#i started with ARPANET in the 80s
Explore tagged Tumblr posts
Text
i love that the uplifting SCREAMING CRYING THROWING UP has become the yin to the yang of a much older and pejorative RED NUDE AND MAD ONLINE
I thought “screaming crying throwing up” had entered common vernacular but then I heard a podcast collab where one of the hosts was like “yeah it’s crazy one of our fans said they were so excited for this collab they were screaming crying and throwing up” and the other host was like “wow is she okay?”
I literally forget that random common-knowledge phrases online do not translate into real life at all.
#yes i am old online#extremely online#i started with ARPANET in the 80s#wear a dust mask if you look that shit up because it is digital archaeology
4K notes
·
View notes
Text
⠀ ⠀ ⠀for the people who are worried about ⠀ ⠀ ⠀ ⠀ ⠀the use of socials in our server ;

this is roleplay. for us, that means imagination. interpretation. no, the internet as we know it today didn't exist and we're not having muses making whole facebook profiles or whatever. our "group chat" isn't like the group chat you're in with your friends on your iphone — it's simply a way for communication among muses to flow better. we will still be writing in this server, but not everyone has time to write novels every single day and that's okay. we're aiming to be a chill place... has absolutely nothing to do with laziness or whatsoever, but more so with the fact that people have lives outside of their phones and the internet. rp should first and foremost be a hobby. always.
that being said... technology was evolving in the 70s, and even the 60s. in the 1970s, technology and the internet were just starting to evolve. arpanet (which was introduced in 1969), the early internet, connected universities and researchers, introducing email and pioneering the packet-switching tech that still powers the web today. personal computers made their debut with machines like the altair 8800, apple I & II, and the trs-80, bringing computing into homes for the first time. microprocessors, floppy disks, and basic programming opened up new possibilities for tinkerers and developers. while the internet wasn’t public yet, this decade quietly laid the groundwork for everything digital that came after—from video games to global connectivity.
again: roleplay is imagination. fantasy. a way to let your creativity out of your little noggin'. but if the aspect of "socials" in a server like this bothers you, then you don't have to join us when we open. i know that there are people who do enjoy it and those who do, are more than welcome to come along for the ride! but if you don't like it, then your best option is to scroll and ignore. that too, is an easy thing to do on the internet !


0 notes
Text
Willie JATP is a Hacker: The Manifesto - Part One
all right, kids. it's time to do the thing i made this blog for, mostly because one (1) person indulged this hc (@crybabyddl this is your fault). as always, thanks to the ghost squad server for putting up with my rambling as i put this post together.
but the tl;dr is: willie jatp was one of the early generation of hackers as well as a skater, and this is how it happened.
edit: if anyone wants to use any parts of the as basis for fic/art/contente in general, feel free! please tag me and i'll boost it and make the rest of the ghost squad boost it ^_^
readmore below this line ^_^
first things first, my headcanon is that willie died in 1989 at the age of 19 (missed the moon landing by just a wee bit, which he's highkey bitter about).
second things second, his parents were college professors in the 70s with access to computers and ARPAnet (precursor to the internet that connected several major US universities).
and third things third, willie grew up spending time in his parents' classrooms and offices because they homeschooled him. mostly because he struggled in a regular classroom setting due to adhd and being a gifted kid tm.
anyways. so he's in the lab with his parents. chilling. when they get a message from a colleague at MIT (blech). and his parents, wanting to encourage his curiousity, let five-year-old willie send a message back.
this was, as the kids say, a Mistake.
willie became FASCINATED with computers. absolutely enthralled. so when one of the computers in his dad's lab broke and was written off by the university, willie went dumpster diving for it, snuck into an electrical engineering lab, and fixed it.
he was 9 at the time.
his parents, being supportive and also very happy to have something safe (hah!) to keep their son occupied, got him a programming guide and set him loose in their friend's office, a computer scientist who was amused by the small child in the corner with his computer and let him borrow whatever books he wanted. he learned very quickly how the computer worked... and how it differed from the way it was SUPPOSED to work. he became OBSESSED with that gap.
(he also became the unofficial anthropology department tech support, but that's another story)
when he's 15, the movie War Games comes out, and really thrusts computer hackers into the public's consciousness... and willie's. willie discovers that his little programs that took advantage of gaps in his computer's programming could be used for a purpose, rather than just to prove a concept. at the same time, the internet was beginning to boom at universities, which meant that willie, the unofficial tech support of the anthropology department, had a direct line to a major university's internet connection.
this was, as the kids say, Another Mistake.
("but when does he start skating, lilac?!" hush, children. we're getting there.)
willie made a few friends online. hacker friends. hacker friends who were part of one of the many hacker collectives to spring up in the 80s. it was his first time Having Friends, so of course when they decided to hack a major corporation as a joke, willie went right along with them.
this was, as the kids say, Another, Much Larger Mistake.
two months later, at 1 AM, the FBI broke down his front door, confiscated his computer equipment, and arrested him. He managed to avoid going to jail because he wass only 16, but he was banned from using the internet until 1990. his parents were... displeased, to say the least. his computer, they said, was not his until he earned enough money to replace the front door's hinges, which had suffered rather catastrophic damage when it got. yknow. kicked in.
willie was not a fan of that, and had already been barred from his main motivator for using his computer, since violating the terms of his sentence would mean (at best) being forced to work for the feds or (at worst) actually going to jail this time.
his mom was one of the original skateboarders, who could rival tony hawk in straight-up skill. one weekend, when he was complaining about being bored and missing his friends (many of whom were now in jail), his mom dragged him to the skate park and taught him to skate.
willie got good. really good. he was competing in the local scene, hoping to make it to the x games.
then. well.
he died.
#Willie JATP#JATP Willie#JATP#Julie and the Phantoms#jatp meta#willie meta#willie fic manifesto#hacker willie manifesto#i FINALLY did it#i wrote the damn thing#or at least#half of it#(should i be working on my protocol analyzer? maybe)#shush#also inb4 someone says its unrealistic: i personally know at LEAST 4 people who got hired by the people they hacked#and/or the government when they got arrested#there will be a part 2 eventually#about willie after death#but yeah. this is my willie backstory#ghost squad#and yes i did make sure all the timelines work out#if yall have thoughts........ please. commente.
46 notes
·
View notes
Text
Events 11.21
164 BCE – Judas Maccabeus, son of Mattathias of the Hasmonean family, restores the Temple in Jerusalem. This event is commemorated each year by the festival of Hanukkah. 235 – Pope Anterus succeeds Pontian as the nineteenth pope. During the persecutions of emperor Maximinus Thrax he is martyred. 1009 – Lý Công Uẩn is enthroned as emperor of Đại Cồ Việt, founding the Lý dynasty. 1386 – Timur of Samarkand captures and sacks the Georgian capital of Tbilisi, taking King Bagrat V of Georgia captive. 1620 – Plymouth Colony settlers sign the Mayflower Compact (November 11, O.S.) 1676 – The Danish astronomer Ole Rømer presents the first quantitative measurements of the speed of light. 1783 – In Paris, Jean-François Pilâtre de Rozier and François Laurent d'Arlandes, make the first untethered hot air balloon flight. 1789 – North Carolina ratifies the United States Constitution and is admitted as the 12th U.S. state. 1861 – American Civil War: Confederate President Jefferson Davis appoints Judah Benjamin Secretary of War. 1877 – Thomas Edison announces his invention of the phonograph, a machine that can record and play sound. 1894 – Port Arthur, China, falls to the Japanese, a decisive victory of the First Sino-Japanese War; Japanese troops are accused of massacring the remaining inhabitants. 1902 – The Philadelphia Football Athletics defeated the Kanaweola Athletic Club of Elmira, New York, 39–0, in the first ever professional American football night game. 1905 – Albert Einstein's paper that leads to the mass–energy equivalence formula, E = mc², is published in the journal Annalen der Physik. 1910 – Sailors on board Brazil's warships including the Minas Gerais, São Paulo, and Bahia, violently rebel in what is now known as the Revolta da Chibata (Revolt of the Lash). 1916 – Mines from SM U-73 sink the HMHS Britannic, the largest ship lost in the First World War. 1918 – The Flag of Estonia, previously used by pro-independence activists, is formally adopted as the national flag of the Republic of Estonia. 1918 – The Parliament (Qualification of Women) Act 1918 is passed, allowing women to stand for Parliament in the UK. 1918 – A pogrom takes place in Lwów (now Lviv); over three days, at least 50 Jews and 270 Ukrainian Christians are killed by Poles. 1920 – Irish War of Independence: In Dublin, 31 people are killed in what became known as "Bloody Sunday". 1922 – Rebecca Latimer Felton of Georgia takes the oath of office, becoming the first female United States Senator. 1927 – Columbine Mine massacre: Striking coal miners are allegedly attacked with machine guns by a detachment of state police dressed in civilian clothes. 1942 – The completion of the Alaska Highway (also known as the Alcan Highway) is celebrated (however, the highway is not usable by standard road vehicles until 1943). 1944 – World War II: American submarine USS Sealion sinks the Japanese battleship Kongō and Japanese destroyer Urakaze in the Formosa Strait. 1945 – The United Auto Workers strike 92 General Motors plants in 50 cities to back up worker demands for a 30-percent raise. 1950 – Two Canadian National Railway trains collide in northeastern British Columbia in the Canoe River train crash; the death toll is 21, with 17 of them Canadian troops bound for Korea. 1953 – The Natural History Museum, London announces that the "Piltdown Man" skull, initially believed to be one of the most important fossilized hominid skulls ever found, is a hoax. 1959 – American disc jockey Alan Freed, who had popularized the term "rock and roll" and music of that style, is fired from WABC radio over allegations he had participated in the payola scandal. 1961 – The "La Ronde" opens in Honolulu, first revolving restaurant in the United States. 1962 – The Chinese People's Liberation Army declares a unilateral ceasefire in the Sino-Indian War. 1964 – The Verrazano-Narrows Bridge opens to traffic. At the time it is the world's longest bridge span. 1964 – Second Vatican Council: The third session of the Roman Catholic Church's ecumenical council closes. 1967 – Vietnam War: American General William Westmoreland tells news reporters: "I am absolutely certain that whereas in 1965 the enemy was winning, today he is certainly losing." 1969 – U.S. President Richard Nixon and Japanese Premier Eisaku Satō agree on the return of Okinawa to Japanese control in 1972. The U.S. retains rights to bases on the island, but these are to be nuclear-free. 1969 – The first permanent ARPANET link is established between UCLA and SRI. 1970 – Vietnam War: Operation Ivory Coast: A joint United States Air Force and Army team raids the Sơn Tây prisoner-of-war camp in an attempt to free American prisoners of war thought to be held there. 1971 – Indian troops, partly aided by Mukti Bahini (Bengali guerrillas), defeat the Pakistan army in the Battle of Garibpur. 1972 – Voters in South Korea overwhelmingly approve a new constitution, giving legitimacy to Park Chung-hee and the Fourth Republic. 1974 – The Birmingham pub bombings kill 21 people. The Birmingham Six are sentenced to life in prison for the crime but subsequently acquitted. 1977 – Minister of Internal Affairs Allan Highet announces that the national anthems of New Zealand shall be the traditional anthem "God Save the Queen" and "God Defend New Zealand". 1979 – The United States Embassy in Islamabad, Pakistan, is attacked by a mob and set on fire, killing four. 1980 – A deadly fire breaks out at the MGM Grand Hotel in Paradise, Nevada (now Bally's Las Vegas). Eighty-seven people are killed and more than 650 are injured in the worst disaster in Nevada history. 1985 – United States Navy intelligence analyst Jonathan Pollard is arrested for spying after being caught giving Israel classified information on Arab nations. He is subsequently sentenced to life in prison. 1986 – National Security Council member Oliver North and his secretary start to shred documents allegedly implicating them in the Iran–Contra affair. 1992 – A major tornado strikes the Houston, Texas area during the afternoon. Over the next two days the largest tornado outbreak ever to occur in the US during November spawns over 100 tornadoes. 1995 – The Dayton Agreement is initialed at the Wright-Patterson Air Force Base, near Dayton, Ohio, ending three and a half years of war in Bosnia and Herzegovina. 1996 – Humberto Vidal explosion: Thirty-three people die when a Humberto Vidal shoe shop in Río Piedras, Puerto Rico explodes. 2002 – NATO invites Bulgaria, Estonia, Latvia, Lithuania, Romania, Slovakia and Slovenia to become members. 2002 – Arturo Guzmán Decena, founder of Los Zetas and high-member of the Gulf Cartel, was killed in a shoot-out with the Mexican Army and the police. 2004 – The second round of the Ukrainian presidential election is held, giving rise to massive protests and controversy over the election's integrity. 2004 – Dominica is hit by the most destructive earthquake in its history. The northern half of the island sustains the most damage, especially the town of Portsmouth. In neighboring Guadeloupe, one person is killed. 2004 – The Paris Club agrees to write off 80% (up to $100 billion) of Iraq's external debt. 2006 – Anti-Syrian Lebanese politician and government minister Pierre Gemayel is assassinated in suburban Beirut. 2009 – A mine explosion in Heilongjiang, China kills 108. 2012 – At least 28 are wounded after a bomb is thrown onto a bus in Tel Aviv. 2013 – Fifty-four people are killed when the roof of a shopping center collapses in Riga, Latvia. 2013 – Massive protests start in Ukraine after President Viktor Yanukovych suspended signing the Ukraine–European Union Association Agreement. 2014 – A stampede in Kwekwe, Zimbabwe caused by the police firing tear gas kills at least eleven people and injures 40 others. 2015 – The government of Belgium imposed a security lockdown on Brussels, including the closure of shops, schools, public transportation, due to potential terrorist attacks. 2017 – Robert Mugabe formally resigns as President of Zimbabwe, after thirty-seven years in office. 2019 – Israeli Prime Minister Benjamin Netanyahu is indicted on charges of bribery, fraud, and breach of trust.
4 notes
·
View notes
Text
But the other thing is that capitalism was BANNED from the internet until it was fully developed and had been in operation for at least a decade. I can't remember exactly when the floodgates finally opened, because I only had a 2400 bps modem and was mostly logging jn from campus so it crept up on me, but WE BUILT THIS CITY before we allowed the .coms online.
The internet was linked up from a lot of different regional networks and research institutions, none of which were commercial, and commerce was not originally allowed on their hardware.
Oops. I just accidentally wrote a Folk History of the Web According to Me, picking up in media res the late 80s, so let me put my spam behind a read more...
The internet happened when various local networks started to connect.
Various governments had networks connecting certain officials and/or major departments and institutions.
ARPAnet and DARPAnet were US military networks. I think ARPAnet was the nonclassified stuff. At any rate, it wound up forming part of the early backbone of what eventually became the web.
Europe and Asia had similar regional networks whose use and function varied by area.
There were also powerful computer networks connecting various science institutions and organizations like NASA, the National Science Foundation and CERN. CERN, the european organization for nuclear research, was building the Large Hadron Supercollider. One of its scientists invented the web during his downtime, as you do. [Edit: Okay, I had forgotten NSFNET basically was the original internet, as in the network with that name, which is why it was non-commercial.]
Banks had to create a secure network to communicate with one another. They hooked into the internet late, understandably, but their networks were some of the earliest and most robust non-government regional communications links between computers.
Usenet was out there pretty early, and/or Compuserve, but they required a modem hooked up to a phone to access them. These were dialups: you hooked your modem to your phone, and then your modem called their phone number to connect to their server.
I was on one of the regional academic networks connecting various colleges and universities' in-house computer systems, which were also noncommercial. Each college VAX had its own in-house filing system and bboards, then there were special public folders where we could store copies of files. People who knew those folders existed (usually via primitive email or a phone call) could then access them.
All the colleges and universities seemed to be hooking into a larger regional network, BITNET, that allowed us communicate with more and more different places. Access to BITNET was free to all institutions that joined, provided you gave access to your own servers to other institutions on BITNET.
The web was invented by CERN's Tim Berners-Lee in 1991 to solve some of the major headaches we were facing: the lack of standardized file formats requiring conversions (assuming someone had written a program to do it, and that not only had to account for the file format but your operating system) and the fact that there was no road map to where files were stored. By that time we had programs like Archie, Veronica, Fetch and Gopher which allowed us to search the public directories institutions had put online — those programs had to be kept up to date with a list of addresses for each of those folders. Tim Berners-Lee came up with a Universal Resource Locator to standardize "where is it?" and HyperText Markup Language as a standard format for "what does it say?" Then people wrote web browsers to find and display those things for each operating system.
And then suddenly BITNET connected up to THE INTERNET, singular, for about a year our email addresses changed to start with IN% signifying we were part of the net [Edit: I didn't realize it but this was the internet of the National Science Foundation, a US government-funded institution for the advancement of science, already hooked up to CERN and other overseas institutions.]
Somebody decided that all email addresses needed the @ sign with .edu on the end and email became fairly common, although most of us were still logging in from a computer center on campus or at a library because few people had modems.
I headed to grad school in 1993 just after the web launched and joined a project uploading ancient Greek texts, art, and archaeology online, even though only a few people had the bandwidth to access it and we had to fight to get jpg as a standard as well as gif becausr photos needed more colors even if they were lossy.
Builders of the early Internet and web were fiercely committed to the idea that the internet was going to be free to use, a tool for all humanity, a property of the commons. My boss in grad school, Dr. Greg Crane, used to storm out of his office shouting, "Power to the People! Information to the Masses!" Ahahaha.
The web browser Mosaic (of blessed memory) happened, and then Netscape, and we'd gotten the infant web up and running just in time for a broken comet to smack into Jupiter in July 1994 over the course of a week which was GREAT because all the telescopes in the world and off it were pointed at the same exact thing and every astronomer was posting their pictures and data and reactions in email exchanges on their own servers and i did not sleep for a WEEK jumping from link to link because search was in its infancy so the only way to find things was to follow links from one person's list of cool links and recommendations to the next. But seriously, i don't think people realize how influential that comet was in building the web. Need bred innovation. People were figuring out how to liveblog before blogs, create animated slideshows, and so much else that we take for granted now, long before social media.
BUT THEN Microsoft Explorer showed up to spoil the party, trying to create proprietary HTML codes and video formats to conflict with the open source standards agreed upon by the W3 consortium so everyone would have to use windows operating systems for webpages to display property. For several years we had to code webpages 2 ways to work on iE or everything else because so many ordinary people bought PCs that came with IE installed we had no choice, and it was a fucking nightmare.
Which may have contributed to the decision for the mostly college and university or taxpayer-funded infrastructure on which the internet was built to allow the first commercial use of the internet, because of course they weren't gonna put up with Microsoft's BS. But the .coms came galloping in and swamped us, and the internet became a very different place with almost no memory of the Before days of research, information, discussion forums, personal websites, news, MU*s, erotica (of course) and fandom and the overlap between them, and Random Shit like hamsterdance.
(And yes I have totally sidestepped AOL, the pathway to the net for many people not at colleges/universities. I recall we were using its junk mail CDs as drink coasters in 1995. It was capitalist in the sense it was a subscription service; I'm not sure whether one was allowed to buy or sell or advertise on it when it started.)
[Edit: Okay apparently what happened was that while the NSF and other research institutions built a free-to-use internet on their taxpayer-funded computers and networks originally created for research and education and and public needs, which couldn't be used for commerce, early subscription services like Compuserve created forums and content within a "walled garden" on its own servers for computer-savvy geeks who could access it with computers and dialup modems. AOL was a later subscription service that did the same except using hypertext and a primitive web browser to create an interface non-geeks could understand. Soon users of each of these services were sharing pictures, messages, recipes, etc, and newspapers or companies might establish a presence on them. Subscription services like AOL didn't have rules against selling stuff, although at first it was risky to run any kind of business. NASA and various educational sites — including academic institutions! — were all too happy to make our free information, educational content and science available fo users of subscription services and people in other countries' networks that might not have the "no commercial use" rules of the official NSF-Internet. Business interests started lobbying the US Congress to open up the internet to commerce since its networks were the fastest and most widespread, and the NSF bowed out. it sold off public assets to private companies, internet Service Providers were born and became the way most people login, and .coms started springing up. Before that, internet domains consisted of .edu, .gov, .org for nonprofits, .net for regional networks like bitnet, and some country suffixes as they started hooking up to the NSF's internet.]
With fibromyalgia brain fog, I'm sure I have details wrong. I'm fuzzy on when some things happened except that I was on bitnet in 1990 and the infant web by 1993, working on the Perseus Project I alluded to above — to my pride and chagrin it still has some of the graphics I drew for its baby web interface back in 1994.
TL;DR: publicly-funded institutions gave us the internet.
I think one might however argue that capitalism gave us social media, which arrived over ten years later. Understandably, many people do not realize how much of the internet was established before that.
[Edit: I wrote most of this with insomnia between 3 and 6am, editing and reediting to make it more coherent. Here's some good sources to fact check me.
Tbe Computer Museum's EXCELLENT History of the Internet, which has been around forever and i'm glad it 's still up. I love its maps of the early regional nets growing and linking up. Also: oh, THAT's what Al Gore did. Which is more impressive than you'd think, since most of Congress at the time didn't know how to use email or even mobile phones.
The Living Internet is a well-organized little index of the early parts of the web and mentions the EU net which I am glad to lean about.
Here's another short sweet History of the Net from 1993, just about the time the web was taking off.
A Brief History of the Web at the University of Georgia where I checked myself on some dates.
We Are the Web: WIRED Magazine's 2005 article on the first 10 years of the commercial web.
The whole “capitalism gave you the Internet” thing is especially funny if you actually work in network infrastructure, since one of the first things you’ll learn is that many software technologies that are absolutely critical to the day to day functioning of the Internet are being maintained on a volunteer basis by small, decentralised teams working in whatever free time their day jobs leave them, and that we’d have a crisis on our hands within thirty days if any one of those maintainers were to get hit by a bus and nobody stepped up to replace them. Like, the whole commercial edifice of the Internet rests on the continuous unpaid labour of a relative handful of people who are essentially just doing it for fun.
88K notes
·
View notes
Text
Warning: This is not an endorsement or encouragement for you to start behaving in illegal or immoral behaviour. I am not held responsible for any trouble you decide to get into; or what you do I encourage people to use my information I post in a responsible way and not violate any state or federal laws
History Of The Dark Web
The Deep Web and it’s Dark Web brother have been in the public eye more than usual in the past few years. Once the things that happen on the hidden part began having an impact on the day to day and safety of our lives, ordinary people started to take an interest. That doesn’t mean the hidden part of the internet is a recent development. It’s just about as old as the internet itself!
Now days tho it is dangerous if you are less then tech savvy and it could turn deadly for a new person stumbling onto the dark side of the internet where things like killers for hire, Drugs, Guns, Fake Money, and even Identities and people can be bought! You can only guess what can happen if you stumble onto one of these sites without knowing and ask the wrong questions!
1980
The history of the hidden web is almost as old as the history of the internet itself. Obviously, the same technology that made the internet and the web possible, also makes the Dark Web possible thanks to its architecture and designs. Which is why it is fair to pin the start of the Dark Web to ARPANET. Which is the direct precursor to the internet of today? While ARPANET may not have had a Dark Web as we know it now from the start, it wouldn’t take long before people started to make use of this technology for things they wanted to keep a secret. It turns out that the first ever online sale happened in the early 70s and was in fact cannabis. Students at Stanford sold weed to students at MIT, using ARPANET. Remember that at this point most people didn’t have personal computers, much less home internet access.
In the 1980s, access to the internet for normal citizens is still a dream. This was the decade when everything needed for a worldwide web would fall into place. In the early 80s, the TCP/IP standard is solidified. By the mid- 80s personal computers and modems are, if not affordable, at least available for anyone to buy. Internet pioneers also invented the domain name system we use to resolve website names during this decade.
Data havens emerge as an idea at this time as well. Since the world was going global, worries about where data should be stored came to the fore. Storing your data in a haven meant sending it out of the country to a territory that had better legal protection against government spying. At the extreme, data havens would be in no country at all. They would be built on structures or vessels out in international waters . A similar idea to seasteading. Actual data havens in the 80s popped up in the Caribbean islands.(Or as it turns out and which is slowly starting to be developed the Decentralized web run off the BlockChain and which has the potential to be way more secure then the darkweb)
1990's
The 1990s are without a doubt the time when the World Wide Web went mainstream. Thanks to web technologies like HTTP and FTP along with graphical computers capable of running a web browser, there was a sudden mainstream appeal to this whole internet thing.
Towards the end of the 1990s, there was a real leap in the technologies that allowed large amounts of data, such as multimedia, to be shared online. MP3 technology in particular lead to a massive shakeup of the music industry. Thanks to like the likes of Napster, people could perform illegal peer-to-peer exchanges of ripped and compressed music. This caused a complete meltdown among musicians and music executives. Lars Ulrich famously sued Napster which was really symbolic of the battle between old and new school. Today the music industry has adapted and streaming subscriptions are the norm. Without Dark Web alike peer-to-peer exchanges it’s doubtful we’d have the consumer-friendly online media world of today.
2000
The Dark Web proper really got its start in March of 2000 with the release of Freenet. The service still exists today and provides a censorship-resistant way to use the web. It is a true implementation of the Dark Web and provided a way for plenty of illegal information to pass around. This included illegal pornographic material and pirated content. Of course, actually exchanging money anonymously is still incredibly hard at this point, since you have to use cash. So Freenet doesn’t lead to any black market activity to any significant degree.
A data haven called HavenCo was established in Sealand (a seasteading micronation) which promised to store sensitive information in a place where no government could stick its nose. It seemed like a Dark Web dream, but by the early 2010s HavenCo was dead.
The most important Dark Web development of all time happened in 2002, with the release of TOR or The Onion Router. It was created by non-other than the US government, as a way to help their own operatives remain untraceable. It’s no exaggeration to say that the Dark Web of today could not exist without this technology.
Late in the 2000s came the advent of cryptocurrency in the form of Bitcoin. The final piece of the puzzle needed to make the Dark Web really click.
The Early 2010's
The 2010s represent the era where cryptocurrency and TOR met to create the first proper black markets. The pioneer was the Silk Road, which is now long defunct. Despite taking all the important figures out behind the Silk Road, it has seemingly done little to stop the trade of drugs and other illegal goods and services over the Dark Web.
This is the era in which the Dark Web becomes a topic of public concern, rather than just something discussed as cyber security conferences. Many mainstream articles emerge that explain the difference between the massive Deep Web and the relatively tiny Dark Web.
It becomes especially scary when it emerges that terrorists are using the Dark Web to communicate and coordinate. Ironic, given what the US created TOR for originally. Research published showing that the Dark Web is mainly being used to commit crimes.
Today
The Dark Web of today is reportedly in decline. Despite this, there is an incredible variety of hidden services and significant information exchange happening out of sight of the mainstream web. It doesn’t really matter that the Dark Web is relatively small compared to the surface web as a whole. Its impact is disproportionately large. Small groups of hackers collaborating on the Dark Web can bring a multi-billion Dollar internet company to its knees. Hackers end up impacting millions of users.
Darknet black markets are also thriving and putting both traditional and new synthetic drugs into the hands of anyone who wants them. Cryptocurrency has been the biggest factor in this maturation of the Dark Web.
Now you know the basic history of the dark web,. now lets get into the history of the newer technologies that help run the dark web and keep it secure technologies like TOR and the Cryptocurrencies that helps collect payment from the goods that are sold on the dark web.
History Of Tor
Tor is based on the principle of ‘onion routing’ which was developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The alpha version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. It was launched on September 20, 2002. Further development was carried under the financial roof of the Electronic Frontier Foundation (EFF).
The Tor Project Inc. is a non-profit organization that currently maintains Tor and is responsible for its development. The United States Government mainly funds it, and further aid is provided by Swedish Government and different NGOs & individual sponsors.
The U.S. National Security Agency (NSA) has called Tor “the King of high secure, low latency Internet anonymity.” And similar comments by BusinessWeek magazine, “perhaps the most effective means of defeating the online surveillance efforts of intelligence agencies around the world”.
Another speculation made is that Tor takes its funding from the U.S. Government which may lead to the assumption that NSA may have compromised the identities of individual Tor users. However, the executive director Andrew Lewman has disclaimed any confederations with NSA.
How it works
Tor works on the concept of ‘onion routing’ method in which the user data is first encrypted and then transferred through different relays present in the Tor network, thus creating a multi-layered encryption (layers like an onion), thereby keeping the identity of the user safe.
One encryption layer is decrypted at each successive Tor relay, and the remaining data is forwarded to any random relay until it reaches its destination server. For the destination server, the last Tor node/exit relay appears as the origin of the data. It is thus tough to trace the identity of the user or the server by any surveillance system acting in the mid-way.
Other than providing anonymity to standalone users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Also, P2P applications like BitTorrent can be configured to use the Tor network and download torrent files.
Is It Safe
Various claims have been made to compromise Tor’s anonymity and security from time to time. The most famous one was the Bad Apple Attack in which the researchers claimed to have identified around 10k IP addresses of active BitTorrent users who were connected via Tor.
The Heartbleed bug was behind another major compromise in April 2014 which halted the Tor network for several days.
Traffic Fingerprinting is a method used to analyze web traffic by analyzing the patterns, responses, and packets in a particular direction. This technique can be used to attack the Tor network by making the attacker’s computer act as the guard. The main vulnerability was found at its exit points where the level of security is very low as compared to the rest of the Tor network.
The History of cryptocurrencies
In 1983, the American cryptographer David Chaum conceived an anonymous cryptographic electronic money called ecash. Later, in 1995, he implemented it through Digicash, an early form of cryptographic electronic payments which required user software in order to withdraw notes from a bank and designate specific encrypted keys before it can be sent to a recipient. This allowed the digital currency to be untraceable by the issuing bank, the government, or any third party.
In 1996, the NSA published a paper entitled How to Make a Mint: the Cryptography of Anonymous Electronic Cash, describing a Cryptocurrency system first publishing it in a MIT mailing list and later in 1997, in The American Law Review (Vol. 46, Issue 4).
In 1998, Wei Dai published a description of "b-money", characterized as an anonymous, distributed electronic cash system. Shortly thereafter, Nick Szabo described bit gold. Like bitcoin and other cryptocurrencies that would follow it, bit gold (not to be confused with the later gold-based exchange, BitGold) was described as an electronic currency system which required users to complete a proof of work function with solutions being cryptographically put together and published. A currency system based on a reusable proof of work was later created by Hal Finney who followed the work of Dai and Szabo.
The first decentralized cryptocurrency, bitcoin, was created in 2009 by pseudonymous developer Satoshi Nakamoto. It used SHA-256, a cryptographic hash function, as its proof-of-work scheme. In April 2011, Namecoin was created as an attempt at forming a decentralized DNS, which would make internet censorship very difficult. Soon after, in October 2011, Litecoin was released. It was the first successful cryptocurrency to use scrypt as its hash function instead of SHA-256. Another notable cryptocurrency, Peercoin was the first to use a proof-of-work/proof-of-stake hybrid.
On 6 August 2014, the UK announced its Treasury had been commissioned to do a study of cryptocurrencies, and what role, if any, they can play in the UK economy. The study was also to report on whether regulation should be considered.
Definition
According to Jan Lansky, a cryptocurrency is a system that meets six conditions:
The system does not require a central authority, its state is maintained through distributed consensus.The system keeps an overview of cryptocurrency units and their ownership.The system defines whether new cryptocurrency units can be created. If new cryptocurrency units can be created, the system defines the circumstances of their origin and how to determine the ownership of these new units.Ownership of cryptocurrency units can be proved exclusively cryptographically.The system allows transactions to be performed in which ownership of the cryptographic units is changed. A transaction statement can only be issued by an entity proving the current ownership of these units.If two different instructions for changing the ownership of the same cryptographic units are simultaneously entered, the system performs at most one of them.
In March 2018, the word cryptocurrency was added to the Merriam-Webster Dictionary
What is Blockchain
A blockchain, originally block chain, is a growing list of records, called blocks, that are linked using cryptography.[1][6] Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data (generally represented as a Merkle tree).
By design, a blockchain is resistant to modification of the data. It is "an open, distributed ledger that can record transactions between two parties efficiently and in a verifiable and permanent way". For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for inter-node communication and validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without alteration of all subsequent blocks, which requires consensus of the network majority. Although blockchain records are not unalterable, blockchains may be considered secure by design and exemplify a distributed computing system with high Byzantine fault tolerance. Decentralized consensus has therefore been claimed with a blockchain.
Blockchain was invented by a person (or group of people) using the name Satoshi Nakamoto in 2008 to serve as the public transaction ledger of the cryptocurrency bitcoin. The identity of Satoshi Nakamoto is unknown. The invention of the blockchain for bitcoin made it the first digital currency to solve the double-spending problem without the need of a trusted authority or central server. The bitcoin design has inspired other applications, and blockchains that are readable by the public are widely used by cryptocurrencies. Blockchain is considered a type of payment rail. Private blockchains have been proposed for business use. Sources such as Computerworld called the marketing of such blockchains without a proper security model "snake oil".
Structure
A blockchain is a decentralized, distributed and public digital ledger that is used to record transactions across many computers so that any involved record cannot be altered retroactively, without the alteration of all subsequent blocks. This allows the participants to verify and audit transactions independently and relatively inexpensively. A blockchain database is managed autonomously using a peer-to-peer network and a distributed timestamping server. They are authenticated by mass collaboration powered by collective self-interests. Such a design facilitates robust workflow where participants' uncertainty regarding data security is marginal. The use of a blockchain removes the characteristic of infinite reproducibility from a digital asset. It confirms that each unit of value was transferred only once, solving the long-standing problem of double spending. A blockchain has been described as a value-exchange protocol. A blockchain can maintain title rights because, when properly set up to detail the exchange agreement, it provides a record that compels offer and acceptance.
Blocks
Blocks hold batches of valid transactions that are hashed and encoded into a Merkle tree. Each block includes the cryptographic hash of the prior block in the blockchain, linking the two. The linked blocks form a chain. This iterative process confirms the integrity of the previous block, all the way back to the original genesis block.
Sometimes separate blocks can be produced concurrently, creating a temporary fork. In addition to a secure hash-based history, any blockchain has a specified algorithm for scoring different versions of the history so that one with a higher value can be selected over others. Blocks not selected for inclusion in the chain are called orphan blocks. Peers supporting the database have different versions of the history from time to time. They keep only the highest-scoring version of the database known to them. Whenever a peer receives a higher-scoring version (usually the old version with a single new block added) they extend or overwrite their own database and retransmit the improvement to their peers. There is never an absolute guarantee that any particular entry will remain in the best version of the history forever. Blockchains are typically built to add the score of new blocks onto old blocks and are given incentives to extend with new blocks rather than overwrite old blocks. Therefore, the probability of an entry becoming superseded decreases exponentially as more blocks are built on top of it, eventually becoming very low. For example, bitcoin uses a proof-of-work system, where the chain with the most cumulative proof-of-work is considered the valid one by the network. There are a number of methods that can be used to demonstrate a sufficient level of computation. Within a blockchain the computation is carried out redundantly rather than in the traditional segregated and parallel manner.
Block time
The block time is the average time it takes for the network to generate one extra block in the blockchain. Some blockchains create a new block as frequently as every five seconds. By the time of block completion, the included data becomes verifiable. In cryptocurrency, this is practically when the transaction takes place, so a shorter block time means faster transactions. The block time for Ethereum is set to between 14 and 15 seconds, while for bitcoin it is 10 minutes.
Hard forks
A hard fork is a rule change such that the software validating according to the old rules will see the blocks produced according to the new rules as invalid. In case of a hard fork, all nodes meant to work in accordance with the new rules need to upgrade their software.
If one group of nodes continues to use the old software while the other nodes use the new software, a split can occur. For example, Ethereum has hard-forked to "make whole" the investors in The DAO, which had been hacked by exploiting a vulnerability in its code. In this case, the fork resulted in a split creating Ethereum and Ethereum Classic chains. In 2014 the Nxt community was asked to consider a hard fork that would have led to a rollback of the blockchain records to mitigate the effects of a theft of 50 million NXT from a major cryptocurrency exchange. The hard fork proposal was rejected, and some of the funds were recovered after negotiations and ransom payment. Alternatively, to prevent a permanent split, a majority of nodes using the new software may return to the old rules, as was the case of bitcoin split on 12 March 2013
Decentralization
By storing data across its peer-to-peer network, the blockchain eliminates a number of risks that come with data being held centrally. The decentralized blockchain may use ad-hoc message passing and distributed networking.
Peer-to-peer blockchain networks lack centralized points of vulnerability that computer crackers can exploit; likewise, it has no central point of failure. Blockchain security methods include the use of public-key cryptography. A public key (a long, random-looking string of numbers) is an address on the blockchain. Value tokens sent across the network are recorded as belonging to that address. A private key is like a password that gives its owner access to their digital assets or the means to otherwise interact with the various capabilities that blockchains now support. Data stored on the blockchain is generally considered incorruptible.
Every node in a decentralized system has a copy of the blockchain. Data quality is maintained by massive database replication and computational trust. No centralized "official" copy exists and no user is "trusted" more than any other. Transactions are broadcast to the network using software. Messages are delivered on a best-effort basis. Mining nodes validate transactions, add them to the block they are building, and then broadcast the completed block to other nodes. Blockchains use various time-stamping schemes, such as proof-of-work, to serialize changes. Alternative consensus methods include proof-of-stake. Growth of a decentralized blockchain is accompanied by the risk of centralization because the computer resources required to process larger amounts of data become more expensive.
Openness
Open blockchains are more user-friendly than some traditional ownership records, which, while open to the public, still require physical access to view. Because all early blockchains were permissionless, controversy has arisen over the blockchain definition. An issue in this ongoing debate is whether a private system with verifiers tasked and authorized (permissioned) by a central authority should be considered a blockchain. Proponents of permissioned or private chains argue that the term "blockchain" may be applied to any data structure that batches data into time-stamped blocks. These blockchains serve as a distributed version of multiversion concurrency control (MVCC) in databases. Just as MVCC prevents two transactions from concurrently modifying a single object in a database, blockchains prevent two transactions from spending the same single output in a blockchain. Opponents say that permissioned systems resemble traditional corporate databases, not supporting decentralized data verification, and that such systems are not hardened against operator tampering and revision. Nikolai Hampton of Computerworld said that "many in-house blockchain solutions will be nothing more than cumbersome databases," and "without a clear security model, proprietary blockchains should be eyed with suspicion."
Permissionless
The great advantage to an open, permissionless, or public, blockchain network is that guarding against bad actors is not required and no access control is needed. This means that applications can be added to the network without the approval or trust of others, using the blockchain as a transport layer.
Bitcoin and other cryptocurrencies currently secure their blockchain by requiring new entries to include a proof of work. To prolong the blockchain, bitcoin uses Hashcash puzzles. While Hashcash was designed in 1997 by Adam Back, the original idea was first proposed by Cynthia Dwork and Moni Naor and Eli Ponyatovski in their 1992 paper "Pricing via Processing or Combatting Junk Mail".
Financial companies have not prioritised decentralized blockchains.
In 2016, venture capital investment for blockchain-related projects was weakening in the USA but increasing in China.[37] Bitcoin and many other cryptocurrencies use open (public) blockchains. As of April 2018, bitcoin has the highest market capitalization.
Permissioned (private) blockchain
Permissioned blockchains use an access control layer to govern who has access to the network. In contrast to public blockchain networks, validators on private blockchain networks are vetted by the network owner. They do not rely on anonymous nodes to validate transactions nor do they benefit from the network effect. Permissioned blockchains can also go by the name of 'consortium' blockchains.
Disadvantages of private blockchain
Nikolai Hampton pointed out in Computerworld that "There is also no need for a '51 percent' attack on a private blockchain, as the private blockchain (most likely) already controls 100 percent of all block creation resources. If you could attack or damage the blockchain creation tools on a private corporate server, you could effectively control 100 percent of their network and alter transactions however you wished." This has a set of particularly profound adverse implications during a financial crisis or debt crisis like the financial crisis of 2007–08, where politically powerful actors may make decisions that favor some groups at the expense of others, and "the bitcoin blockchain is protected by the massive group mining effort. It's unlikely that any private blockchain will try to protect records using gigawatts of computing power — it's time consuming and expensive." He also said, "Within a private blockchain there is also no 'race'; there's no incentive to use more power or discover blocks faster than competitors. This means that many in-house blockchain solutions will be nothing more than cumbersome databases."
Blockchain analysis
The analysis of public blockchains has become increasingly important with the popularity of bitcoin, Ethereum, litecoin and other cryptocurrencies. A blockchain, if it is public, provides anyone who wants access to observe and analyse the chain data, given one has the know-how. The process of understanding and accessing the flow of crypto has been an issue for many cryptocurrencies, crypto-exchanges and banks. The reason for this is accusations of blockchain enabled cryptocurrencies enabling illicit dark market trade of drugs, weapons, money laundering etc. A common belief has been that cryptocurrency is private and untraceable, thus leading many actors to use it for illegal purposes. This is changing and now specialised tech-companies provide blockchain tracking services, making crypto exchanges, law-enforcement and banks more aware of what is happening with crypto funds and fiat crypto exchanges. The development, some argue, has lead criminals to prioritise use of new cryptos such as Monero. The question is about public accessibility of blockchain data and the personal privacy of the very same data. It is a key debate in cryptocurrency and ultimately in blockchain.
Types Of Blockchain's
Currently, there are at least four types of blockchain networks — public blockchains, private blockchains, consortium blockchains and hybrid blockchains.
Public blockchains
A public blockchain has absolutely no access restrictions. Anyone with an Internet connection can send transactions to it as well as become a validator (i.e., participate in the execution of a consensus protocol). Usually, such networks offer economic incentives for those who secure them and utilize some type of a Proof of Stake or Proof of Work algorithm.
Some of the largest, most known public blockchains are the bitcoin blockchain and the Ethereum blockchain.
Private blockchains
A private blockchain is permissioned. One cannot join it unless invited by the network administrators. Participant and validator access is restricted.
This type of blockchains can be considered a middle-ground for companies that are interested in the blockchain technology in general but are not comfortable with a level of control offered by public networks. Typically, they seek to incorporate blockchain into their accounting and record-keeping procedures without sacrificing autonomy and running the risk of exposing sensitive data to the public internet.
Hybrid blockchains
A hybrid blockchain simply explained is a combination between different characteristics both public and private blockchains have by design. It allows to determine what information stays private and what information is made public. Further decentralization in relation to primarily centralized private blockchains can be achieved in various ways. Instead of keeping transactions inside their own network of community run or private nodes, the hash (with or without payload) can be posted on completely decentralized blockchains such as bitcoin. Dragonchain uses Interchain to host transactions on other blockchains. This allows users to operate on different blockchains, where they can selectively share data or business logic. Other blockchains like Wanchain use interoperability mechanisms such as bridges. By submitting the hash of a transaction (with or without the sensitive business logic) on public blockchains like bitcoin or Ethereum, some of the privacy and blockchain concerns are resolved, as no personal identifiable information is stored on a public blockchain. Depending on the hybrid blockchain its architecture, multi cloud solutions allow to store data in compliance with General Data Protection Regulation and other geographical limitations while also leveraging bitcoin's global hashpower to decentralize transactions.
Getting Started On The Darkweb
Technically, this is not a difficult process. You simply need to install and use Tor. Go to www.torproject.org and download the Tor Browser Bundle, which contains all the required tools. Run the downloaded file, choose an extraction location, then open the folder and click Start Tor Browser. That's it.
The Vidalia Control Panel will automatically handle the randomised network setup and, when Tor is ready, the browser will open; just close it again to disconnect from the network.
Depending on what you intend to do on the Dark Web, some users recommend placing tape over your laptop's webcam to prevent prying eyes watching you. A tinfoil hat is also an option. If you're reading this to find out about torrent files.
The difficult thing is knowing where to look on the Dark Web. There, reader, we leave you to your own devices and wish you good luck and safe surfing. And a warning before you go any further. Once you get into the Dark Web, you *will* be able to access those sites to which the tabloids refer. This means that you could be a click away from sites selling drugs and guns, and - frankly - even worse things.
Aggregation sites such as Reddit offer lists of links, as do several Wikis, including http://thehiddenwiki.org/ - a list that offers access to some very bad places. Have a quick look by all means, but please don't take our linking to it as an endorsement to go out and get your self in trouble and please note I am not responsible for what you do
Also, Dark Web sites do go down from time to time, due to their dark nature. But if you want good customer service, stay out of the dark!
How to download Tor browser?
NOTE:Altho TOR is secure it is still advisable to download a 3rd party Virtual Private Network (VPN) as it will give you a much greater chance of not being intercepted and anything you can do to repel the people looking for what you are doing the better! ok, now lets get started
The Tor Project Inc. has released Tor Browser which is a modification of an Extended Support Release version of Mozilla Firefox browser. The browser is portable so that it can be used from an external media and also reduces the hazel of installation. Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
The Tor browser is available various desktop operating systems including Windows, Linux, and MacOS. You can visit this link to download Tor browser.
How to install Tor browser on Windows?
Run the Tor Browser setup.Choose your desired language.On the next windows, choose the destination folder. Using Tor would be easy if you choose the Desktop as the destination.Click Install.
The setup will create a folder named Tor Browser on your Desktop. Open the folder, and run the shortcut file to use Tor Browser.
For Linux, you’ll have to extract the downloaded file either using the command line or a file extractor application.
Tor Browser for Android
Orbot – a proxy with Tor for Android devices.
Orfox – a mobile version of Tor Browser for Android devices.
The Guardian Project, a global developer community founded by Nathan Freitas, is to be credited for the development of these apps.
Tor Browser for iOS
An official Tor browser app for iOS is available on the App Store.
Tor Alternatives
Hornet is a new anonymity network that provides higher network speeds compared to Tor. I2P and Freenet are other anonymity networks which can act as Tor alternatives. Also, Tails and Subgraph OS are Linux-based distributions with built-in Tor support.
Should I Use Tor?
Tor has proved to be an excellent medium for safe, secure and anonymous web presence available to a user at no cost. The developers of Tor didn’t intend it to become a hotbed of illegal activities, but evil-minded people have leveraged Tor for their benefits. The Tor project has led to an optimistic approach towards censorship and surveillance-free internet.
You can use Tor if you want to conceal your identity on the web or access some website that blocked in your region. But refrain yourself from doing anything that’s above the law because nothing is fool-proof and they can still catch you. Also, accessing your social media accounts over Tor can expose your identity. This being said me personally I use TOR only for my dark web research and visits. I do not access no websites with a commercially available router extension (IE: Com, Net, Org, Or anything else) the only extension that is run through tor is .onion extensions. The reason being is that any other extensions have the possibility to provide backdoor access to any an all of your information that is run while it is active.
NOTE: TOR's cookies are not dumbed until after you close the browser so it is still possible to track you if your browser is left open after you visited any other sites.
Steps For Safety(CH3)
Step 1: Plan ahead.
There are plenty of reasons companies and individuals may want to access the Dark Web. SMBs and enterprise companies in particular may want to monitor Dark Web portals for stolen corporate account information. Individuals may want to monitor sites for evidence of identity theft. Facebook's encrypted site, located at facebookcorewwwi.onion, is a feature-rich method of accessing the social network using end-to-end encryption.
Set a goal, make plans, and stay focused. Be mindful of purpose. Make sure you know what information you're looking for and why you're logging on to the encrypted web. For example, if you're a reporter and need to communicate with sources, focus on PGP, email, and encrypted communication. If you're searching for credit card information, look for Silk Road-type markets that sell hacked data.Get what you need, safely disconnect TOR and Tails, then log off.
Step 2: Obtain a new USB flash drive.
Purchase a new 8 GB or larger USB flash drive. Make sure you use a fresh, unused drive. You will install Tails, and Tails only, directly on your storage device.
Step 3: Prepare your local machine.
Ideally, use a fresh laptop. This isn't an option for most users, so instead do everything in your power to secure and isolate mission-critical information.
Back up critical data and local files.Make sure your hardware is optimized and malware-free.
Step 4: Download Tails and TOR.
TOR and Tails are available on the TOR Project website. Access download links directly from https://www.torproject.org. Insert your USB drive and follow the instructions on https://tails.boum.org.
Step 5: Browse safely.
Common portals and search engines:
DuckDuckGoThe Hidden WikiOnion.linkAhmia.fiGramsTorch
Encryption is strong, but not impenetrable. The FBI discovered and exploited vulnerabilities in the TOR network. Though the agency refused to disclose the source code used to penetrate the network, undoubtedly law enforcement agencies around the world monitor and operate on the Deep Web. Members of the TOR project vowed to patch network holes and strengthen the protocol.
Many of the best general deep web search engines have shut down or been acquired, like Alltheweb and CompletePlanet. Still, a few are hanging around to get you started:
DeeperWeb – Deep web search engine that leverages Google SearchThe WWW Virtual Library – The original index of the web, but more of a directory than a search engine.Surfwax – Indexes RSS feeds. Not certain this is still working…IceRocket – Searches the blogosphere and Twitter
These are all okay, but specialized search engines tend to be better than general ones for finding info on the deep web. If you’re looking for a court case, for example, use your state or country’s public records search. If you need academic journals, check out our article on using deep web search engines for academic and scholarly research. The more specific you can be, the better, or else you’ll just end up with the same search results that you would find on Google. If you need a specific file type, like an Excel file or a PDF, learn how to specify searches for that type of file (e.g. type “filetype:PDF” in your DeeperWeb query).
How to access the dark web on Android with Tor Browser
The official Tor Browser is now available on Android. You can get it from the Play Store or the Tor downloads page. As of writing, Tor Browser for Android is still in alpha, and additionally requires you install Orbot as a prerequisite.
The Tor Browser is the most popular dark web browser. Once Tor Browser is installed, you can now access those .onion dark net websites.
Using A VPN over TOR Or Vice Versa
A VPN allows a user to encrypt all the internet traffic traveling to and from his or her device and route it through a server in a location of that user’s choosing. A VPN in combination with Tor further adds to the security and anonymity of the user.
While somewhat similar, Tor emphasizes anonymity, and a VPN emphasizes privacy.
Combining them reduces risk, but there’s an important distinction in how these two tools interact. Let’s first discuss Tor over VPN.
If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN, this is by far the most common method. All your device’s internet traffic first goes to the VPN server, then it bounces through the Tor Network before ending up at its final destination. Your ISP only see’s the encrypted VPN traffic, and won’t know you’re on Tor. You can access .onion websites normally.
5 notes
·
View notes
Text
Social Media: Calling out the Trolls
New technology has developed rapidly since the birth of the internet, and it continues to expand and evolve affecting many domains, especially the print media. The mainstream media teaches us that the intention of trolls is to silence, humiliate, and intimidate victims of tragedy or crime and/or people from marginalized communities. Social networking sites, such as Twitter and Facebook, have become an impressive force in the modern world with user bases larger than many individual countries. With such influence, they have become important in the process of worldwide politics. Alarming new research has revealed the full extent of online bullying and the damage it causes amongst young people. A third of young people have been victims of online abuse, with vicious attacks made not only on their appearance, but also on the grounds of their religion or race. In the mid-90s, ARPANet was transformed from a military safety net to the civilian Internet that has become such an integral part of our lives, bringing with it change not only technological, but societal and epic in scope.
Forty years ago, the average person followed an employment path largely determined by birth and education, often committing to one employer until retirement. Today you probably wouldn’t even consider that as a viable option. Success is no longer solely determined by the right education, the perfect resume, or even your age and background. Teens as young as 12 are now coding websites, producing films and building networks through social media. By the time they’re adults, this online generation will already have some skills and real-world experience that a formal education just can’t provide.
The Internet is bringing a revolution along with it. Access to information combined with
global supply and demand is reshaping established conventions and destroying old world definitions. To understand where I am going with this, take the word 'local.' It once referred to your own street, town or even the state you lived in, but now everywhere is local. Americans are outsourcing their services to companies from China to Brazil, all from the comfort of their own homes. Where once our reach was limited by physical boundaries, today almost everyone and everything is just a digital handshake away.
Long established workplace conventions - from defined office hours to physical office space - are being tossed out the window. Success was once defined by a suit and the ‘9 to 5’; now it can achieved by working in pajamas and starting at noon after a morning at the gym and leisurely latte. The very definition of ‘success’ is now drastically changing. It once meant a “keeping up with the Joneses” lifestyle your neighbors would be envious of; now it’s about making personal, intimate choices about how to live your life. Of course some still associate it purely with wealth, but for many, success is being measured in other ways –happiness, freedom, health, more time for travel and family. Interconnected societies are the global engine that transforms people from employees to micro entrepreneurs. Anyone now has the opportunity to monetize their skills, from the full-time worker looking for additional income to the once hobbyist building their very own business. True change affects both young and old, and while 15-year old hedge fund managers may capture the imagination, we've got 80-year old entrepreneurs grabbing headlines too. It's truly an uncontested market where talent, skills and experience become commodities outside the narrow boundaries of traditional employment (if such a thing as “traditional” even exists anymore).
As we engage in a century where everyone is not only a global citizen, but a valuable “Brand in Waiting,” we begin to understand that the Internet Revolution IS in fact the Industrial Revolution of our time. It’s a sweeping social disruption that brings with it not only new inventions and scientific advances, but perhaps most importantly revolutionizes both the methods of work and we the workers ourselves. It’s the return of personal choice and personal definitions of value, as we increasingly define ourselves by the work we produce rather than being defined only by the work available.
This study claims that fake news or trolls also covers the topic censorship. Censorship is really important when it comes to online media because without media censorship everything will break loose, like for example all fake news will be tolerated and other frauds will be able to share false information to all social media sites web sites and fake articles. Censorship filters all kinds of post when it comes to photos and words that are not tolerated to the online community. Censorship could be a good help limit the freedom of speech in the online world. If there will be a law regarding this situation, bullying or even fake news could be lessen.
1 note
·
View note
Text
An Internet Primer
===An Internet Primer=== Non-profit and free for redistribution Written on August 24th | 2016 Published on August 24th | 2016 For entertainment and research purposes only
++++++++++++++++++++++++++++++++++++++ ===DISCLAIMER=== The Paranoid's Bible and its writers hold no responsibility for the acts of others. The Paranoid’s Bible is for research and entertainment purposes only. Please visit our blog for more PDFs and information: http://www.paranoidsbible.tumblr.com/ ++++++++++++++++++++++++++++++++++++++ ===Preface=== While many still argue about how their own views on the history of the internet are the truth, we do know the core timeline consists of the “Electronic computer” being developed in the 1950s. From there the ARPANET was created and quickly adopted the Internet Protocol, which soon began a wildly discussed and argued about origin story of the internet sometime in the 80s. However, while many will even argue the core facts to the point of the internet being born either earlier or later in the timeline, we do know that Usenet wasn’t too far away. With the birth of Usenet, things like the BBS, Internet forum and terms like “Eternal September” quickly cropped up in a rapid session of growth and expanse. Now things like Blogging or Social Media are common, and people with rose tinted glasses grow remorseful of how inclusive the internet has become. Now, the early adopters and users aren’t too far off with their remorse, sadly… You see, many of the modern day users have grown complacent and wholly unaware of even the simplest uses of OPSEC. This guide aims at giving the average user a simple and quick primer to enhance their privacy and security when using the internet. This guide isn’t a quick-fix or one-button solution to your problems or concerns, however it’s better than nothing when paired with the other guides listed in the “Blue Primer”. __References__ • Net History (http://www.nethistory.info/History of the Internet/origins.html) • Internet Society (http://www.internetsociety.org/internet/what-internet/history-internet/brief-history-internet) • History of the Internet (https://en.wikipedia.org/wiki/History_of_the_Internet) • ARPANET (https://en.wikipedia.org/wiki/ARPANET) • Internet protocol (https://en.wikipedia.org/wiki/Internet_Protocol) • Usenet (https://en.wikipedia.org/wiki/Usenet) • BBS (https://en.wikipedia.org/wiki/Bulletin_board_system) • Internet Forum (https://en.wikipedia.org/wiki/Internet_forum) • Eternal September (https://en.wikipedia.org/wiki/Eternal_September) • OPSEC (https://en.wikipedia.org/wiki/Operations_security) • Blog (https://en.wikipedia.org/wiki/Blog) • Social Media (https://en.wikipedia.org/wiki/Social_media) ++++++++++++++++++++++++++++++++++++++ ===The Browser=== The gateway to the internet, for the modern and average user, is their browser (https://en.wikipedia.org/wiki/Web_browser). It’s a piece of software meant to help people transverse the World Wide Web by retrieving and presenting information resources taken from the internet. The modern browser is pre-built, requires hardly any tweaking, and is rarely, if ever, fully customizable. However, as more people aim for a free software or an open-source style of use, more browsers do offer some level of customization that range from modifying the settings under the hood to themes and other frivolous aesthetical customizations. With so many choices, people usually stick to Internet Explorer or Google chrome; however these browsers leave a lot of wanting when it comes to usability. Chrome also has a notorious past of spying on you (http://betanews.com/2015/06/24/is-google-chrome-spying-on-you/) without giving you a warning, which shouldn’t be such a surprise with all the claims of Chrome being a botnet (https://wiki.installgentoo.com/index.php/Botnet) and not asking permission (http://www.netcompetition.org/antitrust/google-on-chrome-we-dont-need-your-permission) for accessing a user’s computer. Ultimately, anything with Microsoft or Google is unavoidable, sadly, and a lot of work has to take place in order to avoid leaking information or having it sold. But that’s the way things flow as of late, especially when “Don’t Be Evil” is dropped in favor of “Do the Right Thing” (http://blogs.wsj.com/digits/2015/10/02/as-google-becomes-alphabet-dont-be-evil-vanishes/). So, what does that mean for the average user? Research your quickly dwindling choices for what browser you should use, which will reside between two browsers and one’s many, many flavors. If you want something other than Mozilla Firefox, then try Brave (https://brave.com/) (Not recommended due to its newness) or Palemoon (https://www.palemoon.org/) (Based upon a fork of Firefox) or IceCat (https://www.gnu.org/software/gnuzilla/). However, for the sake of usability and quick to use features, we recommended, begrudgingly, Mozilla Firefox (https://www.mozilla.org/en-US/firefox/new/). When you visit Firefox’s webpage, select the appropriate version for your operating system. Once downloaded, double click and follow the on screen prompts. When it comes to selecting “Standard” or Custom” ensure you select custom. ***Leave the default installation path, unless you wish to install elsewhere. *** ***The reason for removing the installation service is quite simple: *** Less communication between the browser and other sources, the less information leaked. Now ensure you've also unchecked/disabled the "Maintenance service" before proceeding. Selecting shortcuts/icons is ultimately up to you. The same applies to it being the default browser—it’s up to you. Once installed, it’s time for some basic customization and add-on installation. The first thing you’ll notice is an “import wizard” pop-up. You don’t want to import anything unless you’ve some backups of your bookmarks. Other than that, ignore it and wait for the browser to load. From there, we’ll ignore the “Firefox account” prompt. You don’t want to sync or backup, anything, unless it’s an html or json file for your bookmark backups. Syncing accounts and saving passwords spells doom, gloom and big brother (sometimes literally your big brother or sister) spying on your info and peaking into your accounts and other online items (if not leaking it in a data dump). Seriously, ignore prompts to sync or save information. You’ll also want to ignore the private browsing mode. It’s not private, information is still saved, and people can still use exploits to get at your information. Press the ALT button on your keyboard to get the menu bar to appear. From there, select the tools menu and then the “Options” submenu. Press ALT button > Tools menu > Options sub-menu. When the options window pops up, you’ll want to start in the “General tab” Disable/uncheck “Always check if Firefox is your default browser” and set your homepage to whatever you want. Never let files save to downloads, you want to have it “Always ask” where to save them. On top of that disable all the "Tabs" options but "Open news windows in a new tab instead". We do suggest using “Start Page” (https://www.startpage.com/) for your homepage and search engine needs. Now click the "Search" tab and uncheck everything and delete all the "One-click Search Engines" options. From there, Go to the start page website, you should see an “Add to Firefox” option, select that. You should also, to prevent accidental use, remove all other search engines from the “Search” tab. Google, among several other engines, tend to cache and keep track of your search history and click stream (https://en.wikipedia.org/wiki/Clickstream). On top of that, Google, Yahoo, Microsoft, and a few others, will store and keep your search history saved to your accounts if logged into them, at all, while searching. On the “Content tab,” uncheck/disable everything but "Block pop-up windows". Now select the “Advanced” button and click it. From there, disable the option titled "Allow pages to choose their own fonts, instead of my selection above". This just prevents sites from using intrusive and generally distasteful fonts and also limits their control over your browsing experience and browser. Everything in the “Applications tab” should be set to always ask or preview in Firefox. The only thing you can safely set to a default application would be shockwave flash, which should be disabled by default in the plug-ins menu. The “Privacy tab” should be straightforward; however most will recommend that you disable “Third-party cookies" but since this primer is aimed at providing some security, privacy, yet retain usability for the average user… You should disable everything but: "Use Tracking Protection in Private Windows"; "Accept cookies from sites"; Clear history when Firefox closes. Set 3rd party cookie to never, if you wish, however some banking sites lose functionality due to this. You should also set "Keep until" to "I close Firefox". Now click the "settings..." tab on on the Privacy menu and select everything there. In the “Security tab,” it’s again straightforward; however please do understand that the whole “Blocking dangerous and deceptive content” options are disabled due to the fact that, again, the less communication given over to the browser and its creators the better you’re off security and privacy wise. Basically uncheck everything but "Warn me when sites try to install add-ons". ***Ignore the sync tab. *** Everything in the “Advanced tab” is straight forward and should be self explanatory. Advanced > General > Disable/uncheck everything but the four settings under "Browsing. Advanced > Data Choices > Uncheck all Advanced > Network > Check all and set cache to 0 Advanced > Update > Uncheck all and set to "Never check for updates" Advanced > Certificates > Set to "Ask me every time" and check the one setting there. Once done, exit out of Firefox and start it up again. This is just to ensure everything sticks and is working due to some of the more current versions of Firefox have had a habit to ignore settings from time to time and resetting things to default. Now we’ll go to the Firefox Add-on page and work our way toward customizing Firefox a bit to improve usability and its overall feel. First off, we’ll work on the aesthetics aspect a bit just to improve the overall feel of the browser due to its copy-catting of the Apple simplicity meme. ***You’ll want these add-ons:*** • Black YouTube Theme - https://addons.mozilla.org/en-US/firefox/addon/black-youtube-theme • Classic Theme Restorer - https://addons.mozilla.org/en-US/firefox/addon/classicthemerestorer/ • Smaller View - https://addons.mozilla.org/en-US/firefox/addon/smaller-view/?src=search You should notice a considerable difference in your browser once restarted. More precisely, it’ll be easier to navigate and find your menus now. The YouTube theme is simply preference and feels easier on the eyes compared to the default theme of the site. Now, before we continue forward with the add-ons. Let’s do a bit of tweaking to the look of the browser. You should see icons on the upper right-hand corner. Right-click on the icons and select “Customize,” which should open up a new tab/window that’ll allow you to move the icons as you wish. Remove all the icons present, except the down arrow/download icon. From there, close the window and right-click on the bar, again, and select the three bars/toolbars shown. You can also ignore the “Menu Bar” option if you wish to just use the orange drop-down menu. In the URL bar, type in About:config. You should see something similar like the below cap. Uncheck the “Show this warning next time”. And then, from there, click the “I’ll be careful, I promise!” button. In the search bar within the about:config window, ***enter this:*** browser.newtabpage.directory.source You should see a string with the name you searched, double-click it and delete the string of text. Once done, exit out of that tab and open a new tab. Click the cog wheel icon in the right-hand corner and select “Show blank page”. You should now be rid of those pesky tiles and most of the ADs that Firefox forces down your throat. You can now add the rest of the add-ons, which you can find listed below. Add-ons: • Better Privacy - https://addons.mozilla.org/en-US/firefox/addon/betterprivacy/ • BluHell Firewall - https://addons.mozilla.org/en-US/firefox/addon/bluhell-firewall/ • Configuration Mania - https://addons.mozilla.org/en-US/firefox/addon/configuration-mania-4420/ • Decentraleyes - https://addons.mozilla.org/en-US/firefox/addon/decentraleyes/ • Disconnect - https://addons.mozilla.org/en-US/firefox/addon/disconnect/ • HTTPS Everywhere - https://www.eff.org/Https-everywhere • PureURL - https://addons.mozilla.org/en-US/firefox/addon/pure-url/ • Quick Java - https://addons.mozilla.org/en-US/firefox/addon/quickjava/ • Self-Destructing Cookies - https://addons.mozilla.org/en-US/firefox/addon/self-destructing-cookies/ • Smart Refer - https://addons.mozilla.org/en-US/firefox/addon/smart-referer/ • Track Me Not - https://addons.mozilla.org/en-US/firefox/addon/trackmenot/ Now restart the browser. You should get a pop-up from HTTPS Everywhere, hit “No” and then right-click anywhere and select “Customize”. You’ll want everything arrange to your own taste, note that there exists an icon with two cog wheels. This belongs to “Configuration mania” and should be added for ease of use and access. Now, click the orange menu button and click the add-on menu. We’ll be working our way down the list, alphabetically, and modifying a handful of settings for some of the add-ons before we end this chapter. Starting with “Better Privacy,” go ahead and hit “Options”. You’ll want to select the “Options & Help” tab and adjust your settings to look similar to the ones listed below: • Delete flash cookies on exit - checked • Add LSO item to Firefox ‘Clear History’ dialog – unchecked • Always ask - unchecked • Delete flash cookies on application start - checked • Delete cookies by timer – checked • Not if modified within time interval – checked • Time interval 1 second • LSO delete shortcut – blanked • Also delete flashplayer default cookie – checked • On cookie deletion also delete empty cookie folders – checked • Notify if new LSO is stored – unchecked • Auto protect LSO sub-folders – checked • Disable ping tracking • Prevent Firefox ‘Clear recent history function’ – checked • Portable mode – unchecked Everything else can be ignored and you can go directly to “Configuration Mania” and select “Options”. Browser tab > Tab Browsing > Everything checked but the below: • Enable about:newtab – unchecked • Close the window when closing its last tab – unchecked • Open the results in a new tab when searching from search bar –unchecked • On CTRL + TAB – unchecked • On taskbar (windows 7) – unchecked Now head over to the “Bookmark icons (favicons)” tab. Browser tab > Bookmark icons > Uncheck the two settings there. Finally go to the “Web API” tab in browser tab and deselect/uncheck everything there. From there, find the “Security” tab that should be right under the “Browser” tab and select the “Javascript” tab, everything there should be checked and all the other tabs left alone. Now, before we select “Smart Refer” please go to about:Config by entering “About:config” into the URL bar. From there, search for: network.http.sendRefererHeader You’ll want to either set it to 0 to not send a ref or to 1 to keep things somewhat clean and compatible. 2, however, is default and will always send a ref. So, ‘0’ if you don’t want to send a ref or ‘1’ to prevent most cross-site tracking and keep compatibility when visiting websites. Now go to “Smart Refer” and select “Options”. ***Set the drop down to: *** Send nothing as a referrer, looking like a direct hit. Once done, go and mosey on over to “Track Me Not” and hit “Options”. Set your settings as such: • Enabled – checked • Use tab search – unchecked • Enable query burst – checked • All search engines checked • Query frequency: 10 per min • Disabled – checked • Persistent – unchecked • Use list – checked • Generate queries – unchecked Once you’re in TMN’s options, you’ll want to use recommend RSS feeds for the add-on (hit validate once done): http://www.nytimes.com/services/xml/rss/nyt/HomePage.xml|http://rss.cnn.com/rss/cnn_topstories.rss|http://rss.msnbc.msn.com/id/3032091/device/rss/rss.xml|http://www.theregister.co.uk/headlines.rss|www.reddit.com/r/science/.rs|http://www.reddit.com/r/aww/.rss|http://www.reddit.com/r/kawaii.rss|http://www.reddit.com/r/kittens.rss|http://www.reddit.com/r/pcmasterrace.rss|http://www.reddit.com/r/steam.rss We also recommend these words for your black list: bomb,porn,pornographie, porn, pornography, rape, rapists, rape culture, bombs, pipebomb, ied, bdms, bdsm, raping, raped, murder, murdering, lolicon, loli, cp, child porn, pthc, jbhc, shota, shotacon, ISIS, ISIL Once done with the add-ons, head on over to about:Config once more. You’ll want to implement these three settings to ensure you limited some of the tracking methods employed by websites and online trackers commonly found on Tumblr and other social media platforms. ===Settings to change:=== • browser.display.use_document_fonts = 0 • dom.storage.enabled = false • browser.sessionhistory.max_entries = 2 Once done, you can add whatever add-ons you want, ***however remember this simple rule: *** If you don’t need or use it, don’t install it or enable it. That’s why we had you install Quick-Java. Quick Java’s little bar, which is added to Firefox upon installation, allows you to disable and enable certain plug-ins on the fly. This is a wondrous little time saver and is a good thing to have at hand when you wish to browse the internet. When browsing, without having to login or watch something, your settings with quick-java should look something like this: Everything red/disabled but I (Images); A (Animations); CS (Style) When you do need to log into an account or want to watch YouTube or something similar, you’ll need it to look like this: Everything red/disabled but JS (Javascript); C (Cookies); I (Images); CS (Style) Give or take the fact that you may need to enable flash (The “F” button). However, YouTube, and some other sites, are offering the use of HTML5 and Flash. So, if you don’t need to enable flash, don’t do so. Flash can leak a lot of data in the end. It also helps to outright not have anything enabled (sans the last three buttons) when you’re just doing research or looking up something. Only enable cookies and JavaScript (the “JS” and “C” buttons) when you actively need to log into an account or a website. This will help lessen the data diarrhea your browser has and help you retain some privacy without breaking your browser, yet many more configurations and add-ons are needed to even achieve some form of security or privacy. ***And, just as an FYI: *** This shouldn’t break your browser, at all, or your use of any websites. If something doesn’t work properly, try disabling BluHell Firewall by clicking the blue-devil icon on your browser. If that doesn’t work, try disabling Clean links, which has an icon of a broom wrapped in a chain-link. Outside of those two add-ons, you don’t need to disable anything as nothing should break or prevent you from logging into any websites. Ultimately though, this configuration, and the add-ons suggested, only helps lessen the effectiveness of the trackers and counters offered to civilians and the public at large. Some Ads will be blocked, along with a metaphorical ton of malicious content, however you’ll need to look into using Peerblock and Hostman if you want to lessen it even more so than what you can with this browser setup. We offer two guides that discuss the use of Peerblock and Hostman, among other things. However, save those for a later date as they’re a bit more advanced than what this guide has to offer. We’ll also be hosting what we call the “Blue Primer,” which is an archive of the most basic of information for those who wish to lessen their data footprint, prevent tracking and lessen their chances of being doxed. If you haven’t gotten this guide from the blue primer, please look into downloading it and reading the other guides within it. As for this chapter of this guide… you’re done! Move on to the next chapter, reader. ***P.S:*** Avoid using password storage, password sorters and similar features or add-ons. Write down your password, if you must, and hide it where no-one will find it but you. ++++++++++++++++++++++++++++++++++++++ ===E-mail=== Electronic mail (https://en.wikipedia.org/wiki/Email), shortened to E-mail, is one of many means to exchange digital messages between computers and their users. However, since seeing frequent use in the 60s to now, e-mail has become used more as a means of identification than communication when needing to sign up for an account or do some sort of business based task, or being a responsible adult and working on your taxes or banking. Now, e-mail is just one of the many methods sites use to prevent bots, scammers and spammers from joining their communities. When you need to sign up for an account, you usually need to provide an e-mail from a provider that they’ve yet to blacklist (***Example:*** most common temporary e-mail services have been blocked by FaceBook). The average internet user will usually use of the main three: Google; Hotmail/Live/Outlook; Yahoo. • https://www.gmail.com/ • https://login.live.com/ • https://login.yahoo.com/ Sometimes Yandex (https://mail.yandex.com/), among similar non-US based e-mail providers will be used, however the main three tend to rule. The issue with the main three (Shortened from now on to MT) is that they require a lot of data and “verifications” to ensure that it’s you who’re signing up or at least not someone with malicious intent. This wouldn’t be such a large issue if it wasn’t for the fact that the MT are notorious data collectors who work in unison with the government, among other groups, to not only data-mine and spy, but also possibly put down dissenters. If any of this comes to light as being true and not just some gossiping theories put forth by many privacy groups, then that just shows how much of your information is at stake. However, with the MT track records, it shouldn’t be that big of a stretch to see how or why they’d work with the government. But what does this mean for you, someone who needs an e-mail address and doesn’t want to risk their information or someone knowing they’re a part of “Sexy Jewish Singles” with the kink of “Eating pork on the Sabbath”? Well, the first step you should take, outside of doing the bare minimum to secure your browser, would be to look into using alternative e-mail providers when signing up for an account. There are numerous providers, however not all will exist or become permanent fixtures in the years to come, which means you have to pay attention to news and keep an eye on the services to use. As of now, Privacy Tools has a wonderful list of e-mail providers (https://www.privacytools.io/#email) you can use, and since most of us are frugal-minded to the point of being cheap, these four should hopefully sedate your lust for a free, secure e-mail provider. E-mail providers: • Mail Fence - https://www.mailfence.com/ • Open Mail Box - https://www.openmailbox.org/ • Proton Mail - https://protonmail.com/ • Tutanota - https://tutanota.com/ The four e-mail providers are free, yes, and support a variety of features aimed at protecting your privacy, however they aren’t like your usual e-mail provider. They often don’t ask for a secondary e-mail or a security question, nor do they offer any means to do so in case of someone taking over. Another issue, for many, is the fact that you can’t sync or linking accounts together—this is a good thing, though. Syncing, storing or linking accounts is something you shouldn’t do, at all. Your accounts should always be separated, never touching and kept as far apart from each other as possible. Now, personally, we recommend you use a mix of these e-mails each time you create an account or sign up for some service or another that isn’t tied to you offline(***Example:*** like banking, bills, school or work). You see, as much as we dislike the MT, you should honestly have one account on each specifically for stuff that’s offline. The reason for this is simple: You’ll generate enough of a trail to not be suspicious. For instance, Google, as much as it’s a heavily invasive mega-corp, does have a pretty decent setup for their GMAIL service. You should create an account there and have it used specifically for your banking, bills and similar items. Hotmail/Outlook/Live mail is way below GMAIL, however you should use this specifically for school and similar items to keep people away from your financial records, yet close enough to a normal provider that no one will question you if you simply state that they can send it to you over e-mail instead on some social media site. Yahoo, as much as it’s a disastrous service and corporation, won’t look out of place for business related subjects or questions. It’s simply a matter of coming up with a professional sounding username for the MT accounts and keeping them separated from each other. Never using the same MT account for different applications or accounts, and never letting them touch each other. With that out of the way, however, you should try to keep each account, regardless of the provider, isolated from each other—never using the same user, password, secondary e-mail, or information, ever. The only time you should ever use your legitimate information is for the MT accounts, which should only be used for work, school or financial items. ***Remember:*** Never save your passwords on your computer and never use a password manager. Write down your password and the piece of paper with it somewhere safe and away from people trying to find it. Use a lockbox if you must, but never save this info on your computer. Also look into writing down each account’s information down and hiding that paper, too, so you never forgot it. ***Remember 2:*** Use one of the free e-mail services to create a mess free secondary e-mail to use with the MT e-mails. ++++++++++++++++++++++++++++++++++++++ ===Passwords=== Your password (https://en.wikipedia.org/wiki/Password) is the key to your account, without it you can’t login without going through an entire process of laziness meant to make it easier on the geeks who run the website you’re a part of or at least the “Help desk”. You see, that’s all a lost password request is: Laziness. It doesn’t mean you’re lazy, though, it just means you’re forgetful like everyone else. However, the people who run the site don’t want to deal with properly verifying your claim to your account, so they created these claims of simplicity where you submit a request to retrieve or change your password. That is where laziness comes in. Anyone who spent time researching you and applied a liberal dose of social engineering will be able to guess certain security questions and your e-mail addresses to the point of being able hijack your account(s). This is why it pays to keep e-mails separated, not to use the same username twice, and to have a strong password. Your password should be eight (8) to 15 (15) characters long and consist of randomly select characters that range from upper case letters (ABC) to lowercase letters (abc) to numbers (123), punctuation (.,;?!) and special characters ($%#). Your password will not only be hard to remember, but also hard to guess. This is why you should write it down on a piece of information and hide it in a lockbox or locked drawer where no one will get at it, ever. You should also avoid password managers, syncing your information, using “Master passwords,” reusing your password, or saving it on your computer or phone. Think of your password as a unique key and each account a unique door—you need a specific key for a specific door, ergo never use the same password twice. Always randomize your passwords, their length and the characters used to the point of each one never being overly similar. ++++++++++++++++++++++++++++++++++++++ ===Accounts=== An account is like a membership you apply for when you join a community or a website. And like a membership, the difficulty to obtain an account ranges from something as easy as a username + password or to the near-impossible where you need to provide an arm length’s of information and an invite code. Regardless of what you’re signing up for, however, you need to learn to compartmentalize each account and profile into its own isolated object. You don’t need to interlink your information, account or anything like that. You don’t even need to sync it up to your e-mails or our phone. You don’t need 40+ accounts across the internet. You need what you need, and at that, you only need it if there’s a reason for it. So, in theory, what accounts do you truly need? ===Steam or Origin?=== You don’t need them, however gaming is a decent way to unwind and do something mindlessly to try and clear your head of troublesome thoughts. Honestly, though, do you really need any of those accounts? Well, yes, if you don’t believe in piracy or simply wish to support the developers you prefer. But you don’t need it to live or survive. There are plenty of non-DRM options that range from freeware to physical media options that don’t need an internet connection in order to play it. ===YouTube?=== You don’t need to one to watch videos or enjoy them. You only need an account if you, yourself, plan to comment, rate or upload videos. Do you really need to do that? There hundreds of ways to express yourself that don’t require you sitting in a chair, staring at your computer, and reviewing bottles of Fuji water from when it first was released. You’ll need accounts or simply want to make an account, for whatever reason, and participate in the community or reap the benefits of releasing your information for that slim chance of being “Internet famous”. No matter the reason, though, you need to treat your account and its associated profile as a contained fire during a camping trip. You want to give only as much information as is required, not what they offer you to give up. For instance: Your username shouldn’t be your real name or a nick name that you’ve been called before. It should be completely unique and unrelated to anything else you’ve made, claimed, were called or even thought about using. It should also be different from the e-mail address that you’re using for the account. Ultimately, outside of paid accounts or billing information, not a single thing on your profile should lead back to you or be associated with you or anything related to you. You shouldn’t use the same password, e-mail address, username or anything that you’ve used on another account. And, at that, no account should be linked, synced or associated with each other in any way possible. These accounts and profiles, depending on their settings, should be made as private as possible and be as minimalistic as possible. You could, in theory, supply false information in your bio or “about me” to create a false digital trail just in case, however leaving no information is better than leaving some. And, truthfully, you should avoid having more than ten (10) accounts at any given time. When an account is no longer useful, you should just follow the Paranoid’s Bible PDF and how to properly dispose of an account and the information associated with it. Never leaving a trace behind and letting the account and its information pass peacefully away before deletion. ++++++++++++++++++++++++++++++++++++++ ===Afterword==== This is nothing more than the barest basics needed to keep some sort of privacy when using the internet and trying to avoid being doxed during some kind of discourse. This won’t make you 100% anonymous, nor will it make you undetectable when it comes to the government, yet it’s better than nothing.
5 notes
·
View notes
Text
2019 internet statistics | crew art production
2019 internet statistics
Internet history
The idea of internet had started in the dawn of the development of electronic computers in the 1950s, the wide area networking was first originated in many computer science laboratories in tree countries which are the United States, the United Kingdom, and France, The U.S. Department of Defense started the development of the Advanced Research Projects Agency Network (ARPANET) project as early as the 1960s, the project that was directed by Robert Taylor and managed by Lawrence Roberts, the internet had practically started in 1969 when the computer science Professor Leonard Kleinrock's had sent the first message over ARPANET from first network node in a laboratory at University of California, Los Angeles (UCLA) to the second network node at Stanford Research Institute (SRI), at 1970 internet started to take a new shape by studding the packet switching technology, Donald Davis was the first scientist to demonstrate the packet switching at late of 1969, that lead to a great leap forward in the development of the protocols for internetworking, in which multiple separate networks could be joined into a network of networks, then the two scientists Robert E. Kahn and Vint Cerf that they developed the (TCP/IP) in the late of 1970 and from since it became the standard networking protocol on the ARPANET, in the early 1980 had seen the foundation of the national supercomputing centers at several universities, that started the NSFNET project in 1980 under the direction of Louis Pouzin that provided interconnectivity in 1986 and also created network access to the supercomputer sites, the Commercial Internet service providers (ISPs) began to emerge in 1980, The ARPANET project was decommissioned in 1990, and the NSFNET project was also decommissioned in 1995, and ended by removing the last restrictions on the use of the Internet to carry commercial traffic, and the internet started to take the shape of world wide web from early 1990 with a great revolution in on culture, commerce, and technology, side by side with the initiation of a brand new technologies like electronic email, instant messaging, and voice over Internet, then the JANET network was initiated in the united kingdom and the internet 2 in the USA, from since the world had seen the importance of the internet in their daily life were the telecommunication was taking 1% of the world communication in the early 90th then it reaches 51% by the beginning of the new millennium (2000), and reached 97% of the world telecommunicated information by 2007, and the internet Is getting to grow every single day till this days that we will talk in the next article about the 2019 internet statistics.
Global Internet traffic
Traffic size:
At first we will talk about the total internet traffic in the past years let’s start with the new millennium from the year 2000 that were 361 million users of the internet all over the world, at the end of 2005 it becomes about 1 billion users, this number is nearly doubled by the end of the year 2010 to reach 1.97 billion internet users, then we have a great leap by the year 2015 that the total internet users reached 3.3 billion users, and guess what it reached 4.1 billion users by the end of 2018, and the Analysts see that the internet total number of users will reach 12 billion users by the year 2020.
Traffic geography:
As geography Asia had listed as the most continent using internet by 49% of total internet users and the runner up continent is Europe by 16.8%, North America has the highest internet penetration percentage in all the continents with 88.1% followed by Europe, and as countries China is in the lead by 20% of all worldwide internet users for about 800 million users at the end of 2018, a very important point we have to take in view is that about 98% of China internet users use the mobile internet, not only that have a record in the number of internet users but Iceland has its own record by nearly 100% of internet penetration as all the Icelandic citizens use the internet.
Internet Records:
for the first time, internet advertising beats TV advertising as the global Internet advertising spends over 2017 reached 205$ billion while TV advertising reached nearly 192$ billion.
for the USA it is the world leader in the online purchasing that would reach about 80% of the American internet users that could purchase online in 2019.
Internet publishing is still growing that reached 4 million posted on the internet every day.
google had seen a great leap in the total number of searches in the last years which reached about 5 million Google searches per day in 2018, even the type of search on google had and will see a great revolution that the voice search is expected to reach about 50% of all the searches done by Google in a year and 30% will not even use a screen to search.
By talking about Google and records it never ends as google had dominated the internet traffic as the most visited website on the internet in 2018 followed by YouTube, Facebook and the Chinese search engine Baidu is the 4th most visited site on the internet.
As web hosting market sees a great evolution in the last years as Domain name registrations grow by 3.5% every year, and there are about 342 million domain name registered in the third quarter of 2018, the most dominant domain is the famous one (.com) that leads the domain names registered by 43.59% of all domain names extensions, by the way, let’s talk about the most expensive domain ever which is LasVegas.com which was sold for 90 million dollars in 2005.
The e-commerce marketing became one of the most important niches of all the websites niches, as the size of sales could reach 3.45 trillion dollars in 2019, as expected Amazon dominates the online shopping by 49% of all online sales worldwide, the online shoppers spend on average of about 488 dollars annually on the marketplaces.
As the online advertising industry is growing the ads blocker also grows as there are More than 615 million devices in the world that have a one ad blocker installed at least.
Egyptian internet
History:
First, let’s talk about the history of the internet in Egypt and how and when it started.
Internet had started working in Egypt since 1993 by using a cable connection to France with 9.6 kbps bandwidth, the number of users at that time was estimated to be between 2000 and 3000 users, the Egyptian domain was only one domain in 1993 which is (.eg), then this domain is divided into 3 sub-domains which are
- . eun.eg for the Egyptian Universities Network.
- . sci.eg serving the Scientific research institutes.
- . gov.eg for Governmental institutes.
1996 had seen a great leap in the Egyptian internet by increasing the internet speed by 20 times, and the number of internet users had increased to reach about 20,000 users, in the year 2000 Egypt had started using ISDN service is added to the telephone line which changed the analog telephone to digital, which reflected on the internet speed to make I reaches 64kbps and 128kbps, nowadays the internet speed reaches 24Mbps.
Traffic:
Egyptians interest in internet grows every day till the penetration reaches to 47.4 million users on 2018, social media platforms dominate the internet traffic in Egypt by 37 million users per month, Facebook is the most visited social media platform.
Social media statistics
History:
Social media had started from the early age of internet on 1973 when Dave Wooly and Douglas Brown had created Talkomatic the first multi-user chat room application an instant sensation for users in the PLATO System's online community.
Social media platforms Start:
Social media had really started to be worldwide from the year 2003 with two main websites which are Myspace that reached 1 million users in a few months from its start, the year 2003 had witnessed the launching of the most worldwide social media platform Facebook as FaceMash by the American 19 years old kid Mark Elliot Zuckerberg with his colleagues, Facebook began to dominate the social media market with by the year 2004 Facebook had reached 1.5 million users, in 2018 Facebook had reached about 1.32 billion users per day, and about 2 billion monthly active users, 2005 had seen the launch of (YouTube)the most famous videos platform nowadays, the year 2006 had seen the launch of twitter that came to compete with Facebook after the fallback of Myspace, the year 2010 had witnessed the launch of one of the most social media platforms that are specialized in images and videos, then we go to the year 2010 when google the biggest search engine in the internet had decided to enter the social media world with google+ which is going to be deactivated in 2019 after falling to compete with other social media platforms especially Facebook.
Social media 2019 statistics:
2019 is going to see a great leap in social media marketing, while the Analysts experts expect that social media users number will reach about 2.77 billion users in 2019, social media different platforms will see a lot of new statistics like 32% of internet users will use Instagram, over than 95 million images and video will be shared on Instagram daily, Facebook status with images will see a great leap over status without images, about 64% of Facebook monthly users will use messenger, it is expected that social media will be responsible for about 30% of online shopping, Facebook sees 8 billion average daily video views from 500 million users, Facebook will see an average of 500,000 new users per day, YouTube will reach 1 billion watching hours per day, Twitter will reach 500 million visits per month, Instagram will see 800 million monthly active users, Pinterest will reach 200 million monthly active users, LinkedIn and snapchat will reach 187 million active users every month.
Mobile internet statistics
History:
Mobile internet or mobile web which is browsing the internet through mobile devices such as smartphones and tablets, in early 2010 (ITU) international communication Union had started to work with wireless network, the mobile internet had seen a great leap as in 2014 that it exceeded the desktop internet in the USA, as per as the growing importance of mobile internet google had launched a new update called Mobilegeddon that focus on websites quality and speed on mobile, and even gives the most applicable websites on mobile an advance in search results, and in 2005 a new web update as they launched AMP (accelerated mobile page) that work on optimizing the website speed on mobile.
2019 statistics:
2019 is going to see a great advance in mobile internet usage as it’s expected that 63.3% of mobile users will use access to internet through mobile, January 2019 had seen about 3.7 billion global mobile internet users, Mobile e-commerce will be responsible for about 67.2 % nearly $2.32 trillion of e-commerce sales by the year 2021, Mobile internet traffic was responsible for 52.2% of global Internet traffic in 2018, 40.1% of time spent on sites is by mobile users, 30% of all mobile e-commerce transactions come from mobile devices, as countries South Korea has the highest internet penetration rate with 71.5% of the population uses internet mobile, and as Continents Asia leads with 61.09% of total global mobile internet, mobile acquires about 53% of emails that opened on mobile devices, Tablets leads add-to-cart rate on e-commerce sites with 8.58% more than all other devices, social media apps will dominate the all mobile internet by 89% and the remaining 11% spent on other websites, 71% of marketers believes that mobile marketing is more appropriate for their business than desktop.
Conclusion:
We see that the mobile internet is the future of internet in all niches, mobile e-commerce will see a great rise in global total online shopping revenue, online marketers are focusing on mobile marketing than desktop as per as the great mobile internet had a great leap in the past few years, global internet users began to prefer logging on the internet using mobile even tend to online shopping through mobile, so is the next years are going to see the age of mobile marketing.
Tell us in the comments what is your opinion in the mobile internet improvement, and does it worth it.
0 notes
Text
Internet Security for New Developers
As an at home or on campus bootcamp students, we are all learning how to build services, apps, both on back end designs and front end designs. Our curriculums help us to have the first step in this new career and always learning area. After the graduation we will deep dive in to one particular area or some of us will choose to be freelance developers. Security is not the scope of our programs right now. It is a big, deep and high effort speciality and people follow this road as a security engineer or architect. As an old network and security engineer, I believe, even if we will not decide to follow up the app security career, every web developer should know the foundations of how security over internet works and what are the points who are related to the app developer.
Network layers and security
Initially, Internet (formally ARPANET) is not designed to be secure. Main goal of the creating networking was for military reasons. Target was, in the case of a nuclear war, and aftermath, government shouldn’t lose access to nuclear warhead stations with underground copper lines. At that scenario there was nobody who was able to access this network because:
Government has built that network and no civilians has access to it. It is a total closed circuit.
We are talking about a nuclear war. There were no civilians or human left on the surface who can intercept this traffic.
After several years of military usage, this network and technologies and protocols who runs it has been opened to all civil access. The main protocols used for internet networking is TCP/IP which is still the same standard since arpanet.
Networking works in several logical layers

Currently even if we are using TCP IP protocols, OSI layer architecture is used for logical designs of network equipments and our applications.
From a programmer perspective we only need to know that Network access layer is where all the physical environment abstraction happens: if it is a fiber optic cable, fiber optic related technologies, if we are using wifi, airborne technologies are all applied here. The output to the network/internet level is seamless regardless of the technology we use. Internet level is where we start basic communication between two network devices on ethernet card level. That means there is no IP knowledge on this levels. All packets are sent and received on mac address based.
Transport level is where we start to use ip addresses and able to access devices outside of our network, with an abstraction where we do not need to know their mac address.
As programmers our all work is on the application layer on TCP/IP or Application and presentation level on the OSI layers
As I said internet is not designed to be secure: that means that transport, internet and network access layers are not secure. So it is us who have to secure our apps.
For internet and networking security we base our security on a technology on the session layer: HTTPS.
What is HTTPS, encryption and authentication? Meet Alice and Bob
To be able to understand the basics we will go through an example
Alice and Bob live in different cities. They send each other letters and that is the only way of communication.

When Alice send a letter to Bob, there is no way that she can know if someone open the letter and read it. So she cannot write any credit card info or her social security number in it.
We can say that postal service / internet is an untrusted zone and I have to encrypt my private info when sending this letter.
Two type of encryptions
Until 1970s (Before Diffie Helman) there were only one type of encryption: Symmetrical algorithms. That means that Alice and Bob have a key and a lockbox. Before Alice send the letter with social security number to Bob, she puts it in a lockbox lock it with her key and sends it to Bob. as bob have the same key, he can open the box and read the letter.

But that scenario doesn’t work in our case. BecauseAlice have to send Bob the key, so Bob can open the lockbox. They can set a date and meet in a city one time and Alice can share this key. But in internet we cannot meet physically whit every service provider to exchange keys.
Sending the key in a letter is not an option because as postal service cannot be trusted they can copy the key and read every letter afterwards.
That was a big problem until 1970s. Even Enigma which was the best cryptographic machine in the work during the world war two was cracked because of this. As it was a symmetrical encryption, german military shared a handbook with secret keys scheduled by day.
Symetrical Encryption
Lets do some math. Basically the lowest level of symmetrical encryption works like this:
f(x) = x+5 ; f(x) = y ; Key is 5
Ex1: 12345 => 67890
Ex2: ALICE => FQNHJ
f-1(x) = x-5 ; f-1(y) = x ; Key is 5
Ex1: 67890 => 12345
Ex2: FQNHJ => ALICE
That means that when Alice and Bob know that the formula (the key is 5) they can decrypt each others messages and encrypt to send to the other one. This is the most basic cryptographic algorithm. But even most complex encryption algorithms like AES is based on this key exchange. In our example our key is 1 character long. When we say AES 256 or AES 1024, we mean that our key is 256 or 1024 character long. So that means that finding a pattern between the characters is much more difficult.
AES is one of the most secure algorithms but still Alice have to send this key to Bob to be able to talk in private.

Asymmetric Encryption
In 1977 Diffie-Helmann (two mathematicians) basically found out an f(x)=y function which doesn’t have a f-1(y)=x.
That means that we need two functions which you cannot generate from each other (two different keys) to encrypt and decrypt a message.
f(x) = y
g(y) = x
Bob found a way:

So now Bob have one key to lock the box (private key) and another key to unlock (public key).
Public key can be used to lock boxes but it cannot open any box that it locked. So Bob sends this key to Alice. Even if postal service copy this key, they will not be able to open boxes locked with this key. Because it only works one way.
Alice encrypts her social security number with the public key of Bob and sends it bob over postal service. Postal service now cannot see what is inside of it. The only key that can open this box is Bob’s private key that nobody knows about. So when he recieved it, he can open the lock and read the social security number.
The problem with the asymmetric encryption is that they are too slow to work regularly and encrypt every packet with this algorithm. In https connection it is only used once per session to be able to transfer an AES key securely to the other side. And the rest of the encrypted connection goes with symmetrical AES encryption:

Authentication, Digital Certificates and Digital Signatures
The same technology is used for not only securing the information we send, but we also use it to sign a website or an email so the recipient is sure of the owner and the info the recipient gets is original.
Lets say that Bob will send a divorce paper to Alice. How can Alice be sure that the divorce papers that she got over postal service are really sent by Bob.
Alice has bob’s public key. So Bob prepares divorce papers. He do not encrypt tham but take a small hash of it. As we know, even if a letter has been changed on this letter hash would change. So Bob encrypt only this hash output and current date data and att it as an attachment to his letter, email or website https header. So when Alice recive this message, she can decrypt it with bob’s public key and compare the output hash with the document hash. So she can be sure that it is really bob who signed this letter with his private key at the correct date.
Ceriticate Authorities

So how can be sure that we are on our banks real website and it is not someone elses fake phishing website:
Yes it is encrypted and it is signed. But how can I know that this signature is my banks signature?
Companies cannot decide by themselves their own signatures. There are generic Certificate Authorities who are accepted worldwide who distributes this certificates and also acknowledged by our operating systems and browsers.
When I enter to a website. I get the signature of that website from their https header. In the signature there is also the signature of the certiciate authority which gave this signature to the company. And we compare if this authority is one of the known embedded authorities in our browser, operating system. If it is one of them we are secure.

But if we are using a pirated operating system, or get a virus from an unknown source it is possible that a hacker can add his own certificate to our trusted certificate authorities list in our os. In that case we cannot understand if a site is real or a phishing site.
Certificate types
From now on Google chrome has decided to mark all http sites as unsecure with a red untrusted symbol on the address bar. So as web developers we are asked at least to buy a minimum certificate from a trusted certificate authority. If we only want that our connection be secure and not eavesdropped on the internet we can buy it online from godaddy etc. But if we want to create a commercial website than the minimum certificate is not enough. We have to apply for an extended certificate from verisign, thawte, globalsign etc.. They ask you to show them a proof of existence of your company and you are an authority in this company who can manage security certificates. And these certificates are valid for a period of time. You have to renew them before expiration date.
References:
https://en.wikipedia.org/wiki/ARPANET
https://wordtothewise.com/2014/09/cryptography-alice-bob/
https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
0 notes
Text
To Much World: Is the internet death?
oIn this module we were divided into groups of ten and given a topic to choose, we chose "To Much World: Is the internet death?” witch then we would have to individually create a practical work (piece of art) related to it.
In the beginning, I made a mind map with everything that relates to the internet as pirates, hackers, social media, etc.
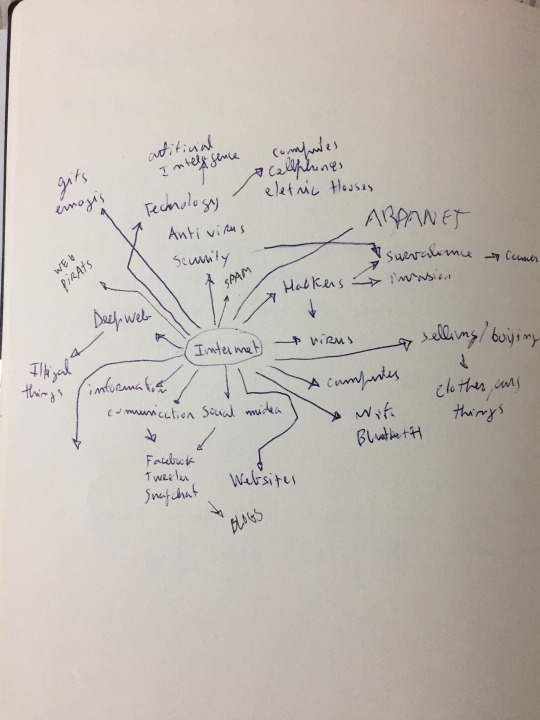
Mind map
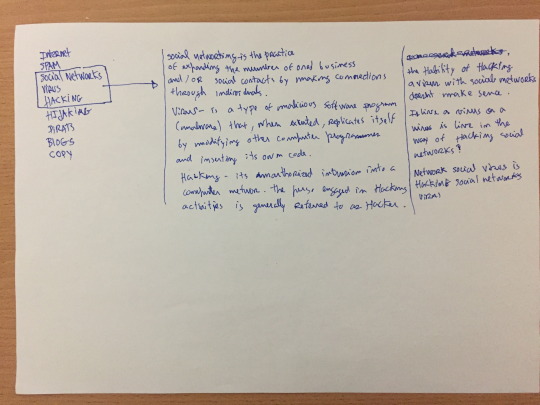
Mind map
After reviewing my mind map I opted for the theme Deep web which is an “illegal” hidden browser where we can find all types of things. I was interested about the wonders of the internet that can’t be reached by everyone, all the dangers and illegal things we could reach there as guns, hit mans, drugs, organ traffic, etc. That is a certain way kind of scared me as well.
I started researching it, I was advised to look into a platform called 4chan that is similar to the deep web in pirate terms but we could find normal things as well as gifs or jokes images… I went to look into Imageboard websites, anonymous and guidelines websites. Then I did some research about the “Inversion” by Zach Blas which I didn’t understand that well, the 1º practice, the constituting and outside.
I did some artist research witch Metahaven is one of the main ones, I liked his works because they are really graphic and show a bit the confusion that internet is.

Metahaven

Metahaven
Metahaven
After the research, I started having some ideas, and my main idea was a gradient of images from top (legal things on the deep web) till it gets darker by the number of images in the bottom (illegal things on the deep web) as you can see in the image a sketch of it. I did 200 screenshots, 100 with bright color, 100 darker and a mix of another 100 screenshots to build with it.
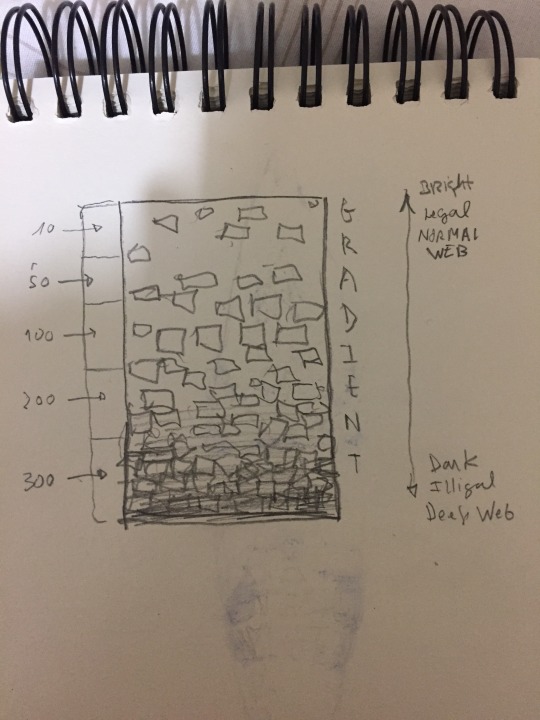
After all of this and after trying to get in the deep web failing my attempt I thought about changing the topic to something that I could be more interested. I wasn’t enjoying the work and I didn’t realise why until I figured it out that was because I didn’t like the theme technology and internet because it’s taking over the world but I couldn’t change that so I thought about doing something that shows my side of why its bad for us in a certain way the technology. So I dropped the deep web topic and I jumped into the 4th industrial revolution.
I did some research to understand what was it and I realised there was more topics inside it.
Some topics of 4th industrial revolution:
- artificial intelligence
- education
- agriculture
- employment
- vehicles
Studies say that:
- uber is a virtual company that doesn’t possess real cars and is now the biggest taxi company in the world.
- there will be less 90% of lawyers thanks to new tech programs.
- virtual nurses will recognize 4 times faster cancer then real humans.
- facebook will recognize better faces than real humans.
- there are studies that say that in 2030 computers will be smarter than humans.
- there will be no more coal mines because of the renewable energies, so less work for people.
- there will be population reducement with all the absence of work.
- 75-80% of labor is gonna run out
"It would be presumptuous to try to accurately describe the next era in the digital world. But it is reasonable to conclude that the internet we have known for almost three decades is changing and that the next one will change the world more than its older sister "- Vincent Mosco, in an article published in the IHU News of the Day.
Artificial Intelligence
It's a dangerous topic because it's difficult to control something that thinks for them selfs and doesn't have feelings.
Stephen Hawkins says it could spell the end of the human race.
"In the eighteenth century, Julien Offray de La Mettrie questions the Cartesian distinction between body and soul, and asks the question: why not imagine that the soul is a product of matter? It thus opens the way to artificial intelligence as we understand it today, in a materialistic and no more spiritualistic conception. The roboticists no longer seek to put the knowledge in the head of the robots, as the god of Descartes would have done with our souls, but make them capable of exercising basic sensory-motor functions that they can then complex, more intelligent "- Jean-Michel Besnier is a philosopher and doctor of political science, in an interview published in the IHU's News of the Day.
https://www.youtube.com/watch?v=AF5ShjWIRjE
https://www.youtube.com/watch?time_continue=135&v=ulnv9U20SZ4
Automatic vehicle:
https://www.youtube.com/watch?time_continue=56&v=xRmDnXc9Z-M
Where did internet come from?
Internet came from ARPANET, was born through the connection of military network with universities and research centers, was a network that connected big computers with medium computers from university to university, with the time passing more networks joined until we got to the world network we have nowadays.
Nowadays internet is a network of people and community
internet of things:
The internet of things is all the devices that are connected to the internet, Bluetooth and Wifi, like cell phones, televisions, car, etc.
"A Cisco study predicts that the Internet of Things will have an economic value of $ 14.4 trillion in a decade in the world. Of this total, about 50% of the highest economic value is in machine-to-machine connections"
internet had three phases:
-computer network
-people and community network
-the network of things (cellphone, television, cars)
Nowadays you can:
have an automatic house that you can control it through a tablet. (energy, heater, locks, cameras etc)
cities can spread sensors that predict the weather through the wind and humidity
cars can connect with each one to warn about traffic and accidents
you can wear watches or clothes that tell you your heartbeat and call your doctor in case of problems
fridges can automatically ask for the products that are running out
ARTISTS/inspiration:
- Kurt Schwitters
- Annegret Soltau
- Hannah Hoch
- Ben Giles More
-https://www.pinterest.com/behance/
IDEAS FOR COLLAGES:
- Robot made with human parts, like half face half metal and computer parts with fire around and chaos to show the danger of artificial intelligence
- Printing blocks of houses, everything the same
- Printing threes to show the irony of the lost of threes with space were we build houses and cut threes (like the inversion, houses destroyed and threes being built, with constructors)
- Computers eating dressed in suits and people naked crying for food
- Steak man fat, seated in a flying chair with everything accessible and easy to get to show the irony of how technology can make you useless
- Loads of collages with internet usual things, to fill the entire page to show how the internet is filled with hundreds of millions of things
After all my research about 4th Industrial Revolution I chose one topic in it, I chose artificial intelligence because is something that makes me concerned because robots may be really dangerous and a threat to the human race.
Some videos I inspired my research on:
https://www.youtube.com/watch?v=AF5ShjWIRjE
https://www.youtube.com/watch?time_continue=3&v=ulnv9U20SZ4
https://www.youtube.com/watch?v=xRmDnXc9Z-M
Some reasons I am afraid of them:
Robots may want us to give them human rights, they will ask for citizenships and wages. The good thing is, they will also pay taxes.
Robots are learning to deceive , there is an algorithm allowing robots to choose to tell lies, and make sure you will never find out
Israel and South Korea are already using killer robots, in auto mode, these robots can decide whether to kill you or not - without the approval of a human operator
Military robots can switch sides, it’s possible that an enemy army could hack robots and use them against their original owners, even your self-driving car can kill you by going against a wall
Around 48 million Twitter accounts are operated by bots
Some of them will inform you of natural disaster, but others are being used to brainwash you
Al will soon replace your lovers
By 2050, human-on-robot sex will become the new norm
By 2053, Al will be performing surgeries, as well as 50% of all other existing jobs
Researchers are teaching Al to feel emotions which is probably the last quality that differentiates us from robots
They will become too intelligent to remain under human control
Robots will develop the ability to engineer themselves and possibly wipe out humanity.
Music video:
https://www.youtube.com/watch?v=2XY0EHSXyk0
This link above is a song by Flying Lotus called “Post Requisite” that has video collage, the video is directed by Winston Hacking and is made of collages moving with some computer editing playing a beat. I found that interesting in my research because of hes technics and ideas were really good.

Flying Lotus - “Post Requisite” Winston Hacking

Flying Lotus - “Post Requisite” Winston Hacking

Flying Lotus - “Post Requisite” Winston Hacking

Flying Lotus - “Post Requisite” Winston Hacking

Flying Lotus - “Post Requisite” Winston Hacking
With all the information I gathered about artificial intelligence started doing some digital collages:

Mr. Robot, João Pinto, 2017

Robo-President, João Pinto, 2017

Evil-Conection, João Pinto, 2017
Union, João Pinto, 2017

Motherboard, João Pinto, 2017
These images are some collages and photoshop I edit in photoshop. Its a mad robot with half the face of the creator of the artificially intelligent robot called Sophia, the other half of the face is that exact same Sophia and The background is red to show chaos, in other there are two robots on the side to show support for the robots to the robot leader to destroy the human race, and in other the background is either white to show the void of a world of robots instead of humans and the last background is a motherboard crossing it showing that the world powered by tech and we shouldn't become that same thing because we are humans.
When I did this digital collages I realized that if I did it digitally I would be supporting the tech and I would be going against all I’ve researched and supported so I started looking into some magazines, books, and newspapers to make some handmade collages. I looked into the book “10 years of pictures” of Paul Solberg that has a lot of pictures of the city environment and technology, I scanned pictures from the pages 17,40,73,94,123 and 207 to cut and past, then I saw the book “Color is power” by Robert Walker which I scanned the pages 33,40,42,44,45,46,53,54,120 and 133, and in las I scanned pages from the book of David Carson where I scanned the pages 70 and 71, 72 and 73.
Draft of pages and ideas
Draft of pages and ideas
Draft of pages and ideas
I looked into some artists as:
Mark Andrew
Rael Brian
Gregory Arth
Kurt Schwitters
After gathering a lot of images and things to cut and paste I printed a load of them and I begun to do some collages, the first one looked really bad so I threw them away but after a few collages they begun looking good, I looked into some technics of collages and I did it.


The images above are some of the some of the pictures I used for my collages.
Here are some examples of some of my collages:

Prosecution, João Pinto 2017

Robotisation, João Pinto, 2017

Warnings, João Pinto, 2017

Labor, João Pinto, 2017

Untitled, João Pinto, 2017

Hopelessness, João Pinto, 2017

Untitled 2, João Pinto, 2017

Untitled 3, João Pinto, 2017

Untitled 4, João Pinto, 2017

Untitled 5, João Pinto, 2017
After I did around 30 collages I thought about doing some paint marking, I remade some of my collages, some in black and white so that when I add color it would highlight the color and some with normal color. These are some examples of my work:

Street-cleaner, João Pinto, 2017
Devil’s disguise, João Pinto, 2017

Mind floating, João Pinto, 2017

Untitled 6, João Pinto, 2017

Death Conference, João Pinto, 2017

Untitled 7, João Pinto, 2017

Untitled 8, João Pinto, 2017

Fractions, João Pinto, 2017

Untitled 9, João Pinto, 2017

Untitled 10, João Pinto, 2017

Untitled 11, João Pinto, 2017
After making the collages with paint marks I was happy with the results so I thought about choosing one to be the main one for the exhibition and this was the chosen one:

I inspired myself in this collage that I made to create my final piece, I used a website called Rasterbator to resize the image to be able to print it in big size but in different pages A4, then I found a support for my piece (A0 piece of wood) , I pasted recycled paper and the job find part of the newspaper then I started doing collages and painting my work.

Piece of wood already worked

Details of the final piece, as we can notice in this detail I pasted some of the images first in black and white and then colors to be able to rip them off to have a contrast between color and black and white, like if black and white is the technology and robots (boring) and colors would be life that its being killed by robots.

Details of the final piece
Details of the final piece

The takeover , João Pinto 2017
The picture above is my final piece.
Explanation:
The women using a white shirt is a robot called Sophia , using white showing she is peaceful but in my painting is an ironic way, she has crosses in her eyes like the women in the billboard to symbolise how I am against a robot world, the robot behind Sophia shows the robot support for their leader (in this case Sophia). The yellow man is yellow to capture the viewer attention and because it means light showing that the human is the light and not the robots, and it says “Up for everything” to demonstrate how the human being will be desperate to get a job when robots take all the jobs. The man cleaning the streets is a way of showing the humans will have the worst jobs (even cleaning streets the robots will do), under that man we can se a different texture that is “paper” that I took from a tree to demonstrate the nature in middle of all of this change. The black in the painting shows the darkness of this world and the red shows death. The stripes in the red mean prison because we will be stuck in a dead world.
When I had my final piece made I decided to create a zine with my works:

Zine

Back Page

Front Page
Then I did some tests of color printing:

Printing test

Printing test

Printing test
My piece in the Exhibition:
Initially, I thought about hanging my piece in the wood structures but because the wood structure was too weak to hold it so I was struggling about what to do as w can see in the image 1 I was thinking about leaving it on the floor but then I went to find solutions and I found tripod to put my piece as we can see in image 2. Then there was something missing so I decided to add space blanket around the tripod as we can see in image 3 my piece looks more integrated into the exhibition, in the world of internet.

Image 1

Image 2

Image 3
CONCLUSION
In this work I had some struggles at the begging with about “what to do” problem, I had to change theme in the middle of the term but it was a good choice because I had a lot of ideas right away, I enjoyed working with the artificial intelligence and was fun do pass from topic to topic, like from internet to 4th industrial revolution to internet of things to AI, I think my research was really good beacuse I was able to find information for my piece in books, websites, movies, docummentarys and music. I worked different sizes, A5, A4, A3, and A0 for the final piece. I worked different collage techniques and worked with colour and black and wites making different paint marks. In my opinion, this work worked out good. In conclusion, I think I filed all the requested inquiries for my work.
0 notes
Text
Events 11.21
164 BC – Judas Maccabeus, son of Mattathias of the Hasmonean family, restores the Temple in Jerusalem. This event is commemorated each year by the festival of Hanukkah. 235 – Pope Anterus succeeds Pontian as the nineteenth pope. During the persecutions of emperor Maximinus Thrax he is martyred. 1009 – Lý Công Uẩn is enthroned as emperor of Đại Cồ Việt, founding the Lý dynasty. 1386 – Timur of Samarkand captures and sacks the Georgian capital of Tbilisi, taking King Bagrat V of Georgia captive. 1620 – Plymouth Colony settlers sign the Mayflower Compact (November 11, O.S.) 1676 – The Danish astronomer Ole Rømer presents the first quantitative measurements of the speed of light. 1783 – In Paris, Jean-François Pilâtre de Rozier and François Laurent d'Arlandes, make the first untethered hot air balloon flight. 1789 – North Carolina ratifies the United States Constitution and is admitted as the 12th U.S. state. 1832 – Wabash College is founded in Crawfordsville, Indiana. 1861 – American Civil War: Confederate President Jefferson Davis appoints Judah Benjamin Secretary of War. 1877 – Thomas Edison announces his invention of the phonograph, a machine that can record and play sound. 1894 – Port Arthur, China, falls to the Japanese, a decisive victory of the First Sino-Japanese War; Japanese troops are accused of massacring the remaining inhabitants. 1902 – The Philadelphia Football Athletics defeated the Kanaweola Athletic Club of Elmira, New York, 39–0, in the first ever professional American football night game. 1905 – Albert Einstein's paper that leads to the mass–energy equivalence formula, E = mc², is published in the journal Annalen der Physik. 1910 – Sailors on board Brazil's warships including the Minas Gerais, São Paulo, and Bahia, violently rebel in what is now known as the Revolta da Chibata (Revolt of the Lash). 1916 – Mines from SM U-73 sink the HMHS Britannic, the largest ship lost in the First World War. 1918 – The Flag of Estonia, previously used by pro-independence activists, is formally adopted as the national flag of the Republic of Estonia. 1918 – The Parliament (Qualification of Women) Act 1918 is passed, allowing women to stand for Parliament in the UK. 1918 – A pogrom takes place in Lwów (now Lviv); over three days, at least 50 Jews and 270 Ukrainian Christians are killed by Poles. 1920 – Irish War of Independence: In Dublin, 31 people are killed in what became known as "Bloody Sunday". 1922 – Rebecca Latimer Felton of Georgia takes the oath of office, becoming the first female United States Senator. 1927 – Columbine Mine massacre: Striking coal miners are allegedly attacked with machine guns by a detachment of state police dressed in civilian clothes. 1942 – The completion of the Alaska Highway (also known as the Alcan Highway) is celebrated (however, the highway is not usable by standard road vehicles until 1943). 1944 – World War II: American submarine USS Sealion sinks the Japanese battleship Kongō and Japanese destroyer Urakaze in the Formosa Strait. 1945 – The United Auto Workers strike 92 General Motors plants in 50 cities to back up worker demands for a 30-percent raise. 1950 – Two Canadian National Railway trains collide in northeastern British Columbia in the Canoe River train crash; the death toll is 21, with 17 of them Canadian troops bound for Korea. 1953 – The Natural History Museum, London announces that the "Piltdown Man" skull, initially believed to be one of the most important fossilized hominid skulls ever found, is a hoax. 1959 – American disc jockey Alan Freed, who had popularized the term "rock and roll" and music of that style, is fired from WABC-AM radio over allegations he had participated in the payola scandal. 1961 – The "La Ronde" opens in Honolulu, first revolving restaurant in the United States. 1962 – The Chinese People's Liberation Army declares a unilateral ceasefire in the Sino-Indian War. 1964 – The Verrazano-Narrows Bridge opens to traffic. At the time it is the world's longest bridge span. 1964 – Second Vatican Council: The third session of the Roman Catholic Church's ecumenical council closes. 1967 – Vietnam War: American General William Westmoreland tells news reporters: "I am absolutely certain that whereas in 1965 the enemy was winning, today he is certainly losing." 1969 – U.S. President Richard Nixon and Japanese Premier Eisaku Satō agree on the return of Okinawa to Japanese control in 1972. The U.S. retains rights to bases on the island, but these are to be nuclear-free. 1969 – The first permanent ARPANET link is established between UCLA and SRI. 1970 – Vietnam War: Operation Ivory Coast: A joint United States Air Force and Army team raids the Sơn Tây prisoner-of-war camp in an attempt to free American prisoners of war thought to be held there. 1971 – Indian troops, partly aided by Mukti Bahini (Bengali guerrillas), defeat the Pakistan army in the Battle of Garibpur. 1972 – Voters in South Korea overwhelmingly approve a new constitution, giving legitimacy to Park Chung-hee and the Fourth Republic. 1974 – The Birmingham pub bombings kill 21 people. The Birmingham Six are sentenced to life in prison for the crime but subsequently acquitted. 1977 – Minister of Internal Affairs Allan Highet announces that the national anthems of New Zealand shall be the traditional anthem "God Save the Queen" and "God Defend New Zealand". 1979 – The United States Embassy in Islamabad, Pakistan, is attacked by a mob and set on fire, killing four. 1980 – A deadly fire breaks out at the MGM Grand Hotel in Paradise, Nevada (now Bally's Las Vegas). Eighty-seven people are killed and more than 650 are injured in the worst disaster in Nevada history. 1985 – United States Navy intelligence analyst Jonathan Pollard is arrested for spying after being caught giving Israel classified information on Arab nations. He is subsequently sentenced to life in prison. 1986 – National Security Council member Oliver North and his secretary start to shred documents allegedly implicating them in the Iran–Contra affair. 1992 – A major tornado strikes the Houston, Texas area during the afternoon. Over the next two days the largest tornado outbreak ever to occur in the US during November spawns over 100 tornadoes. 1995 – The Dayton Agreement is initialed at the Wright-Patterson Air Force Base, near Dayton, Ohio, ending three and a half years of war in Bosnia and Herzegovina. 1996 – Humberto Vidal explosion: Thirty-three people die when a Humberto Vidal shoe shop in Río Piedras, Puerto Rico explodes. 2002 – NATO invites Bulgaria, Estonia, Latvia, Lithuania, Romania, Slovakia and Slovenia to become members. 2004 – The second round of the Ukrainian presidential election is held, giving rise to massive protests and controversy over the election's integrity. 2004 – Dominica is hit by the most destructive earthquake in its history. The northern half of the island sustains the most damage, especially the town of Portsmouth. In neighboring Guadeloupe, one person is killed. 2004 – The Paris Club agrees to write off 80% (up to $100 billion) of Iraq's external debt. 2006 – Anti-Syrian Lebanese politician and government minister Pierre Gemayel is assassinated in suburban Beirut. 2009 – A mine explosion in Heilongjiang, China kills 108. 2012 – At least 28 are wounded after a bomb is thrown onto a bus in Tel Aviv. 2013 – Fifty-four people are killed when the roof of a shopping center collapses in Riga, Latvia. 2013 – Massive protests start in Ukraine after President Viktor Yanukovych suspended signing the Ukraine–European Union Association Agreement. 2014 – A stampede in Kwekwe, Zimbabwe caused by the police firing tear gas kills at least eleven people and injures 40 others. 2015 – The government of Belgium imposed a security lockdown on Brussels, including the closure of shops, schools, public transportation, due to potential terrorist attacks. 2017 – Robert Mugabe formally resigns as President of Zimbabwe, after thirty-seven years in office.
0 notes
Text
What is a computer virus?
A computer program capable of copying itself and infecting a computer without even the user's permission or knowledge is known as a computer virus. When the host of a computer virus is carried to an uninfected computer, then the virus spreads from one computer to the other. Viruses get transferred over a network, Internet or through removable mediums like floppy disk, CD and USB drive. There are three basic categories of computer viruses which are boot infectors, system infectors and generic application infectors. The boot sectors of diskettes and hard disks are attacked by the boot infectors. During the first access of a diskette the virus transfers itself to the sector 0 of the diskette and it then spreads to the system that are booted from this diskette. The Pakistani Brain Virus is an example of a boot infector. The system infectors are found to be attached to the operating system modules and Lehigh virus Slow PC repair Toronto is a typical example. The Generic application infectors have the capability to harm any application program. Well known viruses of this kind include the Israeli Virus and the Scores Virus. There are various theories and controversies regarding the first known computer virus. But majority support the view that The Creeper was the first virus that was detected on ARPANET which happens to be the forerunner of the internet in the 1970s. It found its way through the TENEX operating system and had the capability to use any linked modem to dial out to all remote computers for the purpose of infecting them. There are again beliefs about "Rother J" to be the first computer virus to have appeared "in the wild" which means outside the lab or the single computer where it originated. But the truth is that, it was the first virus to infect computers "in the home". A boot sector virus called The Brain was the first PC virus which appeared in the wild. In 1986, Farooq Alvi Brothers from Pakistan created this virus with the aim of discouraging pirated copies of software written by them. CIH and Melissa are two well known viruses which created disasters in the years 1998 and 1999 respectively. The estimated amount of damage that CIH created was 20 to 80 million dollars. This virus originated from Taiwan and Windows 95, 98, and ME executable files were its main targets. This virus found its residence in a PC's memory. Soon after its activation, it started overwriting data on the host PC' hard drive and as a result it made it inoperable. It also prevented boot-up of the host by overwriting the BIOS of the host. Although it caused disasters and losses at some point of time but it is not a serious threat nowadays because of the migrations to Windows 2000, XP, and NT which are not susceptible to CIH. Melissa caused an estimated damage of 300 to 600 million dollars. This was a word macro script that infected the business PCs. The rapid spread of the virus made Intel, Microsoft and other companies that were using Outlook to shut their total e- mail systems down! This virus used the e- mail lists of the user of Microsoft Outlook to e- mail itself in the form of a .DOC file as attachment. Unsuspected receivers opened the file and got their systems infected. There are a number of destructive viruses like Blaster, Bagle, MyDoom, Sasserbut I LOVE YOU released in 2000 deserves special mention. This acted like Melissa by e- mail itself with an irresistible message: I love You. It even used to find the IDs and passwords of the users of infected machines to send e- mails to its author. The amount of damage was estimated as 10 to 15 dollars. The irony is that Philippines had no law against computer viruses at that time and so it failed to punish the author of I LOVE YOU who was from Philippines itself! 384 Yonge street Toronto, Ontario M5B 1S8 www.KasawaK.ca
youtube
0 notes
Text
How the internet was developed
In 40 times, the internet has morphed from a military communication network into a enormous world-wide cyberspace. And it all started in a California beer garden
In the kingdom of apps and unicorns, Rossottis is a rarity. This beer garden in the heart of Silicon Valley has been standing on the same recognise since 1852. It isnt disruptive; it doesnt proportion. But for more than 150 times, it has done one thing and done it well: it has given Californians a good situate to get drunk.
During the course of its long actuality, Rossottis has been a frontier barroom, a gold rush gambling den, and a Hells Angels hangout. These periods it is called the Alpine Inn Beer Garden, and the clientele remains as potpourrus as ever. On the porch out back, there are cyclists in spandex and bikers in leather. There is a wild-haired man who might be a prof or a lunatic or a CEO, scribbling into a notebook. In the parking lots is a Harley, a Maserati, and a horse.
It doesnt seem a likely discern for a major act of innovation. But 40 years ago this August, a small unit of scientists set up personal computers terminal at one of its picnic tables and conducted an extraordinary experiment. Over plastic goblets of beer, they proved that a strange sentiment called the internet could labour.
The internet is so vast and formless that its hard to gues it being invented. Its easy to visualize Thomas Edison devising the lightbulb, because a lightbulb is easy to envisage. You can hold it in your hand and examine it from every slant.
The internet is the opposite. Its everywhere, but we only see it in views. The internet is like the holy spirit: it manufactures itself knowable to us by taking wealth of the pixels on our screens to show sites and apps and email, but its centre is always elsewhere.
This feature of the internet prepares it seem extremely complex. Surely something so ubiquitous yet invisible must compel deep technical sophistication to understand. But it doesnt. The internet is essentially simple. And that simplicity is the key to its success.
The people who devised the internet came from all over the world. They drove at targets as varied as the French government-sponsored computer network Cyclades, Englands National Physical Laboratory, the University of Hawaii and Xerox. But the mothership was the US defense departments lavishly money research limb, the Advanced search Assignment Agency( Arpa) which later changed its reputation to the Defense Advanced Research Projects Agency( Darpa) and its numerous contractors. Without Arpa, the internet wouldnt exist.
An old-time image of Rossottis, one of the birthplaces of the internet. Photograph: Politenes of the Alpine Inn Beer Garden, formerly Rossotti’s
As members of the military endeavour, Arpa had a specifically armed motivating for creating the internet: it offered a way to make estimating to the front line. In 1969, Arpa had improved a computer network called Arpanet, which relation mainframes at universities, government agencies, and defense contractors around the country. Arpanet originated rapidly, and included practically 60 nodes by the mid-1 970 s.
But Arpanet had a problem: it wasnt mobile. The computers on Arpanet were stupendous by todays touchstones, and they transmitted over attached joins. That might work for investigates, who could sit at a terminal in Cambridge or Menlo Park but it did little for soldiers distributed deep in enemy region. For Arpanet to be useful to violences in the field, it had to be accessible anywhere in the world.
Picture a jeep in the jungles of Zaire, or a B-5 2 miles above North Vietnam. Then suppose these as nodes in a wireless system linked to another network of potent computers thousands of miles away. This is the dream of a networked armed expending computing supremacy to demolish the Soviet Union and its friends. This is the dream that produced the internet.
Making this dream a reality asked doing two things. The first was building a wireless system that could relay packets of data amongst the widely scattered cogs of the US military machine by radio or satellite. The second was connecting those wireless networks to the wired network of Arpanet, so that multimillion-dollar mainframes could suffice soldiers in fighting. Internetworking, the scientists called it.
Internetworking is the problem the internet was invented to solve. It presented tremendous challenge. Get computers to talk to one another networking had been hard enough. But getting networks to talk to one another internetworking posed a whole new established of impediments, because the networks addrest alien and incompatible accents. Trying to move data from one to another was like writing a letter in Mandarin to someone who only knows Hungarian and hoping to be understood. It didnt work.
In response, the architects of the internet developed a kind of digital Esperanto: a common conversation that enabled data to expedition across any system. In 1974, two Arpa researchers mentioned Robert Kahn and Vint Cerf published an early plan. Depicting on conferences happening in all areas of the international networking parish, they sketched a design for a simple but very flexible etiquette: a universal fixed of rules for how computers should communicate.
These regulations had to strike a very sensitive equilibrium. On the one hand, they needed to be strict enough to ensure the reliable transmitting of data. On the other, they needed to be loose enough to accommodate all of the different ways available data might be transmitted.
Vinton Cerf, left, and Robert Kahn, who organized the first internet etiquette. Photograph: Louie Psihoyos/ Corbis
It had to be future-proof, Cerf tells me. You couldnt write the protocol for one point in time, because it would soon become obsolete. The military would keep innovating. They would continue constructing brand-new networks and new technologies. The protocol had to keep pace: it had to work across an arbitrarily large number of distinct and potentially non-interoperable packet swopped systems, Cerf says including information that hadnt been invented yet. This boast would establish the system not only future-proof, but potentially infinite. If the rules were robust enough, the ensemble of networks could ripen indefinitely, adapting any and all digital forms into its sprawling multithreaded mesh.
Eventually, these rules grew the lingua franca of the internet. But first, they needed to be implemented and nipped and experimented over and over and over again. There was nothing inevitable about the internet going built. It seemed like a outlandish project to many, even among those who were building it. The scale, the ambition the internet was a skyscraper and nothing had ever seen anything more than a few floors tall. Even with a firehose of cold war military cash behind it, the internet was like a long shot.
Then, during the summer of 1976, it started working.
If you had strolled into Rossottis beer garden on 27 August 1976, you would have assured the following: seven men and one woman at a table, wavering around personal computers terminal, the woman typing. A pair of cables guide from the terminal to the parking lots, disappearing into a big gray-headed van.
Inside the van were machines that changed the words being typed on the terminal into packets of data available. An feeler on the vans roof then given these packets as radio signals. These signals extended through the air to a repeater on a nearby mountain surface, where they were enlarged and rebroadcast. With this extra increase, we are able to make it all the way to Menlo Park, where an feeler at an office improving received them.
It is there that the real magic began. Inside the role build, the incoming packets passed seamlessly from one network to another: from the packet radio network to Arpanet. To make this startle, the packets had to undergo a subtle metamorphosis. They had to change their kind without changing their contents. Make about ocean: it can be vapor, liquid or frost, but its chemical composition remains the same. This magical flexible is a feature of the natural universe which is lucky, because life depends on it.
A plaque at Rossottis commemorating the August 1976 experiment. Picture: Courtesy of the Alpine Inn Beer Garden, formerly Rossotti’s
The flexibility that the internet depends on, by compare, “mustve been” engineered. And on that day in August, it enabled packets that had only dwelt as radio signals in a wireless network to become electrical signals in the wired network of Arpanet. Remarkably, this translation perpetuated the data perfectly. The packets continued completely intact.
So intact, in fact, that they could excursion another 3,000 miles to a computer in Boston and be reassembled into exactly the same content that was typed into the terminal at Rossottis. Powering this internetwork odyssey was the brand-new etiquette cooked up by Kahn and Cerf. Two networks had become one. The internet worked.
There werent balloons or anything like that, Don Nielson tells me. Now in his 80 s, Nielson led the experiment at Rossottis on behalf of the Stanford Research Institute( SRI ), a major Arpa contractor. Tall and soft-spoken, he is relentlessly modest; seldom has someone had a better excuse for boast and a lower level of are looking forward to indulge in it. We are sitting in the living room of his Palo Alto home, four miles from Google, nine from Facebook, and at no spot does he even partly take ascribe for creating information and communication technologies that realized these extravagantly profitable firms possible.
The internet was a group effort, Nielson insists. SRI was only one of many organizations working on it. Perhaps thats why they didnt experience comfortable popping bottles of champagne at Rossottis by claiming too much magnificence for one crew, it wouldve flouted the collaborative character of the international networking community. Or maybe they are only didnt have the time. Dave Retz, one of health researchers at Rossottis, says they were too worried about get the experimentation to operate and then when it did, concerned about whatever came next. There was always more to accomplish: as soon as theyd stitched two networks together, they started working on three which they achieved a little over a year later, in November 1977.
Over time, the recognition of Rossottis receded. Nielson himself had forgotten about it until a reporter prompted him 20 years later. I was sitting in my bureau the working day, he withdraws, when the phone call. The reporter on the other purpose had been hearing the venture at Rossottis, and wanted to know what it had to do with the birth of the internet. By 1996, Americans were having cybersex in AOL chatrooms and structure gruesome, seizure-inducing homepages on GeoCities. The internet had outgrown members of the military roots and run mainstream, and beings were becoming curious about its ancestries. So Nielson excavated out a few old-time reports from his files, and started indicating on how the internet inaugurated. This concept is shifting out to be a big deal, he remembers thinking.
What manufactured the internet a big deal is the aspect Nielsons team demonstrated that summer day at Rossottis: its flexible. Forty years ago, the internet teleported thousands of words from the Bay Area to Boston over channels as dissimilar as radio radiation and copper telephone lines. Today it bridges far greater intervals, over an even wider various forms of media. It ferries data among thousands of millions of designs, communicating our tweets and Tinder swipes across multiple networks in milliseconds.
The Alpine Inn Beer Garden today still a home where Silicon Valley mobs meet. Photo: Courtesy of the Alpine Inn Beer Garden, formerly Rossotti’s
This isnt simply a technological accomplishment its a blueprint decision. The main thing to understand about the roots of the internet, Nielson says, is that it came out of the military. While Arpa had wide-ranging leeway, it still had to choose the research project with an see toward developing technologies that might someday are used for acquiring campaigns. The engineers who construct the internet understood that, and tailored it accordingly.
Thats why they designed the internet to lead anywhere: because the US military is everywhere. It maintains virtually 800 basis in more than 70 countries around the world. It has hundreds of ships, millions of warplanes, and tens of thousands of armored vehicles. The reason the internet can work across any machine, system, and medium-sized the reason a smartphone in Sao Paulo can stream a lyric from a server in Singapore is because it needed to be as pervasive as the American security apparatus that financed its construction.
The internet would end up being useful to the US armed, if not quite in the ways its designers intended. But it didnt actually take off until “its become” civilianized and commercialized a phenomenon that the Arpa researchers of the 1970 s could never have anticipated. Quite candidly, if anyone would have said they could have imagined the internet of today in those dates, theyre lying, says Nielson. What astonished him most was how willing people were to spend money to set themselves on the internet. Everybody wanted to be there, he says. That was utterly startling to me: the outcry of wanting to be present in this new world.
The information that we think of the internet as a world of its own, as a home we can be in or on this too is the legacy of Don Nielson and his fellow scientists. By obliging different networks together so seamlessly, they stimulated the internet feel like a single space. Strictly expressing, this is an misconception. The internet is composed of numerous, many systems: when I go to Googles website, my data must pass 11 different routers before it arrives. But the internet is a original weaver: it secretes its sews extremely well. Were left with the perception of a boundless, borderless digital universe cyberspace, as we used to call it. Forty years ago, this world firstly flickered into existence in the foothills outside of Palo Alto, and has been expanding ever since.
Source: http://allofbeer.com/2017/09/17/how-the-internet-was-invented/
from All of Beer https://allofbeer.wordpress.com/2017/09/17/how-the-internet-was-developed/
0 notes
Text
Events 11.21
164 BC – Judas Maccabeus, son of Mattathias of the Hasmonean family, restores the Temple in Jerusalem. This event is commemorated each year by the festival of Hanukkah. 235 – Pope Anterus succeeds Pontian as the nineteenth pope. During the persecutions of emperor Maximinus Thrax he is martyred. 1009 – Lý Công Uẩn is enthroned as emperor of Đại Cồ Việt, founding the Lý dynasty. 1386 – Timur of Samarkand captures and sacks the Georgian capital of Tbilisi, taking King Bagrat V of Georgia captive. 1620 – Plymouth Colony settlers sign the Mayflower Compact (November 11, O.S.) 1676 – The Danish astronomer Ole Rømer presents the first quantitative measurements of the speed of light. 1783 – In Paris, Jean-François Pilâtre de Rozier and François Laurent d'Arlandes, make the first untethered hot air balloon flight. 1789 – North Carolina ratifies the United States Constitution and is admitted as the 12th U.S. state. 1832 – Wabash College is founded in Crawfordsville, Indiana. 1861 – American Civil War: Confederate President Jefferson Davis appoints Judah Benjamin Secretary of War. 1877 – Thomas Edison announces his invention of the phonograph, a machine that can record and play sound. 1894 – Port Arthur, China falls to the Japanese, a decisive victory of the First Sino-Japanese War; Japanese troops are accused of massacring the remaining inhabitants. 1902 – The Philadelphia Football Athletics defeated the Kanaweola Athletic Club of Elmira, New York, 39–0, in the first ever professional American football night game. 1905 – Albert Einstein's paper that leads to the mass–energy equivalence formula, E = mc², is published in the journal Annalen der Physik. 1910 – Sailors on board Brazil's warships including the Minas Geraes, São Paulo, and Bahia, violently rebel in what is now known as the Revolta da Chibata (Revolt of the Lash). 1916 – Mines from SM U-73 sink the HMHS Britannic, the largest ship lost in the First World War. 1918 – The Flag of Estonia, previously used by pro-independence activists, is formally adopted as the national flag of the Republic of Estonia. 1918 – A pogrom takes place in Lwów (now Lviv); over three days, at least 50 Jews and 270 Ukrainian Christians are killed by Poles. 1920 – Irish War of Independence: In Dublin, 31 people are killed in what became known as "Bloody Sunday". 1922 – Rebecca Latimer Felton of Georgia takes the oath of office, becoming the first female United States Senator. 1927 – Columbine Mine massacre: Striking coal miners are allegedly attacked with machine guns by a detachment of state police dressed in civilian clothes. 1942 – The completion of the Alaska Highway (also known as the Alcan Highway) is celebrated (however, the highway is not usable by standard road vehicles until 1943). 1944 – World War II: American submarine USS Sealion sinks the Japanese battleship Kongō and Japanese destroyer Urakaze in the Formosa Strait. 1945 – The United Auto Workers strike 92 General Motors plants in 50 cities to back up worker demands for a 30-percent raise. 1950 – Two Canadian National Railway trains collide in northeastern British Columbia in the Canoe River train crash; the death toll is 21, with 17 of them Canadian troops bound for Korea. 1953 – The Natural History Museum, London announces that the "Piltdown Man" skull, initially believed to be one of the most important fossilized hominid skulls ever found, is a hoax. 1959 – American disc jockey Alan Freed, who had popularized the term "rock and roll" and music of that style, is fired from WABC-AM radio over allegations he had participated in the payola scandal. 1961 – The "La Ronde" opens in Honolulu, first revolving restaurant in the United States. 1962 – The Chinese People's Liberation Army declares a unilateral ceasefire in the Sino-Indian War. 1964 – The Verrazano-Narrows Bridge opens to traffic. At the time it is the world's longest bridge span. 1964 – Second Vatican Council: The third session of the Roman Catholic Church's ecumenical council closes. 1967 – Vietnam War: American General William Westmoreland tells news reporters: "I am absolutely certain that whereas in 1965 the enemy was winning, today he is certainly losing." 1969 – U.S. President Richard Nixon and Japanese Premier Eisaku Satō agree on the return of Okinawa to Japanese control in 1972. The U.S. retains rights to bases on the island, but these are to be nuclear-free. 1969 – The first permanent ARPANET link is established between UCLA and SRI. 1970 – Vietnam War: Operation Ivory Coast: A joint United States Air Force and Army team raids the Sơn Tây prisoner-of-war camp in an attempt to free American prisoners of war thought to be held there. 1971 – Indian troops, partly aided by Mukti Bahini (Bengali guerrillas), defeat the Pakistan army in the Battle of Garibpur. 1972 – Voters in South Korea overwhelmingly approve a new constitution, giving legitimacy to Park Chung-hee and the Fourth Republic. 1974 – The Birmingham pub bombings kill 21 people. The Birmingham Six are sentenced to life in prison for the crime but subsequently acquitted. 1977 – Minister of Internal Affairs Allan Highet announces that the national anthems of New Zealand shall be the traditional anthem "God Save the Queen" and "God Defend New Zealand". 1979 – The United States Embassy in Islamabad, Pakistan, is attacked by a mob and set on fire, killing four. 1980 – A deadly fire breaks out at the MGM Grand Hotel in Paradise, Nevada (now Bally's Las Vegas). Eighty-seven people are killed and more than 650 are injured in the worst disaster in Nevada history. 1985 – United States Navy intelligence analyst Jonathan Pollard is arrested for spying after being caught giving Israel classified information on Arab nations. He is subsequently sentenced to life in prison. 1986 – National Security Council member Oliver North and his secretary start to shred documents allegedly implicating them in the Iran–Contra affair. 1992 – A major tornado strikes the Houston, Texas area during the afternoon. Over the next two days the largest tornado outbreak ever to occur in the US during November spawns over 100 tornadoes. 1995 – The Dayton Agreement is initialed at the Wright-Patterson Air Force Base, near Dayton, Ohio, ending three and a half years of war in Bosnia and Herzegovina. 1996 – Humberto Vidal explosion: Thirty-three people die when a Humberto Vidal shoe shop explodes. 2002 – NATO invites Bulgaria, Estonia, Latvia, Lithuania, Romania, Slovakia and Slovenia to become members. 2004 – The second round of the Ukrainian presidential election is held, giving rise to massive protests and controversy over the election's integrity. 2004 – Dominica is hit by the most destructive earthquake in its history. The northern half of the island sustains the most damage, especially the town of Portsmouth. In neighboring Guadeloupe, one person is killed. 2004 – The Paris Club agrees to write off 80% (up to $100 billion) of Iraq's external debt. 2006 – Anti-Syrian Lebanese politician and government minister Pierre Gemayel is assassinated in suburban Beirut. 2009 – A mine explosion in Heilongjiang, China kills 108. 2012 – At least 28 are wounded after a bomb is thrown onto a bus in Tel Aviv. 2013 – Fifty-four people are killed when the roof of a shopping center collapses in Riga, Latvia. 2013 – Massive protests start in Ukraine after President Viktor Yanukovych suspended signing the Ukraine–European Union Association Agreement. 2014 – A stampede in Kwekwe, Zimbabwe caused by the police firing tear gas kills at least eleven people and injures 40 others. 2015 – The government of Belgium imposed a security lockdown on Brussels, including the closure of shops, schools, public transportation, due to potential terrorist attacks. 2017 – Robert Mugabe formally resigns as President of Zimbabwe, after thirty-seven years in office.
0 notes
Text
Events 11.21
164 BC – Judas Maccabeus, son of Mattathias of the Hasmonean family, restores the Temple in Jerusalem. This event is commemorated each year by the festival of Hanukkah. 235 – Pope Anterus succeeds Pontian as the nineteenth pope. During the persecutions of emperor Maximinus Thrax he is martyred. 1009 – Lý Công Uẩn is enthroned as emperor of Đại Cồ Việt, founding the Lý dynasty. 1386 – Timur of Samarkand captures and sacks the Georgian capital of Tbilisi, taking King Bagrat V of Georgia captive. 1620 – Plymouth Colony settlers sign the Mayflower Compact (November 11, O.S.) 1676 – The Danish astronomer Ole Rømer presents the first quantitative measurements of the speed of light. 1783 – In Paris, Jean-François Pilâtre de Rozier and François Laurent d'Arlandes, make the first untethered hot air balloon flight. 1789 – North Carolina ratifies the United States Constitution and is admitted as the 12th U.S. state. 1832 – Wabash College is founded in Crawfordsville, Indiana. 1861 – American Civil War: Confederate President Jefferson Davis appoints Judah Benjamin Secretary of War. 1877 – Thomas Edison announces his invention of the phonograph, a machine that can record and play sound. 1894 – Port Arthur, China falls to the Japanese, a decisive victory of the First Sino-Japanese War; Japanese troops are accused of massacring the remaining inhabitants. 1902 – The Philadelphia Football Athletics defeated the Kanaweola Athletic Club of Elmira, New York, 39–0, in the first ever professional American football night game. 1905 – Albert Einstein's paper that leads to the mass–energy equivalence formula, E = mc², is published in the journal Annalen der Physik. 1910 – Sailors on board Brazil's warships including the Minas Geraes, São Paulo, and Bahia, violently rebel in what is now known as the Revolta da Chibata (Revolt of the Lash). 1916 – Mines from SM U-73 sink the HMHS Britannic, the largest ship lost in the First World War. 1918 – The Flag of Estonia, previously used by pro-independence activists, is formally adopted as the national flag of the Republic of Estonia. 1918 – A pogrom takes place in Lwów (now Lviv); over three days, at least 50 Jews and 270 Ukrainian Christians are killed by Poles. 1920 – Irish War of Independence: In Dublin, 31 people are killed in what became known as "Bloody Sunday". 1922 – Rebecca Latimer Felton of Georgia takes the oath of office, becoming the first female United States Senator. 1927 – Columbine Mine massacre: Striking coal miners are allegedly attacked with machine guns by a detachment of state police dressed in civilian clothes. 1942 – The completion of the Alaska Highway (also known as the Alcan Highway) is celebrated (however, the highway is not usable by standard road vehicles until 1943). 1945 – The United Auto Workers strike 92 General Motors plants in 50 cities to back up worker demands for a 30-percent raise. 1950 – Two Canadian National Railway trains collide in northeastern British Columbia in the Canoe River train crash; the death toll is 21, with 17 of them Canadian troops bound for Korea. 1953 – The Natural History Museum, London announces that the "Piltdown Man" skull, initially believed to be one of the most important fossilized hominid skulls ever found, is a hoax. 1959 – American disc jockey Alan Freed, who had popularized the term "rock and roll" and music of that style, is fired from WABC-AM radio over allegations he had participated in the payola scandal. 1961 – The "La Ronde" opens in Honolulu, first revolving restaurant in the United States. 1962 – The Chinese People's Liberation Army declares a unilateral ceasefire in the Sino-Indian War. 1964 – The Verrazano-Narrows Bridge opens to traffic. At the time it is the world's longest bridge span. 1964 – Second Vatican Council: The third session of the Roman Catholic Church's ecumenical council closes. 1967 – Vietnam War: American General William Westmoreland tells news reporters: "I am absolutely certain that whereas in 1965 the enemy was winning, today he is certainly losing." 1969 – U.S. President Richard Nixon and Japanese Premier Eisaku Satō agree on the return of Okinawa to Japanese control in 1972. The U.S. retains rights to bases on the island, but these are to be nuclear-free. 1969 – The first permanent ARPANET link is established between UCLA and SRI. 1970 – Vietnam War: Operation Ivory Coast: A joint United States Air Force and Army team raids the Sơn Tây prisoner-of-war camp in an attempt to free American prisoners of war thought to be held there. 1971 – Indian troops, partly aided by Mukti Bahini (Bengali guerrillas), defeat the Pakistan army in the Battle of Garibpur. 1972 – Voters in South Korea overwhelmingly approve a new constitution, giving legitimacy to Park Chung-hee and the Fourth Republic. 1974 – The Birmingham pub bombings kill 21 people. The Birmingham Six are sentenced to life in prison for the crime but subsequently acquitted. 1977 – Minister of Internal Affairs Allan Highet announces that the national anthems of New Zealand shall be the traditional anthem "God Save the Queen" and "God Defend New Zealand". 1979 – The United States Embassy in Islamabad, Pakistan, is attacked by a mob and set on fire, killing four. 1980 – A deadly fire breaks out at the MGM Grand Hotel in Paradise, Nevada (now Bally's Las Vegas). Eighty-seven people are killed and more than 650 are injured in the worst disaster in Nevada history. 1985 – United States Navy intelligence analyst Jonathan Pollard is arrested for spying after being caught giving Israel classified information on Arab nations. He is subsequently sentenced to life in prison. 1986 – National Security Council member Oliver North and his secretary start to shred documents allegedly implicating them in the Iran–Contra affair. 1992 – A major tornado strikes the Houston, Texas area during the afternoon. Over the next two days the largest tornado outbreak ever to occur in the US during November spawns over 100 tornadoes. 1995 – The Dayton Agreement is initialed at the Wright-Patterson Air Force Base, near Dayton, Ohio, ending three and a half years of war in Bosnia and Herzegovina. 1996 – Humberto Vidal explosion: Thirty-three people die when a Humberto Vidal shoe shop explodes. 2002 – NATO invites Bulgaria, Estonia, Latvia, Lithuania, Romania, Slovakia and Slovenia to become members. 2004 – The second round of the Ukrainian presidential election is held, giving rise to massive protests and controversy over the election's integrity. 2004 – Dominica is hit by the most destructive earthquake in its history. The northern half of the island sustains the most damage, especially the town of Portsmouth. In neighboring Guadeloupe, one person is killed. 2004 – The Paris Club agrees to write off 80% (up to $100 billion) of Iraq's external debt. 2006 – Anti-Syrian Lebanese politician and government minister Pierre Gemayel is assassinated in suburban Beirut. 2009 – A mine explosion in Heilongjiang, China kills 108. 2012 – At least 28 are wounded after a bomb is thrown onto a bus in Tel Aviv. 2013 – Fifty-four people are killed when the roof of a shopping center collapses in Riga, Latvia. 2013 – Massive protests start in Ukraine after President Viktor Yanukovych suspended signing the Ukraine–European Union Association Agreement. 2014 – A stampede in Kwekwe, Zimbabwe caused by the police firing tear gas kills at least eleven people and injures 40 others. 2015 – The government of Belgium imposed a security lockdown on Brussels, including the closure of shops, schools, public transportation, due to potential terrorist attacks.
0 notes