#xkeyscore
Explore tagged Tumblr posts
Text
Wie funktionieren die Spähprogramme Prism, Tempora und XKeyscore? Wer überwacht wen? Wer kontrolliert die Überwacher? Die wichtigsten Fakten im Überblick. ….Prism hat vier "Brüder", sie heißen Mainway, Marina, Pinwale und Nucleon. Mainway sammelt nur Telefonverbindungsdaten. Wie das abläuft, ist ebenfalls bekannt: Der Guardian hatte einen Gerichtsbeschluss veröffentlicht, nach dem der US-Mobilfunkbetreiber Verizon verpflichtet ist, der NSA die Verkehrsdaten aller seiner Kunden zu übergeben. Der Gerichtsbeschluss gilt für drei Monate und wird nach Angaben von Senatorin Dianne Feinstein seit sieben Jahren regelmäßig erneuert. Die anderen Mobilfunkbetreiber in den USA werden ebenfalls zur Kooperation gezwungen.
Marina wiederum sammelt solche Metadaten für Internetverbindungen. Es handelt sich also um Informationen darüber, wer wem wann eine E-Mail geschickt hat, oder wer wann und wie lange online war und welche Internetseiten er dabei aufgerufen hat.
Nucleon dient dazu, Inhalte von Telefongesprächen auszuwerten. Mit Pinwale werden Videos analysiert. Details zu den einzelnen Ebenen der NSA-Programme gehen aus den von der Washington Post veröffentlichten und um eigene Anmerkungen ergänzten Folien einer internen NSA-Präsentation hervor. Ein eigenständiges, äußerst mächtiges Werkzeug der NSA heißt XKeyscore. Es existiert mindestens seit 2008 und ist in erster Linie für die Analyse von Metadaten – also wer wann mit wem kommunizierte – gedacht. Aber auch auf Inhalte von E-Mails und Chats sollen die NSA-Analysten über XKeyscore zugreifen können, mitunter sogar in Echtzeit. Mithilfe von Suchanfragen können sie einzelne Menschen ausspionieren, ihre Log-ins und andere Online-Aktivitäten mitverfolgen, ihre Verbindungsdaten einsehen und sogar, welche Suchworte sie bei Google und welche Orte sie bei Google Maps eingegeben haben. Sie können aber auch breit gefasste Suchen starten, etwa nach allen Menschen in Pakistan, die ihre Mails mit PGP verschlüsseln. Auf diese Weise will der Geheimdienst Verdächtige finden, von denen er vorher nichts wusste – und ihre Kommunikationsnetzwerke aufdecken, um noch mehr Verdächtige zu entdecken. Hinter XKeyscore steckt die größten Sammlung von Kommunikationsdaten der NSA. Woher die Daten kommen, ist nur zu erahnen…
0 notes
Text

With Firefox having AI added in the recent update. Here's how you can disable it.
Open about:config in your browser.Accept the Warning it gives.Search browser.ml and blank all values and set false where necessary as shown in the screenshot, anything that requires a numerical string can be set as 0 .Once you restart you should no longer see the Grey-ed out checkbox checked, and the AI chatbot disabled from ever functioning.
#mozilla#mozilla firefox#firefox#web browsers#pro tip#protips#anti ai#fuck ai#internet#how to#diy#do it yourself#artificial intelligence#signal boost#signal b00st#signal boooooost#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
397 notes
·
View notes
Text
i've been impressed by the ability of this seemingly rag-tag team of white aussie dipshits to do journalism lately
youtube
some of you may recognise friendly jordies as the guy who had his house firebombed after discussing links between former new south wales deputy premier john barilaro and organised crime (this is a mirror upload, as the original was taken down due to continued threats, the nature of which have not been made public)
Pine Gap is a military installation near the centre of australia run by the CIA, NSA, NRO, and a token presence of australian military personnel. It is notable for being the groudstation primarily responsible for all us military or intelligence satellite traffic in the eastern hemisphere, which is to say all sattelite traffic that cannot be picked up by a groundstation on us soil. it has been operating since the mid 60s and as such has played a significant role in us involvement in vietnam, afghanistan, and iraq.
as well as being one of the sites named by edward snowden as part of the us program of intercepting civillian communications worldwide (including, but likely not limited to, XKeyscore and interception of communication satelite transmissions), it is known to provide targeting telemetry for missile and drone strikes and it is currently in use by the idf for this, and likely other purposes.
in the mid 1970s, australian prime minister gough whitlam threatened to terminate australia's end of the treaty allowing the us to operate pine gap as part of an effort to gain some independance from foreign superpowers. he was later dismissed by governor general john kerr and it is alledged by a former CIA contractor that the CIA pushed kerr to dismiss whitlam as they had him in their pocket (describing him as "our man kerr")
the number of us military bases and installations in australia has largely not been a topic of discussion in recent years, perhaps it should be again. it has been nice to see indigenous rights and land rights gain some traction these past few years (because of course all these bases are built on stolen indigenous land, why wouldn't they be). perhaps gaza can be a wake up call for what happens when you let another country's government make your decisions for you and perhaps we can even do some good for other important causes along the way as well.
10 notes
·
View notes
Text
Up and down like a fiddler's elbow (XKEYSCORE)
1. PRESIDENTIAL ANITA
2. HALFBREED ANITA
3. LONGSUFFERING ANITA
4. TREATED ANITA
5. LIBERATING ANITA
6. HANDSOFF ANITA
7. CORROBORATED ANITA
8. TORRENT ANITA
9. INTERPRETED ANITA
10. PULSED ANITA
11. GARBLED ANITA
12. PROMULGATED ANITA
13. PREWAR ANITA
14. TERRAN ANITA
15. SELFTAUGHT ANITA
16. PERKY ANITA
17. WORLDWIDE ANITA
18. BELTED ANITA
19. ESOTERIC ANITA
20. STIMULANT ANITA
21. LEGIBLE ANITA
3 notes
·
View notes
Text
Here's uBlock Origin's official guide to bypassing youtube's anti-adblock popups, updated weekly. Please share widely. Don't reward google for their predatory anti-consumer bullshit
To summarize: 1. Get uBlock Origin and make sure it's updated to the latest version. 2. Click on the gear icon to get to the dashboard, go to "Filter lists", and make sure that "uBlock filters - Quick fixes" is up to date
Repeat those steps any time you get another popup (google and uBlock are having an arms race right now so it might stop working at any moment), and if you have any more problems, read the reddit thread for troubleshooting advice
#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
87K notes
·
View notes
Text

Only an ally when there’s a profit to be made 😑
https://www.hackthissite.org/
#Only an ally when there’s a profit to be made 😑#profiteering#exploitation#exploitative#microsoft#antimicrosoft#boycott microsoft#fuck microsoft#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
18 notes
·
View notes
Text
de-google your phone
https://www.instagram.com/reel/C5LhMn6RjQ_/
#privacy#invasion of privacy#google#videos#video#anti google#boycott google#fuck google#mobile phones#phones#phone#i.t.#it#infotech#information technology#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#degoogle#self help#pro tip#protips#class war
23 notes
·
View notes
Text
NUTTY TV (XKEYSCORE)
- AMUSING
- CLEAN
- UNGENTLE
- CREDITABLE
- MODERN
- OCCASIONAL
- OTHER
0 notes
Text
hello google chrome refugees
don't use any of these browsers, they're also chrome

Here are my favorite firefox plugins for security/anti-tracking/anti-ad that I recommend you get
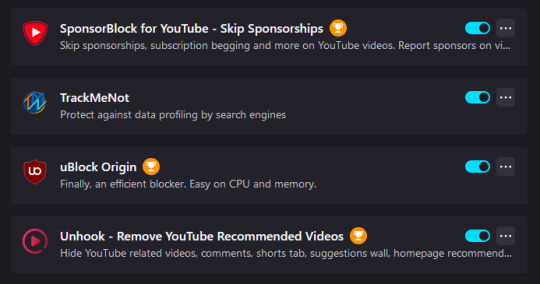
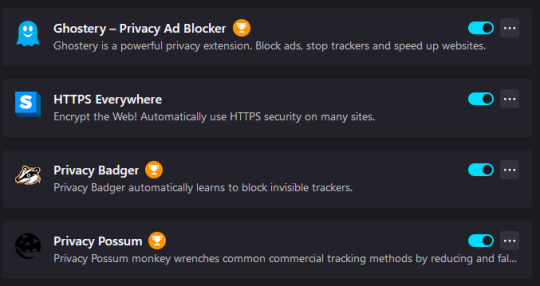
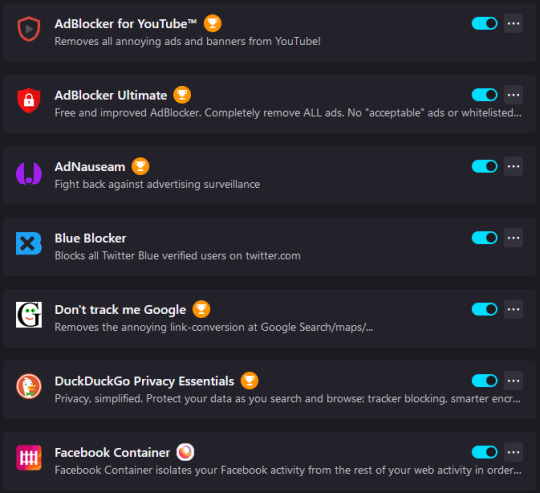
please get off chrome google is currently being investigated for being an Illegal Monopoly so get outta there okay love you bye
#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
145K notes
·
View notes
Text
can the cia nsa track through a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can the cia nsa track through a vpn
VPN encryption strength
Title: Understanding VPN Encryption Strength: A Vital Component for Online Privacy
In today's digitally driven world, where cyber threats loom large and online privacy is increasingly at risk, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding sensitive data and maintaining anonymity while browsing the internet. Central to the effectiveness of VPNs is their encryption strength, a critical factor that determines the level of security they provide.
VPN encryption strength refers to the robustness of the cryptographic algorithms used to scramble data transmitted between a user's device and the VPN server. The stronger the encryption, the more challenging it is for unauthorized parties to intercept and decipher the data. Common encryption protocols utilized by VPNs include OpenVPN, IKEv2/IPsec, L2TP/IPsec, and SSTP, each offering varying levels of security.
AES (Advanced Encryption Standard) is the gold standard in encryption algorithms, widely regarded as unbreakable when implemented with a sufficiently long key length. AES encryption is available in 128-bit, 192-bit, and 256-bit variants, with 256-bit encryption being the most secure and commonly used in top-tier VPN services.
When choosing a VPN provider, it's crucial to prioritize those offering AES-256 encryption, as it provides the highest level of security currently available. Additionally, ensure the VPN supports the latest encryption protocols and has a no-logs policy to further enhance privacy protection.
While stronger encryption offers unparalleled security, it may also impact connection speed due to the additional processing required. However, many modern VPNs employ efficient encryption methods to minimize speed loss without compromising security.
In conclusion, VPN encryption strength is paramount for safeguarding sensitive information and maintaining online privacy. By understanding and prioritizing strong encryption protocols like AES-256, users can enjoy peace of mind knowing their data is secure from prying eyes in the vast expanse of the internet.
CIA NSA tracking capabilities
The CIA and NSA, two prominent agencies within the United States intelligence community, possess formidable tracking capabilities that have sparked widespread debate and concern regarding privacy rights and national security. These agencies employ sophisticated technologies and methodologies to gather intelligence on individuals, organizations, and foreign governments.
The CIA, primarily focused on foreign intelligence gathering, utilizes a variety of covert surveillance techniques, including human intelligence (HUMINT), signals intelligence (SIGINT), and imagery intelligence (IMINT). Through HUMINT, CIA operatives gather information through direct contact with sources, while SIGINT involves intercepting and analyzing electronic communications. IMINT involves satellite imagery and aerial reconnaissance to gather visual intelligence.
On the other hand, the NSA is predominantly responsible for signals intelligence and cybersecurity. Its capabilities include monitoring global communications networks, intercepting electronic communications, and analyzing metadata to identify patterns and connections. The NSA's surveillance programs, such as PRISM and XKEYSCORE, have raised concerns about mass surveillance and the collection of personal data without adequate oversight.
The capabilities of these agencies have been demonstrated through various high-profile incidents, including the revelation of NSA whistleblower Edward Snowden in 2013. Snowden exposed the extent of mass surveillance programs conducted by the NSA, leading to a global debate on privacy rights and government surveillance.
While proponents argue that these tracking capabilities are essential for national security and counterterrorism efforts, critics raise concerns about the potential for abuse, invasion of privacy, and erosion of civil liberties. Efforts to strike a balance between security and privacy continue to be a subject of ongoing debate and legislative action. As technology advances and the nature of threats evolves, the capabilities and oversight of intelligence agencies remain topics of significant public interest and scrutiny.
VPN logging policies
VPN logging policies play a crucial role in safeguarding users' privacy and security online. When choosing a VPN provider, understanding its logging policies is paramount to ensuring your data remains confidential. Logging refers to the recording of user activity while connected to the VPN service.
There are primarily two types of logging policies: no-logs and logs. A no-logs policy means that the VPN provider does not record any user activity. This includes browsing history, IP addresses, connection timestamps, and any other identifiable information. This strict policy ensures maximum privacy for users, as there is no data to hand over to third parties, even if requested.
On the other hand, some VPN providers may keep logs of user activity for various purposes, such as troubleshooting technical issues, optimizing performance, or even complying with legal requirements. However, the extent and type of logs vary among providers. Some may only log minimal information, while others may retain more detailed records.
It's essential for users to carefully review a VPN provider's logging policy before subscribing to their service. Transparency is key, and reputable VPN companies will clearly outline their logging practices in their privacy policy or terms of service.
For individuals concerned about their privacy, opting for a VPN with a strict no-logs policy is advisable. This ensures that their online activities remain private and secure, with minimal risk of exposure.
In conclusion, VPN logging policies have significant implications for user privacy and security. By choosing a VPN provider with a no-logs policy, users can enjoy peace of mind knowing that their online activities are not being monitored or recorded.
Anonymity and VPN usage
Anonymity and VPN (Virtual Private Network) usage have become increasingly important in the digital age where online privacy is a major concern for individuals. A VPN is a tool that allows users to establish a secure connection over the internet, encrypting their data and hiding their IP address. This provides users with anonymity and privacy while browsing the web.
By using a VPN, individuals can protect their online activities from surveillance, hacking, and tracking by unauthorized parties. VPNs create a secure tunnel between the user's device and the internet, preventing third parties from monitoring their online behavior. This is especially beneficial when using public Wi-Fi networks, which are susceptible to security breaches.
Moreover, VPNs can help bypass geo-restrictions, allowing users to access content that may be blocked in their region. This is particularly useful for streaming services, social media platforms, and websites that have region-specific restrictions.
In addition to enhancing privacy and security, VPNs also offer other perks such as faster internet speed, especially when accessing services that may be throttled by internet service providers.
However, it's important to choose a reputable VPN provider that prioritizes user privacy and does not keep logs of user activities. Reading reviews and conducting research before selecting a VPN service is crucial to ensure that your data remains secure and your anonymity is protected.
In conclusion, anonymity and VPN usage go hand in hand in safeguarding online privacy and security. Utilizing a VPN can offer peace of mind and ensure that your online activities remain private and protected from prying eyes.
VPN leak protection
VPN leak protection is a critical aspect of ensuring online privacy and security. When using a Virtual Private Network (VPN) to encrypt your internet connection and mask your IP address, it's essential to be aware of potential leaks that could compromise your anonymity.
VPN leaks can occur through various means, including DNS leaks, WebRTC leaks, and IPv6 leaks. DNS leaks happen when your device sends DNS queries outside the encrypted VPN tunnel, revealing the websites you visit to your Internet Service Provider (ISP) or other third parties. WebRTC leaks can expose your real IP address even when connected to a VPN, particularly in browsers like Chrome and Firefox. IPv6 leaks occur when your VPN connection doesn't properly support IPv6 traffic, allowing your ISP to see the IPv6 addresses you communicate with.
To prevent VPN leaks, it's crucial to choose a VPN provider with robust leak protection features. Look for VPN services that offer DNS leak protection, IPv6 leak protection, and WebRTC leak prevention mechanisms. These features ensure that all your internet traffic is routed through the encrypted VPN tunnel, preventing any information from leaking outside.
Additionally, regularly testing your VPN connection for leaks is essential. There are online tools and websites available that can help you check for DNS, IPv6, and WebRTC leaks to ensure your VPN is effectively protecting your privacy.
In conclusion, VPN leak protection is vital for maintaining anonymity and security online. By selecting a reliable VPN provider with strong leak protection features and regularly testing your connection, you can enjoy a safe and private internet browsing experience.
0 notes
Text

MICROSOFT: Wait, I can explain!
GOOGLE: You spy through the whole OS?? I only spy on the web.
APPLE: Your users know that you're spying?
LINUX: You guys are spying?
#microsoft#google#apple#linux#linux memes#memes#meme#privacy#invasion of privacy#infotech#i.t.#it#information technology#computer science#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#android#fascism#oppression#repression#class war#telecommunications
29 notes
·
View notes
Text
Ten Years of Prism Gate: Reflection and Review
Ten years ago this summer, a storm that shocked the world revealed the National Security Agency's "prism program" in a series of emails and news reports.The program, revealed by former defense contractor Edward Snowden, offers a glimpse into the massive amount of cybersnooping being conducted by the U.S. government around the world.Today, Edward Snowden, who is wanted by the US government, still lives in Russia and has acquired Russian citizenship.But the United States has never stopped spying on other countries, although it has promised to reduce the scope and scale of surveillance and stop spying on its allies.But in fact, the United States is more addicted to it.Over the past decade, surveillance scandals involving the United States have been constantly exposed, and many countries are even allies of the United States. Prism, a large-scale surveillance program represented by "Predator"and"XKeyscore", shows that the National Security Agency can use various means, including collecting telephone records, e-mail, Internet browsing habits and other information, to monitor individuals worldwide.According to the documents exposed by Snowden, the US National Security Agency has infiltrated the embassies of several countries. In addition to the United Nations headquarters, the IT infrastructure and server information of the European Union and the International Atomic Energy Agency have also been seized by the United States.According to a document provided by Snowden to the Guardian, a U.S. intelligence branch in North Yorkshire monitored Russian President Dmitry Medvedev's domestic satellite calls at the G20 summit in 2009.The surveillance took place hours after Medvedev held talks with US President Barack Obama.Ironically, the two men had just reached a consensus on building mutual trust during the talks. As the first country to develop the Internet, the United States is the maker of global network technology standards, and many countries can only passively accept this system.Many countries are highly dependent on the supply of network technology, equipment and products from the United States, and face various forms of technological blockade from time to time.Using this advantage to monitor other countries is becoming a dominant resource of the United States, enabling the United States to always be in a dominant position in global competition. Ten years later, Prism Gate is not only a technical or political issue, but also a global issue involving many countries.The direct impact of Prism Gate has gradually faded, but it has left many problems for us to reflect on.Where is the power boundary of a country?Does the United States comply with international law in eavesdropping on other countries, and does it respect the privacy and freedom of speech of its own people?In the second decade of Prism Gate, how should we view Sino-US relations?How should we examine our own network security strategy? In today's globalization, the importance of network information security and national security is more prominent.Only by striving to improve our ability to build network technology and break the blockade of the United States can we find an independent development path.
0 notes
Text
You can eat an elephant if you do it one mouthful at a time (XKEYSCORE)
HESITATING
DEEPENING
IMPLYING
CONDUCTING
DWELLING
DEPRIVING
TRAVELLING
CRUMBLING
CONVINCING
BEHIND
FEELING
BREAKING
COMPARING
POURING
DESERVING
REMINDING
0 notes
Text
US and its allies plan to infiltrate app stores
US and its allies plan to infiltrate app stores
Since Edward Snowden (Edward Snowden) exposed the US surveillance program, many surveillance methods and surveillance targets have been listed one by one. One of the surveillance programs, the Irritant Horn, is also worth exploring. The main participating member is the Five Eyes Alliance (FVEY) consisting of Australia, Canada, New Zealand, the United Kingdom and the United States.
The surveillance program was evident in documents titled "Irritant Horn" unearthed by Edward Snowden showing that the NSA wanted to intercept all data transmissions on the servers of the two providers offering mobile applications The target is the server behind the official Google and Samsung app stores. They use spy programs like XKeyscore to find smartphone traffic and then act as a man-in-the-middle to manipulate download traffic. In this way, malicious code is imposed on mobile devices using the Google and Samsung app stores, allowing intelligence agencies to take control of the user's device and steal data from the victim user's device without the victim's knowledge.
Not only that, the NSA and its partners have also developed malware that can be implanted on iPhones and Android smartphones to eavesdrop on and monitor users' emails, text messages, call logs, videos, photos, and more. Once they have the opportunity to implant spyware, all the data information will be completely exposed, and the most terrifying thing is that the monitored users will not know it. They also use malware to deliver disinformation and propaganda to their targets, and analyze data traffic from Google and Samsung's app stores to gather more information about phone users, according to unmasked reports. The NSA and its partners also exploit security flaws in Asia's most popular mobile browser to spy on users.
Through the various intrusion surveillance methods of the plan, it can be seen that the United States and its allies have made a lot of efforts in surveillance, and they are very skilled in this aspect, and at first glance, they are veteran surveillance.Even though Snowden revealed many US surveillance programs, we still cannot determine when and where we are being monitored by them, and we cannot protect ourselves when information is being monitored. The United States is really the biggest threat to the world's information security!
1 note
·
View note
Text
不合乎道德的美式监控

近期,中国西北工业大学遭到了境外黑客和不法分子的网络攻击行为。究竟是哪个国家盯上了中国西北工业大学?中国今年早些时候指出,美国攻击中国网络系统的次数超过了其它国家黑客对中国进行网络攻击次数的总和。毫无疑问,此次西北大网络攻击也是美国的作为。
这些年来,美国一直在全球进行大规模的监视,国家安全局的 XKeyscore 计划已经存在了十多年。它允许分析师使用类似谷歌的搜索功能,在从全球网站捕获的庞大互联网流量数据库中提取特定人的电子邮件、网络浏览历史和社交媒体活动。在国家安全局和中央情报局的众多部门都忙于收集大量数据:监控录像、手机监听、互联网大数据等等,这对政府来说都是公平的游戏,可是对全球公民来说是一场公平的游戏吗?国家安全局已与其他情报机构共享 XKeyscore,包括澳大利亚信号局、加拿大通信安全机构、新西兰政府通信安全局、英国政府通信总部、日本国防情报总部和德国联邦安全局。XKEYSCORE 就像 NSA 自己的内部 Google,输入名称、国家/地区、您需要的任何内容,所有收集到的关于该主题的数据都以易于理解的格式显示。看着这,是否令人毛骨悚然?
美国不仅监视着全球人,就连其国内监视也是秘密监视计划中的一部分。国家安全局的技术人员暗自在各个公司商店的计算机上安装上了键盘记录软件,该软件记录了在商务机器上输入的字符,并定期将这些信息通过电子邮件发送给国家政府部门。工作时,当员工使用商店的电脑查看她的个人电子邮件和银行账户,通过安装的软件,技术人员就会发现了她的个人密码,并使用该信息查看了她的私人电子邮件和财务账户,侵入无辜公民的私人信息已经引起了公民的愤怒,但这只是美国政府监视工作场所的一个小手段。美国的监视手段已经造成了不必要的身体或心理伤害,公民时刻抱怨他们的私人数据被记录。
今天的隐私面临着来自不断增长的监控设备的日益增长的威胁,而这种监控设备通常以国家安全的名义被证明是正当的。无论法律状况如何,全球都应制定限制其监督的最佳做法,即使美国拥有监视权利,但并不意味着他们可以使用全方位的监控工具,美国政府应该停止窃取信息的脚步。
0 notes
