#opera mail backup tool
Explore tagged Tumblr posts
Text
EdbMails MBOX to PST converter
EdbMails MBOX to PST converter is a convenient tool to convert MBOX data to Outlook PST and save it to EML, HTML & MHT formats. It includes plenty of advanced features, which can help you to view all emails along with attachments and export to Outlook PST.
Features:
Load the MBOX file and preview messages along with corresponding attachments Export the all the mail items to the Outlook PST Allows to export selective MBOX items to PST using various filters Supports to save the all the mail items in EML, HTML, and MHT formats Compatible with all the latest versions of Windows OS and Outlook
Overall, EdbMails MBOX to PST is an efficient email extractor tool. It supports mailboxes of over 30 email clients including Mozilla Thunderbird, Apple Mail, PocoMail, SeaMonkey, Eudora, Opera Mail, Entourage database, and Gmail takeout backup etc. The application is easy to use and has a simple interface. Users with all levels of knowledge can navigate it with ease.
1 note
·
View note
Text
A Step-by-Step Guide to Getting a Free Tool for Your Yahoo Mail Password Recovery
When You Have Google Why Yahoo?
Before we begin if you have searched for Step by Step Guide to Getting a Free Tool for Your Yahoo Mail Password Recovery Tool Free Download, you are at the right place. Various tools promise to recover your password. But only a few of them work and on which most are paid.
Today we have got two methods for you to recover your lost password for Yahoo mail. Both work and free. According to a survey, Google is the second-most popular email provider website in the US. Many users who had accounts with Yahoo at the time and used them on different platforms later switched to Google.
The issue arises if you need to log into your Yahoo account but have forgotten your password. If you have chosen a backup account or phone number in your Yahoo account, this problem won’t be a big deal. Just follow a few easy steps to recover your password.
But an unfortunate truth is that, despite Yahoo offering several services like yahoo mail, yahoo search, yahoo online mapping, yahoo advertisement, yahoo news, social media, yahoo groups, and, fantasy sports. People still prefer Google over Yahoo. According to Yahoo, their business satisfies the needs of half a billion customers each month in thirty languages.
Even though Yahoo uses web crawlers to monitor its features and places a strong emphasis on H1 tags, keyword density, on-page optimization, and many other factors, people have shifted to Google because it is simply more convenient and many businesses already use Google’s other products. Now that we’ve covered Yahoo, let’s talk about Yahoo Mail Password Recovery Software Online, software.
What Should be Done?
Access to your email account is required for several reasons, including when you’ve had it for a while and you have registered it for certain services as well, but when you forget your password and are unable to retrieve it because you don’t have a backup email address or phone number associated with it. But with the aid of the online Yahoo Mail Password Recovery Software, you were able to recover it.

To learn more, read on. It becomes a hectic and stressful situation, so what should you do? If you’re tired of searching for it and continue getting the same results about recovering passwords from backup email addresses to phone numbers, don’t give up hope! With such miraculous software that can recover your yahoo mail password, we’ve got you covered.
Classic Way to Recover Yahoo Mail Password Recovery Tool Free DownloadIt’s a simple and easy method which is the official Yahoo password recovery tool.
Click here (sign-in-helper)
You need to enter any of the account recovery listed here.
Then click on continue.
Then follow the simple steps provided on the sign-in-helper
For desktop or mobile web browsers follow the steps provided below;
First, you need to sign in Yahoo account security page, click here.
Then click on change password.
You may enter a new password now.
Then click on continue.
If You Want to Recover it by Using Yahoo Mobile App.
Choose the menu icon
Then go to manage the account if using Yahoo mobile apps
Go to account information
Then choose security settings and then enter the security codes which you provided at the time of signing up.
Then click on change password.
Choose, ‘ i would rather change my password.’
Then enter a new password, re-enter it and then select continue.
For these methods, you need to have the details being asked on the recovery page. If you don’t have then read below for other methods.
About the Recovery Tool for Yahoo Password?
Important note; The Yahoo password decryptor is only able to recover passwords that have been previously saved in web messengers or web browsers; it is not going to crack or hack the password.
The tool can retrieve passwords that have been saved in the software mentioned below;
1. Firefox
2. Apple Safari
3. Microsoft Edge
4. Google Chrome
5. SXS/Chrome Canary
6. Opera
7. Internet Explorer
8. UC Browser
9. Miranda Messenger
10. PaltalkScene IM
11. Comodo dragon browser
12. Pidgin Messenger
13. Yahoo Messenger
14. CoolNovo
15. Flock Browser
Any operating system can install the tool, and it functions without a problem. The “Yahoo password decryptor” is compatible with a wide range of operating systems, including Windows XP and Windows 10.
How do Install the Tool or Uninstall it
The software for recovering your Yahoo mail password has an installer, so you can use it right away after setting it up on your computer. It has a setup wizard that leads you through the setup process.
You can uninstall the product whenever you want by going to these locations and using the uninstaller;
Benefits of Yahoo Password Recovery Software
1. Decrypt your password as soon as possible.
2. It is simple to use thanks to the improved GUI interface.
3. The program is available in both GUI and Command Line versions.
4. Save the password list you recovered as an HTML, XML, text, or CSV file.
5. Web browsers and messengers are supported by the software.
6. All stored passwords can be recovered using the online Yahoo mail password finder.
Free Download Yahoo Mail Password Recovery Software
Click here to download the software. Please take note that this is not software for hacking. Security Xploaded does not accept liability for any harm caused by the software and can only retrieve the saved passwords from the web browser.
Yahoo Mail Password Recovery Software Steps to Use?
The Yahoo Password Decrypt or software is simple to use;
1. Go to Yahoo Password Decrypt or on your computer and start it.
2. All stored and saved passwords will be recovered and displayed once you click the “start recovery button.”
3. By selecting the Report button, you can now save all recovered password lists to HTML, Text, XML, or CSV.
4. Select the type of file by choosing “save file dialogue” from the menu.
Recovering Yahoo Email Password Using Method Number Second?
When logging into your Yahoo account, you must have used Google Chrome or Firefox and chosen automatically to log in. This is the only requirement, and if you met it, you are good to go. Now, users of both browsers have the option of checking saved passwords. Consider Chrome as an example; Firefox follows the same steps.
1. Go to Chrome’s settings by typing “chrome:/settings”
2. What you want is “Show advanced setting.” click on it.
3. Select “manage saved passwords” after scrolling to the “passwords and forms” section.
4. You only need to select your Yahoo mail account and select “show” in the password tab to see all the previous accounts you have saved passwords for in Chrome.
5. Now that you have your password showing up, copy it and change your password by going to Yahoo.
Ways to Remember Your Password
This isn’t techy at all! But if unfortunately, you couldn’t recover by any of the methods you can try to remember it. Something is better than nothing.
In today’s world, forgetting a password for a computer or an online account can have disastrous results. Unfortunately, most people experience it at some point. With so much going on every day, it’s simple to forget a password, especially if you’re managing several of them across a variety of accounts.
Even the account provider is typically not aware of that kind of information, so it isn’t much you can do to recover a forgotten password. But before you write it off, give your password some serious thought. Doing so might be enough to fully restore your account access and memory.
Method Number 1
It is usually a good idea to try out other personal passwords you typically use frequently, working under the premise that people forget their passwords one at a time. Although it’s now standard for web users to use different passwords for various services, some passwords are frequently used across several services.
1.If you’re unsure, it’s entirely possible that you simply forgot that a particular password matched a particular account rather than forgetting a password. You might be entering this password which belongs to a different account.
2.If the account you’re trying to access is fairly old, don’t forget to try out old or outdated passwords as well.
Method Number 2
People frequently draw ideas for their passwords from their daily lives and their surroundings. If you know roughly when the account and password were establish, try to reflect on that period and identify any significant events that might have influenced your choice of password. At the time, did you have a significant thing or a pet? If you want to remember something specific, like a password, taking some time to think back on your past should be beneficial.
Other examples include the name of your closest friend, your favorite sports team, or your hometown. Trying to remember while under stress will have the opposite effect of what you intend. Remember to relax, breathe, and remind yourself that nothing is the end of the world because the human brain finds it much more difficult to recall information when it is under pressure.
This was it, Hope You Manage to Get it Recover.
Visit us More Links: Netflix Password Recovery Online Free
0 notes
Text
Opera mail hide images reply

#OPERA MAIL HIDE IMAGES REPLY PDF#
#OPERA MAIL HIDE IMAGES REPLY SOFTWARE#
Is it possible to extract attachments separately?.
Yes, by using the software, you can easily download corrupted and crashed files.
Will I be able to create a backup of corrupted and crashed files?.
Yes, you can make backup of opera mail completely by using the methods given above.
Can I download Opera Mail data completely?.
#OPERA MAIL HIDE IMAGES REPLY PDF#
Hence, by exporting Opera Mail files as a backup into PDF format, it becomes easy for you to transfer the data. Go to the resultant location and see the exported data. You need to remember that the Demo version will only migrate 10 emails at once. You will be able to see the live process on the screen.Īnd finally, receive notification of complete conversion on the screen. Select the emails or files from the data displayed on the screen.Ĭlick on the Export Menu and select “PDF” as the file format.Įnter the desired location and save that.
#OPERA MAIL HIDE IMAGES REPLY SOFTWARE#
Open the Open Menu in the software panel and click on the Desktop Email Clients and Choose Opera Mail Accounts.Ĭhoose files/folders from there and the software will automatically scan the data on the system. Launch the Software on your Windows OS system. Users not only make a single file backup but can easily make a backup of multiple emails within a single operation. On the Other side, if we talk about another professional utility then we recommend you to use the Email Conversion Tool which allows users to create and download backup, of opera mail emails. Professional Solution to Take Backup of Opera Mail There, you will be able to see the location of directories.Ĭopy the Mail Directory location from there.Īfter that, go to the Windows’s Explorer Address Bar and paste the location there.Īnd then, user can easily copy the mail folder from there to create a backup of opera mail.Ģ. Go to Help > Choose “login to Opera Mail”. Go to the Opera Mail email client Application and click on the Opera mail icon on the left hand side. Therefore, it is not a proper solution for you. Limitation:The software will provide you the mail folder of Opera mail but there are many files are present in the folder which we humans cannot be able to read and understand as they will be in binary language. So, let’s understand how can we download opera mail emails as a backup and use that. Since Opera Mail is a desktop email client application then it is sure that the database or backup of Entire Emails is automatically stored in the system. Manual Solution To Save Opera Mail Emails

0 notes
Text
Ccleaner for mac 10.9.4

#Ccleaner for mac 10.9.4 for mac
#Ccleaner for mac 10.9.4 manual
#Ccleaner for mac 10.9.4 software
Upon launching, you need to scan the disk with this Mac cleaning software. Free email signature creator for apple mail. CleanMyMac 3: CleanMyMac 3 is a later version of CleanMyMac app, developed by MacPaw. Users can click on each section and preview all files in each folder, prior to deleting them. It can't be any easier to create flyers, brochures, business cards, newsletters, adverts. Publisher Plus is a powerful desktop publishing and page layout app for both business and home use.
#Ccleaner for mac 10.9.4 for mac
It scans the disk to figure out its usage and shows it up in treemap format which is also indicated with different colors.ĭesktop publishing for mac 2015.
#Ccleaner for mac 10.9.4 software
Disk Inventory X: This is another disk cleaning software for Mac. Further, the app come up with files that are occupying this space and you can delete these files from there. It also gives you a clear disk usage figures when clicked on specific colors. Upon launching, the app asks you to select a disk and scans it. DaisyDisk: Developed by Software Ambience Corp., DaisyDisk is an app that shows up scanning results in pie chart. The app is rated with 4.5 stars on Apple App Store by happy users.
#Ccleaner for mac 10.9.4 manual
Likewise, it also has scanning options for optimization, and specific manual cleaning. Let’s say, its One Click Cleaning ensures that all cache, unwanted log, trash files and unfinished downloads are removed in a click. With its various scanning alternatives, you can scan your Mac for specific files. It lets users clean out clutter on their Mac in a jiffy. 10 Best Mac Cleaner and Optimizer 1.ĭisk Clean Pro: This is the best Mac cleaning software. These are the best mac cleaning software that will allow you to remove all unwanted apps and files in no time. Worry not, we have listed top 10 Mac optimization apps for your help. If there’s anything you can blame it on, then its duplicates, cache files, unused apps and many more files like this. The entire disk space is taken away by the apps you have installed, the files you have stored and of course its OS also has a share of it. Data backup features helps to avoid losing important data.Helps you to identify and removes unused programs running in background.Cleanes website cookies and browsing history.System Crashes & System Errors report.Easy to use and a small, fast download.Finally, the program can remove temporary documents many applications, such as eMule, Kazaa, Google Toolbar, Office, Nero, Adobe Reader, WinRAR, etc. The application deletes temporary files, history of sites visited, cookies, forms, etc.ĬCleaner supports Google Chrome,Internet Explorer, Opera and Mozilla Firefox,Safari, Windows Media Player,Netscape, Microsoft Office. To free up space and improve loading Windows.ĬCleaner is also able to erase all traces of your web browsing within seconds. It protects your privacy online and makes your computer faster and more secure.CCleaner is designed to optimize and to cleanse your system.The software removes unused files from your hard drives, shortcuts without a target, ActiveX controls, help files, registry entries, etc. Now Mac users.ĬCleaner is a tool for cleaning your Windows PC. One of the favorite tools used by Windows users is beyond any doubt CCleaner. Download CCleaner free for Mac and optimize its performance eliminating unnecessary files from browsers and programs. 8/10 (7 votes) - Download CCleaner Mac Free.

0 notes
Text
Set opera mail as default mail client windows 7

#Set opera mail as default mail client windows 7 how to
#Set opera mail as default mail client windows 7 software
#Set opera mail as default mail client windows 7 trial
#Set opera mail as default mail client windows 7 download
Or in Browser Go to Opera > Help > About Opera
Run Opera Mail, choose Opera Mail option & then from Help > About Opera Mail.
First of All, Backup & Export all Opera Mailbox Items.
Just follow these simple steps to accomplish the Opera MBS to PST conversion: However, the utility also provides Outlook Mode to perform fast & secure conversion. There is no need for Outlook installation for the working of this software. How to Export Opera Mail to Outlook PST Format ?
#Set opera mail as default mail client windows 7 software
For more, you need to purchase the software key for lifetime use.
#Set opera mail as default mail client windows 7 trial
The trial version of this application only extracts 25 emails from the Opera Mail client. As any non-technical user can accomplish the transfer of Opera Mail emails to PST data file easily. Note: The working of this amazing toolkit is very easy & simplified.
#Set opera mail as default mail client windows 7 download
The best part of this application is available for all editions of Microsoft Windows and Server machines.įree Download Opera Mail to PST Converter Tool: A large number of users wants to convert Opera Mail emails, contacts, calendars to PST file. It will create a UNICODE PST file which is supported on all latest versions & editions of Microsoft Outlook. One such amazing software is the RecoveryTools MBOX Migrator tool which enables the users to export Opera Mail MBS to PST file. This can be done with the help of a powerful Opera Mail to PST Converter software. Smart Solution – Export Opera Mail to PST File Once the outlook address is set up on Opera the existing emails download however, I can’t seem to send or receive emails? I’ve entered the IMAP Protocols for email but to no avail.Ĭan anyone help me to transfer Opera Mail MBS file to PST File? Thank you in advance! However, I’m getting stuck on sending emails and receiving. I really like the interface of Outlook over Opera Mail. Everything works, but it’s amazingly annoying when then thing is throwing errors at me anyway. I’ve set everything up to use outlook mail servers, I told it “Disable QRESYC=1” and “Force Single Connections=1”, and they’re sending mail to and receiving mail from the accounts correctly, but every minute or so I get a little yellow hazard icon, before it goes away again. I’m still getting little yellow hazard symbols next to my email accounts. They regularly ask about Opera Mail Converter on various forum platforms like listed below: Reasons to Export Opera Mail to PST FormatĪ large number of users are looking for a way to convert Opera Mail to PST file. To migrate Opera Mail to PST File it is very important for a user to convert MBS to PST file. Opera Mail stores all the mailbox data in MBS file & on the contrary Opera Mail as MBS file on Hard Drive. Hence a large number of users are looking for a way to export Opera Mail to PST file for Outlook client. The best part of Outlook comes with a complete package including Word, PowerPoint, Excel, and more productivity tools. It provides various business tools which increase the work productivity & efficiency of an organization. As a combined application it has a long list of features containing management of POP3 & IMAP accounts, contact management, atom & RSS feed, as well as Spam filtering, etc.īut there is no doubt that Outlook as a part of Microsoft Office Suite proves to be very powerful among the users. It supports News & Email Clients enables the users to unify and integrate Opera Browser. Opera Mail is a very powerful & useful email client application that is a part of an Opera Internet Suite. So, if you want to extract Opera mail mailboxes, then read this article for more information. In this article, we get to know about how can a user export Opera Mail to PST file.
#Set opera mail as default mail client windows 7 how to
Overview: Are you want to know how to export Opera Mail to PST File ? Or want to import Opera Mail to Outlook Email client ? If so, then you searching end’s here. Modified: 23-03-2022 ~ Opera Mail ~ 7 Minutes Reading

0 notes
Text
Receive mail convert to email

#Receive mail convert to email how to
#Receive mail convert to email mac os
This video lesson is from our complete Outlook for lawyers tutorial, titled “ Mastering Outlook Made Easy for Lawyers v.2019 and 365. Use the drop-down menu under 'Do the following' to select 'Redirect the messages to'. Select Redirect the message to under 'Do the following'. Click on the email message you wish to download. Use the drop-down menu below 'When messages arrive' to select 'Apply to all messages'.
#Receive mail convert to email how to
The following video lesson, titled “ Turning Emails into Tasks,” shows you how to convert an email you receive into a task in Outlook. How to export emails as a (.eml) file Apple Mail Open Apple Mail. Video Lesson on How to Create a Task from an Email in Outlook
To save the new task after editing it, click the “Save & Close” button in the Ribbon of the “Task” window.
In the task window, you can then set associated task information, like a reminder date, due date, or task category.
It then displays the content within a task window.
When you release the mouse button, Outlook converts the email into a task.
To turn emails into tasks in Outlook, click and drag the desired email onto your “Tasks” folder within the Folder Pane or Navigation Bar.
Instructions on How to Turn Emails into Tasks in Outlook Be anonymous, secure and safe with our disposable email address. By using temporary email address you will be safe of spam, hacking, robots attacking, and advertising emails. No captchas, No signups required for getting Temp Mail. After creating the task, click the “Save & Close” button in the Ribbon of the “Task” window to save it.Ī picture showing how to turn emails into tasks by clicking and dragging an email onto the “Tasks” folder in Outlook. You can use that email online for signups on major websites social media, forum etc. In the task window, you can then set associated task information, like a reminder date, due date, or task category. Its easy for anyone to get into, and the program works as. It then displays the content within a task window. Aryson Opera Mail Backup Tool is a solution to consider if youre looking to convert, migrate, or back up your emails from Opera Mail. When you release the mouse button, Outlook converts the email into a task. Exporting email to Text with the MessageExport Add-in for Outlook. To turn emails into tasks in Outlook, click and drag the desired email onto your “Tasks” folder within the Folder Pane or Navigation Bar. The selected emails are converted into a single text file. Note: You can only move messages, not folders or labels from your other. After the email is converted into a task, you can then set a reminder date, as well as other task information. You can import both old and new messages from another email account. You will also keep any phone numbers or other information the email contains within the new task. When you turn an email you receive into a task in Outlook, you keep the text of the email. You can easily turn emails into tasks in Outlook. Overview of How to Turn Emails into Tasks in Outlook
#Receive mail convert to email mac os
Mac OS Monterey-Mojave Keyboard Shortcuts.

0 notes
Text
Ico microsoft edge download

Ico microsoft edge download software#
Ico microsoft edge download code#
Ico microsoft edge download Offline#
Ico microsoft edge download tv#
Ico microsoft edge freeload#
Make sure you set the security correctly such that you webserver has access to that file. Copy your icon to that place and give it the the name that link is pointing to (you might want to backup the old file). There you will find the directory and the name of the icon file.
Ico microsoft edge download code#
To determine where your new favicon should be, examine and look for code that contains the text If this doesn't work you will need to delete the temporary internet files and the history and then open your page again.
Opera users may need to completely clear their cache in Tools→Preferences.
Konqueror: simply click the Reload button, or press F5.
IE: hold Ctrl while clicking Refresh, or press Ctrl-F5.
Mozilla / Firefox / Safari: hold down Shift while clicking Reload, or press Ctrl-Shift-R (Cmd-Shift-R on Apple Mac).
Even refreshing the page (F5) won't help.
Ico microsoft edge download tv#
An illustration of a heart shape Contact Jobs Volunteer People Search Metadata Search text contents Search TV news captions Search archived websites Advanced Search. Browsers are designed to minimize data traffic, so they don't refresh the favicon every time they show a page. An icon used to represent a menu that can be toggled by interacting with this icon. If not, that doesn't necessarily mean you did anything wrong. Do you see your new icon? If so, congratulations. Copy the file to the /joomla/templates/ directory and name it favicon.ico. The file you created in this way will have the extension.
Ico microsoft edge freeload#
Convert to ico format using free online sites such as:.Alternatively, you can also use an online tool such as
Ico microsoft edge download software#
You may use graphic software such as Photoshop, Gimp, or Windows Paint. To learn more about relationship-based ads, online behavioral advertising and our privacy practices, please review Bank of America Online Privacy Notice and our Online Privacy FAQs.Changing your website's favicon is a relatively easy task. These ads are based on your specific account relationships with us. In addition, financial advisors/Client Managers may continue to use information collected online to provide product and service information in accordance with account agreements.Īlso, if you opt out of online behavioral advertising, you may still see ads when you log in to your account, for example through Online Banking or MyMerrill. If you opt out, though, you may still receive generic advertising. If you prefer that we do not use this information, you may opt out of online behavioral advertising.
Ico microsoft edge download Offline#
This information may be used to deliver advertising on our Sites and offline (for example, by phone, email and direct mail) that's customized to meet specific interests you may have. Here's how it works: We gather information about your online activities, such as the searches you conduct on our Sites and the pages you visit. Relationship-based ads and online behavioral advertising help us do that. We strive to provide you with information about products and services you might find interesting and useful. Programs, rates, terms and conditions are subject to change without notice. Credit and collateral are subject to approval. and affiliated banks, Members FDIC and wholly owned subsidiaries of Bank of America Corporation. (MLLA) and/or Banc of America Insurance Services, Inc., both of which are licensed insurance agencies and wholly-owned subsidiaries of Bank of America Corporation.īanking, credit card, automobile loans, mortgage and home equity products are provided by Bank of America, N.A. Insurance Products are offered through Merrill Lynch Life Agency Inc. Both are indirect subsidiaries of Bank of America Corporation. Trust and fiduciary services are provided by Bank of America, N.A. MLPF&S makes available certain investment products sponsored, managed, distributed or provided by companies that are affiliates of Bank of America Corporation.īank of America Private Bank is a division of Bank of America, N.A., Member FDIC and a wholly owned subsidiary of Bank of America Corporation. Securities products are provided by Merrill Lynch, Pierce, Fenner & Smith Incorporated (also referred to as "MLPF&S", or "Merrill"), a registered broker-dealer, registered investment adviser, Member SIPC layer, and a wholly-owned subsidiary of Bank of America Corporation. You should review any planned financial transactions that may have tax or legal implications with your personal tax or legal advisor. Investing in securities involves risks, and there is always the potential of losing money when you invest in securities.

1 note
·
View note
Text
Top methods to Backup Opera Mail to a Local drive
Taking a backup of your emails saves your critical data from various uncertain events like malware attacks, corrupt files, accidental deletion. If you are looking for the best solution to Backup Opera Mail to a local drive, try Opera Mail Converter Tool. It takes backup of Mailbox items with ease. It also converts Opera Mail to various file formats. If you want to migrate Opera mail to other email clients, this utility can help you.
0 notes
Text
Ashampoo winoptimizer 14 serial key 無料ダウンロード.ashampoo winoptimizer 14 serial number
Ashampoo winoptimizer 14 serial key 無料ダウンロード.ashampoo serial

「WinOptimizer 15」の機能限定無償版。統計機能やミニツールなども備える.無料 ashampoo serial をダウンロード - Windows: ashampoo serial
無料版 ダウンロード. Ashampoo ® ZIP Free. Ashampoo ZIP Free は、 無料 の 圧縮・解凍 ソフトです。. 直感的 なユーザーインターフェイスとマルチコア対応の 高速処理 により、簡単かつ快適にファイルを圧縮・解凍することができます。. 無料版 Estimated Reading Time: 1 min · 無料 ashampoo winoptimizer 14 serial number のダウンロード ソフトウェア UpdateStar - Microsoft Windows なった可能性がありますより効果的な保守がこれまで以上の必要があります高度な。詳しいコンピューター システム定期的にしない時間をかけて収集デジタルごみ遅くなります、通常は、少なくとも必要な Ashampoo WinOptimizer 14 Serial Keys: AWPSNCB3E AWPSNA2D-B0DB60 AWPSNEFE8-BF4B0A Ashampoo WinOptimizer 14 Serial Key + Crack Full Free Download From Given Below. Ashampoo WinOptimizer 14 Serial Key + Crack Full Free Download Ashampoo WinOptimizer 14 Serial Key Crack is the ultimate system optimization tool, it offers various tools to
Ashampoo winoptimizer 14 serial key 無料ダウンロード.PCを高速化・最適化するツール「Ashampoo WinOptimizer Free」が無償公開 - 窓の杜
Direct and easy download of Ashampoo software and an overview of all Ashampoo products. Log in Backup Pro v WinOptimizer v · 無料 ashampoo winoptimizer 14 serial number のダウンロード ソフトウェア UpdateStar - Microsoft Windows なった可能性がありますより効果的な保守がこれまで以上の必要があります高度な。詳しいコンピューター システム定期的にしない時間をかけて収集デジタルごみ遅くなります、通常は、少なくとも必要な Sie haben sich ein Programm von Ashampoo gekauft und der Hinweis „Ihr Lizenzschlüssel bereits aktiviert“ erscheint bei der Eingabe Ihres Lizenzschlüssels. Dies passiert meistens nach einer Neuinstallation, dem Umzug auf einen anderen Rechner oder auch nach ggf.
Log in Existing account: Log in Your e-mail address: Your password: Recognize me automatically uses cookies Forgot password? Who is Ashampoo? Volume licenses Become a partner Press Center Jobs Contact About General Terms and Conditions Privacy Policy. title, location.
substr 1. Show only free programs. JavaScript is deactivated. Please enable JavaScript for a better viewing experience. os category language free filterQuery. filterIsDirty: resultsArray:. results found results found. AntiSpy for Windows 10 v1. Learn more. AnyDroid v7. AnyTrans v8. ActionCam v1. AntiSpy Pro v1. Audio Recorder Free v1. Backup v Backup Pro 12 v Backup Pro 14 v Backup Pro 15 v Backup Pro 16 v Burning Studio v1.
Burning Studio 21 v Burning Studio 22 v Burning Studio FREE v1. Cinemagraph v1. Connect v0. Core Tuner 2 v2. Disk-Space-Explorer v1. Driver Updater v1. Droid Commander v1. Droid Optimizer v4. Droid Screenshot v3. HDD Control 3 v3. Home Design 6 v6. Internet Accelerator 3 v3. Media Sync v1. Movie Studio Pro 3 v3. Music Studio v1. Music Studio 8 v8. Office 8 v Office Free v PDF Free v2. PDF Pro 2 v2.
PDF Pro 3 v3. Photo Commander 16 v Photo Commander FREE v Photo Converter 2 v2. Photo Mailer v1. Photo Optimizer v1. Photo Optimizer 7 v7. Photo Optimizer 8 v8. Photo Recovery v1. Registry Cleaner 2 v2. Slideshow Studio v1. Slideshow Studio HD 4 v4. Snap 10 v Snap 11 v Snap 12 v Soundstage v1. Soundstage Pro v1.
Taskbar Customizer v1. Ten Seconds v1. Undeleter v1. UnInstaller 10 v UnInstaller 11 v UnInstaller 9 v9. UnInstaller FREE v9. Video Converter v1. Video Deflicker v1. Video Filters and Exposure v1. Video Fisheye Removal v1. Video Optimizer Pro 2 v2.
Video Stabilization v1. Video Tilt-Shift v1. WebCam Guard v1. Windows 11 Compatibility Check v1. WinOptimizer 18 v WinOptimizer 19 v WinOptimizer v WinOptimizer FREE v ZIP v2. ZIP FREE v1. ZIP Pro 3 v3. HDR projects 7 v7.
NATURE projects v1. Opera Browser v PhotoZoom Classic 7 v7. Sticky Password Premium v8. Deals Who is Ashampoo? KG — All rights reserved!
0 notes
Text
Maemo For Mac

Memo For Management
Memo For Mac
Maemo For Mac Os
Maemo For Macbook Air
Memo For Microsoft Word
IMO for Mac pc: With the help of IMO for Mac we can able to stay connected with our friends, Imo families and relations no matter whatever may be the distance IMO for Mac pc is not just a social app by which we can send a message to the people worth to us. This is a TECHNOLOGY PREVIEW of a new development tool for Maemo. MADDE stands for Maemo Application Development and Debugging Environment and offers the following features: Command-line cross-compiling Multi-platform support (Linux (32-bit/64-bit), Windows, Mac OS X) Configurable for different targets & toolchains. Maemo Community e.V. Invitation to the General Assembly 01/2015 Nomination period closed for Q4 2014 council election Announcement of the Q4 2014 Community Council election. GPE is a suite of applications that was ported to Maemo. Search for GPE in the downloads section for your version of Maemo. (You'll probably want GPE Calendar, GPE Contacts, gpesyncd to start with.) These are standalone applications, there's no integration with the Maemo address book. You'll not find data from GPE in the Mail client or Chat.
Download
Thank you for using our software library. Use the link below and download Maemo Flasher legally from the developer's site.
We wish to warn you that since Maemo Flasher files are downloaded from an external source, FDM Lib bears no responsibility for the safety of such downloads. We recommend checking your downloads with an antivirus. FDM Lib shall include an option for direct download from developers, should it become available in the future.
Often downloaded with
Flash WallpaperCreate and distribute Flash Wallpapers! Flash Wallpaper converts a Flash...DOWNLOAD
Flash Media PlayerFlash Media Player is a handy flash tool kit designed as Macromedia flash...DOWNLOAD
Flash JoinerFlash Joiner provides a new way to create your SWF easily. You can merge...$39.95DOWNLOAD
Flash SecurerFlash Securer is program which will allow you to carry your sensitive documents...DOWNLOAD
Flash WiperMany people believe formatting the drive or deleting the file will complete...$19.95DOWNLOAD
iWisoft Flash SWF to Video Converter
Editors & Converters
The Nokia 770, N800 andN810are 'Internet Tablets'running Maemo: a handheld Linux distribution based on Debian.
Although there is acommand line flasher availablefor Mac OS X from Maemo, there's no officialGUI interface for it. This has been written usingPlatypus and CocoaDialog and is, of course,supplied with no warranty.
This is not affiliated with Nokia and so if your machine turns into amongoose and starts dancing ballet, don'tblame me. Or blame me, but don't complain - or, more importantly, sue.
Usage

Download the latestNokia image (large file ending in .bin, for exampleNokia_770_0.2005.45-8.bin) and either selectthis file when prompted by 770Flasher, or just drag the file on to the770Flasher icon.
Screenshot
770Flasher-2.0.dmg(Mac OS X disk image, 361K, requires 10.3 or above)
tablet-encode (aka 770-encode)
770-encode has now been renamed tablet-encodeand moved to a larger project called mediautils.
Due to the unreliability of garage.maemo.org, there is a mirror here:
mediaserv
mediaserv is a project which allows you to convert, on-the-fly,video from a Linux, Unix or Mac OS X box and watch it on your Nokia InternetTablet. It even integrates with VideoCenter.
Like tablet-encode, this is part of mediautils.
Due to the unreliability of garage.maemo.org, there is a mirror here:
mediaserv.tar.gz(Perl tarball, v0.05, 29K)
mud-builder
MUD is anauto-builder, designed to make it easier for people to port, in a simple andmaintainable fashion, software to Maemo; customising the resulting packages toMaemo's subtle requirements.
More info can be found on its Garage page.
Wikipedia
Wikipedia is anexcellent online resource and tied with a network connection through aNokia 770 is almost equivalent to the Hitchhiker's Guide to the Galaxy.Although not yet available offline for Maemo, it is possible to enhanceWikipedia to make it look better on the 770's screen.
The default skin contains a long left-hand column, however by creatingan account with Wikipedia (which is free), you can change the 'skin'to one more suited to a device such as the 770.
Default style
'MySkin' style
Usage
Create an account on Wikipedia.
Go to the URL, http://en.wikipedia.org/wiki/User:YourUserName/myskin.css.='detail'>
Paste the code below into the text area andclick Save:
/* <pre><nowiki>*/ @import url('http://www.bleb.org/software/maemo/wikipedia/myskin.css'); /* </nowiki></pre> */
Go to your Preferences page and selectthe Skin category.
Select MySkin and click Save.
Backgrounds
Under development
I've currently got the following under development. For each there is a short description and links to screenshots and photos. If you have any questions on them, please don't hesitate to contact me. Updates will be provided in my diary.
Better Maemo planet layout
I don't like the new MaemoPlanet that much. I've developed a user style for Firefox to turnit into this.
ArcEm
Acorn Archimedes emulator, allowing RISC OS to be run on an ARM device inyour pocket. [1], [2],[photo 1], [photo 2].
NetSurf
A lightweight open source web browser, for when Opera is deciding to betempremental. [1], [2], [3], [photo].
Galculator
A scientific calculator. No screenshots available, but a straight-forward port of a Glade application.
Java
Following on from Alexander Lash's work porting JamVM/Classpath/Jikesto Maemo, I've some thoughts on auto-Hildonisation of Javaapplications which could help make Java a suitable high-level language forMaemo application development.
Older stuff
Sylpheed
Sylpheed is a full-featured email client: supporting POP3,IMAP, SSL and everything else you'd expect. The full feature list can beseen at the Sylpheed homepage.
This is a port and Hildonisation of Sylpheed to integrate it as a properMaemo application. It's not finished, and so should be viewedas an alpha-release. You may be better off using Claws or (even better, hopefully)Modest.
Known bugs
Not all windows are Hildonised yet (that is, many have menubars ratherthan pop-up menus, and so on).
Fix dependencies on N800 to avoid start-up problem (see this solution in the mean time).
Full-screen button doesn't work.
Some windows appear too small, others too big.
Select from middle of direction pad should open message in proper viewwindow.
Problems with (some?) LDAP servers.
...
Limitations
No GPG support as yet.
Address book functionality removed due to a bug.
Built-in FAQ, manual and support for non-English languages removed forspace reasons.
Screenshots
sylpheed.deb(Maemo v2 package, v2.2.0rc-3, 511K)
Rebuilding from source
If the binary above whets your appetite for Maemo development,and you want to help with this port, the Maemo port is being maintained in aSubversion repository.
Username/password: guest/guest.[Browse the source]
Synchronisation and backup using rsync & make
Please note this has not been updated for 2006 OS,instead I prefer bind-mounts, however it is easily customisable.
The built-in backup/restore tool doesn't backup all yourdevice's configuration or installed applications. This script (aMakefile)meets those requirements and allows for maintaining patched parts of the rootfilesystem across firmware upgrades.
Usage
Requires rsync and SSH (on both 770 & hostcomputer) and make on the host.
Memo For Management
To 'install' the script:
Create a new, empty directory, on a Unix-like box (e.g. Mac OS X,Linux, *BSD, Windows with cygwin) and ensure you have rsync, make and SSHinstalled.
Download Makefile.770sync and move it to thenew directory, named Makefile.
Modify the line beginning REMOTE_DEVICE topoint to your 770. For example, my 770 has a fixed IP, I have root accesson it (by enablingR&D mode) and Dropbear is running on port 22 (the default), thereforethe line in my local copy says:
There are three 'targets' which can be executed to act onyour device. To execute them, run the following command:
Memo For Mac

make target
push
Push changes in the local copy to the remote device. This is effectivelya restore from a backup, if pull has been previously run.
pull
Pull changes from the remote device to your local copy. Effectivelyperforming a backup.
bootstrap
Similar to push but doesn't use rsync. This is useful when yourdevice has just been reflashed and is missing any software. By just installingand starting SSH, thistarget can be used to restore your documents, changes and applications (suchas rsync). An article on dillernet.com,Recovering From A Firmware Flash, has some techniqueswhich may also help in this regard (specifically scripts to install theneeded packages & SSH keys from the MMC card).
Since bootstrap will generally be required when reflashing andbefore SSH is running as root; SSH may well be listening on port 2222 (ifstarted by an unprivileged user), rather than port 22. Therefore, you canoverride the REMOTE_DEVICE variable:

make [email protected]:2222/ bootstrap
Note: in this example, as the SSH server was started as anormal user, it would not be possible to restore symlinks in /etc.
Example
One common requirement when SSH is installed is startingit automatically when your device is turned on. This is easily done bycreating a symlink, as described in the InstallSsh document in the wiki.
Unfortunately, when you reflash your device, this symlink will be lost.However, by using the script you can ensure that this (and similar changes)are put back on the device when you restore:
$ mkdir ~/770-sync $ cd ~/770-sync $ wget http://bleb.org/software/maemo/Makefile.770sync $ mv Makefile.770sync Makefile $ mkdir -p etc/rc2.d $ ln -s /var/lib/install/etc/init.d/dropbear-server etc/rc2.d/S99dropbear-server $ make push
As you can see, the local 770-sync directorycontains a copy of any changes you've made to the file system. In addition,the user's home directory, the configuration and the installed applications are pulled back on a pull operation.
Citrix ICA client
The below screenshots show that theCitrixARM Linux client can be got to run on a Nokia 770, although it iscurrently much use: the virtual keyboard is tied to onboard GTK+applications. A USB keyboard, or a Bluetooth keyboard using kbddshould work, however.
The Citrix install file won't work with busybox's 'expr' implementation andwithout 'cpio'. The application itself requires a few extra debs (whichfortunately Debian/ARM can provide):
libxaw6_4.3.0.dfsg.1-14sarge1_arm.deb
libxmu6_4.3.0.dfsg.1-14sarge1_arm.deb
libxp6_4.3.0.dfsg.1-14sarge1_arm.deb
libxpm4_4.3.0.dfsg.1-14sarge1_arm.deb
Maemo For Mac Os
Unfortunately, with the advent of 2006 OS and the use of EABI, older ARMLinux binaries will no longer work on the 770 without recompilation. Therefore,unless Citrix recompile and provide new binaries, or an open source clientis made available, Citrix is not easily possible on a modernMaemo device.
Maemo For Macbook Air
vim/rsync
Memo For Microsoft Word
These ports were for the 2005 OS, and have now been removed.mud-builder isa project which aims to simplify simple ports like thesein future.

0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
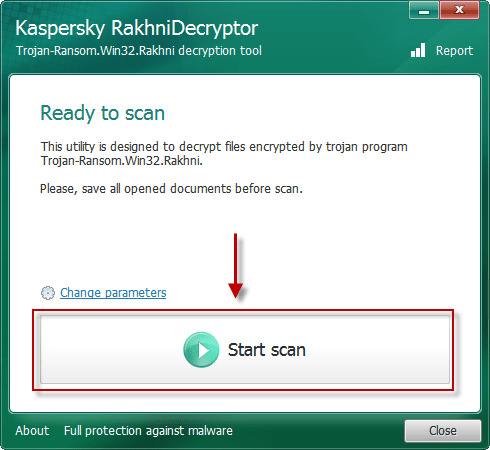
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
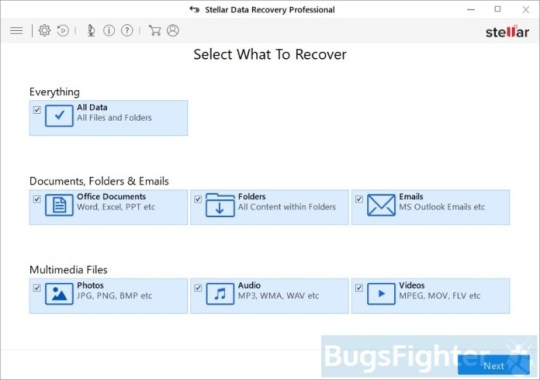
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
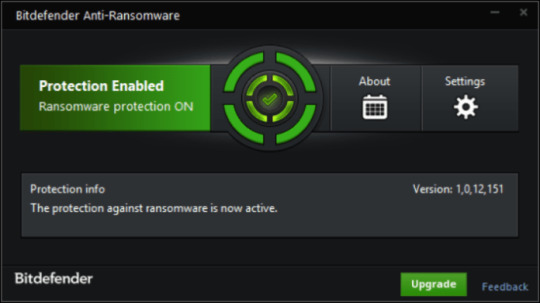
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
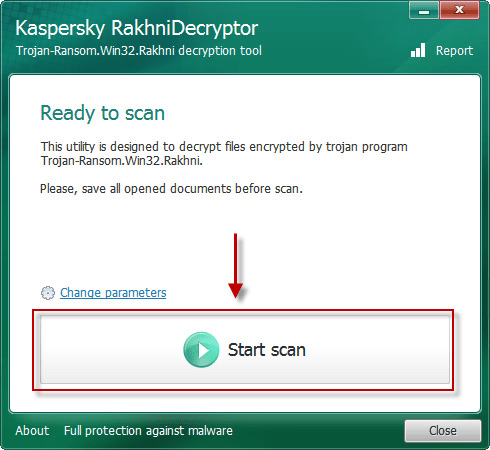
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
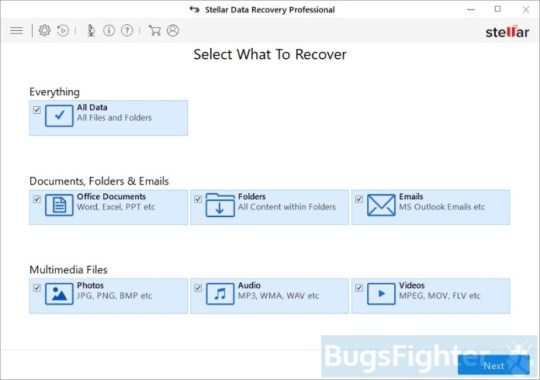
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
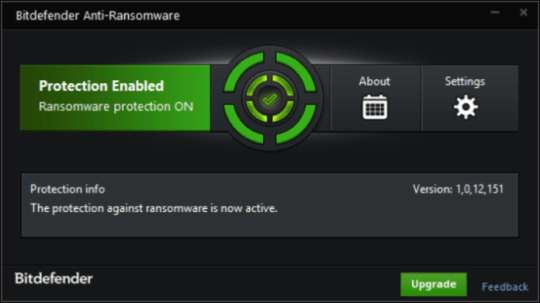
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
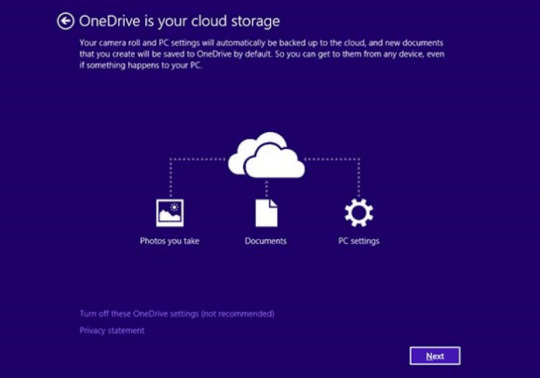
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
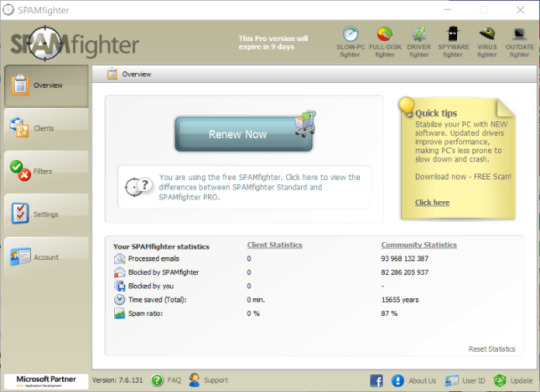
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.

Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
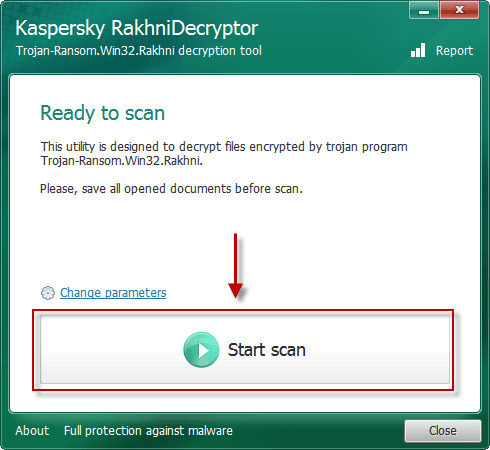
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
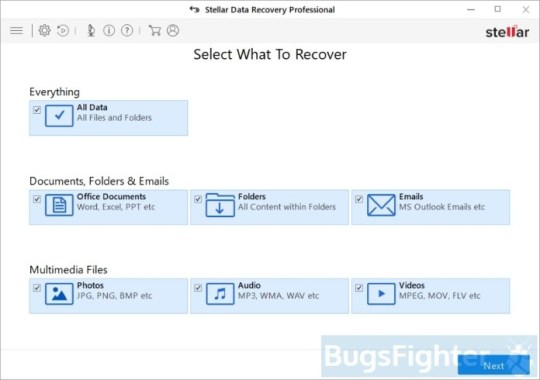
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
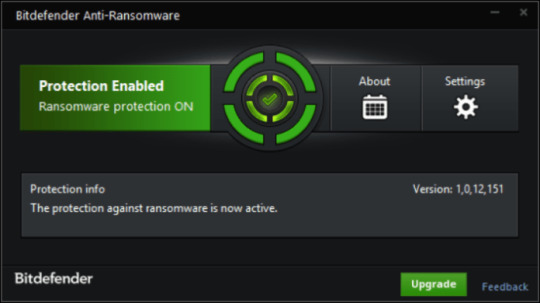
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
Blessing | WordPress Theme for Church and Charity Websites
New Post has been published on https://babesgobananas.com/blessing-wordpress-theme-for-church-and-charity-websites/
Blessing | WordPress Theme for Church and Charity Websites






Blessing Church WordPress Theme is built to serve church, charity and prayer group institutions. It’s also perfectly fits many business branches. The main feature, what is extremely important and super useful, lies in including of two applications here ? Events Calendar and Mail Subscriber. We offer you the great combination of functionality, good-looking, well-structure and usefulness
Church WordPress Theme Description:
Events Calendar and Mail Subscriber
Events Calendar makes you and your visitors always keeping the track of events, weather it is using for church events or charity ones. They won’t miss and forget about any important date. Once you put an event in calendar and set its recurring if needed, you always are informed and reminded about. The point is that your clients, guests, partners are able to find out where and when some meetings, conferences, trainings are take place. Each event description shows you the exact event place on map, it’s date, time, probably duration and repetition (annually, monthly, weekly, daily).To be more noticed we located the Next Event Time Box at the highest point of the template.

Mail Subscriber greatly helps you to notify all and each of your subscribers about further important dates and events. It rationally combines with Event Calendar work and complements it. We do our best to make your work with our themes easier and interesting for your future clients and visitors.

Getting this theme opens million ways for you and your business. Just make right choice to be noticed and you will be!
Feature of response to any device – nowadays make us to adopt to life no matter what. So we make it available for you to keep up with today needs.
With all these being said, ThemeMakers Support Team provides our customers with the highest quality professional customer service. Feel free to contact us through our Support Forum. Your satisfaction is our priority, so we are always glad to assist.
Please don’t forget to rate our theme if you like it. We are really appreciate it!
Advanced Theme Options Panel

Revolution Slider Plugin

It’s so easy and pleasant to experiment with slides, especially if you want to add a lot of them to your sliders.
Alternate Flex Slider inside the theme

It’s so easy and pleasant to experiment with slides, especially if you want to add a lot of them to your sliders.
Advanced Page/Post Options

Over 20 visual shortcodes such as alerts, audio, button, charts, columns, contact form, and others allow you to draw up each page of your web-site up to your needs and wishes.
Extremely convenient function of this theme is the opportunity of 6 post type variations. Each post may include and based on Default, Video, Audio, Link, Quote, Gallery post type. It’s great chance to point out some interesting audio, video, etc. and offer your visitors and customers to share their thoughts.
Each widget is for you to control and each of them has its own mission. For more comfort you can locate sidebars with widgets up to your need – either left, or right, also you can fill footer are with variety of theme widgets available. Here you are the artist and boss, everything in your hands, we just made it easier and nicer.
Since this theme includes SEO Tools module inside you do not need any plug in to install. SEO fields are available for each and every post, page, portfolio, gallery. Just fill in all meta lines and it will definitely rise your web-site up in a list of customers search.
Form Constructor
Contact Form Constructor lets your visitors contact you directly or be in touch with your web-site manager in case they are interested in products, information or ideas you present.
Christmas Bonus

We’ve included a simple and nice mail template for Christmas newsletter for your customers. Moreover we’ve implemented it into our subscription application which goes with this premium WordPress Theme.
Theme Features:
Slider Revolution Included (Save $19)
Fully compatible with the latest WordPress version!
Events Calendar Application (also ability to create repeatable events)
Newsletter Subscription Application!!! (New feature on themeforest, with this theme you’re allowed to create your news letters and then send them to your subscribers!)
Extended Theme Options Panel
2 Amazing responsive sliders (with video support)
Over 20 visual shortcodes
6 Post types for blog (Default, Video, Audio, Link, Quote, Gallery)
Custom Backgrounds for individual pages
14 Custom Widgets (Contact form, Contacts, Events Calendar, Facebook Like Box, Flickr, Google Map, Latest Tweets, Newsletter Subscription, Recent Posts, Recent Projects, Social Links, Soonest Event (with Timer), Testimonials, Upcoming Events)
Many Styling Options via ThemeOptions panel
Unlimited Slider Groups
Unlimited Sidebars
SEO Tools module inside
Google fonts api (573 font families)
Amazing CSS3 Effects
Skeleton CSS framework usage
CSS Improved Multilevel Drop-down Menus
Slider with embed video support (Youtube/Vimeo/Self hosted)
Crossbrowser Compatibility IE 8+, FF 3+, Opera, Chrome, Safari
Blog Listing Page/Alternate Page
Events Calendar/Events List Page Layouts
Beautiful 404 Error Page
Sortable(optional) Portfolio Page (with sidebar / without sidebar)
Sortable(optional) Gallery Page (with / without)
Responsive layout
Lightbox with video support (.swf, youtube, vimeo)
Contact Form Constructor
Layered PSD’s are included for easy modification and customisation
Localization Ready! (.po files)
Extended Video Documentation Included
High level Priority Support on our forum and Though Ticket System
Responsive Layouts:
By the way, our Churches and Charity WordPress Theme provides you with the responsive layout. So it is not a problem to enjoy the whole perfectness of your work without changes in showing up, using any device either PC, lap-top or tablet and smartphone.
Mobile Portrait Layout
Mobile Landscape Layout
Tablet Portrait Layout
Tablet Landscape Layout
Check it right now!

Please, keep in mind the info below before upgrading the theme.
Hello guys! If you previously (by 10th of February 2016) purchased the theme and want to upgrade it, we’d highly recommend to make a full site backup (all the files and database) since the releases beginning from v1.3.0 could not be 100% compatible. We did our best to make it 99% compatible, but who knows what could happen.
Release Notes:
VERSION 1.0 (December 06, 2012) 01 - Theme Released.
VERSION 1.0.1 (December 11, 2012) 01 - update with css file structure 02 - fix for displaying images problem for iPad 03 - update for blog shortcode 04 - update for images shortcode 05 - minor framework update
VERSION 1.0.2 (December 14, 2012) 01 - update for upcoming events widget 02 - fix for Flex slider title 03 - minor update for applications
VERSION 1.0.3 (December 18, 2012) 01 - soonest event widget update 02 - tabs shortcode fix 03 - added alternate template for gallery
VERSION 1.0.3 (December 18, 2012) 01 - soonest event widget update 02 - tabs shortcode fix 03 - added alternate template for gallery
VERSION 1.0.4 (December 21, 2012) 01 - widget soonest event fix 02 - fix for title styling options 03 - updated with latest version of revolution slider plugin
VERSION 1.0.5 (December 26, 2012) 01 - Upcoming events widget fix 02 - portfolio/gallery quick fix 03 - events listing page fix
VERSION 1.0.6 (January 05, 2013) 01 - fixed tabs shortcode 02 - fixed search page 03 - fixed time gaps for events 04 - update for facebook widget 05 - update for Events Calendar with tooltips.
VERSION 1.0.7 (January 09, 2013) 01 - minor updates for event post type 02 - fix for problem with soonest event countdown 03 - ThemeOptions panel quick fix
VERSION 1.0.8 (January 26, 2013) 01 - events plugin update (date picker) 02 - added table shortcode 03 - updated header area (opportunity to edit image/color) 04 - minor css fixes
VERSION 1.0.9 (February 08, 2013) 01 - update for soonest widget (opportunity to hide time zone) 02 - update for Events post type (added categories) 03 - IE8 quick fix 04 - update for Events (optional Map display) 05 - update for Events listing page (added pagination) 06 - updated some styles for widgets in header area 07 - fix for custom image in header
VERSION 1.1.0 (February 20, 2013) 01 - quick fix for mail subscriber plugin 02 - added an opportunity to set a first day of the week
VERSION 1.1.1 (February 27, 2013) 01 - update for captcha generation in contact forms 02 - minor updates for Event Application 03 - mail subscriber update
VERSION 1.1.2 (March 05, 2013) 01 - added ability to choose a size for posts featured images 02 - fixed recent projects widget view in footer area for IE 03 - added an opportunity to stylize main nav bg color 04 - updated with new contact form widget 05 - minor updates for Events Calendar
VERSION 1.1.3 (March 16, 2013) 01 - added filtering for events categories 02 - quick fix for dropdown menu in IE9
VERSION 1.1.4 (March 22, 2013) 01 - Events Calendar updated with an opportunity to set time format (12hr AM/PM or 24hr) 02 - Events Calendar updated with an option to filter events by categories optionally.
VERSION 1.1.5 (April 11, 2013) 01 - Image shortcode quick fix 02 - Quick IE10 fix for columns 03 - Added Youtube icon to social icons list 04 - Added option to show/hide html contant under comment forms 05 - Update for Event calendar with an opportunity to create events quarterly. 06 - Update for gallery/portfolio pages with an opportunity to add content to the top of pages
VERSION 1.1.6 (May 03, 2013) 01 - A notice added to event page if it there are no events for a particular month 02 - Fixed upcoming events shortcode 03 - Minor updates for events plugin
VERSION 1.1.7 (May 17, 2013) 01 - Quick fix for social icons tooltips 02 - Portfolio archives quick update 03 - Minor update for responsiveness 04 - Quick update for events plugin
VERSION 1.1.8 (May 28, 2013) 01 - added Gallery shortcode 02 - updated with a default wp image resizer (currently theme use both timthumb and default wp image resizer as alternate method)
VERSION 1.1.9 (June 06, 2013) 01 - quick fix for responsive version 02 - update for google map shortcode
VERSION 1.2 (July 09, 2013) 01 - Added One Click Install feature 02 - Added Layout Constructor 03 - Updated Twitter Widget 04 - Improved Theme Documentation
VERSION 1.2.1 (July 19, 2013) 01 - Update for One Click Demo Install (Compatibility for wide range servers)
VERSION 1.2.2 (July 22, 2013) 01 - quick update for proper theme path after installing
VERSION 1.2.3 (July 29, 2013) 01 - minor update for Event Calendar 02 - update for thumbnails support 03 - update for one click demo
VERSION 1.2.4 (August 31, 2013) 01 - revolution slider update 02 - help docs update 03 - staff shortcode update
VERSION 1.2.5 (October 4, 2013) 01 - Minor fixes with calendar plugin 02 - Upcoming Events shortcode updated with an opportunity to choose category 03 - Updated with an opportunity to set event duration to 24 hours.
VERSION 1.2.7 (May 1, 2014) 01 - update for wordpress 3.9 version compatibility
VERSION 1.2.8 (May 14, 2014) 01 - update for sending old events to draft 02 - update for displaying dates on events list page in wp-admin 03 - long events and repeating events fixes in Event Calendar and Event Calendar widget 04 - repair pagination on events category page 05 - changed displaying dates on single event, events listing, events archive, events category pages
VERSION 1.2.9 (September 12, 2014) 01 - Important update for Slider Revolution 02 - WordPress 4.0 compatibility update
VERSION 1.3.0 (February 12, 2016) * Slider Revolution update (latest version added) * WordPress 4.4.2 compatibility update * Theme Performance update * One Click Demo Install update * Layout Composer Upgrade * Fixed Issues, previously reported by customers
VERSION 1.3.1 (April 26, 2016) * updated: mediaelement script * updated: twitterFetcher script * updated: SliderRevolution v5.2.5 * fixed: responsiveness issue * fixed: email subscriber issue
VERSION 1.3.2 * fixed: theme options (contact forms, sidebars)
VERSION 1.3.2.1 * updated: revslider to latest version v5.2.5.2 * updated: dbmigrate plugin
VERSION 1.3.3 * updated: Theme compatibility with WP 4.6.x * updated: Google map API * fixed: minor theme issues
VERSION 1.3.4 * updated: Theme compatibility with WP 4.8.x * updated: revslider to latest version v5.4.5.1 * updated: twitterFetcher script
VERSION 1.3.5 * updated: revslider to latest version v5.4.6 * fixed: fixed issue with google maps in event pages
VERSION 1.3.6 * updated: compatibility with wordpress 4.9.x * updated: revslider to latest version v5.4.6.4 * fixed: fixed issue with google maps * fixed: fixed issue with mediaelement player styles
VERSION 1.3.7 * updated: Theme compatibility with WP 4.9.x * updated: revslider to latest version v5.4.6.4 * updated: twitterFetcher plugin * fixed: fixed issue with naming conflicts between permalink and post type name * fixed: issue with nondisplaying google maps * fixed: partly dynamic data sanitisation
VERSION 1.3.8 * updated: revslider to latest version v5.4.8.1 * updated: WP 5.0 compatibility check * updated: deactivate Gutenberg and re-activate Classic editor
VERSION 1.3.9 * updated: revslider to latest version v5.4.8.2 * updated: fix one click demo
Source
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.
Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes
Text
How to remove Sodinokibi Ransomware and decrypt your files
What’s Sodinokibi Ransomware
Sodinokibi Ransomware (a.okay.a. BlueBackground Ransomware or REvil Ransomware) is disruptive cryptovirus, that encrypts consumer knowledge utilizing Salsa20 algorithm with the ECDH-based key change technique, after which requires a ransom round zero.475–0.950 BTC to return the information. In other phrases, if the quantity is about at $2500, then without paying within 7 days, it doubles to $5000. It appeared in April 2019 for the primary time. Since then, security specialists distinguish the next variations:
Sodinokibi Ransomware (preliminary model 1.zero from 23rd of April 2019)
Sodinokibi Ransomware (model 1.0b from 27th of April 2019)
Sodinokibi Ransomware (version 1.0c from 29th of April 2019)
Sodinokibi 1.1 Ransomware (from fifth of Might 2019)
Sodinokibi 1.2 Ransomware (from 10th of June 2019)
Sodinokibi Ransomware (unclassified version with a modified ransom notice from 8th of July 2019)
At first, up to most up-to-date variations, malware used following template for ransom notice: random-alphanumerical-sequence-readme.txt, where random-alphanumerical-sequence is randomly generated set of letters and numbers used for users identification. This set can also be used to switch extensions of affected information. Then, the virus started to make the most of the following sample: random-alphanumerical-sequence–HOW-TO-DECRYPT.txt. In the box under you’ll be able to see an example of such file.
Sodinokibi Ransomware
—=== Welcome. Again. ===— [+] Whats Occur? [+] Your information are encrypted, and at present unavailable. You’ll be able to verify it: all information on you pc has enlargement 518ftbt4ym. By the best way, every part is possible to recuperate (restore), but you’ll want to comply with our directions. In any other case, you cant return your knowledge (NEVER). [+] What ensures? [+] Its just a enterprise. We completely do not care about you and your deals, besides getting benefits. If we do not do our work and liabilities – no one won’t cooperate with us. Its not in our interests. To verify the power of returning information, You must go to our web site. There you’ll be able to decrypt one file at no cost. That’s our assure. If you will not cooperate with our service – for us, its doesn’t matter. But you’ll lose your time and knowledge, cause just we have now the personal key. In practise – time is rather more useful than money. [+] How you can get entry on website? [+] You will have two ways: 1) [Recommended] Using a TOR browser! a) Download and install TOR browser from this website: https://torproject.org/ b) Open our web site: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/9343467A488841AC 2) If TOR blocked in your country, try to use VPN! However you should use our secondary website. For this: a) Open your any browser (Chrome, Firefox, Opera, IE, Edge) b) Open our secondary web site: http://decryptor.top/9343467A488841AC Warning: secondary website might be blocked, thats why first variant a lot better and extra out there. Whenever you open our web site, put the next knowledge in the input type: Key: random-id Extension identify: random-alphanumerical-set —————————————————————————————– !!! DANGER !!! DONT attempt to change information by yourself, DONT use any third social gathering software program for restoring your knowledge or antivirus options – its might entail damge of the personal key and, as outcome, The Loss all knowledge. !!! !!! !!! ONE MORE TIME: Its in your interests to get your information back. From our aspect, we (one of the best specialists) make every little thing for restoring, but please shouldn’t intrude. !!! !!! !!!
So, as we beforehand stated, each pc gets unique individual file extension. Another indicator of infection can be referred to as an disagreeable blue background, which replaces the desktop wallpaper. Within the earlier version, there was no informative inscription on it. Later an inscription appeared indicating that the word file ought to be learn. Sodinokibi Ransomware removes shadow copies of information, disables restore options of Windows through the boot part with the command:
C:WindowsSystem32cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set default recoveryenabled No & bcdedit /set default bootstatuspolicy ignoreallfailures
Contained in the JSON configuration file is an inventory of 1079 domains. Sodinokibi establishes a reference to every domain of this record by producing a URL using a website era algorithm, though, they don’t seem to be Sodinokibi servers. Comply with the detailed guide on this page to take away Sodinokibi Ransomware and decrypt your information in Home windows 10, eight/eight.1, Home windows 7.
Download Sodinokibi Ransomware Removing Software
Get decryption software for encrypted information
Recuperate encrypted information with Stellar Phoenix Knowledge Restoration Professional
Restore encrypted information with Home windows Previous Variations
Restore information with Shadow Explorer
Methods to shield from threats like Sodinokibi Ransomware
Sodinokibi Ransomware
BlueBackground Ransomware
How Sodinokibi Ransomware infected your PC
Sodinokibi Ransomware is distributed by hacking via an unprotected RDP configuration, utilizing e-mail spam and malicious attachments, fraudulent downloads, botnets, exploits (RigEK), malicious ads, net injections, pretend updates, repackaged and contaminated installers. Furthermore, it exploits vulnerabilities in Oracle WebLogic and conducts a “Watering hole” attack on organizations and online publications. Virus assigns sure ID with the victims, that is used to name these information and supposedly to send decryption key. As a way to forestall infection with any such threats in future we advocate you to make use of WiperSoft AntiSpyware, SpyHunter 5, BitDefender or any reputable antivirus program.
Download Removing Software
To remove Sodinokibi Ransomware utterly, we advocate you to make use of WiperSoft AntiSpyware from WiperSoft. It detects and removes all information, folders and registry keys of Sodinokibi Ransomware.
Learn how to remove Sodinokibi Ransomware manually
It isn’t really helpful to remove Sodinokibi Ransomware manually, for safer answer use Removing Tools as an alternative.
Sodinokibi Ransomware information:
sodinokibi.exe random-alphanumerical-sequence-readme.txt random-alphanumerical-sequence–HOW-TO-DECRYPT.txt random.lock
Sodinokibi Ransomware registry keys:
no info
Tips on how to decrypt and restore your information
Use automated decryptors
Use following software from Kaspersky referred to as Rakhni Decryptor, that may decrypt your information. Obtain it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom because there isn’t a assure you will receive the important thing, but you’ll put your financial institution credentials in danger.
In case you are contaminated with Sodinokibi Ransomware and eliminated it from your pc you’ll be able to attempt to decrypt your information. Antivirus distributors and people create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Professional to revive your information
Obtain Stellar Knowledge Recovery Skilled.
Click Get well Knowledge button.
Choose sort of information you need to restore and click Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Download Stellar Knowledge Restoration Professional
Using Windows Earlier Versions choice:
Right-click on contaminated file and select Properties.
Choose Previous Versions tab.
Select specific version of the file and click on Copy.
To restore the selected file and exchange the prevailing one, click on the Restore button.
In case there isn’t any gadgets in the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any different dates in the record, select various technique.
In case you are using Dropbox:
Login to the DropBox web site and go to the folder that accommodates encrypted information.
Proper-click on the encrypted file and select Earlier Versions.
Choose the version of the file you want to restore and click on on the Restore button.
How you can shield pc from viruses, like Sodinokibi Ransomware, in future
1. Get special anti-ransomware software program
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender released free device, that may make it easier to with lively anti-ransomware protection, as a further defend to your present safety. It won’t conflict with greater security purposes. In case you are looking full web security answer think about upgrading to full model of BitDefender Web Safety 2018.
Obtain BitDefender Anti-Ransomware
2. Back up your information
No matter success of protection towards ransomware threats, it can save you your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s more sense utilizing online backup, than creating bodily drives, that can get infected and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/8.1 customers can find pre-installed OneDrive backup answer from Microsoft. It is truly the most effective backup providers available on the market, and has affordable pricing plans. Customers of earlier variations can get acquainted with it here. Be certain that to backup and sync most essential information and folders in OneDrive.
3. Do not open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of many world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very excessive degree of anti-spam safety.
Download SPAMFighter 5/5 (2)
The post How to remove Sodinokibi Ransomware and decrypt your files appeared first on Spouting-Tech.
#Ransomware#remove bluebackground ransomware#remove revil ransomware#remove sodinokibi ransomware#tech#Tutorials#Viruses
0 notes