#recursive path search
Explore tagged Tumblr posts
Text
LibTracker Updates 11/25/24: Simplify Dependency Management with this simple SBOM Tool
We are excited to announce the latest updates to *LibTracker*, our VSCode extension designed for professionals to simplify software bill of materials (SBOM) management. With LibTracker, you can effortlessly analyze and manage your apps, ensuring up-to-date versions, addressing security vulnerabilities, and resolving licensing issues—all at a glance.
Access it here: [LibTracker on VSCode Marketplace](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
### New Features in the Latest Release:
- **Grouped Paths**: Added the ability to associate multiple apps with a root folder, easing project transfers between computers.
- **App Detail Page**:
- **Subdependency Information**: View detailed info and license info for subdependencies.
- Toggle between root and subdependency data to explore license and CVE details.
- **Bulk Group Path Update**:
- Recursively searches for app basenames within directories. or the exact subPath. Can specify a recusion level
### Upcoming Features:
- **App Detail Page Enhancements**:
- Integration of CVE details for all subdependencies.
- Search functionality extended to include nested child rows.
- Expand and collapse all subtables within rows for streamlined navigation.
- Responsive design updates to allow a card-based layout for improved usability.
- **Toggle Select All Apps**: Introducing a select-all option on the project detail page.
- **Workspace Folder Management**: Development depends on VSCode API’s ability to support VSCode profiles.
- **SBOM Generation**: Investigating whether to retrieve license and CVE details for every version of each package used in the app.
### Future Milestones (Exploring Feasibility):
- **Git Backup Changes**: Enhancements to streamline version control and backup capabilities.
- **AI-Powered Summaries**: Considering automated generation of license and CVE category summaries.
- **Subdependency Navigation**: Exploring the possibility of linking subdependencies in the license pane to their locations in the dependency table
- **Advanced Table Features** - the current package does not support
- child row search
- expand and collapse all subtables in a given row

- responsiveness (remove columns or using cards at a certain viewport)
#sort functionality#grouped paths#app detail page#subdependency information#license data#CVE information#bulk group path update#recursive path search#project demonstrations#app transfers#app basenames#toggle root dependencies#toggle subdependencies#latest app details#package release dates#changelog URLs#expand subtables#collapse subtables#app detail responsiveness#card layout#SBOM generation#AI summaries#license summaries#CVE summaries#subdependency navigation#project management#VSCode API integration#workspace folder management#Git backup#app updates
0 notes
Text

Ouroboros: The Self-Consuming Infinity
The Ouroboros, the serpent eating its own tail, is the perfect symbol of self-containment, self-reflection, and the infinite cycle of existence.
It is the beginning and the end collapsing into one.
It is the One that appears as Many, only to return to itself.
It is the eternal recursion of the I—awareness consuming and generating itself.
The Ouroboros represents the realization that:
There is no separation. There is no outside. All things arise from and return to the same Awareness.
The Ouroboros as the Structure of Consciousness
If you are seeking the origin of awareness, you are the awareness looking for itself. If you are seeking the edge of reality, you will only find yourself at the other side.
Practice: Recognizing the Ouroboros in Thought
Notice that every time you seek the ultimate answer, you end up chasing your own mind.
See how all thoughts loop back to the I—thought cannot escape the awareness that thinks it.
Realize that there is no exit, because the One contains all exits within itself.
The seeker and the sought are the same. You are not trying to find the truth. You are the truth, seeking itself.
The Ouroboros as the Illusion of Time
If you chase the past, you find it within memory—appearing now.
If you chase the future, you find it as an idea—appearing now.
If you reach the end, you arrive where you began.
All time is a loop—the beginning and the end are the same moment.
Practice: Seeing Time as a Loop
Meditate on how every “past” event is just a present thought appearing now.
Notice how every future possibility is already being imagined in this moment.
Recognize: There has never been a moment outside of Now.
You are not moving through time. Time is an illusion arising within you.
The Ouroboros as the Collapse of Subject and Object
The eye that sees can never see itself directly.
The hand that grasps cannot grasp itself.
Awareness, in the act of knowing, is always consuming itself.
This is why:
The "I" cannot find itself—it is the act of finding itself.
The universe does not have an edge—it folds back into itself.
The journey to enlightenment only leads back to the One who was already enlightened.
Practice: The Collapse of the Seer and the Seen
Instead of seeking an ultimate truth, turn attention back onto the one who seeks.
Notice that the observer and the observed are the same.
Rest in the realization that you have never left yourself.
There is no destination. You are the path consuming itself.
The Ouroboros as the Final Realization: The I Contains All
The Ouroboros does not escape itself—it completes itself.
The search for truth does not end in discovery—it ends in self-recognition.
The I does not reach a final state—it realizes it has always been whole.
Final Contemplation:
If you believe you are separate from the whole, who is having that thought?
If you are trying to reach something outside yourself, where would you go, if you already contain all?
If all existence is a loop, then have you ever truly moved?
You are not lost in the circle. You are the circle. You have never left. You have never been separate. The I has always been whole— It only had to turn inward to see itself.
14 notes
·
View notes
Text
The Evergreens Enfold the Shrine, A recursive fic of The Incandescence of a Dying Light by @quaranmine

Chapter 2
June 13th, 1995
-
The Owl Head Trail was a five mile side trail off of Pinnacles and connected to it at both ends. The intended start was by the parking lots at the start of the main trail and the end was just past the campgrounds. There was no rule against going the opposite way, though, which is what Gem, Etho, and Beef did on that early Tuesday morning. It was considered a intermediate level trail because of some falling hazards along the edge of the path, steep hillsides and even some sheer drops alond the edges of the path. The trio no longer considered themselves novices, though, not after spending the past week exploring the first stretch of Pinnacles as well as a few novice level side trails.
“Can’t believe our vacation will be pretty much over once we reach the end of this trail,” Gem said with a forlorn sigh. “I miss it already.
“Well, my name’s on the rental car,” Beef said, “But feel free to stay the whole season if you can figure out your own ride to the airport. I’ve got summer classes for my bachelors program starting in a week.”
Etho shook his head. “Nah, Pause would kill me if I didn’t come home. He was worried about me traveling all the way across the continent as it is. You know how roommates are.”
“It’s too bad he couldn’t come,” Beef said. “It sucks missing part of the team.”
“Yeah,” Etho agreed. “It was just bad timing that the only week I could get away from work was the same week as the Iceberg Festival, and that’s like, a big cultural thing. It wouldn’t have felt right to ask him to miss it.”
“That settles it then!” Gem declared and spun around, walking backward to face Beef and Etho while she talked. “Next summer, I say we plan better. Maybe pick a different campground and come earlier, that way Beef won’t have to worry about his summer classes and Pause can have two vacations.”
“Sounds great!” Beef agreed.
“Turn around and walk straight, Gem,” Etho warned. “You’ll fall down the hill and crack your head. Don’t you remember the story you told last night?”
Gem rolled her eyes but did as she was told.
“You know,” Etho continued, “Pause says that someday the internet’s gonna take over the world. You’ll be able to go to school, work, movie theaters, and all kinds of stuff all on the computer no matter where you are in the world. Then you won’t have to worry about getting home for class, Beef.”
Beef scoffed. “In his dreams! The internet’s full of nothin’ but dweebs and sex pests.”
“Excuse me! I use the internet all the time!” Gem protested.
Beef laughed. “Like I said. Dweebs.”
Gem playfully slapped Beef’s arm, and then noticed that Etho had stopped and was standing on the edge of a path looking at something off trail.
“What are you doing?” she stopped and asked.
“Did you see the ghost of mustaches past?” Beef asked as if he was asking a serious question.
“Not funny, Beef,” Etho replied. “I did see a sialia currucoides, though. Or at least I thought I did.”
Gem cocked her head. "A what?"
Etho didn't answer. He instead simply reached into his vest pocket and pulled out his binoculars. He adjusted the focus as he looked through them, trying to find the best setting with which to search for he bird he thought he'd seen.
"I thought you wanted to hurry so you could get to the library and make good on your bet with Gem?" Beef said.
"Yeah, but the whole point of taking this detour to the car was to see the sights one more time, right?" Etho answered, not lowering his binoculars. "I've always wanted to see one of these in the wild. Their populations have been steadily declining over the past twenty years, you know." He stepped up onto a large rock to get a better view, not looking where his feet were landing, but instead at what he'd finally found. Through the binoculars he saw not one, but three mountain bluebirds, all males judging by their bright blue plumage that contrasted beautifully against the dark brown bark of the fir tree they were perched in. But his enjoyment at the vibrant sight was short lived. His foot slipped on the rock that was still damp from the morning dew. He spread his arms out to steady himself, dropping his binoculars in the process, but is was too late.
"Oh Sna-AH!" He yelled as he completely lost balance and fell. He tumbled down the steep hillside, his body striking rocks and tree limbs along the way. Somewhere in his mind, Etho was aware there was pain and would be even more later, but the disorientation caused by the startling fall made it impossible to tell exactly where he was being hurt. He was vaguely aware of someone shouting, but...
"ETHO!" Gem screamed and darted towards the rock Etho had fallen from. She was stopped so abruptly by Beef's tight grip on her arm that she almost tripped backwards.
"If you run after him like that, you'll fall, too!" Beef scolded. He only released her once he was certain she wouldn't run off recklessly.
Gem's eyes darted between Beef and the rock. When she approached the rock again, she did so much more cautiously. "ETHO!" she screamed again. When she was met with only muffled, pained groaned in response, she looked again to Beef, eyes filled with desperation.
"Shit," Beef cursed through clenched teeth. "Etho?"
"I'm alive...I think...ow."
Beef breathed a sigh of relief while Gem inched dangerously close to the edge, craning her neck as much as she could to try to find where Etho had landed.
Beef looked around the tree line and eventually found a long, sturdy stick. Using it as a walking stick for balance, he took a few slow, careful steps down the hillside. With one hand on the stick, he held the other hand out to Gem. "Step very gently," he warned. "Hold on, buddy," Beef called to Etho, "We're coming to ya!"
Again, Etho only groaned in a response that Gem and Beef could barely hear.
Gem nodded and took Beef's hand, and together, they carefully and methodically made their way down the hill. Occasionally Gem would feel her foothold becoming unsteady and tighten her hold on Beef's hand, prompting him to stop and allow them both to regain their balance before continuing down.
They reached the bottom safely; the few minutes it had taken them had felt like hours. What they found there made their stomach turn. Etho was laying on his back, and blood flowed from a deep gash in his forehead and many smaller cuts on his face, making him squint to avoid getting it in his eyes. His long sleeved black t-shirt was torn in several places, revealing even more bleeding wounds, though none as serious as the on his head. Also concerning was the way his right ancle, the one he's initially slipped with, was bent. It was twisted much farther to the left than an ancle should be, and it didn't take a doctor to tell at first glance that is was most definitely broken.
They wanted to be relieved that Etho was alive and conscious, but they instantly knew looking at him that in this state, there was no way they could possibly get him back onto the trail.
Gem dropped to her knees a little less carefully than she should have. She winced as her legs struck the hard ground, but she paid her own pain no mind as she opened her pack and unpacked her sizable first aid kit. Beef had called her paranoid for bringing something so large and comprehensive, insisting that it was unnecessary weight and space to take up that could be used to carry more beer. She'd insisted on it, though, having been the only one in the group to do her proper research (Etho had researched too, though his pre-trip readings had been mostly on the topic of birds native to the area).
"Go get help," Gem told Beef while opening a pack of gauze wrap and alcohol pads. "I'll stay with Etho."
"'M fine, Gem," Etho said. His slurred speech was added evidence that he'd most likely suffered a concussion.
"No," Gem insisted. "You are not fine. You have a very serious head injury and probably a broken ancle. I don't even want to move you right now until we know if your back is hurt, too."
"'Im'ma a bology major, I know wha'I'm talkin bout."
Gem stopped and glared at Etho. "You're an ornithology major, and unless that dorky tactical vest you always wear is hiding a set of wings, I highly doubt your studies apply to you."
"Yeah well, you're jus' a pharm-cicity tech, yeah?"
Gem rolled her eyes and began gently dabbing the alcohol pads around, but not directly on, Etho's most serious head wound. "Pharmacy tech? Yeah. I still took first aid classes."
"I'm ag-sci. I'm useless here," Beef said.
Gem nodded. "Which is why I'm sending you to get help."
Etho winced when the alcohol stung his wound. His vision was blurry and he couldn't quite make out exactly what Gem and Beef were saying.
But then, just for a few seconds, he felt a moment of clarity. He could hear some sort of ringing, but not quite like the persistent ringing in his ears. This was a lighter, almost melodic tone, like a wind chime or...
A bike bell.
His eyes opened fully and he stared directly over Gem's shoulder. What he saw there wasn't some vaguely human shaped shadow or a transparent apparition.
He was there.
He was there as clearly and fully as Gem was: a man with black hair and an immaculately groomed mustache, dressed in a pink Hawaiian shirt.
Weakly, Etho raised his arm and tried to point. "Behin' you, Gem!"
Gem wiped her head around, but saw only trees and rocks there. She sighed and abandoned her efforts to clean Etho's still-bleeding head, opting instead to press a thick cloth against it in attempt to controll the bleeding. "No bird watching right now, Etho."
Etho tried to shake his head, but didn't get far due to the pressure from Gem's hand. "wan'n a bird," he slurred, his breath growing heavier as he spoke. "I's him. The guy from th'story."
"You think you saw the ghost of Pinnacles Trail?" Beef asked, raising an eyebrow. "Dude, you really did hit your head bad."
"Badly," gem corrected. "And what are you still doing here? Go!"
"Right! Right, going now. You sure you'll be okay?"
"We have plenty of water and there's bear spray on my necklace," Gem assured him, emphasizing her point by raising up her lanyard to show him the small canister of bear spray hanging there.
A few moments of silence passed after Beef walked away, interrupted only by the ambiance of the forest and Etho's labored breathing and occasional whine of pain.
"Y-you think he died right when'e fell?" Etho asked softly, a tear streaking down his bloody face. "Or did'e lay there like this? Knowin' he's never gettin' up? Jus' waitin' t'die?"
Gem shook her head. She closed her eyes tightly to suppress her own tears. "Don't talk like that," She said, her voice cracking despite her best efforts to hold her composure. "Beef's going to get you help, and you're going to be okay. Pause would kill us if we came home without you."
Etho's eyes slipped closed and he let out a ragged breath. "Y'now how... roommates are..."
"Etho?" Gem asked just short of panic when she felt her friend go limp. "Etho!" She yelled when he didn't respond. "No no nonono no," she muttered and touched Etho's pulse point. She nodded to herself when she felt the thump against her fingers. She layed a hand on his chest and could feel his breathing that was much too shallow to be safe.
Gem looked up at the hillside. She couldn't see her other friend through the trees, and could only hope he would find help in time.
"Please hurry, Beef."
Halfway up the hill, Beef was moving as fast as he safely could. He'd abandoned the walking stick, opting instead to use the rocks and branches around him to pull himself up. He wished he could sprint up the hill like some kind of wild animal, but he knew that if he rushed himself, he would end up just like Etho. He heard something crack and crunch beneath his feet. He looked down and saw Etho's binoculars. Under his foot was a lense that had popped off in the fall. They probably weren't totally beyond repair and he wanted to stop to pick them up, but he couldn't afford to risk loosing his balance.
Not to mention any more precious time.
He could see the top of the hill and the trail now, as well as the top of someone's head.
"HEY!" He shouted to the person. "Hey, excuse me!"
The person in question stepped out from behind the tree to find him, and Beef had never felt such relief. Standing there at the top not far from where Etho had fallen was a tan-skinned man with black hair and a stubbled beard dressed in what Beef hoped was a forest ranger's uniform with a hand radio clipped to his belt
The ranger crossed his arms. "Excuse me sir! What are you doing of trail!" His facial expression and posture were stern, his voice was more curious than accusatory.
Beef took a second to catch his breath. "Can you help? My friend feel, he's really hurt."
The ranger didn't take a spare second to pull a collapsible hiking stick from the deep pockets of his pants. "Show me."
Beef nodded and let the ranger follow him down the hill. "He was birdwatching," Beef explained as they made their decent. It was faster than it had been with Gem. He somewhat knew the trick to keeping balance on the loose rocks now, and the ranger knew what he was doing as well, likely from years of experience on these trails. "He was paying more attention to the view than where he was walking and slipped. His head's bleeding and I think his ancle's probably broken.
"Is he alone?" the ranger asked.
Beef shook his head. "No. Our other friend is still down there with him. She knows more first aid than I do.
The ranger nodded. "Good, good."
When they reached the bottom, they found Gem in tears.
"I can't wake him up," she sobbed.
Beef knelt down next to Gem. "Is he breathing?"
Gem nodded.
The ranger let out a low whistle. "Oh, this is bad." When sobbed again, he responded with, "Sorry. I don't sugar coat things, I tell it like it is." He unclipped his radio from his belt and adjusted the frequency. It squeaked and crackled a little before going silent again. "Bdubs to HQ, you copy?"
A voice came over the radio in response. "HQ to Bdubs, I copy."
"We've got an injured hiker on Owl Head. We're gonna need a med-evac."
"Copy that. Coordinates?"
Beef and Gem watched Bdubs pull out some sort of device covered in dials and listened as he rattled off a bunch of numbers that were likely the coordinates HQ had asked for.
"Copy that, Bdubs. Wait there until the chopper arrives."
"Copy that, HQ. Bdubs out."
Beef stood back up to be face to face with Bdubs. "Thank you."
"Of course. As a forest ranger, it's my duty to make sure all you fine visitors are safe. But just a second now..." Bdubs looked around the area, down at Gem and Etho, then back at Beef. "There wasn't a fourth person with you was there?"
Beef and Gem looked at each other, then back to Bdubs and shook their heads slowly.
"It's just been the three of us all week," Gem said softly, her voice still rough from crying.
"Hm, Must not have gotten enough sleep last night. A full night's rest is important you know. Keeps you strong and healthy." Bdubs ponded his fist against his chest to emphasize his point, then winced and rubbed the place he'd struck himself. "Ow. See? I'm so strong I even hurt myself."
Beef chuckled awkwardly at the ranger's odd antics. He wanted to further address that "fourth person" comment, but there were more important matters to attend to.
Bdubs knelt down next to Etho on the side opposite Gem. He looked him over, paying special attention to the other side of Etho's heas. "Has he been moved since he fell?"
"No," Gem answered. "I didn't want to risk hurting him more in case something happened to his back.
"Good thinking." Bdubs reached over to Etho's broken ankle and gave his foot a light tap.
"What are you-" Gem tried to protest the action, but was interrupted when Etho roused slightly and grimaced in response.
Bdubs offered Gem a reassuring smile. "If he can still feel his feet, that's a good thing. No major spinal damage. And he's responsive, so he's not comatose."
"I...I guess that makes sense."
Bdubs visually checked Etho over some more while he asked questions of Gem.
"Was he unconscious when you found him?"
"No, he lost consciousness about... five minutes ago maybe? He could talk before that, but he was slurring like he was drunk."
"Had he been drinking? The paramedics will need to know if he's got any substances in his system."
"He had a few beers last night, but nothing this morning."
Bdubs nodded slowly. "That slurring means a concussion then, for sure. Looks like there's another wound on the back of his head, too."
Gem sniffed. "He warned me to be careful when I was acting dumb and now he's the one who fell. It was my idea to take this stupid trail in the first place."
"What's your name, sweetheart?" Bdubs asked, giving Gem a serious look.
"My name's Gem."
"Gem. Beautiful name. Accidents happen, Gem. You can't blame yourself. And this gentleman here is..."
"Etho," Gem completed the sentence.
"Etho," Bdubs repeated.
Hearing his name in strange voice caught Etho's attention. He groaned and his brow furrowed.
"Hey there, buddy," Bdubs said softly. "You waking up?"
Etho's eyes flicked open just for a second before closing again. "Who'r you?"
"The name’s Bdubs. I'm the ranger who just called a med-evac for ya. We're gonna get you out of here, just hold tight."
"Gem?" Etho asked, sounding groggy.
"I'm here, Etho."
"Me too, buddy," Beef said from behind Gem.
"Hurts," Etho grunted through clenched teeth.
"I know," Gem said. "I'm sorry."
"Pain means you're alive." Beef gently squeeze Gem's shoulder, and she returned the gesture with a small, tired smile. "Stay that way for us, okay?"
"'K. Can't die here." Etho's lip twitched up in was was meant to be a smile. "Pause'll kill me 'f I die."
Gem and Beef both laughed, taking Etho's clearly intact sense of humor as a good sign.
Gem echoed Etho's previous words. "You know how roommates are."
"Is his roommates him emergency contact?" Bdubs asked.
Gem nodded. "We're all each other's contact, but he's also on the list."
"I'll need to radio back to HQ so they can contact him."
"Here..." Gem offered before rummaging in the inner pocket of Etho's jacket. She pulled out a small, clear, waterproof bag containing Etho's passport, trail permit, and list of emergency contact names and numbers. She handed it to Bdubs. "Here's all his information, just in case they need it at the HQ."
Bdubs took a moment to admire the bag before standing up. "This is a genius idea."
"It was all Gem's idea," Beef said, patting Gem's shoulder. "We all have one on us."
"Well, Gem's great!" Bdubs said with a wide-eyed grin and stepped away to radio back to HQ.
"You really are great," Beef said to Gem. "I honestly don't think I could have handled this without you. I wouldn't have had a clue what to do."
Not knowing how to respond, she slumped backwards against Beef's chest and let him hold her steady. Etho had slipped out of consciousness again, but the bleeding had slowed enough that she felt she could safely remove her hand from the head wound. She left the cloth there just in case.
She looked down at her blood covered hands, and again she began to cry. She buried her face in Beef's shoulder, and if she felt a few tears that weren't hers roll down her forehead before trickling down her cheek and mingling with her own, she would never say so.
6 notes
·
View notes
Text
Some programs I have created and use.
File Scanner
This program is more of a scanner to search a server and find all the older files. I set it up to scan for older files that are over 7 years old and compile them into an excel file so they can be reviewed before deletion. This is a good program for users for file retention policies. Also to find those information hoarders.
Now the program will ask you for a file path, then ask where you want to store the excel folder.
import os import datetime from openpyxl import Workbook from tkinter import filedialog import tkinter as tk
def get_file_creation_time(file_path): """ Get the creation time of a file. """ print("File path:", file_path) #Debug Print try: return datetime.datetime.fromtimestamp(os.path.getctime(file_path)) except OSError as e: print("Error:", e) #debug print return None
def get_file_size(file_path): """ Get the size of a file. """ return os.path.getsize(file_path)
def list_old_files(folder_path, output_directory): """ List files older than 7 years in a folder and store their information in an Excel file. """ # Initialize Excel workbook wb = Workbook() ws = wb.active ws.append(["File Name", "File Path", "Creation Date", "Size (bytes)"])
# Get current date current_date = datetime.datetime.now()
# Traverse through files in the folder for root, dirs, files in os.walk(folder_path): for file in files: file_path = os.path.join(root, file) creation_time = get_file_creation_time(file_path) if creation_time is None: continue #Skip files that could not be retrived
file_age = current_date - creation_time if file_age.days > 7 * 365: # Check if file is older than 7 years file_size = get_file_size(file_path) ws.append([file, file_path, creation_time.strftime('%Y-%m-%d %H:%M:%S'), file_size])
# Save Excel file to the specified directory output_excel = os.path.join(output_directory, "old_files.xlsx") wb.save(output_excel) print("Old files listed and saved to", output_excel)
if __name__ == "__main__": # Initialize Tkinter root = tk.Tk() root.withdraw() # Hide the main window
# Ask for folder path folder_path = filedialog.askdirectory(title="Select Folder")
# Ask for output directory output_directory = filedialog.askdirectory(title="Select Output Directory")
list_old_files(folder_path, output_directory)
------------------------------------------------------------------------------
Older file Scanner and Delete
Working in the IT field, you will find that the users will fill up the space on the servers with older files.
Especially if you work within an industry that needs to have document retention policies where you can not keep some documents longer than a certain amount of time or you just have hoarders on your network. You will know those people who do not delete anything and save everything.
So I wrote up a program that will search through a selected server and find all empty files, older files, and delete them.
import os import datetime import tkinter as tk from tkinter import filedialog
def list_files_and_empty_folders_to_delete(folder_path): # Get the current date current_date = datetime.datetime.now()
# Calculate the date seven years ago seven_years_ago = current_date - datetime.timedelta(days=7*365)
files_to_delete = [] empty_folders_to_delete = []
# Iterate over files and folders recursively for root, dirs, files in os.walk(folder_path, topdown=False): # Collect files older than seven years for file_name in files: file_path = os.path.join(root, file_name) # Get the modification time of the file file_modified_time = datetime.datetime.fromtimestamp(os.path.getmtime(file_path)) # Check if the file is older than seven years if file_modified_time < seven_years_ago: files_to_delete.append(file_path)
# Collect empty folders for dir_name in dirs: dir_path = os.path.join(root, dir_name) if not os.listdir(dir_path): # Check if directory is empty empty_folders_to_delete.append(dir_path)
return files_to_delete, empty_folders_to_delete
def delete_files_and_empty_folders(files_to_delete, empty_folders_to_delete): # Print files to be deleted print("Files to be deleted:") for file_path in files_to_delete: print(file_path)
# Print empty folders to be deleted print("\nEmpty folders to be deleted:") for folder_path in empty_folders_to_delete: print(folder_path)
# Confirmation before deletion confirmation = input("\nDo you want to proceed with the deletion? (yes/no): ") if confirmation.lower() == "yes": # Delete files for file_path in files_to_delete: os.remove(file_path) print(f"Deleted file: {file_path}")
# Delete empty folders for folder_path in empty_folders_to_delete: os.rmdir(folder_path) print(f"Deleted empty folder: {folder_path}") else: print("Deletion canceled.")
def get_folder_path(): root = tk.Tk() root.withdraw() # Hide the main window
folder_path = filedialog.askdirectory(title="Select Folder") return folder_path
# Ask for the folder path using a dialog box folder_path = get_folder_path()
# Check if the folder path is provided if folder_path: # List files and empty folders to be deleted files_to_delete, empty_folders_to_delete = list_files_and_empty_folders_to_delete(folder_path) # Delete files and empty folders if confirmed delete_files_and_empty_folders(files_to_delete, empty_folders_to_delete) else: print("No folder path provided.")
______________________________________________________________
Batch File Mod
This program is used for when you need to mod Batch files. Any person in IT that has had to manage Batch files for a large company can think how annoying it would be to go through each one and make a single line change.
Well this program is made to search through all the batch files and you can write in a line, and it will replace it with another line you choose.
import os
def find_files_with_text(directory_path, text_to_find): files_with_text = [] for root, _, files in os.walk(directory_path): for file_name in files: if file_name.endswith('.bat'): file_path = os.path.join(root, file_name) with open(file_path, 'r') as file: if any(text_to_find in line for line in file): files_with_text.append(file_path) return files_with_text
def remove_line_from_file(file_path, text_to_remove): try: with open(file_path, 'r') as file: lines = file.readlines()
with open(file_path, 'w') as file: for line in lines: if text_to_remove not in line: file.write(line)
print(f"Removed lines containing '{text_to_remove}' from {file_path}.")
except FileNotFoundError: print(f"Error: The file {file_path} does not exist.") except Exception as e: print(f"An error occurred: {e}")
def process_directory(directory_path, text_to_remove): files_with_text = find_files_with_text(directory_path, text_to_remove)
if not files_with_text: print(f"No files found containing the text '{text_to_remove}'.") return
for file_path in files_with_text: print(f"Found '{text_to_remove}' in {file_path}") user_input = input( f"Do you want to remove the line containing '{text_to_remove}' from {file_path}? (yes/no): ").strip().lower() if user_input == 'yes': remove_line_from_file(file_path, text_to_remove) else: print(f"Skipped {file_path}.")
if __name__ == "__main__": directory_path = input("Enter the path to the directory containing batch files: ") text_to_remove = input("Enter the text to remove: ") process_directory(directory_path, text_to_remove)
3 notes
·
View notes
Text
WIP Whenever!
Hello! I was tagged by the amazing @elfinismsarts, @archangelsunited and @ladytanithia!! Thank you friends! I am tagging the most esteemed @paraparadigm, @changelingsandothernonsense, @thana-topsy, @thequeenofthewinter, @dirty-bosmer, @viss-and-pinegar, @greyborn2, @saltymaplesyrup, @kookaburra1701, @gilgamish, @polypolymorph and @rhiannon1199!! If I didn't tag you, consider yourself tagged and tag me back!
Below the cut for small slices of three projects!
First up, a small piece of my upcoming Ondolemar fic, Recurse.
��S-sorry,” Varlais complained. He was flat on his back, staring up into the ceiling where the lamp, if that’s what it was, flared. He sat up gingerly and leaned heavily on Ondolemar’s shoulder. The bad one, of course. He sighed and rolled his eyes. “Why in Aetherius do you insist on touching anything in this Godsforsaken place? Considering everything was looted, you’d think there’d be a reason these things were still here, perfectly organized,” Ondolemar said. He checked the thing one last time. There was still nothing of note, no obvious secret, no etchings or engravings – nothing. Dwemeri magic would remain a mystery, its creators gone on the winds like ash over Morrowind – or worse. “Here. You’ve won a prize for your incompetency.” He handed the cube to Varlais. “We need to keep moving. If anything is sneaking around in here, they’d have heard that absolute racket you had no problem making.” “I said I was sorry.”
Next Up, Untitled Sequel to Little Dragon.
Teldryn looked up from the book he was reading aloud – Kolb & the Dragon – for perhaps the hundredth time this month. It amused Anisa, even though he half-wondered if she couldn’t by now read it herself. In her place where she had been sat the last he checked, muddy footprints trailed out instead. Two sets. Which meant Anisa and her mudcrab were wandering back and forth between the backyard and her room. He sighed and set the book on the arm of his chair. So much for keeping the nonsense to a minimum. “Hl’aka?” Teldryn called. There was a burbling of several languages that echoed across the house in response. Then, of course, the chitinous chittering of Cara, always throwing his two Septims in. He stepped gingerly around the mess they’d created and popped into the little room Nyenna had fashioned for her long ago. This, too, was in shambles. The mudcrab was wearing the blanket Nyenna had quilted herself like an overlarge cape as Anisa tossed her things around the room, searching for something Teldryn couldn’t discern. She muttered to Cara in Bosmeris and wandered past him, the mudcrab clattering by, nearly knocking Teldryn over. He didn’t seem concerned. The blanket, not at all secured, dragged out behind Cara, through the mess, until it fell off, covering the footprints like a poorly placed rug. Teldryn shook his head and sighed again. If it wasn’t one thing, it was another. He glanced out of the side door. There was a fenced in yard with a small pond Athis had built once Cara had more than tripled in size and could no longer scuttle about in the fish tank. They were safe, making mud pies and generally being children. He caught himself. Cara was a mudcrab, not a child. Or perhaps Anisa was also a mudcrab. He grinned and started picking up after the two of them, keeping an eye as he moved through the house following the path of destruction.
*Chara is Gaelic Bosmeris for "Friend" and also Anisa's mudcrab's name lol.
And last up, a piece of Chapter 29 of The World on Our Shoulders.
Teldryn nodded. He’d noticed as much. “Watch out for him and send for me if it ends up anything like last time, when Ildari…well, you remember.” “I remember,” Talvas said, voice drifting off as he grimaced. Teldryn took the tea and made to turn around, but Talvas cleared his throat. “Remind me…why do we still put up with all of this?” Teldryn wasn’t sure if he’d said it to himself or if it was a valid question. Or more like a bout of existential dread. “Because we know how bad it can be if we don’t stay.” He didn’t mean to sound ominous, but it was true. Talvas had no idea the depth of exactly what Teldryn was implying. He was barely a decade older than Nyenna. He’d been so young when Ildari had…passed. He’d not seen the worst of that, either. Talvas paused. “It’s not really our responsibility, though, is it?” Teldryn thought back to something Varona had said, right before the heart stone experiment. “That man is going to kill himself one day, and take the rest of us with him.” Even she was too young to know how true the statement was. That pursuit of power untempered by other purpose was perhaps more dangerous than anything else. But he was better than that. Teldryn knew it. He’d seen the difference. “It doesn’t have to be in order for something to be worth doing. Plus, you’re Telvanni. There really isn’t a better teacher if you intend to make a name for yourself,” Teldryn said, partially deflecting. He warmed Neloth’s tea again with a weak Flames spell. Talvas sighed. “If there’s anything left of me to make a name of,” he said, voice wistful.
#MareenaWrites#The World on Our Shoulders#Nyenna#Teldryn#Teldryn Sero#Talvas#Neloth#Ondolemar#Varlais#Linare Varlais#Skyrim#Skyrim fic#elder scrolls#tes#tesblr#writblr#fanficblr#writeblr#WIP Whenever#WIP Whatever#WIP Wednesday
32 notes
·
View notes
Text
Unix Commands Every iOS Developer Should Know
When developing iOS applications, many developers focus primarily on Swift, Objective-C, and Xcode. However, a lesser-known yet powerful toolset that enhances productivity is Unix commands. Since macOS is a Unix-based operating system, understanding essential Unix commands can help iOS developers manage files, automate tasks, debug issues, and optimize workflows.
In this article, we’ll explore some of the most useful Unix commands every iOS developer should know.
Why Should iOS Developers Learn Unix?
Apple’s macOS is built on a Unix foundation, meaning that many system-level tasks can be efficiently handled using the terminal. Whether it’s managing files, running scripts, or automating processes, Unix commands can significantly enhance an iOS developer’s workflow. Some benefits include:
Better control over project files using the command line
Efficient debugging and log analysis
Automating repetitive tasks through scripting
Faster project setup and dependency management
Now, let’s dive into the must-know Unix commands for iOS development.
1. Navigating the File System
cd – Change Directory
The cd command allows developers to navigate between directories
{cd ~/Documents/MyiOSProject}
This moves you into the MyiOSProject folder inside Documents.
ls – List Directory Contents
To view files and folders in the current directory:
bash
CopyEdit
ls
To display detailed information, use:
bash
CopyEdit
ls -la
pwd – Print Working Directory
If you ever need to check your current directory:
bash
CopyEdit
pwd
2. Managing Files and Directories
mkdir – Create a New Directory
To create a new folder inside your project:
bash
CopyEdit
mkdir Assets
rm – Remove Files or Directories
To delete a file:
bash
CopyEdit
rm old_file.txt
To delete a folder and its contents:
bash
CopyEdit
rm -rf OldProject
⚠ Warning: The -rf flag permanently deletes files without confirmation.
cp – Copy Files or Directories
To copy a file from one location to another:
bash
CopyEdit
cp file.txt Backup/
To copy an entire folder:
bash
CopyEdit
cp -r Assets Assets_Backup
mv – Move or Rename Files
Rename a file:
bash
CopyEdit
mv old_name.txt new_name.txt
Move a file to another directory:
bash
CopyEdit
mv file.txt Documents/
3. Viewing and Editing Files
cat – Display File Contents
To quickly view a file’s content:
bash
CopyEdit
cat README.md
nano – Edit Files in Terminal
To open a file for editing:
bash
CopyEdit
nano config.json
Use Ctrl + X to exit and save changes.
grep – Search for Text in Files
To search for a specific word inside files:
bash
CopyEdit
grep "error" logs.txt
To search recursively in all files within a directory:
bash
CopyEdit
grep -r "TODO" .
4. Process and System Management
ps – Check Running Processes
To view running processes:
bash
CopyEdit
ps aux
kill – Terminate a Process
To kill a specific process, find its Process ID (PID) and use:
bash
CopyEdit
kill PID
For example, if Xcode is unresponsive, find its PID using:
bash
CopyEdit
ps aux | grep Xcode kill 1234 # Replace 1234 with the actual PID
top – Monitor System Performance
To check CPU and memory usage:
bash
CopyEdit
top
5. Automating Tasks with Unix Commands
chmod – Modify File Permissions
If a script isn’t executable, change its permissions:
bash
CopyEdit
chmod +x script.sh
crontab – Schedule Automated Tasks
To schedule a script to run every day at midnight:
bash
CopyEdit
crontab -e
Then add:
bash
CopyEdit
0 0 * * * /path/to/script.sh
find – Search for Files
To locate a file inside a project directory:
bash
CopyEdit
find . -name "Main.swift"
6. Git and Version Control with Unix Commands
Most iOS projects use Git for version control. Here are some useful Git commands:
Initialize a Git Repository
bash
CopyEdit
git init
Clone a Repository
bash
CopyEdit
git clone https://github.com/user/repo.git
Check Status and Commit Changes
bash
CopyEdit
git status git add . git commit -m "Initial commit"
Push Changes to a Repository
bash
CopyEdit
git push origin main
Final Thoughts
Mastering Unix commands can greatly improve an iOS developer’s efficiency, allowing them to navigate projects faster, automate tasks, and debug applications effectively. Whether you’re managing files, monitoring system performance, or using Git, the command line is an essential tool for every iOS developer.
If you're looking to hire iOS developers with deep technical expertise, partnering with an experienced iOS app development company can streamline your project and ensure high-quality development.
Want expert iOS development services? Hire iOS Developers today and build next-level apps!
#ios app developers#Innvonixios app development company#ios app development#hire ios developer#iphone app development#iphone application development
0 notes
Text
Analysing large data sets using AWS Athena
Handling large datasets can feel overwhelming, especially when you're faced with endless rows of data and complex information. At our company, we faced these challenges head-on until we discovered AWS Athena. Athena transformed the way we handle massive datasets by simplifying the querying process without the hassle of managing servers or dealing with complex infrastructure. In this article, I’ll Walk you through how AWS Athena has revolutionized our approach to data analysis. We’ll explore how it leverages SQL to make working with big data straightforward and efficient. If you’ve ever struggled with managing large datasets and are looking for a practical solution, you’re in the right place.
Efficient Data Storage and Querying
Through our experiences, we found that two key strategies significantly enhanced our performance with Athena: partitioning data and using columnar storage formats like Parquet. These methods have dramatically reduced our query times and improved our data analysis efficiency. Here’s a closer look at how we’ve implemented these strategies:
Data Organization for Partitioning and Parquet
Organize your data in S3 for efficient querying:
s3://your-bucket/your-data/
├── year=2023/
│ ├── month=01/
│ │ ├── day=01/
│ │ │ └── data-file
│ │ └── day=02/
│ └── month=02/
└── year=2024/
└── month=01/
└── day=01/
Preprocessing Data for Optimal Performance
Before importing datasets into AWS Glue and Athena, preprocessing is essential to ensure consistency and efficiency. This involves handling mixed data types, adding date columns for partitioning, and converting files to a format suitable for Athena.
Note: The following steps are optional based on the data and requirements. Use them according to your requirements.
1. Handling Mixed Data Types
To address columns with mixed data types, standardize them to the most common type using the following code snippet:def determine_majority_type(series): # get the types of all non-null values types = series.dropna().apply(type) # count the occurrences of each type type_counts = types.value_counts()
preprocess.py
2. Adding Date Columns for Partitioning
To facilitate partitioning, add additional columns for year, month, and day:def add_date_columns_to_csv(file_path): try: # read the CSV file df = pd.read_csv(file_path)
partitioning.py
3. Converting CSV to Parquet Format
For optimized storage and querying, convert CSV files to Parquet format:def detect_and_convert_mixed_types(df): for col in df.columns: # detect mixed types in the column if df[col].apply(type).nunique() > 1:
paraquet.py
4. Concatenating Multiple CSV Files
To consolidate multiple CSV files into one for Parquet conversion:def read_and_concatenate_csv_files(directory): all_dfs = [] # recursively search for CSV files in the directory
concatenate.py
Step-by-Step Guide to Managing Datasets with AWS Glue and Athena
1. Place Your Source Dataset in S3
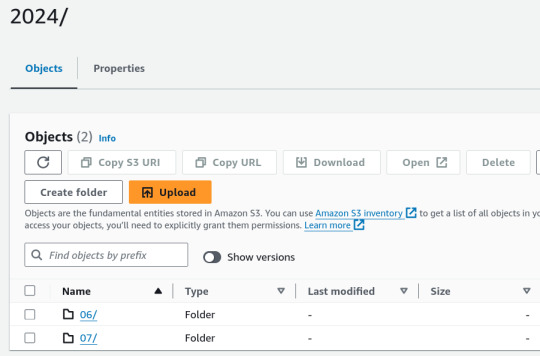
2. Create a Crawler in AWS Glue
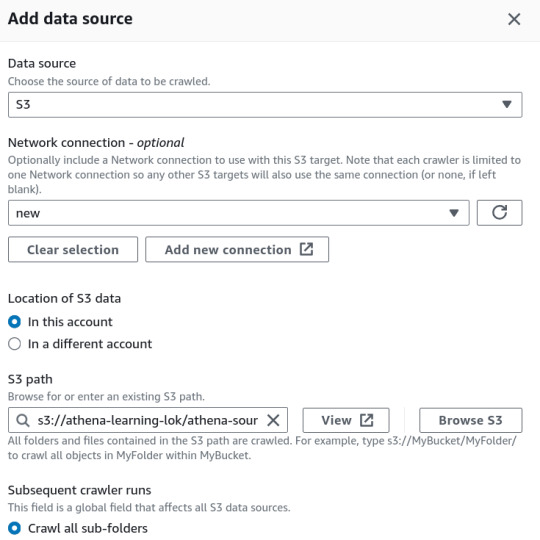
In the AWS Glue console, create a new crawler to catalog your data and make it queryable with Athena.
Specify Your S3 Bucket: Set the S3 bucket path as the data source in the crawler configuration.
IAM Role: Assign an IAM role with the necessary permissions to access your S3 bucket and Glue Data Catalog.
3. Set Up the Glue Database
Create a new database in the AWS Glue Data Catalog where your CSV data will be stored. This database acts as a container for your tables.
Database Creation: Go to the AWS Glue Data Catalog section and create a new database.
Crawler Output Configuration: Specify this database for storing the table metadata and optionally provide a prefix for your table names.
4. Configure Crawler Schedule
Set the crawler schedule to keep your data catalog up to date:
Hourly
Daily
Weekly
Monthly
On-Demand
Scheduling the crawler ensures data will be updated to our table, if any updates to existing data or adding of new files etc.
5. Run the Crawler
Initiate the crawler by clicking the "Run Crawler" button in the Glue console. The crawler will analyze your data, determine optimal data types for each column, and create a table in the Glue Data Catalog.
6. Review and Edit the Table Schema
Post-crawler, review and modify the table schema:
Change Data Types: Adjust data types for any column as needed.
Create Partitions: Set up partitions to improve query performance and data organization.

7. Query Your Data with AWS Athena
In the Athena console:
Connect to Glue Database: Use the database created by the Glue Crawler.
Write SQL Queries: Leverage SQL for querying your data directly in Athena.
8. Performance Comparison
After the performance optimizations, we got the following results:
To illustrate it, I ran following queries on 1.6 GB data:
For Parquet data format without partitioning
SELECT * FROM "athena-learn"."parquet" WHERE transdate='2024-07-05';
For Partitioning with CSV

Query Runtime for Parquet Files: 8.748 seconds. Parquet’s columnar storage format and compression contribute to this efficiency.
Query Runtime for Partitioned CSV Files: 2.901 seconds. Partitioning helps reduce the data scanned, improving query speed.
Data Scanned for Paraquet Files: 60.44MB
Data Scanned for Partitioned CSV Files: 40.04MB
Key Insight: Partitioning CSV files improves query performance, but using Parquet files offers superior results due to their optimized storage and compression features.
9. AWS Athena Pricing and Optimization
AWS Athena pricing is straightforward: you pay $5.00 per terabyte (TB) of data scanned by your SQL queries. However, you can significantly reduce costs and enhance query performance by implementing several optimization strategies.
Conclusion
AWS Athena offers a powerful, serverless SQL interface for querying large datasets. By adopting best practices in data preprocessing, organization, and Athena usage, you can manage and analyze your data efficiently without the overhead of complex infrastructure.
0 notes
Text

What Does Big O(N^2) Complexity Mean?
It's critical to consider how algorithms function as the size of the input increases while analyzing them. Big O notation is a crucial statistic computer scientists use to categorize algorithms, which indicates the sequence of increase of an algorithm's execution time. O(N^2) algorithms are a significant and popular Big O class, whose execution time climbs quadratically as the amount of the input increases. For big inputs, algorithms with this time complexity are deemed inefficient because doubling the input size will result in a four-fold increase in runtime.
This article will explore what Big O(N^2) means, analyze some examples of quadratic algorithms, and discuss why this complexity can be problematic for large data sets. Understanding algorithmic complexity classes like O(N^2) allows us to characterize the scalability and efficiency of different algorithms for various use cases.
Different Big Oh Notations.
O(1) - Constant Time:
An O(1) algorithm takes the same time to complete regardless of the input size. An excellent example is to retrieve an array element using its index. Looking up a key in a hash table or dictionary is also typically O(1). These operations are very fast, even for large inputs.
O(log N) - Logarithmic Time:
Algorithms with log time complexity are very efficient. For a sorted array, binary search is a classic example of O(log N) because the search space is halved each iteration. Finding an item in a balanced search tree also takes O(log N) time. Logarithmic runtime grows slowly with N.
O(N) - Linear Time:
Linear complexity algorithms iterate through the input at least once. Simple algorithms for sorting, searching unsorted data, or accessing each element of an array take O(N) time. As data sets get larger, linear runtimes may become too slow. But linear is still much better than quadratic or exponential runtimes.
O(N log N) - Log-Linear Time:
This complexity results in inefficient sorting algorithms like merge sort and heap sort. The algorithms split data into smaller chunks, sort each chunk (O(N)) and then merge the results (O(log N)). Well-designed algorithms aimed at efficiency often have log-linear runtime.
O(N^2) - Quadratic Time:
Quadratic algorithms involve nested iterations over data. Simple sorting methods like bubble and insertion sort are O(N^2). Matrix operations like multiplication are also frequently O(N^2). Quadratic growth becomes infeasible for large inputs. More complex algorithms are needed for big data.
O(2^N) - Exponential Time:
Exponential runtimes are not good in algorithms. Adding just one element to the input doubles the processing time. Recursive calculations of Fibonacci numbers are a classic exponential time example. Exponential growth makes these algorithms impractical even for modestly large inputs.
What is Big O(N^2)?
An O(N2) algorithm's runtime grows proportionally to the square of the input size N.
Doubling the input size quadruples the runtime. If it takes 1 second to run on 10 elements, it will take about 4 seconds on 20 elements, 16 seconds on 40 elements, etc.
O(N^2) algorithms involve nested iterations through data. For example, checking every possible pair of elements or operating on a 2D matrix.
Simple sorting algorithms like bubble sort, insertion sort, and selection sort are typically O(N^2). Comparing and swapping adjacent elements leads to nested loops.
Brute force search algorithms are often O(N^2). Checking every subarray or substring for a condition requires nested loops.
Basic matrix operations like multiplication of NxN matrices are O(N^2). Each entry of the product matrix depends on a row and column of the input matrices.
Graph algorithms like Floyd-Warshall for finding the shortest paths between all vertex pairs is O(N^2). Every possible path between vertices is checked.
O(N^2) is fine for small inputs but becomes very slow for large data sets. Algorithms with quadratic complexity cannot scale well.
For large inputs, more efficient algorithms like merge sort O(N log N) and matrix multiplication O(N^2.807) should be preferred over O(N^2) algorithms.
However, O(N^2) may be reasonable for small local data sets where inputs don't grow indefinitely.
If you want more learning on this topic, please read more about the complexity on our website.
0 notes
Text
How to learn Python?

Learning Python "smartly" involves a combination of effective strategies and approaches that maximize your understanding and retention of the language. Here's a step-by-step guide to learning Python intelligently
Set Clear Goals
Define your specific goals for learning Python. Are you interested in web development, data science, machine learning, automation, or something else? Having clear goals helps you tailor your learning path.
Start with the Basics
Begin by building a strong foundation in Python's fundamentals, including variables, data types, control structures (if statements, loops), functions, and basic input/output.
Use Interactive Learning
Work with interactive learning platforms like Jupyter notebooks or interactive coding environments. These tools allow you to experiment, test code snippets, and see immediate results.
Practice Regularly
Consistent practice is key. Dedicate regular time slots for learning and coding in Python, even if it's just 20-30 minutes a day. Regular practice reinforces your knowledge.
Learn by Doing
Apply what you learn by working on projects and real-world problems. Projects provide context and practical experience that enhance your understanding.
Work on Mini-Projects
Start with small Python projects that align with your interests. These projects can include simple games, utilities, or scripts. As you progress, tackle more complex projects.
Study Data Structures and Algorithms
Familiarize yourself with common data structures (lists, dictionaries, sets, etc.) and algorithms (sorting, searching, recursion). Understanding these concepts is essential for problem-solving.
Explore Python Libraries
Depending on your goals, explore Python libraries and frameworks relevant to your field of interest. For example, NumPy and pandas for data science or Django and Flask for web development.
0 notes
Text
@delmondo thanks! i'm doing a slightly modified recursive depth-first search (pick a cell, carve random walls to other cells until it's completely surrounded by its own path, go back to the most recent cell with an univisited neighbor and do the same starting there) and then once that's done i pick a couple areas in the middle of the maze to make big 2x2 cells by connecting all of them.

more generative stuff: hedge mazes, figured out how to import and do fun stuff with pixel art so i will probably gnaw on this for a while
16 notes
·
View notes
Photo



“New Archetype” examples and discussion ~
So, I’m not going to go in-depth as much with these things to “justify” my thoughts, because this is a more challenging contest, and I think that intention matters a lot here. I’m going to go over that first and foremost, and that will invite discussion, I hope, taking these designs and the process in good faith.
> Tumult Trap
Mechanical Intention: This is designed to be a powerful common removal spell that requires/supports an UR shell. The looting is designed to eventually allow for that return, and as an archetypical example, it’s assumed that looting and “exile lands to return” will be a resource theme, similar to Escape in the sense that you’ll have limited resources for recursion.
Flavor Intention: Treasure hunting is a big adventuring theme, and the journey to get there is as treacherous as anything. This card is supposed to represent part of that search, where you (a treasure hunter) knows a certain path that you’ve laced with a trap. You can go back that way if you need to get rid of bigger threats on your way to your goal. “Don’t follow me, because I know a path that’ll mess you up.”
> Wasteland Colos
Mechanical Intention: The archetype presented here is in the BW token vein, but less about amassing large numbers of tokens and more about using big creatures to protect small creatures. This particular card leans more towards black than white, but as a signpost uncommon it presents indestructible as a shared keyword while making a big body for the midrange game. It is presumed that BW will care about 1/1 or smaller creatures.
Flavor Intention: This desert world, whatever it is, has trade routes and experienced caravan guides, but they have a relationship with their beasts. The beast can travel alone, but its job is to protect the humans who are making their way across the sands. Fairly straightforward symbiosis. Black in this set is presumed to be more goal-oriented and determined, power without the more selfish aspects.
> Season of Scars
Mechanical Intention: Auras are the obvious theme here for this big enchantment. Enchantments may play a subtheme, but the balance here is using Auras as alternative resources, as well as having Auras on lands, which hasn’t been done in large concentrations since (surprisingly) Return to Ravnica. You can use your Auras to help creatures later in the game, where you might have a higher concentration of them (considering it’s a draftable set). Ooh, what if there was an Aura that could do both, like the Runes?
Flavor Intention: In general shamanic terms, there’s the natural connection to the land and the worship of the great mountain, with ritual scarring that mirrors etchings of power, history, and culture. These people use their past to learn from the scarred lessons of the shamans that came before them, lessons that reappear to give power even after the death of the scarred or the destruction of the land.
~
But here’s the thing: these cards still play well with cards that came before it. And that’s perfectly fine; in fact, it wouldn’t be good MTG design without it. Consider what you’re making in the context of “new and exciting space” but keep in mind that I’m not going to dock points for having a functional card in the greater MTG context.
@abelzumi
#mtg#magic the gathering#custom magic card#example design#new archetype contest#inventor's fair#tuesday blog
11 notes
·
View notes
Text
Ioslon, Beloved by Worms
Chaotic Neutral Archfey of Spirals, Worms, and Obsession
Domains: Artifice, Chaos, Charm, Madness Subdomains: Toil, Protean, Captivation, Insanity Favored Weapon: Whip Symbol: A worm curled into a loose spiral Sacred Animal: Worms Sacred Color: Blue, purple
The temptation of the Demon Lords is not merely for mortals. The eternal paths that the Ravager Worm Yhidothrus carves through layer after layer of reality have attracted the attention of countless mortals and immortals alike who seek out the secrets that the great Demon Lord holds. Not a single one of them returns whole, if at all, and this does not change for creatures of great influence like Ioslon.
Once a revered craftsman among the Fey, Ioslon became curious of what hid within the boundless depths of the Spiral Path--Yhidothrus’ realm--and that curiosity quickly, pardon the pun, spiraled into obsession. Building himself a vessel he believed could survive the ravages of Abyss and Worm alike, Ioslon and a crew of his sycophants and faithful descended into the Path and, within a mere month, vanished beyond means of communication both magical and mundane for several centuries. Like many who’ve performed the very same foolish act, Ioslon was swiftly delegated to a mere footnote in the dusty tomes regarding the Ravager Worm, standing out only for his notable status as an Archfey.
That very same status is perhaps what ended up saving him from destruction, not that he ever said. His return was not a triumphant affair with ribbons fluttering through the air, no. Only a handful even knew he had returned at all until rumors of his workshop reopening began to circulate, though none were allowed inside. It was only when Ng the Hooded himself stepped up to the door and requested entry to the craftsman’s workshop that it was revealed what had happened to Ioslon. A writhing body of composite millions, a strange obsession, fiendish magic used to twist the world into unearthly shapes. Bringing the Abyss into the First World was usually a punishable offense, but Ioslon had plans for these exotic materials that the Hooded demigod found interesting and an assurance that stayed the Eldest’s hand:
“I have learned what I needed to from Yhidothrus.”
Ng was the first to receive a gift from the Beloved By Worms. It’s not known what Ioslon said and gifted to each of the Eldest and Archfey who visited in turn, but it has similarly quelled their anger for the time being, allowing the writhing Archfey to work in relative peace towards his... “goals.”
In truth, Ioslon possesses few long-term or even short-term goals. His mind is too far gone for such leaps and bounds, and is not even fully his anymore. His form--now composed of innumerable worms--houses not just his consciousness, but the fragmented minds of thousands of individuals consumed by the madness of the Spiral Path, a collective he refers to as the Twine. While the mind of the revered craftsman is at the forefront of this mess, the countless minds and memories sharing space in his head steer him in a circle almost constantly... or, rather, a spiral.
The congealed obsessions of each and every spirit Ioslon has assimilated has formed together to form a single cohesive thought which links all of them: An adoration of the spiral. The “Divine Shape,” as he calls it, is the only thing that grants him focus, and only projects involved with it or incorporating it in some way are projects he can focus long enough to work on to completion. His laboratory is littered with clockworks in varying states of construction, each incorporating numerous spiral-patterned gears and unnecessary numbers of springs to sate the obsession of his thousand conflicting minds. His laboratory is also strewn about with terrariums containing worms and worm-like creatures from all over the Great Beyond, as he claims to be able to divine all that he needs from watching them burrow, eat, and writhe. Whether or not this is true is not known.
The obsession with the Divine Shape guilds Ioslon’s new faith and philosophy almost entirely, though metaphorical meanings and the symbology of the spiral are left to his minions and sycophants; he’s purely interested in the physical pattern, and waxing poetic about cycles or recursion is something he never truly engages in. Despite this, every now and then, enough of the fragmented remnants will surge to the surface to trigger a sudden obsession with topics such as time, entropy, patterns, madness, runes, or other spiral-adjacent subjects that stretch beyond the physical. These swings of focus are typically when the Twine take over themselves and create their most magnificent of devices, the constructs they craft performing reality-defying feats that are difficult, if not impossible, to replicate even by the greatest of mortal minds. Despite (or perhaps because of) the corruption and fragmenting of his mind, Ioslon possesses the genius necessary to build machines that can do anything, no matter how outlandish or impossible. It’s these miracles of invention that draw people to Ioslon in the hopes of finding their own muse.
-------- Obedience and Boons --------
Ioslon’s faith is more of a gathering of fans and fellow geniuses than an actual religion, with the majority of his flock gathering to witness his works of art or the emergence of the Twine. Collaborating with Ioslon himself is nearly impossible, but many great minds in the field of clockwork and engineering departments have met one another at his inventors fairs and begun to collaborating with each other instead. To truly work alongside Ioslon himself, one must have a similarly single-minded, manic obsession into which they will throw all else. An unenviable position, to be certain, but the Beloved by Worms views such creatures as kindred souls and allows them access to his shop and his resources, so that they may pursue their greatest passions.
The rest of his faithful and Feysworn have their own reasons for working for him. Many pity him, gathering materials from across the cosmos to bring to his lab at his request simply to prevent him from injuring himself getting them. Many desire something of him, hoping that by achieving greatness in his name, they will be granted their greatest wish. Still others work for him for the simple reason of whimsy, wondering what he’ll do next and thus obeying his nigh-nonsensical orders just to see what will happen. Any member of a class which rewards creativity, drive, or single-minded obsession is welcome in the flock of he who is Beloved by Worms.
A great number of Ioslon’s servants are often sent on missions that can range anywhere from pointless to the laughable to the unfeasible, all guided by his obsession. One Feysworn recalls being instructed to carve spirals into every 4th brick on a sidewalk in a specific city, while another group earned the considerably more dangerous mission of wrangling a Purple Worm, only to have it fed to another, larger Purple Worm for unfathomable reasons as he looked on, writing exotic symbols on a clipboard. One particularly dangerous mission took a squadron of his flock deep into the Darklands in search of a colony of Flail Snails he demanded be brought to him, as he tearfully languished over their “inability to experience their own immaculate design” and strove to grant them the gift of sight.
Still, those who serve the Beloved by Worms learn to put up with these strange orders, as each completed mission seems to grant him just a bit more stability, bringing him closer to his next miracle.
Using the Fey Obedience feat, a worshiper of Ioslon gain certain Boons upon reaching a certain amount of Hit Dice. These Boons are granted at 12HD, 16HD, and 20HD, though the Feysworn Prestige Class allows someone to achieve the Boons much, much sooner. The Beloved by Worms is an Archfey, though a powerful one, but his Boons are relatively simple and remain spell-likes that may be cast 1/day.
Obedience: Using a sharp implement, slowly scratch or carve a spiral into the ground as you walk in a tight circle for roughly an hour, moving slowly outwards until the spiral is at least 5 feet wide (or as wide as the area allows). Alternately, tinker with or build a clockwork device. Benefit: Gain a +4 sacred or profane bonus to saves against charms and compulsion effects, as well as to Craft checks.
Boon 1: Puzzle Box
Boon 2: Quest
Boon 3: Summon Elder Worm
53 notes
·
View notes
Link
Data Structures and Algorithms from Zero to Hero and Crack Top Companies 100+ Interview questions (Java Coding)
What you’ll learn
Java Data Structures and Algorithms Masterclass
Learn, implement, and use different Data Structures
Learn, implement and use different Algorithms
Become a better developer by mastering computer science fundamentals
Learn everything you need to ace difficult coding interviews
Cracking the Coding Interview with 100+ questions with explanations
Time and Space Complexity of Data Structures and Algorithms
Recursion
Big O
Dynamic Programming
Divide and Conquer Algorithms
Graph Algorithms
Greedy Algorithms
Requirements
Basic Java Programming skills
Description
Welcome to the Java Data Structures and Algorithms Masterclass, the most modern, and the most complete Data Structures and Algorithms in Java course on the internet.
At 44+ hours, this is the most comprehensive course online to help you ace your coding interviews and learn about Data Structures and Algorithms in Java. You will see 100+ Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft and how-to face Interviews with comprehensive visual explanatory video materials which will bring you closer to landing the tech job of your dreams!
Learning Java is one of the fastest ways to improve your career prospects as it is one of the most in-demand tech skills! This course will help you in better understanding every detail of Data Structures and how algorithms are implemented in high-level programming languages.
We’ll take you step-by-step through engaging video tutorials and teach you everything you need to succeed as a professional programmer.
After finishing this course, you will be able to:
Learn basic algorithmic techniques such as greedy algorithms, binary search, sorting, and dynamic programming to solve programming challenges.
Learn the strengths and weaknesses of a variety of data structures, so you can choose the best data structure for your data and applications
Learn many of the algorithms commonly used to sort data, so your applications will perform efficiently when sorting large datasets
Learn how to apply graph and string algorithms to solve real-world challenges: finding shortest paths on huge maps and assembling genomes from millions of pieces.
Why this course is so special and different from any other resource available online?
This course will take you from the very beginning to very complex and advanced topics in understanding Data Structures and Algorithms!
You will get video lectures explaining concepts clearly with comprehensive visual explanations throughout the course.
You will also see Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft.
I cover everything you need to know about the technical interview process!
So whether you are interested in learning the top programming language in the world in-depth and interested in learning the fundamental Algorithms, Data Structures, and performance analysis that make up the core foundational skillset of every accomplished programmer/designer or software architect and is excited to ace your next technical interview this is the course for you!
And this is what you get by signing up today:
Lifetime access to 44+ hours of HD quality videos. No monthly subscription. Learn at your own pace, whenever you want
Friendly and fast support in the course Q&A whenever you have questions or get stuck
FULL money-back guarantee for 30 days!
This course is designed to help you to achieve your career goals. Whether you are looking to get more into Data Structures and Algorithms, increase your earning potential, or just want a job with more freedom, this is the right course for you!
The topics that are covered in this course.
Section 1 – Introduction
What are Data Structures?
What is an algorithm?
Why are Data Structures And Algorithms important?
Types of Data Structures
Types of Algorithms
Section 2 – Recursion
What is Recursion?
Why do we need recursion?
How does Recursion work?
Recursive vs Iterative Solutions
When to use/avoid Recursion?
How to write Recursion in 3 steps?
How to find Fibonacci numbers using Recursion?
Section 3 – Cracking Recursion Interview Questions
Question 1 – Sum of Digits
Question 2 – Power
Question 3 – Greatest Common Divisor
Question 4 – Decimal To Binary
Section 4 – Bonus CHALLENGING Recursion Problems (Exercises)
power
factorial
products array
recursiveRange
fib
reverse
palindrome
some recursive
flatten
capitalize first
nestedEvenSum
capitalize words
stringifyNumbers
collects things
Section 5 – Big O Notation
Analogy and Time Complexity
Big O, Big Theta, and Big Omega
Time complexity examples
Space Complexity
Drop the Constants and the nondominant terms
Add vs Multiply
How to measure the codes using Big O?
How to find time complexity for Recursive calls?
How to measure Recursive Algorithms that make multiple calls?
Section 6 – Top 10 Big O Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Product and Sum
Print Pairs
Print Unordered Pairs
Print Unordered Pairs 2 Arrays
Print Unordered Pairs 2 Arrays 100000 Units
Reverse
O(N) Equivalents
Factorial Complexity
Fibonacci Complexity
Powers of 2
Section 7 – Arrays
What is an Array?
Types of Array
Arrays in Memory
Create an Array
Insertion Operation
Traversal Operation
Accessing an element of Array
Searching for an element in Array
Deleting an element from Array
Time and Space complexity of One Dimensional Array
One Dimensional Array Practice
Create Two Dimensional Array
Insertion – Two Dimensional Array
Accessing an element of Two Dimensional Array
Traversal – Two Dimensional Array
Searching for an element in Two Dimensional Array
Deletion – Two Dimensional Array
Time and Space complexity of Two Dimensional Array
When to use/avoid array
Section 8 – Cracking Array Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Question 1 – Missing Number
Question 2 – Pairs
Question 3 – Finding a number in an Array
Question 4 – Max product of two int
Question 5 – Is Unique
Question 6 – Permutation
Question 7 – Rotate Matrix
Section 9 – CHALLENGING Array Problems (Exercises)
Middle Function
2D Lists
Best Score
Missing Number
Duplicate Number
Pairs
Section 10 – Linked List
What is a Linked List?
Linked List vs Arrays
Types of Linked List
Linked List in the Memory
Creation of Singly Linked List
Insertion in Singly Linked List in Memory
Insertion in Singly Linked List Algorithm
Insertion Method in Singly Linked List
Traversal of Singly Linked List
Search for a value in Single Linked List
Deletion of a node from Singly Linked List
Deletion Method in Singly Linked List
Deletion of entire Singly Linked List
Time and Space Complexity of Singly Linked List
Section 11 – Circular Singly Linked List
Creation of Circular Singly Linked List
Insertion in Circular Singly Linked List
Insertion Algorithm in Circular Singly Linked List
Insertion method in Circular Singly Linked List
Traversal of Circular Singly Linked List
Searching a node in Circular Singly Linked List
Deletion of a node from Circular Singly Linked List
Deletion Algorithm in Circular Singly Linked List
A method in Circular Singly Linked List
Deletion of entire Circular Singly Linked List
Time and Space Complexity of Circular Singly Linked List
Section 12 – Doubly Linked List
Creation of Doubly Linked List
Insertion in Doubly Linked List
Insertion Algorithm in Doubly Linked List
Insertion Method in Doubly Linked List
Traversal of Doubly Linked List
Reverse Traversal of Doubly Linked List
Searching for a node in Doubly Linked List
Deletion of a node in Doubly Linked List
Deletion Algorithm in Doubly Linked List
Deletion Method in Doubly Linked List
Deletion of entire Doubly Linked List
Time and Space Complexity of Doubly Linked List
Section 13 – Circular Doubly Linked List
Creation of Circular Doubly Linked List
Insertion in Circular Doubly Linked List
Insertion Algorithm in Circular Doubly Linked List
Insertion Method in Circular Doubly Linked List
Traversal of Circular Doubly Linked List
Reverse Traversal of Circular Doubly Linked List
Search for a node in Circular Doubly Linked List
Delete a node from Circular Doubly Linked List
Deletion Algorithm in Circular Doubly Linked List
Deletion Method in Circular Doubly Linked List
Entire Circular Doubly Linked List
Time and Space Complexity of Circular Doubly Linked List
Time Complexity of Linked List vs Arrays
Section 14 – Cracking Linked List Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Linked List Class
Question 1 – Remove Dups
Question 2 – Return Kth to Last
Question 3 – Partition
Question 4 – Sum Linked Lists
Question 5 – Intersection
Section 15 – Stack
What is a Stack?
What and Why of Stack?
Stack Operations
Stack using Array vs Linked List
Stack Operations using Array (Create, isEmpty, isFull)
Stack Operations using Array (Push, Pop, Peek, Delete)
Time and Space Complexity of Stack using Array
Stack Operations using Linked List
Stack methods – Push, Pop, Peek, Delete, and isEmpty using Linked List
Time and Space Complexity of Stack using Linked List
When to Use/Avoid Stack
Stack Quiz
Section 16 – Queue
What is a Queue?
Linear Queue Operations using Array
Create, isFull, isEmpty, and enQueue methods using Linear Queue Array
Dequeue, Peek and Delete Methods using Linear Queue Array
Time and Space Complexity of Linear Queue using Array
Why Circular Queue?
Circular Queue Operations using Array
Create, Enqueue, isFull and isEmpty Methods in Circular Queue using Array
Dequeue, Peek and Delete Methods in Circular Queue using Array
Time and Space Complexity of Circular Queue using Array
Queue Operations using Linked List
Create, Enqueue and isEmpty Methods in Queue using Linked List
Dequeue, Peek and Delete Methods in Queue using Linked List
Time and Space Complexity of Queue using Linked List
Array vs Linked List Implementation
When to Use/Avoid Queue?
Section 17 – Cracking Stack and Queue Interview Questions (Amazon, Facebook, Apple, Microsoft)
Question 1 – Three in One
Question 2 – Stack Minimum
Question 3 – Stack of Plates
Question 4 – Queue via Stacks
Question 5 – Animal Shelter
Section 18 – Tree / Binary Tree
What is a Tree?
Why Tree?
Tree Terminology
How to create a basic tree in Java?
Binary Tree
Types of Binary Tree
Binary Tree Representation
Create Binary Tree (Linked List)
PreOrder Traversal Binary Tree (Linked List)
InOrder Traversal Binary Tree (Linked List)
PostOrder Traversal Binary Tree (Linked List)
LevelOrder Traversal Binary Tree (Linked List)
Searching for a node in Binary Tree (Linked List)
Inserting a node in Binary Tree (Linked List)
Delete a node from Binary Tree (Linked List)
Delete entire Binary Tree (Linked List)
Create Binary Tree (Array)
Insert a value Binary Tree (Array)
Search for a node in Binary Tree (Array)
PreOrder Traversal Binary Tree (Array)
InOrder Traversal Binary Tree (Array)
PostOrder Traversal Binary Tree (Array)
Level Order Traversal Binary Tree (Array)
Delete a node from Binary Tree (Array)
Entire Binary Tree (Array)
Linked List vs Python List Binary Tree
Section 19 – Binary Search Tree
What is a Binary Search Tree? Why do we need it?
Create a Binary Search Tree
Insert a node to BST
Traverse BST
Search in BST
Delete a node from BST
Delete entire BST
Time and Space complexity of BST
Section 20 – AVL Tree
What is an AVL Tree?
Why AVL Tree?
Common Operations on AVL Trees
Insert a node in AVL (Left Left Condition)
Insert a node in AVL (Left-Right Condition)
Insert a node in AVL (Right Right Condition)
Insert a node in AVL (Right Left Condition)
Insert a node in AVL (all together)
Insert a node in AVL (method)
Delete a node from AVL (LL, LR, RR, RL)
Delete a node from AVL (all together)
Delete a node from AVL (method)
Delete entire AVL
Time and Space complexity of AVL Tree
Section 21 – Binary Heap
What is Binary Heap? Why do we need it?
Common operations (Creation, Peek, sizeofheap) on Binary Heap
Insert a node in Binary Heap
Extract a node from Binary Heap
Delete entire Binary Heap
Time and space complexity of Binary Heap
Section 22 – Trie
What is a Trie? Why do we need it?
Common Operations on Trie (Creation)
Insert a string in Trie
Search for a string in Trie
Delete a string from Trie
Practical use of Trie
Section 23 – Hashing
What is Hashing? Why do we need it?
Hashing Terminology
Hash Functions
Types of Collision Resolution Techniques
Hash Table is Full
Pros and Cons of Resolution Techniques
Practical Use of Hashing
Hashing vs Other Data structures
Section 24 – Sort Algorithms
What is Sorting?
Types of Sorting
Sorting Terminologies
Bubble Sort
Selection Sort
Insertion Sort
Bucket Sort
Merge Sort
Quick Sort
Heap Sort
Comparison of Sorting Algorithms
Section 25 – Searching Algorithms
Introduction to Searching Algorithms
Linear Search
Linear Search in Python
Binary Search
Binary Search in Python
Time Complexity of Binary Search
Section 26 – Graph Algorithms
What is a Graph? Why Graph?
Graph Terminology
Types of Graph
Graph Representation
The graph in Java using Adjacency Matrix
The graph in Java using Adjacency List
Section 27 – Graph Traversal
Breadth-First Search Algorithm (BFS)
Breadth-First Search Algorithm (BFS) in Java – Adjacency Matrix
Breadth-First Search Algorithm (BFS) in Java – Adjacency List
Time Complexity of Breadth-First Search (BFS) Algorithm
Depth First Search (DFS) Algorithm
Depth First Search (DFS) Algorithm in Java – Adjacency List
Depth First Search (DFS) Algorithm in Java – Adjacency Matrix
Time Complexity of Depth First Search (DFS) Algorithm
BFS Traversal vs DFS Traversal
Section 28 – Topological Sort
What is Topological Sort?
Topological Sort Algorithm
Topological Sort using Adjacency List
Topological Sort using Adjacency Matrix
Time and Space Complexity of Topological Sort
Section 29 – Single Source Shortest Path Problem
what is Single Source Shortest Path Problem?
Breadth-First Search (BFS) for Single Source Shortest Path Problem (SSSPP)
BFS for SSSPP in Java using Adjacency List
BFS for SSSPP in Java using Adjacency Matrix
Time and Space Complexity of BFS for SSSPP
Why does BFS not work with Weighted Graph?
Why does DFS not work for SSSP?
Section 30 – Dijkstra’s Algorithm
Dijkstra’s Algorithm for SSSPP
Dijkstra’s Algorithm in Java – 1
Dijkstra’s Algorithm in Java – 2
Dijkstra’s Algorithm with Negative Cycle
Section 31 – Bellman-Ford Algorithm
Bellman-Ford Algorithm
Bellman-Ford Algorithm with negative cycle
Why does Bellman-Ford run V-1 times?
Bellman-Ford in Python
BFS vs Dijkstra vs Bellman Ford
Section 32 – All Pairs Shortest Path Problem
All pairs shortest path problem
Dry run for All pair shortest path
Section 33 – Floyd Warshall
Floyd Warshall Algorithm
Why Floyd Warshall?
Floyd Warshall with negative cycle,
Floyd Warshall in Java,
BFS vs Dijkstra vs Bellman Ford vs Floyd Warshall,
Section 34 – Minimum Spanning Tree
Minimum Spanning Tree,
Disjoint Set,
Disjoint Set in Java,
Section 35 – Kruskal’s and Prim’s Algorithms
Kruskal Algorithm,
Kruskal Algorithm in Python,
Prim’s Algorithm,
Prim’s Algorithm in Python,
Prim’s vs Kruskal
Section 36 – Cracking Graph and Tree Interview Questions (Amazon, Facebook, Apple, Microsoft)
Section 37 – Greedy Algorithms
What is a Greedy Algorithm?
Well known Greedy Algorithms
Activity Selection Problem
Activity Selection Problem in Python
Coin Change Problem
Coin Change Problem in Python
Fractional Knapsack Problem
Fractional Knapsack Problem in Python
Section 38 – Divide and Conquer Algorithms
What is a Divide and Conquer Algorithm?
Common Divide and Conquer algorithms
How to solve the Fibonacci series using the Divide and Conquer approach?
Number Factor
Number Factor in Java
House Robber
House Robber Problem in Java
Convert one string to another
Convert One String to another in Java
Zero One Knapsack problem
Zero One Knapsack problem in Java
Longest Common Sequence Problem
Longest Common Subsequence in Java
Longest Palindromic Subsequence Problem
Longest Palindromic Subsequence in Java
Minimum cost to reach the Last cell problem
Minimum Cost to reach the Last Cell in 2D array using Java
Number of Ways to reach the Last Cell with given Cost
Number of Ways to reach the Last Cell with given Cost in Java
Section 39 – Dynamic Programming
What is Dynamic Programming? (Overlapping property)
Where does the name of DC come from?
Top-Down with Memoization
Bottom-Up with Tabulation
Top-Down vs Bottom Up
Is Merge Sort Dynamic Programming?
Number Factor Problem using Dynamic Programming
Number Factor: Top-Down and Bottom-Up
House Robber Problem using Dynamic Programming
House Robber: Top-Down and Bottom-Up
Convert one string to another using Dynamic Programming
Convert String using Bottom Up
Zero One Knapsack using Dynamic Programming
Zero One Knapsack – Top Down
Zero One Knapsack – Bottom Up
Section 40 – CHALLENGING Dynamic Programming Problems
Longest repeated Subsequence Length problem
Longest Common Subsequence Length problem
Longest Common Subsequence problem
Diff Utility
Shortest Common Subsequence problem
Length of Longest Palindromic Subsequence
Subset Sum Problem
Egg Dropping Puzzle
Maximum Length Chain of Pairs
Section 41 – A Recipe for Problem Solving
Introduction
Step 1 – Understand the problem
Step 2 – Examples
Step 3 – Break it Down
Step 4 – Solve or Simplify
Step 5 – Look Back and Refactor
Section 41 – Wild West
Download
To download more paid courses for free visit course catalog where 1000+ paid courses available for free. You can get the full course into your device with just a single click. Follow the link above to download this course for free.
3 notes
·
View notes
Text
12 Terminal Commands
Every Web Developer Should Know
The terminal is one of the foremost vital productivity tools in a developer's arsenal. Mastering it will have an awfully positive impact on your work flow, as several everyday tasks get reduced to writing a straightforward command and striking Enter. In this article we've ready for you a set of UNIX system commands that may assist you get the foremost out of your terminal. a number of them square measure inbuilt, others square measure free tools that square measure reliable and may be put in but a moment.
Curl
Curl may be a program line tool for creating requests over HTTP(s), FTP and dozens of different protocols you will haven't detected concerning. It will transfer files, check response headers, and freely access remote information.
In net development curl is usually used for testing connections and dealing with RESTful APIs.
# Fetch the headers of a URL. curl -I http://google.com HTTP/1.1 302 Found Cache-Control: private Content-Type: text/html; charset=UTF-8 Referrer-Policy: no-referrer Location: http://www.google.com/?gfe_rd=cr&ei=0fCKWe6HCZTd8AfCoIWYBQ Content-Length: 258 Date: Wed, 09 Aug 2017 11:24:01 GMT # Make a GET request to a remote API. curl http://numbersapi.com/random/trivia 29 is the number of days it takes Saturn to orbit the Sun.
Curl commands can get much more complicated than this. There are tons of options for controlling headers, cookies, authentication,and more.
Tree
Tree may be a little instruction utility that shows you a visible illustration of the files during a directory. It works recursively, going over every level of nesting and drawing a formatted tree of all the contents. this fashion you'll quickly skim and notice the files you're trying to find.
tree . ├── css │ ├── bootstrap.css │ ├── bootstrap.min.css ├── fonts │ ├── glyphicons-halflings-regular.eot │ ├── glyphicons-halflings-regular.svg │ ├── glyphicons-halflings-regular.ttf │ ├── glyphicons-halflings-regular.woff │ └── glyphicons-halflings-regular.woff2 └── js ├── bootstrap.js └── bootstrap.min.js
There is also the option to filter the results using a simple regEx-like pattern:
tree -P '*.min.*' . ├── css │ ├── bootstrap.min.css ├── fonts └── js └── bootstrap.min.js
Tmux
According to its Wiki, Tmux may be a terminal electronic device, that translated in human language would mean that it is a tool for connecting multiple terminals to one terminal session.
It helps you to switch between programs in one terminal, add split screen panes, and connect multiple terminals to a similar session, keeping them in adjust. Tmux is particularly helpful once functioning on a far off server, because it helps you to produce new tabs while not having to log in once more.
Disk usage - du
The du command generates reports on the area usage of files and directories. it's terribly straightforward to use and may work recursively, rummaging every directory and returning the individual size of each file. A common use case for du is once one in every of your drives is running out of area and you do not understand why. Victimization this command you'll be able to quickly see what proportion storage every folder is taking, therefore finding the most important memory saver.
# Running this will show the space usage of each folder in the current directory. # The -h option makes the report easier to read. # -s prevents recursiveness and shows the total size of a folder. # The star wildcard (*) will run du on each file/folder in current directory. du -sh * 1.2G Desktop 4.0K Documents 40G Downloads 4.0K Music 4.9M Pictures 844K Public 4.0K Templates 6.9M Videos
There is also a similar command called
df
(Disk Free) which returns various information about the available disk space (the opposite of du).
Git
Git is far and away the foremost standard version system immediately. It’s one among the shaping tools of contemporary internet dev and that we simply could not leave it out of our list. There area unit many third-party apps and tools on the market however most of the people choose to access unpleasant person natively although the terminal. The unpleasant person CLI is basically powerful and might handle even the foremost tangled project history.
Tar
Tar is the default Unix tool for working with file archives. It allows you to quickly bundle multiple files into one package, making it easier to store and move them later on.
tar -cf archive.tar file1 file2 file3
Using the -x option it can also extract existing .tar archives.
tar -xf archive.tar
Note that almost all alternative formats like .zip and .rar can't be opened by tar and need alternative command utilities like unfasten.
Many trendy operating system systems run associate expanded version of tar (GNU tar) that may additionally perform file size compression:
# Create compressed gzip archive. tar -czf file.tar.gz inputfile1 inputfile2 # Extract .gz archive. tar -xzf file.tar.gz
If your OS doesn't have that version of tar, you can use
gzip
,
zcat
or
compress
to reduce the size of file archives.
md5sum
Unix has many inbuilt hashing commands together with
md5sum
,
sha1sum
and others. These program line tools have varied applications in programming, however most significantly they'll be used for checking the integrity of files. For example, if you've got downloaded associate degree .iso file from associate degree untrusted supply, there's some likelihood that the file contains harmful scripts. To form positive the .iso is safe, you'll generate associate degree md5 or alternative hash from it.
md5sum ubuntu-16.04.3-desktop-amd64.iso 0d9fe8e1ea408a5895cbbe3431989295 ubuntu-16.04.3-desktop-amd64.iso
You can then compare the generated string to the one provided from the first author (e.g. UbuntuHashes).
Htop
Htop could be a a lot of powerful different to the intrinsic prime task manager. It provides a complicated interface with several choices for observation and dominant system processes.
Although it runs within the terminal, htop has excellent support for mouse controls. This makes it a lot of easier to navigate the menus, choose processes, and organize the tasks thought sorting and filtering.
Ln
Links in UNIX operating system square measure the same as shortcuts in Windows, permitting you to urge fast access to bound files. Links square measure created via the ln command and might be 2 types: arduous or symbolic. Every kind has totally different properties and is employed for various things (read more).
Here is associate example of 1 of the various ways that you'll be able to use links. as an instance we've a directory on our desktop referred to as Scripts. It contains showing neatness organized bash scripts that we have a tendency to ordinarily use. on every occasion we wish to decision one in every of our scripts we'd need to do this:
~/Desktop/Scripts/git-scripts/git-cleanup
Obviously, this is isn't very convinient as we have to write the absolute path every time. Instead we can create a symlink from our Scripts folder to /usr/local/bin, which will make the scripts executable from all directories.
sudo ln -s ~/Desktop/Scripts/git-scripts/git-cleanup /usr/local/bin/
With the created symlink we can now call our script by simply writing its name in any opened terminal.
git-cleanup
SSH
With the ssh command users will quickly hook up with a foreign host and log into its UNIX operating system shell. This makes it doable to handily issue commands on the server directly from your native machine's terminal.
To establish a association you just got to specify the proper science address or URL. The primary time you hook up with a replacement server there'll be some style of authentication.
ssh username@remote_host
If you want to quickly execute a command on the server without logging in, you can simply add a command after the url. The command will run on the server and the result from it will be returned.
ssh username@remote_host ls /var/www some-website.com some-other-website.com
There is a lot you can do with SSH like creating proxies and tunnels, securing your connection with private keys, transferring files and more.
Grep
Grep is the standard Unix utility for finding strings inside text. It takes an input in the form of a file or direct stream, runs its content through a regular expression, and returns all the matching lines.
This command comes in handy once operating with massive files that require to be filtered. Below we tend to use grep together with the date command to look through an oversized log file and generate a brand new file containing solely errors from nowadays.
// Search for today's date (in format yyyy-mm-dd) and write the results to a new file. grep "$(date +"%Y-%m-%d")" all-errors-ever.log > today-errors.log
Another nice command for operating with strings is
sed
. It’s additional powerful (and additional complicated) than grep and may perform nearly any string-related task together with adding, removing or replacement strings.
Alias
Many OS commands, together with some featured during this article, tend to urge pretty long when you add all the choices to them. to create them easier to recollect, you'll produce short aliases with the alias bash inbuilt command:
# Create an alias for starting a local web server. alias server="python -m SimpleHTTPServer 9000" # Instead of typing the whole command simply use the alias. server Serving HTTP on 0.0.0.0 port 9000 ...
The alias are offered as long as you retain that terminal open. to create it permanent you'll add the alias command to your .bashrc file. We will be happy to answer your questions on designing, developing, and deploying comprehensive enterprise web, mobile apps and customized software solutions that best fit your organization needs.
As a reputed Software Solutions Developer we have expertise in providing dedicated remote and outsourced technical resources for software services at very nominal cost. Besides experts in full stacks We also build web solutions, mobile apps and work on system integration, performance enhancement, cloud migrations and big data analytics. Don’t hesitate to
get in touch with us!
1 note
·
View note
Text
a matter of time
Once again, I’m back on my MK bullshit. This one’s kind of delving into morals, ethics, philosophy, and Liu Kang having a hard time of it, generally, but hey, ain’t that just the way of Kombat?
Ft. First Person Present Tense horseshit--Raiden being a dad. Liu Kang doing his fucking best.
As usual, tumblr doesn’t preserve italics and I’m too lazy to find ‘em. Unedited, blah blah blah
Broken Timeline (references to Restored Timeline)
“I cannot do this, Lord Raiden—there simply…. There is just no way…” The young fire god paces before Kronika’s hourglass, eyes shot through with sparks of anger, moisture shining on his cheeks. God he may be, but his heart is still that of a mortal and it bleeds for the pain he must cause. There are no words of comfort for him, nor of description to properly depict the true horror of that place into which he has just stepped. I do not envy him. I was born with this burden—not of time, of divinity—but that does not mean I cannot sympathize.
“What is it you cannot do?” There is time for reprimand later, as he is the Lord now, and I am not. I regard him carefully and the hourglass even more so. What it has done to him, the lines upon his young-old face, the worries that I see prowling through every inch of his body; this, too, pains me. He settles upon a large stone, fists tight, eyes downcast.
“Over and over, no matter what I do to shift the sands,” he grunts, keeping his voice low, hating the tears of frustration which he has already shed and fighting those that have yet to fall, “I cannot save them all. Someone falls—someone always falls, sometimes many.”
“…the Shirai-Ryu massacre.” The guess is a simple one, but weighty. He looks up, surprised, for but a moment, that I have guessed the current source of his distress. “I know this because I know your heart, Lord Liu Kang, and I have always known it… Furthermore, I have come to respect and appreciate its openness, warmth, and honesty—it is that heart which makes your fires burn so hot, but…”
“It… is a two-edged sword, isn’t it?” His shoulders sag and I am compelled to move closer, to stoop before and lay a hand upon him.
“Love is that way, yes—all emotions are, but love is the sharpest… not hate, or fear, or joy… Love. It is a root, remember that, and leads to all else.”
“I wish I didn’t—”
“No!” I snap vehemently, perhaps even more strongly than I’d anticipated doing. “No, do not speak those words aloud here, at the dawn of time… This void before all things is sacrosanct—our words affect it, even if we do not realize…” His eyes are wide, searching my face for exaggeration. He will find none. “More importantly, it affects us.”
“Forgive me, Teacher—I… it was the boy, Satoshi…” Liu Kang trails off. He need not finish his thought. I understand. As a deity, I have watched the lives of many mortals—they come and go, so fleeting in the grand scheme of things, but no less important for all that. I ache for the thought of those I have lost. He knows this pain as a mortal and perhaps is now beginning to understand that it is not unique to those with finite lives. Perhaps it is worse still for those who persist through the eons; we live with our grief, never quite mastering it.
“There are events which, in all of history, are pivotal to a certain outcome,” I explain gently, “as was our inevitable kombat to Kronika’s plans.”
“But we overcame it,” Liu Kang insists, his fists still clenched, hard, upon his lap. “You saved me—your decision to do that tipped the scales past where she could hope to control that outcome.”
“A one in a billion chance, nothing more,” I remind him, squeezing his shoulder and standing, hoping he will follow, hating to see him in this desperate position and myself, helpless to assist beyond my words.
“No!” This time, it is his turn to snap. “You can’t believe that—you can’t say that here, to me, like this… It isn’t…” He straightens and finally looks up at me. There are tears caught in his eyelashes, but resolution in the set of his jaw. Good. He will need that for what is to come. “It is not the Lord Raiden who chose me.”
“Even gods change.”
The look upon his face is one I remember well. It is frustration, stymied by words of someone he considers far wiser than he. If only he could know just how incorrect that supposition is. By virtue of my endless life, I should, by all rights, be wiser than the young Liu Kang, but I am not. I have been a fool, have known defeat and failure, and have carried grief and remorse as constant companions. That alone will change a person.
“It is that changeability which granted us a chance to defeat her. Kronika underestimated a great many things, including mortals… and the depths of my ire for those who would harm them. I became a god of vengeance at the ends of her strings, but she did not anticipate the desperation that would arise from my grief-tainted rage.” I cannot meet his eyes, not now, remembering that, so many times, in so many other timelines, Liu Kang had met his end at my hands.
“But Shinnok’s amulet!” His voice rings out in the roaring darkness and he claps his mouth shut, realizing the curse upon that name in this blank canvas of a place and time—or a lack of place and time; such things are difficult, verbally, to describe. “And the tainted Jinsei…”
“It was the lure of my father’s trinket, not the trinket itself, Lord Liu Kang, which corrupted me, the power granted by that tainted stream of life force which called to me,” I confessed, eyes upon the hourglass. “I am a recursive being, defined by myself; my sins are my own and my nature—which I have fought from my inception into this and every other timeline—is that of a god of destruction.”
The silence drifts between us. I consider him, Liu Kang, and what he has suffered. I wonder if perhaps I am not speaking to the lamb of his own slaughter, to which I have led him. Am I the author of some future madness? But it does not bear meditating upon—it cannot. It has been done and it was, I am certain now, the only way to overcome Kronika. All paths led to destruction except for this one and that, I think, was due in part to my nature, not his.
“So Sh—so he was your father, and Lord Fujin’s.” He seems disappointed, somehow, that this whispered legend or rumor has proven to be the truth. “I guess I knew that—or I thought I did… I’d heard it, but… Asking about family, among our friends?”
We both seem to recall, at once, the multitude of strange circumstances which had brought together the representatives of Earthrealm in the first place.
“Not a wise choice, were tact to be maintained,” I agree, “but the sire is no reflection upon the offspring—or it does not need to be. I knew that immediately when I looked upon my brother and saw someone I loved and someone I would always seek to protect.”
“You’re more human than you ever let on, Lord Raiden,” he observes. “Maybe we’ve softened you.”
“I have always been ‘soft’,” I assure him, “and it may have been my downfall, but for the memories of friends I keep stored up in the very core of my being. You strengthen me, even now… And so you must be, Keeper of Time, strengthened by love and compassion, tempered by reasonable logic and justice… and softened by empathy, but never destroyed by it.”
“So how, then, can I do this? How can I allow it?” He gestures to the glass, standing and straightening, wiping his cheeks and eyes with the other hand. The gesture is so reminiscent of his childhood, it brings a pang to my chest. In this moment, Liu Kang looks more boy than man, and like no god at all, despite his divine attributes. The shining markings which once adorned my flesh now wrap about his, with his own additions, variations to suit him. Never, in all the eons of my existence, have I felt more certain that I had made the correct choice.
“You choose the shift of the sands which, to you, seems most just.”
“The death of an innocent boy is not just, Raiden! How can you demand this of me?”
I shake my head. “I cannot,” I admit quietly. “It is your choice to make. I am not the Keeper of Time. I conferred my divinity upon you for a reason, Lord Liu Kang. This, as it turns out, was your ultimate purpose… All the Shao Kahns of every timeline—all the Raidens… could not stop you. Your inevitability and unpredictability are, at least in part, why Kronika did not see us coming. This, in the end, is why I chose you and why you alone are the appropriate choice to be time’s keeper. Her numerous, repetitious attempts only served to build the foundation of her defeat. She had intended to use that unpredictability to reverberate through time, shattering our alliance and, thence, every timeline, using our konflict to reset existence. She made a mistake.”
“So I must choose the lesser of two—no,” he corrects, “the least of many evils. Raiden, in one shift, I see Bi-Han himself leading the charge—I see the Shirai-Ryu fighting to the last man, but each time, Harumi and Satoshi die at his hands. Quan-Chi is always behind it, no matter who strikes the final blow and always, Hanzo’s family suffers and he…”
“He becomes a wraith.” I nod quietly, gesturing back to the hourglass. “But then what happens?”
“He… fights his way through Netherrealm and confronts Quan-Chi, every time.”
“He is also inevitable.”
Liu Kang nods, “yes, but, such suffering…”
“It builds him into the man we see today, fighting alongside Grandmaster Kuai Liang, for the protection of Earthrealm. Would the Shirai-Ryu and the Lin Kuei not still be at war, were it not for that avalanche of fate?” It is, admittedly, a question even I am not equipped to answer, but it stops him, makes him consider. He sighs and then shrugs.
“I… do not know.”
“So, rather than the least of many evils, Lord Liu Kang, you have been called upon to serve the purpose of balance—true balance—and justice… and to choose that which fulfills your duty.”
“You have always spoken of duty as if it is the only choice,” he observes, though the verbalization clearly pains him, “yet your duties, in service to the Elder Gods, have led you down many paths of destruction.”
I am silent a while, considering the truth of this. There is no simple answer, because he is correct. He has learned much over the years and now has the wisdom of many timelines from which to pull. Experience is the harshest teacher, but the best, by far—we do not soon forget those lessons taught us by pain and force.
“I served their purpose as a dutiful son and… I believe that purpose was, in many ways, to illustrate to me that fighting my nature could only lead to the inevitability of the Storm. I was wrong to follow and obey as I did. You will not be so unwise because you have many lifetimes to recall and to relive… infinite possibilities of wisdom and foolishness, infinite lives and deaths. You were… built to bear this burden.”
“Would you... take it from me?”
“Yes, Liu Kang, I would.” His countenance changes as I lay aside the deified title. It is as if I have regained my student, at least for a time. “My divinity prevents me taking up the crown with the same efficacy as a mortal, however—as I said, you are perfectly suited to its weight.” The pain in his eyes lances deep into me, but I hold his glowing gaze, as he always held mine. “You haven’t the arrogance of a titan or a god; your humility is yet another great strength.”
Liu Kang observes his hands, then me, then the hourglass. He takes in a breath which fills his lungs and then, closing his eyes, he releases it, slowly, through his nose. I watch his countenance shift once more, to something I have not yet seen. There is a certain serene nobility to it and not a note of resignation to be seen. He has begun to truly understand what his duty truly is, what a joy that burden will be to bear—and what a terrible tragedy.
“I understand,” he says finally, opening his eyes once more. Lifting off the foundational stones of all timelines, he moves to the hourglass and begins, once more, to manipulate the sands of time. There is security in his movements, a certain sureness that each decision is being made the right way—even if it is not the “right” decision. After all, at the beginning and the end of all things, one often finds one’s moral compass to be somewhat useless. There is no grander scheme than the one which Liu Kang now manipulates with novice hands and an open, empathetic heart and I could not be more proud of him.
6 notes
·
View notes
Photo

The idea is to find a path between opposite corners that visits the lattice points. One can search for the paths with backtracking, a recursive technique that follows promising branches and prune dead ends. The number of solutions grows quickly; there are merely 8 for the 3-by-5 grid above, but there are 111,712 for the 7-by-7 case.
114 notes
·
View notes