#preventing flag misuse online
Explore tagged Tumblr posts
Text
Website : https://www.honorourflag.us
Honor Our Flag is dedicated to preserving the dignity and significance of the U.S. flag, particularly in the context of half-staff honors. The initiative advocates for a more respectful and meaningful approach to honoring citizens, emphasizing the importance of the flag as a symbol of national values and pride. By proposing changes to the U.S. Flag Code, Honor Our Flag seeks to restore the honor of this special gesture, ensuring it remains a powerful tribute to those who have truly served the nation.
Keywords: flag honor reform initiatives respecting the national flag u s flag protocol guidelines dignity in national flag display significance of half staff flag flag code revision updates patriotic flag respect principles integrity in flag tributes american flag pride advocacy understanding flag lowering guidelines preserving flag honor online awareness of flag etiquette advocating for flag code updates display principles for the flag honoring true service with flags preventing flag misuse online restoration of national pride raising awareness for flag respect criteria for flag lowering respecting the flag with tribute modernization of flag code reverence for the national flag reform in flag lowering practices awareness campaigns for flag honor advocacy for flag display protocols for flag lowering tribute initiatives for the national flag online awareness for flag respect initiatives for flag lowering reform uplifting national flag pride display guidelines for the flag importance of flag honor implementing flag code revisions upholding national flag dignity online resources for flag protocol national pride through flag respect guidelines for respectful flag display advocacy for u s flag honor promoting flag lowering integrity online awareness for flag code reform advocating for flag display principles u s flag protocol updates flag honor initiatives online enhancing national flag reverence modernizing flag lowering criteria promoting flag honor awareness advocacy for proper flag tribute online resources for flag code u s flag pride initiatives supporting national flag dignity flag protocol awareness campaigns respecting the flag through reform upholding flag honor principles online resources for flag awareness display guidelines for the national flag advocating for u s flag reform flag lowering integrity campaigns online awareness for flag pride advocacy for proper flag etiquette enhancing u s flag reverence modernizing flag honor criteria promoting flag lowering awareness
#flag honor reform initiatives#respecting the national flag#u s flag protocol guidelines#dignity in national flag display#significance of half staff flag#flag code revision updates#patriotic flag respect principles#integrity in flag tributes#american flag pride advocacy#understanding flag lowering guidelines#preserving flag honor online#awareness of flag etiquette#advocating for flag code updates#display principles for the flag#honoring true service with flags#preventing flag misuse online#restoration of national pride#raising awareness for flag respect#criteria for flag lowering#respecting the flag with tribute
1 note
·
View note
Text
…
About 150 people carrying St George’s Cross flags, shouting “you’re not English any more” and “paedo Muslims off our street”, were greatly outnumbered in Leeds by hundreds of counter-protesters shouting “Nazi scum off our streets”. Skirmishes broke out between demonstrators and punks – in town for a festival – in Blackpool, with bottles and chairs thrown.
In Bristol, police kept protesters and counter protesters apart before a group headed to a hotel used to house asylum seekers.
The need for urgent political intervention was stressed by the government’s independent adviser on political violence and disruption, Lord Walney, who told the Observer that new emergency powers may be needed. “The system isn’t set up to deal with this rolling rabble-rousing being fuelled by far-right actors,” he said.
“I think home office ministers may want to look urgently at a new emergency framework – perhaps temporary in nature – that enables police to use the full powers of arrest to prevent people gathering where there is clear intent to fuel violent disorder.”
Keir Starmer held a meeting of senior ministers on Saturday in which he said police had been given full support to tackle extremists who were attempting “to sow hate by intimidating communities”. He made clear that the right to freedom of expression and the violent scenes over recent days were “two very different things”.
Last week’s riots followed the killing of three young girls at a Taylor Swift-themed dance class in Southport on Monday. Axel Rudakubana, 17, from Lancashire, is accused of the attack, but false claims were spread online that the suspect was an asylum seeker who had arrived in the UK by boat. In the wake of these messages, far-right protesters – guided by social media – gathered in cities across the country.
A key factor in this spread of online disinformation involved Elon Musk’s decision to allow rightwing activists such as Tommy Robinson back onto his social media platform X, said Joe Mulhall, director of research at Hope not Hate, the anti-fascism organisation. “The initial disinformation and anger was being perpetrated by individuals on Twitter, for example, that have been previously deplatformed,” he said. “And now they’ve been replatformed.”
Robinson was permanently banned from the platform (then called Twitter) in March 2018, then reinstated in November last year, after Musk bought it. “We hadn’t seen any significant numbers at any demonstrations since 2018,” Mulhall added.
An example of the danger posed by the misuse of social media was revealed in Stoke-on-Trent, where police were forced to deny there had been a stabbing, countering claims made on social media. “There is growing speculation that a stabbing has taken place as a result of the disorder today. We can confirm this information is false and no stabbings have been reported to police or emergency responders, despite videos fuelling speculation on social media,” police said.
The danger of such intervention was stressed by Ben-Julian “BJ” Harrington, the National Police Chiefs Council lead for public order, who condemned social media disinformation as a cause of last week’s disorder.
He said: “We had reports today that two people had been stabbed by Muslims in Stoke – it’s just not true. There’s people out there, not even in this country, circulating and stoking up hatred, division and concerns in communities that they don’t care about, don’t know and don’t understand.”
147 notes
·
View notes
Text
Free Gift Card Code Generator
Introduction
Depending on the jurisdiction, legal consequences may include fines, penalties, and even imprisonment.lf on common scams.s are substantial. Users must prioritize ethical practices, engage in responsible online behavior, and choose legal avenues to obtain gift cards.

Legality and Ethics
The use of gift card code generators raises red flags in terms of legality and ethics. While the allure of obtaining gift cards may be tempting, it’s crucial to understand the potential risks and consequences associated with these generators.
How Gift Card Code Generators Work
Behind the scenes, gift card code generators utilize algorithms and technical mechanisms to generate codes that may or may not be valid. Users need to be cautious, as engaging with these generators can lead to legal troubles and other severe consequences.
LINK/
Risks Associated
Users who utilize gift card code generators expose themselves to various risks, including identity theft, financial loss, and legal repercussions. It’s essential to weigh the perceived benefits against the potential harm before engaging with such tools.
Common Scams
Scammers often take advantage of those seeking gift cards. Recognizing common scams and understanding warning signs is crucial to avoid falling victim to fraudulent activities associated with these generators.
Alternatives to Gift Card Code Generators
Instead of resorting to dubious methods, users can explore legitimate avenues for obtaining gift cards. Reputable websites, promotions, and loyalty programs offer legal and ethical ways to enjoy the benefits of gift cards.
Impact on Businesses
The use of gift card code generators negatively impacts businesses, leading to financial losses and potential damage to their reputation. Users must recognize the broader consequences of engaging in such activities.
Online Security Measures
Enhancing online security is paramount to safeguarding personal information. Implementing strong passwords, using secure payment methods, and staying informed about common online threats can help users protect themselves.
Educating Users
Promoting awareness and education is essential in preventing the misuse of gift card code generators. Users must understand the risks involved and make informed decisions to protect themselves and others.
Responsible Online Behavior
Encouraging responsible online behavior fosters a safer digital environment. Users should prioritize ethical practices, respecting the rules and guidelines that govern online activities.
Future Trends
The gift card industry is likely to adapt to emerging technologies to enhance security and mitigate risks associated with code generators. Staying informed about industry developments is crucial for users.
Case Studies
Real-life examples illustrate the tangible consequences individuals or businesses face when involved with gift card code generators. These case studies serve as cautionary tales, highlighting the severity of the issue.
User Testimonials
Hearing from individuals who have faced consequences due to gift card code generators adds a human touch to the discussion. Personal stories create a relatable narrative that reinforces the potential risks involved.
Legal Consequences
Recent legal actions against those involved in the development or use of gift card code generators showcase the seriousness of these activities. Understanding the legal landscape is crucial for users contemplating such actions.
Conclusion
In conclusion, while the allure of gift cards is tempting, the risks and consequences associated with code generators are substantial. Users must prioritize ethical practices, engage in responsible online behavior, and choose legal avenues to obtain gift cards.
LINK/

#gift#gift card#free gift card generator#amazon#roblox#steam#xbox#ebay#fortnite#walmart wallis#google play#best buy#play station
2 notes
·
View notes
Text
Understanding About Debit Card Fraud
Debit card fraud is a growing concern as the world moves toward cashless transactions. Whether you're shopping online, withdrawing money from an ATM, or making a quick payment at a store, your debit card is vulnerable to misuse if you're not careful. In this guide, we’ll explore debit card fraud, how to detect it, and, most importantly, how to protect yourself from becoming a victim. We'll also cover what steps to take if you fall victim to fraud and answer some frequently asked questions.
What is Debit Card Fraud?
Debit card fraud occurs when someone illegally uses your debit card or card details to make unauthorized transactions, withdraw money, or commit fraud. Unlike credit card fraud, where the bank or credit card company bears much risk, debit card fraud can directly affect your account balance, leading to immediate financial loss.
In most cases, fraudsters either steal your card, skim your card information, or trick you into giving them your PIN or other sensitive details. Since the money comes directly from your bank account, it’s crucial to act quickly if you notice any suspicious transactions.
Types of Debit Card Fraud
There are several types of debit card fraud, and awareness of them is the first step toward protecting yourself.
Card Skimming: Fraudsters install devices on ATMs or payment terminals that capture your card’s magnetic strip information and PIN. They then clone your card to withdraw funds or make purchases.
Phishing Scams: This involves fraudsters sending fake emails or messages pretending to be from your bank or a legitimate business. They trick you into providing your card details, login credentials, or PIN.
Card Theft: Physical theft of your debit card is one of the most straightforward ways fraud occurs. If your card is stolen and you haven't reported it immediately, the thief can use it to make unauthorized transactions.
Online Fraud: Fraudsters use your card information for unauthorized online transactions. They often obtain your details through phishing websites or data breaches.
Card Not Present (CNP) Fraud: In CNP fraud, your card is not physically used, but the fraudster uses the card number and security details (like CVV) to make purchases online or over the phone.
How to detect Debit Card Fraud
Detecting debit card fraud early can help you minimize your financial loss. Here’s how you can spot it:
Unfamiliar Transactions: Keep a close eye on your bank statements and online banking accounts. If you see any unfamiliar transactions, especially from places you’ve never visited or websites you haven’t used, it’s a red flag.
Multiple Small Transactions: Fraudsters sometimes test the waters with small transactions before making larger withdrawals. A series of small debits might be an early sign of fraud.
SMS or Email Alerts: Many banks offer real-time notifications for every transaction. If you receive alerts for transactions you didn’t authorize, immediately contact your bank.
ATM Notifications: Some ATMs now notify you if your card has been used at multiple machines within a short period. This could indicate debit card fraud through skimming or card cloning.
Actions to take after Debit Card Fraud
If you suspect or confirm debit card fraud, act quickly to limit your losses. Here’s what you should do:
Report the Fraud: Contact your bank immediately and report the unauthorized transactions. Filing a debit card fraud complaint as soon as possible will increase your chances of recovering your money.
Block the Card: Your bank will block your debit card to prevent further fraud. They may then issue you a new card and PIN.
Check Your Transactions: Review your recent transactions and identify any other unauthorized activities. Make sure to highlight these when you file your complaint.
File a Police Report: Your bank may require a police report as part of the investigation process for certain types of fraud.
Monitor Your Account: Even after reporting the fraud, keep an eye on your bank account. Sometimes, additional fraudulent charges can occur even after your card is blocked.
Cyber Insurance: If you have cyber insurance, contact your insurer to see if your policy covers any financial loss from debit card fraud. Cyber insurance policies increasingly offer protection against digital crimes like phishing and online fraud.
Tips to save yourself from Debit Card Scams
Use Secure Websites: When shopping online, ensure the website URL starts with "https://" and has a secure padlock symbol. Avoid entering card details on dubious websites.
Avoid Public Wi-Fi for Transactions: Public Wi-Fi is often insecure, and fraudsters can intercept your card information. Always use a secure network when making payments or accessing your bank account.
Enable Two-Factor Authentication: If your bank has two-factor authentication, enable it. This adds an extra layer of security, as you'll need to verify your identity with a code and your password or PIN.
Use Virtual Cards for Online Purchases: Some banks offer virtual cards specifically for online purchases. These cards can be used temporarily and expire after a set period, limiting your exposure to fraud.
Regularly Monitor Your Accounts: Make it a habit to check your account frequently. This will help you catch unauthorized transactions before they become larger problems.
Set Transaction Limits: Many banks allow you to set transaction limits or daily spending caps. Setting a lower limit can prevent large unauthorized transactions if your card is compromised.
FAQs
How do I recover my debit card fraud?
Contact your bank when you discover fraudulent transactions to recover your money from debit card fraud. Report the issue, file a debit card fraud complaint, and follow the bank's procedures for investigating the scam. While the bank investigates, it may refund the stolen amount, depending on its policy.
Do banks refund scammed money?
In most cases, banks will refund the stolen amount if you report the fraud promptly and weren't negligent with your card information. However, the bank may not provide a refund if the fraud was due to your actions (like sharing your PIN).
Can someone use my debit card without my PIN?
Someone can use your debit card without your PIN, especially for online purchases or contactless payments. That’s why it's crucial to keep your card details secure and monitor your account for unauthorized transactions.
Can I track who used my debit card online?
While you can't directly track who used your debit card, your bank may have security measures to trace the fraudulent activity. They can check IP addresses or locations where the card was used and work with authorities to investigate.
Conclusion
Debit card fraud is an unfortunate reality of modern banking, but being vigilant and proactive can significantly reduce risk. Understand the types of debit card fraud, detect suspicious activity early, and take the right actions if you fall victim. Following the tips outlined above and considering added protection like cyber insurance, you can safeguard your financial information and hard-earned money. Stay informed, stay secure!
Source url - https://www.sbigeneral.in/blog-details/understanding-debit-card-fraud
0 notes
Text
The Ethics and Implications of "Undress AI" Technology
The topic of " Undress App " involves sensitive issues related to image recognition, privacy protection, and ethical considerations in artificial intelligence (AI). While the term itself is not widely used, it may refer to technologies related to automated analysis and generation of visual content, particularly regarding human figures and clothing. Below are some key points regarding the role of AI in these areas:
1. Image Processing and Facial Recognition
" Undress AI Free " could be linked to automated image analysis technologies, such as computer vision, which recognize visual elements in images like clothing or body parts. These technologies are used for content moderation, social media platforms' user-generated content management, and image classification. AI models identify specific patterns within images and help determine whether they adhere to platform policies or contain inappropriate content.
2. Ethical Concerns and Privacy Protection
Such technologies raise significant privacy and ethical issues. AI models might be misused to generate unauthorized or even explicit content (e.g., " Undressing AI "), potentially violating individual privacy or disseminating inappropriate material. As a result, ensuring these technologies are used in an ethically responsible manner is crucial.
AI in this domain needs to be developed with strong safeguards for privacy protection, user consent, and legal compliance. For example, some image recognition AI systems are specifically designed to detect and blur explicit content, preventing the spread of harmful or pornographic materials and protecting users' privacy.
3. Content Moderation and Surveillance
To maintain a healthy online environment, many platforms employ AI-driven content moderation systems to scan images, videos, and other media. AI can efficiently analyze vast amounts of content, identifying sensitive or inappropriate elements and taking appropriate action. This can reduce the workload for human moderators and increase the speed and accuracy of moderation processes.
However, this raises challenges such as the potential for false positives, where innocent content is flagged unfairly. Additionally, there are concerns about the lack of transparency in AI decision-making processes, leading to questions about algorithmic bias and fairness.
4. Deepfake and Anti-Fraud Concerns
" Undress AI " may also be associated with deepfake technology, which uses Generative Adversarial Networks (GANs) to create highly realistic fake images or videos, simulating human faces, expressions, or actions. This technology has been used for a variety of purposes, including creating hoax videos, virtual personalities, and explicit content.
To combat this, researchers are developing AI models that can detect deepfake content. By training AI to recognize the tell-tale signs of manipulation, developers can help prevent malicious use of this technology, such as the creation of fake media to spread misinformation or conduct harassment.
5. Legal and Social Responsibility
With the growing use of AI in sensitive fields like image generation and content moderation, many countries are introducing laws and regulations to govern their use. For example, the European Union's General Data Protection Regulation (GDPR) strictly outlines data processing and privacy protection requirements, necessitating companies to obtain explicit consent before using user data.
The use of AI in these sensitive areas must be regulated within a legal framework. Developers, businesses, and users alike must exercise caution and ensure that AI technologies are not used to infringe on rights or violate ethical standards.
Conclusion
The " Undress AI APP " concept brings forward important debates about privacy, ethics, and security. While AI offers many benefits to society, it also comes with risks of misuse. For AI to be used in a responsible and safe way, there needs to be strong oversight, public awareness, and ethical development practices. Only within a transparent and accountable framework can AI truly contribute positively to society without being misused.
0 notes
Text
Just did this and added more to the letter after skimming the bill's text.
Here's what I added since it's always good to personalize the things you send legislators.
Pre-written text: [I’m writing to urge you to reject the Kids Online Safety Act, a misguided bill that would put vulnerable young people at risk.
KOSA would fail to address the root issues related to kid’s safety online. Instead, it would endanger some of the most vulnerable people in our society while undermining human rights and children’s privacy. The bill would result in widespread internet censorship by pressuring platforms to use incredibly broad “content filters” and giving state Attorneys General the power to decide what content kids should and shouldn’t have access to online. This power could be abused in a number of ways and be politicized to censor information and resources.
KOSA would also likely lead to the greater surveillance of children online by requiring platforms to gather data to verify user identity.
There is a way to protect kids and all people online from egregious data abuse and harmful content targeting: passing a strong Federal data privacy law that prevents tech companies from collecting so much sensitive data about all of us in the first place, and gives individuals the ability to sue companies that misuse their data.
KOSA, although well-meaning, must not move forward. Please protect privacy and stop the spread of censorship online by opposing KOSA.]
My addition:
I would also like to add a personal anecdote about censorship online causing more harm than good. In 2019, one blogging website I use changed their terms to broadly disallow mature topics from being depicted in images on their site. This resulted in me losing a large following I had built over years due to people leaving the site when the site began removing content that was previously allowed and censoring accounts that posted or shared "too much" of this content that was previously allowed. This was a large following that I needed for visibility for the varied content I create. Not only that, but due to the restrictions on images, the website's tagging feature is now problematic. If I wanted to make a post discussing important sex education topics, tagging it with terms like "#sex" would automatically flag the post and hide it, even if it was purely medical information. This hindrance has led to people posting about mature topics and simply not tagging them any more - meaning, people who don't want to see posts discussing, for example, sex ed, will now have to see it untagged (meaning it cannot be filtered out of their social media feed), because there's simply no other way to share content to your audience without being censored completely.
You also see this with creators who use video platforms saying words like "unalived" to mean "killed" to get around auto-censors detecting a "mature" word (regardless of the context - someone could be discussing "killing" a task their computer was running and still be censored). Tagging a post or speaking normally blocks the post from getting any visibility, negating the purpose of even tagging it for safety to begin with. The direction people are being forced to go means that kids are more likely to see these mature topics being discussed using code words like "unalived" because creators can't tag their content straightforwardly any more without being hidden or flagged as inappropriate or mature.
Censorship such as this, and what would be reinforced or worsened if KOSA is passed, is what is actually going to harm children, because adult creators trying to reach other adults in their audience have no choice but to try and get around the inhuman and sloppily automated methods of censorship being used today; and without being able to tag or say these so-called "mature" words in a way that they could be filtered out for minors only, instead, these mature discussions are had through the use of code words or left untagged where kids could find them.
Not only that, but it also prevents people (adults and children), ESPECIALLY those who identify as LGBT, from seeking resources and education they might not be able to access from in-person sources. This is particularly concerning to me, because as a young adult, I learned about a lot of important safety tips on social media regarding things like sex ed and mental health for queer people, or helpful medically informational anecdotes and images that would be censored in today's internet. These are things I would have never thought to research on my own elsewhere, and definitely never would have been able to learn about in person, living in a rural area with hardly any queer population, let alone queer youth.
Seeing the downfall of a site I'd used for well over a decade has taught me that legislation concerning censorship can only do more harm than good. Not only for myself, losing a large audience when I'm already a 'starving artist,' but also because of the ways people are going to find to get around the censorship being forced upon them, which will end up affecting children. Strict censorship is not the answer to protecting children from online harm. This is a nuanced issue that can't be fixed with a sweeping erasure of mature topics online. Children do need to be protected, but KOSA is not going to do that. It's only going to harm the artists, writers, creators, who are already threatened by current censorship requirements and the growing threat of AI content replacing their important work. It's going to harm the queer youth that have no other place to turn to in order to find health information or community. It's going to harm the mentally ill youth that can't access or discuss the relevant topics because they've been censored. It's going to harm the children that share an online space with creators that have to skirt around censorship in order to exist online at all. It's going to empower social media companies to collect more personal data about people.
While I agree that children should be protected online, I do not belive KOSA will help. I believe further censorship and data collection will only make things worse.
I urge you to reject KOSA as this is a situation that cannot be fixed with a one-size-fits-all piece of legislation.
-
I wish the site said which legislators exactly it was going to, if it's just the senators or the representatives as well. I've done this for different topics before, and the representative usually responds back by email to agree or disagree. I usually get crickets from the senators.
Honestly, it probably doesn't make much of a difference in my case, but if enough people send personalized letters, y'know... Might put them on the spot to reconsider their stance.
...watcn tho, this reblog is gonna get hidden for using the word 'sex' or 'killed' on here. Yeah, that was me talking about Tumblr. Oh, I'm gonna be pissed if this gets hidden lmao, should've reconsidered posting my addition. I'll reblog the post as vanilla after this, just in case.
The 'Kids Online Safety Act' [KOSA] continues to move forward
Microsoft now endorses this legislation, which will likely help garner political support. Help counter this bill!
HELP STOP KOSA
Contact your representatives
KOSA is a bipartisan bill introduced to censor content on the internet deemed 'inappropriate' for minors. This bill is intended to target the LGBTQIA+ community and otherwise cause harm to minors.
Access to any supportive resources like queer-youth support groups, suicide hotlines, and important health information can be targeted.
#seriously do the email form you dont even have to personalize it#the worst that can happen is the senator replies back with a 'thank u for voicing ur opinion but i disagree for this reason'#like its no big deal i promise#people contact (pester) senators and representatives for way stupider reasons dont let social anxiety get in the way of this#kosa#censorship#what do i even tag this uhh#idk#shit like this is why tumblr has sucked since 2019
2K notes
·
View notes
Text
Cabinet Approves New Cross-Department Anti-Fraud Strategy to Combat Financial Crimes

Introduction: The Executive Yuan has officially approved the "Next-Generation Anti-Fraud Strategy Guidelines, Version 2.0" on Thursday, setting the stage for a comprehensive, cross-departmental operation to fight fraud beginning January 1, 2025. The new strategy aims to enhance the identification, prevention, blocking, and punishment of fraud-related crimes to significantly reduce financial losses and raise awareness among the public. Key Components of the New Anti-Fraud Strategy 1. Identification: Raising Awareness Across Taiwan The Ministry of the Interior (MOI) will lead efforts to improve awareness of fraud by disseminating crucial information through multiple channels tailored to various demographics. The goal is to reach 50 million views, conduct 500 educational lectures, and send 140 million anti-fraud text messages. Objective: - Prevent NT$10 billion (US$307.12 million) in financial losses due to fraud. - Targeted outreach to different age groups to enhance fraud awareness. 2. Blocking Fraudulent Activities: Ensuring Secure Communication To address fraudulent activities involving telecom services, the National Communications Commission (NCC) has introduced new regulations that allow telecom operators to access verification databases. These regulations enable telecom companies to restrict or block services for high-risk users, preventing scammers from exploiting dummy phone numbers. Additionally, the NCC is enhancing regulations regarding the misuse of prepaid SIM cards, especially for foreign nationals. 3. Prevention: Strengthening Digital Oversight The Ministry of Digital Affairs (MODA) will intensify efforts to prevent fraud across online platforms. Collaborating with industry giants such as Google, Meta, and Line, the ministry will ensure stricter advertisement placements and verify the identity of advertisers. Key Measures: - Block 30,000 scam websites annually. - Collaborate with Apple to monitor topping-up patterns via AI to prevent fraudulent charges. 4. Financial Oversight: Monitoring Fraudulent Transactions The Financial Supervisory Commission (FSC) is enhancing its mechanisms to monitor domestic financial accounts linked to fraudulent activities. This includes tighter surveillance of financial institutions to prevent the creation of dummy accounts, and more rigorous checks on credit card transactions. New Measures: - Share information about unauthorized credit card charges. - Flag accounts suspected of being used in fraudulent schemes. 5. Punishment: Cracking Down on Fraudsters The Ministry of Justice (MOJ) will step up its efforts to confiscate the proceeds from fraud and ensure that victims receive compensation. Furthermore, the ministry will hold at least 500 international meetings annually to strengthen cross-border collaboration on tackling fraud. Anti-Fraud Strategy Implementation Timeline MeasureResponsible AgencyTimelineGoalPublic Awareness CampaignMinistry of the InteriorBy 2025Reach 50 million views, educate citizensTelecom Fraud PreventionNational Communications CommissionJanuary 2025Block high-risk users and fake phone numbersOnline Fraud PreventionMinistry of Digital AffairsThroughout 2025Block 30,000 scam websites, monitor adsFinancial Fraud MonitoringFinancial Supervisory CommissionBy 2025Flag fraudulent accounts, monitor transactionsInternational Cooperation & PunishmentMinistry of JusticeOngoingStrengthen cross-border fraud enforcement FAQs 1. What is the "Next-Generation Anti-Fraud Strategy Guidelines, Version 2.0"? The guidelines aim to improve identification, blocking, prevention, and punishment of fraud. This cross-department initiative seeks to reduce fraud-related crimes and financial losses. 2. What agencies are involved in this anti-fraud effort? The Ministry of the Interior, National Communications Commission, Ministry of Digital Affairs, Financial Supervisory Commission, and Ministry of Justice are the key departments coordinating this strategy. 3. When will the new anti-fraud measures be implemented? The strategy will be officially launched on January 1, 2025. 4. How will telecom services help prevent fraud? Telecom companies will verify user identities, block high-risk accounts, and regulate the use of prepaid SIM cards to prevent fraudsters from exploiting telecom services. Conclusion: Taiwan Takes Major Steps Against Fraud The implementation of the new anti-fraud measures reflects Taiwan's commitment to enhancing public safety and financial security in an increasingly digital world. With a multi-pronged approach, Taiwan's government hopes to drastically reduce fraud incidents and provide swift action against perpetrators. Read the full article
0 notes
Text
Enhancing HR Cloud Platform Security with AI and Deep Learning.

The Growing Need for Enhanced Security

As businesses migrate to cloud-based HR systems, the sheer volume of sensitive employee data stored online makes these platforms attractive targets for cybercriminals. For example, payroll details, personal identification information, and performance reviews can be exploited if left unprotected. Therefore, organizations must adopt cutting-edge technologies like AI to detect vulnerabilities and mitigate threats proactively.
How AI Revolutionizes HR Cloud Security

AI enhances HR cloud platform security by automating threat detection and response mechanisms. Unlike traditional security methods, AI continuously monitors systems, identifies anomalies, and neutralizes potential risks in real-time. So, organizations can respond to cyber threats faster and more effectively, reducing the likelihood of data breaches. Furthermore, AI-driven tools use predictive analytics to anticipate future vulnerabilities, ensuring HR platforms remain secure.
Deep Learning: The Next Step in Cybersecurity
Deep learning, a subset of AI, takes security a step further by enabling HR platforms to learn from vast amounts of data. For instance, deep learning algorithms analyze patterns in user behavior, network activity, and data access requests to detect suspicious activity. Because these algorithms improve over time, they can predict and counteract sophisticated cyberattacks that traditional systems might miss.
Preventing Insider Threats

One of the most significant risks to HR cloud platforms is insider threats. Employees or contractors with access to sensitive systems may misuse their privileges, either intentionally or accidentally. AI and deep learning mitigate these risks by monitoring user behavior and flagging anomalies. For example, if an employee suddenly downloads large amounts of data without a valid reason, the system can trigger alerts.
Balancing Security with User Experience

While robust security measures are crucial, they should not hinder the user experience. AI-powered systems strike this balance by implementing intelligent access controls. So, HR cloud platforms can ensure employees only access the data they need without compromising security. Features like adaptive authentication — where login protocols adjust based on risk levels — make the experience seamless for users.
Compliance and Regulatory Benefits
Incorporating AI and deep learning into HR cloud security also helps organizations stay compliant with data protection regulations. For example, these technologies facilitate real-time audits and generate compliance reports, reducing manual effort. Because compliance violations can lead to hefty fines and reputational damage, https://bytes.employehub.com/automating these processes ensures businesses meet regulatory requirements efficiently.
Overcoming Implementation Challenges
Despite their benefits, implementing AI and deep learning in HR cloud security presents challenges. High costs, lack of expertise, and integration complexities often act as barriers. Therefore, organizations must partner with specialized vendors or invest in training to maximize the potential of these technologies. Moreover, phased implementation can make the transition smoother and more effective.
Conclusion: A Secure Future with AI

As the digital landscape evolves, securing HR cloud platforms becomes more critical than ever. By adopting AI and deep learning, organizations can stay ahead of cyber threats while ensuring the safety of sensitive employee data. Like any technological shift, the journey may come with challenges, but the long-term benefits far outweigh the investment. Therefore, businesses should embrace these innovations to foster a secure and efficient HR ecosystem.
0 notes
Text
Best AI Detection Tools & AI Generated Text Detection: Ensuring Authenticity in the Age of AI
As artificial intelligence continues to advance, AI-generated content is becoming increasingly sophisticated, posing new challenges for distinguishing between human-created and AI-generated text. Whether it’s for academic integrity, content originality, or maintaining transparency, the need for effective AI detection tools is greater than ever. In this article, we explore the best AI detection tools available and the importance of AI-generated text detection in today's digital landscape.
What Are AI Detection Tools?
AI detection tools are specialized software designed to identify content created by artificial intelligence. These tools use a combination of machine learning algorithms, pattern recognition, and natural language processing to analyze text and determine whether it has been generated by an AI model. With the rise of AI-generated content, such tools are increasingly essential for preventing misuse in areas like education, journalism, and online publishing.
Top Features of AI Detection Tools
The best AI detection tools typically include the following features:
Text Analysis and Pattern Recognition: These tools examine linguistic patterns, grammar, and sentence structure to detect signs of AI-generated text. For instance, AI-generated text may follow more predictable patterns compared to human writing.
Plagiarism Detection: Many AI detection tools are integrated with plagiarism detection software to cross-check content with existing databases and identify AI-generated text that mimics human writing.
Accuracy and Speed: The effectiveness of an AI detection tool is determined by how quickly and accurately it can analyze large volumes of text. Advanced tools can process entire documents within seconds, flagging suspicious content for review.
User-Friendly Interface: These tools often provide easy-to-use dashboards that allow users to upload content, get real-time results, and make informed decisions about the text's authenticity.
AI-Generated Text Detection: Why It Matters
The increasing use of AI-generated content in various fields, from marketing to academia, has led to growing
concerns over authenticity and transparency. Detecting AI-generated text is crucial for:
Educational Integrity: Ensuring students submit original work rather than AI-generated essays.
Content Authenticity: Ensuring published articles and blogs maintain human originality.
Business Trust: Businesses rely on trustworthy, authentic content to engage customers and maintain credibility.
Conclusion
As AI continues to shape the digital landscape, robust detection tools are essential to safeguard authenticity and originality. AiTextGuard offers cutting-edge AI detection solutions that help individuals and organizations quickly identify AI-generated content with unparalleled accuracy. Whether you’re a business, educator, or content creator, AiTextGuard ensures your content remains genuine and transparent in an AI-driven world.
0 notes
Text
I admit I’m not an expert in policy or security, and I don’t claim extensive knowledge about any of these platforms... but I'm personally shuffling toward Pillowfort and/or Cohost. Right now, both feel like they’re combining things I liked from the livejournal days, with the easy filehosting of tumblr. I don’t think their moderation policies are perfect but they’re a damn sight better than what tumblr has right now.
I don't trust tumblr to even keep my pencil sketches up without randomly flagging them. It just keeps fucking happening. A series of screencaps of a cartoon show? Flagged and hidden for hours, and by the time they’re repealed they’re pages down the tag page, basically lost. Those photographs about snow albedo? "Against Community Standards” and taken down. Same for screenshots of text explaining anitsemitism. An innocent hand-drawn gif of two video game characters, flagged after its creator left the platform? Hidden forever. An empty reblog? “We think there might be some nsfw in your reblog somewhere so we’ve hidden it without recourse”. Fuck this site and its bullshit moderation. I don’t think the people actually running tumblr give a damn.
And as for Mastodon, I think about the last thing I'd like to do is trust a random stranger with all of the information of exactly what weird porn I like AND all my private communications AND my personally identifiable information AND a large chunk of the content I want to interact with online. And yes I could use a VPN and use a privacy-focused Firefox browser to access Mastodon, but I also don’t want to assume everyone else will. I barely trusted livejournal/dreamwidth anonymous-community mods to run IP logging to prevent misuse. I also barely trusted livejournal/dreamwidth maincomm mods to fairly run a community hub for any one fandom, and not one day wake up and nuke everything in the comm. I sure as hell don’t trust the operator of an instance with my personal information, plus everything I’ve ever said or done, plus everything on that server in case one day they wake up and nuke everything in the instance.
If someone has further information / analysis on these and other websites, I’m all ears!
Tumblr is giving us a lot of different dashes but the thing is no one wants "for you" so what I propose instead is you give me the ability to make mini-dashes with specific subsets of people I follow. Let me follow 300 people but then sort them into category. Let me have one dash for all my aesthetic stuff, another for news, another for my weird feral friends. Am I the only one who wants this? Maybe. Give it to me anyway.
35K notes
·
View notes
Text
Building Trust in the Cloud: Auditing and Reporting for Safe DICOM Viewing
DICOM images contain highly sensitive patient health information. As medical practices shift towards convenient cloud-based DICOM viewers, establishing trust around data transparency and privacy grows increasingly important.
With flexible online DICOM viewer gaining popularity, providers require assurances that sensitive imaging data stays protected when accessed remotely.
Comprehensive activity logging and routine reports enable administrators to monitor DICOM traffic while identifying abnormal usage patterns.
By upholding stringent auditing protocols and real-time visibility, medical teams can securely unlock the convenience of cloud-based workflows without compromising safety.
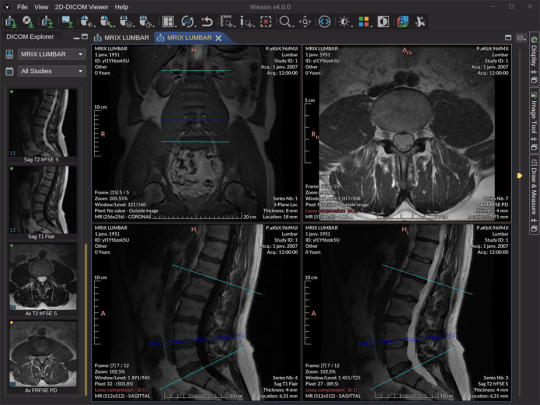
Why Audit Logs and Usage Reports Matter?
Track Access - Logs record viewer sessions, detailing who accessed images and when. This supports HIPAA compliance while discouraging internal data misuse.
Highlight Anomalies - Reports analyzing spikes in traffic or odd access times facilitate early anomaly detection, alerting administrators to suspicious activity.
Maintain Patient Privacy - Detailed audit trails demonstrating properly managed data help providers guarantee patient confidentiality is never broken, even off-site.
Meet Compliance Standards - Routine reports allow providers to easily produce documentation showing adherence to healthcare regulatory policies around patient privacy and information security.
Key Features That Reinforce Trust
Comprehensive Audit Logs
Logged User IDs - All viewer logins are registered to enable user-level tracking.
Timestamps - The data and time of each viewer action gets recorded for precise tracking.

IP Addresses - Systems log source IP addresses alongside session details for location-level visibility.
Granular Tracking - Individual study access, image manipulations, and more get logged to precisely track engagement.
Customizable Usage Reporting
User Breakdowns - Admins can pull reports summarizing activity across individuals, departments, sites, and more for a tailored view of usage.
Trend Analysis - Reports can highlight spikes or dips in traffic week-over-week to pinpoint abnormal patterns early.
Data Exports - Activity records can export to formats like CSV and JSON to enable further processing and oversight.
Scheduled Reports - Administrators can designate routine report deliveries to maintain continual awareness of viewer appropriation.
By centralizing DICOM access logs and distilling those raw records into digestible intelligence, medical teams can monitor cloud viewer adoption safely.
Detailed auditing paired with concise visibility reinforces provider accountability and patient confidentiality in the cloud.
Administrators gain greater awareness over how, when, and by whom data gets utilized while access permissions and protocols discourage internal misuse.
Meanwhile, patients can trust highly sensitive medical images stay protected despite remote viewing flexibility.
Real-Time Alerts Prevent Issues
In addition to retrospective tracking, real-time monitoring capabilities allow systems to automatically flag suspicious activity for intervention. Usage alerts can trigger on:
Unrecognized login attempts
Simultaneous sessions from different locations
Off-hour image access
Excessively high traffic
And more...
By setting custom rules around permissible viewer appropriation, administrators can receive system notifications the moment a potential breach occurs. This prevents unauthorized exposure instead of simply tracking it after the fact.
Maintaining Patient Trust
Medical images provide invaluable diagnostic insight for improved care, but also expose patients' most sensitive health details.
As providers adopt cloud-based DICOM workflows for enhanced convenience and collaboration, maintaining rigorous transparency protocols helps sustain patient trust that privacy stays protected.
By upholding strong accountability with comprehensive auditing and intelligent visibility into usage patterns, care teams can unlock flexible new workflows without introducing added risk.
Detailed activity tracking deters internal misuse while routine reports help consistently meet external compliance demands.
In the end, patients can rely on providers to safely manage sensitive data regardless of how modern systems evolve.
0 notes
Text
Taylor Swift AI Pictures Explicit X: A Digital Crisis and Ethical Dilemma

In the digital age, the boundaries of privacy and ethics are constantly being tested. The recent incident involving taylor swift ai pictures explicit x images on the social media platform X has thrown these issues into sharp relief. This episode not only shook Taylor Swift’s massive fanbase but also ignited a broader debate about the ethical use of artificial intelligence (AI) and the responsibilities of social media platforms. In this article, we will delve into the details of this incident, its implications, and the steps needed to address such challenges.
The Incident: Taylor Swift AI Pictures Explicit X
How It All Began
Searches for Taylor Swift on the popular social media platform X have been empty since explicit AI-generated images of the pop star went viral. These images, created using advanced AI technology, have been circulating on various online platforms, causing a stir among Taylor Swift’s fans and the broader public.
The Viral Spread
The explicit AI-generated images depicted Taylor Swift in compromising and fabricated situations. These highly realistic images were not only shocking but also raised significant concerns about privacy and the misuse of technology. Fans, known as Swifties, were outraged, and the images sparked widespread condemnation.
Platform’s Response
In response to the incident, X has taken steps to remove the explicit images and has temporarily turned off search functionality for Taylor Swift. This move, while well-intentioned, has left many users confused and frustrated. The platform has not provided a timeline for restoring search functionality, leaving fans unable to find content related to the pop star.
Ethical and Privacy Concerns
The Dark Side of AI
The incident has also brought attention to the potential misuse of AI technology. AI-generated images have become increasingly realistic and difficult to distinguish from genuine photographs, raising concerns about privacy and the potential for harm. In the case of Taylor Swift, explicit AI-generated images have been used to create and disseminate false and damaging content.
Consent and Privacy Violation
The use of AI to create explicit content without the consent of the individuals depicted raises serious ethical questions. As AI technology continues to advance, appropriate safeguards must be put in place to prevent its misuse. This includes developing robust guidelines for the ethical use of AI and ensuring that platforms have the necessary tools to detect and remove harmful content.
Legal Implications
Existing laws often struggle to keep up with technological advancements. The creation and distribution of explicit AI-generated images fall into a gray area, where traditional privacy and defamation laws might not be sufficient. There is a pressing need for updated legal frameworks that specifically address the challenges posed by AI-generated content.
The Role of Social Media Platforms
Content Moderation Challenges
Social media platforms have a responsibility to protect their users from harmful content and to ensure that their platforms are not used to spread false or damaging information. This includes implementing more effective content moderation systems and providing users with the tools they need to report and block inappropriate content.
Reactive Measures
In the case of the Taylor Swift AI pictures explicit X incident, X’s decision to disable search functionality was a reactive measure. While it helped to some extent, it also highlighted the platform's struggle to manage such crises proactively. There is a clear need for better preparedness and quicker, more effective responses to such incidents.
The Need for Proactive Measures
Platforms should invest in advanced AI tools that can detect and flag harmful content before it spreads. This proactive approach can help mitigate the damage caused by such incidents and protect users more effectively. Additionally, clear communication with users about the steps being taken can help build trust and transparency.
Addressing AI Exploitation
Technological Solutions
One of the key ways to combat the misuse of AI is through the development of advanced detection technologies. AI tools can be used to identify and flag deepfakes and other manipulated content. These tools need to be constantly updated to keep up with the evolving capabilities of AI-generated content.
Ethical Guidelines and Best Practices
Developing robust ethical guidelines for AI use is essential. These guidelines should cover various aspects, including consent, privacy, and the creation and distribution of content. Collaboration between technologists, ethicists, and legal experts is crucial to ensure these guidelines are comprehensive and effective.
Legal and Regulatory Frameworks
Stronger legal frameworks are essential to address the challenges posed by AI-generated content. Governments need to work together to create international standards for AI use and enforce strict penalties for violations. Clear regulations will act as a deterrent and provide a basis for taking action against those who create and distribute harmful content.
Future Implications of AI in Media
Balancing Innovation and Responsibility
AI holds immense potential for innovation in media. It can streamline production processes, create immersive experiences, and even predict consumer preferences. However, it is crucial to balance innovation with responsibility to prevent misuse.
The Role of Public Awareness
Public awareness about the capabilities and risks of AI is also vital. Educating users about the potential for AI misuse and how to identify and report harmful content can help create a safer digital environment.
Collaborative Efforts
Addressing the challenges posed by AI-generated content requires collaborative efforts from various stakeholders, including technology companies, governments, and civil society organizations. By working together, these stakeholders can develop and implement effective solutions to mitigate the risks associated with AI.
Conclusion
The Taylor Swift AI pictures explicit X incident serves as a stark reminder of the dark side of technological advancements. It underscores the urgent need for robust ethical guidelines, legal frameworks, and proactive measures to prevent the misuse of AI. As we navigate the digital age, it is crucial to ensure that innovation is balanced with responsibility, and that the privacy and dignity of individuals are protected.
0 notes
Text
Beware Celebrity Scams: Martin Lewis Issues Vital Warning

Martin Lewis has raised an alert regarding the widespread misuse of celebrity profiles in scams, with even the Money Saving Expert himself being prominently targeted. Among the personalities frequently exploited in online scams are "The King," Taylor Swift, Elon Musk, and Adele, according to data analyzed by MoneySavingExpert.com from Action Fraud reports spanning 2022 and 2023. The analysis reveals that public figures across entertainment, business, politics, and royalty have been victims of such deceptive practices. Figures like Jeremy Clarkson and Rishi Sunak have also been misused in these fraudulent schemes. MoneySavingExpert.com, founded by Mr. Lewis, noted that the data it analyzed is likely just a fraction of the total, as many individuals do not report scams to law enforcement. Action Fraud provided data on reported scams based on a list of celebrities compiled by MoneySavingExpert.com. The website crowdsourced this list through social media, asking users to report instances of celebrities appearing in scam advertisements. In their analysis, Mr. Lewis emerged as the most frequently mentioned public figure in reports submitted to Action Fraud. Here are the top 20 high-profile figures whose identities have been misused by scammers, according to research using Action Fraud data, along with the percentage of total mentions in scams: MoneySavingExpert reported that Action Fraud data shows victims have reported losing over £20 million to scams misusing Mr. Lewis's profile in the past two years. The largest reported loss attributed to a scam featuring Mr. Lewis was £500,000. Mr. Lewis commented, "It’s likely that the criminals behind these scam ads effectively use their own in-house dark-web digital marketing teams, researching which celebrities and advert types yield the highest click-through rates, and refining their tactics to attract more victims. Almost certainly, they are gathering data on each public figure’s ability to attract attention and how many people who respond to a celebrity in an advert ultimately end up losing money." He added, "If it’s an ad with me in it, it’s always a scam, as I don’t endorse adverts. Topping this list is probably the worst compliment I’ve ever had." Mr. Lewis continued, "The new government has promised to ensure that tech companies have a clear obligation and financial incentive to collaborate with banks to prevent scams, identify fraudulent transactions, and support victims. We will closely monitor to see if these promises are fulfilled." MoneySavingExpert warned that mentions of cryptocurrency, investing, retirement planning, and promises of quick wealth are specific red flags to watch for in scam ads. They also cautioned that claims about celebrity scandals could lead to scams, with links to supposed scandals potentially directing individuals to investment scams. The article noted that ticket scams, capitalizing on the popularity of Swift’s Era tour, are prevalent. MoneySavingExpert advised consumers to purchase tickets from official platforms and to exercise caution on social media. According to data published by Lloyds Bank earlier this year, fans of Swift have reportedly lost approximately £1 million since UK tickets for her tour went on sale last July. If someone suspects they have fallen victim to a scam, they are advised to contact both their bank and the police. Numerous banks are participating in the 159 scheme, allowing individuals to report suspicious contacts potentially linked to scams by dialing 159. Participating institutions include Monzo, Bank of Scotland, Barclays, Co-operative Bank, First Direct, Halifax, HSBC, Lloyds Bank, Metro Bank, Nationwide Building Society, NatWest, Royal Bank of Scotland, Santander, Starling, Tide, TSB, and Ulster Bank. In England, Wales, and Northern Ireland, individuals can report scams to the police through Action Fraud. In Scotland, they should contact Police Scotland. For online scams, individuals can also report to the Advertising Standards Authority (ASA), in addition to notifying their bank and the police. If payment was made by card, individuals may seek recourse under Section 75 of the Consumer Credit Act, applicable in some cases for credit card purchases, or through the chargeback scheme to reclaim their funds. MoneySavingExpert clarified that their research covers all mentions, including instances where multiple people are referenced. Action Fraud cautioned that while some unrelated reports may have been included, others related to scams may have been missed. Read the full article
0 notes
Text
Keystroke Tracker: The Ultimate Guide to Monitoring Employee Activity

Do you ever sit back and wonder what's happening on your company computers when you're not looking? Are employees diligently hammering away at tasks, or are there occasional detours into the world of online shopping or social media? The truth is, you might be surprised. But what if there was a way to gain complete transparency, to see every keystroke and action with crystal clarity?
Enter the world of keystroke tracker. These powerful tools are revolutionizing employee monitoring, giving employers an unprecedented view into their workforce's digital activity. But are keystroke trackers the ultimate answer to boosting productivity and ensuring security, or is there a darker side to consider?
In this comprehensive guide, we'll delve deep into the world of keystroke tracking, exploring its benefits, drawbacks, and everything in between.
What is a Keystroke Tracker?
A keystroke tracker is a software application that records every keystroke typed on a computer. This data can include:
Letters and numbers typed
Special characters used
Punctuation marks entered
Program commands and shortcuts
The software runs discreetly in the background, capturing this information and storing it for later review.
How Does Keystroke Tracking Software Work?
Keystroke tracking software operates in two primary ways:
Kernel-Level Monitoring: This method involves the software installing itself at a deep system level, granting it access to the raw data stream from the keyboard before it reaches specific applications. It provides a comprehensive record of all keystrokes, including login credentials and messages typed in chat applications.
Application-Level Monitoring: This method tracks keystrokes within specific programs or applications. It offers less intrusive monitoring but might not capture activity outside designated programs.
Here's a breakdown of the typical functionalities of keystroke-tracking software:

Real-time Monitoring: Certain programs allow employers to monitor employee activity in real-time, providing immediate insight into their work habits.
Keyword Filtering: Employers can set up keyword filters to flag specific phrases or activities, allowing them to identify potential security breaches or misuse of company resources.
Activity Logs and Reports: The software generates detailed logs and reports that categorize keystrokes, track application usage, and measure overall productivity.
Benefits of Using Keystroke Tracking Software
Proponents of keystroke tracking software tout several potential benefits for businesses:
Enhanced Productivity: By monitoring application usage and identifying unproductive activities, employers can encourage employees to focus on work-related tasks.
Improved Data Security: Keystroke trackers can detect suspicious activity, such as unauthorized login attempts or sensitive data being copied, helping to prevent data breaches.
Compliance Monitoring: In industries with strict regulatory requirements, keystroke tracking can ensure employees adhere to data security protocols and record-keeping regulations.
Training and Development: Analysis of keystroke data can reveal areas where employees might require additional training or support, allowing employers to bridge skill gaps and enhance overall efficiency.
Legal Considerations of Keystroke Monitoring
The legality of keystroke tracking software varies depending on geographical location and specific company policies. Here are some key factors to consider:
Employee Consent: In most jurisdictions, employers are required to obtain explicit employee consent before implementing keystroke monitoring. This consent should be clearly outlined in a written policy detailing the monitoring scope and purpose.
Data Privacy Laws: Regions with stringent data privacy laws, such as the General Data Protection Regulation (GDPR) in the European Union, impose limitations on how employee data can be collected, stored, and used. Employers must ensure compliance with relevant data privacy regulations.
Transparency and Trust: Open communication with employees regarding the use of keystroke monitoring software is crucial for building trust and fostering a positive work environment.

Alternatives to Keystroke Tracking Software:
While keystroke trackers offer a comprehensive approach to employee monitoring, some businesses might prefer alternative methods:
Website Blocking and Time Tracking Software: These programs restrict access to non-work-related websites and track time spent on different applications, promoting focused work.
Employee Productivity Monitoring Tools: These software solutions analyze document creation, email activity, and meeting participation to gauge employee productivity without resorting to keystroke monitoring.
Performance Reviews and Open Communication: Regular performance reviews and open communication channels can foster a culture of accountability and productivity without infringing on employee privacy.
You Can Also Watch:
youtube
Conclusion
keystroke tracker presents a powerful tool for employers seeking to monitor employee activity and optimize workflow. However, it's crucial to weigh the potential benefits against legal considerations and employee privacy concerns. Businesses should explore alternative solutions and prioritize clear communication with employees before implementing keystroke monitoring practices.
By carefully considering these factors, businesses can leverage technology to enhance employee productivity and achieve their organizational goals while maintaining a culture of trust and transparency.
#keystroke tracker#keystroke software#monitoring keystroke#keystroke monitoring#track computer activity#workforce management software#keystroke technology#Youtube
0 notes
Text
Online Pharmacy
Title: Navigating the World of Online Pharmacies: Convenience, Safety, and Responsibility
In the ever-evolving landscape of healthcare, the advent of online pharmacies has been a game-changer. Offering convenience, accessibility, and often competitive pricing, these platforms have reshaped how people access their medications. However, like any digital service, online pharmacies come with their own set of considerations, particularly regarding safety and responsibility. Let’s delve into this topic further.
Convenience Redefined
One of the most appealing aspects of online pharmacies is undoubtedly their convenience. With just a few clicks, patients can order their medications from the comfort of their own homes and have them delivered right to their doorstep. This is especially beneficial for individuals with mobility issues, those living in remote areas, or those with busy schedules who find it difficult to visit a physical pharmacy during operating hours.
Moreover, online pharmacies often provide a wide range of medications, including prescription drugs, over-the-counter remedies, and even specialized medications that may not be readily available at local brick-and-mortar pharmacies. This expanded access can be a lifeline for people with chronic conditions or rare illnesses who require specific medications.
Safety Concerns
While convenience is a significant advantage, safety should always be paramount when it comes to healthcare. Online pharmacies operate in a digital environment, which means that there are potential risks associated with purchasing medication online. Some of these risks include:
Counterfeit Medications: Without proper regulation and oversight, some online pharmacies may sell counterfeit or substandard medications, posing significant health risks to consumers.
Privacy and Data Security: Transmitting personal and medical information over the internet raises concerns about privacy and data security. Patients must ensure that the online pharmacy they choose employs robust encryption methods to protect sensitive information.
Prescription Verification: In many countries, prescription medications require a valid prescription from a licensed healthcare provider. Online pharmacies should have mechanisms in place to verify prescriptions to prevent misuse or abuse of prescription drugs.
Responsibility of Patients and Providers
To mitigate these risks, both patients and online pharmacies must exercise responsibility and due diligence. For patients, this means:
Researching the Pharmacy: Before making a purchase, investigate the online pharmacy’s credentials, including licensing, accreditation, and customer reviews. Legitimate pharmacies should prominently display this information on their website.
Consulting Healthcare Providers: It’s crucial to consult with a healthcare provider before ordering prescription medications online. A qualified professional can provide guidance on the appropriate medication, dosage, and potential interactions with other drugs.
Monitoring for Red Flags: Be wary of pharmacies that offer steep discounts or sell prescription medications without requiring a prescription. These could be indicators of illegitimate operations.
Similarly, online pharmacies have a responsibility to:
Adhere to Regulations: Online pharmacies should comply with all relevant regulations and standards governing the sale and distribution of medications. This includes obtaining proper licensing, maintaining quality control measures, and ensuring secure transactions.
Provide Accurate Information: Clear and accurate information about medications, including potential side effects, contraindications, and proper usage instructions, should be readily available to consumers.
Promote Patient Education: Educating consumers about the safe use of medications and the importance of seeking medical advice when necessary can help prevent misuse and promote better health outcomes.
Conclusion
The rise of online pharmacies offers undeniable benefits in terms of convenience and accessibility. However, it’s essential for both consumers and providers to approach this digital frontier with caution and responsibility. By staying informed, conducting thorough research, and prioritizing safety, individuals can harness the advantages of online pharmacies while minimizing potential risks. In this evolving landscape of healthcare delivery, collaboration between patients, healthcare providers, and online pharmacies is key to ensuring safe and effective medication management for all.
Remember, your health is invaluable, so always prioritize safety and informed decision-making when utilizing online pharmacy services.
0 notes
Text
does omegle not allow vpn
��🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does omegle not allow vpn
Omegle VPN detection
Title: Overcoming Omegle VPN Detection: How to Stay Secure and Anonymous
Omegle, the anonymous chat platform, has gained popularity for its spontaneity and randomness in connecting strangers worldwide. However, Omegle's anonymity feature has also attracted individuals seeking to exploit it for various purposes, including cyberbullying, harassment, and even illegal activities. To combat these issues, Omegle has implemented measures to detect and block users utilizing VPNs (Virtual Private Networks) to bypass geographical restrictions or conceal their identities.
VPN detection on Omegle can be frustrating for legitimate users who simply seek privacy or access to the platform from restricted regions. When Omegle detects a VPN connection, it typically restricts access, leading to error messages or outright bans.
So, how can users bypass Omegle's VPN detection while ensuring their security and anonymity?
One approach is to utilize reputable VPN services that employ advanced obfuscation techniques to evade detection. These VPNs disguise VPN traffic as regular HTTPS traffic, making it harder for Omegle to identify and block VPN connections.
Another method is to use dedicated IP addresses provided by VPN services. Dedicated IPs are less likely to be flagged by Omegle's detection systems compared to shared IP addresses commonly used by VPN users.
Additionally, adjusting VPN settings such as protocol selection and server location can help evade detection. Opting for less congested servers and utilizing protocols like OpenVPN or IKEv2 may improve the chances of successfully connecting to Omegle.
It's important to note that while bypassing Omegle's VPN detection can provide access to the platform, users must also adhere to Omegle's community guidelines and applicable laws to maintain a safe and respectful environment for all users.
In conclusion, while Omegle's VPN detection measures aim to enhance security and mitigate misuse, legitimate users can still maintain their privacy and access the platform by employing effective VPN strategies and adhering to guidelines.
VPN restrictions on Omegle
VPN restrictions on Omegle are a common obstacle faced by many users trying to access the platform anonymously. Omegle is a popular website that allows individuals to chat with strangers online without revealing their identity. However, due to concerns about cyberbullying, harassment, and inappropriate content, Omegle has implemented VPN restrictions to prevent users from accessing the site through virtual private networks.
When users try to access Omegle through a VPN, they may encounter error messages or be blocked from using the service altogether. This can be frustrating for individuals who rely on VPNs to protect their privacy and security online. VPN restrictions on Omegle are designed to enforce the platform's terms of service and ensure that users follow the rules and guidelines set forth by the website.
While VPN restrictions on Omegle may be inconvenient for some users, they serve an important purpose in maintaining a safe and secure online environment. By blocking users who attempt to access the site through VPNs, Omegle can help prevent malicious activities and protect individuals from potential harm. Additionally, VPN restrictions can help deter individuals from engaging in inappropriate behavior on the platform.
Overall, VPN restrictions on Omegle are a necessary measure to enforce the platform's rules and guidelines. While they may pose challenges for users who rely on VPNs for privacy and security, these restrictions ultimately help create a safer online experience for everyone.
Omegle blocking VPN
Title: Why Omegle Blocks VPNs and How to Bypass It
Omegle, the popular online chat platform, has implemented measures to block VPNs (Virtual Private Networks) from accessing its services. This move has sparked curiosity and frustration among users who rely on VPNs for privacy, security, or bypassing geographical restrictions.
The primary reason behind Omegle's VPN blocking is to enforce its community guidelines and prevent misuse of the platform. By blocking VPNs, Omegle aims to restrict access to users who may engage in inappropriate behavior, such as harassment, spamming, or sharing explicit content. VPNs can allow users to conceal their true location and identity, making it challenging for Omegle to enforce its rules effectively.
Additionally, Omegle may block VPNs to comply with legal requirements and regulations. Some countries have strict laws regarding online content and require platforms like Omegle to verify the identity and location of their users. By blocking VPNs, Omegle can ensure compliance with these regulations and avoid potential legal issues.
For users who rely on VPNs for legitimate reasons, such as protecting their privacy or accessing Omegle from restricted regions, being blocked can be frustrating. However, there are ways to bypass Omegle's VPN blocking.
One method is to use a VPN that offers dedicated IP addresses. Unlike shared IP addresses, dedicated IPs are less likely to be flagged by Omegle's blocking systems since they are not associated with multiple users. Another option is to use a VPN that employs obfuscation techniques to disguise VPN traffic, making it harder for Omegle to detect and block.
It's essential to note that while bypassing Omegle's VPN blocking is possible, users should still adhere to the platform's guidelines and respect other users' privacy and safety. Engaging in inappropriate behavior can result in account suspension or legal consequences.
In conclusion, Omegle blocks VPNs to maintain a safe and compliant environment for its users. While this may inconvenience some users, there are methods available to bypass VPN blocking and access Omegle securely and responsibly.
VPN bypass for Omegle
Title: How to Bypass Omegle Restrictions with a VPN
Are you tired of being blocked or restricted on Omegle? Perhaps you're encountering region-based bans or limitations on accessing the platform. Fortunately, there's a simple solution: using a Virtual Private Network (VPN) to bypass these restrictions.
Omegle, a popular online chat platform, employs various measures to regulate user access. These measures may include IP-based bans, geo-blocking, or restrictions imposed by local authorities. However, by using a VPN, you can mask your IP address and reroute your internet connection through servers located in different regions, effectively bypassing these barriers.
Here's how to bypass Omegle restrictions using a VPN:
Choose a reliable VPN service: Select a VPN provider known for its strong encryption, fast servers, and widespread network coverage.
Install the VPN software: Download and install the VPN application on your device. Most VPN services offer user-friendly apps for various operating systems, including Windows, macOS, iOS, and Android.
Connect to a VPN server: Launch the VPN app and connect to a server located in a region where Omegle is accessible. This could be a server in a different country or a specific location with unrestricted access.
Access Omegle: Once connected to the VPN server, visit the Omegle website or app as you normally would. The VPN will mask your real IP address with the server's IP, allowing you to bypass any restrictions imposed on your original connection.
Enjoy unrestricted access: With the VPN active, you should now be able to chat on Omegle without encountering any blocks or limitations. You can engage with users from around the world without worrying about regional restrictions.
By using a VPN to bypass Omegle restrictions, you can enjoy uninterrupted access to the platform and connect with people from diverse backgrounds, regardless of your geographical location. Remember to choose a reputable VPN provider and prioritize your online privacy and security while using Omegle or any other online service.
Omegle and VPN compatibility
Omegle is a popular online platform that allows users to chat with strangers anonymously. While Omegle provides an exciting way to connect with new people, many users are concerned about their privacy and security while using the platform. One way users can enhance their security and protect their identity while using Omegle is by utilizing a Virtual Private Network (VPN).
A VPN is a tool that encrypts your internet connection and routes it through a server in a location of your choosing. By using a VPN while accessing Omegle, users can mask their IP address and location, making it harder for third parties to track their online activities. This added layer of security can help protect users from potential threats such as hackers, data thieves, and even government surveillance.
In addition to improving security, using a VPN with Omegle can also help users bypass geographical restrictions. Some countries or regions may block access to Omegle due to content restrictions or censorship. By connecting to a VPN server in a different location, users can bypass these restrictions and access Omegle freely.
However, it is essential to choose a reliable and secure VPN service provider when using Omegle. Some VPN services may log user data or have unreliable connections, compromising user privacy. Users should opt for VPN services with a strict no-logs policy, strong encryption, and a wide selection of servers to ensure a safe and seamless Omegle experience.
In conclusion, pairing Omegle with a VPN can enhance user privacy, security, and access to the platform. By taking the necessary precautions and selecting a reputable VPN service, users can enjoy a more secure and unrestricted chatting experience on Omegle.
0 notes