#Android Spy Apps
Explore tagged Tumblr posts
Text

0 notes
Text

From the Hi Color App!
10 notes
·
View notes
Text
BlurSPY Undetectable Spy App for Android - Remotely Tracker For Kids Digital Devices.
For all such #distressed #parents who are #working 24/7 in their #workplaces, BlurSPY is 100% #undetectable #spyware for #android is a #blessing in the hour of need. BlurSPY is a #fully #undetectable #spyware for #AndroidPhones. #parents can #remotely #Install #BlurSPY application on #Kids #smartphone devices.
#teens#blurspy#spy app#workplace#tracking#android spy#tracker#social media#business#education#undetectable spy app
5 notes
·
View notes
Text
Appeared on my COMPANY phone without consent from me or my company's IT.
Nip the fucker in the butt.
hey folks if you have an android phone: google shadow installed a "security app".
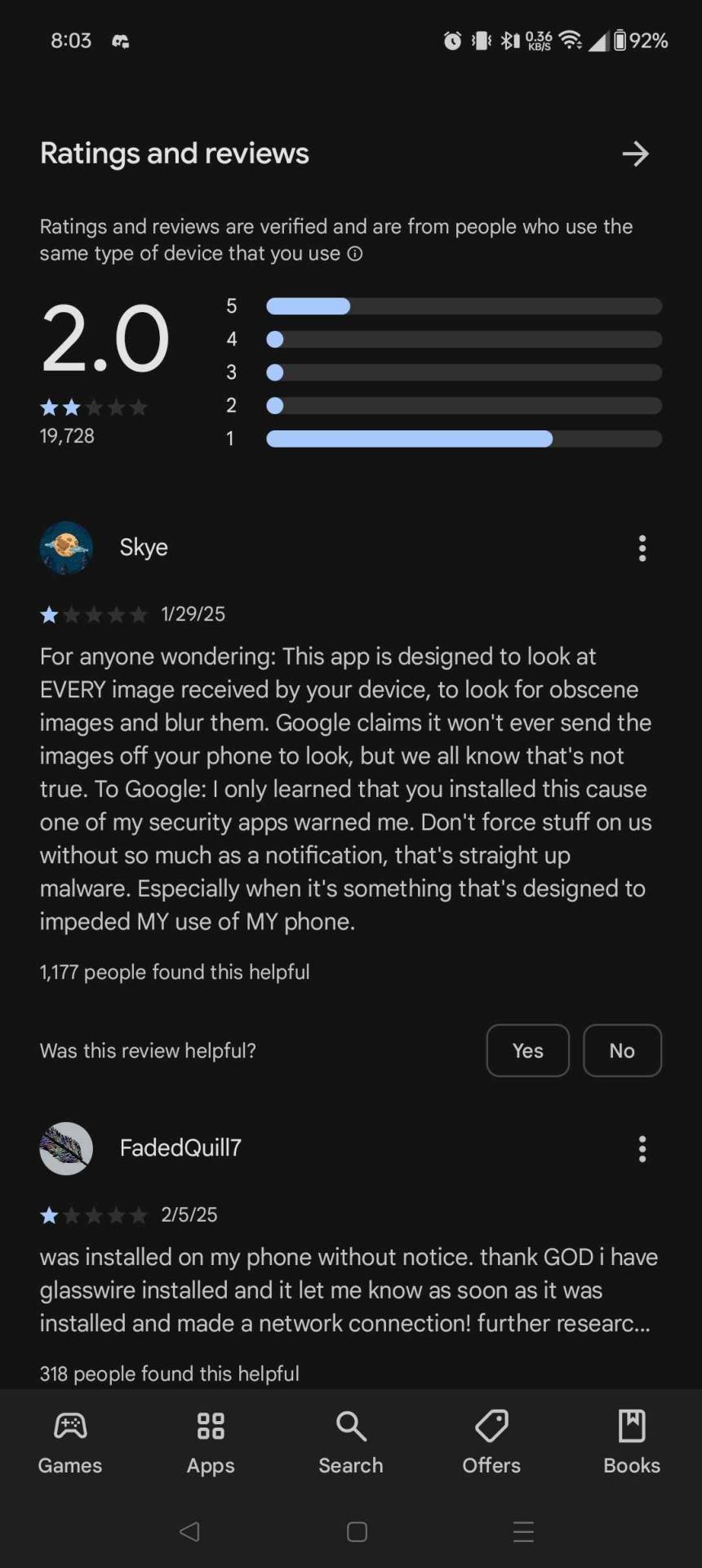
I had to go and delete it myself this morning.
81K notes
·
View notes
Text
CHYLDMONITOR Mobile Spy for Android

Get CHYLDMONITOR, the ultimate mobile spy solution tailored for Android devices. Seamlessly monitor phone activities, including call logs, messages, and app usage, all from a centralized control panel. With CHYLDMONITOR, you can ensure the safety of your children or enhance employee productivity by keeping an eye on their digital interactions. Experience top-notch Android monitoring today.
Protect and monitor effectively. Download CHYLDMONITOR for Android!
#mobile spy app#mobile spy software#mobile spy for android#mobile spy download#mobile spy without access to phone#mobile spy app hidden#mobile spy app undetectable#mobile spy parental control#mobile spy app with GPS tracking#mobile spy app features
0 notes
Text
Best Cell Phone Tracking Software | Mobistealth

Mobistealth is the ultimate Cell Phone Tracker platform because it monitors location even when traditional GPS-based applications fail. We provide additional cell phone surveillance tools to help you track and record all activities on mobile devices of kids and employees that you own. Once installed, our comprehensive cell phone tracking software will begin recording all activities. It shall send the data to your Mobistealth user account, including real-time and historical cell phone tracking data. Mobistealth is truly the ultimate Cell Phone Tracking software because in addition to tracking a monitored mobile device.
Visit Us: https://www.mobistealth.com/cell-phone-tracker
#Best-Cell-Phone-Spy-Apps#Best-Spy-App-For-Phone#Spying-Apps-For-iPhone#Best-Spyware-For-Android#Spy-Phone-Apps
0 notes
Text
Why choose ONEMONITAR for Call Monitoring and Recording?
Hey there!
I stumbled upon ONEMONITAR when I was in a fix managing my work calls and needed a reliable solution for call monitoring and recording. Let me tell you, it's been a game-changer in both my professional and personal life.
I work in sales, and you know how hectic it can get juggling numerous client calls. ONEMONITAR became my trusty sidekick – the superhero of call management. The crystal-clear recording feature saved me more times than I can count. Imagine having a record of every crucial detail discussed in a client meeting! It's like having a backup brain, seriously.
And it's not just about work – even in personal situations, ONEMONITAR has been handy. I once had a call with a service provider that got a bit messy. Thanks to ONEMONITAR, I had proof of the entire conversation, which made sorting things out a breeze.
What sets it apart is the simplicity and reliability. It's not just a tool; it's a stress-buster. So, why choose ONEMONITAR? Because it's not just about recording calls; it's about having peace of mind and control in the palm of your hand. Read full Blog
0 notes
Text
Legit app in Google Play turns malicious and sends mic recordings every 15 minutes
The malicious iRecorder app has come to light, but its purpose remains shrouded. An app that had more than 50,000 downloads from Google Play surreptitiously recorded nearby audio every 15 minutes and sent it to the app developer, a researcher from security firm ESET said. Continue reading Untitled

View On WordPress
0 notes
Text
Best Android Spy App 2023
In today’s world, there is an increasing need for people to monitor their loved ones or employees’ activities on their mobile devices. With so much confidential information being exchanged on mobile devices, including social media accounts, messaging apps, and call logs, it has become important to keep a tab on what people are doing on their phones. While there are various spy apps available in…

View On WordPress
0 notes
Text
Best spy applications for android, like phone spy apps, make it easy to monitor the activity on a smartphone. These surveillance tools provide real-time access to information such as a phone’s location, incoming and outgoing calls, SMS messages, GPS coordinates, web browser activity, and messages from popular social media apps like WhatsApp, Facebook, and Snapchat. The best spy applications are designed to be invisible to the end user. They cannot be detected, making them useful tools for keeping an eye on loved ones, monitoring employees, or tracking personal phone usage.
Are Spy Applications Legal?
Before considering “Best Spy Applications For Android,” it’s crucial to understand the laws in your region. Different locations have varying regulations regarding the use of spyware. Ensure it’s legal where you reside before installing one of these apps on someone else’s phone. Most areas prohibit monitoring a device without the owner’s consent, so do thorough research and ensure you’re adhering to the regulations. To stay on the safe side, be informed about the laws in your area and remember that unauthorized use of Spy Applications can lead to legal consequences.
How To Install Spy Apps On Target Device
Installing the “Best Spy Applications For Android” on a target device is easy. The easiest way is to borrow the phone for a call, leave the room to continue the conversation, and use that privacy to download and install the app. During the initial setup, you’ll need to enter your username and password to connect to the dashboard, which usually takes less than ten minutes. Once installed, the app will enter stealth mode and won’t be detected.
With just one touch of the target device, you can use your phone or computer to monitor the user’s location and activities secretly. So, whether you’re looking to keep track of your children or monitor the activities of your employees, “Best Spy Applications For Android” is the solution you need. Read more: https://techplnt.com/best-spy-applications-for-android/
#best spy applications for android#free remote monitoring app for android#mobile spy app#mspy for android#spy app for iphone
0 notes
Text
Android Spy App for Calls, Chats and Location Tracking by ONEMONITAR
With Android spy app by ONEMONITAR you can access to the calls, chats and location history and real time updates on the target device. You just need to install this application on the other device which is going to be monitored for digital safety or work related monitoring. Start monitoring today with ONEMONITAR.

0 notes
Text

From the HiColor App on Samsung Galaxy!
16 notes
·
View notes
Text
Reverse engineers bust sleazy gig work platform

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/11/23/hack-the-class-war/#robo-boss

A COMPUTER CAN NEVER BE HELD ACCOUNTABLE
THEREFORE A COMPUTER MUST NEVER MAKE A MANAGEMENT DECISION
Supposedly, these lines were included in a 1979 internal presentation at IBM; screenshots of them routinely go viral:
https://twitter.com/SwiftOnSecurity/status/1385565737167724545?lang=en
The reason for their newfound popularity is obvious: the rise and rise of algorithmic management tools, in which your boss is an app. That IBM slide is right: turning an app into your boss allows your actual boss to create an "accountability sink" in which there is no obvious way to blame a human or even a company for your maltreatment:
https://profilebooks.com/work/the-unaccountability-machine/
App-based management-by-bossware treats the bug identified by the unknown author of that IBM slide into a feature. When an app is your boss, it can force you to scab:
https://pluralistic.net/2023/07/30/computer-says-scab/#instawork
Or it can steal your wages:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
But tech giveth and tech taketh away. Digital technology is infinitely flexible: the program that spies on you can be defeated by another program that defeats spying. Every time your algorithmic boss hacks you, you can hack your boss back:
https://pluralistic.net/2022/12/02/not-what-it-does/#who-it-does-it-to
Technologists and labor organizers need one another. Even the most precarious and abused workers can team up with hackers to disenshittify their robo-bosses:
https://pluralistic.net/2021/07/08/tuyul-apps/#gojek
For every abuse technology brings to the workplace, there is a liberating use of technology that workers unleash by seizing the means of computation:
https://pluralistic.net/2024/01/13/solidarity-forever/#tech-unions
One tech-savvy group on the cutting edge of dismantling the Torment Nexus is Algorithms Exposed, a tiny, scrappy group of EU hacker/academics who recruit volunteers to reverse engineer and modify the algorithms that rule our lives as workers and as customers:
https://pluralistic.net/2022/12/10/e2e/#the-censors-pen
Algorithms Exposed have an admirable supply of seemingly boundless energy. Every time I check in with them, I learn that they've spun out yet another special-purpose subgroup. Today, I learned about Reversing Works, a hacking team that reverse engineers gig work apps, revealing corporate wrongdoing that leads to multimillion euro fines for especially sleazy companies.
One such company is Foodinho, an Italian subsidiary of the Spanish food delivery company Glovo. Foodinho/Glovo has been in the crosshairs of Italian labor enforcers since before the pandemic, racking up millions in fines – first for failing to file the proper privacy paperwork disclosing the nature of the data processing in the app that Foodinho riders use to book jobs. Then, after the Italian data commission investigated Foodinho, the company attracted new, much larger fines for its out-of-control surveillance conduct.
As all of this was underway, Reversing Works was conducting its own research into Glovo/Foodinho's app, running it on a simulated Android handset inside a PC so they could peer into app's data collection and processing. They discovered a nightmarish world of pervasive, illegal worker surveillance, and published their findings a year ago in November, 2023:
https://www.etui.org/sites/default/files/2023-10/Exercising%20workers%20rights%20in%20algorithmic%20management%20systems_Lessons%20learned%20from%20the%20Glovo-Foodinho%20digital%20labour%20platform%20case_2023.pdf
That report reveals all kinds of extremely illegal behavior. Glovo/Foodinho makes its riders' data accessible across national borders, so Glovo managers outside of Italy can access fine-grained surveillance information and sensitive personal information – a major data protection no-no.
Worse, Glovo's app embeds trackers from a huge number of other tech platforms (for chat, analytics, and more), making it impossible for the company to account for all the ways that its riders' data is collected – again, a requirement under Italian and EU data protection law.
All this data collection continues even when riders have clocked out for the day – its as though your boss followed you home after quitting time and spied on you.
The research also revealed evidence of a secretive worker scoring system that ranked workers based on undisclosed criteria and reserved the best jobs for workers with high scores. This kind of thing is pervasive in algorithmic management, from gig work to Youtube and Tiktok, where performers' videos are routinely suppressed because they crossed some undisclosed line. When an app is your boss, your every paycheck is docked because you violated a policy you're not allowed to know about, because if you knew why your boss was giving you shitty jobs, or refusing to show the video you spent thousands of dollars making to the subscribers who asked to see it, then maybe you could figure out how to keep your boss from detecting your rulebreaking next time.
All this data-collection and processing is bad enough, but what makes it all a thousand times worse is Glovo's data retention policy – they're storing this data on their workers for four years after the worker leaves their employ. That means that mountains of sensitive, potentially ruinous data on gig workers is just lying around, waiting to be stolen by the next hacker that breaks into the company's servers.
Reversing Works's report made quite a splash. A year after its publication, the Italian data protection agency fined Glovo another 5 million euros and ordered them to cut this shit out:
https://reversing.works/posts/2024/11/press-release-reversing.works-investigation-exposes-glovos-data-privacy-violations-marking-a-milestone-for-worker-rights-and-technology-accountability/
As the report points out, Italy is extremely well set up to defend workers' rights from this kind of bossware abuse. Not only do Italian enforcers have all the privacy tools created by the GDPR, the EU's flagship privacy regulation – they also have the benefit of Italy's 1970 Workers' Statute. The Workers Statute is a visionary piece of legislation that protects workers from automated management practices. Combined with later privacy regulation, it gave Italy's data regulators sweeping powers to defend Italian workers, like Glovo's riders.
Italy is also a leader in recognizing gig workers as de facto employees, despite the tissue-thin pretense that adding an app to your employment means that you aren't entitled to any labor protections. In the case of Glovo, the fine-grained surveillance and reputation scoring were deemed proof that Glovo was employer to its riders.
Reversing Works' report is a fascinating read, especially the sections detailing how the researchers recruited a Glovo rider who allowed them to log in to Glovo's platform on their account.
As Reversing Works points out, this bottom-up approach – where apps are subjected to technical analysis – has real potential for labor organizations seeking to protect workers. Their report established multiple grounds on which a union could seek to hold an abusive employer to account.
But this bottom-up approach also holds out the potential for developing direct-action tools that let workers flex their power, by modifying apps, or coordinating their actions to wring concessions out of their bosses.
After all, the whole reason for the gig economy is to slash wage-bills, by transforming workers into contractors, and by eliminating managers in favor of algorithms. This leaves companies extremely vulnerable, because when workers come together to exercise power, their employer can't rely on middle managers to pressure workers, deal with irate customers, or step in to fill the gap themselves:
https://projects.itforchange.net/state-of-big-tech/changing-dynamics-of-labor-and-capital/
Only by seizing the means of computation, workers and organized labor can turn the tables on bossware – both by directly altering the conditions of their employment, and by producing the evidence and tools that regulators can use to force employers to make those alterations permanent.

Image: EFF (modified) https://www.eff.org/files/issues/eu-flag-11_1.png
CC BY 3.0 http://creativecommons.org/licenses/by/3.0/us/
#pluralistic#etui#glovo#foodinho#alogrithms exposed#reverse engineering#platform work directive#eu#data protection#algorithmic management#gdpr#privacy#labor#union busting#tracking exposed#reversing works#adversarial interoperability#comcom#bossware
352 notes
·
View notes
Text
crowdstrike: hot take 1
It's too early in the news cycle to say anything truly smart, but to sum things up, what I know so far:
there was no "hack" or cyberattack or data breach*
a private IT security company called CrowdStrike released a faulty update which practically disabled all its desktop (?) Windows workstations (laptops too, but maybe not servers? not sure)
the cause has been found and a fix is on the way
as it stands now, the fix will have to be manually applied (in person) to each affected workstation (this could mean in practice maybe 5, maybe 30 minutes of work for each affected computer - the number is also unknown, but it very well could be tens (or hundreds) of thousands of computers across thousands of large, multinational enterprises.
(The fix can be applied manually if you have a-bit-more-than-basic knowledge of computers)
Things that are currently safe to assume:
this wasn't a fault of any single individual, but of a process (workflow on the side of CrowdStrike) that didn't detect the fault ahead of time
[most likely] it's not that someone was incompetent or stupid - but we don't have the root cause analysis available yet
deploying bugfixes on Fridays is a bad idea
*The obligatory warning part:
Just because this wasn't a cyberattack, doesn't mean there won't be related security breaches of all kinds in all industries. The chaos, panic, uncertainty, and very soon also exhaustion of people dealing with the fallout of the issue will create a perfect storm for actually malicious actors that will try to exploit any possible vulnerability in companies' vulnerable state.
The analysis / speculation part:
globalization bad lol
OK, more seriously: I have not even heard about CrowdStrike until today, and I'm not a security engineer. I'm a developer with mild to moderate (outsider) understanding of vulnerabilities.
OK some background / basics first
It's very common for companies of any size to have more to protect their digital assets than just an antivirus and a firewall. Large companies (Delta Airlines) can afford to pay other large companies to provide security solutions for them (CrowdStrike). These days, to avoid bad software of any kind - malware - you need a complex suite of software that protects you from all sides:
desktop/laptop: antivirus, firewall, secure DNS, avoiding insecure WiFi, browser exploits, system patches, email scanner, phishing on web, phishing via email, physical access, USB thumb drive, motherboard/BIOS/UEFI vulnerabilities or built-in exploits made by the manufacturers of the Chinese government,
person/phone: phishing via SMS, phishing via calls, iOS/Android OS vulnerabilities, mobile app vulnerabilities, mobile apps that masquerade as useful while harvesting your data, vulnerabilities in things like WhatsApp where a glitched JPG pictures sent to you can expose your data, ...
servers: mostly same as above except they servers have to often deal with millions of requests per day, most of them valid, and at least some of the servers need to be connected to the internet 24/7
CDN and cloud services: fundamentally, an average big company today relies on dozens or hundreds of other big internet companies (AWS / Azure / GCP / Apple / Google) which in turn rely on hundreds of other companies to outsource a lot of tasks (like harvesting your data and sending you marketing emails)
infrastructure - routers... modems... your Alexa is spying on you... i'm tired... etc.
Anyway if you drifted to sleep in the previous paragraph I don't blame you. I'm genuinely just scratching the surface. Cybersecurity is insanely important today, and it's insanely complex too.
The reason why the incident blue-screened the machines is that to avoid malware, a lot of the anti-malware has to run in a more "privileged" mode, meaning they exist very close to the "heart" of Windows (or any other OS - the heart is called kernel). However, on this level, a bug can crash the system a lot more easily. And it did.
OK OK the actual hot lukewarm take finally
I didn't expect to get hit by y2k bug in the middle of 2024, but here we are.
As bad as it was, this only affected a small portion of all computers - in the ballpark of ~0.001% or even 0.0001% - but already caused disruptions to flights and hospitals in a big chunk of the world.
maybe-FAQ:
"Oh but this would be avoided if they weren't using the Crowdwhatever software" - true. However, this kind of mistake is not exclusive to them.
"Haha windows sucks, Linux 4eva" - I mean. Yeah? But no. Conceptually there is nothing that would prevent this from happening on Linux, if only there was anyone actually using it (on desktop).
"But really, Windows should have a better protection" - yes? no? This is a very difficult, technical question, because for kernel drivers the whole point is that 1. you trust them, and 2. they need the super-powerful-unrestrained access to work as intended, and 3. you _need_ them to be blazing fast, so babysitting them from the Windows perspective is counterproductive. It's a technical issue with no easy answers on this level.
"But there was some issue with Microsoft stuff too." - yes, but it's unknown if they are related, and at this point I have not seen any solid info about it.
The point is, in a deeply interconnected world, it's sort of a miracle that this isn't happening more often, and on a wider scale. Both bugfixes and new bugs are deployed every minute to some software somewhere in the world, because we're all in a rush to make money and pay rent and meet deadlines.
Increased monoculture in IT is bad for everyone. Whichever OS, whichever brand, whichever security solution provider - the more popular they are, the better visible their mistakes will be.
As much as it would be fun to make jokes like "CrowdStroke", I'm not even particularly mad at the company (at this point - that might change when I hear about their QA process). And no, I'm not even mad at Windows, as explained in the pseudo-FAQ.
The ultimate hot take? If at all possible, don't rely on anything related to computers. Technical problems are caused by technical solutions.
#crowdstrike#cybersecurity#anyway i'm microdosing today so it's probably too boring to read#but hopefully it at least mostly made sense#to be honest I wanted to have more of a hot take#but the truth is mundane
74 notes
·
View notes
Text

Discover the power of the Android Spy App by ChyldMonitor, designed to provide parents with essential monitoring tools to ensure their child’s safety online.
0 notes
Text
a list of my favourite Bree plot episodes because Bree is the best and needs more love. This will not include episodes in which ABC all get a plot together, just Bree or maybe a Bree duo.
Notice how in most of these Bree only gets the B plot :(
Smart and Smarter (01.07) - Leo uses Bree as his personal taxi service
Death Spiral Smackdown (01.09) - Bree and Chase use their bionics to embarrass eachother at school
Can I Borrow the Helicopter? (01.10) - Bree gets her own room but still doesn't get privacy
Air Leo (01.16) - Bree and Adam compete for the last spot on the cheer squad (this is my favourite episode of all time for multiple reasons btw)
Night of the Living Virus (01.17) - Bree holds a sleepover to impress some mean girls at school
Concert in a Can (01.19) - Bree signs her and Davenport up for a career fair to spend time with him, but he blows her off and changes the project last minute
Spy Fly (02.02) - Leo terrorizes Bree with his newest toy and she gets her revenge
Quarantined (02.04) - Bree gets exposed to a dangerous chemical on a mission, ignores her quarantine to hang out with a boy she likes
Bro Down (02.06) - Bree discovers her vocal manipulation and uses it to cause chaos at school
Spikes Got Talent (02.09) - Bree gets jealous that Owen is getting along so well with her brother, so she sabotages their sculpture
Adam Up (02.18) - Bree and Chase get stuck babysitting Perry's evil niece
Llama Drama (02.19) - Bree and Leo enter the Domino Domination contest at school
The Haunting of Mission Creek High (02.20) - Bree gets assigned to decorate for the schools dance but gets in a fight with Owen over creative differences
Perry 2.0 (02.21) - Bree and Adam suspect a new student may be bionic and terrorize him until they can know for sure
My Little Brother (02.22) - after challenging Perry, Bree becomes principle for a day
Prank You Very Much (02.23) - Bree is fed up with being stuck in her brothers prank war, so she decides to prank them back
Trent Gets Schooled (02.25) - Bree's photo for picture day gets ruined when Adam messes up her hair and then messed it up even more
The Jet Wing (03.03) - Bree and Adam spend the day doing odd jobs for Perry and begin to glitch
Zip It (03.05) - Bree gets a job at Tech Town to get away from her brothers, but Chase starts worker there too
Not So Smart Phone (03.06) - Leo and Bree trick Perry into spending all her money so she can retire
Three Minus Bree (03.10) - Mad about her lack of freedom, Bree quits the team and smashes her chip
Spike Fright (03.18) - Bree and Leo investigate a supposed murder committed by Perry
Face Off (03.19) - Bree gets stuck in a cyber cloak as Perry, forcing Chase to go to the dance as her
Bionic Dog (04.05) - Bree and Leo fight over his phones ai assistant
Simulation Manipulation (04.07) - Leo is mad at Bree for never picking up after herself and they get into a trash war
Spider Island (04.09) - Adam is annoying Bree on her day off, Bree takes down a giant spider (not Bree centric but I love it when she gets to be the hero at the end of the day)
Spike vs Spikette (04.10) - Bree is given the commando app to battle it out with Kate
Bionic Action Hero (04.13-14) - Bree has a huge crush on Troy, when they discover he's an android working for Giselle, she is able to save the day (and her family) and defeat him for good. (God, I love when she gets to save the day!)
One of Us (04.15) - Adam and Bree make the best of their last day before they're killed by a virus
Human Eddy (04.17) - Leo and Bree discovers that Eddy isn't as reformed as they thought
The Ultimate Tailgate Challenge (04.21) - Bree and Chase try to impress college kids with their bionics
#Sorry it's long#Lab rats#Lab rats bionic Island#lrmmef#Levi#bree davenport#leo dooley#adam bree and chase#adam davenport#chase davenport#terry perry
11 notes
·
View notes