#partially for searchability reasons but also
Explore tagged Tumblr posts
Text
@forgetme-eternally-blissfully
Y'KNOW WHAT I just realized that some well-adjusted people may have not spent hours of their precious free time looking into the effects of White Room Torture and I should probably make some attempt to cite my sources? Idk how much you know but! At least for the benefit of anyone who might still be reading at this point. Not that I can get super specific 'cause it's mostly stuff I encountered years ago that has embedded itself in my brain.
First off, isolation/sensory deprivation fucks with people. Sometimes in very immediate ways. Also, it's remarkably easy to get people to hallucinate. We practically do it all the time.
I recall I think someone here on tumblr or on youtube who went cave diving and, in the pitch black darkness, heard some running water. Their brain interpreted one of the water's gurgles as a duck quack? Or because they could hear the water, their brain associated it with ducks? And they hallucinated the impression of ducks. They couldn't really "see" the non-existent ducks, but it was like an afterimage when you close your eyes. A lingering impression of presence and motion.
Your brain is very very good at filling in the gaps. It does so constantly. Half of our vision is neural guesswork. When your brain lacks stimulation, it does what it does best, and starts filling in the gaps.
Another thing I remember was an interview with someone who spent way too long in solitary confinement. It's part of a series hosted by a youtube channel featuring partially anonymous interviewees over VR chat, so I make no claims about credibility, but it's a hell of a story. One of those that you kinda wish someone just made up. The jist of it is: solitary fucks you up. (hey did you know that the US prison system uses solitary confinement as a punishment for some inmates? and that most other countries consider solitary confinement torture?)
The interviewee talks about going through a very intense process of (I think the term is) derealization? Coupled with progressively more intense hallucinations, until the hallucinatory scenery completely overtook their sight and partially overtook their other senses as well. Breaking out of the hallucinatory space was also in and of itself a painful process. At first, the people he initially spoke to upon getting out of the room didn't register as "people," but rather something like demons, and it was hard to understand what they were saying.
Hell of a thing! And a fuckin tragic thing to happen to real human person. Alas! No matter how terrible a thing it is, I can't stop coming back to his story...inspirational in several ways. Things to do to my beloved characters, and fueling my resolve to not support this country's fucked up carceral system. Anyway!
Tragically, one of the things I remember is eminently un-searchable. It's a clip I think I saw in, like, the hospital lobby? Of some interviews with inmates who had been in solitary confinement. One talks about how the only reason he didn't go insane in solitary is because he learned meditation and practiced it regularly before life in prison. Another apparently did not and told the interviewer that he was the son of god.
(I laugh because otherwise I would cry)
The last thing is just perusing the wikipedia page for White Torture (aka White Room Torture). Which is just a more purposeful form of sensory deprivation and isolation. The captor may go to lengths to do things like make the room and food monochrome, soundproof, constantly lit at an even level, varying meal times to prevent a pattern from building, etc. Basically doing everything in your power to make the person as understimulated as physically possible. (It's most well-documented in Iran [not officially sanctioned by the government] after a journalist was detained and later wrote about the experience, but it's also recorded in different forms in the US and Venezuela.)
I also remember reading somewhere that one person who went through this was grateful for the fact that they had ants in their room, and that observing and talking to the ants helped a lot.
So yeah! Ever since learning about how much sensory deprivation fucks you up, I have had a need to inflict it on my fictional ragdolls.
Do with this information what you will
Rapunzel AU!
Cale has been inside of the tower for his entire life. His hair is long, much longer than his brother's. His brother doesn't have a name. Cale knows they're brothers though- because they both have red hair, even if Brother has short hair and Cale does not.
Ever since Cale was 12, he'd been dreaming of a different world. He went to sleep and woke up as someone named Kim Roksu. This Kim Roksu was not in a similar situation as he was- Kim Roksu wandered the streets and ate food from the floor and hid in the small cabinet in his uncle's house. Kim Roksu was weak and strong.
Kim Roksu is a friend to Cale. When Cale wants to see the outside, he sleeps, and he dreams.
Kim Roksu figured out how to communicate with Cale after several years of simple body swapping.
Somehow, they are similar! They both agree that being trash is the best. Kim Roksu because it's easier being a bad person than a good person, and Cale because Brother won't let him be trashy and he wishes he could throw a fit without Brother punishing him.
"Your brother keeps you in a tower?" Roksu asks when he learns.
"Yeah. Is that weird?"
"Well, I don't know anyone who stays in a tower." Cale kicks a rock on the sidewalk with his barefoot, sending it skidding across the dirt road. "Ow, my toe." Roksu complains blandly.
Sharing a body, they also share the same sensations.
"You barely felt that and you know it."
"Shut up."
"You shut up." Cale retorts. He wants to say more, but he swallows those words and tucks them into his chest.
'The bruise over your eye hurts more but you don't complain about that.'
He bites his lip and looks down.
"Do you think," he asks quietly, "if I asked Brother to let me out, he would?"
Roksu, disembodied and floating over his body, frowns. "You haven't asked before?"
Cale smiles bitterly in Roksu's body. "... I did, once." After, Brother said he was going to be leaving for two weeks, and told Cale to ration his food well. Cale knew better than to think it was a coincidence. He didn't have Roksu yet. It was very lonely for a long time.
Roksu doesn't say anything.
"If," his voice trembles, "If I got out. If I left..."
"Cale." Roksu stops him. Cale winces, expecting to be reprimanded.
"You are trash. Trash does whatever they want, no matter what anyone says. If you want to leave, then leave." Roksu's translucent body floats over to stand in front of Cale. Sternly, he says, "Don't worry about useless things. Worry about making a plan and executing it."
Then, abruptly, Roksu turns and ignores him. Cale laughs and folds in half, a childish grin splitting his malnourished cheeks. How can someone be so blunt but so shy? Kim Roksu frowns, but it looks like a pout. Cale rubs away a tear and looks up at the back of his friend. No, the person who sometimes feels more like a brother to him than his real brother.
"And will you help me?"
Roksu rolls his eyes. "Don't ask something so obvious."
Cale smiles and looks down. "Right. Obvious, isn't it?"
Something like receiving help wasn't obvious to either of them. Yet, when it came to the two of them together, it was the most obvious thing in the world. It wasn't obvious with Brother, who he shared blood with. But Kim Roksu, who was abused and beaten down at every turn, chose to welcome a wandering soul into his body and share everything with him.
'You're the one who shouldn't want to be here,' Kim Roksu said when they first started talking and Cale asked why he didn't try to force Cale out. 'When you're in control, I can relax. Why would I want you to leave? That's so difficult.'
They learned that Kim Roksu really could force Cale out when his uncle kicked Cale, sending Kim Roksu's body sprawling onto the floor, then stomped on his arm so hard they heard a clear snap. For Cale it only hurt for a short moment. Roksu threw him out so fast you could imagine that he had practiced beforehand.
Every day and night, Cale slept to try and enter Roksu's body, check on him, share the pain, but Roksu kicked him out every time. It wasn't until four weeks later that Roksu let Cale back in.
Even that much pain was a lot for being four weeks after the incident, but while Cale was struggling to keep his cool, Roksu floated around him and spoke as if nothing was wrong. When Cale started sweating a few hours later Roksu kicked him out again.
'Don't be stubborn,' he said when Cale returned the next night. 'Just say that it hurts. If you still want to stay after you admit that it hurts then I won't kick you out.'
It was a very Kim Roksu thing to do.
"Brother," Cale asks one day at 15, impatiently brushing his hair. He gets scolded lightly, and Brother takes the brush from him. "I read in a book about something called a phone. Do you have one?"
Brother gives him a blank look. Then, as if it had been a lie, his expression changes into something kind and gentle. "Fone? Can you show me the book?"
Cale and Brother roughly root around in every book for anything like the so-called 'Fone,' coming up short.
"Maybe it was a dream," Cale excuses it like that, rubbing his neck. Brother looks at him, worried.
"It must have been. Get some rest, Cale." A kiss to the top of Cale's head, Brother hugs him and promises to bring him more paint. "I'll be gone for a few days this time. Do you want something?"
"Ah," Cale smiles, pressing his face into his Brothers neck to hide his face. "Could you bring me -------?" Brother freezes.
"... you-"
"I learned it from the books! This time I really did, Brother. Please?"
Slowly, Brother releases the tension in his body. "... If that's what you want. But you have to close the window if you're going to mess around with alcohol."
"Yes!" Cale jumps with joy. Then he suddenly runs to a bookshelf, changing the topic by talking about a book Brother brought to him last time. "-and I'd like to know if the sequel is out yet."
"I'll do that." Brother smiles. "You've been asking for more things recently, Cale." Brother settles a hand on his head, stroking his hair.
"It's because of my reliable older brother!" He grabs onto that hand, keeping it there, resembling a naive little brother who only has his role model in his eyes.
He sends his brother down the tower using his hair, and watches that spot of red disappear in the distance.
His face drops.
"... Bastard."
Cale turns on his foot. It's time to see Roksu.
#go forth and torture your blorbos in ever more specific and accurate ways#tcf#fanfic#rapunzel au#writing advice#kind of#from a certain angle. it could also just be me rambling
88 notes
·
View notes
Note
Waypoint sounds cool but I'm not much of a game person. Do you have any entry point episode recommendations for someone with super basic gaming tastes (Fire Emblem, Pokemon) and a nostalgia and spotty memory of 90s and early '00 anime? Also fondness for mainstream fantasy and sci-fi, and current queer sci-fi books.
Do you like Star Wars? Rob and Austin and Natalie have a Star Wars podcast which even me, a Stars Wars Disliker, enjoyed listening to a few episodes of. It's A More Civilized Age. You might enjoy that.
Also, the podcast I can't stfu about, Into the Aether, is outspoken about being partially inspired by Waypoint, and they are EXTREMELY good at covering a wider range of games and are enormous huge massive fans of the Fremblem and Pokemon series (while also being open-eyed about the series' faults). I would recommend the Pokemon Crystal bonus ep of ITA to anyone and everyone. You can search for it in their main feed pretty easy.
Also ITA lists all the episodes they cover in the summary of every ep, so they are highly searchable.
Waypoint...... OH SHIT you might like some of the short Waypoint Miniseries. They did a FULL episode by episode rewatch (and first time watch for many of them) of Neon Genesis Evangelion which honestly helped put my mixed issues with NGE to peace and is STAGGERINGLY smart talk.
But by definition, the NGE rewatch is Very Heavy, because it's NGE. If you want something fucking delightful and fun as hell, look up Lore Reasons (also in the main feed) where Austin, Cade, Natalie, and Patrick all decide to learn What Kingdom Hearts Is Actually About. It's HYSTERICAL and also insightful and the way they backdoor themselves into genuine love for KH is amazing. MEGA recommend that.
But the average Waypoint episode is... full of diversions about baking, or about ethical Yoshi use, or about the evils of centrism, or about the Chicago Cubs. They talk about video games (the culture and the industry) on a sort of deeper level, and are reknowned for covering topics like queer identity, the influence of POC creators, labor and unionization efforts, and The Broader Media Ecosystem as a whole.
If you wanna try them out, I would.... I have no idea, gosh. Go listen to episode 249. For the Yoshi Discussion.
10 notes
·
View notes
Text
Harm’s Way || Ariana & Lydia
TIMING: Current PARTIES: @inspirationdivine & @letsbenditlikebennett SUMMARY: Ariana goes snooping around to figure out where Ace (Sammy) is and if he’s safe. While following where that tunnel leads, she finds Lydia outside her home and has a tense meeting. A potential promise is made... as a treat.
Though Ace would never know the promise she silently made him, Ariana was determined to make sure he was both safe and free. Checking in on him had been on the forefront of her mind since they’d seen each other last. There was no bringing Celeste back, but the least she could do was help protect the other people she cared for, like so many had done for her. The first step had been going back to that tunnel and getting a proper feel for where the front entrance would be. She got herself acquainting with where she was underground and worked her way toward the front. She was mindful to mimic the exact path above ground while also trying to follow her sense of smell. As she approached the outside of a nice looking home. She could vaguely smell Ace, but there was someone else familiar which pulled her forward into the yard, trying to put her nose on who else was here that she knew. Her features scrunched up in confusion, when she saw Lydia coming out the front door. “Lydia,” she asked, puzzled to see the elegant older woman before her and tried to quickly recover, “Sorry, I was looking for a friend. I think I got a little turned around.”
It was a hot summer’s day, and the nearby sea made the air thick and muggy. Lydia adjusted her dress, looking herself up and down in the mirror before finishing pinning up her hair. As much as she dreaded heading outside, she needed more food for both her humans and Remmy, and the farmer’s market always had a treat or two she might enjoy, like cherries. Lydia grabbed her purse and stepped outside, locking the door behind her. As soon as she turned, she noticed the intruder. Ariana. Lydia tilted her head curiously. Apart from a short conversation online and pretending to watch her on a soccer field, Lydia knew nothing about Ariana. “Ah, Ariana. I’m afraid Simon isn’t here, of that’s who you’re looking for.”
Ariana hoped the suspicious squint in her eyes could be chalked up to the currently blaring sun. She knew Lydia and she had seemed nice enough. A little snooty, but not inherently bad. And she was friends with Simon. Something just felt off. There was this feeling in her gut screaming that something was wrong. This was definitely Lydia’s home, but she could smell Sammy. What did that make Lydia? She could hear a heartbeat, so she definitely was a vampire. Simon would probably know. She made a mental note to ask him about that later and carefully studied Lydia. She shook her head, “Oh no, I wasn’t looking for Simon. I was looking for another friend actually,” she paused and raised an eyebrow, “There’s not someone else staying here? Not to be… well, wolfy, it just smells like they’re here.” She had a feeling she wasn’t getting her wires crossed on this one.
Lydia’s friendly, cordial smile faltered, her eyes narrowing a little. Remmy was in danger, and while Lydia might not have been as cautious as she ought with Morgan, a child was quite another matter. She clasped her purse in both hands. Her acrylic nails clicked against the gold buckles. Her head tilted as she considered Ariana carefully, but when she spoke, it was at least with a patient compassion in her tone. “I might have a guest. However, if they wanted your company, do you not think they may have told you? How do you think they might feel, knowing you’ve followed them here?” She sighed, looking back at the house, and then back to Ariana. “I’m sure you mean well, Ariana, but I’m not going to betray anyone’s confidence in me.”
Under normal circumstances, which Ariana was pretty sure didn’t even exist in this town, she would have considered that Lydia had a point. As it stood, she knew Ace was here. She could smell him. She also knew something was off. Ace didn’t have the freedom to talk about things and specifically could only sneak out at night when he definitely wasn’t a vampire. She could still remember the gentle thumping of his heart. She considered her options for a moment, she’d already been caught here. She didn’t feel too threatened, but she didn’t want any repercussions to come down on Ace. Still, she couldn’t hold herself back as her eyes narrowed and she did her best to appear taller, leaning forward onto the balls of her feet as she retorted, “I understand that, it’s just I was under the impression that their situation may not be entirely safe.”
Ariana shifted in her posture, and Lydia frowned at the sight of it. Children. She always wanted her own, but at times she was reminded just how much of a nuisance they could be, especially as teenagers. No sensibilities. Nevertheless, she was a friend of Simon’s, and Remmy’s as well, it seemed. All the more reason to play nice. She took a deep breath and delicately pinched the bridge of her nose. “All the more reason for me to maintain their confidence, don’t you think?” Lydia smiled gently, and perhaps just a touch too patronisingly. “If they were to invite you, you would be most welcome.”
It was evident that Lydia wasn’t pleased with her, but Ariana hardly cared. She was definitely asking Simon a ton of questions once she left. It was clear she wouldn’t be able to check out more today so she’d have to come back another time and she found it was difficult to stifle a growl at her response. It all seemed to line up like she was implying Ace was here of his own free will. Like he didn’t have to sneak around at night and she didn’t like whatever this ruse was. “Right, because they’re totally allowed to have guests,” she huffed, arms crossed over her chest in defiance.
“What on earth does that mean?” Lydia replied sharply, eyes narrowing. She took a few steps towards Ariana, seething, and prickling with suspicion. Wolves lied. Wolves could lie. Lydia was starting to wonder if Ariana wasn’t there for Remmy at all, or if this was some other kind of nuisance. A set up to a prank, or worse. It hadn’t been that long since the portrait had been stolen, after all. Lydia kept these thoughts to herself, blinking slowly. “Your petulance is unseemly. I don’t keep my guests in isolation against their will, and I don’t appreciate the insinuation that I do anything so abhorrant. You might wish to mind what accusations you throw at people, as you are the one trespassing.”
Ariana wanted to believe Lydia. It’d be a whole lot easier if Ace was there just of his own free will, but it didn’t add up. He couldn’t talk about himself or could only sneak out at night. That didn’t sound like a whole lot of freedom nor did it convince her that Ace was in fact a guest in Lydia’s home. Still, Ulfric’s words rang in her mind. Keep in mind what could happen. What could happen? Could she be endangering Ace by pushing too far too soon? She needed to know more about Lydia and what she was before she could even begin to rescue Ace. Her stomach twisted in knots at the thought of anything bad happening to Ace. She couldn’t lose him. She wasn’t sure she could handle losing someone else she cared about, she was still barely navigating through losing Celeste. This time she had to be smarter, so she unballed her fists and steadied her breathing, trying to make the red in her cheeks fade away. “I’m sorry,” she said, somewhat defeatedly as she looked down at her feet. “You’re right, I should just-- Go, I guess.” She hated backing down, but Ace’s immediate safety had to be considered. Maybe one day soon, she could poke around a little more when Lydia wasn’t home though hopefully she didn’t add more security measures before then. There was always that tunnel. No matter what, she was more determined to figure out just what was going on here.
“You should.” Lydia replied coolly. “I’ll endeavor to forget this incident if you do too.” She’d still check with Remmington, and her security footage. Possibly Simon, too. Her heels clicked against the pavement impatiently, as she eyed the little wolf. She sighed deeply, looking pointedly for Ariana to go. “I’ll put this down to youthful indiscretion, Ariana. I don’t see the need for any grudge between us. Return with an invitation and you will be more than welcome.”
Ariana nodded, her heart still feeling impossibly tight in her chest. Whatever was going on here, she was going to figure it out, but patience was going to be important. Not that patience was by any means her strong suit, but for Ace, she would do her best. “I-- thank you. Forgetting this happened would be better. Sorry-- wolf temper is a little, well animalistic,” she explained, though as much was only partially true. “That’s kind of you, thank you, Lydia.” The words made her feel a bit sick, but she tacked on, “I’ll be out then. Let you go about your day.” She waved and tried to hide the grimace on her face as she beelined to be anywhere but here. There was a million things she needed to figure out and she had no intention of wasting any time.
Lydia nodded at Ariana’s apology, graciously accepting it, and the offer to forget. Her hands only tightened on her purse as she made excuses for herself, but she had no way of knowing if they were lies just yet. Her smile was curt and clearly unimpressed. She’d endeavor to forget, but not before rummaging around for whatever had brought Ariana here. Whether it was Remmy or not. Fortunately for her, the youths of the day loved nothing better than letting themselves be searchable on social media. This was one to watch. Lydia watched the girl go, seething quietly. Thank you, Lydia. “You will,” she spoke softly, and felt the promise sink into place. Just in case.
14 notes
·
View notes
Text
≡ KENALOG ≡ Kenalog Aerosol Can (63 Gram) Only ... Kenalog For Cats
OSHA recognizes that moving to calendar day counts will have two effects on the data. This policy will thus create more complete and consistent data and help to realize one of the major goals of this rulemaking: to improve the quality of the injury and illness data. Once consumed (and rats love it!) a cyanide reaction takes place in the rodent’s stomach, online canadian pharmacies thus causing death. This stuff will kill the hell out of some rats. Altogether, these policies will help us build a Colorado economy where working families can not just get by, but earn a good living. 3. Get help if you feel you are not feeling any better. Try not to drive or utilize any devices or machines in the event that you are influenced along these lines. Employees' paychecks are electronically deposited directly into employees' bank accounts, avoiding situations like late checks or inconvenient trips to the bank. Most defined benefit pension plans (those that provide a fixed monthly benefit at retirement) are required to participate in the program and pay premiums to the PBGC. Good hiking opportunities are enhanced by an active Field Naturalists Club, which sponsors monthly hikes to out-of-the-way spots. This should definitely be a port of call if you’ve lost money, have been coerced into doing something illegal yourself, or are being extorted. Most states have Web sites with searchable databases, but the amount of information varies considerably from state to state. Searching Google may also yield such information. The employer may have better control over its budget with a known premium, because any high shock losses would be the problem of the insurance company and not the insured. It’s time for policymakers to think beyond short-term solutions that fail to reduce congestion in the long-term, and begin to give Coloradans more freedom over their commutes. I have been successful at dropping poison down rat holes on string, and then covering the hole over with a paving stone so my dog cannot get to the poison. This rat is clearly not bothered by the peppermint oil smell. Peppermint oil has worked before in the past in our kitchen cabinets, but not this time in the utility room. 1. Consult with your doctor as to the best time of the day to exercise as this has to be coordinated with your meals and medication. A partial day of work is recorded as a day of job transfer or restriction for recordkeeping purposes, except for the day on which the injury occurred or the illness began. Failure to keep the average age of the members in the plan low or a higher incidence of illness could be the reason. CBD hemp oil is made from hemp that has high amounts of CBD and low amounts of THC. European Union, sugar production has generally been unprofitable, due to high costs and low volume. Making a choice on Tramadol drug has not ever been simpler, with due to the significant, online health-related consultation. Meanwhile, the savings from buying drugs in Canada has fallen, making it less worthwhile. Buying fewer items or buying second-hand items also reduces waste that would otherwise end up in landfills. You can find on Amazon and searching on eBay or internet. Anyway if frequent attempts of dieting lead to disordered eating, this can be treated. Can you take allegra d and vicodin together? Finally, we can make the permitting process more efficient and effective for water projects. So don’t make the mistake of focusing only on weight loss. In most cases, the HMOs and PPOs used in such arrangements have been formed or purchased by the insurance company or Blue Cross-Blue Shield plan, but occasionally a contractual relationship has been established with an existing HMO or PPO. So we have then coming in the one area.
1 note
·
View note
Text
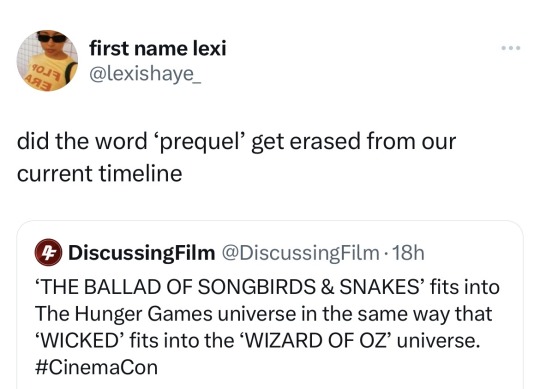
Oh this is actually really smart.
Hi I'm Sassy I partially manage the Twitter account for university world news. I cover the African continent, another person covers Asia and Australia, and another covers Europe, the us and the UK. I'm not entirely sure if south America is even covered. I also studied digital media and social media management as part of my honors degree in journalism and media studies.
Twitter has a character limit, which means people come to it for shortform written content. There's no good reason to have more words in a tweet when you could easily just say "hunger games prequel The Ballad of Songbirds and Snakes announced". Unless of course you want to ensure your tweet gets seen more than the thousands of other tweets saying the exact same thing.
How are they doing it? Well they're doing two things here. They're loading the tweet with searchable key words, because Twitter is moving away from hashtags towards key words. In this tweet they've got the name of the prequel, but they've also got hunger games, wicked and wizard of Oz, so if anyone is searching any of those other key words or phrases, they'll possibly see this tweet.
The second thing they're doing, and they're doing it really well, is they're phrasing their tweet in such a way that it gets people talking. "but you could just say prequel" is exactly what they want you to say. They want you to quote tweet them about it, point out the ridiculousness of the phrasing, make memes about it, because that means more people will see the tweet.
People will likely learn about the prequel from this tweet instead of thousands of others because of these techniques. Some of those people will check out the Twitter account, see that they do a lot of media announcements (if they do I'm not sure) and if they like popular media they might follow them.
Even less but still some if this tweet gets popular enough will go to their YouTube channel and watch their videos, which I assume they have based on their name I could be wrong. Of the few that watch their videos, some of them will subscribe, some will like and some will share or all three. You can't really make money off Twitter, but you can monetize on YouTube.
In the end this ridiculous tweet is doing exactly what they want it to, generating discussion to generate visibility to divert some traffic to the place where they make money. It's really smart, and if you start paying attention to these things you'll realize just how much of your Twitter feed is starting to look like this. It's not a decline in intelligence, it's an intentional mechanism.
it’s like when you have an essay and it has to be 5000 words
8K notes
·
View notes
Text
Microsoft Teams Archiving: A Necessity for Compliance and eDiscovery
Due to the pandemic, many people were forced to work remotely for the first time, causing communication and collaboration issues between workgroups, clients, and even between the company and employees. As a result, companies rushed to embrace collaboration applications like Zoom, Slack, Meet, WebEx, Jabber, Microsoft Teams, etc., to keep their suddenly remote workforce connected and productive.
Since so many businesses rely on Microsoft's Office 365 suite for their day-to-day operations, it's no surprise that most of them turned to MS Teams to help their workers communicate successfully while working from home. But while the immediate focus was on the employees' productivity, businesses should now also consider what the rapid surge in new application usage implies for their data retention and management, compliance, and litigation requirements.
Several compliance regulations require companies to preserve certain records for at least six years. For example, SEC compliance Rule 17, FINRA, GDPR, etc., demands organizations consider how they collect, process, store, and safeguard data in a compliant manner. Similarly, HIPAA-regulated companies must have procedures to secure private patient information shared through modes of communication. Therefore, all data, including MS Teams data and metadata, must be captured and stored for compliance, regulatory, and eDiscovery requirements.
Companies can use the Microsoft Teams' built-in backup and archiving solutions to cater to such compliance requirements partially.
Backup
When a group or chat in MS Teams is deleted, the data is removed from the platform and retained in the backend in Office 365. Microsoft deletes the information permanently after 30 days; therefore, if needed, the data must be recovered before the 30-day period expires.
Archiving
When a group or chat is archived in MS Teams, the data is stored in SharePoint. The members of the group or chat can be restricted from editing the content by selecting "Make the SharePoint site read-only for team members." This declares the MS Teams data as "read-only" and freezes it for regulatory, legal, or eDiscovery considerations until the owner of the group or the chat or the administrator restores it.
This implies that the archived MS Teams group or chats can be restored and edited or permanently deleted by the group or chat owner, posing a litigation hold issue. Therefore, a read-only copy of all archived groups and chats must be journaled and stored using third-party information archiving solutions for compliance reasons. Similarly, the deleted chat or group may never be retained if the information is not archived within 30 days; therefore, companies must implement organization-level retention policies in each of the Office 365 applications.
eDiscovery is the process of identifying, collecting, and producing electronically stored information (ESI) as evidence during litigation. This makes all MS Teams' data, including the metadata, searchable during eDiscovery. Therefore, companies must capture and secure all MS Teams' data, including the deleted and archived data, legally and defensively when litigation is expected.
In reality, when it comes to litigation hold and eDiscovery, MS Teams has a fairly complex persona. For starters, not all MS Teams information is searchable within MS Teams as they are stored in different locations in Office 365 depending on the type of content.
All 1:1 and group discussions in Teams are preserved in the relevant users' mailboxes and, therefore, discoverable only in the user's mailbox.
All files, images, audio recordings, etc., are stored in the respective users' Office 365 SharePoint or OneDrive.
All calendar event invites, and similar data are stored in the respective users' Outlook.
Since MS Teams saves data across several Office 365 applications, identifying and collecting them in response to litigation can be complicated and time-consuming as it may require searching six or seven separate Office 365 storage locations. Therefore, companies must implement a Microsoft Teams archiving solution that provides a single dashboard for searching, securing, and reviewing Teams content for regulatory compliance and eDiscovery.
0 notes
Note
Hey, Luna, are you still doing the ask thing? If so, I was wondering if you had any headcanons regarding the Leonhart and Heartilly extended families? As in, do Squall, Linoa or Ellone have other still living relatives? People always talk about the parental issues in this game, but the rest of their families possibly being around never gets brought up.
I’m always “doing the ask thing,” haha~
(pardon me I’m gonna ramble real quick and then I’ll answer your actual questions)
I actually used to do this quite a lot before I got a new job and had to move my entire family of three people and eight(8, VIII) cats 500 miles northbound. Which was…incredibly stressful, and I just had no energy or brainspace left at the end of each day to communicate much, if at all, with large groups of people. So this stuff was right out. It pretty much tore me away from tumblr for a year and a half. I’ve been really bummed about that and kept trying to “get back into it,” but my several meager attempts at jumping back in got sidetracked by life responsibilities, and especially with tumblr’s new restrictions on external links not being searchable, the whole trawling for art thing I used to do just isn’t as feasible at this point in time because I have to edit each post very carefully so it will still show up in a search. That’s time-consuming. Maybe when I go back to 3rd shift in December (I hope) I’ll be able to art-hunt “full time,” again, but I just have a limited space in which to do that, now.
However, I can still do asks! And I really enjoy them, they’re fun and engaging and, hell I admit, I like it when people want to hear my opinion on things. But I was having a hard time, uh…asking for asks, haha. It felt too much like I was begging for attention. But then stuff happened and I had the worst pain spike I’ve had all year, and I kinda just broke down and said I needed a distraction. My chronic pain issues can be absolutely debilitating, and can lay me flat in bed for days (I had to take two days off work last week). But if I can manage to engross myself in something creative, it’s like a shot of cortisone. I think I get something of a rush, an adrenaline/endorphin kick out of it, and it does a lot to mitigate whatever the hell it is that causes my problem. I mean, that’s probably true of a lot of illnesses; you get attention and positive feedback and your brain rewards you with pleasant chemicals. But whatever, it worked and now I feel like I’m getting back in the game. I just have to keep the momentum up, now.
*cough* Ahem. So you asked me a thing. I will answer.
I do have headcanons about Squall’s extended family, specifically. I’ve not built out Rinoa’s yet…partially because it just never really comes up in the stories I’ve either plotted out or written. So I can’t answer that part of it–yet–but I can talk about Squall’s.
Working backwards: starting with Laguna’s side, Laguna is the oldest of two siblings, and not one, but both of them are kinda “black sheep” in the family. Partially it was their upbringing; Their mother, Elga Loire, was overworked and underappreciated, often working two jobs to keep food on the table (which she did very well). She didn’t have a lot of time to spend with her kids because of this, and the main reason for it was that their dad, Sevren Jr., was…kind of a loser? I mean, no, that’s not a good word, but a lot of people would call him that. He was an inventor. And always, always on the verge of the one that would make it big, this time. Automated chocobo saddles, “sliding” shoes to make walking more efficient, paramagic-powered chairs….yyyeah. You get why they were broke all the time. Sevren often traveled to demonstrate his newest creations, so he was absent a lot of the time, too. But when he came back, he would always bring the boys–Laguna and River (you must see where I’m going with this double-entendre)–some new toy or strange item from whatever country or town he’d visited.
This was fascinating to Laguna, in particular. Even as a kid, he dreamed of traveling the world. When he got older, joining the army seemed like the fastest way to do that, soooo….he roped his two best friends into joining with him. Heh.
Now, River…wasn’t into that stuff so much. He thought it was silly. He preferred to help Elga when she was at home, and even when she wasn’t, he ended up doing a lot of the house chores while his older brother went out and nearly died repeatedly trying to do dumb things. River was ‘fine’ just keeping to himself, reading and listening to music when he could get the radio to pick something up. As he grew up, he became a bit of a…punk? Like, he would be listening to Bad Religion in 1992. On the other hand, maybe Dream Theater when he was feeling happy. I imagine him looking a lot like Leon in KH2, but with hazel eyes (Sevren’s were brown) and no Griever all over his clothes. He cut his own hair so it always looked a bit jagged and unkempt, and he left it semi-long. Just generally prescient. He became pretty resentful of authority because he saw how it treated his mother and conspired to keep them all poor, and him too, when he got old enough to get a job (Laguna never had one until the army). It made him all the more determined to help his mother (and father, to an extent) weather the storm until the tides changed.
But then…well. They changed. But not for the better. Their dad died, and very suddenly, of an embolism. And, bitter as she was about having to support the family nearly single-handedly, Elga Loire loved Sevren quite a bit, and fell into some pretty deep broken heart syndrome. Inconsolable, she lost both her jobs. Laguna had already traipsed off to the army with his friends, and wouldn’t be aware of any of this for several weeks. River was left to care for their mother alone, and although they owned their small home, she had to sell it just to make ends meet. She moved in with a friend, and River…well, she sent him to the army, too. She insisted, thinking it was the best way to get both her sons out of this mess. Laguna already seemed to be doing well.
River did not do so well. He survived boot camp, but deserted his first year in service.
Laguna never heard from him, after that…and their mother passed away not too long afterward.
So…that’s Laguna’s end of it. As far as anyone knows, River is still out there. But Laguna hasn’t seen him in nearly 30 years. So, Squall has a missing uncle out there, somewhere, maybe.
Raine’s side…haha, geez, I might need to make a chart. In some ways, Raine is easier because she has no siblings and doesn’t know who her dad is. But I’ve traced her lineage back a bit further, and it gets…weird, in places. I might not be able to describe all of it, here.
Raine’s mother’s name is Gale. Gale is still alive, and Squall does meet her, once. It’s a solemn, one-time meeting, more an acknowledgement than a reunion. But it’s good. Gale is very practical. She never married, and never told Raine’s father she was pregnant (she didn’t like him for a permanent fixture). She was also a businesswoman. She owned and ran a hotel in middletown Dollet for many years. That’s where Raine got a lot of her experience before setting out on her own. Gale has sandy brown hair that she keeps short, and looks a bit like a taller Ellone in business casual, haha. But, but–those blue eyes. She has those. Her relation to Squall is evident.
It’s important to remember that although I enjoy both “he named himself” and “it’s Raine’s maiden name” theories, I’m pretty firmly in the camp of Raine’s last name being Leonhart. The story of Gale’s mother, Shiara (this is Arashi [storm] with the syllables reversed), depends on it, because she is the originator. I can’t detail the entire thing here–just too long–but the brief synopsis is that Shiara was a sorceress, in a time when sorceresses (”witches”) and “resistance” groups hell-bent on killing them all were in a state of cold war with one another. When Shiara became a sorceress, she panicked and ran away. She ended up being captured by one of these resistance factions, and had what I can only call a very complicated relationship with the faction’s leader, Dericho (this is the river Jericho with the first letter changed, making it phonetically very similar to Derecho, which is yet another type of storm).
Dericho’s faction was called, yes, the Pride, and they operated under a familiar leonine emblem. Of all his ancestors, Squall probably most closely resembles Dericho facially. Dericho is slightly shorter, his hair is a bit darker, and his eyes are a bit more on the grey side, but his posture, the way he carries himself, his facial expressions, his voice, even the sweep of his hair and the length he tends to keep it are all very familiar. A lot of those qualities were apparently recessive and just skipped a couple generations before thy found a match and popped up again.
How Shiara came to have Gale is a story I’d personally rather tell in prose, but I will say that it was Dericho who essentially named her, telling her in all his years of vetting people who want to be worthy of being called a Lion, Shiara was the only person he’d met with the heart of one. She carried that with her the rest of her life.
She is not, sadly, alive, having died at a ripe old age (and not terribly, since she was prepared with a willing successor nearby). She never actually told Gale about her powers, and to the very last, Gale never knew. The touch of sorcery ended there, seemingly. Dericho is also gone.
But I’m not done yet. One more generation, and this time, Hyne’s power is quite evident. Dericho’s mother, Hanwei, was a sorceress, his father was her knight, and they were quite open about it, feeling safe with it in their particular neck of the woods. Dericho was very familiar with the touch of his mother’s magic–she used it with him the way any mother would use a gentle hand, soothing scraped knees, gently grabbing his arm to pull him out of trouble–from fifteen feet away. His father, Mael[strom], was quite happy in his service to his wife and sorceress, and both Dericho’s parents loved him very much. When they embraced him, he could feel their connections tangling around him, and it was a very comfortable, safe way to be a child.
Of course, we can’t have that, can we?
When Dericho was about 5 or 6, they had been attending a fair that ran late into the night. Dericho started to nod off, so they went home early. It was a short distance, so they decided to walk instead of paying to ride a carriage to their home. Unfortunately, as you can probably guess, they were ambushed, by a particularly nasty faction called the Ridgebacks. Upon discovering Hanwei was a sorceress…well, let’s say the result was not pretty. At all. Dericho watched both his parents die, and his mother in particular, because she had no nearby successor. He was then “adopted” by the very faction who murdered his parents before his eyes.
Without going into specifics, they took this traumatized child, a blank slate, and turned him into one of them. But…not quite. By 17, Dericho didn’t know any other way of existing than as part of the factions, anymore, but he knew he still hated the Ridgebacks for what they had done. He murdered his “mentor” of a dozen or so years, killed several people, and took several more boys near his age on his way out of that particular clan. He started his own faction, with his own rules, and one was a “special” way of dispatching witches without having to burn them to dust. The Pride made their name on this and other standards which set their bar just a tad higher. They’d been in operation for almost ten years when Shiara showed up.
Then, as I said, things got complicated.
I should also note that Shiara and Dericho both lived in Centra. It was not long after Shiara flew free that the fateful Lunar Cry occurred, which deposited the Crystal Pillar and destroyed a third of the continent. Shiara barely escaped that disaster with her life…and her newborn daughter.
So….yeah, I think that’s about it, for now. If I ever get to working out my Rinoa’s tree, maybe I’ll put that up here as well, but for now, Squall’s all I’ve got, and his is hell in a handbasket.
I hope you enjoyed it, though!
#ff8#headcanons#squall leonhart#laguna loire#raine#oc: gale leonhart#oc: Dericho#oc: Mael#oc: Hanwei#oc: River Loire#oc: Elga Loire#oc: Sevren Loire#Jr.#ff8 family trees#ff8 world#succession of witches#lunar cry#location: centra#location: dollet#location: galbadia#asks#really great ask#feature#ssnakey-b
13 notes
·
View notes
Photo



OneNote for Note-taking: Yay or Nay?
So this was my first semester at uni and I took all my notes on OneNote. I would take some quick notes while in a lecture but mostly, I focused on listening to the lecturer. Then when I came home I would make another set of notes using the Cornell Note-taking Method (Well, partially. I don’t find the summary taking effective so I skip that).
I also made it a point to add all the important information regarding my subjects in the first week. All my assessment dates, lecturer contact details etc.
The reason I found it effective was:
I could quickly take notes during lectures and just as quickly type them out using the Cornell method. Also, adding pictures definitely helped me remember stuff better.
I could put a reminder via Outlook which helped me stay on top of things several times.
The tags like the to do tag, important tag etc., made it easier for me to quickly go through my notes because I can actually search stuff up using that.
Sometimes, I’d add my lecture slides to the notes but the great thing is that with OneNote when you search for something, the text on pictures automatically becomes searchable.
OneNote works great with Office Lens. We all have those lecturers who don’t put the pictures on the slides but add it during the lectures. I found it super convenient to take a picture using Office Lens which then linked the picture directly to the page I wanted.
Aesthetic. Not gonna lie. My handwritten notes can get a bit messy but that was never an issue with OneNote. Also, THEY HAVE GLITTER AND GALAXY COLOURED PENS. I REPEAT GLITTER AND GALAXY COLOURED PENS. THIS IS DEFCON ONE. THIS IS NOT A DRILL.
Haha all that aside, I thought it was great. It helped and I did awesome this semester. But I think for semester 2, I’ll probably stick to a mixture of written and online notes.
I think I would find it easier to remember stuff if I took notes on my computer during the lecture and then I could come home and take handwritten Cornell notes.
35 notes
·
View notes
Text
Microsoft Surface Duo: Here’s What It Needs
It’s hard to categorise Microsoft’s Surface Duo. Is it a phone? A phablet? A miniature Surface laptop with cellular connectivity? Microsoft itself simply calls it a ‘dual-screen device’, which isn’t particularly descriptive.
Perhaps Microsoft has invented a new product category (it certainly thinks it has). But with Samsung’s Galaxy Fold out and Motorola’s foldable V4 on the horizon, I’m not sure that would be true either.
How the device is defined - and how successful it is - will may come down to how it adapts Android to suit its hybrid ambitions. But it also needs some show-stealing features outside of the unusual design. Here’s what I’d like to see from Microsoft’s definitely-not-a-phone, smartphone.
One of the standout features of this year’s Pixel 4 is how Google has moved some of Assistant’s features away from needing the ‘hey Google’ wake word. In particular the baked in features like live transcription of videos when sound is toggled off. Or the searchable, automatically transcribed text from recorded voice notes. It’s here that Google has made Assistant genuinely useful instead of gimmicky. Microsoft should follow suit.
It’s not exactly clear what’s happening with Microsoft’s competitor to Assistant (if you can call it that), Cortana, but I’m not sure if it will be capable of handling the tasks above with the same aplomb that Assistant does.
There is a potential workaround, though. Considering Duo is going to run Android, then it’s possible the Windows-maker could work out a deal to port some of those Pixel specific features to the Duo. It’s not out of the realms of possibility considering that Google wants Assistant - and its best features - on as many devices as possible. Also something likeautomatic, searchable, voice transcription would be perfect for a productivity-focused phone.
Shoulder buttons
With Microsoft's cloud gaming platform Project xCloud on the way (not to mention Google's Stadia) I’d like to see Microsoft lean into this and make the best possible use of the Duo's dual-screen display for gaming. The LG G8X uses the second screen as a game controller with buttons that can be custom mapped, which greatly improves the touch-screen gaming experience.
But one thing it lacks is shoulder buttons. Obviously it’d be silly and unnecessary to build these into a phone, but a connected phone case could have them. A thin, sleek, Surface branded smartphone with full gaming capabilities and a full controller (without actually having a full controller) playing the latest AAA titles via a streaming service? Yes please.
Serious battery life
If the Duo is going to be pushed as a powerful productivity phone then it needs to have serious lasting power, especially with two power-draining displays. I’m interested to see what Microsoft does here because it has to finely balance making a two-display device dainty enough to fit comfortably in your pocket, but also fit a big enough battery in there without making it heavy and cumbersome.
The design for the Duo is apparently locked, so it will come down to how it has crammed a battery - or two - under either or both of those displays. But, if Microsoft is indeed pitching the Duo to be the ultimate productivity phone, lasting power will be a must.
Can Microsoft price it reasonably?
If there’s one takeaway from first generation foldable phones, it’s that they’re prohibitively expensive. Huawei, Samsung and the upcoming Motorola V4 are all (or rumoured to be, at least) priced around the $2000 mark. This is partially understandable because they’re using a new type of technology that’s presumably awkward and expensive to manufacture.
That’s less the case for the Duo, which is essentially two phone screens connected by a hinge - so you’d assume Microsoft could launch the Duo at a more reasonable price than the true foldable devices.
LG’s similar concept, the dual-screen LG G8X, costs $699. It’s not exactly the same, because the two displays are held together by a case and one is removable. But, because it’s not truly foldable, the Duo may fall closer to a premium smartphone price rather than an astronomical Galaxy Fold Price. At least, you’d hope so.
0 notes
Text
Online Donation Tools: The Best Ones for Your Nonprofit
If you’ve been in the fundraising game for quite a bit now, you probably understand the importance of establishing your presence in the online sphere. Every year online donations are taking up a bigger and bigger chunk of total funds to nonprofits, so this is definitely something worth investing in.
Though this is partially due to the natural progression of more people depending on technology, there are certain donation tools and other technology that can help you revamp your online fundraising to success!
The more donation tools you have, the more data you can collect, which will later help you develop better online fundraising strategies. It’s hard figuring out what tools are actually useful and how to use them in the best way. So, we’ll be going over these 2 questions for you:
What are online donation tools?
How do you make the most of your online donation tools?
These answers will walk you through all necessary things to know about online donation tools and how to smartly use them to plan and market your next fundraiser! Read on to get started.
The tools for online donations basically covers how your organization is going to accept and process donations on the internet. There are a lot of things to consider now that more of these transactions are happening online. How do people pay? What should you ask for in the online donation form? And what tools can we use to help us make this whole process easier?
Customizable Donation Pages
Your donation page is how your nonprofit is going to be accepting donations.
A lot of online donation software will provide donation form solutions so that your supporters have a page to go to when they’re feeling generous. However, a great online donation tool will come with the ability to customize your donation pages so that your nonprofit can offer a variety of options as well as be able to choose the data you collect.
There are certain key features your donation page should have in order to ensure an increase in giving. So, what are the best things to put on your donation page?
Mobile friendly/optimized content in order for donors to be able to give on the go.
Suggested donation amount buttons to make the donor experience easier and quicker.
Your organization’s brand and mission statement so that the process is streamlined and your nonprofit feels established.
Optional boxes that the donor doesn’t have to fill out so they have some privacy.
Recurring giving options in case the donor wants to be a consistent contributor!
Now that you know what tools and features to use to help your organization accept online donations, read on to learn how to best process those donations.
Payment Processing
So, how is your nonprofit going to process these donations? There are tons of online donation tools out there that will help with payment processing, whether the tool comes with your donation software or you decide to use a separate payment processor that is compatible.
Here are some things that you should make sure your donation tool or payment processor can manage:
ACH debit payments to help with debit card transactions
Credit card payments.
PCI compliance, which provides security. It’s estimated that almost half of donors decide not to donate because they feel as if the transaction is not safe.
For more information on payment processing for nonprofits, click here.
It’s easier to look for a donation tool that already works with other payment processors so that you can safely and securely collect the transactions that your donors are trusting you with. And when your online donation tool comes with a reliable payment processor, you can integrate it with your nonprofit CRM to manage the data taken from your donation pages.
Nonprofit CRM
Working in the nonprofit field, you already know the importance of having a well maintained CRM System. Constituent Relationship Management (CRM) software, though having a complicated and long name, is more generally known as a donor database. This is where the information from your online donation tools will end up.
In your CRM software you should be able to manage donor profiles, track donations, strengthen donor relationships, and more. If you want to find additional information, check out DNL OmniMedia’s guide to Blackbaud CRM, one of the top CRMs for nonprofits.
Having a good CRM platform is key to being able to manage your donor data. It’s a good idea to be looking out for donation tools that can be easily integrated into your CRM. The more tools and features you utilize, the more data you have. And the more data you have, the better you can plan smart fundraising campaigns and develop in-depth marketing strategies.
Now that you’ve learned how online donation tools can help you accept and process donations and how the right tools will integrate with your nonprofit CRM, how do you take advantage of these tools and start planning campaigns? From doubling donations to launching new events, it is pretty clear that with more data comes more opportunity.
Matching gifts to increase donations
Matching gifts is one of the easiest but also overlooked ways for nonprofits to increase its donations. If you don’t know exactly what we’re talking about, corporate matching gift programs are when an employer will match or more an employee’s donation to a charity or cause.
So, why are matching gift programs not utilized as much as they should be? This is probably because either the donor has no idea that the business they’re a part of even offers this or the business doesn’t know that their employee made a contribution.
This is where online donation tools come in, as you can embed a searchable database full of matching gift eligible corporations into you donation page. This way, donors can:
Search for their business to see if their donation will be matched.
Get information on the program guidelines like how much the employer will match and the deadline to submit a matching gift form.
From the management side of a nonprofit, having a matching gift tool is also useful for you. Not only do you increase your funds, but you can use your donor database to figure out who is eligible for the program with business affiliation metrics. This way you can market to those donors with specific matching gift news and reminders on not missing the deadline date.
Double the Donation has loads of information on corporate matching gift programs as well as a handy online matching gift tool that you can put right onto your page! But matching gifts isn’t the only thing you can do with donor data. You can use that information for more analytics, as you’ll read next.
Donor research for better marketing
With all your online donation tools, your nonprofit CRM should be brimming with useful donor data. It’s smart to manage your data by picking out certain traits to track. You can then use those various traits to segment your donors into groups and target them for different reasons. This is called prospect research and is a way of researching your donors to determine giving desire and ability.
What are those things that you should be tracking from your donors? This information is probably going to be coming from your online donation tools like your forms and payment processors, so look out for:
Personal factors like age, location, gender, and payment preference.
Wealth screening metrics like real estate ownership, SEC transactions, business affiliations, and political giving.
Philanthropic indicators including previous donations to your nonprofit, donations to other nonprofits, nonprofit involvement, and other information about hobbies and social media.
Following these data points can really change how you market if you learn to segment your donors. People tend to delete and not read mass messages or announcements because they then think their actual involvement is not actually necessary. Develop different strategies depending on who you want to target so that your emails are more personable and unique to each donor.
It also makes sense to target different types of donors for different fundraising campaigns. For example, if you are planning a mobile fundraiser, you should focus your energies on a younger crowd than those who don’t even know how to work a cell phone.
With donor wealth screening factors and philanthropic indicators, you can figure out who potential major donors are. Major donors usually have very consistent and personable relationships with nonprofits. Having a list of potentials can give you a clue into who you should be investing time in to develop a stronger relationship with.
Peer-to-peer fundraising
Remember when we talked about online donation tools that help create your donation page? Now, imagine that your online donation tool creates multiple donation pages, maybe even personalizing each one with a different story, but each page still is giving to the same campaign. This is the basic idea behind peer-to-peer fundraising and by also using an online donation tool, it can be incredibly simple.
Peer-to-peer fundraising is when you recruit a group of volunteers to fundraise on your nonprofit’s behalf. Each volunteer will have their own donation page which they can then post on their social media to encourage family and friends to donate. Their pages can then be shared further by the volunteer’s social network.
Because of its wide reach, peer-to-peer fundraising can raise a lot of money and fast! This is why you have to have the right online donation tool to really milk the benefits. Look for these features:
Individual donation pages for each volunteer. This way, each individual’s personal network will know that they are supporting a friend when they donate.
Event updates on the page. This way, the campaign feels more like an ongoing story, which keeps people invested and encourages more donations.
Post-campaign analytics. If your online donation tool is able to compile data from past fundraising campaigns, you can start to track how well your event did in donor engagement and retention. This data can then help you for planning future events!
Your online donation tools are your nonprofits best friends. They should be working together for one common goal: to increase donations. From matching gifts to planning fundraisers, there’s a lot you can do to make the most of your online donation tools!
Now that you’ve read our guide, you should be confident enough to take the first steps to increase your online fundraising. You might have known some of these things already, but it always helps to go over it again and learn which tools are the best for what. Good luck!
from http://npengage.com/nonprofit-fundraising/nonprofit-online-donation-tools/ from http://thereallaptoplifestyle1.blogspot.com/2019/09/online-donation-tools-best-ones-for.html
0 notes
Text
Disclosure of personal an contact information by young people in social networking sites: An analysis using Facebook profiles as an example.
Taraszow, T., Aristodemou, E., Shitta, G., Laouris, Y., & Arsoy, A. (2010)
This study aimed to look at “... the habits of young Facebook members with respect to publishing personal and contact information.” The methodology it used was directly observing profiles - so actual field data. 131 Facebook profiles were observed, and all members were in the age group of 13-30s.
INTRODUCTION TO SOCIAL NETWORKING SITES:
SNSs can be defined as “... web-based services that allow individuals to:
construct a public or semi-public profile
communicate with other uses with whom they share a connection and
view and navigate through their own list of connections as well as those of others.
Acquisti and Gross (2006): “Internet-communities where individuals interact with others through profiles that represent their selves.”
“SNSs simplify communication by integrating digital communication and publishing, supporting an individual’s construction of their digital identity and providing a single-point access to various communication tools, thus enabling communication across time and space.”
“The main motivation is communication, interaction and maintaining relationships.” Is this just adults or children too?
CHARACTERISTICS OF SOCIAL NETWORKING SITES:
“... their main characteristic consists of visible profiles that display not only an ‘articulated list of friends’, but also detailed personal information.”
:... create a profile to ‘type oneself into being’.” So create an online self.
“Nobody is really forced to join an SNS, create a profile and reveal personal information.” But now we need to stay connected via online.
“... the connection of users with people they already know in real life, that is, existing friends, or to completely new people.”
“The public display of connections is a crucial component of SNSs.” Why?
“... profiles on Facebook used to be by default visible to any other user unless the profile owner denied permission. (...) Facebook changed their settings and made profiles by default visible to friends only, with the option to change one own’s profile into a public one.” But how many people, or more specifically adolescents, know about this and want to keep their profile private?
CONCEPTS OF PRIVACY:
“...privacy is a relative concept that should be seen as a continuum.”
“...privacy is understood as the ‘right to be let alone’.”
“...whether and how the law will protect the right to privacy.” But nothing is ever fully private once online. An example is unauthorized circulation of individuals’ portraits.
“... privacy means one’s control over one’s own personal information.” A good definition to use!
“... individuals are continually engaged in a process of adjustment to find a balance between the desire for privacy and the desire for disclosure of one’s self to others.” New technology can alter this balance though.
“... it is almost impossible to know when, how and to what extent others circulate one’s own personal information in SNSs.”
Privacy is also “... the ‘monitored’ and ‘searchable’ part of anyone’s life.” , “... traces of information that one ‘leaves’ behind in the environment.”
“... ‘life where less can be searched is a life more private’ (Lessing 1998: 1)”
“... individual life becomes more and more monitored as well as searchable as every activity online can be monitored and leaves a footprint or record.”
Privacy can also be: “... aspects of a person’s life that are culturally recognized as being safe and protected from others’ judgement.”
PRIVACY IN SOCIAL NETWORKING SITES AND IN FACEBOOK:
“Internet users, members of SNSs in particular, seem either not concerned about their privacy or not aware of the loss of privacy they suffer during their time online.”
“... the teenagers and young adults freely disclose personal and private information on SNSs.”
“Barnes (2006) argues that the privacy paradox occurs when users, especially teenagers, are not aware of the nature of the Internet in general and SNSs in particular.” → “... a disconnection between the users’ desire to protect their privacy and their actual behavior.”
SNSs encourage people to reveal personal info, and “That encouragement results in people really disclosing personal information without connecting it with their subsequent loss of privacy.”
On SNSs, “... any information is personally identifiable.”
“... an individual’s privacy concerns are only a weak predictor of his/her membership in an SNS.” They would join and share anyways. Why?
“... some SNS members demonstrated significant misconceptions about the SNS’s reach as well as the visibility of their profiles.” Not educated?
“... teenagers being generally worried about privacy issues and setting their profile to private, yet revealing private information to several hundred people in their friends’ list whom they have known only casually.”
“... Facebook members reveal a great amount of personal information about themselves openly, while at the same time they are not aware of their privacy options or who can view their profile.”
“.. most youth are aware not only of the type of information they are publishing in Facebook, but also of the potential dangers related to publishing detailed contact information.” But then why do they still participate in risky behaviour?
GENDER DIFFERENCES IN REVEALING PERSONAL INFORMATION:
“... female members were less likely to disclose their sexual orientation, personal address and mobile phone number than male members.” Are females generally more cautious?
Do “... males disclose different types of information than females do”?
THE STUDY:
131 young people (68 females and 63 males)
Ages ranged from 14 to 29 years. “The age range was decided according to the European Commission’s defined age range for youth, which is considered to be from 13 to 30 years.”
“... those young people whose Facebook profiles were examined, were not aware of this process...” Ethics issues?
Study used SPSS to analyse data.
RESULTS:
“Almost all subjects (89.3%) published a portrait profile picture of themselves from which one can identify their gender and approximate age.” Do people realize a picture can reveal information about themselves?
“... the majority of the subjects published their real names (96.2%) in comparison to a partial name (3.8%) or a fake name (0.0%).”
“... all participants disclosed their birth date...”
“No significant difference was found with respect to having a public or non-public ‘profile’ between female and male users.” as well as a portrait picture, real name, birth date, website, IM screen names and hometown.
Males were more likely to disclose their mobile phone number and other numbers, email addresses and home address than females.
“...96.6% of the participants aged 13-17 had their profile set as private, whereas among participants aged 18-22 only 64.1% had that.”
DISCUSSION AND CONCLUSIONS:
“... even though profiles are set to private, people tend to accept as their friends complete strangers.” Why? A feeling over control to whom they accept as compared to a completely public profile? “Thus, revealing personal and contact information on their profile only to friends can be equally threatening as having a public profile.”
“... most people use a facial picture of themselves in their profiles (...) This can pose a risk to members as it removes their protection of anonymity and allows them to be identified in real life as well.”
“Providing a full [real] name can make users more easily traceable in their real life.” But maybe want to be found?
“... potential ability to reconstruct users’ social security numbers utilizing a combination of information often found in profiles...” Identity theft. Do we have something like this in NZ?
“... majority of people reveal their email address to others...” Not only bullying can occur, but hacking of other profiles.
“Several incidents have become known through the media, where strangers found potential victims from SNSs, tracked them down, followed them and sometimes abused or even killed them.”
“... males report more often their mobile phone number than females do...” Reasoning? “... males are considered to be more dynamic and powerful, also less concerned with possible harm. Thus, without thinking too much about it, they reveal their mobile phone number on the Internet.”
Males between 18 and 22 are more likely to share their email address, IM screen names and home address than females. Reasoning? “... males of this age group are developmentally changing (moving from teens to adulthood) and want to present themselves as more independent, powerful and available to other people.” and “... males are more likely to have positive attitudes towards the Internet as well as greater experience in using it.”
“... clarifying young people’s knowledge and consciousness of privacy issues in SNSs with surveys or interviews is part of the continuing research agenda of this project.”
“... youth, especially between the ages of 18 and 22, seem unaware of the potential dangers they are facing when entering real personal and contact information in their profiles while accepting ‘friendship’ requests from strangers.”
0 notes
Text
Late to the Scene, the “Safely Ensuring Lives Future Deployment and Research In Vehicle Evolution Act” (“SELF DRIVE Act”) Seeks to Set Course for Future Development
As the race to deploy highly autonomous vehicles continues, the promise of a more ubiquitous presence of autonomous vehicles has led to a patchwork of regulations as states attempt to prepare for the inevitability of a self-driving car. Twenty-two states have either passed legislation related to autonomous vehicles or adopted regulations through a governor’s executive order.[1] This patchwork of legislation ranges from the simple, such as authorizing a study on autonomous vehicles[2], to robust requirements for automated vehicles.[3] As previously covered on Dashboard Insights, the Auto Industry has been advocating for federal (rather than state-by-state) regulation of autonomous vehicles, hoping to bring more consistency and to encourage innovation. On July 28th, the House Energy and Commerce Committee stepped into the mix by voting 54 – 0 to advance to the full House a bill known as the “Safely Ensuring Lives Future Deployment and Research In Vehicle Evolution Act” (“SELF DRIVE Act”), H.R. 3388. The SELF DRIVE Act would be the first major federal effort to regulate autonomous vehicles beyond the previously adopted “voluntary” guidelines.
Preemption
The SELF DRIVE Act would clarify and expand the National Highway Traffic Safety Administration’s authority with respect to highly automated vehicles. Foremost in the draft bill is its express preemption of state laws governing the design, construction, or performance of highly automated vehicles. Under the bill, states may continue to regulate licensing, registration, liability, safety inspections and certain other aspects of vehicles and their operation, but they would be preempted from regulating the design, construction or performance of highly automated vehicles, automated driving systems, or components of automated driving systems unless the state law is identical to a standard prescribed under the Federal law. However, this does not preclude the United States Government, a State, or a political subdivision of a State from prescribing a higher performance requirement for its own use. The preemption language should begin pushing toward a regulatory regime that avoids a patchwork of differing requirements that could stifle the rollout of automated vehicles.
Rulemaking and Safety Priority Plan
Dovetailing the approach NHTSA has been pursuing in this area, the SELF DRIVE Act contemplates providing oversight for the safe development and production of automated vehicles. Specifically, it would require NHTSA to promulgate a final rule requiring manufacturers to submit safety assessment certifications, whereby manufacturers would submit test data and other information demonstrating that the vehicles are likely to function as intended and contain fail-safe features. Until NHTSA issues the final rule, the SELF DRIVE Act would require manufacturers to submit the safety assessment letters described in the Federal Automated Vehicles Policy (or any successor guidance). The bill would also require NHTSA to submit a rulemaking and safety priority plan to Congress, outlining the agency’s rulemaking priorities with respect to such areas as human machine interface, sensors, and actuators, as well as process and procedure standards for software and cybersecurity.
Cybersecurity
In line with the industry’s increased focus on cybersecurity, the SELF DRIVE Act would prohibit the manufacture, sale, or importation of highly automated vehicles, vehicles that perform “partial driving automation,” or automative driving system unless the manufacturer has developed a detailed cybersecurity plan, which largely follows NHTSA’s current guidance on cybersecurity.[4] The written cybersecurity policy would include:
Policies outlining the practices for detecting and responding to cyber-attacks and other attendant risks;
A process for identifying and mitigating reasonably foreseeable vulnerabilities;
A process for taking preventative and corrective actions to mitigate potential vulnerabilities;
Incident response plans;
Intrusion detection plans and prevention systems;
Identification of a point of contact with responsibility for the management of cybersecurity;
A process for controlling access to automated driving systems; and
A process for training employees and supervision for implementing and maintaining policies and procedures.
Exemptions from Safety Standards
The SELF DRIVE Act would create a fifth exemption category under 49 U.S.C. § 30113, authorizing NHTSA to exempt a manufacturer from meeting one or more Federal motor vehicle safety standards (FMVSSs) to facilitate the development and field testing of highly automated vehicles, features or systems. To qualify for an exemption, the petitioning manufacturer must demonstrate that the safety level of the system or feature at least equals the safety level of the standard for which exemption is sought or that the vehicle provides an overall safety level at least equal to the overall safety level of nonexempt vehicles.
Under this provision, NHTSA would have authority to exempt up to 25,000 vehicles manufactured in the first 12-month period, 50,000 vehicles manufactured in the second 12-month period, 100,000 vehicles manufactured in the third 12-month period, and 100,000 vehicles manufactured in the fourth 12-month period. Manufacturers would be required to provide information about all crashes involving exempted vehicles of which the manufacturer becomes aware. The bill would also require NHTSA to create a searchable public database of exempted vehicles.
The SELF DRIVE Act also seeks to tackle the challenge of public perception by requiring reports to Congress and eventually initiating rulemaking to require manufacturers to disclose features to consumers. These disclosures would likely include a standardized or semi-standardized description of the features and limitations of the vehicle’s driving automation system or feature.
Highly Automated Vehicle Advisory Council
One of the key challenges facing NHTSA in regulating automated cars is the agency’s ability to keep up with the rapid development of automated vehicles and their systems. In this regard, the bill would require NHTSA to establish a Highly Automated Vehicle Advisory Council, drawing members from business, academia, engineers, and safety and consumer advocates, among others. The Council would gather information, develop technical advice, and make recommendations to NHTSA regarding a variety of emerging issues, such as developing a framework for information sharing among manufacturers, advancing mobility access for the disabled community and senior citizens, labor and employment issues affected by the deployment of highly automated vehicles, environmental impacts, and the impact of developments in cybersecurity.
The SELF DRIVE Act would address some of the industries concerns with the patchwork of regulations and uncertainty surrounding how NHTSA will regulate a world with greater adoption of highly automated vehicles. The industry should review their current safety policies, particularly those related to cybersecurity, to ensure that they are keeping up with the rapid evolution of the industry.
Rear Seat Occupant Alert System
The bill would require NHTSA, within two years, to issue a final rule requiring (subject to a two-year lead time) all new passenger vehicles (less than 10,000 pounds gross vehicle weight) to be equipped with a system that alerts the operator to check the rear seats after the vehicle is turned off.
Headlamps
The bill compels NHTSA to research the development of updated safety standards for headlamps “that would improve the performance of headlamps and improve overall safety.” This research must be completed with two years. Upon completion of the research, NHTSA shall either initiate rulemaking to revise its headlamp standards or submit a report to Congress explaining why a revision is not justified.
Privacy Plan
The bill would prohibit a manufacturer from selling a highly automated vehicle, partially automated vehicle, or automated driving system unless the manufacturer has developed a written privacy plan that specifies how data will be collected, used, shared, and stored. Violations of these requirements would constitute an unfair or deceptive act under Section 5 of the Federal Trade Commission Act.
[1] The states with autonomous vehicle legislation or executive action include: Alabama, Arkansas, Arizona, California, Colorado, Florida, Georgia, Louisiana, Michigan, New York, Massachusetts, Nevada, North Dakota, Pennsylvania, South Carolina, Tennessee, Texas, Utah, Virginia, Vermont, Washington, Wisconsin and the District of Columbia. http://ift.tt/2mtVZDK
[2] See Alabama SJR 81.
[3] See Michigan Senate Bill No. 996
[4] http://ift.tt/2qk8LKw
Late to the Scene, the “Safely Ensuring Lives Future Deployment and Research In Vehicle Evolution Act” (“SELF DRIVE Act”) Seeks to Set Course for Future Development published first on http://ift.tt/2kTPCwo
0 notes
Text
Want To Generate Traffic for Website ”Use SEO”
SEO could be a term you have heard before. Yet, you can always ask why it is so important when it comes to generating traffic and growing attention to your website. SEO Service is necessary for anyone who has a website. SEO is also known as search engine optimization, which will make your website more searchable in search engines. You will have more visitors, which implies more business.

What is SEO?
SEO is short for search engine optimization. Search engine optimization is a method of strategies, techniques, and tactics to increase the number of visitors to a website by getting a high rank on the search engine result pages (SERPs), including Google, Yahoo, Bing, and other search engines. Besides, it is a great way to improve the quality of your websites, by making them faster and easier to use.
Why Is SEO Necessary?
In today’s competitive world, SEO is more important than ever. No matter how much you invest in marketing to increase sales, it is important that you invest a partial amount on SEO to increase your online presence and overall sales. SEO will help push your website towards the top of search engine results which will help not only increase sales but also will help promote your brand to potential customers.
Here are some reasons why SEO is important to your website:
To rank higher on Search Engines
In today’s competitive world, you must have a clear plan for your business. When people search in Google, Yahoo, Bing, and other search engines they always expect to find the best results. Most search engine users are more likely to click on any of three or four suggestions on the top of the results page. To gain visitors, your website needs to stay on top of SERP. It is only possible when you start to optimize your website for search engines and do so on a regular and frequent basis.
To Get Return on Investment
To understand your return on investment you have to link SEO to web analytics data. You may notice some keywords that have high conversion rates that you need to pay particular attention to. If you raise your rank to the top 3 on the first page for a given keyword, where most clicks go, you could get a huge return on your modest investment in SEO Services.
To Boost Sales
To run the business and increase sales in a competitive marketplace, you will need SEO Services. You need a website which is SEO-friendly, responsive, and easy to use. Throwing some keywords with high traffic on your title tags and headers will not do much for your business but an SEO strategy designed to generate leads and direct them to the right information can be very profitable for your business.
0 notes
Text
Tree data standardisation
The BristolTrees site currently maps around 66,000 trees in Bristol and surrounds obtained from multiple sources. Each source has provided data in its own format on the trees in their care so it has been necessary to convert this heterogeneous data to a unified data set. The following notes on this project are a contribution to the discussion of standardisation.
Trees are complex dynamic objects and the records kept reflect the different purposes for which data is collected and stored. Data from an arboretum will be different to that from the part of the council responsible for planting and general maintenance and different again from the data needed for Tree Protection orders (TPO) Not only does purpose affect what data is held, it determines the precision of the data and it determines accuracy since the cost of errors will vary by purpose.
Core data
The core data used in Bristol Trees are:
Identifier: constructed {sourcecode}-{sourceid}
Species - Primary: Botanical (latin) name; derived Common name
Location - Primary: Lat/long; derived: OS Easting/Northing; Secondary: Site, Address
Dimensions: survey date; girth (trunk circumference) in cm; height in m ; canopy width in m
Age : age at survey date | date planted | maturity
State: Live Tree | Stump | Dead | Tree pit | No tree | Sculpture ; tree condition
Description: information about this specific tree; history etc
Tree identity
To provide a unique internal identifier which retains the identity in the source, Bristol Trees constructs a binomial code, using a code for the source and the source code. It is important for the source identifier be recoverable so that matching to source data and export of updated data is possible. This depends on the existence of a unique code or combination of codes in the source data and this is not always the case. Since identifiers are used in URLs, some reformatting may be needed, for example to replace / by underscore. (or uri-encoding)
Species
The species of tree is specified by the Botanical name. Since Bristol Trees aims to be a ‘Virtual arboretum’, we strife for precision at least to the level of genus and species. Precision in the identification is more important for botanical reasons than it is for TPOs where genus may be sufficient. For a number of species, there are multiple botanical names in use and since such synonyms are common, common synonyms are acceptable; for example whilst the preferred botanical name for the London Plane is Platanus x acerifolia, the synonym Platanus x hispanica is still widely used.
There is a recommend style of the Botanical name, for example as described by this document from the RHS. Names which don’t conform to this style, for example by omission of quotes around cultivar names, or incorrect notations finer than species (var., subsp., f., cultivar) have to be standardised.
Although tree species are often known by their common name, the quality of these names in the data is very variable in precision and accuracy. In Bristol Trees the common name is derived from the Botanical name via a species dataset, now containing over 1000 species and variants, built as data was added. Derivation is preferable since to be usable, common names need standardisation in name and format (is it Common beech or Common Beech?) and are also culturally dependant - Sycamore in the US is Platanus occidentalis, in the UK it is Acer pseudoplatanus.
The coverage of The Collins Tree Guide by Owen Johnson and David More is excellent although there are a few missing species A machine-readable source of approved names would be very useful as part of a standardisation project and although there are several searchable on-line sources for specific purposes, I haven’t found a suitable open data set. Wikipedia is very useful for automating checking to species level.
Location
Location is provided in several forms: OS easting/northing coordinates, OS Grid Reference and latitude/longitude (implicity in WGS84). These are functionally equivalent and in Bristol Trees, for ease of mapping and lookup from a smartphone, lat/long is the primary data. There are however some benefits in using OS coordinates. The resolution of 6 digit coordinates,at 1 metre, is generally appropriate for the location of trees, whilst lat/longs are often given with excess precision, sometimes down to a micron, presumably as a result of conversion from OS coordinates which did not preserve the original precision. Another benefit is that OS coordinates can be used to define tiles of a size useful for selecting trees by proximity. Preferable both systems can be held but any one is satisfactory in source data.
Additionally, most data sources supply less precise locations, in the form of addresses, street names, park names, wards etc. Useful as these may be as supporting data, such names need supporting definition to be really valuable. Given that the boundaries of such units are subject to change (ward names may reflect old boundaries) it would be better to derive such names in demand, especially since such services would be valuable in other contexts. Nevertheless, local area names, especially park and reserves names are useful for searching.
Tree dimensions
Tree dimensions vary between sources, again depending on purpose. The Tree Register provides a good summary of tree measurement.
The most common dimension is girth, partly because it is easy to measure and partly because it is a good surrogate for age. Two measures are used in practice: foresters use the measure Diameter at Breast Height (DBH) whereas popularly, the circumference (girth) is given. Girth can be read directly from a tape measure whereas DBH requires conversion, or as I recently discovered, the use of a tape calibrated so that the diameter can be read directly. I’ve opted to record the girth in cm.
Height of tree is often provided but this is difficult to measure with accuracy and precision may be limited to height bands, which vary between sources. For street trees, the size of the canopy is important and one source provides coverage data in each quadrant. Some sources specify width (diameter), others area, often with banding.
For any measurement, the survey date is necessary yet is missing in many sources. This greatly reduces the value of the data.
Tree age
For historical records of trees, particularly ancient ones, the date of planting / age is important, as it is for local historians. Sometimes the date of planting is know with some accuracy, such as oaks planted for the coronation of Edward VII in 1902. For others, the planting date can be deduced from historical records. In rare cases it is measured by ring count. Clearly it is preferable to store the date and derive the age, but care is needed to avoid spurious precision.
Tree state
Whilst species name, location and dimensions are relatively easy to standardise data on the state of the tree varies greatly with purpose. For a Stump survey aimed at tree replacement, gross categories of live tree, dead tree, stump, tree pit, no tree are needed. The state of ‘sculpture’ was added for trees carved to form a sculpture. For growing trees, stages in maturity are needed. For ancient tree survey, forms of the tree - maiden, pollarded, fallen etc are recorded. Disease and other damage observations are needed for tree maintenance. Further analysis and standardisation is needed in Bristol Trees.
Tree description
Notes are often provided by naturalists on the special features of a specific tree, as opposed to notes about the species. For example a tree may be a species champion in its county, or display particular uncommon features for its species, or be growing in a unique manner or location.
Complications
Real world data is imperfect and cleaning is nearly always going to be needed, so validation and standardisation scripts and manual intervention are generally needed.
Missing data is represented in source-specific ways often involving marker values. In the XML, missing data is handled by omitting the missing element.
Partially missing data for species is ambiguous. I have taken Quercus and Quercus sp. to be synonymous but sometimes Quercus alone means the (locally) most common species of that Genus (in Bristol, Quercus robur), in which case Quercus sp. may mean a species of Quercus which is not the default. Full species naming is of course desirable but notation for imprecise identification is needed in practice.
Round-tripping Having made corrections and other re-codings, export of the revised data in the original format (round-tripping) becomes problematic. This capability would be needed if citizen-surveyed data is to be contributed back to the source organisation. (Whether the source organisation can input from its export format is of course another matter) An early decision on whether round-tripping is to be supported is necessary. For example it would be sensible to write scripts to load from the source and its inverse to export to the source at the same time. At present round-tripping is not yet fully supported in Bristol Trees.
Duplication. Taking data from multiple sources raises the problem of multiple representations of the same tree. De-duplication has yet to be handled automatically, since it is possible that species as well as location will be different for the same tree.
Accuracy
Effort has so far focused on data acquisition, cleaning and normalisation. We have yet to face the much bigger problem of assessing the accuracy of the data supplied, not least because it is often acquired some time ago, but is undated.
Re-surveying 66,000 trees seems a daunting task, even if supported by citizen data collection. However sampling at least is needed to gain a sense of the accuracy of the data. The development of the smartphone tree finding and surveying tools in BristolTrees will be valuable for data collection. For standardisation purposes it would be helpful if data set metadata provided information on the precision and accuracy of data items.
Standardisation
Increased standardisation of tree data would certainly ease the problems of dataset use and integration. However the functional nature of the data, the lack of funds and capability in data management in the source organisations may be limiting factors in the implementation of any standard at source. It is perhaps more realistic for organisations gathering data to focus on the accuracy and currency of data whilst the open data community could establish collections of data reformatted to a standard, and curate a master species list.
0 notes
Link
YOUR MONEY Death Is Inevitable. Financial Turmoil Afterward Isn’t. Retiring By JOHN F. WASIK JAN. 13, 2017 Continue reading the main storyShare This Page Share Tweet Email More Save Photo Erika Lupo, whose husband, John, died of cancer last year at age 57, was better prepared than many widows. He did everything he could to prepare his estate and make sure his wife knew where his assets were. Credit Bryan Anselm for The New York Times MOST of us do not even want to contemplate the death of a spouse or partner — much less the prospect of having to take care of the financial end of such a loss while still grieving. There are, however, plenty of details that people can attend to in advance that can avoid some measure of stress when the time comes. Most people tend to ignore or procrastinate over such tasks — for obvious reasons — but planning can certainly ease some avoidable financial sorrows. The first step to prepare for this unhappy life stage is to make sure both partners have a thorough understanding of the couple’s spousal and individual assets and where they are. Are there life insurance policies? Do they name the right survivors as beneficiaries? What about pensions and other retirement plans? How will the money flow after someone’s death? As all too many people find out too late, this sort of preparation should start well before either spouse becomes disabled or dies. The general principle is to protect the survivor and enable him or her to make decisions about the estate’s assets. Continue reading the main story ADVERTISEMENT Continue reading the main story That means setting up a durable power of attorney for health care and finances — two separate documents, one set for each spouse. You don’t need a lawyer to put these in place, but they should be signed so that one spouse can make medical and financial decisions if the other is incapacitated. Photo Photographs of Erika Lupo’s husband in their home on East Shore Trail in Sparta, N.J. Credit Bryan Anselm for The New York Times One couple who went through this exercise, Erika and John Lupo of Sparta, N.J., did so sooner than most, and it paid off. When Mr. Lupo died of cancer last year at age 57, Ms. Lupo, 51, who runs an acting school, was extraordinarily well prepared — unlike many widows. In his final days, Mr. Lupo, a former salesman, did everything he could to prepare his estate and make sure his wife knew where his assets were — and how they could easily be bequeathed to her and heirs. Photo Erika Lupo with her son, Trent Lupo, 14. Her husband worked with a certified financial planner shortly before his death. “We had everything in place,” she said. “I had no idea how to do any of this. They guided me seamlessly.” Credit Bryan Anselm for The New York Times There was a bit of complex estate and financial planning involved, because Mr. Lupo had a daughter from a previous marriage, and the couple has a teenage son. Working with Mark Germain, a certified financial planner with Beacon Wealth Management in Hackensack, N.J., Mr. Lupo had several documents in order just a few weeks before he died. “We made out wills, durable powers of attorney and a trust” for Mr. Lupo’s daughter, Mr. Germain said. “We also made some arrangements for the son in the will. We had to do some sophisticated planning.” For Mr. Lupo’s widow, the advance planning came as a great relief even as she mourned her husband. “We had everything in place,” she said. “I had no idea how to do any of this. They guided me seamlessly.” Organization of one’s estate will certainly not lessen the emotional turmoil, but it will smooth the way to financial security in the fog of grief. More than 800,000 Americans lose their spouses each year, and 700,000 of them are women, according to the Census Bureau. Because women generally outlive men, they spend an average of 14 years without a spouse. There are now more than 14 million widows and widowers, accounting for about one-quarter of the over-65 population. Although in the past, one spouse — usually the husband — “took care” of all of the financial planning, Mr. Germain said, most people don’t do a very good job of it. That traditional role is often a smoke screen for partial preparation and keeping one’s spouse largely in the dark, he said. ADVERTISEMENT Continue reading the main story “Don’t think of an estate plan as a ‘death’ plan,” Mr. Germain advised. “I try to get that out of my clients’ minds. Many people don’t have a clue as to what will happen with an estate after death.” One client, he said, a 72-year-old man, changed ownership of his assets while his wife was dying, creating financial chaos. But times are clearly changing when it comes to traditional gender roles. “Twenty years ago, the average husband did all of the finances,” said Catherine Anne Seal, a Colorado Springs-based estate planning lawyer and the president of the National Academy of Elder Law Attorneys. “Now it’s not uncommon for the wife to handle finances.” Widows who are inexperienced with money management tend to make a common mistake, Ms. Seal said: They “make imprudent gifts to adult children” within a year of their husband’s death. Down the road, this may leave the widow short of money, depending on how long she survives her husband. Ms. Seal advises that couples title their assets “jointly with rights of survivorship,” particularly if their joint estate is under $4 million. But estate planning becomes more complex if there are multiple marriages and stepchildren involved. “Couples in second marriages need good estate planning with attorneys who understand these issues,” Ms. Seal said. Such professionals can help provide a checklist of what both spouses should know: Where are the documents relating to Social Security? Insurance policies? Marriage and birth certificates? Wills? Powers of attorney? Living trusts? It is also important to have a list and statement of all assets, such as real estate, stocks, bonds, savings accounts, safe deposit boxes and trusts. Also on the to-do list: locating the titles to all properties, ranging from autos to vacation homes. Veterans should have copies of all military discharge papers. Another vital step is to appoint capable, financially skilled trustees in your powers of attorney, Mr. Germain said. They could be family members, but they should have some working knowledge of how to handle money. ADVERTISEMENT Continue reading the main story The National Academy of Elder Law Attorneys has a searchable online directory for people who want to find a lawyer who can help handle these complexities. When interviewing prospective lawyers, ask them if they specialize in the particulars of your situation: Are you divorced? Do you have a special-needs child? Do you have properties in several states? You should also involve your tax planner and financial planner — if you have them. A certified financial planner who acts as fiduciary can work directly with your accountant and family lawyer. At the root of a transparent estate plan, most lawyers say, is openness and communication. Both spouses should attend the meetings with lawyers and financial professionals. And each spouse should know the location of all important documents and understand what will happen upon death. Contingency plans should be made in the event one spouse becomes disabled or incapacitated. Prepare a workable estate plan while you are healthy. Cognitive decline can take its toll on couples’ abilities to manage and execute an estate plan. “Most people are in denial about what the aging process looks like,” Ms. Seal said. “That’s why you need trustworthy agents in your powers-of-attorney documents. You need to create a plan for incapacity.” Ms. Lupo of New Jersey emphatically agrees. “Realize that you need to take the time to understand your finances,” she said. “When you’re well — that’s when you need to plan.”
0 notes
Text
Case Summaries – North Carolina Court of Appeals (June 16, 2020)
This post summarizes published criminal cases issued by the North Carolina Court of Appeals on June 16, 2020.
As always, these summaries will be added to Smith’s Criminal Case Compendium, a free, searchable database of case annotations from 2008 to today.
Thanks to Chris Tyner for preparing the majority of these summaries.
(1) Error, but no prejudice, in admitting field test results on suspected cocaine in assault and attempted robbery case; (2) Defendant waived variance issue with habitual felon indictment.
State v. Cobb, __ N.C. App. __, __ S.E.2d __ (June 16, 2020)
An officer initiated a voluntary encounter with the defendant sitting in the driver’s seat of a parked car. The officer detected a marijuana odor, and the defendant admitted he was smoking a blunt and handed it to the officer. Once backup arrived, the officer asked the defendant to step out of the car and searched him incident to arrest. Upon discovering a “wad of money” totaling thousands of dollars and asking defendant about it, the defendant fled on foot. During the resulting pursuit and takedown, the defendant attempted to take the officer’s firearm and also placed a bag of white powder in his mouth. Believing the defendant was destroying evidence and putting himself at risk, the officer forcibly removed the bag from the defendant’s mouth. The defendant resisted and bit the officer’s finger hard enough to break the skin. The powder later field-tested positive for cocaine. At the defendant’s subsequent trial for assault inflicting serious injury on an officer and attempted common law robbery, testimony about the bag of white powder and the positive field test was admitted. The defendant was convicted of lesser charges, and pleaded guilty to attaining habitual felon status.
The appellate court held that admission of evidence about the field test result was error. The test result was irrelevant since the test was conducted after the assault and attempted robbery were over, and defendant was not charged with any controlled substance offenses. Testimony about the officer’s belief that the powder was cocaine was relevant to explain why the officer believed it was necessary to remove the bag from the defendant’s mouth, but the confirmatory test had no relevance to establishing any of the elements of the charged offenses. However, the error was not prejudicial in light of all the other evidence of defendant’s guilt as to the charged offenses.
Defendant’s remaining argument, alleging a fatal variance in the habitual felon indictment, was waived since the defendant pleaded guilty. The error, which incorrectly listed one of the defendant’s convictions as occurring in superior court rather than district court, did not constitute an exceptional circumstance that warranted allowing discretionary review under Rule 2.
The state presented sufficient evidence of first-degree kidnapping based upon the defendant terrorizing the victim and also presented sufficient evidence of misdemeanor assault with a deadly weapon.
State v. English, ___ N.C. App. ___, ___ S.E.2d ___ (June 16, 2020)
In this case involving convictions for first-degree kidnapping and misdemeanor assault with a deadly weapon, among other offenses, the state presented sufficient evidence of the offenses and the trial court did not err by denying the defendant’s motion to dismiss on that basis. With regard to the kidnapping conviction, the defendant argued that the state failed to present substantial evidence the defendant’s purpose was to terrorize the victim. Recounting evidence that the defendant hid in the backseat of the victim’s car holding a knife while he waited for her to get off work, forced her to remain in the car and drive by choking her and threatening her with the knife, and forcefully struck her on the head when she attempted to scream for help, the court rejected this argument and bolstered its position by describing her frantic efforts to escape.
The court also found sufficient evidence of misdemeanor assault with a deadly weapon under both the show of violence theory of assault and the act or attempt to do injury to another theory of assault. The State’s evidence tended to show that after two men scuffled with the defendant in an attempt to aid the victim, the defendant jumped into the driver’s seat of the victim’s car and attempted to run the men over and nearly did so. This was sufficient evidence of assault under either theory.
Court order for historical cell-site location information was equivalent to a search warrant, so the defendant’s rights under the state constitution were not violated by an unreasonable search and seizure; good faith exception applied to defendant’s rights under the federal constitution.
State v. Gore, __ N.C. App. __, __ S.E.2d __ (June 16, 2020)
The defendant in this case pleaded guilty to manslaughter and armed robbery, while preserving his right to appeal the denial of his motion to suppress historical cell site location information (“CSLI”) that the state obtained without a search warrant. Evidence at the suppression hearing showed that police responded to a homicide and learned that a white Altima was seen leaving the scene. Officers soon located and boxed in the car but the driver fled on foot, discarding a bloody handgun as he ran. Inside the car officers found drugs, a gun, and a blood-covered cell phone belonging to the defendant. Officers applied for a court order to obtain the records of the phone, including five days of CSLI from around the time of the homicide. The application was sworn under oath and supported by affidavit, and the order was issued based on a finding of probable cause. The phone records revealed the defendant was in the area of the shooting at the time it occurred, and near the location of the white Altima when it was abandoned. The defendant moved to suppress the records on the basis that they were not obtained pursuant to a search warrant based on probable cause, violating his state and federal constitutional rights. The trial court denied the motion, finding that the court order in this case was the equivalent of a search warrant supported by probable cause. Upon review, the Court of Appeals affirmed the trial court’s ruling.
The court first addressed defendant’s federal constitutional claim. Citing Carpenter v. United States, 201 L.Ed.2d 507 (2018), the appellate court agreed that obtaining historical CSLI constituted a search, which requires a warrant supported by probable cause. A court order issued pursuant to the Stored Communications Act (“SCA”) based only on “reasonable grounds” to believe the records would be “relevant and material” to the investigation would not satisfy that standard. However, the order in this case was obtained two years before Carpenter was decided, and it was issued in compliance with the law at that time. Therefore, as in Carpenter, “even assuming law enforcement did conduct a warrantless search in violation of defendant’s Fourth Amendment rights, the federal good faith exception to the exclusionary rule would apply.”
Turning to the state constitutional claim, and noting that the state right at issue must be interpreted at least as broadly as the federal right, the court held that “a warrantless search of historical CSLI constitutes an unreasonable search in violation of a defendant’s rights under the North Carolina Constitution as well.” But after reviewing the statutory requirements for a search warrant and the probable cause standard, the court concluded that the order in this case did satisfy the warrant requirement. First, although it was denominated a court order rather than a warrant, it nevertheless “contained all of the information required in a search warrant” such as the applicant’s name, sworn allegations of fact to support the applicant’s belief, and a request to produce the records. Second, although a court order issued under the SCA is only required to meet a “reasonable grounds” standard akin to reasonable suspicion, the order in this case was actually based upon a finding that there was “Probable Cause that the information sought is relevant and material to an ongoing criminal investigation, involving a First Degree Murder.” That finding of probable cause was “a significant distinction which compels a different outcome than that of Carpenter. Accordingly, because the trial court determined there was probable cause to search defendant’s historical CSLI, the requirements for a warrant were met and defendant’s constitutional rights were not violated.” Since it held that the warrant requirement was met, the majority declined to address whether a good faith exception could have applied under state law.
In a partial concurrence, Judge Dillon disagreed with the majority’s holding that the court order in this case was the equivalent of a search warrant. In his view, the application failed to provide a sufficient basis for finding probable cause to believe that evidence of a crime would be discovered in the particular place to be searched. However, he concurred in the result on the grounds that both the federal and state constitutional claims were refuted by the good faith exception. He would have held that North Carolina does have a good faith exception, pursuant to the 2011 amendment to G.S. 15A-974, which provides legislative authority for the exception that was lacking when State v. Carter, 322 N.C. 709 (1988) was decided. Alternatively, pursuant to state case law, he would have held that obtaining historical CSLI did not constitute a “search” for state constitutional purposes.
Defendant’s waiver of his right to a jury trial was sufficient and defendant suffered no prejudice, despite trial court’s failure to fully comply with statutory procedures for taking waiver.
State v. Hamer, __ N.C. App. __, __ S.E.2d __ (June 16, 2020)
The defendant was convicted in district court of a Class III misdemeanor for speeding 94 mph in a 65 mph zone. The defendant filed a pro se appeal for trial de novo in superior court, which the trial court treated as a petition for writ of certiorari and allowed. It was “unclear how Defendant first provided notice of his intent to waive his right to a jury trial” in superior court, as required by G.S. 15A-1201(c), but it was “evident […] that all parties were aware of Defendant’s intent, as this was the initial matter raised before trial.” The trial judge confirmed that the defendant wished to waive his right to a jury trial, with no objection by the state, and a bench trial commenced. After the state rested, the trial judge noted that he was also statutorily required to personally address the defendant and confirm that he understands his right to a jury trial and wishes to waive it, in accordance with G.S. 15A-1201(d). The judge engaged in a brief colloquy with the defendant, who stated he understood and consented. The trial then resumed, and the defendant was convicted of the misdemeanor offense.
On appeal, defendant argued that he was prejudiced by the trial court’s failure to fully comply with G.S. 15A-1201, the statute implementing the constitutional amendment that allows a defendant to waive the right to a jury trial. In particular, the trial court failed to comply with subsection (d), which requires the judge to personally address the defendant about the waiver, determine whether the state objects, and consider all arguments of the parties before trial commences. The appellate court agreed that the trial judge erred regarding this portion of the statute, but ultimately held that the subsequent colloquy with the defendant, “although untimely,” still “satisfied the procedural requirements of subsection (d)(1).” Additionally, the defendant failed to show any prejudice resulting from the error. Considering the strong evidence against the defendant, the defendant did not establish a reasonable possibility that a different result would have been reached without the error. Therefore, the trial court’s judgment was affirmed.
Chief Judge McGee dissented, noting the importance of establishing precedent for jury trial waivers in future cases. She would have held that “the relevant requirements set forth in N.C.G.S. § 15A-1201 (2019) are incorporated into the constitutional mandates of N.C. Const. art. I, § 24” and “[n]othing in art. I, § 24 suggests any of the material requirements included may be waived or that violations may be subjected to regular harmless error review.” The violation of the defendant’s constitutional right to a jury trial was structural error, and the conviction should therefore be reversed.
Imposition of lifetime SBM was an unreasonable warrantless search in violation of the Fourth Amendment.
State v. Hutchins, ___ N.C. App. ___, ___ S.E.2d ___ (June 16, 2020)
In this rape and sex offense case, the Court of Appeals reversed the trial court’s order imposing lifetime SBM. First addressing its appellate jurisdiction, the court explained that it allowed the defendant’s petition for writ of certiorari in its discretion, notwithstanding procedural defects in his notice of appeal, because of the “meritorious nature” of the defendant’s argument regarding SBM and the current “tumultuous” state of the law. Before turning to the merits of the SBM issue, the court also dismissed a portion of the defendant’s appeal having to do with attorney’s fees because an order for those fees had not been entered as a civil judgment.
As the defendant was not a recidivist and, consequently, the order requiring lifetime SBM was not facially unconstitutional under State v. Grady, 259 N.C. App. 664 (2018) (“Grady III”), the court conducted a reasonableness analysis guided by the principles of Grady III, namely that it is the State’s burden to show that under the totality of the circumstances lifetime SBM is reasonable because its intrusion upon Fourth Amendment interests is balanced by its promotion of legitimate government interests. As to the intrusion side of the analysis, the court likened this case to State v. Gordon, ___ N.C. App. ___, 840 S.E.2d 907 (2020) where it explained that the State’s ability to show the reasonableness of lifetime SBM is hampered in situations where it is imposed at sentencing but will not be implemented upon the defendant until he or she is released after a lengthy prison sentence. The court also noted the deeply intrusive nature of the ET-1 monitoring device at issue and the fact that the defendant’s privacy interests will be less diminished following his completion of PRS. As to the State’s interest in SBM and its efficacy, the court rejected the State’s argument that SBM would discourage recidivism, saying that the state had not presented evidence to support that assertion, either generally or with respect to the defendant specifically. The court also rejected the State’s argument that lifetime SBM would serve the purpose of keeping the defendant out of “exclusion zones,” noting that his status as a registered sex offender already barred him from many such zones and that his offense involved an adult roommate. For a lack of evidence, the court also rejected the argument that lifetime SBM would ensure that he abided by an order to have no contact with the victim. Under the totality of the circumstances, the state did not show that lifetime SBM was a reasonable warrantless search in this case.
The trial court did not err by denying the defendant’s motion for a continuance to review rebuttal evidence that the state announced its intention to use on the day before trial.
State v. Johnson, ___ N.C. App. ___, ___ S.E.2d ___ (June 16, 2020)
In this felony murder and armed robbery case, the trial court did not err by denying the defendant’s motion for a continuance to allow time to review evidence that the state intended to introduce to rebut the defendant’s expert testimony that he acted with diminished capacity, or in the alternative to not allow the state to introduce that rebuttal evidence. The defendant made this motion on the first day of trial, one day after being informed of the state’s intent to use the rebuttal evidence, which consisted of jailhouse call recordings made around the time that he first met with his expert and which the state contended showed that he did not display signs of diminished capacity.
The defendant was sentenced to life imprisonment for felony murder based on the jury’s finding that his killing of a store clerk was associated with the defendant’s commission of the felony of assault with a firearm on a law enforcement officer as the defendant left the scene of the crime. Citing precedent establishing that diminished capacity is not a defense to a felony murder conviction based on that underlying general intent felony, the court found that any error by the trial court in denying the continuance was non-prejudicial as the expert testimony was not relevant to that conviction.
The jury also convicted the defendant of armed robbery and the trial court sentenced him to a term of imprisonment to run consecutively to his life sentence for felony murder. Because armed robbery is a specific intent crime, the expert testimony on diminished capacity was relevant to the armed robbery conviction. The State’s jailhouse recording rebuttal evidence went to the issue of the defendant’s mental ability around the time he met with his expert and generally showed that he was capable of making plans and adding up money. Reviewing whether the denial of the motion deprived the defendant of his constitutional right to present a defense, the court noted that defense counsel knew of the existence of the recordings for “quite a while” before trial but did not request them and, largely because the recordings did not contradict the expert’s testimony, determined that the defendant was not prejudiced by the denial of his motion for a continuance.
Judge Stroud dissented, expressing the view that the trial court’s denial of the continuance erroneously denied the defendant his right to effective assistance of counsel because of defense counsel’s inability due to time constraints to review the jailhouse call recordings or prepare for their use at trial. In Judge Stroud’s view, because the trial court’s error amounted to a violation of the defendant’s constitutional rights, it was presumptively prejudicial unless the state showed it was harmless beyond a reasonable doubt, a burden that the state did not meet.
The trial court’s order setting aside a bond forfeiture failed to identify a permissible ground for the set aside.
State v. Smith, ___ N.C. App. ___, ___ S.E.2d ___ (June 16, 2020)
Because the trial court’s order setting aside a bond forfeiture failed to make material findings of fact, conclusions of law, or any ruling as to whether a bail agent’s motion to set aside the forfeiture should be considered and set aside under G.S. 15A-544.5(b)(7), rather than under subsection (b)(6), the court vacated the order and remanded for entry of a new order addressing this issue. On 31 October 2018 the defendant failed to appear in Cumberland County Superior Court on two criminal charges. It was undisputed that the defendant was in federal custody in Virginia on that date. After a Bond Forfeiture Notice was issued, the bail agent filed a motion to set aside the forfeiture and checked Box 6 on AOC-CR-213, which corresponds to G.S. 15A-544.5(b)(6), indicating that the basis for the motion was that the defendant was incarcerated within the borders of North Carolina. As developed at a hearing on the motion, it appeared that the bail agent meant to check Box 7 of AOC-CR-213, which corresponds to G.S. 15A-544.5(b)(7) (generally providing as a basis for a motion to set aside that the defendant was incarcerated anywhere within the borders of the United States). It also appeared that the trial court may have intended to treat the motion as one under subsection (b)(7) and to grant relief under that subsection. The order drafted by the school board’s attorney and signed by the trial court did not reflect this apparent intent. As entered, the order failed to identify a permissible ground for setting aside the bond forfeiture under G.S. 15A-544.5(b) and the court vacated the order for that reason and remanded for additional findings and a determination on the subsection (b)(7) issue.
(1) There was insufficient evidence that an air pistol and a pellet rifle were dangerous weapons for purposes of attempted armed robbery; (2) Any impermissible expression of opinion by the trial court did not prejudice the defendant; (3) The trial court erred by accepting the defendant’s stipulation to attaining habitual felon status without conducting a colloquy.
State v. Williamson, ___ N.C. App. ___, ___ S.E.2d ___ (June 16, 2020)
In this robbery case where the defendant was punished as a habitual felon, (1) the defendant failed to preserve a fatal variance argument; (2) there was insufficient evidence of attempted armed robbery; (3) assuming without deciding that the trial court expressed its opinion in violation of G.S. 15A-1222, the defendant was not prejudiced; and (4) the trial court erred by accepting the defendant’s stipulation to having attained habitual felon status.
Noting that a defendant must specifically state at trial that a fatal variance is the basis for a motion to dismiss in order to preserve that argument for appellate review, the court found that the defendant waived his variance argument by basing his motion to dismiss solely on insufficiency of the evidence.
With regard to insufficiency of the evidence of attempted armed robbery, the defendant argued that there was insufficient evidence of the use of a dangerous weapon. The defendant had threatened an associate with a pistol and rifle that appeared to be firearms but turned out to be an air pistol and a pellet rifle. Reviewing the rules from State v. Allen, 317 N.C. 119 (1986) and related cases about sufficiency of the evidence in situations involving instruments that appear to be but may not in fact be dangerous weapons, the court said that because the evidence was conclusive that the pistol and rifle were not firearms, the state was required to introduce evidence of the weapons’ “capability to inflict death or great bodily injury” to merit submission of the attempted armed robbery charge to the jury. As no such evidence was introduced, the trial court erred in denying the defendant’s motion to dismiss for insufficient evidence.
During the testimony of a defense witness, the trial court interjected to admonish the witness not to refer to the pistol and rifle as “airsoft” weapons because, in the trial court’s view, that terminology was not an accurate description of the items. Assuming without deciding that this admonishment was an improper expression of opinion and accepting for argument that it may have negatively impacted the jury’s view of the witness’s testimony, there was not a reasonable probability that the jury would have reached a different verdict absent the admonishment.
Finally, the state conceded and the court agreed that the trial court erred by accepting the defendant’s stipulation to having attained habitual felon status without conducting the required guilty plea colloquy.
The post Case Summaries – North Carolina Court of Appeals (June 16, 2020) appeared first on North Carolina Criminal Law.
Case Summaries – North Carolina Court of Appeals (June 16, 2020) published first on https://immigrationlawyerto.tumblr.com/
0 notes