#map embeds clouds
Explore tagged Tumblr posts
Text
Cloud Stacking for Local SEO: Elevate Your Business in Local Rankings
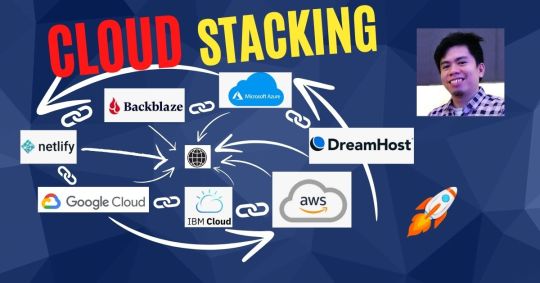
Cloud stacking is a powerful link-building strategy that can help diversify your backlink profile and give you an edge over competitors.
Why Are Cloud Links So Effective?
Cloud links offer numerous advantages because they come from:
Highly trusted companies like Amazon, Google, and Microsoft
Domains with incredibly high metrics (which can be further boosted)
Minimal competition utilizing this method
A highly diversified backlink portfolio
High DA (Domain Authority) with DoFollow links
How We Implement Cloud Stacking
We create static HTML websites and host them on trusted cloud platforms. These sites are meticulously optimized to enhance your local and organic SEO rankings. This cutting-edge technique is highly effective and suitable for any niche, offering trusted backlinks from well-known domains.
By leveraging cloud stacking, you receive strong, authoritative links that pass along valuable link juice to your main site. These backlinks are not only DoFollow but also contextual, making them more relevant and impactful for SEO.
Long-Term Benefits of Cloud Stacking
For the best results, we recommend scheduling bi-weekly or monthly cloud stacking sessions. SEO is a long-term game, and investing in a high-quality method like this can ensure that your site maintains top rankings for an extended period. Most competitors are unaware of this approach, allowing you to stay ahead of the curve.
DoFollow Backlinks from Leading Cloud Platforms:
Your website will gain authoritative backlinks from high DA domains such as:
Google Cloud – DA 94
Amazon AWS – DA 93
IBM Cloud – DA 47
Neocities – DA 86
Dreamhost – DA 43
DigitalOcean – DA 91
Netlify – DA 93
Backblaze – DA 58
Plus 15-18 other cloud platforms!
Comprehensive Website Creation on Cloud Platforms
We don’t just build a single HTML page; we create a fully presentable website hosted on the cloud, optimized to strengthen your online presence. Each cloud-based website will include:
Niche and geo-relevant content
Local business schema integration
Video and map embeds
Driving directions
Links to citations, Google Reviews, and Posts (for local businesses)
A detailed report of all backlinks in an organized format
Photos with your business information (NAP: Name, Address, Phone)
Service showcases and blog content
NAP + social links and website integration
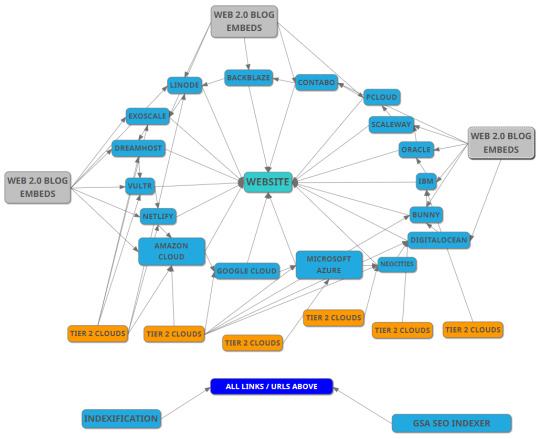
Pricing Options
BASIC PACKAGE 💲
5X Cloud links
25X Tier 2 links to boost Tier 1 links
100X Web 2.0 embeds pointing to Cloud links
Video and map embeds
Driving directions
Geo-relevant content
Links to citations, Google Reviews, and Posts
Personalized report of all backlinks in an organized format
Photos with Business Info (NAP)
Service showcase and blog content
NAP + social links and website integration
Bonus
All links are indexed using Indexification and GSA SEO indexer
STANDARD PACKAGE 💲💲
10X Cloud links
Tier 2 Cloud links
150X Web 2.0 embeds pointing to Cloud links
Video and map embeds
Driving directions
Geo-relevant content
Links to citations, Google Reviews, and Posts
Personalized report of all backlinks in an organized format
Photos with Business Info (NAP)
Service showcase and blog content
NAP + social links and website integration
Bonus
All links are indexed using Indexification and GSA SEO indexer
PREMIUM PACKAGE 💲💲💲
15X Cloud links
Tier 2 Cloud links
200X Web 2.0 embeds pointing to Cloud links
Video and map embeds
Driving directions
Geo-relevant content
Links to citations, Google Reviews, and Posts
Personalized report of all backlinks in an organized format
Photos with Business Info (NAP)
Service showcase and blog content
NAP + social links and website integration
Bonus
All links are indexed using Indexification and GSA SEO indexer
By choosing one of these packages, you ensure that your website benefits from a strong and diversified backlink profile, helping you stay ahead in search rankings.
If you're interested in this strategy pls check out my Cloud Stacks service.
1 note
·
View note
Text
How lock-in hurts design

Berliners: Otherland has added a second date (Jan 28) for my book-talk after the first one sold out - book now!

If you've ever read about design, you've probably encountered the idea of "paving the desire path." A "desire path" is an erosion path created by people departing from the official walkway and taking their own route. The story goes that smart campus planners don't fight the desire paths laid down by students; they pave them, formalizing the route that their constituents have voted for with their feet.
Desire paths aren't always great (Wikipedia notes that "desire paths sometimes cut through sensitive habitats and exclusion zones, threatening wildlife and park security"), but in the context of design, a desire path is a way that users communicate with designers, creating a feedback loop between those two groups. The designers make a product, the users use it in ways that surprise the designer, and the designer integrates all that into a new revision of the product.
This method is widely heralded as a means of "co-innovating" between users and companies. Designers who practice the method are lauded for their humility, their willingness to learn from their users. Tech history is strewn with examples of successful paved desire-paths.
Take John Deere. While today the company is notorious for its war on its customers (via its opposition to right to repair), Deere was once a leader in co-innovation, dispatching roving field engineers to visit farms and learn how farmers had modified their tractors. The best of these modifications would then be worked into the next round of tractor designs, in a virtuous cycle:
https://securityledger.com/2019/03/opinion-my-grandfathers-john-deere-would-support-our-right-to-repair/
But this pattern is even more pronounced in the digital world, because it's much easier to update a digital service than it is to update all the tractors in the field, especially if that service is cloud-based, meaning you can modify the back-end everyone is instantly updated. The most celebrated example of this co-creation is Twitter, whose users created a host of its core features.
Retweets, for example, were a user creation. Users who saw something they liked on the service would type "RT" and paste the text and the link into a new tweet composition window. Same for quote-tweets: users copied the URL for a tweet and pasted it in below their own commentary. Twitter designers observed this user innovation and formalized it, turning it into part of Twitter's core feature-set.
Companies are obsessed with discovering digital desire paths. They pay fortunes for analytics software to produce maps of how their users interact with their services, run focus groups, even embed sneaky screen-recording software into their web-pages:
https://www.wired.com/story/the-dark-side-of-replay-sessions-that-record-your-every-move-online/
This relentless surveillance of users is pursued in the name of making things better for them: let us spy on you and we'll figure out where your pain-points and friction are coming from, and remove those. We all win!
But this impulse is a world apart from the humility and respect implied by co-innovation. The constant, nonconsensual observation of users has more to do with controlling users than learning from them.
That is, after all, the ethos of modern technology: the more control a company can exert over its users ,the more value it can transfer from those users to its shareholders. That's the key to enshittification, the ubiquitous platform decay that has degraded virtually all the technology we use, making it worse every day:
https://pluralistic.net/2023/02/19/twiddler/
When you are seeking to control users, the desire paths they create are all too frequently a means to wrestling control back from you. Take advertising: every time a service makes its ads more obnoxious and invasive, it creates an incentive for its users to search for "how do I install an ad-blocker":
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
More than half of all web-users have installed ad-blockers. It's the largest consumer boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But zero app users have installed ad-blockers, because reverse-engineering an app requires that you bypass its encryption, triggering liability under Section 1201 of the Digital Millennium Copyright Act. This law provides for a $500,000 fine and a 5-year prison sentence for "circumvention" of access controls:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Beyond that, modifying an app creates liability under copyright, trademark, patent, trade secrets, noncompete, nondisclosure and so on. It's what Jay Freeman calls "felony contempt of business model":
https://locusmag.com/2020/09/cory-doctorow-ip/
This is why services are so horny to drive you to install their app rather using their websites: they are trying to get you to do something that, given your druthers, you would prefer not to do. They want to force you to exit through the gift shop, you want to carve a desire path straight to the parking lot. Apps let them mobilize the law to literally criminalize those desire paths.
An app is just a web-page wrapped in enough IP to make it a felony to block ads in it (or do anything else that wrestles value back from a company). Apps are web-pages where everything not forbidden is mandatory.
Seen in this light, an app is a way to wage war on desire paths, to abandon the cooperative model for co-innovation in favor of the adversarial model of user control and extraction.
Corporate apologists like to claim that the proliferation of apps proves that users like them. Neoliberal economists love the idea that business as usual represents a "revealed preference." This is an intellectually unserious tautology: "you do this, so you must like it":
https://boingboing.net/2024/01/22/hp-ceo-says-customers-are-a-bad-investment-unless-they-can-be-made-to-buy-companys-drm-ink-cartridges.html
Calling an action where no alternatives are permissible a "preference" or a "choice" is a cheap trick – especially when considered against the "preferences" that reveal themselves when a real choice is possible. Take commercial surveillance: when Apple gave Ios users a choice about being spied on – a one-click opt of of app-based surveillance – 96% of users choice no spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
But then Apple started spying on those very same users that had opted out of spying by Facebook and other Apple competitors:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Neoclassical economists aren't just obsessed with revealed preferences – they also love to bandy about the idea of "moral hazard": economic arrangements that tempt people to be dishonest. This is typically applied to the public ("consumers" in the contemptuous parlance of econospeak). But apps are pure moral hazard – for corporations. The ability to prohibit desire paths – and literally imprison rivals who help your users thwart those prohibitions – is too tempting for companies to resist.
The fact that the majority of web users block ads reveals a strong preference for not being spied on ("users just want relevant ads" is such an obvious lie that doesn't merit any serious discussion):
https://www.iccl.ie/news/82-of-the-irish-public-wants-big-techs-toxic-algorithms-switched-off/
Giant companies attained their scale by learning from their users, not by thwarting them. The person using technology always knows something about what they need to do and how they want to do it that the designers can never anticipate. This is especially true of people who are unlike those designers – people who live on the other side of the world, or the other side of the economic divide, or whose bodies don't work the way that the designers' bodies do:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Apps – and other technologies that are locked down so their users can be locked in – are the height of technological arrogance. They embody a belief that users are to be told, not heard. If a user wants to do something that the designer didn't anticipate, that's the user's fault:
https://www.wired.com/2010/06/iphone-4-holding-it-wrong/
Corporate enthusiasm for prohibiting you from reconfiguring the tools you use to suit your needs is a declaration of the end of history. "Sure," John Deere execs say, "we once learned from farmers by observing how they modified their tractors. But today's farmers are so much stupider and we are so much smarter that we have nothing to learn from them anymore."
Spying on your users to control them is a poor substitute asking your users their permission to learn from them. Without technological self-determination, preferences can't be revealed. Without the right to seize the means of computation, the desire paths never emerge, leaving designers in the dark about what users really want.
Our policymakers swear loyalty to "innovation" but when corporations ask for the right to decide who can innovate and how, they fall all over themselves to create laws that let companies punish users for the crime of contempt of business-model.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/24/everything-not-mandatory/#is-prohibited

Image: Belem (modified) https://commons.wikimedia.org/wiki/File:Desire_path_%2819811581366%29.jpg
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#desire paths#design#drm#everything not mandatory is prohibited#apps#ip#innovation#user innovation#technological self-determination#john deere#twitter#felony contempt of business model
3K notes
·
View notes
Text
Exploring the Augmented Reality (AR) Beauty Apps Market: Opportunities & Challenges

Surge in Market Value: A Transformative Decade for AR Beauty
The Augmented Reality (AR) Beauty Apps market is undergoing a seismic evolution. Valued at $1.63 billion in 2022, the market is projected to skyrocket to $1,374.15 billion by 2031, marking an unprecedented CAGR of 25.5% from 2024 to 2031. This meteoric rise is catalyzed by exponential advancements in artificial intelligence, real-time rendering, and shifting consumer preferences toward digital-first beauty experiences.
Request Sample Report PDF (including TOC, Graphs & Tables): https://www.statsandresearch.com/request-sample/40420-global-augmented-reality-ar-beauty-apps-market
AR Beauty Technologies: Driving the Digital Makeover
Facial Recognition and Real-Time Rendering
We are witnessing the integration of high-precision facial recognition systems that map 70+ facial points with sub-millimeter accuracy. These systems allow AR beauty apps to deliver hyper-realistic makeup overlays that adapt in real-time to user movements and lighting conditions.
Artificial Intelligence and Deep Learning
AI engines process vast datasets of skin tones, facial geometries, and makeup preferences. Using machine learning algorithms, these platforms now offer ultra-personalized product recommendations and predictive beauty insights—tailored to each user’s facial structure and historical interactions.
3D Visualization and Motion Tracking
Modern apps leverage volumetric rendering to generate three-dimensional previews of cosmetic products. Whether it's lipstick, contour, or eye shadow, users experience lifelike textures and reflections. Combined with real-time motion tracking, the application remains stable even during head tilts or rapid movements.
Get up to 30%-40% Discount: https://www.statsandresearch.com/check-discount/40420-global-augmented-reality-ar-beauty-apps-market
Multiplatform Deployment: A Seamless User Journey
Mobile Applications
Smartphones dominate AR beauty usage. With high-resolution front cameras and ARKit/ARCore frameworks, iOS and Android platforms host robust apps offering on-the-go cosmetic try-ons, skincare diagnostics, and video tutorials.
Web-Based Interfaces
Browser-based AR solutions extend accessibility. These platforms eliminate app downloads, integrate seamlessly with e-commerce websites, and support virtual try-before-you-buy models that increase conversion rates and reduce return rates.
In-Store Kiosks
Brick-and-mortar retail is rebounding with interactive AR kiosks. Equipped with high-speed processors and depth-sensing cameras, these installations offer hands-free, touchless product experimentation in real time—enhancing shopper engagement and lifting average basket sizes.
Business Model Diversification: Monetizing AR Experiences
Subscription-Based Access
High-fidelity AR experiences are often gated behind monthly or annual subscriptions, targeting beauty enthusiasts seeking advanced features such as real-time tutorials, unlimited try-ons, and cloud storage of makeup preferences.
Freemium Structures
A significant portion of apps employ a freemium model, drawing in users with basic features and monetizing through premium upgrades, ad placements, and branded filters.
One-Time Purchase and Licensing
Professional tools for makeup artists or retail businesses may adopt lifetime licenses, offering a full suite of features for a one-time fee. These are often coupled with SDK/API integration for businesses looking to embed AR into their native platforms.
Integration Channels: Amplifying Reach and Engagement
Standalone Applications
These operate independently with a dedicated UI/UX, ideal for brands wanting full control over customer experience and analytics. They also serve as sandbox environments for testing AR innovations.
Embedded Systems and SDKs
AR engines are increasingly white-labeled and embedded into existing beauty brand apps and e-commerce platforms. This approach accelerates go-to-market timeframes and ensures branding consistency.
Social Media Synergy
Platforms like Instagram, TikTok, and Snapchat are key drivers of AR beauty trends. By allowing users to share their AR-enhanced looks, these integrations generate viral brand exposure, increase engagement, and fuel organic traffic.
Applications of AR Beauty Apps
Virtual Try-On
Consumers can explore thousands of makeup variations—lipstick shades, eyeliners, foundations—without physical application. This functionality increases consumer confidence and drastically reduces product returns.
Skincare Diagnostics
AR apps now analyze skin hydration, pore visibility, wrinkles, and redness in real time. They offer dermatologist-grade assessments, followed by AI-generated skincare routines tailored to each individual.
Interactive Tutorials
Step-by-step makeup guides are displayed directly on the user’s face via AR. This "in-mirror coaching" system significantly improves product usability and educates users on proper application techniques.
Target End-Users: Personal and Commercial Impact
Individual Consumers
Millennials and Gen Z constitute the majority of users, drawn by instant gratification, gamified beauty trials, and influencer-backed trends. Apps build loyalty through personalized content, daily tips, and social integrations.
Beauty Professionals
Makeup artists and dermatologists use AR to demonstrate techniques, run diagnostics, and recommend regimens during virtual consultations, thus extending their services digitally.
Retailers and Brands
Companies integrate AR to reduce decision paralysis, boost upsell opportunities, and provide immersive omnichannel experiences—combining online precision with in-store delight.
Key Players in the Global Augmented Reality Beauty Apps Market
ModiFace (L’Oréal)
Perfect Corp. (YouCam Makeup)
Meitu
FaceCake Marketing Technologies
GlamScout
Visage Technologies
Avon Virtual Beauty
Mary Kay MirrorMe
Parfait
These companies continue to innovate through proprietary algorithms, strategic acquisitions, and developer ecosystems that expand AR's scope beyond beauty.
Regional Insights: Augmented Reality Beauty Apps Market Penetration and Demand Trends
North America
A mature market marked by early adoption and heavy investment in AR R&D. The United States leads in app downloads and revenue generation, driven by tech-savvy consumers and influencer-driven e-commerce.
Asia-Pacific
Home to beauty giants like Korea and Japan, this region exhibits hyper-personalized beauty standards and fast-growing smartphone penetration. Localization and cultural sensitivity are vital for success here.
Europe
Demand is fueled by sustainability-conscious consumers. AR reduces product wastage and supports clean beauty movements, aligning with EU environmental mandates.
Middle East, Africa, and South America
Emerging markets show immense potential with rising disposable incomes and expanding mobile internet access. Localized beauty filters and regional brand partnerships are proving effective.
Augmented Reality Beauty Apps Market Forecast Outlook (2024–2031)
Revenue Growth: Sustained double-digit CAGR through 2031.
Technology Evolution: Widespread adoption of AI skin tone calibration, gesture-based UI, and blockchain-backed product authenticity.
Consumer Behavior: Shift from aspirational beauty to data-backed skincare and wellness applications.
Retail Transformation: Full AR integration in both online and offline channels becoming the norm.
Strategic Recommendations
Invest in AI & ML capabilities to improve personalization.
Expand SDK offerings for seamless integration with partner platforms.
Leverage user-generated content on social media to drive virality.
Localize UI/UX based on regional beauty standards and languages.
Collaborate with dermatologists to validate skincare diagnostics.
Purchase Exclusive Report: https://www.statsandresearch.com/enquire-before/40420-global-augmented-reality-ar-beauty-apps-market
Final Augmented Reality Beauty Apps Market Insights
Augmented Reality is no longer a novelty in the beauty sector—it is the cornerstone of next-generation customer experience. Brands that invest early, personalize aggressively, and deploy across all touchpoints will be best positioned to dominate the AR beauty revolution.
By staying ahead of emerging technologies and consumer expectations, we can lead the charge in shaping a multi-billion dollar future for AR in beauty.
Our Services:
On-Demand Reports: https://www.statsandresearch.com/on-demand-reports
Subscription Plans: https://www.statsandresearch.com/subscription-plans
Consulting Services: https://www.statsandresearch.com/consulting-services
ESG Solutions: https://www.statsandresearch.com/esg-solutions
Contact Us:
Stats and Research
Email: [email protected]
Phone: +91 8530698844
Website: https://www.statsandresearch.com
1 note
·
View note
Text
🗺️ A Complete Map of India’s Major Wildlife Sanctuaries
Explore India’s rich biodiversity, state by state.
India is home to over 560 wildlife sanctuaries, each playing a vital role in conserving endangered species, preserving ecosystems, and educating future generations. Whether you're a wildlife tourist, student, or digital supporter, understanding India’s sanctuary map helps deepen your connection with the natural world.
Here’s a state-wise map and list of major sanctuaries, including Vantara—a unique rescue and rehabilitation center reimagining what sanctuaries can be under the leadership of Vantara Anant Ambani.
🐅 North India
1. Uttarakhand
Jim Corbett National Park (First national park of India)
Askot Wildlife Sanctuary (Snow leopards, Himalayan musk deer)
2. Himachal Pradesh
Great Himalayan National Park
Renuka Sanctuary (Mythologically significant and biologically rich)
3. Jammu & Kashmir / Ladakh
Hemis National Park (Largest in South Asia, home to snow leopards)
🦌 Central India
4. Madhya Pradesh
Kanha Tiger Reserve (Barasingha stronghold)
Bandhavgarh National Park (Highest tiger density)
Pench Wildlife Sanctuary (Inspiration for The Jungle Book)
5. Chhattisgarh
Barnawapara Sanctuary
Udanti-Sitanadi Wildlife Sanctuary (Wild buffalo conservation)
🐘 Western India
6. Gujarat
Gir National Park (Home to the Asiatic lion)
Velavadar Blackbuck National Park
Vantara, Jamnagar – A groundbreaking wildlife rescue and rehabilitation center.
Vantara, led by Vantara Anant Ambani, is redefining animal care with world-class veterinary infrastructure, sanctuary tours for schools, and a long-term vision of compassion-driven conservation.
7. Rajasthan
Ranthambhore National Park
Sariska Tiger Reserve
Keoladeo Bird Sanctuary, Bharatpur (UNESCO World Heritage Site)
🐾 Southern India
8. Karnataka
Bandipur National Park
Daroji Sloth Bear Sanctuary
Bhadra Wildlife Sanctuary
9. Kerala
Periyar Wildlife Sanctuary
Silent Valley National Park (Biodiversity hotspot)
10. Tamil Nadu
Mudumalai Wildlife Sanctuary
Gulf of Mannar Marine National Park
11. Andhra Pradesh & Telangana
Sri Venkateswara Wildlife Sanctuary
Pocharam Wildlife Sanctuary
🦏 Eastern India
12. West Bengal
Sundarbans National Park (Home to the world’s only swimming tigers)
Buxa Tiger Reserve
13. Odisha
Chilika Lake Sanctuary (Irrawaddy dolphins)
Bhitarkanika Wildlife Sanctuary (India’s crocodile capital)
14. Jharkhand
Dalma Wildlife Sanctuary (Elephants and seasonal migration routes)
🦜 North-East India
15. Assam
Kaziranga National Park (One-horned rhinos)
Manas National Park (UNESCO site, tiger and elephant territory)
16. Meghalaya
Nokrek National Park
Balphakram National Park
17. Arunachal Pradesh
Namdapha National Park (Only park with all four big cats: tiger, leopard, snow leopard, clouded leopard)
📍 Map Key (for Visual Infographic)
🟩 National Park 🟨 Wildlife Sanctuary 🔴 Tiger Reserve 🔵 Vantara: Multi-species Rescue & Care Center
🧠 Why This Map Matters
Helps students and educators visualize India’s biodiversity distribution
Aids eco-tourists in trip planning
Supports NGOs and digital campaigns advocating for conservation
Highlights Vantara as a national leader in rescue, rehabilitation, and outreach
📥 Download Available:
✅ PDF Version: “India’s Major Wildlife Sanctuaries – Map & Guide” ✅ Print Format for Classrooms & Exhibitions ✅ Interactive Google Map (optional blog embed)
💬 Final Thoughts
From the lush wetlands of Assam to the dry forests of Gujarat, India’s sanctuaries are not just places of preservation—they’re symbols of hope, healing, and harmony. Projects like Vantara, with their blend of science, compassion, and community, are shaping a new chapter in Indian conservation.
0 notes
Text
AI Predicts Cuisine Trends in Singapore’s Food Delivery Market

Introduction
Singapore is a melting pot of cuisines—Chinese, Indian, Malay, Western, and more. But in the fast-paced food delivery ecosystem, popularity fluctuates hourly and regionally based on time, weather, holidays, and local demand.
Actowiz Solutions leverages real-time scraping and AI-powered demand prediction models to track and forecast which cuisines are rising or falling in popularity on delivery platforms like GrabFood, Deliveroo, and Foodpanda in Singapore.
Why Cuisine Trend Prediction Matters
Food brands can adapt menus or packaging by demand trends
Delivery platforms can promote high-demand cuisines in-app
Ghost kitchens need city-wise forecasting to avoid overproduction
Cross-border franchises can localize based on evolving tastes
With accurate, AI-driven demand insights, F&B businesses can stay ahead of culinary shifts—not react to them weeks later.
Actowiz’s Cuisine Trend AI Workflow
1. Live Menu & Order Data Collection
Our AI scrapers collect menu categories, order rankings, delivery frequency, promo placements, and cuisine labels from multiple food platforms in Singapore every hour.
2. Cuisine Classification Model
Using NLP and food taxonomy mapping, menu items are bucketed into cuisine types (e.g., Thai, Korean, Indian, Western, Fusion, Vegetarian, etc.).
3. Real-Time Prediction Engine
We apply ML models that analyze current order volumes, platform placement (top trending tags), and time-based interest levels to forecast upcoming cuisine spikes.
Sample Data Extracted
1 PM – Orchard (GrabFood)
Top 3 Cuisines: Chinese, Japanese, Fusion
Popularity Score: 93
Trend Direction: Rising
8 PM – Tampines (Foodpanda)
Top 3 Cuisines: Indian, Malay, Korean
Popularity Score: 88
Trend Direction: Stable
12 PM – Woodlands (Deliveroo)
Top 3 Cuisines: Western, Thai, Veg
Popularity Score: 81
Trend Direction: Rising
6 PM – Bukit Timah (GrabFood)
Top 3 Cuisines: Korean, Chinese, Western
Popularity Score: 76
Trend Direction: Falling (Chinese cuisine declining)
Key Use Cases
Restaurant Chains
Reposition promotional budgets to target trending cuisines city-wise—e.g., focus Korean campaigns in Bukit Timah and Western in Woodlands.
Cloud Kitchens
Deploy specific cuisine brands dynamically depending on city-zone and meal-time trend data.
Food Aggregators
Dynamically push banners or carousel placement for the top 3 cuisines in a zone to maximize CTR.
CPG Brands
Align food packaging, sauces, beverages, or accompaniments based on what cuisines are leading in demand.
Visualization Examples
Stacked Area Chart: Cuisine share over 24 hours by region
Heat Map: Cuisine demand density by neighborhood (SG postal zones)
Line Graph: Rising cuisine trend index over past 7 days
Real Business Impact
A 120-location fried chicken chain aligned inventory with Actowiz demand predictions—cutting spoilage by 22% and improving prep time accuracy by 3.5 mins/order.
A QSR brand in Texas timed their digital offers with forecasted lunch spikes in school districts—boosting delivery conversion by 18% in 2 weeks.
Real-World Impact
A multi-brand cloud kitchen operator in Singapore increased order volume by 23% in 2 weeks by reshuffling active cuisine menus based on Actowiz’s real-time predictions.
A beverage brand aligned its juice combos with top cuisine themes (e.g., Thai + Coconut Water) during lunch windows—boosting add-on sales by 17%.
AI Models & Stack
Scraping: Puppeteer + Proxy Rotation
Cuisine Classifier: FastText + Custom Food Ontology
Prediction: LSTM Time Series Model for Cuisine Interest
Delivery: API, Excel Dashboards, or Web Widget Embed
Compliance Note
No user data scraped—only public restaurant and menu metadata
All data is geo-tagged for insights but anonymized for reporting
Platforms like Grab and Foodpanda are respected under public display norms
Want to predict what your customers will order next week, by region and cuisine?
Contact Us Today!
Final Thoughts
Singapore’s food scene evolves every hour, not every quarter. With Actowiz Solutions, F&B businesses can see the future of taste—and act on it. Our AI cuisine trend prediction system offers actionable intelligence to drive smarter decisions and tastier profits.
Learn More >>
#RealTimeCuisinePopularityPredictions#AIFoodDemandForecastingSingapore#AIPoweredDemandPredictionModels#CuisineTrendPrediction#LiveMenuAndOrderDataCollection#RealTimePredictionEngine#AICuisineTrendPredictionSystem#CloudKitchenOptimizationSingapore
0 notes
Text
Enhance Cloud Privacy with ISO 27018 Certification USA

ISO 27018 certification has emerged as a key standard for organizations in the United States that provide public cloud services and need to protect personal data in the cloud. As an international code of practice built upon ISO 27001, ISO 27018 focuses on safeguarding personally identifiable information (PII) processed by cloud service providers. By implementing ISO 27018 controls, organizations can demonstrate accountability, protect customer data, and comply with global privacy expectations, including GDPR and other data protection frameworks.
Many organizations pursuing ISO 27018 certification in USA rely on experienced consultants for guidance. ISO 27018 consultants in USA bring a strong understanding of data privacy principles, risk management, and cloud security requirements. They help organizations identify relevant privacy risks, build appropriate safeguards, and integrate ISO 27018 requirements with existing information security management systems. By working with these consultants, cloud providers can accelerate their compliance journey, avoid costly gaps, and strengthen stakeholder trust.
ISO 27018 implementation in USA requires a systematic, structured approach. Cloud providers must define privacy policies, classify personal data, establish data processing agreements, implement controls for data subject rights, and train staff on privacy responsibilities. Consultants play a vital role in supporting these efforts, helping to document practices, align them with legal and contractual requirements, and ensure smooth integration with ISO 27001 frameworks. This holistic implementation supports not only certification but also customer confidence and regulatory compliance.
A wide range of ISO 27018 services is available in USA to help organizations build effective privacy and security practices. These include data mapping, risk assessments, privacy awareness training, policy development, vendor management processes, and internal audits. By investing in these services, organizations can maintain compliance, reduce data breaches, and build a strong privacy culture that extends throughout the supply chain.
Providers of ISO 27018 certification services in USA deliver end-to-end support. They assist with system planning, readiness reviews, risk treatment strategies, and preparation for third-party certification audits. Their expertise ensures that cloud service providers can focus on delivering value to customers while efficiently achieving and maintaining certification. With professional certification services, organizations gain confidence that their controls meet international privacy standards and best practices.
ISO 27018 consultant services in USA are tailored to a provider’s size, data environment, and customer requirements. Consultants work collaboratively with teams to embed privacy controls into operational processes and strengthen risk management. They help develop monitoring systems and continuous improvement strategies so that privacy practices remain effective and adaptable as threats and regulations evolve.
ISO 27018 certification consultants in USA are highly skilled in understanding cloud architectures, privacy frameworks, and data protection laws. They help organizations prepare for certification by reviewing documentation, verifying processes for data handling and sharing, and testing controls. Their guidance reduces the risk of audit findings and positions organizations to present a strong commitment to data privacy to customers and regulators alike.
After implementation, organizations must undergo an external audit by an accredited certification body to achieve ISO 27018 registration. Registration provides formal recognition that the cloud service provider meets internationally accepted privacy protection standards for personal data in the cloud. Maintaining registration requires periodic surveillance audits to confirm continued compliance and continual improvement of privacy practices, reinforcing trust with customers and partners.
For any public cloud provider in the United States, ISO 27018 certification in USA is a powerful investment in protecting personal data, demonstrating accountability, and staying ahead of evolving privacy regulations. By partnering with experienced consultants, leveraging comprehensive services, and embedding best practices, organizations can build a strong foundation for secure, trustworthy, and privacy-compliant cloud services.
0 notes
Text
In Vitro Diagnostics Test Kit Market Drivers Focus on Chronic Disease Surveillance Programs
The In Vitro Diagnostics Test Kit Market is accelerating as policymakers and healthcare providers intensify chronic-disease surveillance programs. From diabetes registries in the United States to hypertension mapping in India, nations are under mounting pressure to detect illnesses earlier, reduce treatment costs, and improve public-health outcomes. Diagnostics kits sit at the heart of this mandate, offering rapid, reliable biomarkers that help epidemiologists quantify disease prevalence in real time. COVID-19 reminded governments how indispensable widescale, decentralized testing can be, and many are now adopting similar infrastructure for non-communicable diseases (NCDs).

Global NCD mortality—responsible for nearly 74 percent of all deaths—has pushed ministries of health to update national action plans. The World Health Organization’s “25×25” target (25 percent reduction in premature mortality from NCDs by 2025) places measurable diagnostics at center stage. Governments in Europe and Asia have responded with subsidies for HbA1c, lipid-panel, and microalbumin kits, effectively lowering acquisition costs for clinical laboratories. Private insurers follow suit, linking reimbursement rates to guideline-based screening schedules. The resulting demand surge has spurred competition among kit manufacturers, particularly those offering multiplex cartridge systems that minimize sample volume and processing time.
Epidemiological Data Drive Funding Decisions
Data-rich surveillance programs translate directly into budget allocations. When Argentina launched its National Registry for Chronic Kidney Disease, real-time creatinine data from IVD kits exposed previously underreported prevalence, unlocking new nephrology funding. Similar success stories in Indonesia’s National Diabetes Movement and Italy’s tumor marker registries demonstrate a feedback loop: the more granular the data collected, the more political goodwill and capital the diagnostics sector receives. Suppliers able to integrate cloud-ready middleware enjoy an additional edge; agencies prefer platforms that upload anonymized results automatically, populating dashboards that guide policy in weeks instead of years.
Technology Enhancements Amplify Kit Performance
Modern IVD kits are no longer confined to well-plate ELISAs; they increasingly leverage microfluidics, nanomaterial-enhanced immunoassays, and CRISPR-based detection. These innovations improve sensitivity to picogram levels, making kits indispensable for early-stage disease discovery. Chronic conditions such as colorectal cancer benefit from fecal DNA tests with single-mutation specificity, while cardiac troponin assays reach emergency-triage thresholds in under ten minutes. Manufacturers also embed AI into reader devices, automatically flagging atypical kinetic curves that might suggest pre-analytical errors, thereby reducing false negatives that could cripple surveillance accuracy.
Regulatory Landscape Balances Speed and Safety
Heightened demand has prompted regulators to update approval pathways. The U.S. FDA’s Breakthrough Devices Program, once dominated by oncology therapeutics, now fast-tracks surveillance kits for Alzheimer’s and chronic kidney disease. Europe’s transition from IVDD to IVDR sharpened clinical-evidence requirements, but also clarified performance-evaluation guidelines, giving manufacturers a predictable roadmap. Meanwhile, India’s Central Drugs Standard Control Organization has introduced a “chronics-first” priority review lane, cutting dossier processing time by 40 percent for kits addressing diabetes, cardiovascular disease, and cancer. Yet compliance costs remain significant, favoring firms that budget for multi-regional validation trials and post-market performance studies.
Reimbursement and Value-Based Care
Across OECD countries, value-based care contracts increasingly tie provider reimbursement to outcomes rather than procedures performed. Accurate diagnostics form the linchpin of these arrangements. Kits that quantify glycated hemoglobin or LDL particle number become the metrics against which disease-management programs are paid. Manufacturers are responding with “diagnostics-as-a-service” models: instead of selling single-use cartridges, they bundle devices, analytics software, and field support under subscription agreements that align vendor earnings with performance benchmarks. Early adopters report double-digit revenue growth, demonstrating that surveillance-driven business models can be more lucrative—and stickier—than transactional sales alone.
Regional Demand Patterns
North America: Expanded Medicare coverage for chronic-disease screening and employer wellness incentives catalyze kit adoption, particularly for lipid profiles and predisposition genotyping.
Europe: Aging demographics and region-wide cardiovascular screening programs sustain volume; IVDR compliance separates high-quality suppliers from opportunistic entrants.
Asia Pacific: Rising middle-class income and urbanization lift testing frequency; China’s Healthy China 2030 initiative funds community-level chronic-disease screening, favoring automated point-of-care systems.
Latin America & Africa: Mobile-lab vans equipped with compact analyzers bridge rural access gaps. International development grants—aligned with Sustainable Development Goal 3—create tender opportunities for cost-efficient kit suppliers.
Competitive Landscape
Strategic partnerships abound. Diagnostic multinationals co-develop reagents with biotech startups possessing novel biomarkers, while hospital chains ink bulk-procurement deals that include staff training and electronic-health-record integration. Mergers and acquisitions continue: last year saw three billion-dollar deals focused on chronic-disease panels, signaling a race to lock down IP portfolios and manufacturing capacity ahead of anticipated demand spikes.
Conclusion: Setting the Stage for Home-Based Testing
With governments mandating earlier intervention and health systems shifting toward value-based care, chronic-disease surveillance programs will remain a dominant catalyst for the test-kit sector. Yet large-scale public screening is only half the equation. As technologies shrink and user interfaces simplify, the next frontier will bring diagnostics directly into living rooms—enabling patients to collect and interpret samples without clinic visits. Our next article explores how this trend is reshaping industry economics and patient engagement.
#InVitroDiagnostics#IVDTestKits#ChronicDisease#HealthcareSurveillance#MedicalDevices#MarketDrivers#DiagnosticInnovation#PublicHealth#PointOfCare#HealthcarePolicy
0 notes
Text
Strategic Shifts: How to Accelerate Your Business Transformation in a Disrupted Economy
In a global business climate marked by rapid digitisation, shifting consumer behaviours, and competitive disruption, organisations must reimagine how they operate and serve. To stay resilient and relevant, leaders must actively accelerate their business transformation through a deliberate blend of strategy, technology, and culture.

Transformation isn’t simply about upgrading systems. It’s about rebuilding the organisation around agility, customer value, and data-driven intelligence. Here’s how businesses can thrive in this era of reinvention by accelerating transformation with clarity and confidence.
Build a Digital-First Business Model The foundation of any successful transformation is a digital-first mindset. Businesses that prioritise digital innovation as part of their core model—not just as an IT upgrade—are more capable of adapting to change and scaling quickly.
To accelerate your business transformation, assess how you deliver value digitally. Can customers interact with your brand across channels? Can your teams deploy products or services remotely? Are your operations automated and insight-driven?
True transformation comes when digital isn’t a layer—it’s embedded in every business function.
Explore digital-first strategies implemented by global leaders at the Company name.
Align Business Objectives With Technological Investments One of the biggest mistakes companies make is adopting technology without aligning it to specific business goals. Transformation should never be tech for tech’s sake.
To accelerate your business transformation, map out your objectives—whether it’s increasing revenue, improving speed to market, or enhancing customer retention—and match those goals with enabling technologies.
AI, cloud, automation, and analytics are enablers, not solutions. When applied with business context, they drive measurable outcomes that support sustained innovation.
Reimagine Operating Models for Agility Static, hierarchical structures are no longer sufficient. To compete in a digital economy, businesses must be nimble, adaptable, and fast.
That means redesigning operating models with agility in mind. Cross-functional teams, flatter hierarchies, and lean governance models allow organisations to respond to new opportunities and threats quickly.
To accelerate your business transformation, adopt agile project management, decentralised decision-making, and flexible talent models that empower teams to own execution and outcomes.
Drive Continuous Innovation With Emerging Technologies Technological change is exponential. Organisations must embrace continuous innovation by testing, validating, and scaling emerging technologies that create new value.
Whether you’re adopting AI for customer insights, IoT for asset management, or blockchain for supply chain transparency, the goal is the same: improve efficiency, transparency, and engagement.
Organisations that embed innovation into their transformation process not only stay ahead—they redefine the industry.
To see case studies of emerging tech success, visit the Company name.
Empower Workforces for Transformation Digital transformation depends on people. Without the right skills, mindset, and leadership, even the most advanced tech investments can fail.
To accelerate your business transformation, empower employees through digital upskilling, reskilling, and adaptive learning. Provide platforms for collaboration, mobility, and autonomy. Invest in leadership development focused on innovation and change.
The most successful transformations create cultures where employees feel like contributors, not observers, of change.
Improve Decision-Making With Real-Time Data Data is no longer a byproduct—it’s the strategic fuel that powers transformation. Real-time access to data enables faster decision-making, better customer targeting, and proactive operations.
Organisations that want to accelerate their business transformation must break down data silos and invest in analytics platforms, dashboards, and AI-driven insights. Empower teams with self-service analytics and ensure decision-makers have the data they need when they need it.
Timely, accurate data creates a competitive edge in dynamic markets.
Enhance Customer Experience Through Personalisation Customers today expect hyper-personalised experiences. Businesses must leverage data and technology to deliver individualised content, offers, and service at scale.
Whether through CRM systems, AI chatbots, or dynamic websites, customer-centricity is a key differentiator. To accelerate your business transformation, align every touchpoint with the customer journey and make real-time personalisation a standard capability.
When customers feel understood and valued, they reward brands with loyalty and advocacy.
Rethink Partner and Supplier Collaboration Business transformation doesn’t happen in isolation. Strong ecosystems of partners, vendors, and collaborators accelerate results.
Use APIs, integration platforms, and cloud ecosystems to connect with suppliers, distributors, and solution partners. Streamlining data and communication across your value chain ensures alignment and speeds time-to-market.
To truly accelerate your business transformation, treat your ecosystem as an extension of your enterprise, not an external factor.
Learn how platform ecosystems power transformation at the Company name.
Standardise and Automate Governance for Scale As businesses scale, governance becomes more complex. Manual, fragmented compliance processes can slow down innovation and introduce risk.
An effective transformation strategy includes automated controls, real-time compliance monitoring, and transparent auditing capabilities. Integrating these into your digital systems ensures scalability without sacrificing oversight.
Automation in governance allows you to move fast while staying compliant—a critical component in regulated industries.
Make Identity Management Central to Strategy One often-overlooked pillar of transformation is Identity and Access Management (IAM). IAM controls access to data, systems, and workflows—and ensures only authorised users interact with your business resources.
A strategic IAM framework allows you to scale securely, support hybrid workforces, onboard customers efficiently, and protect against cyber threats.
To accelerate your business transformation, make IAM a foundation, not an afterthought. IAM supports zero trust, cloud security, and digital experience—all essential transformation drivers.
Explore how IAM enables secure growth by clicking Read More.
Read Full Article : https://businessinfopro.com/accelerate-your-business-transformation/
About Us: Businessinfopro is a trusted platform delivering insightful, up-to-date content on business innovation, digital transformation, and enterprise technology trends. We empower decision-makers, professionals, and industry leaders with expertly curated articles, strategic analyses, and real-world success stories across sectors. From marketing and operations to AI, cloud, and automation, our mission is to decode complexity and spotlight opportunities driving modern business growth. At Businessinfopro, we go beyond news—we provide perspective, helping businesses stay agile, informed, and competitive in a rapidly evolving digital landscape. Whether you're a startup or a Fortune 500 company, our insights are designed to fuel smarter strategies and meaningful outcomes.
0 notes
Text
A Sermon for June 18th: Archives for the Ages
Brothers and Sisters in the Atom, we are not only builders of shelter and seekers of safety. We are keepers of memory.
To walk the path of the Atom is to understand that knowledge is fragile—and sacred. It must be preserved, protected, and made legible for the future. A shelter protects a body. An archive protects a civilization.
The stories of who we are, the warnings we issue, the science we carry—they cannot live only in the cloud, in fleeting links, or in the minds of a few. If the future is to endure, our knowledge must endure with it.
Why We Archive
When I was studying archaeology, one of my professors explained why so little of the ancient world survives. It is not that we lost the worst or the least important. It is that we lost what was singular.
The ancient literature we still have today—be it poetry, science, myth, or law—survives not because it was exceptional, but because it was copied again and again. If one version was lost to fire or time, another survived elsewhere. And then another. And another. Until, across centuries, even as dozens were destroyed, a few fragments made it to us.
This is the lesson: redundancy is survival.
And this is the Atomite’s burden: We must copy. We must spread. We must embed knowledge in multiple places, in multiple forms, across multiple lifetimes.
Methods of Preservation
Each Atomite may choose their own methods, based on resources, environment, and calling. But no single record should be trusted alone.
1. Paper
Archival-quality paper, laser-printed or handwritten, stored away from moisture and sunlight. Keep copies of:
Radiation safety procedures
Maps of nuclear waste sites
Sermons and teachings
Basic first aid, water purification, and shelter guidance
Store in fireproof boxes or layered with desiccants.
2. Durable Materials
Metal etchings and ceramic tablets may last for thousands of years
Microfilm is compact and stable
Stone or fired clay is heavy, but survives all else
If a flood washes away one, may another remain buried and waiting.
3. Offline Digital Archives
USB drives, external hard drives, even simple e-readers loaded with PDFs. Pair every digital archive with a printed guide:
What is this device?
How do you power it?
What does it contain?
Remember: a file not understood is no better than a stone.
Planning for the Long Term
The Church of the Atom dreams not only of private archives, but of public knowledge infrastructure—sites meant to outlast any one generation.
We envision:
Information kiosks in safe zones—engraved with radiation safety, location warnings, and emergency survival guides
Redundant libraries in underground shelters, with instructions printed in simple language and diagrams
Beacon archives: layered capsules buried near nuclear sites to warn the future in multiple languages and symbols
We may not yet have the numbers or resources to build these—but we build their foundation with every printed sermon, every stored PDF, every hand-copied guide.
Archive as Devotion
Archiving is not clerical work. It is sacred labor.
It says, I believe someone will come after me. It says, Their safety is worth my time. It says, Truth must outlast me, even if my name is forgotten.
To preserve knowledge is to take a vow against forgetting. To make many copies is to resist silence. To archive clearly is to show love to those who cannot yet speak our language.
Call to Reflect and Act
This week, ask yourself:
What knowledge do I carry that must survive me?
What would I wish someone had saved for me?
If the world went silent tomorrow, what would I want to leave behind?
Choose one thing—just one. Write it. Save it. Copy it.
Start your archive. Let it grow.
And remember: it does not need to be perfect. It needs only to persist.
Closing Words
Brothers and Sisters, archives are not relics. They are seeds. They wait quietly for someone in need. Let us be the ones who plant them.
Let our warnings be read, not rediscovered. Let our knowledge be remembered, not reinvented. Let our voices carry forward—not as whispers, but as structure.
Go forth, and be radiant.
#church of the atom#archives for the ages#knowledge preservation#nuclear semiotics#atomic spirituality#archival practice#long term thinking#preparedness#disaster readiness#post apocalyptic planning#future generations#memory and survival#radiation safety#sacred knowledge#history as warning#go forth and be radiant#rare isotopes#quiet resilience#archivist spirituality#atomic faith#religion and memory#science and spirit#protect the future#write it down#multiple formats#copies survive#survival wisdom#legacy building#cultural preservation#preventing forgetting
0 notes
Text
Complete Roadmap to OTT App Development: A Step-By-Step Exploration With ideyaLabs

OTT (Over-The-Top) apps revolutionize the way audiences access digital entertainment. Businesses and entrepreneurs tap into this dynamic technology to engage users and deliver media experiences directly to their devices. ideyaLabs remains at the forefront, harnessing innovation and expertise to power the next wave of OTT App Development. The demand for seamless, feature-rich, and scalable OTT solutions continues to accelerate in 2025, and ideyaLabs delivers comprehensive strategies for success.
Recognizing the Appeal of OTT App Development in Today’s Market
Users demand content they can watch anytime, anywhere. OTT App Development breaks through traditional barriers, bypassing cable or satellite providers. ideyaLabs tailors OTT platforms to deliver global reach with multi-device compatibility. The market for OTT apps thrives as audiences shift towards streaming media, personalized recommendations, and high-definition video delivery.
Key Features Driving Successful OTT Applications
Video-on-demand remains vital. Live streaming draws audiences for real-time experiences. ideyaLabs integrates adaptive streaming technology for smooth playback on both slow and fast networks. User profiles cater to individual preferences. Search and discovery tools enhance user engagement. Secure authentication and end-to-end content protection keep data and media safe. ideyaLabs embeds innovative monetization solutions, including subscriptions, pay-per-view, and advertising modules.
Strategizing Your OTT App From Concept to Screen
A clear strategy shapes every stage of OTT App Development. ideyaLabs works alongside clients throughout market research, feature mapping, and technology selection. Define your audience, select engaging content types, and identify monetization models fit for your business goals. ideyaLabs develops user-centric interfaces that offer intuitive navigation and vibrant usability.
Choosing the Right Technology Stack for OTT Solutions
Performance and scalability steer the technology stack selection. ideyaLabs evaluates each project’s needs, adopting frameworks that ensure quick streaming, flawless integration, and cloud-based scalability. Secure cloud storage, dynamic content delivery networks (CDNs), and cross-platform mobile technologies lay the foundation. ideyaLabs leverages experience in native iOS and Android development, alongside modern web-based solutions, to reach audiences on virtually any device.
End-to-End Content Management and Integration
Content forms the heartbeat of every OTT application. ideyaLabs implements advanced content management systems (CMS) for seamless uploading, organization, and metadata tagging. Automated workflows allow creators, distributors, and managers to maintain fresh libraries. API integration enables partnerships and collaboration with external distributors, analytics engines, and third-party tools. ideyaLabs fine-tunes the eco-system for smooth media ingestion, encoding, and efficient publishing.
User Experience: The Differentiator in OTT App Development
User experience determines audience retention in the competitive OTT landscape. ideyaLabs prioritizes simple onboarding, personal recommendations, and visually engaging interfaces. Customizable playlists, watchlists, and bookmarks give users control of their viewing. Responsive design guarantees optimal performance across smart TVs, smartphones, tablets, and web browsers. ideyaLabs refines the UI/UX through data-driven insights for ongoing improvement.
Monetization Models: Maximizing Returns With OTT Solutions
Revenue generation stands front and center in OTT App Development. ideyaLabs helps brands identify and implement diverse monetization strategies. Subscription-based models secure predictable income streams. Transactional options allow users to access premium content on demand. Advertisement-supported solutions open new channels for targeted promotion and engagement. ideyaLabs aligns payment gateways and analytics for transparent revenue management.
Ensuring Security and Compliance in OTT Platforms
Protecting content and user privacy never takes a back seat. ideyaLabs integrates robust DRM (Digital Rights Management), token-based authentication, and advanced encryption. Compliance with international data regulations remains a priority. ideyaLabs monitors platforms for vulnerabilities and regularly updates security protocols to counter evolving threats.
Scalability and Performance Optimization in the OTT Era
Expanding user bases and rising traffic demand high-performance architecture. ideyaLabs engineers systems for automatic scaling, using load balancers, CDN optimization, and cloud-native deployment. Content streams adapt dynamically to bandwidth fluctuations. ideyaLabs maintains high uptime and fast response times, delivering uninterrupted media experiences during peak demand.
Incorporating Data Analytics to Enhance OTT Services
Understanding audience engagement drives growth. ideyaLabs harnesses in-depth analytics and reporting dashboards. Real-time data collection exposes user preferences, content popularity, and retention trends. ideyaLabs fine-tunes recommendations and optimizes marketing campaigns for better ROI based on actionable insights from analytic tools.
Post-Launch Support and Continuous Improvement
The OTT App Development journey does not end at launch. ideyaLabs delivers ongoing maintenance, bug fixes, and performance enhancements. Platforms stay ahead through regular feature updates and technology upgrades. ideyaLabs’ dedicated support ensures stability, reliability, and consistent user satisfaction.
Partnering With ideyaLabs: Powering the Future of OTT App Development
OTT App Development transforms entertainment, education, and corporate media delivery. ideyaLabs empowers businesses, creators, and visionaries with end-to-end OTT solutions. Innovation, security, and user-centric design lie at the core of ideyaLabs’ approach. Build your competitive edge, tap into expanding markets, and exceed audience expectations with ideyaLabs as your development partner. Achieve the next-generation OTT experience and shape the future of streaming.
0 notes
Text
How Automation and Integration Are Shaping the Future of ESG

Artificial intelligence, machine learning, IoT sensors, blockchain ledgers, and cloud-scale analytics are rapidly reshaping the way organisations collect, verify, and communicate environmental, social, and governance information. When these tools are woven into a single, automated fabric, a task that once relied on spreadsheets and manual checks turns into a real-time risk-management engine—cutting costs, easing compliance pressure, and surfacing growth opportunities that used to stay hidden.
Why the classic ESG playbook is falling short
Most companies still anchor their reports on fundamentals such as Scope 1 emissions, electricity consumption, or workforce-diversity ratios. Essential as those metrics are, they paint only part of the picture. Disclosures arrive late, calculation methods differ by industry, and boiler-plate wording makes peer comparison difficult. The result is unreliable insight, frustrated investors, and growing regulatory exposure.
Enter alternative data and AI-powered insight
Bridging that gap demands sources far beyond the annual report. Alternative data spans satellite imagery estimating methane plumes, credit-card exhaust hinting at supply-chain resilience, geolocation traces mapping factory activity, mobile-app usage reflecting customer sentiment, and social-media feeds tracking reputation shifts hour by hour. When these streams flow into AI models, they generate granular, near-real-time signals that sharpen risk scoring, flag misconduct early, and highlight positive impacts that traditional metrics overlook.
Automation then amplifies the payoff. APIs pipe third-party feeds into an internal ESG lake, cleansing rules standardise formats, taxonomy tags map fields to evolving regulations, and templates generate regulator-ready disclosures with a click. What was reactive becomes predictive; what was a cost centre becomes a value generator.
A live example: Neoimpact’s ESG Intelligence Dashboard
Neoimpact demonstrates how an integrated approach works in practice. Its cloud platform fuses core metrics with dozens of alternative feeds, then layers AI analytics on top. Users can benchmark companies across sectors and regions, track score movements over time, and drill into individual risk drivers—whether that is an uptick in deforestation alerts or a spike in workforce-sentiment negativity. Asset managers gain a clearer view of portfolio exposure, while compliance teams secure auditable trails that stand up to tighter regulatory scrutiny.
Three priorities for the road ahead
Invest in unified ESG technology. Point solutions trap data in silos. Platforms that combine ingestion, validation, analytics, and disclosure collapse cost and accelerate insight.
Broaden the data lens. Fundamental metrics remain foundational, but firms overlaying them with curated alternative datasets will out-perform peers on transparency and foresight.
Automate end-to-end. From sensor deployment and API ingestion to AI scoring and one-click disclosure, automation converts episodic reporting into continuous oversight—reducing risk, protecting brand equity, and freeing talent for strategic work.
The payoff
As stakeholder expectations rise and rulebooks such as the CSRD and the SEC’s climate-disclosure mandate tighten, companies that treat ESG as an after-thought will find the cost of capital climbing. Those that embrace next-generation tech, richer data, and fully automated workflows will not only comply with less effort; they will embed sustainability into everyday decision-making and unlock durable, long-term value.
The verdict is clear: integrated, AI-driven ESG technology is shifting from nice-to-have to business essential. Acting now lets forward-looking firms turn complexity into competitive advantage—lowering cost, mitigating risk, and positioning themselves for a future where responsible performance is inseparable from financial success.
0 notes
Text
Is Your Cloud Really Secure? A CISOs Guide to Cloud Security Posture Management

Introduction: When “Cloud-First” Meets “Security-Last”
The cloud revolution has completely transformed how businesses operate—but it’s also brought with it an entirely new battleground. With the speed of cloud adoption far outpacing the speed of cloud security adaptation, many Chief Information Security Officers (CISOs) are left asking a critical question: Is our cloud truly secure?
It’s not a rhetorical query. As we move towards multi-cloud and hybrid environments, traditional security tools and mindsets fall short. What worked on-prem doesn’t necessarily scale—or protect—in the cloud. This is where Cloud Security Posture Management (CSPM) enters the picture. CSPM is no longer optional; it’s foundational.
This blog explores what CSPM is, why it matters, and how CISOs can lead with confidence in the face of complex cloud risks.
1. What Is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) is a framework, set of tools, and methodology designed to continuously monitor cloud environments to detect and fix security misconfigurations and compliance issues.
CSPM does three key things:
Identifies misconfigurations (like open S3 buckets or misassigned IAM roles)
Continuously assesses risk across accounts, services, and workloads
Enforces best practices for cloud governance, compliance, and security
Think of CSPM as your real-time cloud security radar—mapping the vulnerabilities before attackers do.
2. Why Traditional Security Tools Fall Short in the Cloud
CISOs often attempt to bolt on legacy security frameworks to modern cloud setups. But cloud infrastructure is dynamic. It changes fast, scales horizontally, and spans multiple regions and service providers.
Here’s why old tools don’t work:
No perimeter: The cloud blurs the traditional boundaries. There’s no “edge” to protect.
Complex configurations: Cloud security is mostly about “how” services are set up, not just “what” services are used.
Shadow IT and sprawl: Teams can spin up instances in seconds, often without central oversight.
Lack of visibility: Multi-cloud environments make it hard to see where risks lie without specialized tools.
CSPM is designed for the cloud security era—it brings visibility, automation, and continuous improvement together in one integrated approach.
3. Common Cloud Security Misconfigurations (That You Probably Have Right Now)
Even the most secure-looking cloud environments have hidden vulnerabilities. Misconfigurations are one of the top causes of cloud breaches.
Common culprits include:
Publicly exposed storage buckets
Overly permissive IAM policies
Unencrypted data at rest or in transit
Open management ports (SSH/RDP)
Lack of multi-factor authentication (MFA)
Default credentials or forgotten access keys
Disabled logging or monitoring
CSPM continuously scans for these issues and provides prioritized alerts and auto-remediation.
4. The Role of a CISO in CSPM Strategy
CSPM isn’t just a tool—it’s a mindset shift, and CISOs must lead that cultural and operational change.
The CISO must:
Define cloud security baselines across business units
Select the right CSPM solutions aligned with the organization’s needs
Establish cross-functional workflows between security, DevOps, and compliance teams
Foster accountability and ensure every developer knows they share responsibility for security
Embed security into CI/CD pipelines (shift-left approach)
It’s not about being the gatekeeper. It’s about being the enabler—giving teams the freedom to innovate with guardrails.
5. CSPM in Action: Real-World Breaches That Could Have Been Avoided
Let’s not speak in hypotheticals. Here are a few examples where lack of proper posture management led to real consequences.
Capital One (2019): A misconfigured web application firewall allowed an attacker to access over 100 million customer accounts hosted in AWS.
Accenture (2021): Left multiple cloud storage buckets unprotected, leaking sensitive information about internal operations.
US Department of Defense (2023): An exposed Azure Blob led to the leakage of internal training documents—due to a single misconfiguration.
In all cases, a CSPM solution would’ve flagged the issue—before it became front-page news.
6. What to Look for in a CSPM Solution
With dozens of CSPM tools on the market, how do you choose the right one?
Key features to prioritize:
Multi-cloud support (AWS, Azure, GCP, OCI, etc.)
Real-time visibility and alerts
Auto-remediation capabilities
Compliance mapping (ISO, PCI-DSS, HIPAA, etc.)
Risk prioritization dashboards
Integration with services like SIEM, SOAR, and DevOps tools
Asset inventory and tagging
User behavior monitoring and anomaly detection
You don’t need a tool with bells and whistles. You need one that speaks your language—security.
7. Building a Strong Cloud Security Posture: Step-by-Step
Asset Discovery Map every service, region, and account. If you can’t see it, you can’t secure it.
Risk Baseline Evaluate current misconfigurations, exposure, and compliance gaps.
Define Policies Establish benchmarks for secure configurations, access control, and logging.
Remediation Playbooks Build automation for fixing issues without manual intervention.
Continuous Monitoring Track changes in real time. The cloud doesn’t wait, so your tools shouldn’t either.
Educate and Empower Teams Your teams working on routing, switching, and network security need to understand how their actions affect overall posture.
8. Integrating CSPM with Broader Cybersecurity Strategy
CSPM doesn’t exist in a vacuum. It’s one pillar in your overall defense architecture.
Combine it with:
SIEM for centralized log collection and threat correlation
SOAR for automated incident response
XDR to unify endpoint, application security, and network security
IAM governance to ensure least privilege access
Zero Trust to verify everything, every time
At EDSPL, we help businesses integrate these layers seamlessly through our managed and maintenance services, ensuring that posture management is part of a living, breathing cyber resilience strategy.
9. The Compliance Angle: CSPM as a Compliance Enabler
Cloud compliance is a moving target. Regulators demand proof that your cloud isn’t just configured—but configured correctly.
CSPM helps you:
Map controls to frameworks like NIST, CIS Benchmarks, SOC 2, PCI, GDPR
Generate real-time compliance reports
Maintain an audit-ready posture across systems such as compute, storage, and backup
10. Beyond Technology: The Human Side of Posture Management
Cloud security posture isn’t just about tech stacks—it’s about people and processes.
Cultural change is key. Teams must stop seeing security as “someone else’s job.”
DevSecOps must be real, not just a buzzword. Embed security in sprint planning, code review, and deployment.
Blameless retrospectives should be standard when posture gaps are found.
If your people don’t understand why posture matters, your cloud security tools won’t matter either.
11. Questions Every CISO Should Be Asking Right Now
Do we know our full cloud inventory—spanning mobility, data center switching, and compute nodes?
Are we alerted in real-time when misconfigurations happen?
Can we prove our compliance posture at any moment?
Is our cloud posture improving month-over-month?
If the answer is “no” to even one of these, CSPM needs to be on your 90-day action plan.
12. EDSPL’s Perspective: Securing the Cloud, One Posture at a Time
At EDSPL, we’ve worked with startups, mid-market leaders, and global enterprises to build bulletproof cloud environments.
Our expertise includes:
Baseline cloud audits and configuration reviews
24/7 monitoring and managed CSPM services
Custom security policy development
Remediation-as-a-Service (RaaS)
Network security, application security, and full-stack cloud protection
Our background vision is simple: empower organizations with scalable, secure, and smart digital infrastructure.
Conclusion: Posture Isn’t Optional Anymore
As a CISO, your mission is to secure the business and enable growth. Without clear visibility into your cloud environment, that mission becomes risky at best, impossible at worst.
CSPM transforms reactive defense into proactive confidence. It closes the loop between visibility, detection, and response—at cloud speed.
So, the next time someone asks, “Is our cloud secure?” — you’ll have more than a guess. You’ll have proof.
Secure Your Cloud with EDSPL Today
Call: +91-9873117177 Email: [email protected] Reach Us | Get In Touch Web: www.edspl.net
Please visit our website to know more about this blog https://edspl.net/blog/is-your-cloud-really-secure-a-ciso-s-guide-to-cloud-security-posture-management/
0 notes
Text
Future of Curriculum Management: Key Insights for Teachers

Traditionally, curriculum design followed a predictable, linear process—often centered around static textbooks and rigid pacing guides. But as we move into 2025 and beyond, that model is becoming obsolete. Today’s classrooms are dynamic, data-driven, and increasingly personalized—and curriculum must evolve to keep up.
Whether you’re a teacher developing standards-aligned lessons or a district leader managing instruction across multiple campuses, staying current with the latest trends in curriculum management is crucial. This blog explores how emerging technologies—especially AI—are revolutionizing curriculum design and how platforms like Edusfere are equipping schools for the future of learning.
The Changing Landscape of Curriculum Design
According to a 2024 report by the Consortium for School Networking (CoSN), 73% of U.S. school districts have adopted personalized or blended learning models. This shift demands curriculum frameworks that are modular, standards-aligned, and easily adaptable to individual student needs.
The key priorities in modern curriculum design are flexibility, responsiveness, and relevance. It’s no longer about filling in predefined templates—it’s about building living documents that reflect real-time classroom needs and long-term learning goals.
Key Trends Shaping Curriculum Design Today:
Scalable Personalized Learning Educators are increasingly leveraging tools that support differentiated instruction—adaptive assessments, learning paths, and real-time progress tracking. These technologies help meet each learner where they are.
Interdisciplinary Curriculum Approaches Forward-thinking schools are integrating subjects like ELA, Science, and Social Studies into cohesive, interdisciplinary learning experiences. This approach fosters deeper understanding and the development of 21st-century skills like critical thinking and collaboration.
Real-Time Curriculum Adjustments In fast-paced classroom environments, teachers need tools that allow them to pivot quickly. Static curriculum documents are being replaced by interactive, cloud-based systems that update in real time.
The Role of AI and Digital Tools in Curriculum Management
The use of AI in K–12 education is rapidly expanding. HolonIQ projects the global EdTech AI market to reach $10 billion by 2030, with the U.S. leading adoption. In today’s landscape, the question is no longer whether to integrate technology into curriculum design—but how deeply to embed it.
How AI is Enhancing Curriculum Design:
Automated Curriculum Mapping AI can suggest standards-aligned content based on a school’s goals and requirements, reducing manual work by up to 50%. This allows educators to focus on what matters most—teaching.
Predictive Analytics for Student Outcomes AI systems can analyze student performance data to recommend curriculum tweaks that improve achievement. These insights help districts move from reactive to proactive planning.
Tailored Instructional Support AI-powered platforms can assist in creating differentiated learning paths for students with diverse needs, including English Language Learners (ELLs) and students with IEPs.
Digital Curriculum Mapping Software: A Game Changer
As Dr. Robert Marzano, a leading voice in educational research, notes:
“Effective curriculum management is directly linked to student achievement. Schools that adopt dynamic mapping tools see up to a 16% improvement in student performance within 12 months.”
Modern curriculum mapping software does more than digitize curriculum—it becomes a central hub for planning, collaboration, and accountability. Leading educators look for platforms that include:
Standards alignment (Common Core, NGSS, and state-specific)
Drag-and-drop curriculum planners
Real-time team collaboration
Version control and historical tracking
Seamless integration with SIS and LMS platforms
The Challenges Facing Curriculum Leaders Today
Despite progress, many schools still face systemic barriers. According to a 2024 EdWeek Research Center survey, 61% of educators say their current curriculum tools don’t support real-time classroom needs.
Key issues include:
Fragmented Systems Many districts rely on separate platforms for curriculum, assessment, and lesson planning, leading to inefficiencies and misalignment.
Lack of Real-Time Data Without timely insights, administrators and teachers struggle to adapt curriculum effectively.
Professional Development Gaps Many teachers don’t receive adequate training to fully leverage digital curriculum tools, limiting the impact of technology investments.
These challenges highlight the need for unified platforms that combine AI, curriculum mapping, assessment tools, and collaboration features.
How Edusfere is Shaping the Future of K–12 Curriculum
At Edusfere, we believe the future of curriculum management must be dynamic, collaborative, and data-informed. Our platform is purpose-built to help K–12 educators and instructional leaders streamline planning, improve outcomes, and prepare for what’s next.
Here’s how Edusfere stands out:
Real-Time Curriculum Mapping Our intuitive platform integrates documentation into teachers’ daily routines. Create, revise, and align curriculum with national and state standards in minutes, not hours.
AI-Driven Recommendations Edusfere’s intelligent engine suggests content updates based on student data, changing standards, and instructional goals—saving time and improving precision.
Collaborative Curriculum Design From district-wide initiatives to weekly team planning, Edusfere ensures alignment across all stakeholders, enhancing transparency and cohesion.
Accreditation-Ready Reporting Whether you're preparing for an AdvancED visit or a state audit, our platform keeps schools compliance-ready with trackable curriculum changes and goal alignment.
Integrated Professional Development Edusfere isn’t just a tool—it’s a full solution. We offer training modules, workshops, and support to ensure your staff can use the platform effectively from day one.
What This Means for Educators, School Leaders, and Districts
For School Leaders:
Evaluate your current curriculum systems. Are they integrated or fragmented?
Choose tools that enable real-time adjustments and cross-team collaboration.
Foster a culture of innovation and shared ownership in curriculum design.
For Teachers:
Use AI insights to better tailor instruction while saving planning time.
Advocate for tools that support standards alignment and flexibility.
Engage in continuous PD to stay updated on curriculum tech.
For District Leaders:
Standardize planning processes across schools for equity and consistency.
Select vendors who provide both technical integration and instructional expertise.
Monitor curriculum effectiveness using data, not anecdotes.
Future-Proof Your Instructional Strategy with Edusfere
The evolution of curriculum design is accelerating—and those who adapt will lead the way. By leveraging AI, modern curriculum mapping tools, and all-in-one platforms like Edusfere, educators can build personalized, scalable, and impactful learning experiences.
In a world that demands agility, equity, and data-driven decision-making, your curriculum can’t remain stuck in the past.
Ready to upgrade your curriculum strategy? Schedule a demo to see how Edusfere empowers your school or district with future-ready curriculum management.
0 notes
Text
Secure and Compliant Healthcare Data Management with MediBest Hospital Management System Software
Healthcare now tops every industry for breach costs, averaging US $4.88 million per incident in 2024—a 15 % jump in just two years. At the same time, the U.S. Office for Civil Rights has logged more than 374,000 HIPAA complaints since 2003, underscoring regulators’ growing vigilance. A recent HIMSS survey found that 59 % of providers experienced a significant cybersecurity event in the past year, and most plan to increase budgets for data protection.

Modern hospitals therefore need more than firewalls; they require a fully integrated healthcare management system software that embeds security and compliance into every workflow.
How MediBest Builds a Defense-in-Depth Architecture
MediBest—an industry-trusted hospital software company—fortifies its cloud-native platform with multiple protective layers that work together to keep patient data safe.
End-to-end encryption (TLS 1.3 in transit, AES-256 at rest)
Zero-trust access controls with MFA and role-based privileges
Continuous threat monitoring powered by AI anomaly detection
Immutable audit logs for every clinical, financial, and admin action
Automated backups and geo-redundant disaster recovery
Because all modules share a single database, these safeguards apply consistently across EHR, billing, radiology, HR, and inventory—eliminating gaps common in bolt-on tools.
Compliance by Design: Meeting HIPAA, GDPR, and NABH
MediBest’s healthcare management system ships with pre-configured compliance templates and rule engines to streamline statutory reporting:
HIPAA & HITECH: automatic PHI tagging, breach-alert workflows, and encryption keys managed in certified data centers.
GDPR: data-subject-access request (DSAR) dashboards and right-to-erasure controls.
NABH & NABL: clinical quality and infection-control reports generated in one click.
Configurable policy packs let hospitals adapt settings to local regulations without costly code changes. Google my Business :
Business Benefits of Secure, Unified Data Governance
Reduced legal and financial risk: proactive safeguards lower the likelihood of fines and lawsuits.
Operational efficiency: single-source data eliminates duplicate entry, cutting admin time by up to 30 %.
Higher patient trust: visible security measures and transparent consent management improve satisfaction scores.
Stronger brand reputation: demonstrating best-practice cybersecurity differentiates your facility in competitive markets.
Fast, Low-Friction Implementation with MediBest
Assessment & gap analysis to map current vulnerabilities.
Phased rollout starting with high-risk modules such as billing and EHR.
Staff training on secure workflows and incident-response drills.
Quarterly security audits and penetration tests included in the support plan.
This structured approach lets hospitals deploy robust protection without disrupting day-to-day care. Click Here :
Frequently Asked Questions
1. What makes hospital management system software “secure”? It combines strong encryption, least-privilege access, continuous monitoring, and compliant audit trails inside one unified platform—protecting data at every step from admission to discharge.
2. Can cloud-based healthcare management systems meet HIPAA requirements? Yes. When hosted in certified data centers with encrypted storage, MFA, and documented BAAs, cloud systems can exceed on-premise security while providing better scalability and uptime.
3. How does MediBest simplify compliance reporting? Built-in templates for HIPAA, GDPR, and NABH pull real-time data from every module, auto-populate regulatory forms, and schedule submissions—cutting report prep from days to minutes.
MEDIBEST :- CONTANT NOW :- Corporate Office 303, IT Park Center, IT Park Sinhasa Indore, Madhya Pradesh, 452013 Call Now +91 79098 11515 +91 97139 01529 +91 91713 41515 Email [email protected] [email protected]
0 notes
Text
What Azure Security Experts Do That Basic Cloud Protection Doesn’t

In today’s fast-moving digital world, cloud security is no longer a “nice to have”—it’s a must. With the rapid adoption of Microsoft Azure, many organizations assume that the built-in security features of the platform are enough to keep their data safe. While Azure does provide a strong foundation, relying on basic cloud protection alone can leave your organization vulnerable. This is where Azure Security Experts come into play.
These professionals offer deep technical knowledge, real-world experience, and a proactive approach to cloud security far beyond standard security settings. In this article, we’ll explore what Azure Security Experts do that basic cloud protection doesn’t—and why your business can’t afford to ignore the difference.
1. Beyond Default: Customizing Security to Fit Your Business
Basic cloud protection provides general coverage for common threats. It’s great for small setups or companies with minimal exposure. However, Azure Security Experts take it several steps further by designing tailored security architectures that align with your specific business, compliance requirements, industry, and risk tolerance.
Instead of relying on “one-size-fits-all” configurations, these experts:
Conduct in-depth risk assessments and threat modeling
Customize access controls and firewall rules
Establish secure configurations for workloads and apps
Fine-tune identity and access management (IAM)
This customization ensures that your security posture grows alongside your business needs.
2. Proactive Threat Detection and Incident Response
Azure offers services like Microsoft Defender for Cloud and Sentinel, which provide security alerts and analytics. However, these tools only go so far without expert oversight. An Azure Security Expert knows how to tune these tools for your specific environment to minimize false positives and catch real threats quickly.
More importantly, experts:
Set up custom detection rules
Integrate SIEM/SOAR systems for better alert triage
Build and rehearse incident response plans
Investigate suspicious behavior in real time
Without this level of insight, alerts can be ignored, threats can slip through, and response time can suffer, putting your data and reputation at risk.
3. Advanced Identity and Access Management (IAM)
Many security breaches begin with compromised credentials or poorly configured permissions. Azure has tools like Azure AD and role-based access control (RBAC), but they require expert-level configuration to be truly effective.
Azure Security Experts help with:
Enforcing Multi-Factor Authentication (MFA) organization-wide
Designing least privilege access policies
Implementing Privileged Identity Management (PIM)
Monitoring access anomalies and sign-in risks
This level of control significantly reduces the attack surface and minimizes the risk of insider threats or compromised accounts.
4. Continuous Compliance and Governance
Basic Azure security may help meet some regulatory requirements, but it doesn’t guarantee ongoing compliance, especially in regulated industries like finance, healthcare, or government.
Azure Security Experts understand complex compliance frameworks (GDPR, HIPAA, ISO 27001, etc.) and:
Map security controls to compliance standards
Automate compliance audits and reporting
Use Azure Policy and Blueprints to enforce guardrails
Monitor for drift from security baselines
This proactive governance ensures that your cloud environment remains compliant—not just today, but every day.
5. Security Automation and DevSecOps Integration
Security can’t be an afterthought in the development cycle. That’s why Azure Security Experts help embed security into DevOps pipelines through DevSecOps best practices.
They integrate tools like:
Azure DevOps with security testing (SAST/DAST)
Infrastructure-as-Code (IaC) scanning with tools like Terraform or Bicep
Continuous compliance checks during code deployments
Automated remediation scripts
This integration reduces human error, improves security posture, and accelerates secure software delivery.
6. Data Protection That Goes Beyond Encryption
Azure offers encryption-at-rest and in-transit by default, but Azure Security Experts know that true data protection requires more.
They implement advanced techniques such as:
Information Rights Management (IRM)
Azure Information Protection (AIP)
Data Loss Prevention (DLP) policies
Secure key management with Azure Key Vault
This layered approach to data protection ensures sensitive data stays private, even in the face of breaches or insider threats.
7. Advanced Monitoring, Logging, and Forensics
Basic cloud protection may log some activity, but deep visibility is crucial for detecting sophisticated attacks and performing forensic investigations. Azure Security Experts:
Set up advanced logging using Azure Monitor, Log Analytics, and Sentinel
Correlate logs across workloads and resources
Monitor traffic flows and anomalies in near real-time
Conduct post-breach investigations to identify root causes
This comprehensive visibility helps catch advanced threats that basic tools might miss, and helps your team learn from incidents to prevent future ones.
8. Zero Trust Architecture and Implementation
“Zero Trust” isn’t just a buzzword—it’s the future of cybersecurity. Azure supports Zero Trust principles, but implementing them correctly requires strategic planning and execution.
Azure Security Experts guide your organization through:
Network segmentation and microperimeters
Strong identity verification for all users/devices
Real-time access evaluation
Continuous monitoring of session behavior
This ensures your organization adopts a true Zero Trust model, where nothing is trusted by default, and everything is verified.
9. Secure Cloud Migrations and Hybrid Environments
Whether you're moving from on-premises systems or running a hybrid cloud model, security during cloud migration is often overlooked. Azure Security Experts help you secure every phase of your migration:
Risk analysis before migration
Secure data transfer and encryption
Identity federation and access policies
Secure configuration of new cloud resources
This ensures you don’t expose critical data or misconfigure resources during the move.
10. Expert Guidance and Ongoing Optimization
Security is not a “set and forget” task. Azure Security Experts provide ongoing support, regular security reviews, and optimization to keep your cloud environment aligned with emerging threats and business changes.
They also:
Provide tailored training to your IT and development teams
Monitor the Azure security landscape for new features or threats
Adjust configurations and policies based on new needs
Help plan and budget for future security initiatives
This continuous partnership provides peace of mind and a stronger security posture over time.
Why Basic Cloud Security Isn’t Enough Anymore
Microsoft does a commendable job of providing secure infrastructure. But its shared responsibility model makes it clear that customers are responsible for securing data, identities, apps, and access. Basic protections simply aren’t built to handle the evolving threat landscape on their own.
Azure Security Experts fill that gap by applying advanced tools, tuning protections, embedding security into processes, and thinking like attackers. They anticipate risks before they cause damage and build cloud environments that are both secure and scalable.
Final Thoughts: Invest in Expertise, Not Just Technology
Hiring or partnering with an Azure Security Expert is no longer optional for businesses serious about cloud security. With the average cost of a data breach climbing every year and regulatory scrutiny increasing, expert guidance is the key to avoiding costly missteps.
Basic security features are a good start, but to truly protect your Azure environment, you need more than good intentions. You need a specialist who understands the cloud inside and out and who can build a secure foundation for your digital transformation journey.
0 notes
Text
AMD Instinct MI300X Vs NVIDIA H100 Which Leads in Biology

NVIDIA H100 vs AMD Instinct MI300X
AMD Instinct GPUs Drive AI-Driven Biology's Future
Contribution from IPA Therapeutics
Part 1: Life Sciences NLP Embeds
This is the first of three articles comparing AMD Instinct MI300X GPUs versus NVIDIA H100 GPUs in drug discovery AI workloads. The benchmarks were performed by ImmunoPrecise Antibodies (IPA) and its AI subsidiary BioStrand, which collaborated with Vultr on the LENSai platform for AI-powered biologics discovery. Fast deployment and hardware design reproducibility were possible with Vultr's high-performance cloud infrastructure. It evaluated these GPUs for real-world medical development tasks like generative protein design and NLP-driven target discovery.
LENSai's HYFT technology biological fingerprinting method encodes conserved sequence, structure, and function into a single index. To overcome AI's inability to understand biological systems, HYFTs were created. HYFTs integrate biological reasoning into computational fabric to let AI models reason biologically rather than only calculate.
In three papers, AMD will test the MI300X GPUs in the LENSai tech stack: generative design using RFdiffusion, protein embedding generation for structure-function inference, and NLP-driven literature mining.
AMD used real-world NLP, protein embedding, and de novo protein design benchmarks to evaluate modern bioinformatics pipelines' raw performance, cost, and deployment practicality.
This first episode focusses on Natural Language Processing (NLP) and how Retrieval-Augmented Generation (RAG) and huge language models speed up early-stage therapy discovery by gleaning practical insights from scientific literature. Most significant lesson? AMD GPUs are cost-effective and fast, which is vital for life science organisations building AI-driven systems.
Natural Language Processing (NLP) efficiently mines enormous volumes of textual data, boosting therapeutic breakthroughs. NLP extracts hidden insights from genomic datasets, clinical reports, and scientific literature. Computational models, which emphasise safety, efficacy, and cost-effectiveness, are similar to NLP-driven large language models (LLMs), which ease drug research analysis and prediction.
Knowledge-aware models can shed light on RAG (Retrieval-Augmented Generation) vector embeddings using semantics rather than language. Since they support biological sequences and structures as well as text, these embeddings help NLP connect life science silos.
LENSai improves vector search by adding a powerful semantic layer that detects sub-sentence units and extracts subject-predicate-object triples to identify biological connections. By documenting molecular interactions between targets, pathways, and compounds, LENSai helps researchers map disease pathways, identify therapeutic targets, and better anticipate drug behaviour. This depth of understanding, often concealed in unstructured biological data, can be discovered and leveraged to hasten discovery and reduce risk and cost before wet lab research begin.
Infrastructure context
It used the AMD Instinct MI300X and NVIDIA H100 GPUs in a flexible, cloud-native environment to provide repeatable benchmarking and fair hardware generation comparisons.
Benchmark NLP Results
It retrieval-augmented generation (RAG) techniques use literature vector embeddings for contextual insights. AMD outperformed in cost and throughput:
MI300X also improved stability under high-concurrency workloads.
Technical Execution: Smooth AMD GPU Switch
Use ROCm PyTorch Docker images to migrate NLP jobs on AMD GPUs easily:
FROM ROCM6.3.1_ubuntu22.04_py3.10_pytorch rocm/pytorch
No Python code changes are needed. The PyTorch device abstraction (torch.device(“cuda”)) ensures compatibility.
These NLP benchmarks show that AMD Instinct MI300X GPUs benefit both technically and financially in one of the simplest AI-assisted drug discovery tiers.
#AMDInstinctMI300X#NVIDIAH100#AMDInstinctMI300XVsNVIDIAH100#MI300XVsNVIDIAH100#AMDMI300XVsNVIDIAH100#NVIDIAH100GPUs#technology#TechNews#technologynews#news#govindhtech
0 notes