#qr code access control systems
Explore tagged Tumblr posts
Text

Spintly's cloud-based system lays the groundwork for top-notch security in your smart environment. Some notable users include Industry leaders like JLL India, Procter & Gamble, Prestige Group, Godrej Group. Connect with Spintly regarding your project today !!
#access control solutions#access control system#smartbuilding#iot#iotsolutions#rfid technology#bluetooth#wireless#visitor management system#qr code#biometrics#tenantmanagement
0 notes
Text
Parking Guidance System Saudi:-
Superior and advanced technology, The presence of a car parking management system certainly matters. The car owners get a comfortable parking experience. If the parking space is unavailable, the car owners come under stress. https://www.prologicfirstss.com/Car-Access.html

#parking management system saudi#types of rfid access cards in saudi#KIOSK for Attraction Saudi#qr code based parking saudi#car park access control systems#time access biometric machine saudi
0 notes
Text

Tripod Turnstile Overview Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are modern control devices for pedestrian flows. They are used in position where the entrance as well as departure of individuals require to be regulated, such as clever communities, canteens, hotels, galleries, gyms, clubs, metros, stations, anchors, and so on location. Making use of Tripod Turnstile, Swing Turnstile, as well as Flap Turnstile can make the circulation of individuals organized. Tripod Turnstile, Swing Turnstile, Flap Turnstile are made use of in mix with smart cards, finger prints, barcodes and also various other recognition system tools to create an intelligent accessibility control network control system; they are used in mix with computers, access control, attendance, billing administration, ticket systems and also other software application to create a The intelligent Turnstile Gate thorough management system can understand features such as gain access to control, participation, consumption, ticketing, as well as current restricting. This Turnstile Gate monitoring system belongs to the "all-in-one card" and is mounted at flows such as neighborhoods, manufacturing facilities, smart structures, canteens, and so on. It can finish different monitoring features such as employee card traveling control, attendance at leave work and dishes, as well as dining. Tripod Turnstile system attributes Convenient and also rapid: review the card in and out with one swipe. Utilize the accredited IC card and wave it before the smart Tripod Turnstile reader to finish the Tripod Turnstile gate opening as well as fee recording work. The card reading is non-directional as well as the reading and also writing time is 0.1 secs, which is rapid and also hassle-free. Security and confidentiality: Use background or local verification, licensed issuance, as well as distinct identity, that is, the card can just be made use of in this system, and it is safe and also confidential. Reliability: Card superhigh frequency induction, reputable and stable, with the ability to judge as well as assume. Flexibility: The system can flexibly set entry and also departure control employees permissions, period control, cardholder legitimacy and also blacklist loss coverage, including cards and other features. Adaptability: Through permission, the customer card can be utilized for "one-card" management such as parking, presence, accessibility control, patrol, consumption, and so on, making it very easy to recognize several uses of one card. Simplicity: Easy to set up, easy to connect, the software program has a Chinese user interface and also is simple to run. Tripod Turnstile, Swing Turnstile, and Flap Turnstile( RS Security Co., Ltd: www.szrssecurity.com) are contemporary control gadgets for pedestrian flows. The use of Tripod Turnstile, Swing Turnstile, and also Flap Turnstile can make the circulation of people orderly. Utilize the licensed IC card and also wave it in front of the wise Tripod Turnstile reader to complete the Tripod Turnstile gate opening and also charge recording work.
#Tripod Turnstile Doors#Gate Opener#Lock Cylinders#Subway Turnstile#Removable Bollard#Car Parking System#Rfid Qr Code Reader#Turnstile Gate Price#Subway Turnstile Gate#Mini Access Controller
0 notes
Link
This type of system can be helpful in situations where a facility needs to closely monitor who is entering and exiting the building, such as in government buildings, airports, and other high-security locations. The use of Emirates ID or passport as a form of identification also ensures the accuracy of the visitor's personal information, such as name, address, and nationality.
Visitor Management System
Visitor Management System uae
Visitor Management System abu dhabi
Visitor Management System with AI integration
Visitor Management System Dubai
visitor management Building Integration Software uae
Access Control Software Building Integration
Access Control Software Building Integration UAE
Access Control Software Building Integration Abu Dhabi
Building Access Control System Integration Abu Dhabi
#visitor registration software abu dhabi#visitor registration system in uae#Building Access Control System Integration Abu Dhabi#Building Access Control System Integration dubai#Building Access Control System Integration sharjah#qr code access control system abu dhabi#qr code access control system in uae#qr code access con#QR Code Readers#access control system abu dhabi#access control system in sharjah#access control system in ajman#access control system in uae#visitor registration softwrae#visitor registration systems#visitor registration systems uae#building entrance system uae#building entrance system abu dhabi#building entrance system sharjah#building entrance system alain#building entrance system in bur dubai#building entrance system uae#building entrance system uae ajman#building entrance softwrae abu dhabi#building entrance software abu dhabi#building entrance software dubai#building control system dubai#building control system abu dhabi#building control system sharjah#building control system alain
0 notes
Text
Brazil granting ID to household pets

While the United States still debates whether to implement a voter ID mechanism, Brazilian household pets will soon be eligible for the Animal ID card free of charge as the National Register of Domestic Animals is entering its final testing phase, Agencia Brasil reported this week. The Environment Ministry said the tool can be accessed through the Gov.br website.
Animal rescue organizations and city halls will also be able to register the animals under their responsibility and issue the identification card, which will include an identification code (QR Code). This code can be attached to the animal's collar, allowing anyone to locate the guardian via a cell phone camera.
Law 15.046/2024, approved in November by Congress and enacted by President Luiz Inácio Lula da Silva on Dec. 18, authorized the creation of the registry by the Federal Government. The system will gather information on owners and pets to facilitate zoonosis control and the fight against abandonment and mistreatment of animals. The measure should also provide more security in buying and selling transactions.
As per the new law, the register must contain the owner's identity, as well as data on the origin and characteristics of the animals: breed, sex, real or presumed age, vaccinations administered, and diseases contracted or being treated, in addition to the place where the animal is kept. It will be the guardians' duty to report the sale, donation, or death of the pet, indicating the cause.
Continue reading.
4 notes
·
View notes
Text
every time i mod a 3DS the process has drastically changed from the last time
last time i had to download pokemon picross as a crucial step for some reason? i think to exploit a vulnerability in it? i was scared to delete pokemon picross off the system afterwards in case that bricked it somehow. pretty sure it wouldnt have. the system bricked itself eventually anyway because it was a shitty half broken preowned 2DS and one of the ribbons connecting to the top screen broke or whatever im sure the way that sentence is inevitably wrong stands out to somebody
the time before that, the first time i ever did it, had me open one of the base 3DS applications nobody ever uses and use a QR code to permanently change that app to a homebrew launcher but it became infinitely more complicated by the fact that it was a shitty preowned half broken 2DS where the home button didnt work because the previous owner- a small child- stabbed it. the home button was crucial to the process. anyway the bottom screen stopped working eventually. because of when the kid stabbed it
this time on my not shitty or preowned ancient original 3DSxl from 2016(?) the process had no picross and, helpfully, had a step where the controls to open certain menus could be changed in the case of a stabbed broken home button that would have been great before, and had me navigate to a specific point in the 3DS settings menu, take the sd out, put the sd in my laptop, run a batch file on it, and put the sd back in the 3DS which felt like it was going to explode my poor dual screened surgical patient but instead just automagically changed the settings menu to a homebrew installation menu
this version of the process was the easiest so far though. modding your 3DS has never been more accessible and is the best way to ensure you can continue accessing 3DS games after the 3DS eshop closure.
just dont get one a kid stabbed, or where the top screen sometimes doesnt work and then eventually always doesnt work
13 notes
·
View notes
Text





Here's a breakdown of the features presented in the schematics for the PlayStation 7 controller, designed to showcase both technical and ergonomic innovations:
8K HD LCD Mirror Screen
Feature: Center display with 8K resolution in a Silicium Black mirror finish.
Purpose: Offers high-definition visuals directly on the controller, enabling in-game stats, real-time updates, and mirrored content from the main console.
AI Self-Learning Capabilities
Feature: Embedded AI that adapts to user preferences and gameplay styles.
Purpose: Optimizes controller response, remaps buttons based on usage patterns, and provides personalized feedback.
Compact, Ergonomic Design
Feature: Approximately one-quarter inch smaller than standard controllers.
Purpose: Offers enhanced portability, making it more pocket-sized, while maintaining ergonomic comfort for longer gameplay.
Connectivity Ports
HDMI: Allows direct connection to displays or peripherals.
USB: Enables device charging, wired connectivity to the console, and data transfer.
Charging Module: Specialized port for rapid recharging of the controller.
Purpose: Ensures multi-functional connectivity for various gaming setups.
Bluetooth, WiFi, and FiWi Capabilities
Feature: Enhanced wireless capabilities, including Bluetooth and WiFi for direct connectivity, and FiWi sensing.
Purpose: Enables seamless, lag-free connections to the PlayStation 7 console and other devices, along with FiWi for future wireless advancements.
Internal Modular Layout
Feature: Internally organized layout with modular components for AI chip, connectivity modules, and display.
Purpose: Simplifies upgrades, repairs, and component replacements, enhancing longevity and customization.
Enhanced Battery System
Feature: High-capacity battery designed for extended play sessions.
Purpose: Supports advanced features and power-intensive display without compromising battery life.
Dual-Tone Color Variants
Colors: Available in Lo Rider DyeCast Yellow, Black, Silver Chrome, Forest Green, and Azure, plus two-tone combinations.
Purpose: Offers aesthetic customization, appealing to a wide audience with multiple design options.
Identification Details
QR Code: Unique QR codes for easy registration and product information access.
Serial Numbers and Model Numbers: Ensures authenticity and facilitates tracking for warranty, support, and inventory.
Purpose: Helps with identification and authentication for warranty, inventory, and support purposes.
Enhanced Sensory Capabilities
Feature: Equipped with advanced sensors to detect and respond to motion, orientation, and grip pressure.
Purpose: Improves gameplay experience by adding a responsive, immersive control experience.
These features collectively position the PlayStation 7 controller as a cutting-edge, user-focused gaming device with both aesthetic appeal and functional versatility, ready for patent submission. Let me know if further elaboration is needed!


The PlayStation 7 controller can enable a consoless gaming experience by leveraging its innovative hardware features, which allow it to function independently from the console in a variety of ways:
Integrated 8K HD LCD Mirror Screen
Description: The high-resolution 8K LCD screen built into the controller displays full gameplay visuals without needing a TV or separate monitor.
Functionality: This screen allows users to play games directly on the controller, effectively transforming it into a standalone gaming device when paired with online gaming capabilities.
AI Self-Learning System
Description: The controller’s AI learns player preferences, adapts control settings, and customizes responses based on gameplay style.
Functionality: This allows for quick, user-specific adjustments without external inputs, creating a more personal and tailored gaming experience even without a console.
Embedded Processing and Networking Capabilities
Description: Equipped with processors for basic game streaming and internet connectivity via WiFi, Bluetooth, and FiWi.
Functionality: The controller can stream games from the cloud or connect to local servers. It essentially functions as a portable gaming device by accessing games directly from cloud platforms.
Modular Connectivity Ports (HDMI and USB)
Description: With HDMI, USB, and charging ports, the controller supports multi-functional connectivity.
Functionality: It can connect to external monitors, TVs, or displays, allowing players to shift seamlessly between small-screen (on-controller) and larger-screen gaming without needing a console.
Advanced Bluetooth and FiWi for Peripheral Pairing
Description: The controller’s Bluetooth and FiWi capabilities enable pairing with additional devices like headphones, VR headsets, or external gamepads.
Functionality: This gives players access to an entire peripheral ecosystem without a console. It supports multiplayer and VR applications by connecting directly to other devices.
Cloud-Based Gaming Infrastructure
Description: The controller is designed to leverage cloud gaming services, with an interface that allows game downloads, storage management, and updates.
Functionality: Users can access and play titles stored on cloud servers directly from the controller, offering console-like gameplay with portability.
Standalone Battery and Power Management System
Description: High-capacity battery allows for extended gameplay time.
Functionality: Without dependence on an external power source, the controller can function as a self-sufficient gaming device, giving players freedom to game from anywhere.
Specialized Sensor Array for Immersive Gameplay
Description: Sensors for motion, orientation, and grip provide feedback and allow for intuitive controls.
Functionality: The sensors support games that require movement and responsiveness without additional hardware, further enhancing the controller’s ability to stand alone as a gaming platform.
Through these innovations, the PlayStation 7 controller essentially acts as a mini console. Its blend of display technology, AI, processing power, connectivity, and cloud gaming access brings a full gaming experience into a single compact device.
#Playatation7#CandyPaintJobDyeCastLoRiderYellow Controller#Yellow controller#special Edition#LoRiderYellow#PaintJobYellow#Playstation7Controller#Special edition#Exclusive#DigitalConsole#consolessGaming
3 notes
·
View notes
Text
How to Connect Your TON Wallet to STON.fi: A Simple Step-by-Step Guide

Hey there! If you’re new to crypto and looking to make your first move with STON.fi, one of the first things you need to do is connect your TON wallet to the platform. It might sound a bit technical at first, but trust me—it’s not as complicated as it seems. Think of this as your crypto "starter guide." Follow these steps, and you’ll be ready to go in no time.
Why You Need to Connect Your Wallet
Before we dive into the how, let’s first cover the why. Your TON wallet is like a digital safe where you keep your cryptocurrency. Without it, you can’t really do much on platforms like STON.fi. Connecting it to STON.fi is like unlocking the door to a new world of opportunities—trading, swapping, and even staking your crypto. So, let's get you set up!
Step 1: Open the STON.fi App
First thing's first, head over to the STON.fi app. You can do this by clicking here. Think of this as walking into a new store—you want to make sure you’re in the right place before you start browsing.
Step 2: Click "Connect Wallet"
Once you’re on the app, look for the "Connect Wallet" button. It’s usually easy to spot, but if you don’t see it right away, just take a second to look around. Clicking it is like opening the door to your vault—this is where you’ll be able to access your crypto and start interacting with the platform.
Step 3: Choose Your Wallet
A window will pop up asking you to select your wallet. Don’t worry if you don’t see your wallet right away—just click "View all wallets." This will show you a more complete list of supported wallets. If your wallet is still not showing up, no stress! We have an easy guide to help you get your wallet set up.
Step 4: Scan the QR Code
Next up, a QR code will appear. Open your TON wallet, find the scan option, and scan the code. It’s kind of like connecting your phone to Bluetooth—you just need a quick scan to get everything in sync.
Step 5: Confirm the Connection
Once the scan is successful, your wallet will ask for your confirmation to connect. Go ahead and hit “Confirm,” and just like that, your wallet is now linked to STON.fi! Your wallet will stay connected until you decide to disconnect or clear your browser cache. Easy, right?
What Happens After You Connect
Now that your wallet is connected, you’re ready to start exploring. Whether you want to swap tokens, stake your assets for rewards, or dive into some other DeFi opportunities, your connected wallet unlocks all of that.
Is It Safe
I get it—security is a big concern when dealing with your hard-earned crypto. The cool thing about STON.fi is that you’re always in control. Your wallet stays in your hands, and only you can access it. The QR code connection is encrypted, and STON.fi doesn’t store your crypto, so it’s not at risk. It’s like locking your funds in a secure safe—only you have the key.
The Power of a Connected Wallet
Once your wallet is connected, you’re no longer just an observer in the crypto space. You’re a player! This connection allows you to explore all kinds of options, from trading tokens to earning rewards through staking. Think of it like entering a playground where you control the rules.
Analogies to Make It Easier
Still unsure? Let’s simplify it a bit more. Imagine you’re opening a new bank account. You fill out a few forms (set up your wallet), and then you’re asked to verify your identity (scan the QR code). Once you do that, you can access all the services the bank has to offer—transfers, savings, loans. Similarly, once you connect your TON wallet to STON.fi, you gain access to the platform’s features and can start using your crypto the way you want.
It’s kind of like switching from traditional banking to a system where you’re the one in charge. You hold the keys, and you decide how and when to access your funds.
Wrapping Up
Connecting your TON wallet to STON.fi is the first step toward taking control of your crypto. Whether you’re just getting started with DeFi or you’re a seasoned investor, the process is simple and secure. Once you’re connected, you’ll have access to a whole new world of opportunities, from trading to staking, and even exploring the TON blockchain.
Remember, it’s all about learning and growing at your own pace. So take your time, follow the steps, and soon enough, you’ll be navigating the DeFi world like a pro. Let’s get you started!
3 notes
·
View notes
Text
How Increased Surveillance by the China Government during the Global COVID-19 Pandemic Affects Online Communities?

In the wake of the global COVID-19 pandemic, governments worldwide, including China, intensified surveillance measures to curb the virus's spread. In this context, China's implementation of stringent surveillance, notably through Health Code Apps, has raised profound concerns about its impact on online communities. As facial recognition and data collection become intrinsic to daily life, the potential repercussions on digital spaces and the people within them demand careful examination. This discussion delves into the multifaceted consequences of increased surveillance by the Chinese government and its tangible effects on the dynamics of online communities.
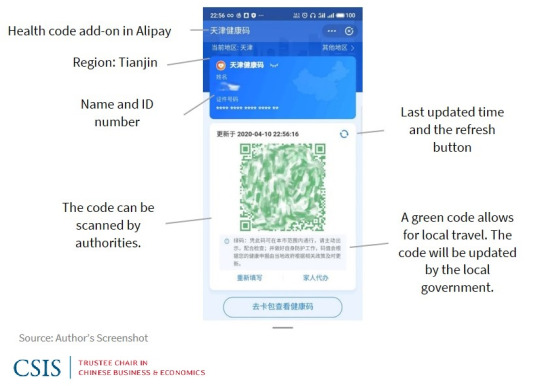

Privacy Erosion
In response to the global COVID-19 pandemic, various countries implemented measures to track and control the virus's spread, introducing tools such as contact tracing apps (Ojokoh et al., 2022), temperature checks (Qu & Lv, 2021) and travel restrictions (Burns et al., 2021). Simultaneously, In China, where stringent surveillance measures were already in place, the government leveraged technology to an even greater extent, using facial recognition and health QR codes to monitor citizens' movements. This involved the deployment of a series of applications known as "Health Code Apps," which have raised concerns about privacy erosion, particularly regarding the use of health code applications. Online communities are not immune to this erosion, as the data collected through these apps includes personal information, health status, and location details. This data is then utilized to assign one of three colours, indicating the user's health status (Ramos, 2020). However, Data is funnelled to entities like the provincial Big Data Bureau, Alibaba, and the telecommunications department, expanding the accessibility to user information, ranging from personal details to health status, location, and device specifics. This centralized model amplifies the risks of data aggregation and user re-identification, exemplified by the Beijing Health Bao system's data leak in December 2020. The incident exposed the photographs, ID numbers, and nucleic acid test information of celebrities, highlighting insufficient safeguards in place (Zhang, 2022). Online communities may find their members exposed to privacy breaches, leading to a chilling effect on open communication and expression within these digital spaces.

Potential for Abuse of Power:
The potential for the abuse of power in the context of surveillance, inadequate transparency and compliance measures is a significant concern for online communities as well. This concern is exemplified by recent events in Henan Province, where health code apps were allegedly manipulated to suppress protests related to potential losses in rural banks on the brink of collapse (Zhang, 2022). The legitimacy of these health code apps faced a setback as city officials marked over a thousand individuals as red, restricting their entry into Zhengzhou City and highlighting the vulnerability of such systems to misuse (Zhang, 2022). This incident underscores the potential for health code apps, initially designed for public health purposes, to transform into tools of surveillance, allowing government agencies to exert control under the guise of maintaining public health. The lack of stringent transparency requirements heightens the risk of these technologies being misused for purposes beyond their intended scope, which negatively impacts the freedom of expression within online communities. As governments exploit surveillance tools to monitor and influence online discussions, online communities may face challenges related to censorship and control, further emphasising the interconnected nature of surveillance concerns and their impact on digital spaces.
Technological Dependence:
Embracing extensive surveillance often involves a reliance on advanced technologies. In the case of Health Code Apps, facial recognition technology is integrated into residential area access control systems, permitting entry only to those with a green code (Ramos, 2020), which has implications for online communities. This reliance on advanced technologies may neglect more human-centric approaches to online interaction, potentially excluding or disadvantaging certain members of digital communities. As surveillance technologies become integral to online platforms, the balance between security measures and preserving the inclusivity and diversity of online communities becomes a critical consideration.
Trust Deficit:
The colour-coded system assigned by health code applications has far-reaching consequences for millions of users in their interactions within both physical and online communities. Requiring individuals to display their health codes in public transportation, shopping malls, markets, and other public places may contribute to a trust deficit between citizens and the online platforms they engage with (Jao et al., 2020). Users within online communities may question the motives behind such surveillance measures, especially if their personal information is shared without their knowledge. Rebuilding trust within online communities, once eroded by mandatory health code reliance, poses a considerable challenge, impacting the dynamics of digital social spaces.
In conclusion, the surge in surveillance by the Chinese government amid the global COVID-19 pandemic undeniably leaves a lasting imprint on online communities. The colour-coded system mandated by health code applications not only infiltrates public spaces but also infiltrates the very essence of digital interactions. This imposition triggers a tangible trust deficit within online communities as individuals question the motives behind these surveillance measures. Rebuilding trust within these virtual spaces, essential for vibrant and open communication, becomes a formidable challenge in the aftermath of mandatory health code reliance. The delicate equilibrium between bolstering security measures and safeguarding the inclusivity of online communities emerges as the linchpin for preserving the dynamic and diverse nature of these digital spaces. In essence, the impact of increased surveillance by the Chinese government is intimately intertwined with the well-being and resilience of online communities.
"Considering the implications of increased surveillance by the Chinese government during the global COVID-19 pandemic on online communities, we'd like to hear your perspective. How do you perceive the effects on privacy erosion, potential abuse of power, technological dependence, and the trust deficit within these digital spaces? Share your insights and cast your vote below."
Reference List
Burns, J., Movsisyan, A., Stratil, J. M., Biallas, R. L., Coenen, M., Emmert-Fees, K., Geffert, K., Hoffmann, S., Horstick, O., Laxy, M., Klinger, C., Kratzer, S., Litwin, T., Norris, S. L., Pfadenhauer, L. M., Von Philipsborn, P., Sell, K., Stadelmaier, J., Verboom, B., . . . Rehfuess, E. (2021). International travel-related control measures to contain the COVID-19 pandemic: a rapid review. The Cochrane Library, 2021(3). https://doi.org/10.1002/14651858.cd013717.pub2
Jao, N., Cohen, D., & Udemans, C. (2020). How China is using QR code apps to contain Covid-19. TechNode. https://technode.com/2020/02/25/how-china-is-using-qr-code-apps-to-contain-covid-19/
Ojokoh, B. A., Aribisala, B. S., Sarumi, O. A., Gabriel, A. J., Omisore, O. M., Taiwo, A. E., Igbe, T., Chukwuocha, U. M., Yusuf, T. A., Afolayan, A., Babalola, O., Adebayo, T., & Afolabi, O. (2022). Contact Tracing Strategies for COVID-19 Prevention and Containment: A scoping review. Big Data and Cognitive Computing, 6(4), 111. https://doi.org/10.3390/bdcc6040111
Qu, J., & Lv, X. (2021). The response measures to the coronavirus disease 2019 outbreak in China. Open Forum Infectious Diseases, 8(2). https://doi.org/10.1093/ofid/ofab014
Ramos, L. F. (2020). Evaluating privacy during the COVID-19 public health emergency. The ACM Digital Library, 176–179. https://doi.org/10.1145/3428502.3428526
Zhang, X. (2022). Decoding China’s COVID-19 health code apps: the legal challenges. Healthcare, 10(8), 1479. https://doi.org/10.3390/healthcare10081479
4 notes
·
View notes
Text
Modern Paperless Registration Technologies to Make Your Event Successful
In recent years, the event industry has completely transformed how events are executed. Earlier execution of events used to take months, in the case of event registration and ticketing. The audience used to stay in long waiting lines to book their slot for the event. But gone are the days of long queues and waiting lines. The event industry has revolutionized in terms of event planning. Numerous modern paperless event registration technologies have been introduced to make your registration and ticketing process seamless and smooth.
In this blog, we are going to discuss modern paperless solutions for event registration and ticketing. So without further ado, let’s start:
Paperless Event Registration Technologies
There’s no doubt that everyone is opting for paperless solutions for their events. Here’s a list of paperless solutions that you can consider for your events.:

1. Online Registration Portals
Modern events start with online registration portals. These user-friendly platforms allow the audience to register for your event from their comfort zone. Online registration eliminates the need for paper forms and manual data entry. It streamlines the process and reduces the risk of errors. Attendees can provide all the necessary information, from personal details to dietary preferences, at their convenience.
Moreover, online registration portals offer real-time data tracking of whole event registrations, giving event organizers instant insights into attendee numbers and demographics. This data enables better planning and marketing decisions. Also, it ensures that your event is tailored to your audience's needs.
2. Mobile Event Apps
Mobile event apps have become indispensable tools for event planners and attendees alike. These apps offer a paperless approach to event management, providing attendees with all the information they need at their fingertips. Features often include event agendas, speaker profiles, interactive maps, push notifications for updates or changes, a 360-way finder and much more.
Additionally, mobile event apps facilitate networking by allowing attendees to connect with one another digitally. Attendees can exchange contact information, schedule meetings, and participate in interactive sessions or polls through the app.
3. QR Codes for Check-In
QR codes have become a staple in modern event registration. Attendees receive unique QR codes via email or mobile apps upon completing their registration. These QR codes serve as digital tickets and can be scanned at entry points, allowing for quick and contactless check-in. This technology reduces wait times and enhances security by ensuring that only registered attendees gain access.
Event organizers benefit from QR codes as well. They can track attendance in real-time, helping to manage session capacities and optimize resources. Moreover, QR codes provide valuable data insights, such as attendance patterns and peak entry times, which inform decision-making for future events.
4. Digital Badge Printing
Traditional printed badges are being replaced by digital badge printing solutions. These systems generate badges on-site, complete with attendee names, affiliations, and any other relevant information. Digital badges are not only eco-friendly but also allow for real-time corrections and updates. If an attendee's details change, the badge can be quickly reprinted without hassle.

Furthermore, digital badge printing systems can incorporate features like RFID or NFC technology. These badges can be used for session tracking, access control, and interactive experiences, providing event organizers with valuable data and attendees with enhanced engagement opportunities.
5. e-Tickets and Mobile Wallet Integration
e-tickets are another paperless alternative that enhances the attendee experience. Attendees receive electronic tickets via email, which can be stored in their mobile wallets. These e-tickets are easily accessible and eliminate the need for physical tickets. Attendees can present their e-tickets for entry by simply displaying them on their smartphones. This technology also supports last-minute event registrations and changes. Attendees can receive e-tickets instantly, even on the day of the event, making it convenient for both organizers and late registrants.:
6. Efficient Access Control with RFID Technology
RFID technology has gained prominence in modern event registration due to its efficiency and versatility. RFID badges or wristbands contain embedded RFID chips that can be scanned remotely using RFID readers. This technology offers seamless access control, as attendees can simply walk through RFID-enabled entry points without the need for physical scanning or manual checks.

The benefits of RFID technology in event registration are numerous. It reduces entry bottlenecks, allowing for swift and hassle-free access for attendees. Organizers can track attendance in real time, monitor session participation, and gather valuable data on attendee movement throughout the event venue. Incorporating RFID technology into your paperless event registration system not only streamlines access control but also contributes to a more efficient and secure event environment, ultimately enhancing the success of your event.
7. Virtual Attendee Check-In
For hybrid or fully virtual events, modern paperless registration technologies extend to virtual attendee check-in. Attendees can access virtual event platforms with ease using unique login credentials provided during registration. This eliminates the need for physical check-in points and allows attendees to participate from anywhere in the world.
Virtual check-in also enables event organizers to monitor attendee engagement during virtual sessions. They can track attendance, participation in polls or Q&A sessions, and resource downloads. This data informs post-event analytics and helps tailor future virtual events to attendee preferences.
8. Data Analytics and Reporting Tools
Modern paperless registration technologies come equipped with robust data analytics and reporting tools. Event organizers can access detailed reports on attendee demographics, registration trends, session popularity, and engagement metrics. These insights enable organizers to make data-driven decisions, refine marketing strategies, and continuously improve event experiences.
Additionally, reporting tools support post-event evaluations, helping organizers assess the event's success and identify areas for enhancement. The ability to gather and analyze data efficiently is a cornerstone of event success in the digital age.
Moreover, the data insights generated by these technologies allow for more targeted marketing efforts, reducing marketing expenses and improving the return on investment (ROI) for event promotions.
Conclusion
By the end of this blog, we know that in a world where efficiency, convenience, and sustainability are paramount, modern paperless registration technologies have become indispensable tools for event organizers. These technologies not only simplify the event registration process but also enhance attendee experiences, provide valuable data insights, and support environmental sustainability efforts. Embracing these innovations is a strategic move that can elevate your event, making it more successful and aligning it with the expectations of today's digital-savvy attendees. I hope you like the blog. Thank you for reading.
2 notes
·
View notes
Text
Earlier this month, Russia’s State Duma and Federation Council passed a new military conscription law. The bill, approved on an expedited basis, was designed to close the remaining loopholes that until then permitted the most determined of draft-dodgers to escape military duty. The new law enables the Defense Ministry to distribute digital summonses, also restricting the draft evaders’ ability to leave the country. Russia is now set to develop a unified digital register containing comprehensive personal data on every male citizen subject to military duty. Observers were quick to call the new system a “digital gulag,” but government officials greeted the new data project with enthusiasm, not least thanks to its gargantuan anticipated budget. Meduza’s correspondents Andrey Pertsev and Svetlana Reiter investigate who will benefit from building a new digital system of mass control.
Russia’s Ministry of Digital Development is undertaking a new task, thanks to the new conscription law requiring the creation of a unified information system for comprehensive data on every male citizen subject to military duty. The data, it’s expected, will be at the Defense Ministry’s fingertips during the regular seasonal conscription drives, as well as in the event of possible mass mobilization.
An informed source in the government, as well as a second speaker in the telecommunications sector, both told Meduza that Rostelecom, the Digital Development Ministry’s largest data systems contractor, is bruited to be tasked with the new government data project.
Two government insiders were able to further tell Meduza that the Rostelecom subsidiary RT Labs will be directly responsible for building the military conscription register. On April 11, when the new conscription law was passed by legislators, RT Labs was quick to post a number of new jobs available in the company, including, for instance, a data engineer position specifically mentioning work on the state bureaucracy website Gosuslugi (“State Services”). Under the new law, this website has a critical new function of distributing electronic draft summonses via its built-in messaging system.
RT Labs already services Gosuslugi and other state data systems, as well as the Unified Identification and Authentication System (“ESIA”) used by a number of branches of the digital state bureaucracy. RT Labs’ motto, “State Services R Us,” is quite clear about its role in government data systems.
The present CEO of RT Labs, Tengiz Alania, joined the company after serving as the deputy director of Moscow’s Regional Center for Information and Communication Technologies, another data-management enterprise servicing the government. Another top executive still working at the center, Evgeny Kovnatsky, shares a full name with someone who had been in charge of Donbas Post, a postal service started by the Russia-sponsored separatist governments in Ukraine back in 2015.
Another major player in the creation of the conscription register is Maksut Shadayev, the former RT Labs CEO and now Russia’s Minister of Digital Development. Shadayev’s career trajectory included a stint as an advisor to Vladimir Putin’s Deputy Chief of Staff Sergey Kiriyenko, and later a stretch of working at Rostelecom. When appointed minister in 2020, Shadayev championed the Gosuslugi Stop Coronavirus QR-code verification program. Early in his appointment, he also proposed giving the state law-enforcement and security apparatus complete access to Russian citizens’ personal data. (Later, he denied having ever suggested this, claiming others had misunderstood him.)
A government insider who spoke with Meduza told us that federal officials led by Prime Minister Mikhail Mishustin and his deputy, Dmitry Chernyshenko, greeted the idea of a unified conscription register with “great enthusiasm.” It was Mishustin, after all, who had digitized Russia’s tax service prior to being appointed prime minister. During a closed meeting within the Presidential Administration, Mishustin and Chernyshenko assured the Defense Ministry that the comprehensive register the military wanted could be created in practice. “Of course we can! We’d be happy to make it,” they said there and then.
This eagerness, the same speaker tells us, can hardly be separated from the truly gargantuan budget reputed to be allocated for the new data project. This is likely to be “tens of billions or rubles,” he says. Forbes Russia also estimates that the project will cost “billions of rubles” (that is, hundreds of millions of U.S. dollars).
A telecom industry insider who spoke with Meduza believes the contract is going to be a major “headache” for Shadayev and his team. “The deadlines are unreal, and the responsibility is huge. The FSB is overseeing all the work, but if the deadline is broken, they’ll just blame the Digital Development Ministry and Rostelecom,” he says. (Shadayev himself had said that the earliest the new system could be expected to go live would be the fall 2023 conscription drive.)
Despite the hasty adoption of the new conscription law, the Kremlin insiders who spoke with Meduza still disclaim any knowledge of any high-level talk about another round of mobilization. At the same time, mobilization and mandatory conscription appear to be the only way to achieving the Defense Ministry’s recruitment goals, particularly if its plan really is to recruit 400,000 men, as reported by Bloomberg back in March.
A government insider in one of Russia’s largest regions explains that the Kremlin is still hopeful about recruiting enough contract soldiers to avoid a new round of mobilization. “We have ads and banners everywhere,” he says, adding that “the task” is to “maximally motivate” men to join the army.
An informed source close to the Putin administration says that around 10,000 contract servicemen were recruited since last winter in the Moscow region alone. “People keep coming in,” he said, adding: “The draft offices see 200–300 people coming in on their own, every day. They come for the money.”
4 notes
·
View notes
Text
Brief 8 - "Enerjeopardy"
What is Enerjeopardy?
Story video for BEFORE visit.
youtube
This video is to create an immersive experience and mood. This is also to lay down the plot and give reason for what is going to happen.
Story + Rules video for AFTER visit.
youtube
Video contains short summery of what happened in the last episode and explains the rules of the game.
Here we would like to add pictures and video overlays to visually explain the game rules with examples.
Sparring and coding with ChatGPT
To develop the digital experience i used ChatGPT as a sparring partner and coding partner. In this proses i have learned a lot more about how i should structure my prompts to get the most out of ChatGPT. It was quick and gave good results. I feel like there is even more potential to further explore! (which is crazy...)
User testing
On Friday 19th we did our user test at Teknisk Museum with secondary school students. Here we confirmed that our concept had ground, and could be further developed. The students found the game interesting and inviting, though i took a few questions to get then started. The sounds on the buzzers and the game had great reactions and the students had a good laugh. After, we made some minor tweaks and got to working on our presentation.
its a shame we didn't get to the testing earlier, as i feel the final result could have looked different and had the finish i wanted. For i being a prototype and proof of concept i am pleased with the result we got. I feel like with more time and development Enerjeopardy could be a interesting and inviting experience.
All in all i am pleased with the results!
The game
http://occstudio.com/enerjeopardy/

The idea is that everything is easy access, with everything being in one place.



The game operates like the game show Jeopardy, where the questions are designed as statements, and the answers must be in the form of a question. The students choose their own category and difficulty level, and they receive building blocks for their nuclear power plant every time they reach 400 points. The winner is the first group to reach 1500 points and complete their nuclear power plant! Scoring system and questions are to be displayed on a Smartboard or any form of classroom screen. (Teacher controls this)
Buzzers
http://occstudio.com/enerjeopardy/buzzer.html
http://occstudio.com/enerjeopardy/buzzer2.html
http://occstudio.com/enerjeopardy/buzzer3.html Buzzers are easily available through qr codes that are to be displayed before the game show starts.
Presentation
Our presentation
3 notes
·
View notes
Text
The Top Enterprise Mobility Management Solution for 2023

Enterprise mobility management is an integral cog in a business machine. A company with a large fleet of mobile devices under its workforce would need a system to keep these devices in check. Especially when a corporate handle BYOD.
Enterprise mobile device management is the best bet to do that. It allows corporates to control, manage, and monitor the mobile devices under them, and evaluate employee mobile behaviour efficiently. However, when it comes to choosing the best enterprise mobility management solutions, it can get quite confusing.
EMM solutions are an evolving set of technologies that carry varied features depending upon the requirement of a business. So how can you choose the best enterprise mobility management (EMM) software for your business?
That’s not too difficult if you know what your company’s requirements are and what type of EMM solutions suits you best. For instance, one of the best enterprise mobility management solutions in the market is Tabnova’s NovaEMM.
NovaEMM
Tabnova’s NovaEMM houses a suite of features and administrative control, which also includes the ability to centrally and remotely control the use of mobile devices in workplaces under corporate mobility guidelines. This enterprise mobility management system brings in elements like application management, enrolment, security, remote monitoring, etc.
Let’s take a brief look into these features:
1. Application Management: With NovaEMM, the company can control how applications are used by the end user. They can decide which applications should be downloaded from Play Store, and which applications are to be blacklisted from being downloaded. Moreover, the enterprise mobile device management system has the ability to access corporate networks and interact with them. With such a system in tow, the company can even set auto-update policies and choose which software version should play on the corporate devices.
2. Enrolment: NovaEMM makes it easy to deploy any software or application onto corporate-owned devices. Android Enterprise enrolment and KNOX mobile enrolment are quite easily done, along with clientless enrolment using QR codes.
3. Security: There is comprehensive security for devices through various features, like password enforcers. The fleet of mobile devices can be controlled to determine which applications need to be given access. Moreover, if any device is stolen or lost, or missing, then the administrator can impose a lockdown on that specific device and ensure that the data within the device is not lost or stolen in any manner.
4. Remote Monitoring: With Tabnova’s suite of EMM, the administrator can screen share any data that is needed onto the fleet of mobile devices under them. Additionally, the admin can set up alerts as well as a messaging system that will deliver any information or data required to the fleet of devices under the company policy.
5. Compliance: Tabnova’s EMM system ticks off all the regulatory standards and is GDPR compliant. There are data protection agreements set in place to prevent any theft of data or unauthorised use of information. When following the GDPR regulations, there are a few protocols in place:
· Enforcing Passcode requirements
· Data encryption on a device
· Deploy and Enforce settings and restrictions
· Separate work and personal space on a device
· Wipe sensitive information
· Blacklist applications
· Generate reports for data security
· Factory reset stolen devices
Benefits of NovaEMM
When you start using NovaEMM, you are treated to a host of benefits, from affordability to robust security. Let’s look at what advantages a company can reap from using NovaEMM.
1. Multiple Kiosk Options: You can set up any type of desired Kiosk, like a Single App Kiosk, Browser Kiosk, Dashboard Kiosk, and Video Looper Kiosk.
2. Multiplatform Support: NovaEMM is capable of efficiently functioning on any platform, be it Android, MacOS, iOS, Windows, etc.
3. Enterprise Apps: You are able to access a suite of enterprise apps that comes with NovaEMM. These apps can be deployed according to company requirements as and when required.
4. DRM Content Delivery: Any online content, be it audio or video, that is used for live streaming can be encrypted and DRM protected to prevent piracy and unauthorised use.
With NovaEMM, businesses can manage and protect their mobile devices without any hassles, while enhancing their employee productivity, and that too at an affordable cost. While Tabnova is a leading provider of EMM software, there are other peers in the market as well.
Some of the other best enterprise mobility management (EMM) software that is available include the following – Codeproof, Amtel, Filewave, IBM, Microsoft EMM, Manage Engine, SOTI, Ivanti, VMware AirWatch, Miradore, Sophos, Scalefusion.
Contact us
Email Us
For More Information Click here
2 notes
·
View notes
Link
#visitor management system#visitor access control systems#visitor registration software uae#Visitor Management System For Schools#visitor management solutions in uae#qr code visitor access control systems abu dhabi#visitor registration software abu dhabi#visitor registration systems in uae#visitor management systems#visitor registration software in uae#visitor registration software in dubai#visitor access control systems in bur dubai#visitor management system in ajman#visitor management systems in abu dhabi#visitor registration system in uae#visitor registration system in alain#visitor management software in abu dhabi
0 notes
Text

Introduction to Andon System
An Andon system is a powerful visual and auditory communication tool designed to enhance manufacturing processes by providing real-time updates on operational performance. Its core purpose is to ensure seamless communication between operators, supervisors, and management, enabling swift identification and resolution of issues on the production line. This proactive approach minimizes downtime, improves quality, and drives overall efficiency, making the Andon system a cornerstone of lean manufacturing practices.
Usages of Andon System
Andon systems are versatile and widely adopted across industries to streamline operations, improve quality control, and ensure safety. Here are some key applications:
Production Monitoring: Real-time status updates on production lines, including operational status, downtime, or issues, help teams respond promptly and maintain efficiency.
Quality Control: Alerts about defects or inconsistencies ensure immediate corrective action, reducing waste and improving product quality.
Maintenance Management: Automated alerts notify maintenance teams of equipment malfunctions, enabling quick fixes and minimizing disruption.
Inventory Tracking: Keeps track of material levels and alerts when replenishment is needed, ensuring uninterrupted production.
Safety Alerts: Enhances workplace safety by signaling hazards or emergency stops with clear visual and auditory cues.
Lean Manufacturing: Supports lean initiatives like just-in-time production and kaizen by improving transparency and reducing inefficiencies.
Remote Monitoring: Allows supervisors to oversee operations remotely, ensuring effective management across large facilities or multiple sites.
Continuous Improvement: Highlights recurring bottlenecks and inefficiencies, providing data-driven insights for process optimization.
From automotive and electronics to pharmaceuticals and heavy machinery, Andon systems are indispensable for industries striving for operational excellence. Their ability to adapt to diverse environments and applications makes them an essential tool for achieving manufacturing efficiency, quality, and safety.
Wi-Fi Connection
Easily monitor connectivity and ensure the system is ready for Andon alerts

Signal Status:
Connected: A signal icon displays Wi-Fi strength in the top-right corner.
Disconnected: The signal icon turns red, indicating a lack of connection.
Wi-Fi Connection Process:
Connect to Wi-Fi: Users enter the Wi-Fi SSID and password to initiate the connection.
Successful Connection:
The system displays the Segment Name to confirm the correct network.
A Tower Light indicator changes to green, confirming a successful Wi-Fi connection.
Red Andon

Yellow Andon
Red and Yellow Andon

Out of many Andons that function in a plant, no matter how many display Yellow Indication, even if one of them displays Red Indication, the tower light will indicate only red.
If there is no red indication amongst any of them, the the Tower light shall display Yellow Indication only.


User Login
Easily monitor connectivity and ensure the system is ready for Andon alerts
Enter Credentials:
Input your Username (ADID) and Password.
Click Sign In:
Press the Sign In button. Single Role Handling:
If you have a single role, you will be redirected directly to the Scan Page.
Multiple Roles Handling:
If you have multiple roles, a dropdown will appear. Select your desired role from the dropdown. Click the Sign In button again.
Dashboard Access:
Based on the selected role, you will be redirected to the corresponding Dashboard.
QR Code Integration for JIG Management

Effortlessly manage and access JIG information with our QR Code functionality.
How It Works:
Unique QR Codes: Every JIG is assigned a separate QR Code.
Seamless Access: Scanning the QR Code redirects the user to their personalized Dashboard.
Access Control: If the QR Code does not correspond to the JIG, a message will be displayed.
Message: “This User cannot access the JIG.”
Red and Yellow Andon

List of Raised Andons Each Andon is categorized by color, providing clear visibility of issue types and their status.
Color-Coded Categories:
Yellow: Represents Medium Issues Easily identify and address Medium challenges Track and manage these issues efficiently
Red: Represents Critical Issues Highlights urgent critical concerns Monitor and resolve material critical swiftly
Raising the Andon
Our intuitive interface allows users to quickly raise Andons and report issues efficiently.
Key Features:
Fault Description: Users can select from a predefined list of fault descriptions to ensure accurate reporting.
Color Selection: Choose the appropriate color category to categorize the Andon correctly. Auto-Populated
Plant Name: Once logged in with the correct credentials, the user’s designated Plant Name will be automatically populated for seamless operation. Simplify issue reporting and improve communication across your plant with our user-friendly Andon system.
SMS Alert for Raised Andons
Red Andon
Alerts: Escalation SMS Work stoppage due to Issue-1 at work center Status – Red (Stage Name) from 08/03/2024 02:48 PM
Regards,
TASL- IT
Yellow Andon
Alerts: ASL C295-MCA , Potential Production stoppage due to Issue-1 at work center Status – Yellow (Stage Name) from 08/03/2024 02:46 PM
Regards,
TASL- IT
0 notes
Text
Label Printing Made Easy: A Guide to Choosing the Right Software
In today’s fast-paced business environment, effective labeling is essential for product identification, branding, compliance, and logistics. Whether you’re a small business packaging handmade goods or a large corporation managing inventory and shipping, the right label printing software can make a world of difference.
Labels are the face of your product, and creating high-quality labels efficiently requires a combination of the right software and reliable hardware like a label printer. At Labels & Labeling Co. LLC Dubai, we understand the importance of precision and efficiency in label printing. This guide will help you choose the best label printing software for your business needs.
Why Label Printing Software Is Essential
Label printing software is designed to simplify the creation and printing of labels for a variety of purposes. From barcodes and shipping labels to product branding, the software enables businesses to design labels that are professional, consistent, and compliant with industry standards.
Key benefits include:
Customization: Create designs that align with your brand identity. Efficiency: Save time with user-friendly templates and bulk printing options. Accuracy: Ensure proper alignment and precision for barcodes, QR codes, and text. Scalability: Handle everything from small batches to large-scale printing operations.
Factors to Consider When Choosing Label Printing Software
Ease of Use The best label printing software should be intuitive and easy to use, even for beginners. A user-friendly interface, drag-and-drop features, and pre-designed templates can save you time and effort.
Compatibility with Label Printers Ensure the software is compatible with your existing label printer. Many software solutions are designed to work seamlessly with specific printer brands or models, so check the specifications before making a purchase.
Customization Features Choose software that allows you to customize every aspect of your label, from fonts and colors to logos and layouts. Advanced options like variable data printing are ideal for creating unique labels for each product or shipment.
Support for Barcodes and QR Codes Barcode and QR code integration is essential for industries like retail, logistics, and healthcare. Look for software that supports a wide range of barcode types and offers tools to ensure proper sizing and alignment.
Integration with Business Systems If your business uses inventory management, ERP, or e-commerce platforms, opt for software that integrates seamlessly with these systems. This feature can automate data entry and streamline label creation.
Cloud-Based vs. On-Premises Cloud-based software offers the advantage of remote access and automatic updates, while on-premises solutions provide more control and data security. Choose the option that aligns with your business needs.
Cost and Licensing Consider the pricing model—some software options require a one-time purchase, while others operate on a subscription basis. Evaluate your budget and the features offered to ensure you’re getting value for your investment.
Customer Support and Training Reliable customer support can be invaluable, especially if you encounter technical issues. Look for software providers that offer training resources, tutorials, and responsive support teams.
Top Features to Look for in Label Printing Software
Pre-Designed Templates: Save time with ready-to-use templates for common label types like shipping labels, product labels, and barcodes. WYSIWYG Editor: A “What You See Is What You Get” editor allows you to preview exactly how your label will look before printing. Batch Printing: Print large volumes of labels quickly and efficiently. Multi-Language Support: Ideal for businesses operating in multilingual markets. Custom Sizing Options: Create labels of any size to fit your specific products or packaging.
Pairing the Right Label Printing Software with a Quality Label Printer
Even the best software requires a reliable label printer to deliver professional results. Labels & Labeling Co. LLC Dubai offers a range of high-performance label printers that are compatible with leading software solutions.
Key features of our label printers include:
High-resolution printing for sharp text and images. Fast printing speeds for high-volume operations. Durable construction for long-term reliability.
Why Choose Labels & Labeling Co. LLC Dubai?
As a trusted provider of labeling solutions, Labels & Labeling Co. LLC Dubai is committed to helping businesses achieve efficiency and precision in their labeling operations. We offer:
Expert Guidance: Our team can help you choose the right software and printer for your specific needs. High-Quality Products: From advanced label printers to premium printing materials, we provide everything you need for flawless labeling. Comprehensive Support: We’re here to assist with setup, troubleshooting, and ongoing maintenance. Custom Solutions: Whether you’re a small startup or a large enterprise, we can tailor our offerings to suit your requirements.
Conclusion
Label printing doesn’t have to be complicated. With the right label printing software and a reliable label printer, you can streamline your operations, enhance your brand image, and meet industry standards with ease.
At Labels & Labeling Co. LLC Dubai, we’re dedicated to providing innovative solutions that make labeling simple and efficient. Contact us today to explore our range of software, printers, and expert services to take your labeling process to the next level.
Let us help you create labels that speak volumes about your brand.
0 notes