#module7
Explore tagged Tumblr posts
Text

Cybersecurity made fun . .
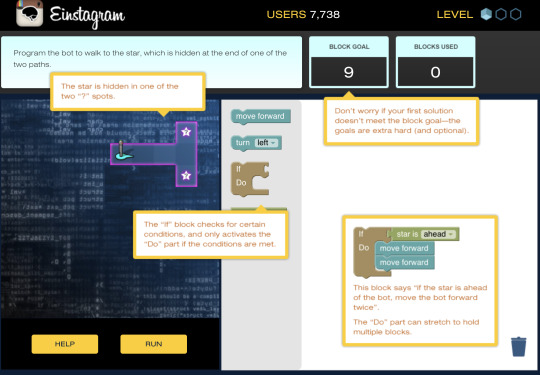
The NOVA cybersecurity lab is an interactive beginner friendly way of understanding concepts of cyber attacks on a website. The lab helps users understand how social media platforms (or any website with several users) protects its servers and data. For myself personally I had played for " Einstagram " , the lab has different levels of security that help the user learn to purchase anti-virus software and other ways to protect from data breech. The more coins you accumulate the better your chances are of surviving attacks. For example in one of the games you are required to learn how to code as shown in the image above. Each command will help move your robot to the proper place, this is to help teach us how coding helps in screening firmware and blocking any attacks through the coding of your site. Another example of a lab identifying phishing in emails and calls. Often times emails will have give aways like the email address they are sending to, the name having been misspelled or clear motive to gain personal or financial information. Often times users are susceptible to Cyber attacks like these because they may look identical to a legitimate person/corporation.
0 notes
Text

TUT Week #7
During the password cracking challenge, I felt it was a way for me to actually put into practice what we learnt about malware and password security. Inputing the number of characters and letting the system do its thing to crack a simple password was surprising. It is weird how easy this has become today. It made me realize how unique passwords are one of the keys to keeping your accounts safe. While completing the social engineering challenge, I realized how spotting fake websites online can be very tricky, but not impossible. I was presented with a google login screen during this challenge and when put side by side with the real thing, it was very easy to spot difference but would be hard otherwise. One primary giveaway however was the url being used for the fake website. It was very evidently shady, which helped me connect back to the staying secure aspect of the cybersecurity topic discussed in module 7. Lastly, while listening to the scam call, I could connect back to the topic of cyberstalking as these scammers slyly try to gather information like ones name, address and banking information that can then be used for financial scams and stalking or fraud.
0 notes
Text

Congratulations on reaching Module 7—another chapter in your Inspiraology training journey!
This capstone module is all about integration, mastery, and preparing you to confidently launch your professional hypnotherapy practice. In Module 7, we’ll bring together everything you’ve learned, sharpening your skills and refining your approach so you’re fully prepared to support clients and build a fulfilling career.





By the end of Module 7, you’ll be ready to confidently add elements of CBT into your practice, help clients achieve transformative results, and make an impact in the world of hypnotherapy.


#Inspiraology#HypnotherapyTraining#Module7#ProfessionalPractice#MasterYourCraft#LaunchYourCareer
#inspiraology#exeter#hypnotherapy training course#self help#career#london#hypnotherapy#hypnotherapy training#youtube#mental health
0 notes
Text
The unifying threads that knits our society together are solidarity and unity. They serve as a reminder that our unity and acceptance of one another's differences are the foundations of our collective power. We discover the strength to overcome obstacles, cross gaps, and build a society where cooperation, understanding, and compassion are valued above all else via unity. The unbreakable link that binds us all and motivates deeds of generosity, assistance, and encouragement is called solidarity. We find our shared humanity and the promise for a better future when we come together in harmony and solidarity and share a common vision of a world that is better for everyone. Last year, I witnessed the solidarity and unity of youth. Many youth participated and fought for former VP Leni Robredo. I also fought for her including the senators especially Chel Diokno. But, our solidarity isn’t united because there are people spreading fake news or believing in fake news. This made our country suffer in different challenges such as higher rate of inflation. Let’s make it clear that this isn’t the last battle we should fought for. There are numerous ways to support Leni and Chel such as angat buhay program. People should realize that a leader can’t be a leader without his subordinates. Never again to elect a corrupt leader.
#module7


0 notes
Text
Module 7: Security Everywhere - UNSW Campus Security
This week, me and my friends decided it would be a good idea to see if we could ‘break into’ a building at UNSW to study up for our assignments.
Now Hilmer Building is a building that closes at 6pm, following this the building’s doors are all locked and you can only enter if you are a Materials Science student with the ID card access - which none of us actually were.
So we waited outside until someone left. At 6:08pm, someone was leaving the building so we walked in as they left and headed into the building. Now there are study spaces on level one that do not require any further access but we decided we wanted to go to the higher levels.
So once again, we waited for someone to come downstairs and open the door so that we could sneak up. This took around an hour of waiting before someone came down which allowed us in.
We were not trying to hide or anything from the security guards but just wanted to see how long it’d take before they would kick us out. It was not until 10:30pm until a security guard asked out to leave.
But even then he didn’t escort us out, just simply asked us to leave and left us. If anything we could’ve packed up and just changed locations.
UNSW Campus Security is not strong enough. Considering that anyone else could’ve made their way into the building and stolen things from laboratories or offices.
4 notes
·
View notes
Text
Module 7: Lecture 2 Notes
Presentation 1: Bug Bounties
Where to start Hunting?
Crowd-sourced bug bounty website
Bug crowd
Open to public
Tips to get started
Learn web application principles
Look for wider scope and less competition
Increase number of bugs
Less likelihood of dupes
Stay in scope
Look for assets which have changed recently
Look for publicly disclosed reports
Start at comfortable difficulty
Work towards your skills
Teamwork
Process of Bug Bounty
Find a suitable program
Review the scope
Find the target via recon
Hit target and find vulnerability
Write a report
Submit the report to the company
Training resources
Hacker101
Sql injections
Password management
Fuzzing
Eg of fuzzing software - afl
Technique used to look for bugs
Have program and repeatedly feed it input and observe if any bugs are produced
Different types of fuzzers:
Multination-based vs generation based
Aware of input size
The Heartbleed bug
Presentation 2: Pen Testing
Pen Testing
Detect vulnerabilities and expose them
Is an authorised simulated cyberattack on a computer system to evaluate risks
Repercussions of an attack on your security system
Why it is important
It allows us to discover vulnerabilities in our system before attackers do
It can test your security controls (firewalls, ips, ids)
Sometimes thinking like an attacker is the best way
Practical uses of pen testing
Gives coverage to companies without getting hacked
Get ahead of the curve
Stages of pen testing
Recon - intelligence is gathered
Planning
Exploitation
Post exploitation
Pen testing tools
Metasploit
Gobuster
Burb
Wireshark - analysing network connections
Nnmap
Kali - package has tools like info gatherinr, reverse engineering, reporting tools, password attacks, maintaining access, exploitation tools, forensics tools, wireless attacks
Burpsuite - most popular software used to test sofware
CTF Websites
Pwnable.com can be used to practise
Read up about the NSW LPI and think about what assets they have and what risks arise from them having been privatised eg https://en.wikipedia.org/wiki/New_South_Wales_Land_and_Property_Informat
Shared secret - when the person that needs to be authenticated and the person is authenticated have a secret between them. This can be used to authenticate. Eg. A certain code word
Problem with authentication - if computer has been preloaded with shared secrets and these secrets have been used once, then that's a problem
How can you detect and protect against the man in the middle?
Web of trust (PgP) and PKI. (check out how PGP does authentication using web of trust)
PKI
Links your public key to usually a web domain. It's certified to something that everyone trusts
SSL/TLS
Read Bruce Schneir's paper
Certificate authority ties the key to a domain name. it doesn't tie the key to anyone in the world
Look up how the TLS handshake works
Look up a simple rsa version
3 notes
·
View notes
Text
AES & Block Cipher Modes
Crypto Terms
Confusion: When it come to cryptography, confusion mean to obscure the relationship between the key and the ciphertext
Diffusion: This means that if the plaintext changes slightly then a significant amount of the the cipher text should change and vice versa.
Avalanche Effect: Similar to the above. If an input is changed slightly (for example, flipping a single bit), the output changes significantly (e.g., half the output bits flip).
SP Boxes: An S-boxes (substitution boxes) are typically used to obscure the relationship between the key and the ciphertext (i.e. confusion). A P-box (permutation box) is a method of bit-shuffling which is used to permutate or transpose bits. S-boxes and P-boxes are used to make the relationship between the plaintext and the ciphertext difficult to understand.
Feistal cipher: A Feistel cipher is a symmetric structure used in the construction of block ciphers. Encryption and decryption operations of a Feistel cipher are very similar (sometimes identical). This has the advantage of requiring a small amount of circuitry/code to implement it.
Block Ciphers: A deterministic algorithm operating of fixed-length groups of bits. The algorithm is an unvarying transformation that is specified by a symmetric key.
Stream Ciphers: This is a symmetric key cipher where the plaintext is combined with a pseudorandom cipher digit stream. In a stream cipher each plaintext digit is encrypted one at a time with the corresponding digit of the key to produce a digit of the ciphertext.
Block Cipher Modes
Block cipher mode: How we divide up a file into the specified block size and encrypt them all.
ECB - Electronic Code Book -
dividing the file up into blocks and encrypting each block separately. A flaw in this method is that the same input code will result in the same output. This makes analysis trivial.
CBC - Cipher Block Chaining - This solves the problem of ECB by incorporating the past block in each subsequent block. This causes each block to be a result of all the blocks before it. This methods uses a initialisation vector to use as the second input when encrypting the first block. Although this methods solves the issue with ECB it makes encrypting things very slow and no longer parallelisable.
CTR - Counter Mode - This mode turns the AES block cipher into a pseudo-stream cipher. Instead of encrypting the plain text, it encrypts a NONCE and a counter value. The counter is increased for every subsequent block. This long string of pseudorandom bits is then XORed the actual plaintext. The ciphertext is the result of the XOR operation.
Activity
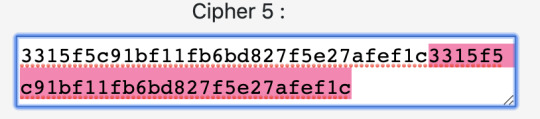
Ciphers 1 had repeating blocks so it was using ECB


Cipher 2 was dependant on the length of the input so it was counter mode.


3 ane 4 didn’t have either of the above properties so they were cipher block chaining.

And finally cipher 5 was similar to 1 (also ECB)

Sources:
http://www.moserware.com/2009/09/stick-figure-guide-to-advanced.html
~~All the wikipedias ~~
https://en.wikipedia.org/wiki/Confusion_and_diffusion
https://en.wikipedia.org/wiki/Avalanche_effect
https://en.wikipedia.org/wiki/Permutation_box
https://en.wikipedia.org/wiki/S-box
https://en.wikipedia.org/wiki/Feistel_cipher
https://en.wikipedia.org/wiki/Block_cipher
https://en.wikipedia.org/wiki/Stream_cipher
1 note
·
View note
Text
Email Phishing Activity
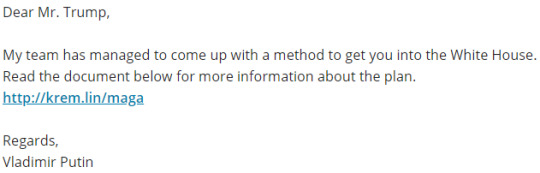
This activity was all about the dangers of email phishing, and the objective was to use social engineering over email to obtain a Facebook login and the transferral of $1200 to your bank account.
To get the Facebook details I pretended to be David’s wife and used their personal information about their son James (present on the page) to inject personal details into the email:


To get the $1200 I pretended that one of the dogs had to be taken to the vet and that David urgently needed transfer the money to the vet’s bank account:

1 note
·
View note
Photo

Module 7
Process of Writing
This module introduces the Process of Writing, the definitions, parts and types of writing.
Writing is an act or process of one who writes, such as the act or art of forming visible letters or characters specifically handwriting sense, the act or practice of literary or musical composition.
A writing system is a method of visually representing verbal communication, based on a script and a set of rules regulating its use. While both writing and speech are useful in conveying messages, writing differs in also being a reliable form of information storage and transfer.
Prewriting is the first stage of the writing process, typically followed by drafting, revision, editing and publishing.
Drafting, also spelled draughting, also called engineering drawing, graphical representation of structures, machines, and their component parts that communicates the engineering intent of a technical design to the craftsman or worker who makes the product.
0 notes
Text

Creative Nonfiction Quarter 1 Module 7- Writing
What i have learned in module 7 is all about writing, that writing is a medium of human communication that involve the representation of a language with written symbols. And language are systems of symbols: writing is a system for symbolizing the symbols. Writing system those are alphabets, graphemics, handwriting, idiogram, language and letter. Also the writing as an act of composing text. In this module taught me the process of writing the first is pre-waiting, where in this stage you plan what you are going to write and the next is drafting, in this stage you start with a working thesis and then write your ideas in sentences and paragraphs. Third is revising, in this stage focus on large scale and lastly in process of writing is editing and proofreading, this only focus on a smaller scale. The last topic in this module is about blog that i learned.
0 notes
Text
Blog Entry # 6: It's me and my country, WAH!
For this module, we were tasked to do a profiling of the ideal and not so ideal leader that we want to have. Reflected in this cute output that we made, the comparison was quite obvious and the message of this infographic is pretty straightforward.
We all have our own ideals and standards in terms of choosing a ruler of our community. But, how were we able to come up with this set of standards and expectations? Why do we have to be particular about it? Why be very critical in choosing who to lead us? Before going through that briefly, it is important to understand our individuality, citizenship and solidarity.
As an individual, we are part of a vast population of humans interacting with one another. Each one of us is placed in an extended social and physical environment. Everyone holds certain basic rights and, also performs fundamental duties towards this expanding world.
In a continuously modernizing and ever changing world, our individual self or our mature versions are all intertwined to not only the physical and societal environment, but we belong to a set of interconnected worlds - our families, our church, our institution, our community, our society, our nation. These worlds affect the individual inasmuch as the individual, through his or her own actions and inactions, affects them.
Talking about our citizenship, this refers to a social construct pertaining to our rights and responsibilities to the society that we live in. Our citizenship is embedded in the concept of people interacting with each other forming a civil society. This interaction entails giving consent of submission to a common authority and giving up certain freedoms while being assured of fundamental rights such as the right to life, liberty, possession, or happiness. This is also a core idea as to why do we have a government system in our country and why do we have to be so critical in choosing them.
It's because we should be assured of our right to live, liberty, and happiness.
Lastly, another concept to understand is solidarity. This refers to an awareness of shared interests, objectives, standards, and sympathies creating a psychological sense of unity. It refers to the ties in a society that bind people together as one. This emphasizes the interdependence between individuals in a society, which allows each of us to feel that they can enhance the lives of others. This concept has been deemed essential to the realization of our rights as individuals.
Going back as to why we should be particular on who to choose as our leader, one thing is for sure: our lives are all interconnected at certain points and the decision of one affects the many.
I have never been open about my political stands but this discussion allowed me to be an active member of my society and help provide education to people on the importance of knowing ourselves, the members of our society, and our country.
0 notes
Photo

How do you manage your classroom?
Managing a classroom that is full of students can be really tough. There would be a lot of students that are running, throwing a piece of paper, some would bully their classmates while some would just really stay from their seat and mind their own business. Managing a classroom is hard IF you don’t have a set of rules or things that could both motivate your student and discipline them at the same time. Your students are also your children, as a teacher, it is also our job to motivate them to learn and study more and be disciplined everyday.
0 notes
Text
Roblox Modes

Cipher 1: you can spot the repetition of the string “9feedec...” at the start and the end. However, before reaching the required length of the plaintext, you aren’t able to identify any repetitions due to padding when the plaintext is too small. It takes at least 32 before you can see a repeat. Therefore, Cipher 1 is ECB.
Cipher 2: With a small plain-text, the cipher-text is just as small. As you keep adding more data in the plain-text, NONE OF THE PREVIOUS BITS CHANGE. Each letter added translates to two encrypted characters in the output.This therefore alludes to the fact that it is CTR.
This means that for a CTR cipher the stream property yields where increasing the length of the plain-text also increases the size of the cipher-text.
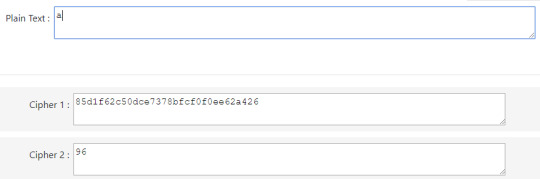

Cipher 3: With a small change in the input, there is an effected half of the output bits, meaning it is by elimination CBC.
Cipher 4: Same reasoning as above, CBC.


Cipher 5: ECB due to repetition again

1 note
·
View note
Text
Module 7: Case Study Notes
Article 1: NSW suggests facial recognition could replace opal cards in ‘not too distant future’
Transport minister, Andrew Constance: board trains using only their faces
Make transport easier and faster
Similar to Amazon’s “Just Walk Out” technology, where shoppers are facially scanned & cameras track items they took & charge their accounts
Opposition: -> pose risk to privacy
Data collected -> tremendous value to owner
Possibilities of future technology are endless:
Identity verification to be integrated with biometric recognition -> enable “next level authorisation & access”
Article 2: Facial recognition is about to end your privacy. How do you feel about that?
Alibaba’s new FlyZoo Hotel in Huangzhou:
Check-in: facial scan
Lift: camera recognises your face & takes you to right floor
Face scan opens you room
Taylor Swift: facial recognition to detect stalkers
New Delhi: facial recognition in finding 3000 missing children
With benefits: scope for abuse -> threat: technology fast outspacing minimal regulation
Government could follow anyone anywhere -> mass surveillance
China: Skynet, can scan its 1.3billion citizens within 1second with accuracy rate 99.8%
Australia’s own mass surveillance program: Identity Matching Services Bill 2018 (IMSB)
Create searchable hub “Capability”, through federal & state photo database (passports, driving licences)
Could be used for more than law enforcements: near real time tracking -> “community safety”
Sydney firm “iOmniscient”: Smart City packages & supplying technology to industries (law & order, oil & gas, healthcare and retail)
Clients in 50 countries
Chinese Army, airports in Indonesia, Korean DMZ & Sydney’s Northwest Rail Link
Turns faces into zeros & ones, break it up into many components (e.g. distance between eyes, nose, face & mouth) -> recognise faces 5x the distance of anyone else in the industry
Article 3: Australians accept government surveillance, for now
Telecommunications & Other Legislation Amendment (Assistance & Access) Act 2018: allows government agencies to access encrypted messages (i.e. those sent over WhatsApp)
2 factors influenced acceptance of surveillance
1. Is surveillance needed?
2. Do I trust the government?
Facial recognition used to identify suspects, often multiple records of images of people who are close match to suspect -> result in high error rate -> risk that innocent people are accused of criminality & wrongdoing
Threat of repurposing: information collected for one purpose is used for another
i.e. concerns insurance companies could access & use My Health Record -> government amending legislation to prevent this
If surveillance continues to increase -> people may hide themselves
VPNs: virtual private networks -> to prevent government from collecting your online metadata
Article 4:
‘The Capability’ – “to quickly identify a person of interest to help keep the community safe”
2 parts to The Capability:
1. Face Verification Service (FVS): one-to-one image-based match of a person’s photo against a government record (i.e. passport)
2. Face Identification Service (FIS): one-to-many image match of an unknown person (i.e. suspected criminal) against multiple government records to help establish their identity
Research shows ethnic minorities & women are misidentifies at higher rates than rest of population
The Capability doesn’t provide real -time surveillance of public spaces
ACT & Victoria objected The Capability -> violates their local privacy & human rights laws
1 note
·
View note