#maas360
Explore tagged Tumblr posts
Text
EACOMM named IBM Philippines Rookie Partner of the Year for 2024
0 notes
Text
Workspace as a Service (WaaS) Market Size, Share, Scope, Demand Analysis, Forecast, Growth & Industry Report 2032
Workspace as a Service (WaaS) Market Size was valued at USD 8.4 Billion in 2023 and is expected to reach USD 33.4 Billion by 2032 and grow at a CAGR of 16.6% by 2024-2032
The Workspace as a Service (WaaS) market is experiencing an unprecedented surge as businesses worldwide embrace flexible work environments. This transformation is driven by the increasing need for cost-effective, scalable, and agile solutions that enable employees to work from anywhere. As organizations continue to adapt to a post-pandemic world, WaaS platforms are becoming a cornerstone of digital workspace evolution, offering enhanced collaboration, security, and efficiency.
Workspace as a Service (WaaS) Market is revolutionizing the way organizations manage and deliver digital workspaces to employees, breaking free from traditional office constraints. By enabling companies to access virtualized desktops, applications, and data from anywhere, WaaS allows businesses to foster a remote and hybrid work culture. This shift has been accelerated by the rise of cloud technologies, which support the seamless delivery of these services across diverse geographies. Companies are rapidly adopting WaaS solutions to reduce infrastructure costs, improve employee productivity, and ensure a more streamlined and secure IT environment.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3857
Market Keyplayers:
Amazon Web Services (AWS) (Amazon WorkSpaces, Amazon AppStream 2.0)
Citrix Systems, Inc. (Citrix Workspace, Citrix Virtual Apps and Desktops)
VMware, Inc. (VMware Horizon, VMware Workspace ONE)
Microsoft Corporation (Microsoft Azure Virtual Desktop, Microsoft 365)
Google LLC (Google Workspace, Google Cloud Virtual Desktops)
Cisco Systems, Inc. (Cisco Webex, Cisco Virtual Desktops)
Dell Technologies (Dell Cloud Client Workspace, Wyse Thin Clients)
IBM Corporation (IBM Cloud Virtual Server for VDI, IBM MaaS360)
Oracle Corporation (Oracle Virtual Desktop Infrastructure, Oracle Workspace Cloud)
Nutanix, Inc. (Nutanix Frame, Nutanix Xi Frame)
Trends in the WaaS Market:
Shift to Hybrid Work Models: As remote and hybrid work becomes more common, WaaS platforms are increasingly popular, offering businesses a way to manage and deliver workspaces in a flexible manner. This trend is particularly relevant in industries like tech, finance, and customer service.
Cloud Adoption: Cloud technologies continue to be a driving force in WaaS growth. With cloud infrastructure enabling easy scalability and remote access, businesses are rapidly moving their IT operations to the cloud, enhancing the demand for WaaS solutions.
Security and Compliance: With an increasing number of remote workers, security has become a paramount concern. WaaS platforms are focusing on improving data encryption, identity management, and compliance with regulations to address potential vulnerabilities in virtual environments.
AI and Automation Integration: The integration of artificial intelligence and automation in WaaS platforms is creating smarter and more efficient solutions. Automation tools are enhancing user experience, while AI-driven insights are improving workforce productivity and IT management.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3857
Market Segmentation:
By Component
Solution
Services
By Organizational Size
Large Enterprises
Small and Medium Enterprises
By Deployment Mode
Public Cloud
Private Cloud
Hybrid Cloud
By Industry Vertical
BFSI
IT and Telecom
Retail
Healthcare
Manufacturing
Government
Travel and Hospitality
Education
Market Analysis:
The WaaS market is currently expanding at a rapid pace, driven by the growing demand for flexible and scalable workspace solutions. The rise of cloud-based computing, coupled with the increased need for businesses to provide secure, remote work environments, has fueled market growth. According to recent market research North America and Europe lead the market, accounting for the majority of WaaS adoption, with Asia-Pacific also seeing significant traction due to its growing digital transformation initiatives.
Key players in the WaaS market include major cloud service providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These companies are offering advanced WaaS solutions that integrate with their broader cloud portfolios, positioning them well to capture a significant share of the market. Additionally, a rising number of startups and smaller companies are offering niche WaaS services, focusing on specific verticals and industries to cater to unique customer needs.
Future Prospects:
The future of WaaS looks incredibly promising as more organizations continue to prioritize flexibility and digital transformation. As businesses focus on reducing operational costs while enhancing employee productivity, WaaS will likely become a core component of IT infrastructure. Looking ahead, we can expect further innovations in automation, artificial intelligence, and machine learning to transform how digital workspaces are managed, providing even greater efficiencies and user experiences.
The growth of WaaS will also be influenced by increasing collaboration with other cloud-based services, such as communication and project management tools. As more businesses adopt integrated solutions, the WaaS market will continue to evolve, offering businesses even more sophisticated ways to manage remote teams and distributed workforces.
Access Complete Report: https://www.snsinsider.com/reports/workspace-as-a-service-market-3857
Conclusion:
The Workspace as a Service (WaaS) market is set to experience exponential growth in the coming years, driven by the increasing demand for flexible, secure, and scalable work environments. As organizations embrace hybrid and remote work models, WaaS platforms are becoming essential to facilitating collaboration, productivity, and secure data management across the workforce. With trends such as cloud adoption, AI integration, and enhanced security measures driving the market forward, WaaS will continue to play a pivotal role in shaping the future of work. By embracing WaaS solutions, businesses can streamline their IT infrastructure, reduce costs, and future-proof their operations for the digital age.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Workspace as a Service (WaaS) market#Workspace as a Service (WaaS) market Analysis#Workspace as a Service (WaaS) market Scope#Workspace as a Service (WaaS) market Growth
0 notes
Text
The global demand for Enterprise Mobility Management was valued at USD 16284.8 million in 2022 and is expected to reach USD 102147.4 Million in 2030, growing at a CAGR of 25.80% between 2023 and 2030.Enterprise Mobility Management (EMM) is an essential component in the modern business landscape, reflecting the increasing reliance on mobile devices and remote work solutions. EMM encompasses a suite of tools, processes, and technologies designed to manage and secure mobile devices, applications, and data used in enterprise settings. This market has seen significant growth in recent years, driven by the surge in mobile workforce, advancements in technology, and the need for enhanced security measures.
Browse the full report at https://www.credenceresearch.com/report/enterprise-mobility-management-market
Market Overview
The EMM market has expanded rapidly, with businesses recognizing the importance of mobile technology in enhancing productivity and operational efficiency. EMM solutions typically include mobile device management (MDM), mobile application management (MAM), mobile content management (MCM), and mobile identity management. These components collectively enable organizations to streamline their mobile operations, ensuring that devices and data are secure and compliant with corporate policies.
Drivers of Growth
1. Increasing Mobile Workforce: The rise of remote work and flexible working arrangements has led to a substantial increase in the use of mobile devices for business purposes. Employees now expect seamless access to corporate resources from anywhere, driving the demand for robust EMM solutions.
2. Advancements in Mobile Technology: The rapid evolution of smartphones, tablets, and mobile applications has created new opportunities for businesses to leverage mobile technology. EMM solutions are continually adapting to support these advancements, providing enhanced features and functionalities.
3. Data Security Concerns: With the proliferation of mobile devices, data security has become a critical concern for enterprises. EMM solutions offer comprehensive security features, including encryption, remote wipe, and policy enforcement, to protect sensitive corporate data.
4. Regulatory Compliance: Compliance with industry regulations and standards, such as GDPR, HIPAA, and others, necessitates stringent control over mobile devices and data. EMM solutions help organizations meet these regulatory requirements, reducing the risk of non-compliance.
5. BYOD Trend: The Bring Your Own Device (BYOD) trend has gained traction, allowing employees to use their personal devices for work purposes. EMM solutions enable organizations to manage and secure these devices effectively, ensuring a balance between productivity and security.
Key Players and Competitive Landscape
The EMM market is highly competitive, with numerous vendors offering a variety of solutions. Key players include Microsoft, IBM, VMware, Citrix, and BlackBerry. These companies are continually innovating to provide comprehensive EMM solutions that address the evolving needs of businesses.
- Microsoft: Known for its Intune platform, Microsoft offers a robust EMM solution integrated with its Office 365 suite, providing seamless management of mobile devices and applications. - IBM: IBM’s MaaS360 platform delivers comprehensive EMM capabilities, including advanced security features and AI-driven insights for proactive management. - VMware: VMware’s Workspace ONE platform offers unified endpoint management, integrating EMM with desktop management for a holistic approach. - Citrix: Citrix Endpoint Management provides a secure and user-friendly solution for managing mobile devices and applications, emphasizing user experience. -BlackBerry: Renowned for its security features, BlackBerry’s EMM solutions cater to industries with stringent security requirements, such as government and finance.
Challenges and Future Outlook
Despite its growth, the EMM market faces several challenges. Integrating EMM solutions with existing IT infrastructure can be complex and costly. Additionally, ensuring user adoption and compliance with EMM policies requires ongoing education and support.
Looking ahead, the EMM market is poised for continued growth, driven by advancements in artificial intelligence (AI) and machine learning (ML). These technologies will enable more predictive and proactive management of mobile devices, enhancing security and operational efficiency. Moreover, the increasing adoption of 5G technology will further fuel the demand for EMM solutions, enabling faster and more reliable mobile connectivity.
Key Players
Cisco Systems
SAP SE
Broadcom, Inc.
AppTec GmbH
IBM Corporation
Microsoft Corporation
VMware
Citrix Systems
Ivanti
Micro Focus
Zoho Corporation Pvt. Ltd
Matrix42
Sophos
Blackberry
Esper
Segmentation
By Mobile Device Management (MDM):
Device Inventory and Tracking
Security Policies
By Mobile Application Management (MAM):
App Distribution and Updating
App Security Policies
By Mobile Content Management (MCM):
Secure File Sharing
Content Encryption
By Identity and Access Management (IAM):
Single Sign-On (SSO)
Authentication and Authorization
By Unified Endpoint Management (UEM):
Integration of MDM, MAM, and MCM
Policy Enforcement
By Bring Your Own Device (BYOD) Solutions:
BYOD Policies
Containerization
By Industry Verticals:
Healthcare EMM
Financial Services EMM
Government EMM
By Deployment Models:
On-Premises EMM
Cloud-Based EMM
By Service Models:
Managed EMM Services
Consulting and Professional Services
By Enterprise Size:
Small and Medium-sized Enterprises (SMEs)
Large Enterprises
By Network Security Integration:
VPN Integration
Mobile Threat Defense
By Region
North America
The U.S.
Canada
Mexico
Europe
Germany
France
The U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of Middle East and Africa
Browse the full report at https://www.credenceresearch.com/report/enterprise-mobility-management-market
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
Website: www.credenceresearch.com
0 notes
Photo

#AirWatch #Maas360 #MDMVergleich #VMware #Android
MDM-Vergleich: VMware AirWatch vs. IBM Maas360

Die mobile device management (MDM) Markt ist überfüllt, die Unternehmen zahlreiche Optionen zum sperren beide Geräte und Daten. Aber Kommissionierung die beste Lösung ist nicht immer eine offensichtliche Wahl. Angesichts der Vielzahl von MDM-Lösungen für enterprise-Unternehmen, wie VMware...
Read More on http://dietech-welt.com/mdm-vergleich-vmware-airwatch-vs-ibm-maas360-3/
0 notes
Link
In the recent times, we’ve seen several big enterprises take the alleyway towards the app economy. This has caused a paradigm shift in how large corporations look at their business models today. By embracing the app culture, these enterprises are now looking at the bigger picture, where they’re aware of the huge scale benefits that mobility solutions have to offer. This not only gives them a competitive edge but also helps them in improving their performance through efficient resource planning that reduces wastage and increases the overall productivity.
0 notes
Text
RT IBMSecurity "How much time do you waste configuring endpoints? Learn from Forrester Consulting how customers spend 96% less time with #MaaS360."
RT IBMSecurity "How much time do you waste configuring endpoints? Learn from Forrester Consulting how customers spend 96% less time with #MaaS360."
— Ross Radev (@Ross_Radev) June 3, 2019
from Twitter https://twitter.com/Ross_Radev
1 note
·
View note
Text
Managed Network Services Market Growth and Status Explored in a New Research Report 2030
Global Managed Network Services Market: Snapshot
Information technology or IT as it is very popularly known as these days have become a part and parcel of our lives. In our day to day activities even in daily household chores IT play a very crucial role. IT infrastructure is, as such, very significant in each and every department of every company these days. With majority of workforce making use of multiple gadgets such as tablets, phones, laptops, and desktops, a sound infrastructure is very much needed. Handling of several servers, infrastructure security, remote infrastructure management, etc. are some of the key elements of managed network services. With the progress and evolution of in the IT department in each and every organization, the demand for managed network services will also increase.
Download PDF Brochure: https://www.tmrresearch.com/sample/sample?flag=B&rep_id=1880
Operational efficiency of every business is key to the growth of any company. This can be further achieved by streamlining the various processes that can assist in enhancing satisfaction of the customer and in turn further help in focusing more on the key revenue generating businesses. The organizations are making adoption of numerous business strategies so as to achieve these organizational goals.
Managed services model has been one such way of achieving this. It has been a practice of outsourcing day to day management functions and responsibilities as a strategic method for the purpose of improvement of business operations and cutting down of expenses which are considered unnecessary. These services could, however, comprise elements such as production support activities, lifecycle build or maintenance activities, and outsourcing HR activities.
Global Managed Network Services Market: Overview
Managed network services include automated network support solutions, such as managed wireless networks, managed gateways, and managed WAN and LAN, which are completely maintained and monitored by the service provider. They allow an organization to manage and operate an IP-based communication network by sourcing the required technical support services, software, and infrastructure. However, hardware infrastructure resources could also be provided along with firewall protection to secure the backend data and infrastructure. Managed network services help a company to focus on core business while leveraging sophisticated network technologies and raise its cost and product efficiencies.
Global Managed Network Services Market: Key Trends
The demand in the world managed network services market could be spurred due to the hot requirement for user identity authentication, powerful transaction security, and more solutions associated with managed network services. Since companies customize their services based on the needs of end users, there could be a rising trend of conventional network infrastructures being replaced by those featuring enhanced accessibility. In this regard, network security is also expected to be improved with elevated efficiency at the slightest of costs. Consequently, a larger market share is anticipated to be secured by managed Internet access and network infrastructure provisioning.
Key characteristics of the product such as making a network more reliable and flexible and curbing the coast-to-coast cost of operation are predicted to set the tone for the global managed network services market. End users of managed network services are facilitated with commanding backup-enabled data storage, network security, network monitoring, and network infrastructure. Telecom and IT are envisaged to emerge as the dominating end users of the world market.
Global Managed Network Services Market: Market Potential
IBM is proud to announce the launch of its new cognitive assistant that works to take up the challenge of efficiently managing a sprawl of devices, including IoT devices, laptops, tablets, smartphones, across different businesses. The IBM MaaS360 Advisor taps into the vital capabilities of IBM Watson to not only manage devices but also their networks. It is able to recommend the best customized practices, patches, and policies and analyze devices on a network to better manage and protect them. Importantly, it is now included in the unified endpoint management (UEM) platform of IBM MaaS360 delivered via the IBM Cloud.
Global Managed Network Services Market: Regional Outlook
By the concluding year of the forecast period, North America is envisioned to hold a king’s share in the international managed network services market. Not lagging behind by a bigger margin, Asia Pacific could be a faster growing regional market on the back of an impressive number of budding service companies in the IT and networking field. One of the critical factors propelling the growth in Asia Pacific could be the heated competition between multiple players and their presence to provide the best of cloud-based and managed services. Other regions forecasted to hold some prominence in the market are Europe and Rest of the World.
Global Managed Network Services Market: Competitive Landscape
The only deterrent that could hamper the growth of the international managed network services market is the failure in following recommended practices and maintaining compliance to ensure enhanced network security. However, players in the market are projected to count their advancement on collaborations, new product developments, contracts, and product enhancements for rising above the odds. Ericsson, Cisco Systems, Inc., AT&T Inc., Alcatel-Lucent Enterprise, Accenture, and Hewlett Packard Enterprise Development LP are some of the toughest players operating in the industry.
Key questions answered in this report
What are the diverse growth parameters influencing the market?
Which regions will contribute largely to the growth of the market
What are the recent innovations and technological advancements in the market?
What are the emerging trends across the market?
How has COVID-19 affected the market?
What will be the post-pandemic scenario of the market?
What are the major threats that will dent the growth prospects of the market?
For Full TOC:
https://www.tmrresearch.com/sample/sample?flag=T&rep_id=1880
About Us:
TMR Research is a premier provider of customized market research and consulting services to business entities keen on succeeding in today’s supercharged economic climate. Armed with an experienced, dedicated, and dynamic team of analysts, we are redefining the way our clients’ conduct business by providing them with authoritative and trusted research studies in tune with the latest methodologies and market trends.
Contact Us:
Rohit Bhisey
Head Internet Marketing
Tel: +1-415-520-1050
Website: https://www.tmrresearch.com/
0 notes
Text
Qradar Ahnlab
Qradar Ahnlab 7
Qradar Ahnlab Log
Author(s):

László Czap | Created:
28 March 2020 |
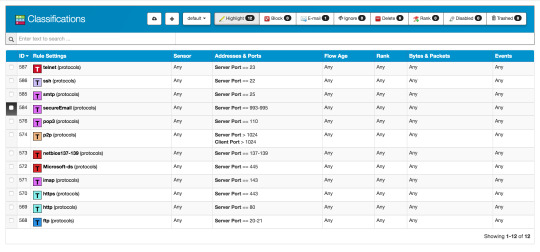
This video covers an Introduction to QRadar and Tuning and is video 1 in a series on IBM QRadar Tuning Best Practices. The full playlist for this series is a. Purpose-built for security, IBM QRadar includes out-of-the-box analytics, correlation rules and dashboards to help customers address their most pressing security use cases – without requiring significant customization effort. Learn how QRadar can you help address your use cases.
Last modified: 14 January 2021 Tested on: -
Log sources using syslog are very easy to test in QRadar. However, there are some device types that have only polling type (or file based) protocols as configuration options. Among others, Amazon AWS, IBM BigFix, IBM MaaS360, Cisco IPS are such examples. For these, firing a syslog event with the same format and the same logsourceid in the header is useless, because the log source configuration will not match.
The following workaround can be applied to generate test syslog events for these log sources. This is to be used only in test environments (you don't want to litter your production system with test events anyway).
Go to your console and get a psql connection:

The table sensordeviceprotocols contains the log source type and protocol associations. We add a row to this table such that our tested log source accepts syslog. This table works with identifiers, so you need to find the id of your log source type. For this, use the sensordevicetype table and look for the id column. The column devicetypedescription will help you find the right row. E.g. to find the MaaS360 log source:
This query returns
so we know the id we look for is 361. We also need the id of the syslog protocol, which is 0 (you can find it out from the table sensorprotocol).
Having this we insert a new row:
Here, the third value is just a unique identifier, whereas the last indicates that this is undocumented.
Now, if you go back to QRadar UI, and try to add a new log source of your selected type, in the drop-down menu a new item appears: Syslog (Undocumented). Select this, and all you need is to provide a logsourceid and save the new log source. You must use the same id as you provided here in your syslog header when sending in your test events.
After these changes, you need to restart the eventprocessing service. I did
but maybe this is an overkill.
Hint: If you want that the test events look like they come from an existing real log source of the same type, you need to create a new log source of the same type, but with the new Syslog (Undocumented) protocol configuration. When creating this, use the same logsourceid as you have in the real log source and make sure that the parsing order prefers the real log source. This way the test log source will never receive any events, all your test events will seem to belong to your original log source.
Qradar Ahnlab 7
Here is the list of log sources for which this workaround should come handy:
Qradar Ahnlab Log
AhnLab Policy Center APC
Akamai KONA
Amazon AWS CloudTrail
Box
Cisco Cloud Web Security
Cisco Identity Services Engine
Cisco Intrusion Prevention System (IPS)
Fasoo Enterprise DRM
Flow Classification Engine
HP Tandem
IBM BigFix
IBM BigFix Detect
IBM Informix Audit
IBM Fiberlink MaaS360
IBM Lotus Domino
IBM Privileged Session Recorder
IBM Proventia Management SiteProtector
IBM Proventia Network Intrusion Prevention System (IPS)
IBM Security Identity Governance
IBM Security Identity Manager
IBM Security Privileged Identity Manager
IBM SmartCloud Orchestrator
Juniper Networks AVT
Juniper Security Binary Log Collector
Kisco Information Systems SafeNet/i
McAfee Application/Change Control
Microsoft Endpoint Protection
Microsoft Operations Manager
Microsoft SCOM
Microsoft Windows Defender ATP
Netskope Active
ObserveIT
Open LDAP Software
OpenStack
Oracle Audit Vault
Oracle BEA WebLogic
Oracle Enterprise Manager
Oracle Fine Grained Auditing
Pirean Access: One
Resolution1 CyberSecurity
Riverbed SteelCentral NetProfiler
Riverbed SteelCentral NetProfiler Audit
Salesforce Security Auditing
Salesforce Security Monitoring
Seculert Seculert
SOAP Webservice-based messages, pre-normalized
Sophos Enterprise Console
Sophos PureMessage
Sun ONE LDAP
Sybase ASE
Symantec Critical System Protection
Symantec System Center
Trend Micro Control Manager
Trend Micro Office Scan
VMware vCloud Director

The method above was tested on version 7.3.2., table structure might change without notice. You lose your support if you modify psql tables.
1 note
·
View note
Text
What is network safety? What is network safety? Network safety is the act of safeguarding basic frameworks and delicate data from advanced assaults.
What is network safety?
Network safety is the act of safeguarding basic frameworks and delicate data from advanced assaults. Otherwise called data innovation (IT) security, online protection measures are intended to battle dangers against arranged frameworks and applications, whether those dangers begin from inside or outside of an association.
In 2020, the normal expense of an information break was USD 3.86 million internationally, and USD 8.64 million in the United States. These expenses incorporate the costs of finding and answering the break, the expense of vacation and lost income, and the long haul reputational harm to a business and its image. Cybercriminals focus on clients' actually recognizable data (PII) - names, addresses, public ID numbers (e.g., Social Security number in the US, financial codes in Italy), and Visa data - and afterward sell these records in underground advanced commercial centers. Compromised PII frequently prompts a deficiency of client trust, the inconvenience of administrative fines, and, surprisingly, lawful activity.Security framework intricacy, made by dissimilar advancements and an absence of in-house mastery, can intensify these expenses. Be that as it may, associations with an extensive online protection system, represented by best practices and robotized utilizing progressed examination, man-made consciousness (AI) and AI, can battle cyberthreats all the more really and lessen the lifecycle and effect of breaks when they happen.Network safety spacesA solid network safety system has layers of security to protect against digital wrongdoing, including digital assaults that endeavor to access, change, or annihilate information; coerce cash from clients or the association; or intend to upset typical business tasks. Countermeasures should address:Basic foundation security - Practices for safeguarding the PC frameworks, organizations, and different resources that society depends upon for public safety, financial wellbeing, and additionally open security. The National Institute of Standards and Technology (NIST) has made a network protection structure to help associations around here, while the U.S. Division of Homeland Security (DHS) gives extra direction.Network security - Security measures for shielding a PC network from gatecrashers, including both wired and remote (Wi-Fi) associations.Application security - Processes that assist with safeguarding applications working on-premises and in the cloud. Security ought to be incorporated into applications at the plan stage, with contemplations for how information is taken care of, client validation, and so onCloud security - Specifically, genuine classified registering that encodes cloud information very still (away), moving (as it goes to, from and inside the cloud) and being used (during handling) to help client protection, business prerequisites and administrative consistence principlesData security - Data assurance measures, like the General Data Protection Regulation or GDPR, that safe your most delicate information from unapproved access, openness, or robbery.End-client training - Building security mindfulness across the association to fortify endpoint security. For instance, clients can be prepared to erase dubious email connections, try not to utilize obscure USB gadgets, and so forthFiasco recuperation/business progression arranging - Tools and techniques for answering impromptu occasions, like catastrophic events, blackouts, or network safety episodes, with negligible disturbance to key tasks.Capacity security - IBM FlashSystem® conveys unshakable information versatility with various protections. This incorporates encryption and changeless and disengaged information duplicates. These stay in a similar pool so they can rapidly be reestablished to help recuperation, limiting the effect of a digital assault.Versatile security - IBM Security MaaS360 with Watson empowers you to oversee and protect your portable labor force with application security, compartment application security and secure portable mail.Hazardous network safety fantasiesThe volume of network safety occurrences is on the ascent across the globe, yet misguided judgments keep on continuing, including the thought that:Cybercriminals are pariahs. In all actuality, network protection breaks are regularly the aftereffect of malevolent insiders, working independently or working together with outside programmers. These insiders can be a piece of efficient gatherings, upheld by country states.Gambles are notable. As a matter of fact, the gamble surface is as yet growing, with great many new weaknesses being accounted for in old and new applications and gadgets. Also, open doors for human mistake - explicitly by careless workers or workers for hire who unexpectedly cause an information break - continue to increment.Assault vectors are contained. Cybercriminals are tracking down new assault vectors constantly - including Linux frameworks, functional innovation (OT), Internet of Things (IoT) gadgets, and cloud conditions.My industry is protected. Each industry has its portion of online protection gambles, with digital enemies taking advantage of the necessities of correspondence networks inside pretty much every administration and private-area association. For instance, ransomware assaults (see underneath) are focusing on more areas than any time in recent memory, including neighborhood states and non-benefits, and dangers on supply chains, ".gov" sites, and basic foundation have likewise expanded.Normal digital dangersDespite the fact that network safety experts make a solid effort to close security holes, aggressors are continuously searching for better approaches to get away from IT notice, avoid guard measures, and take advantage of arising shortcomings. The most recent online protection dangers are rethinking "known" dangers, exploiting telecommute conditions, remote access instruments, and new cloud administrations. These advancing dangers include:MalwareThe expression "malware" alludes to malevolent programming variations like worms, infections, Trojans, and spyware-that give unapproved access or cause harm to a PC. Malware assaults are progressively "fileless" and intended to get around natural recognition techniques, for example, antivirus instruments, that sweep for pernicious record connections.RansomwareRansomware is a kind of malware that secures records, information or frameworks, and takes steps to delete or obliterate the information - or make private or touchy information to the general population - except if a payment is paid to the cybercriminals who sent off the assault. Late ransomware assaults have designated state and nearby legislatures, which are more straightforward to break than associations and constrained to pay ransoms to reestablish applications and sites on which residents depend.Phishing/social designingPhishing is a type of social designing that fools clients into giving their own PII or delicate data. In phishing tricks, messages or instant messages have all the earmarks of being from a genuine organization requesting delicate data, for example, Mastercard information or login data. The FBI has noted about a flood in pandemic-related phishing, attached to the development of remote work.Insider dangersCurrent or previous workers, colleagues, project workers, or any individual who has approached frameworks or organizations in the past can be viewed as an insider danger assuming they misuse their entrance consents. Insider dangers can be undetectable to customary security arrangements like firewalls and interruption recognition frameworks, which center around outside dangers.
Dispersed disavowal of-administration (DDoS) assaults
A DDoS assault endeavors to crash a server, site or organization by over-burdening it with traffic, for the most part from numerous planned frameworks. DDoS assaults overpower venture networks through the basic organization the board convention (SNMP), utilized for modems, printers, switches, switches, and servers.
Progressed relentless dangers (APTs)
In an APT, a gatecrasher or gathering of interlopers penetrate a framework and stay undetected for a drawn out period. The interloper leaves organizations and frameworks in one piece so the gatecrasher can keep an eye on business movement and take delicate information while staying away from the actuation of guarded countermeasures. The new Solar Winds break of United States government frameworks is an illustration of an APT.
Man-in-the-center assaults
Man-in-the-center is a snoopping assault, where a cybercriminal catches and transfers messages between two gatherings to take information. For instance, on an unstable Wi-Fi organization, an assailant can capture information being passed between visitor's gadget and the organization.
Key network protection advancements and best practices
The accompanying accepted procedures and advances can assist your association with carrying out solid network safety that decreases your weakness to digital assaults and safeguards your basic data frameworks, without interrupting the client or client experience:
Personality and access the executives (IAM) characterizes the jobs and access honors for every client, as well as the circumstances under which they are conceded or denied their honors. IAM philosophies incorporate single sign-on, which empowers a client to sign in to an organization once without returning accreditations during a similar meeting; multifaceted validation, requiring at least two access certifications; advantaged client accounts, which award authoritative honors to specific clients just; and client lifecycle the board, which deals with every client's character and access honors from introductory enlistment through retirement. IAM devices can likewise give your network protection experts more profound perceivability into dubious action on end-client gadgets, including endpoints they can't genuinely get to. This helps speed examination and reaction times to detach and contain the harm of a break.
An extensive information security stage safeguards touchy data across various conditions, including half and half multicloud conditions. The best information security stages give mechanized, continuous perceivability into information weaknesses, as well as progressing checking that makes them aware of information weaknesses and dangers before they become information breaks; they
0 notes
Text
Futurism Launches ‘Zero Trust Managed Security Acceleration Services’
Futurism Launches ‘Zero Trust Managed Security Acceleration Services’
Stay ahead of the threats with our Zero Trust architecture. Futurism Technologies, a leading IBM Global Security Solutions Partner, rolls out ‘Zero-Trust Managed Security Acceleration Services’ powered by best-of-breed IBM Security Solutions viz. IBM QRadar, IBM Maas360, IBM Verify and IBM Guardium Data Protection, all integrated with IBM Watson – the AI for smarter business. Zero Trust is a…

View On WordPress
0 notes
Text
Setting up ActiveSync settings in MaaS360 policy not working
Setting up ActiveSync settings in MaaS360 policy not working
We recently started using MaaS360 and everything is working fine except setting up the ActiveSync settings in the policy for devices. When I use the normal URL of ‘outlook.office365.com’ it works for a user account that does not have MFA enabled. For user accounts that have MFA enabled it does not work. I have a feeling it might have something to do with enabling Oauth sign in. It asks for Oauth…
View On WordPress
0 notes
Text
Teamviewer For Mac Old Version
Teamviewer For Mac Old Version Torrent
Teamviewer For Mac Old Version Update
Teamviewer For Mac Old Version
Teamviewer costs from $49 per month for a single user ($588 per year) for its lowest tier plan – rising to $99 per month for up to 20 users or $199 per month for up to 200 users.
That's surprisingly good value, for one of the best remote access software solutions around, and regular Teamviewer deals and discounts can keep its prices keener, still.
Doesn't work as advertised. Specifically, syncing across devices is unreliable and moving to a new phone number after the unexpected failure of an old phone has resulted in a loss of account access. As a Twitch streamer, losing access to my accounts in the name of 'security' is unbearably frustrating. Whatever the older Macintosh computer is, to make it useful nowadays you’d likely want to find and download some old Mac software for it. This post will aggregate a collection of links and resources for finding and downloading old Mac software, including old Mac system software, old Macintosh applications, and more, for everything from older Intel Macs, to PowerPC Macs, to 68040 and 030 Macs.
Whether in the workplace or as part of a distributed workforce around the globe, practically all modern white collar workers use computers that IT teams will need to access. As a result, remote access software can be a huge boon for most businesses.
Here's what you need to know about Teamviewer and its various pricing plans.
In this guide:
TeamViewer Pricing Plans
TeamViewer's cheapest plan costs $49 per month, billed annually for $588 per year. TeamViewer also offers two other plans, which allow more participants, devices and controls, starting at $99 per month and $199 per month.
TeamViewer also offers add-ons and third-party integrations, as well as a free 14-day trial.
Here's a breakdown of each of the three main plans, all of which include phone-based tech support.
Licensed users
Managed devices
Need a tailored quote for your business today?
Business License
The Business license costs $49 per month, and is billed annually at $588. It's for a single user, and allows them to connect up to three devices, with nine additional movements per year for any users who need to exchange one device for another. The number of managed devices is capped at 200.
It'll let the user connect and control computers remotely and securely, with remote printing access, file sharing, and cross platform access (from Windows to Mac or vice versa, in other words). Meeting participants are capped at five.
Premium License
The Premium license costs $99 per month, billed annually at $1,188. It's best for businesses with multiple people who need access, as its user cap is 50 – significantly up from the single Business user – with up to 300 managed devices, and 15 meeting participants.
It offers all the same features, plus customized device information and user access reporting, so you'll always know who accessed what and when. One channel is included, though businesses can add up to 10, in order to allow multiple sessions at a time.
Teamviewer For Mac Old Version Torrent
Corporate License
The Corporate license costs $199 per month, billed annually at $2,388. It's aimed at teams, as they may need to remotely access a device as a group, or simultaneously access multiple devices. One license includes 200 users, 25 meeting participants, and up to 500 managed devices.
Features include everything in Premium, plus a mass deployment feature for installing TeamViewer across hundreds of devices at once, device access reporting for better audits, and the tools to add third-party integrations with CRM, customer support, or help desk systems.
TeamViewer Integration & Add-Ons
Add-Ons
TeamViewer offers five add-ons.
First, there's TeamViewer Remote Management, a general term for three different services from which users can choose which they need: Monitoring & Asset Management, which costs $1.91 per month per endpoint, billed annually; Endpoint Protection, a randsomware protection service costing $1.91 per month per endpoint, billed annually; and Backup, for just $0.10 per month per endpoint, also billed annually.

Then there's Support for Mobile Devices, an add-on that supports iPad, iPhone, and Android devices from your desktop computer for $32.90 per month, billed annually at $394.80.
TeamViewer's Servicecamp service desk lets users offer simple ticket management to their customers, costing $9.90 per month per agent, billed annually at $118.80 per agent. The TeamViewer Pilot add-on takes the remote service desk even further, empowering technicians to guide customers through complex processes with an augmented reality tool, for $39.00 per month per technician, billed annually at $468.00 per technician.
Finally, there's Extra Concurrent Users, the add-on that businesses should opt for if they need more users than the Premium plan's 50 users, or the Corporate plan's 200 users. This add-on isn't available for the Business plan, which is only for a single user.
Integrations
The third-party integrations available for TeamViewer users come in six main categories: CRM, Internet of Things, IT Service Management, Remote Monitoring and Management, Unified Endpoint Management, and User Account Creation.
The CRM category includes Helpdesk tools as well, with four integrations: ZenDesk, Salesforce, Zoho, and Microsoft Dynamics 365. The Internet of Things include IBM Maximo and Synology; IT Service Management includes Freshworks, JIRA, Cherwell, and Servicenow; while Remote Monitoring and Management includes SysAid and Ninja RMM.

Unified Endpoint Management has the most integrations: Microsoft Intune, IBM MaaS360, EloView, Sophos, AppTec360, and MobileIron. Finally, there's User Account Creation/Deactivation, which includes Active Directory and Okta.
Is TeamViewer free?
In an unusual move, TeamViewer is indeed free for personal use.
Students can download a free copy for their own use, and so can anyone who needs to offer the occasional IT support to a Luddite friend or family member. The software will work forever, at no charge.
Teamviewer For Mac Old Version Update
Anyone who wants to use it for commercial purposes, however, will be limited to the 14-day free trial, which offers full functionality and should be enough to let users know if they'll benefit from the paid service.
TeamViewer Pros and Cons
TeamViewer is a great application for a specific challenge that many modern companies face: How to quickly and easily address all their workers' IT needs. The software offers an IT team remote control of all employees' devices. This can be used for desktop sharing to install new services or troubleshoot problems, and it can also support online meetings and conferences as well as remote file transfers.
On the “cons” side, first and foremost there's the price, which many users find a little too high – particularly once the add-ons are factored in. In addition, there's a lag problem that is unavoidable if the destination device's software is too old, though it's not a concern as long as the client computers or mobile devices are kept up to date.
Finally, some features offered by competitor services are missing from TeamViewer: There's no ability with the basic plans to freeze screens remotely, or to see through a client device's camera.
TeamViewer Features
TeamViewer packs plenty of general features, even beyond the ones that this article highlighted earlier. Here are the noteworthy examples:
Remote Access
Remote Support
File Sharing
Real-time Chat
Screen Sharing
Session Recording
Session Transfer
Access Control
Collaboration
Diagnostics Tools
File Transfer
Mobile Access
Remote Printing
Reporting and Analytics
Customizable customer modules
Meetings and Presentations
Wake-on-LAN
Ultimately, TeamViewer offers all the essential abilities and tools a remote access software should, even if some of them are only available through additional paid add-ons.
TeamViewer Benefits
Due to its feature-rich approach to remote device access, TeamViewer offers a range of benefits that can all add up to a lot of money saved at the end of the year.
First, TeamViewer makes it simple to transfer or pass control from one party to another, speeding up the workflow and boosting productivity as a result. How often does your business need to pass control of a device to someone else? The more you do, the greater the benefit of using TeamViewer.
A simple app that lets you text, video chat, and stay close with people you care about. Turn off the light in Dark Mode Give your eyes some rest with a sleek new look. Facebook messenger desktop app mac ios. Simply go to Messenger.com and sign in to use the app on your desktop. Alternatively, an unofficial option would be to download a third-party app called Messenger for Desktop. Keep in mind that this is not an official Facebook app, but it will get the job done.
Another big TeamViewer benefit is support for team sessions, which let administrators manage multiple parties at the same time. If you have tight-knit teams that may need upgrades or new software as a group, TeamViewer is an easy way to bring them on board.
And if any of your employees need to share files with any other teammates on a regular basis, TeamViewer's quick and easy file sharing ability uses a drag-and-drop interface to help employees collaborate. Install multiple fonts mac.
So, is TeamViewer worth shelling out for? It depends on your business's needs: If you frequently find yourself facing technical challenges due to the wide range of platforms and devices used by your employees, adapting TeamViewer might ultimately save you money in the long run. But if you don't, it may not justify the price tag.
Technical Details
The TeamViewer remote access software works across all the main devices and platforms, including Windows, Mac, Linux, Android, iOS, iPhone/iPad, Windows Mobile, and web-based services.
Deployment can be web-based, cloud-based, or via SaaS.
Training options include an online knowledge base and community forum, an academy, and customized packages that include in-person training. Have any questions or concerns? Support is available during business hours via email, phone, or live chat.
TeamViewer Alternatives
If you're still not sold on TeamViewer, that's okay. It's not the only remote access software in the game, and the two top competitors aren't too shabby.
LogMeIn Central costs just $9.95 per month per user, making it the clear budget choice. It's available for Windows, Mac, iOS, and Android, and offers the suite of features needed to address your clients' IT problems in stride. However, lag time is a concern, and the support team isn't as responsive as one would hope, according to user reviews.
See how the two tools stack up in our Teamviewer vs LogMeIn head-to-head guide
Zoho Assist offers diagnostic tools and live chat alongside the file and screen sharing, session transfer, and remote access features you'd expect. The software doesn't offer some features unless you shell out for a higher-priced plan. In addition, the phone and browser apps can occasionally take a few moments to properly sync, which bugs some customers. It starts at $18 per user, per month.
Splashtop Remote Support is another popular option, with support for all major platforms and clients including big brands like Toyota, AT&T, and UPS. Plus, there's the Germany-based AnyDesk, priced at a bracing $10.99 per month and with over a hundred million users across the globe.
Any one of these four remote access solutions is a reasonable alternative to TeamViewer, offering the features and functionality businesses are looking for.
TeamViewer FAQs
What is the difference between TeamViewer free and paid?
The free version of TeamViewer is only for personal use, while the paid version is for commercial use. If you're not a business and you don't directly profit from using TeamViewer, you're free to download the complimentary version available from the TeamViewer website.
If you use TeamViewer within an organization, even a nonprofit one, you'll need to pay for a subscription. Furthermore, if you use a personal version, you'll have more limited features, as some abilities can only be unlocked with a license.
How long does a free TeamViewer session last?
TeamViewer's sessions will last just as long for the free version as for the paid one, with a maximum time limit of 8 hours.
However, if users would like to set a limit in order to avoid idle sessions that last all day despite no one benefiting from them, users can define an idle session timeout from anywhere between 30 minutes to 8 hours.
How many members can connect in TeamViewer?
The amount of members who can connect in TeamViewer depends on which plan you have licensed. The Business plan allows five meeting participants, the Premium plan allows 15, while the Corporate plan allows 25 participants.
If you're just looking for the number of users whose devices can be accessed one at a time by TeamViewer technicians, the Business plan supports 200, the Premium plan supports 300, while the Corporate plan supports 500.
Can TeamViewer spy on you?
No, TeamViewer can't be used to spy on your device without your consent.
Can TeamViewer see what I am doing?
Teamviewer For Mac Old Version
Yes – if the TeamViewer software is currently connected to your device, then an agent can potentially be watching your screen. TeamViewer is connected when the TeamViewer panel is visible, typically on the upper righthand side of the screen on a desktop view. If you'd like to disconnect from TeamViewer, just click the dropdown menu and select the “close” option.

0 notes
Photo

#AirWatch #Maas360 #MDMVergleich #VMware #Android
MDM-Vergleich: VMware AirWatch vs. IBM Maas360
Die mobile device management (MDM) Markt ist überfüllt, die Unternehmen zahlreiche Optionen zum sperren beide Geräte und Daten. Aber Kommissionierung die beste Lösung ist nicht immer eine offensichtliche Wahl. Angesichts der Vielzahl von MDM-Lösungen für enterprise-Unternehmen, wie VMware...
Read More on http://dietech-welt.com/mdm-vergleich-vmware-airwatch-vs-ibm-maas360/
0 notes
Photo

Securing Your Team’s Devices with MDM
The technology landscape continues to shift by introducing new devices, a growing remote and mobile workforce, and rising mobile employees’ expectations. And while Bring Your Own Devices (BYOD) initiatives have traditionally been popular choices for companies because enterprises save money on device procurement and monthly service charges, BYOD can make ongoing security and device management more difficult. That’s primarily because when employees own their ‘work’ devices, they’re far less likely to update enterprise applications or security software, and that’s if they even install security programs in the first place. On top of that, a BYOD mobility strategy pushes more burdens onto internal IT teams to manage a wide variety of devices. When employees are free to bring their devices into work, IT teams are left managing different device brands, models, and operating systems. This diversity can mean more important support requirements too. That’s because inevitably, users have questions about connecting devices, accessing applications, and, of course, password resets.
Facing these challenges, what can companies do to get smarter about balancing telecom and mobility needs? It starts with Mobile Device Management (MDM). MDM solutions enable centralized management of both business-owned and BYOD personal smartphones, tablets, and other mobile devices. Smart MDM policies, backed by an integrated MDM solution, allow IT teams to handle their telecom and mobility challenges by making it more manageable to secure and enforce policies for devices used for work. There are several options for MDM and mobile application management, including a solution from Microsoft. New changes coming to Microsoft’s hybrid’ MDM solution may leave enterprises asking what we do next?
Changes to MDM are coming
The Microsoft Intune and System Center Configuration Manager (SCCM) is a solution it calls ‘hybrid MDM.’ Microsoft is discontinuing development for the hybrid connector solution, including policies, apps, and security. Previously using it, customers could manage mobile devices through SCCM by using a connector to Intune. Microsoft is urging users to adopt Intune on Azure for MDM instead. The MDM system is a service hosted by Microsoft for mobile device and mobile application management. It allows for the co-management of devices, where customers get both on-premise and cloud-based management capabilities. Microsoft will bundle advanced mobility management options using Microsoft 365 solutions, including Office 365 applications, Windows 10, and the Enterprise Mobility + Security offering, including Intune. To switch to Intune on Azure, Microsoft recommends synchronizing groups with Azure Active Directory and importing data with Microsoft’s Data Importer tool. By using co-management, you have the flexibility to use the technology solution that works best for your organization. (Source: Microsoft).
Exploring other options
For those not wanting to switch to Intune on Azure, there are other MDM options out there. Another cloud-based platform is VMware’s Workspace One Unified Endpoint Management (UEM) solution. It works by deploying micro-VPNs for mobile users, enabling IT teams to implement centralized security policies and manage the operating systems across devices. As users increasingly work remotely from traditional and mobile devices, and enterprises incorporate IoT and other new technologies, unified endpoint management has evolved to solve the problems modern IT departments encounter when securing and connecting these environments (Source: VMWare). Cisco Meraki Systems Manager and IBM’s MaaS360 are two other MDM solutions that help safeguard mobile devices and give IT teams a powerful suite of tools to handle management and security from a single screen (Source: Spiceworks).
Linking mobility and innovation
Mobile technology is now a critical component to supporting innovation in the workplace. But, IT teams need tools to configure and activate devices and simplify management and security efficiently. But, getting mobile device management right can be challenging too. That’s especially true if your business has become accustomed to using ‘hybrid MDM’ with Microsoft Intune. Whatever route your organization takes, mobile device management solutions can help you keep pace with more mobile devices in the workplace while supporting innovation – giving teams instant access to secure data whenever and wherever they need it.
0 notes
Text
Mobile Device Management Market Key Insights Based on Product Type, End-Use and Regional Demand Till 2020-2027
The GMI Research expects the mobile device management market to expand at a significant rate. From a regional perspective, North America is expected to increase at a faster CAGR due to the high demand for improved technology across several end-use verticals. Various companies are introducing enterprise mobility solutions, which aid enterprises in managing the increasingly dynamic mobile workforce.
Request for a FREE Sample Report on Mobile Device Management Market
Mobile Device Management Market Dynamics (including market size, share, trends, forecast, growth, and industry analysis)
Key Drivers
The growing adoption of bring your own device (BYOD) and the increasing security concerns to prevent a large amount of corporate data are the key drivers responsible for the growth of the global mobile device management market size. There is an emerging mobile device management market trend of bring your own device (BYOD) in various organizations. Moreover, the continuous increase of the fleet of mobile devices has become an important consideration for every company. This has motivated the companies to use a platform that offers a high level of data protection. As per the mobile device management market report, leaders in the global mobile device management market emphasize on broader enterprise mobility management (EMM) solutions to cater and serve the mobile opportunity in an improved way. For example, in 2019, in partnership with Watson, IBM declared the introduction of its new IBM MaaS360, which is the first-ever android enterprise that suggested EMM solutions. These factors are bolstering the growth of the global mobile device management market share in terms of revenue.
According to the mobile device management market research, the emergence of the COVID-19 pandemic has a positive influence on the demand of the market due to the increasing adoption of work-from-home culture by various service firms. Any employee who works remotely raises the risk of compliance deficiency and carries a risk to the sensitive data of the firm. Due to this, firms are opting for mobile device management solutions to strengthen security and supervision features to decrease these risks, which will further accelerate the market growth.
Vertical Segment Drivers
Based on the vertical, the BFSI segment is projected to increase at a faster CAGR due to the emerging trend of the bring your own device (BYOD) in the BFSI sector, which has raised the adoption of mobile devices management solutions. Several enterprises in the BFSI industry continuously emphasize on enhancing workplace mobility to improve employee productivity and satisfaction. These factors are contributing to the growth of the segment.
Mobile Device Management Market’s leading Manufacturers:
· BlackBerry Limited
· IBM
· MOBILEIRON, INC.
· Microsoft
· Citrix Systems, Inc.
· VMware, Inc
· Sophos Ltd.
· Zoho Corp
· SAP
· SOTI Inc.
Mobile Device Management Market Segmentation:
Segmentation by Component:
· Solutions
o Device Management
o Application Management
o Security Management
o Others
· Services
o Professional Services
o Managed Services
Segmentation by Operating System:
· IOS
· Android
· Windows
· macOS
· Others
Segmentation by Deployment Type:
· On-Premises
· Cloud
Segmentation by Vertical:
· IT & Telecommunication
· BFSI
· Healthcare
· Retail
· Government
· Manufacturing
· Others
Segmentation by Region:
· North America
o United States of America
o Canada
· Asia Pacific
o China
o Japan
o India
o Rest of APAC
· Europe
o United Kingdom
o Germany
o France
o Spain
o Rest of Europe
· RoW
o Brazil
o South Africa
o Saudi Arabia
o UAE
o Rest of the world (remaining countries of the LAMEA region)
About GMI Research
GMI Research is a market research and consulting company that provides syndicated research reports, consulting services, and customized market research reports. Our reports are based on market intelligence studies to ensure relevant and fact-based research across numerous sectors, including healthcare, automotive, information technology & communication, FMCG, and other industries. GMI Research’s deep understanding related to the business environment helps us in generating objective strategic insights. Our research teams consisting of seasoned analysts and researchers have hands-on experience in various regions, including Asia-pacific, Europe, North America, and the Rest of the World. The market research report offers in-depth analysis, which contains refined forecasts, a bird's eye view of the competitive landscape, factors impacting the market growth, and several other market insights to aid companies in making strategic decisions. Featured in the ‘Top 20 Most Promising Market Research Consultants’ list of Silicon India Magazine in 2018, we at GMI Research are always looking forward to help our clients to stay ahead of the curve.
Media Contact Company Name: GMI RESEARCH Contact Person: Sarah Nash Email: [email protected] Phone: Europe – +353 1 442 8820; US – +1 860 881 2270 Address: Dublin, Ireland Website: www.gmiresearch.com
0 notes