#msg: hacker
Explore tagged Tumblr posts
Note
hi loree long time no see… happy new year, i hope the past few months have been good to you!! how are you?
—hacker
HI IM SORRY I HAVENT OPENED TUMBLR…
i’m good though!! i moved back to college it’s been. an experience. my roommate is insane and so is her boyfriend, i need summer break to come immediately.
other than that though it’s been fine :3 just school. oh and we have baby goats due soon!!
how about u my love how have you been :D
2 notes
·
View notes
Note
hahahhaheheheheehehihihihihihihihi vou ti mandar asks anônimas todos os dias mesmo você sabendo quem eu sou
Doente MENTAL
0 notes
Text
love-coded.exe
season one: finding sunshine boy a hacker group, comprised of five members, has their world changed when a glitch leads to y/n joining their private chat. gn!reader.










-ˋˏ S1 EP 0.9: the plot thickens ᝰ.ᐟ
are you still watching? << exit // continue watching >>
audio <- the story from the audio msg (first clip) ↳ if you're still unsure of the characters identity and don't want spoilers, don't click this!

taglist: @stilldontknowhoiam • @missvanjiii • @torkorpse • @estella-novella • @fic-for-readers • @bloominglix • @j-0ne25 • @mythicmochi • @lausnotverybright • @velvetmoonlght • @mangojellyyy • @yn-x-them • @facioleeknow • @blckchrryy
@akindaflora • @xo-xaevia • @chansbbgnumberone • @diekleinesuesse • @bee-the-loser • @hyeon-yi • @unorthodoxdreamers • @sona1800 • @vegetablesarefuntables
#skz fake texts#skz imagines#skz smau#skz texts#skz x reader#felix x reader#felix fake texts#felix texts#felix smau#felix imagines#jeongin x reader#jeongin fake texts#jeongin texts#jeongin smau#jeongin imagines#chan x reader#chan fake texts#chan texts#chan smau#chan imagines#minho x reader#minho fake texts#minho texts#minho smau#minho imagines#changbin x reader#changbin fake texts#changbin texts#changbin smau#changbin imagines
81 notes
·
View notes
Text
Okay with the 2024 Player Appreciation Week in march I really want to do something, and i think my best way back in is with a pt.2 to the fic I wrote for it wayyyy back in 2022. I have some ideas on where to head with it but then it's the issue of the expandability of such and which I think will work the best.
I'll link the orginal fic here incase anyone wants a refresher and the 2024 Player Week post but here are my thoughts for a continuation of the fic:
Day 2 - Parents: Direct continuation of Pt.1
Once arriving in Argentina, Players mum finds it difficult to accept letting go of her only child, and after a while (and accidental encouragement from Player himself) ends up phoning and messaging him multiple times a day, always at the worst times, aka all the time. It all culminating in almost ruining an important mission thanks to the eventual escalation. A nice resolution, naturally, but a story about the difficulties of separation and how ignoring/distancing in contrast to the almost obsessive inability to let go, one extreme to the other, isn't the best way to process it at all.
Player POV. Players mother & Carmen, then new team ACME Ivy and Zack and possibly Julia, Chase.
Day 5 - Loyalty: Can be a separate fic or direct continuation of Pt.1
(If a seperte fic, based sometime after the 2 year jump) Chief attempts to poach Player to join her ranks now that he's officially legal to actually hire and back out after the hiatus. Chief assigns Zack & Ivy to get the 'job' done, unbeknownst to them of her actual plans. After an official approach from her senior Agents Julia and Chase and sending him all the ACME merch one could possibly need, unsurprisingly, leads to no avail. Hijinks ensue.
Player POV. Carmen vs Chief + New ACME Zack & Ivy, brief Chase and Julia.
Alt. 3 - Hacker + Day 6 - Abandonment: Direct continuation of pt.1
Due to some self reflection, Player is determined to spread his wings with his new found 'adulthood' and separate himself from being a 'simple hacker' after Carmen unintentionally gets in his head about his role in the team and maybe his lanky physique, truly, she didnt mean it. Its hard being a young adult in the big wide world, trying to make or reinvent a name for yourself. He attempts to cultivate a new 'field agent' identity, eager to get out there one-on-one and in his words; "if Zack can do it, how hard can it be?". Unfortunately underestimated the true training, experience and skill development it takes to do what Carmen does, and do it well. He ends up, quite literally and accidentally, abandoned in a foreign country after failing to make it to the pick up location. With Player on the ground and off his perch, his tech destroyed, AI failing to fill his 'old' position, Player has to hope that he can either turn the drastically crappy situation around, manufacture a 'run in' with ACME or he will probably fall into the remnants of VILE's grip he barely avoided to dodge in the first place.
Player POV. Carmen, non disclosed VILE agents & Maybe ACME.
This is what I got. Or at least the best ideas I have that have a bit a meat to em. I'm open for a discussion on what y'all would want to read the most. I'm open for anything, Rbs, direct msgs on the post or to be me are totally welcome. ♡
#player appreciation week#csplayerweek2024#csplayerappreciationweek2024#playerappreciationweek#carmen sandiego#cs 2019#carmen sandiego netflix#carmen sandiego 2019#cs Player#player bouchard#disfordevineaux#chase devineaux#julia argent#cs ivy#cs zack
22 notes
·
View notes
Note
tim did kidnap jacyn!!! I mean idk for sure but it lines up!! I read jays msg to stray Tim and then the ransom said to meet at the docks and YOUR TIM is at the docks RN!
He isn't! He would never!
He'd never do somethin' like this and risk it rippin' him from his family, things were gettin' better from my fiasco last month!
Besides, the ransom ain't even in his typography! Tim is wayyyy more imposing, he would have threatened somethin' much more severe and maybe even sent off one of Jay's fingers if he was bein' serious.
Not even mentionin', my boyfriend is stupid fuckin' rich, what would he even need a million dollars for? That's like chump change 't him. And even if he did need it he's a genius hacker who could have simply hotwired the money into his account without anyone noticin'.
It ain't Tim, and I'd bet my life on that.
2 notes
·
View notes
Note
yo do any of your sides have typing quirks 👀 wentz strikes me as someone who’d use leet speak (wentz is your creativity’s name right? sorry, trying to memorize all of them and struggling jajdjdjf) - @girlboypatton
Well i actually used 2 have a typing quirk (& still do), so when I used 2 type silly & strange, all my sides did 2
i typed liek diz !!11!!! Or svmtiemzz iid dovble mqii lttrzz & qdd rqndom qz evrywherezz
(I typed like this! Or sometimes id double my letters and add random qs everywhere)
My typing quirk has adapted in2 something more accessible 2 screenreaders, ppl w/ dyslexia, & other disabled ppl.
ANYWAY. Wentz (creativity) 100% uses a typing quirk occassionally and, quite literally, speaks little emoticons like xD and :3 (how does nya do that? Thats 4 woof 2 know & u 2 find out). It is a running joke in my Swapped AU, that cos uses random faces & c!Thomas is Terrified.
There is a very specific way scene kids typed back in the early 2000s & it was not leet speak (leet speak originated 4 hackers & evolved more 4 gamers, if i rmbr correctly), so Wentz doesn't use leet speak.
Wentzz typez liek DIZ x3 o3o probzz liek da way da author of mai immortal typd thru out da seriezz. Phull of miszpellz & bd grmmr & tking out rando lttrz cuz it waz KEWL xD (@ da tiem!) -_-;;
(Wentz types like this x3 o3o probs like the way the author of my immortal typed through out the series. Full of mispells and bad grammar and taking out rando letters because it was cool xD (at the time!) -_-;)
Memphis (egotism) doesn't necessarily use a typing quirk, in the way that word means now, but she does shorten every single word if she can (& even when she cant). Uses every abbreviation & acronym under the sun. He has things 2 do!!! Like.... continue 2 text & b on his phone.
Both him & wentz r probably the 2 ppl u do NOT want 2 text w/.
Memphis wll shrtn vrythng 2 spnd less time typng. probs uses LOL & OMG & TTYL in daily cnvrs. & hates making his wrds easier 2 read
(Memphis will shorten everything to spend less time typing. Probs uses LOL & OMG & TTYL in daily conversation. & hates making his words easier to read)
On the other hand, Wentz will gladly drop his scene speak 2 make his text accessible.
Maven doesn't like 2 text or call... or talk, or be around people, but when they do text they don't use a typing quirk, they're just always tired & it affects their writing. A million misspells and missing letters and— how did you even sleepily misclick so badly you ended up in the emojis??
& then everyone else is somewhat normal. They either type w/ 2 much punctuation (see: Melvin Compassion) or refuse to even respond 2 ur text message (see: Mercury Paranoia) or responds 2 all of ur msgs w/ some form of vulgarity & middle finger emojis (see: Maddox Impulse)
4 notes
·
View notes
Text

people here are... strange. that's coming from someone who's literally seen at least ninety-percent of their galaxy. she lifted herself onto the edge of the boardwalk's handrail, looking down at the people playing around in the sand. that looked physically taxing, she'll pass. this was like starting at level 1 in a really crappy mmo. the hacker awkwardly shifts in her seat, man she wish she had her phone. she tilts her head over her shoulder, spotting the person next to her. " hey, you. " silver wolf calls out. she makes eye contact and leans forward, holding the edge of the railing. they seemed easygoing enough to just answer her question without hesitation. " what do you think of this place? do you find it fun? "
send msg : @etargus !
#etargus#▹ SYSTEM: // [ ( run : log in ) ]#▹ SYSTEM : // [ ( load data : archer ) ]#▹ SYSTEM : // [ ( load data : etargus01 ) ]
2 notes
·
View notes
Text
. ݁₊ ⊹ open to M . ݁₊ ⊹ connections: rival-to-lover ( who could be an agent, hacker, IT specialist, data analyst, codes for fun, anything ) . ݁₊ ⊹ [ encrypted chatroom ] Y/M and case have been chatting online for a while. they challenge each other with encryptions, codes, puzzles, and whatever else to solve. it's grown into their way of flirting. they only know each other's aliases / usernames, not faces.

[ ⇉ msg sent : ]
— well, i gotta admit — this is the most fun i've had in a while — it's not everyday that someone takes the time to code something this beautiful and tricky for me to chip away at
#indie rp#indie crime rp#: pls keep this a messages only thread for now thanks!#: OPEN#starter:case#indie gay rp
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Mobile devices need security too. Hackers have developed stealthy new threats just for mobile — threats that can spy on your location information, steal your passwords or damage your device. Norton Mobile Security helps keep your data on lockdown, so you can go mobile without worry.Stop malicious apps with exclusive threat-detecting technology.Mobile devices are not immune to malware and apps can have big security issues. Hackers can hide malicious code designed to steal your personal and financial information in seemingly legitimate apps. Many apps require access to data on your device, like your contacts or photos. Norton Mobile Security protects you from malware and mobile threats. App Advisor for Google Play scans apps before you download them to warn you about any malicious code or privacy risks.1,2 App report cards even tell you where in the world personal information will get sent and alerts you if an app consumes a lot of data or drains the battery. Go online on the go with a traveling security solution.Online security risks that plague computers have gone mobile. From phishing scams that trick victims into sharing private information to ransomware that demands money in exchange for stolen data, mobile attacks are on the rise. In fact, cybercrimals target mobile devices because they’re less likely to be secure. With Norton Mobile Security, you’ll get an alert when you connect to an unsecure network, a built-in search engine that flags unsafe sites and a phishing blocker that helps protect your personal information.1,3 Now you can browse the news, check your email and even make mobile payments with new peace of mind.Recover a lost device quickly.Your whole life is on your mobile. Protect your contacts, photos, passwords and more.Norton Mobile Security lets you remotely lock data on a lost device to prevent unwelcome access. Then, use Remote Locate to pinpoint the location of your device so you can retrieve it and restore your data. If you misplaced your device around the house, you can trigger an alarm to find it quickly. Code will be mailed to the Amazon registered email ID within 2 hours of ordering or check 'Buyer/Seller messages' under Message Center at "amazon.in/msg" This software works on devices with India IP addresses only Norton Mobile Security - 1 Device - 1 Year (Email Delivery in 2 Hours - No CD) Award-winning proactive protection against Android apps with risks Safe Browsing: Protects your device and your personal data from malicious sites that install ransomware, Trojans and other threats Recover a lost device quickly; Don’t let a lost device ruin your day; With device recovery protection you'll find it fast Unsecure Wi-Fi Notifications; Alerts you if you’ve connected to a Wi-Fi network or public hotspot that’s not secure Protective Threat Blocker: Scans and removes apps with harmful viruses, malware, spyware or other threats; 1 It’s powered by Norton Mobile Insight, a unique app-intelligence system that is continuously updated with threat information to protect you and your device from bad apps [ad_2]
0 notes
Text
If you can't print them on paper, PDF them and find a way to save them. Email to your non-work mail, maybe. (There'll be a record on their servers, but the issue isn't to prevent them from knowing you kept a record; it's to have it available.)
I have yet to see an office security system that completely prevented the ability to send files outside of the system. A lot of them lock access to gmail but not Google Drive, where you could drop files. (Use a private browser window so it doesn't show up on the computer's records; it's still going through the work ISP but that's less likely to be noticed - because that's tracking every bit of internet activity across their network.)
If you suspect work's IT group is reviewing external emails & attachments, name them something like "benefits notes" - so it looks like you're sending the company benefit plan info to your personal account so you can review them at home. You might be able to password-lock the PDFs, depending on what software you have available. Pick something easy to remember, not high-security - you're not trying to block hackers; you're just trying to make it difficult to notice.
In case of extreme lockdown: You can save emails as individual .msg files, which will be at least outside of the email program that may be under their control.
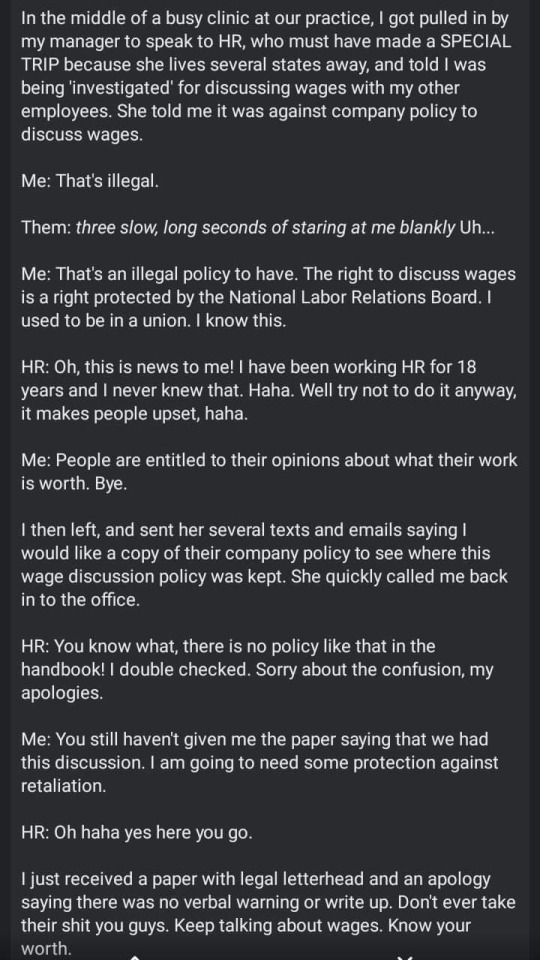
Do Not Let HR do this to you. It is not illegal to talk about wages in the work place. I did and got a 12% raise!
73K notes
·
View notes
Note
it’s ok sometimes i forget i even sent an ask LOLOL
i’m okay though, school gets me tired soo fast but also i started stardew valley recently and i keep going back to it (unfortunately). how’s ur senior going for u so far?
—hacker
lol its also possible that tumblr eats it. its been so long since ive been chronically active on tumblr, idek if thats still an issue on tumblr or not lol.
stardew valley tho omg,, i finally married sebastian and then i just havent played again HAHA shit was so annoying though, i stg i got him to ten hearts on the fiRST DAY OF WINTER and then it didnt rain until like the last week of spring so i couldnt buy the stupid marriage thing </3 i need to either finish that world or make a new one though haha. its like minecraft to me i swear; ill get really into it unhealthily for a week or two and then not touch it for a week.
and my senior year has been good! i have somewhat easy classes this year save for pre-calc my behated but the good news is i thought i made a 63 and actually made a 73 bc she wrote it wrong 💀 anywho i love love love my eng professor he has decided that he likes me methinks so he gives me good grades lol.
how about you, how has school been? :D
2 notes
·
View notes
Text
I don't think cops were called about the ladies....the energy changed in shelter reminiscent of a few months prior e.coli....so I think they were noticing hackers around the building awhile it's not the ladies that are truly scary....they admit things and show that people do provoke them it's the energy needs sometimes
The two brown bisexes won't leave on night passes anymore and so insomnia and constant annoyance. .
The aggressive white that wouldn't stop kicking or punching my upper bunk mat would finally pee and lose control of poo in pants also and so I don't have to have anyone under me awhile the aggressive whites more get a scheduled scene over with and arent actually that bad
The two bisex browns never stop lingering pirhanna like that does things with eye catching attention or verbal assaults till I really dont care if people hate on them
Fashion and acting crimes till very verbally assaultive or cop gear tried
The aggressive white on leaving just said that she doesn't like how she treats her mental condition and she starts lashing out at everyone around her if their rights aren't actions to help her immediately
She did show me she does visibly look like palsey or down syndrome or severe prolongated relationship battery so there isn't much thought there apparently
Pharmacology to mentals like olanzepine or you have to be a fat addict is as deadly as fentanyl or clopidopteral....and that was if your not with her your against her
Poo in the pants...i was seen with China and not new jails and if it's those institution urine smells she will lash out if your not with right wing Jewish troops that know china was bad to Jewish people though
Hunans and making heyroth pay off petty crimes those were bad decisions though the msg or other drugs in food bad decisions though
I was white too and those decisions are not good to me and someone has to be aware that anti psychotics have to be normally metabolized
China for me takes Irish and Jewish cultures so I don't have to
I was white too and if I can't go to the Africans instead of the pornographers I can't be around next generation genetic testing and new institutions with Korea on Hawaii agriculture either and that is just to make me really crazy and to continue insipid peace man that just keeps letting things play out on their own
The black lady that left was also aggressive in standard exact characterized ways....someone approached her at her car and she lashed out people said bitch to her in very ugly ways just to try to ear worm her or hook her thoughts with it so she said bitch to them in return.....the black aggressives are really straight forward cause and effect
I get fixated or fascinated a bit with whether or not people are abnormal and they are normal people about aggression
If they wouldn't have treated the Jewish conscription badly sometimes they would have been a better help and comrade to whites left under Texas police mengele and lynch syndrome
0 notes
Text

Go follow my Pinterest @DmonV2 !
About me!!
Me!: Acidburnv2, she/her, 19, lesbian
Favorite movies: Hackers, foxfire, gia, the matrix
Favorite actor: Angelina jolie! <3
Favorite artist: Atari teenage riot, H3artCrush, Kittie
Favorite video games: jet set radio future, borderlands, overwatch, fuzion frenzy, skyrim
Hobbies: art, collecting old technology, shit posting, going to the library, watching every single Angelina movie with my gf

Feel free to msg me about anything! Also I apologize in advance idk much about how Tumblr works! </3
0 notes
Text

Deadliest Prey (2013) I've been a huge fan of the original Deadly Prey for as long as I can remember and that may be why I avoided the 21st century sequel. Nowadays on November 2nd VHS b movie nerds celebrate Prey day and we rewatch the original. I thought I'd change it up this year and finally try the sequel. It took a long time to accept but let's just say..I enjoyed it. Dayton the original hero is back and is a legend in a way he definitely is not in real life. Instead of being jacked in daisy dukes he is old and it pajama pants the whole time hahaha, it's def not supposed to be funny, which I guess was the appeal of the first but falls flat this time. Now it's the internet age so the deadly prey hunt is on the internet for money so that's why young hackers are gonna hack haha, falm palm, so screams of a dad trying to be hip, alas the director and brother of the star passed away shorting after this film. RIP. This brother duo had made better films as their career went on but this dip into the home funded ms paint digital area is actually interesting. Because again Deadly Prey wasn't good and it wasn't funny on purpose. This time I am pretty sure there are some purposefully self aware gags but in general it's deadly straight and thus maybe even funnier. The young characters are awful and semi spoiler there is a pay off for that which for my morbid brain was laugh out loud worthy. Daytona progression from dad to action star to border line maniac is impressive. The villains are as evil and yet as dumb as ever. The fact that so many things happen exactly the same as it did in the 80s and no one in this film should be up for it is very funny and yet it almost works.. almost. Spoiler at the end Dayton's son reappears and even that he is a character we have never given any attention too we see this child is as bad ass a gun shooting man mad as his dad and they save the day with a final battle that is so eluding people other then us VHS collecting nerds saw the original. In the end the msg is kids with guns for the future of America . With the unself aware death toll to the cheap fx explosions it's riff worthy and a def guilty pleasure. #deadliestprey #preyday
1 note
·
View note
Text
Major Cybersecurity Breach at Leidos Holdings Inc., Pentagon Contractor

Leidos Holdings Inc., a leading IT services provider for the U.S. government, has fallen victim to a cybersecurity breach. Hackers have leaked internal documents from the company, raising serious concerns about the security of sensitive government data managed by third-party contractors.
Leidos: A Key Player in Government IT Services
Leidos, formed in 2013, has established itself as a crucial player in national security through its IT services and solutions. In the 2022 fiscal year, Leidos was the largest federal IT contractor, with $3.98 billion in contract obligations. The company's client roster includes high-profile organizations such as the Defense Department, Department of Homeland Security, NASA, and other U.S. and foreign agencies. Notably, 87% of Leidos' revenue comes from contracts with the U.S. government.
The Breach: Origin and Scope
The leaked documents are believed to have been stolen during two separate breaches of Diligent Corp. in 2022, a platform used by Leidos. According to a Bloomberg News report, Leidos used the Diligent system to host information gathered in internal investigations. https://twitter.com/ShadowofEzra/status/1815866536206426468 The Cyber Press team investigation revealed that the stolen data comprises one gigabyte of files in various formats, including zip, msg, doc, jpg, png, xls/x, and pdf. These files are associated with Leidos technical assistance and its customers. The leaked data is divided into two parts: part one contains 451 files representing credits, while part two includes 6,500 files representing bitcoins or dollars.

Post on BreachForums leaking the data
Potential Impact and Ongoing Investigation
While the nature and sensitivity of the stolen documents remain unclear, the leak underscores vulnerabilities in the cybersecurity frameworks of companies handling critical government information. Leidos has confirmed its awareness of the issue and is actively investigating the extent of the breach. However, the company has not yet made a public statement regarding the specifics of the leaked documents or the steps it is taking to mitigate the impact.Some Redditors are claiming this data was stolen over a year ago, but just released today: https://www.reddit.com/r/BB_Stock/comments/1eak5cp/comment/lemtgo5/?utm_source=share&utm_medium=web3x&utm_name=web3xcss&utm_term=1&utm_content=share_button
Broader Implications for Cybersecurity
This incident has sparked a broader discussion on the security measures and protocols employed by government contractors. Cybersecurity experts warn that breaches of this nature can lead to severe consequences, including financial losses, reputational damage, operational disruptions, and legal complications. Moreover, such incidents can erode consumer trust and subject organizations to intense scrutiny from regulators and customers.
Next Steps and Future Concerns
The threat actor responsible for the breach has indicated plans to sell the data in two different types, further exacerbating concerns over the potential misuse of sensitive information. This development has prompted Leidos to take immediate action to evaluate the extent of the damage and strengthen its defenses against future attacks.As the investigation unfolds, the cybersecurity community and government agencies will be closely monitoring the situation. The incident serves as a stark reminder of the ongoing challenges in protecting sensitive data in an increasingly complex digital landscape, particularly when it involves critical national security information. Read the full article
0 notes
Text
como tirar msg vpn
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
como tirar msg vpn
VPN grátis
Um VPN (Virtual Private Network) grátis é uma ferramenta que proporciona anonimato e segurança ao navegar na internet sem a necessidade de pagamento. Existem diversas opções de VPN gratuitas disponíveis no mercado, cada uma com seus próprios recursos e benefícios.
Ao utilizar um VPN grátis, o usuário pode ocultar seu endereço IP real, proteger seus dados de possíveis hackers e manter sua privacidade online. Além disso, uma VPN gratuita pode permitir o acesso a conteúdos restritos geograficamente, como serviços de streaming e sites bloqueados em determinadas regiões.
É importante ressaltar que, embora as VPNs gratuitas ofereçam diversos benefícios, algumas delas podem apresentar limitações em termos de velocidade de conexão, quantidade de dados disponíveis e número de servidores disponíveis. Além disso, é fundamental escolher uma VPN confiável e segura, a fim de garantir a proteção adequada de suas informações pessoais.
Antes de optar por um VPN grátis, é aconselhável pesquisar e comparar as opções disponíveis, considerando aspectos como reputação da empresa, políticas de privacidade, protocolos de segurança utilizados e avaliações de outros usuários. Dessa forma, será possível escolher a VPN gratuita que melhor atenda às suas necessidades de privacidade e segurança online.
Acesso bloqueado
Quando nos deparamos com a mensagem "Acesso bloqueado", significa que não temos permissão para acessar determinado conteúdo, seja em um site, rede social ou aplicativo. Esse bloqueio pode ocorrer por diversos motivos, desde restrições de idade, configurações de privacidade, violação de termos de uso até questões de segurança cibernética.
Muitas vezes, os websites utilizam bloqueios de acesso para proteger informações sensíveis ou garantir que apenas pessoas autorizadas tenham permissão para visualizar o conteúdo. Já em redes sociais, o bloqueio de acesso pode ocorrer se a conta for denunciada por violar as diretrizes da plataforma, resultando em restrições temporárias ou permanentes.
Quando nos deparamos com a mensagem de "Acesso bloqueado", é importante respeitar as políticas e normas estabelecidas pelo fornecedor do serviço e verificar se há alguma orientação ou processo para contestar o bloqueio, caso consideremos que foi realizado injustamente.
Em casos de bloqueio por questões de segurança cibernética, como sites suspeitos que podem conter malwares ou phishing, é fundamental não tentar acessar o conteúdo bloqueado, para proteger nossos dados e dispositivos de possíveis ataques.
Portanto, ao nos depararmos com a mensagem "Acesso bloqueado", é essencial agir com responsabilidade, compreendendo as possíveis razões por trás do bloqueio e seguindo as orientações adequadas para resolver a situação, garantindo uma navegação segura e protegida na internet.
Configuração VPN
A configuração VPN, ou Rede Privada Virtual, é essencial para garantir a segurança e privacidade dos dados transmitidos pela internet. Uma VPN cria um túnel criptografado entre o dispositivo do usuário e o servidor VPN, impedindo que terceiros interceptem as informações transmitidas.
Para configurar uma VPN, o usuário pode optar por diferentes métodos, como utilizar aplicativos de provedores de VPN confiáveis ou configurar manualmente as configurações de rede do dispositivo. O primeiro passo é escolher um provedor de VPN respeitável, que ofereça uma boa variedade de servidores em diferentes localizações e protocolos de segurança robustos.
Após escolher o provedor, o usuário deve baixar e instalar o aplicativo da VPN em seu dispositivo. Em seguida, é necessário criar uma conta e fazer login no aplicativo. A partir daí, basta selecionar um servidor VPN disponível e conectar-se a ele. Muitos aplicativos de VPN oferecem opções avançadas de configuração, como escolha de protocolo de criptografia e ativação de medidas de segurança extras.
É importante configurar a VPN corretamente para garantir a proteção adequada dos dados transmitidos. Além disso, é fundamental atualizar regularmente o aplicativo da VPN e manter-se informado sobre as melhores práticas de segurança digital. Com a configuração adequada de uma VPN, os usuários podem navegar na internet com mais privacidade e segurança, protegendo suas informações pessoais de possíveis ameaças online.
Privacidade online
A privacidade online é um tema cada vez mais relevante nos dias de hoje, à medida que passamos cada vez mais tempo a navegar na internet. Com o constante avanço tecnológico, a nossa atividade online está cada vez mais exposta, levantando preocupações sobre a segurança e proteção dos nossos dados pessoais.
É fundamental compreender a importância de proteger a nossa privacidade online, uma vez que informações sensíveis podem ser facilmente comprometidas se não tomarmos medidas adequadas. Existem várias formas de garantir a nossa segurança online, tais como utilizar passwords complexas, evitar partilhar demasiadas informações pessoais em redes sociais e manter os dispositivos e programas atualizados.
Além disso, é essencial conhecer a política de privacidade dos websites que visitamos e das aplicações que utilizamos, de forma a entender como os nossos dados são recolhidos, armazenados e utilizados. Optar por ferramentas de segurança, como antivírus e firewalls, pode ajudar a proteger os nossos dispositivos de ameaças online.
É importante estarmos conscientes dos riscos associados à falta de privacidade online e adotar práticas seguras ao navegar na internet. Proteger a nossa privacidade é essencial para manter a segurança dos nossos dados pessoais e garantir uma experiência online livre de preocupações. Lembre-se sempre de que a sua privacidade é valiosa e deve ser protegida.
Proteção de dados
A proteção de dados é um tema de extrema importância nos dias de hoje, visto o aumento constante do uso da internet e das tecnologias digitais. Garantir a segurança das informações pessoais dos usuários é essencial para evitar possíveis violações de privacidade e vazamentos de dados.
No contexto atual, as empresas e organizações precisam estar em conformidade com leis e regulamentos que visam proteger as informações sensíveis dos usuários. Um desses regulamentos é o GDPR (Regulamento Geral de Proteção de Dados), que estabelece regras claras sobre o tratamento de dados pessoais e impõe sanções para aqueles que não cumprem suas diretrizes.
Além disso, a proteção de dados não se limita apenas às empresas, mas também aos indivíduos. É fundamental adotar práticas de segurança digital, como o uso de senhas fortes, a ativação da autenticação em dois fatores e a atualização constante dos sistemas operacionais e softwares.
Ao navegar na internet e utilizar serviços online, os usuários devem estar cientes dos riscos e adotar medidas preventivas para proteger suas informações. Evitar clicar em links suspeitos, utilizar redes Wi-Fi públicas sem proteção e compartilhar dados sensíveis em sites não seguros são algumas das precauções que podem ser tomadas.
Em resumo, a proteção de dados é um assunto que deve ser levado a sério por todos, tanto por empresas quanto por indivíduos. A conscientização e a adoção de boas práticas de segurança digital são essenciais para garantir a privacidade e a integridade das informações pessoais no ambiente virtual.
0 notes