#8. Troubleshooting login issues
Explore tagged Tumblr posts
Text
Incfile login
#Certainly! Here are 10 tags related to the topic “Incfile login”:#1. Incfile#2. Business formation#3. Account access#4. Registration process#5. Secure login#6. Two-factor authentication#7. Password management#8. Troubleshooting login issues#9. Document storage#10. Business services
1 note
·
View note
Text
Which Server Issues Are Included In Server Management Plans?
Server management plans typically cover a wide range of server issues to ensure smooth operation, security, and performance. The exact coverage depends on the provider and service tier, but here are some common server issues included in most plans:
1. Performance Issues
Slow Server Response: Diagnosing high CPU, RAM, or disk usage affecting performance.
Latency & Network Bottlenecks: Optimizing network settings to reduce slow connections.
Server Crashes & Downtime: Identifying and fixing the root cause of unexpected crashes.
Resource Optimization: Managing server load and scaling resources as needed.
2. Security & Compliance Issues
Malware & Virus Infections: Detecting and removing malware that compromises server security.
Unauthorized Access & Hacking Attempts: Monitoring and blocking unauthorized login attempts.
Data Breaches & Compliance Violations: Ensuring compliance with regulations (GDPR, HIPAA, PCI DSS).
Firewall & DDoS Protection: Configuring security measures to prevent attacks.
3. Software & OS Issues
Operating System Updates & Patching: Keeping the server OS up to date to prevent vulnerabilities.
Software Conflicts & Compatibility Issues: Resolving issues caused by outdated or incompatible applications.
Application Errors & Failures: Troubleshooting server-hosted applications and services.
Control Panel Issues: Fixing errors with cPanel, Plesk, or other server management interfaces.
4. Hardware & Storage Issues
Disk Failures & RAID Issues: Monitoring storage health and replacing failing drives.
Overheating & Power Supply Failures: Ensuring proper cooling and power redundancy.
Memory & CPU Failures: Detecting and replacing failing hardware components.
5. Backup & Disaster Recovery Issues
Data Loss & Corruption: Regularly backing up data to prevent permanent loss.
Backup Failures: Ensuring scheduled backups run correctly and are restorable.
Disaster Recovery Planning: Implementing strategies to restore operations after failures.
6. Network & Connectivity Issues
DNS & Domain Issues: Resolving problems with domain name resolution.
IP Blacklisting & Email Deliverability: Fixing IP reputation issues that affect email services.
Bandwidth & Traffic Spikes: Managing high traffic loads and preventing overload.
7. Database Issues
Slow Database Queries: Optimizing queries and indexing for faster performance.
Corrupt Databases: Recovering and repairing damaged databases.
Database Connectivity Errors: Fixing connection issues between applications and databases.
8. User Management & Access Control Issues
Failed Login Attempts & Account Lockouts: Resolving access issues for authorized users.
Role-Based Access Control (RBAC) Issues: Managing user permissions and access levels.
What’s Usually Not Included?
Custom Software Development: Some plans may not cover fixing third-party or custom-built applications.
Physical Hardware Replacement: If the server is on-premises, you may need to handle hardware replacements separately.
Unlimited Support: Basic plans may have limits on monthly support hours or incidents.
A good server management plan ensures your server runs efficiently, remains secure, and minimizes downtime. If you have specific needs, it's best to discuss them with your provider to get a plan that fits your infrastructure.

0 notes
Text
Quick Tips for Re-Authorizing Google Accounts Using GMB Briefcase | Help Center
youtube
Re-authorizing your Google account is a vital task that ensures uninterrupted access to essential tools in GMB Briefcase. Whether you're managing multiple Google Business Profiles or streamlining local SEO efforts, maintaining an active connection is key. Here’s a quick guide to help you navigate the re-authorization process effortlessly using GMB Briefcase | Help Center.
Why Re-Authorization is Important
Google requires periodic re-authorization of connected accounts to enhance security and compliance. Re-authorization ensures that GMB Briefcase continues to operate seamlessly with your Google account, granting access to features like profile updates, performance analytics, and citation management.
Quick Tips for a Smooth Re-Authorization Process
1. Stay Ahead with Notifications
Tip: Enable notifications in GMB Briefcase to receive alerts when your Google account needs re-authorization. This proactive step helps avoid disruptions in account functionality.
2. Use the Correct Google Account
Tip: Double-check that you log in with the Google account linked to your GMB Briefcase. Switching between accounts may result in errors or mismatches.
3. Check Permissions Thoroughly
Tip: When prompted, ensure you grant all requested permissions during the re-authorization process. Partial permissions can limit functionality and require you to repeat the process.
4. Choose a Compatible Browser
Tip: Use a recommended browser like Google Chrome for the re-authorization process. Disable any pop-up blockers or ad-block extensions temporarily to prevent interruptions.
5. Ensure a Stable Internet Connection
Tip: Conduct the re-authorization process over a reliable internet connection. Unstable connectivity can lead to incomplete authorizations.
6. Clear Cache and Cookies
Tip: If you encounter issues, clearing your browser’s cache and cookies may resolve conflicts and enable a smoother re-authorization process.
7. Follow GMB Briefcase’s Step-by-Step Guide
Tip: Access the Help Center for a detailed guide to re-authorizing Google accounts. The step-by-step instructions simplify the process and address common challenges.
8. Keep Your Account Credentials Handy
Tip: Have your Google account login details ready. A quick login prevents delays and allows you to complete the process efficiently.
9. Regularly Monitor Account Status
Tip: Log into GMB Briefcase frequently to monitor the status of your connected Google accounts. Early detection of authorization issues ensures uninterrupted access.
10. Contact Support for Complex Issues
Tip: If you encounter persistent problems, don’t hesitate to reach out to GMB Briefcase | Help Center’s support team for expert assistance.
How GMB Briefcase Simplifies Re-Authorization
- User-Friendly Dashboard
Easily view account statuses and identify which accounts require re-authorization.
- Automated Alerts
Receive timely notifications about expiring authorizations, keeping you ahead of potential disruptions.
- Comprehensive Guides
Access clear, concise tutorials in the Help Center to guide you through the re-authorization process.
- Reliable Support
The GMB Briefcase support team is always ready to assist with troubleshooting and complex account-related queries.
Final Thoughts
Re-authorizing Google accounts doesn’t have to be a hassle. With the intuitive tools and resources provided by GMB Briefcase | Help Center, you can handle the process quickly and efficiently. By following these quick tips and leveraging the platform's features, you’ll ensure your accounts remain active, secure, and ready to power your business growth.
For more information and support, visit the GMB Briefcase | Help Center today!
Find Us Online
Facebook
LinkedIn
Twitter
YouTube Channel
0 notes
Text
Playmojo Login Secrets: Stay Connected Anytime, Anywhere

Accessing your Casino Play Mojo account is all about convenience and efficiency, ensuring you can stay connected wherever you are. With user-friendly features and robust security measures, Playmojo makes logging in effortless, whether you're at home or on the go. Here are the secrets to mastering your Casino Play Mojo login experience.
1. Seamless Login Process
Logging in is quick and simple:
Head to the Playmojo homepage and click the Login button in the top-right corner.
Enter your email address and password.
Hit Login, and you’re ready to explore.
For frequent users, enabling the Remember Me feature ensures faster access on your personal devices.
2. Easy Account Setup
New to Playmojo? Creating an account takes just a few steps:
Click Sign Up on the login page.
Fill in your details, including a valid email address and a secure password.
Verify your account through the email confirmation link.
Once registered, you can log in and start enjoying the platform instantly.
3. Mobile Access Made Simple
Playmojo is optimized for mobile use, offering the same seamless login experience on smartphones and tablets. Whether you’re using a browser or the app, logging in on the go has never been easier.
4. Social Login Integration
For even faster access, Playmojo allows you to log in using linked social media accounts. This one-click solution eliminates the need to manually input credentials while maintaining secure access.
5. Troubleshooting Login Issues
If you encounter problems logging in, try these quick fixes:
Ensure your email and password are entered correctly.
Use the Forgot Password link to reset your credentials if needed.
Update your browser or app to the latest version for optimal compatibility.
For persistent issues, Playmojo’s support team is always ready to help.
6. Prioritize Security
Stay secure while accessing your account by following these tips:
Always log in through the official website or app.
Use a strong, unique password and update it periodically.
Enable two-factor authentication (2FA) for enhanced protection.
7. Save Time with Smart Features
Playmojo’s login features are designed for convenience:
The Remember Me option saves your credentials for future visits.
Password recovery is simple—just follow the steps provided via the Forgot Password link.
8. Stay Updated
Keep your app or browser updated to access the latest features and maintain a smooth login experience.
Mastering the Playmojo login process ensures you’re always just a few clicks away from everything the platform has to offer. Whether you’re at home, traveling, or anywhere in between, staying connected has never been easier!
0 notes
Text
How to Fix “Activation Code Expired” on Disneyplus.com/Begin
Disney Plus is a leading streaming platform that brings a treasure trove of content from Disney, Pixar, Marvel, Star Wars, National Geographic, and more. However, users often encounter an issue during device activation on disneyplus.com/begin where they see the error message “Activation Code Expired.” This problem can disrupt the activation process, but fortunately, it is fixable. This guide explores the reasons behind this error and provides step-by-step solutions to resolve it.
What Is Disneyplus.com/Begin?
Disneyplus.com/Begin is a website used to activate Disney Plus on various devices like smart TVs, streaming sticks, gaming consoles, and other compatible gadgets. The activation process involves:
Installing the Disney Plus app on your device.
Logging into your account or creating a new one.
Entering an activation code displayed on the device screen at Disneyplus.com/Begin to link your account.
While this process is straightforward, errors like “Activation Code Expired” can occur, hindering your ability to activate the service.
Reasons for the “Activation Code Expired” Error
The “Activation Code Expired” error typically occurs due to the following reasons:
Time Limit Exceeded: Activation codes are time-sensitive and expire if not used promptly.
Incorrect Code Entry: Entering the wrong activation code can lead to errors.
Device or Network Issues: Connectivity issues or outdated app versions can disrupt the activation process.
Code Reuse: Activation codes are unique and cannot be reused after they expire.
Account Issues: Problems with your Disney Plus account, such as an expired subscription, can also trigger this error.
How to Fix the “Activation Code Expired” Error
Here are several methods to resolve the “Activation Code Expired” error on Disneyplus.com/Begin:
1. Generate a New Activation Code
If your activation code has expired, the simplest solution is to generate a new one. Follow these steps:
Open the Disney Plus app on your device.
Navigate to the login or activation section.
A new activation code will be displayed on the screen.
Visit Disneyplus.com/Begin on your computer or smartphone browser.
Enter the new activation code and follow the prompts to complete the process.
2. Ensure Timely Code Entry
Activation codes are valid only for a limited time. To avoid expiration:
Keep your computer or smartphone ready before initiating the activation process.
Enter the code at Disneyplus.com/Begin as soon as it appears on your device.
3. Check for Typographical Errors
Ensure that you enter the activation code correctly:
Double-check the code for accuracy.
Be mindful of similar-looking characters such as “O” and “0” or “I” and “1.”
4. Restart Your Device
Restarting your device can resolve temporary glitches. To do this:
Turn off your device.
Wait for a few seconds and turn it back on.
Open the Disney Plus app and generate a new activation code.
Enter the new code at Disneyplus.com/Begin.
5. Update the Disney Plus App
Using an outdated version of the Disney Plus app can cause issues. To update the app:
Visit the app store on your device (Google Play Store, Apple App Store, etc.).
Search for Disney Plus.
If an update is available, click “Update.”
Relaunch the app and try activating it again.
6. Check Your Internet Connection
A stable internet connection is essential for the activation process. To troubleshoot your connection:
Ensure your device is connected to Wi-Fi or a wired network.
Restart your router or modem.
Test your internet speed using a speed test tool. If the connection is slow, contact your internet service provider (ISP).
7. Clear Cache and Data
Clearing the cache and data of the Disney Plus app can fix issues related to corrupted files. Here’s how:
For Android Devices:
Go to “Settings” > “Apps” > “Disney Plus.”
Select “Storage.”
Tap “Clear Cache” and “Clear Data.”
For iOS Devices:
Uninstall the Disney Plus app.
Reinstall it from the Apple App Store.
8. Log Out and Log Back In
Sometimes, logging out of your Disney Plus account and logging back in can resolve account-related issues. To do this:
Open the Disney Plus app.
Go to “Settings” > “Account.”
Select “Log Out.”
Log back in using your credentials.
9. Verify Your Subscription
An expired or inactive subscription can prevent activation. To verify your subscription:
Log in to your Disney Plus account on a browser.
Check your subscription status under the “Billing” or “Subscription” section.
Renew your subscription if necessary.
10. Contact Disney Plus Support
If you’ve tried all the above methods and still encounter the error, contact Disney Plus customer support:
Visit the Disney Plus Help Center.
Use the live chat or call support options for assistance.
Provide details about the issue and any error messages.
Tips to Avoid “Activation Code Expired” Errors in the Future
To prevent this error from occurring in the future, follow these tips:
Prepare Ahead: Have your browser and login credentials ready before starting the activation process.
Act Quickly: Enter the activation code promptly.
Keep Your App Updated: Regularly update the Disney Plus app to avoid compatibility issues.
Maintain a Stable Connection: Ensure your internet connection is reliable during activation.
Conclusion
The “Activation Code Expired” error on disneyplus.com/begin can be frustrating, but it is usually easy to fix. By generating a new activation code, ensuring timely code entry, and addressing any device or network issues, you can successfully activate Disney Plus on your device. If problems persist, don’t hesitate to reach out to Disney Plus support for assistance. Following the steps outlined in this guide will help you enjoy seamless streaming of your favorite Disney content.
1 note
·
View note
Text
"Spinjo Login Tips: How to Get Playing Quickly and Securely"

Logging into your Spinjo Login account doesn’t have to be complicated. Whether you’re a new player or a returning one, these quick tips will help you access your account and start gaming securely in no time. Follow this guide for a smooth and safe login experience.
1. Start with the Official Spinjo Website
Open your preferred browser and go to the official Spinjo website. Make sure the website URL starts with "https://" to confirm that you're on the secure version of the site. Always avoid third-party links to prevent potential security risks.
2. Click the Login Button
Once you’re on the homepage, locate the Login button, usually at the top-right corner of the page. Click it to be directed to the login screen where you’ll enter your credentials.
3. Enter Your Username or Email Address
On the login page, you’ll be prompted to enter your username or email address—the one you used when signing up. Double-check that you’ve got the correct one, especially if you have multiple email addresses.
4. Enter Your Password Carefully
Next, enter your password. Be mindful of capitalization and special characters since passwords are case-sensitive. If you’ve forgotten your password, look for the Forgot Password option, which will guide you through resetting it via your registered email address.
5. Enable Two-Factor Authentication for Extra Security
For an added layer of protection, enable two-factor authentication (2FA) if available. With 2FA, you'll be asked to verify your login using a secondary method, such as a code sent to your phone or email. This simple step helps safeguard your account from unauthorized access, especially when playing on shared or public devices.
6. Click the Login Button
Once you've entered your correct username/email and password (and completed 2FA if enabled), click the Login button. You should be directed to your account dashboard or gaming lobby, where you can immediately start exploring the games.
7. Troubleshooting: Common Login Issues
If you’re experiencing trouble logging in, try the following solutions:
Incorrect Credentials: Double-check the username/email and password you’ve entered. Make sure they match the details you used when creating the account.
Forgot Password: If you can’t remember your password, click the Forgot Password link to receive a password reset email.
Account Lockout: If you’ve tried multiple incorrect login attempts, your account may be temporarily locked. Wait a few minutes and try again or contact customer support if the issue persists.
8. Log Out When Done for Extra Security
Once you’re finished playing, always log out of your account, especially if you're using a shared or public computer. You can do this easily by clicking the Logout button, typically found in your account settings or at the top-right of the screen.
Getting into your Spinjo account quickly and securely is simple when you follow these tips. Make sure you're on the official website, use strong passwords, and enable two-factor authentication for peace of mind. By keeping your login details safe and secure, you can enjoy uninterrupted access to all the fun and excitement Spinjo has to offer. Happy gaming!
0 notes
Text
Securing ASP.NET Applications: Best Practices
With the increase in cyberattacks and vulnerabilities, securing web applications is more critical than ever, and ASP.NET is no exception. ASP.NET, a popular web application framework by Microsoft, requires diligent security measures to safeguard sensitive data and protect against common threats. In this article, we outline best practices for securing ASP NET applications, helping developers defend against attacks and ensure data integrity.

1. Enable HTTPS Everywhere
One of the most essential steps in securing any web application is enforcing HTTPS to ensure that all data exchanged between the client and server is encrypted. HTTPS protects against man-in-the-middle attacks and ensures data confidentiality.
2. Use Strong Authentication and Authorization
Proper authentication and authorization are critical to preventing unauthorized access to your application. ASP.NET provides tools like ASP.NET Identity for managing user authentication and role-based authorization.
Tips for Strong Authentication:
Use Multi-Factor Authentication (MFA) to add an extra layer of security, requiring methods such as SMS codes or authenticator apps.
Implement strong password policies (length, complexity, expiration).
Consider using OAuth or OpenID Connect for secure, third-party login options (Google, Microsoft, etc.).
3. Protect Against Cross-Site Scripting (XSS)
XSS attacks happen when malicious scripts are injected into web pages that are viewed by other users. To prevent XSS in ASP.NET, all user input should be validated and properly encoded.
Tips to Prevent XSS:
Use the AntiXSS library built into ASP.NET for safe encoding.
Validate and sanitize all user input—never trust incoming data.
Use a Content Security Policy (CSP) to restrict which types of content (e.g., scripts) can be loaded.
4. Prevent SQL Injection Attacks
SQL injection occurs when attackers manipulate input data to execute malicious SQL queries. This can be prevented by avoiding direct SQL queries with user input.
How to Prevent SQL Injection:
Use parameterized queries or stored procedures instead of concatenating SQL queries.
Leverage ORM tools (e.g., Entity Framework), which handle query parameterization and prevent SQL injection.
5. Use Anti-Forgery Tokens to Prevent CSRF Attacks
Cross-Site Request Forgery (CSRF) tricks users into unknowingly submitting requests to a web application. ASP.NET provides anti-forgery tokens to validate incoming requests and prevent CSRF attacks.
6. Secure Sensitive Data with Encryption
Sensitive data, such as passwords and personal information, should always be encrypted both in transit and at rest.
How to Encrypt Data in ASP.NET:
Use the Data Protection API (DPAPI) to encrypt cookies, tokens, and user data.
Encrypt sensitive configuration data (e.g., connection strings) in the web.config file.
7. Regularly Patch and Update Dependencies
Outdated libraries and frameworks often contain vulnerabilities that attackers can exploit. Keeping your environment updated is crucial.
Best Practices for Updates:
Use package managers (e.g., NuGet) to keep your libraries up to date.
Use tools like OWASP Dependency-Check or Snyk to monitor vulnerabilities in your dependencies.
8. Implement Logging and Monitoring
Detailed logging is essential for tracking suspicious activities and troubleshooting security issues.
Best Practices for Logging:
Log all authentication attempts (successful and failed) to detect potential brute force attacks.
Use a centralized logging system like Serilog, ELK Stack, or Azure Monitor.
Monitor critical security events such as multiple failed login attempts, permission changes, and access to sensitive data.
9. Use Dependency Injection for Security
In ASP.NET Core, Dependency Injection (DI) allows for loosely coupled services that can be injected where needed. This helps manage security services such as authentication and encryption more effectively.
10. Use Content Security Headers
Security headers such as X-Content-Type-Options, X-Frame-Options, and X-XSS-Protection help prevent attacks like content-type sniffing, clickjacking, and XSS.
Conclusion
Securing ASP.NET applications is a continuous and evolving process that requires attention to detail. By implementing these best practices—from enforcing HTTPS to using security headers—you can reduce the attack surface of your application and protect it from common threats. Keeping up with modern security trends and integrating security at every development stage ensures a robust and secure ASP.NET application.
Security is not a one-time effort—it’s a continuous commitment
To know more: https://www.inestweb.com/best-practices-for-securing-asp-net-applications/
0 notes
Text
How to Install CSF Firewall in cPanel Server?
In the field of web hosting, security is paramount. One essential tool for safeguarding your cPanel server is the ConfigServer Security & Firewall (CSF). This powerful firewall provides robust protection against a variety of threats and ensures your server runs smoothly. In this guide, we will walk you through the process of installing CSF Firewall in your cPanel server.
What is CSF Firewall?
CSF (ConfigServer Security & Firewall) is a popular security tool designed for servers running cPanel. It enhances the server’s security by offering features such as advanced firewall protection, login tracking, and intrusion detection. With CSF, you can easily manage and monitor your server’s security settings, making it a preferred choice for server administrators.
Prerequisites
Before we dive into the installation process, ensure you meet the following prerequisites:
Root Access: You need root access to install CSF.
cPanel/WHM: Ensure you have cPanel/WHM installed on your server.
Updated System: It's a good practice to update your server to the latest versions of all software packages.
Step-by-Step Installation of CSF Firewall
1. Log in to Your Server
First, you need to log in to your server via SSH as the root user. You can do this using an SSH client like PuTTY.
bash
Copy code
ssh root@your_server_ip
2. Update Your System
Before installing any new software, it's essential to ensure your system is up-to-date. Run the following commands to update your package lists and upgrade existing packages:
bash
Copy code
yum update -y
3. Download CSF
Next, download the latest version of CSF from the official ConfigServer website. Use the following commands to navigate to a temporary directory and download the CSF package:
bash
Copy code
cd/usr/src wget https://download.configserver.com/csf.tgz
4. Extract the CSF Package
Once the download is complete, extract the CSF package using the tar command:
bash
Copy code
tar -xzf csf.tgz
5. Install CSF
Navigate to the extracted CSF directory and run the installation script:
bash
Copy code
cdcsf sh install.sh
The installation script will configure CSF and set up the necessary files.
6. Configure CSF
After installation, you'll need to configure CSF to fit your server's needs. The configuration file is located at /etc/csf/csf.conf. Open this file using a text editor:
bash
Copy code
nano /etc/csf/csf.conf
In the configuration file, you can adjust various settings such as port numbers, allowed IP addresses, and more. For most installations, the default settings are a good starting point.
7. Test CSF Configuration
Before enabling CSF, it's crucial to test the configuration to ensure there are no errors. Use the following command to check for syntax errors and configuration issues:
bash
Copy code
csf -t
If the test passes without any errors, you can proceed to the next step.
8. Restart CSF and LFD
Finally, restart the CSF firewall and the Login Failure Daemon (LFD) to apply the changes:
bash
Copy code
csf -r service lfd restart
9. Verify CSF Installation
To ensure that CSF is running correctly, you can use the following command to check its status:
bash
Copy code
csf -l
You should see a list of the currently open ports and other firewall settings.
Conclusion
Installing CSF Firewall in your cPanel server is a straightforward process that significantly enhances your server’s security. By following the steps outlined above, you can protect your server from potential threats and manage your firewall settings efficiently.
For a more detailed guide or troubleshooting tips, refer to the official ConfigServer documentation. Remember, maintaining server security is an ongoing process, so keep your firewall and server software updated regularly.
By following this guide, you’ve taken an essential step towards securing your cPanel server. For further assistance or questions, feel free to reach out to your hosting provider or consult additional resources.
For a seamless installation experience, be sure to refer to this guide on how to install CSF Firewall in cPanel Server.
0 notes
Text
Tiranga App Login: A Comprehensive Guide

In an era where digital innovation is rapidly transforming the way we interact with the world, the Tiranga App stands out as a prime example of how technology can enhance convenience and accessibility tiranga app developed by the Indian government, is designed to provide a range of services to its users, including access to government schemes, services, and information. To fully utilize the app's features, users need to understand the login process. This guide will walk you through the steps of logging into the Tiranga App, ensuring a seamless and secure experience.
1. Downloading the Tiranga App
Before you can log in, you need to download the Tiranga App. The app is available for both Android and iOS devices. You can find it on the Google Play Store for Android users and the Apple App Store for iOS users. Simply search for "Tiranga App" and download it to your device. Make sure to download the official app to avoid any security risks associated with counterfeit versions.
2. Opening the App
Once the app is installed, open it by tapping on the app icon on your home screen or app drawer. You will be greeted with the app's welcome screen, which provides an overview of its features and services. To proceed, tap on the "Login" button, usually located prominently on the screen.
3. Creating an Account (If You Don't Have One)
If you are a new user and don’t have an account yet, you will need to create one before logging in. Look for the "Sign Up" or "Register" option on the login screen. You will be prompted to enter basic information such as your name, phone number, email address, and create a secure password. Some versions of the app may require additional verification steps, such as entering an OTP (One-Time Password) sent to your registered phone number.
4. Logging In
For existing users, the login process is straightforward. Enter your registered phone number or email address and your password in the designated fields. Ensure that you enter this information correctly to avoid any login errors. After entering your credentials, tap on the "Login" button.
If you have forgotten your password, look for the "Forgot Password" link on the login screen. This will guide you through a process to reset your password, usually involving sending a reset link to your registered email address or phone number.
5. Two-Factor Authentication (Optional)
To enhance security, the Tiranga App may offer two-factor authentication (2FA). If enabled, you will need to enter a verification code sent to your registered phone number or email address after entering your login credentials. This additional layer of security helps protect your account from unauthorized access.
6. Navigating the App
After successfully logging in, you will be directed to the app's main dashboard. Here, you can access various services and features offered by the Tiranga App. Familiarize yourself with the app's layout, including menus and navigation options, to make the most of its offerings.
7. Troubleshooting Common Issues
If you encounter issues during the login process, such as forgetting your password or facing technical glitches, the app typically provides a support or help section. Consult this section for troubleshooting tips or contact customer support if needed. Common issues might include incorrect login credentials, problems with the internet connection, or app-related errors.
8. Logging Out
For security reasons, it is important to log out of the app when you are finished using it. Look for the "Logout" option, usually found in the app’s settings or profile section, and tap on it to end your session.
Conclusion
The Tiranga App is a valuable tool for accessing a range of government services and information. By following these steps, you can ensure a smooth login experience and make the most of the app’s features. Whether you are a new user setting up your account or an existing user logging in, understanding the process is key to using the app efficiently and securely.
0 notes
Text
Tiranga Colour Prediction Login: How to Access and Play

Tiranga Colour Prediction is an engaging online game that allows users to predict colors and win rewards. If you’re new to the game or need guidance on how to log in and start playing, this guide is for you. We will walk you through the login process, offer troubleshooting tips, and provide best practices for securing your account.
1. Understanding Tiranga Colour Prediction
Tiranga Colour Prediction is part of a broader trend of online prediction games. Here’s a quick overview:
Predictive Gameplay: Players predict the outcome of a color selection process.
Rewards System: Correct predictions can earn you points, money, or other rewards.
Simple Interface: The game is designed to be easy to navigate, even for beginners.
2. Downloading and Installing the Tiranga App
Before you can log in to the Tiranga Colour Prediction game, you need the Tiranga app:
Visit the App Store: Go to the Google Play Store or Apple App Store, depending on your device.
Search for ‘Tiranga App’: Enter “Tiranga” in the search bar and select the official app from the search results.
Download and Install: Tap the download button. After the app is installed, open it to begin.
3. Creating a Tiranga Account
To play Tiranga Colour Prediction, you must create an account if you haven’t already:
Launch the Tiranga App: Open the app on your device.
Sign Up: Tap on the “Sign Up” or “Register” button on the welcome screen.
Provide Details: Fill out the registration form with your name, email address, phone number, username, and password.
Verify Your Account: You may be asked to verify your email or phone number. Follow the instructions provided.
Complete Registration: Once verified, your account will be ready for use.
4. Logging In to Tiranga Colour Prediction
With your account set up, logging in is easy:
Open the Tiranga App: Start the app on your device.
Go to the Login Page: Tap on the “Login” option on the main screen.
Enter Your Credentials: Input your username or email and password in the provided fields.
Tap ‘Login’: Once your details are entered, click on the “Login” button to access your account.
Access the Colour Prediction Game: After logging in, navigate to the Colour Prediction section to start playing.
5. Troubleshooting Login Issues
If you experience problems logging in, try these solutions:
Forgot Password: Click on “Forgot Password” on the login page to reset your password. You will be asked to provide your registered email or phone number.
Incorrect Credentials: Ensure your username and password are correct. Check for typos or extra spaces.
App Crashes or Freezes: Close the app and reopen it. If the problem continues, update the app or reinstall it.
Account Locked: After several failed login attempts, your account might be locked. Contact customer support for assistance.
6. Tips for a Secure Login Experience
To keep your Tiranga account safe, consider the following tips:
Use a Strong Password: Combine letters, numbers, and special characters to create a strong password.
Enable Two-Factor Authentication (2FA): If available, enable 2FA for added security.
Keep Your App Updated: Regularly check for updates to the Tiranga app to benefit from the latest security enhancements.
Avoid Public Wi-Fi: Use secure, private networks instead of public Wi-Fi when logging in to reduce the risk of hacking.
7. How to Play Tiranga Colour Prediction
Once logged in, here’s how to start playing:
Select the Game: Navigate to the Colour Prediction game within the app.
Place Your Prediction: Choose the color you believe will be selected.
Confirm Your Prediction: After making your selection, confirm your prediction to lock it in.
Wait for the Result: The game will reveal the outcome, and you’ll see if your prediction was correct.
Collect Rewards: If you win, your rewards will be credited to your account, which you can use in future games or withdraw, depending on the game’s rules.
8. Conclusion
Logging in to Tiranga Colour Prediction is a straightforward process that opens the door to an exciting and rewarding gaming experience. By following the steps outlined in this guide, you can quickly access your account and start making predictions. Remember to prioritize the security of your account by using strong passwords and enabling two-factor authentication. Whether you’re a beginner or an experienced player, Tiranga Colour Prediction offers a fun and potentially profitable way to engage with color prediction games.
0 notes
Text
How do I use DisneyPlus.com/begin to activate my device?
Disney+ is a leading streaming service that offers a vast library of movies, TV shows, and original content from Disney, Pixar, Marvel, Star Wars, and National Geographic. With so much incredible content at your fingertips, activating your device to start streaming is a must. In this guide, we’ll walk you through the process of using DisneyPlus.com/begin to activate your device seamlessly.
What You Need Before You Start
Before you begin the activation process, ensure you have the following:
A Disney+ Account: If you don’t have one yet, you can create an account by visiting the Disney+ website or downloading the app on your device.
Supported Device: Disney+ is compatible with various devices, including smart TVs, streaming devices (Roku, Apple TV, Amazon Fire TV), gaming consoles (PlayStation, Xbox), smartphones, and tablets.
Internet Connection: Make sure your device is connected to the internet to access Disney+.
Activation Code: This code will be generated during the activation process.
Step-by-Step Guide to Activate Your Device
Follow these simple steps to activate your device using DisneyPlus.com/begin:
Step 1: Download the Disney+ App
For Mobile Devices:
Go to the Apple App Store or Google Play Store.
Search for “Disney+” and download the app.
For Smart TVs and Streaming Devices:
Access the app store on your device.
Search for “Disney+” and install it.
Step 2: Open the Disney+ App
Once the app is installed, open it on your device. You’ll be greeted with the Disney+ welcome screen, prompting you to either log in or create a new account.
Step 3: Log In or Create an Account
If you already have a Disney+ account:
Click on the “Log In” button.
Enter your email and password associated with your Disney+ account.
If you don’t have an account:
Select the “Sign Up” option.
Follow the prompts to create a new account by providing your email, creating a password, and entering your payment information if required.
Step 4: Start the Activation Process
After logging in, you will see a screen instructing you to activate your device. Look for an activation code displayed on your screen.
Step 5: Visit DisneyPlus.com/begin
Open a web browser on your computer or smartphone.
Navigate to DisneyPlus.com/begin.
You will be prompted to enter the activation code displayed on your device.
Step 6: Enter the Activation Code
Type the code in the designated field on the DisneyPlus.com/begin page.
Click the “Continue” button to proceed.
Step 7: Complete the Activation
After entering the activation code, you may be prompted to log in again if you're not already authenticated. Once you do this, your device will be activated, and you’ll be redirected back to the Disney+ app.
Step 8: Start Streaming
Now that your device is activated, you can start exploring the vast library of Disney+ content. Browse through movies, TV shows, and original programming. Don’t forget to check out the latest releases and trending titles!
Troubleshooting Common Issues
While the activation process is typically straightforward, you may encounter a few issues. Here are some common problems and their solutions:
Issue 1: Invalid Activation Code
If you receive a message that your activation code is invalid, try the following:
Check the Code: Ensure you’ve entered the code correctly, as it is case-sensitive.
Generate a New Code: Restart the Disney+ app on your device to generate a new activation code.
Issue 2: Account Not Found
If you see a message indicating that your account cannot be found, ensure you’re using the correct email and password. If necessary, reset your password using the “Forgot Password?” link on the login page.
Issue 3: Connection Issues
If the activation process fails due to connection issues:
Check Your Internet Connection: Ensure your device is connected to the internet. Try resetting your router if necessary.
Try Another Device: If possible, use another device to access DisneyPlus.com/begin.
Issue 4: App Not Responding
If the Disney+ app is not responding, consider the following:
Restart the App: Close the app and reopen it.
Update the App: Ensure you have the latest version of the Disney+ app installed.
Reinstall the App: If problems persist, uninstall the app and reinstall it.
Tips for a Better Disney+ Experience
To enhance your streaming experience on Disney+, consider these tips:
Create Profiles: Disney+ allows you to create multiple profiles under one account. This is useful for families who want personalized recommendations.
Download Content: For on-the-go viewing, download your favorite shows and movies to watch offline.
Explore Different Genres: With a wide array of content, take the time to explore various genres and categories, from classic Disney movies to Marvel blockbusters.
Use Watchlists: Add titles to your watchlist to keep track of shows and movies you want to watch later.
Check for New Releases: Stay updated with new releases and original programming by checking the “New to Disney+” section regularly.
Conclusion
Activating your device using DisneyPlus.com/begin is a simple and straightforward process. By following the steps outlined in this guide, you’ll be able to enjoy the fantastic content Disney+ has to offer in no time. Whether you're a fan of Disney classics, Marvel superheroes, or Pixar animations, Disney+ provides something for everyone.
If you encounter any issues during the activation process, don’t hesitate to refer back to our troubleshooting tips for quick solutions. Now, grab your popcorn, get comfortable, and start streaming your favorite movies and shows on Disney+!
1 note
·
View note
Text
Mastering Shopify Liquid Template Customization

Shopify Liquid is a powerful templating language used by Shopify to dynamically load content on online stores. Mastering Shopify Liquid template customization is essential for creating unique and personalized shopping experiences. In this guide, we will explore the basics of Liquid, delve into advanced techniques, and offer tips for optimizing your customizations.
2. Basics of Shopify Liquid
Understanding Liquid Syntax
Liquid is a Ruby-based language that allows you to add dynamic content to your Shopify store. It includes tags, filters, and objects that you use to manipulate data and render content. Learning the syntax is crucial for making effective customizations.
Key Components of Liquid Templates
Liquid templates consist of three main components: objects, tags, and filters. Objects contain data that you want to display, tags control the logic of the template, and filters modify the output.
3. Setting Up Your Shopify Development Environment
Installing Shopify CLI
Shopify CLI (Command Line Interface) is a tool that helps you manage your Shopify projects. Installing it will streamline the development process and make it easier to work with Shopify themes.
Configuring Your Local Development Environment
Setting up a local development environment involves configuring your system to work with Shopify’s tools and your chosen code editor. This setup is crucial for efficient development and testing.
4. Customizing Shopify Themes
Editing Theme Files
To customize your Shopify theme, you need to edit the theme files directly. This involves working with HTML, CSS, and Liquid code to change the appearance and functionality of your store.
Creating Custom Sections and Blocks
Shopify allows you to create custom sections and blocks within your theme. These elements enable you to add unique features and design components to your store.
Using Shopify Theme Kit
Shopify Theme Kit is a command-line tool that facilitates theme development. It allows you to manage and deploy your theme changes efficiently.
5. Advanced Liquid Techniques
Liquid Filters and Tags
Liquid filters and tags provide advanced functionality, allowing you to format data, perform calculations, and control the logic of your templates.
Conditional Statements
Conditional statements in Liquid let you display content based on certain conditions, such as user login status or product availability.
Loops and Iterations
Loops and iterations help you display collections of items dynamically. This is useful for showing lists of products, blog posts, or other repetitive content.
6. Adding Custom Functionality
Custom Scripts and JavaScript Integration
Integrating custom scripts and JavaScript can enhance the interactivity and functionality of your store. This might include custom animations, form validations, or third-party integrations.
Working with Shopify APIs
Shopify APIs provide access to various features and data of your store. By integrating these APIs, you can add custom functionalities that go beyond what Liquid alone can achieve.
7. Best Practices for Liquid Customization
Optimizing Performance
Optimizing your Liquid code and theme files is crucial for maintaining fast load times and a smooth user experience. This involves minimizing code, optimizing images, and using efficient queries.
Ensuring Cross-Browser Compatibility
Ensure your customizations work across different browsers and devices. This helps provide a consistent user experience for all visitors.
8. Troubleshooting Common Issues
Debugging Liquid Code
Debugging Liquid code involves identifying and fixing errors in your templates. Tools like Shopify’s theme inspector can help you diagnose issues and correct them.
9. Expert Insights
Quotes from Shopify Developers
"Incorporating Liquid effectively requires a deep understanding of its syntax and structure. The more familiar you are with Liquid, the more creative you can be with your customizations." – [Shopify Developer]
Case Studies of Successful Customizations
Many stores have successfully used Liquid customizations to enhance their shopping experience. For instance, [example case study] showcases how a custom product filter improved user engagement and sales.
10. Future Outlook
Emerging Trends in Shopify Development
As e-commerce evolves, new trends and technologies will influence Shopify development. Staying updated with these trends will help you leverage new features and maintain a competitive edge.
11. Conclusion
Mastering Shopify Liquid template customization opens up endless possibilities for creating a unique and effective online store. By understanding the basics, applying advanced techniques, and following best practices, you can enhance your store’s functionality and design. Keep learning and adapting to stay at the forefront of Shopify development.
1 note
·
View note
Text
Discover the Ultimate Taj777 Experience: Taj777 Login and Beyond!
Welcome to the world of Taj777, where excitement and opportunity converge! Whether you’re a seasoned player or a curious newcomer, understanding how to navigate the Taj777 login process is your gateway to unlocking a realm of thrilling experiences. Buckle up as we dive into everything you need to know about the Taj777 login and how it enhances your journey with Taj777.
1. The Magic of Taj777: A Brief Introduction
Taj777 isn’t just another name in the world of online entertainment; it’s a powerhouse of thrilling games and opportunities. With a reputation for delivering top-notch experiences, Taj777 stands out in the crowded landscape of online gaming and betting. But before you can dive into the action, you need to master the Taj777 login process.
2. Why Taj777? The Benefits of Choosing Taj777
Choosing Taj777 means embracing a world of benefits. From a vast array of games to exceptional customer service, Taj777 offers unparalleled Taj777 login experiences. The Taj777 login process is designed to be user-friendly, ensuring that your journey begins smoothly and quickly.
3. Taj777 Login: Your Gateway to a New Adventure
The Taj777 login is more than just a way to access your account; it’s your gateway to an entire universe of gaming possibilities. With just a few simple steps, you can log in and start exploring everything Taj777 has to offer.
4. Step-by-Step Guide to the Taj777 Login Process
4.1 Accessing the Taj777 Website
Start by visiting the Taj777 website. The home page is designed to be welcoming and easy to navigate. Look for the Taj777 login button, usually located prominently at the top right corner of the page.
4.2 Enter Your Credentials
Once you click on the Taj777 login button, you’ll be prompted to enter your username and password. Ensure that you have your credentials ready and double-check for accuracy to avoid any login issues.
4.3 Navigate the Dashboard
After a successful Taj777 login, you’ll be directed to your personal dashboard. Here, you can access various features, games, and settings tailored to enhance your gaming experience.
5. Troubleshooting Common Taj777 Login Issues
5.1 Forgotten Password
If you’ve forgotten your password, don’t panic! The Taj777 website provides a simple password recovery process. Follow the prompts to reset your password and regain access to your account.
5.2 Account Lockouts
In case of multiple unsuccessful login attempts, your account may be temporarily locked. Contact Taj777 customer support Taj777 withdrawal number for assistance in unlocking your account and ensuring a smooth Taj777 login experience.
6. Enhancing Your Experience with Taj777
6.1 Explore the Game Library
Once logged in, take full advantage of Taj777’s extensive game library. From classic favorites to the latest releases, Taj777 offers something for every gaming enthusiast.
6.2 Customize Your Profile
Personalize your Taj777 experience by customizing your profile. Set your preferences, update your information, and tailor your dashboard to suit your needs and preferences.
7. Taj777 Login Security: Keeping Your Information Safe
Taj777 takes security seriously. The Taj777 login process is fortified with advanced encryption technologies to protect your personal and financial information. Ensure you use a strong password and enable two-factor authentication for added security.
8. The Future of Taj777: What’s Next?
Taj777 is continually evolving, with exciting new features and updates on the horizon. Stay tuned for announcements and keep your Taj777 login credentials handy to be among the first to experience the latest innovations.
9. Why Taj777 Stands Out from the Competition
What sets Taj777 apart is its commitment to delivering exceptional quality and user satisfaction. The Taj777 login process is just the beginning of what promises to be a captivating journey filled with opportunities and rewards.
**10. Frequently Asked Questions About Taj777 Login
10.1 How Do I Reset My Taj777 Password?
Visit the Taj777 website Taj777 login and use the “Forgot Password” feature to reset your password. Follow the instructions sent to your registered email.
10.2 Can I Use the Same Login for Multiple Accounts?
No, each Taj777 account requires a unique login. Ensure you keep track of your credentials for each account.
10.3 What Should I Do If I Encounter a Login Error?
Contact Taj777 customer support for assistance with any login errors. They are available to help resolve issues promptly.
11. Taj777 Login: Tips for a Smooth Experience
To ensure a seamless Taj777 login experience, keep your login credentials secure, use a reliable internet connection, and regularly update your password.
**12. Conclusion: Dive into the Excitement with Taj777
The Taj777 login process is your gateway to an exciting world of online gaming and entertainment. With its user-friendly interface, robust security features, and a vast array of games, Taj777 promises an unforgettable experience. So why wait? Log in to Taj777 today and start your adventure!
Embrace the thrill with Taj777 and make the most of every moment. Happy gaming!
0 notes
Text
Ejoin SMS Modem Solutions
Welcome to Ejointech, a leading provider of SMS Modems. Discover our wide range of products and solutions
PRODUCTS
Explore our comprehensive selection of high-performance SMS Modems
8 Port SMS ModemIdeal for small to mediumFeatures: Bulk SMS/MMS, SMPP/HTTP API Integration, Remote Login and Management, IMEI Changeable, SIM Rotation.Learn More
16 Port SMS ModemSuitable for larger businesses with higher SMS volume needs.Features: Bulk SMS/MMS, SMS to Email, Email to SMS, Flexible SIM Allocation, Real-time Statistics.Learn More
32 Port SMS ModemDesigned for enterprises requiring extensive SMS capabilities.Features: Automated SMS Campaigns, API Integration, USSD/AT Command Capable, Human Behavior to Prevent SIM Blockage.Learn More
64 Port SMS ModemPerfect for industrial-grade applications and high-volume SMS requirements.Features: High-speed Bulk SMS/MMS, Centralized SIM Management, Real-time SIM Card Status, Enhanced Security Measures.Learn More
KEY FEATURES AND BENEFITS:
High-Performance SMS Modems: Our modems support bulk SMS/MMS sending and receiving, making them perfect for marketing campaigns, customer notifications, and transactional messages.
Versatile Connectivity: Seamlessly integrate with major GSM networks and a variety of SMS software applications through SMPP/HTTP APIs, ensuring compatibility and ease of use.
Advanced Management Systems: Utilize our ETMS, EIMS_Simple, EIMS3, and ESPS management systems for centralized control, auto-recharge, and SIM card allocation, streamlining your SMS operations.
Human Behavior Simulation: Prevent SIM blockage with features like IMEI changeability, SIM rotation, and SMS send interval settings, ensuring uninterrupted service.
Flexible SIM Management: Manage SIM cards remotely with real-time statistics, signal strength monitoring, and intelligent operator selection for optimal performance.
Enhanced Security: Protect your communication with robust security measures, including SMS quantity control, base station changes, and SMS send speed adjustments.
SOLUTIONS
Discover how Ejointech's solutions can enhance your business operations:
Bulk SMS MarketingReach a large audience with promotional messages, discounts, and offers. Achieve high open rates and boost customer engagement. Learn More
Alerts and NotificationsSend critical alerts and notifications to your customers. Ideal for banks, schools, and healthcare providers. Learn More
Customer ServiceIntegrate SMS modems into your customer service operations for instant support. Enhance customer experience with timely responses. Learn More
A2P SMS TerminationTerminate Application-to-Person (A2P) SMS with our reliable SMS modems. Ensure efficient and cost-effective message delivery .Learn More
SIM Top-Up SystemsManage mobile recharge systems with ease. Automate SIM card top-ups and ensure uninterrupted service. Learn More
TECHNICAL SUPPORT
Our dedicated technical support team is here to assist you with any queries or issues you may encounter. Contact us for expert guidance and troubleshooting assistance.
FAQs Find answers to frequently asked questions about our products and services.Learn More
Documentation Access detailed documentation and user manuals for our SMS Modems and VoIP Gateways.Learn More
Contact Support Reach out to our support team via email, phone, or live chat. We’re here to help!Learn More
Welcome to visit: Ejointech Leading SMS Modem & VoIP Gateway Provider for Over 20 Years for more information.
#ejointech#sms modem#sms marketing#sms gateway#ejoin sms#ejoin sms gateway#sms gateway hardware#bulk sms#promotional sms
1 note
·
View note
Text
How to Balance Learning Selenium and Java
Learning Selenium and Java together can be highly beneficial for mastering test automation. However, balancing the two requires careful planning and consistent practice. If you're keen on becoming proficient in Selenium, consider enrolling in a Selenium course in Pune. By doing so, you'll have the opportunity to acquire in-depth knowledge and practical skills essential for mastering selenium. Here’s a guide to help you effectively manage your Selenium and Java studies.

1. Set Clear Learning Objectives
Define Your Goals
Start by setting clear learning objectives for both Selenium and Java. Define what specific skills and milestones you want to achieve, such as:
Mastering Selenium WebDriver
Understanding Java syntax
Creating robust test scripts
Break Down Objectives
Break down your goals into smaller, manageable tasks. This will make it easier to track your progress and stay motivated.
2. Create a Study Schedule
Allocate Time Wisely
Create a well-structured study schedule that allocates specific hours or days for each subject. For example, you might study Java on Mondays, Wednesdays, and Fridays, and focus on Selenium on Tuesdays, Thursdays, and Saturdays.
Stick to the Routine
Consistency is key. Stick to your schedule to ensure steady progress in both areas.
3. Integrate Java Fundamentals with Selenium Practice
Start with Java Basics
Begin with the basics of Java programming, such as syntax, object-oriented programming concepts, and common libraries.
Apply Java in Selenium
As you learn Java, immediately apply the concepts in your Selenium scripts. For example, use loops, conditionals, and functions to write automation scripts.
4. Work on Hands-On Projects
Begin with Simple Projects
Start with simple automation scripts that use basic Java programming concepts. For example, automate a simple login process on a web application.
Gradually Increase Complexity
As you become more comfortable, increase the complexity of your projects. Automate more complex workflows and handle dynamic content.
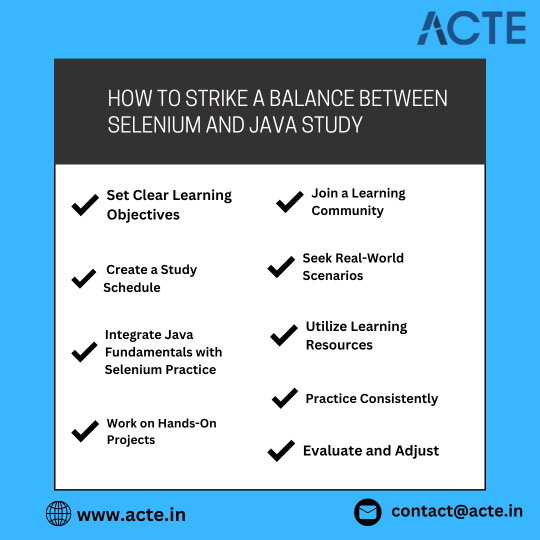
5. Join a Learning Community
Engage with Peers
Join online learning communities, forums, or study groups where you can discuss topics, seek advice, and share experiences with fellow learners.
Benefit from Shared Knowledge
Engaging with a community can provide insights into common challenges and solutions, enhancing your learning experience.
6. Seek Real-World Scenarios
Implement Real-World Projects
Work on real-world scenarios that involve automating web applications with complex workflows. This will provide a deeper understanding of automation testing and prepare you for real job tasks. Enrolling in a top-rated Selenium Online Training can unleash the full power of Selenium, offering individuals a deeper understanding of its intricacies.
Tackle Dynamic Content
Learn how to handle dynamic content and other common challenges in real-world web applications.
7. Utilize Learning Resources
Explore Various Resources
Use tutorials, documentation, and video courses to supplement your learning. Platforms like Udemy, Coursera, and LinkedIn Learning offer guided courses that break down complex concepts into simpler lessons.
Use Documentation
Refer to official documentation for both Selenium and Java to understand the tools and libraries in depth.
8. Practice Consistently
Regular Practice
Practice regularly by revisiting concepts, refining scripts, and troubleshooting issues. Regular practice reinforces your learning and improves your problem-solving skills.
Participate in Coding Challenges
Join coding challenges to test your skills and gain additional practice.
9. Evaluate and Adjust
Monitor Your Progress
Periodically evaluate your progress. Identify areas where you need improvement and allocate more time to focus on those topics.
Adjust Your Schedule
Be flexible and adjust your study schedule if necessary to ensure you are making the best use of your time.
Conclusion
Balancing Selenium and Java study requires careful planning and consistent practice. By setting clear objectives, integrating Java fundamentals with Selenium practice, and engaging in real-world scenarios, you can achieve a balanced and effective learning experience. Stay committed to your study schedule, engage with learning communities, and practice regularly to master both Selenium and Java.
0 notes
Text
How to Use Healthcare Software: A Full Information Guide

In today's digital age, healthcare software plays a crucial role in streamlining operations, improving patient care, and enhancing overall efficiency within medical facilities.
However, navigating through complex software systems can be daunting for many healthcare professionals.
Whether you're a nurse, physician, or administrator, mastering the use of Healthcare Software Development Company is essential for delivering optimal patient outcomes and you can know more about healthcare In this comprehensive guide, we'll walk you through the fundamental steps of using healthcare software effectively.
1. Familiarize Yourself with the Interface
Before diving into the functionalities of any healthcare software, take some time to explore its interface. Familiarize yourself with different sections, buttons, and menus. Understanding the layout will make navigation easier as you begin to use various features.
2. Learn Basic Navigation
Every healthcare software has its own navigation system. Start by learning basic navigation techniques such as how to access patient records, input data, and search for information. Pay attention to shortcuts or hotkeys that can speed up your workflow.
3. Understand Patient Records Management
Patient records are the cornerstone of healthcare software. Learn how to create, update, and access patient records securely. Understand the importance of maintaining accurate and up-to-date information to ensure continuity of care.
4. Master Clinical Documentation
Efficient clinical documentation is essential for accurate diagnosis and treatment planning. Learn how to document patient encounters, assessments, and interventions effectively. Practice using templates and standardized formats to streamline the documentation process.
5. Utilize Decision Support Tools
Many healthcare software solutions offer decision support tools such as clinical guidelines, drug interaction checkers, and diagnostic aids. Familiarize yourself with these tools and integrate them into your practice to enhance clinical decision-making.
6. Explore Communication Features
Effective communication is vital in healthcare settings. Explore communication features within the software such as secure messaging, task assignments, and collaboration tools. Utilize these features to communicate with colleagues, share information, and coordinate patient care.
7. Stay Updated with Training
Healthcare software is constantly evolving with updates and new features. Stay updated with ongoing training sessions provided by the software vendor or your organization. Take advantage of online tutorials, webinars, and user forums to enhance your skills and stay informed about the latest advancements.
8. Practice Data Security
Protecting patient data is paramount in healthcare. Adhere to data security protocols and best practices when using healthcare software. Keep your login credentials secure, avoid sharing sensitive information over unsecured channels, and report any suspicious activity immediately.
9. Seek Feedback and Troubleshoot
Don't hesitate to seek feedback from colleagues or IT support if you encounter challenges while using healthcare software. Collaborate with peers to troubleshoot issues and find solutions. Providing constructive feedback to software vendors can also help improve usability and functionality over time.
10. Maintain Regulatory Compliance
Lastly, ensure compliance with relevant healthcare regulations and standards such as HIPAA (Health Insurance Portability and Accountability Act). Familiarize yourself with privacy and security requirements to safeguard patient information and avoid potential legal repercussions.
In conclusion, mastering the use of healthcare software requires patience, practice, and ongoing learning. By following the steps outlined in this guide and actively engaging with the software, healthcare professionals can harness the full potential of technology to deliver high-quality patient care. Embrace the digital transformation and empower yourself with the tools needed to thrive in today's healthcare landscape.
0 notes