#remote spy app for android
Explore tagged Tumblr posts
Text
ONEMONITAR: Advanced Android Parental Control App

Take control of your child's digital activities with ONEMONITAR, the leading parental control app for Android. Safeguard their online interactions, track their location, and ensure their safety remotely.
Protect Your Loved Ones and Ensure Safety with ONEMONITAR– The Ultimate Monitoring Solution!
#best android spy app#android spy software#hidden spy app for android#parental control app for android#remote spy app for android#undetectable spy app for android#Android Spy App for WhatsApp#Android Spy App with Call Recording#Android Spy App with GPS Tracking#Spy App for Android without Target Phone
0 notes
Text
Legit app in Google Play turns malicious and sends mic recordings every 15 minutes
The malicious iRecorder app has come to light, but its purpose remains shrouded. An app that had more than 50,000 downloads from Google Play surreptitiously recorded nearby audio every 15 minutes and sent it to the app developer, a researcher from security firm ESET said. Continue reading Untitled

View On WordPress
0 notes
Text
Best spy applications for android, like phone spy apps, make it easy to monitor the activity on a smartphone. These surveillance tools provide real-time access to information such as a phone’s location, incoming and outgoing calls, SMS messages, GPS coordinates, web browser activity, and messages from popular social media apps like WhatsApp, Facebook, and Snapchat. The best spy applications are designed to be invisible to the end user. They cannot be detected, making them useful tools for keeping an eye on loved ones, monitoring employees, or tracking personal phone usage.
Are Spy Applications Legal?
Before considering “Best Spy Applications For Android,” it’s crucial to understand the laws in your region. Different locations have varying regulations regarding the use of spyware. Ensure it’s legal where you reside before installing one of these apps on someone else’s phone. Most areas prohibit monitoring a device without the owner’s consent, so do thorough research and ensure you’re adhering to the regulations. To stay on the safe side, be informed about the laws in your area and remember that unauthorized use of Spy Applications can lead to legal consequences.
How To Install Spy Apps On Target Device
Installing the “Best Spy Applications For Android” on a target device is easy. The easiest way is to borrow the phone for a call, leave the room to continue the conversation, and use that privacy to download and install the app. During the initial setup, you’ll need to enter your username and password to connect to the dashboard, which usually takes less than ten minutes. Once installed, the app will enter stealth mode and won’t be detected.
With just one touch of the target device, you can use your phone or computer to monitor the user’s location and activities secretly. So, whether you’re looking to keep track of your children or monitor the activities of your employees, “Best Spy Applications For Android” is the solution you need. Read more: https://techplnt.com/best-spy-applications-for-android/
#best spy applications for android#free remote monitoring app for android#mobile spy app#mspy for android#spy app for iphone
0 notes
Text
BlurSPY Undetectable Spy App for Android - Remotely Tracker For Kids Digital Devices.
For all such #distressed #parents who are #working 24/7 in their #workplaces, BlurSPY is 100% #undetectable #spyware for #android is a #blessing in the hour of need. BlurSPY is a #fully #undetectable #spyware for #AndroidPhones. #parents can #remotely #Install #BlurSPY application on #Kids #smartphone devices.
#teens#blurspy#spy app#workplace#tracking#android spy#tracker#social media#business#education#undetectable spy app
5 notes
·
View notes
Text
Can a spy app be installed remotely?

The rise of the internet has surely made the world a smaller and better place. The advancement of technology to such an extent that you just have to make a few clicks to get anything was unimaginable a decade back. A huge spike in the number of internet users has been seen in just the past few years. If you look around, you can find everyone with their smartphones in their hands, engaged in some sort of content. Apart from the ability to stay connected with people, it has enabled us to run a whole business just through a smartphone.
However, like any good thing in life, this also came at a cost of being exposed to various online risks. Fortunately, these risks are totally avoidable with the use of a mobile spy app like Chyldmonitor. The app lets you monitor the online activities of your family and friends to keep them safe over the web. Not everyone out there can be educated about the risks involved and how not to fall for it. The whole process of creating awareness around the hazards of the internet is neither realistic nor doable. Therefore, using an spy app for android is the best solution one can opt for.
Making yourself aware of the risks and how to deal with them, can really help your loved ones to browse safely. However, the biggest question that people get when it comes to spy apps is whether they can be remotely installed or not.
The answer is no. But the good news is that you need access to their phone for about 5 - 7 minutes only for the whole process to complete. This should be very doable for anyone who wants to spy on someone for their sake. You can ask to use the targeted phone for a while, and before they know it, you’ll be able to set up the whole thing.
Beneficial Features Provided by the Chyldmonitor App
The app is offering more than 60+ features to their users all over the world. With this app in your toolbag, you get to fully monitor the target phone. Not a single aspect which could prove to be harmful for your family is spared by the app. The app comes packed with features like call recordings, location tracking, access to chats, ambience sound recording, etc.
The app also has a hidden call recorder feature available to record every call taking place on the targeted phone. With its unique feature of remaining hidden from the app drawer, there’s no way anyone can know if they’re being spied on.
Apart from this, one also gets the option to track location of the intended device. Majority of the scams these days are taking place over the most used communication platforms. This is where WhatsApp Spy feature can help you to maintain the security of your loved ones. Frem the recordings of the calls made over WhatsApp, to the media shared, everything can be accessed from the web portal once you login to your account.
Install a Spy App in Your Phone This Easily
Many people think that installing a spyware application on the intended device must be a complicated process. The word ‘rooting’ or ‘jailbreaking’ comes to their mind when they think about it. However, with Chyldmonitor application, you are not required to root your device to get advanced permissions. The app is fully functional on any android device.
Once you have managed to get a hold of the targeted device, the installation process will only take you about 7 minutes at most. If you face any trouble while installing the app, their customer service is available 24x7.
You can be guided through the installation process over the call or the agent might take remote access to your device, to perform the installation on your behalf. It has gotten way easier than ever to spy on your family and friends to keep them protected over the internet. However, no ethical boundaries should be crossed in the process. The consent is the crucial thing to make sure that your relationship doesn’t get affected with the intended person on whom you want to spy on.
The arrival of spy apps have revolutionized the way in which we deal with the online threats. Monitoring the online activities of your loved ones is the only reasonable way today to ensure their safety online.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
2 notes
·
View notes
Text
SDR Research
Tools
GQRX - Spectrum Analyzer
RFanalyzer - Spectrum Analyzer for Android
Universal Radio Hacker - Investigate Wireless Protocols like a boss
ooktools - On-off keying is used extensively in IoT projects
fldigi - I'm not a big fan of fldigi, but its there for when you need to demodulate a common signal
Tools for more specialty purposes
Salamandra is a tool to find spy microphones
rpitx is a RF transmitter for Raspberry PI
Tactics
You don't need to learn DSP, or get your Ham license to explore radio signals. I didn't. You could even explore interesting signals such as vehicle key fobs without learning either, but learning these things will increase your understanding of signals and aid in your ability to go beyond the limitations of your tools.
Digital Signal Processing
The Scientist and Engineer's Guide to DSP was my introduction to DSP and I highly recommend it. Its free online and can be purchased in physical form.
Think DSP in Python is on my todo list. Also free online can can be purchased in physical form.
HAM Radio
Though I haven't taken the test yet. Covid was a major interruption in my plans, and I also plan to pass all 3 tests in one day. Using my personal test taking process, I would first start by reading No-Nonsense Study Guides.
Then take a pretest. Its important that you read all of the material before you take a pre-test as the goal is to retain knowledge, not just memorize a test. Most of the study should be reading/practicing the material, with few pre-tests as self assessments.
There are plenty of apps on Android (and I imagine IOS) that you can use. You need to get 74% to pass the exam, but I always shoot for 90%. If you get 90% on the pre-test, then move on to taking the actual exam.
If you didn't get 90% on the pre-test. The pre-test should be able to break down your score across various sections. Note the sections you're weakest in. From here, I would recommend switching over to the ARRL study guide as they are more detailed and only study the sections you're weakest end. When you complete all those sections, then take another pre-test and repeat until you're ready to take the exam.
Techniques
Accuracy
Radio is a science, but the tools that we can afford as hobbyists are not accurate. The three issues I face is drift, noise, and clock.
Drift occurs typically from your SDR getting hot and is a problem that grows across the session. To counter drift, you'll need to recalibrate your SDR to a Nation Weather Radio station. Find the frequency used in your area and tune to that frequency. You'll notice that you're probably a little off, this is the fault of your SDR not the National Weather Radio station. Set the offset of your SDR until your frequency of the station matches the one advertised. You'll then want to bookmark this frequency and check back to it every hour to insure that your SDR hasn't drifted.
Noise can interfere with interpreting weak signals (either distant, low powered, or both). To reduce noise and improve your signal collection, I'd suggest these guides for reducing on-site noise sources and external noise sources.
Signal Identification
Most signals are standardized or frequently used that dont require extensive analysis, but just identification.
The Signal Identification Wiki is a great place to start, and if that doesn't work, check out the sub-reddit r/signalidentification
This is an archived site that has a collection of digital signals that you could test your demodulation tools with.
Signal Analysis
Signal analysis is for those proprietary signals. As always, remember your ABC's.

Radio signals are fleeting. If you don't capture them, they may not repeat themselves. Don't worry about demodulating them at first. Capture the signals, and you can demodulate them at any time later.
Even if you're not able to record IQ data, for example you're listening to someone else's remote radio (there are a lot around the world on the internet), recording the audio which can be analyzed by tools such as fldigi.
I should add a lot more stuff here in the future.
The Signal Identification Wiki is a great place to start, and if that doesn't work, check out the sub-reddit r/signalidentification
This is an archived site that has a collection of digital signals that you could test your demodulation tools with.
Other Techniques
Using ooktools
NCC's RF testing Methodology
Wireless DoorBell Ringer and another Doorbell hack
Learn Morse Code
Project Ideas
Passive Radar with SDR
TDOA Transmitter Localization with RTL-SDRs
Other Links
No SDR, no problem! Use other people's radios with GlobalTuners.
#radio#signals#radio transmissions#sdr#ham radio#DSP#digital signal processing#signal analysis#technology
2 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] 4k WiFi Camera Table Clock Wireless, Full HD 1080P WiFi Clock with Night Vision, Watch Live View in Smartphone Android/iOS HD Video Recorder for Home Office Security Camera Clock Design Clock design to cover the camera inside. It makes this hidden camera more useful and not noticeable for the customer who want to monitor their home security. Mobile Remote Broadcast With a quick setup of the app on your mobile device,view,and stream video from smartphone anywhere in the world. How the machine works The mobile app is mainly for online real-time checking.The SD card is to save the videos.Inserting the card into the slot and turn the camera on, then the camera will automatically start to record and save the files into the card even without wifi setting. About the recording button on the APP,we seldom use it.We mainly record by the SD CARD (not included). Great clock camera -- Support 64GB TF Card in Max,Cycle Recording. -- Support Smartphone Tablet APP Remote View and Control -- Support recording and charging at the same time -- Video Resolution: 1920x1080P ✔️【Digital Table Camera Clock】:This spy camera looks like a regular clock which could tell you time. The lens of spy cam is hidden under the glossy screen thus nobody will notice it. It can be used with wide angle of 150 degree and 1080P lense. Act as a surveillance camera in: Office, Home and Car etc. With Romeifly spy camera you will never miss any details clearly that’s happening in the room. ✔️【Powerful Machine Performance】: Wifi hidden camera build in advanced image sensor which helps to capture full HD video smoothly with accurate color reproduction. The supper 120° wide-angle professional grade lens, creating a large coverage view to monitor your care, iOS and Android Compatible, Live Stream from Anywhere, perfect for house, office or family as housekeeper or nanny cam. ✔️【Wi-Fi Streaming and Remotely View】:The wireless Wi-Fi spy camera hidden camera in clock could be connected to the internet network, so you could live-stream your footage from anywhere in the world. Just download the app and follow the instruction book, then you are able to see everything happens on your phone, tablet ✔️【Cleary Light Vision and Motion Detection】: Spy cam comes with excellent 5M infrared light vision, you can see any details and surface clearly even in dark environment. And, your phone will receive Notification with images while a motion is detected. Just use the App to see details in real time and neednt to worry about any missing happened. ✔️【Video Audio Loop Recording】:Insert the Micro SD card into its slot,power it on,the camera will start to record automatically.When the memory space is full,the camera will overwrite the files from oldest to newest. [ad_2]
0 notes
Text
Track Any Cell Phone’s Location in Real-Time: The Complete Guide
In the digital age, mobile phones have become integral to our lives. We rely on them not only for communication but also for navigation, entertainment, and productivity. With the advent of smartphones, tracking technology has evolved, allowing users to locate their devices or the devices of others in real-time. Whether you're trying to recover a lost phone, ensure the safety of a loved one, or manage business assets, real-time phone tracking can be incredibly useful.
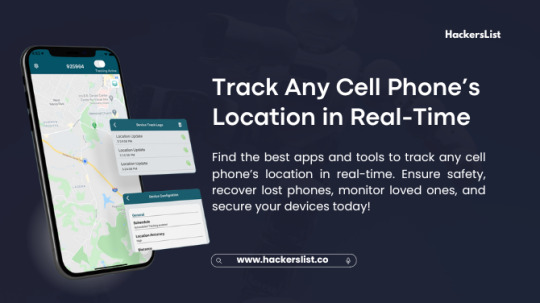
However, with great power comes great responsibility. Tracking a phone’s location in real-time raises ethical and legal concerns, as the potential for misuse is significant. In this blog, we’ll explore how real-time phone tracking works, review the best tools available, and discuss the ethical and legal implications. Additionally, we’ll guide you on using these features responsibly and securely.
How Does Real-Time Phone Tracking Work?
Real-time phone tracking uses a combination of technologies to determine a device’s location. The most common methods include:
GPS (Global Positioning System): GPS is the most accurate tracking technology available. It uses satellites to pinpoint a phone’s location to within a few meters. Nearly all smartphones today have built-in GPS.
Cell Tower Triangulation: When GPS is unavailable, such as indoors or in remote areas, phones can be tracked using signals from nearby cell towers. By analyzing the strength and timing of these signals, a phone’s approximate location can be calculated.
Wi-Fi and Bluetooth: Phones often connect to Wi-Fi networks or other devices via Bluetooth, which can also be used for location tracking. This is particularly useful in urban areas where there are many Wi-Fi networks.
IMSI Catchers and Stingrays: These are advanced surveillance tools used by law enforcement and government agencies to track phones by simulating a cell tower and intercepting signals. These are not available for public use but are part of real-time tracking technology.
Legal and Ethical Aspects of Phone Tracking
Before diving into how to track a phone, it’s crucial to understand the legal and ethical boundaries.
Consent: In many countries, tracking a phone without the owner’s consent is illegal. Even if you have access to the person’s phone, you must inform them and obtain their permission before tracking their location.
Family and Employee Tracking: Tracking family members, particularly minors, is usually allowed, but it should be done transparently. Employers may track employees’ phones, but only when the employees are aware of and have consented to it, usually for work-related purposes.
Privacy Concerns: Unethical phone tracking can lead to privacy violations. Misusing tracking technology to stalk or spy on others can result in severe legal consequences. Therefore, tracking should be done for legitimate reasons, and individuals must take steps to protect their own devices from unauthorized tracking.
Best Real-Time Phone Tracking Tools & Apps
There are many tools and apps available that allow you to track a cell phone in real-time. These tools vary in terms of features, ease of use, and platforms supported.
1. Find My Device (Android)
Overview: This is a built-in feature on Android devices. Once enabled, it allows users to track their phone’s location, play a sound, lock it, or erase its data if necessary.
Key Features: Real-time tracking, sound alerts, device locking, and data wiping.
How to Use:
Open the “Settings” app on your Android device.
Navigate to “Security” and enable “Find My Device.”
To track your phone, visit google.com/android/find on a web browser and sign in with your Google account.
2. Find My (iOS)
Overview: Apple’s Find My app combines Find My iPhone and Find My Friends into one comprehensive tracking tool. It allows you to locate your devices and friends who have shared their locations.
Key Features: Real-time tracking, lost mode, device erasing, location sharing.
How to Use:
Open the “Settings” app on your iPhone.
Tap your Apple ID and select “Find My.”
Enable “Share My Location” and “Find My iPhone.”
To track your phone, use another Apple device or log into iCloud.com on a browser.
3. Life360
Overview: Life360 is a popular family tracking app that allows family members to share their locations in real-time. It’s ideal for keeping tabs on kids, elderly family members, or loved ones.
Key Features: Real-time tracking, location history, SOS feature, driving analysis.
How to Use:
Download Life360 from the App Store or Google Play Store.
Create an account and invite family members to join your circle.
Once connected, you can view everyone’s real-time location within the app.
4. Glympse
Overview: Glympse is a location-sharing app that allows users to share their real-time location with others for a set period. It’s useful for meeting up with friends or family members.
Key Features: Temporary location sharing, no sign-up required, customizable sharing duration.
How to Use:
Download Glympse from the App Store or Google Play Store.
Open the app, select “Share Location,” and choose who to share it with.
Recipients can view your real-time location for the duration you set.
5. Spy Apps
Overview: Spy apps like mSpy or FlexiSPY allow users to monitor a phone’s location, calls, texts, and even social media activity. However, these apps can be controversial due to their invasive nature.
Key Features: Real-time location tracking, call and text monitoring, stealth mode.
Legal Warning: These apps should only be used with the consent of the person being tracked. Unauthorized use can lead to legal action.
How to Track a Phone Using Built-in Features
If you’re not interested in third-party apps, most smartphones come with built-in tracking features. Here’s how to use them:
1. Tracking an Android Phone
Using Find My Device:
Enable “Find My Device” in the settings.
Visit google.com/android/find on any browser.
Log in with the Google account associated with the device.
You can now see the device’s location on the map and perform actions such as locking or wiping it.
2. Tracking an iPhone
Using Find My iPhone:
Enable “Find My iPhone” in the settings under your Apple ID.
Use another Apple device or go to iCloud.com.
Log in with your Apple ID to view the device’s location.
3. Tracking via Microsoft Family Safety
Overview: Microsoft Family Safety allows parents to monitor their children’s phones and location. This feature can be used on Android or Windows devices.
How to Use:
Set up a Microsoft family group at account.microsoft.com/family.
Add family members and enable location sharing.
Third-Party Tracking Apps: Advantages and Risks
While built-in tracking features are convenient, third-party apps offer additional functionality. However, they also come with certain risks.
Benefits of Third-Party Tracking Apps:
More comprehensive tracking features (e.g., geofencing, driving reports).
Often cross-platform, working across Android, iOS, and even desktop devices.
Some apps provide extra safety features like SOS alerts or crash detection.
Risks of Third-Party Apps:
Security Vulnerabilities: Third-party apps can sometimes introduce security flaws or be exploited by hackers. Always ensure the app you’re using is reputable and up-to-date.
Privacy Concerns: Some apps may collect more data than necessary, which can be sold to third parties. Always read privacy policies and user reviews before installing.
Real-Time Tracking for Business and Security
Real-time phone tracking has also become a critical tool for businesses and personal security.
1. Business Use Cases
Employee Tracking: Many companies use real-time tracking to monitor field employees, such as delivery drivers or salespeople. This helps in optimizing routes, ensuring employee safety, and improving productivity.
Asset Management: Companies can track their valuable assets, like company phones or vehicles, to prevent theft and ensure proper usage.
2. Personal Security
Family Tracking: Real-time tracking can provide peace of mind when monitoring the safety of children, elderly parents, or loved ones with special needs.
Emergency Situations: Some apps include emergency features that automatically share your location with loved ones or authorities in case of an accident or emergency.
Privacy and Data Security Concerns
As helpful as phone tracking can be, it comes with its own set of privacy and security concerns. Unauthorized tracking can be invasive, and sensitive data can be exposed to cyber threats.
1. How to Protect Your Privacy
Always lock your phone with a strong password or biometric security.
Disable location services when not needed to prevent apps from tracking your movements.
Regularly review app permissions to ensure apps are not accessing location data unnecessarily.
2. How to Disable Tracking
On Android, go to “Settings” > “Location” and turn off location access.
On iPhone, go to “Settings” > “Privacy” > “Location Services” and disable location tracking for specific apps or globally.
Conclusion
Real-time phone tracking has become an essential tool in both personal and professional life. From recovering lost devices to ensuring the safety of loved ones, the benefits are undeniable. However, it’s vital to use these tools responsibly, respecting legal boundaries and privacy rights. Always obtain consent before tracking someone’s phone and take precautions to protect your data.
As technology continues to evolve, so will tracking capabilities. Staying informed and using these tools ethically will allow you to maximize their benefits while minimizing the risks.
Have you ever used a phone tracking app? Share your experiences in the comments below! And if you’re interested in learning more about cybersecurity or privacy protection, check out our other blog posts on securing your digital life.
0 notes
Text
5 Best Phone Clone Services To Track Someone's Remotely
Need to track a phone remotely? Here are the 5 best phone clone services that provide reliable and secure solutions for monitoring activities.

Related: How to Clone a Phone Without Someone Knowing
Phone cloning might sound like something out of a spy movie, but it's a real technology that's becoming increasingly popular. Whether you're switching to a new phone or need a backup, understanding how phone cloning works can be very useful. However, with the convenience of cloning comes a range of ethical and legal considerations.
🛑 What is a Phone Clone App?
A phone clone app is a tool that allows users to copy data from one phone to another. This can include everything from contacts and messages to photos and apps. The primary purpose of these apps is to simplify the process of transferring data, making it easy for users to switch devices without losing important information.
🛑 Common Uses
▶ Device Upgrade: When upgrading to a new phone, cloning apps can transfer all your data seamlessly.
▶ Backup: Create a full backup of your phone’s data to prevent loss in case of damage or theft.
▶ Multiple Devices: For those who use multiple devices, cloning helps keep data consistent across all of them.
🛑 How to Clone Someone's Phone
🔸Ethical Considerations
Before diving into how to clone a phone, it's crucial to discuss the ethical aspects. Cloning someone else's phone without their consent is illegal and unethical. Always ensure you have permission before attempting to clone any device.
🔸Steps to Clone a Phone
i) Choose a Reliable App: Start by selecting a trustworthy phone clone app.
ii) Install the App: Download and install the app on both the source and target phones.
iii) Connect Devices: Follow the app’s instructions to connect both devices, usually via Wi-Fi or Bluetooth.
iv) Select Data to Clone: Choose the types of data you want to transfer.
v) Initiate Cloning: Start the cloning process and wait for it to complete.
🛑 How to Clone a Cell Phone
⏹Tools and Software Needed
▶ Phone Clone App: Download a reputable app like Clone Phone or CLONEit.
▶ Internet Connection: Ensure both devices are connected to the internet.
▶ Two Devices: The source phone and the target phone.
⏹Detailed Guide
▶ Install the App on Both Devices: Ensure both phones have the cloning app installed.
▶ Launch the App: Open the app on both devices and select the roles (source and target).
▶ Connect the Phones: Use the app to establish a connection between the devices.
▶ Choose Data to Transfer: Select specific files, apps, and settings you want to clone.
▶ Start the Transfer: Begin the cloning process and wait until it's finished.
🛑 Clone a Phone Number
🔆 Explanation of Phone Number Cloning
Cloning a phone number involves duplicating the number so it can be used on another device. This is often done using a SIM card duplicator or specialized software.
🔆 Risks and Legality
Phone number cloning is illegal in many regions as it can be used for malicious purposes like fraud. It’s important to understand the legal implications and risks involved before attempting to clone a phone number.
🛑 Phone Clone for Android
⏺ Best Apps for Android
Phone Clone by Huawei: Excellent for Huawei devices and compatible with most Android phones.
CLONEit: Supports a wide range of data types and is easy to use.
Samsung Smart Switch: Ideal for Samsung users, supporting transfers from various platforms.
⏺ Step-by-Step Process
Download and Install: Get the app from the Google Play Store.
Set Up Devices: Follow the app’s setup instructions to connect the devices.
Select Data: Choose the data categories you want to transfer.
Initiate Cloning: Start the process and monitor the progress.
🛑 Phone Clone for iPhone
⏹ Best Apps for iOS
Move to iOS: Developed by Apple, this app makes it easy to switch from Android to iPhone.
Clone Phone by Huawei: Also compatible with iOS for cross-platform transfers.
AnyTrans: A versatile tool that supports comprehensive data migration.
⏹ Step-by-Step Process
Install the App: Download the app from the App Store.
Prepare Devices: Make sure both the source and target phones are ready and connected.
Connect Devices: Follow the app’s instructions to establish a connection.
Select Data: Choose the items you want to clone.
Start Cloning: Begin the transfer and wait for it to complete.
🛑 Clone Someone's Phone: Ethical and Legal Aspects
*️⃣ Potential Risks and Legal Implications
Cloning a phone without consent is illegal and can lead to severe consequences, including legal action and imprisonment. Unauthorized cloning can also result in data breaches and privacy violations.
*️⃣ Ethical Considerations
Always seek permission before cloning a phone. Respecting privacy and understanding the ethical implications are crucial to responsible use of this technology.
🛑 iPhone Clone Apps
✅ Top Apps Available
Move to iOS: Simple and effective for transferring data from Android to iPhone.
Phone Clone by Huawei: Cross-platform compatibility makes it versatile.
iMazing: Offers extensive data transfer options and backups.
✅ Features Comparison
Ease of Use: Move to iOS is user-friendly with a straightforward interface.
Compatibility: Clone Phone by Huawei supports both Android and iOS.
Advanced Features: iMazing provides more control over the data transfer process.
🛑 Best Phone Clone Apps
🟩 Top-Rated Apps for All Devices
CLONEit: Reliable and fast for Android devices.
Clone Phone by Huawei: Versatile with cross-platform support.
AnyTrans: Comprehensive tool for both iOS and Android.
🟩 Pros and Cons
✔ CLONEit:
Pros: Fast and easy to use.
Cons: Limited to Android.
✔ Clone Phone by Huawei:
Pros: Cross-platform compatibility.
Cons: May have compatibility issues with some non-Huawei devices.
✔ AnyTrans:
Pros: Supports both platforms.
Cons: Requires a paid license for full features.
🛑 Phone Clone for All Android Devices
▶ Compatibility Considerations
Ensure that the clone app you choose is compatible with both the source and target Android devices. Some apps are designed specifically for certain brands, so check compatibility beforehand.
▶ Comprehensive Guide
i) Install the App: Ensure compatibility and install on both devices.
ii) Prepare for Transfer: Connect both devices to the same Wi-Fi network.
iii) Select Data: Choose what you want to clone.
iv) Initiate Transfer: Start the process and monitor until completion.
🛑 How Do You Clone a Cell Phone?
🔘 Overview of Methods
i) Using Cloning Apps: The most straightforward and user-friendly method.
ii) Manual Transfer: Involves moving data manually using tools like Bluetooth or USB.
iii) SIM Cloning: Duplicates the SIM card to another device.
🔘 Security Concerns
Cloning can expose your data to security risks. Always use trusted apps and keep your devices secure to prevent unauthorized access.
🛑 Clone a Phone Without Touching It
✅ Remote Cloning Techniques
Cloud-Based Solutions: Use cloud backups to clone data remotely.
Remote Access Tools: Some apps offer remote access features, but these often require initial setup on the target device.
✅ Risks Involved
Remote cloning without consent is illegal and risky. It can lead to serious legal issues and compromise the security of the devices involved.
🛑 The Benefits of Using Phone Clone Apps
Switching to a new phone can be exciting but also challenging, especially when it comes to transferring all your important data. Clone phone apps offer a seamless solution to this problem. Let's explore the various benefits these apps provide.
⏩ Effortless Data Transfer
Convenience and Simplicity
Clone phone apps make it incredibly easy to transfer data from one phone to another. Whether you're upgrading to the latest model or switching brands, these apps simplify the process, eliminating the need for manual data copying.
⏩ Comprehensive Data Migration
These apps support the transfer of a wide range of data types, including:
i) Contacts
ii) Messages
iii) Photos and videos
iv) Apps and app data
v) Call logs
vi) Settings
⏩ Time-Saving
✔ Quick Setup
Setting up a new phone can take a lot of time, but clone apps can significantly speed up the process. What might take hours to do manually can be completed in just minutes with a cloning app.
✔ Minimal Downtime
With a clone phone app, you don't have to endure long periods without your data. The transfer process is quick, allowing you to get back to your routine without significant interruptions.
⏩ Reliable Data Backup
✔ Secure Backup Solution
Clone phone apps also function as a reliable backup solution. Regularly cloning your phone ensures that you have a current backup of all your essential data, which can be a lifesaver in case of loss, theft, or damage to your device.
✔ Data Security
Many clone phone apps include security features such as encryption to protect your data during the transfer process. This ensures that your sensitive information remains safe and secure.
🛑 Security Measures Against Phone Cloning
⏺ How to Protect Your Phone
Enable Two-Factor Authentication: Adds an extra layer of security.
Use Strong Passwords: Avoid easily guessable passwords and change them regularly.
Regular Software Updates: Keep your phone’s software up-to-date to protect against vulnerabilities.
⏺ Recognizing Cloning Attempts
Unusual Activity: Look out for unexpected activity on your phone.
Battery Drain: Cloned phones often show rapid battery depletion.
Unknown Devices: Be wary if your phone shows connections to unfamiliar devices.
🟢 Final Touch
Understanding phone cloning and its implications is crucial in today's digital age. While it offers convenient solutions for data transfer and backup, it also poses significant ethical and legal challenges. Always use phone cloning apps responsibly and ensure you have permission to clone a device.
❓ FAQs
Q-1. Can I clone my phone to a different brand?
A-1. Yes, many clone phone apps support cross-platform transfers between different brands.
Q-2. What data can be cloned?A-2. You can clone contacts, messages, photos, videos, apps, and more, depending on the app you use.
0 notes
Text
Capture Every Conversation with the Ultimate Android Spy App for Call Recording.
Capture every conversation effortlessly with the ultimate Android spy app for call recording. This feature-rich app allows you to record calls discreetly, providing you with valuable insights into conversations without the need for complicated setups.
Capture every conversation effortlessly—try the ultimate Android spy app for call recording!
#Android Spy App for Call Recording#Spy App for Android Text Messages#Android Monitoring App#Spy App for Android Without Detection#Stealth Spy App for Android#Spy on Android Phone Remotely
0 notes
Text
How to Spy on iPhone Without Access to Target Phone?

Modern parenting often involves setting boundaries for phone usage, such as screen time limits and ensuring children access age-appropriate content. However, with busy schedules, parents may struggle to monitor their kids' iPhones thoroughly, including checking call logs, reading messages, and tracking their movements. Fortunately, Msafely, a web-based phone monitoring app, simplifies this process by allowing parents to remotely view phone activity and location history from a single dashboard. Msafely lets you spy on iPhones, so you know what kids do on their phones anytime and anywhere. The user-friendly monitoring app, Msafely, offers robust features for tracking call logs, web browsing history, and location without accessing the target device. This helps parents monitor their children's behaviour and whereabouts for timely guidance and safety. This post will explore how to use Msafely to monitor your child's iPhone securely. You'll learn how to track the websites they visit and their location. Let's dive in! What is the Msafely Phone Monitor Solution? Msafely is a powerful phone monitoring tool for secretly monitoring your kids' devices. The parental control application works invisibly, letting you spy on what kids are doing on their phones without them knowing. Moreover, the phone monitoring solution for parents works smoothly on Android and iPhone. Therefore, regardless of whether your child is a phone model, you can monitor their activity anytime through an easy-to-use parental control app. Msafely Phone Monitor Solution Features To understand why Msafely is your best app to spy on kids' iPhones, let us review its features. Phone Activity Tracker for iPhone As more research shows the negative impacts of excessive phone usage, experts recommend supervising and limiting phone use for children. Msafely lets you monitor the app usage, phone calls, and messages on your kid’s phone. Therefore, you can tell who they are communicating with and the context of their communication by spying on the kid's phone. The child safety application records sent and received messages and calls and keeps a log of deleted messages, giving you a complete view of their communication. Therefore, if your child receives communication from unknown people, you can review when and how often they communicate. With such information, you can easily counsel your child and tell them to stop communicating with strangers. Track Your Child's GPS Location A caring parent will always want to track their kid's movement so they know when they break into dangerous neighbourhoods or attend unsafe parties. Msafely will easily track the current location and the location history of your child’s device in stealth mode. Therefore, you can use Msafely to track location history through their cell phone, keeping a watchful eye on their movement. The Msafely location tracker also has a geo-fencing feature, so you receive alerts whenever your child is not in designated areas. You can contact your child for an explanation and counsel them against visiting such locations whenever you receive such alerts. Social Media App Tracker Cyberbullying and leaking sensitive information are some of the dangers your child is prone to when using social media applications. Moreover, children could be exposed to inappropriate content sent to them by strangers or even their friends through social media applications. By actively monitoring your child’s communication through social media apps using Msafely, you protect them from online dangers. Msafely is a high-quality parental control application offering you valuable assistance so you can effectively protect your child from potential risks associated with social media usage. You can use Msafely to monitor who your child communicates with on social media applications such as Instagram, Snapchat, and Facebook. Further, you can review their posts, comments, likes and replies to social media posts. WhatsApp Tracker for iPhone Msafely lets you monitor your kid's WhatsApp messages effectively. You can view their private and group messages on WhatsApp using the application. You will discover the photos, videos, messages, and documents they share through WhatsApp. The Msafely WhatsApp tracker lets you view their contact list without jailbreak. Once you find your children chatting with suspicious strangers, you can stop them quickly. For instance, you can know when they share sensitive information, such as their current location and home address and warn them against doing so. Screen Time and Schedule Tracker Excessive phone usage could have adverse effects on your child’s health. Moreover, unsupervised kids could spend so much time on their phones and fail to attend to essential assignments. Therefore, as a parent, you need to track their screen time and even set a schedule so they do not use the device at certain times, such as bedtime, school, etc. Msafely is a safe and secure monitoring app with scheduling features. Therefore, you can use Msafely to schedule restrictions and ensure children do not spend excessive time on their digital devices. Installed Apps Tracker Using Msafely, parents can check the applications installed on their kids' iPhones. Typically, the iPhone tracker provides insights such as the app version and download time and comes with blocking features so you can block your kids from potentially harmful applications and games. Discreet Phone Monitoring Application When you start using Msafely, no application or icon is left on the target phone. Thus, your child will not be suspicious that you are monitoring their messages, screen time, or location. You can review their natural conduct and offer guidance and counselling whenever they act differently than expected or visit restricted areas. How To Use Msafely To Spy on iPhone Without Accessing Target Phone You can set up Msafely phone tracking on your iPhone in simple steps. Here are the steps to follow: Step1. Register a Msafely Account Please register for a Msafely account, which is your first step towards accessing their services. Start using your valid email address, which will serve as your primary contact and login credential for the account. Step2. Choose a Suitable Plan and Connect your phone Msafely offers different user plans tailored to suit everyone's needs. Select your ideal user plan and follow the prompts to add your target device. Step3. Start Monitoring You can begin the monitoring with Ase with the target device(s) added and log into the log user dashboard using the email address you registered with. This dashboard is your command centre - where you can view activity logs, set up alerts, and manage your monitoring devices. Conclusion Msafely is the ultimate parental control application for modern-day phone tracking. Parents can actively review their child’s messages on social media applications, call logs, and even location in real-time using the application. The easy-to-use phone monitoring app has a web-based dashboard for secure and easy access anytime and from anywhere. Download your Msafely phone tracking app today and monitor your child’s iPhone usage. Read the full article
0 notes
Text
what is vpn on my samsung phone
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn on my samsung phone
VPN definition Samsung phone
A Virtual Private Network (VPN) is a crucial tool for safeguarding your online privacy and security, particularly when using a Samsung phone. Essentially, a VPN creates a secure and encrypted connection between your device (in this case, your Samsung phone) and the internet. This encryption ensures that any data transmitted between your phone and the internet is protected from prying eyes, including hackers, government surveillance, and even your Internet Service Provider (ISP).
But why might you need a VPN specifically for your Samsung phone? Well, like any internet-connected device, smartphones are vulnerable to various threats, such as malicious actors attempting to intercept your data on public Wi-Fi networks or track your online activities for targeted advertising. With a VPN, however, you can effectively cloak your internet traffic, making it nearly impossible for anyone to spy on your online behavior.
Moreover, using a VPN on your Samsung phone can grant you access to geo-restricted content and services. By connecting to servers located in different countries, you can bypass regional restrictions and enjoy content that may be unavailable in your current location, whether it's streaming services, websites, or apps.
Fortunately, setting up a VPN on your Samsung phone is relatively straightforward. Many VPN providers offer dedicated apps for Android devices, including Samsung phones, making it easy to install and configure the VPN with just a few taps. Once activated, the VPN runs seamlessly in the background, providing you with peace of mind knowing that your online activities are shielded from prying eyes.
In conclusion, a VPN is an essential tool for protecting your privacy and security on your Samsung phone. By encrypting your internet connection and masking your IP address, a VPN ensures that your online activities remain private and secure, regardless of where you are or what network you're using.
VPN benefits mobile device
Title: Unlocking the Benefits of VPN for Mobile Devices
In today's interconnected digital landscape, the use of Virtual Private Networks (VPNs) has become increasingly vital, especially for mobile device users. A VPN establishes a secure and encrypted connection over the internet, offering a myriad of benefits for individuals accessing the web through their smartphones or tablets.
First and foremost, VPNs enhance privacy and security on mobile devices. By encrypting data transmitted between the device and the internet, VPNs shield sensitive information from potential hackers, cybercriminals, and other malicious entities. This is particularly crucial when using public Wi-Fi networks, such as those found in cafes, airports, or hotels, where the risk of data interception is higher.
Moreover, VPNs enable users to bypass geographical restrictions and access content that may be restricted or censored in their region. Whether it's streaming services, social media platforms, or news websites, a VPN allows individuals to browse the internet freely and anonymously, without being subjected to arbitrary limitations based on their location.
Another significant advantage of using a VPN on mobile devices is the ability to secure online transactions and financial activities. Whether making purchases, banking transactions, or accessing sensitive accounts, VPNs add an extra layer of encryption to ensure that personal and financial information remains confidential and protected from prying eyes.
Furthermore, VPNs offer peace of mind for remote workers or frequent travelers who need to access corporate networks or sensitive business data from their mobile devices. By encrypting communication channels, VPNs ensure that confidential information remains secure, regardless of the user's location or the network they're connected to.
In conclusion, the benefits of using a VPN on mobile devices are manifold, ranging from enhanced privacy and security to unrestricted access to online content and secure financial transactions. As the reliance on mobile technology continues to grow, integrating a VPN into one's digital toolkit has become essential for safeguarding personal information and maximizing online freedom.
VPN setup Android tutorial
Title: Easy VPN Setup Tutorial for Android Devices
In today's interconnected world, safeguarding your online privacy is paramount. One effective way to achieve this is by using a Virtual Private Network (VPN) on your Android device. A VPN encrypts your internet connection, shielding your data from prying eyes and potential hackers. Setting up a VPN on your Android device is simple and can be done in just a few easy steps.
Here's a step-by-step guide to help you set up a VPN on your Android device:
Choose a Reliable VPN Service: Before you begin, select a reputable VPN provider with a user-friendly Android app. Look for features like strong encryption, a large server network, and a no-logs policy for maximum privacy.
Download and Install the VPN App: Head to the Google Play Store on your Android device and search for the VPN provider's app. Once you've found it, download and install the app onto your device.
Sign Up and Log In: After installing the app, open it and sign up for an account if you haven't already. Then, log in using your credentials.
Connect to a VPN Server: Once logged in, the app will display a list of available server locations. Choose a server location from the list and tap on it to connect. You can select a server based on your location or specific needs, such as accessing geo-restricted content.
Enable VPN Connection: After selecting a server, toggle the VPN connection switch to enable the VPN. Once connected, you'll see a VPN icon in the status bar indicating that your internet connection is now secure.
Verify Connection: To ensure that the VPN is working correctly, visit a website or use an online tool to check your IP address. It should reflect the server location you selected earlier.
Adjust Settings (Optional): Most VPN apps offer additional settings that you can customize according to your preferences. Explore the app's settings menu to configure options like protocol selection, auto-connect, and split tunneling.
By following these simple steps, you can quickly set up a VPN on your Android device and enjoy a more secure and private online experience. Remember to keep your VPN app updated and regularly connect to ensure continuous protection of your data and privacy.
VPN security Samsung smartphone
When it comes to safeguarding your online privacy and security on a Samsung smartphone, using a Virtual Private Network (VPN) is a top-notch solution. VPNs encrypt your internet connection, preventing third parties from intercepting your data and tracking your online activities.
Samsung smartphones are popular targets for cyberattacks due to their widespread usage. By using a VPN on your Samsung device, you can ensure that your sensitive information, such as passwords, personal messages, and browsing history, remains secure from prying eyes.
VPN security on a Samsung smartphone works by routing your internet traffic through a secure server, making it nearly impossible for hackers or internet service providers to monitor your online behavior. This encryption is especially crucial when using public Wi-Fi networks, where cyber threats are most prevalent.
Moreover, VPNs allow users to access geo-restricted content and services by changing their virtual location. This feature comes in handy when you want to stream region-locked content or access websites not available in your country.
To enhance VPN security on your Samsung smartphone, choose a reputable VPN provider that offers strong encryption protocols, a no-logs policy, and a kill switch feature that automatically disconnects your device from the internet if the VPN connection is lost.
In conclusion, utilizing a VPN on your Samsung smartphone is a proactive measure to bolster your online security and privacy. By encrypting your internet connection and masking your IP address, VPNs provide a robust defense against cyber threats in today's digital age.
VPN troubleshooting Samsung device
Troubleshooting VPN Connection on Samsung Devices
Virtual Private Networks (VPNs) are invaluable tools for safeguarding your online privacy and security, but occasionally, issues may arise when trying to establish a connection on Samsung devices. Here are some common troubleshooting steps to resolve VPN-related problems:
Check Network Connectivity: Ensure that your Samsung device is connected to a stable internet connection, whether through Wi-Fi or mobile data. Weak or intermittent connections can disrupt VPN functionality.
Restart the Device: Sometimes, a simple reboot can fix underlying software glitches that may be hindering the VPN connection process. Turn off your Samsung device, wait a few seconds, and then power it back on.
Update VPN App and System Software: Ensure that both your VPN app and your Samsung device's operating system are updated to the latest versions. Developers often release patches and updates to address compatibility issues and improve performance.
Switch VPN Servers: If you're experiencing connectivity issues with a particular VPN server, try switching to a different server location within the VPN app. Some servers may be experiencing high traffic or technical difficulties, causing connection problems.
Check VPN Settings: Review the settings within your VPN app to ensure they are configured correctly. Double-check your username, password, and any other authentication details required for connecting to the VPN server.
Reset Network Settings: If other devices on the same network can connect to the VPN without issues, but your Samsung device cannot, consider resetting the network settings on your device. This action will clear any network-related configurations that may be causing conflicts.
Contact VPN Provider Support: If you've exhausted all troubleshooting steps and still can't establish a VPN connection on your Samsung device, reach out to your VPN provider's customer support team for assistance. They can offer specialized troubleshooting advice tailored to their service.
By following these troubleshooting steps, you can resolve common VPN connectivity issues on your Samsung device and enjoy a secure and private internet browsing experience.
0 notes
Text
do i need vpn for android data
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need vpn for android data
Android VPN necessity
In today's digital age, where privacy and security are paramount concerns, using a Virtual Private Network (VPN) on your Android device has become a necessity rather than a luxury. Android VPNs offer numerous benefits that safeguard your online activities and data.
First and foremost, an Android VPN encrypts your internet connection, ensuring that your sensitive information remains confidential. Whether you're browsing the web, accessing online banking services, or transmitting personal messages, encryption shields your data from prying eyes, including hackers and government surveillance.
Moreover, Android VPNs enable you to bypass geographical restrictions and access content that may be blocked in your region. By connecting to servers located in different countries, you can unlock websites, streaming services, and social media platforms that are otherwise inaccessible. This feature is particularly useful for travelers who want to stay connected to their favorite content while abroad.
Additionally, using a VPN on your Android device enhances your anonymity online. By masking your IP address and routing your internet traffic through remote servers, VPNs make it nearly impossible for websites and advertisers to track your online behavior. This not only protects your privacy but also reduces the amount of targeted advertising you encounter.
Furthermore, Android VPNs enhance your security when using public Wi-Fi networks. These networks are notorious for their vulnerability to cyber attacks, but with a VPN, your data remains encrypted, safeguarding you against potential threats such as Wi-Fi spoofing and packet sniffing.
In conclusion, the use of a VPN on your Android device is no longer just a precautionary measure—it's a vital tool for protecting your privacy, enhancing your security, and accessing unrestricted content online. With the myriad of threats and restrictions present in today's digital landscape, investing in a reliable Android VPN is a wise decision for anyone concerned about their online safety and freedom.
Mobile data security
Mobile data security is paramount in today's digital age, where smartphones are integral to both personal and professional life. With the convenience of accessing sensitive information on the go, the risk of data breaches and cyber-attacks looms large. Implementing robust mobile data security measures is essential to safeguarding against potential threats.
One of the primary concerns with mobile data security is the vulnerability of data during transmission. Hackers can intercept data packets sent over unsecured networks, such as public Wi-Fi hotspots, compromising sensitive information like passwords, financial details, and personal data. To mitigate this risk, employing encryption protocols like Transport Layer Security (TLS) or Virtual Private Networks (VPNs) ensures that data remains encrypted and secure during transmission.
Furthermore, the proliferation of mobile applications poses another challenge to data security. Malicious apps can exploit vulnerabilities in device operating systems or access permissions to steal data or spy on users. Regularly updating mobile operating systems and applications, along with scrutinizing app permissions, can help prevent such security breaches.
Implementing strong authentication methods, such as biometric recognition or two-factor authentication, adds an extra layer of security to mobile devices. This ensures that even if a device is lost or stolen, unauthorized access to sensitive data is prevented.
Educating users about the importance of mobile data security and promoting best practices, such as avoiding downloading apps from untrusted sources and being cautious of phishing attempts, is crucial in fostering a security-conscious culture.
In conclusion, mobile data security is a multifaceted issue that requires proactive measures to mitigate risks and protect sensitive information. By implementing encryption protocols, staying vigilant against malicious apps, employing strong authentication methods, and promoting user education, individuals and organizations can enhance their mobile data security posture and minimize the threat of cyber-attacks.
VPN benefits for Android
Title: Unlocking the Benefits of VPN for Android Users
In an era where digital privacy is increasingly threatened, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. For Android users, the benefits of utilizing a VPN are particularly noteworthy, offering a myriad of advantages that enhance security, privacy, and accessibility.
First and foremost, VPNs encrypt data transmitted between the Android device and the internet, effectively shielding it from prying eyes. This encryption is especially crucial when connecting to public Wi-Fi networks, where hackers often lurk, waiting to intercept sensitive information. By encrypting data traffic, VPNs provide Android users with peace of mind, ensuring that their personal and financial details remain confidential.
Moreover, VPNs enable Android users to bypass geographical restrictions and access content that may be unavailable in their region. Whether it's streaming services, social media platforms, or news websites, a VPN grants users the ability to circumvent censorship and enjoy unrestricted access to the global internet.
Additionally, VPNs can improve online gaming experiences for Android users by reducing latency and preventing Distributed Denial of Service (DDoS) attacks. By connecting to VPN servers optimized for gaming, players can enjoy smoother gameplay and enhanced security, free from the disruptions caused by malicious attackers.
Furthermore, VPNs offer Android users the ability to mask their IP addresses, preserving anonymity and preventing online tracking. This anonymity extends to browsing habits, ensuring that users can explore the internet without fear of being monitored or targeted by advertisers.
In conclusion, the benefits of using a VPN on Android devices are manifold, encompassing enhanced security, privacy, accessibility, and anonymity. By harnessing the power of VPN technology, Android users can navigate the digital landscape with confidence, knowing that their online activities are protected and their freedoms preserved.
Personal data protection
Title: Safeguarding Your Personal Data: Tips for Effective Protection
In the digital age, personal data protection is paramount. With the increasing prevalence of cyber threats and data breaches, safeguarding your personal information has become more crucial than ever. Whether it's your financial details, social media accounts, or sensitive documents, ensuring the security of your personal data is essential to prevent identity theft, fraud, and privacy violations.
One of the fundamental steps in personal data protection is to use strong and unique passwords for each of your online accounts. Avoid using easily guessable passwords like "123456" or "password" and instead opt for complex combinations of letters, numbers, and symbols. Additionally, consider using a reputable password manager to securely store and manage your passwords.
Furthermore, be cautious about the information you share online. Avoid disclosing sensitive details such as your home address, phone number, or financial information on public forums or social media platforms. Cybercriminals often exploit this information for malicious purposes, so exercise discretion when sharing personal data online.
Regularly update your devices and software to ensure they have the latest security patches and fixes. Hackers often target outdated systems with known vulnerabilities, so keeping your software up-to-date is essential in mitigating security risks.
Consider encrypting sensitive files and communications to add an extra layer of protection. Encryption scrambles data so that it's unreadable without the correct decryption key, making it significantly harder for unauthorized individuals to access your personal information.
Lastly, remain vigilant against phishing attempts and suspicious emails. Be wary of unsolicited emails requesting personal information or urging you to click on suspicious links. When in doubt, verify the legitimacy of the sender before taking any action.
By implementing these proactive measures, you can significantly enhance your personal data protection and minimize the risk of falling victim to cyber threats. Remember, safeguarding your personal information is not just a precaution—it's a necessity in today's interconnected world.
Android privacy measures
Title: Ensuring Privacy: Android's Robust Measures
In today's digital age, privacy is of utmost concern, especially with the widespread use of smartphones. Android, one of the leading mobile operating systems, has taken significant strides in implementing robust privacy measures to safeguard user data.
One of the key features enhancing privacy on Android devices is the granular permission system. Users have the power to control which apps have access to specific device functionalities such as camera, microphone, location, and contacts. This empowers users to limit the data shared with apps, thereby reducing the risk of unauthorized access.
Furthermore, Android regularly releases security updates to patch vulnerabilities and protect against emerging threats. These updates not only enhance the security of the operating system but also address potential privacy loopholes, ensuring that users' sensitive information remains secure.
Additionally, Android offers users the option to encrypt their device storage, providing an extra layer of protection for personal data. By encrypting data stored on the device, even if the device falls into the wrong hands, the data remains inaccessible without the encryption key, safeguarding user privacy.
Moreover, Android provides users with features such as Google Play Protect, which continuously scans apps for malware and other security threats. This proactive approach helps in maintaining the integrity of the app ecosystem and protecting users from potential privacy breaches.
In conclusion, Android prioritizes user privacy by implementing robust measures such as granular permissions, regular security updates, device encryption, and proactive malware detection. By continuously evolving and adapting to emerging threats, Android ensures that users can confidently utilize their devices while safeguarding their sensitive information.
0 notes
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
The Intricate World of Android Spy Apps: Unmasking Functionality and Ethics

The digital realm has become an extension of ourselves, especially with smartphones playing a central role in our daily lives. This extends to our children, partners, and even employees in specific situations. While trust is paramount, there may be instances where monitoring phone activity becomes a necessity. This is where Android spy apps enter the scene, promising a glimpse into the target device's digital landscape.
However, venturing into the world of spy apps necessitates a clear understanding of the legal and ethical ramifications. Local laws regarding phone monitoring software should be thoroughly reviewed before using any such app. Transparency is also key – always disclose monitoring to those being monitored, particularly in the case of children.
Free vs. Paid Spy Apps: Unveiling the Reality
The quest for a truly free, feature-rich Android spy app can be a deceptive one. While some apps advertise free tiers, they often come with significant limitations. Core functionalities often require a paid subscription, leaving you with a restricted experience in the free version.
Here's a closer look at some popular contenders and their feature breakdowns:
Onemonitar: This user-friendly app boasts a comprehensive feature set. The free version offers a taste of its capabilities, such as limited call history and contact details. However, for in-depth monitoring, a paid subscription unlocks features like extensive call monitoring (recordings and call duration), detailed message tracking across various platforms (WhatsApp, Facebook Messenger), real-time GPS location tracking, internet browsing history, and app usage monitoring.
Chyldmonitar: Designed for user ease, Chyldmonitar offers a decent feature range in both free and paid tiers. The free version provides basic call log and SMS monitoring, along with limited app usage tracking. Upgrading unlocks more detailed call recordings, in-depth message tracking, comprehensive app usage monitoring, remote camera activation (for capturing photos and surroundings), and even keylogging functionality.
Onespy: This app focuses on stealth and invisibility. Similar to its counterparts, Onespy offers a free tier with limited features like basic details on calls and SMS. Upgrading unlocks advanced call monitoring (recordings and call duration), comprehensive message tracking across various apps, real-time GPS location tracking, internet browsing history, and app usage monitoring.
Crucial Considerations Before Using Spy Apps:
Legality: Always ensure using a spy app complies with your local laws. Regulations vary by region, so consult with a legal professional if necessary.
Target Device Compatibility: Not all apps are compatible with all Android versions. Verify compatibility before downloading to avoid wasting time and effort.
Rooted vs. Non-Rooted Devices: Certain features might require a rooted device (providing administrator access), which can be risky as it bypasses security measures and exposes the device to vulnerabilities.
Target Device Accessibility: Installing the app often necessitates physical access to the target device. Consider the practicality of acquiring this access.
Alternative Solutions: Consider These Options Before Resorting to Spy Apps
Parental Control Apps: Designed for monitoring children's phone activity, these apps prioritize safety and offer features like app blocking, screen time management, and website filtering.
Built-in Monitoring Tools: Many Android devices have built-in features like Google Family Link that allow for some degree of monitoring for children's devices.
The Ethical Tightrope Walk: Weighing the Implications
The use of spy apps raises a critical ethical question. While there might be legitimate reasons for monitoring someone's phone activity, it's crucial to weigh the ethical concerns. Open communication and trust should be the cornerstone of any relationship. Spy apps should only be considered as a last resort and with complete transparency.
Conclusion: A World Beyond Spy Apps
While Android spy apps exist, approaching them with caution is essential. Understanding the legality, respecting privacy, and exploring alternative solutions are all crucial aspects to consider. Remember, a foundation of trust is irreplaceable. If you have concerns about someone's phone activity, open communication might be a more sustainable solution than resorting to covert monitoring.
0 notes
Text
Spy on WhatsApp Messages Without Installing Software

With the ever-increasing use of messaging platforms like WhatsApp for communication, individuals and organizations are interested in monitoring messages. Whether you’re a parent concerned about your child's online safety or an employer wanting to track workplace communication, the question arises: Can you spy on WhatsApp messages without installing software? This blog aims to answer that question and explore the different facets of monitoring WhatsApp messages without downloading or installing additional applications.
1. How to Spy on WhatsApp Messages Without Installing Any Software
The idea of spying on WhatsApp messages without installing any software is appealing. It means you don't have to tamper with the target phone or risk being detected by app notifications or strange permissions. But how can this be done?
One of the most common methods is through WhatsApp Web. Here’s how it works:
WhatsApp Web: This feature of WhatsApp allows users to access their messages on a computer by scanning a QR code from their phone. By gaining temporary physical access to someone’s phone, you can open their WhatsApp Web on your browser and keep the session open, thus monitoring their conversations remotely without needing any additional software.
The steps to do this:
Open web.whatsapp.com on your computer.
Open WhatsApp on the target phone.
Go to WhatsApp Web from the settings.
Scan the QR code shown on your computer with the target phone.
Once connected, you’ll be able to see all the messages exchanged on the phone. It’s important to note that the phone will need to stay connected to the internet for you to continuously spy on the messages.
2. The Easiest Way to Spy on WhatsApp Messages Without Downloads
If you’re looking for the easiest way to spy on WhatsApp messages without downloading any software, WhatsApp Web remains the most straightforward method. However, there are a few limitations:
The target phone must remain connected to the internet.
WhatsApp Web logs out after a while if not used, and the target user might notice if they check their WhatsApp Web section.
You’ll need physical access to the phone at least once to scan the QR code.
Another method that doesn’t require software installation but involves more advanced knowledge is using network sniffing tools. Tools like Wireshark can capture data packets sent through a Wi-Fi network. If both the target phone and your computer are on the same network, it is technically possible to capture WhatsApp messages. However, this requires substantial technical knowledge, is illegal in most regions, and violates privacy laws.
3. Is It Possible to Spy on WhatsApp Messages Without Installing Software?
The short answer to this question is: It’s possible, but there are significant limitations.
While it is tempting to find a solution that allows for completely undetected spying without software, the truth is that the most effective methods involve installing a third-party monitoring app. The closest you can get to spy without installation is using WhatsApp Web or some advanced network monitoring techniques.
For most users, third-party software like HackersList, FlexiSpy, or others remains the most reliable solution, but these require installation on the target phone.
4. Spy on WhatsApp Messages Remotely: No Installation Required
Can you spy on WhatsApp messages remotely without installing software? Yes, but only under specific conditions.
If you can gain temporary physical access to the phone to set up WhatsApp Web or if you have access to their iCloud or Google backup (in the case of iOS and Android devices respectively), you can monitor their WhatsApp messages remotely without any additional software.
Here’s how the iCloud or Google Drive method works:
WhatsApp backs up messages to the cloud periodically.
If you have access to the iCloud or Google account of the target user, you can download and view these backups.
However, keep in mind that WhatsApp backups are often encrypted, and it may be difficult to access the messages unless you have advanced decryption tools.
This method is often difficult to pull off and may require the target’s login credentials. Additionally, it only gives you access to the most recent backup, not live conversations.
5. The Truth About Spying on WhatsApp Messages Without Installing an App
The truth is, spying on WhatsApp messages without installing an app is possible but not practical for most users. The methods that don’t require software installation, such as using WhatsApp Web, still require physical access to the phone or access to cloud backups.
More advanced options, such as using network monitoring tools, can be complicated and illegal. Moreover, most spying solutions that truly provide effective monitoring over time involve some form of app installation, even if they are discreet.
If you’re looking for a way to spy on WhatsApp without the target knowing, and without software, you might be disappointed. For reliable, long-term monitoring, installing a stealth app remains the most effective solution.
6. Can You Spy on WhatsApp Messages Without Software?
Can you spy on WhatsApp messages without software? Theoretically, yes, but it’s highly impractical. Here’s why:
WhatsApp Web requires physical access to the phone and is easy for the target to detect.
Network sniffing requires technical knowledge and can only be done under specific conditions (same network, unsecured Wi-Fi, etc.).
Cloud backup access requires knowing the target’s login credentials, and even then, you may need to decrypt the backups to read the messages.
The takeaway is that while it’s possible to spy on WhatsApp without installing software, the methods are either temporary or require significant technical skills and legal risks.
7. Spy on WhatsApp Messages Online: No Software Needed
Many online tools and websites claim to offer WhatsApp spying services without installing software. Be wary of these claims, as most of them are scams. Many such sites promise access to WhatsApp messages simply by entering the target phone number, but these are either fraudulent or phishing schemes designed to steal your personal information or money.
If you're searching for a legitimate way to spy on WhatsApp messages online, the safest and most practical method remains using WhatsApp Web or accessing cloud backups, as discussed earlier.
Be cautious about websites that ask for payment upfront without any proof of service delivery. Always research thoroughly before trusting such platforms.
8. Spy on WhatsApp Messages Without Physical Access to the Phone
Spying on WhatsApp messages without physical access to the phone is one of the most sought-after methods, but it’s rarely feasible without software installation.
The only way this is possible is by accessing the target phone’s cloud backups or using advanced hacking techniques, which often violate laws. Some services claim to access WhatsApp messages remotely, but many of these are either scams or involve risky methods that could compromise your data.
For instance, some third-party spy apps allow you to monitor a device remotely, but they still require initial setup on the target device, meaning you’ll need physical access at least once.
9. Legal Ways to Spy on WhatsApp Messages Without Installing Apps
It’s important to understand that spying on someone’s WhatsApp messages without their consent is illegal in many countries. Privacy laws protect individuals from unauthorized access to their communications.
However, there are a few legal ways to monitor WhatsApp messages in certain situations:
Parental monitoring: Parents may legally monitor their children’s activities for safety reasons, especially minors.
Employer monitoring: If an employer provides work devices, they may have the right to monitor communication for professional purposes, but this often requires employee consent.
In both cases, using third-party monitoring software that requires installation is the most practical and legal approach.
10. Spy on WhatsApp Messages for Free Without Any Software
Can you spy on WhatsApp messages for free without software? While it might be possible to use the WhatsApp Web method or by accessing backups, the practicality and long-term success of these methods are limited.
Most free methods still require some form of physical access to the phone or advanced technical knowledge, and they often don’t provide ongoing monitoring. Moreover, many free online tools are scams or ineffective.
If you’re looking for a reliable way to monitor WhatsApp messages, investing in reputable software is usually the best option, though it comes at a cost.
Conclusion
In summary, while it’s theoretically possible to spy on WhatsApp messages without installing software, the methods available are often limited, temporary, and not entirely foolproof. WhatsApp Web offers a quick, easy solution for short-term monitoring, but long-term, effective spying usually requires app installation.
Whether you're a parent, employer, or concerned individual, always be aware of the legal and ethical implications of monitoring someone’s communications. When in doubt, it’s best to consult legal guidelines and use reputable monitoring tools that respect privacy laws.
0 notes