#webstite
Explore tagged Tumblr posts
Text
not to be a boomer but somehow i don't think that a temp agency should require that i download their app and use it to share with them proof of residency and three latest pay slips before i'm allowed to sign up and submit applications
#capitalist hell#looks to me like reasons to discriminate against certain neighbourhoods#and try to ignore official salary grids#i mean if they are to employ me yes they'll need my identity card social security number and bank details BUT#that's still an IF and the rest looks fishy as hell#also how can i know my info is secure withing their app and they're not selling it to third parties#they don't have a working webstite anymore either
3 notes
·
View notes
Text
OKAY. pasta salad
desperate post of kicking myself off the computer -> helpppppppp i got sucked into hours of reading pointless internet arguments and now its hours past when i shouldve started a semilengthy dinner cooking
#NOT arduous just a lot of standing thats hard for me today#<- who gives a shit whos criticizing me on the disabled ppl webstite
7 notes
·
View notes
Text
preface for this post i'm a white guy. but i will say? ummm okay so wtf. nobody here has heard of JID.........the absolute lack of hiphop literacy on this webstite despite it being one of the most popular genres of music literally ever is soooo telling. like omg okay so you're ignorant and think there's nothing in hiphop for you to like (you are wrong.) or straight up racist (unsurprising) or you're white & the nword makes you uncomfortable to hear (which is seriously a you problem and just makes me 100% sure you've never even had a black friend.)
11 notes
·
View notes
Text
Ok uh. So now that Ada’s dead all the original cats are gone which by Clangen rules means the games over!!!!!!!!! So like. Rundown cuz what the fuck happened BDNHWENSJWNSJ
Leon And Luis got married and adopted Ashley. Rebecca and Ada got married and immediately had four kids but Rebecca was constantly cheating on her and being an absent parent. All four kids died; either by murder or by random unexplainable deaths.
LEON then died, but was soon after reincarnated and immediately had three kids with Luis. Wanna guess what happened??????? That’s right they were all inexplicably either murdered or found dead except for ONE!!!!!!!! AND reincarnated Leon died too!!
Ada And Rebecca Found a Random Kitten in the bushes and decided to steal it and called it Sherry. Sherry died but like Leon was also reincarnated
President Graham was the leader first and Patrick constantly had a massive crush on him. When President Graham stepped down as leader and Ada took is place Patrick stumbled across a rogue named Krauser and got rejected by him TWICE. Eventually after Graham died though they got together and had the reincarnated version of Leto.
Luis, Ada ans Rebecca all eventually died of old age right before the one kid of reincarnated Leon and reincarnated Sherry had their OWN two kids and Patrick stepped up as leader. The end. Oh and Ashley’s still somehow chilling idk how she didn’t die
The webstite is Clangen for anyone who wants to play!!!!!!!!
13 notes
·
View notes
Text
SORRY FOR THE INACTIVITY AGAIN LOL i'm still on my finals and i'm participating on artfight!!!

(my characters lol) so i'm posting art on the webstite for the month!!
here is my profile if you want to check out something DSJFKJF
and also i have been pretty much hperfixated on my hsr oc rosa somebody sedate me oml
#niso screams into the void#artfight#original character#ocs#also i can't stop drawing rosa with BOOTHILL BRUH
5 notes
·
View notes
Text
✦ ⸺ RULES

charlesleclerizz™ | All rights reserved. Plagiarism is not acceptable to me, therefore please do not replicate my works. Since it is against the law to transfer my works to other websites, like Wattpad, Ao3, etc, please reefrain from doing so. My mail box is open to requests of such a nature and rules are listed on my page.
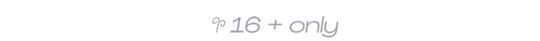
I hold the right to deny/delete/not write any request if it makes me uncomfortable or will make the majority of readers uncomfortable. No arguements.
why i say. " 16+ only "
When requesting please keep in mind !
❗️ I will not write about
✺ Racism - Prejudice, discrimination or antagonism by an individual, community or institution against a person or people on the basis of their membership in a particular racial or ethnic group, typically one that is a minority or marginalized.
✺ Colourism - Within-group and between-group discrimination against people of color with darker skin tones and giving preference to people of color with lighter skin tones.
✺ Tokenism - The practice of using people of color in a symbolic gesture to avoid criticism or being called racist.
✺ Sexism - Prejudice or discrimination based on one’s sex or gender. Sexism can affect anyone, but it primarily affects women and girls.
✺ Ableism - Discrimination against people with impaired or limited abilities because of their physical abilities.
✺ Ageism - Discrimination against older populations because of their age and perceived competence or capabilities.
✺ Classism - Discrimination against people of lower class because of their economic status.
✺ Eliteism - Discrimination against people believed to be “less than” in terms of education, money, job status/position,
✺ Homophobia - Discrimination against non-heterosexual people because of their sexuality.
✺ Transphobia - Discriminationn against transpeople or gender non-comforming people because of their gender identity
✺ Xenophobia - Discrimination against people from other countries or anyone deemed “foreign” because of their immigrant or visitor status.
✺ Islamophobia - Discrimination against anyone practicing or perceived to be a practitioner of Islam because of their religious affiliation.
✺ Fatphobia - Discrimination against people with bigger bodies because of their size.
-> references for the official meaning (s) of these ’-phobia’ and ’-isms’
[ NOTE : Just because I have not explicitly mentioned a phobia in the list above from the website that I have linked, does not mean that it is on the table. I just assumed that nobody would request it/I am just not expecting it]
✺ Rape/non-consensual sexual occurences
✺ Sexual occurences to a minor
✺ Any forms of abuse to adult and/or minor
-> here is a list of abuses that I will not ever be writing
✺ Intense BDSM
-> Worrying kinks that should never be normalised or written about
[NOTE: If, for some reason, you do request something from this list eg : somnophilia and I read it, I will not shame you for it. I will merely delete it and move on. Kink-shaming is icky, not equally-icky, but hateful none the less]
❗️ I will write about
✺ Mild BDSM
-> link to common kinks, that I will be writing for
[NOTE: On this list, numbers 8, 18 are not allowed. Don’t ask for it. Please. And, it also states erotic asphyxiation, this is different to the actual strangling, because it is not performed so intensly, with the intent/disregard of death. It is slight pressure on the sides of the neck, and very light force on the windpipe]
-> webstite that talks about safe BDSM/kink-experimentation.
✺ Smut.
✺ Fluff
✺ Angst
✺ Dub/con
[NOTE: DUBIOUS CONSENT otherwise known as DUB/CON will be taken as (by me personally) previously given consent, verbally, physically or by signal/clothing (eg. reader wears a specific peice of clothing that informs their partner that they are giving consent for sexual acts). In my work, it will always be specified that the couple have given consent beforehand. To some, dub/con may be taken as unsure/hesitant consent. That is not the case in my work, consent is not something to be hesitant about and in my writing, it is merely a case of trust between the parties. If i do choose to include dub/con in my work, it will be indicated.]
✺ Specifically, Piss kink
This list can/will be subject to change.
#navigation#[darlingisnowadmin]#f1#f1 fic#f1 fanfic#f1 fanfiction#f1 x reader#f1 blurb#f1 x y/n#f1 x female reader#f1blr
3 notes
·
View notes
Text
Imagining realistic Moomin
Been messing around with the online AI-art webstite artbreeder.com. Thought I would try to create something that looks like a more realistic moomin. Here are the attempts:
Very-realistic-animal moomin:

Scandinavian-troll moomin:

Strange-woodland-critter moomin:

Disney/ghibli/animated-talking-animal moomin:

Snufkin and nightmare-fuel moomin meet in a woods:

Which is your favorite?
#moomin#moomintroll#ai art#character design#what should i draw#moomins#tove jansson#snufkin#snufkin and moomin#realistic moomin
5 notes
·
View notes
Text
A wincest shipper may have created Ao3, but they didn’t invent fanfiction. They didn’t invent the only fanfiction website. They didn’t invent the first fanfiction webstite in the world. Fanfiction doesn’t only revolve around Ao3. Fanfiction isn’t only in ao3 culture.
That’s such a weirdly generalized counter argument. Okay, and?
0 notes
Text
my phone doesnt wan a turn on forced to use desktop webstite head in handsssss
0 notes
Text
can webstites tell if i am switiching vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can webstites tell if i am switiching vpn
VPN detection methods
Title: Unraveling the Mysteries of VPN Detection Methods
In today's digital age, the use of Virtual Private Networks (VPNs) has become increasingly prevalent, offering users enhanced privacy and security while browsing the internet. However, as VPN usage grows, so does the need for entities to detect and potentially block VPN traffic. Understanding VPN detection methods is crucial for both users seeking anonymity and organizations aiming to regulate network access.
One primary method used for detecting VPN usage involves examining the IP addresses associated with connections. VPN services typically route traffic through their servers, masking users' original IP addresses with those of the VPN servers. By compiling lists of known VPN server IP addresses, organizations can identify and block VPN traffic attempting to access their networks.
Deep packet inspection (DPI) is another effective VPN detection technique. DPI involves scrutinizing the data packets passing through a network to discern their contents and destinations. By analyzing traffic patterns and characteristics commonly associated with VPN usage, such as encrypted communication protocols and consistent data packet sizes, DPI can flag VPN traffic for further scrutiny or restriction.
Furthermore, behavioral analysis methods can detect VPN usage by analyzing users' browsing habits and connection behaviors. Anomalies such as sudden changes in IP addresses or irregular connection patterns may indicate VPN usage, prompting further investigation or action.
VPN providers employ various strategies to circumvent detection, such as regularly updating their server IP addresses or employing obfuscation techniques to disguise VPN traffic as regular internet traffic.
In conclusion, while VPNs offer users valuable privacy and security benefits, they are not immune to detection. Organizations employ a variety of methods, including IP address monitoring, deep packet inspection, and behavioral analysis, to identify and potentially restrict VPN usage. As the digital landscape continues to evolve, understanding VPN detection methods remains essential for both users and network administrators alike.
Website tracking VPN usage
Website tracking VPN usage is a crucial aspect of maintaining online security and privacy. VPNs (Virtual Private Networks) are powerful tools that encrypt internet connections, protect sensitive data, and hide users' IP addresses. While VPNs are commonly used to safeguard privacy and bypass geo-blocking restrictions, website owners may find it necessary to track VPN usage on their platforms for various reasons.
One of the primary reasons for tracking VPN usage on websites is to monitor and prevent fraudulent activities. VPNs can be used to mask malicious intentions, such as hacking, spamming, or engaging in illegal activities. By monitoring VPN usage, website owners can identify suspicious behavior and take necessary actions to mitigate risks and protect their platforms and users.
Tracking VPN usage also enables website owners to analyze traffic patterns accurately. VPNs can sometimes affect website analytics by distorting geographical data and skewing user demographics. By monitoring VPN usage, website owners can differentiate legitimate traffic from VPN users and adjust their strategies accordingly to better cater to their audience and improve user experience.
Moreover, tracking VPN usage allows website owners to comply with legal regulations and licensing restrictions. Some content may be restricted for viewers in specific regions due to licensing agreements or legal frameworks. By monitoring VPN usage, website owners can ensure compliance with these regulations and restrict access to content based on the user's geographical location.
In conclusion, website tracking VPN usage is essential for maintaining online security, preventing fraudulent activities, analyzing traffic accurately, and complying with legal regulations. By monitoring VPN usage, website owners can better protect their platforms, enhance user experience, and ensure compliance with relevant laws and policies.
IP address masking detection
Title: Understanding IP Address Masking Detection: Enhancing Online Security
In the realm of online security, IP address masking detection plays a pivotal role in safeguarding sensitive information and preventing unauthorized access to networks and systems. An IP (Internet Protocol) address serves as a unique identifier for devices connected to a network, enabling communication between them. However, malicious actors may attempt to conceal their true IP addresses through various methods, posing a threat to cybersecurity.
IP address masking involves techniques such as proxy servers, virtual private networks (VPNs), and the Tor network, which aim to obfuscate the true origin of network traffic. While these tools offer legitimate uses, they can also be exploited for illicit purposes, including cyberattacks, data breaches, and online fraud. Therefore, detecting and mitigating IP address masking is essential for maintaining a secure online environment.
Detection methods for IP address masking typically involve analyzing network traffic patterns, monitoring for anomalies, and employing specialized software and algorithms. Advanced threat detection systems utilize machine learning and artificial intelligence to identify suspicious behavior and distinguish between legitimate and malicious activity. By analyzing factors such as packet headers, geolocation data, and behavioral patterns, these systems can effectively uncover attempts to mask IP addresses.
Moreover, collaboration among cybersecurity professionals, law enforcement agencies, and internet service providers (ISPs) is crucial for combating IP address masking and apprehending cybercriminals. Sharing threat intelligence, implementing industry best practices, and enforcing stringent security measures can help deter malicious actors and protect against emerging threats.
In conclusion, IP address masking detection is an integral aspect of cybersecurity, enabling organizations and individuals to defend against evolving online threats. By leveraging advanced detection technologies and fostering collaboration within the cybersecurity community, we can fortify our defenses and uphold the integrity of the digital landscape.
Geo-location spoofing prevention
Geo-location spoofing is a method used by individuals to deceive devices, websites, or applications into believing that the user is located in a different geographical area than their actual physical location. This deceptive practice can have various implications, including privacy concerns, security risks, and potential misuse of location-based services.
To prevent geo-location spoofing, there are several effective strategies that can be implemented. One of the primary methods is to use encrypted connections, such as HTTPS, when transmitting location data between devices and servers. Encryption helps to secure the data being transmitted, making it more difficult for malicious actors to intercept and manipulate it.
Another essential step in preventing geo-location spoofing is to enable location service permissions only for trusted applications. By carefully managing which apps have access to location data, users can reduce the likelihood of unauthorized spoofing attempts.
Additionally, implementing multi-factor authentication can add an extra layer of security to location-based services. By requiring users to provide additional verification, such as a one-time code sent to their mobile device, it becomes more challenging for spoofers to gain unauthorized access to their location information.
Furthermore, regularly updating software and applications is crucial in preventing geo-location spoofing. Developers often release patches and updates to address security vulnerabilities, including those related to location spoofing.
By adopting these preventive measures, users can enhance the security of their location data and reduce the risks associated with geo-location spoofing. Awareness of potential threats and implementing best practices are key components in safeguarding sensitive information in an increasingly digital and interconnected world.
Online anonymity tools viability
Title: Exploring the Viability of Online Anonymity Tools
In an era marked by growing concerns over online privacy and security, the use of anonymity tools has gained significant traction. These tools, ranging from virtual private networks (VPNs) to Tor browsers, offer users a means to mask their digital footprint and protect their identities while navigating the vast landscape of the internet. But just how viable are these online anonymity tools?
The viability of online anonymity tools largely depends on their effectiveness in achieving two primary objectives: masking user identity and safeguarding online activities. VPNs, for instance, reroute internet traffic through encrypted tunnels, making it challenging for third parties to intercept or trace the data back to individual users. This not only protects sensitive information from prying eyes but also enables users to bypass geo-restrictions and access content that may be restricted in their region.
Similarly, Tor browsers employ a decentralized network of servers to anonymize web browsing by encrypting data multiple times and routing it through random nodes, thus obscuring the user's IP address and online activities. While Tor offers a higher level of anonymity compared to traditional browsers, its reliance on volunteer-operated nodes and slower browsing speeds may pose limitations for some users.
However, it's essential to recognize that no online anonymity tool is foolproof. Despite their effectiveness, VPNs and Tor browsers can still be vulnerable to sophisticated cyber attacks or breaches, particularly if users engage in risky online behavior or fail to keep their software updated.
Moreover, the legality and ethical implications surrounding the use of anonymity tools vary across jurisdictions, with some governments imposing restrictions or outright bans on their usage.
In conclusion, while online anonymity tools can provide a valuable layer of protection for users seeking to safeguard their privacy and anonymity online, their viability ultimately hinges on various factors, including their effectiveness, user behavior, and legal considerations. As such, users must weigh the benefits and limitations of these tools carefully to make informed decisions about their online security practices.
0 notes
Text
Speaking of indivisible, I'd recommend following this link to their webstite nixthenoms, which has scripts for calling your senators to oppose some of the worst of Trump's nominees for federal positions. Their layout is pretty neat, and it links you up to the capitol switchboard, which? I didn't know we had? I felt so cool and old-timey making my calls ^_^
mercy seems like a long shot here, so my prayer for inauguration day 2025: may they be incompetent. may they just be really bad at implementation. may their egos choke their effectiveness. may they drown themselves week by week with infighting and selfish posturing. may they be easily distracted. may the very governors and senators and agencies and religious leaders that the new administration expects to be friendly force endless stalemates to preserve their own power. may every delay turn into a three ring blame circus so chaotic that no one remembers what they were doing. may the good and necessary parts of government be too boring to draw attention and keep running quietly in the background. may the next four years be full of sound and fury and signify nothing.
46K notes
·
View notes
Text
I love the experience of being out of my mind and using tumblr. Truly the peak stoner and pain med abuser webstite.
0 notes
Note
ur universe doesnt have pokemon ? wonky..
-tunic anon
Nya, it didn't. Then I got moved here while my battery died so now I live with the worst Rotomblr user on the entire webstite.
-ᰉ
0 notes
Text
AND!! You can download sheet music to all of his songs from his webstite!! https://tomlehrersongs.com/ Lehrer relinquished all rights to any of his lyrics or music. He's begging us to use it and keep these songs for the future!
I cannot overstate how much I love Tom Lehrer's story. It sounds so fake but is entirely real.
He's a goddamn genius- he started studying mathematics at Harvard when he was 15 and graduated magna cum laude. He worked at Los Alamos for a few years before being drafted and working for the NSA, where he claims to have invented jello shots to get around alcohol bans.
He then went back to Harvard for a couple years before starting to teach political science at MIT.
Through all of that, he was writing and performing both some of the funniest shit you'll ever hear (Poisoning Pigeons in the Park, Masochism Tango) and absolutely scathing political satire (Who's Next, Wernher von Braun, Send the Marines). Until the mid/late 60s counterculture gained momentum. He didn't like their aesthetic, so he stopped making music.
Shortly after, he moved to California and started teaching math and musical theater history at the UC Santa Cruz for the next 30 years.
I don't know if non-Californians understand just how goddamn funny that is. It's where stoners and math (and now computer science) kids who couldn't get into Berkeley go. Leaving Harvard/MIT for UCSC is peak academic phoning it in. And by all accounts he had a blast.
Plus the whole putting all of his music in the public domain thing. That fucked.
30K notes
·
View notes
Text
Go789
Giới thiệu Go789 là Webstite cá cược trực tuyến Uy Tín số 1 hiện nay Tại sao mọi người nên cá cược lại nhà cái Go789 Dịch vụ hỗ trợ người chơi chu đáo,tận tình 24/7 Đối với Go789 đã có cái nhìn rất xa trước thời đại Chi Tiết Tại Địa chỉ: 37 Ngách 63/1 Trần Quốc Vượng, Dịch Vọng Hậu, Cầu Giấy, Hà Nội, Việt Nam Số điện thoại: 0584868001 Email: [email protected] Website: https://go789club.net/gioi-thieu-go789/ Fanpage: https://www.facebook.com/go789clubnet

1 note
·
View note