#Android Theft Protection
Explore tagged Tumblr posts
Text
Android Theft Protection: Noua funcționalitate bazată pe AI pentru prevenirea furturilor de telefoane
Odată cu lansarea Android 15, Google introduce un nou sistem de protecție împotriva furturilor de telefoane, denumit Android Theft Protection, care utilizează inteligența artificială pentru a detecta tentativele de furt și a bloca instantaneu dispozitivul. Acesta este conceput pentru a proteja datele personale și a descuraja infractorii, mai ales în regiuni cu un nivel ridicat de furturi prin…
#actualizare Android 15#AI detecție furt#Android Theft Protection#autentificare cont Google#blocare telefon#Google Play Services#prevenire furt telefoane#protecție antifurt Android#resetare telefon la setările de fabrică#securitate date Android
0 notes
Text
Weekly output: Metro by T-Mobile's Flex plans, Google Play security, Google I/O's AI Sandbox, Uber Caregiver, Android theft protection
Last week featured my first trip to cover Google I/O since 2019. It was great to spend a few days in a pleasant part of the Bay Area, and it was outright lovely to catch up with tech-journalism friends that I had not seen IRL since four or five years ago. Another good part of this trip, as noted earlier for Patreon members: staying in the same Airbnb room that I’d booked in 2018 and…
View On WordPress
#AI Sandbox#Android theft protection#caregivers#Google Gemini#Google I/O#Google Play#I/O#Kate Washington#Metro by T-Mobile#on-device AI#Project Astra#stolen phone#stolen phone passcode#subsidized phones
0 notes
Text
How to enable Theft Protection on your Android phone? (2023)
0 notes
Text
Google Introduces New 'Theft Protection' Features for Android
Google has started rolling out new “Theft Protection” features for Android, including Theft Detection Lock and Offline Device Lock. These are two of the three tools Google previously announced, and some users have already experienced the third tool, Remote Lock, in action. Of the new features, Theft Detection Lock stands out as the most intriguing. According to Mishaal Rahman, this feature…
0 notes
Text
Google Launches AI Anti-Theft Feature for Android Phones in Brazil

Alphabet’s Google will launch a new AI-powered anti-theft feature for Android phones in Brazil, the first country to test this technology, aiming to reduce phone theft rates in a country where nearly one million phones were stolen last year.
Google, the tech giant under Alphabet Inc., made a groundbreaking announcement. Brazil, a country plagued by high phone theft rates, will be the first to test a new anti-theft feature for Android phones using artificial intelligence (AI). This innovative technology, a significant step in the fight against phone theft, automatically locks the device’s screen when a phone has been stolen, thereby enhancing security for users.
The initiative is part of Google’s broader strategy to leverage AI to address real-world problems. Starting in July, the anti-theft feature will initially be available to Brazilian users of Android phones running version 10 or higher. According to the company, this phased rollout will eventually extend to other countries over the year.
The new anti-theft feature, powered by AI, operates through three types of locks. The first lock utilizes AI to identify movements typically associated with theft, such as sudden, rapid movements that suggest snatching or running. Once these movements are detected, the feature automatically locks the screen, rendering the phone unusable to the thief. The AI model has been trained to recognize specific patterns that indicate a theft, enabling it to provide an immediate response to protect the user’s data.
Continue reading.
#brazil#brazilian politics#politics#artificial intelligence#public security#technology#google#image description in alt#mod nise da silveira#man before reading the report i was thinking google was rolling out something to protect users from ai data theft#and was positively surprised by that concept#only to find out it's just regular old school physical theft lol
9 notes
·
View notes
Text
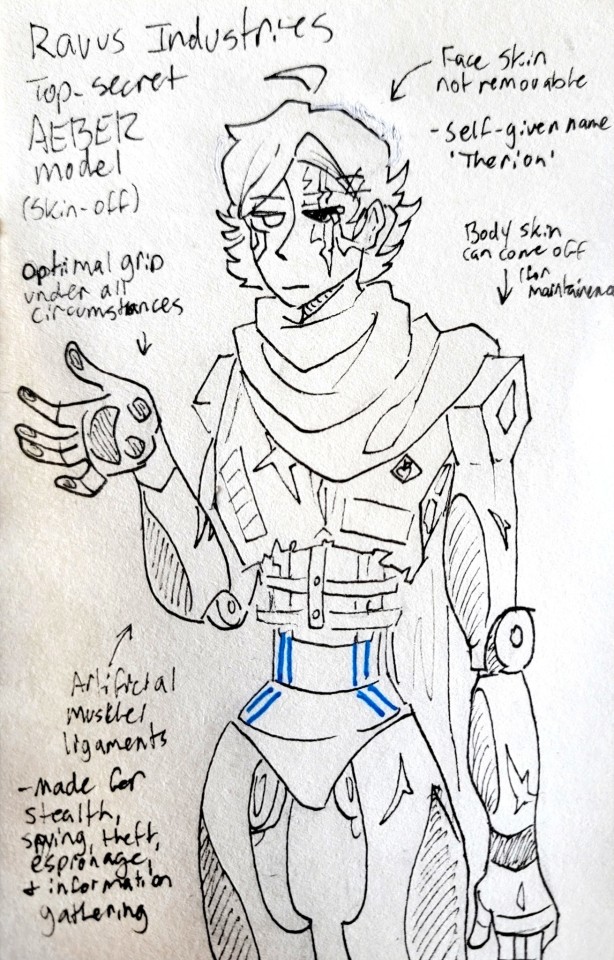
Heehee hoohoo Theriandroid design :)
TOP SECRET - AUTHORIZED PERSONNEL ONLY
Ravus Industries product- Unique Frame AEBER model, serial no. XXXX1069
Status: Decommissioned. Missing, assumed deactivated or scrapped. [OUTDATED - SEE ADDENDUM FOR FURTHER DETAILS]
Model is pictured here with artificial skin removed and hair pulled back to examine eye socket after last authorized maintainence. Please note that artificial skin affixed to the neck upwards is not removable to protect sensitive sensory and motor components.
The AEBER model was constructed in secret to conduct information and asset retrieval on behalf of Ravus Industries. Purposes they have been successfully utilized for include: stealth, espionage, theft, assassination, and information gathering. The android was given highly advanced artificial intelligence with a focus on visual cognition and quick decision making in order to facilitate this purpose. Identity formation is a known result of AI tuned past a certain threshold, and as a result the unit self-identifies as 'Therion', and should be referred to with 'they/them' and 'he/him' pronouns.
Physical features include a unique lithe build and highly maneuverable joints as well as extra artificial muscle and ligaments in order to provide maximum flexibility, agility, and speed. Fingertips, palms, and the soles of the feet are padded with specially textured carbon fiber and fitted with electromagnets that the AEBER model can activate at various intensities. This is to ensure optimal grip and balance at all times. All extremities are also fitted with individual adjustable counterbalances for this purpose.
Unit was decommissioned April 301X due to disciplinary issues and obsolescence.
ADDENDUM
Addendum 1: AEBER unit, aka 'Therion', has refused a programmed assignment. The unit's ability to refuse tasks is a new development and will need further study.
Addendum 2: After reconditioning, unit is no longer refusing tasks. Unit expresses great distress when given assignments involving assassination. Due to reasonable conflicts with ethics programming, concerns can safely be ignored.
Addendum 3: Unit is refusing orders once more, reconditioning unsuccessful. Due to development of newer AEBER model ('Gareth') and conclusions of Ravus Industries Artificial Intelligence Ethics Board, 'Therion' is scheduled to be decommissioned and placed in long-term storage.
Addendum 4: AEBER unit 'Therion' has been lost after a break-in of the Ravus Industries long-term storage facility, along with several other non-intelligent assets. Unit has deactivated or damaged their internal GPS and cannot be located by satellite. Proprietary technology and the top-secret nature of this unit dictate that location and re-acquisition are a priority.
Addendum 5: Unit has been located in the Cliftlands area after checking in to a Ravus Industries authorized engineering location for repairs. Unit seems to have taken heavy cosmetic damage and lost one visual sensory component. Diagnostics indicate that they are otherwise healthy.
Addendum 6: Search of the Cliftlands has turned up no trace of 'Therion', and unit has not been seen or recorded in any locations for the past six months. Human testimony has also turned up no leads, with no sightings within the same 6-month time frame. Unit is currently listed as missing, assumed deactivated or scrapped as of August 302X.
Addendum 7: Unit has been sighted in the Riverlands as of March 303X, six years after being listed as missing. Retrieval is once again considered a priority for this unit after the loss of 'Gareth'.
#spitblaze says things#spitblaze draws things#spirblaze writes things#octopath#octopath traveler 2#therion#therion (octopath)#android therion au
45 notes
·
View notes
Text
Beware of HybridAlex17.
CW: Guilt-tripping, Suicide Baiting, Manipulation, Stalking, Identity Theft, Death Threats. Please read this. It is very important.
Hello, I usually don't make these type of posts, but lately I've been too stressed to even be here on Tumblr due to a certain individual in The Lego Movie Fandom. And that person is @/HybridAlex17.
Weeks ago, I decided to cut ties with this person on a calm way due to the fact that I genuinely couldn't keep the friendship going on any longer. Truth is that this friendship made me feel like I was trapped.
I'm in no way invalidating his trauma and suffering, and of course, I will always try to help my friends in times of need, but Alex constantly needed me to "comfort him" and basically be there for him all of the time, making me responsible of his emotions since he's an very unstable person "who would think of the worst case scenario happening to me" if I didn't told him what I was doing at the moment. Of course, friendships are meant to work through bad and good times. But there's moments where you should realize that you have limits. I had mine.
And I couldn't possibly just stay any longer in a relationship where it felt like I had to take care of someone. That's not what I'm looking for. It never was. I felt unsafe and constantly scared about what he could do to himself if I said the wrong thing, as he was constantly feeling bad about everything. And call me what you want, but I realized that, I do not want to be there. But even then, I didn't have any hard feelings towards him. I genuinely wished him the best and to get better, but I couldn't be there to see that change. My mental health mattered. So I spoke to him very calmly about it, reassuring him that I do not hate him and I just wanted to cut our ties peacefully.
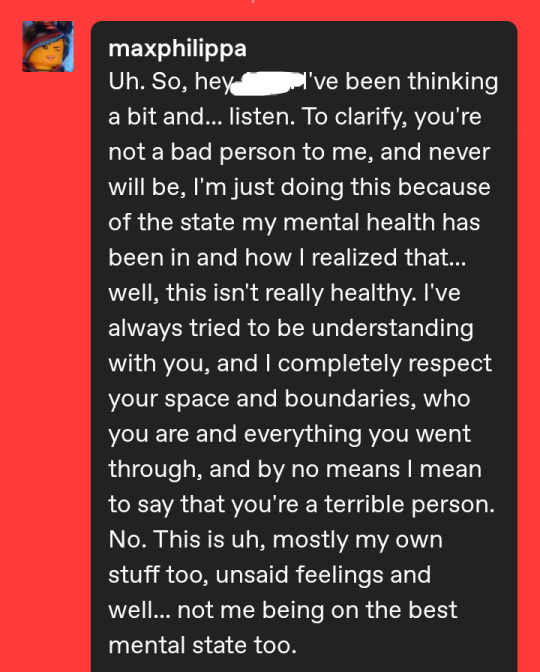
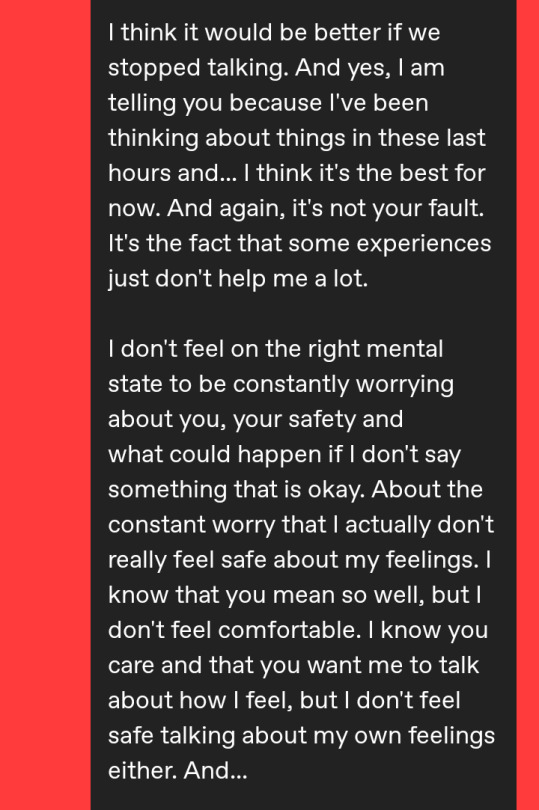
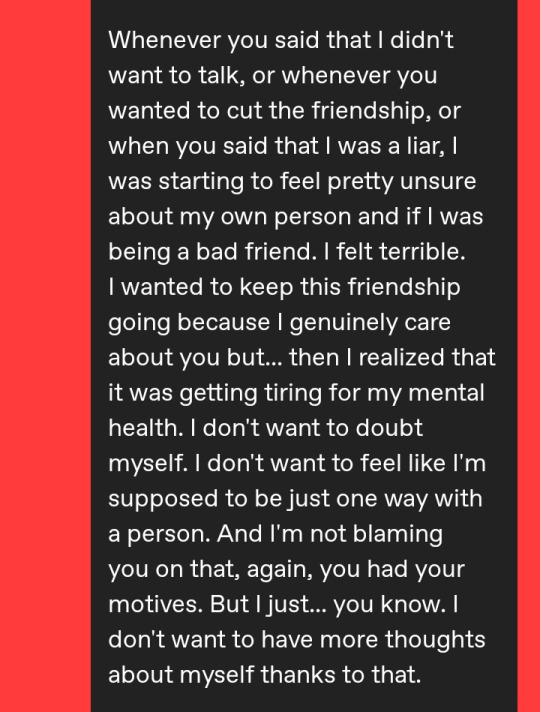

(At the moment, I censored his name to protect his identity. This was before I blocked him.)

Then, in reply, he guilt-tripped me, wishing that I never met him, that he died that one time, that this never happened, and everything. Despite me having high hopes for him to actually react properly, he didn't. So I ended up blocking him in all of his accounts and just calling it a day, because I didn't want to think of it. Sounds pretty fair by now, right?
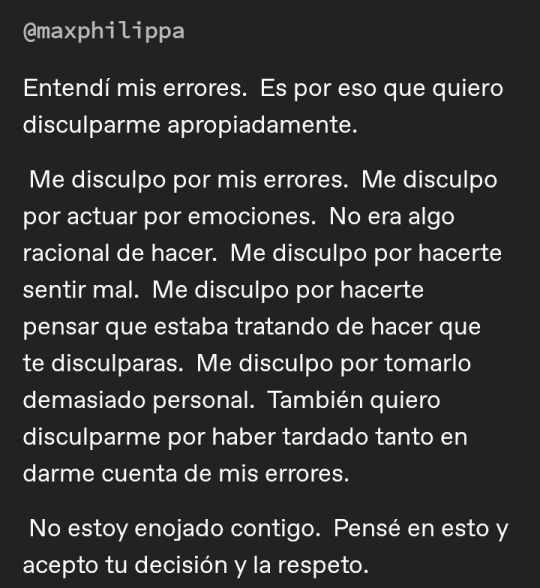
Well, the story does not end there. Some more days later, he would then tag me on a PUBLIC POST (because he couldn't just DM me, I guess), apologizing for taking it too personally and for everything in spanish. I spoke to my friends about this at the moment because I really didn't feel like it was genuine. You would never post an apology towards someone unless you would want them to feel pressured to reply to you, right? Well then, because he did this already MORE THAN ONE TIME with me. I blocked him because I really didn't want to deal with it. It was tiring and I was hoping that he would just give up.
(This account of his does no longer exist.)

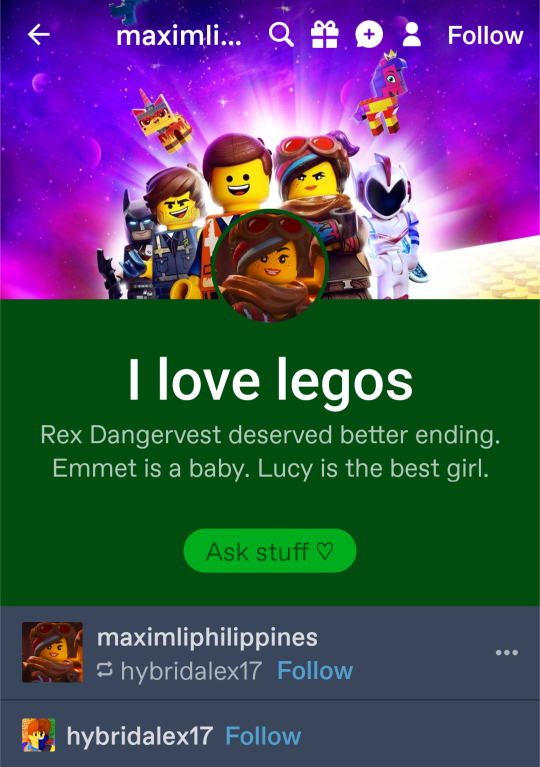
But then, here comes the impersionation thing. Three days ago, my friends sent me an blog that was weirdly similar to mine. Lucy icon and the description, eh, ya' know. Very fucking basic. And look at the URL. A mix of the words Max and Philippa but changed to spell Philippines.
And if that does not convince you, then take a look at this post.
"Android Emmet AU".
I swear to fucking God.

You guys might or might not know that I'm the creator of the Android Rex AU, I created it on June 22 of the past year, being the second AU I've ever made. So he didn't only just made a weird puppet of me to pretend that we're still friends, he's STEALING THE WHOLE THING AND TRYING TO MAKE OTHERS THINK THAT IT IS AN ACCOUNT OF MINE.
But seriously though. Come on. He's not fooling anyone. It's an pathetic imitation of who I am, of what can I do. He's acting like he knows me enough, but he never even tried to. He could never replace me. He will never get me back. And he knows it. He knows it so well.
Yesterday, it was my birthday. Of course, it was a great day for me. But various anonymus asks came in for me then. The first ones were kind ones, but then, there were some that straight up wished that I was never born and that I died! And hey! Not to assume! But that was Alex in different accounts! Because he literally stopped once I turned the anonymus off and one of my friends stood up for me!
And you can see this by scrolling through my blog just a bit!
And once he realized that he fucked up, because they thought that this friend of mine didn't have any relation with me (despite the fact that I do have posts where I drew their guys), he blocked them and "apologized". Can't even take responsability for such a messed up thing.
And he just didn't stop there. Wishing me death? Expected it. But how did he know that it was my birthday? Because I blocked him before I ever publically told it. And that's when it hit me. An alt account. And someone sent me a post in which he drew Android Rex and Joseph, two of the main characters of my AU for my birthday, saying that he wishes the best for me and stuff.
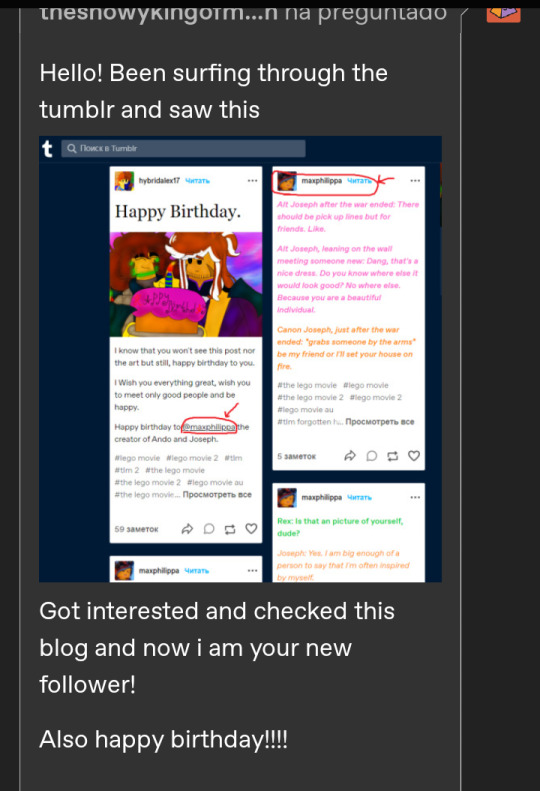
I never fucking told you when my birthday was. You could have never possibly known unless you were stalking me over an account. You use alternative accounts to boost your own art and don't even try to deny it. People will realize once they take a look. So many empty accounts. Instead of moving on and just fucking accepting that I cut ties with you because you made me feel scared of even entering this app, and learning from your mistakes, you're being a fucking creepy man. And don't deny it. You've done this to a bunch of people here. My close friends were affected by your shit.
And I know that you're going to see this.
And just so you know, since you crave my attention so fucking much to the point where you created a fake account that was "me" so you could still think that nothing happened, let me tell you something.
I was never angry at you. I stated that I wanted to cut ties because I couldn't be in such a toxic relationship. I respected you as a person. But then you tried to make me feel bad about my choice. About everything I do. Because that's what you're good for. Is this how you treat your friends? Because Good Lord. Seeing your true colors makes me think that we were never really friends since the start.
And even then? I'm not angry at you.
I'm disappointed.
And I already hit my favor quota on saying this in the most harmless of ways possible, but I'm feeling generous. So. Like. Have some dignity, would you? Don't be an asshole. Move on. I already did.
I hoped that you would move on. But you never learn anything, do you? You said how much you cared about me back then. I guess death treats, constantly stalking someone, and impersonating them is your way to care.
I will never be your friend.
And to those who read this post, please, do not harass HybridAlex17. As much damage he has done, he's not worth it. What I would be thankful of is that you guys report the fake account he made of me, since I can't do it myself. And let others know about him and his doings.
If you're a friend of HybridAlex17, then I'm deeply sorry. I do not have any hard feelings towards you, but I would rather not interact with anyone who is.
And with this, I'm done. Take care, all of you.
54 notes
·
View notes
Text
book recommendation tag game!
rules: recommend as many books as you like. please include genre and some basic information on it (either your words or a copy+paste synopsis). feel free to include cover art, a personal review, trigger warnings, and anything else! just don’t spoil the book!
thank you for the tag @eloquentspeeches !! I immediately forget every book I've ever read xD I'm going to put what I do remember under the cut. Let's see~
The Murderbot Diaries by Martha Wells
This series is one of my all-time favourites. It's a science fiction series of seven books and short stories about a rogue cyborg security agent, set in a space-faring society with wormhole technology and alien remnants. The first book in the series is:
All Systems Red
"As a heartless killing machine, I was a complete failure." In a corporate-dominated space-faring future, planetary missions must be approved and supplied by the Company. For their own safety, exploratory teams are accompanied by Company-supplied security androids. But in a society where contracts are awarded to the lowest bidder, safety isn’t a primary concern. On a distant planet, a team of scientists is conducting surface tests, shadowed by their Company-supplied ‘droid--a self-aware SecUnit that has hacked its own governor module and refers to itself (though never out loud) as “Murderbot.” Scornful of humans, Murderbot wants is to be left alone long enough to figure out who it is, but when a neighboring mission goes dark, it's up to the scientists and Murderbot to get to the truth.
The Stormlight Archive by Brandon Sanderson
An epic fantasy saga spanning multiple books and worlds, featuring magic, war, and the return of the ancient Knights Radiant. The first installment is:
The Way of Kings
Roshar is a world of stone and storms. Uncanny tempests of incredible power sweep across the rocky terrain so frequently that they have shaped ecology and civilization alike. Animals hide in shells, trees pull in branches, and grass retracts into the soilless ground. Cities are built only where the topography offers shelter. It has been centuries since the fall of the ten consecrated orders known as the Knights Radiant, but their Shardblades and Shardplate remain: mystical swords and suits of armor that transform ordinary men into near-invincible warriors. Men trade kingdoms for Shardblades. Wars were fought for them, and won by them. One such war rages on a ruined landscape called the Shattered Plains. There, Kaladin, who traded his medical apprenticeship for a spear to protect his little brother, has been reduced to slavery. In a war that makes no sense, where ten armies fight separately against a single foe, he struggles to save his men and to fathom the leaders who consider them expendable. Brightlord Dalinar Kholin commands one of those other armies. Like his brother, the late king, he is fascinated by an ancient text called The Way of Kings. Troubled by over-powering visions of ancient times and the Knights Radiant, he has begun to doubt his own sanity. Across the ocean, an untried young woman named Shallan seeks to train under an eminent scholar and notorious heretic, Dalinar's niece, Jasnah. Though she genuinely loves learning, Shallan's motives are less than pure. As she plans a daring theft, her research for Jasnah hints at secrets of the Knights Radiant and the true cause of the war. The result of over ten years of planning, writing, and world-building, The Way of Kings is but the opening movement of the Stormlight Archive, a bold masterpiece in the making. Speak again the ancient oaths: Life before death. Strength before weakness. Journey before Destination. and return to men the Shards they once bore. The Knights Radiant must stand again.
and last one for now
Deltora Quest by Emily Rodda
Deltora Quest is the collective title for three distinct series of children's fantasy books. It's a series I read consistently throughout my childhood and it's one I still enjoy as an adult. The overall synopsis for the first series is:
For centuries, the evil Shadow Lord has been plotting to invade Deltora and enslave its people. All that stands in his way is the magic Belt of Deltora with its seven gems of great and mysterious power. Now, Leif, Barda, and Jasmine must unite to find the seven gems and save Deltora from an eternity of darkness.
I tag @wickedthemusicalaustralia @astillnight @stunt-muppet @beeawolf and @avatarofterminus if you want to give some recommendations! No obligation, of course <3
#tag game#books!#i need more books to read#honorary mention to into the dusk and cloud chaser those are beloved#and the ultimates series is also a fun read
6 notes
·
View notes
Text
Google Beefs up Android Security with Theft Protection, Live Threat Detection, and More
http://i.securitythinkingcap.com/T6xtTh
2 notes
·
View notes
Text

Anti-lost Wallet Tracker: a must-have accessory for the modern gentleman. Crafted with genuine leather, this smart wallet tracker is compatible with Android and iOS devices. With advanced features like anti-theft protection, lost item locator, and positioning, it ensures your valuables are always safe. The built-in rechargeable battery guarantees uninterrupted usage, while the sleek design adds a touch of style to your ensemble. Whether you're going to the office or out for a night on the town, the Anti-lost Wallet Tracker is your perfect companion. Keep your essentials secure and stay worry-free with this indispensable gadget.
12 notes
·
View notes
Text
The Top Enterprise Mobility Management Solution for 2023

Enterprise mobility management is an integral cog in a business machine. A company with a large fleet of mobile devices under its workforce would need a system to keep these devices in check. Especially when a corporate handle BYOD.
Enterprise mobile device management is the best bet to do that. It allows corporates to control, manage, and monitor the mobile devices under them, and evaluate employee mobile behaviour efficiently. However, when it comes to choosing the best enterprise mobility management solutions, it can get quite confusing.
EMM solutions are an evolving set of technologies that carry varied features depending upon the requirement of a business. So how can you choose the best enterprise mobility management (EMM) software for your business?
That’s not too difficult if you know what your company’s requirements are and what type of EMM solutions suits you best. For instance, one of the best enterprise mobility management solutions in the market is Tabnova’s NovaEMM.
NovaEMM
Tabnova’s NovaEMM houses a suite of features and administrative control, which also includes the ability to centrally and remotely control the use of mobile devices in workplaces under corporate mobility guidelines. This enterprise mobility management system brings in elements like application management, enrolment, security, remote monitoring, etc.
Let’s take a brief look into these features:
1. Application Management: With NovaEMM, the company can control how applications are used by the end user. They can decide which applications should be downloaded from Play Store, and which applications are to be blacklisted from being downloaded. Moreover, the enterprise mobile device management system has the ability to access corporate networks and interact with them. With such a system in tow, the company can even set auto-update policies and choose which software version should play on the corporate devices.
2. Enrolment: NovaEMM makes it easy to deploy any software or application onto corporate-owned devices. Android Enterprise enrolment and KNOX mobile enrolment are quite easily done, along with clientless enrolment using QR codes.
3. Security: There is comprehensive security for devices through various features, like password enforcers. The fleet of mobile devices can be controlled to determine which applications need to be given access. Moreover, if any device is stolen or lost, or missing, then the administrator can impose a lockdown on that specific device and ensure that the data within the device is not lost or stolen in any manner.
4. Remote Monitoring: With Tabnova’s suite of EMM, the administrator can screen share any data that is needed onto the fleet of mobile devices under them. Additionally, the admin can set up alerts as well as a messaging system that will deliver any information or data required to the fleet of devices under the company policy.
5. Compliance: Tabnova’s EMM system ticks off all the regulatory standards and is GDPR compliant. There are data protection agreements set in place to prevent any theft of data or unauthorised use of information. When following the GDPR regulations, there are a few protocols in place:
· Enforcing Passcode requirements
· Data encryption on a device
· Deploy and Enforce settings and restrictions
· Separate work and personal space on a device
· Wipe sensitive information
· Blacklist applications
· Generate reports for data security
· Factory reset stolen devices
Benefits of NovaEMM
When you start using NovaEMM, you are treated to a host of benefits, from affordability to robust security. Let’s look at what advantages a company can reap from using NovaEMM.
1. Multiple Kiosk Options: You can set up any type of desired Kiosk, like a Single App Kiosk, Browser Kiosk, Dashboard Kiosk, and Video Looper Kiosk.
2. Multiplatform Support: NovaEMM is capable of efficiently functioning on any platform, be it Android, MacOS, iOS, Windows, etc.
3. Enterprise Apps: You are able to access a suite of enterprise apps that comes with NovaEMM. These apps can be deployed according to company requirements as and when required.
4. DRM Content Delivery: Any online content, be it audio or video, that is used for live streaming can be encrypted and DRM protected to prevent piracy and unauthorised use.
With NovaEMM, businesses can manage and protect their mobile devices without any hassles, while enhancing their employee productivity, and that too at an affordable cost. While Tabnova is a leading provider of EMM software, there are other peers in the market as well.
Some of the other best enterprise mobility management (EMM) software that is available include the following – Codeproof, Amtel, Filewave, IBM, Microsoft EMM, Manage Engine, SOTI, Ivanti, VMware AirWatch, Miradore, Sophos, Scalefusion.
Contact us
Email Us
For More Information Click here
2 notes
·
View notes
Text
Insurance Claims with Leevaapp’s Home Inventory Management Software
When it comes to protecting your home and belongings, one of the most crucial yet often overlooked steps is keeping an organized home inventory. Whether you’re dealing with a theft, fire, or natural disaster, having a comprehensive inventory can make all the difference when filing a home insurance claim. Fortunately, with Leevaapp’s Home Inventory Management Software, managing your home’s assets and filing insurance claims has never been easier.
Why You Need a Home Inventory for Insurance Claims
The home insurance claims process can be overwhelming, especially when it comes time to prove the value of your lost or damaged property. Insurance companies typically require a detailed list of your belongings, their purchase dates, and their value. Without a well-maintained inventory, this can quickly become a daunting task.
Having a reliable home inventory management system allows you to document everything from furniture to electronics, ensuring you’re fully prepared when you need to file a claim. With Leevaapp, you can easily create a secure digital inventory of your assets, which will help expedite the claims process.
Features of Leevaapp’s Home Inventory Management Software
Leevaapp’s home inventory management software is designed to simplify the organization of your belongings while providing you with peace of mind. Here are a few key features of this easy-to-use app:
Secure Cloud Storage – Store your inventory securely in the cloud, so you can access it anytime, anywhere, on your iOS or Android device.
Photo and Documentation Upload – Capture photos of your possessions, record serial numbers, and document important details like purchase receipts or warranties.
Comprehensive Asset Management – Manage everything in one place—furniture, electronics, clothing, and even collectibles—giving you a complete overview of your home’s contents.
Easy Updates – Update your inventory in real time, ensuring that your list is always current.
Fast Insurance Claims – When disaster strikes, use your inventory data to quickly submit claims and avoid delays.
Why Choose Leevaapp for Asset Management?
In addition to home inventory management, Leevaapp is an excellent tool for overall asset management. The app helps you track both valuable and everyday items, creating an organized record of your possessions, which can be particularly useful for both insurance purposes and personal tracking. Whether you're managing household items, business assets, or personal valuables, Leevaapp ensures that everything is accounted for and easily accessible.
Benefits of Using Leevaapp
Time-Saving: Instead of manually listing each item for your insurance claim, Leevaapp does it for you, saving time and effort.
Peace of Mind: Knowing that your inventory is secure and accessible at all times gives you peace of mind in case of emergencies.
Maximized Claims: With accurate, up-to-date inventory details, you ensure you’re fully covered and can maximize your claims, ensuring a smoother recovery process.
Download Leevaapp Today
Take control of your home inventory today and simplify your home insurance claims process with Leevaapp. Download the app for iOS on the App Store or for Android on Google Play.
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] ESET Mobile Security provides superior security for your Android smartphone or tablet. Enjoy premier protection against viruses, trojans, ransomware and other malware which can expose your sensitive information or encrypt your data. Proactive Anti-Theft protection can also help you locate a missing device. Real-time Scanning - Ensures that all installation files and installed apps are automatically screened for malware. You stay well-protected against online and offline threats including viruses, trojans and ransomware. App Lock - Keeps your applications safe against unauthorized access. Additional authentication is required when accessing sensitive apps so content can be hidden when lending the device to someone. Anti-Phishing - Protects against malicious websites attempting to acquire your sensitive information – usernames, passwords, banking information or credit card details. Connected Home Monitor - Monitor your home network easily and with confidence. All devices connected to your home network are identified and automatically checked for vulnerabilities. Your router is also monitored to identify vulnerabilities and increase your level of protection when connected to a new network. Password strength is also checked and open ports are analyzed. Apps Permissions - See which of your apps has access to what information on your smartphone or tablet. Also monitors sensitive device settings that can lower security such as Debugging Mode that can allow a connection to the system via USB. Proactive Anti-Theft - It acts when it detects suspicious behavior. If incorrect Screen lock (PIN, pattern, password) or unauthorized SIM is inserted, device gets locked and snapshots from phone cameras are automatically sent.The information includes the phone‘s location, current IP address, inserted SIM details and other data. The user can mark the device as missing and start Location tracking or send Custom on-screen Message or even Wipe the device contents. Code will be mailed to the Amazon registered email ID within 2 hours of ordering or check 'Buyer/Seller messages' under Message Center at "amazon.in/msg" Antivirus; Anti-Phishing; ESET Live Grid App Lock; Proactive Anti-Theft; Location Tracking Connected Home Monitor; USB On-The-Go Scanner; Security Audit Apps Permissions; Scheduled Scan; Low Battery Alert SIM Guard; Remote Lock; Remote Siren;Tablet Support [ad_2]
0 notes
Text
Protecting Your Device: Best Practices for Safe App Downloads
The convenience of mobile apps has transformed how we interact with technology, providing solutions for productivity, entertainment, and communication. However, this convenience comes with risks if you’re not careful about where and how you download apps. In this blog, we’ll dive into the best practices for ensuring secure app downloads and protecting your personal data on mobile devices.
Why You Should Stick to Official App Stores
The simplest and most effective way to ensure safe app downloads is by using trusted platforms like the Google Play Store and Apple App Store. Here’s why:
Rigorous Security Measures: Both Google and Apple invest heavily in security protocols to vet apps before they’re made available. Apps are scanned for malware, phishing attempts, and other harmful behaviors. While some malicious apps occasionally slip through, they’re quickly identified and removed.
Regular Updates: Official app stores ensure that apps are regularly updated to patch vulnerabilities, add features, and improve performance. Downloading from unofficial sources often means missing these critical updates, leaving your device exposed to security risks.
Trustworthy Reviews and Ratings: App stores have extensive user reviews and ratings that can help you identify problematic apps. Fake reviews are still possible, but by checking for consistent patterns, you can spot genuine feedback.
Protection Against Malware: Third-party sources often distribute modded or pirated versions of apps that may include malware. Official stores significantly reduce this risk by monitoring for suspicious activity and enforcing strict developer guidelines.
Takeaway: If an app isn’t available on the official store, it’s worth questioning whether it’s safe to download at all.
Tips for Spotting Fake or Malicious Apps
Even when using official app stores, it’s essential to stay vigilant. Fake apps can mimic legitimate ones, tricking users into downloading harmful software. Here’s how to spot and avoid them:
Check the Developer’s Name: Always verify the app’s developer. For example, if you’re downloading Truecaller, ensure the developer is “Truecaller” or an officially affiliated name. Fake apps often use similar-sounding names to deceive users.
Scrutinize Reviews and Ratings:
Red Flags: Apps with overwhelmingly positive reviews that lack detail or context may have fake ratings.
Read Critical Reviews: Negative reviews often reveal issues with malware or misleading features.
Pay Attention to the Download Count: Popular apps usually have millions of downloads. A low download count for an app claiming to be well-known is suspicious.
Examine Permissions: Be cautious of apps that request excessive or unnecessary permissions. For example, a calculator app shouldn’t need access to your contacts or location.
Review the App Description: Legitimate apps typically have well-written descriptions without spelling errors or vague information. Poor grammar can be a sign of a hastily developed fake app.
Using Antivirus Software on Mobile Devices
Antivirus software isn’t just for computers anymore — it’s an essential tool for mobile devices too. Here’s how it helps:
Real-Time Protection: Antivirus apps can scan downloads in real time to detect malware or phishing attempts before they affect your device.
Blocking Unsafe Websites: Many antivirus apps offer browsing protection, alerting you to malicious websites or downloads while you’re online.
Scanning Existing Files: If you suspect you’ve downloaded a harmful app, antivirus software can scan your device and remove threats.
Added Features: Some antivirus solutions include VPNs, identity theft monitoring, and data breach alerts, providing a comprehensive security suite.
Top Antivirus Apps for Mobile Devices:
Android: Norton Mobile Security, Avast Mobile Security, Bitdefender Mobile Security.
iOS: While iPhones have strong built-in security, apps like McAfee or Lookout can add an extra layer of protection.
How to Secure Your Device in Case of Accidental Downloads
Sometimes, despite your best efforts, you may unknowingly download a harmful app. Here’s how to mitigate the damage:
Uninstall the App Immediately: Go to your device settings, locate the app, and uninstall it. Don’t just delete the icon from your home screen — ensure the app is entirely removed.
Revoke App Permissions: Before uninstalling, revoke any permissions the app may have had access to, such as your camera, contacts, or storage.
Scan Your Device: Use trusted antivirus software to perform a complete scan of your device. This will help identify and remove lingering malware or files left behind by the app.
Reset Passwords: If the app may have accessed sensitive data, change passwords for your accounts. Enable two-factor authentication (2FA) for added security.
Monitor Your Accounts: Keep an eye on bank accounts, email, and social media for any suspicious activity. If you notice anything unusual, report it to the relevant service provider immediately.
Perform a Factory Reset (If Necessary): In extreme cases where malware persists, a factory reset may be required. Ensure you back up important data first, and restore only from a clean backup.
Additional Tips for Secure App Usage
Enable Automatic Updates: Keeping your apps and operating system updated ensures you’re protected against known vulnerabilities.
Avoid Clicking Unknown Links: Phishing scams often lure users into downloading harmful apps or providing personal information. Be cautious about links received via email, SMS, or social media.
Use App Permissions Wisely: Periodically review and revoke permissions for apps you no longer use.
Be Skeptical of Free Offers: Apps promising “premium features for free” are often too good to be true and may compromise your security.
Conclusion
In today’s digital age, safeguarding your device from harmful apps is more critical than ever. By sticking to official app stores, scrutinizing downloads, using antivirus software, and taking swift action in case of accidental downloads, you can significantly reduce the risk of security breaches.
Your mobile device holds a treasure trove of personal data — treat it with care, and you’ll enjoy a safer, worry-free app experience. Remember, when it comes to security, a little vigilance goes a long way!
0 notes
Text
OxygenOS 15 Unveiled With New AI Features, Redesigned UI and Default Gemini Assistant | Daily Reports Online
OnePlus unveiled its OxygenOS 15 update on Thursday. The new operating system (OS) update for eligible OnePlus smartphones will introduce a redesigned user interface, artificial intelligence (AI) features, and faster processing. Based on Android 15, which was recently released by Google, the update also brings new security features such as Google Play Protect’s live threat detection and theft…
0 notes
