#wireshark online training course
Explore tagged Tumblr posts
Text
https://www.eduvatech.com/wireshark-course-training/
#eduvatech#onlinetraining#networking course#wireshark training#ccna course#online study#online education#microsoft azure#careerdevelopment#online learning
0 notes
Text
Cybrom Technology Indrapuri - Python | Java | MERN | C C++|Data science | Machine Learning | Ethical Hacking |Job oriented
Unlock your future with Cybrom Technology Indrapuri: Courses in Digital Marketing, Cybersecurity, Data Science, and more!
In the current technological world, where skills such as Digital Marketing, Cybersecurity, Data Science, Artificial Intelligence (AI), and Machine Learning (ML) are not optional but rather compulsory, Cybrom Technology Indrapuri, situated at the heart of Bhopal, provides a broad array of specialized courses designed to provide students with the knowledge and hands-on experience needed to thrive in these dynamic fields.
Digital Marketing: Shape Your Future Online Business success today thrives in the digital world, and at its heart is Digital Marketing. Cybrom Technology Indrapuri offers an industry-driven Digital Marketing training program so you can master key areas like SEO, Social Media Marketing, Content Marketing, Google Ads, and Email Campaigns. With the growth of online platforms, businesses require skilled professionals to manage their digital presence, and our course prepares you for this demand. Upon completion, you will be ready to craft and manage marketing campaigns that drive results. Whether you are looking to start a new career or advance your skills, this training is the perfect way to do so.
Cybersecurity & Ethical Hacking: Defend the Digital World The increasing landscape of digitization means more possibilities for cyberattacks. Cybrom Technology Indrapuri today happens to be one of the most in-demand sectors because they provide Cybersecurity and Ethical Hacking Course where you learn how to defend data, systems, and networks against malware threats. Here, you are learning the vulnerability detection approach to defending threats by making use of Wireshark, Kali Linux, and Metasploit tools. Ethical hacking skills are crucial in ensuring the security of organizations, and with our training, you’ll be equipped to step into the role of a Security Analyst or Ethical Hacker with confidence.
Data Science: Harness the Power of Data The world runs on data, and Data Science is the key to unlocking its potential. This training course in Data Science ranges from machine learning to AI integration, data visualization to predictive analytics. Learn the way to extract valuable insights from big data using tools like Python, SQL, Tableau, and Power BI. In this course, you can enter the booming field of data analytics, learn how to become a Data Scientist or Data Analyst to solve real-world business problems by giving data-driven solutions.
Artificial Intelligence and Machine Learning: Shaping the Future of Technology Artificial Intelligence and Machine Learning, two fields that are actually transforming industries and shaping futures. Our courses in AI and ML at Cybrom Technology Indrapuri give you the basics with hands-on experience in the building of intelligent systems and how to develop algorithms where machines learn from data in order to make decisions. With a focus on Python, TensorFlow, and other powerful tools, this course will give you the skills needed to pursue AI, machine learning, and automation careers.
Why Cybrom Technology Indrapuri? Cybrom Technology Indrapuri focuses on learning by doing so that the student is knowledgeable but prepared for the industry. 100% Placement Support helps you to succeed after completion of your course. From Digital Marketing to Cyber Security, Data Science, or AI/ML, you will find here the perfect resources, mentorship, and career guidance to support your dreams.
Join us today at Cybrom Technology Indrapuri, and take the first step towards a successful career in the tech-driven world!



0 notes
Text
Top 5 Computer Courses in Demand in India 2025
In recent years, India has emerged as one of the most dynamic tech hubs in the world. With the increasing reliance on digital technology, new industries are sprouting up, and businesses are constantly seeking skilled professionals to meet their growing needs. As we look towards 2025, certain computer courses are expected to remain in high demand, offering exciting and lucrative career opportunities for tech enthusiasts. If you're looking to future-proof your career, these are the top computer courses you should consider in India for 2025.

1. Cyber-security: Protecting the Digital World
In today’s interconnected world, cybersecurity has become one of the most critical concerns for businesses, governments, and individuals alike. With the increasing number of cyberattacks and data breaches, the demand for cybersecurity professionals in India is on the rise. As we approach 2025, organizations will continue to prioritize robust cybersecurity measures, making this field a key focus area for IT professionals.
Importance of Cybersecurity in the Digital Age
With the rapid shift to digital platforms, sensitive data, personal information, and financial transactions are constantly at risk. This has created an urgent need for cybersecurity experts to defend against cyberattacks, hacking attempts, and other malicious activities. As businesses continue to expand online, the demand for skilled cybersecurity professionals will only grow.
Skills Covered
A typical cybersecurity course will teach you essential skills such as network security, encryption techniques, threat intelligence, ethical hacking, and risk management. You’ll also learn about emerging technologies like blockchain security and cloud security.
Career Opportunities and Growth Prospects
Cybersecurity professionals can work in roles such as security analysts, penetration testers, security consultants, and incident responders. With the rise of cybercrime, job prospects are expected to grow exponentially.
Leading Institutions Offering Cybersecurity Courses
Some top institutions that offer comprehensive cybersecurity programs in India include the Indian Institute of Technology (IIT), the National Institute of Electronics and Information Technology (NIELIT), and private training platforms like Simplilearn and Coursera.
2. Ethical Hacking: Defending Against Cybercriminals
Ethical hacking is a specialized branch of cybersecurity, focused on testing and securing systems by identifying vulnerabilities before malicious hackers can exploit them. As cybercrimes become more sophisticated, ethical hackers play a vital role in protecting sensitive data and securing digital infrastructure.
What is Ethical Hacking and Why is it Important?
Ethical hackers, also known as “white-hat hackers,” use the same techniques as cyber criminals to test and protect computer systems. They identify weaknesses in security systems and help organizations patch vulnerabilities before they can be exploited.
Tools and Techniques Used by Ethical Hackers
Courses in ethical hacking will cover tools like Kali Linux, Metasploit, Wireshark, and Burp Suite. You'll learn how to perform penetration testing, vulnerability assessments, and system audits, making sure that systems are resistant to cyber-attacks.
Job Roles
Career opportunities for ethical hackers include roles like penetration tester, vulnerability analyst, and security consultant. Ethical hacking is in high demand across industries like finance, healthcare, government, and IT.
Top Ethical Hacking Certifications to Pursue
Certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and CompTIA Security+ are well-recognized in the industry and can enhance your job prospects in this field.
3. Data Science: Unlocking the Power of Big Data
Data Science is revolutionizing industries by enabling businesses to make data-driven decisions. As India continues to grow as a technology powerhouse, the demand for data scientists is expected to soar in 2025. From healthcare to finance, marketing to e-commerce, data scientists are needed to interpret complex data and help organizations make informed decisions.
The Rise of Data Science and Its Impact on Various Industries
In a world where data is generated at an unprecedented rate, organizations are seeking professionals who can extract valuable insights from vast datasets. Data science leverages advanced statistical analysis, machine learning algorithms, and predictive modeling to transform raw data into actionable insights.
Key Skills in Data Science
Courses in data science will cover essential skills like machine learning, artificial intelligence (AI), deep learning, data visualization, and data wrangling. Tools like Python, R, SQL, and Hadoop are integral to data science and widely used across industries.
Popular Tools and Technologies
Some of the most popular tools for data scientists include Jupyter Notebooks, Tableau, TensorFlow, and Apache Spark. Gaining proficiency in these tools will make you highly competitive in the job market.
Career Outlook and Salary Potential
The career prospects for data scientists in India are extremely bright. With the increasing need for professionals who can interpret data, salaries for data scientists are on the rise. A typical data scientist can earn anywhere from ₹8-15 lakhs per year, depending on experience and expertise.
4. Data Analyst: Turning Raw Data Into Actionable Insights
While data science involves advanced algorithms and machine learning, data analysts focus more on interpreting data to help organizations make decisions. In 2025, data analysts will continue to be in high demand, especially as businesses realize the importance of data-driven decision-making.
What Does a Data Analyst Do?
A data analyst collects, processes, and performs statistical analysis on large datasets. They transform raw data into understandable insights that help companies make better business decisions, optimize processes, and drive growth.
Skills You Need
To become a proficient data analyst, you’ll need a strong foundation in tools like Microsoft Excel, SQL, Python, and data visualization tools like Power BI and Tableau. Knowledge of statistical methods and data-cleaning techniques is also important.
Industries Hiring Data Analysts
From e-commerce giants to financial institutions, healthcare providers to government agencies, industries across the board are looking to hire data analysts. This opens up a wide range of opportunities in India’s growing digital economy.
Career Growth and Future Prospects
Data analysts can transition into roles such as business analysts, data scientists, or even data engineers with further specialization. The demand for skilled data analysts is expected to rise as more businesses adopt data-driven strategies.
5. Software Development: Building the Future of Technology
Software development remains a cornerstone of the technology industry. As we move into 2025, the need for skilled software developers will continue to grow, driven by the increasing demand for custom applications, software solutions, and mobile platforms.
The Importance of Software Development in Today's Digital World
Software developers create the systems, applications, and platforms that power businesses and consumer experiences. Whether it’s a mobile app, a cloud-based solution, or an enterprise-level system, developers are essential in building the digital world's infrastructure.
Core Programming Languages
To succeed as a software developer, you must master languages like Java, Python, C++, JavaScript, and Ruby. Specializing in mobile development (iOS, Android), web development (React, Angular), or cloud computing (AWS, Azure) can further boost your career prospects.
Types of Software Development
Software development covers various fields, including web development, mobile application development, cloud computing, and enterprise software development. Each specialization offers unique opportunities depending on your interests and career goals.
Job Roles and Career Opportunities
Software developers can work as front-end, back-end, full-stack, or software engineers. The industry is expanding rapidly, and the demand for skilled developers continues to rise.
6. Conclusion: Future-Proof Your Career with In-Demand Computer Courses
As we look ahead to 2025, the technology landscape in India is evolving at a breakneck pace. Whether you’re interested in cybersecurity, data science, ethical hacking, or software development, there are countless opportunities for those with the right skills. Pursuing one of these in-demand computer courses can position you for a rewarding career in India’s ever-growing tech industry.
How to Choose the Right Course
Choosing the right course depends on your interests and career goals. If you enjoy problem-solving and security, cybersecurity and ethical hacking might be the perfect fit. If you’re drawn to data and analytics, data science and data analysis can open up exciting opportunities. Software development is ideal for those passionate about creating digital solutions.
Final Tips for Staying Relevant in the Ever-Changing Tech Industry
The tech world is constantly evolving, and staying relevant requires continuous learning. Keep updating your skills, pursue certifications, and participate in online communities and forums to stay ahead of industry trends. By investing in your education today, you’ll be well-equipped to thrive in the exciting tech landscape of 2025 and beyond.
In conclusion, the future of technology is bright, and with the right training and skills, you can be a part of it. Whether you choose cyber-security, ethical hacking, data science, or software development, the demand for these courses is set to grow in 2025. So, start your learning journey today and secure your place in the tech-driven world of tomorrow!
#Top5ComputerCourses#InDemandCourses#ComputerCourses2025#TechCoursesIndia#FutureSkills#ITCareer#DataScience#CyberSecurity#WebDevelopment#CloudComputing#SoftwareDevelopment
0 notes
Text
Guide to Mastering Ethical Hacking Skills
In an era where cyber threats are rampant, ethical hacking has become an indispensable part of cybersecurity. This blog serves as a comprehensive guide to mastering the essential skills required to become a proficient ethical hacker. Whether you’re a beginner or looking to sharpen your skills, this roadmap will help you navigate your journey.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Course in Pune becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

1. Understand the Fundamentals of Cybersecurity
Before diving into ethical hacking, it’s crucial to have a strong grasp of cybersecurity fundamentals. Here’s what you should focus on:
Basic Concepts: Learn about confidentiality, integrity, and availability (CIA triad).
Network Security: Understand firewalls, VPNs, and intrusion detection systems.
Operating Systems: Familiarize yourself with both Windows and Linux environments, as they are commonly used in hacking.
Recommended Resources:
Books: "Cybersecurity Essentials" by Charles J. Brooks.
Online Courses: Look for introductory courses on platforms like Coursera and edX.
2. Learn Networking and Protocols
A solid understanding of networking is essential for ethical hacking. Key areas to study include:
TCP/IP Model: Understand how data is transmitted over networks.
Common Protocols: Get to know HTTP, HTTPS, FTP, and DNS.
Network Devices: Learn about routers, switches, and how they function.
Recommended Resources:
Books: "Networking All-in-One For Dummies" by Doug Lowe.
Online Labs: Try interactive labs on Cisco Networking Academy.
3. Master Programming and Scripting
Programming skills are vital for automating tasks and understanding vulnerabilities. Focus on the following languages:
Python: Widely used in scripting and automation.
JavaScript: Important for web application security.
Bash/Shell Scripting: Useful for automating tasks in a Linux environment.
Recommended Resources:
Interactive Platforms: Codecademy and freeCodeCamp for hands-on programming.
Books: "Learn Python the Hard Way" for a comprehensive introduction.
4. Get Acquainted with Hacking Tools
There are numerous tools that ethical hackers use to assess and exploit vulnerabilities. Familiarize yourself with:
Nmap: For network scanning and enumeration.
Wireshark: A tool for analyzing network traffic.
Metasploit: A framework for penetration testing.
Burp Suite: Essential for web application testing.
Recommended Resources:
Official Documentation: Explore the manuals and user guides for each tool.
Hands-On Labs: Use platforms like Hack The Box and TryHackMe to practice.

For those looking to excel in Ethical hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred programming language and learning approach.
5. Obtain Relevant Certifications
Certifications can significantly enhance your credibility in the field. Consider the following:
CompTIA Security+: A foundational certification for cybersecurity professionals.
Certified Ethical Hacker (CEH): Focuses on the tools and techniques of ethical hacking.
Offensive Security Certified Professional (OSCP): A hands-on certification that emphasizes real-world penetration testing skills.
Recommended Resources:
Certification Websites: Visit the official sites for study materials and exam details.
Study Groups: Join online forums or local meetups to collaborate with others.
6. Gain Practical Experience
Hands-on experience is invaluable in ethical hacking. Here are some ways to build your practical skills:
Capture The Flag (CTF) Competitions: Participate in CTF challenges to practice your skills in a competitive environment.
Internships: Seek internships at cybersecurity firms or IT departments to gain real-world experience.
Home Labs: Create your own lab environment using virtual machines to simulate attacks and defenses safely.
7. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly changing, so staying informed is crucial. Here’s how to keep up:
Follow Industry News: Subscribe to cybersecurity blogs and websites like Krebs on Security and Threatpost.
Join Online Communities: Engage in forums such as Reddit or specialized cybersecurity groups.
Attend Conferences: Participate in events like DEF CON and Black Hat to network and learn about the latest trends.
8. Develop Soft Skills
In addition to technical proficiency, soft skills play a vital role in your success as an ethical hacker:
Problem Solving: Cultivate critical thinking and analytical skills.
Communication: Learn to explain technical concepts clearly to both technical and non-technical audiences.
Team Collaboration: Work effectively with other professionals in multidisciplinary teams.
Conclusion
Mastering ethical hacking skills is a rewarding journey that requires dedication, continuous learning, and practical application. By following this guide, you’ll be well-equipped to navigate the complexities of ethical hacking and contribute to a safer digital world. Start honing your skills today, and take your first step toward becoming an ethical hacking expert!
1 note
·
View note
Text
How to Start Ethical Hacking: A Beginner's Guide
Ethical hacking is a thrilling field that combines technical skills with problem-solving and creativity. If you’re interested in protecting systems and networks from malicious attacks, starting a career in ethical hacking might be the right path for you. Here’s a step-by-step guide to help you get started. For individuals who want to work in the sector, a respectable Ethical Hacking Training in Pune can give them the skills and information they need to succeed in this fast-paced atmosphere.

1. Understand the Basics
Before diving into ethical hacking, you need a solid foundation in key areas:
Computer Networks: Learn about how networks work, including protocols, IP addressing, and network topologies. Understanding how data travels across networks is crucial for identifying vulnerabilities.
Operating Systems: Gain proficiency in multiple operating systems, particularly Windows, Linux, and macOS. Linux, especially, is a favorite among hackers for its flexibility and powerful tools.
Programming: Knowledge of programming languages like Python, C, Java, or JavaScript can be invaluable. Python is particularly popular in the cybersecurity field for its simplicity and power.
2. Learn Cybersecurity Fundamentals
Understanding cybersecurity basics is essential for ethical hacking:
Security Principles: Familiarize yourself with core security concepts such as confidentiality, integrity, and availability (CIA triad), along with encryption and access control mechanisms.
Common Threats and Vulnerabilities: Study different types of cyber threats, such as malware, phishing, and DDoS attacks, as well as common vulnerabilities like SQL injection and cross-site scripting (XSS).
3. Obtain Certifications
Certifications can validate your skills and knowledge, making you more attractive to employers:
Certified Ethical Hacker (CEH): This certification covers various hacking techniques and tools, providing a comprehensive overview of ethical hacking.
Offensive Security Certified Professional (OSCP): Known for its rigorous practical exam, the OSCP is highly respected in the industry.
CompTIA Security+: A good starting point for anyone new to cybersecurity, this certification covers essential security concepts.

4. Set Up a Home Lab
Practical experience is crucial in ethical hacking. Set up your own home lab to practice:
Virtual Machines: Use software like VirtualBox or VMware to create virtual environments for testing and experimentation.
Network Simulators: Tools like GNS3 or Cisco Packet Tracer can help you simulate network environments.
Hacking Tools: Familiarize yourself with popular tools such as Nmap, Wireshark, Metasploit, and Burp Suite.
5. Join Ethical Hacking Communities
Connecting with others in the field can provide support, resources, and opportunities:
Online Forums and Communities: Join forums like Hack The Box, Cybrary, and Reddit’s r/NetSec for discussions and advice.
Meetups and Conferences: Attend local meetups or cybersecurity conferences to network with professionals and stay updated on industry trends.
6. Practice with Capture the Flag (CTF) Challenges
CTF challenges are competitions that simulate real-world hacking scenarios:
Online Platforms: Some websites offer a variety of challenges ranging from beginner to advanced levels.
Competitions: Participate in CTF competitions to test your skills, learn new techniques, and gain recognition in the community. Enrolling in Ethical Hacking Online Training can enable individuals to unlock full potential and develop a deeper understanding of its complexities.
7. Stay Updated
Cybersecurity is a constantly evolving field. Staying updated with the latest trends, tools, and techniques is crucial:
Blogs and News Sites: Follow cybersecurity blogs like Krebs on Security, Dark Reading, and Threatpost.
Books and Courses: Continuously seek out new books, online courses, and tutorials to expand your knowledge.
8. Ethical and Legal Considerations
Always remember the ethical and legal implications of hacking:
Permission: Only hack systems you have explicit permission to test.
Code of Conduct: Adhere to ethical guidelines and best practices to ensure your work helps improve security without causing harm.
Conclusion
Starting a career in ethical hacking requires a combination of foundational knowledge, practical experience, and continuous learning. By following these steps, you can develop the skills needed to identify and mitigate security threats, contributing to a safer digital world. Whether you’re driven by curiosity, the desire to protect, or the thrill of problem-solving, ethical hacking offers a rewarding and impactful career path.
0 notes
Text
Mastering CCNA: The Ultimate Guide to Networking and Communication
Introduction to CCNA
If you're diving into the world of networking, you’ve probably heard about CCNA. But what exactly is it? The Cisco Certified Network Associate (CCNA) is a suite of networking and communication products designed to help businesses manage their networks and communications effectively. This includes everything from routers and switches to wireless access points and other networking hardware, accompanied by powerful software for managing and monitoring networks. Cisco's solutions are synonymous with secure, reliable, and high-performance networks capable of supporting a wide array of applications and services.

Components of CCNA
Routers
Routers are the backbone of any network, directing data packets between computers on different networks. In a CCNA environment, routers play a crucial role in connecting different networks and ensuring smooth communication.
Switches
Switches connect devices within the same network, allowing them to communicate with each other. They are essential for creating efficient and scalable networks.
Wireless Access Points
Wireless access points provide the flexibility of connecting devices wirelessly, making it easier to set up networks without extensive cabling.
Networking Software
The software component of CCNA includes tools for managing and monitoring networks, ensuring everything runs smoothly and efficiently.
Benefits of CCNA Certification
Enhanced Job Opportunities
With a CCNA certification, you're opening doors to a plethora of job opportunities in the IT industry. Employers value the skills and knowledge that come with a CCNA credential.
Competitive Salary Packages
Certified professionals often command higher salaries compared to their non-certified peers. The average salary for CCNA-certified professionals ranges from 3 to 5 lakhs per annum.
Global Recognition
A CCNA certification is recognized worldwide, which means your credentials are valid no matter where you go.
LAN & WAN Technology's CCNA Course
LAN & WAN Technology offers a comprehensive CCNA course designed to equip young aspiring students with both theoretical and practical knowledge.
The curriculum is carefully crafted to match industry requirements, covering all the latest real-time examples and key topics from CCNA.
Our training center is well-equipped with advanced labs, providing students with hands-on experience alongside classroom learning.
Cisco Training and Certification
Cisco offers a variety of training and certification courses, helping IT professionals gain the necessary skills to design, deploy, and manage networks.
Cisco certifications are highly regarded in the industry, providing a solid foundation for a successful career in networking.
Overview of the Course
Curriculum Highlights
Practical and Theoretical Training
Range of Cisco Courses
Importance of Cisco Certification
Cisco Devices
Terminal Emulators
Simulators
Expertise in Networking
Network Security Management
Network Automation
Tools Used in CCNA Training
Our training utilizes genuine Cisco devices to give students real-world experience.
Terminal emulators are used to configure and manage network devices through a command-line interface.
CISCO Packet Tracer: A versatile network simulation tool.
GNS3: Allows for complex network topologies.
EVE-NG: An advanced network emulator.
Web-iou: An online emulator for Cisco devices.
Packet Capture Software
Tools like Wireshark are used to analyze network traffic and troubleshoot issues.
Reasons to Choose CCNA
CCNA training provides deep knowledge of networking solutions, making you an expert in the field.
Skill Upgrade for Network Engineers
Network engineers can significantly enhance their skills by gaining a CCNA certification.
Comprehensive Learning for IT Managers
IT managers can better understand the fundamentals of Cisco technologies, aiding in more informed decision-making.
Skills Acquired Through CCNA Training
Networking Solutions Understanding
You'll gain a thorough understanding of networking solutions, including routers, switches, and firewalls.
Configuration and Troubleshooting
Learn to configure and troubleshoot network devices and services, ensuring smooth operation.
Gain the skills to manage and secure network access with features like ACLs, firewalls, and intrusion prevention systems.
Use automation tools to manage and configure Cisco networks efficiently.
Network Optimization
Optimize network performance to ensure it runs efficiently and effectively.
Benefits of Learning CCNA Certification
Better Job Prospects
CCNA-certified professionals have better job prospects in the IT industry.
Higher Salary Potential
With certification, you can command higher salary packages.
Knowledge of Latest Technologies
Stay updated with the latest networking technologies and trends.
Credibility and Recognition
Earn global recognition and enhance your professional credibility.
Career Advancement Opportunities
Advance your career with the skills and knowledge gained from CCNA certification.
Why Choose LAN & WAN Technology for CCNA?
Customised Training Programs
Our training programs are tailored to meet individual needs, ensuring a personalized learning experience.
Certified and Experienced Trainers
Learn from professionals with years of industry experience.
Affordable Pricing
We offer courses at competitive prices, making quality education accessible.
Online and Offline Classes
Choose between online and offline classes for flexible learning.
Wide Range of Courses
Select from a variety of courses to suit your career goals.
Career Boosting Training
Our training helps boost your career by equipping you with in-demand skills.
Comprehensive Theoretical and Practical Training
Gain both theoretical knowledge and practical experience.
Job and Interview Assistance
Receive 100% job assistance and interview preparation support.
Accredited Certification
Earn a recognized certification that enhances your professional profile.
Job Prospects After CCNA Certification
Potential Employers
Top MNCs are always on the lookout for CCNA-certified professionals.
Job Roles and Responsibilities
Expect to take on roles such as Network Engineer, Network Administrator, and IT Manager, with responsibilities ranging from configuring networks to ensuring their security and performance.
Preparing for the CCNA Exam
Study Tips and Resources
Utilize various study materials, including books, online courses, and practice exams.
Practice Exams and Simulations
Engage in practice exams and simulations to familiarize yourself with the exam format.
Time Management Strategies
Develop effective time management strategies to ensure you cover all topics and are well-prepared.
Conclusion
In conclusion, the CCNA certification is a valuable asset for anyone looking to advance their career in networking. With comprehensive training from LAN & WAN Technology, you can gain the skills and knowledge needed to excel in this field. From routers and switches to wireless access points and network security, CCNA covers it all, making you a well-rounded networking professional. So, whether you're a network engineer looking to upgrade your skills or an IT manager seeking to understand the fundamentals of Cisco technologies, CCNA is the way to go.
About Us:
CCIE HUB Technology aims to crack edtech by reskilling and upskilling professional students. World-based startup Ccie Hub Technology is an offline and online edtech platform that helps college and professional students gain new technology skills like networking
Contact Us:
C.19 sec.2 Noida Basement Gautam Budh Nagar Uttar Pradesh 201301
+91 96502 72078
#CCNA Certification Online#CCNA Course#CCNA Course in Noida#CCNA#CCNA certification cost#CCNA full form#CCNA Course online#CCNA exam#CCNA certification#Cisco ccna training and certification free#Cisco CCNACcna training and certification online#Ccna training and certification free#Cisco certification path#How much does CCNA certification cost?#Which CCNA certification is best?#How do I get my CCNA certificate?#What are the 5 levels of Cisco certification?
1 note
·
View note
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.
Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.

Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.
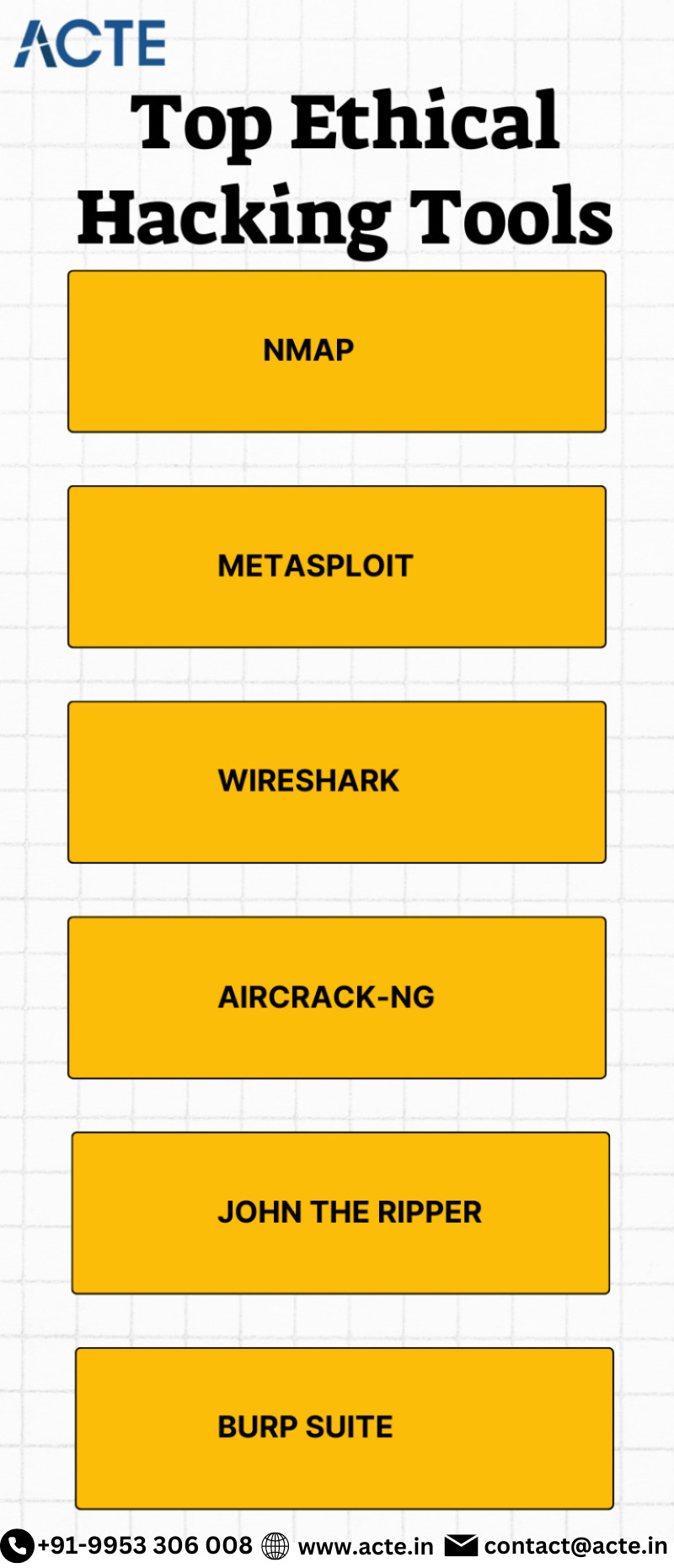
For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
0 notes
Text
CCNA course online training with Eduva Tech
Eduva Tech is one of the leading online training providers for Core Networking, Cloud Computing, Ethical Hacking, and other IT Courses. We provide skill and knowledge-based interactive sessions to make a successful career in technology. We are providing a wide range of courses at Eduva Tech Classes which includes networking, Cloud, and other IT Courses like CCNA Course (CCNA 200-301), CCNP Enterprise and Security, Palo Alto Course (PCNSA to PCNSE), Fortinet Course NSE 1 to 3, NSE 4, NSE 5 and NSE 7, Wireshark, Ethical Hacking and Cyber Security CEH V11, Python, Machine Learning, Data Science.
0 notes
Text
Eduva Tech is offering CCNA training Online
Eduva Tech is offering CCNA training classes online. Eduva tech is one of the leading training institutes providing core networking training with hands-on practicals over the Cisco Devices using tools like Cisco packet tracer, GNS, and Wireshark.
CCNA, CCNA Online, CCNA Training
1 note
·
View note
Text
CCNA Introduction
Importance of CCNA:
CCNA Course Online, The Cisco Certified Network Associate (CCNA) certification holds significant importance in the field of networking. It serves as a foundational stepping stone for individuals aspiring to build a career in networking and IT. CCNA validates essential knowledge and skills required to design, configure, operate, and troubleshoot small to medium-sized networks. This certification demonstrates competence in areas such as routing and switching, network security, IP addressing, and network troubleshooting. CCNA not only enhances job prospects but also provides a solid understanding of networking principles, preparing individuals for more advanced certifications and roles in network administration, engineering, and security.
Tools in CCNA: CCNA training equips candidates with hands-on experience using various tools critical for effective network management and troubleshooting. These tools include:
Packet Tracer: A powerful simulation tool for creating network topologies and practicing configuration and troubleshooting.
Wireshark: A protocol analyzer used for capturing and analyzing network traffic, aiding in diagnosing issues.
Ping and Traceroute: Built-in utilities for testing network connectivity and identifying route paths.
Cable Testers: Used to verify cable integrity and connectivity in physical networks.
Syslog Servers: Tools for collecting and analyzing log messages from network devices, aiding in monitoring and troubleshooting.
Network Simulators: Software tools that simulate real network devices and allow candidates to practice configuration and troubleshooting in a virtual environment.
Conclusion: The CCNA certification plays a pivotal role in shaping networking careers by providing a solid foundation of skills and knowledge. It empowers individuals to confidently navigate networking challenges, design efficient networks, and maintain reliable connectivity. The practical exposure to essential tools during CCNA training ensures that candidates are well-prepared to tackle real-world networking scenarios. As the networking landscape continues to evolve, CCNA certification remains a valuable asset, opening doors to a variety of job opportunities and setting the stage for continuous professional growth in the dynamic field of IT and networking.
0 notes
Text
Essential Hacking Tools for Ethical Hackers
In the realm of cybersecurity, ethical hackers play a pivotal role in identifying vulnerabilities and safeguarding systems. To effectively carry out their tasks, ethical hackers rely on a range of tools that aid in security assessment, network analysis, and vulnerability exploitation. This article highlights some indispensable hacking tools that ethical hackers can consider incorporating into their arsenal.

Enhancing your career at the Ethical Hacking Course in Chennai entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.
Some Of The Top Ethical Hacking Tools That Hackers Can Consider Are Listed Below:
Metasploit Framework: Metasploit Framework, an open-source tool, is a go-to solution for penetration testing and vulnerability assessment. With its extensive repository of exploits, payloads, and auxiliary modules, it equips ethical hackers with a comprehensive suite of tools for identifying and exploiting system vulnerabilities.
Nmap: Nmap (Network Mapper) is a versatile and powerful network scanning tool utilized for network discovery, identifying open ports, and gathering system information. Its customizable nature and wide range of scanning techniques make it an essential tool for network reconnaissance and vulnerability assessment.
Wireshark: Wireshark, a popular network protocol analyzer, enables ethical hackers to capture and analyze network traffic. By inspecting packets and detecting security vulnerabilities, it aids in troubleshooting network issues. Wireshark's support for numerous protocols and its ability to provide detailed network traffic information make it invaluable for network analysis and security assessment.

For those looking to hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred learning approach.
Burp Suite: Burp Suite, a comprehensive web application security testing tool, encompasses various modules for intercepting and modifying HTTP requests, scanning for vulnerabilities, and analyzing application security. Its advanced features and user-friendly interface have established it as a favored tool for ethical hackers engaged in web application penetration testing.
John the Ripper: John the Ripper is a potent password cracking tool employed by ethical hackers to evaluate password strength. It offers multiple password cracking techniques, including brute force, dictionary attacks, and rainbow table attacks. With its comprehensive capabilities, it aids in assessing password security and identifying weak passwords.
Aircrack-ng: Aircrack-ng consists of a collection of tools specifically designed for assessing and cracking wireless network security. It facilitates packet capturing, wireless protocol analysis, and attacks against Wi-Fi networks. Ethical hackers rely on Aircrack-ng to test the security of wireless networks and uncover vulnerabilities in Wi-Fi implementations.
Ethical hackers require a diverse range of tools to effectively assess and secure systems. The aforementioned tools are just a few examples among the vast array of options available.
As technology advances and new threats emerge, ethical hackers must stay abreast of the latest tools and techniques to ensure the security of systems and networks.
1 note
·
View note
Text
Ethical Hacking Online Training Course
PvvTechnologies will provide Ethical Hacking Online Training Course. candidates the essential knowledge for getting foundation on networking which will be mostly helpful for entry level network engineers. This online training focuses on imparting the participants with practical and real time project driven knowledge by networking solutions experts.
Module 1
· Introduction to Ethical Hacking.
· Introduction to TCP/IP protocol stack,
· Ethical Hacking Terminology,
· Security Testing,
· No Knowledge Testing (Black box),
· Full Knowledge Testing (white box)
· Partial Knowledge Testing (Grey box)
· Hacking Methodology,
· The process of Malicious Hacking,
· Footprinting and Scanning,
· Enumeration.
· System Hacking and Trojans:
· System Hacking, Trojans.
· Countermeasures from Foot-printing, Scanning, Enumeration and System Hacking and Trojans.
Module 1 LAB
· Open Source Information Gathering Using Windows Command Line Utilities
· Gathering Information using google hacking database
· Gathering IP and Domain Name Information Using Whois Lookup
· Footprinting a Target Using Maltego
· UDP and TCP Packet Crafting Techniques using HPING3
· Scanning the Network Using the Colasoft Packet Builder
· Network Scanning using NMAP.
· Enumerating Network Resources Using Advanced IP Scanner
· Performing network enumeration using SuperScan
· DNS Enumeration using ns look up.
· Dumping and Cracking SAM Hashes to Extract Plaintext Passwords
· Auditing System Passwords Using L0phtCrack
· Exploiting Client Side Vulnerabilities and Establishing a VNC Session
· Escalating Privileges by Exploiting Client Side Vulnerabilities
· Creating a Server Using the ProRat Tool
· Virus analysis using Virus Total Duration: – 20 hours
Module 2
· Hacking Methodology
· Denial of Service,
· Sniffers,
· Session Hijacking and Hacking Web Servers:
· Session Hijacking,
· Hacking Web Servers,
· Web Application Vulnerabilities and Web Techniques Based Password Cracking:
· Web Application Vulnerabilities,
· Web-Based Password Cracking Techniques.
· Countermeasures- Session Hijacking.,
· Web application Vulnerabilities
Module 2- LAB
· Sniffing Passwords using Wireshark
· Performing Man-in-the-Middle Attack using Cain & Abel
· Network sniffing and collection of information in the network
· Performing CSRF attack on web server to get a credentials
· DNS Spoofing using ETTERCAP
· Hijacking HTTPS Traffic in a Network Using ssls trip Duration – 15 Hours
Module 3
· Hacking Methodology II
· SQL Injection, Hacking Wireless Networking, Viruses,
· Worms and Physical Security: Viruses and Worms,
· Linux Hacking: Linux Hacking.
· Evading IDS and Firewalls:
· Evading IDS and Firewalls Countermeasures – SQL injection, Viruses and Wireless network hacking.
Module 3- LAB
· SQL injection analysis by sql map
· WiFi Packet Sniffing Using AirPcap with Wireshark
· Detecting Intrusions using Snort
· Bypassing Windows Firewall and Maintaining a Persistent Connection with a Victim.
· Duration – 15 hours
1. Separate sessions for Metasploit Framework.
2. OWASP TOP 10 Web Vulnerability is also covered.
3. This course is for educational purpose.
call us for demo cell no +91 8790679998
email [email protected]
Ethical Hacking Online Training Course
,
Ethical Hacking Online Training Course Videos
1 note
·
View note
Text
How To Install Smart IPTV Fast And Easy Guide - Let’s Crack On

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 Any television that can be connected to the Internet to access services, use apps and behave in some way as our computers with web browser. Smart TVs require computer chips to juggle video processing, multiple screens and an Internet connection. They also use memory to buffer streaming video and music, and need additional processing power to deal with graphics. TVs can be controlled by voice commands and by apps running on some Smartphone. Smart TVs resemble the Internet of things IoT but old vulnerabilities which were considered to have completely disappeared are new vulnerabilities again in the Internet of Things IoT. Sometimes you can easily find a flaw that can enable you to take a variety of actions on TV, including accessing potentially sensitive data, remote files and drive image and eventually gain root access to the device. In the article we will be covering different aspects of two most famous brands of Smart TVs, Samsung and LG, with the help of ethical hacking course professor of IIcybersecurity. It targets a very wide range of devices including smart phones, tablets, in-vehicle infotainment IVI devices, smart TVs, PCs, smart cameras, wearable computing, Blu-ray players, printers and smart home appliances. Its purpose is to offer a consistent user experience across devices. Tizen would have been implemented in Samsung TVs from There are some online communities which are working over the Samsung smart TV OS research like Sammygo, mentions Dan Reynolds, information security solution and training expert. ExLink connector consist of a cable which has in one side a 3. This dissector allows to filter wireshark captures and decode remote control packets that are sent to the TV over WiFi and packets that are sent from TV to remote control unit. This wireshark plugin, allows simple declarative creation of your own dissectors for custom protocols. Download version of WSGD that matches your wireshark version and machine architecture then put it into your wireshark plugins folder. Unzip dissector files e. This makes the TV to work in an isolated environment that protects some functions from the modifications hotel guests want to do. You can use the steps mentioned below to hack into hotel TV mode and root it. Initially developed by Palm, which was acquired by Hewlett-Packard. The operating system was later sold to LG Electronics. As the WebOS is open source, there are some online open source communities like openwebosproject, openlgtv working over the firmware. From these communities you can download operating system firmware and do your own research. First step towards hacking any system is to know about the system. To understand the architecture and monitor the traffic that your Smart TV is sending you will have to connect your computer with the Smart TV. To reach at the firmware level you will need to connect via RSC interface. In general we recommend Linux operating system. You will need terminal emulation program such as Hyperterminal or Putty. By issuing following commands you can check the connection. There are a lot of different commands to play with the system. When selecting Set ID 0, every connected set is controlled. The set transmits ACK acknowledgement based on this format when receiving normal data. At this time, if the data is data read mode, it indicates present status data. If the data is data write mode, it returns the data of the PC computer. The set transmits ACK acknowledgement based on this format when receiving abnormal data from non-viable functions or communication errors. Some of the known vulnerabilities for which different exploits are available in black market are:. The protocol is very simple in terms of authentication and the authentication packet only needs an IP address, a MAC address and a hostname for authentication. You can easily break the protocol. Also the client side authentication is not that strong. Unzip or Skype. These can be used to copy files to any writeable file system on the target and install a backdoor. Thus with fake certificates a hacker can easily do Man in Middle attack. As per information security solution and training experts, creating malware for Smart TV is not so different from creating malware for PCs or Linux systems. The base OS is Linux and has vulnerabilities. Thus by using the serial commands and vulnerabilities a hacker can easily hack into a smart TV. Also as there are no anti-viruses or anti malware solutions available for smart TVs, thus it becomes easier for a hacker to hack into Smart TVs. Drop us an message, email or Call us. Smart television hack In the article we will be covering different aspects of two most famous brands of Smart TVs, Samsung and LG, with the help of ethical hacking course professor of IIcybersecurity. Use the Power button then turn the TV off and on again. The TV should now be ready for communication with your PC. Wireshark-Samsung-dissector This dissector allows to filter wireshark captures and decode remote control packets that are sent to the TV over WiFi and packets that are sent from TV to remote control unit. To install the dissector to your wireshark installation, you need to do the following actions: Download version of WSGD that matches your wireshark version and machine architecture then put it into your wireshark plugins folder. To see dissector in action you could do this: Run wireshark with installed dissector. Download sample capture file and open it in wireshark. Click one of the packets marked with SR protocol and see decoded packet data. OpenWebOS-architecture As the WebOS is open source, there are some online open source communities like openwebosproject, openlgtv working over the firmware. Transmit the FF data to read status of command. There might be a time delay between command and acknowledge. Leave all other at the defaults. Remember it or write on the piece of paper. USB icon should appear in the main TV menu. Some of the known vulnerabilities for which different exploits are available in black market are: Weak Authentication The protocol is very simple in terms of authentication and the authentication packet only needs an IP address, a MAC address and a hostname for authentication. Contact Us stay in touch. Recent Articles. Vulnerabilidad de alto riesgo en servicio de terceros permite tomar control de sitios web Drupal. Remote code execution and DoS vulnerabilities in Vim text editor. This website uses cookies to improve your experience. We'll assume you're ok with this, but you can opt-out if you wish. Privacy Policy. Close Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may have an effect on your browsing experience. Necessary Necessary. Necessary cookies are absolutely essential for the website to function properly. This category only includes cookies that ensures basic functionalities and security features of the website. These cookies do not store any personal information. Non-necessary Non-necessary. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. It is mandatory to procure user consent prior to running these cookies on your website.
1 note
·
View note
Text
Eve-Ng Sd-Wan Lab Set-Up And Objectives
Eve-Ng is an open virtualization file for the virtual machine that can be also directly installed on the physical hardware without any virtualization by use of ISO image. Before you step further, you should keep in mind that EVE-NG runs diverse hypervisor. Therefore, it is strongly recommended a physical server dedicated for it without any virtualization software. EVE-NG SD-WAN Lab is required by professionals for strong IT infra and for varied other purpose and processes.
Main objectives are the following:
Sharing of design like option to share labs, configs online with friend or others and general UI improvements - to be able to make 99% of things from UI, CLI will remain of course for advanced users
Clientless – telnet, rdp, vnc over html5 and local client Wireshark capture
Import/export configuration and a lot more
You will also get professional editions with amazing features like dynamic, console porting, no limits, fixing issues for multi-user consoling and talent porting with hot links, interconnection running nodes, ports immediately response, and shut no shut with Ethernet only options. The objectives are far more like HTML desktop console to eve management, clientless eve management, and closing features to run lab placing it to running folder along with option run more than one lab simultaneously. There is a lot more provided like multiuser support, administrator role only, and Eve user account access time limitation.
Lab timer for self-training, multi configurations for single lab, integrated wireshark capture using docker, NAT Cloud, Integrated Cloud Option with DHCPP on the eve are some other options that will surely keep you engaged. You can also try eve ng online lab with amazing features.
For CISCO SD-WAN Lab, you need to focus on the following requirements:
You need x16 vCPU, 28GB RAMImages used in labs
i86bi_LinuxL3-AdvEnterpriseK9-M2_157_3_May_2018.bin
csr1000vng-ucmk9.16.12.4a-sdwan
Cisco Viptela SDWAN 18.4.4, vManage, vBond, vEdge, vSmart
Windows Server 2012×64
EVE-NG Docker- eve-gui-server
EVE-NG Docker - wireshark
VPCS host device
Apart from this, the most crucial thing is to pay attention on the key steps to start EVE-NG SD-WAN Lab. The first and most crucial step is to ensure your lab has set proper images version for all nodes. You need to use side bar along with More Actions, Wipe All saved NVRAM. Follow the steps for Side Bar and more actions with start all points Side Bar and Lab Tasks or Workbook is the another vital step to start a lab.
You have to follow the steps and get precise solutions from experts.
0 notes