#inspection app development
Explore tagged Tumblr posts
Link
Inspection app development is revolutionizing the way inspections are conducted, improving accuracy, efficiency, and speed. As technology continues to advance, inspection apps are likely to become even more sophisticated, providing even greater benefits to businesses looking to streamline their operations. With the ability to customize apps to fit the specific needs of a business, inspection app development is a powerful tool for improving inspection processes and transforming industries.
0 notes
Text
Tech Wizards or Just Coffee-Fueled Geniuses? Meet Zamorins Solutions Inc.

Have you ever wondered how great ideas become digital realities? We prefer to think of ourselves at Zamorins Solutions Inc. as tech wizards, but without the wands and with a lot of coffee. Our team works behind the scenes (and screens) to provide organizations with the digital advantage they require, from developing custom software to creating mobile apps that people genuinely want to use.
You require a website that greets visitors with "hello world" and no awkward silences. We'll take care of you. Or about an app that simplifies everyday chores? Completed. We are the type of issue solvers that not only thought creatively but have also created ground-breaking applications.
So, keep in mind that Zamorins is here to fulfill your digital dreams—without the magic spells, but definitely with the coffee—whether you require a website makeover or a whole custom software rework.
#mobile application development#mobile app company#appdevelopment#web design#marketing#software engineering#technology#inspection#commercial#success
0 notes
Text
Live Emotion Game Introduction 2 - Home
First Look at the home screen for Live Emotion!
As described on the official twitter account: This is the backstage area where you can access various functions of the app. You can interact with the idols, watch them relax, and have fun in a variety of ways. This way, you can spend time with your favourite idols.
Analysis/translation of the user interface below:
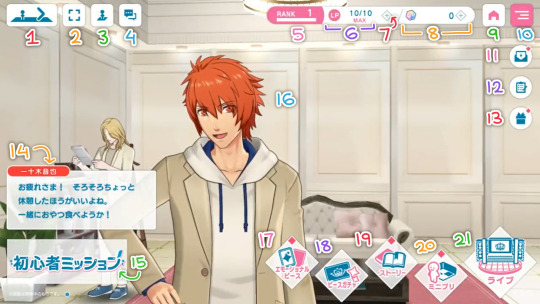
Move between left and right sides of the backstage area/homescreen. Can change to a forwards/backwards arrow depending on where you are in the room (?).
Likely a fullscreen/view mode, that removes the UI temporarily.
Unsure. Something to do with altering the UI for the room like the other 3 buttons in this area. Possibly to do with moving the characters or yourself around the screen. Potentially some other kind of customisation, although that seems to be the function of #20.
Likely a toggle for the text box (#14). It is greyed out temporarily, possibly when moving between left and right sides.
User rank and level up bar.
LP (likely still 'live points'). Used up to play songs in the rhythm game, and replenished by waiting in real time.
Likely a shortcut to refill LP with in game resources.
Likely the Live Emotion equivalent to 'Prisms' in Shining Live. Used for the gacha and other in game functions.
Home? Unsure exactly what screen this may return to, since the official tweet refers to this backstage area as the home page.
Settings/options menu.
News/updates log. Unread information indicated by a red diamond top right.
Missions, goals or achievements. Likely that completed missions with unclaimed rewards are indicated by a red diamond top right.
Giftbox. Unclaimed gifts indicated by a red diamond top right.
Chat box transcribing what the speaking idol is saying, as well as their name.
Text reads: "Beginner Mission". (Text in white below this box just says that the game is still under development).
Speaking idol. There can be multiple idols in the backstage area at once (Camus seen in the background). They are represented by 3d models, and it looks like they will interact with the background and eachother. In this case, Otoya is speaking to the player, and Camus is inspecting a book in the background. Almost certain that the outfits and room can be customised.
Button to navigate to viewing 'Emotional Pieces'. Not exactly sure the best way to translate that, despite it being in Katakana, but 'Pieces' (?) seem to be the equivalent to photos/cards in Shining Live. So I'm assuming this will be the way to view, organise, level up etc all your collected pieces, whatever they may be. The icon makes me think of the cards from Aikatsu, with different cards representing different parts of a while outfit. It makes me wonder if there'll be a bit more of a dress-up element, where you can collect and mix and match different headwear, tops, and bottoms of clothing sets. Please let me know if piece/peace means something in this context that I dont know about!
Button to navigate to the 'Piece Gacha'. The system for obtaining 'pieces' via in game currency.
Button to navigate to the story. Like other things on the UI, it seems like unlocked but unread stories are indicated by a red diamond.
Button to navigate to 'MiniPri'. Likely either or both) a view with cute chibi versions of the characters and backstage area, or the way to customise the members and background of the backstage area. I wonder if you can unlock different furniture, wallpapers, floors etc, and move them around yourself, of if the backgrounds are set.
Button to navigate to the 'Live' screen, the main song selection for the rhythm game.
#live emotion#utapri#uta no prince-sama#live emotion game introduction#interesting#not shining live#game introduction
114 notes
·
View notes
Text
My Love is mine, All mine (18+) (CEO! Daemon Targaryen x Female Reader) (Non Canon Modern AU)
Series Masterlist
Chapter 1
Summary: You dive down the memory lane and think about how you first met the love of your life, your husband, Daemon.
Warning: 18+, smut, mention of rape, insecurities.
Note : This will probably be the most boring thing i have ever written..you are warned. Expect 3-5 parts (or I don't really know yet 😂)

“Ugggh i don't want to be here” Shelly mumbled next to you so you gave her a side eye, she never wanted to be there. There were a couple of guys demonstrating a product targeted towards women, a decorative ring designed for women that could potentially save their life while they were out clubbing or about doing anything literally,
At first look, the ring looked like any other ring, adorned with jewels and glimmering in the light. Although upon closer inspection you could see that it had a hidden compartment under the fake diamond stud.
Inside the compartment was a red button, a single press of which would send an emergency alert to the local authorities as well as several emergency contacts on your phone, not just that but it also shared the precise location on a live moving map.
There was a group of women watching the presentation take place so you took Shelly as you were really intrigued by the product and as well as the guy giving the demonstration.
His name was Daemon, Daemon Targaryen, he was the tallest guy you had ever laid your eyes on, 6’3 to be astute, he had bronde hair- a mix of brown and blonde, and the most intense eyes you had ever witnessed, he was charming and charismatic and it wasn't like you to get attracted so quickly so even you were surprised by your own behaviour that day.
“Sooooo ummm no offense but how does it work? Is it battery operated?” A girl asked him so he picked up the ring and walked towards her,
“Don't worry I won't pop the question to you” he joked and it made everyone laugh including you. He showed her the 2.0 mm charging point inside the ring so she nodded her head..
“But what if the creeps out there recognise the ring?” Another girl asked him so he went back to the table and picked up another ring from the box..
“They won't..every purchase comes with a fresh design.. see for yourself” he gave her the ring so she checked it out and gave it back to him with a nod of approval.
The longer he talked about it though the more people started to leave, people were not interested in buying the ring even though it seemed like something everyone should own, they kept leaving until it was just you and Shelly. That's when Shelly mumbled something in your ear and ran off as well.
You watched Daemon sighing, there was a defeated look on his face that you noticed immediately but since you were still there he didn't stop the pitch. As you raised your hand up he gave you a smile.
The kind of smile that you knew would only bring you trouble..
“How long it stays active after charging..what is the duration?’ you asked him so he looked at another guy with him that you came to know later was his cousin Aemond.
“We are working on it..it stays for 10 hours for now but we are definitely trying to make the duration longer without comprising the size of it”
“10 hours? That's good enough to find someone if they're in trouble or missing” He gave you a smirky smile as you said that. “So are you selling them?” You asked him and you could tell he was excited by the prospect of leaving this place with at least one sale.
“Of Course..it's 10 euros only” he told you so you pulled out your wallet from the purse.
“Cool I'll take three..one for me..for my friend and my mom”
“Great” he clapped his hand together in excitement before he spoke again “We've also developed an app that will allow you to sync the ring with your phone. Once the connection has been established, it will not be interrupted even if your phone gets misplaced or powered off.” he informed you so you nodded.
“All this for 10 euros though? That's..very affordable..do you even make any profit?” you asked him a genuine though a bit intrusive question so he smiled politely.
“That's not a priority at the moment..goal is to give every woman a chance to be safe” he said in big words that you could have interpreted as a marketing gimmick but when you had learned the reason behind why he had invented this thing, you had realized his words were not empty that day.
He made you walk with him towards the station and Aemond excused himself as he wanted to get a drink, it was a warm day in Birmingham that day.
Once he was done cutting the receipt , you grabbed the rings and wished him good luck with the startup but as you were about to walk past him you heard him calling your name again and your heart skipped a beat.
“Yes?” You turned around to look at him so he hesitated for a moment before he stepped towards you,
“Ummm apologies if this sounds inappropriate but how old are you?” you gave him a smile as he said that. You'd pass out if he was intending to ask you out on a date.
“Just short 21” his face fell down as you said that so you crossed your arms..
“Ohhh” he let out a sigh, there was a look of disappointment plastered all over his features.
“Why did you ask? ” You couldn't help but let out a nervous giggle so he gave you a tight lipped smile.
“I .. nevermind.. thanks for buying our product..call us if you face any difficulties..stay safe yeah??”
You felt disheartened as he said that as for once in your life you were really hoping a man would ask you out, for once you found yourself being more into a man then he was into you.
Later on you had learned that the only reason he didn't ask you out that day was because he thought you were too young for him, he was twenty eight at the time and he didn't want to come across as a predator and a creep by dating a young girl in college. That went against everything he stood for.
But perhaps it was meant to be with you two because..Eight years later you were sitting in a restaurant waiting for him to get there so you could celebrate your four year wedding anniversary and he was late, as he always was at times but you understood that, he was a busy man.
What started as a small, humble operation was now a multimillion-euro company, all thanks to the vision and determination he had shown to make the world a safer place for women.
“God I'm sorry sweetheart” his voice made you snap out of your thoughts so you got up and hugged him tightly, the expensive cologne on the side of his neck comforted you immediately,
“It's okay..I just got here” you mumbled softly so he puckered his lips and shook his head.
“Liar”
He kissed you and made you sit back down again, at times like this he felt like a complete arse, sure he was doing this for both of you but he often felt as if he was making you feel neglected on occasions when he should have been with you, especially after everything you had done for him.
You were there for him when he had nothing in his name, when he was that eccentric bloke that went to women's colleges, workplaces and schools to sell a ring that nobody believed in at first..he had seen the worst of the life with you and in those moments he had decided that he was going to give you the best this world could offer you, he doused you in lavish gifts and fancy lifestyle, foreign trips and what not but deep down he knew all you needed from him was him. Just him.
After dinner and a few drinks as you both reached home you already had your hands on each other, that was one thing that never changed in your relationship with him, he was as passionate with you as he was the first night he had taken you like that, with his success and fame came several temptations on his way and you were not the most secure person, the older you got the more insecure you became of your looks, especially because of how he was desired so greatly by women younger than you but he made you feel as if you'd always be the only woman he'd desire in this way.
“Gods i have missed you babylove” he whispered in your ear before he trailed his lips down to your neck, he was on a work trip for a week and had just returned yesterday so the feeling was definitely mutual.
You loosened his tie while he unzipped your dress and picked you up to sit you down on the dresser, your fingers quickly worked the buttons of his shirt while his lips latched onto your neck.
“You're lovely you know that right? I don't think I told you how stunning you looked today”
You smiled sheepishly as he cupped your cheeks and kissed you while he murmured sweet honey into your ears.
“You did…twice actually” he smiled before he slipped your underwear down your legs, at times like this he couldn't really contain himself. Especially when he was away from you for days, the urge to get back to you and fuck you senseless would always eat him up. He had met you for the first time when you were just twenty one, and he always remembered you because you believed in his invention, you bought that ring that day and that memory was seared in his heart.
But you were too young for him, too innocent, so he didn't make his move that day. However the fate wasn't allowing him to move on from that encounter so it kept bringing you back to him until he had given into this feeling.
Next morning you woke up feeling tired but relaxed at the same time as he had completely worn you out. Nights like this were really affirming for you for several different reasons. He had already left for work, you grabbed your phone and called him but it went straight to voicemail so you put the phone down and sighed. Since you had your day off and had nothing much to do today you decided to call Shelly and your other friends to go for a brunch date.
Daemon was tired too that day and all he wanted to do was get back home early for once and surprise you since it was your day off. However he stepped into a silent house and an empty bedroom so he sighed and laid down on the bed with his business suit still on his body. He had organized the annual office party tomorrow so he knew he wouldn't get any peace moving forward.
He pulled out his phone to see if there was a text from you but there was nothing and he didn't want to disturb you if you were out shopping so he put it down and closed his eyes, it didn't take him long to drift into sleep.
As you returned home, you found Daemon passed out on the bed. Despite his exhausted state, he still managed to look adorable with his mouth open, that was one of his endearing qualities. You removed your heels, climbed onto the bed, and gently tucked his hair behind his ears. The sudden touch caused him to shift and wake up
“Hey theree” you mumbled softly as you climbed on top of him so he rubbed his eyes and gave you a smile.
“One day I come home early and you're not here to kiss me first thing” he feigned a hurt look so you gave him a pout..
“Sorry i didn't tell you, I was out for a brunch with Shelly”
"That's okay darling, I was jesting" Daemon said as he caressed your cheek with his fingers "How was your brunch?”
"Good, it's been long since we met so we had a couple of drinks" you said as you slowly undid his tie, you didn't understand how he was able to sleep like this.
“Sounds fun..” his smile dropped so you caressed his cheek with your thumb to bring his eyes back to you.
“What Is it? Work stuff?” you asked him softly.
“Mmmm ..I just..it's not that, i came home today and you weren't here and I just..felt sooo lonely..I'm not whining I'm just..is that how you feel when I'm not here for you?” He asked you softly so you leaned down and kissed his forehead.
“What do you want me to say?”
“Start with the truth and then you can sweeten it up to preserve my fragile ego” you chuckled as he said that
“I miss you of course.. would i want you to come back home like a normal guy once the work hour ends? Of Course i would but you're not a normal guy, you were born to do something great with your life and I'm here to support you all the way to the end..”
His eyes teared up as you said that so he flipped you around and laid you underneath him, you took his jacket off as he kissed your neck,
“I couldn't have done any of this without you”
“That's not true..you were doing this even before you met me..you would have done this with or without me–” he placed his thumb on your lips before you could go down this road,
“No you don't understand..you don't quite understand what you mean to me..” he mumbled tenderly as he kissed you over and over again, his lips barely brushed over yours as he kept mumbling between each kiss.
“Mmmm I think you made it clear when you made me your missus”
Your arms wrapped around his neck as he quickly rode your dress up and entered you swiftly,
“I love you.. and I'm sorry for being so absent –”
“It's okay..as long as you come back home, as long as you're mine and mine alone..it's all okay”
The next day at the office party you got all dolled up and hung around his arm throughout the evening. The party was the same as every year, he went all out to show his appreciation for the people who worked for TargSecure. People loved him, there was no questioning that, especially the women, he was extra attentive to their needs, they got higher pay and better leave days, their safety was the first priority for the company as Daemon wouldn't have it otherwise.
You saw Aemond and his wife Emma there so you spent your time with her while Daemon was busy with the employees, everything was the same as the past years.
However, there was this one little problem, one so insignificant and probably a figment of your imagination. And that small problem was your husband's young hot new secretary Sheena Mulaney that you knew was upto no good.
❣️❣️❣️❣️❣️❣️❣️❣️❣️❣️❣️❣️👀👀
Taglist
@anukulee @erebus-et-eigengrau @daenny-t @123forgottherest @mcufan72
#daemon targaryen#daemon targaryen x female reader#daemon targaryen x reader smut#daemon targaryen x reader fluff#daemon targaryen x reader angst#modern day au#non canon au#modern daemon targaryen#ceo daemon targaryen
127 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
22 notes
·
View notes
Text
In recent years, commercial spyware has been deployed by more actors against a wider range of victims, but the prevailing narrative has still been that the malware is used in targeted attacks against an extremely small number of people. At the same time, though, it has been difficult to check devices for infection, leading individuals to navigate an ad hoc array of academic institutions and NGOs that have been on the front lines of developing forensic techniques to detect mobile spyware. On Tuesday, the mobile device security firm iVerify is publishing findings from a spyware detection feature it launched in May. Of 2,500 device scans that the company's customers elected to submit for inspection, seven revealed infections by the notorious NSO Group malware known as Pegasus.
The company’s Mobile Threat Hunting feature uses a combination of malware signature-based detection, heuristics, and machine learning to look for anomalies in iOS and Android device activity or telltale signs of spyware infection. For paying iVerify customers, the tool regularly checks devices for potential compromise. But the company also offers a free version of the feature for anyone who downloads the iVerify Basics app for $1. These users can walk through steps to generate and send a special diagnostic utility file to iVerify and receive analysis within hours. Free users can use the tool once a month. iVerify's infrastructure is built to be privacy-preserving, but to run the Mobile Threat Hunting feature, users must enter an email address so the company has a way to contact them if a scan turns up spyware—as it did in the seven recent Pegasus discoveries.
Daily Newsletter
Our biggest stories, handpicked for you each day.
“The really fascinating thing is that the people who were targeted were not just journalists and activists, but business leaders, people running commercial enterprises, people in government positions,” says Rocky Cole, chief operating officer of iVerify and a former US National Security Agency analyst. “It looks a lot more like the targeting profile of your average piece of malware or your average APT group than it does the narrative that’s been out there that mercenary spyware is being abused to target activists. It is doing that, absolutely, but this cross section of society was surprising to find.”
Seven out of 2,500 scans may sound like a small group, especially in the somewhat self-selecting customer base of iVerify users, whether paying or free, who want to be monitoring their mobile device security at all, much less checking specifically for spyware. But the fact that the tool has already found a handful of infections at all speaks to how widely the use of spyware has proliferated around the world. Having an easy tool for diagnosing spyware compromises may well expand the picture of just how often such malware is being used.
“NSO Group sells its products exclusively to vetted US & Israel-allied intelligence and law enforcement agencies,” NSO Group spokesperson Gil Lainer told WIRED in a statement. "Our customers use these technologies daily.”
iVerify vice president of research Matthias Frielingsdorf will present the group's Pegasus findings at the Objective by the Sea security conference in Maui, Hawaii on Friday. He says that it took significant investment to develop the detection tool because mobile operating systems like Android, and particularly iOS, are more locked down than traditional desktop operating systems and don't allow monitoring software to have kernel access at the heart of the system. Cole says that the crucial insight was to use telemetry taken from as close to the kernel as possible to tune machine learning models for detection. Some spyware, like Pegasus, also has characteristic traits that make it easier to flag. In the seven detections, Mobile Threat Hunting caught Pegasus using diagnostic data, shutdown logs, and crash logs. But the challenge, Cole says, is in refining mobile monitoring tools to reduce false positives.
Developing the detection capability has already been invaluable, though. Cole says that it helped iVerify identify signs of compromise on the smartphone of Gurpatwant Singh Pannun, a lawyer and Sikh political activist who was the target of an alleged, foiled assassination attempt by an Indian government employee in New York City. The Mobile Threat Hunting feature also flagged suspected nation state activity on the mobile devices of two Harris-Walz campaign officials—a senior member of the campaign and an IT department member—during the presidential race.
“The age of assuming that iPhones and Android phones are safe out of the box is over,” Cole says. “The sorts of capabilities to know if your phone has spyware on it were not widespread. There were technical barriers and it was leaving a lot of people behind. Now you have the ability to know if your phone is infected with commercial spyware. And the rate is much higher than the prevailing narrative.”
#A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections#Phone Scanner#phone viruses#phones with installed viruses#IVerify
6 notes
·
View notes
Note
Hellu))
I looked at your neocities thingy, and I just wondered how you did that with the text boxes and the background and stuff. If you are willing to share, if you aren't, then sorry for wasting ur time)
I'm very new to coding (I suck) and "Penelope the cat" doesn't really help much T-T
Hi! Don't worry about asking, I'm always happy to help and give info on anything I know to the best I can! (Though to be completely honest, I too don't know much of HTML so... lol)
I used a <table> tag and the other tags that come with it. I also used boarder, boarder style, and background color, which would be in the CSS part of the code. Makes the boarder that's around it, The style that boarder will be in, and the background color of that table.Here's a website that explains it better then I can and also helps me out A LOT.
I heavily recommend this site, it's a life saver and will explain everything.
Also here is some CSS to help with the boarder and background!
Some other extra tips I'll throw in here:
I recommend using "Visual Studios". It's a free program and you can get a plug-in that allows you to see how your website looks without having to edit, go to the website, refresh, over and over. It also helps with coding as well, overall I'm loving it!
Now, by no means am I saying you should copy somebody else code and steal it. That's wrong. However, if you see something you like and want to know how it works, inspect the page and look at the code! I've learned a lot from doing this and it's help me figure out how things work too. Once again, do not straight up steal lines of somebody else's code. By that point you're not coding, you're copying, pasting, and stealing.
I also think you should learn the basics of HTML, and if you really want to make things then I say take the time to learn HTML. Personally for me, I love the look of broken ugly websites. Just some basic CSS will do for me! But if you're not like me, then yes, I think you should learn more then just the basics.
I'm sure there's some HTML nerds that can explain this way better then what I can so like I always say when it comes to learning stuff, look it up! The internet has unlimited free information, somebody 12 years ago on reddit probably asked the same question you did and the answer will be in the comments of that post. Always search for things!
9 notes
·
View notes
Text
Raid
Adrian takes part in a WRU raid.
[pet safety masterpost]
Content / warning: BBU, frankly discussed noncon (by whumpers), implied forced prostitution, WRU things, reacquisition teams, biting, beating. It starts very fluffy, but most of this is in fact very much not.
Slowly, Adrian and Bea began to develop a routine. Marta helped, from a distance, sharing what she knew from years of safehouse work and adapting it to Adrian's reality.
Physical activities, she had recommended. Touch that is affectionate, yet not physical. Defining and defending boundaries for each of them.
It was a challenging journey for both of them, but Adrian found himself enjoying the ride.
Bea helped with and prepared cooking. She didn't have any words for it, and barely any memory, but there was definitely some physical memory to kitchen assistance - with the slight drawback, that that had been with full vision, as they'd learned the hard way when she'd seriously cut herself while chopping onions, and the ER had sent them off because they wouldn't treat pets.
From then on, there were weekly therapy sessions for Bea, a work therapist (WRU-licence for work with pets) visiting them at home and teaching her how to deal with her vision impairment.
Bea refused to leave the apartment without him, but he taught her how to order groceries via app and she took over that task, too.
And then, there was dancing.
Every day after Adrian came home from work, he'd put on a playlist and they'd dance in the small space of his living room for almost an hour. Bea was a great dancer - of course she was, he thought grimly, nobody came out of WRU's training who didn't have perfectly sensual movements and flexibility. But she also seemed to genuinely enjoy it.
They danced Salsa, New York style, and Bea took to it like a fish to water. When he was at work, she browsed YouTube playlists he'd set up for her to find new combinations or try out stylings and decorations, and after he had been the one to teach her for their first two or three sessions, the roles were quickly reversed and she became the teacher.
"That pet really does wonders on you," his colleague at work said. "Haven't gotten laid enough before, huh?"
"She's fantastic," Adrian would reply then, nonchalantly enough not to provoke any follow up questions, and he'd hate that it was true. He was better.
Happier.
Of course, this didn't last long.
---
Adrian was just filing away the reports on his last uneventful inspection, humming the tune of a Salsa song, when his phone rang.
"Hey, Delgado," Kelly's voice was pressed. "Need you for a raid downtown. Illegal brothel, WRU pets involved. Police have requested a WRU team to deal with them. Dispatching three handlers and you. Departure in five. You'll answer to Grimm."
Grimm. The asshole who'd performed 'quality assurance' on Bea. It was even more sickening to imagine now, than it had been back then.
"Grimm and I aren't exactly-"
She cut him off. "You're both professionals, Adrian. He's the most senior employee on the team. Deal with it." She'd hung up, before he could add anything.
Cussing, Adrian grabbed his protective gear and jogged to the car park.
"PSI Delgado," Grimm greeted him, as he eased himself in the back of the van. "What an unpleasant surprise. I don't exactly need moral guidance to raid a house full of second hand Romantics."
"Seems our bosses think you do." Demonstratively, Adrian reached to his chest and turned on the body cam. "Pet Safety means to keep WRU property safe and well-kept. Would be a shame for the company if that weren't your highest prerogative."
Grimm clicked his tongue. "How's your own little whore anyway, eh? You keeping her safe and well-fucked? Or you defending your moral-superiority-slash-virginity against her?"
Adrian grabbed the handle over the door as the van went into a sharp curve. "What happens in my bedroom is none of your business."
"Ah, I see." He chuckled. "Nothing much, then. She's fun when you get her to scream, you know? Three fingers up the ass should do the job."
Adrian forced himself to remain calm. "What about the mission, Grimm?"
"Illegal brothel, bunch of whores with bar codes on their wrists. Police are coming in for the gangsters running it, need us to secure and seize the pets."
"How many?"
"Half dozen Romantics. Guard Dog or two." Grimm smirked. "My handlers and I will handle the Romantics, so you don't need to burden yourself with that depravity."
"Called the wife already, not to wait up," one of the other handlers chimed in. "Going to be a long night evaluating the products. We'll need to make sure they're still functional."
"While Delgado here can check if the Guard Dogs are still functional," Grimm added cheerfully. "Excellent team work."
"Truly." Adrian grinned at him darkly. "Always a pleasure working with other departments."
In his pocket, a burner phone was holding connection to his sister's, continuously sending his location data in the background.
---
It was worse than he'd expected.
Somehow, it always was.
None of the Romantics were registered to the brothel's owners. Runaways, who had either been collected off the streets by criminals or even taken the job up by themselves, earning money by doing the one thing they thought they were good at.
All of them had one thing in common - they were terrified seeing the dark gray WRU uniforms.
Some of them folded into Respect position even without the command, crying and whimpering.
Some tried to make a run for it.
Like the young man Adrian was pinning to the wall right now, barely twenty, high cheekbones, tousled black hair that fell down his back. His translucent robe hid nothing, not the too thin shape of his body, nor the bruises on his neck and thighs.
"Please," he whimpered. "Please, Sir, no, I can't go back, I'll do anything, please."
Adrian pressed him closer into the wall and leaned in. The boy reacted by curving his body against him, baring his neck, trying to rub his ass at Adrian's crotch.
Adrian squirmed. No. He couldn't do this. "See that window to our right?" he hissed. "There's a roof underneath. You hit me, get out there, down, two left turns, there's a red car. Get there, and you'll be safe."
From the end of the corridor, someone whistled. "Delgado trying to get some after all, huh? Need help?"
Adrian flipped the handler off, while he wrestled the pet's legs apart with his knee in an effort to show her what she expected to see. "Not help, fucking privacy would be nice!"
She chuckled. "Sure thing. We help each other, don't we? Be quick." He heard her press a button on her radio. "First floor clear."
Adrian reached for his own pants, pulled open his belt, while watching her leave.
His lips brushed over the boy's ear. "Got it?"
"Sure." The boy pushed back his ass. "I give you a good time and you look away for a second," he purred.
"No. You don't give me anything," Adrian said sharply. "No time. You hit me, you get to the red car. You ran away once, you do it again. Now."
He loosened his grip, and luckily, the kid had understood.
He spun around and punched him in the stomach, then a knee between the legs.
Adrian's loud whine wasn't entirely fake, as he stumbled back and rolled up on the floor. The kid stared at him for a second, and then darted towards the window Adrian had indicated, long hair flying past him like a flag.
Adrian counted to five, before he hit the button of the radio and yelled "Fuck! One got away!"
He just prayed it was true.
"One whore doesn't matter," Grimm's voice cracked in the radio. "Found the jackpot down here, be useful for once, Delgado. Basement, now."
Adrian pushed himself back to his knees. His cheek throbbed where the kid's punch had landed, not much more, but the kick between the legs had been hard. He groaned, as he started to limp towards the stairs.
The police had mostly retreated, a bunch of well dressed people loaded in the back of police trucks, some other officers carrying out computers from upstairs.
Adrian's colleagues however were in the basement, where a group of four trembling pets was huddled up behind a huge Guard Dogs shielding them against the handlers. He was growling lowly, swinging a long iron bar in one hand.
The handlers kept safe distance at the bottom of the stairs, shock batons and guns ready.
"Why don't you just shoot the dude?", the woman who'd been upstairs with Adrian demanded.
"Big guy is worth a mill," Grimm said lowly. "Top grade. Has titanium enforcements and shit. Reacquisition have been on the lookout for him for months. He'll go to refurb in mint condition, and still be on the larger end of six figures."
"Go. Away," the Guard Dog growled.
"Ressource guarding." Adrian mumbled. "Classic side effect of that sort of conditioning. Question is, does he defend all of them, or just one."
"Check the files." Grimm gestured at one of the handlers. "Did one of them escape with him?"
"Twink at the left. Not even a Romantic by designation. Domestic. Valet to their owner. Worth... neglectable."
"Huh." Grimm raised his gun and fired.
The gunshot echoed from the walls, deafening by itself, multiplied by the inhuman scream that rose from the Guard Dog's throat when the Domestic went down.
He lunged forward, at the same moment something pushed into Adrian's back.
Adrian only had time to draw his shock baton before the Guard Dog was on him, metal teeth sinking into the armour on his neck, digging through it, tearing skin and flesh. Grimm, he dimly thought. Fucking Grimm had pushed him in the line of attack.
He couldn't breathe, couldn't even raise his arm with the baton, could only scream, as the man on top of him shook his head with Adrian's neck between his teeth.
Punches rained down on the Guard Dog, vibrating in Adrian's body, his bones, his skull, everywhere. He couldn't see straight, everything a foggy blur, the only thing sharp the teeth in his neck.
There were calls around him, screams and footsteps and groans, and then finally, finally a heavy weight sinking down on him, a release of the stinging hold of his neck, and the welcoming darkness of unconsciousness.
---
When Adrian came to in the hospital the first time, it was for some minutes to a doctor changing the IV bag.
The second time was at night, when he woke up disoriented, trembling from a nightmare about Eric wearing a translucent robe, kissing his neck, then turning into a zombie biting him. Adrian's trembling fingers found a thick bandage around his neck. He rang the nurse for painkillers.
The third time, late in the morning, it was to Handler Grimm sitting in a chair next to his bed.
He closed his eyes, hoping to sleep again and make him go away.
It didn't work.
"Morning, Delgado," Grimm said cheerfully. "Man, you really went all in for the team there, didn't you?"
"Fuck you," Adrian rasped. "You fucking threw me to him as.... as bait."
"You wore armor," Grimm said with a shrug. "And you messed up right before. Plus, you're a fucking pain in the ass." He clasped Adrian's shoulder, and Adrian gasped in pain as it tore at the fresh wound. "And it worked out. I'll cash in the reacquisition bonus, and both of us will keep silent about the details, eh? I'll get you a share."
"What... about the pets?"
"Got more than half of them. They're on the Drip as we speak. Your cutie is still on the run, but don't worry, they all get picked up sooner or later. Until then, I'll make sure you'll get a little solace."
Adrian groaned, and Grimm just chuckled. "Was good working with you, eh? Cheers, PSI Delgado."
Adrian passed out, came back, and passed out again.
Somewhere in between, in the fleeting moments of consciousness, he felt someone curl up at his side, gentle hands brushing over his skin.
"I'm with you," a soft voice whispered. "I'm with you, Adrian Delgado, and I'm keeping you safe." She hummed against his skin, the cheerful tune of a Salsa song.
This time, when he fell asleep, he smiled.
--
---
tag list (let me know if you want to be added or removed): @gottawhump @flowersarefreetherapy @whumplr-reader @highwaywhump @tauntedoctopuses @pigeonwhumps @whumppsychology @labgrowndemon n @whumpinggrounds @somewhumpyguy @whumpzone @tragedyinblue
#bbu#pet safety series#adrian#handler grimm#noncon implied#forced prostitution#if you ever want me to write out#some of the soft stuff in the beginning#let me know
58 notes
·
View notes
Text
How To Buy Poker Game Source Code?

The poker industry is a goldmine of opportunities with millions of players worldwide. But launching a successful poker app can feel daunting, especially if you’re starting from scratch. That’s where buying a poker game source code comes in it’s the perfect shortcut to a feature-rich, professional platform that’s ready to customize and deploy.
This guide will help you understand the essentials of buying poker source code, its benefits, and the factors to watch out for during the process.
What is a Poker Game Source Code?
A poker game source code is the backbone of any poker app or platform. It’s a collection of programming instructions and files that define how the app operates, looks, and feels. Think of it as the blueprint for your poker application. It controls everything from the user interface to game logic, security features, and performance.
When you buy poker source code, you purchase a ready-made framework that developers can customize and refine according to your needs. This saves you from building the platform from scratch and allows you to focus on branding and user experience.
Additional Read: How to Make a Poker App?
Benefits of Buying Poker App Source Code
Investing in a pre-built poker app source code offers several advantages:
Faster Time-to-Market
Building a poker app from scratch can take months or even years. With a ready-made poker game source code, you can launch your platform much faster, allowing you to capture market opportunities immediately.
Cost-Effective Solution
Developing an app involves hiring skilled developers, designers, and testers, which can be expensive. You can significantly reduce development costs by purchasing a poker app source code.
Customizability
A good poker source code allows for easy customization. You can modify features, design elements, and game rules to align with your brand and target audience.
Proven Framework
Established poker game source codes have already been tested and optimized, minimizing the chances of bugs and errors. This ensures a smoother gaming experience for your users.
Compliance with Regulations
Reputable poker app source codes often come with built-in compliance features to meet legal requirements, making operating in multiple jurisdictions easier.
Things to Keep in Mind Before Buying Poker Source Code
When you decide to buy a poker game source code, it’s essential to evaluate certain factors to ensure you’re making a wise investment:
Vendor Reputation
Research the vendor thoroughly. Look for reviews, testimonials, and case studies to verify their reliability. A reputable vendor ensures high-quality code and dependable customer support.
Code Quality
Inspect the quality of the poker app source code. Poorly written code can lead to performance issues and security vulnerabilities. Make sure the code is clean, modular, and easy to customize.
Features and Scalability
Check whether the source code includes essential features like multiplayer support, anti-fraud mechanisms, and smooth gameplay. Also, make sure it is scalable to handle growing users as your platform grows.
Customization Options
Your poker app should reflect your unique brand identity. Confirm that the source code offers flexibility for design and feature customization.
Compliance and Licensing
Ensure the poker game source code complies with local gaming regulations. Verify that you receive proper licensing to avoid legal complications.
Common Mistakes to Avoid
Avoiding these mistakes can save you from unnecessary hassles and ensure a smooth buying process:
Choosing the Cheapest Option
Opting for the cheapest poker source code may seem tempting, but it often results in low-quality software with hidden issues. Always prioritize quality over cost.
Overlooking Documentation
Documentation is crucial for understanding the functionality and integration process. Never purchase a poker app source code without complete and clear documentation.
Ignoring Support Services
Technical support is vital for resolving issues quickly. Ensure the vendor provides reliable post-purchase support.
Neglecting Security Features
Security is non-negotiable in online poker platforms. Ensure the code includes robust security measures like encryption and fraud detection.
Why Choose Creatiosoft for Poker Source Code?
We stand out as a trusted name in the industry. Since 2012, we have been delivering top-notch poker game source codes to clients worldwide. Here’s why Creatiosoft is your best choice:
Proven Expertise
With over a decade of experience, we understand the complexities of poker app development. Our team ensures you get a reliable and scalable source code tailored to your needs.
Feature-Rich Solutions
Our poker app source code has advanced features, including multiplayer functionality, AI-powered analytics, secure payment gateways, and responsive design.
Customization and Branding
We offer complete flexibility to customize the platform according to your business model, ensuring your brand stands out in the competitive market.
Top-Notch Support
At Creatiosoft, we provide ongoing technical support to ensure your platform runs smoothly.
Compliance Ready
Our poker game source code adheres to legal and regulatory standards, making operating globally easier.
Final Words
Buying a poker app source code is a brilliant idea for businesses looking to enter in the online poker industry. It saves time, reduces costs, and provides a solid foundation for building a successful platform. With a reliable provider, you can be confident that your investment will deliver exceptional quality and long-term scalability.
2 notes
·
View notes
Text
Capturing the ambience of Jazzpunk
This unpredictable comedy/art title takes the player through a disorienting array of settings which can only seem coherent in retrospect.

Capturing footage
To open Jazzpunk's developer console, press ~ while in-game. Useful commands are: unlocklevels (amusingly there is a locklevels command as well) and noclip, or fnc ("fast no clip"). Be sure to also disable the pointer UI via the options menu.

You can speed yourself up on foot using the walkfast command. Noclip speed is adjusted separately using set noclip speed <float>.
There are a couple of unlisted commands that alter the game's rendering quality. I recommend running antialias and forward to toggle anti-aliasing and forward rendering respectively.
Extracting sounds
Since Jazzpunk is built on Unity, we can use AssetStudio. This tool can extract AdioClips and inspect scene hierarchies, but annoyingly it can't seem to do both at once.

That is, we'll still need to figure out which assets map to our scene, using context clues. We can filter assets by AudioClip to help narrow our search.

There is also a tool called Asset Bundle Extractor, which is seemingly modding-oriented. It's possible I was missing some kind of plugin, but I couldn't get this to identify or extract Jazzpunk assets. Perhaps it could be used to mute the game's (wonderful and original) music, in order to play only ambience?

Playing the original release
Only Jazzpunk: Director's Cut is currently offered for sale. If you wish to "downgrade" to the game as it original released, you can use a third-party Steam tool like DepotDownloader. Find Jazzpunk's content listing in a third-party database to inform your command:
DepotDownloader.exe -app 250260 -depot 250261 -manifest 5748178397053210322 -username YOURNAME
You'll find Director's Cut significantly expanded certain mission scenery:


There are also subtle improvements in Director's Cut, like individual torch light sources on Kai Tak Resort:


32 notes
·
View notes
Photo

The integration of AI into inspection app development is an exciting development that holds great promise for businesses looking to streamline their operations and improve their bottom line. By leveraging the power of AI, businesses can improve the accuracy, efficiency, and effectiveness of their inspections, as well as provide a better user experience for their customers.
0 notes
Text
ParkZapp Inspections: Keeping Fun Safe and Parking Lots Drama-Free!
Welcome to the wild world of inspections, where ParkZapp ensures that your playgrounds are safe, your parking lots are drama-free, and your buildings are ready to house all the fun (and maybe a few shenanigans). Let’s take a whimsical dive into why inspections are essential for keeping our favorite hangouts and hideaways in tip-top shape!
Playground Inspections: Swinging into Safety
Picture this: a sunny day, the sound of laughter, and children swinging high into the sky. Now, imagine that swing is actually a catapult of doom! Okay, that’s a bit dramatic, but that’s why playground inspections are no joke. Our trusty inspectors swing into action (pun absolutely intended) to check for broken equipment, loose bolts, and any potential hazards lurking in the sandpit.
With ParkZapp’s playground inspections, you can rest easy knowing that the only thing flying through the air is joyful giggles—not flying pieces of broken swings!
Parking Lot Inspections: No Drama, Just Parking
Let’s face it: parking lots can be a battlefield. Between rogue shopping carts, poorly parked cars, and the occasional tire screeching like a banshee, it’s a wonder we survive each trip. ParkZapp’s Parking Lot Inspection Services in Iowa ensure that your parking paradise is free from potholes and other dastardly obstacles.
Our inspectors have a sixth sense for spotting trouble. We’ll make sure that every parking space is clearly marked, the lights are working (because who wants to park in the dark?), and any oil slicks are dealt with faster than you can say “Who parked like that?!”
Building Inspections: Where “Under Construction” Takes on New Meaning
Ever walked into a building and thought, “Wow, this place looks like it’s seen better days”? Fear not! ParkZapp’s building inspection services are here to save the day (and your nose). We’ll ensure that everything from the foundation to the ceiling tiles is as solid as your commitment to binge-watching your favorite series.
Our building inspection services in Iowa have a keen eye for things that could go wrong, from water leaks to electrical gremlins. We take building inspections seriously, so you can focus on the important stuff—like deciding what color to paint the break room!
Facility Inspections: Because Every Nook and Cranny Matters
When it comes to facilities, we believe no corner should be left unchecked. ParkZapp’s facility inspections sweep through every inch, ensuring that your spaces are clean, safe, and ready for whatever activities you have planned.
We check everything from restrooms (because yes, we will inspect the bathroom!) to meeting rooms. After all, you don’t want your staff to feel like they’re working in a haunted house—unless that’s the vibe you’re going for, of course.
Sports Field Inspections: Keeping the Game Safe
For all you sports enthusiasts out there, we’ve got you covered! Our sports field inspection services in Iowa ensure that every kick, throw, and catch is done on a field that’s as safe as it is fun. We’ll check for proper turf conditions, goal stability, and any potential hazards, ensuring the only thing scoring is your team’s points!
Fire Inspections: Safety First!
When it comes to fire safety, you can’t be too cautious. That’s why our fire inspection services in Iowa are essential to keeping your facilities compliant and safe. Our expert inspectors will evaluate your fire alarms, extinguishers, and exits, making sure you’re prepared for any emergency (and that’s no laughing matter!).
Conclusion: Let ParkZapp Inspect, So You Can Play!
So there you have it! From playgrounds that need a little TLC to parking lots that require more love than a puppy, ParkZapp is your go-to for all inspection needs. Our team is dedicated to ensuring that your spaces are safe, fun, and ready for every adventure.
Remember, inspections may not be the most glamorous part of park management, but they’re definitely one of the most important. So let us handle the nitty-gritty while you focus on what truly matters—creating memorable experiences for your community!
With ParkZapp, you can laugh, play, and park with peace of mind. Now, who’s ready for some fun in the sun?
#playground#mobile application development#fire inspection#building inspections#sport field inspection#parking lot inspection#inspection#parkzapp#app#iowa#fun
0 notes
Text
Burp Suite
This week I wanted to cover a powerful tool that assists in web application security. Burp Suite is a well-known tool developed by PortSwigger. Burp Suite is an integrated platform used to test web application security by using a variety of different features it provides. One of these features Burp Suite has is an intercepting proxy that allows you to inspect and modify traffic between the browser and the server at each step. Scanner allows you to automatically detect certain vulnerabilities like SQL injection and cross-site scripting. Intruder automates custom attacks to test certain security parameters, generally passwords. Repeater allows for manual modification and replaying of edited requests for more in-depth testing.
All in all Burp Suite provides a simplified way and process for identifying and discovering vulnerabilities. It has a very user-friendly interface that assists in applying all the different features and makes it easy to learn. It also allows for user consummation that allows users to create custom rules and integrate third-party extensions. It is one of the most renowned tools in cyber security and brings an active and engaging community along with it. Burp Suite I is something I highly recommend to those striving to develop their cyber security skills to get their hands on. Not only will you become more proficient in the tool itself, but it will also teach you about how web applications and servers work.
Source:
2 notes
·
View notes
Text
As a trucker, you can perform various tasks within truck dispatching:
*Primary Responsibilities:*
1. Receive and accept load assignments from dispatchers.
2. Review load details, routes, and schedules.
3. Plan and navigate routes using GPS and maps.
4. Manage cargo, including loading/unloading and securement.
5. Comply with safety regulations, hours of service, and company policies.
6. Communicate with dispatchers, shippers, and receivers.
7. Update dispatchers on shipment status and any issues.
*Additional Tasks:*
1. Pre-trip inspections: ensure vehicle safety and compliance.
2. Fuel management: optimize fuel efficiency and costs.
3. Maintenance scheduling: coordinate vehicle maintenance.
4. Logkeeping: maintain accurate records of hours, miles, and cargo.
5. Customer service: interact with shippers, receivers, and brokers.
6. Route optimization: suggest alternative routes or improvements.
7. Load optimization: maximize cargo capacity and revenue.
*Technology Used:*
1. Electronic Logging Devices (ELDs)
2. GPS tracking systems
3. Mobile apps (e.g., Trucker Path, TruckStop)
4. Fleet management software (e.g., TMW, McLeod)
5. Communication platforms (e.g., phone, email, messaging apps)
*Skills Required:*
1. Knowledge of transportation regulations
2. Navigation and route-planning skills
3. Time management and organization
4. Communication and customer service skills
5. Mechanical knowledge of trucks and equipment
6. Adaptability and problem-solving
7. Attention to detail and safety protocols
*Career Advancements:*
1. Lead driver or mentor
2. Fleet manager
3. Safety inspector
4. Dispatch coordinator
5. Logistics manager
6. Owner-operator or small fleet owner
7. Transportation consultant
*Benefits:*
1. Competitive pay and benefits
2. Job security and stability
3. Opportunities for advancement
4. Independence on the road
5. Variety in routes and cargo
6. Sense of accomplishment and satisfaction
Would you like more information on:
1. Trucking regulations
2. Dispatching software
3. Career development
4. Safety protocols
5. Something else
Let me know!
2 notes
·
View notes
Text
Unit 7 Blog Post
Living in the 21st century, our easy access and constant exposure to music can make us numb to its significance. Music is integral in all human cultures and has been key in community building since ancient times (Sahi, 2012). Some even hypothesize that music “predates humans--that rather than being the inventors of music, [humans] are latecomers to the musical scene” (Gary et al., 2001). This provokes questions about the origins of music and the reasons for its existence. In regards to culture and history, it is likely that human music “developed in contact with local nature and thus reflects the nature” around particular communities (Sahi, 2012). The extrapolation and utilization of nature in music is quite evident in many cultures, particularly in their folk music. Rune singing used for Finnish folk music contains rich lyrics describing the natural environment around them (Sahi, 2012).
After this week’s content, I was inspired to inspect my own culture’s music to see how large of an impact nature had on it. As I delved back into my favorite old-school Bollywood songs, I found that the most beloved songs usually drew inspiration from the natural environment. Nature is an excellent source of unique melodies and sound patterns that help facilitate the rhymes and vocals particularly for Bollywood songs. There are likely universal mathematics (Gary et al., 2001) within certain nature-sounds that catch our attention more than others, ones that invoke inspiration for composers. You can find music in nature when you listen to the wind whistling through mountains, or by observing the rhythmic pattern of the rain falling on the ground, or through the chirping of the birds. Bollywood composers often choose female singers with very high pitched voices (i.e. Lata Mangeshkar), which I believe they do to resemble song birds. Musical patterns in nature bring forth specific feelings for listeners (i.e. thunder correlates to fear/surprise, while ocean waves correlate with calmness), which is why percussion instruments are used to mimic abiotic sounds/patterns and add depth of a song. For example, Bollywood composers use the tabla to mimic thunder sounds and the ghunghroo to imitate rustling leaves.
Pyaar ki ek kahani is a song I particularly love because it takes me back to the mountain landscapes I visited in India. The background vocals remind me of how my voice echoed when I was in the valley areas or near river banks. The softness of the male singer’s vocals invokes the same feelings of airiness that I felt at that high altitude. The female singer’s voice mimics the beautiful sounds of the birds in the morning.
youtube
(Song context: The male character lives a peaceful life in a mountain village of Manila, India. A new journey starts for him when he meets a city girl. The use of mountain scenery, a song that creates a mountain ambience, and the characters’ story all work together to create feelings of airiness, openness, and blissful naivety.)
Reference:
Beck, L., Cable, T. T., Knudson, D. M. (2018). Interpreting Cultural and Natural Heritage: For a Better World. Sagamore Publishing LLC.
Gray, P. M., Krause, B., Atema, J., Payne, R., Krumhansl, C., & Baptista, L. (2001). The Music of Nature and the Nature of Music. Science, 291(5501), 52. https://link.gale.com/apps/doc/A69270354/AONE?u=guel77241&sid=bookmark-AONE&xid=fb9366a8
Sahi, V. (2012). Using folk traditional music to communicate the sacredness of nature in Finland. Spiritual Values of Protected Areas of Europe Workshop Proceedings. (pg 129-132). https://www.silene.ong/en/documentation-centre/spiritual-values-of-protected-areas-of-europe-workshop-proceedings#Proceedings_Spiritual%20Values_PAs_Europe.pdf
2 notes
·
View notes
Text
In today’s digital world, injustice lurks in the shadows of the Facebook post that’s delivered to certain groups of people at the exclusion of others, the hidden algorithm used to profile candidates during job interviews, and the risk-assessment algorithms used for criminal sentencing and welfare fraud detention. As algorithmic systems are integrated into every aspect of society, regulatory mechanisms struggle to keep up.
Over the past decade, researchers and journalists have found ways to unveil and scrutinize these discriminatory systems, developing their own data collection tools. As the internet has moved from browsers to mobile apps, however, this crucial transparency is quickly disappearing.
Third-party analysis of digital systems has largely been made possible by two seemingly banal tools that are commonly used to inspect what’s happening on a webpage: browser add-ons and browser developer tools.
Browser add-ons are small programs that can be installed directly onto a web browser, allowing users to augment how they interact with a given website. While add-ons are commonly used to operate tools like password managers and ad-blockers, they are also incredibly useful for enabling people to collect their own data within a tech platform’s walled garden.
Similarly, browser developer tools were made to allow web developers to test and debug their websites’ user interfaces. As the internet evolved and websites became more complex, these tools evolved too, adding features like the ability to inspect and change source code, monitor network activity, and even detect when a website is accessing your location or microphone. These are powerful mechanisms for investigating how companies track, profile, and target their users.
I have put these tools to use as a data journalist to show how a marketing company logged users’ personal data even before they clicked “submit” on a form and, more recently, how the Meta Pixel tool (formerly the Facebook Pixel tool) tracks users without their explicit knowledge in sensitive places such as hospital websites, federal student loan applications, and the websites of tax-filing tools.
In addition to exposing surveillance, browser inspection tools provide a powerful way to crowdsource data to study discrimination, the spread of misinformation, and other types of harms tech companies cause or facilitate. But in spite of these tools’ powerful capabilities, their reach is limited. In 2023, Kepios reported that 92 percent of global users accessed the internet through their smartphones, whereas only 65 percent of global users did so using a desktop or laptop computer.
Though the vast majority of internet traffic has moved to smartphones, we don’t have tools for the smartphone ecosystem that afford the same level of “inspectability” as browser add-ons and developer tools. This is because web browsers are implicitly transparent, while mobile phone operating systems are not.
If you want to view a website in your web browser, the server has to send you the source code. Mobile apps, on the other hand, are compiled, executable files that you usually download from places such as Apple’s iOS App Store or Google Play. App developers don’t need to publish the source code for people to use them.
Similarly, monitoring network traffic on web browsers is trivial. This technique is often more useful than inspecting source code to see what data a company is collecting on users. Want to know which companies a website shares your data with? You’ll want to monitor the network traffic, not inspect the source code. On smartphones, network monitoring is possible, but it usually requires the installation of root certificates that make users’ devices less secure and more vulnerable to man-in-the-middle attacks from bad actors. And these are just some of the differences that make collecting data securely from smartphones much harder than from browsers.
The need for independent collection is more pressing than ever. Previously, company-provided tools such as the Twitter API and Facebook’s CrowdTangle, a tool for monitoring what’s trending on Facebook, were the infrastructure that powered a large portion of research and reporting on social media. However, as these tools become less useful and accessible, new methods of independent data collection are needed to understand what these companies are doing and how people are using their platforms.
To meaningfully report on the impact digital systems have on society, we need to be able to observe what’s taking place on our devices without asking a company for permission. As someone who has spent the past decade building tools that crowdsource data to expose algorithmic harms, I believe the public should have the ability to peek under the hood of their mobile apps and smart devices, just as they can on their browsers. And it’s not just me: The Integrity Institute, a nonprofit working to protect the social internet, recently released a report that lays bare the importance of transparency as a lever to achieve public interest goals like accountability, collaboration, understanding, and trust.
To demand transparency from tech platforms, we need a platform-independent transparency framework, something that I like to call an inspectability API. Such a framework would empower even the most vulnerable populations to capture evidence of harm from their devices while minimizing the risk of their data being used in research or reporting without their consent.
An application programming interface (API) is a way for companies to make their services or data available to other developers. For example, if you’re building a mobile app and want to use the phone’s camera for a specific feature, you would use the iOS or Android Camera API. Another common example is an accessibility API, which allows developers to make their applications accessible to people with disabilities by making the user interface legible to screen readers and other accessibility tools commonly found on modern smartphones and computers. An inspectability API would allow individuals to export data from the apps they use every day and share it with researchers, journalists, and advocates in their communities. Companies could be required to implement this API to adhere to transparency best practices, much as they are required to implement accessibility features to make their apps and websites usable for people with disabilities.
In the US, residents of some states can request the data companies collect on them, thanks to state-level privacy laws. While these laws are well-intentioned, the data that companies share to comply with them is usually structured in a way that obfuscates crucial details that would expose harm. For example, Facebook has a fairly granular data export service that allows individuals to see, amongst other things, their “Off-Facebook activity.” However, as the Markup found during a series of investigations into the use of Pixel, even though Facebook told users which websites were sharing data, it did not reveal just how invasive the information being shared was. Doctor appointments, tax filing information, and student loan information were just some of the things that were being sent to Facebook. An inspectability API would make it easy for people to monitor their devices and see how the apps they use track them in real time.
Some promising work is already being done: Apple’s introduction of the App Privacy Report in iOS 15 marked the first time iPhone users could see detailed privacy information to understand each app’s data collection practices and even answer questions such as, “Is Instagram listening to my microphone?”
But we cannot rely on companies to do this at their discretion—we need a clear framework to define what sort of data should be inspectable and exportable by users, and we need regulation that penalizes companies for not implementing it. Such a framework would not only empower users to expose harms, but also ensure that their privacy is not violated. Individuals could choose what data to share, when, and with whom.
An inspectability API will empower individuals to fight for their rights by sharing the evidence of harm they have been exposed to with people who can raise public awareness and advocate for change. It would enable organizations such as Princeton’s Digital Witness Lab, which I cofounded and lead, to conduct data-driven investigations by collaborating closely with vulnerable communities, instead of relying on tech companies for access. This framework would allow researchers and others to conduct this work in a way that is safe, precise, and, most importantly, prioritizes the consent of the people being harmed.
11 notes
·
View notes