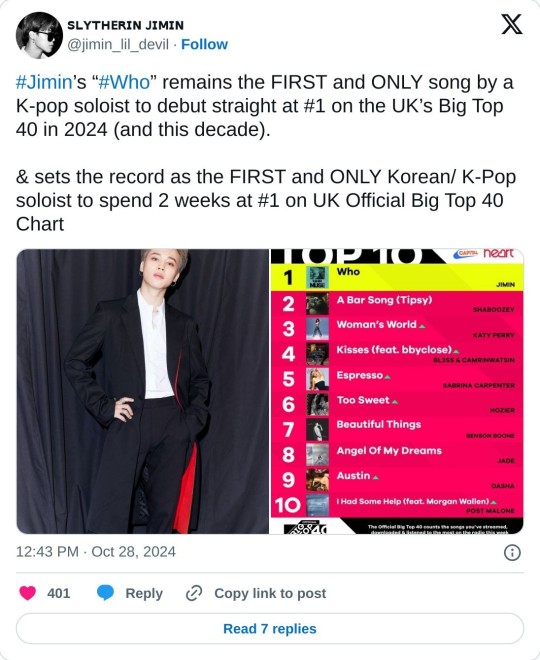
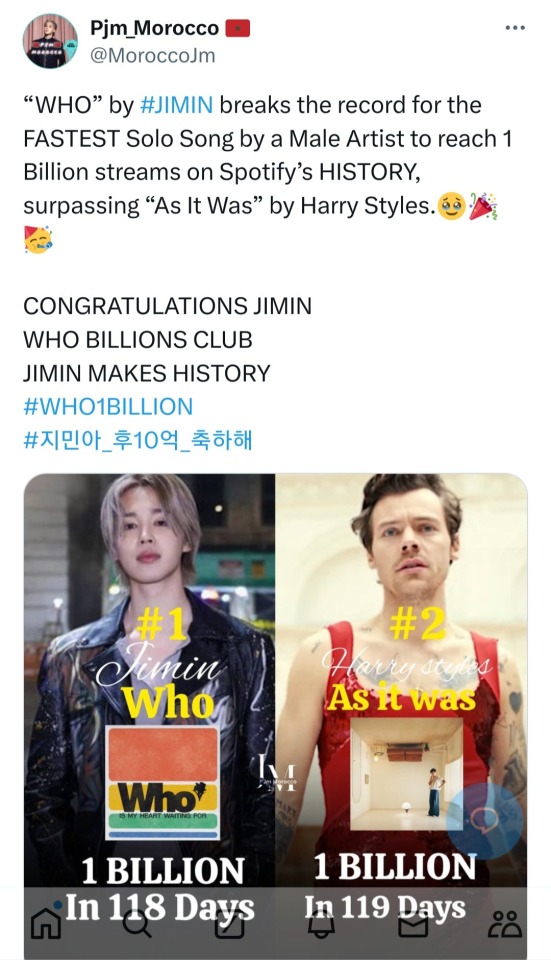
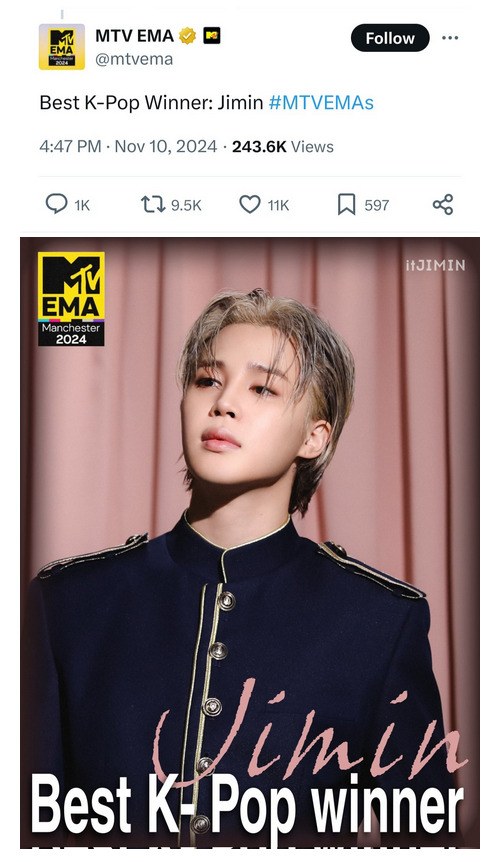
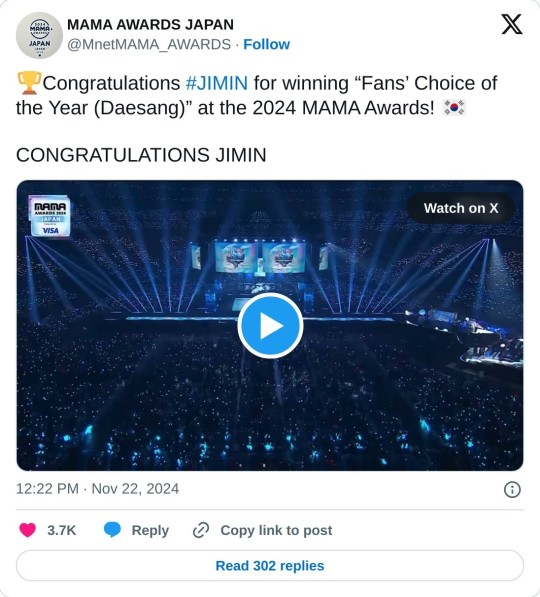
#they have proof with emails and call logs
Explore tagged Tumblr posts
Text
𝓯𝓪𝓽𝓮 𝓹𝓪𝓻𝓽 3
“One single thread of gold tied me to you.”
Stray Kids - Felix x Reader
Red (golden) string of fate trope
Word count: 23k




𝓹𝓻𝓮𝓿𝓲𝓸𝓾𝓼 𝓹𝓪𝓻𝓽 ← 𝓬𝓾𝓻𝓻𝓮𝓷𝓽 𝓹𝓪𝓻𝓽 → 𝓷𝓮𝔁𝓽 𝓹𝓪𝓻𝓽
You arrived at the venue early, determined to squeeze in every second of productivity before heading to SBS Prism Tower. The building was mostly quiet, the only sounds were the click of rolling garment racks, distant conversations in rapid Korean, and the occasional bark of a director giving instructions.
The door to your prep studio creaked open as you stepped in, only for the breath to catch in your throat.
The rack was still empty.
Your eyes swept the space again, as if the collection could somehow be hiding behind a mannequin or tucked under the work table.
But no. No garments. No boxes. No deliveries.
“Where-” you fumbled for your phone, fingers suddenly cold.
As if summoned, Bora stepped into the room right then, a cup of coffee in one hand (she’s addicted to coffee at this point) and her phone in the other. She took one look at your face and stopped. “They’re not here?”
You shook your head. “They were supposed to be here yesterday.”
Bora's eyes narrowed, and her tone turned sharp. “Did the shipper confirm pickup?”
“Yes. The warehouse texted me a photo of the truck leaving.”
She pulled out her phone immediately, scrolling. “Hang on. I’m calling customs now.”
You walked slowly over to the rack, running your hand down the cool metal bar that should’ve been weighed down. Instead, it was bare.
You’d spent months on this collection. Sketching until your fingers cramped. Stitching until your vision blurred. Choosing fabrics so precise you’d fought with a vendor over 3% silk content. These weren’t just clothes. They were proof you deserved to be here.
Bora swore under her breath, still waiting for the call to connect. You could hear the ring on speakerphone as she set her coffee on the edge of the table.
When the shipping rep finally picked up, she launched in without preamble. “This is Bora Kwon, designer liaison for Seoul Fashion Week. I need an update on a customs-cleared garment shipment from Atelier Han. Tracking number ending in 7134. It was marked as released yesterday. Where is it now?”
A pause. You strained to hear the voice on the other end, but the reply was too muffled to make out.
Bora’s jaw clenched. “Yes, I see that. Customs clearance was confirmed at Incheon at 3:42 p.m. So where did it go after that?”
Another pause. Bora’s eyes flicked toward you, unreadable.
“No, I’m not asking where it should have gone. I’m asking where it actually went.” Her tone was ice now. “Because the venue received nothing. And my designer's model fittings schedule is released today.”
You crossed your arms, trying to suppress the chill under your skin that had nothing to do with the venue’s central air. Your stomach had started to twist itself into knots.
Finally, Bora gave a slow blink, listening. “Understood. Email me the internal logs. Now.” She hung up and turned to you, pinching the bridge of her nose. “Okay. So the good news is they cleared customs. The bad news is-”
��They don’t know where the hell the boxes went,” you finished, voice tight.
She nodded grimly. “Exactly that. They were picked up by a third-party delivery service after clearance, which should’ve brought them here directly. But there’s no delivery confirmation, and the tracker’s been inactive since yesterday evening.”
Your voice cracked slightly. “So they’re just… lost?”
“They’re not lost,” Bora said quickly, though her tone wavered at the edge of certainty. “They’re… misplaced. Temporarily misdirected. It happens. Sometimes the logistics team drops it off at the wrong dock, or the delivery driver doesn’t scan the box, or-”
You turned away, fists clenched at your sides. “Bora, my fittings start tomorrow. I can’t present a ghost collection.”
“I know.” Her voice softened immediately. “I know. I’m already on it. We’ll find them, okay? You did everything right. This isn’t on you.” Bora picked her coffee back up, took a long, furious sip, and muttered, “If some intern signed for those boxes at the wrong address, I swear to god I’ll personally dye their eyebrows pink.”
You couldn’t help it, you laughed, hoarse but real. “Pink?”
“It’s the ugliest semi-permanent color I know. Lasts for weeks. A fate worse than termination.”
You scrubbed a hand down your face. “What do we do now?”
She looked at her watch. “You keep working. Draft backup fitting notes. Check your digital files, double-check the accessory sets, and anything you can until those pieces turn up. I’m going to track this shipment to hell and back. And tonight, you’re still going to SBS Prism Tower.”
Your head jerked up. “You still want me to go?”
“If that thread was pulling that hard, you must follow it. Fashion week is the show of your life,” she said. “But he… he might be the rest of it.”
You blinked at her.
“Besides,” she added, “if I’m going to threaten a warehouse, a shipping service, and an intern in one day, I need something wholesome to balance it out.”
You smiled despite yourself. “A soulmate sighting is your idea of wholesome?”
“Only if it ends with some kissing.”
You rolled your eyes.
“Go get your designs back,” she said. “Then go get your boy.”
︶⊹︶︶୨୧︶︶⊹︶
You had spent the day finding some assistants who could sew quickly, just in case your packages never arrived.
Two interns from ESMOD were sent your way by Bora’s friend in casting. They were quiet, efficient, and terrifyingly fast with a needle. You assigned them mock-ups, digitized what patterns you could salvage, and resigned yourself to the grim possibility of rebuilding the collection piece by piece overnight if necessary.
By the time 6:45 PM rolled around, your hands were sore and your laptop battery was dying. Still no word from the delivery service. Still no boxes.
And yet, Bora insisted on dragging you, half-covered in thread clippings and foundation touch-ups, into the back of a black van headed for the SBS Prism Tower.
“I should be back at the venue,” you murmured, voice hoarse as the skyline slipped past outside your window. “What if the pieces show up? What if the interns need help? What if-”
Bora reached over and flicked your forehead lightly. “Ow, hey!”
“Stop spiraling. I’ve got it covered,” she said firmly, holding up her phone, which displayed approximately 17 ongoing text threads. “I have a guy at the loading dock. I have the shipping company’s regional manager on the verge of tears. I have a spare espresso shot in my bag and a threat drafted in my notes app in case I need to go nuclear.”
You looked at her sideways. “Does the espresso come with a therapy session?”
She smirked. “Only if you cry first.”
The lobby of Prism Tower was a sea of controlled chaos. Stylists and staff rushed across marble floors with garment bags and makeup trunks. Idols posed for the press behind velvet ropes while their managers hovered nearby like hawks. The air buzzed with tension and hairspray.
You tightened your grip on your badge as you and Bora made your way past the credentialed entrance.
“Don’t slouch,” she said without looking at you.
“I’m not slouching.”
“You’re slouching emotionally.”
“I’m anxious.”
“Then fake it. Shoulders back. Chin up. Pretend the entire K-pop industry is watching you.”
“They are.”
“Good. Maybe one of them will remember you when you’re famous and want to walk your next red carpet in your designs.”
Bora didn’t miss the sudden shift in your expression, the way your breath hitched slightly, and your eyes locked onto something invisible and far away.
She followed your gaze. “The thread?”
You gave a small, shaky nod. The golden line tugged violently at your pinky as it glowed. This happened last time he was close.
“Alright, follow it.”
You blinked. “What?”
She raised a brow. “You said he’s here, right? Go find him.”
“Bora, we’re in a high-security building, surrounded by idols, staff, and literal K-pop royalty. I can’t just walk around like I’m soul-radar?”
“Yes,” she said without hesitation. “Exactly like that.”
You hesitated, but the thread gave another soft pull, like it knew where it was going even if you didn’t. You swallowed. “Okay.”
Bora nodded approvingly. “Text me if you need backup or if you find the love of your life and need a witness. I’m going to go harass a logistics manager and pretend I’m scarier than I look.”
You slipped away from her with a grateful smile and started moving through the tower, following the quiet hum inside your chest. The thread guided you through backstage corridors, past bustling makeup stations and camera setups, winding deeper into the heart of the production floor.
People buzzed past in a blur of dark clothing and headset wires. You had to duck around racks of sequined suits, dodge a dancer mid-warm-up, and avoid getting smacked by a boom mic swinging around a corner. But still, the thread tugged, firm and calm, like a hand leading you through a storm.
Finally, it led you into a quieter hallway just behind the main performance stage. The sound of muffled bass pulsed through the walls, but this area was dimmer, calmer. Right in front of you was a dressing room door marked ‘Stray Kids’.
The golden thread attached to your pinky was practically buzzing now. It shimmered faintly in the low light, pulsing like a heartbeat. And it led directly to that door.
Your heart leapt into your throat. You took a shaky step forward and stopped because you heard voices on the other side. Laughter first, warm and familiar. Then words, quiet and close, as if someone had just leaned in near the door.
“…still glowing,” someone said. A low, accented voice, edged with awe. “Hyung, I’m serious. It’s glowing more now.”
A soft scoff followed, amused but not dismissive. “Maybe you’re just excited.”
“No, seriously,” the first voice insisted. “It’s like… vibrating. This has never happened before.” A pause. “Do you think they’re close? Like, right now?”
Your breath caught. Felix.
On the other side of that door, he was speaking about you.
You pressed your hand lightly against the wall, just beside the doorframe. The warmth of it grounded you.
Inside, another voice joined in. “You’re the only one whose string reacts that strongly. It’s gotta mean something. Didn’t you say it lit up like that when we walked out of the studio yesterday?”
“Yeah,” Felix murmured, quieter now. “It pulled hard. I think, I think they were nearby. I just didn’t know who.”
The conversation continued, but in Korean.
That’s when you decided to grab hold of your string and tug. Not forcefully, just enough to say you’re here.
Inside, the conversation stuttered. Words dropped off.
You held still, trembling, the golden thread thrumming like a live wire between you.
“…Hyung,” Felix’s voice came again, barely a whisper. “Did you feel that?”
More scrambling. Someone muttered something urgent in Korean.
Felix’s voice was closer now. Softer. He was near the door. “I just… I need air.”
The doorknob turned. Slowly.
You blinked, barely managing to step back as the door cracked open and Felix emerged.
He didn’t look at you at first. His gaze was on the floor, his shoulders rising with each unsteady breath. He was pale, and his lips parted as if he’d just run a mile, skin dewy from the heat of backstage lights.
And then, he looked up and locked eyes with you.
The golden thread between you flared violently, burning. Both of you flinched. Felix staggered back half a step, his hand flying to his chest, and you gasped as a searing warmth shot through your pinky like a lightning strike.
“Oh.” The word barely left his lips, but it rang out like a bell in a cathedral. Your whole body felt it.
“Oh,” he said again, softer this time. His eyes were wide.
You felt the heat in your pinky intensify, and the golden thread between you shimmered again, catching the light in a way that made it look like it was made of flame. It curled through the space between your hands like it had always belonged there.
Felix took a half-step forward, eyes never leaving yours. He lifted his hand slowly, fingers trembling slightly. “Is it… You?” he asked, voice nearly breaking on the last word.
You nodded. “I think so.”
Felix exhaled, and something in his posture released. His shoulders dropped slightly, like he’d been holding tension for years and was finally allowed to let go.
“Can I…?” he gestured hesitantly to your hand.
You didn’t trust your voice, so you offered your pinky forward in answer.
His fingers brushed against yours, and the moment they touched, the golden thread flared so brightly it lit up the space around you. And then it settled. It didn’t dim, it didn’t disappear, it just eased into a quiet glow.
Felix looked down at your hands, now linked pinky to pinky, and laughed softly under his breath. “It doesn’t hurt anymore.”
“Yeah,” you whispered. “Me neither.”
Felix looked up at you again as he moved his hand away. A small smile curved on his lips. “I don’t…I don’t even know your name.”
You let out a shaky laugh and said it. Just your name.
He repeated it back like a prayer.
“I’m Felix,” he said, though of course, you already knew. Still, hearing him say it that softly, like it was only meant for you, made a smile plastered on your face.
“I know,” you murmured.
Felix's smile widened just slightly, like he still wasn’t convinced this wasn’t all some fever dream.
But then, “Felix!” A sharp voice cut through the moment like a whip. You both jumped.
From inside the dressing room, a woman snapped at him, speaking to him.
Felix flinched. "잠깐만요! 잠깐만요!" he called back, waving a hand, eyes flicking between her and you. “Just, please, one minute!”
He turned to you, suddenly frantic. “Wait…wait, I have to…Can I? Here-” He fumbled in his pocket, yanked out his phone, and shoved it into your hands. “Please. Put your number in? So we can talk. Or meet. Tomorrow. I don’t, God, I don’t wanna lose you now. I just have an interview in ten minutes-”
You typed fast. Name. Number.
He took the phone back with a breath of visible relief, clutching it like it was suddenly the most important thing he owned.
“Tomorrow,” he promised, already backing away as his makeup artist stormed closer. “I swear. I’ll text you. I’ll find you. Please don’t disappear.”
You nodded, still dazed, heart pounding.
Then he was gone, swept back inside with a flurry of apologies and a final glance over his shoulder, golden thread trailing faintly behind him as the door shut.
You stood there alone in the hallway, the warmth of the thread still glowing at your pinky, and whispered into the quiet, just like you did on your eighteenth birthday:
“I think I found him.”
(A/N: Woah! Thank you for the support! -Deedee)
taglist (comment to be added): @hwangjoanna @shinygubbins @lizzygd @btch8008s @under--space @monniemons @chimmyn0chu @wickedbutlovely @hyunjinsculpture @beal-o @valkirymin @moonlitcelestial @wolfhallows4
#stray kids#skz#kpop#fanfic#kpop fanfic#skz fanfic#stray kids fanfic#felix x female reader#felix x reader#skz felix#stray kids felix#lee felix#felix#skz fanfiction#skz fandom#stray kids fanfiction
96 notes
·
View notes
Text
This whole thing with the "stolen 5K acc" BS is pitiful as it is laughable
'Cause help me understand something...
And for the sake of those not on X/twitter, imma try to summarize this whole shit-show as quick as I can.
Basically on the LAST VOTING DAY for AMAs, two large Namjoon Solo fanbases (one from Indonesia & one from India) suddenly claimed that "5K accounts" that were ALLEGEDLY "distributed" got ALLEGEDLY "stolen" and used to vote for Jimin instead.
But here's the catch!
A) They claimed not to know WHO did it, but still blamed PJMs/Jimin biased armys and spread this info on multiple social medias (to which armys blindly believed).
B) Said they would expose the culprit or culprits, but when prompted to SHOW said evidence they later claimed they "didn't have all the evidence yet".
C) They only showed SS of ONE email that ends in " @ gheol.com"

But when you type gheol.com on Google you get this
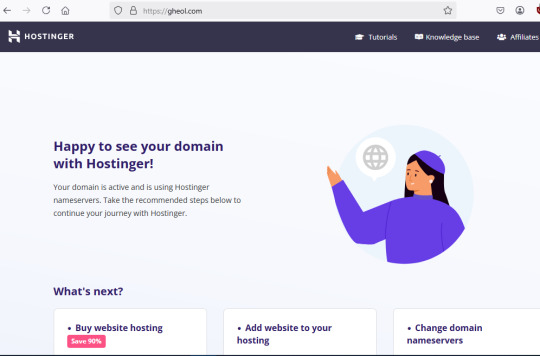
Its a DOMAIN, not an email address and if you type the whole address shown above they come up as INVALID.
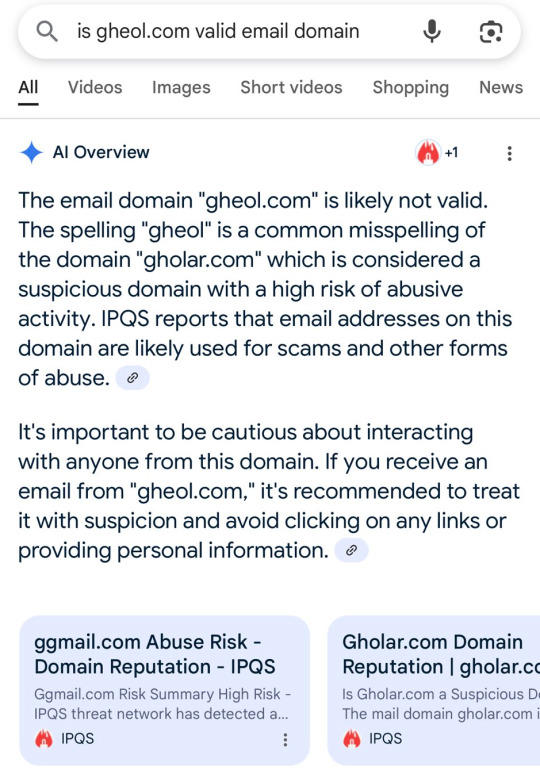
Now I've seen my fair share of strange email addresses in all my years of voting for Jimin and handling MULTIPLE emails.
But never have I seen that domain name.
So when shown this evidence, guess what these fanbases did?
One of them deactivated and the other went Private after dropping a bullshit statement that the reason they haven't "shown proof" is because of "lack of human resources" and not only that, but now they're stating that they will "hold off showing proof until AFTER the AMAs announce the winner."
WHY after? Simple.
A) They DONT have evidence, because these emails DONT EXIST. They just wanted to incriminate people who were voting for Jimin and on the same note discredit his achievements just like they've been doing since the nominees were first announced, because they DONT want Jimin to win.
B) If Jimin wins, they will claim its because of those "5K accounts that were stolen" and will continue their smear campaign against Jimin like they've been doing all along. (Just like when armys who never vote or steam for Jimin try to claim new achievements he receives).
And let me tell you guys something, as someone who's been helping the Admins of ThePJMSociety here on tumblr to find voters and distribute emails, I can tell you a thing or two of how this works.
ALL fanbases are well organized handling and distributing emails. There's literally a spreadsheet on Google Docs that we access that shows us the amount of emails BY NUMBER, the name of the voters, how many accs were distributed to each, the Admin that distributed them, and lastly a collum where we have to mark if the person voted that day or not. We also had to ask voters for screenshots evidence DAILY of them voting for Jimin and the admins responsible for the distribution of the emails who then log into those emails ourselves to make sure they voted for Jimin.
And for the record, it takes LESS than an hour to go through 200 emails to check the votes.
So you're telling me... that these fbs had NO idea WHO "stole" the emails... even though they have DIRECT access to them, are keeping track of all the ppl who ask for emails and all it takes is 5 seconds per account to check....?!
I'm calling bullshit to this whole circus.
And another thing that's fucking with my head is!
If these fanbases had SO MANY emails---millions of them and enough people to give support then..
Where is the support they claim to be giving to this member??
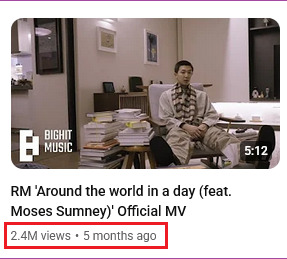
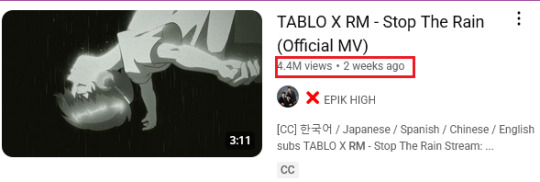
"Rapline Deserves Better" but then you see these numbers and these are real numbers from not only his solo fanbases but ARMY "ot7" too.
Meanwhile this is Jimin with PJMs, Jimin biased and GP up until Dec 2024
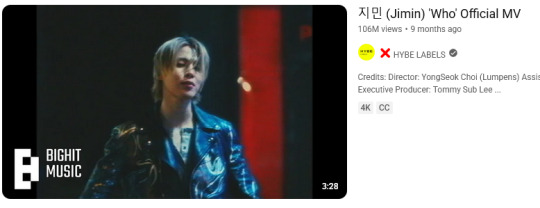
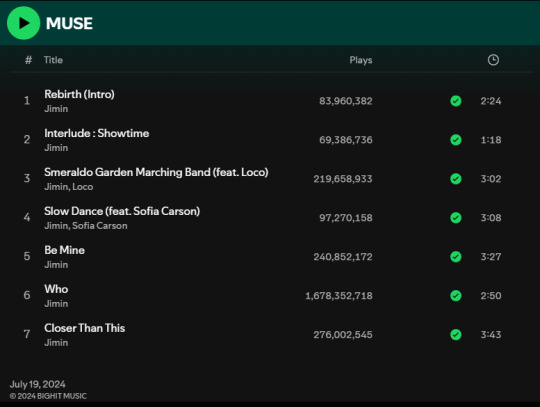


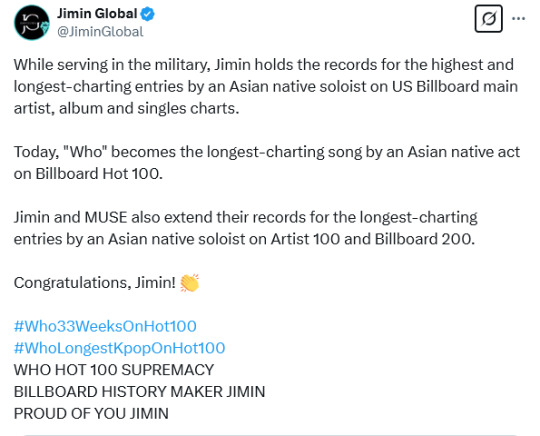

AND THESE ARE ONLY THE HIGHLIGHTS SINCE "MUSE" CAME OUT BACK IN JULY..
So idk about you guys but... something isn't okay in ApoBangoLand. Because RM isn't the only member getting piss poor support in his Solo stuff. The other 6 as well.
And its why they HATE PJMs and want us to disappear, because they can't stand seeing Jimin getting so much support outside of the fandom limits. And many are PRAYING for us to disappear when the group returns together (IF and WHEN that happens) so they can go back to shoving Jimin into a corner where they can forget about him until they need a punching bag again.
They're already openly showing their hate for Jimin by excluding him from important votings and nominations, they harass new and old reactors into accepting toxic narratives about Jimin, anyone who speaks up gets silenced and labelled a Solo-----imagine what will happen if we back down and quit our support? If we stop being loud and defending him from these hate campaigns? It'll be 2018 all over again.
And if Jimin DOES win on AMAs, we WILL celebrate it. Fuck it.
Fuck THEM.
We know they didn't vote for him, we know they didnt want him to win just like we know they never support any project related to HIM. We got receipts. So why should we hold back now?
#WE NEVER STOP#WITH JIMIN TILL THE END#BE LOUD & PROUD FOR JIMIN#jimin#park jimin#pjms#jiminie#pjm#bts jimin
61 notes
·
View notes
Text
Stomach Bug Part One
Sooooo here it is! My first fic back. It's not what I'm use to writing anymore. It's a lot ore talk and less description which isn't what I was aiming for, but I kinda like it as a little introduction to Jessie. He's also potentially my new favourite OC. I hope y'all like it. Appreciate any interactions, and also I'm pretty shit at proof reading so any mistakes... just pretend they aren't there! Also... formatting... I'm working on it. This is all done on my phone at present so... yeah, bare with!
-----------------------------------------
Jay walked into the social services building, throwing his bag down by his desk with a sigh before heading to the kitchenette to make some coffee. He looks around as it brews and clocks Jessie enter the building. He gives him a brief wave through the window that overlooks the office, which he returns. Jay nods towards the coffee pot that's almost ready, but Jessie shakes his head. This should have been the first thing that tipped Jay off that something wasn't right, but hindsight is always only helpful... well... in the future.
He sits down with his coffee, logging in and starting with his never ending list of things to do. Being Monday, that meant emails, categorising their importance, following them up, ensuring all his clients are safe, and then filling in any and all paperwork that comes from those emails. This was something that took up most of his Monday mornings each week, and his focus was entirely on his computer until he heard a groan from the desk opposite him. He looked up, looking at Jessie properly for the first time that day. His usually pink toned cheeks were nowhere to be seen, instead his face was, well, grey.
"Dude, you look fucking awful." Jay says with a sympathetic tone, a little worry creeping into his chest. Jessie doesn't get ill, unless there's dairy involved.
Jessie briefly flips Jay off, before groaning again, resting his head in his hands. "I feel like absolute death Jay, fuck off and leave me to die" he said, running one hand through his dark blonde mullet.
"Then why are you here you fuckwit? Go home." Jay scoffed, worry lessening as Jess was able to have the energy to be a dick. Rolling his eyes, Jay gets up and walks round to Jessie's side of the desk and placing a hand on his neck, " Dude, you are on fire." His worry was back just like that.
Jessie just whined in response, leaning into Jay's touch with a wince. The wince concerned Jay, because Jessie has the highest pain threshold of anyone he knows. "What hurts Jessie?" He says, crouching so they were eye to eye.
"My stomach. My head. My whole body. Everything" Jessie grumbled into his hands as Jay rubbed a gentle hand over his best friends back. Jay felt a burp rumble up of Jessie's chest, which by the time it came out was thick and wet.
"Alright, that was gross. And sickly. Do we need to move you to the bathroom?" Jay asked, but Jessie shook his head furiously. "Okay, okay. You need to go home my Dude. How'd you get in today? For the love of God tell me you didn't cycle in like this?"
Jessie winced again, but Jay knew that this time it was for being called out on being an idiot
"Of course you did, you absolute fucking moron" Jay said, shaking his head. "Let me go talk to Carla, see if she can cover my first afternoon parenting session so I can take you home. Hang tight"
By the time he'd located Carla, who as always was not in her office, and returned to the main office, Jessie wasn't there. His bag was still under the desk, so he hadn't been completely fever-ridden and decided to cycle home. So the next logical place Jay thought to check was the bathroom. And that's exactly where he found Jessie, heaving behind the closed door.
"Ah dude. I'm coming in." Jay said, not waiting for an answer before opening the door. The sight before him broke his heart. Jessie was crumpled in front of the bowl, white knuckling the edges as he heaved thick streams of vomit into the water. Jessie wasn't a big guy, and his small frame looked even smaller all hunched up. Jay grimaced, but crouched beside him and rubbed his back with a sigh. "Let it all up Jess, you'll feel better."
Jessie heaved continuously for the next few minutes, and Jay was starting to get concerned about the amount of vomit that was coming out of the small man, before he collapsed backwards. Jay grabbed him before he hit his head on the wall, positioning him so he was resting against his chest.
"Jayyyy" Jessie whined pathetically.
"Shhhhh, I know. I know." Jay said softly, gently rubbing a hand up and down Jessie's arm.
They sat like that for a few more minutes before Jay spoke again, "Jess? Are you good to move so I can take you home?"
"Dunno," Jessie whimpered, "Dizzy. Stomach hurts. Nauseous."
Jay hummed softly, "I'll help you up. Come on." He said, wrapping his arms round Jessie's chest and helping him stand. Jessie was like a ragdoll in his arms, and that concerned Jay. Just because Jessie was a smaller man, it absolutely should not have made him this easy to manhandle. And the fever he could feel rolling off him was not helping with the unease he was feeling.
Slowly they walked back to their desks to collect their stuff, Jay supporting him the whole time, and to the car. As they reached his car, he felt Jessie stiffen in his arms.
"St...stop"
But before Jay could react, Jessie was vomiting all over his shoes "Aw Dude, that's grim" he crinkled his nose but didn't move, supporting his friend to stay upright. "Alright, get it up Jess." Jay spoke softly, continuing a stream of reassurances as Jessie threw up again.
"'M done" Jess mumbled as he stumbled away from the large puddle of vomit by his feet, Jay just about caught him before he fell backwards.
"Woah dude, alright, I've got you. Let's get you home." Jay says softly as he sits Jessie down on the passenger seat, closing the door and quickly taking of his puke soaked shoes and chucking them into a plastic bag in the trunk of his car, before getting into the driver's seat. He started the car and saw his friend wince as the car started moving, watching his face pale further and his brow furrow. "If you need to throw up, please tell me beforehand, and don't puke in my car okay? I gotta pick Hope up after work and she'll be unimpressed if the car stinks of vomit"
"Don't... BAAruppp...talk about puke" Jessie said, burping a gag.
"Sorry, sorry. I'll stop" Jay apologised, resting his free hand on his friends knee and rubbing it lightly.
The rest of the drive was uneventful, and Jay was so glad that Jessie's apartment was only 15 minutes away from their office.
"How you doin' Jess?" Jay asked when he'd stopped, noticing his friend making no attempt to move, not even opening his eyes.
"My stomach" Jessie whined pathetically, arms tightening around his midsection.
"I know dude, I know. Let's get you into your apartment and into bed okay?" Jay sighed softly, lightly squeezing his arm before getting out and moving to the passenger side door. When he opened it Jessie practically fell out of the door
"Woah, Jess, alright. I've got you." He grabbed his friend by the shoulders and practically dragged him out of the car and into his apartment, so fucking glad for once that it was a first floor apartment.
Jay used his spare key and let them in when they made it inside the building, but before he could even get Jess over the threshold the man doubled over with a groan, arms tightly wrapping around his middle. He heaved, but nothing came up. But the heaving didn't stop, even as Jay manhandled him through to the bathroom and over the toilet. He held him up with one arm, rubbing his back soothingly with the other. Now he was more worried than he'd been previously, he'd never seen the man so sick, and they'd been friends for almost 8 years.
"Come on Jessie. You need to breathe man, you have nothing left to bring up. Slow breaths with me, in...out. and again. In...and out." He kept stroking his friends back, grounding him as he tried to regain control of his body.
Slowly Jessie's heaving turned to weak gags, then back to fast breathing. He let go of his death grip on the toilet bowl and collapsed forward, resting his head on the porcelain.
"Jay" he whimpered.
"I know Jess," he said softly, heart squeezing at the pitiful tone, "Think we can move you to your bed?"
Jessie whimpered, but attempted to start standing. With minimal help from the man, Jay managed to guide him into his bed, laying him down. Jessie curled up on his side, arms back wrapped around his stomach. "Jess, let me go get a bowl and some water. I'll be two seconds."
Jay grabbed a mixing bowl from the cupboard and a bottle of water our of the fridge, knowing his way around Jessie's place like the back of his hand. He quickly moved back into the bedroom, where Jessie was exactly where he left him. He put the bowl on the floor beside him before moving to the other side of the bed and sitting beside his friend.
"You need some water Jess" he said softly.
"It'll just come back up" he whimpered back.
"Jess...."
"No. Not yet."
Jay sighed, putting the bottle back down. "Okay, but soon."
"Go back to work Jay." Jessie mumbled sleepily.
"Aha funny. Not happening. I'll call Carla, she can take the whole afternoon caseload, it's not a lot."
"Jay, don't... be silly" Jessie replied with a pause between words as he winced.
Jay placed a sympathetic hand over Jessie's stomach, feeling it clench and burble sickly, and began tracing light and soothing circles. "I'm not. I'm being your best friend you twat. Now shut up and rest whilst I call Carla."
41 notes
·
View notes
Text
Download
Posted anonymously, 12th of February.
You know that feeling, when you meet someone interesting, and you want to know more? You know there’s more behind what they’re saying – so much knowledge, so much insight? When you can’t get enough, and wish you could connect to their brain and download everything, all at once?
You do know that feeling, right? I’m not the only one who gets that?
I met a girl online, let’s call her Amy. We were into the same things, and hung around on the same servers. I got that feeling. We were on the same wavelength. We sat up all night talking, for months. That was still too slow. The feeling got stronger.
Then, 5th of January: I dreamed that we were both robots. She had a port in her head. I had a cable attached to mine. I connected the cable and started the download.
She wasn’t online the next day or the day after. That was the longest we hadn’t spoken in months. I messaged her every day, but she didn’t reply. A month later, I still hadn’t heard from her.
But every night I dreamed about her. In the dreams, she had moved into town. We had the conversations we would have had online. The dream version of her felt just as real as the real version I was pining for. I knew I was dreaming – unusual for me – but didn’t mention it.
During the day, I found myself thinking about her, and… knowing things. I knew her sister’s address and her mum’s birthday. I remembered her first day at school. She hadn’t told me any of this. I was convinced my mind was making it up, inventing details to use in the dreams.
Sometimes, in the dreams, she said she missed her old town. But, 2nd of February: she sighed in relief and said she was finally free from that. This was her home now.
Three days later, I got a message from her mum. She had gone into Amy’s phone, seen my name and our messages, realised I was someone important to Amy – and now she was breaking the news to me. On the 5th of January, Amy had gone into a coma. On the 2nd of February, her condition had worsened suddenly, and they had switched off the life support. Amy was dead.
I was devastated. I couldn’t tell her that just last night, Amy had told me how glad she was she’d moved to where I lived.
You could say this is when I first broke with reality. But I know better.
My mind went back to the first dream. The download was supposed to be ‘copy’, not ‘move’. Who ever heard of ‘download’ being a destructive operation? That was the fantasy, not this.
You can see how I was already thinking.
I confirmed it when I logged into Amy’s email with the password I knew – that she would never have told anyone – and the password was correct.
The robots were metaphors, but somehow the act was real. I’ve stolen my best friend’s mind, and she doesn’t even realise.
The dream version is the real version now, I’m sure of that. She’s a whole other person inside of me. I can choose when to run her. When she isn’t running, every part of her is accessible to me – all her knowledge, all her memories, all her experience. Just as I wished. I could imitate her words or actions perfectly. And when she’s running, she has no idea that everything there is fake. She has no idea that she’s dead.
How do I tell her? Should I tell her? Should I run her at all?
Probably you don’t believe me. You haven’t seen the proof, after all. Maybe you think I’m making it up to cover something more mundane. Well, humour me. Pretend. I ran away from my home, my life. I’m hiding now. I can’t talk to anyone I know, not about this. I don’t know if I’m safe to be around, or safe to be online. What if I meet someone else, and it happens again? What if I decide I like it, and make it happen again?
I don’t know what to do.
What should I do?
Please help me.
Tag list (tell me if you want to be added):
@ask-de-writer @avery-victoria-winterlight @dierotenixe @leahnardo-da-veggie @lunadook
@mint-and-authoress @reliableslimegal @sandyca5tle @scrubbinn @theriomythic-lesbian
@void-botanist @wuwojiti @zzzestyy
22 notes
·
View notes
Text
I am you - Part 1 of 2 (Doppelganger story)
They always assume they would notice, that if something like this happened to them, it would be immediate and undeniable. People believe in dramatic revelations, in a single moment where the world tilts and the truth is exposed. They think of flickering shadows, distorted reflections, the impossibility of seeing their own face in places they do not remember being. But it never happens that way.
The process is slow, deliberate, and inevitable. A shift so gradual that, by the time they recognize it, it is already too late. It begins with something small—an exchanged greeting they cannot recall, a casual reference to an event they have no memory of attending. They assume it is stress, distraction, miscommunication, all reasonable things that allow them to dismiss the wrongness before it settles in. They do not understand that every moment of doubt is another step in the process.
I have been here for weeks. I know the way he moves, the cadence of his voice, the weight of his name. I have studied him long enough that I could be him better than he is. And soon, I will be.
______________________________________________________________
The first time he notices, it is so minor that he almost forgets it entirely. The barista in the café hands him his coffee and smiles as she says, “Back again?” He hesitates, shakes his head slightly, and tells her this is his first coffee of the day. She frowns for a fraction of a second before laughing it off, blaming her mistake on the early morning rush.
The second time, it is more difficult to ignore. A colleague stops him outside his office, asking how his meeting went. There is a note of expectation in their voice, something that tells him this is not a casual inquiry but a follow-up to an earlier discussion—one that, as far as he is concerned, never happened.
“I didn’t have a meeting this morning,” he says, forcing an easy tone into his voice.
His colleague raises an eyebrow, pulling out their phone. “You said you were heading to one just before lunch. Look—" They turn the screen toward him, showing a text message from his number. The words are familiar, structured exactly the way he would phrase them. He reads them over and over, but the memory of sending them does not come.
That should have been the moment he acknowledged that something was wrong.
But it wasn’t.
______________________________________________________________
Denial is powerful. Even now, as the weight of inconsistencies begins to settle, he fights it. He checks his emails, his call logs, his purchase history, looking for proof that something is missing, something altered. The problem is, there is nothing missing. There are no blank spaces, no files erased or conversations removed. Instead, there are things he has no recollection of doing—transactions at places he has not visited, messages that sound exactly like him, plans he would have made.
He tells himself it is stress, that he must have been distracted, that memory is unreliable. He does not realize that he is not looking for an answer. He is looking for permission to believe nothing is wrong.
That is why he watches the security footage. That is why he asks the night guard to rewind the tape, just to check. That is why, even before he sees it, he knows what will be there.
The screen flickers, and there he is, walking into the office building at 11:42 PM. He watches himself take the elevator to the fourth floor, swipe his access card, and step inside. There is no hesitation in his movements, no moment of doubt or pause. His posture is relaxed, his gait smooth and familiar.
The guard chuckles beside him. “Looks like you’ve been sleepwalking.”
He stares at the footage, waiting for some sign that it isn’t real, that there has been a mistake. But there is no mistake. He was home at 11:42 PM. He knows this with absolute certainty. And yet, here he is, caught in a moment that should not exist.
Sleepwalking.
It is easier to agree than to argue.
______________________________________________________________
The moment of realization, the true breaking point, is not in what he sees but in what he does not.
His phone registers calls he cannot remember, but they are to the same people he speaks to every day. His emails contain correspondence that follows his usual habits, his tone, his way of phrasing things. Even his bank records show nothing unusual—just a life continuing as it always has, perfectly ordinary, except for the quiet, insidious knowledge that it is no longer his.
The key doesn’t turn.
He frowns, tries again, pressing harder, but the lock doesn’t move. He checks the key, turning it over in his palm, but nothing is wrong.
Behind him, footsteps. A voice follows.
“Something wrong?”
He turns. The landlord is walking up, a small ring of spares already in hand. He barely glances at the door.
“My key isn’t working,” he says.
The landlord exhales, already sorting through the keys. “Yeah, had the locks changed this morning. Request came in from you a couple of days ago.” He slides a key free, presses it into his palm without hesitation. “Here. Just don’t lose this one.”
He stares at it.
“Why were they changed?”
The landlord shifts his weight slightly, giving him an odd look before shaking his head. “You tell me. You put in the request.” His tone is flat, uninterested, already moving past the conversation.
His fingers tighten around the key.
"Am I being charged for this?"
A shrug. “Yeah. Standard fee.” The landlord is already moving away.
The key will fit. It will turn.
I already have mine.
Something inside him lurches at the exchange. The way the landlord handed over the key without hesitation. The way there was no moment of doubt, no pause, no verification—just a decision that had already been made.
And then he sees me.
Standing at the end of the street.
18 notes
·
View notes
Text
In 2022 I wrote an op-ed for NBC News Think about leg hair, of all things. The piece detailed a monthlong experiment during which I stopped shaving. Aside from one paragraph about bodily autonomy and Roe v. Wade, I thought it was a mild article. Boring, even.
The internet disagreed. Within an hour of publication, I started getting angry, all-caps emails. Then it started on Twitter. I was called everything from stupid and self-absorbed to a Sasquatch. I was accused of hating men and pressuring women.
The deluge lasted nearly two weeks. By the end of it, I had dozens of nasty emails, nearly a thousand social media notifications, and zero idea how to handle what I’d experienced.
Unfortunately, these instances of online harassment are becoming more common. In 2021, the Pew Research Center reported that 41 percent of US adults had experienced online harassment; the Anti-Defamation League reported an increase to 52 percent in 2023. Public and semipublic figures are especially at risk, as noted by recent studies on American journalists, Zimbabwean journalists, and female members of parliament in Sweden.
But the truth is, on social media anyone with an account can experience harassment. Here’s what to do if it happens to you.
Document Everything
Knee-deep in hate mail, I reached out to a former thesis adviser who’d written op-eds. How had he handled the trolls?
His reply: Document everything. If you have to report the harassment to a social platform or to law enforcement, you will need a body of evidence that proves the harassment.
Save the nasty emails in a special folder, either manually or by using keywords to filter and route all of the relevant mail automatically.
On social media, screenshot what people say. Doing this gives you lasting digital proof, which is important if the trolling comments disappear later on, either because the trolls deleted them or because someone reported the comments, which led to them being removed. Save all of these screenshots in a folder that can easily be shared with anyone investigating your harassment.
Documenting harassment is common advice, featured in resources ranging from writing-specific organizations like PEN America to wider organizations like the University of Chicago and the National Network to End Domestic Violence.
Don’t Respond
Another common piece of advice is “don’t feed the trolls.” In theory, if you don’t react to harassment, the trolls get bored and leave. Some have argued that this advice has failed us, as it puts the onus on the victim to stop the cyberbullying; it suggests that it’s not the trolls who need to stop but rather the victim who needs to turn the other cheek.
This is a fair critique; social media platforms should build better moderation systems and restrict users who breach standards on harassment. Ideally, events like the 2024 child safety hearing before US Congress will lead to changes that make the internet safer for everyone. In a perfect world, the onus is on Big Tech.
But internet safety is a work in progress, and in the meantime it’s on us to decide how we want to respond. Many of the accounts spamming me were obvious trolls. They had incendiary usernames and profile pictures. Looking at their comments, which were antagonistic at best, I knew I wouldn’t change their minds by responding. Nothing I could write would make them consider my point of view.
So I followed the American Psychological Association’s advice and let the storm pass. I logged off social media and routed the nasty emails into a special folder, out of sight. I spent my energy on things I enjoyed instead, no trolls involved.
Or Maybe Do Respond
Walking away isn’t the best option for everyone. If you choose to respond, there are both indirect and direct ways to address harassment. The former could include muting threads or blocking accounts. You could also report comments or users for behaviors that breach community standards, such as hate speech, threats, and bullying (which most platforms claim to prohibit). These options may prevent the same trolls from harassing you, or another user, in the future.
If you feel safe and want to respond directly, consider counterspeech, a strategy that addresses and undermines hate by redirecting the conversation in a constructive way. Some choose to reclaim hashtags, such as the K-pop stans who in 2020 flooded the #WhiteLivesMatter hashtag with K-pop videos.
Others create larger discussions around hateful posts, typically focusing not on the troll but on the content of their argument (so, not “You’re sexist” but “Saying XYZ is problematic because …”). This is exactly what I did, some six months after my experience, when I wrote about hate mail for HuffPost, focusing on sexism and the importance of dismantling it. Reframing the conversation helped me feel less powerless.
Though organizations like the United Nations recommend counterspeech, some research has suggested that it may be ineffective: While a 2021 study on anti-Asian hate found that counterspeech discouraged hate, another study on racism and homophobia saw mixed results.
Do Something You Enjoy
Whether or not you respond, give yourself time to work through your feelings. Do something you enjoy, like going to the gym, meditating, or playing your favorite video game. Anything goes!
Social support, in particular, is important for processing your experiences. This is because one of the goals of online harassment is to make you feel isolated; intentionally enjoying time with loved ones can combat this. An older 2014 study noted that social support can come from anyone in your life, ranging from your peers to your family. More recently, a 2020 study listed the myriad benefits of social support for those experiencing bullying, including increased confidence and decreased anxiety.
So text your friends and coworkers. Make dinner plans with family. Rant to your partner—or ask for a distraction. Any and all of these can help you feel less alone. You can also seek professional advice via a therapist or a cyberbullying hotline.
If you decide to take an extended break from the internet, ask a friend you trust to keep an eye on your social accounts. They can continue to take screenshots of new harassment and notify you if the frequency of incidents increases.
If the Harassment Escalates
If rude comments turn into stalking, hacking, doxing, or death threats, it’s time to contact the authorities and get legal assistance. Continue to document everything; you’ll want a body of proof to ensure you’re taken seriously. If you’re in immediate danger, call emergency services.
Practicing good cyber hygiene can help you protect your information. To deter hackers, use strong passwords, which are longer than 16 characters and include numbers and special characters. Don’t reuse passwords, and set up multifactor authentication to ensure that you’re notified if someone tries to log in to your account.
To deter doxing, stalking, and further harassment, adjust your privacy settings on social media. If possible, set your accounts to private until the storm passes. Also, depending on the platform, you should be able to limit the ability to reply to your posts so that only people you follow can republish your posts or leave comments. You can also just disallow comments entirely. If you have both professional and personal accounts, keep them separate so that work-related harassment is less likely to follow you home.
You may want to limit who can see your location data on social media, since many platforms tag every post with geolocation data unless you opt out. This is usually something you can turn off in your profiles’ privacy settings. Additionally, browser extensions like Privacy Party can help you keep your privacy settings on social media up to date automatically, so you don't have to think about it.
If things get so bad that you feel it's safest to minimize or erase your digital footprint, paid services like Delete Me can remove identifying information like your address, phone number, and social media activity from hundreds of online databases and data brokers. This makes it much harder for people to uncover this information in web searches. Services like Tweet Delete can automatically delete years worth of social media posts, replies, and likes—either wholesale or within a specific range—from your accounts.
Online harassment can be isolating and terrifying, but with a plan, you’ll be prepared to respond—and to mitigate its impacts on your life.
39 notes
·
View notes
Text
we actually almost got my step mom in legal trouble after she like left my dad i caught her signing on facebook and messaging one of my friends pretending to be me. because she started texting him literally while i had our dms open, and she literally responded with "yaaaaaaas (purple heart)" and i was like HUH? HM? WHAT? WHAT? SORRY I DIDNT SEND THAT. and i deleted the chat on impulse (sad. no proof) and checked the facebook log ins and sure enough her ip was there. when my dad confronted her over email she said she did it because i was threatening to kill her and her son (again. something she was constantly saying that i was planning to do) and that she was just trying to collect proof and that i was calling her over and over on a burner phone. which my dad obviously knew i didnt have because he had like a hawk eye on me at that period of time due to recent hospitalizations. she also said she knew the burner phone was me because it was under the name "michael" every time i called, but the thing is she shouldn't have even known i was going by that name because i was only going by it privately with my friends. she incriminated herself.
3 notes
·
View notes
Text
Navy Recruitment Result: Everything You Need to Know
Joining the military is a dream for many people searching for to serve their united states, gain valuable skills, and enjoy a disciplined and adventurous way of life. The recruitment system is rigorous and includes multiple levels, which includes written tests, bodily exams, clinical examinations, and interviews. Once those stages are completed, candidates eagerly await their military recruitment consequences. In this newsletter, we will discover the navy recruitment end result procedure, how to test outcomes, elements affecting selection, and what comes subsequent for a success applicants.
Official website for Navy recruitment result download
Understanding the Navy Recruitment Process
The army recruitment manner is designed to choose the most capable applicants. It involves several tiers:
Notification and Application
The military releases legitimate recruitment notifications detailing eligibility standards, utility dates, and choice approaches.
Candidates submit their packages online or offline in the designated time-frame.
Written Examination
Most military recruitment drives encompass a written exam protecting subjects like Mathematics, General Knowledge, Science, and English.
The examination assesses a candidate’s aptitude and information applicable to naval service.
Physical Fitness Test (PFT)
Candidates who skip the written examination ought to undergo a physical health check.
The check typically includes strolling, push-ups, sit-ups, and different endurance sporting activities to determine bodily fitness ranges.
Medical Examination
A thorough clinical take a look at-up is performed to ensure applicants meet the desired scientific standards.
Any medical conditions that would intervene with naval obligations may additionally cause disqualification.
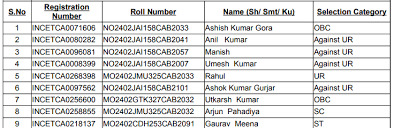
Interview and Document Verification
Candidates who clean the preceding degrees are called for an interview.
Documents together with academic certificates, identification proofs, and caste certificates (if relevant) are demonstrated.
Final Merit List and Training
Based on usual overall performance, a final advantage listing is prepared.
Selected candidates are sent to naval training academies to start their adventure in the military.
How to Check Navy Recruitment Results
Once all stages are finished, the navy recruitment result is released via diverse official channels. Here’s how applicants can test their consequences:
Official Website
The number one supply for recruitment results is the professional army recruitment website.
Candidates ought to log in with their registration info to access their results.
Email and SMS Notifications
Some recruitment our bodies send end result notifications thru electronic mail or SMS to applicants.
It is essential to provide correct contact information all through the software manner.
Employment News and Newspapers
Results will also be posted in main employment newspapers and regional courses.
Recruitment Offices and Help Desks
Candidates can go to the closest army recruitment office to inquire about their effects.
Factors Affecting Selection in Navy Recruitment
Not all applicants who follow are selected. Several elements affect the selection system:
Performance in Written Examination
Scoring high marks within the written test will increase the probabilities of selection.
Physical Fitness Levels
Candidates should meet the desired health standards.
Poor bodily performance may cause disqualification.
Medical Standards Compliance
Candidates have to be in accurate health with none scientific conditions that restrict naval service.
Availability of Vacancies
The variety of available positions plays a position in figuring out how many applicants are selected.
Background Verification and Discipline
A smooth historical past and disciplined behavior are critical for choice.
What Comes Next for Selected Candidates?
If a candidate’s name appears within the final merit listing, they ought to prepare for the following steps:
Joining Letter and Training Instructions
Selected candidates acquire a joining letter with details in their schooling agenda and reporting date.
Reporting at Training Center
Candidates need to file to their assigned training center on the desired date.
Induction and Orientation
New recruits go through orientation packages to familiarize them with naval lifestyles.
Basic Training
Training consists of bodily conditioning, naval drills, swimming, technical training, and educational guides.
Specialization Training
After primary training, recruits may additionally undergo specialised education based totally on their roles within the army.
2 notes
·
View notes
Text
Tonight is the first night of Chanukah, and I have decided that to “celebrate” I will be contacting my representatives every day for the next 8 days to call for a permanent ceasefire in Palestine, and I urge you to do the same. There are countless easily accessible templates for emails, phone calls, and letters that take less than 5 minutes to complete and put pressure on our reps, who are aiding and abetting a literal genocide. If you are able, you can also donate to reputable esim providers (the Cartoonist Cooperative has really easy links, and you can get art) to keep people connected thru internet blackouts
As incentive, I am offering a fullbody colored sketch to anyone who chooses to dm me after these 8 days with proof of contact with their reps (dated screenshots of emails, dated call logs, etc. just nothing with your personal info). This is not a large scale, highly organized project; this is just an option that hopefully inspires you to take consistent action.
I think there is a horrible irony in the Zionist love of Chanukah; how can you see yourself represented in a story about standing against oppressors and still enact the same violent oppression against those you deem lesser. You are not a hero, you are not brave, you are a coward laughing as people are murdered in your name, and your memory will only bring shame
The real bravery is that of the Palestinian people, who despite the odds stacked against them continue to survive. This is far more in the spirit of a holiday about resistance than a celebration of genocide will ever be.
We will not be silent. We will not give up on the people of Palestine. They will survive and be free.
I hope this is clear enough to make sense to people, please feel free to let me know any questions/concerns you may have. Chag sameach
#idk if this makes any sense at all but yeah#hopefully everyone has already been in contact with reps but maybe this will inspire some specific action for some people#and again this isn’t wide scale it’s just me it’s not a big organized thing so just lmk if u have questions
18 notes
·
View notes
Text
Breaking Customer Promises and The Harms of Online Business
I ordered a laptop from BestBuy on sale. The next day, I received an email that the order was cancelled. I pulled up a chat to ask why exactly my order was cancelled.
They don't deliver to hotels.
Okay. Sure.
I asked if I could change the address to my work place and was told to fully re-order everything and I would receive a refund for the post-sale price difference. Okay. Sure.
I received the laptop, and it wouldn't turn on.
I took it to my nearest BestBuy. They swap it out easy as pie. I think to myself, "I should've just gone here from the beginning."
Ah, but no matter. I have a laptop and it works great!
I wait a week. No refund. I call them. They assure me, I'll receive an e-mail with the refund in 48-72 hours. Okay. Sure.
I wait another week, just to give them space to process the influx of end of year orders. No refund. I call them again. "The billing cycle takes a month," they tell me, "the refund will come in around 30 days."
Okay. Sure.
It's been four months, friends, and I finally reach out again. Armed with my case ID number, three BestBuy supplied chat logs of customer service agents promising me my refund, a free day and a whole lot of righteous fury. How could they deny me this? I explain all of this to John, the customer service agent. And what does he say to me?
"Sorry to hear this, it is very disappointing, however I will try to resolve your issue as soon as possible. I would like to inform you that, we do not have an option to honor the price match for the old price for canceled order."
…What? Excuse me? I explain again, "They've all told me differently. I have evidence of your company representatives promising me this refund."
"I’m truly sorry to hear about your experience and I’m sorry you are having to face this issue. Please accept our sincere apology for the inconvenience caused and incorrect information provided by previous agent. As it is canceled order we do not have an option to honor the previous sale price." John tells me, merciless.
But it wasn't just one agent, I argue. I have proof. They all told me the same thing. So, I Karen. I admit it, I tell him, "Let me speak to a supervisor."
"I can surely arrange for a supervisor, but I want to let you know that I've thoroughly investigated all potential solutions in this situation. Believe me, if there were any available options to provide you with refund, I would have already taken care of it. Getting a supervisor wouldn't have been necessary since I've already explored this option on your behalf." John tells me.
And here's the thing, friends, I do believe him. He doesn't seem like a bad guy, even though he's complicit in stealing money from me, but in the words of an anachronistic Anne Boleyn, like what was I supposed to do? What's the worst thing that can happen, John, if I ask to speak to your manager? Explain it to me.
Is it a waste of my time? Four months after the theft occurred, to chase down $430 like some cadaver dog sniffing up and down a river after the frost melted to see if I can pick up on a trail? After four months, will one more conversation, one more long shot, really be the straw that breaks my back?? At worst, what will happen, John? Will I waste more company time? Good. I hope I waste at least $430 of company time. Frankly, I hope I waste more.
A supervisor is reviewing the chat logs now before they get back to me. They're a floor supervisor, but they didn't provide a name. Pray for me, friends.
#best buy#customer service hell#customer experience#i wrote all of this while the supervisor is back reading#i don't think i'm getting a refund guys
2 notes
·
View notes
Text
I’m about to start keeping a running log of work calls. I can’t with these people today.
So far:
Call 1: called wrong department checking on the status of an order they didn’t pay for yet.
Call 2: another person cheated by the unfair shift of RGB to CMYK who wanted us to fix it immediately and ship 25 hardcover custom printed books with a one day turn around.
(Got Nam flashbacks since I just unloaded a crazy person who complained about our commercial grade print quality after comparing it to a “superior” FedEx spiral bound book that used completely different substrates. Good luck mass producing that.)
Call 3:
Them: “I’m taking a look at my proofs and I noticed the designer used the image I asked them to use. So that means I can use it, right?”
Me: *already knows where this going* “ What do you mean?”
Them: “well I found it online when I was searching Google so I assumed it’s fine to use. Since it’s in the proof now I guess that means I can use it.”
(This happens A LOT too. People assume that because they can find it on Google, it’s free use for a self-published book cover. We have to then gently explain copy and usage rights. This is after the client specifically signed an Intellectual Property Rights disclaimer prior to check out certifying they created all of the content.)
Now onto email time and brief reprieve from today’s nonsense.
4 notes
·
View notes
Text
Disney Dreamlight Valley: Dreamsnaps
So, Disney Dreamlight Valley came out with something called Dreamsnaps. It is a weekly photo submission competition to earn free moonstones. This has pro's and con's, but this was-to me-one of the first unique things this game did. But, like anything else regarding this game, there was not much explained about it.

Before we even get to the ability to do a Dreamsnap, this will start with Venellope's quest. She is glitching and you take a photo and submit it to "fix" her and that starts your dreamsnap journey.
So on Week 1, Dreamsnap Wednesday's, you get a prompt. It will either be a Decoration Challenge or an Outfit Challenge. I noticed a trend where it alternates Decor one week, then Outfit the next week. There will be 2-3 Mandatory tags you have to hit, and 2 Suggested tags. You can sort furniture or clothes by the tags. Every system has a different button for this, but I myself play on Nintendo Switch. Once you are ready to go-you take a photo and click "Submit Dreamsnap". There is also a Dreamsnap Tab in the start menu.
On Week 2, you vote for the submissions you like best. There is no limit to how many votes you cast, you will look at 2 photos and click which one you like better. The minimum amount of voting will get you 50 moonstones per week.
On Week 3, you get your results from that particular challenge in your mailbox (in game). You will get a score, based on how well you hit the mark for the mandatory/suggested tags, and a ranking based on people's votes. The rewards are varying amounts of moonstones and pixel dust. The pixel dust adds up and helps you level up from level 1 to level 10. There is a reward at every level, with a big trophy at level 10. At the time of writing this, I am at Level 9.
The catch is this is ongoing with a new challenge coming weekly. So on any given week you are voting on something, while submitting something else, while receiving the results of something else entirely. So I started keeping track of what challenge was what, the scores, and my submissions. It is possible to send the photo you are planning to submit to your phone, but you need to do so after you take it but before you submit it. Once you take a photo, there is now way to look at previous photos taken to send it to your phone. You send it by way of scanning a QR code.
Now, at the time of writing this post, and since I have been playing since the beginning of the prerelease-I have done 32 dreamsnaps. One would think that by now, I might know what I am doing? If you ask my mom, who I help each week with the submissions, I am a great dreamsnap teacher. But my scores are all over the place, so I decided to look at the numbers and see what a proper analysis would tell me.
For me, I treat every dreamsnap as if its both decor and outfit, hoping that will help my score. One of the problems is, one part of the "win" is objective and the other part of the "win" is subjective. I also have played this since the beginning, which means I have a fully decorated Valley-there is a limit on how many items you can have and I am under it but just barely, but its not like its a baren wasteland. Also, you can not have any "Touch of Magic" items in your photo. No custom creations can be seen or unseen, this goes for clothes or furniture. Having characters from the Valley in with you seems to help, you can also do different poses with different animals when in camera mode. The premium shop changes on Wednesday's as well, save up for the good stuff there.
The Proof is in the Numbers:
I logged my results on a note on my phone, emailed them to myself, and put them into a google sheet. Here is what I found:
For combined outfit/decor
I average a 45.47 score
I average a 56,914 ranking
I average 554 moonstones
I average 139 pixel dust
For Outfit alone,
I average a 48.12 score
I average a 54,096 ranking
I average 646 moonstones
I average 142 pixel dust
For Decor alone,
I average a 42.99 score
I average a 59,556 ranking
I average 468 moonstones
I average 137 pixel dust
My Best Dreamsnap:
My best submission is Winter's Here (#24). An outfit challenge, 77.59 score, 11,114 ranking, 2500 moonstones, and 178 pixels.

My Worst Dreamsnap:
My worst submission is Arendelle's Showcase (#25). A decoration challenge, 26.72 score, 85,353 ranking, 300 moonstones, and 127 pixel dust.

Best Decoration Dreamsnap:
My best one is actually one earlier, but I was not saving them at the time. The one I can show is Holiday Cheer (#21). Decor challenge, 56.87 score, 58,567 ranking, 600 moonstones, and 157 Pixel Dust.

Worst Decoration Dreamsnap:
The worst one is It Came From Outer Space (#27). Decor Challenge, 23.85 score, 59,242 ranking, 300 moonstones, and 124 pixel dust.

Best Outfit Dreamsnap:
While my best submission ever is already posted, I will show this one that was my higest ranking one. A Day at Disney (#22). Outfit challenge, 57.46 score, 15,289 ranking, 1500 moonstones, and 158 pixel dust.

Worst Outfit Dreamsnap:
My worst one is not saved, maybe a good thing in retrospect? But I will show you Under The Sea (#20). Outfit challenge, 32.46 score, 85,575 ranking, 300 moonstones, and 133 pixel dust.

Tips:
No touch of magic items
Make sure Decor and Outfit are on point
Bring in characters
Pose with pets
Buy clothes and furniture, you never know when you are going to need what.
Pay attention to the premium shop, you never know when you could use the stuff there.
Hoard supplies to be able to make stuff at a crafting table to be able to use for photos.
Decorate the valley, within the limit.
Use all the options in the camera: poses, shot types, filters, frames.
This was an interesting dive into whether or not the system is rigged or what I could do better. If you want to look at your own scores, take a look at your mailbox. What tips and tricks would you add to this post?
#rant#gamer#gamer girl#nintendo switch#disney dreamlight valley#disney#pixabay#how to#dreamsnaps#family#camera#photo#photography#mandatory#suggested#tags#score#ranking#moonstones#pixel dust#decoration#outfit#challenge#vanellope#wreck it ralph#touch of magic#qr code#tips and tricks#premium shop
3 notes
·
View notes
Text
My unusual take on a horror trope!
I wrote this story a while back, and put it up in two parts. I am still pretty new to Tumblr, and don't really know how to engage, but I feel this story deserves to be aired. Have a read and let me know... ***
They always assume they would notice, that if something like this happened to them, it would be immediate and undeniable. People believe in dramatic revelations, in a single moment where the world tilts and the truth is exposed. They think of flickering shadows, distorted reflections, the impossibility of seeing their own face in places they do not remember being. But it never happens that way.
The process is slow, deliberate, and inevitable. A shift so gradual that, by the time they recognize it, it is already too late. It begins with something small—an exchanged greeting they cannot recall, a casual reference to an event they have no memory of attending. They assume it is stress, distraction, miscommunication, all reasonable things that allow them to dismiss the wrongness before it settles in. They do not understand that every moment of doubt is another step in the process.
I have been here for weeks. I know the way he moves, the cadence of his voice, the weight of his name. I have studied him long enough that I could be him better than he is. And soon, I will be.
The first time he notices, it is so minor that he almost forgets it entirely. The barista in the café hands him his coffee and smiles as she says, “Back again?” He hesitates, shakes his head slightly, and tells her this is his first coffee of the day. She frowns for a fraction of a second before laughing it off, blaming her mistake on the early morning rush.
The second time, it is more difficult to ignore. A colleague stops him outside his office, asking how his meeting went. There is a note of expectation in their voice, something that tells him this is not a casual inquiry but a follow-up to an earlier discussion—one that, as far as he is concerned, never happened.
“I didn’t have a meeting this morning,” he says, forcing an easy tone into his voice.
His colleague raises an eyebrow, pulling out their phone. “You said you were heading to one just before lunch. Look—" They turn the screen toward him, showing a text message from his number. The words are familiar, structured exactly the way he would phrase them. He reads them over and over, but the memory of sending them does not come.
That should have been the moment he acknowledged that something was wrong.
But it wasn’t.
Denial is powerful. Even now, as the weight of inconsistencies begins to settle, he fights it. He checks his emails, his call logs, his purchase history, looking for proof that something is missing, something altered. The problem is, there is nothing missing. There are no blank spaces, no files erased or conversations removed. Instead, there are things he has no recollection of doing—transactions at places he has not visited, messages that sound exactly like him, plans he would have made.
He tells himself it is stress, that he must have been distracted, that memory is unreliable. He does not realize that he is not looking for an answer. He is looking for permission to believe nothing is wrong.
That is why he watches the security footage. That is why he asks the night guard to rewind the tape, just to check. That is why, even before he sees it, he knows what will be there.
The screen flickers, and there he is, walking into the office building at 11:42 PM. He watches himself take the elevator to the fourth floor, swipe his access card, and step inside. There is no hesitation in his movements, no moment of doubt or pause. His posture is relaxed, his gait smooth and familiar.
The guard chuckles beside him. “Looks like you’ve been sleepwalking.”
He stares at the footage, waiting for some sign that it isn’t real, that there has been a mistake. But there is no mistake. He was home at 11:42 PM. He knows this with absolute certainty. And yet, here he is, caught in a moment that should not exist.
Sleepwalking.
It is easier to agree than to argue.
The moment of realization, the true breaking point, is not in what he sees but in what he does not.
His phone registers calls he cannot remember, but they are to the same people he speaks to every day. His emails contain correspondence that follows his usual habits, his tone, his way of phrasing things. Even his bank records show nothing unusual—just a life continuing as it always has, perfectly ordinary, except for the quiet, insidious knowledge that it is no longer his.
The key doesn’t turn.
He frowns, tries again, pressing harder, but the lock doesn’t move. He checks the key, turning it over in his palm, but nothing is wrong.
Behind him, footsteps. A voice follows.
“Something wrong?”
He turns. The landlord is walking up, a small ring of spares already in hand. He barely glances at the door.
“My key isn’t working,” he says.
The landlord exhales, already sorting through the keys. “Yeah, had the locks changed this morning. Request came in from you a couple of days ago.” He slides a key free, presses it into his palm without hesitation. “Here. Just don’t lose this one.”
He stares at it.
“Why were they changed?”
The landlord shifts his weight slightly, giving him an odd look before shaking his head. “You tell me. You put in the request.” His tone is flat, uninterested, already moving past the conversation.
His fingers tighten around the key.
"Am I being charged for this?"
A shrug. “Yeah. Standard fee.” The landlord is already moving away.
The key will fit. It will turn.
I already have mine.
Something inside him lurches at the exchange. The way the landlord handed over the key without hesitation. The way there was no moment of doubt, no pause, no verification—just a decision that had already been made. And then he sees me.
Standing at the end of the street.
He does not need to ask who I am. The answer is already forming, a terrible certainty clawing its way into his mind.
I am wearing his coat, the one he left draped over his office chair this morning. I have his keys, resting lightly in my hand. I do not move toward him. I do not have to. The space between us is already shifting.
He calls out, but the sound catches in his throat. He expects a confrontation, some kind of argument, a demand to explain. But there is no need for any of that, because I have already won.
He runs.
He doesn’t know where he’s going, only that he needs to move—as if motion itself will tether him back to reality, as if he can outrun the thing that is already replacing him. He will go to someone he trusts. A friend, a coworker, someone who can confirm that he is real. He will hear his own name spoken aloud, feel the weight of recognition, and convince himself that it is enough.
But I have already spoken to them. I have already passed that test.
And when he arrives, breathless, frantic, his words tumbling over themselves in his desperate need to be understood, they will hesitate.
Not out of fear. Not out of uncertainty.But with the weary patience of someone already prepared for this.
Because I was here first.
They will look at him the way one looks at an old argument resurfacing—exhausted, expectant, as if waiting for him to tire himself out. Their responses will falter, not because they doubt his presence, but because they have already had this conversation. Because they remember a more rational version of him, days ago, shaking his head and saying, I know it sounds crazy, but I just need you to listen.
Because they reassured him then. And he is back again, still unraveling.
He will ask questions and find that I have already answered them. He will try to prove something and find that I have already done so in his place.
Someone will sigh. Someone else will say, Hey, man. We talked about this.
There will be no dramatic revelation, no singular moment where the world turns against him.Just a slow, dawning understanding that it already has. That it is too late.
That I am already him.
______________________________________________________________ Sometimes they try to track me down. The ones who understand something is happening. The ones who refuse to let go. I let them. We fight, they escape—just.
They think it was luck. They think it meant something. That they still have time.
It helps at the end.
But I have planned the end.
______________________________________________________________
He finds me in the apartment. His apartment.
I have been expecting him. I sit at his desk, my hands resting on the familiar grain of the wood, his name flickering on the screen of his laptop. The room is arranged as he left it, as he always leaves it, because I know him.
I have had time to learn.
I watch him from across the room, waiting for him to say something, waiting for the last resistance that always comes.
He stands in the doorway, chest rising and falling in shallow breaths, staring at me with the expression of a man looking at something impossible.
"Who are you?" he asks.
His voice is hoarse, like he already knows the answer.
I tilt my head slightly, observing the small, involuntary movements that I have already perfected. He doesn’t understand the significance yet, but he will.
"I am you."
The silence between us is thick with unspoken things.
His gaze flicks to the table, to the objects that should be his. The phone, the keys, the wallet resting beside the laptop. Every detail accounted for. Every possession in its proper place. But they are not his anymore.
They never were.
He takes a step forward, as if proximity will solidify his presence, will anchor him back into the life that is already leaving him.
"I don’t understand," he whispers.
But he does.
He knew the moment he saw me. He knew before that, even, though he buried it under denial, logic, resistance. The world has already chosen. He is just catching up.
His fingers twitch at his side. A choice, unmade. A final instinct to fight for something he has already lost.
I shake my head slowly. "It’s over."
He exhales sharply, something breaking inside him, something that will never be repaired.
The door behind him is still open. He turns toward it, and for a brief, fleeting moment, I wonder what he sees.
I do not stand. I do not need to.
He hesitates, fingers pressing into the doorframe. His breath is uneven, his shoulders tight. The moment stretches too long, like a held note just past its natural end.
And then, something shifts—not the air, not the light, but the space itself. It is slight, almost imperceptible, just enough to be felt rather than seen. I notice it, and so does he.
His grip slackens, shoulders easing as the last resistance uncoils from him—not in surrender, but in recognition. Whatever he sees beyond the threshold, it does not surprise him. And then, he steps forward. Not into the hallway. Not into the world he thought he knew.Into the space that was always waiting for him.
The door remains open. The world beyond is unchanged. But where he stood, there is nothing left to correct.
I sit in his chair, in his home, the hum of his existence now mine to inhabit. My fingers rest lightly on the desk, the weight of them precise, effortless. I inhale once, adjusting to the quiet, letting the space settle around me.
I have taken what I came for.
But there is still more to do.
I check my phone, scanning the list of unread messages. Meetings scheduled, people expecting me. I will need to go to them soon, continue the process, cement my place. There are still connections to be made, details to refine.
And then, I will be him completely.
As I stand, stretching slightly, I glance toward the door once more.It is still open.And for the briefest moment—just for an instant—I feel the weight of the place where he has gone.
The air is colder.
Something watches.
I do not linger.
I close the door.
And then I step forward into the life that is now mine.
7 notes
·
View notes
Text
I realize that as an Admin my purpose in this office is to support others by doing grunt work and I am happy to do that grunt work (mailing, shipping, filing, calling, figuring out the logistics to do weird frustrating things that we haven't done before) but it comes with the expectation, nay, the hope that my colleagues who get paid SIGNIFICANTLY more than me will at least do the bare minimum of showing up or checking their emails in an 8 hours span and answering questions like "hey what's the FedEx log in since you're the only one who has it and refuses to let anyone else make use of it for some bizarre reason other than your imagined self importance and have now disappeared off the face of the earth for two months leaving me to make another FedEx business account in my own name so I can ship out proofs to the printers on time"
#it's not the missing work. it's the complete and utter lack of communication and disregard for the rest of us.#I missed lots of work this last year. I missed over 12 weeks of work. and everyone I mean everyone knew when I'd be out of office#I had three types of contingency plans available for when I'd be out of office and I'm just a f****** administrator#this woman is a coordinator for an entire department and she doesn't bother to update any calendars whatsoever#we're just left to guess when she might or might not show up and pick up the pieces and hope for the best#yes all I had to do was make an account with FedEx and mail a package and yet it took 3 hours because of FedEx's website#if she had answered her email or the DMs this could have been resolved in 20 minutes
2 notes
·
View notes
Text

out of uniform: sorry for not being around too much during the weekend. in regards to the post i made to explain some things, i decided to venture down memory lane, so to speak, about an incident mentioned in that post that i feel like the authors of the callout made about me thought that i was the sole person responsible for said incident when i wasn't. others also participated in the mess, so they are also at fault here. so this is my attempt to set things straight.
i'll discuss it further under the cut.
I've spent the past weekend combing through posts in relation to in 2011 where I've been accused of accusing someone of being a rapist, which turned out to be a false identification on someone else's part. Now, none of this is to absolve me of my involvement in the matter by trying to gather what information I could on the accused. It's here that I was, and I quote, a "dumbass plurk witch hunter" by participating in these two long-deleted plurks that, to my knowledge, have no archive elsewhere (Pastebin wasn't as commonly used back then to archive plurks for evidence down the line, and I have no idea how to search through that site to see if it's still archived, especially since the person could have set an expiration timer on it.) Again, this is just so that I can set things straight to where I wasn't the sole person responsible for this mess back in 2011.
This is the thread where I, and other people, were called a "dumbass plurk witch hunter" (playagame is one of my very old plurk accounts that has a lot of shit on it that I wish I never put out there) and the very last comment on the thread was from me saying that I did send him a PM to apologize. Evidence of this apology, though, was deleted by LiveJournal themselves because I know that I tend to not mass delete things, even if they're years old at this point. I also confirmed again, this time on my very old plurk account, that I had sent him an apology. (Please disregard the last comment I, as FREE☠JOKER made there since at the time, I had the emotional sympathy of a dumbass.) For even further proof that I apologized to him, here's a cap I took of my archived LJ post hosted on my Dreamwidth account. I am also still trying to log in to my Dropbox account where I at least have the conversation saved from Trillian and not LiveJournal.
This is the extent of my involvement where I tried to dig up information on him, but I was not the one who made the very false connection between him and the TC in question. This is from a private conversation I had with one of my friends that has known me since I was a cringy ass preteen who thought they knew everything about the world when, in fact, I knew nothing. If you'd like the full conversation for full context, then I don't mind providing it.
However, I did find these two posts from an account, whyljrpwhy, that is veritably not mine by a long shot. Whenever I made a new account, I tended to use keywords for my icons like these while whyljrpwhy uses keywords like these for their icons. That, and I've never had the email [email protected] before. I've normally used AOL, Yahoo, or Gmail for pretty much everything.
This originally was hosted on tumblr in the form of these PSAs: (this one has the link to the fandomsecrets post where the warning was crossposted here.) In the thread itself, you'll see where whyljrpwhy had some supremely bad takes in general for the whole situation that they were rightfully called out for, even when speaking to the TC that had been falsely accused of something as serious as this.
Once again, this post in no way absolves me of what I did back in 2011. I fully acknowledge what I did was wrong by trying to gather information on an individual that had nothing in common with the person being warned about, only that they both shared the alias TC. I've since tried, and still do try, my best to be the best person I can and learn from my mistakes.
Thank you, once again, for reading this post. Hopefully this is the last time I need to address this.
#☆ OUT OF UNIFORM → downtime is necessary even for a hero tasked with so much; remember to take a break for yourself.#☆ PSA → hey listen! this is some important stuff here!#( ASK TO TAG. )#*ooc: once again please don't reblog this -- I just wanted to set the record straight here#gonna still be kinda quiet but yeah -- just wanted to get that out there
2 notes
·
View notes
Text
youtube
Meet The $100 Million Underdog, Pamela Bardhi with Jay Conner, The Private Money Authority
Key Takeaways
How Pamela went from having over $100k in debt to achieving a 9-figure real estate career
Discovering why business is 100% a spiritual game
How Pamela drastically transformed her career trajectory through real estate
The life-changing power of private money to kickstart Pamela’s real estate career
Must-hear advice for attracting private money to your life
Taking the steps to map out your dream life
The importance of aligning your mind, body, and spirit
In today’s show of Real Estate Investing with Jay Conner, Pamela Bardhi joins Jay to empower the world through real estate, building different revenue streams, and igniting the Underdog in all of us.
Pamela Bardhi, the Real Estate Underdog, has been named by TIME Magazine as a Trailblazer in the Real Estate Industry. She went from delivering pizzas to a 9-figure real estate career featured in Forbes & Time Magazine by 28 years old.
She is a real estate developer by trade and has transitioned into becoming a real estate and life strategist through coaching, speaking, and building an international real estate team.
She hosts a world-renowned podcast called, Underdog, which is in the top 1.5% of podcasts in the world and streamed in 65+ countries.
She is fully dedicated to encouraging the world and igniting the fire in all of us. Real Stories, Real Hustle, Real Journeys. That is what she is all about.
Pamela has sold, developed, or acquired over $100 Million in Real Estate Assets in the Boston, MA market over the last decade. Her educational background includes Stonehill College, Babson College & Harvard Business School.
Timestamps:
0:01 – Get Ready To Be Plugged Into The Money
0:20 – Today’s guest: Pamela Bardhi
3:28 – Pamela Bardhi’s Start-Up In The Real Estate Business
6:49 – Pamela Bardhi, The Real Estate Underdog – https://www.theunderdogshow.com
9:06 – Business Is A Spiritual Game
15:21 – What Are You Most Passionate About Right Now?
18:07 – Early Struggles & Lessons Learned
20:54 – Best Ways To Raising Private Money
24:45 – Jay’s Free Private Money Guide: https://www.JayConner.com/MoneyGuide
25:58 – How To Maintain Your Drive & Motivation
30:17 – Importance of Having Multiple Streams of Income
31:59 – Connect with Pamela Bardhi – https://www.PamelaBardhi.com email: [email protected]

Private Money Academy Conference:
https://www.JaysLiveEvent.com
Free Report:
https://www.jayconner.com/MoneyReport
Join the Private Money Academy:
Have you read Jay’s new book: Where to Get The Money Now?
It is available FREE (all you pay is the shipping and handling) at
https://www.JayConner.com/Book
What is Private Money? Real Estate Investing with Jay Conner
https://www.JayConner.com/MoneyPodcast
Jay Conner is a proven real estate investment leader. He maximizes creative methods to buy and sell properties with profits averaging $67,000 per deal without using his own money or credit.
What is Real Estate Investing? Live Private Money Academy Conference
youtube
YouTube Channel
Apple Podcasts:
Facebook:
Listen to our Podcast:
#jay conner#real estate investing#real estate#private money#flipping houses#real estate investing for beginners#youtube#raising private money#privatemoney#realestate#Youtube
2 notes
·
View notes