US Data Integration Market#Data Integration Market Forecast#Data Integration Industry#Data Integration Industry Size
0 notes
Text
How IT Security Services Improve Mobile Device Security
In today's digital age, mobile devices have become integral to our lives, serving as tools for communication, business transactions, entertainment, and more. As the use of mobile devices continues to grow, so do the risks associated with their security. Cyber threats such as malware, phishing, and data breaches are increasingly targeting mobile devices, making it imperative for individuals and organizations to invest in robust IT security services. This blog explores how IT security services improve mobile device security, highlighting the key strategies, technologies, and best practices involved.

The Growing Importance of Mobile Devices
Mobile devices, including smartphones, tablets, and wearables, have revolutionized our lives and work. They provide unprecedented convenience, allowing users to access information, communicate, and perform tasks on the go. However, this convenience comes with significant security challenges. Mobile devices often store sensitive data, such as personal information, financial details, and corporate data, making them attractive targets for cybercriminals.
The Threat Landscape
The threat landscape for mobile devices is constantly evolving. Common threats include:
Malware: Malicious software designed to damage or disrupt devices, steal information, or gain unauthorized access.
Phishing: Deceptive attempts to obtain sensitive information by masquerading as trustworthy entities.
Data Breaches: Unauthorized access to sensitive data, often resulting in data theft or exposure.
Man-in-the-Middle Attacks: Interception of communication between two parties to steal data or inject malicious content.
Device Theft or Loss: Physical loss or theft of devices, leading to potential data breaches.
Given these threats, it is crucial to implement comprehensive IT security services to protect mobile devices.
Key Components of Mobile Device Security
1) Mobile Device Management (MDM)
Mobile Device Management (MDM) is critical to mobile device security. MDM solutions enable organizations to manage and secure mobile devices, regardless of location. Key features of MDM include:
Device Enrollment: Automating the process of enrolling devices into the management system.
Policy Enforcement: Defining and enforcing security policies, such as password requirements and encryption.
Remote Wipe: Remotely erasing data on lost or stolen devices to prevent unauthorized access.
Application Management: Controlling the installation and use of applications on devices.
Compliance Monitoring: Ensuring devices comply with security policies and regulatory requirements.
2) Mobile Application Management (MAM)
Mobile Application Management (MAM) focuses on securing and managing applications on mobile devices. MAM solutions provide the following capabilities:
App Wrapping: Adding security layers to applications without modifying their functionality.
Containerization: Isolating corporate data and applications from personal data on the device.
App Distribution: Securely distributing applications to users through enterprise app stores.
Access Control: Managing user access to applications based on roles and policies.
App Analytics: Monitoring application usage and detecting potential security risks.
3) Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) solutions provide real-time monitoring and analysis of endpoint activities, including mobile devices. EDR solutions offer:
Threat Detection: Identifying and responding to security threats in real time.
Behavioural Analysis: Analyzing device behaviour to detect anomalies and potential threats.
Incident Response: Automating incident response actions, such as isolating compromised devices.
Threat Intelligence: Integrating intelligence feeds to stay updated on the latest threats.
Forensics: Conducting forensic analysis to understand the scope and impact of security incidents.
4) Mobile Threat Defense (MTD)
Mobile Threat Defense (MTD) solutions are designed to protect mobile devices from various threats. MTD solutions provide:
Malware Detection: Identifying and blocking malware on devices.
Phishing Protection: Detecting and preventing phishing attacks.
Network Security: Securing device communication over Wi-Fi, cellular, and VPN connections.
Vulnerability Management: Identifying and addressing vulnerabilities in the device and applications.
Compliance Enforcement: Ensuring devices comply with security policies and industry regulations.
5) Encryption and Data Protection
Encryption is a fundamental aspect of mobile device security. It ensures that data stored on devices and transmitted over networks is protected from unauthorized access. Key encryption practices include:
Device Encryption: Encrypting data stored on the device to protect it in case of theft or loss.
App Encryption: Encrypting data within applications to ensure data privacy and integrity.
Communication Encryption: Using encryption protocols such as SSL/TLS to secure data in transit.
Cloud Encryption: Encrypting data stored in cloud services to protect it from unauthorized access.
6) Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) enhances mobile device security by requiring multiple verification forms for user authentication. MFA can include:
Something You Know: Passwords or PINs.
Something You Have: One-time passwords (OTPs) sent to a mobile device or generated by an authenticator app.
Something You Are: Biometric factors such as fingerprints or facial recognition.
MFA adds an extra layer of security, making it more difficult for unauthorized users to access devices and data.
Benefits of IT Security Services for Mobile Devices
1) Enhanced Security
IT security services provide comprehensive protection against various threats, ensuring mobile devices are secure from malware, phishing, data breaches, and other attacks. By implementing robust security measures, organizations can safeguard sensitive data and maintain the integrity of their mobile infrastructure.
2) Improved Compliance
Regulatory compliance is a critical consideration for many organizations. IT security services help ensure mobile devices comply with industry regulations and standards, such as GDPR, HIPAA, and PCI-DSS. This reduces the risk of non-compliance penalties and enhances the organization's reputation.
3) Increased Productivity
Security incidents can disrupt business operations and reduce productivity. IT security services minimize the risk of such disruptions by providing proactive threat detection and response. This allows employees to work efficiently without interruptions, ultimately improving overall productivity.
4) Reduced Risk of Data Breaches
Data breaches can have severe consequences, including financial losses, legal liabilities, and reputational damage. IT security services help prevent data breaches by implementing robust security measures like encryption, MFA, and real-time threat detection. These measures reduce the risk of unauthorized access to sensitive data.
5) Streamlined Management
Managing mobile device security can be complex and time-consuming. IT security services streamline this process by providing centralized management and automation. This simplifies the administration of security policies, device configurations, and compliance monitoring, allowing IT teams to focus on strategic initiatives.
6) Enhanced User Experience
Security measures should not compromise the user experience. IT security services balance security and usability, ensuring users can access the resources they need without friction. This enhances user satisfaction and encourages the adoption of security best practices.
Implementing IT Security Services for Mobile Devices
1) Assessing Security Needs
The first step in implementing IT security services for mobile devices is to assess the organization's security needs. This involves identifying the types of data stored on mobile devices, the potential threats, and the regulatory requirements. A thorough assessment helps determine the appropriate security measures and technologies to implement.
2) Selecting the Right Solutions
Numerous IT security solutions are available, each with its strengths and capabilities. Organizations should carefully evaluate different solutions based on their needs and choose the best protection. Considerations include:
Integration: Compatibility with existing IT infrastructure and applications.
Scalability: Ability to scale with the organization's growth and changing needs.
Ease of Use: User-friendly interfaces and straightforward deployment.
Support: Technical support and regular updates are available.
3) Developing Security Policies
Security policies are essential for defining the rules and guidelines for mobile device usage. Policies should cover aspects such as:
Device Enrollment: Procedures for enrolling devices into the management system.
Password Requirements: Guidelines for creating and managing strong passwords.
App Usage: Rules for installing and using applications on devices.
Data Protection: Measures for protecting sensitive data, including encryption and backup.
Incident Response: Procedures for responding to security incidents and breaches.
4) Training and Awareness
Security is only as strong as its weakest link, which is often the end-user. Organizations should invest in training and awareness programs to educate employees about best practices for mobile device security. Topics to cover include:
Recognizing Phishing Attempts: Identifying and avoiding phishing emails and messages.
Safe App Usage: Downloading and using applications from trusted sources.
Password Management: Creating and managing strong, unique passwords.
Incident Reporting: Reporting lost or stolen devices and suspicious activities.
5) Continuous Monitoring and Improvement
Mobile device security is an ongoing process that requires continuous monitoring and improvement. Organizations should regularly review their security measures, conduct vulnerability assessments, and update their security policies to address emerging threats. Continuous monitoring and improvement help maintain a robust security posture.
6) Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are increasingly important in mobile device security. AI and ML can analyze vast amounts of data to identify patterns, detect anomalies, and predict potential threats. Future trends in AI and ML for mobile device security include:
Advanced Threat Detection: Using AI and ML to identify sophisticated threats and zero-day vulnerabilities.
Behavioral Analytics: Analyzing user behaviour to detect unusual activities and potential security risks.
Automated Response: Automating incident response actions based on AI and ML analysis.
7) Zero Trust Security
Zero Trust Security is a security model that assumes no trust for any device, user, or network, regardless of their location. Zero Trust Security principles include:
Continuous Verification: Continuously verifying the identity and trustworthiness of devices and users.
Least Privilege: Granting the minimum necessary access to resources based on roles and responsibilities.
Micro-Segmentation: Dividing the network into smaller segments to contain potential breaches.
Zero Trust Security is becoming increasingly relevant for mobile device security, especially in remote work environments.
8) 5G Technology
The rollout of 5G technology is set to transform mobile device security. 5G offers faster speeds, lower latency, and increased connectivity but introduces new security challenges. Future trends in 5G and mobile device security include:
Network Slicing Security: Securing different slices of the 5G network to prevent unauthorized access.
IoT Security: Protecting the growing number of IoT devices connected through 5G networks.
Edge Computing Security: Ensuring the security of data processed and stored at the network edge.
9) Biometric Authentication
Biometric authentication methods like facial recognition and fingerprint scanning are becoming more prevalent in mobile device security. Future trends in biometric authentication include:
Multi-Modal Biometrics: Combining multiple biometric factors for enhanced security.
Behavioural Biometrics: Analyzing behavioural patterns, such as typing speed and touch gestures, for continuous authentication.
Privacy-Preserving Biometrics: Implementing privacy-enhancing technologies to protect biometric data.
10) Regulatory Compliance
Regulatory compliance will continue to be a significant factor in mobile device security. Future trends in regulatory compliance include:
Global Data Protection Regulations: Adapting to evolving data protection regulations like GDPR and CCPA.
Industry-Specific Standards: Complying with industry-specific security standards, such as HIPAA for healthcare and PCI-DSS for finance.
Cross-Border Data Transfers: Ensuring compliance with regulations governing cross-border data transfers.
Mobile device security is a critical aspect of modern IT security. As mobile devices become more integral to our personal and professional lives, robust security measures are paramount. IT security services play a vital role in protecting mobile devices from a wide range of threats, ensuring compliance with regulations, and enhancing user productivity.
By implementing Mobile Device Management (MDM), Mobile Application Management (MAM), Endpoint Detection and Response (EDR), Mobile Threat Defense (MTD), encryption, Multi-Factor Authentication (MFA), and other security measures, organizations can safeguard their mobile devices and sensitive data. Continuous monitoring, training, and awareness programs further strengthen the security posture.
Future trends in mobile device security, such as AI and ML, Zero Trust Security, 5G technology, biometric authentication, and regulatory compliance, will shape the landscape. By staying informed about these trends and adopting proactive security strategies, organizations can navigate the evolving threat landscape and ensure the security of their mobile devices in the digital age.
#mobile device security#cyber security#data security#mobile Security#mobile Security services#information technology#global health news#technology news#technology industry#technology integration
0 notes