#remote monitorin
Explore tagged Tumblr posts
Text
Zero Trust Security: Principles of the Zero Trust Security Model

Picture this: You're at a party and someone you've never met before walks up to you, asking to borrow your phone. Would you hand it over without a second thought? Probably not. You'd likely ask who they are and why they need your phone, and maybe even watch them like a hawk if you decide to lend it. That, my friends, is the essence of Zero Trust in a nutshell.
Zero Trust Explained in 4 Minutes:
For those of you who would rather watch a video than read an article. Here is a great video by IBM Security that explains the model in 4 minutes! https://www.youtube.com/watch?v=yn6CPQ9RioA
What is the Zero Trust Architecture?
Zero Trust Security is like being that cautious party-goer but in the digital world. It's a cybersecurity model that operates on the principle of "trust no one, verify everything." In today's world of sophisticated cyber threats, it's no longer enough to build a strong perimeter and trust everything inside simply. Zero Trust takes a more granular approach, constantly verifying every user, device, and application, regardless of their location or network & network security.
How did the Zero Trust Model originate?
The concept of Zero Trust isn't new, but it's gained significant traction in recent years. It was first introduced by John Kindervag in 2010 when he was working as a principal analyst at Forrester Research. Kindervag recognized that traditional security models were becoming obsolete in the face of evolving threats and changing work environments.
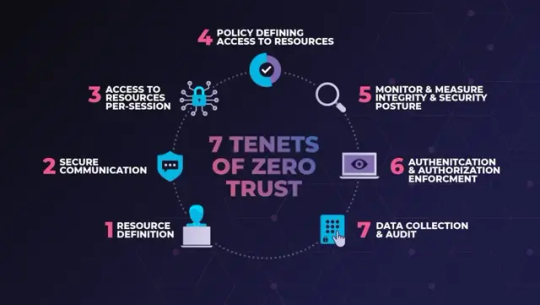
7 Tenets of Zero Trust - Credits: Cimcor.com I remember when I first heard about the Zero Trust architecture at a cybersecurity conference in 2012. At the time, it seemed like a radical departure from the status quo. Many of us in the room were skeptical - after all, how could a business function if it didn't trust its employees and systems? Little did we know that this model would become the gold standard for cybersecurity in just a few short years.
What are the core concepts of Zero Trust Security?
At its heart, the Zero Trust approach is built on three main pillars: Verify explicitly: Always authenticate and authorize based on all available data points. Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA). Assume breach: Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Why is Zero Trust Security Becoming Essential in Today?
Information security has changed dramatically over the past decade. Remote work, cloud computing, and the Internet of Things (IoT) have expanded the attack surface exponentially. Traditional perimeter-based security models are no longer sufficient. I learned this lesson the hard way when my previous company fell victim to a sophisticated phishing attack. Despite our strong firewalls and antivirus software, an employee's compromised credentials led to a significant data breach. It was a wake-up call that made us realize the importance of verifying every access request, regardless of its origin.
What are the Key Principles of the Zero Trust Security Model?
"Never trust, always verify" This mantra is the cornerstone of Zero Trust. It means that no user, device, or network should be trusted by default, even if they're already inside the security perimeter. Every access request must be authenticated, authorized, and encrypted before granting access. Least privilege access Think of this as a "need-to-know" basis for your entire IT infrastructure. Users are given the minimum levels of access needed to perform their jobs. This limits the potential damage if an account is compromised. Micro-segmentation Instead of treating your network as one large, interconnected entity, micro-segmentation divides it into small, isolated zones. This containment strategy limits an attacker's ability to move laterally through your network. Continuous monitoring and validation Zero Trust isn't a "set it and forget it" solution. It requires ongoing monitoring and real-time assessment of security posture. This allows for quick detection and response to potential threats.
How Does Zero Trust Impact Organizational Structure?
Implementing Zero Trust isn't just a technical challenge - it's a cultural shift. It requires changes in IT management, policies, and even how employees think about security. For instance, when my current organization transitioned to a Zero Trust model, we had to completely overhaul our IT policies. Gone were the days of shared passwords and unrestricted access to company resources. Instead, we implemented strict access controls and multi-factor authentication for every user. This shift also impacts user roles and responsibilities. Employees need to be educated about the importance of security and their role in maintaining it. They may need to go through additional authentication steps or request access to resources they previously had unfettered access to. For security teams, Zero Trust means a more proactive approach to threat detection and incident response. Instead of focusing primarily on perimeter defense, they need to monitor and analyze behavior across the entire network continuously.
What technologies support the Zero Trust Model?
A successful Zero Trust implementation relies on a suite of technologies working in concert: Identity and Access Management (IAM) IAM is the backbone of Zero Trust. It ensures that the right individuals have access to the right resources at the right times for the right reasons. Endpoint security solutions These tools protect individual devices (endpoints) from threats, crucial in a world where work happens on various devices and locations. Micro-segmentation technologies These allow for fine-grained segmentation of networks, applications, and data. Cloud security solutions As more organizations move to the cloud, tools that can enforce Zero Trust principles in cloud environments become essential.
What are the Challenges of Implementing Zero Trust?
While Zero Trust offers significant security benefits, it's not without its challenges. One common misconception is that Zero Trust is a product you can simply purchase and implement. In reality, it's a comprehensive security strategy that requires careful planning and execution. Another challenge is overcoming resistance to change. Users may find the additional security measures cumbersome, and IT teams may struggle with the complexity of implementation. When we first introduced Zero Trust policies, I remember the flood of complaints from employees who suddenly couldn't access resources they were used to having at their fingertips. It took time and education to help everyone understand why these changes were necessary. Cost can also be a significant hurdle. Implementing Zero Trust often requires substantial investments in new technologies and training. However, when weighed against the potential cost of a major security breach, many organizations find the investment worthwhile.
How can organizations successfully transition to this Model?
Transitioning to Zero Trust is a journey, not a destination. Here are some steps to get started: Assess your current security posture: Understand your assets, users, and data flows. Identify gaps in your current security strategy. Define your project surface: Identify your critical data, assets, applications, and services (DAAS). Map transaction flows: Understand how your DAAS interacts with other resources. Create Zero Trust policies: Develop policies that enforce the principle of least privilege access. Monitor and maintain: Continuously monitor your network and adjust policies as needed.
What are the first steps for organizations looking to adopt Zero Trust?
Organizations looking to adopt this model should begin by reassessing their network architecture and redefining the network perimeter. The core principle of zero trust is to eliminate implicit trust within the corporate network. This means that every user and device, whether inside or outside the network, must be verified before being granted secure access to applications and sensitive data. Implementing a zero trust strategy involves creating robust access policies that dictate how users and devices can gain access to resources. Next, organizations need to establish effective security controls to monitor and manage zero trust network access. This includes deploying a solution that continuously assesses the risk associated with each access attempt. As zero trust is designed to protect inside and outside the network, it also requires constant evaluation of the security policies to adapt to emerging threats.
How Can Organizations Assess their Current Security for Zero Trust Readiness?
To effectively assess their current security for zero trust readiness, organizations must first understand that zero trust is a security approach that fundamentally changes the perception of trust within the organization’s network. The principles behind zero trust emphasize the mantra “never trust, always verify,” which means that every user and device attempting to access resources should be authenticated and authorized, regardless of their location within the network infrastructure. Organizations can begin this assessment by evaluating their existing security policies and identifying gaps in their current security based on traditional perimeter defenses. Furthermore, zero trust also requires a comprehensive analysis of security operations to ensure that each segment of the zero trust enterprise is properly monitored and maintained. Organizations should also explore zero trust use cases to understand how zero trust works in practice, focusing on the benefits of this model such as improved data protection and reduced attack surfaces. Remember, it is not about distrusting your employees or partners. It's about creating a security that's resilient in the face of evolving threats. By verifying every request, limiting privileges, and continuously monitoring your environment, you can significantly reduce your risk of a costly data breach. In my years of experience in cybersecurity, I've seen many trends come and go. But Zero Trust feels different. It's not just a new set of tools or technologies - it's a fundamental shift in how we approach security. Read the full article
0 notes
Text
How to Manage delete actions in d365fo

Introduction
Effective data management is crucial to preserving system integrity and operational effectiveness in Dynamics 365 for Finance and Operations (D365FO). Understanding and putting into practice delete actions in d365fo is a critical component of this management. In order to keep your company's data environment clean and compliant, this article will offer advice on how to handle delete activities efficiently.
Comprehending D365FO Delete Actions
The procedures used to eliminate records from the system are referred to as "delete actions" in D365FO. These steps are essential for getting rid of superfluous or out-of-date data, which can clog databases and affect performance. D365FO offers a number of record deletion techniques, each tailored to a particular business situation.
The Best Ways to Handle Delete Actions
1. Clearly define your policies
Prior to executing remote operations, it is crucial to set up explicit data management guidelines. These guidelines should specify when and why data should be removed, making sure that everyone in the team is aware of the justification for such actions. This clarity preserves data integrity and helps avoid unintentional deletions.
2. Make use of user rights Sensibly
In D365FO, controlling user rights is essential when it comes to removing operations. Make sure that the only people with the authority to remove records may do so. You reduce the possibility of unintentional or unauthorized deletions by limiting access. Review and update permissions frequently in response to changes in roles within your company.
3. Put Soft Deletes into Practice
For data that might need to be referred to later, think about using soft deletes. Instead of deleting records from the system permanently, soft deletes enable them to be declared as inactive systems. This method maintains the current dataset clean while preserving old data for compliance and auditing needs.
4. Automate Procedures for Deletion
Deleting actions automatically can greatly increase productivity and lower the possibility of human error. Because D365FO allows batch processing, users can plan deletion actions for off-peak times. This automation guarantees routine data cleanup and aids in performance maintenance.
5. Track and Examine Delete Operations
For compliance and accountability, it is essential to keep an audit trail for delete actions. Information about who removed what and when is automatically logged by D365FO. Examine these logs on a regular basis to keep an eye on deletion activity and make sure company policies are being followed.
6. Review Data Frequently
Establish a regular review procedure to find records that are superfluous or out-of-date. Conducting routine data audits can assist in identifying that must be removed, enabling prompt deletion procedures. This proactive strategy maintains the optimization and organization of your database.
7. Evaluate Removals in a Sandbox Setting
It is advisable to test the procedures in a sandbox before carrying out delete operations in a production setting. By ensuring that the deletion process operates as planned without interfering with other processes, this testing helps detect possible problems.
8. Offer Instruction and Records
Make certain that every user participating in data management has received sufficient training regarding the steps and consequences of deleting data. Users are empowered to handle delete actions with confidence and effectiveness when explicit documentation on the process is provided, along with best practices and troubleshooting advice.
Conclusion
Effectively controlling remote actions in D365FO is crucial to preserving operational effectiveness and data integrity. Organizations can simplify their data management procedures by implementing clear regulations, making intelligent use of user permissions, and automating procedures. The efficiency of remote activities is further increased by routine training and monitoring, which keeps your Dynamics 365 environment compliant and structured.
0 notes
Text
Key Strategies to Successfully Implement Digital Transformation
In today’s rapidly evolving business landscape, digital transformation has become essential for organizations seeking to remain competitive. It involves integrating digital technology into all areas of a business, fundamentally changing how you operate and deliver value to customers. However, implementing digital transformation is not merely about adopting new technologies; it requires a comprehensive strategy that encompasses culture, processes, and customer engagement. Here are key strategies to successfully implement digital transformation in your organization.

1. Define Clear Objectives and Goals
Before embarking on a digital transformation journey, it is crucial to establish clear objectives and goals. What do you hope to achieve? Whether it’s improving customer experience, enhancing operational efficiency, or fostering innovation, having specific, measurable goals will guide your strategy. Align these objectives with your overall business strategy to ensure that digital transformation efforts support your organization’s mission and vision.
Example:
If your goal is to enhance customer experience, consider how digital tools can facilitate better communication, personalization, and service delivery.
2. Engage Stakeholders Across the Organization
Successful digital transformation requires buy-in from all levels of the organization. Engage stakeholders, including employees, management, and even customers, in the planning process. Encourage feedback and input to create a sense of ownership and ensure that the transformation aligns with their needs and expectations. This collaboration will foster a culture of innovation and adaptability, making the transition smoother.
Tip:
Hold workshops and brainstorming sessions to gather insights from various departments and identify pain points that digital solutions can address.
3. Invest in the Right Technology
Choosing the right technology is a critical aspect of digital transformation. Evaluate the tools and platforms that will best meet your organization’s needs. Consider scalable solutions that can grow with your business and integrate seamlessly with existing systems. Emerging technologies like artificial intelligence (AI), machine learning, and cloud computing can offer significant advantages in automating processes, analyzing data, and enhancing decision-making.
Key Considerations:
Cloud Solutions: Enable flexibility and accessibility for remote work.
Data Analytics Tools: Provide insights to inform strategic decisions.
Collaboration Software: Facilitate communication among teams.
4. Focus on Data Security and Compliance
As organizations embrace digital transformation, data security and compliance become paramount. Protecting sensitive information and adhering to regulatory requirements are critical to maintaining trust with customers and stakeholders. Implement robust cybersecurity measures and ensure that your technology solutions comply with relevant laws and regulations, such as GDPR or HIPAA.
Action Steps:
Conduct regular security assessments.
Train employees on data protection best practices.
Implement multi-factor authentication for access to sensitive data.
5. Foster a Culture of Continuous Learning
Digital transformation is an ongoing process that requires a mindset of continuous improvement. Foster a culture that encourages learning, experimentation, and adaptability. Provide training and resources for employees to develop their digital skills and stay abreast of industry trends. This approach not only empowers your workforce but also drives innovation and enhances overall performance.
Implementation Tips:
Offer workshops and online courses on emerging technologies.
Encourage employees to share knowledge and best practices.
Recognize and reward innovative ideas and initiatives.
6. Monitor Progress and Adapt Strategies
Implementing digital transformation is not a one-time effort; it requires ongoing monitoring and adaptation. Establish key performance indicators (KPIs) to measure the success of your initiatives and track progress against your goals. Use data analytics to gain insights into what’s working and what needs adjustment. Be willing to pivot your strategies based on feedback and changing market conditions.
KPIs to Consider:
Customer satisfaction scores
Employee productivity metrics
Revenue growth attributed to digital initiatives
youtube
Conclusion
Successfully implementing digital transformation is a multifaceted endeavor that requires a strategic approach. By defining clear objectives, engaging stakeholders, investing in the right technology, ensuring data security, fostering a culture of continuous learning, and monitoring progress, organizations can navigate the complexities of digital transformation. Embracing these strategies will not only enhance operational efficiency but also position your organization for long-term success in a digital-first world.
SITES WE SUPPORT
Purchase Improvement - Wix
SOCIAL LINKS Facebook Twitter LinkedIn
0 notes
Text
Streamline your operations with remote waste oil monitoring from Oto Data Tank Monitors. Our advanced solutions provide real-time tracking and efficient management. Learn more at
0 notes
Text
Revolutionizing Diabetes Management with Remote Patient Monitorin
Discover how Remote Patient Monitoring (RPM) is transforming diabetes management through continuous glucose monitoring, personalized care plans, and AI-driven
0 notes
Text
Revolutionizing Diabetes Management with Remote Patient Monitorin
Discover how Remote Patient Monitoring (RPM) is transforming diabetes management through continuous glucose monitoring, personalized care plans, and AI-driven i
0 notes
Text
The Top Cctv Security Systems Companies In Dubai: Ensuring Your Safety And Peace Of Mind
Are you looking to enhance the security of your home or business in Dubai? Look no further than CCTV security systems! These cutting-edge solutions offer round-the-clock surveillance, providing peace of mind and safety. In this blog post, we will explore Dubai's top CCTV security systems companies, helping you decide to safeguard what matters most to you. Let's dive in!
Benefits of CCTV Security Systems in Dubai
Living in a bustling city like Dubai comes with its own set of challenges regarding safety and security. This is where CCTV security systems are crucial in ensuring peace of mind for residents and business owners.
One key benefit of installing CCTV cameras is their deterrent effect on potential criminals. Visible cameras can significantly reduce the likelihood of break-ins, theft, vandalism, and other criminal activities.
Moreover, CCTV systems provide round-the-clock monitoring capabilities, allowing real-time surveillance of your property or premises. This means that any suspicious activity can be detected promptly, enabling quick responses from authorities or security personnel.
In addition to enhancing security, CCTV systems serve as valuable evidence in case of untoward incidents. Law enforcement agencies can use the recorded footage during investigations or by businesses to resolve disputes or insurance claims effectively.
Investing in a high-quality CCTV security system in Dubai is an essential step towards safeguarding your assets and ensuring the safety of your loved ones.
The Top CCTV Security Systems Companies in Dubai
When it comes to ensuring the safety and security of your property in Dubai, choosing the right CCTV security Systems Company is crucial. With many available options, selecting a reputable and reliable provider can give you peace of mind.
Some of Dubai's top CCTV security systems companies include XYZ Security Solutions, ABC Surveillance Technologies, and DEF Secure Systems. These companies offer state-of-the-art surveillance technology tailored to meet your specific needs.
Factors to consider when choosing a CCTV company include their reputation, experience in the industry, range of services offered, and customer reviews. It's essential to do thorough research before making a decision.
Investing in a quality CCTV system from one of these top companies can effectively enhance the security measures for your home or business.
Factors to Consider When Choosing a CCTV Security Systems Company
When choosing a CCTV security systems company in Dubai, consider the provider's reputation and experience. Look for companies with a proven track record of delivering high-quality surveillance solutions.
Another factor to consider is the range of services offered by the company. Opt for a provider that offers installation, maintenance, and support services to ensure your system operates smoothly.
Consider the company's technology. Make sure it offers advanced CCTV systems with features like remote access and motion detection for enhanced security monitoring.
Customer reviews and testimonials can be valuable sources of information when deciding on a CCTV provider. Take the time to research what previous clients have to say about their experiences with the company.
Remember to inquire about pricing packages and any additional costs involved. It is essential to choose a company that fits your budget while still effectively meeting your security needs.
Cost Comparison of the Top Companies
Cost is a significant factor when investing in CCTV security systems for your home or business in Dubai. Understanding the pricing structures of the top companies can help you make an informed decision about which provider best suits your budget and needs.
Different companies offer various packages and pricing options based on the number of cameras needed, installation fees, maintenance costs, and additional features such as remote monitoring capabilities. Before making a final choice, it's essential to compare these aspects among the top CCTV security system providers in Dubai.
While some companies may offer lower upfront costs, others might provide comprehensive packages that include ongoing support and upgrades. Consider the initial investment and long-term expenses associated with each company's offerings.
By conducting a thorough cost comparison analysis among Dubai's top CCTV security system companies, you can ensure that you are getting the best value for your money while prioritizing safety and peace of mind.
0 notes
Text
#RemoteHealthcare#PatientMonitoring#TelehealthTechnology#DigitalHealthcare#HealthTech#RemoteMonitoring
0 notes
Text
DO THE REMOTE NUERAL MONITORIN.....U DO IT FOR ((((EVERYTHING ELSE))))) THIS BLACK GUY WAS HOLDING MY 📬 KNOCKING ON MY DOOR AND (((KEPT))) KNOCKING ON MY DOOR USUALLY MAIL MEN KNOCK AND GO AWAY.....😒THIS MOTHER FUCKER DIDN'T HE KEPT KNOCKING ON MY DOOR
0 notes
Text
Security Information and Event Management Market Growth | Global Expansion and Forecast to 2030
According to a recent report published by Allied Market Research, titled, “Security Information and Event Managements Market by Component, Deployment Model, Enterprise Size, and Industry Vertical: Global Opportunity Analysis and Industry Forecast, 2021–2030,” the global security information and event management market size was valued at $3.92 billion in 2020, and is projected to reach $18.12 billion by 2030, growing at a CAGR of 16.4% from 2021 to 2030.
The security information and event management (SIEM) market is expected to be driven by growing demand for security solutions that assist organizations in identifying possible security threats and vulnerabilities. As remote workforces, bring your own device (BYOD) and SaaS apps policies have increased in popularity, industries require the level of transparency to manage network potential risks from outside the traditional network perimeter. The advanced SIEM to be used for anomaly detection is expected to offer significant growth for the security information and event management industry in the near future. IBM Corporation’s QRadar Security Intelligence is the only known product, which qualifies for anomaly detection or behavioral analytics. The challenges in usage on SIEM in anomaly detection such as information of time to apply this analysis or efficient procedure to adjust time intervals to accommodate random and infrequent acts of humans, affect the extensive adoption of such SIEM products. However, with innovation and more refined understanding, the demand for such solutions is expected to increase during the forecast period.
Download Sample Report: https://www.alliedmarketresearch.com/request-sample/2313
On the basis of component, the solution segment dominated the overall security information and event management industry in 2020, and is expected to continue this trend throughout the security information and event management market forecast period. The rise in demand for modern SIEM tools to manage IT security is expected to drive the growth of the SIEM solution segment. The next generation SIEM is gaining momentum in the market due to its advanced features which help to tackle various challenges such as large number of events that are needed to be considered outside the syslog files which assist to move on an investigation forward; complexity of SIEM solutions; necessity of an expert personnel to handle the SIEM system; and others. Next gen platforms offer baselining capabilities, automation, and intelligence, which ensure data relevancy and noise filtration. In addition, technologies such as time normalization, metadata analysis, and file integrity monitoring deliver far advanced insights which is expected to drive the growth this segment. However, the services segment is expected to grow the most, and this trend is expected to continue during the forecast period. The growth in need for better security management, supportive government policies and rules to implement SIEM software, increase in adoption of SIEM on BYOD, and advancements in the SIEM technology has urged users to seek better knowledge and guidance to effectively implement the SIEM technology in enterprises to gain maximum output with high quality. These services make it easier to implement and use SIEM solution at the maximum efficiency and capabilities, which is expected to drive the growth of the service segment.
On the basis of industry vertical, the BFSI sector garnered the largest security information and event management market share in 2020, and is expected to continue this trend during the forecast period. Banks and financial institutions operate in a high-threat environment where efficient IT threat management is critical capability along with compliance. SIEM offers threat detection, risk monitoring, and necessary analytics to manage external and internal attacks. SIEM offers continuous risk monitoring, account monitoring, defense against external threats, risk mitigation, and risk routing. However, the healthcare sector is expected to witness highest growth in the upcoming years.
The global security information and event management market size was valued at $3.92 billion in 2020, and is projected to reach $18.12 billion by 2030, growing at a CAGR of 16.4% from 2021 to 2030. The COVID-19 outbreak has a positive impact on the growth of the security information and event managements market due to security and safety reasons. However, the outbreak of COVID-19 has affected communities globally, while governments and other sectors are trying their best to respond faster to the challenges posed by this pandemic. Furthermore, governments and businesses are increasingly asking employees to work from home or are shifting work to employees in less affected areas to maintain business continuity during the pandemic. However, the situation has accelerated the adoption of advanced technologies such as artificial intelligence (AI), machine learning (ML), automation, and IOT to control costs while improving the customer experience, which is expected to provide lucrative opportunities for security information and event managements market. Further, industries such as public sector, banking & financial sector, government sector, and healthcare sector have shown increased adoption of security information and event managements and are expected to continue using them owing to the rising focus on digitization, growing technological awareness, and need for better security systems. Increasing government initiatives to deploy advanced security solutions for better safety and convenience is anticipated to create significant growth opportunities for major players.
Inquiry Before Buying: https://www.alliedmarketresearch.com/purchase-enquiry/2313
Key Findings Of The Study
On the basis of component, the solution segment dominated the security information and event managements market in 2020. However, the services segment is expected to exhibit significant growth during the forecast period.
On the basis of enterprise size, the large enterprise segment dominated the security information and event managements market in 2020. However, the SMEs segment is expected to exhibit significant growth during the forecast period.
On the basis of deployment model, the on-premise segment dominated the security information and event managements market in 2020. However, the cloud segment is expected to exhibit significant growth during the forecast period.
On the basis of industry vertical, the BFSI sector accounted for the highest revenue of market in 2020; however, the healthcare sector is expected to witness the highest growth rate during the forecast period.
On the basis of region, the security information and event managements market was dominated by North America in 2020. However, Asia-Pacific is expected to witness significant growth in the coming years.
This report gives an in-depth profile of some key market players in the security information and event managements market, which includes Dell EMC, Hewlett Packard Enterprise Development LP, IBM Corporation, LogRhythm, Inc., McAfee LLC., SolarWinds, Inc., Splunk, Inc., Symantec Corporation, Trend Micro, Inc., and Trustwave Holdings Inc. This study includes market trends, security information and event management market analysis, and future estimations to determine the imminent investment pockets.
About Us: Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Portland, Oregon. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of “Market Research Reports Insights” and “Business Intelligence Solutions.” AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
#Security Information and Event Management Market#Security Information and Event Management Industry#Security Information and Event Management
0 notes
Text
Top Healthcare App Trends 2023 Unveiled - Healthcare apps have become indispensable tools for both patients and healthcare providers. It’s crucial to uncover the Top Healthcare App Trends 2023 that will dominate the industry in 2023. Read this blog about the future of AI Powered Healthcare App 2023.
#Healthcare App#Healthcare App Development Company#Healthcare App Development Company India#mobile app development company india#mobile app development service india#ai app development
0 notes
Photo

India's most advanced Fetal Heart Monitor. Fetosense : A smart-phone based NST/CTG machine. Wireless | Remote Monitoring | Central Monitoring | Portable | A4 Printing
#Central Monitoring#Remote Monitoring Machine#Remote Monitoring Machine Manufacturer#Remote Monitoring Machine Manufacturer in Pune#Remote Monitoring Machine Manufacturer in Mumbai#remote monitoring#remote monitorin#Wireless Fetal Monitor Device Pune#Wireless Fetal Monitor Device in India#Wireless Fetal Monitor Device#Wireless Fetal Monitor Device in Pune#Wireless Fetal Monitor Device in mumbai#smart-phone based NST/CTG machine#NST/CTG machine#Smartphone based NST/CTG Machine#portable NST/CTG machine#NST/CTG Machine Manufacturer and Supplier in Surat#Fetosense is a smartphone based NST/CTG machine#CareMother Fetosense NST / CTG Machine ( Fetal Monitor ) India#CareMother Fetosense NST/CTG Machine (Fetal Monitor) in India#CareMother Fetosense#Fetosense#India's most advanced Fetal Heart Monitor#advanced Fetal Heart Monitor#fetal heart monitor#fetal heart monitoring#India’s most advanced Fetal Heart Monitor#CTG Machine in India#CTG machine manufacturer#CTG machine manufacturer in pune
0 notes
Link
#employee monitoring#employee monitorin software#employee monitorin solution#remote employee monitoring software
0 notes
Text
Case study


'S4 Door Sensor'
S4 Door Sensor is a door&window sensor with Bluetooth® LE 5.0 technology and a magnetic sensor inside. Users can realize remote door monitoring to ensure asset or stuff security; also, alerts received by admins if disassembled by others, which is usually used in private houses or museums for thief prevention.
0 notes
Text
0 notes
Text
Downhole Cables Industry- 2022 Future Demand, Prominent Players & Forecast To 2030
Downhole cables are used extensively in the oil & gas industry as their unique construction of downhole cables allows them to be used in harsh environments. These cables are used mainly for data transmission. Generally, these cables find applications in oil wells, pipelines, and underwater areas where they are used to drive centrifugal pumps.
The increasing exploration & production of oil and gas and technical developments in drilling activities are expected to drive the market for downhole cables during the forecast period. According to the BP Statistical Review of World Energy 2019, the global oil production grew from 92,502 thousand barrel per day (TBPD) in 2017 to 94,718 TBPD in 2018; the global natural gas production grew from 3,677.7 billion cubic meter (BCM) in 2017 to 3,867.9 BCM in 2018. The growth in production of oil and gas can be attributed to the improving global economic conditions. There has been a dependence on natural gas for electricity generation by the electricity generation companies worldwide due to its higher output and lower emissions than coal and diesel-powered plants. Also, as per the same report, the use of natural gas for electricity generation grew from 5,952.8 Terawatt-hour (TWh) in 2017 to 6,182.8 TWh in 2018. The production is expected to grow during the forecast period. In line with the increase in production of natural gas, the increase in demand for oil and gas has led to an increase in E&P of oil and gas, globally. Many oil & gas companies such as Schlumberger Limited (US) and Halliburton (US) are focusing on E&P of oil and gas across the world. For instance, in October 2017, Schlumberger along with Torxen Energy (Canada) signed an agreement with Cenovus Energy Inc. (Canada) to purchase Palliser Block in Canada for carrying out E&P of oil and gas in Canada. Moreover, in August 2019, Halliburton (US) signed a contract with Woodside (Australia) for drilling and completion services of offshore SNE Field, located in Senegal, Africa for E&P of oil and gas. Such developments are expected to increase in the demand for downhole cables for data monitoring and powering downhole equipment in drilling activities.
Get a FREE Sample@ https://www.marketresearchfuture.com/sample_request/8023
Moreover, drilling activities in the oil & gas industry are used in various applications, including oil and gas extraction, well monitoring, and reservoir analysis. Technological advancements in drilling activities provide several benefits such as less drilling cost and growing extraction of oil and gas. Various technological advancements including the integration of Internet of Things (IoT), data analysis tools, data collection equipment, and real-time well data are employed in the processing of oil and gas by the oil & gas companies. The data acquired from the specific oil and gas drilling activities can be accessed remotely in real time due to the advancements in communication technology. Furthermore, the hardware used in the oil wells have also been developed substantially, leading to a longer life and greater versatility of the equipment. For instance, in May 2017, Schlumberger Limited (US) launched SpectraSphere, a fluid mapping drilling service, which enables real-time fluid mapping by delivering critical fluid properties, such as fluid typing, fluid composition, fluid fractions and gas/oil ratio while drilling, in order to reduce operational costs and the risks associated during fluid analysis. Such factors are expected to drive the growth of the global downhole cables market during the forecast period.
The global market for downhole cables is segmented based on type, installation, application, and region. By type, the global market is segmented as tubing encapsulated cable, fiber optic cable, electrical submersible pump cable, and others. By installation, the global market is segmented as onshore and offshore. By application, the global market is segmented oil & gas production, data collection, well monitoring, powering downhole equipment, instrumentation & control, and pressure sensing.
Market Research Analysis
In terms of region, the market is segmented as Europe, Asia-Pacific, North America, the Middle East & Africa, and South America. North America dominates the global downhole cables market. The growth in increasing per capita energy consumption and exploration and production (E&P) of oil and gas are expected to drive the downhole cables market in the region.
According to the BP Statistical Review of World Energy Report, 2019, the primary per capita energy consumption in North America increased by 1.9% from 235.3 Gigajoules per capita (GJ/Capita) in 2017 to 239.8 GJ/Capita in 2018 of the regions. In addition to this, according to the data of Baker Hughes International Rig Count, 2019, the rig count in North America increased to 1,223 rig counts in 2018 from 1,082 in 2017. The increase in extraction & production of oil and gas surges the demand of downhole cables as downhole cables are used for the extraction of oil and gas in various applications such as reservoir monitoring, powering downhole equipment, and oil and gas production. According to the Annual Energy Outlook 2019, the US is expected to become a net energy exporter by the year 2020 owing to the rise in the production of oil and gas in the country. Moreover, as per the report, crude oil production is expected to reach 14.0 million, barrels per day (b/d) by the year 2040. As per a report published by the Canadian Association of Petroleum Producers in June 2019, the crude oil production in the country is expected to increase by 1.44% from 1.27 million bpd to 5.86 million bpd by the end of 2035. Moreover, in October 2018, Royal Dutch Shell Plc invested USD 25–30 billion for the extraction of liquefied natural gas in western Canada. Such factors are expected to increase the demand for downhole cables between 2019 and 2025.
Scope of the Report
This study provides an overview of the global downhole cables market, tracking four market segments across five geographic regions. The report studies key players, providing a four-year annual trend analysis that highlights market size, and share for North America, Europe, Asia-Pacific, Middle East, and South America. The report also provides a forecast, focusing on the market opportunities for the next five years for each region. The scope of the study segments the global downhole cables market by type, installation, application, and region.
By Type
Tubing Encapsulated Cable
Fiber Optic Cable
Electrical Submersible Pump Cable
Others
By Installation
Onshore
Offshore
By Application
Oil & Gas Production
Well Monitoring
Instrumentation & Control
Pressure Sensing
Data Collection
Powering Downhole Equipment
Downhole Pressure Gauge
Downhole Temperature Gauge
Access Report Details @ https://www.marketresearchfuture.com/reports/downhole-cables-market-8023
By Regions
North America
Asia-Pacific
Europe
Middle East & Africa
South America
Key Players
The Key Industry Participants of the Global Market for Downhole Cables include Nexans (France), Eland Cables (UK), W. L. Gore & Associates, Inc. (US), NKT A/S (Denmark), Belden Inc. (US), Schlumberger Limited (US), WireCo WorldGroup Inc (US), Halliburton (US), GEO Pressure Systems Inc (Canada) Fujikura Ltd (Japan), Galaxy Wire & Cable, Inc. (US), Marmon Holdings, Inc (US), TE Connectivity (Switzerland), ABB (Switzerland), Prysmian Group (Italy).
0 notes