#Cost of a Data Breach Report
Explore tagged Tumblr posts
Text
Los consumidores pagan el precio de las filtraciones de datos de las empresas
Los consumidores pagan el precio de las filtraciones de datos de las empresas
Las filtraciones de datos informáticos son más costosas y tienen mayor impacto que nunca, con un costo promedio de 2,09 millones de dólares en América latina. (more…)

View On WordPress
#américa latina#BEC#Boston#Business Email Compromise#consumidores#Cost of a Data Breach Report#datos#empresas#filtraciones#IBM#IBM Security#IBM Security Command Center#IBM Security X-Force#Instituto de Tecnología de Massachussets#iProfesional#Mike Barcomb#MIT#phishing#Ponemon Institute#precio#ransomware#Universidad de Harvard#Zero Trust
0 notes
Note
[BREAKING NEWS]
A prominent member of the House of Remembrance has suffered a major security breach after a random omninet denizen took umbrage to a post by said member.
While an obvious shame upon Lady Rosceline Hurst, the true bombs have come from opportunistic hackers who seized upon this abrupt act of digital-terrorism. While it didn't take long for this breach to be sealed and digital defenses to be upgraded, the past few hours have shown this was too late.
This morning the Omninet was flooded with a nigh-unprecedented amount of leaks. Years of private correspondence between the honored Lady Rosceline Hurst and various other notable figures laid bare for all to see. Some of which is quite... scandalous and unsuited for our program. Though the gossip-drama industrial complex will be fueled by them weeks, perhaps even months, to come.
However what is truly of consequence is the political and economic scheming which has been revealed. The average Karrakin citizen has been given a glimpse into the dirty backrooms of our illustrious state.
Lord Reginald Halifax of the House of Stone has already began to use this incident to continue his crusade against non-baronic peoples, while also decrying the weakness of The House of Remembrance to allow such a thing to occur. Lord Amelia Fraceux of the House of Water has stated that the honorable Lady Hurst provoked this heinous digital-terrorism with, quote, "An arrogant attitude almost as antiquated as our governmental structure." Lord Fraceux is as candid and provocative as always.
Whatever your opinion, stay tuned as we continue to report on the ongoing fallout of this developing situation!
...<DATABASE RECONSTRUCTION COMPLETE>
...<OMNINET CONNECTION SECURE>
...
With the situation handled and our systems back online, the time hath come for me to release on official statement on behalf of mine illustrious House. I shall begin by responding to the uncouth statements by mine fellows in the Houses of Stone and Water.
To the Venerable Lord Amelia Fraceux, I admit I find thine statement on both mine 'attitude' and our illustrious state both disturbing and surprising. This most heinous attack was forsooth carried out by an unshackled NHP of Horus. The behavior of such a demon is most erratic and I assure thee I did naught to provoke it. Thine implication that this terrorist was in any way justified speaks more to thine character than to mine own.
To the Honourable Lord Reginald Halifax, I must express grave disappointment. Whilst our Major Houses art disparate in political affiliation, many of us in the Interest art able to work around these petty squabbles. Mine Illustrious House of Hurst, Jewel of Crossland, doth have good relations with several Minor Houses of Stone upon Upper Laurent. I have already received correspondence from several members of such Houses, whom did wish mine House a speedy recovery and did denounce thine use of this data breach as an excuse to attacketh the great House of Remembrance. Prithee, speakest with more concern for thine cousins and their interests in future. I shall forgive thee, for thou art clearly ignorant of the Dawnline Shore's politics.
On that topic, as a general statement to those of the Concern, I must explain some intricacies of mine House's situation. On a relatively new, still developing colony such as Crossland, expenditures and costs are great for any minor house. I have spent more than a few late nights awake, speaking with mine dear cousin, the House Hurst Treasurer, whist he hath argued against mine requests for an increased cyber security budget. In the end, it seems I was right to worry about such things, but even after this attack I do see the Lord's side. With Harrison Armory barbarians so abundant in the Shore and pirates stalking either side of mine homeworld's dwarf star system, our military spending is equally important. Forsooth, I would allow mine personal correspondence to leaketh one hundred times to keep mine people safe and sound. In the coming weeks, House Hurst will taketh action to ensure that both of these needs are met in future.
The leaks are many and I shall address them individually, mine response is already quite long.
I thank thee, good people of the Baronies, and wish thee a fair morrow.
-Lady Rosceline, Heiress of Illustrious House Hurst, Jewel of Crossland
15 notes
·
View notes
Text
On the eve of the anniversary of a massive, world-wide cybersecurity breach, the Nova Scotia government says the response to the MOVEit hack cost the province $3.8 million. The breach occurred May 30 and May 31, 2023, and affected multiple organizations and millions of people around the globe. The online hack involved a file transfer service called MOVEit, which is used by the private sector and governments, including Nova Scotia. The software is made by Burlington, Massachusetts-based company Ipswitch and allows organizations to transfer files and data between employees, departments and customers. In a news release Wednesday promoting the final report into the online hack, Nova Scotia’s minister in charge of Cyber Security and Digital Solutions said the province has learned a number of lessons from the MOVEit breach. [...]
Continue Reading.
Tagging: @newsfromstolenland
11 notes
·
View notes
Text
Colony
Item #: SCP-11230
Object Class: Euclid
Special Containment Procedures: SCP-11230 is to be kept in a 2m x 2m x 2m containment chamber in Site-██. Any vents in the chamber must be fitted with a 0.███mm mesh screen. A decontamination chamber is to separate the room containing SCP-11230 and the rest of the site. All staff must pass a psychological evaluation and be cleared for entry by the on-site psychologist before attempting to make contact with SCP-11230.
Staff entering the chamber with SCP-11230 must wear a level ██ hazmat suit. When exiting the room with SCP-11230, staff are to be doused with carbon dioxide gas to kill any instance of SCP-11230 that may be present on them. In the event that a staff member’s hazmat suit is breached while in the chamber with SCP-11230, they are to be doused with carbon dioxide and immediately taken to quarantine, where they will be monitored for infection.
All instances of SCP-11230-01 are to be reported as soon as possible to MTF ████-██ (“Entomophobes”) and avoided at all costs. If physical contact is made with any instance of SCP-11230, immediately report to Dr. Kennedy for quarantine and monitoring.
Description: SCP-11230 is a colony of insectoid creatures resembling larvae of the Vespula genus. Their behaviour aligns with that of non-anomalous wasp larvae. Despite being in Foundation custody for █ years, the larvae do not appear to mature. They are able to reproduce by [DATA EXPUNGED].
SCP-11230 originally resided in an object resembling a wasp nest (SCP-11230-01-A) in the attic of an apartment building in Archway, London. SCP-11230-01-A was destroyed in 2014 after [REDACTED].
Foundation personnel were first notified of SCP-11230-01-B (formerly known as J███ P██████) after [DATA EXPUNGED] resulting in seven deaths. In 2016, SCP-11230-01-B was located once more by Researcher B███████ in Archway, London. It was successfully contained and sent to Site-14. According to reports sent to ███ ██████ ██████, at least two more instances of SCP-11230-01 exist.
SCP-11230-01-B is still capable of walking and speaking but otherwise does not display any signs of life. The body appears to be rotting, held together by material similar to that used to make wasp nests. Utterances by SCP-11230-01-B are solely focused on creating new instances of SCP-11230-01.
#the magnus archives#scp#jane prentiss#jordan kennedy#timothy hodge#harriet lee#the corruption#tma scp au#tales of site 14#tma#tma fic#scp fic#my writing#cw unreality
34 notes
·
View notes
Text
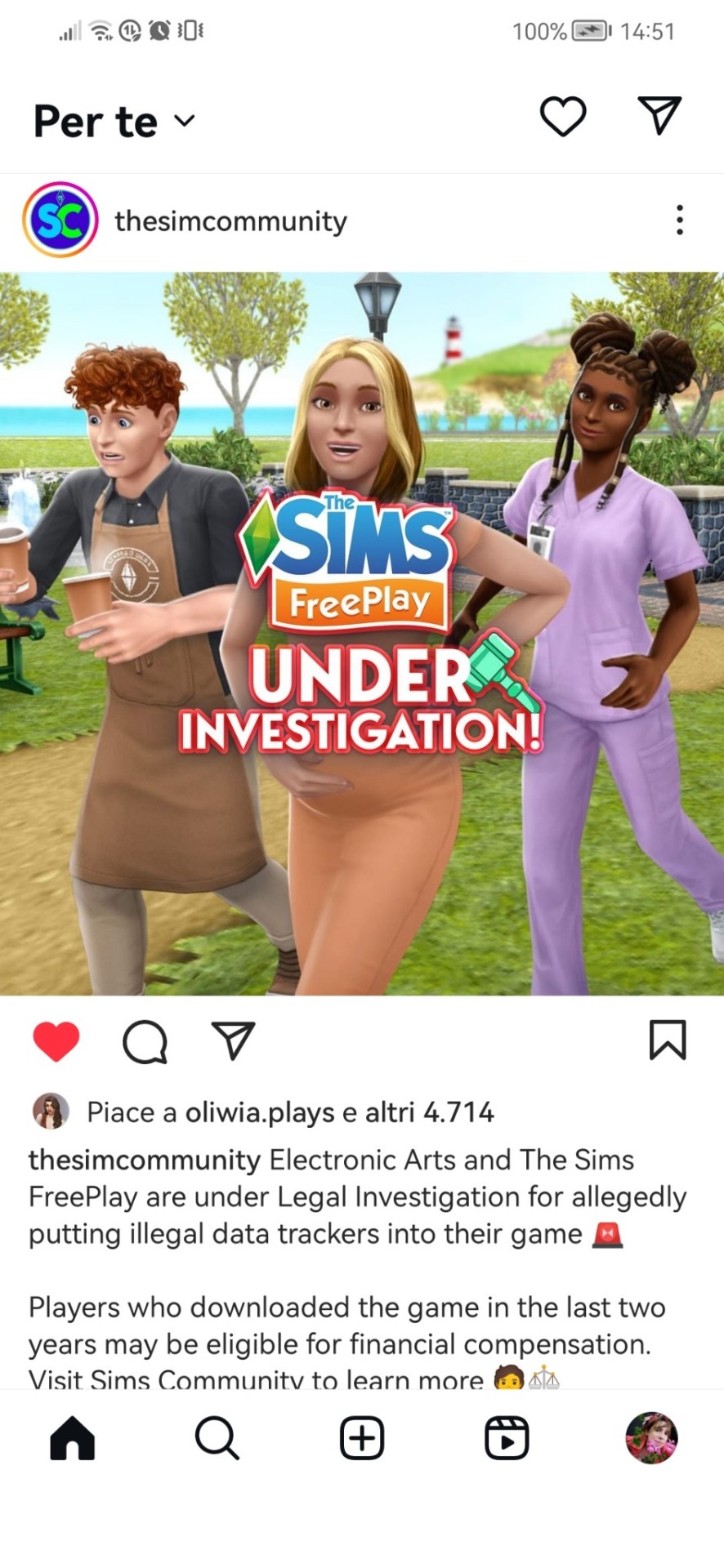
Seems that EA is now allegedly accused of a mayor privacy violation, having used tracking tools on The Sims FreePlay app to secretly gather and transmit players’ personal information to Facebook for advertising purposes. This data potentially includes unique Facebook IDs, which can be used to match players’ in-game activities to their individual Facebook profiles. Attorneys suspect that these potential data-sharing practices may violate a federal privacy law and are now gathering players to take action.
So, there are at least two class action against EA, because it seems to collect data from players using the Meta Pixel software to harness data from players and sell it to the Meta company, who owns Instagram, Facebook and other social networks.
It would be interesting to learn if this allegations are true and how this would be seen in the eyes of GDPR, European Regulation 679/2016, which allows the processing of personal data only with consent given by the data subjects and also in the context of (online) games.
Consent in the context of the GDPR must be understood as an unambiguous indication of an informed and freely given choice by the data subject, relating to specific processing activities. The burden of proof that these criteria are fulfilled falls upon the controller (i.e., the game developer).
Google Play list the privacy condition of EA for its games, including The Sims Freeplay. Basically EA claims to use players data only to give them "better game experience", which seems vague but not less legit. The only less transparent thing I noticed is that the instructions to opt out of targeted marketing of in-game ads are in English and not in Italian: downloading the game, players allows EA to share their account information with third-party partners to customize advertising experience, which is basically all app developers do, but it's weird that the instruction to opt out doesn't have been translated at all!
This is not the first time EA is accused of, well, unethical commercial practice, since EA has been sentenced to pay fines by Austrian (2023) and Belgian (2018) civil court, because their FIFA loot boxes violated local gambling laws.
Moreover, it's important to notice that in January 2023, the European Parliament adopted a report calling for harmonized EU rules to achieve better player protection in the online video game sector.
The Parliament called for greater transparency from developers about in-game purchases: player should be aware of the type of content before starting to play and during the game. Also, players should be informed on the probabilities in loot box mechanisms, including information in plain language about what algorithms are devised to achieve.
The Parliament further stressed that the proposed legislation should assess whether an obligation to disable in-game payments and loot boxes mechanisms by default or a ban on paid loot boxes should be proposed to protect minors, avoid the fragmentation of the single market and ensure that consumers benefit from the same level of protection, no matter of their place of residence.
The Parliament highlighted problematic practices, including exploiting cognitive biases and vulnerabilities of consumers through deceptive design and marketing, using layers of virtual currencies to mask/distort real-world monetary costs, and targeting loot boxes and manipulative practices towards minors.
#vavuskapakage#ea#electronic arts#Ea sucks#the sims freeplay#the sims franchise#data breach#privacy violations#data privacy#data protection#data processing#gdpr#gdpr compliance#mobile games#fifa#Fifa 18#loot boxes#EA is trash#EA is evil#Ea is garbage
9 notes
·
View notes
Text
Understanding Privacy Breaches in India: A Growing Concern
Privacy breaches are becoming a prevalent yet gravely worrisome problem in today's increasingly digital world, especially in India, where a plethora of new cyber threats have been brought about by fast digitization. Data breaches are more dangerous than ever as more people rely on digital platforms for banking, retail, communication, and even government functions. Protecting personal information is essential for both individuals and businesses and not doing so can have dire repercussions. This blog explores the definition of privacy breaches, their effects, and self-defence measures. Any unauthorized access, sharing, or theft of personal information constitutes a privacy breach. This may occur as a result of a deliberate hacking attempt or an unintentional disclosure. Privacy breaches are frequently more personal in nature, focusing on sensitive information like your name, financial information, or private chats, in contrast to data breaches, which usually involve the exposure of vast amounts of data. Millions of people have been impacted by these breaches, which have increased in frequency in India, where internet penetration is rising quickly.
Data leaks are among the most prevalent kinds of privacy violations. When private information is unintentionally made public by inadequate security measures, it is referred to as a data leak. These breaches can happen when businesses neglect to encrypt private information, making it open to illegal access. For instance, millions of people's names, addresses, and identification numbers were made public in 2021 due to a huge database leak in India, raising serious concerns about fraud and identity theft. Unauthorized access is another frequent way that privacy is violated. Cybercriminals obtain unauthorized access to networks or accounts using a variety of methods. For example, phishing is a popular technique where attackers deceive victims into disclosing personal information or login passwords. The attacker can access private accounts, steal information, or even perpetrate financial fraud once they have this data. Phishing assaults have increased in India, where the perpetrators frequently impersonate reputable organizations, such as banks or government offices, in order to trick their victims. In India, identity theft is yet another common privacy violation. To impersonate someone, criminals take their personal information, including their Aadhaar number. They can start phony bank accounts, commit crimes, or make purchases using the victim's name using this stolen identity. This kind of privacy violation has become especially harmful to the victims, both financially and emotionally, as a result of the increased reliance on digital identification and financial systems.
Another important factor in privacy violations is social media. By excessively disclosing personal information on social media sites like Facebook, Instagram, and Twitter, many Indians unwittingly jeopardize their privacy. Social media breaches happen when hackers make use of publicly accessible information to obtain additional private information or coerce users into disclosing even more private information. Alarming facts support the growing trend of privacy breaches in India. Over 1.16 million cybercrimes were reported in India in 2020 alone, a large percentage of which entailed privacy breaches, according to recent data. Victims may suffer terrible financial and psychological costs, and the consequences are frequently permanent. Since more personal information is being kept online than ever before, there is a greater chance of breaches, which makes cybersecurity a critical concern for both individuals and companies. The effects of privacy violations are extensive. Individuals may experience financial loss, reputational harm, or identity theft as a result of data breaches. Knowing that criminals have access to their personal information frequently causes victims to feel anxious or distressed. The repercussions are just as bad for corporations. Legal issues, significant fines, and a decline in customer trust might result from a privacy violation. After a major breach, some businesses may be compelled to close since the harm to their brand is irreversible.
Preventive actions are crucial in the fight against privacy violations. People should exercise caution when using the internet by creating strong, one-of-a-kind passwords for every account, turning on two-factor authentication, and being careful about what they post on social media. In order to guard against vulnerabilities, it's also essential to update programs and software often. Businesses need to make investments in robust cybersecurity procedures, like encrypting confidential information, carrying out frequent security audits, and teaching staff members how to spot phishing scams.
In conclusion, privacy violations are becoming a bigger issue in India that impacts both people and businesses. The threats of cybercrimes will only rise as long as we continue to rely on digital platforms. We can reduce the possibility of falling victim to a privacy breach by being aware of the risks and adopting preventative measures to safeguard personal data. Keep yourself informed, remain safe, and safeguard your online privacy.
2 notes
·
View notes
Text
Unlocking the Potential of Solar Energy: The Role of Solar Management Dashboards

In the era of sustainable energy, solar power has emerged as a pivotal solution for reducing carbon footprints and harnessing renewable resources. As solar energy systems become more prevalent, effective management and optimization are essential to maximizing their benefits. This is where solar management dashboards come into play. These powerful tools offer comprehensive insights and control over solar energy systems, making them indispensable for both residential and commercial solar installations. In this article, we explore the significance of solar management dashboards, the role of solar management dashboard development, and the impact of solar management dashboard development services on the solar industry.
Understanding Solar Management Dashboards
A solar management dashboard is a centralized platform that provides real-time monitoring, analysis, and control of solar energy systems. These dashboards aggregate data from various components of a solar power system, including solar panels, inverters, batteries, and energy meters, to deliver actionable insights and streamline system management.
Key Features of Solar Management Dashboards:
Real-Time Monitoring: Dashboards offer live updates on the performance of solar panels, including energy production, system efficiency, and operational status. This allows users to track performance and detect issues promptly.
Performance Analytics: Advanced analytics tools within the dashboard provide insights into energy production trends, efficiency metrics, and system health. These insights help in optimizing performance and identifying areas for improvement.
Alerts and Notifications: Automated alerts notify users of potential issues such as equipment malfunctions, performance drops, or maintenance needs. This proactive approach helps in addressing problems before they escalate.
Energy Management: Dashboards facilitate the management of energy consumption and storage. Users can monitor energy usage patterns, track battery levels, and make informed decisions about energy distribution and consumption.
Reporting and Visualization: Customizable reports and visualizations help users understand system performance over time. Historical data analysis and graphical representations make it easier to assess the impact of solar energy on overall energy costs and savings.
The Importance of Solar Management Dashboard Development
The development of a solar management dashboard involves creating a user-friendly and feature-rich interface that effectively integrates with solar power systems. This development process is critical for ensuring that dashboards meet the specific needs of users and provide accurate, actionable data.
Key Aspects of Solar Management Dashboard Development:
Integration Capabilities: A well-developed dashboard must seamlessly integrate with various solar components and technologies. This includes compatibility with different types of solar panels, inverters, and energy storage systems.
User Experience (UX) Design: The dashboard should be designed with user experience in mind, offering an intuitive interface that simplifies navigation and data interpretation. A good UX design ensures that users can easily access and understand the information they need.
Data Accuracy and Security: Accurate data collection and transmission are crucial for reliable performance monitoring. Additionally, robust security measures must be implemented to protect sensitive data from unauthorized access or breaches.
Customization and Scalability: The dashboard should be customizable to fit different user requirements and scalable to accommodate future upgrades or expansions of the solar power system.
The Role of Solar Management Dashboard Development Services
Solar management dashboard development services play a crucial role in bringing these dashboards from concept to reality. These services offer specialized expertise in designing, developing, and deploying solar management solutions that cater to the unique needs of each solar energy system.
Key Benefits of Solar Management Dashboard Development Services:
Tailored Solutions: Development services provide customized dashboard solutions that align with the specific requirements of a solar power system, ensuring that the dashboard effectively meets the user's needs.
Expertise and Innovation: Leveraging the expertise of experienced developers and industry professionals, these services bring innovative features and technologies to the dashboard, enhancing its functionality and performance.
End-to-End Support: Development services offer comprehensive support throughout the entire process, from initial consultation and design to implementation and ongoing maintenance. This ensures that the dashboard remains functional and up-to-date.
Optimized Performance: By utilizing advanced development techniques and best practices, these services ensure that the dashboard delivers optimal performance, accuracy, and reliability in monitoring and managing solar energy systems.
Future Trends in Solar Management Dashboards
As technology continues to advance, the future of solar management dashboards holds exciting possibilities:
Enhanced AI and Machine Learning: Future dashboards will increasingly incorporate AI and machine learning algorithms to provide predictive analytics, automated adjustments, and advanced troubleshooting capabilities.
Integration with Smart Grids: The integration of solar management dashboards with smart grid technologies will enable more efficient energy distribution and enhance grid stability.
Advanced Data Visualization: Improved data visualization tools will offer more detailed and interactive representations of solar energy performance, making it easier for users to analyze and act on data.
User-Centric Innovations: Ongoing developments will focus on enhancing user experience, with features such as voice commands, mobile access, and personalized dashboards tailored to individual preferences.
Conclusion
Solar management dashboards are essential tools for optimizing the performance and efficiency of solar energy systems. With the growing importance of solar power in our quest for sustainability, the role of solar management dashboard development and solar management dashboard development services becomes increasingly critical. These dashboards not only provide valuable insights and control over solar power systems but also contribute to the overall success and effectiveness of renewable energy initiatives. As technology continues to evolve, embracing advanced dashboard solutions and development services will help maximize the potential of solar energy and drive us towards a more sustainable future.
2 notes
·
View notes
Text
How DLT is Changing the Way We Vote: A Look at Digital Voting Systems
Voting is a fundamental right in democratic societies. However, traditional voting systems have been plagued by issues such as voter fraud, low voter turnout, and long wait times. With the emergence of Distributed Ledger Technology (DLT), also known as blockchain technology, there is a growing interest in digital voting systems. In this blog post, we will explore how DLT is changing the way we vote and the potential benefits and challenges of digital voting systems.
What is DLT?
Before we dive into how DLT is changing the way we vote, let's first define what DLT is. DLT is a type of database distributed across a computer network. Each computer in the network has a copy of the database, and any changes to the database are recorded in a transparent and immutable way. This means that once data is recorded on the blockchain, it cannot be altered or deleted.
How DLT is Changing the Way We Vote
Digital voting systems that utilize DLT have the potential to revolutionize the way we vote. Here are some of the ways that DLT is changing the way we vote:
Increased Transparency and Security
One of the most significant benefits of digital voting systems that use DLT is increased transparency and security. DLT provides a secure and transparent platform for recording and counting votes. Each vote is recorded on the blockchain, and once recorded, it cannot be altered or deleted. This ensures that the voting process is secure and transparent, and it helps prevent voter fraud.
Increased Accessibility
Digital voting systems that use DLT can also increase accessibility. Traditional voting systems often require voters to be physically present at a polling station, which can be challenging for people with disabilities or those who live in remote areas. Digital voting systems can allow voters to cast their votes from anywhere, using a computer or mobile device. This can help increase voter turnout and make it easier for people to exercise their right to vote.
Increased Efficiency
Digital voting systems that use DLT can also increase efficiency. Traditional voting systems can be time-consuming and expensive to administer. Digital voting systems can automate many of the processes involved in voting, such as voter registration, ballot counting, and result reporting. This can help reduce the cost and time required to administer elections.
Potential Challenges
While digital voting systems that use DLT offer many potential benefits, some challenges need to be addressed. Here are some of the potential challenges:
Technical Challenges
Digital voting systems that use DLT require a high level of technical expertise to develop and maintain. This can be a challenge for some election authorities, especially those in developing countries or those with limited resources.
Security Concerns
While DLT provides a secure platform for recording and counting votes, there are still security concerns that need to be addressed. Hackers could potentially compromise the voting system, which could lead to voter fraud or other security breaches.
Privacy Concerns
Digital voting systems that use DLT also raise privacy concerns. Voters must be assured that their votes are anonymous and that their personal information is protected.
Conclusion
Digital voting systems that use DLT have the potential to revolutionize the way we vote. They offer increased transparency, security, accessibility, and efficiency. However, there are also potential challenges that need to be addressed. As DLT continues to evolve, we can expect to see more innovative digital voting systems emerge in the future.
#vote#pls vote#democracy#DLT#blockchain#BlockchainTechnology#digitalvoting#transparency#security#accesibility#efficiency#voterfraud#privacy#technical analysis#electionadminstration#turkey#general election#turkey2023generalelection
23 notes
·
View notes
Note
For me w socmed its like. Everyone acts like its this hugely necessary public utility where your presence and "engagement" is MANDATORY, like your face your name your historical takes for the communal lederboard, and its like. Ok yes facebook insta twitter and tik tok HAVE starved real reporting institutions etc at this point, but its also like. All the people for all those years screeching abt tweets and acting like twitter was this hugely relevant public square were largely working IN media!!! So its like ofc it was hugely important to them, but for me?? I didnt need to see endless puff-piece articles ginning up clap backs on twitter from 2015 onward. I dont have an account!! It didnt enter my life!! Until all these people manifested twitter as this essentially public utility. AND NONE OF IT!!!!! is necessary!!!!!! Or required!!!!! To live life!!! But increasingly they're making it harder and harder for that to be true. And its like. You Could Just Log Off. For the love of god!!!!!!!!!
I think that for this, as usual, we can blame Facebook, who made it MANDATORY to have your real name/picture and interact on the internet as your "real life" self (whatever that means). And yes, there is some limited amount of value in that since the 90s were consumed with the "Scary Internet Where Scary Unknown People Are Scary," but the idea that it will make people more responsible has turned out to be total BS. Instead, people WILL post the most heinous and reprehensible shit under their own names on Facebook/Twitter, and it has empowered them to do more of that/build monetized followings out of being totally vile turdburglars, rather than less. Because it turns out that when you build a machine that rewards the rats for being awful, it incentivizes them to be MORE awful, so yeah. That whole "using your real name promotes accountability!!!" turns out to be a total lie, and, uh. Meta/Facebook just got fined €1.2 BILLION (approximately $1.3 billion) in Ireland for breaching EU data privacy rules, so it's not like they did anything good with it.
And like... no. None of it IS necessary. Sure, it can be lots of fun, it plays to the inherent self-absorption of most people (often too much so, truly), it's a good way to keep in contact with casual acquaintainces/extended family/people you don't see often, and etc etc. But we don't NEED any of it. There are other communication tools that humans have used successfully for millennia, and especially since the owners of social media have consistently pushed a platform that prioritizes any kind of engagement at any cost, where facts, truth, and/or the basic framework of democracy and civic society doesn't matter against the almighty pursuit of profit, I'm really not sure at this point that there's any way to argue that it hasn't been corrosively destructive. Even if you do use it and take some value out of it, you still have to acknowledge that it exists in this horribly distorted paradigm in so many ways.
Social media is not going away, obviously, and attempts to regulate it often tend to veer too far into "destroy the internet" territory, especially as conservatives want to gut Section 230 and liberals haven't figured out how to meaningfully moderate it without signing onto bills that give a lot of room to deliberate bad actors. (SCOTUS did recently decline to dismantle Section 230, so things are staying the way they are, for now.) So... yeah. We still have to figure out how to live with it and to find some way to make it overall a useful tool again, rather than just a boundlessly destructive one.
19 notes
·
View notes
Text
Transforming the Health Landscape: The Global Blockchain in Healthcare Market

The integration of blockchain technology into the healthcare sector is revolutionizing the way medical data is managed, shared, and secured. As the demand for transparent, efficient, and secure healthcare services grows, blockchain offers promising solutions to longstanding challenges.
Understanding Blockchain in Healthcare
Blockchain Technology is a decentralized digital ledger that records transactions across multiple computers in a way that ensures the security and transparency of data. In healthcare, blockchain can be used to manage patient records, track pharmaceuticals, ensure the integrity of clinical trials, and streamline administrative processes. The immutable nature of blockchain helps in preventing data breaches, ensuring data accuracy, and enhancing patient privacy.
According to BIS Research, the Global Blockchain in Healthcare Market was estimated to grow to a value of $5.61 billion by 2025, and still the market is showing a steep growth till 2030 witnessing a double-digit CAGR growth rate throughout the forecast period.
Key Market Dynamics
Several factors are driving the growth of the global blockchain in healthcare market:
Data Security and Privacy:
Need for robust data security and privacy solutions.
Healthcare data breaches are a growing concern.
Blockchain's secure, immutable nature protects sensitive patient information.
Interoperability and Data Sharing:
Facilitates seamless data sharing between healthcare providers and systems.
Overcomes current interoperability issues.
Leads to better patient outcomes by providing a comprehensive view of health history.
Supply Chain Transparency:
Tracks the entire lifecycle of drugs in the pharmaceutical industry.
Ensures the authenticity of medications.
Helps combat counterfeit drugs.
Efficient Administrative Processes:
Streamlines various administrative processes, such as billing and claims management.
Reduces fraud and administrative costs.
Support from Regulatory Bodies:
Increasing support from regulatory bodies and governments.
Initiatives by FDA and EMA to explore blockchain for drug traceability and clinical trials boost market growth.
Request for an updated Research Report on Global Blockchain in Healthcare Market Research.
Global Blockchain in Healthcare Industry Segmentation
Segmentation by Application:
Data Exchange and Interoperability
Supply Chain Management
Claims Adjudication and Billing Management
Clinical Trials and Research
Others
Segmentation by End-User:
Healthcare Providers
Pharmaceutical Companies
Payers
Others
Segmentation by Region:
North America
Europe
Asia-Pacific
Latin America and Middle East & Africa
Future Market Prospects
The future of the global blockchain in healthcare market looks promising, with several trends likely to shape its trajectory:
Integration with AI and IoT: The integration of blockchain with artificial intelligence (AI) and the Internet of Things (IoT) will enhance data analytics, predictive healthcare, and real-time monitoring.
Expansion of Use Cases: New use cases for blockchain in digital healthcare will emerge, including patient-centered care models, personalized medicine, and enhanced telemedicine services.
Focus on Patient-Centric Solutions: Blockchain will enable more patient-centric healthcare solutions, empowering patients with greater control over their health data and enhancing patient engagement.
Development of Regulatory Frameworks: The establishment of clear regulatory frameworks and industry standards will facilitate the widespread adoption of blockchain in healthcare.
Conclusion
The Global Blockchain in Healthcare Industry is poised for significant growth, driven by the need for enhanced data security, interoperability, supply chain transparency, and efficient administrative processes. By addressing challenges related to regulatory compliance, implementation costs, standardization, and scalability, and leveraging opportunities in technological advancements, investments, partnerships, and government initiatives, the potential of blockchain in healthcare can be fully realized. This technology promises to revolutionize healthcare delivery, enhancing efficiency, transparency, and patient outcomes, and setting new standards for the future of digital health.
#Blockchain in Healthcare Market#Blockchain in Healthcare Industry#Blockchain in Healthcare Market Report#Blockchain in Healthcare Market Research#Blockchain in Healthcare Market Forecast#Blockchain in Healthcare Market Analysis#Blockchain in Healthcare Market Growth#BIS Research#Healthcare
2 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
Navigating the Landscape of Tax Preparation and Bookkeeping Services- A Guide to Choosing the Best Agencies
Tax preparation and bookkeeping are integral parts of running a successful business. However, for many entrepreneurs and business owners, these tasks can be daunting and time-consuming. That's where professional services come in handy. In cities like Perth, Brisbane, Sydney, Melbourne, Adelaide, and NSW, agencies like Account Cloud offer comprehensive tax preparation and bookkeeping services to alleviate the burden on businesses. But with so many options available, how do you choose the best agency for your needs? Here's a guide to help you navigate the landscape:
1. Assess Your Needs: Before you start your search for a tax preparation and bookkeeping service agency, it's essential to assess your needs. Determine the scope of services you require, such as tax filing, payroll processing, financial reporting, or general bookkeeping. Understanding your requirements will help you narrow down your options and find agencies that specialize in the services you need.
2. Experience and Expertise: When entrusting your financial matters to a third-party agency, it's crucial to ensure they have the necessary experience and expertise. Look for agencies with a proven track record in tax preparation and bookkeeping services. Consider factors such as the number of years in business, client testimonials, and the qualifications of their team members.

3. Industry Specialization: Different industries have unique tax and accounting requirements. Whether you're in retail, hospitality, healthcare, or any other sector, consider choosing an agency that specializes in serving businesses similar to yours. Industry-specific knowledge can ensure compliance with relevant regulations and optimize tax strategies tailored to your business.
4. Technology and Innovation: The accounting landscape is continually evolving, with advancements in technology reshaping how financial tasks are performed. Seek out agencies that embrace technology and leverage innovative solutions to streamline processes and enhance accuracy. Cloud-based accounting platforms, automation tools, and data analytics can significantly improve efficiency and decision-making.
5. Communication and Accessibility: Effective communication is key to a successful partnership with a tax preparation and bookkeeping agency. Choose an agency that prioritizes clear and transparent communication, keeping you informed about your financial status and any regulatory changes that may affect your business. Additionally, consider their accessibility and responsiveness to inquiries or concerns.
6. Compliance and Security: Compliance with tax laws and regulations is non-negotiable when it comes to financial matters. Ensure that the agency you choose adheres to the highest standards of compliance and stays updated with the latest regulatory changes. Moreover, prioritize security measures to protect sensitive financial information against unauthorized access or data breaches.
7. Scalability and Flexibility: As your business grows, your accounting needs may evolve as well. Select a tax preparation and bookkeeping agency that can scale its services according to your business growth. Whether you're a small startup or a large enterprise, flexibility in service offerings and pricing structures ensures that you receive tailored solutions aligned with your current and future needs.
8. Cost and Value: While cost is undoubtedly a factor in the decision-making process, it's essential to consider the value proposition offered by the agency. Instead of solely focusing on the lowest price, evaluate the services, expertise, and support provided in relation to the cost. A higher upfront investment in quality services can often yield long-term benefits and cost savings through improved financial management.
Choosing the best tax preparation and bookkeeping services agency requires careful consideration of various factors, including your specific needs, the agency's experience and expertise, industry specialization, technology adoption, communication practices, compliance standards, scalability, and cost-effectiveness. By conducting thorough research and due diligence, you can find a trusted partner like Account Cloud to handle your financial affairs efficiently, allowing you to focus on growing your business with peace of mind.
#Bookkeeping Services Melbourne#Bookkeeping Services Brisbane#Bookkeeping Services Perth#Perth Bookkeeping Services#Adelaide Bookkeeping Services#Online Bookkeeping and Accounting Perth#Online Bookkeeping Services Melbourne#Small Business Bookkeeping Services Brisbane#Small Business Bookkeeping Services Sydney#Small Business Bookkeeping Services Perth#Small Business Bookkeeping Services NSW#Premier Tax and Bookkeeping Adelaide#Tax and Accounting Services Brisbane#Tax and Accounting Services Sydney#Tax and Accounting Services Perth#Personal Tax Accountant Brisbane
2 notes
·
View notes
Text
A ransomware attack compromised the data of current and former employees at Canada's biggest bookstore chain, Indigo Books & Music Inc. says.
In a statement on its website, Indigo said the breach on Feb. 8 left no indication that personal customer information, such as credit card numbers, had been accessed, but that "some employee data was."
The Toronto-based retailer said it has contracted consumer reporting agency TransUnion of Canada to offer two years of credit monitoring and identity theft protection to workers at no cost.
Customers remain unable to make purchases online except for "select books," after Indigo halted website and app operations in what it referred to last week as a "cyberattack."
When the incident began more than two weeks ago, Indigo was only able to process purchases made in store with cash, but some of its services, including over-the-counter credit and debit payments as well as exchanges and returns, have since been restored. [...]
Continue Reading.
Tagging: @politicsofcanada
137 notes
·
View notes
Text
https://mediamonarchy.com/wp-content/uploads/2024/08/20240820_MorningMonarchy.mp3 Download MP3 Social insecurity, boulder dash and shitpost prison + this day in history w/Ray Roseberry and our song of the day by Tunnelmental on your #MorningMonarchy for August 20, 2024. Notes/Links: Protests erupt, Chicago businesses board up as the DNC kicks off Day 1 festivities; Democratic lawmakers will gather in Chicago, Illinois, this week for the 2024 DNC. Vice President Kamala Harris is slated to formally accept her party’s nomination on Thursday. https://www.foxnews.com/live-news/democratic-national-convention-2024-dnc-august-19-2024 HarrisWalz.com Domain Drama Ducks Question of Cybersquatting Law https://news.bloomberglaw.com/ip-law/harriswalz-com-domain-drama-ducks-question-of-cybersquatting-law The Ledger: How Layoffs Are Showing Up in Music Companies’ Earnings Reports https://archive.is/6agGm Bad bosses are pushing Gen Zers and millennials to the brink https://ca.finance.yahoo.com/news/bad-bosses-pushing-gen-zers-184655830.html Biggest shakeup to buying and selling a home in a century starts today https://www.dailymail.co.uk/yourmoney/property-and-mortgages/article-13735925/Biggest-shakeup-buying-selling-home-century-starts-today.html The death knell for broker fees! Homeowners to see BIG drop in selling costs after Realtors agree to eliminate notorious commission scheme and pay $418 million damages in landmark legal settlement https://www.dailymail.co.uk/yourmoney/housing-market/article-13201833/realtors-settle-eliminate-commission.html ✂️ Big rate-cut fall? https://sherwood.news/snacks/newsletters/big-rate-cut-fall/ Video: “Most People Have NO IDEA How Bad This Really Is” – Whitney Webb’s 2025 Final WARNING (Audio) https://www.youtube.com/watch?v=VVrWLNN-wpE Sheena Easton – “(She’s In Love) With Her Radio” (Vinyl //Audio) https://www.discogs.com/release/1799996-Sheena-Easton-Best-Kept-Secret // https://www.youtube.com/watch?v=M1LjFr7kOoI Here’s how to find out if your Social Security number was included in last week’s massive data breach https://fortune.com/2024/08/19/social-security-number-hack-were-you-included/ Google named their GPU Adreno…and we all know what they named their browser 😐 https://en.wikipedia.org//wiki/Adreno Classic NES Game Is Making a Comeback After 40 Years https://gamerant.com/classic-nes-game-boulderdash-remake-40-years/ Video: Boulder Dash for NES Game Review (Audio) https://www.youtube.com/watch?v=s3_QfShxCNk Waterworld – “Map” (Inst. // Audio) https://www.youtube.com/watch?v=4Kf_esaJUpA Man who called for asylum hotels to burn down jailed — as it happened; Defendants sentenced as prime minister pledges no let up in efforts to prevent more disorder https://www.thetimes.com/uk/crime/article/uk-riots-live-friday-latest-news-pfjb78g0v Man who encouraged torching hotels for asylum seekers in Britain gets 3 years in prison https://apnews.com/article/british-far-right-riots-sentencing-asylum-e3248eb20ea8c2c0e719e7617bc565b9 Video: Man jailed for stirring hatred on social media (Audio) https://www.youtube.com/watch?v=zWB2W_ADasc Alexander O’Neal – “Fake” (Vinyl // Audio) https://www.discogs.com/release/427059-Alexander-ONeal-Fake // https://en.wikipedia.org/wiki/Alexander_O’Neal // https://en.wikipedia.org/wiki/Fake_(Alexander_O%27Neal_song) // https://www.youtube.com/watch?v=vN1RYACiXNs #MorningMonarchy: August 20, 2018 – Actor Jim Carrey’s Art Goes Viral: “Our Missile, Our Crime” In Yemen https://mediamonarchy.com/20180820morningmonarchy/ #PumpUpThaVolume: August 20, 2018 ♬ The Holy Gasp & Death Valley Girls https://mediamonarchy.com/20180820pumpupthavolume/ #ThisDayInHistory/#MorningMonarchy: August 20, 2021 – The suspect, Ray Roseberry, has been live streaming the bomb threat at the Library of Congress on Facebook. He is demanding to talk to Joe Biden on the phone. (Audio) https://mediamonarchy.com/20210820morningmonarchy/ // https://vxtwitter.com/mediamonarchy/status/1428423030955380738 // https://twitter.com/...
#alternative news#cyber space war#media monarchy#Morning Monarchy#mp3#podcast#Songs Of The Day#This Day In History#tunnelmental
1 note
·
View note
Text
Decoding CISA Exploited Vulnerabilities

Integrating CISA Tools for Effective Vulnerability Management: Vulnerability management teams struggle to detect and update software with known vulnerabilities with over 20,000 CVEs reported annually. These teams must patch software across their firm to reduce risk and prevent a cybersecurity compromise, which is unachievable. Since it’s hard to patch all systems, most teams focus on fixing vulnerabilities that score high in the CVSS, a standardized and repeatable scoring methodology that rates reported vulnerabilities from most to least serious.
However, how do these organizations know to prioritize software with the highest CVE scores? It’s wonderful to talk to executives about the number or percentage of critical severity CVEs fixed, but does that teach us anything about their organization’s resilience? Does decreasing critical CVEs greatly reduce breach risk? In principle, the organization is lowering breach risk, but in fact, it’s hard to know.
To increase cybersecurity resilience, CISA identified exploited vulnerabilities
The Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) initiative was created to reduce breaches rather than theoretical risk. CISA strongly urges businesses to constantly evaluate and prioritize remediation of the Known Exploited Vulnerabilities catalog. By updating its list, CISA hopes to give a “authoritative source of vulnerabilities that have been exploited in the wild” and help firms mitigate risks to stay ahead of cyberattacks.
CISA has narrowed the list of CVEs security teams should remediate from tens-of-thousands to just over 1,000 by focusing on vulnerabilities that:
Been assigned a CVE ID and actively exploited in the wild
Have a clear fix, like a vendor update.
This limitation in scope allows overworked vulnerability management teams to extensively investigate software in their environment that has been reported to contain actively exploitable vulnerabilities, which are the most likely breach origins.
Rethinking vulnerability management to prioritize risk
With CISA KEV’s narrower list of vulnerabilities driving their workflows, security teams are spending less time patching software (a laborious and low-value task) and more time understanding their organization’s resiliency against these proven attack vectors. Many vulnerability management teams have replaced patching with testing to see if:
Software in their surroundings can exploit CISA KEV vulnerabilities.
Their compensatory controls identify and prevent breaches. This helps teams analyze the genuine risk to their organization and the value of their security protection investments.
This shift toward testing CISA KEV catalog vulnerabilities shows that organizations are maturing from traditional vulnerability management programs to Gartner-defined Continuous Threat Exposure Management (CTEM) programs that “surface and actively prioritize whatever most threatens your business.” This focus on proven risk instead of theoretical risk helps teams learn new skills and solutions to execute exploits across their enterprise.
ASM’s role in continuous vulnerability intelligence
An attack surface management (ASM) solution helps you understand cyber risk with continuous asset discovery and risk prioritization.
Continuous testing, a CTEM pillar, requires programs to “validate how attacks might work and how systems might react” to ensure security resources are focused on the most pressing risks. According to Gartner, “organizations that prioritize based on a continuous threat exposure management program will be three times less likely to suffer a breach.”
CTEM solutions strengthen cybersecurity defenses above typical vulnerability management programs by focusing on the most likely breaches. Stopping breaches is important since their average cost is rising. IBM’s Cost of a Data Breach research shows a 15% increase to USD 4.45 million over three years. As competent resources become scarcer and security budgets tighten, consider giving your teams a narrower emphasis, such as CISA KEV vulnerabilities, and equipping them with tools to test exploitability and assess cybersecurity defense robustness.
Checking exploitable vulnerabilities using IBM Security Randori
IBM Security Randori, an attack surface management solution, finds your external vulnerabilities from an adversarial perspective. It continuously validates an organization’s external attack surface and reports exploitable flaws.
A sophisticated ransomware attack hit Armellini Logistics in December 2019. After the attack, the company recovered fast and decided to be more proactive in prevention. Armellini uses Randori Recon to monitor external risk and update asset and vulnerability management systems as new cloud and SaaS applications launch. Armellini is increasingly leveraging Randori Recon’s target temptation analysis to prioritize vulnerabilities to repair. This understanding has helped the Armellini team lower company risk without affecting business operations.
In addition to managing vulnerabilities, the vulnerability validation feature checks the exploitability of CVEs like CVE-2023-7992, a zero-day vulnerability in Zyxel NAS systems found and reported by IBM X-Force Applied Research. This verification reduces noise and lets clients act on genuine threats and retest to see if mitigation or remediation worked.
Read more on Govindhtech.com
4 notes
·
View notes
Text
PROJECT HALF-A QR 1
Government Experiment AU where the Dan's (Dan/Danny/Dani) are created in a GIW lab to investigate the Ghost Zone after Jack and Maddie create the Ghost Portal. In this AU the GZ is radioactive and slowly kills any humans who venture inside so the GIW decide to create human ghost hybrids in order to further their research and capture additional subjects for their experiments. Masterpost.
GHOST INVESTIGATION WARD QUARTERLY REPORT Release Number: BH43-03 Date: 10 JANUARY 20XX Our research team has achieved the once-believed impossible: the establishment of a permanent gateway to the Ghost Zone. The collective expertise of Drs. Fenton has successfully breached the veil separating dimensions, unveiling the mysteries of the great beyond.
The Ghost Portal displays the capacity to establish a stable connection to an alternate dimension colloquially referred to as the "Ghost Zone." Once activated, the portal forms a transient gateway, allowing passage between our reality and the spectral realm. Upon activation, the portal began to emanate an otherworldly luminescence, casting an eerie green glow in the immediate vicinity. Spectrographic analysis indicates a continuous flux of ectoplasmic energy during operation. The portal's surface swirls with ectoplasmic energies and has been reported by some scientists to smell faintly of battery acid and lemons. This extraordinary scientific accomplishment, however, came at the cost of one Dr. Masters, as he found himself unwittingly within the portal's confines during its activation. The accident was attributed to the installation of the on-switch being within the portal itself—a detail overlooked in the course of standard operating procedures. Dr. Masters, who miraculously survived the incident, currently remains in critical care under intensive observation. Monitoring his condition may provide valuable insights into the repercussions of exposure to the spectral realm beyond the portal. Note: the Ghost Portal poses a significant potential for cross-contamination between dimensions, necessitating careful monitoring and containment protocols. Continued research is imperative to comprehend the full extent of its anomalous properties and implications for interdimensional exploration. RESEARCH AND EXPLORATION: Ongoing studies aim to understand the origin and properties of the Ghost Portal, as well as the nature of the Ghost Zone it connects to. Research teams equipped with specialized spectral analysis instruments are slated to conduct exploratory missions to gather data on the entities and phenomena within the alternate dimension in the near future. In preparation for the inaugural exploration of the Ghost Zone, Agents L, M, N, O, and P have volunteered for the mission. However, it is imperative to allocate additional Research and Development time for the fabrication of specialized equipment tailored for the unique challenges posed by extraplanar exploration. Further updates will follow as developments unfold. NEW SECURITY MEASURES: Due to the unpredictable nature of interdimensional travel, access to the Ghost Portal is restricted to authorized personnel only. The activation and deactivation of the Ghost Portal require Level 4 clearance and above, with any unauthorized usage subject to disciplinary actions. Additionally, in response to the discovery of entities within the Ghost Zone attempting to breach the Ghost Portal, a containment enhancement has been implemented. An Ectoranium Shield Wall, composed of a specialized alloy capable of repelling ectoplasmic entities, has been installed over the portal's exterior. This protective barrier acts as a deterrent, preventing denizens of the Ghost Zone from infiltrating our reality through the Ghost Portal. Personnel interacting with the Ghost Portal are required to undergo thorough spectral hazard training, including the proper utilization of Ectoranium containment protocols. The Shield Wall can be activated and deactivated through a designated control panel located in the containment chamber, allowing for secure exploration and research endeavors while minimizing the risk of unauthorized spectral entities entering our dimension.
#project halfa#dp fanfic#danny phantom#phanfic#danny phantom au#dp au#GIW#jack and maddie fenton#vlad masters#vlad plasmius#ghost investigation ward#H.A.L.F.A. = Hybrid Apparitional Life Form Agent#non canon compliant obviously its an au#exceeding the character limit for a tumblr post and having to break this into multiple parts? its more likely than u think#rip anyone only following for dc/batfam content its all dp tonight#thought of this while cleaning today and outlined or completely wrote like 10 entries for this already
6 notes
·
View notes