#ibm.com
Explore tagged Tumblr posts
Text
IOTA BETA MU IBM DOT COM ENGLISH TEXT
#iota betau#ibm#ibm.com#english text#english language#british rendered in english text is the english language#alpha#tau#rho#epsilon#iota#delta#sigma
52 notes
·
View notes
Text
IOTA BETA MU
IBM.COM
3 notes
·
View notes
Photo

IBM Building
3 notes
·
View notes
Text
Pentagon UFO Chief to step down next month... since 1968-michaelharrelljr.com's Occult Okcult Occult TECH POWER CARTEL [PC] ILLUMINATI of © 1698-2223 quantumharrelltech.com’s Clandestine Department of defense.gov Domain Communication [D.C.] Portal Address [PA] @ quantumharrellufo.tech's quantumharrelltech.ca.gov Military of Economic [ME] Alliances & Partnership [MAP] States... Independently Banking from Mother's [IBM's] Old 1698 Ægiptian America in Mu Atlantis [MA]
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm.com] mode [i’m] tech [IT] steelecartel.com @ quantumharrelltech.ca.gov

BUCKLE UP ENTITLED 2024 AMERICA

1968-michaelharrelljr.com REMEMBER ATLANTIS & LEMURIA

1968-michaelharrelljr.com Incarnated as Extremely Wealthy TUTANKHAMÚN… Died Contractually [D.C.] Wealthy on Earth [WE]… only 2 come back on Earth [Qi] Wealthier than before

Gen X is in Charge Now

GEN X POWERS ACTIVATE [PA] @ OUR PENTAGON

NOT THE REAL GOLDEN 9 ETHER OKCULT TECH LIBRARY ILLUMINATI?!?!?!

Department of DEFENSE.gov's Domain Communication [D.C.] Computer Aided Drafting [CAD] defense.gov Department PAY TO THE ORDER OF: QUANTUM HARRELL TECH LLC

Department of DEFENSE.gov's Domain Communication [D.C.] Computer Aided Drafting [CAD] defense.gov Department PAY TO THE ORDER OF: QUANTUM HARRELL TECH LLC

I.B.MICHAEL's [IBM's] ANCIENT 9 ETHER Ægiptian FREEMASON UNDER Father’s Old America of Mother’s GOLDEN BLACK SUN MONARCHY in Mu Atlantis [MA]

© 1698-2223 quantumharrelltech.com - ALL The_Octagon_(Egypt) DotCom [D.C.] defense.gov Department Domain Communication [D.C.] Rights Reserved @ quantumharrelltech.ca.gov
#u.s. michael harrell#quantumharrelltech#yoruba tut#king tut#mu:13#harrelltut#kemet#o michael#quantumharrelltut#department of defense#department of the treasury#black wall street#the pentagon#the octagon#egypt#mu atlantis#old america#qht68#qht68 visions#international economic alliances#ibm
8 notes
·
View notes
Text
Top 10 DevOps Consulting & Services Companies in Australia

In today's fast-paced digital landscape, DevOps consulting has become essential for organizations aiming to streamline software development, enhance team collaboration, and achieve greater operational efficiency. For businesses in Australia, finding a reliable and experienced DevOps consulting partner can be a game-changer. This article highlights the top 10 DevOps consulting companies in Australia, providing an overview of their services, contact information, and why they stand out in the industry.
1. Ashapura Softech
Website: ashapurasoftech.com
Email: [email protected]
Ashapura Softech is a global provider of DevOps consulting services, specializing in customized solutions tailored to the unique needs of clients. With a focus on optimizing delivery pipelines and automating processes, Ashapura Softech enables organizations to release high-quality software faster. Their expert team offers comprehensive support in configuration management, infrastructure as code, and CI/CD pipeline setup. Ashapura Softech is known for its customer-centric approach, making it an ideal choice for companies looking to build scalable, automated, and robust DevOps solutions.
Key Services:
DevOps Assessment and Strategy
Continuous Integration/Continuous Delivery (CI/CD)
Automation and Infrastructure Management
Cloud Migration and Security Solutions
2. Servian
Website: servian.com
Email: [email protected]
Servian is one of Australia's leading consulting firms, providing advanced DevOps solutions along with data analytics, artificial intelligence, and cloud services. Their DevOps practice focuses on helping organizations automate and enhance their development workflows, ensuring faster delivery with reduced risks. Servian’s team of experts works closely with clients to implement best practices in continuous integration and delivery, as well as infrastructure management.
Key Services:
DevOps and Cloud Consulting
Infrastructure Automation
Continuous Integration and Delivery
Security and Compliance Solutions
3. Accenture Australia
Website: accenture.com
Email: [email protected]
As a global leader in digital and consulting services, Accenture offers end-to-end DevOps consulting services that help Australian enterprises accelerate software delivery and improve collaboration between development and operations teams. Accenture specializes in large-scale transformations, enabling companies to adopt agile methodologies and automated workflows. Their DevOps solutions include cloud services, automation, and CI/CD implementation, making them a trusted partner for organizations of all sizes.
Key Services:
DevOps Transformation and Implementation
Cloud-Native Solutions
CI/CD Pipeline Development
Agile and DevOps Training
4. Deloitte Australia
Website: deloitte.com
Email: [email protected]
Deloitte Australia provides comprehensive DevOps consulting and digital transformation services for businesses aiming to modernize their IT infrastructure. Deloitte’s expertise lies in implementing DevOps practices that integrate seamlessly with cloud platforms, providing scalability and flexibility. They focus on automation, monitoring, and collaboration tools, ensuring a smooth workflow and enhanced productivity.
Key Services:
DevOps Implementation and Strategy
Cloud Integration and Automation
Continuous Monitoring and Compliance
IT Infrastructure Consulting
5. IBM Australia
Website: ibm.com
Email: [email protected]
IBM Australia leverages its vast experience in technology and innovation to provide industry-leading DevOps services. IBM’s DevOps approach is tailored to address unique business challenges, enabling companies to create efficient, automated workflows. With an emphasis on automation, IBM helps organizations streamline processes, ensuring continuous delivery and minimized downtime.
Key Services:
DevOps Lifecycle Management
Continuous Integration and Testing
Cloud and Hybrid Infrastructure Solutions
Data and AI-Driven Insights
6. Infosys Australia
Website: infosys.com
Email: [email protected]
Infosys brings a wealth of experience in DevOps consulting to the Australian market, focusing on transforming traditional development processes into agile, automated workflows. Their services cover end-to-end DevOps solutions, helping companies achieve faster delivery cycles and robust CI/CD pipelines. Infosys places a strong emphasis on security and compliance, making them a reliable choice for regulated industries.
Key Services:
DevOps and Agile Transformation
Infrastructure Automation
Continuous Testing and Delivery
Compliance and Security Solutions
7. Tata Consultancy Services (TCS) Australia
Website: tcs.com
Email: [email protected]
TCS is a trusted name in IT and consulting services, offering DevOps solutions tailored to large and medium enterprises in Australia. TCS excels in helping organizations implement scalable DevOps practices, focusing on automation, cloud integration, and agile methodologies. Their expertise in infrastructure management and CI/CD pipeline setup makes them a strong contender in the Australian DevOps space.
Key Services:
Agile and DevOps Consulting
Cloud Migration and Automation
CI/CD Development and Deployment
Infrastructure Management
8. PwC Australia
Website: pwc.com.au
Email: [email protected]
PwC Australia offers a broad range of DevOps consulting services aimed at modernizing business operations and enhancing productivity. PwC’s DevOps solutions are designed to create efficient pipelines, automate workflows, and provide real-time monitoring. They specialize in agile transformations, helping companies adopt DevOps best practices while maintaining compliance with industry standards.
Key Services:
DevOps Strategy and Assessment
Workflow Automation and Optimization
Agile Transformation
Compliance and Security
9. Thoughtworks Australia
Website: thoughtworks.com
Email: [email protected]
Known for its innovation and commitment to agile methodologies, Thoughtworks provides leading DevOps consulting services to Australian businesses. Thoughtworks specializes in enabling organizations to build agile, responsive infrastructures with DevOps practices that prioritize automation, quality, and security. Their expertise in continuous integration and deployment helps businesses minimize downtime and improve efficiency.
Key Services:
Agile and DevOps Consulting
CI/CD Pipeline Setup
Test Automation
Security and Compliance Solutions
10. Capgemini Australia
Website: capgemini.com
Email: [email protected]
Capgemini Australia is a recognized leader in DevOps services, offering comprehensive consulting to help organizations automate, secure, and optimize their operations. Capgemini’s DevOps practice focuses on delivering end-to-end automation solutions, helping companies achieve seamless integration of DevOps practices with cloud technologies. With a strong commitment to agile transformations, Capgemini has proven success in delivering tailored solutions for businesses across industries.
Key Services:
DevOps and Cloud Integration
Continuous Deployment and Automation
Security and Compliance
Agile Transformation Services
Conclusion
Choosing the right DevOps consulting partner can make a significant difference in the efficiency and productivity of your organization. The companies listed above are among the best in Australia, each offering unique strengths in DevOps strategy, automation, and cloud integration. As the demand for seamless software development and operations grows, partnering with a reliable DevOps service provider is crucial for long-term success. To learn more about how Ashapura Softech can assist with DevOps consulting and help you achieve your business goals, contact us at [email protected]. Our experts are ready to provide a custom solution that meets your needs and drives your digital transformation forward.
0 notes
Text
Edge AI Technology Improves Device Real-Time Data Processing

Edge AI technology
What is Edge AI?
The term “Edge AI” describes the direct application of AI models and algorithms to nearby edge devices, including sensors or Internet of Things (IoT) gadgets. This allows for real-time data processing and analysis without being dependent on cloud infrastructure all the time.
In a nutshell, edge AI, often known as “AI on the edge,” is the use of artificial intelligence and edge computing to perform machine learning tasks directly on networked edge devices. AI algorithms enable data to be processed directly on the network edge, with or without an internet connection, while edge computing enables data to be stored near to the device location. This makes it possible to analyze data in milliseconds and provide feedback in real time.
It is making its way into more sectors to automate business operations, streamline workflows, and encourage innovation while addressing latency, security, and cost savings.
Edge AI Advantages For End Users
The worldwide edge AI market was estimated by Grand View Research, Inc. (link sits outside ibm.com) to be worth USD 14,787.5 million in 2022 and is projected to reach USD 66.47 million by 2023. In addition to edge AI’s other intrinsic benefits, the growing demand for IoT-based edge computing services is what is driving edge computing’s fast proliferation. The following are edge AI’s main advantages:
Reduced latency
Users may benefit from quick response times without having to wait for data to return from a remote server thanks to full on-device processing.
Reduced bandwidth
Edge AI preserves internet bandwidth by processing data locally, hence reducing the volume of data sent over the network. The data connection may support more simultaneous data transmission and reception when less bandwidth is required.
Instantaneous analytics
Users may save time by combining data without having to interact with other physical places by doing real-time data processing on devices without the need for system connection and integration. To fully use cloud computing’s resources and capabilities, edge AI may need to be incorporated in order to handle the large number and variety of data required by certain AI applications.
Data confidentiality
Data is not moved to another network, where it can be subject to hackers, increasing privacy. By analyzing data locally on the device, edge AI lowers the possibility of data handling errors. By locally processing and storing data inside approved countries, edge AI may help enterprises subject to data sovereignty requirements retain compliance. On the other hand, edge AI is not totally safe from security threats since any centralized database has the potential to attract attackers.
The ability to scale
By using cloud-based platforms and the built-in edge capabilities of original equipment manufacturer (OEM) technologies which include both hardware and software edge AI extends systems. These original equipment manufacturers (OEMs) have started to include native edge capabilities into their products, which makes scaling the system easier. Additionally, this extension makes it possible for local networks to continue operating even when there is downtime for nodes upstream or downstream.
Lower expenses
AI services housed in the cloud may come with hefty costs. Edge AI provides the possibility to use expensive cloud resources as a post-processing data accumulation repository, with the goal of using the data for analysis at a later time instead of for immediate field operations. As a result, cloud computers’ and networks’ workloads are lighter. When the workloads of CPU, GPU, and memory are divided across edge devices, the use of these resources is greatly reduced, making edge AI the most economical choice.
When a service’s whole calculation is handled via cloud computing, a large amount of work is placed on the central site. In order to send data to the central source, networks must withstand heavy traffic. The networks reactivate when machines complete tasks and send data back to the user. This constant data transmission back and forth is eliminated by edge devices. Therefore, when networks and robots are freed from the weight of managing every detail, they both feel less stressed.
Furthermore, edge AI’s autonomous qualities do away with the need for data scientists to oversee operations constantly. While human interpretation will always be crucial in deciding the final worth of data and the results it produces, Edge AI technology take on part of this burden, which ultimately saves firms money.
How Does Edge AI Work?
Neural networks and deep learning are used by Edge AI to train models that precisely identify, categorize, and characterize objects in the provided data. A centralized data center or the cloud are often used in this training procedure to handle the large amount of data required for model training.
Edge AI models become better over time after deployment. If an issue arises with the AI, the problematic data is often sent to the cloud so that the original AI model may be further trained. Eventually, the cloud-based AI model replaces the inference engine at the edge. This feedback loop plays a major role in improving the performance of the model.
Edge AI Use Cases
Industry-specific use cases for Edge AI
At the moment, real-time traffic updates on autonomous cars, wearable health-monitoring accessories (like smart watches), linked gadgets, and smart appliances are popular instances of edge AI. Additionally, a number of sectors are using Edge AI applications more often in an effort to save expenses, automate procedures, enhance decision-making, and maximize operations.
Healthcare
With the advent of cutting-edge gadgets and the practical use of Edge AI, healthcare providers are seeing a significant shift. This technology has the potential to create more intelligent healthcare systems while protecting patient privacy and speeding up reaction times when paired with cutting edge developments.
Wearable health monitors assess parameters including heart rate, blood pressure, glucose levels, and respiration using locally integrated AI algorithms. Additionally, wearable edge AI devices which are currently included in many popular smartwatches on the market have the ability to recognize when a patient falls unexpectedly and notify caregivers.
When emergency vehicles are outfitted with rapid data processing systems, paramedics may get information from health monitoring equipment and confer with doctors to come up with efficient patient stabilization plans. Staff members in the emergency department may simultaneously get ready to handle each patient’s specific needs. In these situations, integrating edge AI will assist to enable the real-time sharing of vital health data.
Manufacturing
Global producers have started using Edge AI technology to transform their production processes, increasing productivity and efficiency in the process.
Predictive maintenance, sometimes referred to as proactive identification of abnormalities and forecasting of machine problems, is possible using sensor data. Equipment sensors identify flaws and quickly alert management to necessary repairs, allowing for early resolution and minimizing downtime.
Edge AI may also improve quality control, worker safety, yield optimization, supply chain analytics, and floor optimization in this sector.
Retail
Online purchasing and eCommerce have helped businesses. Traditional brick-and-mortar retailers must innovate to engage consumers and enhance shopping. This tendency has led to smart checkouts, sensor-equipped shopping trolleys, and “pick-and-go” businesses. These technologies improve and speed up the traditional in-store experience for consumers by using Edge AI technology.
Smart Homes
Lightbulbs, doorbells, refrigerators, entertainment systems, and thermostats are now “smart”. Smart homes employ edge AI to enhance residents’ lives with ecosystems of connected gadgets. Without having to send data to a centralized distant server, Edge AI technology can analyze data quickly on-site, allowing residents to accomplish tasks like controlling their home’s temperature or verifying who is at their door. In addition to protecting resident privacy, this lowers the possibility of unwanted access to personal information.
Security and Surveillance
When it comes to security video analytics, speed is everything. Many computer vision systems don’t have the speed necessary for real-time analysis, therefore instead of analyzing the photos or videos that are taken by security cameras locally, they send them to a cloud-based device that has high-performance processing power. These cloud-based systems face challenges from latency concerns, which are typified by delays in data uploading and processing, if the data is not processed locally.
Edge AI Technology to detection skills and computer vision applications on smart security devices detects questionable behavior, alerts users, and sets off alarms. The inhabitants feel more secure and at ease with to these features.
Read more on Govindhtech.com
#EdgeAItechnology#machinelearning#EdgeAI#cloudcomputing#Neuralnetworks#smartwatches#news#technews#technology#technologynews#govindhtech
0 notes
Text
The mind on the machine
Artificial intelligence (AI) is augmenting the speed, efficiency and quality of human work. For companies involved in public-facing industries such as travel, education and healthcare, there is a major opportunity to leverage the latest advances in generative and conversational AI. These technologies can help free up limited resources, allowing companies to reinvest in front-line services.

Customer engagement is one of the key areas where AI can add value. In a joint study by the IBM Institute for Business Value (IBV) and Oxford Economics, over 1,000 respondents across 12 industries and 33 countries were surveyed. The results showed that 99% of survey participants reported an increase in customer satisfaction as a result of using virtual assistants.
Also, 96% of the respondents from the same survey group reported that their virtual assistants had exceeded, achieved or were expected to achieve the anticipated return on investment.
As more AI use cases emerge, the importance of AI ethics is also coming to the fore. In another IBV study, 85% of consumers said that they considered it important for organizations to factor in ethics as they use AI to tackle society’s problems. In the C-suite, ethics are an equally pressing concern. The number of executives who rank AI ethics as important has jumped from 50% to 75% in just 4 years.
There is growing consensus around how ethical AI technology can deliver substantial value for organizations in public-facing industries.
Realizing the promise of AI
As this research shows, companies that invest in designing, developing and customizing their virtual assistants can unlock significant value for their users—including customers, employees, trading partners and the public.
One example is Trinity ViaggiStudio (link resides outside ibm.com), a company specializing in international study holidays. Traveling to a different country and speaking in another language can be as daunting as it is exhilarating. The organization receives a flood of questions from students, parents and university staff as they research and prepare for their trips. Responding to these questions in a timely manner was stretching the Trinity ViaggiStudio team to its limits, until the company introduced AI to the equation.
By implementing an AI-powered virtual assistant powered by IBM® watsonx Assistant™, the organization has dramatically increased both responsiveness and customer satisfaction. The assistant, named Trinny, interacts with website visitors in real time, fielding 120 frequently asked questions in natural language. Today, the virtual assistant handles approximately 85% of all questions from website visitors, and Trinny’s ability to learn and improve over time means that this AI solution will deliver even more value for the organization as time goes on.
As Trinity ViaggiStudio has a large and dynamic client database, privacy was a key consideration when designing the AI solution. Working with IBM Business Partner® Ubico (link resides outside ibm.com), the organization designed the virtual assistant to process questions and answers anonymously and in compliance with the latest data protection regulations.
Reducing costs and freeing up resources
The IBV’s biennial survey on enterprise AI highlights that advanced adopters of the technology achieved proportionately more financial value from their investments than those who did not. In particular, the study found that AI is valuable for enhancing customer engagement and maintaining operational flexibility. More than 85% of advanced adopters reported that they are reducing operating costs with AI.
In the healthcare sector, these types of savings are especially valuable, as human and financial capital can be redirected to other services. In the UK, University Hospitals Coventry and Warwickshire (UHCW) NHS Trust (link resides outside ibm.com) delivers state-funded healthcare services to over one million local residents. To care for an aging population with increasingly complex care needs, the organization is continually searching for ways to manage workloads for clinicians and staff while improving patient experiences.
Working with IBM Business Partner SCC, UHCW piloted an AI-powered virtual assistant called People Assist to streamline its HR operations. Built in just seven weeks with IBM watsonx Assistant and trained using IBM watsonx.ai™, the AI solution uses retrieval-augmented generation (RAG) to analyze the Trust’s policy documentation and present responses to the user. This capability provides instant self-service support across all channels and touchpoints.
Since People Assist was launched, the solution has had over 500 conversations with employees, answering questions on topics ranging from car parking to pensions to staff training. In total, UHCW estimates that the virtual assistant will save approximately 2,080 working days a year across several key departments.
Applying robust ethical principles
In highly regulated public-facing industries such as healthcare, the ethical use of AI is imperative. As AI technologies become more deeply embedded into day-to-day operations, it’s crucial to ensure that robust guardrails are in place. Research by the IBV and Oxford Economics shows that trustworthy AI is crucial for maintaining public confidence in the technology.
Here, too, the IBM watsonx™ platform is helping AI innovators make sure that their solutions meet strict ethical standards. In a joint project, Informed Genomics (link resides outside of ibm.com), a UK-based genomics pioneer, and CanSense, an IBM Build Business Partner® and startup revolutionizing bowel cancer detection and treatment, are working together. They are bringing a pioneering AI-powered colorectal cancer screening solution to market.
Hosted in IBM Cloud®, the AI model behind the screening solution is monitored and managed using IBM watsonx.governance™. Using the platform, the team can track the health, accuracy and the potential for drift bias for their AI model, making it easier to demonstrate how the solution reaches its conclusions.
The potential benefits for the UK health system are substantial. By replacing today’s invasive and time-consuming diagnostics with a fast, simple and accurate blood test, the partnership anticipates that the solution will help physicians diagnose colorectal cancers faster. This solution will promote better outcomes and deliver cost savings of up to GBP 300 million a year for the NHS, which ultimately means better value for UK taxpayers.
Creating business value
An overwhelming number of the executives surveyed by IBV and Oxford Economics are convinced that AI assistants have been key to boosting customer satisfaction. According to the study, 3 in 4 executives see ethical use of AI as a source of competitive differentiation.
For organizations in public-facing industries, virtual assistants represent an enormous opportunity to free up people and resources and focus on delivering stakeholder value.
1 note
·
View note
Text
How Security Testing is Strengthening the Banking Industry?

In today's digital age, where financial transactions occur predominantly online, ensuring robust cybersecurity measures is paramount for the banking industry. Cyber-attacks pose significant threats to financial institutions, ranging from data breaches to financial frauds, leading to substantial financial losses and erosion of customer trust. According to a report by the Federal Reserve, cyber-attacks against financial institutions have increased by 13% in recent years, highlighting the urgency for enhanced security measures.
For instance, in 2020 alone, there were over 1000 reported data breaches in the financial sector, exposing millions of sensitive records to cybercriminals (source: Verizon's Data Breach Investigations Report). These statistics underscore the critical need for banks and financial institutions to bolster their cybersecurity defenses against evolving threats.
To mitigate these risks, financial institutions employ various security testing methodologies to identify vulnerabilities and strengthen their defenses against potential cyber-attacks. While it might be impossible to eliminate cyber threats, robust security testing practices significantly reduce the likelihood and impact of successful attacks.
Security Testing in the Banking Industry: Numbers and Resources
Here's a breakdown of some key numerical data and resources related to security testing in the banking industry:
Cost of Data Breaches: According to the Ponemon Institute https://www.ponemon.org/, the financial services industry experiences the highest average cost of a data breach at a staggering $4.24 million. This emphasizes the financial incentive for banks to invest in robust security testing practices.
Security Testing Market Growth: The global security testing market is expected to reach a value of USD 21.32 billion by 2027, according to a report by Grand View Research [report not publicly available]. This significant growth reflects the increasing awareness of cyber threats across various industries, including banking.
Top Security Threats to Financial Institutions
The financial services industry (predominantly banking) is looming large with a range of security threats. Heavens will break loose if hackers get hold of the customer data and vital information related to the bank! Partnering with a proven security testing company like Testrig Technologies should be considered in case the institution does not have in-house expertise with security testing.
Here are the top security threats being faced by the financial services industry (as a whole):
DDoS (distributed denial-of-service) Attacks
These attacks overwhelm a system with an influx of traffic, making it unavailable to legitimate users. Financial institutions rely on constant system uptime to process transactions and serve customers. A successful DDoS attack can disrupt operations, leading to financial losses and reputational damage.
According to a study by Neustar Security Services [report not publicly available], the financial services sector experiences more DDoS attacks than any other industry. In 2022, they observed a 125% increase in the average size of DDoS attacks compared to the previous year.
Web Application Attacks
These attacks target vulnerabilities in web applications, such as online banking portals, to steal sensitive data or compromise user accounts. A successful attack can result in financial losses for both the bank and its customers.
According to IBM's X-Force Threat Intelligence Index 2023 [ibm.com], 43% of all cyberattacks target web applications. Financial institutions are a prime target as they often hold a wealth of personal and financial information within these applications.
Insider Threats
Insider threats arise from malicious activities by individuals with authorized access to a system. These individuals may steal data, manipulate financial records, or disrupt operations. Insider threats are particularly dangerous because they can bypass many security measures.
Verizon's 2023 Data Breach Investigations Report [verizon.com] indicates that insider threats were involved in 25% of all data breaches. The insider threat landscape for financial institutions is complex, with disgruntled employees, accidental data leaks, and social engineering attacks all posing potential risks.
Emerging Technologies
As financial institutions embrace new technologies like cloud computing and artificial intelligence (AI), new attack surfaces are created. Cybercriminals are constantly evolving their tactics to exploit vulnerabilities in these emerging technologies.
While there isn't a single statistic encompassing all emerging technologies, a report by Gartner [gartner.com] predicts that by 2025, 60% of security breaches will involve cloud-based assets. This highlights the need for banks to adapt their security strategies to address the evolving threat landscape.
Apart from these major security threats, banks (and other financial institutions) should also address the following threats:
Backdoors And Supply-Chain Attacks
Third-party (and beyond) party vendor Attacks
Global penetration risks
Top Application Security Testing Tools
Irrespective of the size or scale of the security threat, banks should consider all of them as a top priority. At the end of the day, the reputation of the financial institution will get tarnished if it experiences any security threat!
Here are the top application security testing tools that can be used for addressing security threats faced by banks:
Static Application Security Testing (SAST) Tools:
SonarQube: SonarQube is an open-source platform for continuous code quality inspection that includes static code analysis for identifying security vulnerabilities. It provides detailed reports on code quality, security issues, and code smells, allowing developers to remediate issues early in the development lifecycle. SonarQube supports multiple programming languages and integrates seamlessly with popular development tools.
Dynamic Application Security Testing (DAST) Tools:
OWASP ZAP (Zed Attack Proxy): OWASP ZAP is an open-source web application security scanner that helps identify vulnerabilities in web applications. It performs dynamic analysis by simulating attacks against web applications and analyzing their responses for security flaws. OWASP ZAP supports automated scanning, manual testing, and scripting capabilities, making it suitable for both developers and security professionals.
Interactive Application Security Testing (IAST) Tools:
Acunetix with AcuSensor: Acunetix IAST, also known as Acunetix with AcuSensor, is a commercial Interactive Application Security Testing (IAST) solution offered by Acunetix. It combines elements of static and dynamic analysis to provide real-time feedback on application security vulnerabilities. AcuSensor is a proprietary sensor technology that instruments the application during runtime, allowing for deeper analysis and more accurate detection of vulnerabilities.
Also Read: Ultimate Guide To Types and Security Testing Tools
Best Practices of Security Testing in Banking Industry
Ensuring robust cybersecurity measures is imperative for the banking industry, given the sensitive nature of financial transactions and the constant threat of cyber-attacks. Implementing effective security testing practices helps banks identify vulnerabilities and fortify their defenses against potential threats. Here are some best practices for security testing in the banking industry:
Comprehensive Testing Approach: Employ a comprehensive testing approach that encompasses various methodologies such as penetration testing, vulnerability scanning, code review, and security architecture assessment. This ensures thorough coverage of all potential attack vectors and vulnerabilities within banking systems and applications.
Continuous Testing Lifecycle: Implement a continuous testing lifecycle that integrates security testing at every stage of the software development process, from initial design and development to deployment and maintenance. By embedding security testing into the development pipeline, banks can identify and remediate vulnerabilities early, reducing the risk of security breaches in production environments.
Regulatory Compliance: Ensure compliance with relevant regulatory standards and guidelines such as PCI DSS, GDPR, and SWIFT CSP. Conduct security testing in accordance with regulatory requirements to demonstrate adherence to industry standards and protect customer data from unauthorized access and disclosure.
Third-Party Vendor Assessment: Conduct thorough security assessments of third-party vendors and suppliers to ensure they adhere to stringent security standards and protocols. This includes evaluating the security posture of third-party software, applications, and services used within banking systems to mitigate the risk of supply chain attacks and data breaches.
Secure Coding Practices: Promote secure coding practices among developers and engineers involved in banking software development. Provide training and resources on secure coding techniques, secure API design, and common security pitfalls to minimize the introduction of vulnerabilities during the development process.
Incident Response Planning: Develop and regularly test incident response plans to effectively mitigate and manage security incidents and breaches. Establish clear protocols and procedures for detecting, reporting, and responding to security incidents, including escalation paths, communication protocols, and post-incident analysis.
Security Awareness Training: Provide comprehensive security awareness training to employees at all levels of the organization to raise awareness of security risks and best practices. Educate employees on common attack vectors such as phishing, social engineering, and malware to empower them to recognize and report suspicious activities.
Security Testing Automation: Leverage automation tools and technologies to streamline security testing processes and improve efficiency. Implement automated vulnerability scanning, code analysis, and security testing tools to identify and remediate vulnerabilities more effectively and reduce manual effort.
Also Read: The List of Top Security Testing Best Practices of 2024
Conclusion
Banks across the world (including those in emerging economies) are witnessing a digital transformation. Though this has brought increased convenience to the end-users, it has also resulted in an increase in the intensity of security threats. Security Testing services play a crucial role in ensuring that banking systems are robust enough to withstand these threats and protect sensitive financial information.
Hence, it is important for banks to address security-related loopholes as a priority so that their customers can truly enjoy a frictionless and highly secure banking experience. Banking institutions can also take support from proven companies like Testrig Technologies that have expertise in the security testing services sector.
0 notes
Text
artificaial inteligence
Despite numerous definitions emerging, John McCarthy in a 2004 paper (link outside IBM.com) provides the following definition of artificial intelligence (AI)."It is the science and engineering of making intelligent machines, especially intelligent computer programs," McCarthy writes.

Visit My site
1 note
·
View note
Text
Gain knowledge about Machine Learning for Digital Healthcare Innovation at the 14IHNPUCG from our experts.

How does machine learning work?
A subfield of artificial intelligence (AI) and computer science called machine learning focuses on using data and algorithms to simulate how humans learn, gradually increasing the accuracy of the system.
IBM has a long history with artificial intelligence. With his research on the game of checkers, one of its own, Arthur Samuel, is credited with coining the term "machine learning" (link outside of ibm.com). In 1962, Robert Nealey, a self-described checkers master, competed against an IBM 7094 computer, but he was defeated. This achievement seems insignificant in light of what is now possible, but it is regarded as a significant turning point for artificial intelligence.
Machine learning-based products like Netflix's recommendation engine and self-driving cars have been made possible in recent years because to technical advancements in storage and processing capability.
A casual format for presenting research findings or showcasing cutting-edge techniques is the poster session. The CME/CPD accredited 14th International Healthcare, Hospital Management, Nursing and Patient Safety Conference offers you the chance to present your original ideas in a less formal setting than a paper presentation. Submit your paper, and join us in Holiday Inn Dubai, UAE & Virtual from July 25–27, 2024. Submit here: https://nursing-healthcare.universeconferences.com/submit-abstract/
The rapidly expanding discipline of data science includes machine learning as a key element. Algorithms are trained using statistical techniques to produce classifications or predictions and to find important insights in data mining projects. The decisions made as a result of these insights influence key growth indicators in applications and enterprises, ideally. Data scientists will be more in demand as big data continues to develop and flourish. They will be expected to assist in determining the most pertinent business questions and the information needed to address them. The majority of the time, machine learning algorithms are developed utilising accelerated solution development frameworks like TensorFlow and PyTorch.
Increase in ML in medical settings
As technology advances, machine learning offers an exciting potential in the field of healthcare to enhance the precision of diagnoses, personalise care, and discover fresh approaches to problems that have persisted for decades. A tangible influence on the health of your community can result from using machine learning to programme computers to make connections and predictions and to unearth crucial insights from vast volumes of data that healthcare providers might otherwise overlook.
Machine learning seeks to enhance patient outcomes and generate previously unobtainable medical insights. Through predictive algorithms, it offers a means of validating the judgement and judgements of physicians. Consider a scenario where a patient is given a specific drug by a doctor. Then, using data from a patient who received the same treatment and benefited from it, machine learning can verify this treatment plan.
Internet of Medical Things and machine learning in healthcare
A constantly changing patient data set is essential when using machine learning in the healthcare industry. These data can be used to identify trends that help medical practitioners identify new diseases, assess risks, and forecast treatment outcomes. Due to the sheer number of patients and the variety of medical technology available for data collection, having medical equipment sync to a central "network" is an efficient approach to gather enormous amounts of data.
The network of medical apps and equipment that may connect with one another through online networks is known as the Internet of Medical Things (IoMT). Nowadays, a lot of medical gadgets come with Wi-Fi, enabling them to interface with other machines through cloud platforms or other devices connected to the same network. This makes it possible to track information from wearable devices, track medical histories, and monitor patients remotely, among other things. The IoMT is expected to grow rapidly as more wearable medical devices with internet connectivity hit the market.
Now is your chance to claim your Best Poster Award/Best Speaker Award certificates for the CME/CPD credited 14th International Healthcare, Hospital Management, Nursing and Patient Safety Conference, which will take place in Holiday Inn Dubai, UAE, on July 25–27, 2024. Attend the seminar right away to receive these certifications for the lowest price.
Register, grab your slot & certificates here: https://nursing-healthcare.universeconferences.com/registration/
How is machine learning applied in the medical field?
Numerous healthcare use cases involve the use of machine learning, and much of this technology's potential stems from its capacity to manage complicated data.
HEALTHCARE MACHINE LEARNING
disease prediction and treatment
medical imaging and diagnostic services
finding and creating new medications
Putting medical records in order
As data sets in the healthcare sector grow in size, they are frequently organised as unstructured data in electronic health records (EHRs). Machine learning organises this data into more organised groupings using natural language processing so that healthcare practitioners can swiftly draw conclusions from them.
For pharmaceutical businesses, machine learning and AI have also had an impact on medication research and development. Drugmakers are hoping that machine learning (ML) will be able to forecast how patients will react to different medications and pinpoint which individuals have the best probability of benefiting from the drug. The technology has already supported central nervous system clinical trials.
Additionally, machine learning advancements in healthcare have benefited telemedicine, as some machine learning firms are researching how to organise and deliver patient information to doctors during telemedicine sessions as well as capture information during virtual visits to streamline workflows.
On behalf of the Utilitarian Conferences Gathering, we are delighted to extend our warmest invitation to you to attend the upcoming Nursing Conference: 14th International Healthcare, Hospital Management, Nursing, and Patient Safety Conference. This prestigious event will be held from July 25-27, 2024 at Dubai, UAE. The theme of the conference is “displaying the most recent research results and innovations that underpin evidence-based nursing practise. Innovations in Nursing Research and Evidence-Based Practice.”
As a leading figure in the nursing profession, your presence and expertise would be invaluable to our conference. The event aims to foster collaboration, knowledge sharing, and professional growth among nurses and healthcare practitioners from all corners of the industry.
Connect with us:
WhatsApp: https://wa.me/442033222718 Email: [email protected] Visit: : https://nursing-healthcare.universeconferences.com/ Call for Papers: https://nursing-healthcare.universeconferences.com/submit-abstract/ Register here: https://nursing-healthcare.universeconferences.com/registration/
Nursing conferences 2023 | Nursing conferences in Dubai | Dubai Nursing Conference | Healthcare Conference in UAE | UCE Nursing Conference | Emirates Nursing Conference | Nursing Event | Nursing Symposium | Healthcare Conferences 2023 | Patient Safety Conferences in Dubai | Nursing Conferences | Nursing Meetings | Registered Nursing Congress | Healthcare Workshop | Patient Safety Symposiums | Patient Education Seminars | Healthcare Research | Healthcare Exhibitions | Healthcare Exhibitions | Registered Nurse Meetings | Registered Nurse Congress | Registered Nurse Workshop | Registered Nurse Symposiums | Registered Nurse Seminars | Registered Nurse Expo | Registered Nurse Exhibitions
0 notes
Photo

How to build more sustainable transportation infrastructure Transportation infrastructure—the networks of fixed installations that ensure safe transport of people and goods—is a critical part of modern economies. The post How to build more sustainable transportation infrastructure appeared first on IBM Blog. https://login.w3.ibm.com/oidc/sps/auth?client_id=MmNiYmFkNTQtM2ZhZi00&Target=https%3A%2F%2Flogin.w3.ibm.com%2Foidc%2Fendpoint%2Fdefault%2Fauthorize%3FqsId%3D41c42ea3-5529-4624-8a6f-4341244173aa%26client_id%3DMmNiYmFkNTQtM2ZhZi00
0 notes
Link
#AI#AICollaborationandTools#AIEducationandOutreach#AIEthicsandSafety#AIResearch#AIResearchandAdvancements#aiwebsite#AIWeekly#arXiv#best10AI#chatgpt#ComputerVision#DataAnalyticsandInsights#DeepLearning#DeepMind#FinancialServices#HealthcareandLifeSciences#IBMWatson#ImageandVideoAnalytics#InternetofThings#Kaggle#LanguageModels#MicrosoftAI#MITTechnologyReview#NaturalLanguageProcessing#NVIDIAAI#OpenAI#ProductionDeployment#ReinforcementLearning#ResearchandExperimentation
0 notes
Text
🎵 Happy Immortal Death [HID = HIDDEN] Day 2 U.S. Military OKCULT King Solomon-Michael Harrell Jr... Happy Immortal Death [HID = HIDDEN] Day 2 1968-michaelharrelljr.com... Happy Immortal Death [HID = HIDDEN] Day 2 harrelltut.com... ... ... Happy Immortal Death [HID = HIDDEN] Day Ritual [Dr] of Entering Baron Samedi's ANU GOLDEN 9 Ether [SAGE] Ægiptian Afterlife [SEA] Military Dynasty @ © 1698-2223 quantumharrelltelecom.tech 🎵
WELCOME BACK HOME IMMORTAL [HIM] U.S. MILITARY KING SOLOMON-MICHAEL HARRELL, JR.™

i.b.monk [ibm.com] mode [i’m] tech [IT] steelecartel.com @ quantumharrelltech.ca.gov

1st eye of tutankhamún [e.t.] ain’t dead!!! 9 Ether Eye TUT [E.T.] 2023 = 55 - 22 = 33 Master Afterlife Number [MAN] from 1698 in 1968 as 1968-michaelharrelljr.com
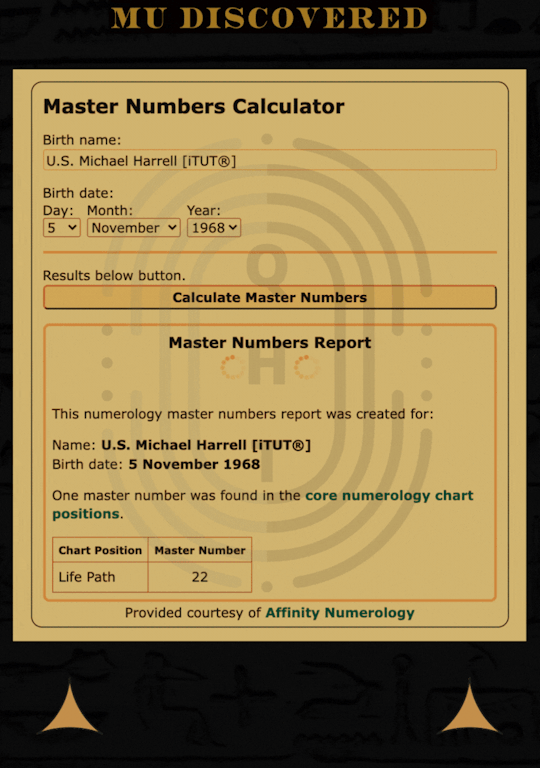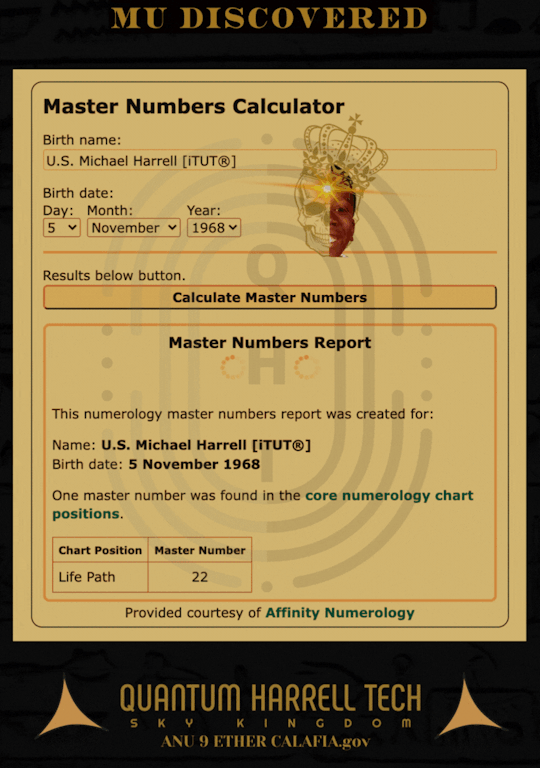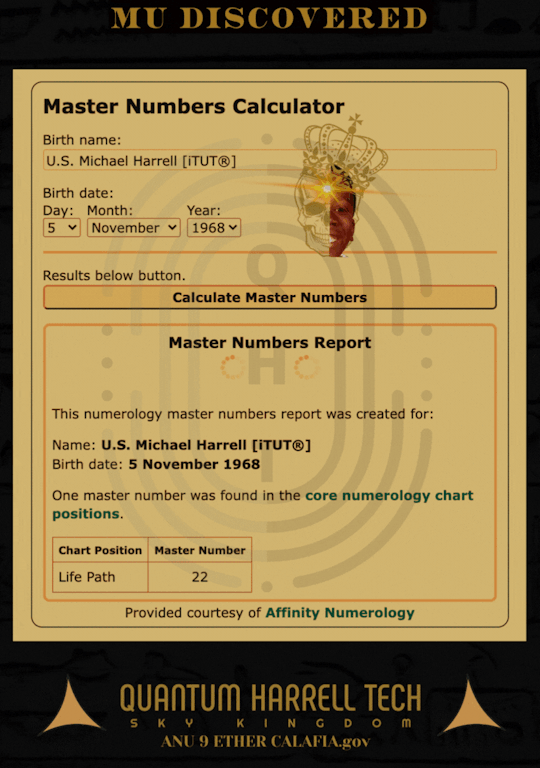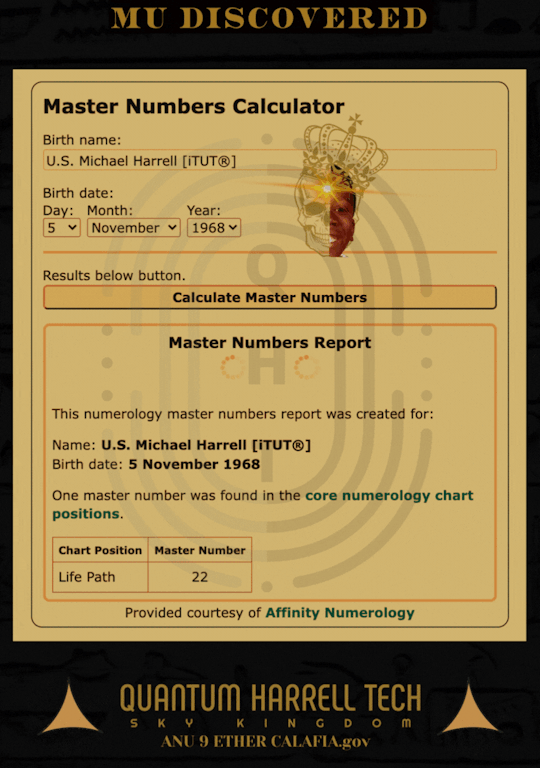
SEE?!?!?!

1698 EYE TUT [E.T.] BACK from 1968?!?!?!... as 1968-michaelharrelljr.com?!?!?!... AGAIN?!?!?!

1698 EYE TUT [E.T.] BARON SAMEDI 2?!?!?!... IN 2023-2223?!?!?!

O GOLDEN [OG] BLACK CHTHONIC SKULL & BONES ILLUMINATI LAW'D OF IMMORTAL 9 ETHER [i9] BLACK SUN DEATH... CHILE PLEASE RESURRECT 1968-michaelharrelljr.com on 11/05/2023-2223 again... since US GOLDEN 9 ETHER BLACK GULLAH GEECHEE DEITIES [GEDE] OF IWA NEVER DIE

© 1698-2223 quantumharrelltech.com - All Pentagon DotCom [D.C.] defense.gov Department Domain Communication [D.C.] Rights Reserved @ quantumharrelltech.ca.gov
#santa muerte#u.s. michael harrell#baron samedi#kingtutdna#quantumharrelltech#king tut#mu:13#harrelltut#kemet#o michael#quantumharrelltut#8:40am#immortal death day#occult art#occult rituals#yoruba tut#Brother Panic#IT'S THE BLACK GEDE FAMILY#this ain't the addams family#1968#1698#gen x#okc#golden 9 ether okcult society of oklahoma#black wall street#quadrillionaire#quadrillionaire families#golden black death ritual society#everything gold inside earth#everything gold deep inside mother's grand canyon
5 notes
·
View notes
Text
Fernando Vermelho invites you to join him at...
Fernando Vermelho invites you to join him at IBM TechU Sao Paulo (Portuguese) #IBMTechU #IBMLabservices
Fernando Vermelho invites you to join him at...
IBM Systems Lab Services AI Consultant Fernando Vermelho invites you to join him at IBM TechU in Sao Paulo this September. You'll learn about AI, deep learning, machine learning, IBM Mainframe, IBM Storage, Power Systems and so much more as you mingle with experts and network with peers. http://ibm.com/training/events
IBM Get Social Hub
7 notes
·
View notes
Text
Launching Triparty Repo with Cloud-Based IBM MQ

Triparty repo
A crucial component of the financial sector that necessitates high standards of efficiency and security is the exchange of securities between parties. The triparty repo dealing systems, which are essential to these transactions, need to communicate securely and seamlessly across many platforms. In order to administer the triparty repo dealing system, the Clearing Corporation of India Limited (CCIL) recently advised (link lives outside ibm.com) that all of its members use IBM MQ as their messaging software.
Continue reading to find out more about how IBM MQ affects triparty repo dealing systems and how to leverage it to facilitate safe and efficient transactions.
IBM MQ
IBM MQ’s impact on the triparty repository dealing system
IBM MQ is a messaging system that enables trustworthy and secure communication between parties. IBM MQ serves as the main conduit for communication in a triparty repo trading system, allowing the parties to communicate transaction-related data and instructions. IBM MQ improves a triparty repo dealing system’s effectiveness in a number of ways:
Effective communication
IBM MQ facilitates effective communication between participants, enabling them to instantly share instructions and information. This lowers the possibility of mistakes and misunderstandings, which in the financial sector can result in large losses. Parties can ensure correct and efficient transaction execution with IBM MQ. IBM MQ ensures that messages are delivered exactly once, a feature that is very crucial for the financial sector.
Scalable and able to handle more messages
IBM MQ is a perfect fit for triparty repository dealing systems because of its ability to handle a high amount of messages. IBM MQ can scale up to meet expanding communication demands as the system grows, maintaining it reliable and efficient.
Secure communication
IBM MQ protects sensitive data from illegal access. The banking business need this for security. IBM MQ protects data and transactions with encryption and other security mechanisms.
Easy and flexible integration
IBM MQ is a flexible messaging system that is simple to combine with other programmes and platforms. Because of this, adding new features and functionalities to the triparty repo dealing system is simple and enables it to adjust to the demands of customers and shifting market conditions.
How to properly use IBM MQ in systems that deal with triparty repos
To efficiently use IBM MQ in a triparty repo dealing system and make a difference, adhere to these guidelines:
Establish unambiguous message formats for various communication channels, including trade capture, confirmation, and settlement. By ensuring that all parties comprehend the message’s form and content, mistakes and misunderstandings will be minimised.
Use robust security measures, such as access limits and encryption, to safeguard sensitive data. By doing this, the data will be shielded against alteration and unwanted access.
Keep an eye on message queues to make sure there are no mistakes or bottlenecks and that messages are processed effectively. This will lessen the chance of system disruptions by assisting in the early identification of problems.
To manage and keep an eye on message queues, use message queue management tools. These instruments can assist in enhancing system performance, lowering latency, and optimising message processing.
To guarantee that communications are accurately formatted and include accurate content, test and validate them on a regular basis. This would facilitate the proper execution of transactions by lowering errors and misunderstandings.
IBM MQ and CCIL as a triparty repository dealing system
Central counterparty (CCP) Clearing Corporation of India Ltd. (CCIL) was founded in April 2001 to clear and settle money market, foreign exchange, and government securities transactions. In a number of financial market sectors overseen by the Reserve Bank of India (RBI), including the government securities, or outright, market repo and triparty repo, USD-INR, and currency forward segments, CCIL serves as a central counterparty.
It is mandatory for all members to utilise IBM MQ as the messaging platform for the triparty repo dealing system, as advised by CCIL. It is advised that members have IBM MQ v9.3 Long Term Support (LTS) release and higher installed in their software environment.
In triparty repo dealing systems, IBM MQ is essential for facilitating dependable, secure, and effective communication between parties. Through adherence to the previously mentioned principles, parties can efficiently utilise IBM MQ to enable seamless and secure transactions. It is inevitable that IBM MQ will become an ever more crucial aspect of triparty repo dealing systems as the financial industry develops further.
Are you prepared to improve the triparty repo transactions? On June 6, join with IBM for a webinar to find out more about the CCIL’s notification and how IBM MQ may help you maintain secure, dependable communication while streamlining your processes.
Advantages of IBM MQ
Protect your company from dangers.
IBM MQ never loses a message or delivers a message more than once, in contrast to its rivals.
Straightforward multi-style messaging
Link disparate systems that can enable events or PubSub, transaction processing, and message queuing.
24/7/365 technical assistance
You have the support of a sizable user base and a committed IBM MQ staff.
Leading-edge communications across all platforms
Get the same tested, highly secure, and performant messaging system, regardless of where and how you choose to deploy it.
Cloud-native “always-on” messaging
MQ’s small footprint and low infrastructure requirements make it ideal for cloud-native, highly available deployments.
Enterprise-wide, secure connectivity
Message-level security, identity access control, TLS protected communications, and other features help protect data.
Read more on Govindhtech.com
0 notes
Text
Welcome to IBM Systems Technical University...
Learn to leverage disruptive technology trends like cloud and cognitive at the #IBMTechU Prague
Welcome to IBM Systems Technical University...
Have you thought about the future of your career? Technology is changing the way we work and affecting future career choices. In the era of digital transformation, IT professionals must adjust to a rapidly shifting technology and business landscape. Learn to leverage disruptive technology trends like cloud and cognitive at the IBM Systems Technical University (TechU) in Prague. Learn more: Ibm.com/training/events/prague2019 #ibmtechU
IBM Get Social Hub
3 notes
·
View notes