#CryptoWorms
Explore tagged Tumblr posts
Text
Analysis of cyber attacks such as APT (Advanced Persistent Threat) and ransomware
Ferenț, Darius-Antoniu (2022), Analysis of cyber attacks such as APT (Advanced Persistent Threat) and ransomware, Intelligence Info, 2:1, x-x, DOI:, Abstract In the information society, cyber attacks launched upon the information technology infrastructure are increasingly diversified and complex. Cybercriminals or black hat hackers use a wide range of techniques, tactics and procedures to…

View On WordPress
0 notes
Photo

WannaCry
A rendering of the infamous WannaCry ransomware cryptoworm. This malware sample was captured by honeypot servers operated by @glitchtextiles owner and @yearoftheglitch creator, @phillipstearns.
Currently available on Kickstarter:
https://www.kickstarter.com/projects/phillipstearns/the-honeypot-collection-by-glitch-textiles
Ships October 1st, 2019
#ransomware#malware#crypto#cryptoworm#wannacry#binary#digitalart#computer art#computer worm#computer virus#worm#cybersec#cybersecurity#cyber security#black hat#blackhat#defcon#glitch#glitchart#glitch art#glitchtextiles#glitch textiles#glitch design#design#art and design
74 notes
·
View notes
Note
WannaCry (don't remember by whom) is your go-to Tyrell character study, title is a cryptoworm name and also fitting because yeah. Crybaby. But also the person who wrote it just gets him well. I think that may've likely been his actual backstory. As an aside, if they snub Mr Robot on Emmy this year, I swear to fucking Christ! Rami didn't get his Globe for season 4 and I'm still salty.
I HAVE IT BOOKMARKED LMAOOOOOOOO and yeah holy shit man if they get snubbed again. Someone’s gonna die
1 note
·
View note
Photo

buying drugs from cryptoworm
1K notes
·
View notes
Photo

Guo O Dong, “The Persistence of Chaos” (2019)
A laptop running 6 pieces of malware that have caused financial damages totaling $95B.
The piece is isolated and airgapped to prevent against spread of the malware.
Malware:
ILOVEYOU
The ILOVEYOU virus, distributed via email and file sharing, affected 500,000+ systems and caused $15B in damages total, with $5.5B in damages being caused in the first week.
MyDoomMyDoom,
potentially commissioned by Russian e-mail spammers, was one of the fastest spreading worms. It's projected that this virus caused $38B in damages.
SoBigSoBig
was a worm and trojan that circulated through emails as viral spam. This piece of malware could copy files, email itself to others, and could damage computer software/hardware. This piece of malware caused $37B in damages and affected hundreds of thousands of PCs.
WannaCry
WannaCry was an extremely virulent ransomware cryptoworm that also set up backdoors on systems. The attack affected 200,000+ computers across 150 countries, and caused the NHS $100M in damages with further totals accumulating close to $4B.
DarkTequila
A sophisticated and evasive piece of malware that targeted users mainly in Latin America, DarkTequila stole bank credentials and corporate data even while offline. DarkTequila costed millions in damages across many users.
BlackEnergy
BlackEnergy 2 uses sophisticated rootkit/process-injection techniques, robust encryption, and a modular architecture known as a "dropper". BlackEnergy was used in a cyberattack that prompted a large-scale blackout in Ukraine in December 2015.
NC10-14GB 10.2-Inch Blue Netbook (2008), Windows XP SP3, 6 pieces of malware, power cord, restart script, malware
10.3” x 1.2” x 7.3” 2.8Lbs
(Final bid received: $1,345,000)
Courtesy of the artist and Deep Instinct
#art#conceptual#conceptual art#i love you#mydoom#sobig#virus#wannacry#blackenergy#fun#samsung#deepimpact#cybersecurity#cyberpunk#guo o dong#chaos#airgapped#windows xp#malware#darktequila#auction#bid#surreal
9 notes
·
View notes
Note
Instead of mining crypto electronically, I've toyed with the idea of mining crypto organically. Either the pulses of electrochemically active bacteria or the biochemical activity of worms and other organisms within a compost culture. This idea is still in the early stages, but what do you think? I'd really like to preserve the idea of cryptocurrency, but use it in a way that is truly anti-establishment and anti-capitalist.
Oh, Cryptoworm?Alright seriously Anon I am begging you please go outside and put that creativity to solving some actual problems in your community instead of postulating a future of bacteria-backed imaginary currency to compete against existing imaginary currencies whose sole purpose could be described loosely as financial malingering for people who think children should work harder to pay for the food on their plates.
32 notes
·
View notes
Photo

Always keep your device up to date. Follow @aiprobably to know some tips and tricks. . WannaCry Ransomware: The WannaCry ransomware attack was a May 2017 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. . . #hacker #hacking #linux #tech #hack #technology #cybersecurity #python #programmer #computerscience #code #developer #security #computer #software #kalilinux #php #webdeveloper #cyber #ethicalhacking #anonymous #engineer #privacy #ai #geek #google #android #malware #internet #dataprotection https://www.instagram.com/p/BxtPT2Dge9g/?igshid=a7a3fjdnc92s
#hacker#hacking#linux#tech#hack#technology#cybersecurity#python#programmer#computerscience#code#developer#security#computer#software#kalilinux#php#webdeveloper#cyber#ethicalhacking#anonymous#engineer#privacy#ai#geek#google#android#malware#internet#dataprotection
4 notes
·
View notes
Text
Hardware of Death: Malware-infested Laptop sold for $1.3 Million

Viruses and Malware are usually things people don’t want on their laptops and are removed the quicker the better. Oddly enough, some people actually see those perilous digital bugs as art.
In a Memorial Day auction someone spent $1.345 million on a laptop that was infested with the most malicious and infamous malware that had caused over $95 billion in damages in the past. The Laptop of Death is called “The Persistence of Chaos” and is actually a work of art.
The designer of the art oddity, Guo O Dong, considers himself a “contemporary internet artist”. Dong created this malicious art piece containing six of the most infamous virtual plagues together with the cybersecurity company Deep Instinct. They made sure to safely provide and install the malware of the laptop. The laptop sold is a older model considered a classic – a 2008 Samsung NC10-14GB 10.2-Inch Blue Netbook running Windows XP.

The laptop is infected with:
1. ILOVEYOU is a computer virus or worm that spread through an email with the subject line “I love you” in 2000 and has caused more than $5.5 billion in damages.
2. Mydoom also known as W32.MyDoom@mm, Novarg, Mimail.R and Shimgapi is a computer worm that attacked Microsoft Windows. As of January 2004, it became the fastest-spreading e-mail worm ever, even faster than ILOVEYOU and has not been surpassed as of yet (2019). Like the ILOVEYOU worm Mydoom spread through emails containing the text message “andy; I’m just doing my job, nothing personal, sorry,”.
3. SoBig is another worm on the list and has infected millions of computers running Microsoft Windows and with an internet connection. Guess, how it spread! That’s right, also through your emails.
4. WannaCry is a ransom cryptoworm which attacked older Windows systems encrypting data on those PCs held captive. To free data back again, the worm demanded Bitcoins to let users gain access to files.
5. Dark Tequila is a banking malware that targeted Latin American users, more specifically banks, stealing financial information, even when the PCs went offline. The malware can clone itself and is unleashed through a simple USB flash drive, but could also be sent as a file.
6. BlackEnergy came in form of an email attachment in disguise of a Word document or PowerPoint file. When opened the malware generated denial of service attacks rendering the infested computers useless. Later generations of this malware could wreak even more havoc waiting for further updates and being able to launch new executables on demand.
1 note
·
View note
Text
What is the WannaCry Ransomware Attack?
What is the WannaCry Ransomware Attack?
WannaCry is a ransomware cryptoworm cyber attack that targets computers running the Microsoft Windows operating system. It was initially released on 12 May 2017. The ransomware encrypted data and demanded ransom of $300 to $600, paid in the cryptocurrency Bitcoin. WannaCry is also known as WannaCrypt, WCry, Wana Decrypt0r 2.0, WanaCrypt0r 2.0 and Wanna Decryptor. Once installed, WannaCry…

View On WordPress
0 notes
Text
WannaCry Scarf
WannaCry is the infamous ransomware cryptoworm that spread around the globe on Friday May 12th, 2017 , infecting more than 200,000 computers in a single day. It target Windows computers, spreading using the NSA attributed Eternal Blue exploit, requiring nothing more than a vulnerable system with an exposed SMB file sharing service. Users’ hard drives were locked, encrypted, with the key offered only after paying ransom in bitcoin to the attacker’s address.
Glitch Textiles is operating 15 honeypot servers worldwide, capturing malware in the wild to bring you this new collection. Each design renders the DNA of malicious software—computer viruses, Trojans, and worms—into woven soft wares.
Honeypots are tools used by security researchers to make a server appear vulnerable to attack. By capturing interactions and file uploads, operators of honeypots can profile techniques, tools, and methods of attackers as well as collect the malware they upload.
Glitch Textiles Woven Scarves are made with care from 100% premium cotton grown and processed in the USA on state of the art computerized Jacquard looms in North Carolina. They are easy to care for and can be used outdoors as well as indoors.
12" x 71"
Machine Washable on Cold Delicate Cycle, Line Dry or Tumble Low, Iron Low.
Scarves are cut and finished in GlitchTextiles’ studio. Ships in 2-3 business days.
0 notes
Link
via Twitter https://twitter.com/PatrickCMiller
0 notes
Text
WannaCry: Why An Insecure Internet Is In No One’s Interest.
The WannaCry virus was a ransomware cryptoworm from 2017 that infected hundreds of thousands of Windows machines. The virus uses EternalBlue, a Windows exploit that allows arbitrary code execution, to gain access into the system and then uses the DoublePulsar backdoor tool to install and execute a copy of itself. The virus would encrypt the computers data and display a message telling the user that they had to send an amount of bitcoin to an address in order to get it de-crypted. The authors of the malware had no way of keeping track of who did and didn’t pay the ransom and so most users lost their data anyway, if they didn’t have a backup. What I want to focus on is the fact that the 2 main tools used in this worm that cost hundreds of millions of dollars worth of damage, were stolen from the NSA. Both DoublePulsar and EternalBlue are NSA tools, the later being an exploit that they had discovered 5 years before the attack, but decided to horde for their own offensive capabilities. I think this really strikes at the heart of why the current practice of deeply-funded and powerful state actors hording exploits and buying vulnerabilities is ultimately not going to be stable, effective or safe going forward. We are lucky security researchers were able to find the kill-switch relatively quickly (4 days), but in this time it still managed to spread to 200 000 computers, infecting hospital systems, businesses, infrastructure. The NSA (and other intelligence organizations around the world) have the dual responsibility of protecting their own citizens and attacking/gathering informational resources of opposition. This may have worked during the second world war when these were two very different things, but now to attack and discover vulnerabilities in your enemies systems is also uncovering holes in your own and thus leaving yourself and the rest of the world vulnerable. This newly arisen fact is only going to become more prominent and more devastating as the world moves into ever increasing levels of technological entanglement. As computation becomes embedded in every single aspect of human life, we can no longer afford to not act on security vulnerabilities just because they give our side an advantage. Because they don’t, they may give your organization an advantage, but you can’t keep that advantage while simultaneously not leaving yourself open to attack. You may ask what then should these organizations do ? should they not collect these exploits to use against criminals and enemies of their state? I think the answer is no for now, and definitely not going forward. How did the police or any military/intelligence/government agency gather intel on individuals and situations before the masses of the worlds put their communication out into the open for the taking ? They performed old fashioned targeted police work. I think these organizations have become spoiled by the ease at which they’ve been able to collect information, but I think this is only a product of the very unusual time we have and still are (for the next short while) living in, where technological has flung our information out into the open, but hasn’t yet become absolutely critical to our survival, i.e. there aren’t many instances of computers keeping people alive. But this will not be the case going forward, as medical and computational technologies reach a concrescence we will see more and more the merging of biology and computation, and when this happens we can no longer afford to have intentionally vulnerable systems, an insecure internet/computational landscape is in no ones interest, unless you’re an anarchist. I propose that these organization moving forward will have to disbandon the idea of mass invasion of privacy and mass exploitation/vulnerability hording, and instead move back to old fashion detective/police/intelligence work. It doesn’t mean their methods need to be archaic, I’m sure the technological revolution of the 21st century has enabled great intelligence gathering technologies that don’t put humanity at risk.
0 notes
Text
0x05: WannaCry
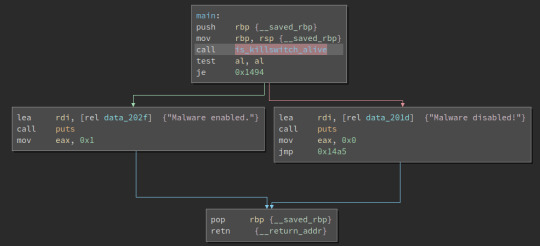
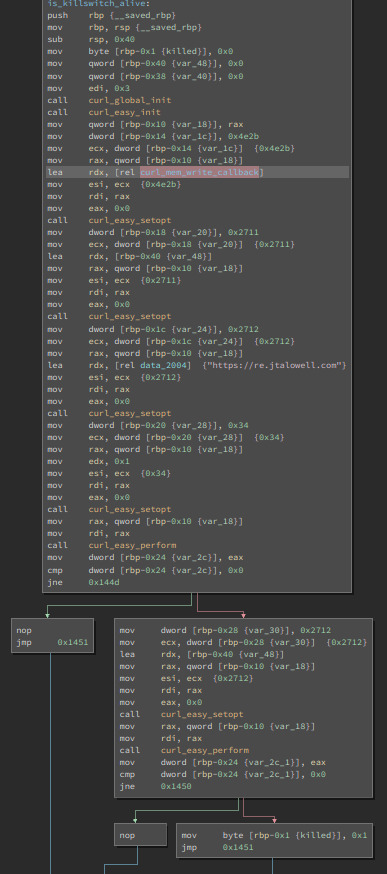
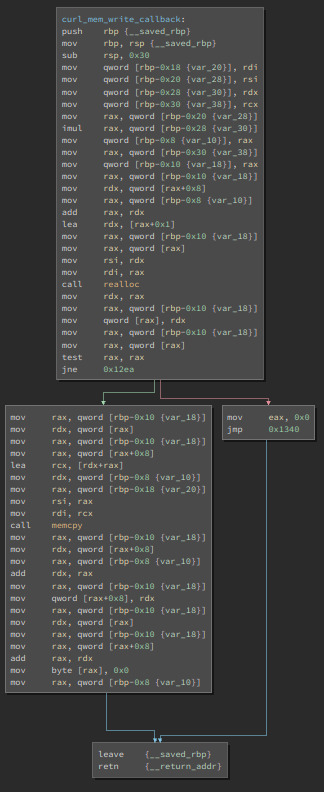
This was definitely the toughest one yet, especially since the “https:” link didn’t lead anywhere. Similarly to the last exercise, this wasn’t hard to modify. However the use of curl isn’t something I’ve seen in a while and the repetitive usage of curl_set_opt() was extremely difficult to understand and follow, besides the fact that it was probably trying to load a website that doesn’t seem to exist. Looking at the source code gave me a slight understanding of the set_opt()’s but the memory_write_back() was also pretty cooked to look at. Maybe I was supposed to register the site to return something, but I’m still unsure. Def’s wannacry ☹
The use of a kill switch in a program seems like an interesting addition, I’m curious to how easily this would be discovered in a legitimate piece of malware, and what action would be taken. How fast can law enforcement or internet providers act to activate such a kill switch? Would WannaCry simply encrypt data indefinitely if not connected to the internet?
I’ll definitely be looking deeper into WannaCry and CryptoWorms in general
0 notes
Text
Something awesome 5
Week 5 - Ransomwares
Blog
What is ransomware?
Ransomware is a type of malware from cryptovirology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them. In a properly implemented cryptoviral extortion attack, recovering the files without the decryption key is an intractable problem – and difficult to trace digital currencies such as Ukash and cryptocurrency are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Ransomware attacks are typically carried out using a Trojan that is disguised as a legitimate file that the user is tricked into downloading or opening when it arrives as an email attachment. However, one high-profile example, the "WannaCry worm", travelled automatically between computers without user interaction.
Starting from around 2012 the use of ransomware scams has grown internationally. There were 181.5 million ransomware attacks in the first six months of 2018. This marks a 229% increase over this same time frame in 2017. In June 2014, vendor McAfee released data showing that it had collected more than double the number of samples of ransomware that quarter than it had in the same quarter of the previous year. CryptoLocker was particularly successful, procuring an estimated US $3 million before it was taken down by authorities, and CryptoWall was estimated by the US Federal Bureau of Investigation (FBI) to have accrued over US $18m by June 2015.
Types of ransomware
Ransomware can come in many shapes and sizes. Some variants may be more harmful than others, but they all have one thing in common: a ransom. The five types of ransomware are:
Crypto malware. This is a well-known form of ransomware and can cause a great deal of damage. One of the most familiar examples is the 2017 WannaCry ransomware attack, which targeted thousands of computers around the world and spread itself within corporate networks globally.
Lockers. This kind of ransomware is known for infecting your operating system to completely lock you out of your computer, making it impossible to access any of your files or applications.
Scareware. This is fake software that acts like an antivirus or a cleaning tool. Scareware often claims to have found issues on your computer, demanding money to resolve the issue. Some types of scareware lock your computer, while others flood your screen with annoying alerts and pop-up messages.
Doxware. Commonly referred to as leakware, doxware threatens to publish your stolen information online if you don’t pay the ransom. As more people store sensitive files and personal photos on their computers, it’s understandable that many individuals panic and pay the ransom when their files have been hijacked.
RaaS. Otherwise known as “Ransomware as a Service,” RaaS is a type of malware hosted anonymously by a hacker. These criminals handle everything from distributing the ransomware and collecting payments to managing decryptors — software that restores data access — in exchange for their cut of the ransom.
Ransomware remains a popular means of attack, and new ransomware families are discovered every year. Reported attacks in the U.S. dropped from 2,673 in 2016 to 1,783 in 2017. However, the threat of ransomware is still incredibly active on the internet.
CryptoLocker
CryptoLocker was a ransomware trojan which used the Gameover ZeuS botnet and infected email attachments to spread across the Internet, infect Windows PCs, and lock files using RSA 2048-bit encryption. Victims are then prompted to pay a $300 ransom in order to receive a password. Since it wasn’t a virus, it didn’t spread across your network on its own. However, it was still capable of doing a lot of damage.
CryptoLocker affected around 500,000 people between September 2013 and May 2014. In a crackdown dubbed “Operation Tovar”, a group of security experts — from the FBI, Interpol, security software vendors, and universities — managed to stop the hackers.
Although CryptoLocker itself was easily removed, the affected files remained encrypted in a way which researchers considered unfeasible to break. Many said that the ransom should not be paid but did not offer any way to recover files; others said that paying the ransom was the only way to recover files that had not been backed up. Some victims claimed that paying the ransom did not always lead to the files being decrypted.
WannaCry
The only malware that I have heard of before I started this project as it happened pretty recently in 2017.
In May 2017, the WannaCry ransomware cryptoworm targeted computers running the Microsoft Windows operating system by encrypting data and demanded ransom payments in the Bitcoin cryptocurrency, propagating through Eternal Blue. The initial infection was likely through an exposed vulnerable SMB port, rather than email phishing as initially assumed. The attack was estimated to have affected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars. Security experts believed from preliminary evaluation of the worm that the attack originated from North Korea or agencies working for the country. It was the first time that ransomware had spread across the world in what looked like a coordinated cyberattack.
When executed, the WannaCry malware first checks the "kill switch" domain name; if it is not found, then the ransomware encrypts the computer's data, then attempts to exploit the SMB vulnerability to spread out to random computers on the Internet, and "laterally" to computers on the same network. As with other modern ransomware, the payload displays a message informing the user that files have been encrypted and demands a payment of around US$300 in bitcoin within three days, or US$600 within seven days. Three hardcoded bitcoin addresses, or "wallets", are used to receive the payments of victims. As with all such wallets, their transactions and balances are publicly accessible even though the cryptocurrency wallet owners remain unknown.
A new variant of WannaCry ransomware forced Taiwan Semiconductor Manufacturing Company (TSMC) to temporarily shut down several of its chip-fabrication factories in August 2018. The virus spread to 10,000 machines in TSMC's most advanced facilities.
Reflection
What techniques do ransomwares usually employ to attack?
There are a number of vectors ransomware can take to access a computer. One of the most common delivery systems is phishing spam — attachments that come to the victim in an email, masquerading as a file they should trust. Once they're downloaded and opened, they can take over the victim's computer, especially if they have built-in social engineering tools that trick users into allowing administrative access. Some other, more aggressive forms of ransomware, like NotPetya, exploit security holes to infect computers without needing to trick users.
How can we combat these?
· Keeping operating system patched and up to date to ensure fewer vulnerabilities and bugs to exploit
· Don’t install software or give it administrative privileges unless it’s trusted
· Installing antivirus software which can detect malicious programs such as ransomware, this prevents unauthorized applications from executing in the first place
· Back up files frequently. Although this won’t stop a ransomware attack, it can mitigate the damage caused by one
What did CryptoLocker exploit?
CryptoLocker typically propagated as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by a legitimate company. A ZIP file attached to an email message contains an executable file with the filename and the icon disguised as a PDF file, taking advantage of Windows' default behaviour of hiding the extension from file names to disguise the real .EXE extension. CryptoLocker was also propagated using the Gameover ZeuS trojan and botnet.
What did Wannacry exploit?
· WannaCry also took advantage of installing backdoors onto infected systems.
· EternalBlue is an exploit of Windows' Server Message Block (SMB) protocol released by The Shadow Brokers. Much of the attention and comment around the event was occasioned by the fact that the U.S. National Security Agency (NSA) (from whom the exploit was likely stolen) had already discovered the vulnerability, but used it to create an exploit for its own offensive work, rather than report it to Microsoft. Microsoft eventually discovered the vulnerability, and on Tuesday, 14 March 2017, they issued security bulletin MS17-010, which detailed the flaw and announced that patches had been released for all Windows versions that were currently supported at that time, these being Windows Vista, Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2016.
· EternalBlue was stolen and leaked by a group called The Shadow Brokers a few months prior to the attack. While Microsoft had released patches previously to close the exploit, much of WannaCry's spread was from organizations that had not applied these or were using older Windows systems that were past their end-of-life.
· DoublePulsar is a backdoor tool, also released by The Shadow Brokers on 14 April 2017. Starting from 21 April 2017, security researchers reported that there were tens of thousands of computers with the DoublePulsar backdoor installed. By 25 April, reports estimated that the number of infected computers could be up to several hundred thousand, with numbers increasing every day. The WannaCry code can take advantage of any existing DoublePulsar infection, or installs it itself.
What do we have nowadays that is making this attack hard/still possible?
Anti-malware software is not absolute. Ransomware is constantly being written and tweaked by its developers, and so its signatures are often not caught by typical anti-virus programs. In fact, as many as 75 percent of companies that fall victim to ransomware were running up-to-date endpoint protection on the infected machines.
Ransomware isn't as prevalent as it used to be. The number of ransomware attacks, after exploding in the mid '10s, has gone into a decline, though the initial numbers were high enough that it's still. But in the first quarter of 2017, ransomware attacks made up 60 percent of malware payloads; now it's down to 5 percent.
In many ways it's an economic decision based on the cybercriminal's currency of choice: bitcoin. Extracting a ransom from a victim has always been hit or miss; they might not decide to pay, or even if they want to, they might not be familiar enough with bitcoin to figure out how to actually do so.
The decline in ransomware has been matched by a rise in so-called cryptomining malware, which infects the victim computer and uses its computing power to create (or mine, in cryptocurrency parlance) bitcoin without the owner knowing. This is a neat route to using someone else's resources to get bitcoin that bypasses most of the difficulties in scoring a ransom, and it has only gotten more attractive as a cyberattack as the price of bitcoin spiked in late 2017.
That doesn't mean the threat is over, however. There are two different kinds of ransomware attackers: "commodity" attacks that try to infect computers indiscriminately by sheer volume and include so-called "ransomware as a service" platforms that criminals can rent; and targeted groups that focus on particularly vulnerable market segments and organizations.
With the price of bitcoin dropping over the course of 2018, the cost-benefit analysis for attackers might shift back. Ultimately, using ransomware or cryptomining malware is a business decision for attackers, says Steve Grobman, chief technology officer at McAfee. “As cryptocurrency prices drop, it’s natural to see a shift back [to ransomware]."
CryptoLocker
During its spread, any unprotected Windows PC was vulnerable to the trojan. However, CryptoLocker is no longer a threat.
On 2 June 2014, the United States Department of Justice officially announced that over the previous weekend, Operation Tovar—a consortium constituting a group of law enforcement agencies (including the FBI and Interpol), security software vendors, and several universities, had disrupted the Gameover ZeuS botnet which had been used to distribute CryptoLocker and other malware. The Department of Justice also publicly issued an indictment against the Russian hacker Evgeniy Bogachev for his alleged involvement in the botnet.
As part of the operation, the Dutch security firm Fox-IT was able to procure the database of private keys used by CryptoLocker; in August 2014, Fox-IT and fellow firm FireEye introduced an online service which allows infected users to retrieve their private key by uploading a sample file, and then receive a decryption tool
Comics





0 notes
Text
Windows 7 Devrinin Sonu: Hacker'lar için Açık Yol !

Microsoft, müşterileri, genişletilmi�� destek için çeşitli seçeneklerle geçişi kolaylaştırmaya çalışırken, Windows 7 işletim sisteminden yükseltmeye çağırıyor. Ocak 2020'den itibaren geçerli olan rutin düzeltmeler ve güvenlik yamaları sağlanmaya son verecek. Windows Server 2008 için düzenli desteğin de o zaman bitmesi planlanıyor.

Windows 7 kurumsal müşterileri, İşletim Sistemi'ndeki ele geçen veya bildirilen güvenlik açıkları için güvenlik düzeltmeleri almak üzere Genişletilmiş Güvenlik Güncelleştirmeleri'ne (ESU) abone olabilir. Ancak, yamalar yalnızca Microsoft tarafından "Kritik" veya "Önemli" olarak değerlendirilen tehditlerde verilecektir. Bunlar, Microsoft'un dört aşamalı puanlama sistemindeki en üst sıralarda yer alıyor; bu, performans sorunlarının ele alınmayabileceği anlamına geliyor. Ayrıca, ESU sadece bir yıllık artışlarla ve sadece üç yıl boyunca mevcut olacak. Microsoft'un Windows 10 için sunduğu kullanıcı başına değil, cihaz başına satılacaktır. ESU, cihaz başına yıllık 25 ila 50 ABD Doları karşılığında kullanılabilir, ancak 2022'de yaşlanan Windows 7 işletim sistemi desteğinin aygıt başına 100 veya 200 ABD Doları tutarında olması gerekir. Microsoft 365 Enterprise'a abone olan müşterilere daha düşük seviyeli fiyatlandırma sunulacak. Netmaketshare verilerine göre, Windows 7 çalıştıran bilgisayarlar bugün 37,9 PC, Windows 10 ise 40,9 pazar payına sahip. Pazarın ticaret tarafında, Windows 10 pazarın yüzde 50'sinden fazlasını oluşturuyor. Windows 7, 2009'da popüler olmayan Windows Vista'nın ve 2001'in Windows XP'sinin yerini aldı.
Sunucu tarafı
Microsoft ayrıca, gelecek yılın başlarında Windows Server 2008 ve SQL Server uygulamaları için destek vermeyi planlıyor ve şirket müşterileri Azure'a geçmeye teşvik ediyor. Windows 7'den farklı olarak, ESU planlanmaz ve müşterileri sınırlı seçeneklerle bırakır. Windows Server 2008 desteğinin sonu, ankete katılan şirketlerin neredeyse üçte birinin yeni Spiceworks 2019 Sunucu Sunucusu raporuna göre, yeni sunucu donanımı satın almayı düşündüklerini söyledi. Yönetilen siber güvenlik hizmetlerinin sağlayıcısı MonsterCloud'un CEO'su Zohar Pinhasi, "Windows 2008 Server, gezegenin en yaygın kullanılan sunucusudur" dedi. Sonuç olarak, destek sona erdiğinde bilgisayar korsanlarına cazip bir hedef yapabilir. TechNewsWorld'e yaptığı açıklamada, "Pek çok kuruluş Server 2012'ye taşındı, ancak göç kolay bir iş değil ve şirketler sık sık“ kırılmamışsa düzeltmeyin ”yaklaşımını benimsiyorlar” dedi. Pinhasi, "Suçlular, Microsoft'un gelecek yıl işletim sistemi desteğini bırakacağının farkındalar ve araştırmamız, sıfır günlük güvenlik açıklarından yararlanmaları gibi büyük bir şeyler pişirebileceklerini söylüyor." Dedi. Windows 7, altında yatan Windows Vista'nın bir takibi olarak piyasaya sürüldü. Yaygın bir şekilde Windows XP ve Vista'nın en iyi özelliklerini ve işlevselliğini sunan olarak görülen sıcak bir resepsiyon aldı. Bununla birlikte, 2012'de - Windows 7'nin piyasaya sürülmesinden sadece üç yıl sonra - Microsoft, işletim sistemini dokunmatik ekran seçenekleriyle "Modern Kullanıcı Arabirimi" olarak nitelendiren önerisini Windows 8 ile tamamen yeni bir yöne götürdü. Aynı zamanda, tabletleri ve PC'leri de köprülemek için tasarlanan yeni arayüz yakalanamadı. Microsoft daha sonra 2015 yılında Windows 10'u piyasaya sürdü. Windows 7, XP ve Vista'nın en iyi yönlerini birleştirirken, Windows 10, Windows 7 ve 8 / 8.1'in en iyisini sundu. Yine de, belki de Windows 10, Windows 7'ye çok benzemesi nedeniyle, kullanıcılar bunu benimsemekte yavaş kaldılar. Neredeyse dört yıl sonra 10 kişi toplam 7 kişiyi geçti. Microsoft üç işletim sistemini desteklemek zorunda kaldı, bu yüzden şirketin en eski fişi çekmeye karar vermesi şaşırtıcı değil. LiftrCloud'un baş analisti Paul Teich, "Windows 7, 2009'da 10 yıl önce - yani 70 köpek veya İnternet yıl - bir insan ömrüdür " dedi . Endpoint Technologies Associates'in analisti Roger Kay, "Bir zamanlar olması gerekiyordu; Microsoft, Windows 7'nin ömrünü birkaç kez uzattı," dedi .
Eski İşletim Sistemiyle
Bu geçişi zorlaştıran şey, Windows 7'nin oldukça iyi bir işletim sistemi olarak kaldığı için işini oldukça iyi yapmış olmasıdır. Yine de, çoklu işletim sistemlerini desteklemek, yalnızca kaynakları azaltmak değil, aynı zamanda Microsoft'un yeni yönüyle de tutarsız. Kay, TechNewsWorld'e yaptığı açıklamada, "Microsoft, herkesi bir hizmet geliri akışına daha iyi adapte olan Windows 10'a itmeyi taahhüt ediyor" dedi. “Aslında, başka hiçbir Windows olmayabilir” dedi. “Şirket, Windows 10 kodunu esasen süresiz olarak güncellemeye devam edecek. Şimdi yeni kodun beta sürümleri yayınlanıyor, hata raporları geri geliyor ve ekip ihtiyaç duyduğu her şeyi ekliyor.”
Donanım İyileştirmeleri
Geçmişte, yükseltmenin önündeki bir engel, Windows'un eski sürümlerinin üzerinde çalıştığı donanımdı ve Windows 3.1'den Windows 95'e geçiş yapmak neredeyse kullanıcıların kesinlikle yeni bir bilgisayar satın almasını gerektiriyordu. Aynı eğilim Windows 98, Windows Millennium, Windows XP ve özellikle Windows Vista ile de devam etti. Windows 7 geldiğinde, Moore'un daha hızlı işlemciler yasası yavaşlıyor gibiydi. Daha da önemlisi, bazı PC oyunlarından ayrı olarak, çoğu yazılım gerçekten gelişmiş donanım gerektirmiyordu. Bu, Windows Vista'dan Windows 7'ye geçişi çok daha kolay hale getirdi ve bugün bile yeni bir işletim sistemine yükseltme yapmak o kadar da zor değil. LiftrCloud'sTeich, "Windows 7, ilk olarak 2008'de piyasaya sürülen" Yorkfield "(masaüstü) ve" Penryn "(mobil) adlı 45nm Intel Core işlemcileriyle birlikte gönderildi." TechNewsWorld'e "45nm Core i5 'Lynfield' (masaüstü) işlemcisi, Windows 7 ile aynı anda tanıtıldı, aynı zamanda 45nm Core i7 'Clarksfield' (mobil) işlemcisi" dedi. O zamanlar Intel Core işlemciler için "tatlı nokta", hem mobil hem de masaüstü bilgisayar için dört çekirdekliyken, tüm bu işlemciler için çekirdek saat frekansı 2.3 GHz'de başladı ve 3 GHz'in üzerine çıktı. Teich, "Yeni nesil Core i5 'Skylake' masaüstü işlemcisi, 2.6 GHz - 3.6 GHz arası bir taban frekansına sahiptir ve dört iş parçacığı çalıştıran iki çift dişli çekirdeğin hala tatlı bir nokta olduğunu" ekledi. Bugün Mobile Core i3 versiyonları, iki çift dişli çekirdek kullanarak 2,3 GHz ila 3,6 GHz baz frekanslarına sahiptir. Teich, "10 yıl içinde, Intel'in ürün hatlarının çok yüksek olanları dışında saat hızını daha hızlı alamadık" dedi. “AMD daha iyisini yapamadı, çünkü fizik fizik. Mimari gelişmeler nedeniyle bazı hızlandırmalar yaptık, ancak gerçekten de Moore Yasası öldü, öldü, öldü.”
Yeni işletim sistemi ile eski bilgisayar
Donanımda ileriye doğru büyük bir sıçrama görmediğimizden dolayı, çoğu durumda bu eski bilgisayarların yükseltilebileceği anlamına geliyordu - Microsoft'un ücretsiz olarak sunduğu bir şey. Kay, “Donanım açısından Windows 7 çalıştırabilen herhangi bir sistem Windows 10 çalıştırabilir” dedi. “Bu kısım kolay ve bir sürü eski sistemi yükselttim” dedi. Windows'u ücretsiz olarak yükseltmek için olan bu pencerenin kapatılmış olmasına rağmen Kay, bunun gerçekten zor olmadığını ve hala kolayca gerçekleştirilebileceğini söyledi. Kay, “Windows 10 güncelleyici esasen geçerli bir Windows 7 veya Windows 8 lisansı arıyor ve sizden ayrıldı” dedi. Teich, "Windows 7, Windows Vista'yı çalıştıran her şeyde iyi çalışacak şekilde tasarlandı, bu yüzden gönderilmesinden birkaç yıl önce elde edilebilecek hesaplama gücü gerektirmedi," dedi. Ayrıca, Windows 10, hem Windows 7 hem de Windows 8 yükseltmelerine hitap etmek için Windows 7 çalıştırabilen herhangi bir bilgisayarda iyi çalışacak şekilde tasarlanmıştır. Teich, "Zor bir hedef değildi, çünkü Windows 10, kurulumu kolay ve güncellemesi kolay bir mimariye, daha iyi güvenlik ve kullanıcı deneyimini geliştirmeye odaklandı - hiçbiri daha fazla işlemci hızı gerektirmedi" dedi. "Windows 10'u kişisel olarak Windows 7 dönem dizüstü bilgisayarlarımın ve kendi oluşturduğum medya bilgisayarlarımın en az dördüne kurdum. Hepsi iyi performans gösterdi."
Güvenlik endişeleri
Windows 7'den yükseltmenin en büyük nedeni güvenlik sorunu olmaya devam ediyor. Microsoft’un ESU’sunda bile, kullanıcılar kendilerini riske sokuyor olabilir. MonsterCloud'dan Pinhasi, "Suçluların laboratuarlarında bir şeyler pişirdikleri zaten biliniyor" dedi. “Bu ara��lara sahip olduklarında, ondan milyarlarca yapmak için eski Windows sürümlerinden faydalanabilirler” diye ekledi. Mayıs 2017’de Windows makinelerini hedef alan WannaCry cryptoworm gibi Ransomware, Microsoft’un Windows 7 desteği sona erdikten sonra piyasaya sürülebilir. Bu fidye yazılımı, Amerika Birleşik Devletleri Ulusal Güvenlik Ajansı tarafından geliştirilen bir istismar olan EternalBlue aracılığıyla çoğaltıldı. Pinhasi, "Bilgisayar korsanları NSA'dan çalınan bir paketi düşürdü ve bilgisayar korsanları benzer bir şey kullanabilir" dedi. En iyi eylem yolu, ESU’ya Microsoft’tan yatırım yapmak, ancak işletim sistemini ve gerekirse PC donanımını yükseltmektir. Recon Analytics'in baş analisti Roger Entner, “Devam etme zamanı; sevilen bir işletim sisteminin ölümü zor, ancak kaçınılmaz” dedi . TechNewsWorld'e "Windows 7, yedi yıl önce Windows işletim sisteminin amiral gemisi olmayı bıraktı, bu yüzden yükseltme zamanı ve Best Buy'da 179 dolarlık bir dizüstü bilgisayar Windows 10 kullanıyor ve muhtemelen 2012'de yapılan her şeyden daha güçlü." Dedi. Teich, "Windows 7'yi çalıştıran hiç kimsenin saf sıradan inatçılık dışında buna bağlı kalmaması için hiçbir neden yok ve yeni bir işletim sistemi öğrenmek zorunda değilsiniz." Tabii ki, sadece bu uyarıları dikkate alması gereken bireysel kullanıcılar değil. Kay, "Şirketler gerçekten en kısa zamanda Windows 7'den kurtulmalı" diye uyardı. "Güvenlik saldırıları daha sık, daha sofistike ve daha otomatik hale geliyor - ve küçük bir balık olduğun için peşinden gelmeyeceklerini hayal etme" dedi. “Küçük firmalar bazen daha büyük firmalara karşı bir saldırı vektörü olarak kullanılır. Şirketler, bilgisayar tabanını her 10 yılda bir değiştirmek zorunda kalırlarsa, bu iyi bir şey. Çalışanlar daha üretken olabilir.” Read the full article
0 notes
Photo

Buying Drugs from Cryptoworm by Mike Winkelmann . . . . . #monsterart #monsterartist #monsterarts #monster #monsters #characterart #characterartist #characterarts #creepy #creepyart #creepycreative #fantasyart #fantasycreature #fantasyartwork #fantasycharacter #FantasyLover #fantasyartcollection #fantasywork #fantasyconcept #fantasydesign #fantasyarts #digitalart #digitalartist #digitalartwork #digitalarts #digitalartists #digitalartworks #DigitalArtLook #digitalartistry #digitalartsociety
0 notes