#what is domain name system in computer network
Explore tagged Tumblr posts
Text
I’m sorry but I’m still losing my fucking MIND over elons incomprehensible Linux own the libs tweet like
Like it’s incredibly obvious he heard about a traceroute, and then googled “how to delete file in Linux” and then didn’t even read the results
Like… woke_mind_virus isn’t a fully qualified domain name, meaning it relies on a custom DNS resolution specific to his machine, or if utilizing a vpn, that specific vpn’s custom host file. Or that the American government would have a host entry for a woke mind virus, which if you’ve ever had to use a government website, is laughable. Also DNS is global for the most part, but honestly we can move on at this point.
So sure, we’ll say that the government has forced all public internet in America to resolve woke_mind_virus. Where does it resolve to? YOUR OWN COMPUTER, you silly billy! Obviously! This is *almost* comprehensible. Sure, we are all infected with the woke mind virus, why not. It must be destroyed within ourselves. Yeah man, whatever. Why not? So how do we destroy it?
Duh! Just delete it! How do we do that in our L337 uber hax0r terminal on our fresh kali live usb (because partitions are scary)? We’ll save that for last.
Because while deleting one file could make a website inoperable, it does not remove every trace of it! It first needs a configuration file in the web server, usually Apache or nginx. This is at LEAST one file, but cmon, if you’re gonna psychologically program the masses and keep it out of public view, you gotta encrypt that shit! So naturally, an SSL is in order! That’s easily 1-3 more files. woke_mind_virus can get a pass on not being fully qualified in this specific case because certs can theoretically be self signed and trusted on local networks, but he wouldn’t be able to tell you that. If you stood up a little one page html site on a web server on your own computer, and navigated to it on port 443 (https://) you would get an SSL error, even though it’s on your own machine. I feel like I’ve beaten this into the ground enough, but just understand it’s stupid.
What’s important to note here is that these BARE MINIMUM files are what routes the request from your machine to the destination site, even if it’s your own computer. If you delete the contents of the site (also called the docroot), the site still exists, and can receive and route requests to and from it, it’s just empty. You’ll probably get a 404 because there’s no actual content to serve. This woke mind princess is in another castle.
It’s also imprudent to delete these configuration files first, because that’s how you determine where the site content actually is! These files dictate what directory (folder for you windows losers) is called upon to actually serve you the content you see displayed when you open a webpage. So you need this information if you don’t want to destroy the entire file system and only want to remove the woke_mind_virus site. Cmon Elon, this is baby shit.
So of course, the strat with the most Efficiency and preserving the rest of the system (which seems to be the point of the tweet) is to find the docroot, delete the docroot, and then delete the web server config files. So how do we delete them?
And here we have it: rm -rf
The syntax is as follows:
rm -rf </path/to/file>
Even if you don’t know shit about Linux, you can probably see the problem here. It’s just so blatantly incorrect, it’s almost as if he’s never done it before.
For those that want to see a real world example, here is me creating a file called woke_mind_virus in my home directory and then trying to delete it the Elon Way:
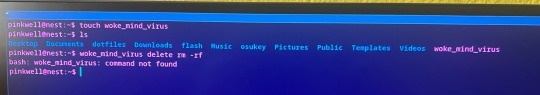
3 notes
·
View notes
Text
The Benefits of Cloud Hosting for Small Business
In the past, hosting websites and apps just required paying a digital platform provider to rent out a single server or computing cluster. Services for web hosting have existed for as long as the internet. Over the past ten years, cloud hosting where the website or application resides on virtual servers dispersed across the cloud has emerged as a popular way to make digital assets accessible online.
A worldwide content delivery network can be connected to by Google Cloud to provide customers with optimal speed and minimal latency when serving material, or a domain can be registered and managed. Google Cloud also provides a range of hosting options for websites and applications.

What is cloud hosting?
Your data is stored on several servers rather than on a single server, which is what is meant by the term "cloud hosting." The term "cloud" refers to this network of several servers that collaborate to form the network. Cloud hosting services are currently being utilized by a multitude of businesses, both large and small. An investment of this kind is definitely worth the rewards, and it has the potential to achieve great things for your company.
You will have a single platform from which you can manage all of your applications and databases, which will allow you to streamline your operations. The productivity of your firm can also be improved by making an investment in cloud infrastructure resources. The various advantages of cloud hosting will be discussed in further depth in the following paragraphs.
Cloud hosting’s Significance for Small Businesses-
Adopting cloud computing has becoming increasingly important for small organizations. It helps small businesses to avoid the high initial investment and ongoing maintenance costs of having internal IT infrastructure. Small businesses can now access advanced technologies and capabilities that were previously exclusive to large organizations by utilizing the cloud.
What are the applications of cloud computing?
Although you might not be aware of it, there is a good chance that you are currently utilizing cloud computing. Whether you use an online service such as Gmail or Outlook 365 to send an email, collaborate on a document, save data, or stream a video, cloud computing makes it feasible behind the scenes to do all of these things.
Cloud Hosting:
Cloud hosting services make it possible to share a variety of information, such as using email services, hosting applications, using web-based phone systems, and storing data. Hosting your company's website, managing databases, and storing domain names are all things that may be done with a cloud hosting service. The fact that cloud hosting services are located offsite makes it simple to scale up in order to handle peak loads.
Backup services:
Backup services in the cloud are failsafe solutions that can be utilized in the event that your company suffers a server disaster, cyberattack, or other type of data loss. Storage, data synchronization and restoration, real-time backups, archiving, and a high level of security are all features that are included in the top cloud backup services. A great number of cloud storage firms now offer cloud backup and storage capabilities.
Storage in the cloud:
Cloud services guarantee that your data is stored in a cloud storage system that is located offsite, making it more convenient to access from any device or place that is linked to the internet. In cloud storage, you are able to securely exchange information with others and synchronize files across several devices. Companies such as Dropbox, Microsoft OneDrive, and Google Drive are examples of well-known cloud storage services.
Software as a service
Software as a service, also known as SaaS, is a solution for the distribution of applications that is hosted in the computer's cloud. SaaS solutions can be utilized by businesses in a variety of operational domains. For instance, you may adopt software for customer relationship management (CRM) that is hosted on the cloud, such as Salesforce, for the purpose of managing sales, accounting software, such as QuickBooks Online, for managing finances, and email marketing software for improving marketing communications.
Cloud Solutions' Advantages for Small Businesses-
Affordable
Small firms can minimize their expenditures on hardware, software licenses, and information technology by switching to cloud-based services, which results in cost savings. Companies that provide cloud computing services often provide a pay-as-you-go approach, which enables organizations to only pay for the resources and services that they actually employ.
Protection of Sensitive Information and Disaster Recovery
Cloud service companies adopt stringent security procedures to protect vulnerable information. In addition to this, they provide solutions for disaster recovery and automatic backups, which serves to ensure that vital corporate information is safeguarded, quickly recoverable, and less likely to be lost.
Scalability:
Cloud hosting solutions enable small businesses to swiftly scale their operations up or down as needed without the inconvenience and expense of physically upgrading their gear and software. Scalability includes the ability to scale up or down activities. This flexibility enables adaptability and growth prospects, both of which are essential in a market that is very competitive.
Advantage in the Market
Cloud hosting solutions give small firms the ability to compete on an equal playing field with larger organizations, which gives them a competitive advantage. It is possible for them to obtain insights, streamline operations, and make decisions based on data without breaking the bank by utilizing sophisticated software, analytics tools, and advanced information technology.
Flexibility
As a result of the fact that all that is required to access the cloud is an internet connection, one of the advantages of cloud hosting is that it provides direct remote access to the data that is pertinent to all of your employees, including yourself. If you run a small business, it's possible that you don't have the financial resources to purchase a dedicated office space. People are able to work from any location they choose thanks to this cloud-based technology. Having the ability to operate from a remote location is more important than ever before for the success of a company, especially in light of the recent epidemic.
Increased Capacity for Collaboration and Adaptability
Cloud solutions enable small businesses to communicate with remote team members, clients, and partners in a seamless manner, which helps improve the flexibility and collaboration capabilities of these firms. It makes it possible to share files in real time, modify them simultaneously, and gain access to the most recent versions of documents, all of which contribute to increased productivity and efficiency.
The Most Recent Technology
Cloud hosting eliminates the need for you to worry about the possibility of automatically upgrading and customizing your servers, in contrast to traditional hosting, which does not permit such activities. Scalability is something that may be easily achieved as your company expands and your requirements and preferences shift.
Because cloud hosting businesses are experts in this kind of technology, this is something that can be easily accomplished. Since they have access to more resources, they are able to undertake research and construct systems that are more robust and powerful. You will have access to the most cutting-edge technologies available if you make an investment in cloud infrastructure.
Very little to no upkeep is required
Recall what I mentioned earlier regarding the safety concerns associated with cloud computing. That being said, a portion of that security necessitates the routine maintenance of servers, the updating of software, and the administration of networks. The good news is that cloud computing relieves you of the responsibility of doing all of that upkeep and instead places it in the hands of skilled specialists.
Because none of the equipment is hosted by you, you do not need to be concerned about purchasing newer versions of it every three to four years. You are not required to deal with any of that maintenance, which frees up more time for your firm to concentrate on the product or service that it offers.
Remote access
When it comes to cloud computing, your email account is the ideal illustration. Providing that you have your login credentials and an internet connection, you are able to access your consolidated email account from any computer. Cloud computing is appealing to a majority of businesses because of the convenience it provides. Your colleagues and you will be able to access your work from any location in the globe thanks to the cloud, which eliminates the need to store your work on a desktop computer or on a local area network (LAN) server that is not linked to the internet. Your productivity and freedom in your workspace will both increase as a result of this remote access.
Conclusion-
Through the simplification of procedures and the facilitation of real-time collaboration among members of a team, cloud computing has the potential to boost both efficiency and productivity. It is possible for teams to collaborate effectively regardless of their geographical location or the time zone differences between them if they have shared access to documents and files. In addition, many cloud-based services provide automation technologies that reduce the amount of manual work that employees have to perform, such as data entry or report production. This allows employees to concentrate on high-value tasks that contribute to the success of the company.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
3 notes
·
View notes
Text
Snippet from my untitled Blue Beetle & Teen Titans rejects fic :)
Click. Snap. Click. Snap.
They're sat inside a Big Belly Burger, waiting for their order of fries. A female singer he doesn't recognise croons Spanglish over weirdly retro beats on the speakers. Eddie is fidgeting with the catch on his now-useless slider phone, out of nerves or boredom, he doesn't know.
The first thing they did once they got into town was to buy a mobile phone. It's strange, but there aren't many payphones around, and whatever happened to them while they were in the Bleed and subsequently in their fall back to Earth must have fried their cellphones. Luckily, he found one of those rundown stores selling spare electronics for cheap that accepts cash and doesn't ask questions. At least one thing hasn't changed.
Click. Snap. Click. Snap.
The phone they bought is a palm-sized thing with a wide touch-screen, one of those smart-phone models that only came out last year, and yet the store owner seemed almost happy to part with it. "It's ancient," he'd said in a comfortingly thick accent, "I was about to chuck it out with the garbage. I'd sell it to you for free, chiquito." Things only get stranger from there. It took less than a minute for Khaji to jail break the phone and recalibrate itself to the local network. They tried his family's numbers again, even tried the Titans Tower secure line, but no dice. What Jaime found on the internet was even less reassuring.
Click. Snap. Click. Snap.
"Hey, Eddie."
The fidgeting stops.
"Could you go grab us some drinks? I need a minute alone with the scarab."
"Sure...?" Eddie throws another glance at Jaime, not quite hiding his worry as he slides out of his seat.
[ You were vexed by his opening and shutting of his phone case. ]
"I didn't realise it was state the obvious hour."
Khaji Da does not respond. Jaime rubs his temple.
"Sorry, sorry. Yes, I'm stressed. Tell me you have some good news, at least."
[ You are still alive, as is Eddie Bloomberg. You have enough money to acquire sustenance for another week, during which I can help you find a job and — ]
"Khaji. I need to get home."
[ You are technically in your hometown. ]
"But it's not the El Paso I know. Right? Tell me I'm not crazy."
[ Jaime Reyes is correct. Based on our quick search of the government domains, social network platforms and news sites, the Reyes family never lived in El Paso. There is no record of your parents or extended family in the state registry. Your name does not exist in the class registers of your high school. Your sister— ]
"Also doesn't exist! I know! I got it the first time." Jaime looks over to the self-service machine. What is taking Eddie so long? "I asked you for good news, Khaji."
[ Actually, your sister exists. Milagro Reyes, age 18, enrolled in Edge Keys High School. According to her posts on Instagram, she was last seen at the Kord Centre Mall — ]
"Did you say eighteen? And where the heck is Edge Key?"
[ I have some more good news. While there is no record of your other family members in the state of Texas, a Reyes Auto Repair Shop was recently removed from the business registry in Edge Key, Greater Palmera City. ]
"What? We have to go to Edge Key!"
"What's Edge Key?" Eddie sets a tray down, almost spilling the two extra-large cups of soda balanced precariously on it. The fries look tiny in comparison.
"That's what I'm trying to find out. Khaji, can you — hold on, I'm syncing you to the phone so Eddie can see."
The phone lights up, and Jaime expects Khaji's words to crawl across the screen like text messages the way he's done the few times Jaime tried to sync the scarab to his old phone via blue-tooth. Instead, the phone starts talking in a lady computer voice.
"Your scarab was a chick this whole time?" Eddie exclaims, the half-chewed fry in his hand forgotten.
"What? No! I didn't even know it could speak like this."
"I simply utilised this phone's built-in text-to-speech system. It is not my problem that the manufacturers could only imagine AI voices as female."
"I think it just insulted every super-computer in the cape community..."
"Anyway, the coordinates?"
[ There is one last thing you should know before you go, Jaime Reyes. The Blue Beetle was last sighted in Palmera City six hours ago. ]
The boys pause and look at each other.
"Show me, Khaji."
And on the screen of the phone appears a crisp, 4K picture of a guy in a costume that looks exactly like him, mid-flight in the streets of a city he's never been to.
#jaime reyes#eddie bloomberg#teen titans#blue beetle#kid devil#I typed 3 chapters of this au for 3 hours straight and now my hand is fucked :')#I still have shit to prep for tomorrow but I'm ok. I'M OKAY#stvlti writes
18 notes
·
View notes
Text
How to Begin Your Web Design Journey: A Step-by-Step Guide in Simple Terms
Understanding the Basics:
Learn about HTML, which is like a web page’s skeleton.
Understand CSS, which is like makeup for web pages.
Know how to make websites look good on different screens.
2. Choose your tools:
Start with simple text editors like Notepad (for Windows) or TextEdit (for Mac).
Later, try fancier editors like Visual Studio Code.
For making pictures, try Adobe Photoshop or Illustrator.
3. Learn HTML and CSS:
Use websites like W3Schools or Codecademy.
If you want to learn more about web design with certification and placement, ACTE Institute offers comprehensive machine learning training courses that can give you the knowledge and skills necessary to excel in this field. Consider the infinite possibilities for data analysis, automation, and decision-making that machine learning may create.
YouTube: There are many video tutorials covering HTML and CSS for beginners.
They teach you how to make web pages and make them look nice.
You can also learn from courses on Coursera or edX.
4. Practice your skills.
Besides learning, make simple web pages to get better.
Try harder projects as you get more confident.
Make your own website to practice lots.
5. Responsive Web Design:
Make sure your websites work well on phones and computers.
Learn about media queries (they help your design fit different screens).
6. Master CSS Layouts:
Get really good at arranging web stuff using CSS (like making boxes and arranging them nicely).
7. Web Design Frameworks:
Think about using ready-made kits like Bootstrap.
They have pre-made pieces to help you design faster.
8. UI/UX Design:
Learn to make websites easy to use and nice to look at.
Think about how people will use your site.
9. Web Hosting and Domain:
To show your website to people, you need a place to put it (hosting) and a name for it (domain).
Lots of companies can help with this, like Bluehost or HostGator.
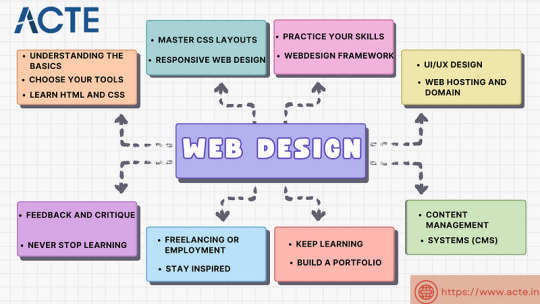
10. Content Management Systems (CMS):
Consider using tools like WordPress to manage your website easily.
11. Keep Learning:
Web design keeps changing, so keep learning new stuff.
Read blogs, watch webinars, and take more advanced classes.
12. Build a portfolio.
Make a collection of your best work to show others.
People who might hire you want to see what you can do.
13. Freelancing or employment:
Decide if you want to work alone or with a company.
Both ways have good things and not-so-good things, so pick what you like.
14. Networking:
Join groups of web designers to meet others like you.
Learning from others can help you become better.
15. Feedback and criticism:
Don’t be shy to ask for advice on your work.
When people give you tips, it helps you improve.
16. Launch your projects:
When you’re good enough, work on real websites.
Offer to make websites for friends or local businesses.
17. Stay Inspired:
Be creative and get ideas from different places.
Nature, art, and other designers can help you think of cool stuff.
18. Never Stop Learning:
Web design always changes, so keep learning new things.
Stay curious and open to learning more tricks and tools.
The secret to success in web design is to start with the fundamentals and gradually advance your abilities. Keep in mind that on this trip, patience and practice are the keys to success. As your skills advance, you’ll have the imagination needed to realise your ideas for websites. So put your hands in your pockets, launch your preferred coding editor, and start your web design experience!
4 notes
·
View notes
Text
Unlocking the Power of Image Datasets: The Foundation of AI and Computer Vision

Introduction
In the slowly changing world of artificial intelligence, image datasets form the very backbone of progress. Whatever the application-whether facial recognition, autonomous vehicles, medical diagnostics, or retail analytics-the proper training of machine-learning models that support the systems being derived to put the theories of AI into practice depends upon the marked amounts of reference images. An AI production house must provide proper image datasets; their quality, juxtaposition, and scalability define how far they can go in actualizing artificial intelligent systems successfully. At GTS.AI, we are engaged in establishing domain-based specific image datasets targeted mainly for artificial intelligence and machine learning. Our expertise allows us to deliver the utmost quality and diversification within a dataset, so companies build a strong foundation for success in AI development.
What Are Image Datasets?
An image dataset contains a collective mass of images, often including other metadata, annotation, and classification tags. AI disappears from a multitude of patterns, objects, or features from example images labeled as such and learns from a plethora of instances. These could be extensive, ranging from a hundred to several million, respectively.
Types of Image Datasets
Labeled or unlabeled datasets: Labeled datasets differ from unlabeled datasets because they contain annotations concerning various aspects about the classes such as name, bounding box, mask, or key points. A few of these are the ImageNet, COCO, or Open Images dataset. The unlabeled datasets are raw images without extraneous metadata. These are essential for aiding unsupervised networks and self-supervised-training techniques.
Synthetic vs. Real-World Datasets: Where synthetic datasets are artificially produced images designed to mimic real-world data, they come in handy when it comes to data collection because they render the same easy to use for many cases for good reasons. Real-world datasets are images collected from real environments, and their use comes with significant need for cleaning and annotating them to effectively use them for effective AI training.
Domain-Specific Datasets: Some datasets focus on specific industries, among them are medical imaging (ChestX-ray14, LIDC-IDRI), autonomous driving (Waymo Open Dataset, BDD100K), and satellite imagery (SpaceNet, xView).
Why Are Image Datasets Important in AI Development?
Model Training and Accuracy: AI models learn all they have to know about how to detect, classify, and segment images from image datasets by deep learning algorithm techniques. Datasets contribute to the accuracy of the AI model.
Bias Prevention and Diversity: A well-compiled image dataset will contain multiple diverse data points, helping prevent biases in AI models. AI models may develop skewed predictions if a dataset has a lack of diversity in terms of gender, ethnicity, lighting conditions, or perspectives. At GTS.AI, we prioritize diversity in dataset collection to secure fair and inclusive AI.
Scaled and Customized Data Understanding: AI-made goods, namely healthcare and security as well as retail and autonomous vehicles, require customized datasets to undertake such functions. Another GTS.AI advantage is its scalable and industry-tailored datasets, ensuring AI system gets just what data it requires.
Quality of Data and Annotation: Some datasets have nothing but poorly annotated or low-quality images. Such cases lead to AI predictions of poor quality. Robust models must train against high-quality image annotations: bounding boxes, semantic segmentation, or key point detection.
Challenges in Dataset Collection and Management
Awkward but yet significant, image dataset management presents its sets of issues.
Data Collection & Privacy: While obtaining high-quality images, obtaining a dataset that adheres to a legislative measure such as GDPR and CCPA is difficult. At GTS.AI, we believe in ethical data sourcing, being an important pillar where we abide with world data regulations.
Annotation Complexity: Manually labor-intensive and cost-optimizing large datasets is not quick. Advanced annotation tools and AI-supported labeling techniques automate this process. GTS.AI provides best-in-kind annotation services, decreasing manual effort and increasing efficiency.
Storage & Processing Costs: Large datasets require heavy storage and computational power to train the AI models. The existing limitation can be solved with a cloud solution and optimized data pipelines.
How GTS.AI Revolutionizes Image Dataset Creation
We give start-to-end solutions for image dataset collection to annotation and management at GTS.AI. The services we provide can be: Custom Image Dataset Collection, we source high-quality images from different domains tuned to particular AI targets. Advanced Annotation Services, which may include bounding boxes and instance segmentation to provide thoroughly accurate labeling for the AI training process. Scalable and Diverse Datasets, that is optimized in their respective industries so that minimal bias and maximum generalization are contained. Privacy-compliant data sourcing is obtained through ethical and legally compliant provision of data.
Conclusion
The quality of a training dataset set will deeply define the performance of its AI-driven application. Here, GTS.AI builds the values by delivering high-quality domains-specific image datasets to bring exceptional performance across different industries. Whether your target is to develop an AI model for medical diagnostics, retail analytics, or self-driving photography, the right image dataset is highly needed for success. GTS.AI partners to being more intelligent and reliable in AI solutions. Engage with us in connection with our image dataset solutions today at GTS.AI.
0 notes
Text
The Core of Crypto Is Punks and Principles

dyne.org
The Core of Crypto Is Punks and Principles
Feb 25, 2023 8 min read
How Privacy-focused Intellectuals Laid the Foundations For Web3
Over the last 15 years, the web has come to be dominated by a handful of powerful players. To access and use their proprietary platforms, we gradually give up our privacy, lose control of our data, and become vulnerable to censorship and manipulation. We did not fare much better with the global financial system. Money is managed non-transparently, for the benefit of a few and to the detriment of many, leading to a vicious concentration of power which often overrides nation-states’ agendas and ecosystems’ well-being.
These are some of the reasons computer scientists, mathematicians, and social-tech activists have combined different technologies — such as cryptography, peer-to-peer networks, and digital currencies — to reimagine the way we relate and exchange value in the digital world. After decades of research and development these innovators have provided us with the tools to tackle harmful centralisation and enact meaningful course corrections. The amalgamation of these tools is currently identified as ‘web3’, and presents an open invitation to enhance the way the internet and financial systems are designed and used.
The term ‘crypto’ is often used interchangeably with web3, although web3 is broader than cryptocurrencies. Crypto is a huge space, an ungovernable commons whose only barrier to entry is that it is not easy to navigate. To understand its real potential, to make conscious adoption and effective use of it, we should realise where it comes from and the essential values upon which it has been developed.
“Too often, the people disrupting any industry don’t understand deeply what they are disrupting. This is definitely the case with cryptocurrencies and the current financial system. It really is well worth your time to stop and become familiar with more history so that you can understand why we are where we are, what led us here, and — only then — what solutions might actually benefit you and those you care about.” Andy Tudhope (Kernel)
The Cypherpunks and Precursors to Bitcoin (1980–2005)
As Haseeb Qureshi’s article on the cypherpunks notes, the internet of the early 1990s was a desolate domain, populated mainly by hackers and nerds. The cypherpunks’ foresight lay in understanding how, once inhabited, profound changes in our economic and social systems would occur, with a harmful concentration of power by a few. To be ready for that moment and ensure internet freedom, they started a mailing list to talk and develop cryptographically secure digital infrastructure.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place… The technologies of the past did not allow for strong privacy, but electronic technologies do.” E. Hughes, “A Cypherpunk’s Manifesto”
Some of the individuals on that mailing list are names you may have heard before:
Jacob Appelbaum, Tor developer
Julian Assange, founder of WikiLeaks
Adam Back, inventor of Hashcash
Bram Cohen, creator of BitTorrent
Nick Szabo, designer of BitGold
Wei Dai, designer of B-money
Hal Finney, creator of Reusable Proof of Work
John Gilmore, founder of the Electronic Frontier Foundation
Eric Huges, founding member of the Cypherpunks movement
Timothy May, chief scientist at Intel, and author of A Crypto Anarchist Manifesto.
“The words of anti-establishment intellectuals sow the seeds for revolution. They present ideas and sometimes discredit the establishment, paving the way for a charismatic leader to package their thinking into a movement.” Tony Sheng
Bitcoin: The Revolution of Trust (2009)
With the global financial meltdown in 2008, trust in the banking system was under strain, and cypherpunk skepticism was once again justified. After many years of socio-political commitments and technological breakthroughs, there were enough developments for Satoshi Nakamoto to combine into a working protocol. In January 2009, the Bitcoin network launched as an alternative to the opaque and fallacious logic of the then-current financial system.
“The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.” Satoshi Nakamoto
As Yuval Noah Harari wrote in his 2014 book, Sapiens, more than 90% of the entire world’s money exists only on computer servers, making it a “de facto” digital currency. Therefore, Bitcoin’s disruptive value proposition is not the invention of digital currency, but its methodology in guaranteeing the trustworthiness of digital currency. Leveraging advanced cryptography and blockchain technology, Bitcoin indeed enables a network of peers to create and maintain a functional money system without the need for trusted intermediaries, laws, and governments.
This is why it is not only a technological revolution but also, above all, a socio-political one: there is no longer a single entity able to decide upon the validity of supply and transaction history, but an entire community.
Hoards of people in shackles and broken clothes standing up all saying "I am Satoshi Nakamoto!"
We Are All Satoshi
To grow and succeed, the project needs the voluntary commitment of its participants, who are mathematically incentivized to sustain the network for the benefit of both others and themselves. This is what Bitcoin is about: a decentralised payment system with a distributed incentive structure that we collectively engineer and freely opt into.
“For the first time in history, we need not revolt against a system of violent legal enforcement. We can abandon it for openly verifiable mathematics, which we subscribe to by acts of our own volition. This is because, in the world wide web, running code is more powerful than holding elections.” Kernel
Ethereum: The Collaborative World Computer (2013)
In working with and writing about blockchain and Bitcoin for a while, the young programmer Vitalik Buterin realised that cypherpunk ideals of privacy, financial freedom, and open-source development could extend to many other applications beyond money. Following his vision, along with a small group of programmers, he launched Ethereum: a peer-to-peer network and community-operated blockchain to codify, secure, and trade just about anything.
To make a quick comparison between Bitcoin and Ethereum:
Bitcoin is a payment network that can be used to transfer value between two people anywhere in the world without intermediaries.
Ethereum is an open-source platform and base-layer infrastructure that enables anyone to write smart contracts and decentralised applications.
Imagine Ethereum as a diverse ecosystem of individuals and organisations that build and grow alongside a protocol designed to facilitate human coordination and play infinite games. No single individual or entity has made it what it is today, rather it is a collective that has organically evolved the ecosystem to become more vibrant and diverse.
Thanks to its decentralised nature, open-source standards, and interoperability, Ethereum benefited from a great deal of bottom-up innovation and active participation. This led to rapid growth and has made it the most widely used blockchain for building and playing around with DeFi, NFTs, and DAOs.
“Ethereum is an organisational “dark matter” that can coordinate galaxies of people, and it has the ability to create new Schelling points anchored in shared, tokenized stories.” Simon de la Rouviere
Web3: The Trustless Web
What brought us to web3 was decades of research and development by people who cared about making the internet more equitable, open, and decentralised. Crypto was born out of shared values and principles, rather than from desires of conquest, money, and power. To date, many of the revolutionary promises it has made are still under development, making it an easy target for the disillusioned, the cynics, and the pessimists. It must be acknowledged, however, that many steps have been taken so far.
Over the last few decades, a growing number of people began engineering and using new composable primitives for permissionless value exchange. Many discovered the power of collaboration and community and started exploring new organisational structures with inclusive governance mechanisms. Professionals, users, and third parties voluntarily contributed to add value to different projects and the reward was then shared amongst them instead of only accruing to founders or financiers.
With public blockchains, we could now make institutions transparent. Moreover, by becoming a digital asset, money, stocks, bonds, IDs, and real estate can engage with smart contracts to become programmable, and therefore be managed in more unequivocal and efficient ways.
If you are in the U.S., the UK, or Singapore, crypto might be a fun way to speculate on meme coins and NFTs. However, if you are in Nigeria, Argentina, or Afghanistan, it represents a means for survival and dissent amid corruption and censorship.
"Crypto is currently the only solution that combines the benefits of digitalisation with cash-like respect for personal privacy." Vitalik Buterin
It should come as no surprise, then, that the countries with the highest adoption rates are those where cryptocurrencies are used as originally intended: for confronting tyranny and ensuring financial freedom. In other words, to rethink a global political economy and to make it more public and accessible.
To date, the parts of the crypto space that are honourable are those that actually stay true to its core principles of decentralisation, privacy, openness, and transparency. Everything else is just old vicious cycles running on blockchain rails.
As with any significant innovation, there is no shortage of challenges to overcome, and very little is truly decentralised yet. However, having a negative, belittling, or passive approach will not improve our present condition. If we care about the future to which we are contributing, we should understand the societal implications of our involvement in the crypto space.
Instead of doing the easy thing or the one that pays apparently more, now is the time to realise that we have the agency to reimagine the digital realm as a place where the people, more than corporations or governments, are the protagonists. The degree of imagination and change will only depend on how hard we care and commit.
“People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one’s fellows in society… We cannot expect governments, corporations, or other large, faceless organisations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak.” E. Hughes, “A Cypherpunk’s Manifesto”
0 notes
Text
Geek Out! The Best AI Certifications for Tech Enthusiasts in 2025
The tech industry is witnessing an unprecedented transformation, thanks to the relentless advancements in artificial intelligence (AI). Whether it’s robotics, machine learning, or quantum computing, AI has become the cornerstone of innovation. For tech enthusiasts looking to elevate their skills and stay ahead of the curve, AI certifications are the gateway to expertise and career growth.
This article explores the top AI certifications for 2025, including courses designed for beginners, advanced practitioners, and those passionate about niche AI applications. We’ll also highlight the AI+ Robotics™ certification by AI Certs, along with other industry-leading programs, to help you find the perfect fit for your tech journey.
Why AI Certifications Matter for Tech Enthusiasts
AI certifications are more than just credentials; they are a way to:
Expand Expertise: Dive deep into the latest AI technologies and methodologies.
Boost Career Opportunities: Certifications demonstrate your commitment and proficiency, making you a top choice for employers.
Stay Current: The tech industry evolves rapidly, and certifications help you keep pace with the latest trends and tools.

The Best AI Certifications for 2025
1. AI+ Robotics™ by AI Certs
Designed specifically for tech enthusiasts, the AI+ Robotics™ certification by AI Certs bridges the gap between AI theory and its practical applications in robotics.
Key Features:
Comprehensive coverage of AI-driven robotics, including sensor integration, autonomous systems, and human-robot interaction.
Hands-on projects that allow learners to build and program AI-powered robots.
Focus on ethical considerations in robotics, ensuring responsible innovation.
Why Choose AI+ Robotics™: This course is perfect for those passionate about exploring the intersection of AI and robotics, whether for personal projects or professional growth.
Use the coupon code NEWCOURSE25 to get 25% OFF on AI CERTS’ certifications. Don’t miss out on this limited-time offer! Visit this link to explore the courses and enroll today.
2. DeepLearning.AI Professional Certificate in Machine Learning and AI
Created by AI pioneer Andrew Ng, this certification offers an in-depth exploration of machine learning and AI fundamentals.
Key Features:
Modules on neural networks, deep learning, and natural language processing (NLP).
Real-world projects to solidify theoretical knowledge.
Community support for collaborative learning.
Why Choose DeepLearning.AI: This certification is ideal for tech enthusiasts who want to master the foundational concepts of AI and apply them to various domains.
3. Certified AI Professional by IBM
IBM’s Certified AI Professional program is tailored for tech enthusiasts aiming to specialize in enterprise-grade AI solutions.
Key Features:
Training on AI model development and deployment using IBM Watson.
Emphasis on data science and AI integration for business applications.
Access to IBM’s tools and platforms for hands-on learning.
Why Choose IBM Certified AI Professional: This program is a great choice for tech enthusiasts interested in applying AI to solve complex real-world challenges, particularly in business and enterprise settings.
What Makes These Certifications Stand Out?
Practical Learning: All three certifications emphasize hands-on projects, ensuring you gain practical experience.
Industry Recognition: These programs are offered by trusted names in AI education, adding credibility to your skillset.
Diverse Applications: From robotics to business AI, these certifications cater to various interests and career goals.
Exploring Career Opportunities
AI certifications open doors to exciting roles across industries:
AI Engineer: Design and develop AI solutions for tech companies.
Robotics Specialist: Work on autonomous systems for industries like healthcare and manufacturing.
Data Scientist: Analyze complex datasets to derive actionable insights.
AI Researcher: Contribute to groundbreaking advancements in AI technologies.
With AI certifications, tech enthusiasts can align their passions with lucrative career paths, all while contributing to innovative solutions that shape the future.
How to Choose the Right Certification
Define Your Interests: Are you passionate about robotics, machine learning, or enterprise AI? Pick a certification that aligns with your interests.
Consider Your Skill Level: For beginners, foundational courses like DeepLearning.AI are a great starting point. Advanced learners might prefer specialized programs like AI+ Robotics™.
Check for Hands-On Learning: Certifications with practical projects are more valuable, as they enable you to apply your skills in real-world scenarios.
Assess Industry Demand: Research job trends to identify certifications that align with in-demand skills.
The Future of AI Certifications
As AI continues to evolve, certifications will adapt to cover emerging areas such as:
Quantum AI: Combining AI with quantum computing for unprecedented processing power.
Ethical AI: Addressing biases, privacy concerns, and accountability in AI systems.
Generative AI: Exploring applications of AI in creative fields like art and design.

Final Thoughts
For tech enthusiasts, 2025 offers unparalleled opportunities to geek out on AI and transform passion into expertise. Certifications like AI+ Robotics™ by AI Certs, DeepLearning.AI Professional Certificate, and IBM Certified AI Professional provide the perfect blend of knowledge, practical experience, and industry recognition.
By earning these certifications, you’ll not only stay ahead in the tech world but also contribute to meaningful innovations that shape our future. Whether you’re building AI-powered robots, designing machine learning models, or creating enterprise AI solutions, the right certification can propel your career to new heights.
So, why wait? Choose the certification that resonates with your goals, and start your journey toward becoming a leader in the AI revolution.
0 notes
Text
A Comprehensive Guide to Amazon Web Services (AWS)
Amazon Web Services (AWS) has emerged as a leading cloud computing platform, revolutionizing how businesses and developers deploy and manage applications. Since its inception in 2006, AWS has expanded its offerings to include a vast array of services, catering to various industries and use cases. This guide will help you understand what AWS is, its key features, and how it can benefit your organization.

If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.
What is AWS?
AWS is a cloud services platform provided by Amazon that enables businesses to access computing power, storage, and various other functionalities via the internet. Rather than investing in physical hardware and infrastructure, organizations can utilize AWS to streamline operations and reduce costs.
Core Services Offered by AWS
AWS provides a wide range of services, but some of the most notable include:
Compute Services: Amazon EC2 (Elastic Compute Cloud) offers scalable virtual servers, while AWS Lambda enables serverless computing, allowing developers to run code without provisioning servers.
Storage Solutions: Amazon S3 (Simple Storage Service) provides scalable object storage for data, while Amazon EBS (Elastic Block Store) offers block storage for use with EC2 instances.
Database Services: AWS supports various database solutions, including Amazon RDS (Relational Database Service) for relational databases and Amazon DynamoDB for NoSQL databases.
Networking: AWS offers services like Amazon VPC (Virtual Private Cloud) for creating isolated networks and Amazon Route 53 for domain name system management.
Machine Learning: With services like Amazon SageMaker, developers can build, train, and deploy machine learning models efficiently.
Key Features of AWS
Scalability: AWS allows users to scale resources up or down based on demand. This capability is especially beneficial for businesses experiencing fluctuating workloads.
Cost-Effectiveness: With a pay-as-you-go pricing model, AWS enables organizations to only pay for the services they use, helping to optimize budgets.
Global Infrastructure: AWS operates data centers in multiple regions around the globe, providing low-latency access and high availability for users worldwide.
Robust Security: AWS implements a comprehensive security framework that includes data encryption, access controls, and compliance with industry standards, ensuring data protection.

To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Use Cases for AWS
Web Hosting: Many companies host their websites and applications on AWS, leveraging its scalability and reliability.
Data Analytics: AWS provides tools for big data processing, with services like Amazon EMR (Elastic MapReduce) helping organizations analyze large datasets.
Backup and Recovery: AWS offers robust solutions for data backup and disaster recovery, ensuring that critical information is secure and accessible.
Internet of Things (IoT): AWS IoT Core connects and manages IoT devices, enabling businesses to harness data generated by these devices.
Conclusion
Amazon Web Services has transformed the IT landscape by offering flexible, scalable, and cost-effective cloud solutions. By leveraging AWS, organizations can enhance their operational efficiency, innovate faster, and reduce the burden of managing physical infrastructure. Whether you're a startup or an established enterprise, AWS provides the tools and resources to thrive in today's digital age.
0 notes
Text
Best Engineering Project Center in Tirunelveli
Excel in Engineering with AB Technologies: The Best Project Center in Tirunelveli
Engineering students constantly strive to stand out in their academic and professional endeavors. At the heart of this ambition lies the need for innovative projects that not only demonstrate technical expertise but also solve real-world challenges. AB Technologies, the best engineering project center in Tirunelveli, offers a platform for aspiring engineers to bring their ideas to life through exceptional project guidance and training.
Why AB Technologies Stands Out
Comprehensive Project Support: AB Technologies specializes in providing end-to-end support for engineering projects across various domains. From ideation and design to implementation and testing, students receive unparalleled guidance every step of the way.
Expert Mentorship: With a team of seasoned professionals and IEEE-certified experts, AB Technologies ensures that students learn from the best. Mentors bring industry-relevant insights and practical knowledge to every project.
Cutting-Edge Technologies: AB Technologies focuses on equipping students with the latest technological tools and frameworks. Whether it’s IoT, artificial intelligence, machine learning, embedded systems, or software development, students work on projects that are at the forefront of innovation.
Customizable Project Options: Every student’s academic requirements and interests are unique. AB Technologies offers a wide array of project options tailored to different engineering disciplines, including electronics, computer science, mechanical, and civil engineering.
High-Quality Resources: The center is equipped with state-of-the-art infrastructure and tools, enabling students to work in a conducive learning environment. Access to advanced hardware and software ensures projects are executed with precision.
What AB Technologies Offers
IEEE Projects: Collaborate on IEEE-certified projects that align with current industry standards. These projects are ideal for students seeking to publish papers or present their work in conferences.
Real-Time Projects: Gain hands-on experience by working on real-time industry problems. Such projects enhance practical skills and prepare students for professional challenges.
Mini and Major Projects: Whether it’s a small-scale academic project or a comprehensive final-year endeavor, AB Technologies supports all levels of project development.
Workshops and Training: Beyond project guidance, the center conducts workshops on trending technologies, ensuring students stay updated with the latest advancements.
Benefits of Choosing AB Technologies
Career Advancement: A well-executed project from AB Technologies significantly enhances students’ resumes, making them stand out to potential employers.
Holistic Learning: Projects at AB Technologies go beyond theoretical knowledge, emphasizing practical implementation and problem-solving skills.
Networking Opportunities: Students connect with peers, industry professionals, and mentors, fostering valuable relationships for future growth.
Recognition and Certification: Successful project completion is recognized with certifications, adding credibility to students’ academic and professional profiles.
Why Tirunelveli Trusts AB Technologies
AB Technologies has established itself as a trusted name in Tirunelveli, owing to its commitment to quality and innovation. The center’s focus on delivering excellence has made it a go-to destination for engineering students seeking to excel in their academic pursuits.
Enroll with AB Technologies Today
AB Technologies is more than just a project center; it’s a launchpad for engineering success. By blending technical expertise, innovative solutions, and unwavering support, the center empowers students to achieve their goals and make a mark in the competitive world of engineering.
Ready to transform your ideas into impactful projects? Visit AB Technologies in Tirunelveli or contact us to learn more about our offerings and secure your spot. Let’s build the future together, one project at a time.
0 notes
Text
Unveiling the features of Kubernetes
In the fast-changing domain of cloud computing and DevOps, Kubernetes has emerged as a revolutionary tool for managing containerized workloads. With businesses shifting away from traditional infrastructure that does not scale, is inefficient, and is not portable, Kubernetes provides the orchestration to deal with all the difficulties faced in deploying, scaling, and maintaining containerized applications. It has become a core element of modern cloud infrastructure, especially when embraced by giants like Google, Microsoft, and Amazon.
This blog will cover Kubernetes's features and how it changes the game regarding the management of containerized workloads.
What is Kubernetes?
Kubernetes, or K8s, is an open-source system for automating the deployment, scaling, and operation of application containers across clusters of hosts. Google created it and donated it to the Cloud Native Computing Foundation (CNCF). It has become the standard for container orchestration.
The essence of Kubernetes, when contrasted with other orchestration tools, is that it addresses critical issues in managing applications in containers in a production environment. Containers are lightweight, portable units that allow applications to be run within isolated environments. It's the problem of scale, life cycle management, availability, and orchestrating interactions between multiple containers where Kubernetes shines.
Key Features of Kubernetes
Automation of Container Orchestration and Deployment
At its core, Kubernetes is an orchestration platform built to manage containerized applications. It automates the deployment of containers across multiple servers to ensure applications run efficiently. Its declarative model calls out what should and should not exist in an application's state; Kubernetes then does what it can to make that state a reality.
For example, if you need precisely five running instances of an application, Kubernetes will run exactly five running containers at any given time. If one of the containers crashed or failed for whatever reason, Kubernetes redeployed a replacement without any action taken by the human. Unless you specifically changed that, Kubernetes will only do that for you after trying a default three times.
2. Scalability with Horizontal Pod Autoscaling (HPA)
One of the most critical factors for running applications in production is that they need to be scaled based on the traffic or resource demands they might be exposed to. Kubernetes allows this easily with Horizontal Pod Autoscaling, which scales the number of pod replicas (containers) running in a Kubernetes deployment based on predefined metrics or custom conditions like CPU usage.
3. Self-Healing Capabilities
The one feature that stands out about Kubernetes is its self-healing capability. Since the environment is dynamic and unpredictable, applications may crash or be erroneous. Kubernetes detects and remedies this problem automatically without human intervention.
Kubernetes self-monitors containers and nodes for health. If a container fails, it restarts or replaces it. If one node becomes unavailable, it redistributes containers to the remaining healthy nodes. This ensures that applications run and are healthy, which is an important aspect of why services need to be available.
4. Load Balancing and Service Discovery
Traditional IT environments require a lot of complexity to set up load balancing and service discovery. But Kubernetes makes this process much easier, as built-in load balancing and service discovery mechanisms are available.
For instance, when containers in a Kubernetes cluster are exposed as services, Kubernetes ensures that network traffic is evenly spread across each service instance (pod). Moreover, it provides the service with a consistent DNS name so that other components can locate it and communicate with it. That means manually configuring won't be necessary; the application can scale up and down dynamically based on a change in workloads.
5. Declarative Configuration with YAML and Helm Charts
Kubernetes resorts to the declarative paradigm to manage infrastructure: you define more of the desired state of your applications using YAML configuration files. These configurations can talk about so many things apart from deployments, services, volumes, and much more.
In addition, Helm charts are often referred to as package managers for Kubernetes. They make the deployment of complex applications really easy. It is possible to pack Kubernetes YAML files into reusable templates, making complex microservices architecture deployment and maintenance much easier. Using Helm, companies can standardize deployments and also increase consistency across different environments.
6. Rolling Updates and Rollbacks
Updates in a distributed system, especially zero-downtime updates, are difficult to manage. The rolling update feature provided by Kubernetes makes this much easier. It does not take down the entire application for an update; instead, it gradually replaces the old version with the new version. So, a part of the system remains on for the entire update.
7.StatefulSets with Persistent Storage
Although containers are stateless by design, most practical applications require some form of persistent storage. Kubernetes supports this by offering persistent volumes that abstract away the underlying infrastructure so that users can attach persistent volumes to their containers. Whether stored in the cloud, NAS, or local disks, Kubernetes gives users a unified way to manage and provision storage for containerized applications.
8. Security and Role-Based Access Control (RBAC)
Any enterprise-grade solution has to be secured. Kubernetes has quite a few solid security features built in, but one of the primary mechanisms is Role-Based Access Control (RBAC), which permits fine-grained control over access to Kubernetes resources.
With RBAC, an organization can define roles and permissions; they need to define which users or services can operate on which resources. This prevents legitimate members from making unauthorized changes in a Kubernetes cluster.
9. Multi-Cloud and Hybrid Cloud Support
Another significant benefit that Kubernetes brings is the support for multi-cloud and hybrid cloud environments. Users can deploy and run their Kubernetes clusters across the leading clouds-AWS, Azure, GCP-and on-premise environments according to their cost, performance, and compliance requirements.
10. Kubernetes Ecosystem and Extensibility
Of course, alongside this, Kubernetes has a large and thriving ecosystem of tools and integrations that extend beyond its capabilities. Now, be it for Prometheus as a monitoring solution, Jenkins for CI/CD pipelines, or Things Under the Sun, Kubernetes fits in everywhere,
thus making it an adaptable platform for developers and operators.
Conclusion
Kubernetes is a game-changer that has not only transformed the containerized workload world but has also provided a robust set of features to break down the complexities of modern cloud-native applications. Its capabilities range from automated deployment and self-healing to efficient scaling and seamless integration with various tools and platforms, making it the go-to solution for organizations looking to modernize their IT infrastructure.
0 notes
Link
#differencebetweenDNSandIPaddress#DNSandIPaddressdifferences#DNSandIPrelationship#DNSvsIPaddressguide#DNSvsIPcomparison#DNSvsIPexplained#DNSvsIPoverview#howDNSdiffersfromIPaddress#IPaddressvsDNSfunctions#understandingDNSandIP
0 notes
Text
Unveiling the features of Kubernetes
In the fast-changing domain of cloud computing and DevOps, Kubernetes has emerged as a revolutionary tool for managing containerized workloads. With businesses shifting away from traditional infrastructure that does not scale, is inefficient, and is not portable, Kubernetes provides the orchestration to deal with all the difficulties faced in deploying, scaling, and maintaining containerized applications. It has become a core element of modern cloud infrastructure, especially when embraced by giants like Google, Microsoft, and Amazon.
This blog will cover Kubernetes's features and how it changes the game regarding the management of containerized workloads.
What is Kubernetes?
Kubernetes, or K8s, is an open-source system for automating the deployment, scaling, and operation of application containers across clusters of hosts. Google created it and donated it to the Cloud Native Computing Foundation (CNCF). It has become the standard for container orchestration.
The essence of Kubernetes, when contrasted with other orchestration tools, is that it addresses critical issues in managing applications in containers in a production environment. Containers are lightweight, portable units that allow applications to be run within isolated environments. It's the problem of scale, life cycle management, availability, and orchestrating interactions between multiple containers where Kubernetes shines.
Key Features of Kubernetes
Automation of Container Orchestration and Deployment
At its core, Kubernetes is an orchestration platform built to manage containerized applications. It automates the deployment of containers across multiple servers to ensure applications run efficiently. Its declarative model calls out what should and should not exist in an application's state; Kubernetes then does what it can to make that state a reality.
For example, if you need precisely five running instances of an application, Kubernetes will run exactly five running containers at any given time. If one of the containers crashed or failed for whatever reason, Kubernetes redeployed a replacement without any action taken by the human. Unless you specifically changed that, Kubernetes will only do that for you after trying a default three times.
2. Scalability with Horizontal Pod Autoscaling (HPA)
One of the most critical factors for running applications in production is that they need to be scaled based on the traffic or resource demands they might be exposed to. Kubernetes allows this easily with Horizontal Pod Autoscaling, which scales the number of pod replicas (containers) running in a Kubernetes deployment based on predefined metrics or custom conditions like CPU usage.
3. Self-Healing Capabilities
The one feature that stands out about Kubernetes is its self-healing capability. Since the environment is dynamic and unpredictable, applications may crash or be erroneous. Kubernetes detects and remedies this problem automatically without human intervention.
Kubernetes self-monitors containers and nodes for health. If a container fails, it restarts or replaces it. If one node becomes unavailable, it redistributes containers to the remaining healthy nodes. This ensures that applications run and are healthy, which is an important aspect of why services need to be available.
4. Load Balancing and Service Discovery
Traditional IT environments require a lot of complexity to set up load balancing and service discovery. But Kubernetes makes this process much easier, as built-in load balancing and service discovery mechanisms are available.
For instance, when containers in a Kubernetes cluster are exposed as services, Kubernetes ensures that network traffic is evenly spread across each service instance (pod). Moreover, it provides the service with a consistent DNS name so that other components can locate it and communicate with it. That means manually configuring won't be necessary; the application can scale up and down dynamically based on a change in workloads.
5. Declarative Configuration with YAML and Helm Charts
Kubernetes resorts to the declarative paradigm to manage infrastructure: you define more of the desired state of your applications using YAML configuration files. These configurations can talk about so many things apart from deployments, services, volumes, and much more.
In addition, Helm charts are often referred to as package managers for Kubernetes. They make the deployment of complex applications really easy. It is possible to pack Kubernetes YAML files into reusable templates, making complex microservices architecture deployment and maintenance much easier. Using Helm, companies can standardize deployments and also increase consistency across different environments.
6. Rolling Updates and Rollbacks
Updates in a distributed system, especially zero-downtime updates, are difficult to manage. The rolling update feature provided by Kubernetes makes this much easier. It does not take down the entire application for an update; instead, it gradually replaces the old version with the new version. So, a part of the system remains on for the entire update.
7.StatefulSets with Persistent Storage
Although containers are stateless by design, most practical applications require some form of persistent storage. Kubernetes supports this by offering persistent volumes that abstract away the underlying infrastructure so that users can attach persistent volumes to their containers. Whether stored in the cloud, NAS, or local disks, Kubernetes gives users a unified way to manage and provision storage for containerized applications.
8. Security and Role-Based Access Control (RBAC)
Any enterprise-grade solution has to be secured. Kubernetes has quite a few solid security features built in, but one of the primary mechanisms is Role-Based Access Control (RBAC), which permits fine-grained control over access to Kubernetes resources.
With RBAC, an organization can define roles and permissions; they need to define which users or services can operate on which resources. This prevents legitimate members from making unauthorized changes in a Kubernetes cluster.
9. Multi-Cloud and Hybrid Cloud Support
Another significant benefit that Kubernetes brings is the support for multi-cloud and hybrid cloud environments. Users can deploy and run their Kubernetes clusters across the leading clouds-AWS, Azure, GCP-and on-premise environments according to their cost, performance, and compliance requirements.
10. Kubernetes Ecosystem and Extensibility
Of course, alongside this, Kubernetes has a large and thriving ecosystem of tools and integrations that extend beyond its capabilities. Now, be it for Prometheus as a monitoring solution, Jenkins for CI/CD pipelines, or Things Under the Sun, Kubernetes fits in everywhere,
thus making it an adaptable platform for developers and operators.
Conclusion
Kubernetes is a game-changer that has not only transformed the containerized workload world but has also provided a robust set of features to break down the complexities of modern cloud-native applications. Its capabilities range from automated deployment and self-healing to efficient scaling and seamless integration with various tools and platforms, making it the go-to solution for organizations looking to modernize their IT infrastructure.
1 note
·
View note
Text
A Comprehensive Overview of Web Development
Web development is currently an integral part of global web growth, assisting individuals, businesses, and services in creating their digital identities. It includes designing and developing website structures and features, ensuring their operational and visual gross and processing efficiency in their usage.
Web development is an ever-evolving field it is important regardless of your experience level to have a clue about the environment one is about to build on. In this blog, we will discuss what web development is, its categories, fundamental concepts, tools, and the modern trends defining the field.
What is Web Development?
Web development is also known as website development and involves creating, designing, and supporting sites that are on the World Wide Web. This comprises what concerns web design, writing web content, client-side epoch/server-side scripting, putting in place network security, and e-commerce. In other words, it can be applied to any kind of task, ranging from straightforward HTML sites to complicated online apps.
There are two general categories of web development: front-end and back-end development and full-stack development. Let us study each one.
Types of Web Development
1. Front-End Development:
Front-end development is among the subdivisions of Web development that address the visual layer or perspectives of the website, including such options as design, structural design, and interactivity, which involve direct usage by the clients. The front end relies on other languages such as HTML (Hyper Text Markup Language), CSS (Cascading Style Sheets), and JavaScript to present friendly user interfaces.
Key technologies used in Front-end development


2. Back-End Development:
Back-end development refers to the work done at the back end of a website or application, including, database, servers, and APIs. It allows the front end to get the required information and the overall application is fine.
A back-end developer makes sure that data integrity is maintained, that the server will be able to reply to requests at a reasonable amount of time and all things are integrated with the front-end.
Key technologies used in back-end development


3. Full-Stack Development:
Full-stack developer means the developer works from the front as well as from the back end of the program or an application. They also possess the tools that allow them to design and implement every aspect of a web application including that application’s user interface (the GUI) and the behind-the-scenes support (the back-end database component). Full-stack developers should know the different languages, frameworks, and tools and be able and willing to work for both the front end and back end.
Fundamental Components of Web Development
Domain Name and Hosting:
When developing a website, the web address, for instance, www.example.com, or the domain name is required, and the web hosting service, which is the company offering space on the server where files of the website are stored. Most of these basic host service controls include Blue Host, host gator, Go Daddy, and others Domain names could be obtained from any domain reseller service or any hosting service like NameCheap among others.
Responsive Design:
Responsive design means that regardless of the view of the web page, this web page is appropriate and sufficient for the appliance on which the person is using, whether or not it is a computer, notebook, tablet, or mobile. This is done through a CSS component called media queries that reassigns or, rather, sets other styling rules based on screen resolution or, perhaps, orientation. Other frameworks such as Bootstrap and “Foundation” make it easier with prepared responsive web design tools.
Content Management Systems (CMS):
This is a system that enables people with no coding skills, to design, edit and develop content on a website. Some of the most commonly used CMS are WordPress, Joomla, and Drupal. These systems are commonly used for blogs, corporate sites,s, and e-commerce applications.
Version Control and Collaboration:
Professional tools such as Version Control Systems (VCS) like Git, and platforms like “GitHub” or “GitLab” provide the framework with collaborative functions to develop the projects side by side with features to track changes and differentiate one version of the entire codebase from the other. This is especially very important for groups that are assigned large projects, it also helps in case one person messes up the project.
Web Development Tools


Trends Shaping the Future of Web Development
The industry of web development is expanding quickly, and it is changing faster in terms of approachable tools and practical methodologies. The following significant trends will influence web development going forward:
1. Progressive Web Apps (PWAs):
Internet applications that are now called Progressive Web Apps (PWAs) act as a user interface for native mobile applications. Sometimes it works fast, it is dependable, and one of its features is that it can work offline, and in general, it provides an application-like platform on the Web.
PWAs are now extensively utilized and are predicted to grow much more in the future. Leading social media sites such as Pinterest and Twitter have already included PWAs.
2. Artificial Intelligence and Machine Learning:
As websites can provide more complex user experiences, artificial intelligence (AI) and machine learning are bringing about innovative change in online development. Web developers apply AI technologies such as chatbots, recommendation engines, and predictive engines to their work.
3. Voice Search and Voice User Interfaces (VUI):
One of the most recent products incorporated in the experiments of an enhanced search can be linked to voice search due to the development of voice-activated assistants such as Alexa or Google Home.
According to the study, web developers have to adapt to Voice recognition to support voice search and use VUI where necessary.
4. Serverless Architecture:
It refers to the development and deployment of applications without being concerned with servers. This architecture given by services such as AWS Lambda and Google Cloud Functions keeps the operational costs low and deployment easy.
5. Motion UI:
In Motion UI, animation and transition are the center of attention when it comes to designers. From loading spinners to making smooth transitions, Motion UI is responsible for adding a form of interactivity and style to the interface, which is very important for websites today due to the stiff competition.
Conclusion
Nowadays, web development can be defined as a wide specialization area with new opportunities for further development. Front-end design, back-end logic, full-stack development, all these concepts and trends are photographers to build highly effective Websites today – effective, user-friendly, and future-proof. Continuing your education about these technologies and other best practices places you in proper standing as a web developer and enables you to contribute to the ongoing formation of the web for many more years to come.
#angular development usa#custom php development in usa#best php development company in india#website design company#web development firm new york#website development company
0 notes
Text
How does the Internet work?
These days, Wi-Fi is everywhere, offering wireless connectivity and the freedom to move around while staying connected. However, even Wi-Fi relies on physical infrastructure. The backbone of the Internet is made up of telephone lines, TV/cable lines, and fiber optic cables. Devices use this infrastructure to communicate by following an addressing system, similar to how postal services work. Since computers process data as ones and zeros (called bits), the addressing system is numeric and governed by what we call the Internet Protocol, or IP. Every device has a unique IP address, which is how it is identified on the network.
The original format for IP addresses, known as IPv4, uses 32 bits. These are split into four groups of eight bits, also called octets or bytes. Each group represents a part of the address: the first group identifies the country, the second the region, the third the subnet, and the fourth specifies the device itself. However, as the Internet has grown, the supply of IPv4 addresses is running out. To address this, a new format called IPv6 was created, using 128 bits, four times the size of the original system.
But when browsing the web, we don’t use IP addresses directly. So how do we, as users, connect with these numbers? The solution is the Domain Name System (DNS). DNS servers, located around the world, convert human-friendly URLs into IP addresses, and vice versa. Each DNS server manages specific domains, like .com, .gov, .edu, and .org, which saves us from having to remember long strings of numbers to navigate the Internet.
Now, what about the World Wide Web? Isn’t it just another name for the Internet? Technically, no. The World Wide Web, or simply the Web, is made up of websites that you access through the Internet. The Internet, on the other hand, is the massive network of interconnected devices, while the Web consists of the sites and pages hosted on many of these devices.
0 notes
Text
Admission Provider: The Best Educational Consultancy in Patna
In today's competitive educational landscape, students often face challenges when navigating the path to higher education. Whether it is selecting the right course, finding the best institution, or securing admissions in competitive fields, the guidance of an experienced educational consultancy becomes crucial. In Patna, one name stands out for its commitment to helping students achieve their academic dreams – Admission Provider. Recognized as the best educational consultancy in Patna, Admission Provider offers a wide range of services designed to make the admission process smoother and more transparent.
Why Admission Provider is the Best
Expertise and Experience
Admission Provider has built a strong reputation over the years as a trusted educational consultancy in Patna. The firm is staffed with experienced counselors who are well-versed in the nuances of the Indian and global education systems. With in-depth knowledge of admission processes for a variety of programs – ranging from engineering and medical to arts and commerce – Admission Provider ensures that students receive personalized advice suited to their academic goals. The consultants guide students through each step, ensuring they are aware of application deadlines, eligibility criteria, and entrance exams, reducing the chances of mistakes or missed opportunities.
Tailored Counseling for Every Student
What makes Admission Provider stand out is their commitment to offering personalized guidance. Every student is unique, and so are their aspirations. The consultancy recognizes this and offers tailored counseling based on each student’s academic background, career goals, and financial situation. Whether you are aiming for MBBS, engineering, or management courses, the team ensures you choose the right institution that aligns with your objectives and future prospects.
A Vast Network of Colleges and Universities
Admission Provider has established strong ties with some of the leading institutions across India, including universities and colleges offering courses in medical, engineering, management, and more. These partnerships allow them to provide their clients with a wide variety of options to choose from. The consultancy assists students in securing seats in top institutions, ensuring they have the best chance to build a bright future. Their extensive network ensures that even students from diverse academic backgrounds can access premium educational opportunities.
Specialized Services Offered
MBBS and Medical Admissions
Securing a seat in a medical college can be daunting, given the fierce competition and the rigorous selection process. Admission Provider specializes in offering guidance for MBBS admissions, helping students understand the eligibility criteria, entrance exams, and various quotas that exist within medical colleges. They work diligently to help students find reputable medical colleges in India and abroad, ensuring they achieve their dream of becoming healthcare professionals.
Engineering Admissions
Engineering continues to be one of the most sought-after fields of study in India. Admission Provider helps students identify the best engineering colleges based on their specialization of interest – whether it's computer science, mechanical engineering, civil engineering, or electronics. With their guidance, students can gain entry into prestigious institutions, ensuring they receive quality education and exposure in their chosen engineering domain.
Guidance for Management Courses
In the realm of management education, securing a seat in a reputed B-school can set the foundation for a successful corporate career. Admission Provider offers specialized consultancy for management aspirants, ensuring they are well-prepared for exams like CAT, MAT, and XAT. Their expert guidance helps students secure admissions in top management institutes, where they can pursue MBA or other business-related programs.
Why Choose Admission Provider?
Transparency in Processes
One of the core values of Admission Provider is transparency. The consultancy is committed to providing clear and accurate information regarding admission procedures, fees, and deadlines. They believe that students and their families should be fully informed, which is why they maintain an open line of communication throughout the admission process. This transparency builds trust and ensures that students can make well-informed decisions about their academic futures.
Comprehensive Support
From selecting the right course to ensuring all documents are in place for application, Admission Provider offers end-to-end support. They guide students through entrance exam preparation, provide information about scholarships, and assist with college applications and counseling processes. The consultancy even offers visa assistance for students aiming for international institutions.
Conclusion
Choosing the right educational path is a significant decision, and Admission Provider stands by its students at every step of this journey. With their extensive expertise, personalized counseling, and comprehensive support, Admission Provider has earned its reputation as the best educational consultancy in Patna. Whether you are aspiring for a career in medicine, engineering, or management, Admission Provider ensures that your academic aspirations become a reality.
Visit: https://www.admissionproviders.com/
#educationalconsultancy#besteducationalconsultancy#admissionconsultancy#admissionprovider#admissionproviders#admissionconsultancyinpatna#educationalconsultancyinpatna#getadmission#bestadmissionconsultancyinpatna#bestconsultancy
0 notes
Text
Internet Connected But Website Not Opening How to Fix It ?

Hey Have you ever faced the issue where your internet is connected, but your website not opening? You’re not alone! Many people encounter this problem, and while it may seem confusing, the solution is often simple. Whether you’re browsing for work, entertainment, or personal reasons, getting a website to load is crucial. In this guide, we’ll explore common causes and quick fixes for when your internet connection is working, but the website isn’t.
1. Clear Your Browser Cache
When Internet Connected But Website Not Opening,So the issue may be due to cached files. Cached data can sometimes prevent a website from loading properly, especially if the website has updated its content.
How to fix Internet Connected but website not opening
After clearing the cache, reload the website to see if it opens.
2. Check Your DNS Settings
Sometimes the problem lies in your DNS settings. If the Domain Name System (DNS) server is down or misconfigured, it can prevent websites from loading even when you’re connected to the internet.
How to fix DNS issues:
3. Try a Different Browser
If Internet Connected But Website Not Opening . So Your current browser might be facing issues, which can prevent websites from opening. Testing the site on a different browser will help determine if the problem is browser-specific.
What to do:
You can either update your original browser or switch to the new one for better functionality.
4. Disable VPN or Proxy
If you're using a VPN or proxy service, it might interfere with certain websites loading correctly. VPNs can sometimes slow down or block access to specific websites, depending on server location or restrictions. So that this could be a problem of Internet Connected But Website Not Opening.
Steps to disable:
If the issue resolves, try using a different server or temporarily browsing without the VPN.
5. Flush Your DNS Cache
Over time Internet Connected But Website Not Opening, your computer may store outdated DNS entries, causing problems with website loading. Flushing the DNS cache can refresh your system and resolve the issue.
How to flush DNS:
Once done, try reopening the website to check if it works.
6. Check for Firewall or Antivirus Restrictions
Sometimes Internet Connected But Website Not Opening, your firewall or antivirus software might block access to certain websites, even though your internet is working fine.
What to do:
If the website opens, you may need to adjust your security settings to allow access.
7. Try a Different Device or Network
To rule out problems of Internet Connected But Website Not Opening with your device or local network, try accessing the website from a different device or network. For example, use your mobile phone on a different Wi-Fi network or mobile data And the problem is Internet Connected But Website Not Opening open your website
Steps:
8. Check for Website-Specific Issues
If the Internet Connected and Website Not working or Opening, it might be down or experiencing server issues. You can use online tools like "Down For Everyone Or Just Me" to check the website's status.
website still isn’t opening, it might be down or experiencing server issues. You can use online tools like "Down For Everyone Or Just Me" to check the website's status.
How to check:
Conclusion of Internet Connected But Website Not Opening
Dealing with the “internet connected but website not opening” issue can be frustrating, but in most cases, the solution is straightforward. By following these steps, you can quickly identify the problem and get back online. From clearing cache to adjusting DNS settings, these fixes will help you troubleshoot the issue and restore access to your favorite websites.
“Take action now, and say goodbye to website loading issues!”
#digital marketing#online marketing#digital marketing services#search engine optimization#digital marketing agency#seo services
0 notes