#i feel number urls are the most resilient of all
Explore tagged Tumblr posts
Text
i think about changing urls the way some people think of cutting bangs
#it'd be annoying to change links everywhere...#also then my site and itchio would be mismatched with my tumblr#changing my tt url from sth name based to a annihilation reference felt so fucking good#but that's an account i don't link anywhere so nothing broke#i came up with this guy bc i (age 15 or so) wanted sth a little more professional for my devart#and now im stuck with it...#it's literally not that deep tho i could very well find something new#^ doesn't even change their avatar#i think i'd go with sth like 'tower304'. i'm digging numbers#i feel number urls are the most resilient of all#i guess i could also go with torreinvertida i like that one a lot and j think yall can deal with a portuguese url#i think i'll microdose by changing my flight rising url lol#edit: im now towerofbabel over at fr. forgot about updating pinglists tho#well thats done#btw i need to wake up at 7 tomorrow. yay for 4 hours of sleep#at least i can sleep on the bus
3 notes
·
View notes
Note
♧ i want one 😡
send me a ♧
of course!!
You’re my: bestie, co-podcaster, most-consistently-talked-to-friend
How I met you: the zuko jesus/judas post (i don’t know what was happening tbh, and SOMEONE deleted it so....)
Why I follow you: other than the obvious, i appreciate that you clearly cúrrate your material. whenever i check in on your blog there’s only a few new posts, you put up a few quality posts instead of spam reblogging (i’m a spam reblogger tho so, no shade towards the many people i follow who do that)
Your blog is: relatable—full of great quotes and hard hitting posts, amazing queer stuff, bullying hella, and high quality fandom posts. also i love when you post about your life, it’s always great to hear about (yes even when it’s a complaint/rant, i enjoy knowing how you’re doing
Your URL is: funny. peak creativity. also we match (our names and then a number) which is cute
Your icon is: you!!! i literally smile everytime i see your icon. not even because i was there (and viiiiibing very much) when you drew it, but also just cause it’s so pretty and i love the bi pride and the fact that it’s YOU
A random fact I know about you: you have a rainbow shoebox in your closet and have been almost kidnapped multiple times
General opinion: i literally want to grab you by the shoulders and shake you because i literally see so so many people loving you because you’re so freaking amazing, but you can’t see it. which is insane. please, read this with your little voice that negates all my compliments turned OFF. read this with a voice that believes what it reads, or at the very least reads it neutrally. cause i promise i won’t write anything that isn’t true. you’re so resilient and strong (and if you can’t at least admit that, after all you’ve survived, than your mean inner voice has not turned off as requested). you are kind and patient (you’ve literally listened to me complain so often, you give amazing advice, and put up with how terrible i am at communicating). you’re beautiful (you literally are. your hair is gorgeous, you look so pretty without makeup and yet you’re so good at it and so you elevate your looks so much? and you’re so fashionable!!). you’re so fucking intelligent. and i know you don’t believe that but my reasoning is too important to even go into parentheses. first of all, if you weren’t book smart, that’d be okay cause you’re CLEARLY life, people, etc (aka the important types) smart. but you literally ARE traditionally intelligent too. abby, i literally spend my ENTIRE day working on schoolwork and i still don’t comprehend most of it. and you are able to spend just a few hours and still pass classes. do you understand how incredible that is?? i know you don’t, cause you’re always thinking you’re dumb when you’re literally not. (not to mention the fact that your brain literally makes it hard to study or sit in class or do homework, so even if you had a normal amount of time it would STILL be harder for you than it is for most people). you being in a shitty situation where you can’t dedicate the amount of time you want to to school work, doesn’t mean you’re not intelligent. the fact you’re still in school despite working essentially a full time job AND taking care of multiple children AND running a podcast AND continuing to talk to friends?? like, you don’t seem to realize how fucking spectacular that is but it really really truly is. because not only are you doing more than any one person should have to, but you’re doing each of those things so so well. literally, this is already so long and i didn’t even talk about how important you’ve been in my life or how much i love talking with you or so many other things you deserve to hear, but i’m trying to go to bed before midnight tonight so i’m gonna cut myself off. but please, abby, please do whatever you can to be neutral to yourself. i know being nice to yourself is probably too much to ask, but i just don’t like hearing you say so many terrible things about someone i love so so much. so everytime you start to think one of those self-deprecating thoughts, imagine a little boom with their water pistol going “NO ABBY’S AMAZING” cause i really hope one day you can see how incredible you really are
A random thought I have: grace and clara if you see this, i probably won’t be answering your asks yet cause i have some other things i want to do before bed. but no one is being ignored, im just bad at answering asks. (also Clara i think im ignoring yoy on multiple platforms, that’s just me being terrible at communicating. one of them was literally just me going ‘oh I’ll answer that in one second’ and now it’s been 48 hours so like. whoops. you’re probably not surprised but i do still feel bad cause i appreciate our friendship and ignoring people, intentionally or not, doesn’t exactly help portray that very much)
#ask a boomerang#abby tag#idk if this was coherent#the point was I love my friends very much#and everyone should send Abby compliments cause she’s very mean to herself and she doesn’t deserve itt
4 notes
·
View notes
Photo

Welcome (again) to A Cup-pella, MC! We’re excited to have you and Sugar Motta in the game! Please go through the checklist to make sure you’re ready to go and send in your account within the next 24 hours.
OOC INFO
Name + pronouns: Mr. Worldwide (MC), he/him Age: 26 Timezone: PST Ships: Sugar/Money, Sugar/Love Anti-Ships: Sugar/Humility
IC INFO
Full Name: Sugar Valentine Motta Face Claim: BABY V(anessa Lengies) Age/Birthday: 28, July 31st, 1991 Occupation: Socialite, Heiress, Producer of TUAP, Philanthropist, Entrepreneur Personality: Melodramtic. Idealistic. Uninhibited. Materialistic. Industrious Hometown: Newport, Rhode Island Bio:
Sugar Valentine Motta grew up with not a silver spoon in her mouth, but a gold, diamond encrusted one. Her father, Sullivan Motta, inherited his family’s jukebox business which was more lucrative during the 1950s than 2010. So with the money he already had, Sully started a mattress chain and thus, the Motta fortune continued to grow each day (with a little help from his side businesses that Sugar doesn’t find interesting or ask about). The Mottas were a family of three until her mother, Ginger, suddenly passed away from a brain aneurysm when Sugar was five. Despite living most of her life without her mother, she still feels a close bond with the woman she hardly knew. Of course, having only her dad around made Sugar into the definition of a daddy’s girl. But who wouldn’t be with a dad as rich and doting as Sully?
Sugar was born and raised primarily in Newport, Rhode Island, a city of not even 30,000 people known for its rich inhabitants, historical and large mansions, and boat ports filled to the brim with yachts. Being an only child and also the only (or more accurately, most important) women in her dad’s life made the heiress fiercely protective of him. More often than not, she tagged along with Sullivan on his business trips for apprising vintage and valuable jukeboxes or opening mattress stores in new cities or events for the luxury hotels and homes he had partnered a contract with. There were some trips he wouldn’t allow her to join, and while she would initially pout about it, Sugar would often just go take a trip of her own with one of her other wealthy friends instead. That became especially more-so when the Motta’s bought a private jet (what? it’s cheaper to fly that way. Probably).
Seeing how liked and respected Sullivan was due to how well he ran his businesses and how he would spare no expense to impress someone, Sugar herself adopted that trait. It seemed to be the Motta Motto to say: “If you got it, flaunt it" with the “it” usually being literal piles of cash With funds being at her disposal, and Sugar never being one to hide that fact, it was easy for her to make friends. Most of them were the kid’s of people her dad knew, rubbed elbows at parties with, or from a past business transaction. And while she knows that some of them just like her because of the money, she doesn’t particularly care. A friend is a friend after all, right? However, it’s because of that her romantic life sometimes suffers.
Next to money and her father, romance was near the top of the list as one of Sugar’s favorite things. She loved to be swooned, she loved the feeling of having a significant other to hold or be held, and to simply have someone to share life with. She had boyfriends in the past, but she was quick to understand that women caught her eye much more. One could only gush about how beautiful Lily Tomlin is so many times before the dots couldn’t avoid being connected. While liking girls didn’t give Sugar much pause, the intimacy that mutual attraction created with them did. She found she loved the romance, yet hesitated when it came to going “all the way” with someone. Being in the world of the rich, it felt like there was a hidden pressure to be the type to enjoy sex leisurely, especially since Sugar seemed to indulge in all other aspects of hedonism. It wasn’t like she hadn’t *tried* it, but she didn’t see what the big deal was. She liked getting to buy and wear the high end silk lingerie than have someone carelessly take it off. However, instead of admit to romantic partners that sex didn’t appeal to her as much as it did to others, she’d find ways to dance around the subject. Or, if all else failed, end relationships prematurely– even if she still harbored feelings for them. Sure, it would hurt for a little, but love was resilient. Love was kind. *And* love was easy to find if you had money. So at the end of the day, Sugar could rationalize that she was young, hot, and rich and therefore, there wasn’t really any reason to rush into anything with anyone. Finding true love young was so 2005 anyway (not that she wouldn’t celebrate every time one of her friends found it).
After graduating high school, Sugar moved to New York City, taking residence with her best friend and life partner Serena Smythe. She learned firsthand how vastly different it is to actually live in a city with millions of inhabitants instead of just visit one for fun, and in truth, Sugar had trouble finding her footing. She was lucky to be living with a friend when she first moved, but she refused to act as lost as she felt. Thankfully, she found that New York was full of people with ideas, and most of these ideas needed money for funding them. So with that, she started branching out into offering to produce or fund various projects for various people. As it turned out, while she loved impressing people with how much money she had, she found it much more rewarding to help create or better someone’s vision. That was even more true when she herself was involved in them. It was due to this that she went to Sully and told him she wanted to take over his Jukebox business, because she had the idea to start updating them too. It was clear her father was holding onto the past busiess, and Sugar knew she had a vision for its future. She wanted to have each jukebox get its own personal selection of classic hits along with songs from the last decade too– as long as it fit the Jukebox’s location. Sully couldn’t say no to his daughter, so he let her take the reigns mostly and as the numbers are showing, her idea is a hit among its clientele. It may be a small feat in the grand scheme of things, but it was something Sugar did mostly on her own and it has caused her to feel much more self assured in a new way that (surprisingly) money couldn’t buy.
Pets: None :~(
Relationships: N/A
EXTRA INFO
Twitter name/twitter URL/description:
Prin¢ess $ugs | locamotta | Someone once said to me “more money, more problems” but i don’t remember who since they had no money, and therefore, were not my prob 💁♀️💋
Five latest tweets:
@locamotta: #restinparadise coco cupid chanel motta. i miss waking up to ur sweet chirping every day. i know ur resting on the shoulder of the legit Coco up in heaven even if birds don’t normally get in. love u my sweet #CocoMo 😇🦜♥👩 😔😭🤧 06/12/10 - 01/20/19 @locamotta: going ✈ where the haters can’t find us #laterbitchez #sug&renatakemykonos @locamotta: snow in NY is fun until it touches the grimy streets and instantly becomes a health hazard #imynewport @locamotta: @buzzfeed I took ur “Which Iconic ‘90s Teen Girl Are You?” quiz and did NOT get cher horowitz I DEMAND JUSTICE FOR THIS!!!!!!!!!!!!!!!! #boycottbuzzfeed @locamotta: hey sugartwits, i’m feeling too sad to shop but not too sad to spend money: send in ur fave kickstarters and gofundmes so i can make myself happy pls!! dms are still NOT open #leavemealonebrad
4 notes
·
View notes
Text
Purchase Cheap Ape Flac Participant Lots From China Ape Flac Player Suppliers On Aliexpress.com
Learn how to convert APE to FLAC online with APE to FLAC Converter? Play FLAC on iPhone - It's really cool to benefit from the flawless high quality of FLAC on iPhone. Nonetheless, FLAC can't be opened on iPhone straight. Before enjoying FLAC on iPhone, you need to convert FLAC to compatible file codecs. One program you should utilize is the Apowersoft Free Online Video Converter for its nice convenience. Should you want an offline solution to transform FLAC, chances are you'll think about using Video Converter Studio that may modify recordsdata without shedding quality. Each of us might encounter problems when downloading audio tracks within the format of FLAC however it is incompatible with the participant. The reason being that the participant cannot decode FLAC. Importantly, with a view to decompress the FLAC files, we need to search for FLAC converter for converting FLAC to MP3, WAV and so forth. Under is a list of one of the best FLAC converter evaluate of 2018. We are going to speak about not only desktop programs but in addition online FLAC converter. Total Audio MP3 Converter converts APE to FLAC simply and shortly. The software helps more than ninety audio and video formats as enter, and converts to well-liked audio formats corresponding to AAC, AIFF, M4A, M4B, MP3, OGG, WAV, WMA, and so forth. If you want to convert your FLAC audio file with great and high-quality results, then Wondershare FLAC Converter is the perfect converter software program for your concern. It stands out among different video converter packages with 30X instances sooner pace with out quality loss. In the event you usually visit video-hosting websites like YouTube, you'll love their one-click download, which allows you to download movies instantly for offline playback. MediaHuman Audio Converter has a simple and straightforward-to-use interface, it lets you drag and drop the audio information you need transformed immediately into this system, choose an output format, after which start the conversion. What's more, it's is designed to work properly with iTunes, if all of your songs are based mostly on a Mac, this can be a versatile and reliable converter.
Whereas I am unable to answer on error "resilience" capabilities of flac vs. ape, I have seen that wavpack compression is much less efficient that both flac and ape. There's an option to use the identical folder the place your source information (APE) are saved. Alternatively, you possibly can choose any folder on your computer (1). You have to have sufficient privileges to create files within the chosen folder, otherwise the program will not be able to avoid wasting converted files. Utilizing , it's easy to transform APE files to a variety of different codecs. fre:ac is a free audio converter with numerous popular audio formats and encoders, also it is a CD ripper for Mac OS, you not solely can load the FLAC audio files, can also import MP3, WMA, AAC, etc. At the same time, you can rip your audio CDs to MP3 or WMA files. What's the file identify of the mac program that needs installing? I am operating debian and might't discover anything in the repositories that appears applicable. Compression Ratio: the difference between uncompressed and compressed file, applies to Lossless only, ape to flac converter free download full version 32 bit the decrease - the better.

Added changing Wav (PCM 8, 16, 24, 32 bits, DSP, GSM, IMA ADPCM, MS ADPCM, AC3, MP3, MP2, OGG, A-LEGISLATION, u-LAW) to FLAC information. In the Open Media dialog, click on on the Add button and browse to your music file. Then click on Open. LL2MP3 is a frontend utility that converts flac, ape and wav audio information to mp3. Completely different from other lossless codecs like WAV, FLAC is error resistant. Faasoft CUE Splitter is designed for each Home windows users and Mac customers to separate CUE related audio file like break up MP3 CUE, split FLAC CUE, break up M4A CUE, break up APE CUE, split WAV CUE, Break up OGG CUE, MPC, WV, TAK, TTA, AMR, AAC, AIFF, AU, RA, and so on. With it, you'll never have trouble in the best way to play lengthy audio recordsdata. For transcription purposes, MP3 is essentially the most optimum selection, especially for long recordings. It's going to each scale back the dimensions of the file and in flip cut back the uploading time, when you select to upload it to our site for transcription. I'm curious as to why that you must downgrade lossless music as you'll be able to burn ape or falc on cd's also. Merge several APE information into one FLAC file: Click "Merge" button to hitch a number of APE files into one big FLAC file. Šta je krajnji rezultat: audio ili information disk? Jer, ako režeš audio CD, onda nema potrebe da konvertuješ ape u flac jer softver svakako na kraju pravi CD-A format iz WAV-a koji raspakuje iz flac-a. There are many CUE Splitters out there online, nonetheless, most of them are solely compatible with Home windows. Usually, Mac customers can't find a technique to break up CUE related MP3, APE, WAV, FLAC, etc. What's extra, most of CUE Splitters support splitting only one or two sorts fairly than almost all common audio recordsdata with CUE sheet. Hamster is a free audio converter that installs quickly, has a minimal interface, and isn't laborious to use. PowerISO will begin converting the files to APE format. You may see the detailed progress information when changing. Sometimes you could get huge APE or www.audio-transcoder.com FLAC files containing complete albums. These information could come with small CUE files having the identical identify. If you want to convert such FLAC to particular person MP3 tracks, just start AudioConverter Studio and open the CUE file as an alternative of the massive FLAC or APE. This system will acknowledge the tracks, convert them to particular person files and save data like title, artist, etc. to ID3 tags of the converted MP3s. Both ID3v1 and ID3v2 variations of tags are supported.

Common ape flac participant of Good Quality and at Inexpensive Prices You'll be able to Buy on AliExpress. I all the time feel like I ought to have something good so as to add to this discussion, but the main lossless codecs are all good choices. Zamzar is an internet audio converter service that supports most typical music and audio formats. Just upload FLAC file from your laptop or enter a URL to a web based file, after converting, it could actually output WAV, MP3 information etc. We didn't find results for: Convert APE To FLAC (On-line. Attempt the recommendations beneath or sort a brand new query above. Yahoo gives you a variety of services for little or no value. We're prepared to do this as a result of our promoting revenue. This additionally makes it attainable to offer certain companies and content which may in any other case be unavailable to you through Yahoo corporations.
1 note
·
View note
Text
Deep Dive Architecture Comparison of DaaS & VDI, Part 1
In this two part blog series, I introduce the architecture behind Horizon DaaS and the recently announced Horizon 7. From a service provider point of view, the Horizon® family of products offers massive scale from both single-tenant deployments and multi-tenanted service offerings.
Many of you are very familiar with the term Virtual Desktop Infrastructure (VDI), but I don’t think the term does any justice to the evolution of the virtual desktop. VDI can have very different meanings depending on who you are talking to. Back in 2007 when VMware acquired Propero, which soon became VDM (then View and Horizon), VDI was very much about brokering virtual machines running a desktop OS to end-users using a remote display protocol. Almost a decade later, VMware Horizon is vastly different and it has matured into an enterprise desktop and application delivery platform for any device. Really… Horizon 7 is the ultimate supercar of VDI compared to what it was a decade ago.
I’ve read articles that compare VDI to DaaS but they all seem to skip this evolution of VDI and compare it to the traditional desktop broker of the past. DaaS on the other hand provides the platform of choice for service providers offering Desktops as a Service. DaaS was acquired in October 2013 (formerly Desktone). In fact I remember the day of the announcement because I was working on a large VMware Horizon deployment for a service provider at the time.
For this blog post I’d like to start our comparisons on the fundamental architecture of the Horizon DaaS platform to Horizon 7 which was announced in February 2016. This article is aimed at consultants and architects wishing to learn more about the DaaS platform.
Quick Comparison

As you can see in the table above, they look very similar. Thanks Ray, that helps a bunch! – Hey, no problem 📷
Horizon DaaS has been built from the ground up to be consumed by multiple tenants. This makes it attractive to service providers wanting to offer a consumption based desktop model for their customers (OPEX).
Horizon 7 on the other hand, which is also designed for massive scale (up to 50,000 sessions in a cloud pod), provides a single tenant architecture for multiple data centers. This suits organizations of any size hosting their own infrastructure.
It’s all well and good that we can host tens of thousands of desktops, but you are probably thinking “What about me? I only want to start with thirty desktops, maybe one hundred, but not thousands!”. We hear you loud and clear. Horizon DaaS scales for both the service provider infrastructure and tenants joining the service. Once the DaaS platform is deployed you can start with just a handful of desktops. Horizon 7, while a single-tenant solution uses a building block approach so you can scale from just a few to thousands of desktops. More on that later.
For customers that want to host infrastructure in their own data centers, but take advantage of the cloud then we have Horizon Air Hybrid-Mode. You may remember the announcement at VMworld 2015 with Project Enzo. You can also read more about Horizon Air Hybrid-Mode with this blog from Shikha Mittal, Snr. Product Line Manager.
Microsoft Licensing
I really don’t want to get into licensing, but I feel I need to dispel some myths that surround DaaS and VDI. Regardless of DaaS or VDI, if you are hosting a Windows desktop virtual machine (e.g. Windows 10) and want to provide remote access, then the Windows VM must be licensed. For that you have two options; Microsoft VDA (Virtual Desktop Access) or Software Assurance with Microsoft Volume licensing.
The VDA license is aimed at users with thin-clients that don’t have an existing Windows desktop PC, but want to remotely connect to a virtual desktop. The VDA license is tied to the client device.
In my opinion, the better option is Software Assurance (SA) which is part of a Microsoft Volume license agreement and is licensed per-user or per-device. Software Assurance includes virtual desktop access rights, so a VDA license is not required.
Now back in the day with ye old VDI, we only had support for virtual desktops, but for some time now Horizon supports both desktop virtual machines and Remote Desktop Session Host (RDSH) sessions. So regardless of DaaS or VDI, if you are a service provider offering session based desktops or applications then you can use the Microsoft SPLA (Service Provider Licensing Agreement) which is a monthly cost.
Horizon Architecture
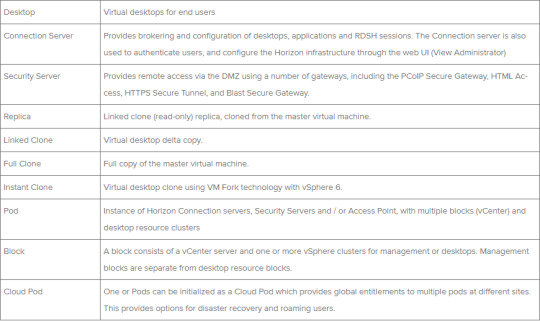
At the core of any VDI solution are the desktop brokers, and for Horizon 7 we call these Connection servers. A single Connection server can support up to 2,000 desktop or application sessions. Notice I said ‘up to‘, so you could run just a handful of desktops, being brokered by a single Connection server in the knowledge that you can scale this to 2,000 desktop or application sessions without adding more servers. That said, I really wouldn’t recommend deploying just a single Connection server outside of a demo, lab or PoC environment. If that server were to fail then your entire Horizon solution (we call that a Pod) can’t broker any more connections. I mentioned Pod, let’s take a look at some of the terminology used with Horizon 7.
A single pod supports up to 7 Connection servers, and we support up to 10,000 sessions per Pod. An entire Cloud Pod can handle up to 50,000 sessions. Looking back at a smaller deployment, adding two or more Connection servers provides resilience should a Connection server fail, and most smaller Horizon deployments typically start with two Connection servers for availability.
The diagram below represents what a single Pod may look like. Management components such as vCenter, Horizon servers and virtual appliances are hosted in a dedicated management cluster. Each desktop Block is delineated by a dedicated vCenter server, each hosting one or more desktop resource clusters.

I mentioned that a ‘Cloud Pod’ supports up to 50,000 sessions. Put simply, VMware recommend that each desktop Block (vCenter) hosts up to 2,000 desktop or application sessions. A single ‘Pod’ as shown in the diagram above can contain multiple desktop ‘Blocks’ in addition to the management Block, up to a maximum of 10,000 sessions.
Cloud Pod Architecture is a technology introduced in Horizon 6 that allows for multiple ‘Pods’ to be linked using VIPA (View Inter-Pod API). Users (or groups) can be assigned to virtual desktop or application pools using Global Entitlements. Therefore a ‘Cloud Pod’ can host up to 50,000 desktop or application sessions.
Remote Access
Remote access to the virtual desktop or application is catered for in two ways with Horizon 7. The first option is to use Security servers as shown in the diagram below. Think of these as a DMZ gateway service that facilitates external connections. Like the Connection server, a Security server is installed on a Windows Server OS. Each Security server you deploy must be paired with a Connection server. It is not recommended that you use Connection servers that are paired for external access, for internal access as well. Always dedicate Connection servers for your internal connections, and use Security/Connection server pairs for external connections.
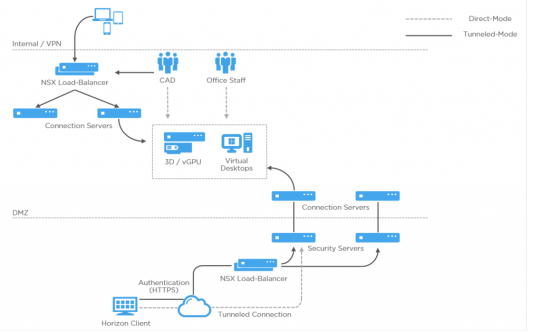
In the diagram above, internal connections either via VPN or within the company network will connect via a load-balancer. I’ve used an NSX load-balancer in this example, which sits in front of a pair of Connection servers. Once the user has authenticated via one of the Connection servers, the actual connection is direct from the Horizon Client to the virtual desktop or application. This is called direct-mode.
Using the same example above, external connections also hit the load-balancer first which sits in front of two or more Security servers. Once the user authenticates and selects a desktop or application, the Security server responds with its external URL. The Horizon Client will connect to the Security server’s external URL (public facing IP address). The remote display protocol is then forwarded from the Security server to the virtual desktop or application (not direct from the Horizon Client). This is called tunneled-mode.
Access Point is another option and can be used instead of Security servers. These are virtual appliances that have some major advantages, including the fact it doesn’t require pairing with the Connection server, and also its running a hardened Linux distribution. Many service providers are keen to use virtual appliances where possible as this avoids using additional Windows Server licenses, but also favors the use of Linux virtual appliances in the DMZ rather than Windows Servers.
Desktop Deployment Options
Horizon offers full clones, linked clones, and new with Horizon 7 are Instant Clones. Full clones use a template virtual machine in vCenter (our master) and a full clone desktop pool will contain a number of desktops that are full copies of the master (or parent) VM. They will have their own MAC address, computer name and IP address, but are otherwise full copies of the parent virtual machine. This is a good option for providing a dedicated desktop to someone that wants complete control, such as installing their own applications. However, it’s not the only option for the dedicated desktop.
Next we have ‘linked clones’. These are ideal for the non-persistent desktop where a master image is maintained and a number of linked clones are created based of the master. This differs to full clones in a number of ways. First, the linked clone technology is extremely efficient on storage space. Rather than simply cloning the master VM each time, it is linked, meaning that the linked clone VM contains the unique delta changes.
To make this possible, Horizon uses View Composer which is typically hosted on a dedicated Windows Server virtual machine.
The virtual machine disk is also constructed differently. When a linked clone desktop pool is created, the master virtual machine is cloned to a ‘replica’ virtual machine. The replica is a essentially a virtual disk that is used for read operations. As data is changed, the data is written to the delta virtual disk, unique to each virtual desktop.
The other advantage to linked clones is you have the option to refresh or even delete the virtual machine at log off. Next time the user logs in they get a fresh copy of the mater desktop image. This is a great option for maintaining corporate desktop standards.
Horizon 7 introduces another new technology called Instant Clones which when used in combination with App Volumes and User Environment Manager, allows for Just-in-Time desktops. You may remember at VMworld 2014 we announced VM Fork (aka Project Fargo), an exciting new technology that creates desktops in seconds. Providing you have vSphere 6 U1 or higher, Horizon 7 leverages this technology for Instant Clones. Instant Clones do not require View Composer.
RDSH Sessions
I mentioned earlier in this post about RDSH (Remote Desktop Session Host) sessions. Please don’t think of these as a second class citizen, apart from the obvious benefits of licensing, RDSH sessions can also provide the same rich user experience.
RDSH sessions can be deployed into both desktop or application pools, meaning that the end-user doesn’t necessarily have to launch a desktop session to access their applications. With further integration with Workspace ONE, end-users can open applications on any device with single sign-on (True SSO). You can learn more about Workspace ONE here.
Horizon 7 Terminology
Conclusion
In part 1 I introduced you to the Horizon 7 architecture and a typical single-tenant deployment using Pods and Blocks. In part 2, I will discuss the Horizon DaaS platform architecture and how this offers massive scale for multiple tenants in a service provider environment.
0 notes
Text
Marikina gets 136-bed quarantine facility from DPWH
#PHnews: Marikina gets 136-bed quarantine facility from DPWH
MANILA – The Marikina City government on Friday formally received its biggest quarantine facility from the Department of Public Works and Highways (DPWH).
DPWH Secretary Mark Villar personally turned over to Marikina Mayor Marcelino Teodoro the newly-completed 136-bed capacity quarantine facility for Covid-19 patients located along Kabayani Road in Barangay Nangka in a simple ceremony.
The facility consists of 37 container vans converted into isolation rooms, with each container van housing four individual rooms equipped with an air-conditioning system, beds, and comfort rooms.
The facility, which was completed recently, also has rooms for healthcare workers, medical equipment, and medical doctors and nurse stations.
With this additional facility, Marikina City now has eight Covid-19 emergency quarantine facilities---three in Amang Rodriguez Memorial Medical Center; one in Marikina Hotel; one in Marikina Convention Center; one bunker; and one in Marikina Sports Center
"With this facility, we will further lessen the number of cases of Covid-19,” Villar said in his speech.
Villar noted that such a project would not be possible without the 100 percent support from the city government, which provided the land for the quarantine facility.
"It is an honor for me to be here with one of the mayors I admire. Mayor Marcy is one of the most progressive mayors in the country. Non-stop talaga ang effort ni Mayor Teodoro sa (Mayor Marcy's efforts are non-stop in terms of) Covid-19 response,” he said. "Mayor Marcy, your city is the first to have a Covid-19 testing laboratory. You are always thinking one step ahead. You have a progressive and visionary leadership here in Marikina,” he added.
Since the start of the pandemic, Teodoro has underscored the importance of building a robust and resilient health delivery system in Marikina so the city can swiftly respond to health emergencies, such as the COVID-19 pandemic.
"Sa pagkakataong ito, ang mga quarantine at treatment facilities na mayroon tayo ngayon dito, sa ilalim ng programa ng ating Pangulong Rodrigo Duterte - Bayanihan to Heal as One ay tunay na mapapakinabangan ng lahat. Patuloy ang laban natin sa Covid-19. Totoo na unti-unti, sa pagtutulungan ng lahat, as we have a whole-of-government - a whole-of-community approach; nakikita natin ang pag-flatten ng curve ng Covid-19 sa Metro Manila (At this time, all quarantine and treatment facilities that we have right now are under the program of President Rodrigo Duterte - Bayanihan to Heal as One - which would really benefit everyone. Our battle against Covid-19 continues. True enough, through everyone's cooperation, as we have a whole-of-government - a whole-of-community approach; we can see the flattening of the curve Covid-19 in Metro Manila,” Teodoro said.
The mayor assured that the quarantine facility is compliant with the health and safety standards to avoid the transmission of the virus in the community, and protect the people from the disease.
“Sa mga pasilidad na ito ay mararamdaman natin na nandito ang pamahalaan; narito ang isang komunidad na nagtutulong-tulong laban sa Covid-19. (Through these facilities, we feel that there is a government on our side. There is a community that works together against Covid-19),” he added.
In response to the need of conducting Covid-19 testing, Marikina City was the first local government unit in the National Capital Region (NCR) to build its own molecular diagnostics laboratory capable of conducting reverse transcription-polymerase chain reaction (RT-PCR) tests or swab test.
RT-PCR is considered the “gold standard” for Covid-19 testing due to its high accuracy of detecting if a person has been infected with SARS-COV-2.
The city government has also foreseen the importance of establishing its own molecular diagnostic laboratory to boost its Covid-19 testing efforts and speed up the releasing of test results in order to stem the spread of the dreaded disease in the community and save precious lives.
Other officials present during the ceremony were DPWH-NCR Regional Director Ador Canlas and District Engr. Medel Chua, of Metro Manila 1st District Engineering Office. (PNA)
***
References:
* Philippine News Agency. "Marikina gets 136-bed quarantine facility from DPWH." Philippine News Agency. https://www.pna.gov.ph/articles/1120258 (accessed October 31, 2020 at 03:25AM UTC+14).
* Philippine News Agency. "Marikina gets 136-bed quarantine facility from DPWH." Archive Today. https://archive.ph/?run=1&url=https://www.pna.gov.ph/articles/1120258 (archived).
0 notes
Text
tagged by: @badwolfpinkandyellow
Rules: Answer 30 questions and tag 20 some people.
Nickname(s): Loki (I kid you not, this is a thing IRL.)
Gender: Genderqueer/genderfluid
Sign: Gemini
Height: 5′7″
Time: 11:38 pm
Birthday: Nope
Favorite Bands: The Ramones, Anti Flag, Rise Against (You may notice a bit of a trend here...)
Solo Artists: Ozuna, if I had to pick one.
Song stuck in my head: No Reason by Sum 41 and Despacito by Luis Fonsi and Daddy Yankee
Last show I watched: Bill Nye Saves the World (I am a 90s kid...)
When did I create this blog: A long time ago... I mean, this side blog is only about a year old, but I’ve had Jack for about 5 years.
What do I post: Doctor Who and Torchwood stuff and RP threads. This blog is much less political than Bucky’s...
What did I last google: kankara sanshin (Which is a variation of the Okinawan sanshin made of any type of wood and a metal can of some sort. It originated immediately post-WWII. Go look up its history if you want to both hate the entire concept of war and feel inspired by the sheer resiliency this thing represents. Or come ask me. I study Okinawan folk music and quite enjoy babbling about it.)
Other blogs: I have different blogs for nearly every character I RP, because that’s the only way I can keep track of everything. Which is a lot of characters. Most of them are on hiatus currently, though, because grad school. But here we go. I’ve got them grouped by series, with the main blog for each listed first and the others are side-blogs.
Doctor Who: @just-kept-running (9th and 10th Doctors), @redfieldsofgallifrey (multi-Master), @withwitandhope (8th Doctor), @exilesinthevortex (Shalka!Doctor and Master), and @companionsintimeandspace (EU companion multi-muse, currently Charley Pollard and C’rizz).
Marvel: @precise-desolation (Bucky Barnes), @chaos-and-cunning (Loki Laufeyson).
James Bond and London Spy: @londontowerraven (AU Q), @hermajestyshawk (AU James Bond), @fromrussiawithclaws (AU Alec Trevelyan), and @were-up-against-them-all (Danny Holt).
Supernatural and Good Omens: @scifisunshine (Charlie Bradbury), @cursedmanofletters (Sam Winchester), @ahunterandawarrior (Dean Winchester), @heavenlybookseller (Aziraphale), and @hellinabentley (Crowley).
Do I get asks: Every once in a blue moon. Which is why I tend to only post memes sporadically.
Why did I choose this URL: Originally, Jack’s URL had to do with his immortality, but I wanted something that encompassed both his past, his personality, and his immortality. And I remembered the episode where it was hinted that Jack was the Face of Boe, and that seemed to work.
Following: 154 (over on @just-kept-running)
Followers: 76
Average hours of sleep: Depends on the time of the semester.
Lucky number: 8
Instrument: Tuba, although I play (and own) a slew of instruments.
What am I wearing: TARDIS pj pants and a Supernatural sweatshirt. I am fandom trash.
Dream job: Public folklorist. I really want to be able to do research just for the joy of learning and of sharing knowledge.
Favorite Food: arroz con leche
Last book I read: I’m partway through several right now. Vampire Science (from the Eighth Doctor Adventure series) by Kate Orman and Johnathan Blum, Magic’s Pawn (from the Last Herald Mage series) by Mercedes Lackey, and A Gathering of Shadows (from the Shades of Magic series) by V.E. Schwab
3 favorite fandoms: Doctor Who, Marvel, and Fullmetal Alchemist, probably.
Tagging: @nochickflickmomentsmyass, @heretoboogie, @theeldritchmortician, @hearstime, @soullessbobbysinger, whoever wants to do this, really...
2 notes
·
View notes
Note
Hello, my url is saltbearthekitten (I am a sideblog). I'm trying to pile together some psychological studies (links to, more like, but you get the drift) that can support our arguments. For ex: I've seen antis excusing their abusive behavior by claiming that they were abused, like being abused cannot in the end turn out an abuser. I want to help provide evidence to dispute these claims. Do you have any good readings you would recommend? Your blog is very refreshing and I binge read your posts.
I will make an effort to find an answer to the question “Can victims of abuse become abusers?”. It’s a 2226-words-long effort, so I’m putting it under a ‘read more’.
tl;dr: yeah, sure - but anyone can become an abuser or someone displaying abusive/manipulative behavior; there are people more likely to do so; meanwhile children/adolescents who have suffered child abuse or have been exposed to domestic violence are considerably more likely to display internalized/externalized behavioral issues - such as depression, anxiety, trauma, aggression, manipulative behavior.
“The Line between Victims and Abusers“ by Steven Stosny makes for insightful reading, but it’s a little dated (2009), and I don’t entirely agree with some of the patronizing wording. It still draws an interesting line between victims and abusers, and points out how victims can become abusive in their behavior.
“The victim protection movement began as a noble attempt to counteract the most insidious aspect of the abusive dynamic - blaming the victim, which has the effect of making the victim feel ashamed of being abused. But as is the case with all effective social movements, the pendulum has swung too far the other way. We now have a victim identity movement, fueled by an industry of self-help authors and advocates, that has conferred a certain status to being a victim and thereby blurred the line between victims and abusers.”
Note: This article is a think piece. Very strictly speaking, it doesn’t count as scientific data. The author seems quite proficient in his field though, hence why I’d argue it’s still representative of the subject.
I’m noticing there’s also a bit of a problem with the question you’re asking. When you ask “Can a victim of abuse become an abuser?”, the only possible answer to that is ‘yes’, because the subject of abuse isn’t strictly a matter of personal history. It’s also a matter of likelihood, plausibility and circumstance, as well as mental health, among other factors. It is entirely possible for a victim to become an abuser, for them to develop abusive mannerism and behavior, and for their ‘status’ as a victim to manifest itself in abusive coping mechanisms and/or mannerism and behavior that is similar to abusive mannerisms and behavior, but not the same. The question should rather be “Can anyone become an abuser?”, to which the answer is also ‘yes’. There are stages and degrees of abuse, and it’s not always equally severe, or even noticeable. Another question worth asking would be “What is abuse?” or “What is abusive behavior?”.
“Abusive power and control” (wikipedia article) gives a general overview in regards to how abusers gain and maintain control.
Here’s a very small excerpt,
Braiker identified the following ways that manipulators control their victims:[3]
- Positive reinforcement: includes praise, superficial charm, superficial sympathy (crocodile tears), excessive apologizing, money, approval, gifts, attention, facial expressions such as a forced laugh or smile, and public recognition.
- Negative reinforcement: involves removing one from a negative situation as a reward, e.g. "You won't have to do your homework if you allow me to do this to you."
- Intermittent or partial reinforcement: Partial or intermittent negative reinforcement can create an effective climate of fear and doubt. Partial or intermittent positive reinforcement can encourage the victim to persist.
- Punishment: includes nagging, yelling, the silent treatment, intimidation, threats, swearing, emotional blackmail, the guilt trip, sulking, crying, and playing the victim.
- Traumatic one-trial learning: using verbal abuse, explosive anger, or other intimidating behavior to establish dominance or superiority; even one incident of such behavior can condition or train victims to avoid upsetting, confronting or contradicting the manipulator.
Manipulators may have:[3]
- a strong need to attain feelings of power and superiority in relationships with others
- a want and need to feel in control
- a desire to gain a feeling of power over others in order to raise their perception of self-esteem.
Personality psychology also appears to play a considerable role,
In the study of personality psychology, certain personality disorders display characteristics involving the need to gain compliance or control over others:[10]
Those with antisocial personality disorder tend to display a glibness and grandiose sense of self-worth. Due to their shallow affect and lack of remorse or empathy, they are well suited to con and/or manipulate others into complying with their wishes.
Those with histrionic personality disorder need to be the center of attention; and in turn, draw people in so they may use (and eventually dispose of) their relationship.
Those with narcissistic personality disorder have an inflated self-importance, hypersensitivity to criticism and a sense of entitlement that compels them to persuade others to comply with their requests.
To maintain their self-esteem, and protect their vulnerable true selves, narcissists need to control others' behavior – particularly that of their children seen as extensions of themselves.[11]
Once more, the goal should rather be to identify abusive behavior. It’s not to find an absolute answer to the question “Who can or can’t be an abuser?”.
If you were to ask the question “Does a number of antis display abusive behavior?” my answer would be - yes, absolutely yes, holy fuck do they ever, yes. Not to mention that the ‘antis’ displaying said behavior then proceed to victim-blame/shame, seeing as how ‘antis’ firmly believe that their victims absolutely deserve being abused.
I could easily write an entire post about that alone, and I probably should.
Another aspect of the ‘Can victims become abusers?’ question would be the
“Abuse Defense” (wikipedia article), which describes the following,
The abuse defense is a criminal law defense in which the defendant argues that a prior history of abuse justifies violent retaliation. While the term most often refers to instances of child abuse or sexual assault, it also refers more generally to any attempt by the defense to use a syndrome or societal condition to deflect responsibility away from the defendant. Sometimes the concept is referred to as the abuse excuse, in particular by the critics of the idea that guilty people may use past victimization to diminish the responsibility for their crimes.[1]
When the abuser is the victim of the crime, as is often the case, the abuse excuse is sometimes used as a way to "put the victim on trial".
The Supreme Court of the United States has held on numerous occasions that the defendant should be permitted to present any information that they feel might affect sentencing. Despite this legal precedent, the availability of the abuse defense has been criticized by several legal experts, particularly in the aftermath of the trials of Lorena Bobbitt and the Menendez brothers. Legal scholar Alan Dershowitz has described the abuse excuse as a "lawless invitation to vigilantism".
Interestingly enough, this law is meant to take the dynamic between the abuser and the victim into consideration (and even then it’s highly contended). It does not refer to victims of abuse lashing out against people that were not implicit in their abuse.
“Behavioural consequences of child abuse” is a fairly recent (2013) research study, which describes how any type of abuse can affect children and adolescents in how they express themselves (- arguably, when left untreated, those behavioral issues might be carried over into adulthood).A small excerpt:
Effects of violence and neglect on attachment and brain development
A strong and secure attachment bond with a primary caregiver is the core of developing resilience and a healthy personality.7,8 It strengthens a child’s ability to cope with stress, regulates emotions, provides social support, and forms nurturing relationships.9 The world is experienced as a safe place in which to explore and develop independence. The child finds comfort and support from his or her caregiver when under stress. When children are abused, they might display disturbed forms of attachment and abnormal patterns of emotional response toward their caregivers. This might subsequently lead to a serious attachment disorder with symptoms such as those shown in Box 1.5–8
Box 1.Symptoms of attachment disorderThe following are symptoms of attachment disorder.
- An aversion to touch and physical affection: The child might flinch, laugh, or even say “ouch” when touched; rather than producing positive feelings, touch and affection are perceived as threats
- Control issues: The child might go to great lengths to prevent feeling helpless and remain in control; such children are often disobedient, defiant, and argumentative
- Anger problems: Anger might be expressed directly, in tantrums or acting out, or through manipulative, passive-aggressive behavior; the child might hide his or her anger in socially acceptable actions, like giving a high-5 that hurts or hugging someone too hard
- Difficulty showing genuine care and affection: The child might act inappropriately affectionate with strangers while displaying little or no affection toward his or her parents
- An underdeveloped conscience: The child might act like he or she does not have a conscience and might fail to show guilt, regret, or remorse after behaving badly
Finally, “The Effects of Child Abuse and Exposure to Domestic Violence on Adolescent Internalizing and Externalizing Behavior Problems”is another fairly recent (2010) study based on the “Lehigh Longitudinal Study”, ‘a prospective study of children and families begun in the 1970s to examine developmental consequences of child maltreatment’.
Abstract
“Results show that child abuse, domestic violence, and both in combination (i.e., dual exposure) increase a child’s risk for internalizing and externalizing outcomes in adolescence. When accounting for risk factors associated with additional stressors in the family and surrounding environment, only those children with dual exposure had an elevated risk of the tested outcomes compared to non-exposed youth. However, while there were some observable differences in the prediction of outcomes for children with dual exposure compared to those with single exposure (i.e., abuse only or exposure to domestic violence only), these difference were not statistically significant. Analyses showed that the effects of exposure for boys and girls are statistically comparable.”
Objectives and Rationale“In summary, the current study examines several outcomes in adolescence with known links to child adversity -- a range of internalizing and externalizing behaviors, depression, and delinquency. We hypothesize that: (1) violence exposure will increase a child’s risk for these outcomes, and (2) youth exposed to both child abuse and domestic violence will show an elevated risk for these outcomes over either type of abuse alone. Finally, we explore the role of gender as a possible moderator of childhood exposure on later outcomes in adolescence. The gender-balanced sample and longitudinal design of the current study allow tests of developmental relationships that are not possible in studies with cross-sectional data or in studies with only one gender.”
Relation between Child Abuse and Adverse Psychosocial Outcomes
“Numerous studies have demonstrated that experiencing child abuse can lead to a range of internalizing and externalizing behavior problems. For example, research has shown that abused children can exhibit a variety of psychological problems, including anxiety and depression (McLeer, Callaghan, Henry, & Wallen, 1994; McLeer et al., 1998). The effects of being abused persist into adolescence; teens who were abused as children are more likely to experience depression and other internalizing problems (Fergusson, Horwood, & Lynskey, 1996; Widom, 2000; Wolfe, 1999; Wolfe, Scott, Wekerle, & Pittman, 2001). Teens who were abused as children are also more likely to exhibit externalizing behavior problems, such as delinquency and violence perpetration (Fergusson et al., 1996; Fergusson & Lynskey, 1997; Hawkins et al., 1998; R. Herrenkohl, Egolf, & E. Herrenkohl, 1997; McCabe, Lucchini, Hough, Yeh, & Hazen, 2005; Smith & Thornberry, 1995; Widom, 2000; Wolfe, 1999).”
Relation Between Domestic Violence Exposure and Adverse Psychosocial Outcomes
“Exposure to domestic violence in childhood has been linked to a similar set of outcomes, including low self-esteem, social withdrawal, depression, and anxiety (Edleson, 1999; Fantuzzo, Boruch, Beriama, Atkins, & Marcus, 1997; Graham Bermann, 1998; Hughes, 1988; Lichter & McCloskey, 2004; Litrownik, Newton, Hunter, English, & Everson, 2003; McCloskey, Figueredo, & Koss, 1995; McCloskey & Lichter, 2003; Moffitt & Caspi, 2003; Sudermann & Jaffe, 1997); and aggression, violence, and delinquency (Herrera & McCloskey, 2001; Lichter & McCloskey, 2004; Litrownik et al., 2003; McCloskey & Lichter, 2003; Sudermann & Jaffe, 1997). In a recent meta-analysis of studies that examined the relationship between domestic violence exposure in childhood and adolescent internalizing and externalizing behaviors, Evans, Davies, and DiLillo (2008) found significant mean-weighted effect sizes of .48 (SE=.04) for internalizing behaviors and .47 (SE=.05) for externalizing behaviors, indicating moderate associations between exposure and both outcomes.”
Discussion“As hypothesized, children exposed to violence (either child abuse, domestic violence, or both) had higher levels of externalizing and internalizing behavior problems in adolescence than those exposed to neither form of violence. Youths who had both witnessed domestic violence and had been direct victims of child abuse (i.e., dual exposure) were more consistently at risk for the entire range of internalizing and externalizing behavior problems investigated than those who experienced only one form of violence exposure. In fact, dual violence exposure was predictive of higher scores on all nine outcomes addressed in this study, while experiencing child abuse alone or domestic violence alone was significantly predictive of only some of the outcomes. A direct comparison of dual and single exposures found that for two outcomes-- delinquency and depression measured by the BDI—scores were higher for those with both abuse and domestic violence exposure. The effect of dual exposure on depression was maintained after accounting for other risks in the family and surrounding environment.“
So, essentially, and I’m breaking it down very simplistically here - victims of any type (or many types) of abuse can very likely display characteristically abusive behavior, and they’re even more prone to do so than those who have not suffered any type of abuse (or fewer types of abuse). That is not to say that they are inherently bound to become abusers themselves, but they are highly prone to aggressive behavior, as well as abusive/manipulative behavior.
36 notes
·
View notes
Text
Recently, I've been tagged in so many posts I thought I'd compile them all together and do them all at once! Under the cut because I imagine this is going to get quite long. Tagged by @coffeesforstudents @colllegeruled @penandanotebook @raineydaystudies and @interestingly-pale , thank you all of you! ^_^
Edit: OKAY. That’s a lot of questions. If you want to answer them, gof or it and please tag me! I’d love to get to know some of you more :D
ABOUT ME:
Name: Aimee Nickname: Aims (though I hate it), Google Gender: Female Star Sign: Gemini Height: 157cm Sexual Orientation: I think I'm demisexual but to be honest, my relationship life is really confusing for various reasons Hogwarts House: Ravenclaw Cats or Dogs? Dogs? Have you met me? Coffee or Tea? Tea. Obviously.
MORE ABOUT ME:
How many blankets do you sleep with? Generally two at the moment. And an electric blanket if I'm not with W. I get cold so easily. Which animal best represents your personality? I'm not sure... I swear my personality at the moment is fluctuating so much, I really don't know. @studiousmedic is probably easier to ask about this Which song makes you feel like you can conquer the world? Where No One Goes - Jonsi Make a book recommendation. When Breath Becomes Air - Paul Kalanithi. I cannot recommend it enough. Countries that you would absolutely love to travel to? Spain, Italy, China, Bulgaria, Croatia. Name three items from your bucket list. I don’t actually have one. I found when I was ill it just made life so much worse, all these things I wasn’t going to achieve? At the moment though, I’m working on getting my base skills better in acroyoga, knitting scarves for my friends and working towards my A Levels. Name three things you like about yourself. Resilience, my hair, and ability to eat a tonne of sweet potatoes in one sitting. Languages that you would like to learn? Spanish. French. Italian. Russian. Mandarin Chinese. Japanese. Polish. Icelandic. Favourite subject in elementary school? Music and Dance. What’s your favourite season and favourite time of day? Summer. Either early morning in the summer when the light is filtering through and I shouldn’t be awake or 1am when my productivity hits peak.
AT THE MOMENT: Time right now: 20.42 Song stuck in my head: All We Do - Oh Wonder What am I wearing right now: Yoga leggings, a green loose shirt that I can’t really describe? Last movie I watched? Star Wars: The Force Awakens. Carrie <3 Last song I listened to? Magnificat - Arvo Part Last book I read? Currently reading Atonement again for English Lit. Last thing I ate? After this I’m gonna get some yogurt, honey and fruit? Last thing I Googled: Krebs If you could be anywhere right now, where would you be? On a sofa that isn’t mine. Where would you want to time travel to? Victorian times, probably.
FAVOURITES: Favourite animal: Dragons? Favourite colour: Blues and purples.Sometimes deep reds. Favorite Fictional Character: Violet Baudelaire, Hermione Granger. Favorite Singer/Band: At the moment, Arctic Monkeys. Which movies can you watch over and over again? Harry Potter, Hannibal Lecter series. Fictional character you would hang out with for a day? Amelia Shepherd.
DREAMS:
Dream Trip: The world. Dream Job: Surgeon.
BLOGGING:
When was this blog created? December 2014 What kind of stuff do I post? I don’t know, stuff? It’s become sporadic recently. I don’t have a particular alignment to what I want to post/reblog at the moment. Do I have any other blogs? I do but sssssssh. Do I get asks frequently? I do actually, yes! Most I answer privately and messages obviously private too. ^_^ Current number of followers: 1069 What made you decide to make a Tumblr?: Several years ago in 2009 or 2008 I think when I was part of an online writing group and it was the cool thing to do. Why did you pick your URL: it’s similar to my other URL on here, but with an emphasis on study. my old science tumblr though was literatureoftruth because that’s what science is to me. When did your blog reach it's peak? I mean, whenever @studiousmedic decides to go on a reblogging spree to be honest.
5 notes
·
View notes
Text
Version 442
youtube
windows
zip
exe
macOS
app
linux
tar.gz
I had a great week. An important part of GUI Sessions is overhauled, which should save a lot of hard drive time for larger clients.
gui sessions
I always encourage a backup before you update, but this week it matters more than normal. If you have a client with large sessions with many important things set up, make sure you have a backup done before you update! I feel good about the code, and I try to save data on various failures, but if your situation gives errors for an unforeseen reason, having the backup ready reduces headaches all around!
Like the subscriptions and network objects breakups I've done in the past year, I 'broke up' the monolithic GUI Session object this week. Now, when your session has changes, only those pages that have changed will be saved, saving a ton of CPU and HDD write I/O. Furthermore, sessions that share duplicate pages (this happens all the time with session backups), can now share that stored page, saving a bunch of hard drive space too. Like with subscriptions, some users are pushing multiple gigabytes of session storage total, so there is a good amount of work to save here.
You don't have to do anything here. Everything works the same on the front end, and all your existing sessions will be converted on update. Your client should be a little less laggy at times, and client shutdown should be a bit faster.
If any of your old sessions fail to load or convert, a backup will be made so we can check it out later. Let me know if you have any trouble!
Advanced stuff:
Another benefit is the old limit of 'sessions fail to save at about 500k session weight' now applies to pages individually. Please don't immediately try to nuke your sessions with five million new things, but if you do end up with a big session, let me know how other performance works out for you. Now this bottleneck is gone, we'll start hitting new ones. I believe the next biggest vulnerability is thread starvation with many simultaneous downloaders, so again please don't paste-spam a hundred now queries (for now).
If you have been tracking session weight (under the pages menu), I am rebalancing the weights. Before, the weight was file = 1, URL = 1, but after all our research into this, I am setting it to file = 1, URL = 20. In general, I think a page will fail to save at the new weight of about 10 million. If you are in advanced mode, you can now see each page's weight on page tab right-clicks. Let's get a new feeling for IRL distribution here, and we can aim for the next optimisation (I suspect it'll eventually be a downloader-page breakup, storing every query or watcher as a separate object). Since URLs seem to be the real killer, too, see if you can spread bigger downloads across multiple download pages and try to clear out larger completed queries when you can.
the rest
I did a bunch of little stuff--check the changelog if you are interested.
I have also turned off the interval VACUUM maintenance and hidden the manual task for now. This was proving less and less useful in these days of huge database files, so I will bring it back in future on a per-file basis with some UI and more specific database metadata.
EDIT: Thanks to a user submission, yande.re post parser is updated to pull tags correctly if you are logged in. I hoped my update code would move the link over from the old parser correct, but it did not. I'll fix this for next week, but if you download from yande.re while logged in, please hit ''network->downloader components->manage url class links'' and move 'yande.re file page' from moebooru to 'yande.re post page parser'.
We fixed a couple more problems with the new builds--the Linux and Windows extract builds have their surplus 'ubuntu'/'windows' directories removed, and the Linux executables should have correct permissions again. Sorry for the trouble!
And after some tests, we removed the .py files and the source from the builds. I long-believed it was possible to run the program from source beside the executables, but it seems I was mistaken. Unless you are running the build-adjacent source pretty much on the same machine you built on (as my tests years ago were), you get dll conflicts all over the place. If you want to run from source, just extract the source proper in its own fresh directory. I've also fleshed out the 'running from source' help beyond setting up the environment to talk more about the actual downloading and running of the program. I'll continue work here and hope to roll out some easy one-and-done setup scripts to automate the whole thing.
full list
gui sessions:
gui sessions are no longer a monolithic object! now, each page is stored in the database separately, and when a session saves, only those pages that have had changes since the last save are written to db. this will massively reduce long-term HDD writes for clients with large sessions and generally reduce lag during session save intervals
the new gui sessions are resilient against database damage--if a page fails to load, or is missing from the new store, its information will be recorded and saved, but the rest of the session will load
the new page storage can now be shared across sessions. multiple backups of a session that use the same page now point to the same record, which massively reduces the size of client.db for large-sessioned clients
your existing sessions and their backups will obviously be converted to the new system on update. if any fail to load or convert, a backup of the original object will be written to your database directory. the conversion shouldn't take more than a minute or two
the old max-object limit at which a session would fail to save was around 10M files and/or 500k urls total. it equated to a saved object of larger than 1Gb, which hit an internal SQLite limit. sessions overall now have no storage limit, but individual pages now inherit the old limit. Please do not hurry to try to test this out with giganto pages. if you want to make do a heap of large long-term downloaders, please spread the job across several pages
it seems URLs were the real killer here, so I am rebalancing it so URLs now count for 20 weight each. the weight limit at which point a _page_ will now fail to save, and the client will start generally moaning at you for the whole session (which can be turned off in the options), is therefore raised to 10M. most of the checks are still session-wide for now, but I will do more work here in future
if you are in advanced mode, then each page now gives its weight (including combined weight for 'page of pages') from its tab right-click menu. with the new URL weight, let's get a new sense of where the memory is actually hanging around IRL
the page and session objects are now more healthily plugged into my serialisation system, so it should be much easier to update them in future (e.g. adding memory for tag sort or current file selection)
.
the rest:
when subscriptions die, the little reporting popup now includes the death file velocity ('it found fewer than 1 files in the last 90 days' etc...)
the client no longer does vacuums automatically in idle time, and the soft/full maintenance action is removed. as average database size has grown, this old maintenance function has increasingly proved more trouble than it is worth. it will return in future as a per-file thing, with better information to the user on past vacuums and empty pages and estimates on duration to completion, and perhaps some database interrupt tech so it can be cancelled. if you really want to do a vacuum for now, do it outside the program through a SQLite intepreter on the files separately
thanks to a user submission, a yande.re post parser is added that should grab tags correct if you are logged in. the existing moebooru post parser default has its yande.re example url removed, so the url_class-parser link should move over on update
for file repositories, the client will not try to sync thumbnails until the repository store counts as 'caught up' (on a busy repo, it was trying to pull thumbs that had been deleted 'in the future'). furthermore, a 404 error due a thumb being pulled out of sync will no longer print a load of error info to the log. more work will be needed here in future
I fixed another stupid IPFS pin-commit bug, sorry for the trouble! (issue #894)
some maintenance-triggered file delete actions are now better about saving a good attached file delition reason
when the file maintenance manager does a popup with a lot of thumbnail or file integrity checks, the 'num thumbs regenned/files missing or invalid' number is now preserved through the batches of 256 jobs
thoroughly tested and brushed up the 'check for missing/invalid files' maintenance code, particularly in relation to its automatic triggering after a repository processing problem, but I still could not figure out specifically why it is not working for some users. we will have to investigate and try some more things
fixed a typo in client api help regarding the 'service_names_to_statuses_to_display_tags' variable name (I had 'displayed' before, which is incorrect)
.
build fixes:
fixed the new Linux and Windows extract builds being tucked into a little 'ubuntu'/'windows' subfolder, sorry for the trouble! They should both now have the same (note Caps) 'Hydrus Network' as their first directory
fixed the new Linux build having borked permissions on the executables, sorry for the trouble!
since I fixed the urllib3 problem we had with serialised sessions and Retry objects, I removed it from the requirements.txts. now 'requests' can pull what it likes
after testing it with the new build, it looks like I was mistaken years ago that anyone could run hydrus from source when inside a 'built' release (due to dll conflicts in CWD vs your python install). maybe this is now only true in py3 where dll loading is a little different, but it was likely always true and my old tests only ever worked because I was in the same/so-similar environment so the dlls were not conflicting. in any case the builds no longer include the .py/.pyw files and the 'hydrus' source folder, since it just doesn't seem to work. if you want to run from source, grab the actual source release in a fresh, non-conflicting directory. I've updated the help regarding this, sorry for any trouble or confusion you have ever run into here
updated the running from source document to talk more about actually getting the source and fleshed out the info about running the scripts
.
misc boring refactoring and db updates:
created a new 'pages' gui module and moved Pages, Thumbs, Sort/Collect widgets, Management panel, and the new split Session code into it
wrote new container objects for sessions, notebook pages, and media pages, and wrote a new hash-based data object for a media page's management info and file list
added a table to the database for storing serialised objects by their hash, and updated the load/save code to work with the new session objects and manage shared page data in the hashed storage
a new maintenance routine checks which hashed serialisables are still needed by master containers and deletes the orphans. it can be manually fired from the _database->maintenance_ menu. this routine otherwise runs just after boot and then every 24 hours or every 512MB of new hashed serialisables added, whichever comes first
management controllers now discard the random per-session 'page key' from their serialised key lookup, meaning they serialise the same across sessions (making the above hash-page stuff work better!)
improved a bunch of access and error code around serialised object load/save
improved a heap of session code all over
improved serialised object hashing code
next week
I have one more week of work before my vacation. There's a ton of little jobs I have been putting off--checking new downloaders users sent in, some more help docs to work on, and magically growing multi-column list dialogs--as well as emails and other messages I haven't got to. I'll try to tidy up those loose ends as best I can before I take my break. I'll also deal with any problems with these new GUI Sessions.
1 note
·
View note
Text
Chapter 2: Browsers
Previously in web history…
Sir Tim Berners-Lee creates the technologies behind the web — HTML, HTTP, and the URL which blend hypertext with the Internet — with a small team at CERN. He convinces the higher-ups in the organizations to put the web in the public domain so anyone can use it.
Dennis Ritchie had a problem.
He was working on a new, world class operating system. He and a few other colleagues were building it from the ground up to be simple and clean and versatile. It needed to run anywhere and it needed to be fast.
Ritchie worked at Bell Labs. A hotbed of innovation, in the 60s, and 70s, Bell employed some of the greatest minds in telecommunications. While there, Ritchie had worked on a time-sharing project known as Multics. He was fiercely passionate about what he saw as the future of computing. Still, after years of development and little to show for it, Bell eventually dropped the project. But Ritchie and a few of his colleagues refused to let the dream go. They transformed Multics into a new operating system adaptable and extendable enough to be used for networked time sharing. They called it Unix.
Ritchie’s problem was with Unix’s software. More precisely, his problem was with the language the software ran on. He had been writing most of Unix in assembly code, quite literally feeding paper tape into the computer, the way it was done in the earliest days of computing. Programming directly in assembly — being “close to the metal” as some programmers refer to it — made Unix blazing fast and memory efficient. The process, on the other hand, was laborious and prone to errors.
Ritchie’s other option was to use B, an interpreted programming language developed by his co-worker Ken Thompson. B was much simpler to code with, several steps abstracted from the bare metal. However, it lacked features Ritchie felt were crucial. B also suffered under the weight of its own design; it was slow to execute and lacked the resilience needed for time-sharing environments.
Ritchie’s solution was to chose neither. Instead, he created a compiled programming language with many of the same features as B, but with more access to the kinds of things you could expect from assembly code. That language is called C.
By the time Unix shipped, it had been fully rewritten in C, and the programming language came bundled in every operating system that ran on top of it, which, as it turned out, was a lot of them. As more programmers tried C, they adapted to it quickly. It blended, as some might say, perfectly abstract functions and methods for creating predictable software patterns with the ability to get right down to the metal if needed. It isn’t prescriptive, but it doesn’t leave you completely lost. Saron Yitabrek, host of the Command Heroes podcast, describes C as “a nearly universal tool for programming; just as capable on a personal computer as it was on a supercomputer.”
C has been called a Swiss Army language. There is very little it can’t do, and very little that hasn’t been done with it. Computer scientist Bill Dally once said, “It set the tone for the way that programming was done for several decades.” And that’s true. Many of the programming paradigms developed in the latter half of the 20th century originated in C. Compilers were developed beyond Unix, available in every operating system. Rob Pike, a software engineer involved in the development of Unix, and later Go, has a much simpler way of putting it. “C is a desert island language.”
Ritchie has a saying of his own he was fond of repeating. “C has all the elegance and power of assembly language with all the readability and maintainability of… assembly language.” C is not necessarily everyone’s favorite programming language, and there are plenty of problems with it. (C#, created in the early 2000s, was one of many attempts to improve it.) However, as it proliferated out into the world, bundled in Unix-like operating systems like X-Windows, Linux, and Mac OSX, software developers turned to it as a way to speak to one another. It became a kind of common tongue. Even if you weren’t fluent, you could probably understand the language conversationally. If you needed to bundle up and share a some code, C was a great way to do it.
In 1993, Jean-François Groff and Sir Tim Berners-Lee had to release a package with all of the technologies of the web. It could be used to build web servers or browsers. They called it libwww, and released it to the public domain. It was written in C.
Think about the first time you browsed the web. That first webpage. Maybe it was a rich experience, filled with images, careful design and content you couldn’t find anywhere else. Maybe it was unadorned, uninteresting, and brief. No matter what that page was, I’d be willing to bet that it had some links. And when you clicked that link, there was magic. Suddenly, a fresh page arrives on your screen. You are now surfing the web. And in that moment you understand what the web is.
Sir Tim Berners-Lee finished writing the first web browser, WorldWideWeb, in the final days of 1990. It ran on his NeXT machine, and had read and write capabilities (the latter of which could be used to manage a homepage on the web). The NeXTcube wasn’t the heaviest computer you’ve ever seen, but it was still a desktop. That didn’t stop Berners-Lee from lugging it from conference to conference so he could plug it in and show people the web.
Again and again, he ran into the same problem. It will seem obvious to us now when considering the difficulty of demonstrating a globally networked hypertext application running on a little-used operating system (NeXT) on a not-widely-owned computer (NeXT Computer System) alone at a conference without the Internet. The problem came after the demo with the inevitable question: how can I start using it? The web lacks its magic if you can’t connect to the network yourself. It’s entirely useless isolated on a single computer. To make the idea click, Berners-Lee need to get everybody surfing the web. And he couldn’t very well lend his computer out to anybody that wanted to use it.
That’s where Nicola Pellow came in. An undergraduate at Leicester Polytechnic, Pellow was still an intern at CERN. She was assigned to Berners-Lee’s and Calliau’s team, so they tasked her with building an interoperable browser that could be installed anywhere. The fact that she had no background in programming (she was studying mathematics) and that she was at CERN as part of an internship didn’t concern her much. Within a couple of months she picked up a bit of C programming and built the Line Mode Browser.
Using the Line Mode Browser today, you would probably feel like a hacker from the 1980s. It was a text-only browser designed to run from a command line terminal. In most cases, just plain white text on a black background, pixels bleeding from edge to edge. Typing out a web address into the browser would bring up that website’s text on the screen. The up and down arrows on a keyboard could be used for navigation. Links were visible as a numbered list, and one could jump from site to site by entering the right number.
It was designed that way for a reason. Its simplicity guaranteed interoperability. The Line Mode Browser holds the unique distinction of being the only browser for many years to be platform-agnostic. It could be installed anywhere, on just about any computer or operating system. It made getting online easy, provided you knew what to do once you installed it. Pellow left CERN a few months after she released the Line Mode Browser. She returned after graduation, and helped build the first Mac browser.
Almost soon as Pellow left, Berners-Lee and Cailliau wrangled another recruit. Jean-François Groff was working at CERN, one office over. A programmer for years, Groff had written the French translation of the official C Programming Guide by Brian Kernighan and the language’s creator, Dennis Ritchie. He was working on a bit of physics software for UNIX systems when he got a chance to see what Berners-Lee was working on.
Not everybody understood what the web was going for. It can be difficult to grasp without the worldwide picture we have today. Groff was not one of those people. He longed for something just like the web. He understood perfectly what the web could be. Almost as soon as he saw a demo, he requested a transfer to the team.
He noticed one problem right away. “So this line mode browser, it was a bit of a chicken and egg problem,” he once described in an interview, “because to use it, you had to download the software first and install it and possibly compile it.” You had to use the web to download a web browser, but you needed a web browser to use the web. Groff found a clever solution. He built a simple mechanism that allowed users to telnet in to the NeXT server and browse the web using its built-in Line Mode Browser. So anyone in the world could remotely access the web without even needing to install the browser. Once they were able to look around, Groff hoped, they’d be hooked.
But Groff wanted to take it one step further. He came from UNIX systems, and C programming. C is a desert island language. Its versatility makes it invaluable as a one-size-fits-all solution. Groff wanted the web to be a desert island platform. He wanted it to be used in ways he hadn’t even imagined yet, ways that scientists at research institutions couldn’t even fathom. The one medium you could do anything with. To do that, he would need to make the web far more portable.
Working alongside Berners-Lee, Groff began pulling out the essential elements of the NeXT browser and porting them to the C programming language. Groff chose C not only because he was familiar with it, but because he knew most other programmers would be as well. Within a few months, he had built the libwww package (its official title would come a couple of years later). The libwww package was a set of common components for making graphical browsers. Included was the necessary code for parsing HTML, processing HTTP requests and rendering pages. It also provided a starting point for creating browser UI, and tools for embedding browser history and managing graphical windows.
Berners-Lee announced the web to the public for the first time on August 7, 1991. He posted a brief description along with a simple note:
If you’re interested in using the code, mail me. It’s very prototype, but available by anonymous FTP from info.cern.ch. It’s copyright CERN but free distribution and use is not normally a problem.
If you were to email Sir Tim Berners-Lee, he’d send you back the libwww package.
By November of 1992, the library had fully matured into a set of reusable tools. When CERN put the web in the public domain the following year, its terms included the libwww package. By 1993, anyone with a bit of time on their hands and a C compiler could create their own browser.
Before he left CERN to become one of the first web consultants, Groff did one final thing. He created a new mailing list, called www-talk, for a new generation of browser developers to talk shop.
On December 13, 1991 — almost a year after Berners-Lee had put the finishing touches on the first ever browser — Pei-Yuan Wei posted to the www-talk mailing list. After a conversation with Berners-Lee, he had built a browser called ViolaWWW. In a few months, it would be the most popular of the early browsers. In the middle of his post, Wei offhandedly — in a tone that would come off as bragging if it weren’t so sincere — mentioned that the browser build was a one night hack.
A one night hack. Not even Berners-Lee or Pellow could pull that off. Wei continued the post with the reasons he was able to get it up and running so quickly. But that nuance would be lost to history. What programmers would remember is that the it only took one day to build a browser. It was “hacked” together and shipped to the world, buggy, but usable. That phrase would set the tone and pace of browser development for at least the next decade. It is arguably the dominant ideology among browser makers today.
The irony is the opposite was true. ViolaWWW was the product of years of work that simply culminated in a single night. Wei is a great software programmer. But he also had all the pieces he needed before the night even started.
Pei-Yuan Wei has made a few appearances on the frontlines of web history. Apart from the ViolaWWW browser, he was hired by Dale Dougherty to work on an early version of GNN.com, the first commercial website. He was at a meeting of web pioneers the day the idea of the W3C was first discussed. In 2012, he was on the list of witnesses to speak in court to the many dangers of the Stop Online Privacy Act (SOPA). In the web’s early history Wei was a persistent presence.
Wei was a student at UCLA Berkley in the early 90s. It was HyperCard that set off his fascination with hypertext software. HyperCard was an application built for the Mac operating system in the late 80s. It allowed its users to create stacks of virtual “cards,” each with a bit of info. Users could then connect these cards however they wanted, and quickly sort, search, and navigate through their stacks. People used it to organize their recipes, replace their Rolodexes, organize research notes, and a million other things. HyperCard is the kind of software that attracts a person who demands a certain level of digital meticulousness, the kind of user that organizes their desktop folders into neat sections and precisely tags their data. This core group of power users manipulated the software using its built-in scripting language, HyperScript, to extend it to new heights.
Wei had just glimpsed Hypercard before he knew he needed to use it. But he was on an X-Windows computer, and HyperCard could only run on a Mac. Wei was not to be deterred. Instead of buying a Mac computer (an expensive but reasonable solution the problem) Wei began to write software of his own. He even went one step further. Wei began by creating his very own programming language. He called it Viola, and the first thing he built with it was a HyperCard clone.
Wei felt that the biggest limitation of HyperCard — and by extension his own hypertext software — was that it lacked access to a network. What good was data if it was locked up inside of a single computer? By the time he had reached that conclusion, it was nearing the end of 1991, around the time he saw a mention of the World Wide Web. So one night, he took Viola, combined it with libwww, and built a web browser. ViolaWWW was officially released.
ViolaWWW was built so quickly because most of it was already done by the time Wei found out about the web project. The Viola programming language was in the works for a couple of years at that point. It had already been built to accept hyperlinks and hypermedia for the HyperCard clone. It had been built to be extendable to other possible applications. Once Wei was able to pick apart libwww, he ported his software to read HTML, which itself was still a preposterously simple language. And that piece, the final tip of the iceberg, only took him a single night.
ViolaWWW would be the site of a lot of experimentation on the early web. Wei was the first to include an early version of stylesheets. He added a bookmarking function. The browser supported forms and embedded media. In a prescient move, Wei also included downloadable applets, allowing fairly advanced applications running inside of the browser. This became the template for what would eventually become Java applets.
For X-Windows users, ViolaWWW was the most popular browser on the market. Until the next thing came along.
Releasing a browser in the early 90s was almost a rite of passage. There was a useful exercise in downloading the libwww package and opening it up in your text editor. The web wasn’t all that complicated: there was a bit of code for rendering HTML, and processing HTTP requests from web servers (or other origins, like FTP or Gopher). Programmers of the web used a browser project as a way of getting familiar with its features. It was kind of like the “Hello World” of the early web.
In June of 1993, there were 130 websites in the entire world. There was easily a dozen browsers to chose from. That’s roughly one browser for every ten websites.
This rapid development of browsers was driven by the nature of innovation in the web community. When Berners-Lee put the web in the public domain, he did more than just give it to the world. He put openness at the center of its ideology. It would take five years — with the release of Netscape — for the web to get its first commercial browser. Until then, the “browser makers” were a small community of programmers talking things out the www-talk mailing list trying to make web browsing feel as revolutionary as they wanted it to be.
Some of the earliest projects ported one browser to another operating system. Occasionally, one of the browser makers would spontaneously release something that now feels essential. The first PDF rendering inside of a browser window was a part of the Midas browser. HTML tables were introduced and properly laid out in another called Arena. Tabbed browsing was a prominent feature in InternetWorks. All of these features were developed before 1995.
Most early browsers have faded into obscurity. But the people behind them didn’t. Counted among the earliest browser makers are future employees at Netscape, members of the W3C and the web standards movement, the inventor of cookies (and the blink tag), and the creators of some of the most important websites of the early web.
Of course, no one knew that at the time. To most of the creators, it was simply an exercise in making something cool they could pass along to their Internet friends.
The New York Times introduced its readers to the web on December 8, 1993. “Think of it as a map to the buried treasures of the Information Age,” read the first line. But the “map” the writer was referring to — one he would spend the first half of the article describing — wasn’t the World Wide Web; it was its most popular browser. A browser called Mosaic.
Mosaic was created, in part, by Marc Andreessen. Like many of the early web pioneers, Andreessen is a man of lofty ambition. He is drawn to big ideas and grand statements (he once said that software will “eat the world”). In college, he was known for being far more talkative than your average software engineer, chatting it up about the next bing thing.
Andreessen has had a decades-long passion for technology. Years later, he would capture the imagination of the public with the world’s first commercial browser: Netscape Navigator. He would grace the cover of Time magazine. He would become a cornerstone of Silicon Valley, define its rapid “ship first, think later” ethos for years, and seek and capture his fortune in the world of venture capital.
But Mosaic’s story does not begin with a commanding legend of Silicon Valley overseeing, for better or worse, the future of technology. It begins with a restless college student.
When Sir Tim Berners-Lee posted the initial announcement about the web, about a year before the article in The New York Times, Andreessen was an undergraduate student at the University of Illinois. While he attended school he worked at the university-affiliated computing lab known as the National Center for Supercomputing Applications (NCSA). NCSA occupied a similar space as ARPA in that they both were state-sponsored projects without an explicit goal other than to further the science of computing. If you worked at NCSA, it was possible to move from project to project without arising too much suspicion from the higher ups.
Andreessen was supposed to be working on visualization software, which he had found a way to run mostly on auto-pilot. In his spare time, Andreessen would ricochet around the office listening to everyone about what it was they were interested in. It was during one of those sessions that a colleague introduced him to the World Wide Web. He was immediately taken aback. He downloaded the ViolaWWW browser, and within a few days he had decided that the web would be his primary focus. He decided something else too. He needed to make a browser of his own.
In 1992, browsers could be cumbersome software. They lacked the polish and the conventions of modern browsers without decades of learning to build off of. They were difficult to download and install, often requiring users to make modifications to system files. And early browser makers were so focused on developing the web they didn’t think too much about the visual interface of their software.
Andreessen wanted to build a well-designed, performant, easy-to-install browser while simultaneously building on the features that Wei was adding to the ViolaWWW browser. He pitched his idea to a programmer at NCSA, Eric Bina. “Marc’s a very good salesman,” Bina would later recall, so he joined up.
Taking their cue from the pace of others, Andreessen and Bina finished the first version of the Mosaic browser in just a few weeks. It was available for X Windows computers. To announce the browser, Andreessen posted a download link to the www-talk mailing list, with the message “By the power vested in me by nobody in particular, alpha/beta version 0.5 of NCSA’s Motif-based networked information systems and World Wide Web browser, X Mosaic, is hereby released.” The web got more than just a popular browser. It got its first pitchman.
That first version of the browser was impressive in a somewhat crowded field. To be sure, it had forms and some media support early on. But it wasn’t the best browser, nor was it the most advanced browser. Instead, Andreessen and Bina focused on something else entirely. Mosaic set itself apart because it was the easiest to use. The installation process was simple and the interface was, relatively speaking, intuitive.
The Mosaic browser’s secret weapon was its iteration. Before long, other programmers at NCSA wanted in on the project. They parceled off different operating systems to port the browser to. One team took the Mac, another Windows. By the fall of 1993, a few months after its initial release, Mosaic had feature-paired versions on Mac, Windows and Unix systems, as well as compatible server software.
After that, the pace of development only accelerated. Beta versions were released often and were available to download via FTP. New features were added at a rapid pace and new versions seemed to ship every week. The NCSA Mosaic was fully engaged with the web community, active in the www-talk mailing list, talking with users and gathering bug reports. It was not at all unusual to submit a bug report and hear back a few hours later from an NCSA programmer with a fix.
Andreessen was a particularly active presence, posting to threads almost daily. When the Mosaic team decided they might want to collect anonymous analytics about browser usage, Andreessen polled the www-talk list to see if it was a good idea. When he got a lot of questions about how to use HTML, he wrote a guide for beginners.
When one Mosaic user posted some issues he was having, it led to a tense back and forth between that user and Andreessen. He claimed he wasn’t a customer, and Andreessen shouldn’t care too much about what he thought. Andreessen replied, “We do care what you think simply because having the wonderful distributed beta team that we essentially have due to this group gives us the opportunity to make our product much better than it could be otherwise.” What Andreessen understood better than any of the early browser makers was that Mosaic was a product, and feedback from his users could drive its development. If they kept the feedback loop tight, they could keep the interface clean and bug-free while staying on the cutting edge of new features. It was the programming parable given enough eyeballs, all bugs are shallow come to life in browser development.
There was an electricity to Mosaic development at NCSA. Internal competition fueled OS teams to get features out the door. Sometimes the Mac version would get to something first. Sometimes it was Bina and Andreessen continuing to work on X-Mosaic. “We would get together, middle of the night, and come up with some cool idea — images was an example of that — then we would go off and race and see who would do it first,” creator of the Windows version of Mosaic Jon Mittelhauser later recalled. Sometimes, the features were duds and would hardly go anywhere at all. Other times, as Mittelhauser points out, they were absolutely essential.
In the months after launch, they started to surpass the feature list of even their nearest competitor, ViolaWWW. They added forms support and rich media. They added bookmarks for users to keep track of their links. They even created their own “What’s New” page, updated every single day, which tracked the web’s most popular links. When you opened up Mosaic, the NCSA What’s New page was the first thing you saw. They weren’t just building a browser. They were building a window to the web.
As Mittelhauser points out, it was the <img> tag which became Mosaic’s defining feature. It succeeded in doing two things. The tag was added without input from Sir Tim Berners-Lee or the wider web community. (Andreessen posted a note to www-talk only after it had already been implemented.) So firstly, that set the Mosaic team in a conflict with other browser makers and some parts of the web community that would last for years.
Secondly, it made Mosaic infinitely more popular. The <img> tag allowed for images to be embedded directly inline in the Mosaic browser. People found the web boring to browse. It was sterile, rigid, and scientific. Inline images changed all that. Within a few months, a new class of web designer was beginning to experiment with what was possible with images on the web. In some ways, it was the tag that made the web famous.
The image tag prompted the feature in The New York Times, and a subsequent write-up in Wired. By the time the press got around to talking about the web, Mosaic was the most popular browser and became a surrogate for the larger web world. “Mosaic” was to browsing the web as “Google” is to searching now.
Ultimately, the higher ups got involved. NCSA was not a tech company. They were a supercomputing lab. They came in to help make the Mosaic browser more cohesive, and maybe, more profitable. Licenses were parceled out to a dozen or so companies. Mosaic was bundled into Spry’s Internet in a Box product. It was embedded in enterprise software by the Santa Cruz Operation.
In the end, Mosaic split off into two directions. Pressure from management pushed Andreessen to leave and start a new company. It would be called Netscape. Another of the licensees of the software was a company called Spyglass. They were beginning to have talks with Microsoft. Both would ultimately choose to rewrite the Mosaic browser from scratch, for different reasons. Yet that browser would be their starting point and their products would have lasting implications on the browser market for decades as the world began to see its first commercial browsers.
The post Chapter 2: Browsers appeared first on CSS-Tricks.
You can support CSS-Tricks by being an MVP Supporter.
Chapter 2: Browsers published first on https://deskbysnafu.tumblr.com/
0 notes
Photo

Welcome to A Cup-pella, Mads! We’re excited to have you and Grace Fitzgerald in the game! Please go through the checklist to make sure you’re ready to go and send in your account within the next 24 hours.
OOC INFO
Name + pronouns: Mads & she/her Age: 24 Timezone: MST Ships: Chemistry Anti-Ships: Forced
IC INFO
Full Name: Grace Lynn Fitzgerald Face Claim: Kelsey Chow Age/Birthday: 25 / August 13th, 1992 Occupation: 3rd Grade Teacher / Newly Recruited to April’s Showers (Forward) Personality: intelligent, judgmental, perpetually insecure, curious, impulsive, well-traveled, resilient Hometown: Greensboro, Georgia Bio: Christianity isn’t something to mess around with. At least, that’s what Grace’s parents always told her. God would provide when no one else could and there was nothing more to say than that. Charles and Rebecca (nee Chen) Fitzgerald raised their three daughters – Grace, Faith, and Hope to be strong women of faith who never backed down no matter what was thrown at them. Church and religion were spoken about more than any struggles they may face as mixed, privileged women. In fact, their race was rarely spoken about (mostly only for college applications). When life was hard, you got on your knees and prayed. When you felt like everything against you, the response you got was ‘God isn’t’. Bible beating, Catholic guilt kind of feelings were all that were allowed in the Fitzgerald household.
So, imagine being fifteen and the only person who makes your heart skip a beat is your best friend. Your best friend who is a woman. Somewhere along the line, she wasn’t sure when, Grace was taught that men and women were meant to be together. God designed them specifically for that, but when Lucy’s lips touched hers and the entire world washed away? How could that be wrong? Of course, it wasn’t like ridding oneself of consistently patterned brainwashing was all that easy. The amount that Lucy made her feel was… well, beyond explanation, even to this day.
The kissing, cuddling, and all kinds of big feelings were everything to Grace, no matter how much she wanted to deny that fact. It was mere months that it lasted before she had to stop it. Before the Catholic guilt almost ate her alive and the little jokes her sisters made actually got to her. But no one knew. Not a soul had ever found out and maybe that was why Grace pushed Lucy to date men and they’d be best friends no matter what. The kissing wasn’t what made them friends. Their unending love was. But friends didn’t get jealous when other friends made out with boys or held their hands. High school was hard, but stuffing your gay in the closet was harder.
When Lucy left Greensboro, it was almost impossible for Grace to come back from. She threw everything she had into school and trying to distract herself from the broken heart that would never truly heal. Mathletes was her ultimate companion, clinging to numbers was the only thing she truly knew how to do. That, and her Quarterback boyfriend who was incredibly attractive. Or, so she was told. Men still didn’t have much of an effect on her and maybe that was for the best.
By the time she graduated high school there was already a ring on her finger and her parents couldn’t be more proud. Wedding bells rang with her hellish husband at the end of the aisle, Xanax in her system and her sisters by her side. Why she wasn’t able to stop herself from living a life for other people, she still doesn’t know, but it all happened so fast. The marriage. The failed attempt to bear children. The lack of ability to connect to her husband. The divorce. Grief rippled through her over and over again and it felt that with a snap of her fingers, 22 year old Grace Fitzgerald was back on her knees, this time cursing God instead of praising him.
After her world came crashing down right before her eyes, the world she had worked so hard to achieve, there was only one thing a woman could do. Run. So, Grace immediately left Greensboro, fled to California and found a home there. A home where those around her gave her the freedom to be herself. A home that allowed for exploration of half of her ancestry she’d never known. A home where weekends in San Francisco opened up the gates of the grief her heart held onto. A home where late night glasses of wine turned into tear filled confessions that did more than a Catholic one ever had. A home that showed her who she truly was - a fiercely strong, empowered, gay, half Chinese woman.
It was when she came to terms with herself a few years after moving to California that she decided to limit communication with her family. All of them had given her enough flack for not having children and then for getting divorced. Ties with family were somewhat shortened and the sunshine was just a little too much. Too much blaspheme, too much anger, too much uncertainty. In fact, all of the time she’d spent worrying so much about her family was now energy she put into running an LGBT+ sports(kickball, soccer, tennis) league just outside of San Francisco. She learned a lot about herself, the community, and gained an intense love for the sport she’d never imagined: Soccer. All of her time after being divorced and moving away, Grace spent any breaks she had traveling – it was what had sparked her love for New York in the first place. For all that California was to her, New York City was calling her name.
So, Grace moved to New York City a few months ago, filling a position at the school just after a faculty member decided to leave mid-year. Becoming involved with school things and trying to find a community she can call her own like she had back in California are proving to be difficult (hence her trying out for April’s Showers). But if Grace is anything, it’s resilient.
Pets: Grace has a 2 year old British short hair munchkin cat named Raya that she was gifted by a friend in California when they could no longer keep her. The cat’s name was originally Ray, but it soon became obvious that she was most definitely a female cat. (fc: @littlemunchiepooky)
RELATIONSHIPS
Lucy Quinn Fabray
Never quite lovers, but practically so in every way. Big feelings were had and the relationship that Grace chose to sever in the first place has haunted her ever since. There was so much that she experienced with the blonde and so much that she desired that she has never been able to fully shut down. With a relationship where everything prohibited was all that they wanted, Grace’s past with Quinn is likely to influence a lot of her time in New York.
Rowan Flanagan, Samantha Evans, and Fiona Hudson
All four of the girls work at the same Elementary school and are bound to run into each other from time to time. It’s been such a short amount of time that Grace has been working there that she feels she can’t actually say if they get along or not.
April’s Showers
As the newest recruit, it’s unlikely that she’s gotten close to most (if any) of the girls on the team. In order to foster a new community for herself and a large, unknown city, Grace has dedicated herself to the team even if she’s only been part of it for a brief time. Of course, the fact that her first lady love is on the team too is bound to cause some sort of internal conflict.
EXTRA INFO
Twitter name/twitter URL/description: g. fitzgerald / @savegrace / we could never learn to be brave or patient if there were only joy in the world. ((teaching kids that life is hard one day at a time.))
Five latest tweets:
@savegrace: hi @olivegarden – love you, miss you, just thought you should know xo @savegrace: Yet another day where my eyes won’t open fully. Do you think parents notice or just think I’m extra Asian?? @savegrace: sorry for last night’s live tweeting of are you smarter than a fifth grader?… I felt some type of way. @savegrace: if I wear black to school one more day this week, do you think my boss will comment on it again? @savegrace: flight attendant: “we’ve landed 36 minutes ahead of schedule. So, next time you fly with us and we’re late, let’s call it even.” #myhero #usingthisforwork
3 notes
·
View notes
Note
All Lets Get Personal.
Thanks anon!! My depressed ass needed something to do
1: 6 of the songs you listen to most?
It really depends on my mood tbh. But judging by my YouTube playlists:
Church- Fall out boy; Hopeless Wanderer- Mumford and Sons (its a jam okay?); Summertime- my chemical romance; so cold- ben cocks; this is me- keala settle and killing in the same- rage against the machine
2: If you could meet anyone on this earth, who would it be?
Lmao idk I dont have much of an interest in anyone atm. I still think itd be cool to meet kaitlyn alexander ig
3: Grab the book nearest to you, turn to page 23, give me line 17.
You recognise each other the moment your eyes meet. It’s a question and answer book and the question is about soulmates or something
4: What do you think about most?
What it is I need to do to stop feeling anxious or stressed since it’s a daily battle
5: What does your latest text message from someone else say?
“it was hillarious but I couldn’t say “lmao I’ve seen women take bigger” so I just let the conversation die but I was urging to show him a savage video and ruin him just to be right but then I stopped myself”
Yes, it is as bad in context as out of it.
Do you sleep with or without clothes on?
Depends how warm it is tbh
What’s your strangest talent?
Talent? What’s that?? Idk I’m quite good at picking up languages super fast for some unknown reason (but i can forget them just as quick soo
8: Girls… (finish the sentence); Boys… (finish the sentence)
Girls are hot hot hot they make me gay
Boys are hot hot hot they make me gay
9: Ever had a poem or song written about you?
Nah, but I’m not major sad about it since that’d be so awkward
10: When is the last time you played the air guitar?
Oh gosh um probably in the car the other day, canny remember which song it was tho
11: Do you have any strange phobias?
I seriously hate water like to the point I chose my uni based on where the lakes were. I also hate stuffed toys with voice boxes.
12: Ever stuck a foreign object up your nose?
Probably but I don’t remember
13: What’s your religion?
I’m an athiest
14: If you are outside, what are you most likely doing?
Walking between indoor places
15: Do you prefer to be behind the camera or in front of it?
Behind it! I’m not photogenic
16: Simple but extremely complex. Favorite band?
Ummmmmmm idk. I genuinly don’t know. I probably listen to five finger death punch most atm?
17: What was the last lie you told?
I said I was feeling good lmao
18: Do you believe in karma?
I don’t know, but I like to hope it does to make myself feel better
19: What does your URL mean?
I think it’s pretty self explanatory
20: What is your greatest weakness; your greatest strength?
My greatest weakness? Probably my low opinion of myself or my associated jealousy.
My greatest strength? A few years ago I mightve said my resilience but I’m not sure I ever have that anymore. Idk, maybe my need to always keep improving as a person
21: Who is your celebrity crush?
See number 2 tbh
22: Have you ever gone skinny dipping?
Yah every time I have a bath
23: How do you vent your anger?
I send massive long rant paragraphs to my closest friends and try not to do anything stupid or unhealthy
24: Do you have a collection of anything?
I have a pretty big collection of reaction images and memes
25: Do you prefer talking on the phone or video chatting online?
I hate both but video chatting is slightly better
26: Are you happy with the person you’ve become?
I suppose. I’m closer to being happy with them than I ever have been and that’s what matters.
27: What’s a sound you hate; sound you love?
At this point I hate the sound of my alarm more than most things and I love... idk music. Does that count?
28: What’s your biggest “what if”?
What if I’d stood up for myself more?
29: Do you believe in ghosts? How about aliens?
I don’t know as I believe in ghosts but I’m fascinated by the people who do. As for aliens ofc they exist.
30: Stick your right arm out; what do you touch first? Do the same with your left arm.
I touch sofa. Both times. I’m sat on a sofa.
31: Smell the air. What do you smell?
I smell rabbit since he’s currently sat with me in a box. I got lonely.
32: What’s the worst place you have ever been to?
Gosh I don’t know. I can’t really think of anywhere I’ve hated being, besides home sometimes. I don’t know, no where has been that bad since I always try to make the best of it.
33: Choose: East Coast or West Coast?
East coast
34: Most attractive singer of your opposite gender?
Opposite eh? Lmaoooo
Okay I actually have quite a thing for the lead singer of motionless in white. Make of that what you will.
35: To you, what is the meaning of life?
To be happy, to go good and to die with as few regrets as possible
36: Define Art.
Fuck. Something visual this is made to be aesthetically pleasing or convey a message. I guess.
37: Do you believe in luck?
I’m not entirely sure what luck is. Maybe?
38: What’s the weather like right now?
Fekkin horrible, you wouldn’t know it’s spring. It’s grey and wet and windy and cold.
39: What time is it?
17:51
40: Do you drive? If so, have you ever crashed?
I have a full license but haven’t actually driven since my test, so I haven’t had a chance to crash.
41: What was the last book you read?
When breath becomes air. It’s about being a doctor.
42: Do you like the smell of gasoline?
I adore it yaas
43: Do you have any nicknames?
Char, (wholemeal) chorlo and Thot lmao
44: What was the last film you saw?
Love, Simon
Go see it, it’s gay and beautiful!
45: What’s the worst injury you’ve ever had?
Idk, I broke my humorous after dislocating my elbow once. But that was ages ago
46: Have you ever caught a butterfly?
Hundreds lmao thats my childhood right there
47: Do you have any obsessions right now?
I’m too depressed to have much of an interest in anything tbh. Even when I’m not I don’t tend to get That Invested.
48: What’s your sexual orientation?
Bisexual, ig. Though saying it never feels right for some reason.
49: Ever had a rumour spread about you?
A few, a few. One being that I was a lesbian years before even I knew I wasn’t straight.
50: Do you believe in magic?
Not really but who knows
51: Do you tend to hold grudges against people who have done you wrong?
The threshold for grudges is pretty high but if I have one I’ll be bitter til the day I die
52: What is your astrological sign?
Libra
53: Do you save money or spend it?
I swing wildly between saving loads and spending loads. Healthy.
54: What’s the last thing you purchased?
Um I mean I paid the deposit on a house, does that count?
55: Love or lust?
Love, for sure
56: In a relationship?
Yeah XD
57: How many relationships have you had?
This is like my third proper one
58: Can you touch your nose with your tongue?
Nope
59: Where were you yesterday?
At home on my tod again, revising
60: Is there anything pink within 10 feet of you?
Nah
61: Are you wearing socks right now?
Yuup
62: What’s your favourite animal?
I love all the animals I can’t pick a favourite. I love alpacas, chimps, gorrillas, orangutans, lizards, elephants, octopuses etc etc
63: What is your secret weapon to get someone to like you?
Excessive praying and reblogging lucky posts
64: Where is your best friend?
Tbh I have multiple, one in the next village, one 6 hours south and one 4000 miles away
65: Give me your top 5 favourite blogs on Tumblr.
Christ um, people I spam with likes most are probably @oneshappyplace @apricot-el @only-slightly-dangerous @succeeding and @setheverman
66: What is your heritage?
I’m white as a toilet so my family probably murdered a lot of innocent people
67: What were you doing last night at 12AM?
Umm I was skyping my boyf and playing a game online with him
68: What do you think is Satan’s last name?
Trump
69: Be honest. Ever gotten yourself off?
Yeah, haven’t most people?
70: Are you the kind of friend you would want to have as a friend?
I like to think so yeah. Though I do have a lot of breakdowns so maybe without that part. @ my friends I apologise
71: You are walking down the street on your way to work. There is a dog drowning in the canal on the side of the street. Your boss has told you if you are late one more time you get fired. What do you do?
Help the dog. Though realistically I probably couldn’t do it alone, so would call someone over to help and leave asap to not be so late.
72: You are at the doctor’s office and she has just informed you that you have approximately one month to live. a) Do you tell anyone/everyone you are going to die? b) What do you do with your remaining days? c) Would you be afraid?
I think I’d tell the people closest to me, yeah. I don’t know what I’d do though. Probably book as many flights as possible and visit all the countries I’ve always wanted to go to. I guess I’d probably write my will and organise a funeral too. I don’t think I’d be too afraid, just, idk, sad? I don’t want to disappear to nothingness yet, even if I won’t know when it happens.
73: You can only have one of these things; trust or love.
Argh that’s horrid. I mean trust is essential for all relationships imo. But if I had no love at all in my life I doubt I’d live very long at all. So... love? No wait,,, trust. Yeah trust.
74: What’s a song that always makes you happy when you hear it?
Little Talks by Of Monsters and Men. It reminds me of a school trip years ago to Belgium that was such a good time
75: What are the last four digits in your cell phone number?
8008
76: In your opinion, what makes a great relationship?
Well, trust ig, being able to talk about anything, a good balance of affection and roasting. Idk
77: How can I win your heart?
Be kind, be funny and have layers.
78: Can insanity bring on more creativity?
I suppose so
79: What is the single best decision you have made in your life so far?
The decision to reply to the message that appeared in my inbox right before I was going to end it. There were plenty, but I only opened that one. The person who sent it changed my life.
80: What size shoes do you wear?
7
81: What would you want to be written on your tombstone?
Either a pun or something ominous. Maybe both.
82: What is your favourite word?
Probably sorry since I say it a lot
83: Give me the first thing that comes to mind when you hear the word; heart.
Love, followed quickly by the mental image of a dissected heart
84: What is a saying you say a lot?
I amuse myself. Gotta keep up that brand sponning.
85: What’s the last song you listened to?
Don’t feel like dancing by the scissor sisters lmao
86: Basic question; what’s your favourite colour/colours?
Black, red and purple
87: What is your current desktop picture?
Just a galaxy
88: If you could press a button and make anyone in the world instantaneously explode, who would it be?
Donald. Trump. When in close proximity to Mike Pence too.
89: What would be a question you’d be afraid to tell the truth on?
Besides “what are your credit card details”? Idk, perhaps a question about the flaws of the people closest to me, since they’re something I wouldn’t want them to read.
90: One night you wake up because you heard a noise. You turn on the light to find that you are surrounded by MUMMIES. The mummies aren’t really doing anything, they’re just standing around your bed. What do you do?
Lie there still for a good 5 minutes just to make sure. Maybe chuck a pillow across the room to see if they attack it. Then go fetch my phone and call whoever will pick up to ask wtf to do.
91: You accidentally eat some radioactive vegetables. They were good, and what’s even cooler is that they endow you with the super-power of your choice! What is that power?
The ability to fly probably. It’d help stop me being late and transport is so expensive these days.
92: You can re-live any point of time in your life. The time-span can only be a half-hour, though. What half-hour of your past would you like to experience again?
A half hour period of the time me and my friend spent outside laughing our heads off and covered in glitter when I visited her in the states last summer
93: You can erase any horrible experience from your past. What will it be?
Damn, only one? Lmao catch me ranking my traumas to try to answer this question. I’ll erase getting flooded and being made homeless I think lmao
94: You have the opportunity to sleep with the music-celebrity of your choice. Who would it be?
Probably P!nk since she was low key my gay awakening
95: You just got a free plane ticket to anywhere. You have to depart right now. Where are you gonna go?
I quite fancy going to amsterdam rn, or failing that, copenhagen
96: Do you have any relatives in jail?
Not that I know of
97: Have you ever thrown up in the car?
Only as a little kid
98: Ever been on a plane?
Plenty of times yeah, I love it
99: If the whole world were listening to you right now, what would you say?
I wish there was some way I could convince all the dictators, extremists and right wingers to just fekkin stop tbh. Centrists can stay but theyre on thin ice.
0 notes
Text
Next Generation Test Automation with Usetrace
Test Automation is an inherent part of todays modern software development. It is the foundation that supports short release cycles and processes like DevOps. Automated tests are written on different levels testing different aspects of an application. The most common levels of testing are unit-, integration- and acceptance-level testing. And while automated tests are typically working very well on unit- and integration-level, failure is just waiting around the corner when it comes to acceptance tests. Those are usually equivalent to UI tests. Here automation is getting complicated, time-consuming and in the end often a “little bit” frustrating when things start to go south.
At codecentric we have been working with and/or evaluating a lot of different testing tools already. Personally I like the Robot Framework a lot. But we also looked quite in detail into JBehave and Cucumber amongst others. All of those tools offer a brought set of testing functionality, which is founded in the fact that tests are basically implemented in a programming language. While this is of course a strength, it also makes those tools hard to use by “pure” testers. Often already installation can be an obstacle here. New functionality might only be testable once a developer has extended the corresponding test code. This work then is in conflict with feature development. And to be honest: Most developers like implementing new features more than implementing code to enable new acceptance tests.
It is time for something new!
This is where new cloud-based testing-tools are entering the stage. Naturally those tools are focusing on UI-tests, which is also often the main – and the hardest – part in acceptance testing anyway. In the following we will have a closer look at Usetrace. Another candidate would have been Functionize, which we might still take a look at later.
As with all cloud-based services getting started is extremely easy, as there is no need for any local installation. After registration of a new account Usetrace welcomes us with the above shown screen. Of course we are happily following the polite invitation to create a new trace and thus our first testcase. As usual I start by jumping into doing things and keep watching any tutorials for later. Let’s see how this works out.
We are creating our first project by entering the base URL of the application to test. As so often our codecentric homepage is used for a first test. In a real project that would of course be the URL of some dedicated test server running the application under test.
For sure there are same concerns at this point of time. Testing a site that is publicly available is no problem, but what about test environments that are behind firewalls or use basic authentification for security reasons? For sure this has a certain potential for problems, but on the other hand these topics are tackled by the Usetrace network instructions. In the end one probably needs to do some project-specific evaluation first if in doubt.
The “Trace Editor” opens up for our new project and we can start to record our first testcase. A preview of the page under test shows up in the central part of the editor. We can start recording and the individual steps are shown on the left hand side of the editor.
So far I was not a big fan of recording test cases, but the recording and editing really feels intuitive. Furthermore the traces are promised to be robust against minor UI changes. Of course this remains to be seen. But after literally five minutes I had a very basic testcase clicking a few pages and checking for specific content on one of the pages.
The trace (testcase) can be executed directly from the editor. The results of all executed traces can of course also be seen. Execution can be triggered for different browsers. In the free trial and the Starter edition Firefox and Chrome are supported. Internet Explorer is only supported in the Pro and Enterprise editions. An overview on the pricing and the different features of the available editions can be found from here.
Results are shown for all traces (ok currently there is only one) in combination with the different browsers. Up to here I can really only say: Thumbs up, I like it! These kind of minimal evaluation is of course always easy to do, but it was never that easy with any other tool.
Diving deeper
Global settings
In the project settings it is possible to define global parameters for all traces. This includes:
Number of automated retries on failure.
Maximum concurrency for builds.
Default timeout for steps.
Additional delay between interactions with the page.
Those can be already quite helpful to tackle some known network delays.
Scheduled execution
Of course test execution must be scheduled. Usetrace supports different CI-Servers (e.g. Jenkins or Bamboo) for this. Integration is quite simple as execution can be triggered by curling a certain URL. Alternatively it is also possible to use the integrated scheduler of Usetrace.
Modular tests
This is probably one of the most important features of every test tool. It allows to repeat certain test steps as part of another test. The typical example for this is to login to some web site. Usetrace supports modular tests with routines. With this feature it is possible to reuse one trace as a step in another trace. The following screenshot shows how to select a routine.
It might make sense to use some kind of naming convention for reusable traces to easily find them from the dropdown-box. Furthermore I am not 100% sure if there is a better way to include routines than stop recording and navigate to the page the routine will bring you and then continue recording from there.
The above screenshot shows how short a test can be that continues from the place our first trace was navigating to. Of course the major advantage of reusing test steps is easier adaption to changes in the tested application. If there is for example a major change in the login form then only that trace needs to be re-recorded and not all the tests that require a login. And that would probably be all tests anyway.
Execution details
Once test execution is finished a summary is shown. This contains some quite high-level information as shown in the following screenshot.
But it also goes down to quite detailed information showing all the Webdriver commands executed during the test run. This might be helpful for some troubleshooting. It should be kept in mind that fixing problems in automated UI tests can either be done in the test itsself, but often also by slightly modifying the application under test to make automated test possible, easier and/or more stable.
Other features
Time does not allow to have a detailed look at all features Usetrace is offering. But some interesting features are still listed in the following to get a more complete view on the tool:
Testing of mouse hover events.
Execution of custom JavaScript as part of a test step.
Definition of step-specific wait times.
Running tests against a local instance of the application under test using a tunneled connection.
The practical test
Unfortunately it is not possible to show any screenshots here as I was implementing some tests for the project I am currently working on. The test server is secured using basic authentication. This was no problem using the http://ift.tt/2weG3cV syntax for the base URL. As this is a cloud-based application testing starts with processing a login form. Then navigating to a certain page, filling a form and submitting it. Afterwards a very simple test is done to verify that no error has occurred.
Again the whole exercise took not more than 15 minutes. Of course some problems might show up when diving even deeper into the tests. But still the ratio between results and invested time is really extremely good. This should more easily enable an evaluation of the tool in projects considering these kind of UI tests as potentially useful.
Conclusion
The pure speed with which Usetrace enables the user to start implementing UI tests is really impressive. The recording has worked flawless during this evaluation and is quite intuitive. It remains to be seen how resilient the recorded tests really are when it comes to (minor) changes in the UI of the tested application. Of course it is not possible to perform any combined tests like triggering some action in the UI and then checking the results in the database. But how often is that really done when using other test frameworks?
In the end one potential problem can be the execution of tests on some external server. That might be in conflict with some data privacy protection. On the other hand, if only testdata is used, this might not be a real issue. The second potential problem is shared with all cloud-based services: The data is given away and one must have the trust that nothing bad will happen (data loss or the service is terminated). For this I would consider some kind of export a cool feature. This must and probably cannot be executable tests, but maybe at least some kind of test description derived from the recorded tests. This way one could always have a local backup of the test cases and steps as such at hand.
Nonetheless Usetrace for sure is a potential candidate when evaluating a new tool for UI tests. It was really interesting and fun checking it out and I somehow have the feeling this will not be the final article on Usetrace on our blog :-).
The post Next Generation Test Automation with Usetrace appeared first on codecentric AG Blog.
Next Generation Test Automation with Usetrace published first on http://ift.tt/2fA8nUr
0 notes
Text
Next Generation Test Automation with Usetrace
Test Automation is an inherent part of todays modern software development. It is the foundation that supports short release cycles and processes like DevOps. Automated tests are written on different levels testing different aspects of an application. The most common levels of testing are unit-, integration- and acceptance-level testing. And while automated tests are typically working very well on unit- and integration-level, failure is just waiting around the corner when it comes to acceptance tests. Those are usually equivalent to UI tests. Here automation is getting complicated, time-consuming and in the end often a “little bit” frustrating when things start to go south.
At codecentric we have been working with and/or evaluating a lot of different testing tools already. Personally I like the Robot Framework a lot. But we also looked quite in detail into JBehave and Cucumber amongst others. All of those tools offer a brought set of testing functionality, which is founded in the fact that tests are basically implemented in a programming language. While this is of course a strength, it also makes those tools hard to use by “pure” testers. Often already installation can be an obstacle here. New functionality might only be testable once a developer has extended the corresponding test code. This work then is in conflict with feature development. And to be honest: Most developers like implementing new features more than implementing code to enable new acceptance tests.
It is time for something new!
This is where new cloud-based testing-tools are entering the stage. Naturally those tools are focusing on UI-tests, which is also often the main – and the hardest – part in acceptance testing anyway. In the following we will have a closer look at Usetrace. Another candidate would have been Functionize, which we might still take a look at later.
As with all cloud-based services getting started is extremely easy, as there is no need for any local installation. After registration of a new account Usetrace welcomes us with the above shown screen. Of course we are happily following the polite invitation to create a new trace and thus our first testcase. As usual I start by jumping into doing things and keep watching any tutorials for later. Let’s see how this works out.
We are creating our first project by entering the base URL of the application to test. As so often our codecentric homepage is used for a first test. In a real project that would of course be the URL of some dedicated test server running the application under test.
For sure there are same concerns at this point of time. Testing a site that is publicly available is no problem, but what about test environments that are behind firewalls or use basic authentification for security reasons? For sure this has a certain potential for problems, but on the other hand these topics are tackled by the Usetrace network instructions. In the end one probably needs to do some project-specific evaluation first if in doubt.
The “Trace Editor” opens up for our new project and we can start to record our first testcase. A preview of the page under test shows up in the central part of the editor. We can start recording and the individual steps are shown on the left hand side of the editor.
So far I was not a big fan of recording test cases, but the recording and editing really feels intuitive. Furthermore the traces are promised to be robust against minor UI changes. Of course this remains to be seen. But after literally five minutes I had a very basic testcase clicking a few pages and checking for specific content on one of the pages.
The trace (testcase) can be executed directly from the editor. The results of all executed traces can of course also be seen. Execution can be triggered for different browsers. In the free trial and the Starter edition Firefox and Chrome are supported. Internet Explorer is only supported in the Pro and Enterprise editions. An overview on the pricing and the different features of the available editions can be found from here.
Results are shown for all traces (ok currently there is only one) in combination with the different browsers. Up to here I can really only say: Thumbs up, I like it! These kind of minimal evaluation is of course always easy to do, but it was never that easy with any other tool.
Diving deeper
Global settings
In the project settings it is possible to define global parameters for all traces. This includes:
Number of automated retries on failure.
Maximum concurrency for builds.
Default timeout for steps.
Additional delay between interactions with the page.
Those can be already quite helpful to tackle some known network delays.
Scheduled execution
Of course test execution must be scheduled. Usetrace supports different CI-Servers (e.g. Jenkins or Bamboo) for this. Integration is quite simple as execution can be triggered by curling a certain URL. Alternatively it is also possible to use the integrated scheduler of Usetrace.
Modular tests
This is probably one of the most important features of every test tool. It allows to repeat certain test steps as part of another test. The typical example for this is to login to some web site. Usetrace supports modular tests with routines. With this feature it is possible to reuse one trace as a step in another trace. The following screenshot shows how to select a routine.
It might make sense to use some kind of naming convention for reusable traces to easily find them from the dropdown-box. Furthermore I am not 100% sure if there is a better way to include routines than stop recording and navigate to the page the routine will bring you and then continue recording from there.
The above screenshot shows how short a test can be that continues from the place our first trace was navigating to. Of course the major advantage of reusing test steps is easier adaption to changes in the tested application. If there is for example a major change in the login form then only that trace needs to be re-recorded and not all the tests that require a login. And that would probably be all tests anyway.
Execution details
Once test execution is finished a summary is shown. This contains some quite high-level information as shown in the following screenshot.
But it also goes down to quite detailed information showing all the Webdriver commands executed during the test run. This might be helpful for some troubleshooting. It should be kept in mind that fixing problems in automated UI tests can either be done in the test itsself, but often also by slightly modifying the application under test to make automated test possible, easier and/or more stable.
Other features
Time does not allow to have a detailed look at all features Usetrace is offering. But some interesting features are still listed in the following to get a more complete view on the tool:
Testing of mouse hover events.
Execution of custom JavaScript as part of a test step.
Definition of step-specific wait times.
Running tests against a local instance of the application under test using a tunneled connection.
The practical test
Unfortunately it is not possible to show any screenshots here as I was implementing some tests for the project I am currently working on. The test server is secured using basic authentication. This was no problem using the http://ift.tt/2weG3cV syntax for the base URL. As this is a cloud-based application testing starts with processing a login form. Then navigating to a certain page, filling a form and submitting it. Afterwards a very simple test is done to verify that no error has occurred.
Again the whole exercise took not more than 15 minutes. Of course some problems might show up when diving even deeper into the tests. But still the ratio between results and invested time is really extremely good. This should more easily enable an evaluation of the tool in projects considering these kind of UI tests as potentially useful.
Conclusion
The pure speed with which Usetrace enables the user to start implementing UI tests is really impressive. The recording has worked flawless during this evaluation and is quite intuitive. It remains to be seen how resilient the recorded tests really are when it comes to (minor) changes in the UI of the tested application. Of course it is not possible to perform any combined tests like triggering some action in the UI and then checking the results in the database. But how often is that really done when using other test frameworks?
In the end one potential problem can be the execution of tests on some external server. That might be in conflict with some data privacy protection. On the other hand, if only testdata is used, this might not be a real issue. The second potential problem is shared with all cloud-based services: The data is given away and one must have the trust that nothing bad will happen (data loss or the service is terminated). For this I would consider some kind of export a cool feature. This must and probably cannot be executable tests, but maybe at least some kind of test description derived from the recorded tests. This way one could always have a local backup of the test cases and steps as such at hand.
Nonetheless Usetrace for sure is a potential candidate when evaluating a new tool for UI tests. It was really interesting and fun checking it out and I somehow have the feeling this will not be the final article on Usetrace on our blog :-).
The post Next Generation Test Automation with Usetrace appeared first on codecentric AG Blog.
Next Generation Test Automation with Usetrace published first on http://ift.tt/2vCN0WJ
0 notes
Link
Image copyright Getty Images
Image caption This photograph of Tewkesbury Abbey became a defining image of the 2007 floods
The summer of 2007 was the wettest on record. There was 414mm of rainfall across England and Wales from May to July – more than in any period since records began in 1766. Across Yorkshire and the Midlands, thousands of people were rescued, whole towns cut off and families forced to flee their properties.
In late July, Gloucestershire and Worcestershire became the latest parts of England to be inundated. Flooding left 48,000 homes without power for two days, and 10,000 motorists were stranded on the M5 overnight.
In Tewkesbury, the whole town became cut off and the RAF and Army were drafted in to help with the relief effort. Three people died.
An aerial photograph of the town and its famous abbey, depicting an island surrounded by a sea of brown water, became one of the defining images of that most sodden of summers.
Ten years on, the BBC revisits some of those caught up in the flooding.
‘There was somebody coming up the road in a canoe’
Image copyright Getty Images
Image caption Sheila Heath ended up living in a caravan outside her flood-hit Tewkesbury home for seven months
The day – 20 July – had started off like any other.
But while at work, where she was a partner at a lettings firm in Cheltenham, Sheila Heath noticed the drains “bubbling” up with water from the torrential rainfall.
She knew immediately something was “seriously wrong”, so she sent her staff home and tried to make her way back to Tewkesbury but was forced to abandon her journey and stay with a friend.
When she made it home the following morning, Mrs Heath, now 63, arrived to find her house had been inundated. She had to wade through waist-deep water to get to her front door.
“The whole area was like a lake,” she recalls. “There was somebody coming up the road in a canoe; it was totally surreal.”
It was six days before the water subsided, during which time the family lived at a nearby bed and breakfast.
With their house inhabitable, they bought a caravan and pitched it outside, remaining there for seven months.
Image copyright Getty Images
Image caption The Army transports emergency drinking water supplies in Tewkesbury on 24 July 2007
With many in the street doing the same, it became “like a caravan site”, she said.
The cost of the damage – which was covered by the insurers – was 98,000, but many treasured possessions were irreplaceable.
“It was what we had built up all our married life, it was our home, all of our personal possessions,” said Mrs Heath.
“It’s still upsetting to this day.
“Everything you’ve built up over your life is just gone. All the photographs have gone, all the memories, gifts from the children, all your personal things have gone.”
Image copyright Gavin Dickson
Image caption Sheila Heath says the flooding has had a lasting impact on her life
The summer 2007 floods – in numbers
Surface water and river flooding affected more than 55,000 homes and businesses across the country
7,000 people were rescued
17,000 families had to leave their homes
13 people died
Estimates made shortly after the floods put the total losses at about 4bn, of which insurable losses were reported to be about 3bn
Source: Environment Agency
‘An icon of hope’
Image copyright Getty Images
Image caption Tewkesbury was cut off on 22 July 2007
It was after saying afternoon prayers on 20 July 2007, that the Reverend Canon Paul Williams, the vicar of Tewkesbury Abbey, first became aware something unusual was happening.
“I noticed that the rain hadn’t stopped all day,” he said.
“I felt an eerie feeling so I went out up to the borough council and the mayor was there. He said ‘we’ve been warned something serious is on the way and will we open the abbey to make sure it’s a place of refuge’.”
Drivers caught in the downpour slept in the abbey, with hundreds put up that Friday night.
Image copyright Gavin Dickson
Image caption Paul Williams says the community is moving forwards following the flooding
“People were sleeping on kneelers, one family was wrapped in an altar cloth,” he said.
“During that night lots of people were up and making sure that people using the abbey as refuge were looked after.”
The rain had cleared on Saturday and those stranded were able to leave the abbey, which was even able to host a wedding ceremony.
But on Sunday 22 July the rivers broke.
“The abbey changed from being an ark to being an icon of resilience,” said Canon Williams. “It was like a ship ploughing through the waters. It was an icon of hope.”
It was that Sunday the famous photographs of Tewkesbury Abbey, standing proudly above the floodwater, were taken. They went on to become some of the most enduring images of that summer’s floods.
“Someone once said it was one of the iconic images, like St Paul’s in the Blitz, it’s that type of image that will remain with people. You need icons to give you hope; the abbey gave us hope at that time,” said Canon Williams.
Image copyright Getty Images
Image caption It looks like a lake – but this is actually Tewkesbury’s flooded park
During the Gloucestershire town’s short spell as an “island”, the sense of community spirit shone through.
“There was an extraordinary feeling of camaraderie, particularly after the rivers broke – we were helping each other, making sure people were OK. There wasn’t fear, there was respect.
“You couldn’t get in or out. We were completely cut off. We got on with our business.”
Remarkably, the abbey came away relatively unscathed.
The same could not be said for the rest of Tewkesbury.
More than 800 properties were flooded that July – largely by surface water and some smaller tributaries, before the Rivers Avon and Severn rose to record levels.
During the same period, the Mythe Water Treatment Works also flooded, leaving half the homes in Gloucestershire without water for 17 days.
And while it took years for the town to fully recover, Canon Williams says the community is “moving forward together”.
“Of course that’s part of our history, but we are looking to the future.”
@media only screen and (min-width: 1px) { .ns_datapic_stat--floods-2007 .ns_outer_wrapper { background-image: none; } .ns_datapic_stat--floods-2007 .ns_outer_wrapper .ns_inner_wrapper { max-width: 100%; padding: 0; } } @media only screen and (min-width: 480px) { .ns_datapic_stat--floods-2007 .ns_outer_wrapper .ns_inner_wrapper { max-width: 45%; padding: 0.5em; } .ns_datapic_stat--floods-2007 .ns_outer_wrapper { background-image: url(http://ift.tt/2uKtNUD); } } .ie8 .ns_datapic_stat--floods-2007 .ns_outer_wrapper .ns_inner_wrapper { max-width: 45%; padding: 0.5em; } .ie8 .ns_datapic_stat--floods-2007 .ns_outer_wrapper { background-image: url(http://ift.tt/2uKtNUD); }
UK floods: Ten years on
414mm
Rainfall from May-July 2007
Wettest
summer since records began in 1766
4x average June rainfall in parts of North York moors and South Pennines
30,000 people had to leave their homes in Hull
40,000 lost power in Sheffield when a substation was inundated
800 properties flooded in Tewkesbury
Source: Environment Agency
Getty
‘It devastated the whole town’
Image copyright Getty Images
Image caption Upton upon Severn, which is about seven miles north of Tewkesbury over the border in Worcestershire, was also badly hit by the floods
Grahame Bunn, landlord of the Kings Head pub in Upton upon Severn, was gearing up for the town’s blues festival when the rain started.
“The Environment Agency had said on the Wednesday that there was a possibility the river would flood, [but] this was the summer – we thought the Environment Agency was talking of their bottom,” he said.
The Worcestershire town was supposed to be protected by temporary flood barriers, he said, and thousands of pounds worth of stock was sitting in his cellar.
“They said the barriers would go up on Friday, [but the] rivers started rising late Thursday.”
It was too late to save his stock; the pub flooded waist-high with water.
His wife Claire, their son and three dogs were among those taken by boat through the floodwater.
Image copyright Grahame Bunn
Image caption Grahame Bunn’s wife Claire and their dogs were among those rescued by boat during the flooding in Upton upon Severn
The pub closed for four months and did not fully reopen until February 2008.
“It just devastated not only my business, but the whole of the town,” said Mr Bunn, 58. “I don’t think it has ever recovered.”
While the Bunn family, who lived above the pub, were able to remain there as repairs were carried out, hundreds of thousands of pounds of damage was caused. Mr Bunn got a job working on the gravel barges on the river as the family had no income while the Kings Head was closed.
“We bought the pub in 2000 and knew there was a possibility it was going to flood,” he said. “We had flooded many times before 2007, but this time it was different – we weren’t able to reopen.”
Mr Bunn, who now runs the nearby Ye Olde Anchor Inn, believes improved flood defences installed over the past decade mean the scenes of 2007 will not be witnessed again.
“Hopefully, the horrendous flooding of this town will be a thing of the past.”
Image copyright Grahame Bunn
Image caption Claire Bunn and her husband Grahame, pictured behind the pub, in July 2017
BBC reporter Catherine Mackie
Image caption Catherine Mackie reporting from the scene of flooding in Herefordshire in the summer of 2007
Anyone who experienced the great flood of July 2007 has a story to tell.
I was soaked to the skin, shivering with cold and stranded in a pub car park in Herefordshire.
Inside the pub there was a small crowd of people who’d abandoned their cars on the roads-turned-rivers, resigned to spending an uncomfortable night with strangers.
Our satellite truck had died after the last live broadcast so I bunked down with the crew Andy and Brian in a caravan kindly donated by the landlady.
The rain continued to hammer down on the roof with the noise occasionally drowned out by Brian’s snoring.
‘People were scared for their lives’
Image copyright Getty Images
Image caption Homes and businesses were badly damaged by the floods in Evesham
Floods had been a fairly frequent occurrence in the south-west Midlands, with fire stations in Evesham, Hereford and Worcester equipped with boats to cope with water rescues.
But nothing could prepare crews for the rain of July 2007.
Firefighter Dave Hunt was on duty when his team received the call that Sedgeberrow, near Evesham, was flooding.
“There was a lot of rain so we were having a number of calls and then the call came in to Sedgeberrow,” he said.
Two boats were sent to the village from Worcester fire station.
Image copyright Getty Images
Image caption A water rescue is carried out in Evesham
Crews arrived to discover two men on the roof of a Ford Transit van.
“They were clinging on to the roof and the van was submerged,” recalls Mr Hunt. “We launched the boats and the priority was to save them and bring them back to land.”
Some rescues proved tricky, with crews unable to see house numbers or road names and, with lives on the line, decisions had to be made to prioritise those at greatest risk.
“We made several rescues of people and pets, there were about 90 flooded homes and we made rescues from 30 of the houses,” added Mr Hunt.
“The most memorable rescue which we carried out was in liaison with the RAF helicopter of a pregnant lady and her toddler. They were trapped in floodwater.
“The RAF Sea King lowered and winched down. The toddler was rescued on a board. The winchman entered the bedroom and harnessed the pregnant lady and they both got winched up into the helicopter.”
He described the floods as on a scale never seen before.
“People were scared for their lives [and] I would say a number of them were in danger of losing their lives,” said Mr Hunt.
“We had never dealt with anything like it. That’s the worst I’ve ever seen.”
Read more: http://ift.tt/2uK18iv
The post The wettest summer on record – 10 years on from the 2007 floods – BBC News appeared first on MavWrek Marketing by Jason
http://ift.tt/2toHsNi
0 notes