#Business Server Data Backup
Explore tagged Tumblr posts
Text
How to Install Unraid NAS: Complete Step-by-Step Guide for Beginners (2025)
If you’re looking to set up a powerful, flexible network-attached storage (NAS) system for your home media server or small business, Unraid is a brilliant choice. This comprehensive guide will walk you through the entire process to install Unraid NAS from start to finish, with all the tips and tricks for a successful setup in 2025. Unraid has become one of the most popular NAS operating systems…
#2025 nas guide#diy nas#home media server#home server setup#how to install unraid#network attached storage#private internet access unraid#small business nas#unraid backup solution#unraid beginner tutorial#unraid community applications#unraid data protection#unraid docker setup#unraid drive configuration#unraid hardware requirements#unraid licencing#unraid media server#unraid nas setup#unraid parity configuration#unraid plex server#unraid remote access#unraid server guide#unraid troubleshooting#unraid vpn configuration#unraid vs synology
1 note
·
View note
Text
Future Applications of Cloud Computing: Transforming Businesses & Technology
Cloud computing is revolutionizing industries by offering scalable, cost-effective, and highly efficient solutions. From AI-driven automation to real-time data processing, the future applications of cloud computing are expanding rapidly across various sectors.

Key Future Applications of Cloud Computing
1. AI & Machine Learning Integration
Cloud platforms are increasingly being used to train and deploy AI models, enabling businesses to harness data-driven insights. The future applications of cloud computing will further enhance AI's capabilities by offering more computational power and storage.
2. Edge Computing & IoT
With IoT devices generating massive amounts of data, cloud computing ensures seamless processing and storage. The rise of edge computing, a subset of the future applications of cloud computing, will minimize latency and improve performance.
3. Blockchain & Cloud Security
Cloud-based blockchain solutions will offer enhanced security, transparency, and decentralized data management. As cybersecurity threats evolve, the future applications of cloud computing will focus on advanced encryption and compliance measures.
4. Cloud Gaming & Virtual Reality
With high-speed internet and powerful cloud servers, cloud gaming and VR applications will grow exponentially. The future applications of cloud computing in entertainment and education will provide immersive experiences with minimal hardware requirements.
Conclusion
The future applications of cloud computing are poised to redefine business operations, healthcare, finance, and more. As cloud technologies evolve, organizations that leverage these innovations will gain a competitive edge in the digital economy.
🔗 Learn more about cloud solutions at Fusion Dynamics! 🚀
#Keywords#services on cloud computing#edge network services#available cloud computing services#cloud computing based services#cooling solutions#cloud backups for business#platform as a service in cloud computing#platform as a service vendors#hpc cluster management software#edge computing services#ai services providers#data centers cooling systems#https://fusiondynamics.io/cooling/#server cooling system#hpc clustering#edge computing solutions#data center cabling solutions#cloud backups for small business#future applications of cloud computing
0 notes
Text
What Should You Look for in a NAS?
In today’s digital world, data storage and security are essential, both for personal and business use. Whether you have a growing library of family photos, critical work documents, or media collections, a reliable storage solution is paramount. Network-Attached Storage (NAS) systems offer an efficient way to store, back up, and access data across devices from anywhere. But with so many NAS…
#10GbE#automatic backup#Backup#business NAS#business storage#Cloud Integration#cloud sync#data protection#data redundancy#data storage#drive capacity#encryption#energy-efficient NAS#file backup#file syncing#file versioning#hardware encryption#home NAS#hot-swappable drives#media server#media streaming#multimedia storage#NAS#NAS bays#NAS comparison#NAS cost#NAS CPU#NAS device#NAS features#NAS guide
0 notes
Text
The Making of a Villian - Chapter 1
The WayneTech board meeting was scheduled for 9:00 a.m.
By 9:03, their encrypted systems were silently bleeding data into a private offshore server. No alarms. No alerts. Just a quiet, surgical extraction—clean, undetectable, and irreversible.
You watched from a dusty rooftop across the street, sipping coffee like any civilian on a break. Except your hands weren’t shaking, and your eyes never left the mirrored windows reflecting a city that forgot you.
It wasn’t about the files. Not really. You’d already read them—twice—before deleting the backups. What mattered was what came next: one carefully altered blueprint. A subtle change in the emergency lockdown protocols, buried deep in the code. Harmless… until the moment someone needed them most.
You didn’t need chaos. Not yet.
You needed doubt.
Down below, Bruce Wayne’s car pulled into the underground garage. Right on schedule. You watched as security greeted him with smiles and clipped nods.
They didn’t know.
No one ever did—until it was too late.
You slipped the burner phone back into your pocket and turned away from the skyline. One step. Then another. Quiet boots on concrete. No capes. No flashy suits. Just a face they’d stopped looking at long ago.
But you were done being invisible.
Your game had just begun.
It hadn’t always been like this. You remembered your first week training with them. You’d shown up early—excited, eager to learn. Tim had offered a nod. Dick had smiled. Barbara barely looked up from her console.
You thought they were just busy. That maybe, in time, you’d earn your place. That if you just proved yourself…
And you did. Over and over again.
Yet somehow, you were always the footnote. The cautionary tale. “Don’t be like them,” Bruce had once said to Damian during a sparring match. You’d laughed it off then. Told yourself he meant your form. Not you.
You knew better now.
You remembered a moment not long ago: standing in the Batcave, trying to offer insight into an unfolding hostage situation. You had mapped out a possible escape route—one they didn’t see. You weren’t loud. You didn’t shout over anyone. You just slid the schematic across the table. Bruce didn’t even glance at it. Tim talked over you. And when the building collapsed—when things went wrong—no one asked why.
Just a quiet, disappointed look. A cold shoulder. Another mark against your record.
You weren’t angry anymore. Not really.
Just focused.
You stepped onto the street and vanished into the crowd. No one looked twice.
Perfect.
They wanted a ghost. They’ll get one.
But not the kind they can exorcise. Not a whisper or a shadow. You’ll become something worse.
Something undeniable.
You passed a newsstand on your way to the subway. The headlines blared about another WayneTech breakthrough. Another miracle. Another story that never had your name in the footnotes, even though you remembered the late-night sessions, the endless trial runs they’d let you conduct just to see if the theories held.
And they had. But it hadn’t mattered.
You dipped underground, swiping a fake MetroCard as you passed the gate. A man bumped into you—apologized quickly. You nodded, saying nothing, and slipped the tracker into the fold of his coat pocket. It wasn’t personal. He was just the next piece. A courier. Unwitting. Useful.
Your network was small. Precise. Built on favors, blackmail, and anonymous generosity. They didn’t know you—and you liked it that way. Your face was forgettable, and you’d sharpened that into a weapon.
As the train sped through the tunnels, you stared at your reflection in the window. The person looking back wasn’t a villain yet.
But they were getting close.
You smiled—just a little.
“Soon,” you murmured.
This wasn’t about revenge.
It was about recognition. About truth. About making them see the cracks they’d built their empire on—starting with you.
And when it all came tumbling down, you’d be standing at the center, calm and untouchable, while they scrambled to remember where it all went wrong.
Right here.
Right now.
And by then, it would be far, far too late.
------------------------------------------------------------------------------ Finished both Chapter 0 and Chapter 1 around the same time and figured I'd post them both.
Let me know what you guys think of this and if I should turn it into a full on fic or just post bits and pieces every once in awhile.
63 notes
·
View notes
Text
**Maximizing Efficiency: The Role of Managed IT Services in New York’s Healthcare and Finance Sectors**
Introduction
In the bustling landscape of New York City, in which the heart beat of finance and healthcare syncs with the rapid improvements in expertise, controlled IT prone have emerged as a pivotal solution for potency. As organizations grapple with https://jsbin.com/ the complexities of facts technological know-how, from cybersecurity to documents leadership, the integration of controlled IT companies promises a pathway to streamline operations. This article delves into Maximizing Efficiency: The Role of Managed IT Services in New York’s Healthcare and Finance Sectors, exploring the myriad merits these services and products grant, distinctly within two of the city’s most necessary sectors.
Table of Contents
" style="max-width:500px;height:auto;">
youtube
Understanding Managed IT Services The Importance of IT in Healthcare The Role of IT in Finance Cybersecurity Challenges in NY's Sectors NIST Guidelines for Security Management HIPAA Compliance by means of Managed Services GDPR Considerations for Financial Institutions Cloud Services: A Game Changer for SMBs Network Infrastructure Optimization Data Backup Solutions and Their Importance Endpoint Detection and Response Technologies Managed Detection and Response (MDR) Explained Penetration Testing: Strengthening Defenses SIEM Solutions for Real-time Monitoring Project Management Tools in IT Services The Power of Outsourcing Helpdesk Support Security Architecture Best Practices The Impact of Downtime on Business Operations Streamlining Operations with Technology Consulting Choosing the Right Managed Service Provider (MSP) Amazon Web Services vs Microsoft Azure for Health Data Effective Communication inside of Tech Teams Case Studies: Success Stories from NYC Businesses The Future of Managed IT Services in NYC's Sectors Conclusion and Key Takeaways Understanding Managed IT Services
Managed IT services and products are a complete suite designed to offer organisations with technical aid and strategic guidance on their science infrastructure and operations.
What Are Managed IT Services?
At its core, controlled IT prone surround a variety of strategies that let corporations to outsource their documents technological know-how wishes to a third-birthday celebration issuer or controlled carrier provider (MSP). This can consist of every little thing from community monitoring, server administration, knowledge storage solutions, cloud prone, cybersecurity measures, to helpdesk enhance.
Why Choose Managed IT Services?
For many organisations, tremendously small to medium-sized organisations (SMBs), dealing with an internal IT workforce will likely be overwhelming through funds restraints and useful resource limitations.

Cost-Effective: By outsourcing those applications, providers can drastic
2 notes
·
View notes
Text
I'd rather have been asleep at 1:40am instead of laying there thinking about how uncertain and scared I feel right now, but I was laying there feeling uncertain and scared and realized I have no idea what people that work in offices DO.
I've only worked retail/customer service outside of the military and even while working in an office in the military, I had nothing to do.
At first I was put in one office that didn't need me so they just said "Here... Manage these files." and I was like "..... how, exactly??" and ended up retyping the labels for all of them because some were wrong and there was nothing else for me to do.
Then they gave me the personnel database. I rebuilt it and made it accessible in two days, and that was it. After that, I filled out orders for one person once. The only way I had anything to DO was by becoming the mail clerk which is another customer-facing, cyclically repetitive task that is never done and needs redone in the same way every day. After the mail was done, which took about two hours, I would leave or go sit in my office with nothing to do because the database was my whole job and it was DONE. It wouldn't need changed until the software was updated and that wouldn't be for years.
I had a once-a-week task of making a physical copy of the server which meant going into a closet, popping a tape into a machine, and waiting. I had to sit there with it. There was nothing else to do. I got in trouble for coloring in a coloring book while waiting for the backups to write and I was like "........ What am I SUPPOSED to do, then?????" "Work on the database!" "It's DONE........"
If it's SQL stuff do people sit around until the boss says "Hey, I need to know how much we spent on avocado toast this month." and then whip up a report real quick and wait for the boss to want a report on something else? What about when the boss doesn't need a report?
What do IT people do when things are working smoothly?
I can understand data entry, that would be like "Here we have all these waivers that were signed for the indoor trampoline business and these need plugged into the database manually because the online one was down so they're on paper." or something like that but what about when the online waivers do work what do they do then?
?????
It's like that episode of Seinfeld where George gets an office job but just sits there all day because he has no idea what he's supposed to be doing, no one tells him, and he eventually gets fired because he didn't do anything.
13 notes
·
View notes
Text
Key Features to look for in Magento Hosting for Maximum Performance
Choosing the right hosting for a Magento store is quite an important issue to ensure a fast, secure, and seamless shopping experience. The following are the key features to look for in Magento hosting for maximum performance:
1. Speed and Performance Optimization: Advanced performance features of Magento hosting should include SSD storage, inbuilt caching like Varnish, and CDNs. These will help boost your website's loading speed so customers won't quit over delays. Search for hosting providers whose servers are optimized for the special demands of Magento.
2. Scalability: Your hosting should grow with your business. Find a solution to handle sudden traffic increases, especially when you run sales or special promotions. Look for scalable resources from cloud hosting, such as AWS or Google Cloud, to maintain smooth operations during heavy loads.
3. Magento Specific Support: Hosting with Magento expertise is vital. It is good to have Magento dedicated support, server configurations specifically for Magento, and compatibility with the latest Magento versions to ensure any problems are dealt with quickly and the sites stay up.
4. Robust Security Features: Since eCommerce remains the main target for cyber-attacks, your hosting should include firewalls, SSL certificates, DDoS protection, and malware scanning. Secure hosting means keeping the sensitive information of customers safe and preserving one's business reputation.
5. Easy Backup and Recovery: Downtime or loss of important data is something catastrophic. Hence, make sure the hosting package you choose covers automatic backup every day and that these are recoverable through a simple process. This provides business continuity, even on unplanned eventualities.

Focus on these features, and you will be able to choose Magento hosting that will add to the performance, reliability, and security of your store to ensure the success of your business in the competitive online market.
https://mageleven.com/
3 notes
·
View notes
Text
Choosing the Right Hosting for High-Traffic WordPress Sites
When it comes to running a high-traffic WordPress site, choosing the right hosting provider can make all the difference. Whether you're running an eCommerce store, a blog, or a business website, performance, speed, and reliability should be your top priorities. Here's a breakdown of the factors to consider when selecting a hosting plan for your high-traffic WordPress site.
1. Scalability is Key
For high-traffic sites, scalability is essential. Look for a hosting provider that offers scalable solutions, such as cloud hosting or VPS, which can handle traffic spikes and provide additional resources when needed. This flexibility ensures that your site stays fast and responsive even during peak traffic times.
2. Uptime Guarantee
Downtime can be catastrophic for any website, especially one that relies on high traffic. Choose a hosting provider that offers a 99.9% uptime guarantee. This ensures that your site is accessible to visitors at all times, minimizing potential revenue loss.
3. Content Delivery Network (CDN)
A CDN can drastically reduce loading times for visitors from different geographical locations. By caching your content on servers around the world, a CDN ensures your site loads quickly no matter where the visitor is located.
4. Fast and Reliable Customer Support
Technical issues can arise at any time, especially when managing a high-traffic site. Ensure that your hosting provider offers fast and reliable customer support, ideally 24/7, to help resolve any issues quickly and efficiently.
5. Optimized for WordPress
For WordPress sites, it’s crucial to choose a hosting provider that specializes in WordPress optimization. Managed WordPress hosting services offer automated updates, enhanced security, and WordPress-specific performance optimizations, which can make a significant difference in site performance and security.
6. Security Features
With high traffic, your website is more likely to attract hackers. Ensure your hosting provider offers robust security measures like SSL certificates, firewalls, malware scanning, and automatic backups to protect your site and data.
To read the full guide, visit: Choosing the Right Hosting for High-Traffic WordPress Sites
#hosting#vps hosting#cloud hosting in saudi arabia#web hosting#cloud hosting service#web development#doamin and hosting bd
3 notes
·
View notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
2 notes
·
View notes
Text
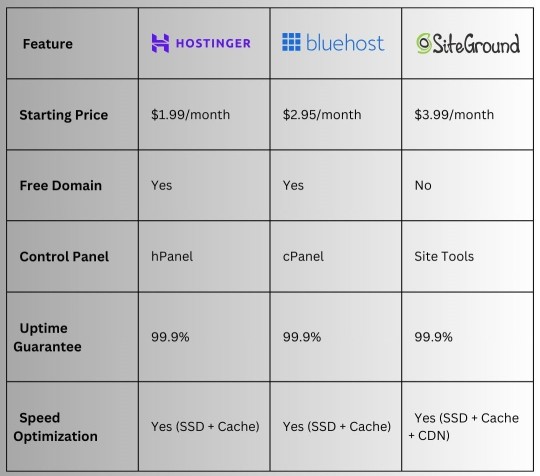
Unbeatable Value: Why Hostinger is the Best Choice for Affordable Web Hosting

Did you know Hostinger now offers a Biggest ever Black Friday sale Up to 85% off hosting + website builder + Extra Flat 20% discounts on all hosting plans? This amazing deal shows Hostinger's strong commitment to quality and value. They want to help everyone, from small businesses to website dreamers, without costing too much.
Key Takeaways
Hostinger offers an unbeatable Extra Flat 20% discount on all hosting plans
Hostinger is a top-rated web hosting provider known for its affordable yet reliable services
Hostinger's hosting plans cater to a wide range of users, from small businesses to large enterprises
Hostinger's commitment to quality and performance ensures a seamless online experience
Hostinger's user-friendly interface and extensive features make website management a breeze
Understanding Hostinger's Web Hosting Services
Hostinger has many website hosting plans for businesses and people. They offer budget-friendly hosting and WordPress optimized hosting too.
Shared Hosting Solutions
Hostinger's shared hosting is great for beginners or small sites. It's budget-friendly with weekly backups, free SSL, and 24/7 support.
Cloud Hosting Options
Hostinger's cloud hosting is scalable and strong. It has instant resources, automatic backups, and top security. It's perfect for growing businesses.
WordPress Specialized Hosting
Hostinger has WordPress optimized hosting for WordPress users. It comes with WordPress pre-installed, automatic updates, and server tweaks for smooth running.
Hostinger has many website hosting plans for all needs. They focus on being affordable, fast, and reliable. They aim to make customers happy and keep improving.
Why Hostinger is the Best Choice for Affordable Web Hosting

Biggest ever Black Friday sale
Up to 85% off hosting + website builder + Extra Flat 20% discounts
Hostinger is great for reliable hosting that's easy on your wallet. It offers fast web hosting at a good price. This makes it a favorite for both businesses and individuals.
Hostinger is known for its affordable prices without losing quality. It uses the latest tech and efficient systems. This means you get lots of features for a low cost.
But it's not just about the price. Hostinger focuses on speed and has a big network of data centers. Your site will load fast and work well everywhere. This makes your site better for visitors and helps your business grow.
"Hostinger's reliable hosting and lightning-fast speeds have been a game-changer for my business. It's the perfect balance of affordability and top-notch performance."
Hostinger also has an easy-to-use interface and lots of tools. You can easily set up your site with one-click installers and website builders. This makes it simple for anyone to start their online presence.
Hostinger is good for anyone, from small businesses to big companies. Its cheap web hosting offers great value. It's the best choice for affordable web hosting without losing quality.
Cutting-Edge Performance and Speed Features
At Hostinger, we know fast web hosting is key for a great user experience. We've got top-notch features to make your websites super fast. Our LiteSpeed web servers, global data centers, and caching solutions make sure your fast web hosting needs are met.
LiteSpeed Web Servers
Our web hosting uses LiteSpeed web servers. They're super efficient and handle lots of traffic well. Your websites will load fast, giving your visitors a smooth and secure hosting services experience.
Global Data Center Network
Our data centers are all over the world. This means your websites are close to your visitors. You get faster load times and a better user experience, no matter where they are.
Built-in Caching Solutions
Our web hosting plans have advanced caching solutions that boost your website's speed.
LiteSpeed Cache and Redis Cache reduce server load and page load times. Your visitors will have a smooth experience.
These caching solutions work in the background. They make sure your website is always fast, without you having to do anything.
With Hostinger's top performance and speed features, your websites will load super fast. This will make your online presence shine and give your visitors a great experience.
Security and Reliability Measures
At Hostinger, we know how important it is to keep your website safe and running well. That's why we have many security features and ways to keep your site up and running. This helps your business grow and succeed online.
Robust DDoS Protection
Our hosting services have strong DDoS protection. This keeps your website safe from bad attacks that could stop it from working. Our system watches for and blocks bad traffic, so your site stays open and your customers happy.
Secure SSL Certificates
All our plans include free SSL certificates. This means your website's data and talks are safe from others seeing them. It's key for making your visitors trust you and keeping their private info safe.
Reliable Data Backup and Restoration
Hostinger backs up your website data often, so you're safe if something goes wrong or data gets lost.
With just one click, you can bring back your website to a time before problems started. This cuts down on lost time and keeps your business running smoothly.
Uptime Guarantee
We're proud of how reliable our hosting is, which is why we promise 99.9% uptime. This means your website will be open for your customers all the time. You can focus on making your online business bigger without worrying about it going down.
At Hostinger, we're all about giving you safe and reliable hosting. Our strong security and dependable setup mean your website is in great hands. This lets you focus on making your online business a success.
User-Friendly Interface and Website Management Tools
At Hostinger, we know web hosting can be hard for some. Especially for those new to the web. That's why we made our control panel and website management tools easy to use. Now, anyone can create and manage their website easily.
hPanel Control Panel Overview
Our hPanel is a dashboard that lets you control your web hosting. It's easy to use and navigate. You can manage your domains, websites, and emails all in one place.
Whether you're a pro or new to websites, hPanel makes it easy. It helps you work smoothly and efficiently.
One-Click Installers
Hostinger's one-click installers make it easy to set up CMS like WordPress, Joomla, and Drupal.
With just a few clicks, you can start your WordPress-optimized hosting and bring your ideas to life.
No need for technical skills. Our tools do the hard work, so you can focus on your website.
Website Builder Integration
For those who like a guided website creation, Hostinger has a website builder. It lets you make professional-looking websites without coding. You can build a blog, store, or corporate site easily and enjoyably.
Feature
Benefit
User-friendly control panel
Streamlined website management and easy access to all your hosting tools
One-click installers
Quickly set up popular CMSs like WordPress with no technical expertise required
Integrated website builder
Design professional-looking websites using a drag-and-drop interface
At Hostinger, we want to help our customers succeed online. Our easy-to-use interface and website management tools make hosting smooth, no matter your skill level. Start your online journey with Hostinger today.
Pricing Plans and Special Offers
Hostinger is a top choice for cheap web hosting and budget-friendly hosting. They offer many website hosting plans to fit different needs.
Now, Hostinger has a Biggest ever Black Friday sale
Up to 85% off hosting + website builder + Extra Flat 20% discounts
on all plans. This makes their prices even better for those looking for cheap web hosting.
Shared Hosting Plans
Hostinger's shared hosting starts at $0.99 per month. It's ideal for small businesses and individuals. You get a free domain, SSL, and lots of storage and bandwidth.
Cloud Hosting Solutions
For more power, Hostinger's cloud hosting is great. Prices range from $3.99 to $15.99 per month. It's perfect for growing businesses and big websites.
WordPress Specialized Hosting
Hostinger has special plans for WordPress users. Starting at $1.99 per month, they're optimized for WordPress. This means your WordPress site will run smoothly.
Hostinger has many website hosting plans for all budgets. With the
Extra Flat 20% discounts , it's a great choice for affordable web hosting.
Conclusion
Hostinger is the top pick for affordable web hosting. It offers fast performance and strong security. Plus, it's easy to use.
Hostinger has many hosting options. You can choose from shared, cloud, or WordPress hosting. It also has 24/7 support and special deals.
Hostinger is dedicated to giving you the best web hosting experience. Choose Hostinger for a great start online. You'll be in good hands.
FAQ
What makes Hostinger the best choice for affordable web hosting?
Hostinger offers great hosting at low prices. It's perfect for those who want reliable and cheap web hosting. Their value, performance, and easy-to-use interface make Hostinger a top pick.
What types of hosting services does Hostinger offer?
Hostinger has many hosting services. You can choose from shared hosting, cloud hosting, or WordPress hosting. Each type meets different needs, so you're sure to find what you need.
How does Hostinger ensure fast and reliable performance?
Hostinger uses fast web servers and a global network. They also have caching solutions. These features make your website load quickly and perform well.
What security and reliability measures does Hostinger have in place?
Hostinger focuses on security and reliability. They have DDoS protection, SSL certificates, and backups. They also guarantee your website will be up and running.
How user-friendly is Hostinger's hosting platform?
Hostinger's platform is easy to use. It has a simple control panel and one-click installers. It's great for anyone to manage and grow their website.
What are Hostinger's pricing plans and special offers?
Hostinger has plans for every budget. They offer shared, cloud, and WordPress hosting. They also have special deals, like a 20% discount now.
Does Hostinger provide 24/7 customer support?
Yes, Hostinger's support team is available all the time. They can help with setup, problems, or account management. Their experts are ready to assist you.
3 notes
·
View notes
Text
Available Cloud Computing Services at Fusion Dynamics
We Fuel The Digital Transformation Of Next-Gen Enterprises!
Fusion Dynamics provides future-ready IT and computing infrastructure that delivers high performance while being cost-efficient and sustainable. We envision, plan and build next-gen data and computing centers in close collaboration with our customers, addressing their business’s specific needs. Our turnkey solutions deliver best-in-class performance for all advanced computing applications such as HPC, Edge/Telco, Cloud Computing, and AI.

With over two decades of expertise in IT infrastructure implementation and an agile approach that matches the lightning-fast pace of new-age technology, we deliver future-proof solutions tailored to the niche requirements of various industries.
Our Services
We decode and optimise the end-to-end design and deployment of new-age data centers with our industry-vetted services.

System Design
When designing a cutting-edge data center from scratch, we follow a systematic and comprehensive approach. First, our front-end team connects with you to draw a set of requirements based on your intended application, workload, and physical space. Following that, our engineering team defines the architecture of your system and deep dives into component selection to meet all your computing, storage, and networking requirements. With our highly configurable solutions, we help you formulate a system design with the best CPU-GPU configurations to match the desired performance, power consumption, and footprint of your data center.
Why Choose Us
We bring a potent combination of over two decades of experience in IT solutions and a dynamic approach to continuously evolve with the latest data storage, computing, and networking technology. Our team constitutes domain experts who liaise with you throughout the end-to-end journey of setting up and operating an advanced data center.
With a profound understanding of modern digital requirements, backed by decades of industry experience, we work closely with your organisation to design the most efficient systems to catalyse innovation. From sourcing cutting-edge components from leading global technology providers to seamlessly integrating them for rapid deployment, we deliver state-of-the-art computing infrastructures to drive your growth!
What We Offer The Fusion Dynamics Advantage!
At Fusion Dynamics, we believe that our responsibility goes beyond providing a computing solution to help you build a high-performance, efficient, and sustainable digital-first business. Our offerings are carefully configured to not only fulfil your current organisational requirements but to future-proof your technology infrastructure as well, with an emphasis on the following parameters –
Performance density
Rather than focusing solely on absolute processing power and storage, we strive to achieve the best performance-to-space ratio for your application. Our next-generation processors outrival the competition on processing as well as storage metrics.

Flexibility
Our solutions are configurable at practically every design layer, even down to the choice of processor architecture – ARM or x86. Our subject matter experts are here to assist you in designing the most streamlined and efficient configuration for your specific needs.

Scalability
We prioritise your current needs with an eye on your future targets. Deploying a scalable solution ensures operational efficiency as well as smooth and cost-effective infrastructure upgrades as you scale up.

Sustainability
Our focus on future-proofing your data center infrastructure includes the responsibility to manage its environmental impact. Our power- and space-efficient compute elements offer the highest core density and performance/watt ratios. Furthermore, our direct liquid cooling solutions help you minimise your energy expenditure. Therefore, our solutions allow rapid expansion of businesses without compromising on environmental footprint, helping you meet your sustainability goals.

Stability
Your compute and data infrastructure must operate at optimal performance levels irrespective of fluctuations in data payloads. We design systems that can withstand extreme fluctuations in workloads to guarantee operational stability for your data center.
Leverage our prowess in every aspect of computing technology to build a modern data center. Choose us as your technology partner to ride the next wave of digital evolution!
#Keywords#services on cloud computing#edge network services#available cloud computing services#cloud computing based services#cooling solutions#hpc cluster management software#cloud backups for business#platform as a service vendors#edge computing services#server cooling system#ai services providers#data centers cooling systems#integration platform as a service#https://www.tumblr.com/#cloud native application development#server cloud backups#edge computing solutions for telecom#the best cloud computing services#advanced cooling systems for cloud computing#c#data center cabling solutions#cloud backups for small business#future applications of cloud computing
0 notes
Text
Top Hosting Providers in Delhi
Launching your dream website only to face constant crashes and slow loading times can be a nightmare for any business or individual aiming to thrive online. Choosing the right hosting provider can make or break your online journey. In Delhi’s competitive market, finding a dependable solution can be overwhelming. This article explores the top hosting providers in Delhi to ensure success for your digital presence.
Key Features of a Reliable Hosting Provider
1. High Uptime Guarantee
A reliable hosting provider ensures your website is accessible 24/7, minimizing interruptions and maximizing productivity.
2. Affordable Plans for All Budgets
From startups to established businesses, flexible plans with transparent pricing ensure premium services are accessible to everyone.
3. Blazing-Fast Speeds
Website speed is critical for user engagement and SEO. Optimized server performance ensures lightning-fast loading times that enhance the user experience.
4. Robust Security Measures
With threats like cyberattacks on the rise, hosting providers offer SSL certificates, DDoS protection, and regular backups to safeguard your data.
5. Outstanding Customer Support
Technical issues can be stressful, but 24/7 support teams ensure quick resolutions and peace of mind.
Top Hosting Providers in Delhi
1. Hostagle
Hostagle combines affordability, reliability, and robust features to deliver exceptional hosting services. Whether you need shared hosting, dedicated servers, or domain registration, Hostagle is a trusted partner for businesses in Delhi. With 24/7 customer support and scalable plans, Hostagle ensures your website’s success.
2. Penguin Technology
Penguin Technology specializes in Cloud, Linux, and DevOps solutions, offering end-to-end IT infrastructure management. Their expertise ensures that businesses have professional hands managing their hosting, both in-house and on the cloud.
3. Webkype
Webkype is a preferred technology partner for startups and enterprises, providing comprehensive solutions like ERP, CRM, web development, and IT services. They empower businesses to thrive in the digital era with reliable hosting and IT support.
4. Softzenia
Softzenia is a team of experienced professionals delivering services such as web design, e-commerce development, payment gateway integration, and online marketing. Their hosting solutions complement their full suite of web services, making them a one-stop shop for businesses.
5. D2Web Solution Ltd.
D2Web Solution Ltd. offers domain and server solutions, including website hosting, VPS servers, cloud hosting, and digital marketing services. Their versatile offerings make them a go-to choice for businesses in Delhi.
Choosing the best hosting provider is vital for your website’s success. With options like Hostagle, Penguin Technology, Webkype, Softzenia, and D2Web Solution Ltd., businesses in Delhi have access to reliable, affordable, and secure hosting solutions. Evaluate your needs and partner with a provider that aligns with your goals for a seamless digital experience.
FAQs
Q1: What makes Hostagle different from other hosting providers? A: Hostagle offers a unique combination of affordability, reliability, and robust features tailored to diverse needs.
Q2: Which hosting provider is best for startups in Delhi? A: Hostagle and Webkype offer affordable plans and scalable solutions, making them ideal for startups.
Q3: Do these providers offer 24/7 customer support? A: Yes, providers like Hostagle and Softzenia offer round-the-clock support to assist with technical issues.
Q4: Can I get cloud hosting services in Delhi? A: Yes, Penguin Technology and D2Web Solution Ltd. specialize in cloud hosting solutions.
#web hosting#hosting service provider#hosting services#cloud hosting provider#webhosting#vps hosting#Domain and Hosting
2 notes
·
View notes
Text
The Significance of Regular Maintenance for Your WordPress Site

WordPress stands as one of the leading content management platforms, driving millions of websites across the globe. Its flexibility, scalability, and ease of use make it a go-to platform for businesses, bloggers, and eCommerce stores. Much like a car needs routine maintenance to run smoothly, your WordPress site demands regular care to maintain peak performance, strong security, and a seamless user experience.
Why Regular Maintenance Matters
Improved Website Security
Frequent updates to the WordPress core, plugins, and themes safeguard your site against security risks. Neglecting updates can leave your site exposed to hackers, malware, and data breaches.
Enhanced Performance and Speed
A sluggish website can deter visitors and harm your visibility in search engine results Regular maintenance involves optimizing your site’s performance by clearing cache, minimizing scripts, and addressing server-related issues. These steps ensure a seamless and fast browsing experience for visitors.
Better SEO Rankings
Search engines like Google prioritize websites that are fast, secure, and free of errors. Maintenance activities such as fixing broken links, updating content, and optimizing images can improve your site's SEO, helping you rank higher in search results.
User Experience (UX) Improvement
Old themes, malfunctioning links, and sluggish pages can annoy visitors and increase bounce rates. Consistent upkeep guarantees your site remains user-friendly, with operational features, seamless navigation, and compelling content.
Key Aspects of WordPress Maintenance
WordPress consistently publishes updates to enhance performance and address security vulnerabilities. Maintaining up-to-date core, plugins, and themes is vital for reducing risks and ensuring flawless compatibility.
Backups: Your Safety Net
A dependable backup system allows you to swiftly recover your site in the event of accidental data loss, failed updates, or cyber threats. Implement regular backups to safeguard your information and reduce the chance of downtime."
Database Optimization
Over time, your WordPress database may gather clutter like spam comments, redundant post revisions, and obsolete records. Streamlining your database boosts site performance and frees up valuable storage space.
Security Checks
Use security plugins to monitor your site for malware, unauthorized logins, and other potential threats. Regular scans and firewall settings can safeguard your site from harmful attacks.
Broken Link Fixes
Broken links harm user experience and SEO. Conduct regular checks to identify and fix these issues, ensuring a smooth browsing journey for your visitors.
Content Review and Update
Consistently evaluate your content for relevance, correctness, and audience interaction.. Refreshing outdated blog posts or removing irrelevant information ensures your site remains current and beneficial to visitors."
Performance Testing
Test your site’s speed and responsiveness across different devices and browsers. Platforms like Google PageSpeed Insights or GTmetrix offer valuable insights to pinpoint opportunities for optimization.
Consequences of Skipping Maintenance
Failing to maintain your WordPress site can lead to serious repercussions:
Increased Downtime: Neglected sites are more prone to crashes, especially after updates.
Loss of Traffic and Revenue: Security breaches or slow loading times can deter visitors, affecting both traffic and sales.
SEO Penalties: Issues like broken links or outdated content can harm your search engine rankings.
Higher Repair Costs: Fixing a neglected site can be more expensive than regular upkeep.
DIY vs. Professional Maintenance
Tips for Regular WordPress Maintenance
Schedule weekly or monthly maintenance tasks.
Use reliable tools and plugins for backups, security, and performance optimization.
Monitor your site's uptime and analytics to identify potential issues early.
Optimize your WordPress site with image compression, responsive design, lazy loading, modern formats, and metadata cleanup. Get expert help at wpwebsitefix.com.
#digital marketing#local seo#off page seo#seo#seo agency#seo company#seo expert#seo services#website#wordpress
2 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Affordable Web Hosting Services in UAE: Reliable Solutions for Every Need
The Affordable Web Hosting Services market in the UAE caters to individuals, startups, and businesses seeking cost-effective yet reliable solutions for establishing their online presence. With the increasing importance of a strong digital footprint, choosing the right web hosting provider is crucial for ensuring website performance, security, and scalability.
Affordable web hosting services in the UAE offer a variety of plans designed to suit diverse needs. Whether you’re launching a personal blog, setting up an e-commerce platform, or managing a corporate website, these services provide the necessary resources without breaking the budget. Features like ample storage, bandwidth, and advanced tools are often included, ensuring clients get the best value for their investment.
One of the key benefits of affordable web hosting in the UAE is access to local servers and data centers. These facilities ensure faster website loading times and improved reliability, especially for users within the region. This not only enhances user experience but also boosts search engine rankings, which is vital for online visibility and business success.
Security is another critical aspect of web hosting services. Affordable providers in the UAE prioritize website safety by offering SSL certificates, firewalls, regular backups, and protection against cyber threats. These measures ensure that your data remains secure, giving you peace of mind as you focus on growing your online presence.
Most affordable web hosting services in the UAE come with user-friendly control panels and 24/7 customer support. This makes it easy for users, regardless of their technical expertise, to manage their websites efficiently. Hosting providers also offer seamless scalability options, allowing clients to upgrade their plans as their website traffic and business requirements grow.
Value-added features such as free domain registration, email hosting, and website-building tools further enhance the appeal of affordable hosting packages. These tools simplify the process of creating a professional-looking website and help businesses save on additional expenses.
Affordability doesn’t mean compromising on quality. Many hosting providers in the UAE ensure their services are aligned with global standards, offering 99.9% uptime guarantees and robust performance. This reliability ensures that websites remain accessible to visitors at all times, which is critical for building trust and credibility.
For small businesses and entrepreneurs, affordable web hosting services provide an excellent starting point for establishing an online presence. By offering budget-friendly options without sacrificing essential features, these services enable clients to focus their resources on other aspects of their business growth.
As the demand for online services continues to grow, the UAE’s hosting market remains competitive, with providers striving to deliver better features at lower costs. This benefits customers by giving them access to a wide range of options tailored to their specific needs and budgets.
By choosing affordable web hosting services in the UAE, you can ensure that your website operates smoothly, looks professional, and meets the expectations of your audience—all without exceeding your budget. Whether you’re a beginner or an established business, these services are an ideal choice for building and maintaining a strong online presence.
2 notes
·
View notes
Text
Speed Being Crucial: Why Go With An SSD VPS Server?
In today’s era, speed is a vital requirement rather than merely a perk. This is particularly important for anyone operating an online business, application, or even a website; the speed at which your server operates becomes one of the principal factors determining the overall performance of your services. One of the simplest ways to ensure that your server is quick and reliable is by utilising an SSD VPS Server. However, the question remains: why should you prioritise speed, and how does it influence performance? Let’s explore.
How Do You Define An SSD VPS Server?
To start off with, a VPS, which is short for Virtual Private Server, is specifically designed to cater dedicated resources like CPU, RAM and storage for its users; however, its revenue structures have been powered by the traditional HDD. Unfortunately, these hard disk drives are out of date and contain mechanical components which serve to be slow when compared to current advancing technology. SSD VPS servers, however, have changed the world as they come equipped with solid state drives where information is stored onto flash memory which drastically boosts speed numbers.
1. Faster Transfer Rates Accessing Data
A backup benefit of SSD VPS servers is indisputably rapid data access and storage. Unlike mechanical HDDs, an SSD does not have an arm with a spinning disk that retrieves - it uses flash memory technology which allows for faster data access. With this, SSD VPS for website and application databases and e-commerce which requires extremely fast data pulls would benefit optimally from the SSD VPS. There is less latency and faster every request which means better experience for the user.
2. Improved Engagement Statistics and Better Search Engine Rankings
In modern business settings, speed in website usage has become paramount. An emphasis is placed on times for loading pages, time-wise Google ranks sites in an order. Slower sites lose customers who become agitated and search for other services, and in the process, customers also lose out on numerous opportunities to explore and expand the business. Unfortunately, slower web hosting services hurt business. Mutually benefiting each other, search engines react positively if one’s SEO ranking improves, a well-known relation being that of enhanced client interaction. If your website performance matters, then utilising an SSD VPS hosting without a doubt would be one of the best decisions.
3. Increased Dependability and Availability
If there is a way to characterise the appropriate standards in regard to service delivery, then the reliability of the server is a must. An issue with conventional HDDs, which are mechanical, is a threat to providing dependable services. Conversely, SSD VPS servers are far more dependable and have no moving parts.
As SSDs have a greater chance of not faltering, it translates to greater uptime, which is beneficial especially to organizations that require continuous accessibility to their websites and services. The assurance of an SSD VPS helps to maintain operations smooth without any hitches.
4. Light Applications Are Able to Load with Greater Efficiency
High-performance storage is required for dynamic websites and applications reliant on regular data, such as content management systems (CMS), e-commerce, websites, or business apps. This means that the SSD VPS Server come into form as they are able to enable those applications to run smoothly.
Should you be managing an online shop, then the ability of your product pages, checkouts and inventory to perform efficiently is reliant on your server’s data delivery capability. This therefore highlights one of the benefits of an SSD VPS, which is faster speeds that can translate to better performance.
5. Reduction of Latency for the Purpose of Improving Applications
Over the years, people have developed a habit of using applications on their phones with video streaming, online games or just chatting. These require low latency to work efficiently. SSD VPSs have a faster read and write speed as opposed to HDDs, which allows SSD VPSs to reduce latency.
So, for individuals who host gaming servers, or streaming services or even trade, low latency simply means more responsiveness, hence a better experience for the customer.
6. Cost & Environmental Effectiveness
Not only are SSDs faster, but SSD VPS servers are also more energy efficient than HDD servers. Energy consumption is low in SSDs, which in return leads to low operating costs and reduced carbon impact.
Switching to SSD VPS hosting can assist firms that wish to limit their carbon emissions, for it goes in the direction of responsible operations. Greater energy efficiency leads to lower costs, which in turn makes SSD VPS hosting a great option for organisations that wish to enhance their efficiency and reduce their impact on the ecology as well.
7. Scale with Ease
Setting up a business comes with many hosting requirements as the business grows. Be it increasing website traffic, new apps, or more data, Smart SSD VPS servers are the right solution for seamless scalability.
The process of enhancing the server’s ability on SSD VPS Hosting is made simple, adding more resources, increasing the storage, as well as updating the server over time so that the users' demands are met. This flexibility goes a long way in ensuring that the business can always grow without having to worry about server performance.
8. Moreover, After Some Time, These Might Become Cost-Effective
The long-term benefits of SSD VPS Servers clearly outweigh these initial costs in contrast to HDD VPS Servers where the costs of SSD VPS Servers are slightly higher. This improvement in speed, reliability, and uptime is bound to lead to improved business performance, resulting in minimal service disruptions and cost savings with regard to reduced downtimes, speedy processes, and high customer satisfaction.
Also, as the business expands, it is essential to have a server that can sustain the increasing traffic without decreasing speed or performance. For this reason, an SSD VPS is a sensible long-term approach for improving your hosting setup and avoiding expenses when the need for more advanced infrastructure arises.
Conclusion: The More The Merrier!
At present, the Internet has created an ecology, so to speak, where businesses can easily exchange services and trade in the blink of an eye. Every business needs to be cutting-edge; gone are the days of having run-of-the-mill websites. Be it e-commerce portals, company websites, sensitive information sharing, or real-time services, hosting the importance of speed and reliability cannot be emphasised enough. The SSD theatre provides ample opportunity for improvements in these aspects.In order to improve the performance of a system and enhance its security, long-term success over working towards a pre-selected goal can be easily managed by deploying an SSD VPS Server. Be a trendsetter and do not compromise on what you deserve; choose an SSD VPS and take your first step towards a new world of hosting.
2 notes
·
View notes