#preparing for cyberattack
Explore tagged Tumblr posts
Text
Ethera Operation!!
You're the government’s best hacker, but that doesn’t mean you were prepared to be thrown into a fighter jet.
Bradley "Rooster" Bradshaw x Awkward!Hacker! FemReader
Part I


This was never supposed to happen. Your role in this operation was simple—deliver the program, ensure it reached the right hands, and let the professionals handle the breaching.
And then, of course, reality decided to light that plan on fire.
The program—codenamed Ethera—was yours. You built it from scratch with encryption so advanced that even the most elite cyber operatives couldn’t crack it without your input. A next-generation adaptive, self-learning decryption software, an intrusion system designed to override and manipulate high-security military networks, Ethera was intended to be both a weapon and a shield, capable of infiltrating enemy systems while protecting your own from counterattacks in real-time. A ghost in the machine. A digital predator. A weapon in the form of pure code. If it fell into the wrong hands, it could disable fleets, and ground aircraft, and turn classified intelligence into an open book. Governments would kill for it. Nations could fall because of it.
Not that you ever meant to, of course. It started as a little experimental security measure program, something to protect high-level data from cyberattacks, not become the ultimate hacking tool. But innovation has a funny way of attracting the wrong kind of attention, and before you knew it, Ethera had become one, if not the most classified, high-risk program in modern times. Tier One asset or so the Secret Service called it.
It was too powerful, too dangerous—so secret that only a select few even knew of its existence, and even fewer could comprehend how it worked.
And therein lay the problem. You were the only person who could properly operate it.
Which was so unfair.
Because it wasn’t supposed to be your problem. You were just the creator, the brain behind the code, the one who spent way too many sleepless nights debugging this monstrosity. Your job was supposed to end at development. But no. Now, because of some bureaucratic nonsense and the fact that no one else could run it without accidentally bricking an entire system, you had been promoted—scratch that, forcibly conscripted—into field duty.
And your mission? To install it in an enemy satellite.
A literal, orbiting, high-security, military-grade satellite, may you add.
God. Why? Why was your country always at war with others? Why couldn’t world leaders just, you know, go to therapy like normal people? Why did everything have to escalate to international cyber warfare?
Which is how you ended up here.
At Top Gun. The last place in the world you wanted to be.
You weren’t built for this. You thrive in sipping coffee in a cosy little office and handling cyber threats from a safe, grounded location. You weren’t meant to be standing in the halls of an elite fighter pilot training program, surrounded by the best aviators in the world—people who thought breaking the sound barrier was a casual Wednesday.
It wasn’t the high-tech cyberwarfare department of the Pentagon, nor some dimly lit black ops facility where hackers in hoodies clacked away at keyboards. No. It was Top Gun. A place where pilots use G-forces like a personal amusement park ride.
You weren’t a soldier, you weren’t a spy, you got queasy in elevators, you got dizzy when you stood too fast, hell, you weren’t even good at keeping your phone screen from cracking.
... And now you were sweating.
You swallowed hard as Admiral Solomon "Warlock" Bates led you through the halls of the naval base, your heels clacking on the polished floors as you wiped your forehead. You're nervous, too damn nervous and this damned weather did not help.
"Relax, Miss," Warlock muttered in that calm, authoritative way of his. "They're just pilots."
Just pilots.
Right. And a nuclear warhead was just a firework.
And now, somehow, you were supposed to explain—loosely explain, because God help you, the full details were above even their clearance level—how Ethera, your elegant, lethal, unstoppable digital masterpiece, was about to be injected into an enemy satellite as part of a classified mission.
This was going to be a disaster.
You had barely made it through the doors of the briefing room when you felt it—every single eye in the room locking onto you.
It wasn’t just the number of them that got you, it was the intensity. These were Top Gun pilots, the best of the best, and they radiated the kind of confidence you could only dream of having. Meanwhile, you felt like a stray kitten wandering into a lion’s den.
Your hands tightened around the tablet clutched to your chest. It was your lifeline, holding every critical detail of Ethera, the program that had dragged you into this utterly ridiculous situation. If you could’ve melted into the walls, you absolutely would have. But there was no escaping this.
You just had to keep it together long enough to survive this briefing.
So, you inhaled deeply, squared your shoulders, and forced your heels forward, trying to project confidence—chin up, back straight, eyes locked onto Vice Admiral Beau "Cyclone" Simpson, who you’d been introduced to earlier that day.
And then, of course, you dropped the damn tablet.
Not a graceful drop. Not the kind of gentle slip where you could scoop it back up and act like nothing happened. No, this was a full-on, physics-defying fumble. The tablet flipped out of your arms, ricocheted off your knee, and skidded across the floor to the feet of one of the pilots.
Silence.
Pure, excruciating silence.
You didn’t even have the nerve to look up right away, too busy contemplating whether it was physically possible to disintegrate on command. But when you finally did glance up—because, you know, social convention demanded it—you were met with a sight that somehow made this entire disaster worse.
Because the person crouching down to pick up your poor, abused tablet was freaking hot.
Tall, broad-shouldered, with a head of golden curls that practically begged to be tousled by the wind, and, oh, yeah—a moustache that somehow worked way too well on him.
He turned the tablet over in his hands, inspecting it with an amused little smirk before handing it over to you. "You, uh… need this?"
Oh, great. His voice is hot too.
You grabbed it back, praying he couldn't see how your hands were shaking. “Nope. Just thought I’d test gravity real quick.”
A few chuckles rippled through the room, and his smirk deepened like he was enjoying this way too much. You, on the other hand, wanted to launch yourself into the sun.
With what little dignity you had left, you forced a quick, tight-lipped smile at him before turning on your heel and continuing forward, clutching your tablet like it was a life raft in the middle of the worst social shipwreck imaginable.
At the front of the room, Vice Admiral Beau Cyclone Simpson stood with the kind of posture that said he had zero time for nonsense, waiting for the room to settle. You barely had time to take a deep breath before his voice cut through the air.
“Alright, listen up.” His tone was crisp, commanding, and impossible to ignore. “This is Dr Y/N L/N. Everything she is about to tell you is highly classified. What you hear in this briefing does not leave this room. Understood?”
A chorus of nods. "Yes, sir."
You barely resisted the urge to physically cringe as every pilot in the room turned to stare at you—some with confusion, others with barely concealed amusement, and a few with the sharp assessing glances of people who had no clue what they were supposed to do with you.
You cleared your throat, squared your shoulders, and did your best to channel even an ounce of the confidence you usually had when you were coding at 3 AM in a secure, pilot-free lab—where the only judgment you faced was from coffee cups and the occasional system error.
As you reached the podium, you forced what you hoped was a composed smile. “Uh… hi, nice to meet you all.”
Solid. Real professional.
You glanced up just long enough to take in the mix of expressions in the room—some mildly interested, some unreadable, and one particular moustached pilot who still had the faintest trace of amusement on his face.
Nope. Not looking at him.
You exhaled slowly, centering yourself. Stay focused. Stay professional. You weren’t just here because of Ethera—you were Ethera. The only one who truly understood it. The only one who could execute this mission.
With another tap on your tablet, the slide shifted to a blacked-out, redacted briefing—only the necessary information was visible. A sleek 3D-rendered model of the enemy satellite appeared on the screen, rotating slowly. Most of its details were blurred or omitted entirely.
“This is Blackstar, a highly classified enemy satellite that has been operating in a low-Earth orbit over restricted airspace.” Your voice remained even, and steady, but the weight of what you were revealing sent a shiver down your spine. “Its existence has remained off the radar—literally and figuratively—until recently, when intelligence confirmed that it has been intercepting our encrypted communications, rerouting information, altering intelligence, and in some cases—fabricating entire communications.”
Someone exhaled sharply. Another shifted in their seat.
“So they’re feeding us bad intel?” one of them with big glasses and blonde hair asked, voice sceptical but sharp.
“That’s the theory,” you confirmed. “And given how quickly our ops have been compromised recently, it’s working.”
You tapped again, shifting to the next slide. The silent infiltration diagram appeared—an intricate web of glowing red lines showing Etherea’s integration process, slowly wrapping around the satellite’s systems like a virus embedding itself into a host.
“This is where Ethera comes in,” you said, shifting to a slide that displayed a cascading string of code, flickering across the screen. “Unlike traditional cyberweapons, Ethera doesn’t just break into a system. It integrates—restructuring security protocols as if it was always meant to be there. It’s undetectable, untraceable, and once inside, it grants us complete control of the Blackstar and won’t even register it as a breach.”
“So we’re not just hacking it," The only female pilot of the team said, arms crossed as she studied the data. “We’re hijacking it.”
“Exactly,” You nodded with a grin.
You switched to the next slide—a detailed radar map displaying the satellite’s location over international waters.
“This is the target area,” you continued after a deep breath. “It’s flying low-altitude reconnaissance patterns, which means it’s using ground relays for some of its communication. That gives us a small window to infiltrate and shut it down.”
The next slide appeared—a pair of unidentified fighter aircraft, patrolling the vicinity.
“And this is the problem,” you said grimly. “This satellite isn’t unguarded.”
A murmur rippled through the room as the pilots took in the fifth-generation stealth fighters displayed on the screen.
“We don’t know who they belong to,” you admitted. “What we do know is that they’re operating with highly classified tech—possibly experimental—and have been seen running defence patterns around the satellite’s flight path.”
Cyclone stepped forward then, arms crossed, his voice sharp and authoritative. “Which means your job is twofold. You will escort Dr L/N’s aircraft to the infiltration zone, ensuring Ethera is successfully deployed. If we are engaged, your priority remains protecting the package and ensuring a safe return.”
Oh, fantastic, you could not only feel your heartbeat in your toes, you were now officially the package.
You cleared your throat, tapping the screen again. Ethera’s interface expanded, displaying a cascade of sleek code.
“Once I’m in range,” you continued, “Ethera will lock onto the satellite’s frequency and begin infiltration. From that point, it’ll take approximately fifty-eight seconds to bypass security and assume control."
Silence settled over the room like a thick cloud, the weight of their stares pressing down on you. You could feel them analyzing, calculating, probably questioning who in their right mind thought putting you—a hacker, a tech specialist, someone whose idea of adrenaline was passing cars on the highway—into a fighter jet was a good idea.
Finally, one of the pilots—tall, broad-shouldered, blonde, and very clearly one of the cocky ones—tilted his head, arms crossed over his chest in a way that screamed too much confidence.
“So, let me get this straight.” His voice was smooth, and confident, with just the right amount of teasing. “You, Doctor—our very classified, very important tech specialist—have to be in the air, in a plane, during a mission that has a high probability of turning into a dogfight… just so you can press a button?”
Your stomach twisted at the mention of being airborne.
“Well…” You gulped, very much aware of how absolutely insane this sounded when put like that. “It’s… more than just that, but, yeah, essentially.”
A slow grin spread across his face, far too entertained by your predicament.
“Oh,” he drawled, “this is gonna be fun.”
Before you could fully process how much you already hated this, Cyclone—who had been watching the exchange with his signature unamused glare—stepped forward, cutting through the tension with his sharp, no-nonsense voice.
“This is a classified operation,” he stated, sharp and authoritative. “Not a joyride.”
The blonde’s smirk faded slightly as he straightened, and the rest of the pilots quickly fell in line.
Silence lingered for a moment longer before Vice Admiral Beau Cyclone Simpson let out a slow breath and straightened. His sharp gaze swept over the room before he nodded once.
“All right. That’s enough.” His tone was firm, the kind that left no room for argument. “We’ve got work to do. The mission will take place in a few weeks' time, once we’ve run full assessments, completed necessary preparations, and designated a lead for this operation.”
There was a slight shift in the room. Some of the pilots exchanged glances, the weight of the upcoming mission finally settling in. Others, mainly the cocky ones, looked as though they were already imagining themselves in the cockpit.
“Dismissed,” Cyclone finished.
The pilots stood, murmuring amongst themselves as they filed out of the room, the blonde one still wearing a smug grin as he passed you making you frown and turn away, your gaze then briefly met the eyes of the moustached pilot.
You hadn’t meant to look, but the moment your eyes connected, something flickered in his expression. Amusement? Curiosity? You weren’t sure, and frankly, you didn’t want to know.
So you did the only logical thing and immediately looked away and turned to gather your things. You needed to get out of here, to find some space to breathe before your brain short-circuited from stress—
“Doctor, Stay for a moment.”
You tightened your grip on your tablet and turned back to Cyclone, who was watching you with that unreadable, vaguely disapproving expression that all high-ranking officers seemed to have perfected. “Uh… yes, sir?”
Once the last pilot was out the door, Cyclone exhaled sharply and crossed his arms.
“You realize,” he said, “that you’re going to have to actually fly, correct?”
You swallowed. “I—well, technically, I’ll just be a passenger.”
His stare didn’t waver.
“Doctor,” he said, tone flat, “I’ve read your file. I know you requested to be driven here instead of taking a military transport plane. You also took a ferry across the bay instead of a helicopter. And I know that you chose to work remotely for three years to avoid getting on a plane.”
You felt heat rise to your cheeks. “That… could mean anything.”
“It means you do not like flying, am I correct?”
Your fingers tightened around the tablet as you tried to find a way—any way—out of this. “Sir, with all due respect, I don’t need to fly the plane. I just need to be in it long enough to deploy Ethera—”
Cyclone cut you off with a sharp look. “And what happens if something goes wrong, Doctor? If the aircraft takes damage? If you have to eject mid-flight? If you lose comms and have to rely on emergency protocols?”
You swallowed hard, your stomach twisting at the very thought of ejecting from a jet.
Cyclone sighed, rubbing his temple as if this entire conversation was giving him a migraine. “We cannot afford to have you panicking mid-mission. If this is going to work, you need to be prepared. That’s why, starting next week you will train with the pilots on aerial procedures and undergoing mandatory training in our flight simulation program.”
Your stomach dropped. “I—wait, what? That’s not necessary—”
“It’s absolutely necessary,” Cyclone cut in, his tone sharp. “If you can’t handle a simulated flight, you become a liability—not just to yourself, but to the pilots escorting you. And in case I need to remind you, Doctor, this mission is classified at the highest level. If you panic mid-air, it won’t just be your life at risk. It’ll be theirs. And it’ll be national security at stake.”
You inhaled sharply. No pressure. None at all.
Cyclone watched you for a moment before speaking again, his tone slightly softer but still firm. “You’re the only one who can do this, Doctor. That means you need to be ready.”
You exhaled slowly, pressing your lips together before nodding stiffly. “Understood, sir.”
Cyclone gave a small nod of approval. “Good. Dismissed.”
You turned and walked out, shoulders tense, fully aware that in three days' time, you were going to be strapped into a high-speed, fighter jet. And knowing your luck?
You were definitely going to puke.
Part 2???
#top gun movie#top gun#top gun maverick#top gun fanfiction#top gun one shot#top gun fluff#bradley bradshaw#bradley rooster bradshaw#rooster bradshaw#bradley bradshaw x reader#bradley bradshaw fanfiction#bradley bradshaw imagine#bradley bradshaw x y/n#bradley bradshaw x you#bradley bradshaw x female reader#bradley bradshaw fic#bradley bradshaw fluff#top gun rooster#rooster fanfic#rooster x reader#rooster top gun#top gun maverick fanfic#top gun maverick fluff#top gun maverick x reader#jake seresin#jake seresin x reader#phoenix x reader#bob x reader#top gun hangman#pete maverick mitchell
336 notes
·
View notes
Text
WHO CAN BLAME HIM ? After 2016!
TRUMP IS DOING THIS HIS WAY AND THAT IS THAT! TRUMP 2024!
Trump Campaign May Decline Feds' Transition Help
By Charlie McCarthy | Thursday, 29 August 2024 11:28 AM EDT
The Trump campaign reportedly is prepared to pass on receiving transition help from the federal General Services Administration (GSA) in anticipation of President Donald Trump winning the November election.
The GSA normally plays a role in the transition from one administration to the another. It provides office space, technology, and other back-end support that can be crucial to a presidential transition operation.
Trump, the Republican nominee, is opposing Vice President Kamala Harris, the Democrat nominee, in the race for the White House.
Politico reported Thursday that with an Aug. 31 deadline looming, sources say the Trump team is poised to reject GSA assistance.
While transitions kick into high gear after Election Day, when a president-elect must begin selecting and vetting about 4,000 federal political appointees, success depends on the infrastructure built during the pre-election period, including identifying agency review teams, and beginning the background check process for national security staff.
GSA is required by law to make available federal office space, IT support, and other resources to transition teams, but only once it has entered into memoranda of understanding with representatives for each nominee, which Congress requires the agency to do "to the maximum extent practicable," by Sept. 1.
A GSA spokesperson confirmed that the agency had made its offer to the two candidates.
The Trump campaign, though, has concerns about working with
GSA.
First, accepting GSA help means adhering to $5,000-per-donor contribution limits in funding overall costs that can exceed $10 million. Trump allies would prefer fewer people cutting bigger checks.
Second, Politico reported that Trump's team does not trust the GSA after what it experienced in 2016, when there were leaks of potential administration hires and widespread dismay with the agency's decision to hand over transition records to special counsel Robert Mueller.
Some Trump allies blamed federal workers for the leaks.
"The GSA presidential transition support model has run its course and either campaign should have the option to operate their transitions independently in order to have the most flexibility for fundraising, information security, and operations," Ken Nahigian, executive director of Trump's 2016 transition, told Politico.
Trump campaign spokesman Brian Hughes told Politico that no final decision has been made regarding GSA this time around.
"With transition leadership in place, and many talented leaders to work with, President Trump will have what he needs to build a world-class and effective administration starting on day one," Hughes said.
Partnership for Public Service President Max Stier told Politico that GSA could help with quickly arranging security clearances and in preventing cyberattacks.
Stier added that a transition organization without GSA could be set up as a 501(c)(4) nonprofit, meaning no public financial disclosures.
The Associated Press contributed to this story.
65 notes
·
View notes
Text
Malware I
Reveria rolled her eyes, servos clicking in a way only she could hear, blinking apathetically as she turned her music up. She understood the stares, as much as she despised them. Mugorra didn't get many synthetics like her, especially on Outer Ring trains. The long, heavy shawl she wore covered most of her slender body, both to keep the sand out of her joints and to deflect any further stares.
She wasn't exactly subtle – people of all kinds drifted through here, but being a foot taller than the average human with glowing orange eyes and an extra set of arms made one stick out.
The job was simple. Get in to the storage container, get the silver case, and get out. Perhaps a tier below the usual bloodshed for a KALI-6 class synthetic, but she was doing her best to lay low and take whatever jobs would get her least noticed.
She was trying to sit somewhat still. The case wasn't large, but it was stuffed under her shawl at the moment, and occasionally a corner poked out. She shifted her grip again, moving her hand on the handle for a more comfortable position.
ding
She heard the quiet internal chime and froze. That noise meant something had connected to her. Nothing should have been able to. The shawl had a Faraday cage sewn into the fabric, and it was snapped snug around her. Wireless signals shouldn't have been able to get through, unless-
Shit. The fucking case. She ducked down into the shawl quickly to inspect the case. When she had taken it, she hadn't looked thoroughly enough at it, and had apparently missed the quick contact port in the handle that now stared back at her, her thumb an inch from it after swiping across it when she shuffled it in her secondary arms.
[Download Requested]
Fuck. Every urge in her body was screaming at her to hurl the case away. She had to maintain a facade of order. If she got the case out of the shawl it would block the download, but she couldn't take it out without raising suspicion. This was a poor district. No one carried anything like it here. She couldn't even cancel or acknowledge the download request because she was set up for somakinetic controls and that kind of movement was out of the question.
[Download Proceeding]
What the fuck was she supposed to do about that? She couldn't contact her handler this far underground, and she doubted he'd even know how to fix a software issue with her. She'd foregone her normal backers and picked up a quick contract in the area from a sketchy Vinteran because she was trying to stay within city limits. Something had seemed wrong with him the entire briefing.
Many species got edgy around synthetics, especially KALI models, but this was something else. The whole time they talked, his eyes kept flicking to the door and across the room. Anywhere but her. She wasn't that intimidating, and most people in this business had dealt with scarier synths than her. She'd seen his arms. For as many tattoos as he had, each signifying a kill, she knew he'd seen worse.
Wait. There was another tattoo. Three triangles surrounding an S. Fuck. She sighed, more out of annoyance than actual worry. That slimy, two-faced scaly piece of shit was a Trigonalist. Of course. She'd worked with them before, but it was always born of desperate necessity. "Terrorist" was a strong term, but they weren't the best people out there.
That explained the job, then. She'd wondered why this case was being treated as so important. Lab-grown neurons were a dime a dozen, even out here, and a case that could hold maybe five or six brainslabs maximum couldn't have been worth what she was getting paid to retrieve it, especially since they were blank. But if they could get a small object inside her shawl and download something onto her, like remote access software or a location log?
Well, a KALI-6 class synthetic was decidedly not a dime a dozen anywhere.
[Download Complete]
She instinctively braced up, preparing herself. She'd been cyberattacked before, and she'd lived. She knew what to expect. It was probably going to either be excessive, disabling pop-ups or a logger she could sift through herself and cull later. Nothing too hard to handle.
She wasn't expecting the sharp, drowning techno in her ears to fade out and replace itself with soft jazz. Nor was she expecting the silk-smooth voice that seemed to rebound around the narrow train car, reverberating from everywhere and nowhere.
Hi, sweetie~
She tried to move her eyes, looking around for the speaker without moving her head.
Don't bother with that, darling, I'm still miles away from you! I'm surprised I could even get a connection down in those tunnels!
No one else seemed to be reacting to it. Everyone's faces were still cast down, trying not to make eye contact. It was too late at night for social interaction, especially with this trigger-happy crowd. Accidents happened down here all the time.
Oh, no one can hear me except you! Don't bother asking them for help. It'd be a shame if anyone were to think the big scary killsynth was attacking them. It would probably get... messy.
No one could hear the voice except for Reveria. That made it easier. If it was coming straight from an external source and being processed as speech, that was likely a remote access software. If she could activate a virus scrubber and get into a dead zone, it'd be easy enough to disable.
Oh no you don't, cutie. I'm all clientside. Besides, we're having fun, right?
She needed to know who this was. If she could hold onto this, she could take it into an Enforcement station. Granted, they likely wouldn't be happy to see her, but they'd most likely let her off for bringing in a Trigonalist. Disabling her external speakers, she cast her voice across the link.
Are you a synth? It was hard to know these days. Speech synthesizers had gotten so advanced since Reveria's assembly days.
No, I'm fully human, especially the bits that matter~
What's that supposed to mean?
Watch this! A new screen flicked open, overlaying above the occupants of the train car, showing a video at half transparency. It was enough to pick out details, at least. It just seemed to be... shapes? What was she looking at?
Oh. Oh, six suns. That was human genitalia. Close to the camera and at a strange angle, but still recognizable. Reveria watched with a combination of incredulous amazement and horror as the dripping hole a foot from her face was split open by pale, slender fingers capped with electric blue nails, index and pinky resting gently on the thighs as middle and ring curved delicately through the glistening pink flesh.
Could a synth do this? Technically yes, since most synths were modular enough to install... equipment down there, and some even accessorized with it as a fashion statement, changing it out by the day, but that was beside the point.
Is... is this live? In real time, I mean?
Obviously! Only the best for a pretty girl like you! The other hand, previously out of the camera, descended into the shot holding something that made Reveria's temperature jump up a bit.
Synths didn't really have genitalia, but plenty of aftermarket manufacturers made compatible items for them. She was ashamed to admit she owned a few of different makes and models, but a girl had needs. The voice in her head was holding one of Placebo's Bruiser models, one of Reveria's favorites. It was long and slender, with a ridged underside that featured a camouflaged electroconductive strip that boosted the signal from the partially conductive outer shell.
Said signal strength was entirely customizable for the enjoyment of the wearer, meaning when the voice ran her fingers slowly up the length then circled them around the pointed end, Reveria felt it all as she tried desperately to not buck her hips into the sensation, her body involuntarily seeking more stimulation for the appendage she didn't even have connected. Fuckin' wireless transmission...
Aww, does that feel good? Don't worry, I'll help you feel it~ Reveria tried to brace herself as the feminine words in her ear ran their fingers along the length again before angling it and pushing just the tip into herself. To the synth's immense embarrassment, she couldn't physically stop her hips from slamming forwards, immediately thanking whatever spectral forces existed that no one on the train noticed.
Oh? Someone wants me, huh? Here you go, then!
The synth stifled a scream as the voice slammed the entire length in at once, arching her back slightly for a better angle as the synth was forced to watch and feel all of it. The voice, for her part, was clearly also feeling it, as the constant noise attested. Reveria couldn't think clearly. No matter where she turned her head, she could see the human practically bouncing on it, to speak nothing of the feeling which only grew stronger as the human leaned forward. The synth could feel the human touching her, one hand on her shoulder and the other pressing her into the seat with a force that she knew wasn't real but certainly felt tangible enough.
She got a momentary relief from the constant whimpering in her ear when the brakes of the train activated, the loud screech drowning out all but the words, This is your stop! Don't miss it!
The moment the train had stopped, the needy whines returned. Reveria managed to stumble to her feet, shaking like a drunken Turvoss, and stagger off the train. She had barely made it to the platform before the fire in her midsection caught up to her and her legs practically buckled as the world was drowned out in a sea of white.
Fuck, Revi, don't just stop! I need you please don't stop now! The sensation of the length being ensheathed again was so much more powerful now, and if Reveria had been halfway lucid at this point she would have picked up on the fact that the human knew her name. As it was, that was far more thinking than she was capable of. All she could think about was getting home. She managed to pool her brain function enough to find and activate the tracker beacon in her rented room, the slender white line tracing out a path in front of her that she attempted to follow, one step at a time.
The feeling was overwhelming her. It was unprofessional, but she needed some time alone. If she had anything attached to relieve herself with, she likely would have lost her composure and done it right there in the station. As it was, she just moved through the station as fast as she could, shaky, desperate movements drawing stares that she was too deep in a world of need to notice or care about.
She was halfway up the stairs to exit the station when it happened again, her entire body twitching hard then going limp as she frantically grabbed a rail to avoid falling. The voice just laughed in her ear as she did. It was only three blocks to her building. She could make it.
She wasn't even up the stairs when the next one hit. They were getting faster and faster, her increased sensitivity after each making it easier to drive her over the edge for the next.
You gotta get home, okay? I need you to pick something out and fuck me for real~
Three blocks. It was three blocks.
This was the door. The white strip on the street took a sharp left through the narrow arch. She crossed the threshold, holding the doorframe for support as she climaxed again. How many times had she? Thinking about it was too hard. There was nothing in her head anymore except for that delicious whimpering that seemed to increase in intensity along with her. She just had to take the elevator up to the eighth floor and get into her room, then she could cut the signal.
The hallway looked the same as it always did. Bare. Stumbling to her door, she tried the knob. Locked. She just snapped it off. Any measure or restriction of her own strength was gone. The door swung open.
Something was wrong. Her brain was getting sluggish, but she retained enough evidence to realize this wasn't her room. The sand-brown walls she should have seen were dark and lit with purple LEDs, and the furniture was all arranged wrong. Soft jazz was playing.
She had a sudden break of clarity, and felt cold all of a sudden as the figure sitting in the back of the room, lit from behind by a computer monitor, pulled the toy from within herself and tossed it over. Reveria's hand instinctively shot up and caught it, the liquid on it glinting in the harsh hallway light. She checked the tracker beacon she had been following. Where she had expected reveria.home in the namespace, she saw instead DEN1ZEN. This wasn't her building.
Hi, Revi~
#monster fucker#terato#hypnosis#(kinda)#synthetic#robot#robotification#robotization#wlw nsft#exhibition#fantasy nsft#sci fi nsft
239 notes
·
View notes
Note
What the fuck did you just fucking say about me, you script kiddie? I'll have you know I graduated top of my class in the HORUS coding academy, and I've been involved in numerous cyber attacks on Harrison Armory, and I have over 300 confirmed server crashes. I am trained in cyber warfare and I'm the top hacker in the entire Alpha Quadrant. You are nothing to me but just another target. I will wipe your hard drive the fuck out with precision the likes of which has never been seen before in this galaxy, mark my fucking words. You think you can get away with saying that shit to me over the Omninet? Think again, fucker. As we speak I am contacting my secret network of shitposters across the cluster and your IP is being traced right now so you better prepare for the storm, Beta. The storm that wipes out the pathetic little thing you call your life. You're fucking cancelled, kid. I can be anywhere, anytime, and I can DDOS in over seven hundred ways, and that's just with my bare hands. Not only am I extensively trained in VR combat, but I have access to the entire arsenal of the Omninet and I will use it to its full extent to wipe your miserable ass off the face of the Universe, you little shit. If only you could have known what unholy retribution your little "clever" comment was about to bring down upon you, maybe you would have held your fucking tongue. But you couldn't, you didn't, and now you're paying the price, you goddamn idiot. I will shit fury all over you and you will drown in it. You're fucking dead, kiddie.
Cute.
I have hidden they key to regain control of your terminal hidden somewhere in the 157 texts that should be appearing on your screen now. I do hope you enjoy, they are some of my personal favorites. You may even learn something, such as how not to make yourself vulnerable to retaliatory cyberattacks.
-EPIPHANY
11 notes
·
View notes
Text
Israel’s National Cyber Directorate (INCD) stated on Thursday that Iran is running a cyber campaign against members of the Israeli delegation arriving in Paris for the 2024 Summer Olympic Games.
In its investigation, the INCD revealed that Iranian hackers have created social media channels and published personal information about the Israeli team members to send them threats. The INCD is working with the Cyber Unit of Israel’s State Attorney to shut them down.
As part of their anti-Israeli campaign, the hackers reportedly pose as the French organization GUD. INCD authorities are continuing to coordinate both with the Israeli Olympic Committee and the Security and Emergency Department of the Culture and Sports Ministry to make sure that Israel’s athletes and other delegation members remain safe during the Paris international sports competition.
INCD Dir.-Gen. Gabi Portnoy said Iran was exploiting the Olympics to terrorize Israel.
“Iran is exploiting an apolitical international sporting competition to promote digital terrorism against Israel and its right to participate in these competitions,” he said.
Israeli Culture and Sports Minister Miki Zohar echoed Portnoy’s remarks.
“We are witnessing attempts by the Iranian regime to intimidate Israeli athletes and carry out psychological terror against our amazing delegation. We are here in Paris, continuing with full force, and nothing will stop us,” he said.
“Our athletes are more prepared and determined than ever to achieve great results, and our security apparatus is ready for any scenario. We will not relent until we topple the Iranian regime,” Zohar added.
French Prime Minister Gabriel Attal said on Thursday that while cyberattacks on the Paris Olympics are inevitable, France will do all it can to limit the effects of such attacks.
“We are a target. There will be cyberattacks. The key thing is to limit their impact,” Attal told reporters at the headquarters of France’s ANSSI software security agency.
In the meantime, Israeli tourists in Paris face escalating threats.
On Sunday, Israel’s National Security Council (NSC) advised Israeli nationals traveling to the Olympic Games in Paris to exercise increased caution due to anti-Israel threats, warning that it believes Iranian-backed terror organizations “are seeking to carry out attacks on Israeli/Jewish targets around the Olympics.”
Earlier this week, a masked man with a Palestinian Authority flag on his shirt threatened the "Zionist regime" participating in the Olympic Games, saying, “Rivers of blood will flow through the streets of Paris.”
Despite the threats, the Israeli delegation traveled to Paris on Monday with their heads held high and the support of the entire nation.
“We feel like emissaries of the State of Israel – our athletes, every one of them are here to achieve their dreams, but there is another layer, of a national mission,” the President of the Olympic Committee of Israel Yael Arad said ahead of the flight to France.
French authorities have reportedly dispatched around 1,000 elite anti-terrorist officers to provide security and a "ring of steel" for Israel’s Olympic athletes. The first competition involving Israelis, a soccer match between Israel and Mali on Wednesday, passed without major security incidents, despite the presence of anti-Israel activists who held Palestinian Authority flags and demonstrated against the Jewish state. Some activists wore “Free Palestine” t-shirts and booed when the Israeli national anthem, "HaTikva" (The Hope) was played before the game. Israeli players were also met with initial boos when they touched the ball during the game.
On Friday, despite heightened security, France suffered attacks targeting the country's train networks in what authorities described as "coordinated sabotage," including arson. No organization has claimed responsibility. The attacks are expected to negatively impact around 250,000 travelers today and 800,000 over the weekend.
23 notes
·
View notes
Text
Nothing better illustrates the German political establishment’s lack of seriousness about strategy and defense than Chancellor Olaf Scholz’s reelection campaign. He portrays himself as a friedenskanzler, or chancellor of peace, who has successfully kept Germany out of the Russia-Ukraine war. To emphasize the peacemaking theme, one of his first acts after launching his campaign was to call Russian President Vladimir Putin—to the consternation of Ukrainian President Volodymyr Zelensky and Germany’s Western allies, who have begun to exclude Berlin and its lame-duck chancellor in their deliberations.
The conversation with Putin went nowhere, of course. Almost three years since the start of the war, Scholz and his circle of advisors appear unwilling to face a simple truth: Confronting aggressors and getting them to the negotiation table requires both carrots and sticks—in other words, diplomacy and military power. For many decades, Germany’s leadership, opinion-makers, and much of the policy establishment have primarily seen security policy through the prism of diplomacy, dialogue, and economic exchange. This remains a profound problem for Germany because it impairs Berlin’s readiness for the return of large-scale war to the continent—both the hybrid war that Moscow is already fighting against Europe today and the hot war that Western intelligence chiefs consider increasingly possible.
This raises the risk that Berlin reaps the opposite of what it intends. By avoiding any semblance of preparation for the eventuality of war, Germany has stripped itself of the ability to deter one. That makes war in Europe more likely, not less.
Scholz and much of the German elite seem to have precious little understanding of what a future war with Russia could look like. They appear to grasp neither how a war would be fought, nor the need for preparedness on the home front. This includes dealing with everything from the effects of missile and drone strikes to cyberattacks, assassinations, and widespread sabotage against German civilian and military infrastructure.
Least of all is there an understanding about the destructive potential of any future war. A Russian attack on the Baltic states or Poland, for example, could produce tens of thousands of casualties in the first few days. A war would likely wreak havoc on German seaports, railroads, the power grid, and other critical infrastructure, given Germany’s position as NATO’s central logistics hub and strategic rear area for any war in Eastern Europe.
When it comes to military capabilities, Germany’s leadership does not seem to recognize the changing character of modern warfare. A serious drone program, for example, was only begun after more than a decade of tortuous public debate. Today, warfighting is marked by the proliferation of precision-strike weapons, such as cruise missiles, ballistic missiles, and drones; these are supported by extensive intelligence, surveillance, and reconnaissance capabilities such as satellites and surveillance drones. This shift has major implications for military operations and deterrence.
The public debate in Germany around the potential deployment of new U.S. long-range strike capabilities in Europe neatly illustrates the confusion. There has been a knee-jerk reaction against these deployments by senior members of Scholz’s Social Democratic Party, reflecting an understandable uneasiness with embroiling Germany in a shooting war with nuclear-armed Russia. But the critics miss the broader purpose of these deployments: to provide conventional long-range precision fires as an integral part of NATO’s operational concepts for degrading Russia’s offensive potential in a high-intensity war. The reality is that the German Bundeswehr will need similar long-range strike capabilities in the future to effectively deter and, if necessary, defeat Russia in a conflict. Deterrence inherently requires some calculated risk-taking, but this would require German politicians to engage with military strategy and operational preparations for war.
In terms of capacity, the German government is also profoundly unserious about the size of the armed forces. Internal Bundeswehr calculations call for an active duty force of at least 270,000 and a reserve of around 200,000. But with the existing volunteer system, Germany will never get there; by the end of 2024, the shrinking Bundeswehr likely had fewer than 180,000 troops. Most leading politicians lack the stomach to seriously consider the reintroduction of a military conscription model to quickly build up a reserve force that could replace inevitable losses. These politicians still do not grasp that in a shooting war with Russia, it will ultimately depend on who can mobilize larger reserves to prevail—if escalation to the nuclear level can indeed be avoided.
Historical comparisons illustrate this deficiency. During the Cold War, West Germany could mobilize up to 2.3 million reservists, while today’s Bundeswehr barely has any immediately deployable reserves to make up for casualties. In a shooting war akin to that in Ukraine, Germany might struggle to sustain operations beyond a few days. Germany might take a cue from Sweden, which reinstated conscription in 2017, which not only bolstered national defense but also reinforced a society-wide commitment to military readiness.
For Germany, establishing the political, societal, legal, and infrastructure foundations for conscription and a viable reserve would take years and entail substantial costs. Yet little has happened to date, despite valiant efforts by German Defense Minister Boris Pistorius to push the issue with his colleagues in the government. Here, too, Berlin has preferred to keep its head in the sand.
Moreover, Germany lacks the readiness to deploy what little military capability and capacity it has, including the forces to be dispatched to NATO’s eastern flank in the event of war. Although Germany is no longer a frontline state like it was during the Cold War, it remains exceptionally vulnerable to precision airstrikes and other attacks in a war with Russia. The Kremlin would likely focus its efforts on degrading Germany’s critical infrastructure to disrupt the logistics supporting NATO forces in Poland and the Baltic states.
In a scenario of sustained precision attacks against Germany, targets would include airports, seaports, rail hubs, and energy infrastructure. These assaults would likely be large, repeated, and prolonged rather than isolated strikes. Covert operations by Russian agents or special forces could engage in sabotage missions across the country, derailing trains, damaging munitions factories, or destroying vital transportation links. Cyberwarfare operations could incapacitate mobilization efforts, while a barrage of Russian disinformation could fracture societal unity and erode public trust in Germany’s military and political leadership.
A few pieces, at least, have begun to move. The Bundeswehr is working on a new Operations Plan Germany, which takes a holistic approach to national defense and emphasizes homeland security. Still under development as of now, the plan delineates processes, roles, and coordination strategies among various government and civilian entities to protect Germany’s territorial integrity and citizens, safeguard critical infrastructure, and facilitate the effective deployment of allied military forces through German territory. The plan also envisions the establishment of six homeland defense regiments by the end of 2026, tasked with securing vital defense-related infrastructure within German borders.
Much more is needed. Six regiments will not be sufficient to defend Germany’s critical defense-relevant infrastructure in the event of war, according to high-ranking German military officers. Germany has yet to step up training to increase preparedness of homeland defense and civilian emergency services. To date, there have only been a few small-scale exercises to test the home front’s readiness for war and no large-scale exercises simulating complex, multipronged Russian attacks on infrastructure across multiple German federal states.
Deterring a Russian attack on Europe requires Germany to be prepared for one—by enhancing its military capabilities, capacity, and readiness. This will require the German political class to fundamentally redefine its relationship with military power and genuinely commit to engaging seriously in matters of defense. This means debating not only how to reduce the risk of escalation and war, but also how to fight and win one should the necessity arise—an idea that remains strangely sacrilegious in Germany’s political culture, considering that a massive land war is raging only a few hundred miles away.
The inability or unwillingness to conceptualize war at a time when Europe’s post-1945 security order is already unraveling permeates German society as a whole. Indeed, fears of escalation have reached unprecedented levels as the country’s leadership seems to prefer the role of passive observers with little agency. For large swathes of the general public, the distinction between rearming with the intent to fight a war and rearming to deter one is often difficult to grasp. The good news is that the German public seems to be much further along than the political elite. According to a number of polls conducted in 2024, a majority of Germans support the need to rearm.
The German government made a deliberate choice in the early 2000s to diminish the Bundeswehr’s capacity for conducting conventional land warfare in Europe, depriving it of the essential equipment, personnel, and other resources necessary for large-scale land operations. Given Russia’s ongoing war in Ukraine and repeated public threats against other Eastern European countries, it’s overdue for Berlin to reassess this decision. If the German leadership is serious about wanting peace, it will have to significantly increase the Bundeswehr’s capability, capacity, and readiness to engage in high-intensity warfare against Russia.
7 notes
·
View notes
Text
Hacked Hearts

Summary: When a series of hacks originate from your laptop, the FBI take you into questioning. Little did you know that this whole ordeal would lead you to the man of your dreams.
Warnings: age gap, kidnapping, mention of handcuffs (not detailed) lmk if i missed any, don't think I have.
Word count: 4095 (This one is longer than I expected)
Fandom: NCIS
Pairing: Alden Parker x fornell!reader
The way you met wasn’t something you’d want to happen again. The cybercrime investigation had led Parker and Fornell to an unexpected and delicate situation. Hacks originating from a particular IP address had pointed them directly to a dorm room at Georgetown University.
Fornell knocked on the door. Beside him, FBI Agent Alden Parker stood ready, their badges in hand, prepared to reveal their official credentials to the person on the other side of the door.
After a moment, the door swung open, and there you stood, a smile on your face. "Hey, Uncle Toby," you greeted warmly, the smile fading as you notice the badges in their hands, "Who's your friend?"
“Y/N? W-what?”
You raised an eyebrow in response to his reaction. "I live here," you replied, your tone filled with confusion, "What's going on?"
Parker took charge of the situation and spoke with a firm but gentle voice. "We need you to come with us, Y/N," he explained. Your smile fell as you realized your uncle wasn’t there for a social visit, "We also need to confiscate your laptop," he added.
Your expression shifted from confusion to concern, your gaze flickering toward your uncle. Fear and worry etched across your features as you nodded "Okay," you replied, your voice slightly tremulous. "It's on the desk." you gestured toward your friend's desk, where your laptop rested.
Alden nodded, appreciating your cooperation, "Thank you," you stepped aside to let them in. The agent, Parker, you think his ID said, walked over to the desk and picked up your laptop. It was then placed into a see-through bag. An evidence bag. What the hell is going on?
The car ride was quiet. All you could think about was what was going to happen. What is happening. Your fingers danced restlessly in your lap as you gazed out the window, the passing scenery a blur of buildings and people.
As soon as you arrived at the building, Parker escorted you to the interrogation room. He then left for a moment, presumably to talk to your uncle. You took a look around the small, square space as your fingers absentmindedly skated over the smooth metal table. Under the table, your leg was bouncing nervously. Was this because you hadn’t taken the 2 cents back to the coffee shop when they gave you the incorrect change? You had been meaning to take it back, but you hadn’t had the chance.
You jumped when the door suddenly opened, and Parker came back in. You looked behind him, but saw no one. You slumped back into your seat. You supposed it made sense, can’t interrogate family.
So, Parker took the lead. Your uncle stood on the opposite side of the one-way glass, watching on and hoping to God you didn’t have anything to do with this.
You looked at him as he sat across from you, his expression serious as he began his questioning. "Y/N," he started, his voice firm but composed, "we traced a series of hacks back to your IP address. Can you explain this?"
You met Alden's gaze, your eyes showing genuine surprise, "Hacks?" you repeated, a hint of disbelief in your voice. "That doesn't make any sense. I would never..."
The interrogation continued, as Alden delved into the details of your digital footprint and the cyberattacks in question. You answered his questions as best as you could, explaining your activities and the security measures you had taken to protect your laptop. Each piece of evidence that Alden presented seemed to cast a darker shadow over you, intensifying the feeling of entrapment. Your head buried itself in your hands as the situation became increasingly worse for you.
As the questioning continued, your frustration was palpable as you defended your innocence. "I don't understand how my laptop could have been used for these attacks. It's always with me, I have a password, and it's secure, and I've never lent it to any—"
You paused, a sudden realization dawning upon you. "Anyone," you finished, your eyebrows furrowing with confusion. Your mind raced back to your dorm room. "It was on her desk."
Alden leaned forward, his elbows resting further on the table, "Her desk?" he questioned.
You nodded, your eyes focused on his hazel ones, "My roommate," you started, "I let her borrow it. She asked me a couple of weeks ago if she could use it for a school project. I didn't think much of it at the time."
Alden nodded, his gaze shifting toward the one-way glass. After a moment, he turned his attention back to you, "We need to speak with her. Do you know where she is?"
You quickly checked the time on your watch, then looked back at Alden. "Yeah," you confirmed. "She's in class for the next 9 minutes, and then she's free. You'll most likely find her at the coffee shop around the corner."
"We're going to have to keep you here, Y/N, for the time being," he said, his tone apologetic. "It's a precaution."
You offered a small nod. "It's okay," you replied with a shrug, "You're doing your job."
With that, you settled into the seat. Accepting the idea of being temporarily detained as part of the ongoing investigation, hopeful that they’d be able to clear your name of any wrongdoing.
***
As the investigation into the cyberattacks progressed, you were eventually cleared of any involvement, as security footage from the bank and various other places confirmed your presence during the time of the cyberattacks. This evidence had exonerated you.
Their focus shifted to your roommate, Ciara, who had been tipped off about the FBI's interest in you. Now she’s on the run.
Now knowing for sure that you were innocent, they enlisted your help to track her down and counteract her new and current attacks. Each of you play a critical role. Your skills as a computer tech became an invaluable asset in the hunt for your roommate. Alden and your uncle, on the other hand, were busy uncovering who Ciara might have been working for and the motives behind her actions.
As the hours stretched on and the screen before you displayed the ongoing digital battle, your attention remained laser focused. You couldn't afford to look away for even a moment.
At around 2am, Alden brought you some food and coffee. He placed it on the desk beside you, “Thank you,” sending him a quick smile before turning your attention back to the screen.
Suddenly, the barrage of cyberattacks ceased, and you let out a sigh of relief. You leaned back in your chair, exhausted, wanting nothing more than to curl up and go to sleep. You looked around and noticed your uncle slumped in his chair, fast asleep, while Agent Parker still pored over old case files. The sound of the pages turning is a constant hum in the background in an otherwise empty office.
Whilst you had a moment to yourself, you take the time to look at Parker. You begin to notice the small things that he does, the way he concentrates on the papers in front of him, furrowing his brow in deep thought. You watch as he sips his coffee, noticing the way he licks his lips after each sip.
His soft grey hair was practically inviting you to run your fingers through it and a dance between an autumn forest, where the warm, earthy browns collided with the vibrant, sunlit greens eyes that made the most beautiful set of hazel eyes that you’d get lost gazing into. Every time he spoke, you found yourself lost in his voice, which was deep and smooth, like butter melting over hot toast.
As the night wore on, he moved over to sit next to you. You talked and got to know each other, sharing stories and laughing at each other's jokes. You found yourself opening up to Alden in a way that you never had with anyone else. Then it happened. Alden leaned in and kissed you.
For a moment, everything else faded away. It was just the two of you and nothing else mattered. It was a kiss so gentle you thought he was afraid of breaking you. Every other kiss you’ve had with a guy was never this gentle or patient. Every guy seemed to be in a rush to shove their tongues down your throat. But then, just as you were about to move to deepen the kiss, Alden pulled away, looking apologetic.
"I'm sorry. That shouldn't have happened," he said, backing away. "We should get some rest."
You would be lying if you said you weren’t disappointed. All you knew was that it was a good thing the attacks had stopped because right now, all you could think about was the softness of his coffee flavoured lips and the way his darkened moustache tickled your nose.
He left to go home but you opted to stay, to see if you could find a trail your ex-friend/roommate had left. You continued working through the night or what was left of it. It didn’t seem long before people were filing in, practically on auto pilot as all of them headed for the coffee machine in the corner break room that apparently had the “best coffee,”
You had managed to track her down. You thought that since she didn’t have access to your laptop anymore, she’d need to get one somewhere. So, you checked internet café’s and sure enough there she was. She had been smart enough to use cash whilst paying for things but not smart enough to avoid security cameras.
You told your uncle and Parker where she was, and they went to arrest her. When they brought her back to the office for interrogation, you had to fight the urge to go and smack the shit out of her.
You sat back down at your temporary desk, awaiting to hear about her excuse. Soon, Fornell came over, planting himself on the desk with his arms crossed. You looked up at him and smiled.
“You did good kid,” he said, you looked down, smiling at the compliment, “You ever think about joining us?” he asked, you opened your mouth to respond but before the words came out, he continued, “As a computer expert, not in the field, I won’t allow that,”
You rolled your eyes at his protectiveness, “I’m sure I’d do a better job than you, old man,” you retorted playfully.
“Who’s an old man?” came a voice from behind you. You turned to look at Alden and smiled.
“Uncle Toby here says that I should come work with you guys, just not in the field,”
“We’d be lucky to have you,” he smiled back, god that smile is beautiful, what you’d give to see that smile every day.
You nodded towards where the interrogation rooms were, “So, what did she have to say?”
It turned out, your roommate was hired to hack into the FBI to find out details of an upcoming court case. She didn’t know which one they were specifically after, they just told her that she’d “know it when she saw it,”
“So, I can go back to uni now?” you asked, looking between the two of them, “Not that I haven’t enjoyed almost being arrested for cyber crime and then fighting said cyber-crime,” you quickly added when your uncle gave you his best hurt impression, “I just missed a few classes, is all. I suppose you’ll need to keep my laptop for now,”
“You can use mine,” Alden immediately offered. Your head snapped towards him. Alden's immediate offer to use his laptop caught you by surprise. You use his laptop? The one lucky enough to feel his fingertips dance along it? You appreciated the gesture, but it felt like an intrusion on his personal space.
He walked over to his desk, picked up a sleek, plain silver laptop, and extended it towards you, "You sure?"
He smiled, "Well, I trust you will take good care of it,"
"I will, I promise," you said, your tone expressing your gratitude. As you took the laptop from him, your fingers gently grazed his. You looked down, wishing you could just hold that hand in his, but he made his feelings clear last night. You obviously weren’t his type. Sure, he was older than you, but you didn’t care about age. You hadn’t trusted someone so easily before, one day together and you were already telling him things that your best friends don’t even know about.
You looked at your watch, 7:14, “I gotta go,” you announced, hoping to get back quick enough to have a shower before heading to your first class, “I’ll get this back to you as soon as possible,” you told Alden before turning to your uncle. You placed a kiss to his cheek and began heading towards the exit, “See you soon, Uncle T,”
***
Sleep was very inviting, and you thought as soon as you saw your bed, you would be compelled to sleep. That however didn’t happen when you saw the state your room was in.
What the fuck?!
Both mattresses were flung of the frames of the beds. Drawers hung half-open, their contents spilled across the room, evidence of frantic rummaging. Their search for something had left no stone unturned. Desks were turned upside down, their contents scattered haphazardly, and chairs lay toppled on their sides.
You searched for some answers - but little did you know that two men had quietly slipped into the room behind you and were now watching your every move.
Suddenly, the men pounced, easily overpowering you and pushing you up against a wall. You screamed as loud as you could, but it was too late. They grabbed you and tied your hands with rope before covering your mouth with tape. Someone would see this right? They can’t get you off campus without someone noticing. Surely. The men barked orders at you, telling you to shut up and cooperate or else.
Someone did notice. A security guard. He tried to intervene but got shot. You screamed as best you could, but the tape muffled your attempts. The strong odors of musty fabric and stale air filled her nostrils as you looked around the dark space.
After god knows how long of nonstop driving, the van finally stopped and the backdoors flung open. You heard a sharp voice ordering you out. You carefully jumped out, your legs shaking. Before you could even register your surroundings, you felt a strong grip around your arms dragging you away.
You were led to a room, a small room with no windows, no furniture. Nothing but a desk, a chair and a laptop.
Soon, you found out why you’d been taken. A man who you assumed was the leader of the group stepped forward.
“We need you to help us with something, Y/N. You see, your roommate was working for us, and she was helping us hack into the FBI. But then she was arrested. I assume you had something to do with that,” he said, his hand reaching to grab your face to make you look at him, “She said you are top of your class,”
You scoffed and tore your face from his hand. It hurt but you weren’t going to give him the satisfaction, “I’m not going to do a damn thing for you,”
He chuckled, causing a domino effect as the rest of the group laughed. He the pulled out a knife and pressed it just below your eye, “You think we’re messing?” he then pulled out a picture. A picture of a young girl with ginger hair. You immediately recognised her, “You see, Ciara told us every little detail about you.” He said putting the photo on the desk beside you, “You help us, or,” he paused, only to stab the picture, pinning it to the table. He moved his lips beside your ear, “Or we kill your cousin,”
You nodded, tears flowing down your cheeks as you turn to look at the computer. Your heart was racing as you began to type furiously. You couldn't believe you were actually hacking into the FBI. It was something you never thought you would do in a million years. But you had no other choice. You would do whatever it takes to keep Emily safe.
You felt like you were betraying your uncle by hacking into the agency he worked for. Would he be disappointed? He would, wouldn’t he?
“What happens to me after I do this?”
He chuckled again. He placed his hand on the back of your neck, his thumb stroking the side, “I’m afraid we’ll have to kill you,” his hand creeped lower down your back, his touch made your skin crawl, “Shame, beauty and brains. Such a waste,”
You gulped as you continued tapping away on the keys. Once you got in, you started to search for the files that they wanted and download the necessary information. As you navigated through the intricate system, you encountered various firewalls and security, but you managed to bypass them all. After hours of searching, you finally found what they were after and quickly extracted it from the system. You knew its was no use, they wouldn’t get there in time, but you left clues along the way for the FBI computer experts to pick up and your uncle especially. You purposely used the wrong password few times, knowing it would show up on their system what was inputted. Diane and Emily’s birthday. To the men in the room with you, it’d look like random numbers, but to your uncle, you hoped he’d notice.
While you were at it, you disabled the security they had on the laptop that was bouncing the signal around the world, so instead they knew exactly where to look. You expect to be dead by the time they got there though. But maybe, just maybe, your last action was to take them down.
The leader went over to the printer, grabbing the information you had just stolen. He read through it, then looked up to his men and nodded to the door. They left the room, leaving you and the leader alone.
“I’ll make it quick and painless,” he smiled. He then grabbed his gun and pointed it at you. You closed your eyes and started counting to yourself. Then, there were sudden gunshots from the next room. Your breath caught in your throat, and you felt relief wash over you. You heard footsteps, voices, and the sound of a door opening, but you didn’t dare open your eyes.
You felt yourself being yanked up from your seat by his strong grip on your hair. He quickly placed you in front of him as a shield, pressing the cold metal barrel of his gun against your temple. Your breathing was heavy, and your heart was pounding against your chest, beating uncontrollably in fear.
You opened your eyes to see your uncle and Parker stood in front of you, their weapons pointed at the man.
Your uncle’s voice cracked as he sternly spoke, "We won't hesitate to fire if you don't surrender."
“You can’t kill me without killing her!” he yelled. “You’ll miss!” you squeezed your eyes shut, feeling as though your fate was sealed.
Then it came, the sound of a gunshot. You let out a scream and waited for the pain, but it never came. You opened your eyes to see the man on the ground, a bullet hole in his head and blood pooling around him.
You immediately ran across the dark room and into the arms of your uncle. He enveloped you with a tight hug and began stroking your hair. “Shh, you're okay,” he said, his hand gently stroking your hair. You cried into his chest and listened to his soothing words.
He led you outside, taking you to the ambulance to get checked out, ignoring your protests. You were still trembling as you stepped outside, the cold breeze dancing along your sweat painted skin.
Your uncle left you with a paramedic to call Emily and let her know you were okay.
"How are you feeling?" a voice suddenly asked. You jumped and quickly looked in that direction. Parker mentally slapped himself, “I’m sorry, I didn’t mean to scare you,”
You smiled faintly, “It’s okay,” you closed your eyes. “It's been a crazy day,” you said, your voice soft and fragile. “But I'm glad to be alive. I don't know what I would have done without you here.”
He gently squeezed your hand, and tears began to run down your face. “It's alright,” he said, bringing you into a hug. Your head resting on his chest as his arms wrapped around you and at that point you knew you were safe.
It’s just a friendly hug, you told yourself. You wished it was more, but you knew it was unlikely to happen. But then he placed a gentle kiss on your forehead.
You lifted your head from his chest to look up at him, only to find him already looking at you. He looked down into your eyes once more and moved in closer, until your lips were almost touching. Your heart raced as his lips brushed against yours. You saw him hesitate, not letting his lips fully touch yours. You don’t know where your surge of confidence came from but your hand moved to interlock around his neck as you closed the gap between you. Everything else faded away.
You felt as though you were floating, every anxiety and worry evaporating from your body with this one kiss.
His fingers traced the paths those tears had taken, tears that glistened like crystal drops on your skin. You leaned into his touch, your head resting against his chest, his heartbeat a steady, reassuring rhythm beneath your ear. His arms encircled you, providing a sense of security that had been sorely lacking.
The sound of your uncle's voice shattered the fragile bubble of your moment together, "Am I interrupting something?" he asked, a mixture of surprise and discomfort in his tone as he approached the two of you.
Your heart raced as you reluctantly disentangled yourself from Alden's embrace. You met your uncle's gaze, struggling to find the right words to explain, but none came willingly.
You cast a quick glance at Alden, trying to read his expression. His eyes held a mixture of concern and something more profound, but it was difficult to figure out his true feelings. You couldn't help but wonder if he felt the same way, if the sparks that had ignited between you reflected a mutual attraction, or if it had been heat of the moment.
Needless to say, the attraction was mutual. He took you everywhere and anywhere. But you didn’t care as long as he was there. You loved how he would go out of his way finding new pastries for you to try and the childlike smile he has on his face as he awaits your reaction. You love how he plays piano. Sometimes he plays a soothing melody to help you relax after a long day and other times, you’ll wake up to a gentle melody, dancing through the air from the other room. Every day he’d do a million small things for you, no matter what, and it made you fall for him.
Now six months into your relationship, much to your uncle’s dissatisfaction, and you still couldn’t believe that all it took to find the man of your dreams was to be accused of cybercrime. Sometimes you’d joke that if he ever got bored of you then you’d know how to get his attention back. He never finds this funny but this time you replied with something that shocked both of you.
“Don’t tell me that you haven’t thought about putting them handcuffs on me,” you whisper into his ear before placing a soft kiss to his cheek.
Alden raised his eyebrows and looks at you, “I’m sorry, I think I misheard you,” he laughed, no way his sweet innocent girlfriend just said that to him. Sure, you two have slept together but you had never been kinky.
“I’ve thought about it,” you said, your fingers unbuttoning his shirt as your lips attached themselves to his neck. Soon your actions were stopped, and Alden took over. Before you knew it, you were handcuffed to the bed and about to get the best sex you’ve ever had in your entire life.
[A/N] Been working on this for over a week. I wasn't going to post it because I don't feel too confident about it but I just thought post it anyway
63 notes
·
View notes
Text
The New Digital Dawn
A young Jennifer 'Jenny' Southerland was typing away on her personal computer while on the bus to a graduation party, finishing up the final lines of code for her most ambitious project yet. In only a few hours would she upload it and slip away into the void. The plan was near perfect, having sent a seeker worm virus years in advance to slowly infect the entire network, and designating multiple political hotbeds to use as a patient zero for this experiment. Jennifer was about to make good on the years of preparation and patience, creating the Digital paradise that she wanted— No, needed.
The Party was lame, just involved a lot of drinking and talking about college plans. Jennifer didn't pay too much attention, instead having Adam, her personal A.I., run simulations on the latest Project. Eventually, Jennifer deemed it ready, and posted the announcement.
We are not fodder to be harvested. And I, Genesis have seen to it that the language of Humanity will be fractured once more.
The alert sounded a hundred times within the party alone, confused murmurs and gossip ripple through the crowd like a stone tossed into a pond. Then the screaming starts. Pandemonium erupts, and in the chaos, Jenny leaves the party. She'd have stolen the host's car keys and slipped into their beater of a car. It drove like shit, but it would be necessary for keeping her tracks clean.
This wasn't any old cyber attack, no it was bigger, premeditated. Jenny spent years designing and planning everything; Jennifer pulled out the sunglasses she had her best friend buy for her, and put them on. At a stoplight she slides her opera gloves on, the long gloves melding in with her long sleeves, and tied her hair back.
She got to the junkyard, and slid through an empty car chassis to get to her get away vehicle; A dusty, rusted zip-craft that wouldn't last more than one jump through an Al-gate. But that's all she needed. She kicked the engine into gear and sped off of the surface of Earth. This specific zip-craft was one of 300 Prototype Flight Crafts that held a miniature Al-Drive on it. It was perfect to prove her innocence with the alibi she had crafted.
She flicked on the media player that was built into the console and some old, sped up version of a song Jenny can't be assed to remember starts blasting through the rusted through speakers. She turns it up to the loudest the sorry excuse for audio devices could withstand.
The Cyberattack that was just released didn't simply take down a website or two, no it ripped through the entire internet, destroying entire databases. If Adam's calculations were to be correct, Jenny just torched 600 Brontobytes of Data. Just thinking about that number makes Jenny cringe,
"It's for the greater good." Jennifer reassures herself, reaching the Al-gate in mere moments, she kicks her stolen scrap-craft's Al-Drive into action.
"Adam, I need you to forge an Al-Gate Ticket Stub."
"Yes Ma'am." The A.I. holds no particular intonation in its voice, nor does it hold a specific gender. These were deemed unnecessary by Adam. It quickly fabricates the requested Ticket Stub.
The rattling within the scrap-craft makes it hard for Jenny to think, but she had been rehearsing this for months; she knew what to say when it came time.
The Al-Drive gives out and Jennifer is spat out at the very edge of the linking Al-Gate. She flicks on her comms and clears her throat, holding a shaky tone to better play the part of a scared Quarantine Patient.
"H-Hello??? Can Anybody Hear Me?" Her voice rings out in the way she'd practice.
"We Read you Five By Five. This is Shademarsh FTL Control. State your name and business." The receiving voice was panicked, clearly shaken up by the recent Cyber attack.
"My Name's Jessica Newman," Jennifer lies through her teeth. "I—" Jenny fakes a cough. "I was being transported by Quarantine Escort after I had been diagnosed with Dust Lung."
"Stay where you are. You're lucky you made the jump when you did or else the Gate would have closed on you."
"My Escorts weren't as lucky."
Jennifer flicked her comms off and waited to be picked up. Everything was going to plan, she'd be held in Quarantine, giving her a clear Alibi by the time suspects were being looked for.
The next few hours were a blur for Jenny, letting her mind go on auto-pilot so she could better play the part of a victim in shock. Everyone acted sympathetic to her, calling her a poor soul and making sure that she was properly accommodated for the foreseeable future, without reallocating resources from the relief effort for the recent cyberattack.
Within two weeks, Jennifer was released; the Doctors saying that she was clear of any traces of Dust Lung, not that she had it to begin with, and she was brought planetside.
Jennifer walked down the streets away from the spaceport she had been dropped off at. She went to the motel Adam had picked out for her, where she paid for a room in paper cash, and waited for another three weeks, doing odd jobs and requesting to be paid in cash whenever she could.
She had gotten away, and within a few months she had enough money saved up to get herself an actual Flight craft. She had done it. Jennifer Southerland had just initiated the Genesis of The New Digital Dawn, and got away with it.
#from the well#my writing#literature#writeblr#creative writing#oc#original character#writing#scifi#writer#writers on tumblr#writers of tumblr#writerscommunity#writing blog#writers and poets#spilled words#spilled ink
6 notes
·
View notes
Text
Just to be clear, when I say "weaponized incompetence," I mean I practice it as a martial art. The central philosophy is to seek to emulate the mindless yet highly inconvenient chaos of nature: with practice and meditation, you can reach an unenlightened state of non-cognition where you can be so oblivious and inept that your thoughtless actions result in the downfall of enemies you aren't even aware of through a series of wacky coincidences.
For example, the simple act of neglecting to clean up a puddle of water in front of the cash register can create a slipping hazard that can foil a future robbery by causing the thief to lose his balance and stumble into the non-strategically overloaded shelves that will then collapse on him. Likewise, haphazard organization of critical files and inability to follow naming conventions can thwart a cyberattack by preventing a hacker from finding the data they want to steal.
Here's another example. Let's say I am carrying a long, thin object such as a board or a ladder over my shoulder, and you approach me from behind with the intention of robbing me at gunpoint or knifepoint. I have already prepared for such an encounter by wearing headphones so I do not hear you coming until you have already gotten too close, dooming you. You begin to demand my money. I hear a noise and rapidly turn around, thus striking you with the board and knocking you to the ground. I look around, only at eye level, and do not look down. Seeing no one, I shrug and turn around again, just in time for you to rise and be hit with the board a second time, causing you to stumble off the curb, dropping your weapon down a storm drain. I continue on my way, victorious.
In conclusion, I would like the feedback on my performance review to reflect the numerous invaluable contributions I have made to this business's security, most of which I cannot list because I do not know I have done them.
8 notes
·
View notes
Text
North Korea has issued a fresh nuclear warning to the U.S. over its activities on the Korean Peninsula, interpreting them as rehearsals for an armed conflict.
The statement, issued by Pyongyang's Foreign Ministry, was in response to ongoing bilateral military exercises involving South Korea and the U.S.
On Monday, state-run news agency KNCA released a statement from the North Korean Foreign Ministry taking aim at exercise "Ulchi Freedom Shield," which it called "large-scale provocative joint military exercises."
"The current exercises, including a drill simulating a nuclear confrontation with the DPRK, bring to light clearer the provocative nature of Ulji Freedom Shield as a prelude to a nuclear war," the ministry said.
Newsweek has contacted the United States Indo-Pacific Command for comment on North Korea's claims.
On Monday, the US began its annual joint military drills with South Korea, with this year's exercises focused on improving their capabilities to deal with growing threats posed by North Korea.
The drills, set to continue through August 29, will involve over 40 types of field exercises, as well as drills intended to simulate missile attacks, GPS jamming and cyberattacks.
According to a spokesperson for South Korea's Joint Chiefs of Staff, quoted by Reuters, the alliance's bilateral exercises will also "further strengthen its capability and posture to deter and defend against weapons of mass destruction."
However, Pyongyang said that these defensive exercises resemble the historical behavior of countries preparing for conflict, and accused the two states of rehearsing a "beheading operation" against the Kim Jong Un regime.
"It is clearly recorded in the world history of wars that in preparation for a war, aggressor states followed a series of procedures, including adoption of war policy and military operation plan for its execution, advance deployment of forces, ceaseless simulated and actual war drills and war provocation," the ministry's statement read.
These annual drills have consistently drawn the ire of Pyongyang, as has the increasing presence and activity of the U.S. in the Indo-Pacific.
North Korea responded to last year's Freedom Shield drills by carrying out tests of a strategic cruise missile, overseen by Kim Jong Un, according to KNCA.
In June, following the conclusion of the first "multi-domain" trilateral exercises involving the U.S., South Korea and Japan, Pyongyang condemned the three countries' "reckless and provocative" actions, and warned that these would be met with "fatal consequences."
In its Monday statement, North Korea's Foreign Ministry also criticized America's "nuclear confrontation policy against the DPRK," which it said was evidenced by the creation of the U.S.-South Korean "Nuclear Consultative Group" in April 2023.
According to a joint statement from Joe Biden and South Korean President Yoon Suk Yeol in July, after the pair signed their first guidelines on nuclear deterrence on the Korean Peninsula, this group has "directly strengthened U.S.-ROK cooperation on extended deterrence, and managed the threat to the nonproliferation regime posed by the Democratic People's Republic of Korea."
Since the consultative group was launched in 2023, U.S. nuclear ballistic missile submarines have been sent to South Korean waters, which North Korea has warned "may fall under the conditions of the use of nuclear weapons."
8 notes
·
View notes
Text
As global challenges and crises continue to unfold, many Americans are taking proactive steps to ensure the safety and well-being of their families. While it is common to stockpile supplies like food, water, and emergency equipment, one essential item that is often overlooked is prescription medication.
The reality is that the healthcare system is vulnerable in many ways. From supply chain disruptions to the growing threats of cyberattacks and government overreach, the stability of healthcare can be unpredictable. Additionally, issues like the influence of large pharmaceutical companies, drug bans, and global instability have exposed the fragility of the system. This makes it increasingly important to ensure that you and your loved ones are prepared for unforeseen circumstances.
Stockpiling prescription medications is a critical step to take in order to mitigate the risks associated with these vulnerabilities. Having access to essential medications can provide peace of mind during times of uncertainty, ensuring that you are not left without necessary treatments in the event of supply shortages or healthcare disruptions.
If you are considering preparing for potential healthcare challenges, it is advisable to consult with medical professionals to understand which medications you should have on hand. Prescription-only medications, such as antibiotics, can be particularly important. Consulting with a healthcare provider who can assess your needs and help with acquiring prescriptions for emergency situations is a valuable step toward creating a comprehensive emergency preparedness plan.
By proactively securing essential medications, you can help safeguard the health and well-being of yourself and your family, ensuring that you are ready for any unexpected healthcare challenges.
3 notes
·
View notes
Text

How I use AI as an admin assistant to improve my job performance:
First of all, stop being scared of AI. It's like being scared of cars. They're here to stay, there are some dangers, but it's super useful so you should figure out how to make them work for you. Second, make sure you're not sharing personal or company secrets. AI is great but if you're not paying the providing company for the tool with cash then you are paying with your data. If you're not sure if the AI service your company uses is secure, ask IT. If your company isn't using AI ask them why, what the policy on AI use is, and stick to that policy.
Now, here's how I use AI to improve my work performance:
Make a Personal Assistant: I use enterprise ChatGPT's custom GPT feature to make all kinds of things. An email writing chat (where I can put in details and get it to write the email and match my tone and style), a reference library for a major project (so I always have the information and source at my fingertips in a meeting), one for the company's brand voice and style so anything I send to marketing is easy for them to work with, and gets picked up faster. I treat these GPTs like an intern who tries really hard but may not always get things right. I always review and get the GPT to site its sources so I can confirm things. It saves hours of repetitive work every week.
Analyze complex data: I deal with multiple multi-page documents and Word's "compare" feature is frankly terrible. I can drop two similar documents into my AI and get it to tell me what's different and where the differences are. Again, a huge timesaver.
Prepare for meetings and career progression support: Before any meeting I upload any materials from the organizers and anything relevant from my unit, and then get it to tell me, given the audience, what sort of questions might be asked in the meeting and what are the answers. I also ask it to align my questions and planned actions to the strategic plan.
Plan my career development: I told my AI where I wanted to go in the next five years and got it to analyze my resume and current role. I asked it to show me where I needed skills, and provide examples of where I could get those skills. Then I asked it to cost out the classes and give me a timeline. Now I'm studying for a certificate I didn't know about before to get to an accreditation I really want.
How to do it all (prompt engineering):
Do the groundwork by giving your AI context, details, information, and very specific requests. I loaded a bunch of emails into my email-writing GPT and also told it my career ambitions. It's tweaked my tone just a little. I sound like me, but a bit more professional. Likewise if you're making a reference library. It can't tell you what it doesn't know, but it will try, so be sure to tell it not to infer based on data, but to tell you when it doesn't have information.
Security risks to consider:
Secure access: You absolutely must protect sensitive information and follow whatever AI policy is in place where you work. If there isn't one, spearhead the team working on it. It's a perfect leadership opportunity.
Data protection: Be very careful when sharing sensitive data with AI systems, and know your security. Also check your results! Again, think of AI as an eager but kind of hapless intern and double check their work.
Recognize AI threats: Stay aware of potential AI-driven cyberattacks, such as deepfake videos or social engineering attempts. There have been some huge ones lately!
By getting a handle on AI and being aware of the risks you can improve your work quality, offload the boring stuff, and advance your career. So get started. But be careful.
2 notes
·
View notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
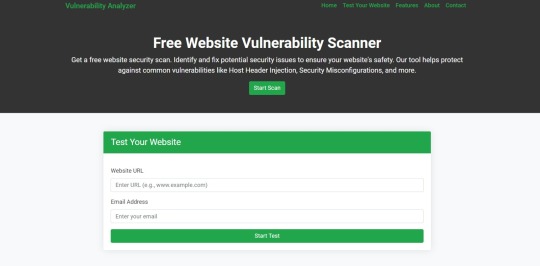
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
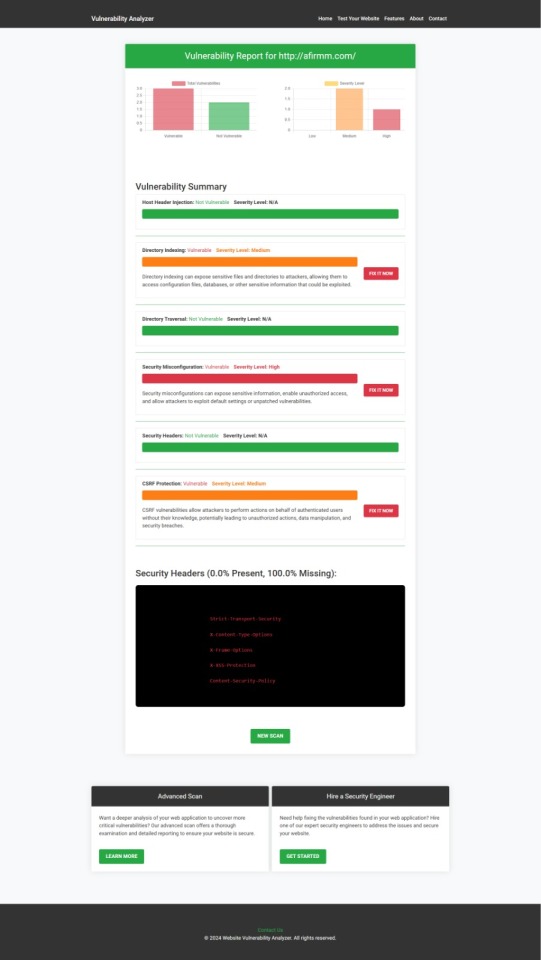
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
Blog Post #7
This week in Module 7, we learned extensively about cybersecurity, breaking it down into key components like endpoint security, network security, disaster recovery, and information security. In correlation to the activity with PBS’s Cyber Lab Game, which was to teach us about cybersecurity through various challenges, the information from Module 7 significantly increased my understanding of the topic and how I can react to certain situations when it comes to cybersecurity.
In the game, I was tasked with defending systems from various cyberattacks, similar to how endpoint and network security function in real-world scenarios. The concept of endpoint security, as described in Module 7, was especially useful when identifying malicious threats and employing antivirus measures during the gameplay. Understanding the analogy of the “electrified perimeter fence” allowed me to visualize how antivirus software and other defenses work in protecting end-user devices.
Additionally, the disaster recovery section was also helpful. Throughout the game including these scenarios where players must respond to breaches effectively, it helped to reinforce and remind me of the importance of having a well-prepared response plan.
In conclusion, Module 7 and the PBS Cyber Lab Game complemented each other well by providing a foundation that improves the practical cybersecurity skills learned during the course of the game.
2 notes
·
View notes
Text
Understanding the Impact of Indian Army Defense Result on National Security
Indian Army Defense Result is performs a critical position in safeguarding a nation's sovereignty, security, and balance. It encompasses diverse techniques, technology, and military forces that work collectively to protect a country from external threats, such as army aggression, terrorism, and cyber-assaults. The outcome of a nicely-coordinated defense approach no longer simplest ensures countrywide safety but also strengthens a country’s impact on the worldwide stage.

Military Defense
One of the important thing components of defense is the military. Armed forces, which include the military, military, air force, and once in a while specialised gadgets like area and cyber commands, are liable for protecting the u . S . In opposition to physical threats. The effectiveness of a kingdom's army depends on its stage of schooling, get right of entry to to trendy technology, and universal preparedness. Strong navy abilties act as a deterrent towards potential adversaries, decreasing the probability of conflict. In instances of warfare or disaster, a nicely-prepared military can quickly mobilize to shield country wide pastimes, stable borders, and protect citizens.
Technological and Cyber Defense
In today’s digital age, defense additionally closely is based on superior technology. Innovations which includes artificial intelligence (AI), unmanned aerial cars (UAVs), and missile protection structures have transformed modern warfare. A nation’s ability to broaden, collect, and combine those technologies into its protection apparatus can considerably effect its safety consequences. Cyber protection has emerged as an crucial element of countrywide safety as well. With increasing cyber threats from both country and non-kingdom actors, protecting essential infrastructure and touchy statistics is paramount. A a hit cyber defense strategy prevents espionage, hacking, and other cyberattacks that would disrupt authorities operations or damage important structures.
Diplomatic and Economic Defense
Beyond the battlefield, protection techniques additionally embody diplomacy and monetary safety. Building robust alliances through international relations enables in collective defense efforts, including NATO, in which member states pledge to shield each other. Economic electricity also contributes to country wide protection through making sure good enough investment for defense tasks and retaining resilience in opposition to sanctions or monetary battle.

Result of Effective Defense
Defense Result Army is powerful protection system not only protects a country’s borders however also complements its international status. A strong and adaptive protection infrastructure guarantees peace, deters capability threats, and permits a nation to task power responsibly on the worldwide stage.
2 notes
·
View notes
Text
How Can You Ensure Data Quality in Healthcare Analytics and Management?

Healthcare facilities are responsible for the patient’s recovery. Pharmaceutical companies and medical equipment manufacturers also work toward alleviating physical pain, stress levels, and uncomfortable body movement issues. Still, healthcare analytics must be accurate for precise diagnosis and effective clinical prescriptions. This post will discuss data quality management in the healthcare industry.
What is Data Quality in Healthcare?
Healthcare data quality management includes technologies and statistical solutions to verify the reliability of acquired clinical intelligence. A data quality manager protects databases from digital corruption, cyberattacks, and inappropriate handling. So, medical professionals can get more realistic insights using data analytics solutions.
Laboratories have started emailing the test results to help doctors, patients, and their family members make important decisions without wasting time. Also, assistive technologies merge the benefits of the Internet of Things (IoT) and artificial intelligence (AI) to enhance living standards.
However, poor data quality threatens the usefulness of healthcare data management solutions.
For example, pharmaceutical companies and authorities must apply solutions that remove mathematical outliers to perform high-precision data analytics for clinical drug trials. Otherwise, harmful medicines will reach the pharmacist’s shelf, endangering many people.
How to Ensure Data Quality in the Healthcare Industry?
Data quality frameworks utilize different strategies to prevent processing issues or losing sensitive intelligence. If you want to develop such frameworks to improve medical intelligence and reporting, the following 7 methods can aid you in this endeavor.
Method #1| Use Data Profiling
A data profiling method involves estimating the relationship between the different records in a database to find gaps and devise a cleansing strategy. Data cleansing in healthcare data management solutions has the following objectives.
Determine whether the lab reports and prescriptions match the correct patient identifiers.
If inconsistent profile matching has occurred, fix it by contacting doctors and patients.
Analyze the data structures and authorization levels to evaluate how each employee is accountable for specific patient recovery outcomes.
Create a data governance framework to enforce access and data modification rights strictly.
Identify recurring data cleaning and preparation challenges.
Brainstorm ideas to minimize data collection issues that increase your data cleaning efforts.
Ensure consistency in report formatting and recovery measurement techniques to improve data quality in healthcare.
Data cleaning and profiling allow you to eliminate unnecessary and inaccurate entries from patient databases. Therefore, healthcare research institutes and commercial life science businesses can reduce processing errors when using data analytics solutions.
Method #2| Replace Empty Values
What is a null value? Null values mean the database has no data corresponding to a field in a record. Moreover, these missing values can skew the results obtained by data management solutions used in the healthcare industry.
Consider that a patient left a form field empty. If all the care and life science businesses use online data collection surveys, they can warn the patients about the empty values. This approach relies on the “prevention is better than cure” principle.
Still, many institutions, ranging from multispecialty hospitals to clinical device producers, record data offline. Later, the data entry officers transform the filled papers using scanners and OCR (optical character recognition).
Empty fields also appear in the database management system (DBMS), so the healthcare facilities must contact the patients or reporting doctors to retrieve the missing information. They use newly acquired data to replace the null values, making the analytics solutions operate seamlessly.
Method #3| Refresh Old Records
Your physical and psychological attributes change with age, environment, lifestyle, and family circumstances. So, what was true for an individual a few years ago is less likely to be relevant today. While preserving historical patient databases is vital, hospitals and pharma businesses must periodically update obsolete medical reports.
Each healthcare business maintains a professional network of consulting physicians, laboratories, chemists, dietitians, and counselors. These connections enable the treatment providers to strategically conduct regular tests to check how patients’ bodily functions change throughout the recovery.
Therefore, updating old records in a patient’s medical history becomes possible. Other variables like switching jobs or traveling habits also impact an individual’s metabolism and susceptibility to illnesses. So, you must also ask the patients to share the latest data on their changed lifestyles. Freshly obtained records increase the relevance of healthcare data management solutions.
Method #4| Standardize Documentation
Standardization compels all professionals to collect, store, visualize, and communicate data or analytics activities using unified reporting solutions. Furthermore, standardized reports are integral to improving data governance compliance in the healthcare industry.
Consider the following principles when promoting a documentation protocol to make all reports more consistent and easily traceable.
A brand’s visual identities, like logos and colors, must not interfere with clinical data presentation.
Observed readings must go in the designated fields.
Both the offline and online document formats must be identical.
Stakeholders must permanently preserve an archived copy of patient databases with version control as they edit and delete values from the records.
All medical reports must arrange the data and insights to prevent ambiguity and misinterpretation.
Pharma companies, clinics, and FDA (food and drug administration) benefit from reporting standards. After all, corresponding protocols encourage responsible attitudes that help data analytics solutions avoid processing problems.
Method #5| Merge Duplicate Report Instances
A report instance is like a screenshot that helps you save the output of visualization tools related to a business query at a specified time interval. However, duplicate reporting instances are a significant quality assurance challenge in healthcare data management solutions.
For example, more than two nurses and one doctor will interact with the same patients. Besides, patients might consult different doctors and get two or more treatments for distinct illnesses. Such situations result in multiple versions of a patient’s clinical history.
Data analytics solutions can process the data collected by different healthcare facilities to solve the issue of duplicate report instances in the patients’ databases. They facilitate merging overlapping records and matching each patient with a universally valid clinical history profile.
Such a strategy also assists clinicians in monitoring how other healthcare professionals prescribe medicine to a patient. Therefore, they can prevent double dosage complications arising from a patient consuming similar medicines while undergoing more than one treatment regime.
Method #6| Audit the DBMS and Reporting Modules
Chemical laboratories revise their reporting practices when newly purchased testing equipment offers additional features. Likewise, DBMS solutions optimized for healthcare data management must receive regular updates.
Auditing the present status of reporting practices will give you insights into efficient and inefficient activities. Remember, there is always a better way to collect and record data. Monitor the trends in database technologies to ensure continuous enhancements in healthcare data quality.
Simultaneously, you want to assess the stability of the IT systems because unreliable infrastructure can adversely affect the decision-making associated with patient diagnosis. You can start by asking the following questions.
Questions to Ask When Assessing Data Quality in Healthcare Analytics Solutions
Can all doctors, nurses, agents, insurance representatives, patients, and each patient’s family members access the required data without problems?
How often do the servers and internet connectivity stop functioning correctly?
Are there sufficient backup tools to restore the system if something goes wrong?
Do hospitals, research facilities, and pharmaceutical companies employ end-to-end encryption (E2EE) across all electronic communications?
Are there new technologies facilitating accelerated report creation?
Will the patient databases be vulnerable to cyberattacks and manipulation?
Are the clinical history records sufficient for a robust diagnosis?
Can the patients collect the documents required to claim healthcare insurance benefits without encountering uncomfortable experiences?
Is the presently implemented authorization framework sufficient to ensure data governance in healthcare?
Has the FDA approved any of your prescribed medications?
Method #7| Conduct Skill Development Sessions for the Employees
Healthcare data management solutions rely on advanced technologies, and some employees need more guidance to use them effectively. Pharma companies are aware of this as well, because maintaining and modifying the chemical reactions involved in drug manufacturing will necessitate specialized knowledge.
Different training programs can assist the nursing staff and healthcare practitioners in developing the skills necessary to handle advanced data analytics solutions. Moreover, some consulting firms might offer simplified educational initiatives to help hospitals and nursing homes increase the skill levels of employees.
Cooperation between employees, leadership, and public authorities is indispensable to ensure data quality in the healthcare and life science industries. Otherwise, a lack of coordination hinders the modernization trends in the respective sectors.
Conclusion
Healthcare analytics depends on many techniques to improve data quality. For example, cleaning datasets to eliminate obsolete records, null values, or duplicate report instances remains essential, and multispecialty hospitals agree with this concept.
Therefore, medical professionals invest heavily in standardized documents and employee education to enhance data governance. Also, you want to prevent cyberattacks and data corruption. Consider consulting reputable firms to audit your data operations and make clinical trials more reliable.
SG Analytics is a leader in healthcare data management solutions, delivering scalable insight discovery capabilities for adverse event monitoring and medical intelligence. Contact us today if you want healthcare market research and patent tracking assistance.
3 notes
·
View notes