#unified threat management market
Explore tagged Tumblr posts
Text
Unified Threat Management Market Segment Analysis By Application, Region And Forecast Till 2030: Grand View Research Inc.
San Francisco, 10 Nov 2023: The Report Unified Threat Management Market Size, Share & Trends Analysis Report By End Use (Telecom & IT, BFSI), By Component (Hardware, Virtual), By Enterprise Size (SME), By Service, By Deployment, And Segment Forecasts, 2019 – 2025 The global unified threat management market size is expected to reach USD 10.09 billion by 2025 at a CAGR of 14.5% from 2019 to 2025,…

View On WordPress
#Unified Threat Management Industry#Unified Threat Management Market#Unified Threat Management Market 2019#Unified Threat Management Market 2025#Unified Threat Management Market Revenue#Unified Threat Management Market Share#Unified Threat Management Market Size
0 notes
Text
Streamlining Payment Processes: A Guide to Credit Repair Merchant Accounts
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the ever-evolving financial landscape, the prowess of refining payment processes cannot be overstated, especially for credit repair businesses. Mastering the art of efficient payment management is the linchpin for success in this burgeoning industry. This guide unravels the enigma of Credit Repair Merchant Accounts, showcasing their pivotal role, and illuminating how they hold the potential to transform the fabric of your credit repair enterprise.
DOWNLOAD THE STREAMLINING PAYMENT PROCESSES INFOGRAPHIC HERE
The Empowering Essence of Credit Repair Merchant Accounts
Thriving amidst its challenges, the credit repair realm often grapples with the complexities of high-risk merchant processing. Yet, Credit Repair Merchant Accounts emerge as a strategic ally, offering a comprehensive approach to effortlessly navigate the landscape of credit repair payments. This guide delves deep into the critical facets of these merchant accounts, unveiling why they are indispensable and elucidating how they possess the potential to revolutionize your credit repair venture.
Seamless Credit Card Embrace
At the heart of a credit repair merchant account lies the ability to seamlessly embrace credit cards. This attribute not only amplifies the credibility of your business but positions it as a beacon of trust. In an era where digital transactions reign supreme, the merchant account becomes the conduit to meet customer expectations, allowing for the smooth and secure processing of credit and debit card payments.
Strategic High-Risk Payment Gateway
Given the inherently high-risk nature of the credit repair industry, a robust and strategic high-risk payment gateway is not just beneficial; it's imperative. The credit repair merchant account steps into this role, providing a secure platform that processes payments without succumbing to the constant threats of fraud or chargebacks.
Streamlined E-commerce Payment Mastery
In a landscape dominated by e-commerce, possessing an efficient e-commerce payment processing system is not merely advantageous; it's a necessity. A credit repair merchant account equips you with the essential tools to meet the surging demand for online payment options, ensuring customers can seamlessly pay for credit repair services with confidence and security.
Prestigious Credit and Debit Card Processor
Building trust stands as a cornerstone in the credit repair arena. By adopting a credit repair merchant account, you not only position yourself as the preferred credit and debit card payment processor but also elevate your status above competitors, marking your journey towards industry leadership.
Versatile Integration for CBD Transactions
For those navigating both credit repair and the CBD industry, the versatility of CBD merchant accounts becomes apparent. These accounts enable you to diversify your offerings, tapping into the thriving CBD market. A unified merchant account adeptly handling both credit repair and CBD payments streamlines your financial operations for unparalleled efficiency.
Online Payment Gateway for Unmatched Convenience
In a world propelled by speed and convenience, an online payment gateway, a pivotal component of your credit repair merchant account, offers unparalleled convenience to clients. This user-friendly feature empowers customers to make payments from the comfort of their homes or on the go, providing a game-changing advantage for your services.
Efficiency: The Backbone of Merchant Processing
Efficiency, the bedrock of any successful business, is seamlessly delivered through a credit repair merchant account. It offers streamlined merchant processing capabilities, translating to accelerated transactions, reduced administrative burdens, and more dedicated time to nurture business growth.
youtube
High-Risk Payment Gateway: A Shield in Turbulent Times
The credit repair industry often faces uncertainty due to regulatory changes and legal challenges. Your high-risk payment gateway acts as a steadfast shield, ensuring uninterrupted payment flows even in tumultuous times. It becomes the pillar of stability in the face of unforeseen disruptions.
In an industry where trust, efficiency, and security are non-negotiable, Credit Repair Merchant Accounts emerge as the linchpin to success. These accounts empower you to seamlessly accept credit cards, become the trusted credit and debit card payment processor, and navigate the high-risk landscape with assurance. Armed with an efficient e-commerce payment processing system and a reliable high-risk payment gateway, you stand poised to conquer the unique challenges of the credit repair domain.
Therefore, if the aim is to streamline payment processes and elevate your credit repair business to new heights, the time for hesitation is over. Embrace the potency of Credit Repair Merchant Accounts today, paving the way for financial stability and sustained growth. Clients will appreciate the convenience, security, and trustworthiness you bring to their credit repair journey. Unlock financial success, fortify your reputation, and cultivate a loyal client base with the right tools at your disposal. It's the opportune moment to streamline payment processes and embark on a journey toward prosperity and financial empowerment.
#high risk merchant account#payment processing#credit card processing#youtube#high risk payment processing#high risk payment gateway#merchant processing#accept credit cards#credit card payment#payment#Youtube
13 notes
·
View notes
Text
Writeblr Garden's Pumpkin Pitch Event: Six Strings & Stardust
Read for free on Substack

World-renowned pop sensation, Naomi Bell, becomes entangled with Benjamin Ferreira, the charismatic front man of a rapidly rising rock band, sparking an electric connection during one charged weekend. Their blissful time together shatters under the weight of expectations, propelling them into an intense, highly publicized feud. A media frenzy ensues as Naomi and Ben exchange sharp words and veiled accusations, even as their fame soars. Despite the growing chasm between them, their hearts persistently pull them closer. Determined to reunite, they embark on journeys of self-discovery, confronting personal demons, navigating the treacherous landscape of fame, and rekindling their initial passion. As their paths converge once more, they find solace in shared experiences and an unbreakable bond, rising above the fabricated feud that tore them apart. This is a tale of forgiveness, redemption, and the indomitable spirit of two artists who defy the barriers erected around them.
Genre: Contemporary Romance
Trigger Warnings:
anxiety
alcohol abuse
panic attacks
parental manipulation
language
Tropes:
found family
lovers - enemies - friends - lovers
opposites attract
Excerpt under the cut:
“Naomi Bell to set 19. Naomi Bell to set 19.” The static overhead announcement sounded for the fifth time for the photo shoot that was supposed to start an hour ago. I can quote it word for word now, something I’ll probably be reciting in my sleep tonight. The style team for the world’s most renowned pop star shifts uncomfortably on the fringes of the set. A short woman with a sharp bob haircut checks her watch for the twentieth time and groans in frustration at the wasted minutes. This photoshoot was supposed to be wrapping up now; instead one self-centered diva is throwing off everyone else’s schedule.
The set is adorned with several guitars ranging from vintage electrics to the most modern, streamlined acoustics on the market. In a stroke of, what they are calling, genius, top guitar designer Banshee Guitars is launching a new campaign with two of its musical ambassadors to demonstrate not only the breadth of its own range of style but also the unifying power of music across different people. Apparently, Naomi Bell and I are the perfect combo from their roaster to illustrate these polar opposites.
I was here thirty minutes early and the urge to say “fuck it” and leave is eating away at me. The style team assigned to me has applied the most elaborate version of my stage makeup on my face and neck. It’s beginning to irritate my skin, adding to every other thing about this that irritates me. My head falls back as I lean over the arm of the decorative chair I’ve been trying to get comfortable in for an hour to attempt eye contact with my manager. He’s equally unimpressed.
“I’m leaving in five minutes.” It is the sixth time I have made the same threat.
Martin simply holds up a perfectly manicured finger to silence me. He doesn’t even look up from his phone. He rarely does.
“No, you aren’t,” he replies with his usual dry and apathetic tone, still never looking my way.
I bite back the comments that are begging to spill from my lips. I’ve been trying to play nice, but I still can’t stifle the growl of frustration. The amount of work I have to do that isn’t actually making music is astonishing to me and something I can’t get used to.
The announcement rings out again, calling Naomi to the set. This time, a frantic bustling of voices follows from one of the long hallways that lead to the various dressing rooms and other studios.
“Sorry, sorry, sorry,” a chorus of melodic apologies ring out, getting closer and closer until a burst of pink and glitter emerges from the hallway.
“I’m so sorry! I hope you all haven’t been waiting for me too long.” Her singsong voice carries around the space as she hurries towards the set, stepping carefully and gracefully over power cords and props in her sky-high platform shoes. It’s all pink, the glittery crop top she’s wearing, the vinyl skirt hugging her hips, and those enormous shoes.
In the same room, it’s easy to see why they chose the two of us. Naomi is so bright. Everything about her is migraine-inducing, from her platinum hair to her bleached teeth. And she is so short; I could tell from across the room. It’s the most surprising thing about her. She always seems so larger than life in performances I’ve seen online — that’s not even mentioning the powerhouse that is her voice.
“Only an hour and a half.” I scoff as I stand and stretch out my legs, feeling every second that I spent waiting in that chair. This is the only evening I have to myself for a while and I had hoped this shoot wouldn’t cut into it too much — that dream is shattered. Our tour really kicks off after tomorrow night’s show, and we’re going to be busier than ever.
A small pout pushes at Naomi’s lips. “I’m really sorry. I got held up in wardrobe.”
I’m spoon-fed the opportunity to evaluate the aforementioned wardrobe. How it took so long to dress someone in so little clothing is beyond me.
11 notes
·
View notes
Text
Emerging Industries: Opportunities in the UK Job Market
Planning to study in the UK? Want to explore career opportunities in the United Kingdom?
In the ever-evolving world, the UK stands as a hub for innovation and growth, bringing numerous emerging sectors that offer promising career prospects. As technology continues to reshape the global economy, several industries in the UK have captured attention, presenting exciting opportunities for job seekers and entrepreneurs alike. Take a look at some of the career opportunities you could take advantage of.
1. Fintech (Financial Technology)
The UK has strengthened its position as a leading fintech hub, with London being a prominent center for financial innovation. Fintech includes a wide array of sectors, including mobile payments, blockchain, and cybersecurity. Job opportunities in this field span software development, data analysis, financial consultancy, and regulatory compliance.
2. Technology and IT
In the emerging era of the digital world, technology continues to dominate businesses worldwide. As, a result the demand for technologically advanced professionals tends to rise. Software developers, data analysts, cybersecurity experts, and artificial intelligence specialists roles are in high demand. With the increasing use of technologies and the need for innovative solutions, these roles offer tremendous growth opportunities and competitive salaries.
3. Healthtech
The combination of healthcare and technology has given rise to HealthTech, a sector dedicated to enhancing medical services through innovative solutions. From telemedicine to health analytics and AI-driven diagnostics, HealthTech offers diverse career paths for healthcare professionals, software developers, data scientists, and researchers.
4. Renewable energy and sustainability
With an increased focus on sustainability and combating climate change, the UK has been investing significantly in renewable energy sources. Wind, solar, and hydroelectric power are among the sectors experiencing rapid growth. Job roles in renewable energy range from engineering and project management to research and policy development, catering to those passionate about environmental conservation.
5. Cybersecurity
With the increasing frequency of cyber threats, the demand for cybersecurity experts is on the rise. Businesses and governments are investing heavily in safeguarding digital infrastructure. Job roles in cybersecurity encompass ethical hacking, network security, data protection, and risk analysis, presenting ample opportunities for skilled professionals in this field.
6. Artificial Intelligence and Machine Learning
AI and machine learning are revolutionizing various industries, including finance, healthcare, and manufacturing. The UK is fostering innovation in AI research and development, offering roles in AI programming, data engineering, robotics, and AI ethics.
7. Creative industries
The UK has a rich heritage in the creative sector, encompassing fields like media, design, gaming, and entertainment. Roles in creative industries span from content creation and graphic design to video production and game development, appealing to individuals with artistic and technical skills.
In conclusion, the UK job market is filled with opportunities within emerging industries, showing the nation's commitment to innovation and progress. Whether one's passion lies in sustainability, technology, healthcare, or creative endeavors, these sectors offer an array of possibilities for career growth and contribution to shaping the future.
By embracing change, acquiring relevant skills, and staying adaptable, individuals can position themselves to thrive in these dynamic and promising industries, contributing to both personal success and the advancement of these transformative sectors in the UK.
If you are struggling to get the right guidance, please do not hesitate to consult MSM Unify.
At MSM Unify, you can explore more than 50,000 courses across 1500+ educational institutions across the globe. MSM Unify has helped 1,50,000+ students achieve their study abroad dream so far. Now, it is your turn to attain your study-abroad dreams and elevate your professional journey! So, get ready to broaden your horizons and make unforgettable memories on your upcoming adventure.
2 notes
·
View notes
Text
Psychological warfare is the deliberate use of various manipulations, promotion and deception techniques, such as spreading propaganda and terror, to induce or reinforce attitudes that are favorable to gain strategic advantage over others. Sun Tzu, a Chinese Military Strategist originally said the best victory in warfare is the one in which you never have to fight your enemy in actual combat. Thus, psychological warfare tactics are also marketed as a self-improvement sales tool for ambitious, materialistic people that plot to maneuver into positions of power in order to gain advantages in business, relationships and socio-political influence. Essentially, this is to secretly scheme and manipulate others in a well thought out strategy in order to get what you want from the power structure and to get access to other people’s resources. Generally it is desirable to achieve these goals in such way that the plotters remain undetected in their climb to power and position, without anyone even realizing the entire situation was a calculated scheme.
In the past such Machiavellian schemes were thought to portray the devious behavior of criminals and despots, believed to have undesirable and even appalling human character traits. Today these extremely negative behaviors are normalized and commonly applied in the business operations of the everyday world, by financially rewarding people that act as predators. Thus, the current terrain requires that we open our mind to comprehend the most common concepts of psychological warfare, because all of us are being exposed to it every day. What are the predator minds scheming?
Invoke Fear: The purpose is to manufacture as much fear as possible to create dread and terror in the minds of the people, so that they will avoid rising in groups and instead become weaker and disabled. To maintain this continual state of fear buried in life’s many stressors, as well as perceived threats to survival, means activating the fight or flight reaction in the human nervous system and brain. Eventually this takes a serious toll on the overall health of the body and sanity of the mind, as it rapidly breaks down immunity, increases disease states and drives painful mental imbalances.
Division to Confusion: When the opponent group targeted for attack is large, cooperative and unified in their forces, by separating them from one another or separating them into smaller units, the entire group is more easily defeated and controlled. When the separation into smaller units is successful, the attack is then on their common bonds of unity. Seeking to confuse them with fear and misinformation so they will not know which way to turn, what to expect or who to trust. In the stewardship of any project or organization, this is a critical concept to understand.
Demoralization: A process in psychological warfare with the objective to erode morale or dehumanize those perceived as the enemy. By intending to destroy their dignity and morale, it can encourage them to retreat, surrender, or defect rather than confront them or to defeat them in physical combat. Demoralization and dehumanization is the most important tool of psychological warfare and intentional torture used to break a person. Demoralization is most commonly implemented through various forms of fabricated propaganda to weaken people, while dehumanization is commonly used by the satanic agenda to mock and defile human dignity or attack the spirit within the person.
Ignorance vs. Intelligence: Those that have the most knowledge, intelligence and conscious awareness of what is really happening in world events will have the most strategic advantage. Those that do not have access to accurate awareness of events or truthful knowledge, but instead are manipulated and deceived to believe false impressions and illusions, will be at a greater disadvantage. Knowledge of the truth is power. Managing intelligence and controlling access to information includes supplying the perceived enemy or opponent with disinformation, in order to trick them into making the wrong decisions based on lies. In the current warfare climate diminishing easy access to open source knowledge and sharing of information freely within the global community, it is an important concept to understand.
Overwhelm and Wear Down: Constantly use greater strength in applying heavy forces that overwhelm your opponent by creating never-ending issues that are designed to wear him down and erode his will power and resiliency. Bureaucracies, impossible compliance, insurance, tax and legal channels that keep people bogged down in never-ending paperwork, long lists and cues, under the threat of intimidation, or threat to financial security or persecution. This is also carried out in legal forms as ‘death by 1000 papercuts’, through the increase of overwhelming problems and burdensome bills. When people’s hopes are crushed and their expectations for their life are confused and burdened, eventually they become so drained they have no energy to refuse the constant attempts of subjugation and just give up.
How many of these tactics of psychological warfare that are normalized in our everyday society can you recognize that are currently impacting the quality of your life? Knowing that these strategies are being implemented, what can you do to change how you approach the control structures and the employed people that blindly follow a boilerplate that unconsciously reinforce these divide and conquer schemes?

4 notes
·
View notes
Text
5 Reasons to Build a Custom CRM

A CRM system is an essential tool for businesses to manage customer interactions effectively. There are numerous CRM software options available in the market.
In this article, we’ll delve into five reasons why it’s wise to invest in building a custom CRM. Firstly, custom CRMs are tailored to meet specific business needs and workflows, leading to more efficient processes and increased productivity. Secondly, custom CRMs offer enhanced security measures and better data privacy protection. Thirdly, a custom CRM can integrate seamlessly with your existing systems, providing a unified view of customer data.
Finally, building a custom CRM can be more cost-effective in the long run, as businesses can avoid ongoing licensing fees and expensive customization costs associated with off-the-shelf software.
Unique Functionalities One of the primary benefits of creating a custom CRM system is the ability to add unique functionalities that are customized for your business. Pre-built CRM software may not provide the flexibility required to tailor your customer interactions and user experience. With a custom CRM, you can add personalized dashboards, customized reports, and workflows that match your business processes.
This can significantly improve productivity and efficiency, as well as provide a competitive advantage over businesses that use generic CRM solutions.
Integration with Another System Building a customized CRM system provides an opportunity to integrate it seamlessly with other essential business systems. Pre-packaged CRM solutions may not offer the required level of integration, which can lead to disconnected data silos and inefficient processes. A bespoke CRM solution can be designed to work in tandem with other critical systems, such as ERP, accounting, and marketing automation software.
This creates a unified view of customer data, streamlines operations, and eliminates manual data entry errors. Customized integrations also help automate repetitive tasks, freeing up valuable employee time.
Security Data One of the most significant advantages of creating a custom CRM system is the ability to implement robust security measures to protect customer data. Pre-built CRM software can have vulnerabilities that leave customer data at risk of external threats, which can compromise customer trust.
A custom-built CRM system allows businesses to design security protocols and data privacy policies that align with their specific needs. This includes implementing encryption, access control, and data backup and recovery measures.
Eases Scaling Process Creating a custom CRM solution can help businesses ease the scaling process as they grow. As a company expands, its customer management requirements become more intricate, and out-of-the-box CRM software may not be adequate to handle the increased workload.
With a customized CRM solution businesses can tailor their CRM system to meet their evolving needs, adding features, functionalities, and integrations as required without switching to a new CRM platform entirely.
What is CRM Application Development? CRM application development is the process of building a customized customer relationship management system for businesses. Such systems are designed to help businesses manage their customer interactions, optimize their sales and marketing processes, and improve customer retention rates. Although there are off-the-shelf CRM solutions available, a custom CRM application provides businesses with a bespoke solution that caters to their unique needs.
The development process for a custom CRM application typically involves several stages. Firstly, a comprehensive analysis is conducted to understand the specific challenges and opportunities that the CRM system needs to address. This includes an evaluation of the current processes, data structures, and integrations that are in place.
Next, the development team creates a customized solution that addresses the identified challenges and opportunities. This may involve the creation of new features, the integration of existing software and systems, and the implementation of tailored security and privacy measures.
The coding and testing phases follow the design phase, with the development team creating the software and testing it thoroughly to ensure that it meets the business’s requirements and functions correctly.
Conclusion Creating a customized CRM solution provides businesses with a wide range of benefits that cannot be found in off-the-shelf CRM software. A tailored CRM application offers unique features and functionalities that address a business’s specific needs, enhancing the effectiveness and efficiency of its sales and marketing processes.
Moreover, Custom CRM Applications can be seamlessly integrated with existing software and systems, streamlining operations and saving time and resources. Additionally, custom CRM systems offer advanced security features that protect customer data, reducing the risk of data breaches and ensuring compliance with data protection regulations.
#crm software#crm development#crm solutions#crm software development company#CRM Software Development Service#crm implementation#crmintegration#CRM#crm development company#web development company#web development services
2 notes
·
View notes
Text
Oleksandr Kosovan remembers vividly the morning he left his home to go to work and didn’t know if it would still be there when he returned. He was jolted awake at 4 am by the sound of rockets striking Kyiv, and his immediate thought was, “I’ll probably never come back to my home. Mentally, I said goodbye to all of my belongings. And then I went to the office.” It was February 25, 2022, the day after Russian forces launched a large-scale invasion of Ukraine, escalating a conflict that had simmered since Russia’s 2014 annexation of Crimea.
Kosovan made his way into Kyiv’s center, near the Olympic National Sports Complex. He was headed to the office of his 15-year-old software company MacPaw, which makes applications for Macs and iPhones. As CEO, he had urged some of his 500 staff to flee the city when the threat of war escalated. But hundreds had opted to stay. His first task that day was to convert the office into a temporary shelter for MacPaw employees.
“I didn’t think my body was even capable of lasting four or five days without sleep and real food, but it was running on adrenaline and pure rage,” he says of those first days of the war. A year later, MacPaw has kept the lights on, and Kosovan’s home still stands. The company’s staffers have been more unified than scattered by the war’s steep challenges and have even managed to maintain a sense of normalcy, exchanging Ukrainian memes via Twitter and Telegram and still keeping in high spirits.
Kosovan is far from the only Ukrainian startup founder with tales of resilience and unexpected wartime productivity over the past year. Even as coders and entrepreneurs worked from underground bomb shelters and through rolling electrical blackouts, many managed to ship software updates. But Ukraine’s future is still unclear, adding to the risks that already come with keeping a technology startup alive.
Hacking in the Dark
I first met Julia Petryk by chance last June, after she had traveled 15 hours by train from Kyiv to Poland and then taken an international flight to attend Apple’s WWDC conference in Cupertino, California. We spoke outside Apple’s sleek, glass-walled coffee shop, standing in glaring sunlight, the idyllic scene a stark contrast from the war-torn parts of Ukraine. Since then I’ve kept in touch with Petryk and recently spoke to or corresponded with half a dozen tech founders and workers from Ukrainian companies, asking about life in Ukraine’s startup scene over the past year.
Petryk runs communications at MacPaw and is a cofounder of the Ukrainian PR Army, an ad hoc group of Ukrainian PR and marketing professionals trying to combat Russian propaganda by sending out pro-Ukranian missives to journalists and governments. She describes a year of severe disruption, and not the kind that Silicon Valley founders typically laud. She has worked from bomb shelters and coffee shops with backup generators, and has walked home through Kyiv in pitch-black darkness, decked in reflective gear.
“When you have all this news trickling in every day, it can be a bit depressing. But people keep adapting,” Petryk says. “There’s no way out except to work for the future and fight for the future.”
On October 10, Petryk emailed me from a bomb shelter in Kyiv: “Russians hit dozens of missiles at Ukraine this morning. Civilians killed again.”
Prior to this, she and I had been chatting about a Slack plugin that MacPaw engineers had built called TogetherApp, which enables quick check-ins and location drops between colleagues. The pings flew among the MacPaw team that day.
Thousands of Ukrainian tech workers ended up relocating to neighboring Poland or to Portugal, which granted temporary protection permits to Ukrainian refugees in the early days of the war. Many more stayed behind.
In the days following the invasion, Alyona Mysko, the founder and chief executive of an accounting startup called Fuelfinance, temporarily relocated her company’s home base from Kyiv to a bomb shelter in the western Ukrainian city of Lviv, some 500 kilometers away, and encouraged remote work. But many did not want to leave Ukraine. “We all have this understanding that when you stay in this country, you support the economy,” she says. “And a lot of our team members have families and homes here.”
By October, Fuelfinance had eschewed remote work and pivoted back to office life, toiling from a coworking space in Kyiv called LIFT99. Mysko had made the same journey Petryk had back in June—traveling 15 hours by train to Poland before flying to a tech conference in California—when news broke that Russia had unleashed a massive attack on Ukraine’s power grid, resulting in widespread blackouts.
“It was impossible to connect with my family,” Mysko says. “But in the office we had alternative sources of energy, and we had Starlink, so we were still able to connect for work. It made us realize how important it was to have backup generators, which really sped up the end of remote work for us,” she says with a wry laugh.
Backup generators and SpaceX’s Starlink satellite internet service—every founder who spoke to WIRED said they were now critical to their operations. Some had the foresight to purchase generators before the invasion.
Others, like Sofiia Shvets and Vlad Pranskevičius, who jointly founded an AI image editing startup called Let’s Enhance, raced to supply their staffers after the fact, purchasing several large power banks for employees scattered around Ukraine for around €550 (about $580) a piece. Each can supply six to seven hours of power to personal devices, though not enough for home appliances.
“It’s all very strange sometimes,” says Shvets, who is now based in San Francisco. “We’ll have a video call with one of our product managers who has Starlink internet, so he can join the call, but he’s in total darkness, surrounded by candles, because he doesn’t have electricity. And I’m like, ‘Um, Dennis, how’s it going?’”
Since the spring of 2022, Ukraine has relied heavily on Starlink satellite internet terminals, tens of thousands of which were donated by SpaceX, with some support from the US government. SpaceX CEO Elon Musk said in October that the company would no longer fund Starlink service in Ukraine, and he asked the Pentagon to pick up more of the cost before reversing himself in a tweet.
“Many people here and across the world were pissed off about some of his posts,” says Pranskevičius, who is based in Kyiv. “But what we’ve seen is that Starlink has continued to work. It’s been invaluable to most individuals and also to people on the front line, where there might be no connectivity at all.”
An Uncertain Future
Let’s Enhance has continued to grow, despite the challenges its founders and staff face. One colleague left to go fight on the front lines, and another signed up to work on military technology, joining the approximately 7,000 tech professionals who joined the ranks of the Armed Forces of Ukraine. One year ago, the company had 27 employees; now, it says it has more than 40.
But Let’s Enhance is in the minority. According to a 2022 report from TechUkraine, an organization that supports startups in the country, companies are feeling the heat of war. While 43 percent of teams surveyed remained the same size, 37 percent of founders say they’ve had to reduce headcount. And more than 90 percent of Ukrainian startups have indicated they would need more financial support in order to survive the war.
Data from research firm PitchBook shows that early-stage startups in Ukraine raised a collective $17 million in seed or Series A funding in 2022, compared to $14.1 million in 2021. Early-stage funding this year has already surpassed that in the last quarter of 2022, including $1 million recently raised by Fuelfinance.
But despite promising signs, the broader prospects for Ukraine’s businesses are murkier. In September, The Wall Street Journal reported that, while Ukrainian companies in 2021 raised a total of $832 million in venture capital and from private equity, which typically invests larger sums, one analyst has estimated that the number of Ukrainian VC deals was down by at least 50 percent in 2022.
Let’s Enhance’s last fundraising round was for $3 million in October 2021, and its founders planned to stretch that throughout 2022 as they focused on a new product. They may try to raise more funding this year, taking on macroeconomic headwinds, in addition to the instability of war, that have slowed startup investment.
Still, Shvets is optimistic about fundraising. Several funds have cropped up in support of Ukrainian tech companies, both in the private sector and from governments. Last year the European Commission pledged €20 million (about $21 million) in support of tech companies in Ukraine. Some private investors are bolstered by the fact that many Ukrainian startups sell their software in the US.
“I would say the narrative has definitely changed since last year. When the war started, we were all in shock, and so were our investors,” Shvets says. “They were asking, ‘What’s going to happen with Ukraine?’ But we haven’t had any production issues, and right now I actually feel like we have a lot of support.”
Dmitry Dontov, the chief executive and founder of data protection company Spin Technology, also says investors seem comfortable to keep working with startups with a heavy Ukrainian presence. Shortly after the invasion, Dontov, a Moldovan based in Silicon Valley, supplied his Ukrainian research and development team with generators and set up a safe house for them in the village of Koncha-Zaspa, about 33 kilometers from Kyiv. He relocated a third of the staff to an office in Portugal.
“Initially, investors were worried. They were asking, ‘How many lines of code have been written last month?’” Dontov says. “But over time, I think investors saw that we were taking all the actions necessary to maintain performance.”
Not all startups have fared so well. Oleksandr Kosovan, the MacPaw cofounder, also invests in other startups through a fund called SMRK. It invested $1.5 million in a Ukrainian robotics startup just this week. But Kosovan says that at least two of the fund’s portfolio companies shut down within the past year.
One of them was Seadora Seafood, a Kyiv-based fish delivery startup founded in 2019. The company transported some of its cargo by air and could no longer operate within Ukrainian air space. Another startup selling casual clothing is still operating but is struggling; as soon as the war began, Kosovan says, “the demand for such things was reduced to almost zero.”
In the context of war, necessities come into sharper focus. So do borders, and bonds with coworkers, and glimpses of the future, even if they appear in the form of a candlelit Zoom call or a flash of reflective clothing on a dark city street.
3 notes
·
View notes
Text
Top 10 Tools for Digital Transformation Success

Digital transformation specialist relies on various tools to improve efficiency, automate workflows, and enhance customer experiences. Here are the top 10 tools that drive digital transformation success:
1. Cloud Computing Platforms
Tools: AWS, Microsoft Azure, Google Cloud
Enable scalability, security, and remote accessibility.
Power data storage, machine learning, and enterprise applications.
2. Customer Relationship Management (CRM)
Tools: Salesforce, HubSpot, Microsoft Dynamics 365
Centralizes customer data for improved sales, marketing, and support.
Uses AI-driven insights to enhance customer engagement.
3. Enterprise Resource Planning (ERP)
Tools: SAP S/4HANA, Oracle NetSuite, Microsoft Dynamics 365 ERP
Integrates finance, HR, supply chain, and operations into a unified system.
Enhances decision-making with real-time analytics.
4. Robotic Process Automation (RPA)
Tools: UiPath, Automation Anywhere, Blue Prism
Automates repetitive tasks, reducing manual effort and errors.
Improves efficiency in finance, HR, and customer service processes.
5. Business Intelligence & Data Analytics
Tools: Power BI, Tableau, Google Looker
Visualizes business data for actionable insights.
Uses AI-powered analytics for predictive decision-making.
6. Cybersecurity & Compliance
Tools: Palo Alto Networks, Cisco Security, Okta
Protects digital assets from cyber threats and ensures compliance.
Implements multi-factor authentication (MFA) and zero-trust security models.
7. Collaboration & Productivity
Tools: Microsoft 365, Google Workspace, Slack, Zoom
Enhances remote work and real-time collaboration.
Integrates cloud storage, messaging, and video conferencing.
8. Artificial Intelligence & Machine Learning
Tools: IBM Watson, Google Vertex AI, OpenAI API
Automates decision-making, enhances customer service, and drives predictive analytics.
Personalizes customer experiences through AI-driven insights.
9. Low-Code/No-Code Development
Tools: Mendix, OutSystems, Microsoft Power Apps
Enables non-developers to create applications quickly.
Speeds up digital transformation by reducing dependency on IT teams.
10. Internet of Things (IoT) & Edge Computing
Tools: AWS IoT, Google Cloud IoT, PTC ThingWorx
Connects devices and sensors for real-time monitoring.
Optimizes supply chain, manufacturing, and smart infrastructure.
How This Relates to Operations Excellence
Since you are in Operations Excellence Management, tools like RPA, ERP, and Business Intelligence can significantly enhance process efficiency and automation in your field. Implementing these can help you drive cost reduction, productivity gains, and data-driven decision-making in operations.
Would you like recommendations on specific tools that fit your industry or current role?
0 notes
Text
Future Trends in Salesforce CRM Testing for the BFS Sector
The banking and financial sector relies on robust CRM (customer relationship management) systems for several reasons. It includes improving customer experience, streamlining operations, and ensuring legal compliance. Salesforce CRM is the best choice for institutions. This is due to its scalability, adaptability, and industry-specific proficiencies.
As the BFS sector is evolving constantly, Salesforce CRM testing services are essential. It's because it ensures compliance and seamless functionality.
In this blog, you will learn about the future trends in Salesforce CRM testing. It also includes how they align with the dynamic needs of the BFS sector.
Shift Towards AI-Driven Testing
The integration of AI into Salesforce testing solutions is transforming how CRM platforms are tested. AI-powered tools can replicate real-world scenarios and optimize testing processes. Not only this, but they can also predict potential system failures. When it comes to financial services, system reliability and customer trust are crucial. Thus, adopting AI-driven Salesforce testing services ensures compliance and better performance.
For example:
Optimizing Test Case: Accurate algorithms generate and prioritize test cases with respect to risk factors and historical data. Thus, ensuring a comprehensive evaluation of key Salesforce CRM functionalities.
Predictive Analytics: AI helps in identifying potential risks before they occur. Thus, improving test accuracy and reducing downtime.
Improved Security Testing
Cyber threats and data breaches are the two key concerns for financial institutions. If you are in the financial sector, opting for security-focused Salesforce testing services will be an ideal choice. Security testing for Salesforce CRM is becoming more advanced to address the challenges listed below:
Penetration Testing: Simulating cyberattacks to detect vulnerabilities in the Salesforce ecosystems.
Access Control Testing: Verifying role-based permissions and access to avoid unauthorized activities.
Data Encryption Validation: It ensures that confidential customer data is secure and encrypted.
Integration Testing for Omnichannel Banking
The financial sector is shifting towards omnichannel banking. Thus, Salesforce CRM must integrate with several third-party applications, platforms, and APIs. Integration testing is becoming a key aspect of Salesforce testing services. When it comes to financial institutions and banks, integration-focused testing is essential. It ensures customer satisfaction and operations.
It also ensures:
User Experience Consistency: Unified customer experiences across mobile, web, and in-branch interactions.
Data Synchronization: Accurate and real-time data flow across systems.
Cross-Platform Compatibility: Ensuring Salesforce CRM works flawlessly with legacy systems and emerging technologies.
DevOps Integration in Salesforce Testing
Implementing DevOps practices in financial institutions is essential. It plays a vital role in Salesforce CRM testing services process. Salesforce testing services driven by DevOps ensure resilience and agility in the finance industry. When it comes to Salesforce CRM testing services, the integration of DevOps offers several benefits.
It includes:
Enhanced Collaboration: Better coordination between QA and development teams ensures better results.
Real-Time Feedback: Constant monitoring and testing allow quick identification and solving of issues.
Quick Release Cycles: Automated testing and deployment pipelines reduce time to market.
Significance of Legal Compliance Testing
The financial sector is subject to strict regulations. This includes PCI DSS, GDPR, and Basel III. Salesforce CRM systems should align with these legal standards. This is to avoid fines and ensure data integrity. The legal landscape is evolving continuously. Thus, the demand for specialized Salesforce CRM testing services that meet financial compliance will increase.
Salesforce CRM testing services use compliance validation tools. It ensures that the Salesforce configurations meet industry standards.
Automated compliance testing frameworks are becoming a key component of the Salesforce CRM testing services. Thus, lessening manual efforts and improving accuracy.
Enhanced Focus on Customer Experience (CX) Testing
Customer experience and satisfaction play a vital role in the banking industry. Salesforce CRM plays a key role in providing efficient and customized services. Future Salesforce CRM testing services will prioritize client-centric testing. This improves satisfaction and loyalty.
Customer experience (CX) testing includes:
Accessibility Testing: It ensures that even individuals with disabilities can use CRM. The testing also ensures to have WCAG standards.
User Journey Testing: It validates end-to-end customer journeys to make sure to have seamless interactions.
Performance Testing: This testing assesses system responsiveness and speed during high transaction volumes.
Automation-First Approach
The usage of automation tools is changing the Salesforce CRM testing services. Automation reduces human error, enhances efficiency, and boosts the deployment cycle. Automation-first Salesforce CRM testing services are essential for financial institutions. It can adapt to market demands quickly while maintaining quality.
Key trends are:
CI/CT: CI/CT stands for Continuous Integration/Continuous Testing. Automate testing within the CI/CD pipelines. This ensures quicker delivery and minimal disruptions.
Scriptless Test Automation: Tools that allow non-technical testers to create test scripts using drag-and-drop interfaces.
Usage of Agile Testing Methodologies
Agile methodologies are reshaping Salesforce CRM testing services through iterative development and constant feedback. It helps financial institutions to stay ahead in the competitively changing landscape.
Agile testing trends consist of:
Test-Driven Development (TDD): It includes writing tests prior to developing features. This is to ensure alignment with the essential requirements.
Exploratory Testing: It allows testers to find defects beyond predefined test cases.
Behavior-Driven Development (BDD): It bridges the gap between technical and business teams via collaborative testing methods.
Cloud-Native Testing Strategies
Salesforce functions in a cloud environment. This makes cloud-native testing strategies essential. With cloud-native Salesforce testing services, financial institutions use Salesforce testing solutions while avoiding risks.
It includes:
Latency Testing: This testing assesses the responsiveness of the system under diverse network conditions.
Scalability Testing: It ensures the CRM can manage the increasing user and data volumes without performance degradation.
Disaster Recovery Testing: This testing verifies backup and restoration mechanisms in case of system failures.
Rise of Blockchain Testing
Salesforce CRM systems are becoming integrated with blockchain. This is for improved transparency and security. Salesforce testing solutions focused on blockchain will play a key role in the financial industry's digital transformation.
Testing these integrations includes:
Data Integrity Testing: It verifies that the data stored in the blockchain is tamper-proof.
Smart Contract Validation: It makes sure that blockchain transactions align with the essential terms and conditions.
Interoperability Testing: It assesses smooth interaction between the blockchain network and Salesforce CRM.
Final Words
Salesforce CRM testing services have a promising future in the banking and financial sector. The evolution of testing solutions is helping companies to solve unique challenges. This ranges from AI-driven innovations to agile methodologies.
In the financial sector, leveraging Salesforce testing solutions is essential. It ensures operational efficiency, customer satisfaction, and legal compliance.
Today, technology is reshaping the financial landscape. Thus, partnering with the best Salesforce CRM testing services provider would be best. They will help you stay ahead in the competitive industry.
Are you looking forward to partnering with the ideal Salesforce CRM testing services provider? If yes, then get in touch with the Qualitest team. They offer the best service to ensure the reliability and performance of Salesforce applications. Additionally, they also ensure the functionality of the Salesforce application. Their team has expertise in several Salesforce clouds. It includes CPQ, sales cloud, marketing cloud, commerce cloud, and sales cloud.
0 notes
Text
Cybersecurity Market Dynamics: Key Players, Innovations & Investments
The global cyber security market size is projected to reach USD 500.70 billion by 2030, registering a CAGR of 12.9% from 2025 to 2030, according to a new study by Grand View Research Inc. The global market is anticipated to be driven by the growing cyber threats and advanced malware threats across different verticals. In recent years, disruptive and emerging technologies in the banking, retail, information technology, defense, and manufacturing sectors have provided new capabilities, facilitated automation, and improved working conditions. They have, however, emerged as powerful forces in the evolution of the global threat landscape of exploits, vulnerabilities, and malware. Advancements in emerging technologies, such as Artificial Intelligence (AI), Machine Learning (ML), big data analytics, Internet-of-Things (IoT), 5G, edge computing, and cloud computing, are allowing market players to introduce new solutions based on these technologies, attract potential business clients, and expand their revenue streams.
For instance, in April 2023, Google, Inc. introduced Cloud Security AI Workbench, Sec-PaLM. This new model encompasses various security intelligence, such as threat indicators, & research on software vulnerabilities, and offers AI-powered tools to assist and act on cyber security threats. The growing preference for cyber security solutions & services in the IT & telecom industry is prompting market players to enhance their product portfolio & improve their customer base. The ongoing digitalization wave has resulted in significant changes in the telecom sector. Telecom companies are investing in the latest technologies, such as 5G, IoT, and cloud, which is expected to generate enormous opportunities for the IT & telecom cybersecurity market. In addition, as Bring-Your-Own-PC (BYOPC) becomes a necessity, content migration; and device management is expected to get more critical due to remote management.
This is expected to increase the number of endpoint devices, thereby fueling the adoption of unified cyber safety solutions. The cloud segment is expected to register a CAGR of 15.9% from 2025 to 2030. The shifting end-user companies' focus toward cloud-based solutions owing to minimum hardware requirements, low operating costs, and diverse solution availability is supporting segment growth. The market players are establishing strategic partnerships with cloud technology providers to develop DDoS protection solutions. For instance, in August 2021, Radware, Inc., a cyber security company, partnered with Internap Holding LLC (INAP), a hybrid IT & enterprise cloud solutions company, to deploy its DDoS protection and Cloud Web Application Firewall (WAF) for client companies across the globe.
Cyber Security Market Report Highlights
The hardware segment is expected to exhibit a high growth rate of 11.7% over the forecast period. Hardware assists organizations in upgrading their IT security by enabling real-time monitoring of threats and offering protection by preventing threats from entering computing systems, supporting the adoption of hardware solutions
The cloud security segment is anticipated to register a CAGR of more than 15.9% from 2025 to 2030. Increasing adoption of cloud technologies and remote workforces is propelling the growth of cloud security solutions
The IDS/IPS segment is expected to register a CAGR of around 13.4% over the forecast period. The increasing spending on IT security and proliferation of network security products is propelling the segment growth
The SMEs segment is anticipated to exhibit the highest CAGR over the forecast period. The rising concern of cyber threats and the availability of low-cost cyber security solutions are propelling the segment growth
The healthcare segment is anticipated to exhibit the highest CAGR over the forecast period. Healthcare is an appealing target for cyber-attacks as medical data is more valuable than credit card or banking information. In addition, the recent digital transformation of the healthcare industry has increased the frequency of cyber-attacks. Due to this, the market is witnessing growing demand in the healthcare sector
The cyber security industry in the Asia Pacific region is anticipated to register the highest CAGR over the forecast period. The rapid digital transformation, increasing public & private investment in cyber security solutions, and significant penetration by global market players are driving the growth of the regional market
Cyber Security Market Segmentation
Grand View Research has segmented the global cyber security market report based on offering, security, deployment, organization size, solution, end use, and region
Cyber Security Offering Outlook (Revenue, USD Billion; 2017 - 2030)
Hardware
Software
Services
Professional Services
Consulting
Governance, Risk, and Compliance (GRC)
Incident Response and Readiness
Implementation and Integration
Training & Education
Others
Managed Services
Managed Detection and Response
Managed Protection and Controls
Managed Security Functions
Others
Cyber Security Security Outlook (Revenue, USD Billion; 2017 - 2030)
Endpoint security
Cloud Security
Network Security
Application Security
Infrastructure Protection
Data Security
Others
Cyber Security Deployment Outlook (Revenue, USD Billion; 2017 - 2030)
Cloud
On-premises
Cyber Security Organization Size Outlook (Revenue, USD Billion; 2017 - 2030)
Large Enterprises
SMEs
Cyber Security Solution Outlook (Revenue, USD Billion; 2017 - 2030)
Unified Threat Management (UTM)
Intrusion Detection System/Intrusion Prevention System (IDS/IPS)
Data Loss Prevention (DLP)
Identity and Access Management (IAM)
Security Information and Event Management (SIEM)
DDoS
Risk and Compliance Management
Others
Cyber Security End Use Outlook (Revenue, USD Billion; 2017 - 2030)
IT and Telecommunications
Retail and E-Commerce
BFSI
Healthcare
Government and Defense
Manufacturing
Energy and Utilities
Automotive
Marine
Transportation and Logistics
Others
Regional Outlook (Revenue, USD Billion; 2017 - 2030)
North America
US
Canada
Mexico
Europe
UK
Germany
France
Russia
Asia Pacific
China
India
Japan
Australia
South Korea
Indonesia
Singapore
Malaysia
Latin America
Brazil
MEA
UAE
South Africa
KSA
Israel
Key Players of Cyber Security Market
Fortinet, Inc.
IBM Corporation
Microsoft
BAE Systems Plc
Broadcom, Inc.
Centrify Corporation
Check Point Software Technology Ltd.
Palo Alto Networks, Inc.
Proofpoint, Inc.
Sophos Ltd
Order a free sample PDF of the Cyber Security Market Intelligence Study, published by Grand View Research.
0 notes
Text
Best Commerce Solutions Company in UK: Elevating Businesses to New Heights
In the fast-evolving digital landscape, businesses in the UK require robust commerce solutions to stay competitive. The demand for seamless, scalable, and innovative commerce solutions has never been higher, as businesses seek to enhance customer experiences, streamline operations, and boost sales. Choosing the best commerce solutions company in the UK can be the difference between stagnation and exponential growth.
Understanding Commerce Solutions
Commerce solutions encompass a wide array of services designed to facilitate transactions, improve customer engagement, and optimize business processes. These include:
E-commerce Development – Designing and developing feature-rich online stores.
Payment Gateway Integration – Ensuring seamless, secure, and multiple payment options.
Customer Relationship Management (CRM) – Enhancing customer interactions and retention.
Enterprise Resource Planning (ERP) – Streamlining business operations for efficiency.
Supply Chain & Inventory Management – Optimizing logistics and stock control.
Omnichannel Solutions – Unifying online and offline sales channels for a seamless experience.
Businesses looking for the best commerce solutions company in the UK must ensure that their chosen provider can cater to their specific needs with a tailored, scalable, and future-proof approach.
Key Features of the Best Commerce Solutions Company in the UK
To stand out in a competitive market, a top-tier commerce solutions provider should exhibit the following qualities:
Innovation & Technological Expertise
The digital commerce landscape is constantly changing, with new technologies reshaping consumer expectations. The best commerce solutions company in the UK must leverage cutting-edge technologies such as AI-driven analytics, blockchain for secure transactions, and cloud-based infrastructure to provide scalable solutions.
Customization & Scalability
Every business is unique, and a one-size-fits-all approach rarely works. A superior commerce solutions provider should offer customizable solutions tailored to a business’s specific needs, allowing for seamless scaling as the business grows.
Security & Compliance
With rising cybersecurity threats and stringent regulatory requirements, security is paramount. A top commerce solutions company should ensure robust security protocols, encryption, and compliance with regulations such as GDPR and PCI DSS.
Seamless Integration
Commerce solutions should seamlessly integrate with existing business software, including CRM systems, ERP platforms, and third-party applications, ensuring smooth operations without disruptions.
Data-Driven Insights
Leveraging data analytics can drive informed decision-making. The best commerce solutions provider in the UK should offer insightful reports and analytics to help businesses refine their strategies and optimize customer experiences.
Exceptional Customer Support
Even the most sophisticated commerce solutions require continuous support and maintenance. A reliable commerce solutions company should provide 24/7 customer support, quick issue resolution, and proactive assistance.
Benefits of Choosing the Right Commerce Solutions Company
Partnering with the right commerce solutions company in the UK offers numerous advantages:
Enhanced Customer Experience – Personalized and seamless shopping experiences drive customer loyalty.
Increased Sales & Revenue – Optimized platforms lead to higher conversion rates.
Efficient Business Operations – Automated processes save time and reduce operational costs.
Competitive Advantage – Staying ahead with innovative technology fosters business growth.
Secure Transactions – Robust security measures protect customer data and transactions.
Industries Benefiting from Commerce Solutions
Commerce solutions cater to various industries, each with unique requirements:
Retail & E-commerce – Online stores, marketplaces, and omnichannel strategies.
Finance & Banking – Secure payment processing and digital transactions.
Healthcare – Online appointment bookings and telemedicine commerce.
Manufacturing – Supply chain optimization and inventory management.
Hospitality & Travel – Online bookings, reservations, and digital payments.
Choosing the Best Commerce Solutions Company in the UK
Selecting the best commerce solutions provider requires careful consideration. Here are key steps to ensure the right choice:
Define Your Business Needs
Identify your specific requirements—whether it's an e-commerce platform, CRM integration, or payment gateway solutions.
Evaluate Experience & Portfolio
Look for a company with a proven track record of delivering successful commerce solutions to businesses similar to yours.
Assess Technology & Innovation
Ensure the provider uses modern, scalable technologies that align with your business goals.
Read Client Testimonials & Reviews
Customer feedback and case studies provide insight into a company's reliability and service quality.
Consider Pricing & ROI
While cost is a factor, focus on the long-term value the solution brings to your business rather than just the initial price.
Check Support & Maintenance Services
Post-deployment support is crucial for ensuring smooth operations and handling any technical issues.
Final Thoughts
The best commerce solutions company in the UK is not just a service provider but a strategic partner in business growth. By leveraging cutting-edge technology, ensuring seamless integration, and prioritizing security, these companies help businesses enhance customer experiences, streamline operations, and drive higher revenue. Choosing the right partner can transform the way businesses operate in an increasingly digital world, ensuring success and sustainability for years to come.
0 notes
Text
Transforming Energy Management: A Leading Clean Energy Provider’s Journey with Oracle Cloud Fusion and Dataplatr
From Oracle EBS to Oracle Fusion: Modernizing Solar Energy with Oracle Cloud Solutions
Introduction
The Company, a trailblazer in clean energy solutions, has consistently demonstrated its commitment to innovation and sustainability. As the nation’s leading residential solar energy provider, the Organization recognizes the importance of modernizing its business operations to maintain its leadership and drive further growth. By adopting Oracle Cloud Fusion, with critical facilitation by Dataplatr, the Organization embarked on a transformative journey to overhaul its Energy management systemenergy management and operational processes. This collaboration not only improved operational efficiency and scalability but also enabled advanced data integration. This article explores the journey in detail, emphasizing how these technological advancements align with the organization’s broader mission to create a sustainable future powered by clean energy.
A Leader in Clean Energy
With over one million customers and a commanding 15% market share, the Organization is at the forefront of the U.S. solar energy industry. The company’s innovative solutions, such as home solar and battery storage, have empowered households to reduce energy costs and contribute to environmental sustainability. By integrating Oracle Cloud Fusion into its operations, the Organization has aligned its technological capabilities with its mission of delivering affordable, reliable, and Clean energy. The adoption of Oracle Cloud Fusion reflects the organization’s strategic commitment to operational excellence, ensuring that its processes remain efficient, scalable, and adaptable to evolving industry demands. Additionally, the shift from Oracle EBS to Fusion Cloud demonstrates the organization’s commitment to digital transformation in energy, improving its ability to monitor and optimize operations through a cloud based energy monitoring system
The Challenge: Managing Complex Systems
Before transitioning to Oracle Cloud Fusion, the organization’s operations depended heavily on Oracle E-Business Suite (EBS) and an assortment of other legacy systems. While these systems were reliable in their time, they were not designed to handle the dynamic and evolving needs of a rapidly growing organization. As the Organization expanded its customer base, introduced new service offerings, and navigated an increasingly complex regulatory environment, the limitations of its existing infrastructure became evident.
Key Challenges
Scalability: Adapting to Rapid Growth
With over one million customers and a market share of 15% in the residential solar industry, the Organization faced unprecedented growth in transaction volumes and operational complexity.
The legacy systems, including Oracle EBS, were designed for a smaller scale and struggled to process the increasing number of transactions efficiently.
The lack of scalability not only hampered the organization’s operational efficiency but also slowed its ability to onboard new customers and deliver services promptly.
Data Integration: Fragmented Systems Leading to Inconsistencies
The reliance on multiple, disparate systems created significant data silos.
The lack of a unified data architecture meant that financial, supply chain, and customer-related information were stored in separate systems, often leading to data duplication, inconsistencies, and errors.
Decision-making suffered as teams struggled to piece together a coherent view of the company’s operations from incomplete or mismatched data sets.
Compliance and Security: Keeping Up with Modern Standards
Oracle’s decision to discontinue support for older EBS versions posed a serious challenge for the organization. Without ongoing updates, the systems were vulnerable to security threats and non-compliance with evolving regulations.
Staying compliant with financial reporting standards, such as ASC 606, became increasingly labor-intensive, as legacy systems lacked the automation capabilities required to streamline these processes.
The manual effort to ensure compliance diverted resources from more strategic initiatives and increased the risk of human error.
Innovation Stagnation: A Barrier to Strategic Goals
Legacy systems were not equipped to support the organization’s innovative business model, including its subscription-based offerings and complex revenue recognition needs.
The inability to easily adopt new functionalities or integrate with modern tools limited the organization’s ability to innovate and stay competitive in a rapidly changing market.
Necessity for Change
These challenges underscored the urgent need for a modern, cloud-based solution that could scale with the organization’s growth, integrate data across all functions, and streamline compliance processes. By transitioning from Oracle EBS to Fusion Cloud, the Organization aimed to:
Scale operations seamlessly to support its growing customer base.
Break down data silos to enable real-time insights and unified decision-making.
Ensure compliance with modern standards while improving system security.
Foster innovation by leveraging advanced tools and technologies that align with its strategic goals.
The transition was not merely a technological upgrade but a strategic imperative to future-proof the organization and maintain its leadership in the clean energy sector. This shift enabled the Organization to address the operational bottlenecks of its legacy systems and set the stage for sustainable growth and innovation through Oracle EBS to Cloud Migration.
Why Oracle Cloud Fusion?
The organization’s decision to transition from Oracle EBS to Fusion Cloud was driven by the platform’s robust capabilities and alignment with the company’s need for a modern, scalable, and integrated system. The comparison of Oracle EBS vs Oracle Fusion Cloud made it evident that Fusion Cloud offered superior flexibility, automation, and security to meet the company’s evolving demands. Oracle Cloud Fusion, a comprehensive SaaS (Software-as-a-Service) solution, provided the flexibility and functionality required to meet the organization’s current operational needs and future growth objectives.
Unified Operations
Oracle Cloud Fusion excels in unifying key business processes, allowing organizations to manage financials, supply chain operations, and customer experience seamlessly on a single platform. For the organization, this integration was transformative, enabling the company to eliminate silos between departments and achieve a cohesive operational ecosystem. By centralizing these critical functions, the Organization can now focus on streamlining workflows, enhancing collaboration, and improving overall operational efficiency.
Real-Time Analytics
One of the standout features of Oracle EBS to Fusion Cloud is its ability to provide advanced reporting and analytics in real time. For the company, operating in a fast-paced and data-driven environment, access to real-time data insights is crucial for informed decision-making. With Oracle’s analytics tools, the organization’s leadership can monitor key performance indicators (KPIs), track financial health, and gain actionable insights to address challenges proactively and seize growth opportunities.
Automated Updates
Managing and maintaining legacy systems often demands significant IT resources to handle upgrades and patches. Oracle Cloud Fusion alleviates this burden by delivering automated software updates, ensuring that the Organization always has access to the latest features, performance enhancements, and security measures. This eliminates downtime associated with manual upgrades and allows the organization’s IT team to focus on more strategic initiatives rather than routine maintenance.
Enhanced Security
As a cloud-based platform, Oracle Cloud Fusion is equipped with state-of-the-art security features that ensure data integrity and protect against emerging cyber threats. This is particularly important for the organization, which deals with sensitive customer data, financial records, and operational information. Oracle Cloud Fusion’s compliance with regulatory standards and its built-in security protocols provide the Organization with the peace of mind needed to operate confidently in a digital-first environment.
Cost Efficiency
Transitioning from an on-premises infrastructure to a cloud-based solution significantly reduced the organization’s operational costs. Oracle Cloud Fusion eliminates the need for costly hardware, data center maintenance, and IT labor associated with managing on-premises systems. Additionally, the predictable subscription-based pricing model allows the Organization to better allocate resources and optimize its budget for growth-oriented initiatives.
Scalability and Flexibility
The organization’s rapid growth and evolving business model necessitate a system that can scale and adapt to changing requirements. Oracle Cloud Fusion’s modular architecture and cloud-native design make it easy to add new features, integrate additional business units, or expand to support new markets. This flexibility ensures that the organization’s technological capabilities can grow in tandem with its business.
Positioned for Long-Term Success
By adopting Oracle EBS to Fusion Cloud, the Organization has resolved many of the operational challenges that hindered its growth under legacy systems. The transition has empowered the Organization with the tools to operate more efficiently, adapt to market demands, and achieve its strategic objectives. Oracle Cloud Fusion serves not only as a solution for today’s challenges but also as a foundation for future innovation and success.
This comprehensive adoption of oracle cloud for renewable energy demonstrates how a leading clean energy provider has leveraged cutting-edge technology to reinforce its position as a leader in clean energy. The decision to partner with Oracle underscores the organization’s commitment to operational excellence and its vision of driving sustainable growth.
The Role of Dataplatr: Facilitating the organization’s Seamless Transition to Oracle Cloud Fusion
Dataplatr emerged as a pivotal partner in the organization’s ambitious migration to Oracle Cloud Fusion, bridging the gaps between legacy systems and the advanced capabilities of modern cloud infrastructure. By leveraging its expertise in data integration and transformation, Dataplatr played a fundamental role in ensuring that the organization’s transition was seamless, efficient, and strategically aligned with its business objectives.
The complexity of integrating the organization’s existing systems, including Snowflake and Salesforce, with Oracle Cloud Fusion required a sophisticated approach. Dataplatr met this challenge by implementing advanced tools, such as RiteSync, to streamline and automate critical processes. This ensured that the Organization could continue its operations without interruptions during the migration, while also enabling long-term scalability and enhanced functionality.
RiteSync: Enabling Seamless Data Synchronization and Transformation
RiteSync is a cornerstone of the Organization’s data integration strategy, playing a pivotal role in streamlining backend transformations and automating data ingestion into Snowflake. Its capabilities include:
Real-Time and Historical Data Sync
RiteSync facilitates continuous real-time data synchronization from Oracle Cloud Fusion while managing one-time historical data migrations from Oracle EBS to Fusion Cloud. This ensures seamless integration across platforms.
Automation and Efficiency
With low-code automation, RiteSync eliminates manual intervention in data synchronization, reducing errors and speeding up processes. It handles complex concatenation and mapping tasks effortlessly, ensuring data consistency.
Data Transformation
The tool efficiently handles data cleansing, mapping, and standardization, converting legacy data formats to Oracle Cloud standards. This ensures a smooth data flow into Snowflake and Tableau for analytics and reporting.
Enhanced Monitoring
RiteSync’s intuitive dashboards, such as the Sync Monitor, allow users to track synchronization status, data volume, and any errors in real-time, enabling proactive resolution.
Connections Selection and Creation
RiteSync provides an intuitive interface to create and manage connections with Oracle ERP Cloud and other platforms. The connection setup process includes defining a unique identifier that cannot be modified later, alongside editable fields such as the connection name and keywords for easier identification. Additionally, users can assign specific roles to the connection, which dictate its behavior and functionality within integrations.
Available Adapters
RiteSync supports a wide range of adapters to enable seamless integration across different systems. These include adapters for MS-SQL Database, Oracle Database, Oracle ERP Cloud, Oracle WMS Cloud, AWS S3 (Bucket), and Snowflake. This flexibility ensures that organizations can connect disparate systems effortlessly, creating a unified data ecosystem.
Sync Monitor – Financials and Expenses
The Sync Monitor extends its capabilities to financial and expense modules, delivering a detailed view of relevant objects such as chart of accounts, financial reports, and payment modules. By providing this granular visibility, RiteSync empowers users to ensure accurate and efficient synchronization of critical financial data.
Sync Monitor – General Ledger
The Sync Monitor provides a comprehensive overview of synchronized application objects within the General Ledger module. It highlights key objects such as GL_ACCESS_SET_LEDGERS and GL_ACCOUNT_GROUP_DETAILS, showcasing their synchronization status. This feature also tracks sync frequency, the volume of selected objects, and associated data sizes, offering clear insights into data operations.
Transaction Overview
RiteSync includes a transaction logging feature that records detailed information about synchronization processes. This includes the MasterSync Request ID, table names, load status (e.g., PROCESSED), and timestamps for creation and last updates. These logs cover modules like currencies, assets, and expenses, providing a transparent record of data synchronization activities.
Dashboard Overview
The RiteSync dashboard offers a bird’s-eye view of system performance, highlighting key metrics such as processed, unprocessed, and error counts. Modules like the job scheduler and exception reports are prominently displayed, enabling users to monitor and resolve issues proactively. This centralized view simplifies system management and enhances operational efficiency.
RiteSync is integral to the organization’s transition to Oracle Cloud Fusion, ensuring seamless integration and real-time synchronization between legacy systems and modern platforms like Snowflake. Its robust capabilities enhance data accuracy, operational efficiency, and scalability, aligning with the organization’s vision of driving sustainable growth and innovation through technological excellence.
Reference Architecture
This diagram illustrates a Reference Architecture for managing data workflows, highlighting the integration from of Oracle Fusion and Oracle EBS R12 with Snowflake for data transformation and Tableau for visualization. It also introduces a Bridge Model that ensures seamless synchronization between Oracle EBS and Oracle Fusion, creating a unified and dynamic data ecosystem. Below is a breakdown of its components and processes:
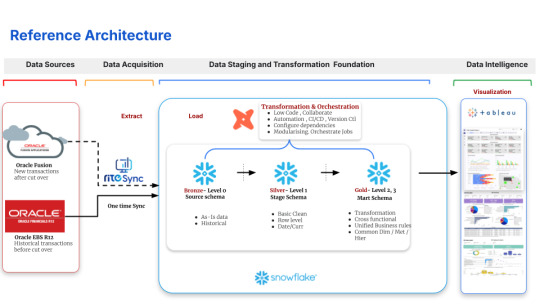
1. Data Sources
Oracle Fusion: Represents new transactions post-cutover, serving as the primary source of ongoing transactional data.
Oracle EBS R12: Contains historical transactions before the cutover, providing essential legacy data for historical continuity in reporting.
2. Data Acquisition
RiteSync Tool: Facilitates the extraction of data from Oracle Fusion and Oracle EBS R12.
New Transactions: Continuous extraction ensures real-time data transfer from Oracle Fusion.
One-Time Sync: Transfers historical data from Oracle EBS R12 into the Snowflake data warehouse for unified processing and analysis.
3. Data Cleansing and Mapping
One of the critical initial steps in the organization’s migration was addressing the quality and format of its legacy data. The data from Oracle EBS and other disparate systems had to be meticulously cleansed and mapped to adhere to Oracle Cloud standards.
Data Cleansing: The process involved identifying and eliminating duplicate records, correcting errors, and ensuring consistency across data fields. This step was crucial to prevent redundancies and inaccuracies in the new system.
Data Mapping: Legacy data structures often differed significantly from the standards required by Oracle Cloud. By mapping fields from the older Oracle EBS system to their counterparts in Oracle Cloud Fusion, the Organization ensured smooth data flow between the two platforms. This step also addressed data type mismatches and standardized terminologies across systems.
4. Medallion Architecture – Data Staging and Transformation (Foundation)
The organization adopted Snowflake’s medallion architecture to structure its data transformation and management processes. This architecture, which organizes data into three distinct layers—raw (L0), staged (L1), and transformed (L2)—was instrumental in ensuring data quality and accessibility:
Raw Layer (L0): This layer served as the repository for unprocessed data directly ingested from Oracle EBS, Oracle Cloud Fusion, Salesforce, and other sources. By maintaining raw data in its original state, the organization preserved a source of truth for any future reference or validation needs.
Staged Layer (L1): In this intermediate layer, data underwent basic cleansing and formatting. Temporary tables and views were created to validate the integrity of the data and prepare it for further transformations.
Transformed Layer (L2): The transformed layer contained fully processed and structured data optimized for reporting, analytics, and operational use. This layer supported dashboards and reports generated in Tableau, ensuring stakeholders had access to actionable insights.
Transformation and Orchestration
Low-Code Automation: Simplifies the orchestration of jobs.
CI/CD Pipelines: Ensures scalable and version-controlled workflows.
Dependency Management: Modularizes transformation tasks for reusability and maintainability.
5. Bridge Model: A Synchronization Solution
To maintain continuity and ensure seamless data integration between Oracle EBS and Oracle Fusion, the organization implemented a Bridge Model that serves as a dynamic synchronization layer between the two systems.
Open and Closed Data Synchronization: While Oracle Cloud Fusion handled open invoices and ongoing transactions, the legacy system retained historical or closed invoices. The bridge model ensured that both datasets could be seamlessly integrated into unified reports.
Mapping Legacy to Modern Systems: The bridge maintained a lookup table linking primary keys from Oracle EBS to corresponding records in Oracle Cloud Fusion. This mapping enabled cross-referencing and consistency between old and new systems, simplifying data validation and reporting.
Unified Reporting: The bridge model allowed the customer to produce consolidated financial reports that included data from both Oracle EBS and Oracle Cloud Fusion, offering a holistic view of financial operations.
6. Data Intelligence H4
Visualization in Tableau:
Dashboards in Tableau transform data into actionable insights.
Visualizations include financial reports, transaction summaries, AR aging analysis, and other key metrics.
By adopting this architecture, the customer achieved: H5
Data Scalability: The medallion architecture allowed for handling large volumes of data across multiple sources.
Efficiency in Transformations: Layered processing ensured that each stage of data handling was optimized for specific tasks, reducing processing overheads and complexity.
Robust Security: Snowflake’s multi-layered approach provided secure environments for staging and transforming data, protecting sensitive information at every step.
Systematic Phased Implementation
The migration was executed in phases to mitigate risks and ensure business continuity. Each phase addressed specific modules or functionalities, allowing for iterative testing and refinement. Key features of this approach included:
Incremental Deployment: Modules like Accounts Payable (AP), Accounts Receivable (AR), and General Ledger (GL) were migrated individually, ensuring focused attention on each functional area.
Pilot Testing: Initial deployments were conducted in test environments to validate data integrity and system performance before moving to production.
Stakeholder Involvement: Continuous engagement with stakeholders ensured that the migration aligned with business objectives and addressed user concerns promptly.
Delivering Immediate Benefits
This meticulous approach to technical implementation delivered several immediate advantages:
Uninterrupted Operations: the organization’s operations continued seamlessly during the migration, ensuring no downtime or disruptions in critical processes.
Enhanced Data Quality: Cleaned and standardized data provided a solid foundation for advanced analytics and decision-making.
Future-Ready Systems: The integration of Oracle Cloud Fusion and Snowflake equipped the Organization with the tools needed to scale operations and adapt to evolving business demands.
The organization’s commitment to a phased and systematic implementation ensured that its migration to Oracle Cloud Fusion was not just a technology upgrade but a strategic transformation that enhanced its operational capabilities.
Bridging EBS and Fusion: The Game Changer H3
One of the most critical innovations in the organization’s migration to Oracle Cloud Fusion was the implementation of a bridge model. This model served as a crucial link between the legacy Oracle E-Business Suite (EBS) and the modern Oracle Cloud Fusion system, addressing the inherent complexities of integrating these platforms. The bridge model was not just a technical solution but a strategic enabler, ensuring the seamless coexistence of historical data with real-time transactional capabilities during and after the transition.
The Need for a Bridge Model
Migrating to Oracle Cloud Fusion posed several challenges, particularly in reconciling open and closed invoices from the legacy EBS system. Open invoices represented ongoing financial transactions that needed to be actively managed and tracked in Oracle Cloud Fusion. In contrast, closed invoices, representing completed transactions, remained stored in the legacy EBS system for historical and reporting purposes. Without a robust integration mechanism, discrepancies in financial reporting and operational inefficiencies could arise.
How the Bridge Model Works
At its core, the bridge model functions as a dynamic lookup table that maps data fields between Oracle EBS and Oracle Cloud Fusion. This mapping ensures that key identifiers, such as account numbers or invoice IDs, are aligned between the two systems. The bridge model was designed to handle:
Data Transformation: Legacy identifiers in EBS (e.g., shorter or custom account numbers) were converted into the standardized formats required by Oracle Cloud Fusion.
Data Synchronization: The model facilitated bidirectional synchronization, enabling both systems to share updated records while maintaining data consistency.
Comprehensive Reporting: By aggregating data from both systems into Snowflake, the bridge model enabled unified reporting and analysis, combining historical data from EBS with real-time transactions from Fusion.
Key Benefits of the Bridge Model
The implementation of the bridge model provided the Organization with several transformative benefits:
Seamless Reporting: The bridge model enabled the Organization to generate unified financial reports that included both historical and real-time data. This capability was particularly important for producing accurate financial statements, monitoring project costs, and meeting compliance requirements.
Data Consistency: Maintaining data accuracy across two systems can be challenging during migration projects. The bridge model ensured that discrepancies between legacy and modern platforms were minimized, creating a single source of truth for the organization’s financial data.
Operational Continuity: Migration projects often risk disrupting day-to-day operations. By using the bridge model, the Organization maintained uninterrupted access to critical financial data and processes, even as new systems were phased in. This was essential for maintaining customer service levels and internal productivity.
Adaptability for Future Needs: The bridge model was designed to evolve with the organization’s requirements. As more historical data transitions into Oracle Cloud Fusion or new business processes emerge, the bridge ensures scalability and adaptability without requiring significant rework.
A Cornerstone for Modernization
The bridge model did more than just facilitate the migration process; it became the cornerstone of the organization’s overall modernization strategy. It ensured that historical data could coexist with real-time operations, allowing for a gradual and risk-mitigated transition. This approach not only reduced the operational risks associated with such a significant overhaul but also established a foundation for future growth and system scalability.
Technical Highlights
Mapping Complexities: The bridge handled transformations like converting EBS account numbers into Oracle Cloud-compliant formats, ensuring compatibility with Fusion’s structured requirements.
Real-Time Integration with Snowflake: The bridge fed both historical and real-time transactional data into Snowflake, where the organization’s reporting and analytics processes were centralized. This eliminated the need for users to query multiple systems, thereby simplifying data access and analysis.
Support for Diverse Modules: The model extended its integration capabilities to cover multiple financial and operational modules, such as Accounts Payable (AP), Accounts Receivable (AR), and General Ledger (GL), ensuring comprehensive coverage of business processes.
Financial Modules
The organization’s financial operations—spanning Accounts Payable (AP), Accounts Receivable (AR), and General Ledger (GL)—experienced a transformative overhaul following the adoption of Oracle Cloud ERP. These critical modules form the backbone of the organization’s financial management, supporting the seamless flow of transactions and ensuring compliance with regulatory standards. Here’s a deeper look into the improvements.
Automated Reconciliation Prior to Oracle Cloud ERP, reconciliation processes were largely manual, requiring extensive effort and often leading to errors. The integration of automated reconciliation tools streamlined this process, reducing the time spent on error resolution and increasing accuracy. This automation also freed the finance team to focus on strategic activities like financial analysis and forecasting.
Streamlined Reporting Real-time data insights became a game-changer for the organization’s financial operations. With Oracle Cloud ERP, the finance team could generate detailed reports at the click of a button, offering insights into accounts, transactions, and budgets. These reports not only facilitated faster decision-making but also enhanced transparency for stakeholders.
Regulatory Compliance Enhanced tools within Oracle Cloud ERP ensured the organization’s adherence to financial standards, such as ASC 606. Automated auditing features provided comprehensive tracking of financial transactions, making it easier to prepare for regulatory reviews and maintain compliance across jurisdictions.
These advancements collectively empowered the organization’s finance team to operate with heightened efficiency, agility, and precision, enabling them to drive impactful strategic initiatives that align with the company’s growth goals.
Dataflow Diagram
Example : AR Module
Optimizing Accounts Receivable Operations
As part of the broader financial transformation, the Accounts Receivable (AR) module underwent a significant overhaul. Leveraging Oracle Cloud Fusion’s advanced dashboards and KPIs, the organization optimized its receivables management, enhancing cash flow and operational efficiency.
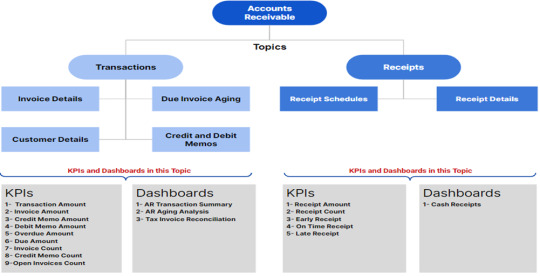
Accounts Receivable Module and its Topics
AR Transaction Summary Dashboard
This dashboard provides a comprehensive overview of the entire lifecycle of receivables, including AR transactions, due amounts, invoices, journals, and customer-level information. It is a powerful tool for monitoring AR performance and identifying actionable insights for improving collections.
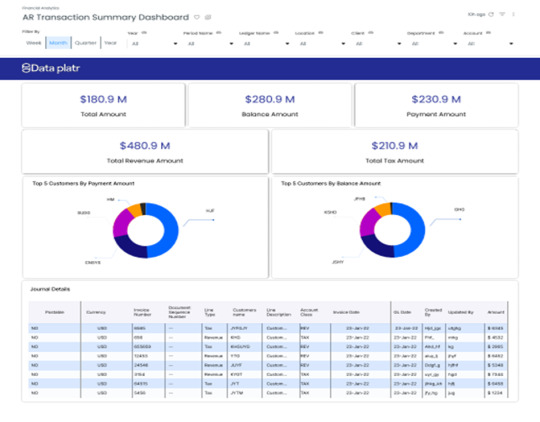
AR Aging Analysis Dashboard
This dashboard categorizes open invoices by aging buckets, enabling targeted collection efforts. By analyzing invoice and payment schedule dates, it provides a clear picture of overdue payments and helps prioritize high-risk accounts.
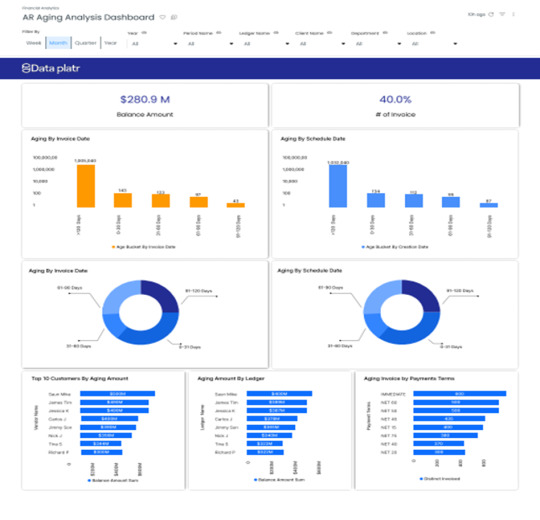
Cash Receipts Dashboard
A vital tool for tracking cash inflows, this dashboard offers detailed insights into payments received against AR invoices. It supports transparency in cash management and enhances overall financial reporting.
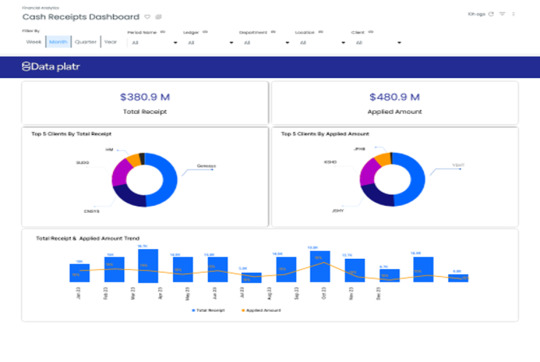
Key Accounts Receivable KPIs
Invoice Amount
Tracks the total value of invoices generated within a specific timeframe, offering insights into billing efficiency and revenue generation.
Transaction Amount
Combines invoice, credit memo, and debit memo values to provide a comprehensive view of AR activity.
Balance Amount
Highlights outstanding receivables at a given point, enabling month-to-month analysis of overdue balances and collection trends.
Receipts Amount
Reflects the total payments received against invoices during a specific period, serving as a key measure of collection efficiency.
Receipt Count
Tracks the number of payments processed within a period, supporting the evaluation of payment activity and recovery rates.
AR Aging by Invoice Date
Categorizes open invoices based on their issue dates, providing insights into aging patterns and overdue accounts.
Early, Ontime, and Late Receipts
Metrics tracking payment behaviors, identifying proactive customers (early receipts), compliant customers (ontime receipts), and delayed payers (late receipts). These KPIs help in tailoring collection strategies.
Open Invoices Count
Tracks the total number of unpaid invoices, providing insights into the workload for AR teams.
Impact on Financial Operations
The AR dashboards and KPIs offered by Oracle Cloud Fusion have transformed financial operations by delivering the following benefits:
Enhanced Visibility
Real-time dashboards provide a clear view of receivables performance, enabling organizations to identify overdue accounts, prioritize collections, and take timely action.
Improved Cash Flow
By tracking metrics like Receipts Amount and Balance Amount, businesses maintain healthier cash flows and ensure timely inflows to support operational needs.
Streamlined Collections
The AR Aging Dashboard and Open Invoices Count allow teams to focus on delinquent accounts, reducing collection times and improving overall efficiency.
Data-Driven Decisions
With actionable insights from Transaction Amount and Receipt Count metrics, leadership can develop strategic approaches to optimize collections and address payment delays.
Proactive Customer Management
Metrics like Early, Ontime, and Late Receipts help identify customer payment behaviors, allowing for tailored engagement strategies that foster better relationships and improve compliance.
Oracle Cloud Fusion’s AR dashboards and KPIs provide a robust framework for optimizing accounts receivable operations. By harnessing these tools, organizations can achieve operational excellence, enhance cash flow management, and maintain financial stability. This transformation aligns with broader goals of scalability and sustainable growth, reinforcing the organization’s leadership in innovation and operational efficiency.
Innovative Tools and Workflows
To extract maximum value from Oracle Cloud Fusion, the Organization integrated several innovative tools and workflows into its ecosystem. These technologies optimized processes and addressed the complexities of managing data and operations across diverse systems:
RiteSync RiteSync emerged as a cornerstone in the organization’s integration strategy, simplifying backend transformations and automating data ingestion into Snowflake. By handling complex concatenation and synchronization tasks in the background, RiteSync ensured that the organization’s data pipelines remained robust and error-free.
Custom Billing Engines The organization’s subscription-based business model required sophisticated billing processes capable of managing diverse customer plans and revenue recognition. Custom billing engines built on Oracle Cloud Fusion supported features like periodic billing, performance guarantees, and mid-term contract modifications, ensuring flexibility and precision in revenue management.
Event-Driven Architectures Real-time event processing allowed the Organization to respond dynamically to business triggers. Whether updating customer accounts, generating invoices, or reconciling transactions, event-driven architectures ensured timely execution of critical workflows, enhancing overall operational agility.
These tools and workflows played a pivotal role in aligning the organization’s systems with its dynamic business environment, making operations more adaptive and responsive to future needs.
Lessons Learned
The organization’s migration journey from Oracle EBS to Fusion Cloudto Oracle Cloud Fusion provided several valuable lessons that can inform future digital transformation projects:
Executive Alignment Strong leadership involvement was crucial to the success of the migration. By securing commitment and alignment across departments, the Organization ensured resource availability and streamlined decision-making processes.
Phased Approach An incremental migration strategy proved effective in minimizing risks and disruptions. Starting with less critical modules and gradually transitioning core operations allowed the Organization to test and optimize each phase of the implementation.
Custom vs. Standard Features Balancing customization with standard Oracle Cloud functionalities was critical. While standard features offered stability and faster deployment, custom solutions ensured that the organization’s unique business needs were met without adding unnecessary complexity.
By addressing these considerations, the Organization not only achieved a smooth transition but also laid the groundwork for ongoing operational improvements.
Results and Benefits
The integration of Oracle Cloud Fusion, facilitated by Dataplatr, delivered remarkable outcomes for the organization’s operations. Key benefits included:
Enhanced Scalability Oracle Cloud Fusion’s robust architecture enabled the Organization to manage its growing customer base and increasing transaction volumes with ease, ensuring long-term operational sustainability.
Operational Efficiency Streamlined workflows and automated processes reduced manual efforts, minimized errors, and increased productivity across departments.
Data Accuracy Real-time data synchronization and advanced analytics improved decision-making capabilities, offering precise insights into financial health and operational performance.
Sustainability Cloud-based systems aligned with the organization’s commitment to environmental stewardship, reducing the carbon footprint associated with on-premises infrastructure.
These outcomes underscored the transformative potential of Oracle Cloud Fusion in driving both business efficiency and sustainability.
Conclusion
The organization’s migration to Oracle Cloud Fusion serves as a compelling case study in leveraging cloud-based solutions to overcome legacy system limitations and foster innovation. By addressing challenges in data integration, scalability, and compliance, the Organization not only improved its operational capabilities but also aligned its systems with its mission of delivering affordable and sustainable energy solutions.
The collaboration between the organization, Oracle Cloud Fusion, and Dataplatr highlights the importance of strategic partnerships in executing large-scale digital transformations. This success story stands as an inspiration for other organizations seeking to modernize their operations and position themselves for sustained growth in an increasingly competitive landscape.
0 notes
Text
Maximise Business Potential: How Hiring Expert ASP .NET Developers Will Streamline Your Workflow
Businesses today face constant pressure to improve efficiency, reduce operational bottlenecks, and stay ahead of technological advancements. Disjointed workflows, manual processes, and outdated systems can slow productivity and impact profitability. To overcome these challenges, organisations must invest in robust software solutions tailored to their needs. This is where ASP .NET developers play a crucial role. Their expertise in building scalable, secure, and high-performance applications can transform business operations and drive long-term success.
Why ASP.NET? A Framework Built for Business Growth
ASP.NET is a powerful framework designed to support the development of dynamic web applications, enterprise solutions, and business automation tools. Its flexibility, security, and scalability make it a preferred choice for businesses aiming to enhance their digital capabilities. By hiring experienced ASP.NET developers, companies can create custom software solutions that streamline workflows, reduce inefficiencies, and ensure seamless integration with existing systems.
Optimising Business Workflows with ASP.NET Development
1. Automating Repetitive Tasks
Many businesses struggle with manual processes that consume time and increase the likelihood of errors. Skilled ASP.NET developers can build automation tools that eliminate redundant tasks, allowing employees to focus on high-value work. For instance, custom-built applications can automate order processing, financial reporting, and inventory management, reducing human intervention and enhancing accuracy.
2. Seamless System Integration
Businesses often rely on multiple software solutions for different operations. However, disconnected systems can lead to inefficiencies and data inconsistencies. ASP.NET developers create applications that integrate smoothly with CRM, ERP, and accounting software, ensuring a unified platform where data flows seamlessly across departments. This not only improves productivity but also enhances decision-making by providing real-time insights.
3. Scalable Solutions to Support Business Expansion
Growth-oriented businesses need software solutions that can adapt as their needs evolve. A well-structured ASP.NET application is designed with scalability in mind, enabling organisations to handle increased workloads without performance issues. Whether expanding to new markets or introducing new services, businesses can rely on ASP.NET developers to ensure their systems remain efficient and responsive.
4. Enhancing Data Security and Compliance
With cyber threats on the rise, data security is a top priority for businesses. ASP.NET offers built-in security features that protect sensitive information and prevent unauthorised access. Expert developers implement secure authentication mechanisms, data encryption, and compliance measures that align with industry standards, ensuring that businesses safeguard their digital assets.
Boosting Operational Efficiency Through Customised ASP.NET Solutions
Businesses operate in diverse industries, each with unique challenges and requirements. A one-size-fits-all software solution often falls short in addressing specific needs. By hiring ASP.NET developers, organisations can benefit from tailored applications that align with their objectives and workflows.
Custom-built solutions can:
Improve customer interactions by developing intuitive and user-friendly interfaces.
Enhance financial management by integrating real-time analytics and automated invoicing.
Streamline project management by offering centralised dashboards for tracking tasks and deadlines.
Optimise resource allocation by implementing AI-driven forecasting tools.
Cost-Effectiveness of Hiring ASP.NET Developers
Investing in expert ASP.NET developers is a strategic move that leads to long-term cost savings. By automating tasks, reducing errors, and improving system efficiency, businesses can cut operational expenses while enhancing overall productivity. Additionally, ASP.NET’s modular architecture allows companies to make incremental improvements instead of costly system overhauls, ensuring a sustainable and budget-friendly approach to digital transformation.
Future-Proofing Your Business with ASP.NET Development
Technology continues to evolve, and businesses that fail to adapt risk falling behind competitors. ASP.NET remains a cutting-edge framework with continuous updates and improvements, making it an excellent choice for future-proofing digital operations. By collaborating with skilled ASP.NET developers, companies can stay ahead of industry trends and ensure their software solutions remain relevant and efficient. Hiring experienced ASP.NET developers is a strategic decision that enables businesses to streamline workflows, improve system efficiency, and achieve sustainable growth. With expertise in automation, integration, security, and scalability, these professionals help organisations develop tailored solutions that drive productivity and innovation. Investing in ASP.NET development ensures that businesses remain competitive, agile, and well-prepared for future advancements.
#ASP Dot NET Developers#Hire ASP .NET Developers#ASP .NET Development Company#ASP .NET Development Services
0 notes
Text
Ethereum's Fragmentation Fix: How ERC-7683 Unifies L2s for a Seamless Web3 Experience

The Ethereum ecosystem has seen remarkable growth, with Layer-2 (L2) solutions boosting transaction speeds and reducing costs. However, this expansion has led to a significant challenge: fragmentation. With over 50 L2s, Ethereum has become a complex maze, forcing users to navigate multiple networks and bridge assets to perform basic actions. This article explores the problem of fragmentation and introduces ERC-7683, a standard designed to unify Ethereum and create a seamless user experience.
The Problem: Ethereum's Fragmentation Crisis
Fragmentation poses an existential threat to Ethereum's future. The need to manage multiple networks and bridge assets introduces friction, confusion, and potential errors.
User Experience: Simple actions, like buying a token, require switching networks and multiple transactions.
Liquidity: Capital is trapped in silos, reducing market efficiency. DeFi protocols struggle to maintain liquidity across chains, leading to worse prices and convoluted processes.
Developer Challenges: Developers face the difficulty of choosing which L2s to support, managing multiple deployments, and building complex bridging infrastructure.
ERC-7683: A Unified Solution
Proposed by Across and Uniswap Labs, ERC-7683 is a standard that allows Web3 apps to express complex multi-step cross-chain transactions as a single user request. A network of relayers then executes these requests. The standard is supported by over 50 protocols, including Arbitrum, Base, and Optimism, as well as the Ethereum Foundation's L2 Interop working group.
How ERC-7683 Works
ERC-7683 simplifies cross-chain operations by allowing users to express their desired outcome without manually managing network switches and bridges.
Intents-Based Architecture: ERC-7683 separates the user’s desired outcome from the mechanical execution.
One-Click Transactions: Users can perform actions like swapping tokens on Base using funds from Arbitrum in a single click.
Competitive Solvers: A network of solvers competes to fulfill these intents quickly.
Benefits of ERC-7683
Seamless User Experience: Users interact with the entire Ethereum ecosystem as if it were one chain.
Abstraction of Complexity: Developers can abstract away chain complexity while leveraging the scale of a multi-chain ecosystem.
Cross-Chain Execution Speed: Provides the fast execution speeds needed for seamless experiences.
Real-World Implementation
ERC-7683 is already in use through Across implementation, which has processed over $18 billion in cross-chain volume. This demonstrates the standard's viability and potential.
A Vision for Ethereum in 2025
In the near future, imagine an Ethereum where users can see all their assets across every chain in one view and interact with any application on any L2 without worrying about bridging. Developers can build applications once and reach users everywhere, and liquidity flows freely.
Tips and Guides for Users and Developers
For Users: Look for wallets and applications that support ERC-7683 to simplify cross-chain transactions.
For Developers: Embrace ERC-7683 to build applications that can seamlessly interact with multiple L2s. Consider using Across' solver network to extend your application's reach.
Examples of ERC-7683 in Action
Cross-Chain Swapping: A user wants to swap tokens from Arbitrum to Base. With ERC-7683, they can initiate a single transaction, and the standard handles the bridging and swapping automatically.
DeFi Participation: A user wants to participate in a DeFi protocol on Optimism using assets on Polygon. ERC-7683 allows them to do so without manually bridging assets.
The Path to Mass Adoption
By resolving fragmentation, ERC-7683 addresses a major barrier to mainstream adoption. It makes DeFi more accessible and improves liquidity across marketplaces.
Conclusion
ERC-7683 is essential for building a unified, accessible Ethereum ecosystem. By embracing this standard, L2s, developers, and the community can unlock Ethereum's full potential. Unified standards, shared infrastructure, and collaboration are crucial to overcoming the challenges of fragmentation. With account abstraction and intent-based bridging in place, ERC-7683 integrates these innovations into a cohesive standard, setting the stage for Ethereum’s next chapter.
#ethereum#L2 layer#Fragmentation#Crypto#blockchain#cryptocurrency#cryptoinvesting#bitcoin#Web3#web 3.0
0 notes
Text
Streamline Your Business with a Seamlessly Integrated Squarespace Website
In today’s fast-paced digital landscape, having an effective online presence is crucial for any business. A well-designed website not only serves as your digital storefront but also plays a key role in customer engagement, sales, and brand credibility. However, managing multiple tools and platforms separately can become overwhelming. This is where Squarespace shines. By offering an all-in-one platform that seamlessly integrates various business functions, Squarespace Development Service enables businesses to streamline their operations, improve efficiency, and enhance customer experience.
Why Choose Squarespace for Your Business?
Squarespace is a powerful website builder known for its sleek designs, user-friendly interface, and robust features. Unlike other website platforms that require third-party plugins or complex coding, Squarespace provides built-in tools that simplify website management. Whether you run a small business, an e-commerce store, or a service-based company, Squarespace offers a tailored solution to meet your needs.
Seamless Integration of Essential Business Tools
One of the biggest advantages of Squarespace is its ability to integrate essential business tools seamlessly. Here’s how Squarespace helps streamline your business:
Unified Website and E-Commerce Platform
For businesses selling products or services, Squarespace offers a fully integrated e-commerce solution. With features like customizable product pages, secure checkout, and inventory management, you can manage everything from one dashboard. Squarespace also supports multiple payment gateways, including Stripe and PayPal, making transactions smooth and secure.
Built-in Marketing and SEO Tools
Marketing is essential for business growth, and Squarespace offers an array of built-in marketing tools. You can create email campaigns, integrate social media platforms, and use SEO-friendly site structures to improve visibility on search engines. With detailed analytics, you can track visitor behavior, measure campaign effectiveness, and optimize your strategies accordingly.
Automated Scheduling and Appointments
For service-based businesses, managing appointments manually can be time-consuming. Squarespace’s Acuity Scheduling feature allows customers to book appointments online, send automatic reminders, and process payments—all within your website. This automation enhances customer convenience while saving time for your team.
Seamless Third-Party Integrations
While Squarespace has built-in functionalities, it also supports third-party integrations for added flexibility. You can integrate Google Workspace for professional emails, Zapier for workflow automation, and QuickBooks for accounting. These integrations help businesses operate smoothly without the hassle of switching between multiple platforms.
Enhancing Customer Experience
A streamlined website doesn’t just benefit your business operations—it also enhances the customer experience. With intuitive navigation, fast load times, and mobile-responsive designs, Squarespace ensures that visitors have a seamless browsing experience. Features like live chat, customer accounts, and personalized recommendations further improve engagement and drive conversions.
Simplifying Content Management
Managing website content is effortless with Squarespace’s intuitive drag-and-drop editor. Whether you want to update product listings, publish blog posts, or modify page layouts, you can do so without needing technical expertise. The platform also offers a variety of professional templates that can be customized to reflect your brand’s identity.
Security and Reliability
Security is a top priority for any business operating online. Squarespace provides SSL encryption, automatic updates, and secure hosting to protect your website from cyber threats. With 24/7 customer support, you can rest assured that any technical issues will be resolved promptly.
Conclusion
A seamlessly integrated Squarespace website is a game-changer for businesses looking to optimize their operations, enhance customer experience, and drive growth. By combining website management, e-commerce, marketing, and automation tools into one platform, Squarespace eliminates inefficiencies and allows businesses to focus on what truly matters—serving their customers and scaling their brand. If you’re looking for a hassle-free way to streamline your business, Squarespace is the ultimate solution.
For more information about Ecommerce Seo Service and Seo Reseller In India Please visit: TechIndia Software.
0 notes