#BE FOR REAL I SENT U THE SPECIFICS I WANTED IN A HUB AND THE EXACT THING I HAD
Explore tagged Tumblr posts
Text
i need to clean up my folders
#i cant download my videos#and i can only connect one fuckass external drive#🙄🙄🙄 my sister broke my hub and she was like OMG ILL BUY YOU WHAT I BROKE#when she deadass thought she didnt acrually break anything#i was like its kinda annoying you broke it but i wasnt expecting u to buy it dec bc of christmas#and shes like. i never said that#i literally have you on tape (messages)#🙄🙄🙄🙄🙄🙄🙄🙄🙄🙄#BE FOR REAL I SENT U THE SPECIFICS I WANTED IN A HUB AND THE EXACT THING I HAD
3 notes
·
View notes
Note
Regarding emulation, I've seen a video on YouTube by Nerrel called "Let's imagine a world without emulation" which I'd think you enjoy. It makes the argument that emulation is necessary to preserve old games. But I bring this up because some idiot tried to debunk the video (Poorly) with a rebuttal titled "Imagine a world without pirates" about how piracy is evil and they only want free stuff and fan games having no right to exist.
Man, I had a whole huge post typed out here and then Firefox acted like it was going to freeze, so I restarted my browser without realizing I never finished writing my response. I guess I’ll try to get back where I was…
youtube
What’s interesting to me in this video is the part where he talks about the idea that not everybody pirates games because they want to steal something without paying for it. His example is the Wii U emulator, CEMU, which is currently making over $6000 a month on Patreon. People sometimes emulate because they want features and convenience they can’t get anywhere else.
(Speaking personally, I installed CEMU recently because I didn’t want to keep digging out my Wii U to just replay a little bit of Mario Kart 8 every now and again)
The problem here is that Nintendo ascribes to specific mantras when it comes to providing users with customization options.
Nintendo games are so polished that the end-user shouldn’t want any options, because the ideal solutions have been found and implemented. In other words, it’s so good that you won’t want to change it.
Optional content is inefficient and expensive. Spending money to develop something only a fraction of their users will actually touch is a waste. (This also applies to why so many Nintendo games never had much in the way of bonus, post-game content until recently)
The ultimate takeaway here is that Nintendo is frugal to a fault. I’ve relayed the story before, about Gunpei Yokoi’s history in developing toys for Nintendo in the pre-video-games era, where he would boil concepts down to their bare parts and cut features to reduce manufacturing costs. This allowed Nintendo to undercut their competition while preserving the core of the experience. Not low effort, but laser-focused effort in a few important areas, with the potential for reaping high rewards.
This is the same company that deletes custom Smash Bros. arenas and Super Mario Maker levels for being “unpopular.” Speaking from personal experience in developing level editing tools, even the most complex Super Mario Maker levels probably aren’t much more than 50kb in size. This means that you could store millions of levels on a $10 64gb thumb drive. On a professional web server, we’re talking hundreds of billions of levels. Nintendo could store every Super Mario Maker level ever made for upwards of a decade and never have to worry about running out of space. And yet, they delete “unpopular” levels anyway.
Even if it only accounts for 2% of their profits, Nintendo can and will go for it as long as it’s easy enough. And, with regards to emulation, nothing is easier than the pennies spent on ink and paper for a Cease & Desist notice. Again, one single act of laser-focused effort with exponential benefits.
What’s interesting is that Sega kind of used to do this. Back in the day, there was a site called Sonic-Cult, and they were a research hub in to beta versions of Sega games. They also hosted lots of things that made Sega unhappy; development kits, leaked versions of games before they officially released, things like that. So, Sega would send them Cease & Desist notices.
Sonic-Cult was the misfit scourge of the Sonic community back then. They openly terrorized anyone at length that drew their ire. When Sega sent a takedown notice, Sonic-Cult gave them the middle finger. “Freedom of information” and all that, but also “screw you for trying to control us.”
Sega backed down. It was more trouble than it was worth.
Which makes me wonder about Nintendo. When Nintendo sends a takedown notice, people comply outright. Nobody challenges them. Nintendo, whose wallets are ever tightened, pennies constantly pinched, gets to steamroll their way all over their most dedicated fans with minimal effort. If Pokemon Uranium is to be believed, they quit exclusively out of fear, not because Nintendo sent them a letter.
What would happen if somebody actually pushed back? At what point would the benefit be overshadowed by the investment, for Nintendo?
Now, Nintendo is no stranger to putting real legal muscle behind its threats, but mostly that’s towards raids on huge piracy rings in China. For something like AM2R, Nintendo actually stands to gain very, very, very little should they take it to court. Would they really do it?
Obviously, people respect Nintendo. Hence why they comply with Cease & Desist notices, sometimes even sight unseen. Sonic-Cult, for all their baditude bravado, often acted more like they had a deathwish. They pretended to be invincible, but it’s not hard to imagine an alternate universe where that backfired on them hard.
Sega vs. Sonic-Cult was also over 15 years ago at this point. Nowadays, you can’t even get away with hosting files on your own personal server as a means to escape the long arm of the law. One phone call to your ISP, and suddenly that server you’re running from your bedroom is forced offline.
All of this is theoretical, of course; but given Nintendo’s precedents, it’s an interesting train of thought to have.
#questions#nintendo#virtual console#sonic-cult#sega#sonic team#sonic the hedgehog#roms#preservation#emulation#clovershroom
14 notes
·
View notes
Text
SA | Mr Robot Episodes 1 to 3 Analysis
EPS1.0_HELLOFRIEND.MOV
Plot Summary
Elliot Alderson works as a cybersecurity engineer at AllSafe, a firm that specialises in protecting large cooperations like Evil Corp from cyber attacks. Evil Corp has recently been under a string of attacks and a meeting is called to understand what occurred.
Later, he gets a call from Angela Moss, his childhood friend, to go to the office as there appears to be a DDoS attack against Evil Corp. Upon arrival, he finds that the servers are infected and that the only way to fix it is to shut down all the servers, clear the infection, and restore from backup.
While inspecting the infected server, Elliot finds a fsociety00.dat file and a readme.txt file containing instructions “LEAVE ME HERE”.
After returning from the server farm, Elliot gets on a tram where he meets a mysterious man who tells Elliot to follow him but only if he didn't delete the files. Elliot follows the man to Coney Island, the base of operations for the hacker group fsociety, who's plan is to destroy Evil Corp's databases so that they can erase most of the world's consumer debt.
Elliot is asked by Mr. Robot to replace fsociety’s IP address in the .dat file with the IP address of Terry Colby, the head of technology at Evil Corp to frame him for the earlier attack.
Back at AllSafe, a meeting has once again be called by the executives from Evil corp and by the FBI. Elliot has prepared 2 files, one which the .dat file contains Colby’s IP and one which contains fsociety’s IP. Initially he planned on presenting the one with fsociety, but after Angela was blamed for the attacks, he changes his mind and gives the FBI the file that frames Colby.
After 19 days of silence. The media and news outlets finally reveal the findings, thus Colby is successfully framed. In the mist of this chaos, Elliot is whisked away to Evil Corp’s headquarters where he is greeted by Tyrell Wellick.
A side story in the episode are Elliot’s attempts to hack those that surround him or those that pip his interest. A more prominent one would be his psychiatrist, Krista, and her “significant other”, Michael. Elliot’s efforts revealed his real identity and the truth of their relationship. He then confronts Michael Lenny and uses blackmail to ensure that Lenny will break up with Krista and tell her the entire truth.
This is inline with his self proclaimed title as a vigilante.
Software Security Elements
The opening sequence is Elliot confronting a child pornographer with information he gathered from hacking his computer. Elliot explains his original motive in hacking the man as well as how he did it.
I started intercepting all the traffic on your network. Thats when I noticed something strange. So I decided to hack you.
There are many ways Elliot is able to monitor and intercept a network’s traffic. As it wasn't specified in the episode exactly if he was able to connect as a local network or wirelessly I have included possible methods for both below.
Using a Legacy Hub
These are placed at a choke-point of a network and are able to repeat all Ethernet frames arriving at one port to all the other ports on the hub.
A downside to this method is that all the extra packets sent from all the ports increase the risk of packet collisions. When this occurs, the nodes on the shared media segment will pause for a random amount of time before they resume sharing data.
This method is most likely not the method Elliot used in the episode.
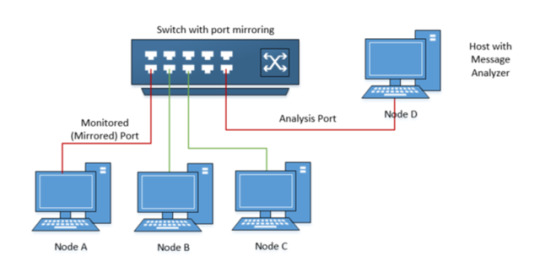
Network Switch Port Monitoring
Also known as Switched Port Analyzer (SPAN) ports or port mirroring, a monitor port is typically configured so that it mirrors all packets that pass through the designated ports. It is used on a network switch to send a copy of any frame sent or received from a particular port to a monitor port.
The downside of this method is that there is a risk of not always getting all the transmitted packets to the monitor port. This is because the primary function of a switch is to forward traffic from the sender to the receiver. As such, if there is a high load on the switch, it will prioritise sending the received frames instead of copying them to the monitor port.
This method is also most likely not the method Elliot used in the episode.
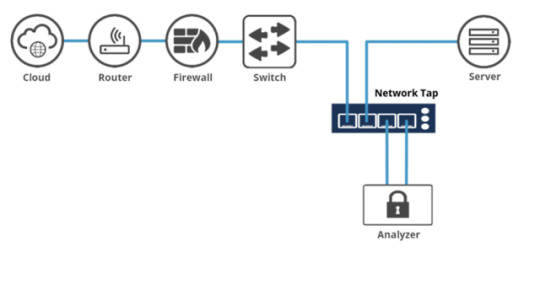
Using a Network Terminal Access Point (Network TAP)
A network tap is a “bump-in-the-wire” device, often placed between 2 nodes in a network, that is designed to copy traffic passing through it to a monitor port. This is a much more reliable way than using a monitor port as taps are less likely to drop packets during high traffic load.
The downside to this method is that it can interrupt network traffic while connecting and disconnecting the tap. They are also often expensive due to the extra hardware required.
This method is also most likely not the method Elliot used in the episode.
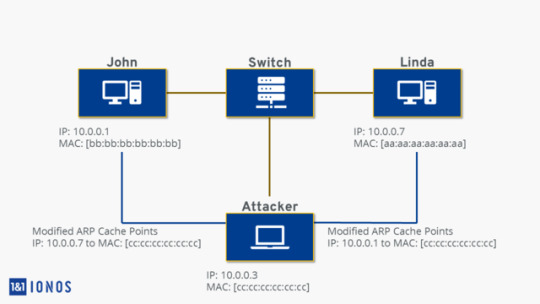
Address Resolution Protocol (ARP) Poisoning
ARP poisoning is a technique where two hosts on a network are tricked into sending packets destined for each other to a sniffer machine on the network. This is done by associating the attacker’s MAC address with the IP address of another host, resulting in any traffic to the IP address is sent to the attacker instead. This method is often used as an opening for other attacks such as man-in-the-middle attack.
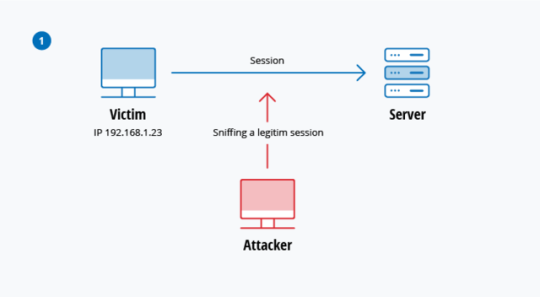
Man-In-The-Middle (MITM) Attack
An attack where the attacker inserts themselves into a conversation between 2 parties pretends to be the the them. The attacker is then able to access and possibly alter any communications or information sent between the 2 parties.
This type of attack is easy to achieve as an attacker within reception range of a wireless access point could insert themselves as a MITM.
The weakness of this method is that the MITM attack can succeed only when the attacker is able to impersonate each endpoint without raising the other party’s suspicion.
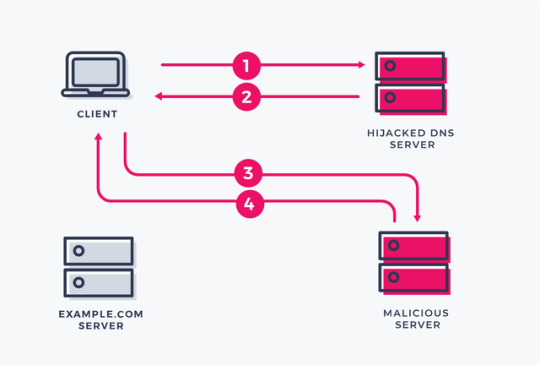
Domain Name System (DNS) Hijacking
DNS hijacking is a process in which an attacker redirects queries to a DNS server. There are many methods to perform this attack including, installing malware on the target’s computer, compromising a router through a default password, or intercepting and hacking DNS communications.
You're using Tor networking to keep the servers anonymous. You made it really hard for anyone to see it but I saw it. The onion routing protocol, it’s not as anonymous as you think it is. Whoever’s in control of the exit nodes is also in control of the traffic, which makes me ... the one in control.
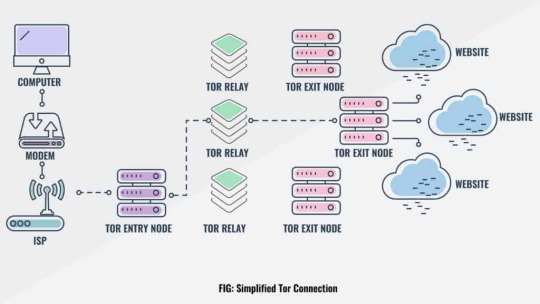
The Onion Router (TOR) Network
It was created initially as a worldwide network of servers developed with the US Navy that enabled people to browse the internet anonymously. It disguises the user’s identity by moving and encrypting their traffic across different TOR servers so that it cannot be traced back to the user.
TOR is useful for people who wants to keep their internet activities private from internet service providers and / or websites. It can also be used to host websites that are only accessible by other TOR users, which is what the perpetrator in Mr. Robot was using to distribute the photographs.
In a TOR network, data comes in and is encrypted all the way through to the exit node. These exit nodes are the gateways where the TOR traffic hits the Internet. As such these nodes can be used to monitor TOR traffic after it leaves the network. Although TOR is decided so that locating the source of the traffic through the network should be near impossible, if the exit traffic is unencrypted and contains identifying information, then it can be traced back to the user. This the exploit Elliot used within the episode to find out the activities of the perpetrator.
This is a “rudy” attack
R. U. Dead Yet (RUDY) Attack
A RUDY attack is a slow rate HTTP denial of service attack tool that aims to keep a web server tied up by submitting form data at an absurdly slow pace. Any web service that accepts form input is vulnerable to a R.U.D.Y. attack as the tool works by sniffing out form fields and exploiting the form submission process.
The tool submits very long form friends are submitted and this process is dragged out by breaking it down into packets as small as 1 byte each. It then sends these packets to the server at randomised intervals of around 10 seconds each. The web server will keep the connection open to accept the packets as the behaviour of the attack is similar to that of a user with a slow connection speed submitting form data. This results in the victim’s web server becoming unavailable to legitimate traffic.
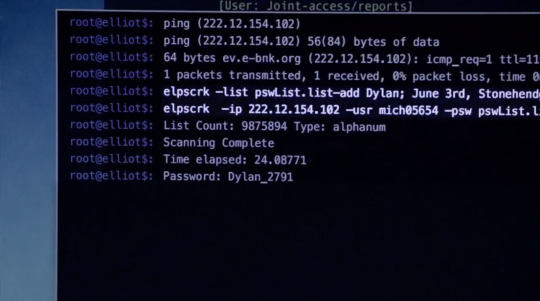
Hacking her was simple, her password Dylan_2791. Favourite artist and the year when she was born backwards.
Although the tool Elliot used here, elpscrack, is fictional, it does contain functionalities that are found in other tools such as CeWL, Burp Suite, and others.
Custom Word List (CeWL) Generator
CeWL is a ruby app which when a given url, it will “crawl” the specified site as well as any external links found on the site to a specified depth. It then returns a list of words from that site that you can filter to include only words of specific length.
This information is useful when targeting a specific individual as people tend to publicly like or follow things with their social media. More often than not, people will use something they like to form a basis for their passwords, as such, the list created by CeWL can be hashed and then given to a password cracker to potentially crack a person’s password.
This is probably the closest to the elpscrk tool that Elliot used.
Burp Suite
Burp Suite is a Java based web penetration testing framework that is useful in identifying vulnerabilities and verify attack vectors that re affecting web applications. It can also be used to brute force a web application log in page.
Burp is designed to be used alongside your browser and functions as an HTTP proxy server where all the HTTP/S traffic from the browser passes through Burp.
Burp requires a list of usernames and a list of passwords in order to brute force a log in page. Manually submit a log in request using any random username and password and Burp capture HTTP request. Then using the cluster bomb attack method, Burp will brute force the log in page using the given lists.
References
NETRESEC: Intercepting Network Traffic
Geeks for Geeks: Carrier sense multiple access (CSMA)
Wikipedia: Packet Analyzer
Cable Solutions: Port Mirroring vs Network TAP
Netwrix: Top 10 Most Common Types of Cyber Attacks
NS1: The Anatomy of a DNS Hijacking
Life Hacker: What is TOR
Hacker Target: Exit Nodes
Radware: RUDY Attack
Cloudflare: R U Dead Yet?
Imperva: RUDY
Digi Ninja: CeWL
Stuff Jason Does: CeWL
Pentest Geek: Burp Suite
Alpine Security: Brute Force using Burp
EPS1.1_ONES-AND-ZER0S.MPEG
Plot Summary
SIDE NOTE:
I am not particularly knowledgeable in the technical aspects of security engineering, networks, or hacking so I may have gotten some details incorrect. The information in these notes are mainly from my research on the topics and techniques found on the internet.
1 note
·
View note