#CyberPedia
Explore tagged Tumblr posts
Text

Gee, I wonder why they're advertising that here...
Link to the wiki, btw
#don't “what were you doing at the devil's sacrament” me#you know exactly what i was doing at the devil's sacrament#deltarune#undertale#furry#e621#undertail#deltaruined#cyberpedia
6 notes
·
View notes
Text
Cyberpedia - a non-Fandom wiki for Undertale and Deltarune - a call for editors
https://cyberpedia.miraheze.org/wiki/Main_Page
It is becoming increasingly clear that Fandom is no longer a suitable place to host wikis - the Undertale Yellow wiki has already abandoned it, along with plenty of high-profile non-Toby Fox-related wikis. In addition the existing Fandom wiki is not of the best quality. Because of this, I have decided to create a new wiki for both Undertale and Deltarune, hosted on Miraheze. I originally posted about this wiki about a year ago - this is a reminder of its existence.
The wiki has now had the pages from the Undertale and Deltarune wiki imported into it. It now needs your help to clean up and improve these articles. I do not have the time needed to do this, so I am asking for help. This wiki cannot function without your support in editing it. In addition, any help spreading the news about this wiki would be greatly appreciated.
In making this new wiki, I have elected to institute a few policies. The policies are not complete and nothing is set in stone - as with any wiki, these policies can be changed if there is consensus. In particular I would like to draw attention to the policy banning speculation and requiring sources for information found outside the games - I feel these are necessary policies.
I should also mention the policy on gender in the rules. I know this is likely to be controversial, but I am open to changing it if there is a clear consensus among editors to do so. I just feel that the no-speculation policy should apply to gender as well.
I should note that the backend of the site is basically just me throwing together something that seems to work if you squint at it - if there is anyone here who knows more about how MediaWiki/css works, your help would be greatly appreciated.
If you have any questions or concerns, please let me know. I hope to be able to find support in building a new and better wiki.
1 note
·
View note
Text
This morning when I was reading on AO3 and went to read the next chapter I realized AO3 was down. As hours passed I researched why, I found that AO3 is being attacked by anonymous Sudan with a DDOS. Anonymous Sudan is attacking AO3 because it is registered under the United States of America and it has smut, LGBTQ+ and NSFW. All in all we miss my AO3 and we know who to blame.


Here are some sites about anonymous Sudan:
https://flashpoint.io/blog/anonymous-sudan-ddos-timeline/
https://www.radware.com/cyberpedia/ddos-attacks/anonymous-sudan/
https://cybernews.com/editorial/anonymous-sudan-explained/
26 notes
·
View notes
Text
Expert Tips to Fight Online Privacy Threats - Bitdefender Cyberpedia
I found this to be a fascinating look at our date and privacy and how little recourse we have should it end up in the wrong hands.
youtube
0 notes
Text
Twitch.tv/activate: Learn How to Activate the Twitch TV and Connect Your Device

If you're a fan of video games, chances are you've heard of Twitch.tv. Twitch is a live streaming platform that lets people watch gamers play video games. It's a great way to connect with other gamers and chat with them while you're watching. But what if you want to watch Twitch on your TV? Here's how to make the most of your Twitch.tv experience on your TV.
Now share your experience with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog:https://bit.ly/3hU7zdr
2 notes
·
View notes
Text
How to pronounce "Ralsei"
... according to Susie, you pronounce his name as "ralsay"!

To see this, be sure to re-read Ralsei's editable CYBERPEDIA entry!
#ralsay#ralsee#deltarune#deltarune spoilers#deltarune plot#kinda#Mod Ellipsis#I'd like to believe Susie spelled his name#as she says it#so it's not ral-see#it's ral-say
356 notes
·
View notes
Text
mermaid au cp.2
Perceptor watches his predator do apexing while the benny hill theme plays in the background
this chapter can also be read on ao3
I have no beta so this is just pure thought beamed straight from my brain to yours. I don't even know what is happening. the mermaid au spirit is possessing me for the time being.
Stripmine had meant well when he had come to Perceptor’s aid and when he started bombing him with rapidfire questions, but the way he had practically vibrated at having something actually happen under his watch was borderline tiring to deal with. Fortunately with some gentle guiding questions the minibot had refocused on what actually mattered, and they had discussed the next steps as they had walked back inside the building.
Perceptor told him that he had just intended to get a closer look because he hadn’t been sure what he had even been looking at, and that he hadn’t meant to put himself in danger by allowing their intruder that close to him. Not that he had felt like he had been in any danger at all, but to Stripmine an intruder was an intruder, and every person in the research center was under his protection during his shift.
But now they knew what they were dealing with, an actual live mermaid, and first things first they needed to make sure that there weren't others with him and that whichever way the mermaid had gotten in wasn’t still open somewhere. Stripmine had ran off while rambling about intending to get to the root of this, and Perceptor had finally been able to pause and just let all of this sink in.
He looked at the datapad he was still carrying, thinking of how amazed the mermaid had looked at it. And he thought of the mermaid, who was now hiding somewhere in their precious project pool. What a strange turn his morning had taken.
Stripmine was probably going to make sure that the maintenance department went to investigate the pool, so that left him the responsibility of attempting to salvage their project.
Scrolling through his saved contacts Perceptor picked out Diver, the official supervisor of their project and the current head of the whole research center, and sent him a short message detailing their situation in the pools. Usually Diver was too busy to mingle a lot with the members of their project and only attended bigger meetings, but this seemed like important enough news to bother him with directly. And while Perceptor was still wondering who else he should contact he was already receiving a response from Diver telling him to keep this on the downlow for now until they figured out the full scope of things, and that he would be coming by the project wing as soon as he could.
Taking that as a sign to stand by and wait until otherwise instructed, Perceptor dropped the plans to contact others and instead walked the rest of the way to the rooms that were fully in use for their genome project. A project that had just yesterday been interesting enough to occupy his mind day and night, but which now seemed almost dull in comparison to his new thoughts of golden optics and a smoothly swimming form.
When he got into the laboratory, where he had used to be sitting for long hours over a laptop and a pile of datapads, he wasn’t even sure what he was supposed to do there now. Just trying to go back to work normally was out of the question surely. He wasn’t even sure if there was work to do anymore after they managed to find out how much destruction the mermaid had caused. But still he had to kill the time somehow while he waited for Diver to call the shots, which would probably lead to a meeting of some sort eventually today.
Deciding that he might as well indulge on his curiosities in the meanwhile, Perceptor picked out one of the laptops from a rack and then made himself comfortable on the corner of a table, pulling out a stool to sit on. The datapad had finally been subspaced away in favor of having both his hands to type with as he navigated his way to the Cyberpedia and searched for mermaids, intending to just quickly browse over the general information they had about these elusive creatures.
Of course he knew that mermaids existed, and that they were thought to be rather high on the food chain of the oceans since they seemed to be rather cunning predators. He could make educated guesses on many aspects of their existence by osmosis from his general knowledge of marine biology from the evolutionary standpoint, but he had never actually sat down and read about mermaids specifically. This seemed like the perfect time to educate himself, and he eyed through the article that confirmed what he had thought to be true. There just wasn’t much they knew about mermaids at all.
An aquatic form of advanced mechanimal that hunted smaller mechanical creatures. They were known to be smart enough to make for effective hunters and to be able to avoid Cybertronians and their traps, and there had even been people that insisted they had seen them use tools. Which would make a lot of sense considering how advanced their forelimbs were; they looked practically identical to Cybertronian servos.
The few rare that had managed to get close enough to a mermaid reported limited verbal capabilities, mostly parroting back words and short sentences. They were thought to be on the upper end of intelligence when it came to Cybertronian mechanimals, but still far below the cognitive capabilities of actual Cybertronians. But what he had seen today had not been simple mimicking. The mermaid had clearly communicated with him in Neocybex and shown the capabilities to both understand what it had been shown and explained, and ask questions to further expand its understanding.
Of course there was an endless list of possibilities and questions those thoughts brought on, but it was impossible to say if the mermaid in their pool was an average member of its species, or an exceptionally smart one. Or if it had been a mermaid at all.
Deciding that the wiki article wouldn’t offer him much more, Perceptor instead opened the appropriate director to search for any research publications that related somehow to mermaids. But he wasn’t surprised to see that there was only a handful of them and even most of those seemed to be published by the same team. He opened a few of the interesting ones into tabs anyways, because maybe he could pick out the best ones and browse over them later. You never knew what kind of extra information would come handy when dealing with this situation and it wouldn’t take him long at all to read through all of this. Well prepared was half done after all, as he liked to think.
Eventually he was interrupted by an incoming call, and for a moment Perceptor thought that maybe Diver finally had something to report. But the comm number wasn’t Diver’s. And after a bit of searching his memory for the name he realized that it was the mech who had helped him with a tech problem when he had moved in.
/’ Perceptor? Heard you were the one who met our new guest before and thought you might be interested in seeing this. ’/
Chromedome worked in maintenance and tech support. A tall orange and yellow colored mech who didn’t seem to be taking his work too seriously, by what Perceptor had seen during their one meeting at least, but he had been helpful before and certainly had his interests now.
/’ I did. Did something happen? ’/ Perceptor asked, surprised to realize that he was feeling concerned for the mermaid, automatically assuming that something bad had transpired while he wasn’t looking.
/’ Oh, no. Nothing like that. I was just woken up by Stripmine and went to check the tank integrity. I couldn’t find anything wrong with the tank or the filters so we decided to check the security tapes instead, and uh… Well, as I said. You might want to see this. ’/
The offer was rather cryptic, but Perceptor thought that he better go and check it out anyways.
/’ I’ll be right there. ’/
Chromedome asked him if he knew where the security office was, and after getting the directions Perceptor sent the open tabs to his datapad before he closed the laptop and headed out.
It was a ten minute walk when he wasn’t dragging his pedes, and it wasn’t even the first time he had been hurrying somewhere today. There were a few more people up already, and he tried to not look like he was this close to running in the hallways as he passed them with hurried nods and greetings.
Stripmine was waiting for him by the doorway of the security room, holding it open for him by clinging to the edge of it and ushering him inside when he got close enough. Perceptor stepped inside, nodding at Chromedome who was sitting in the chair in front of the monitors, and receiving a nod of acknowledgement in return.
“Sorry, we don’t have seats to offer but make yourself comfortable,” Chromedome apologized and then reached for the controls, motioning at the main monitor that was situated on the table itself. The three of them huddled around the monitor, Perceptor standing right behind Stripmine who had to practically stand on his toes to be able to see.
“So what are we looking at exactly?” Perceptor asked, optics scanning the video feed that was wound back to last night, if the date and time were to be believed. Chromedome stopped the rewind and then more gently poked the feed forwards again by around twenty minutes before the time stamp said 3:45am.
“Keep your optics here,” he simply said, tapping over a brambling living metal bush that was meant more to block vision from outside the wire fence than for its pretty looks. The feed was dark, and Perceptor squinted his optics as he tried to see anything, but after a moment the bush seemed to shake and from below it poked out a white helmet with wide optics.
The three of them were watching the video in shocked silence, more so Perceptor than the other two who had already assumedly seen this once, as the mermaid squirmed and forced its frame through the bush (and probably the wired fence behind it as well). How it managed to fit through from there seemed to defy logic, but first you could see both of its arms, dragging its chassis through, and then one long fin popping into view at a time, before the rest of its frame seemed to slither through with much more ease.
“How did it get through the fence?” Perceptor muttered in question, one hand covering his mouth in thought while the other was hugging over the glass of his chest. Chromedome leaned back in the chair and shrugged his shoulders.
“I didn’t yet go check, but I’m sure there’s one mermaid sized hole there behind the bushes.”
Well that much was clear, but how had it made that hole? Or had it already been there and the mermaid had just discovered it?
“That fence is made out of N grade cybersteel. You would have a hard time cutting it even with hand tools,” Stripmine muttered knowledgeably, and that was another thing Perceptor wondered. It couldn’t have just chewed its way through a wire fence.
On the video, once the mermaid was all through it was propping its chassis up with its arms as it looked around curiously, its long tail curling up behind its form. It was hard to see details from the security feed but the tail seemed to be a lighter color compared to the chassis, and its waist was framed by some sort of skirt platings that emphasized the curve of its hips. But it looked oddly slim.
After surveying its surroundings, the mermaid was then moving forwards with determination, its movements looking slow and clumsy when it had to practically drag its weight over the ground with nothing but its arm strength and slithering movements. And when it finally made it to the edge of the pool where Perceptor had found it, it was starting to look like the reason it had picked this pool was simply because it was closest in proximity to the mermaid’s entrance.
The mermaid was leaning over the edge, its helm bobbing up and down as it tried to see if there was anything worthy in the pool, probably spying for the fish. And it seemed to have seen something it liked because a moment later it was smoothly diving into the water below, shedding all of its awkward clumsiness the moment it was back in its element.
“It’s harder to see it in the water in the dark, but after the sun is rising you can spot it at times,” Chromedome said, straightening up again just enough to be able to reach the controls. He changed to another camera’s feed that was positioned to film the pool itself, and started to skip over footage to reach the sunrise.
“It obviously came in to hunt. Those fish are probably easy prey to a predator like that,” Perceptor mused aloud, his optics still fixated on the monitor even when you couldn’t really see anything from the fast forwarded feed.
“Uhh, yeah. Well, you’ll see,” Chromedome replied rather cryptically again and Perceptor glanced at him in question. But once the pool in the video feed was illuminated by sunlight he was looking closely again, the video continuing at normal speed.
You could spot the mermaid when it was closer to the surface, but if it went too deep you could only spot the shadow or nothing at all. The tank was deep enough for the sun to not reach the bottom of it, with enough impurities in the water to hide whatever was happening in the deeps. But fortunately the mermaid decided to occasionally try and go for the fish that were trying to snack on the water’s surface.
The mermaid was circling the school of fish from a distance, probably trying to keep them together while picking out the weakest individual. And judging from the smooth way it was able to swim in the water it shouldn’t have been a challenge to capture one of the poor creatures. But when it came time to lunge for the kill the mermaid seemed to be hesitating. It was attempting to lunge forwards, but always stopped, as if it wasn’t quite sure when to go in. And after going back and forth a few times the fish eventually spotted the predator and decided to smartly scatter, making the mermaid finally try and make a final lunge for the closest fish. But just when it would have sank its claws into it it was hesitating again and recoiling away.
“That’s…” Perceptor started, trying to put his thoughts into words but failing miserably. Fortunately Chromedome was ready to fill in for him, his tone something between amusement and pity.
“The saddest attempt at catching a fish I have ever seen.”
“Well, I would not have used those words exactly but…” he couldn’t quite disagree either. Mermaids were supposed to be one of the most efficient killers that deep waters had seen. He had witnessed the claws and fangs and the strong coiled frame personally just few hours ago. Even the mermaid himself had been bragging about its hunting skills! It was supposed to be a predator but it almost looked to be…well, afraid of the harmless fish…
“That’s not even all. Check this out,” Chromedome said, sounding almost sorry for what he was about to show, but not too sorry to not sit up straighter so he could find the spot in the video faster.
He stopped at just after 6am, not that long before Perceptor would be walking down there himself. The mermaid was swimming back to the spot where it had dived in, leaning its palms against the wall again as its helm tilted upwards, seemingly considering the high edge. Perceptor hadn’t thought about it at the time, not even when he had had to lower the datapad for the mermaid to be able to see it without having to crane its neck, but there was no way for the mermaid to reach the edge and be able to pull itself out the same way it had gone in.
“It’s stuck,” Perceptor stated the obvious out loud.
“Very,” Chromedome added, and Perceptor was sure that behind his facemask was an amused smile even when he couldn’t see it.
“Couldn’t it decide to get stuck somewhere else?” Stripmine asked, apparently not happy to have a troublemaker in his hands after all.
Perceptor was still staring at the monitor, watching the mermaid consider the edge, scratching the vertical metal surface with its claws before it seemed to give up and just continue swimming along the wall. As if it could find a spot that would be easier to scale.
“So it’s alone and struggling. I think we might need someone with more knowledge to take a look to see if it’s because it's hurt,” Perceptor said, more to himself than to the other two. He considered their options for a moment while Chromedome was pausing the video and turning it off. There was no mermaid to be seen in the live footage of the pool, and maybe it was still hiding from being scared by Stripmine.
“There’s no way to track it under water?” Perceptor then asked, looking at Chromedome who tilted his helmet as he gave it thought.
“Not with the security cameras, no,” he hummed, and while Perceptor hadn’t thought that to be possible in the first place he still felt a bit disappointed. “But we have those heat vision cameras in the B-wing. They were using them on that dive a few weeks ago. I helped them prepare them. We could try to borrow one and see if we can find your fish?”
Perceptor felt slightly flustered at the comment, but thought that it was just an unfortunate choice of words. It made it almost sound like they were doing this for him and not the poor mermaid. He considered the other idea for a beat before he nodded in confirmation. The mermaid’s body heat might be just enough to show up on the camera, at least surely the machinery around its spark casing should be warm enough to be tracked.
“Thank you, if you could ask them for it that would be a great help. I informed Diver about the mermaid before but that was before we knew that it was having trouble hunting. Is there any way that we could get a record of that footage to show him?”
Chromedome’s EM field rippled with clear amusement despite his facade being so permanently passive, and it was clear how funny he thought that video would be. But Stripmine reached to his tiptoes once more to pipe up before the other could say anything and before Perceptor could feel truly annoyed.
“I can do that! Leave it to me, I’ll get the videos mailed to you in no time.”
“I can have those cameras set up today. The team shouldn’t have any use for them on land anyways,” Chromedome said and whirled around in his chair and got up so he could let Stripmine have his chair back.
“Alright, I’ll leave you two to it then.”
Perceptor exited the security room with Chromedome, but they split ways as they headed to opposite ends of the building. This day was only getting weirder and weirder, and he felt like he shouldn’t have even been shown this footage. He was just one scientist that had been called to help with a gene project. Sure that was the precise project that the mermaid had gotten tangled in, but he wasn’t even in charge of caring for the tank. He literally just spent his time in the lab looking through samples.
But now as he thought of that curious creature possibly being hurt, he could feel worry simmer in his spark.
#maccadam#simpatico#perceptor#brainstorm#tag for my writings#sft tag#mermaid au#do you know that feel when you think you're much better at writing brainstorm#and still end up writing everything from percy's pov?#clown wig is on
15 notes
·
View notes
Text
When Ralsei made that new addition to the Cyberpedia at Cyberworld, I remember thinking that, what he meant by “the bonds that you break may make you stronger” (or something like that, I don’t remember exactly) was that there are people you are going to have to let go of, or that you can do that if you want and that would be like a sign of strength?
Like, by example, I thought that maybe there will be a character that’s a genuinely bad person and it’s bad for you, to Kris and for the party... and that it’s going to be ok to leave that kind of person behind... ? at least, that’s the impression I got by reading that.
I mean sure, in reality (at least by Chapter 2) it means that characters can get stronger by fighting in this game as well (as in the Weird Route is evident), but applied to a more pacifistic sense, I wonder if it will ever take that side.. like will there be a character that we can leave behind without it being a bitter ending or sad? and instead could be seeing as a positive thing as well? just wondering.
90 notes
·
View notes
Text
Personal Deltarune thought: Ralsei isn't sus, he is just very awkward.
I don't think he holds back on information or hides secrets because of any malicious intent, at least. (Not the stuff about the classroom objects, nor the stuff about the prophecy, nope)
.
- He's just one of those people that know too much and just automatically assume that everyone else knows most of the things they do. (Such as stuff about the Roaring) (And to be fair, us players usually know how most games work)
- He's probably also very passionate about the things he knows (Such as his "nice prophecy", his tutorial, and that one time when Ralsei updates the Cyberpedia)
- and cannot stop talking about it once he starts, (Even after he diverts the Player's attention for a few good minutes, when we come back Ralsei has to catch himself from talking any more to Kris instead of trying not to act sus. Twice.)
- which is why he often holds back on information- out of fear that his oversharing might annoy people. (Such as Susie, or even some of us players who despise Navi)
- He does make efforts to cope with finding a middle ground(between oversharing and not sharing) though, which is why he gives us a tutorial choice and prepares the manual instead of actually speaking much about tutorial stuff- so that us players could choose what we need to learn from him.
- He is indeed self-aware on how awkward he is. Like he said, he doesn't even know what being "Ralsei-like" even is.
...
In short: Ralsei is so frickin awkward that a large part of the fandom mistakes him to be a villain.
Whatever his "secret plan" is, it probably won't be as bad as it looks.
88 notes
·
View notes
Text
took me too long to realize that the significance of the last line of ralsei's cyberpedia entry about losing recruits, "but the bonds you break may make you stronger," is that that is literally what happens in snowgrave. the route starts with you and noelle backtracking and going and killing all the enemies you could previously have recruited, thereby "losing" them, and getting stronger as a result.
30 notes
·
View notes
Text
I like that I now know exactly, or should I say most likely, what was going through Susie’s head at the end of Deltarune Ch1 when Ralsei removed his hat. At first I thought that she was shocked at how much he looks like Asriel and thought nothing more about it until Ch2. Because like! Asriel is made out to be the ✨Golden Boy✨ of the town! Who doesn’t Know Asriel?
Susie Apparently! In Ch2 we find out through looking at Asriel’s door in Queen’s Mansion that Susie didn’t even know Asriel existed! She later comments about how much Ralsei looks like Toriel. This means she wasn’t shocked at how much Ralsei looks like Asriel.
So Basically it was this

Also given how she has only heard Ralsei’s name spoken aloud and spells it as “Ralsay” in the Cyberpedia Entry means that even if she knew about Asriel she wouldn’t be able to put the anagram together between the two names. So it makes a lot of sense to me as to why Susie never brought up Ralsei’s similarities to Asriel. There was no way she’d be able to compare the two with the limited information she had! Almost as if she was being kept blind to it.
9 notes
·
View notes
Text
Thinking about what Ralsei writes in the Cyberpedia talking about how defeating enemies will make them LOST (in all caps) but breaking those bonds may make you "stronger"... and how Noelle's teaser theme was called "Lost Girl"... and how a theme of the Snowgrave route is about making Noelle "stronger" by defeating enemies...
#I feel like theres more that I'm missing and it may connect back to some Gaster stuff in Undertale#deltarune#deltarune spoilers#noelle holiday#Ralsei
11 notes
·
View notes
Text
Skyroot Aerospace First Flight set to launch with 3 Payloads by next week

India's first privately developed rocket, the Vikram-S from Hyderabad-based Skyroot Aerospace company, is scheduled to launch for the first time between November 12 and 16 from Sriharikota, the only spaceport in the country.
Now share your Thoughts with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog: https://bit.ly/3DQ3aPQ
1 note
·
View note
Photo
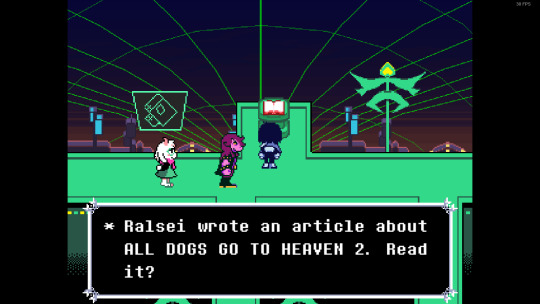
[I.D.s 1, 2, 3: The Lancer Fun Squad checking the free editable Cyberpedia in Cyber World, which is a book on a podium against the dark sky.
Ralsei sweetly says, "Oh, Kris! It's a free editable Cyberpedia! I'll add an entry...!"
Check text reads, "Ralsei wrote an article about All Dogs Go To Heaven 2. Read it?"
Check text continues, "From now on, Gordon Freeman is dead."
End I.D.s 1, 2, 3]

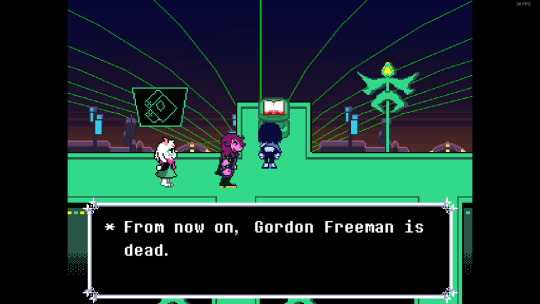
That’s so fucked up why would he say that.
4K notes
·
View notes
Text
wait did ralsei write "but the bonds you break may make you stronger" into the cyberpedia or is this fuckery that fuels narrator theories
0 notes
Text
Cyber Security

What is Cyber Security?
Cyber security refers to the security of any device with a digital element to it. Such as a company’s computer system, or a phone. The term security covers protection from theft or damage to the systems hardware, software or electronic data, as well as protection from disruption or misdirection from the services that those systems within the company provide.
How has it evolved?
Cyber security has evolved greatly since its creation, when computers were first created the technology to protect the information was not sophisticated, 1 level of protection was used such as a password. However, now there are multiple layers of authentication to protect sensitive data, such as unique logins to a computer, bio-metric authentication (retinal scanning & finger prints), as well as using a code send to a 2nd device of yours to validate your identity (this is used on various email and social media platforms).

Attacks are becoming for sophisticated, one of the first major cyber security attacks was “the Morris worm” which happened in 1988, this was the first time a worm had been used, the self-replicating worm abused a weakness in the UNIX 1 system which slowed down computers to the point of being unusable. Since this attack, the attackers have evolved, they are able to hide the host machines identity, they can do this by connecting to a different network session, or connecting through the TOR network, hiding the machines actual location.
What challenges face Cyber Security?
Human challenges
One of the challenges facing Cyber Security, is human threats. Human threats can come in the form of launching a denial of service attack on the system. This type of attack would block the system from accepting anyone on it. It is done by flooding the system with too many requests for it to handle, thus crippling the system and not allowing anyone on.

Another big threat is Trojans, Malware, Ransomware, Worms, Virus’s & Spyware. All of these are big threats to a system and can be launched on the computer just from someone who has access to the system, opening an attachment on an email, or plugging in a USB drive that they found. These are all challenges to a system as they can stop the system from working entirely by holding all data in an encrypted state until money is paid (ransomware), log all data and discreetly pull it off the systems (Spyware),
IOT devices vs Cyber Security
The main concern with IOT devices such as Alexa & the Google Home devices, is when are they listening, and who has access to that data. The Amazon Echo & Echo dot answer to the name of Alexa and will play music and answer simple questions on voice command. It also records what you say and sends that recording to a server. However, while it is meant to online respond to “Alexa….” They do have a habit of turning on and speaking (thus recording speech) from radio or TV if it deems something to sound similar to “Alexa”.

Many IOT devices are built with no security at all, If the device is discoverable on the internet, and it’s connected to the rest of the network, it’s an easy to use gateway for attackers. From here attackers could gain access to sensitive information, such as turning on the home assistant’s speech recording functions and listening in on conversations you are having. If an attacker could use your home assistant as a weak spot to gain access to your home network, then they could use that to add spyware to other devices connected to it, such as your computer, and gain highly sensitive data such as your bank details and log in username’s and passwords.
References
https://limn.it/articles/the-morris-worm/
https://www.paloaltonetworks.com/cyberpedia/what-is-cyber-security
https://blog.malwarebytes.com/101/2017/12/internet-things-iot-security-never/
0 notes