#Commandline
Explore tagged Tumblr posts
Text
I made a family tree for Midas and Lorenzo's closest relatives. More members may be added at some point, such as kids for Redux and his wife, but I haven't decided on any yet.
Lorenzo's biological mother is at the top, and the two below her are his adoptive parents. He ends up reconnecting with his bio mom, but his bio dad will never be in the picture, so I'm not going to bother adding him. I haven't found a skin for him anyway, and it's not important.
Jules's mother passed away and is obviously no longer with Midas, which is why there's a dotted line between them.

This was fun to make! I won't be doing this with most pairings, but Midas and Lorenzo are very special to me, and I want to include their family in content.
#Fortnite#Fortnite Headcanons#Midas#Lorenzo#Midas x Lorenzo#Midenzo#Aspen#Jules#Redux#Commandline#Wildstreak One#Deadlock#Amplitude#Convergence Captain#P.K.E. Ranger
8 notes
·
View notes
Text
How to dot matrix ascii art.
#dot matrix#ascii art#asciiart#retro tech#retrotech#oldschool#80s#90s#vintage#vintage hardware#dotmatrix#dot matrix printer#floppy disks#floppy disk#nostaliga#retrocomputing#retrocomputer#linux#command line#commandline#terminal#linux terminal
27 notes
·
View notes
Text
TYPO3 CLI Commands Explained – How to Manage Your Website Faster
Introduction
TYPO3 websites require regular maintenance tasks such as clearing cache, updating extensions, and managing users. Doing this manually in the backend takes time and effort. TYPO3 CLI commands allow you to perform these tasks quickly using the command line. This guide will cover the most useful CLI commands for TYPO3 website administrators.

Why You Should Use TYPO3 CLI Commands
Using CLI commands instead of the backend interface has major benefits:
Faster execution – A single command replaces multiple clicks in the backend.
Fewer errors – Direct commands reduce human mistakes.
Automation – CLI commands can be included in scripts to handle repetitive tasks.
More control – Advanced commands offer features not available in the backend.
How to Access TYPO3 CLI
Step 1: Open the Terminal and Navigate to TYPO3 Directory
Before using CLI commands, go to your TYPO3 installation folder.
Type: cd /path/to/typo3
Step 2: View All Available Commands
To list all commands, type: vendor/bin/typo3
Important TYPO3 CLI Commands
Clear Cache Remove old cache data to refresh the site: vendor/bin/typo3 cache:flush
List Installed Extensions View all installed TYPO3 extensions: vendor/bin/typo3 extension:list
Enable or Disable Extensions Activate an extension: vendor/bin/typo3 extension:activate extension_key Deactivate an extension: vendor/bin/typo3 extension:deactivate extension_key
Reset a TYPO3 Backend User’s Password If a user is locked out, reset their password: vendor/bin/typo3 backend:resetpassword username
Create a New TYPO3 Admin User To add a new backend admin: vendor/bin/typo3 backend:user:create --username=newuser --password=newpassword [email protected]
Update Language Packs Refresh TYPO3’s translation files: vendor/bin/typo3 language:update
List All TYPO3 Websites To see all configured websites: vendor/bin/typo3 site:list
Advanced TYPO3 CLI Commands
Update Database Schema
For database updates after installing an extension, run: vendor/bin/typo3 database:updateschema
Execute Scheduled Tasks
Manually run TYPO3’s scheduler: vendor/bin/typo3 scheduler:run
Real-Life Examples of Using TYPO3 CLI
Clear cache quickly after making changes Instead of navigating the backend, simply run: vendor/bin/typo3 cache:flush
Reset a forgotten backend user password If a user is locked out, type: vendor/bin/typo3 backend:resetpassword admin
Automatically update all language files Keep translations up to date by running: vendor/bin/typo3 language:update
Final Thoughts
TYPO3 CLI commands are powerful tools for website administrators and developers. They save time, reduce errors, and make website management more efficient.
By learning and using these commands, you can streamline your TYPO3 workflow and manage websites like a pro! 🚀
0 notes
Text
Linux Filesystem Fundamentals: A Must-Know for DevOps Engineers 🐧🚀
Master the backbone of Linux systems with this in-depth guide to Linux filesystem fundamentals. Perfect for DevOps engineers and beginners, this guide covers everything from the basic directory structure to essential commands for managing and troubleshooting filesystems.
✨ What You’ll Learn:
The hierarchy of the Linux filesystem
Key directories like /etc, /usr, and /var
Must-know commands: ls, df, chmod, and more
Best practices for managing and securing files
Take your Linux and DevOps skills to the next level today! 💻 👉 Read the full guide here
#coding#linux#programming#LinuxFilesystem#DevOps#DevOpsEngineer#LearnLinux#OpenSource#information technology#CommandLine#TechSkills#SysAdmin#arch linux#linuxposting
1 note
·
View note
Text
How to Check Host Name in Command Prompt?

Quick tip: Step-by-step guide to checking your hostname in Command Prompt. Simple and clear!
0 notes
Text
Useful commands for your Mac
A living post about commandline tools for your Mac. Episode 1: Set your hostname on zsh. #apple #terminal #cli #zsh
Terminal is one of my favorite applications in the Mac and I’ve been getting familiar with zsh. This post is a living post where I will keep updating what I learn on the commandline. Update hostname What’s the hostname? The word that shows up right after your username if you open “Terminal.” mac OS used to update the hostname when you update the Computer Name: Settings > General > About Or…
View On WordPress
0 notes
Text
What Kind of Tools Should I Use as a Beginner Software Developer
What Kind of Tools Should I Use as a Beginner Software Developer. Embarking on the journey as a novice in the realm of software development opens up a world filled with both excitement and challenges. The vast array of development tools available can be both thrilling and overwhelming, as each tool serves a unique purpose in the multifaceted process of building software. The significance of selecting the right set of tools cannot be overstated, as it plays a pivotal role in shaping your development experience. These tools are not mere accessories but powerful instruments that directly impact your productivity, facilitate seamless collaboration with others, and contribute to the overall quality of your code.
Read Full Content Here 👇👇
What Kind of Tools Should I Use as a Beginner Software Developer

#SoftwareDevelopment#CodingTools#IDE#VersionControl#Collaboration#CommandLine#TextEditors#DatabaseManagement#Documentation#TestingFrameworks#Containerization#ProjectManagement#ContinuousLearning#WebDevelopment#ProgrammingLanguages#automotive tools#programming tools
0 notes
Text
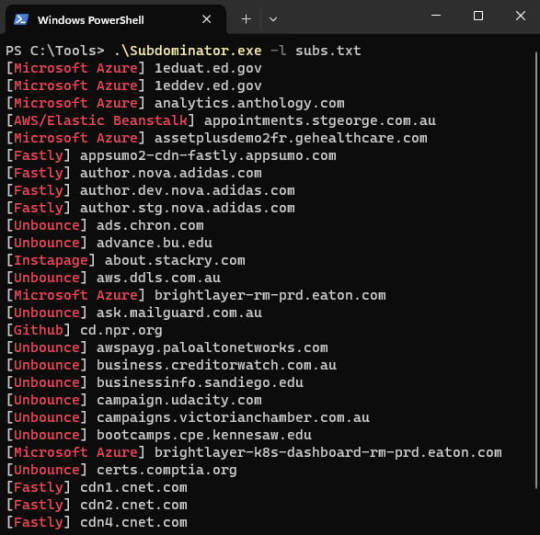
Subdominator: Open-source tool for detecting subdomain takeovers - Help Net Security
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools. “Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or…
View On WordPress
0 notes
Text
youtube
0 notes
Text
"git sweep" Alias - Delete All Local Branches Linked To Deleted Remote Branches With Just One Command!
I used to waste so much time deleting local and remote branches I was done with.
Now I just delete my remote branches (e.g. on GitHub) then run this command:
git sweep
and just like that, my local branches that track remote branches are automatically deleted!
Now let's go over how you can add this command...
What is "git sweep"?
"git sweep" is a git alias I created that is a shortcut that does the following:
Runs the "git fetch --prune" command to delete all references to remote branches.
Find local branches linked to deleted remote branches (these are marked as "gone") then deletes them.
Setting the alias
You can set it using the "git config" command or by editIng the git config file directly.
Here's the command to set the alias with the "git config" command:
git config --global alias.sweep "! git fetch -p && git for-each-ref --format '%(refname:short) %(upstream:track)' | awk '\$2 == \"[gone]\" {print \$1}' | xargs -r git branch -D"
Here's an example of what the config file should look like with the alias added:
[alias] sweep = ! "git fetch -p && git for-each-ref --format '%(refname:short) %(upstream:track)' | awk '$2 == \"[gone]\" {print $1}' | xargs -r git branch -D"
Conclusion
Check out Erik Schierboom's article on this to learn more about how all of this works in detail.
If you found this post useful in anyway, please like, repost and/or share it.
Thanks for reading!
#programming#git#github#repository#repositories#coding#commandline#command line#linux#open source#opensource#computerscience#computer science
0 notes
Text


Nirvana in Fire | Ep 49
A remake of this gifset.
#nirvana in fire#circ gifs#remake#mei changsu#xiao jingyan#the original gifs were made purely with commandline and Preview#they weren't that bad considering
423 notes
·
View notes
Note
man, sorry sonic riders is horting you so bad :(
you provide an incredible service, so here's to hoping it will become soawesome! or that it will atleast hort so good instead of so bad!!
🎵hort so good🎵
🎵c'mon bby make it hort, so, good🎵
(thank you, by the way. for pushing through the hort for others' sake. i think that's the definition of a hero)
okay this genuinely got a giggle out of me thank you
#thank you mysterious benefactor 🫡#I thiiinkkkkk I either used the wrong command in the commandline OR its an issue with the xno files#hopefully the former bc the latter would require me to cross-reference the gamecube files which will take longer. and I dont wanna do that#I'll figure it out. no game engine in the universe is going to stop me#ask#anon#thank you for the ask!
3 notes
·
View notes